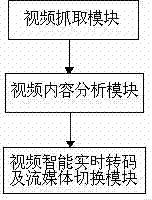
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
206 results about "Traffic flow analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Traffic flow analysis is the process of measuring the bandwidth usage on a network and analyzing the data for the purpose of performance tuning, capacity planning, and making hardware improvement decisions. Traffic flow analysis is done using traffic flow analysis software.
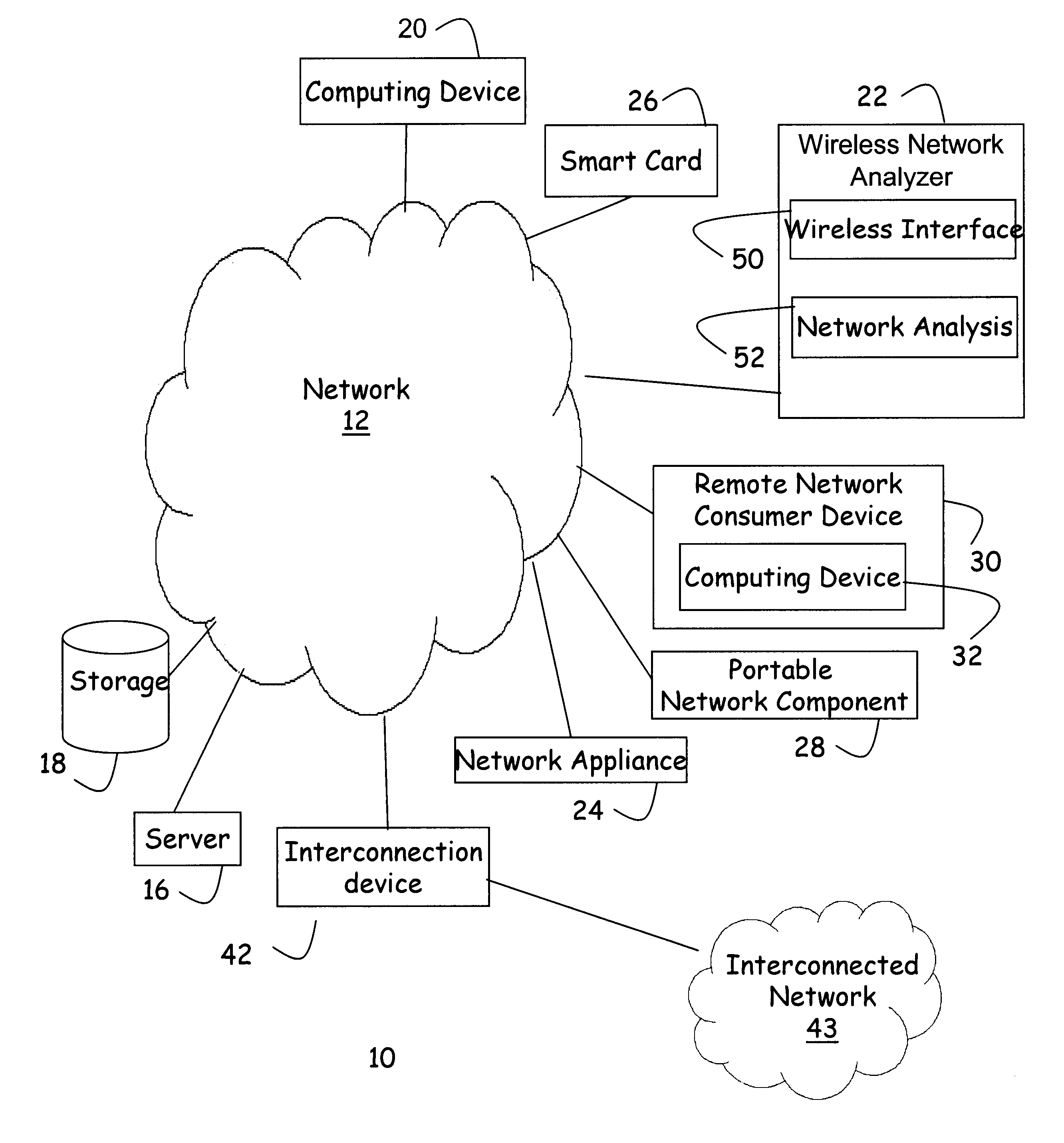
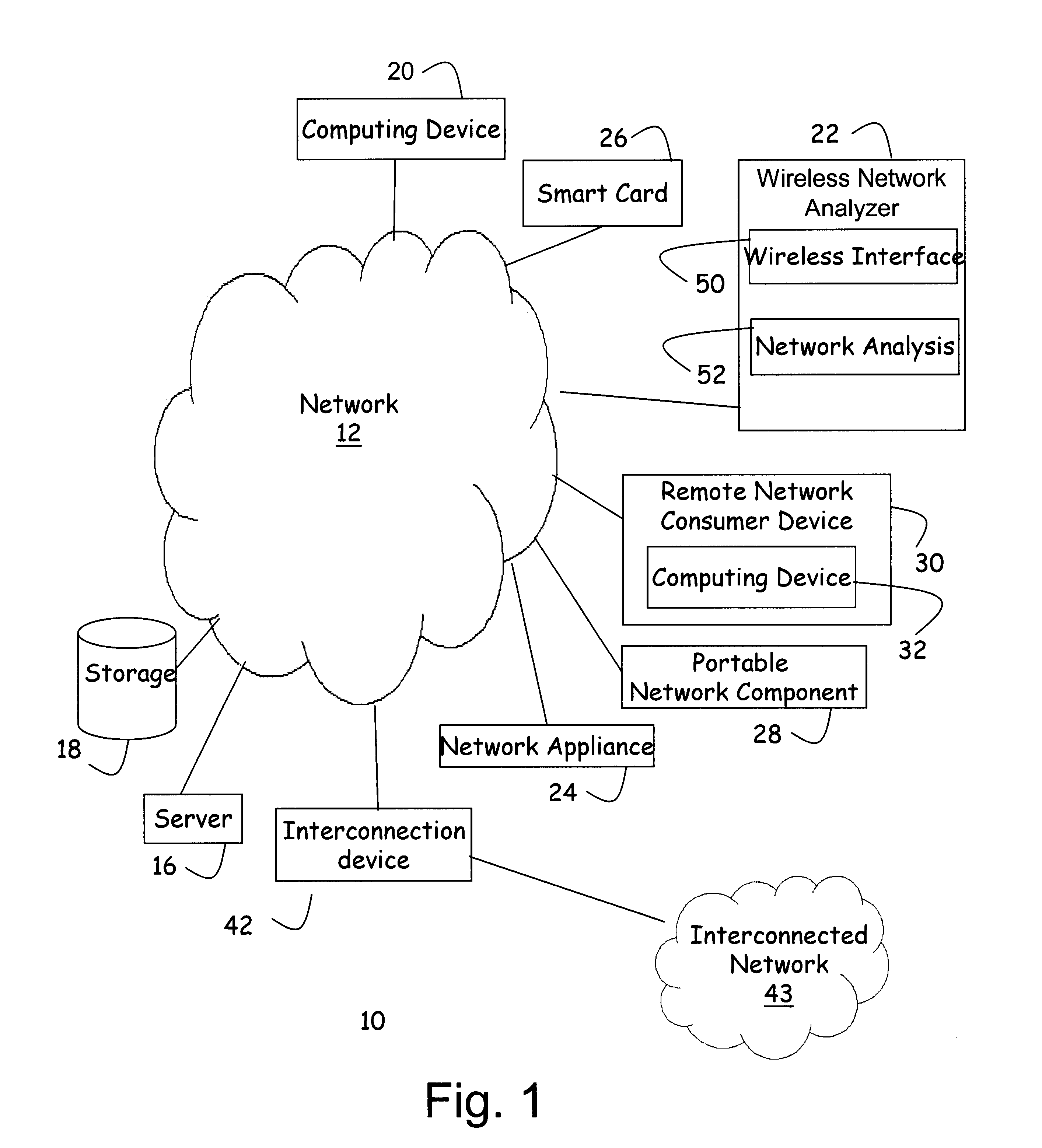
Portable computing device and associated method for analyzing a wireless local area network
Aspects of the invention are found in an apparatus for monitoring data on a wireless network. The data is transmitted according to a wireless data network protocol across the network. The apparatus is contained on a portable wireless network analysis device. The portable wireless network analysis device has a wireless network interface that communicatively couples the portable wireless network analysis device to the wireless network. This allows the portable wireless network analysis device to receive data from the wireless network. The portable wireless network analysis device also has a network traffic analyzer. The network traffic analyzer is communicatively coupled to the wireless network interface. The analyzer receives and analyzes the data received from the wireless network. The portable wireless network analysis device is capable of being operated by user at one location and transported to second location. The portable wireless network analysis device is able to continue to monitor data on the wireless network while being transported from the first location to the second location. The apparatus may also have a user interface. Information about the data may be displayed on the user interface. In a specific instance, the user interface is a display screen. The apparatus can have a storage system. The storage system stores the data when initiated by a user. The apparatus can also have a filter system. The filter system filters the data based on a predefined criteria. The apparatus may have an alarm system. The alarm system indicates when a predefined network event has occurred.
Owner:MCAFEE LLC
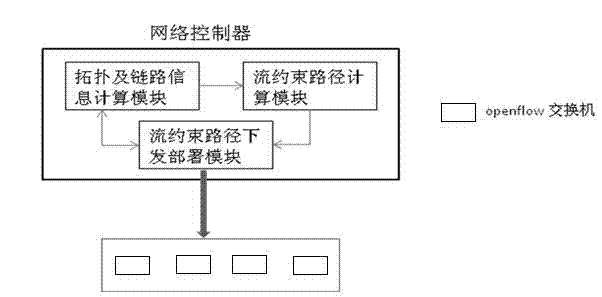
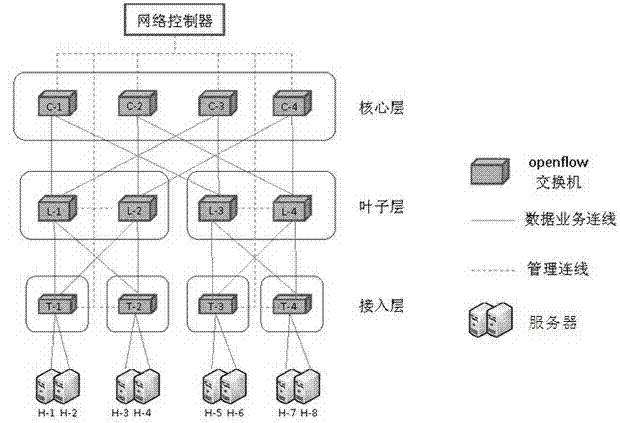
Data center flow control method and data center flow control system based on openflow
InactiveCN103179046AIncrease profitHigh precisionData switching networksTraffic capacityTraffic flow analysis
The invention discloses a data center flow control method and a data center flow control system based on openflow. Openflow switchboards are controlled to operate a topology discovery protocol through a network controller, so tha information of all network nodes and links is collected and a network topology value is calculated; and the network controller periodically carries out end-to-end flow analysis on flows, calculates optimized paths of all the flows and transmits the optimized paths to each openflow switchboard, monitors the states of all the network links in real time, and maintains or downloads the optimized paths of the new flows to each openflow switchboard, so that the use rate of network bandwidth resources and the accuracy and the reliability of network concentrated management can be improved, the variation of the network flow can be fitted by sensitively regulating a flow load in a network, and the use rate and the reliability of the network can be effectively improved. The data center flow control method and the data center flow control system based on the openflow has a good application prospect.
Owner:深圳数字动能信息技术有限公司
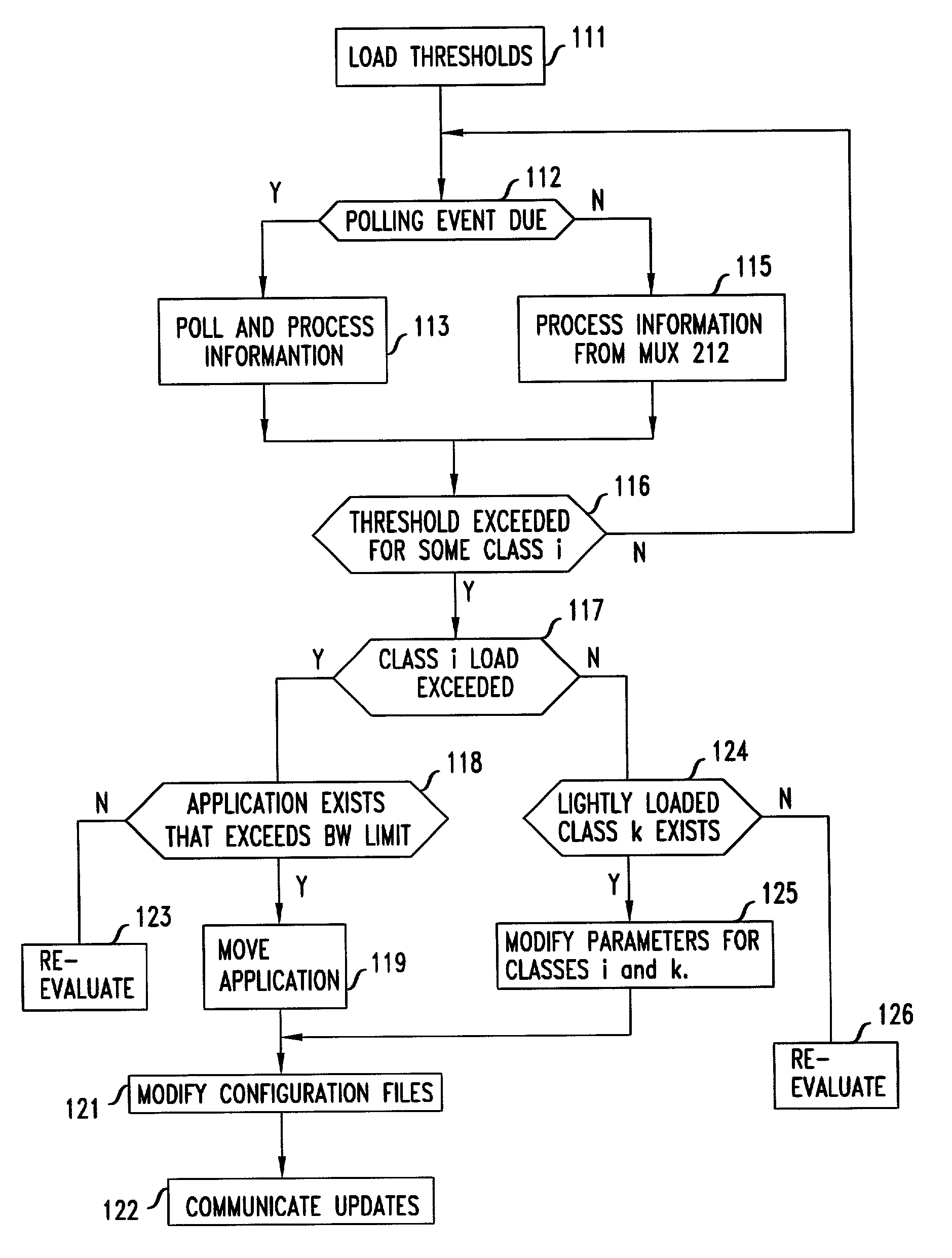
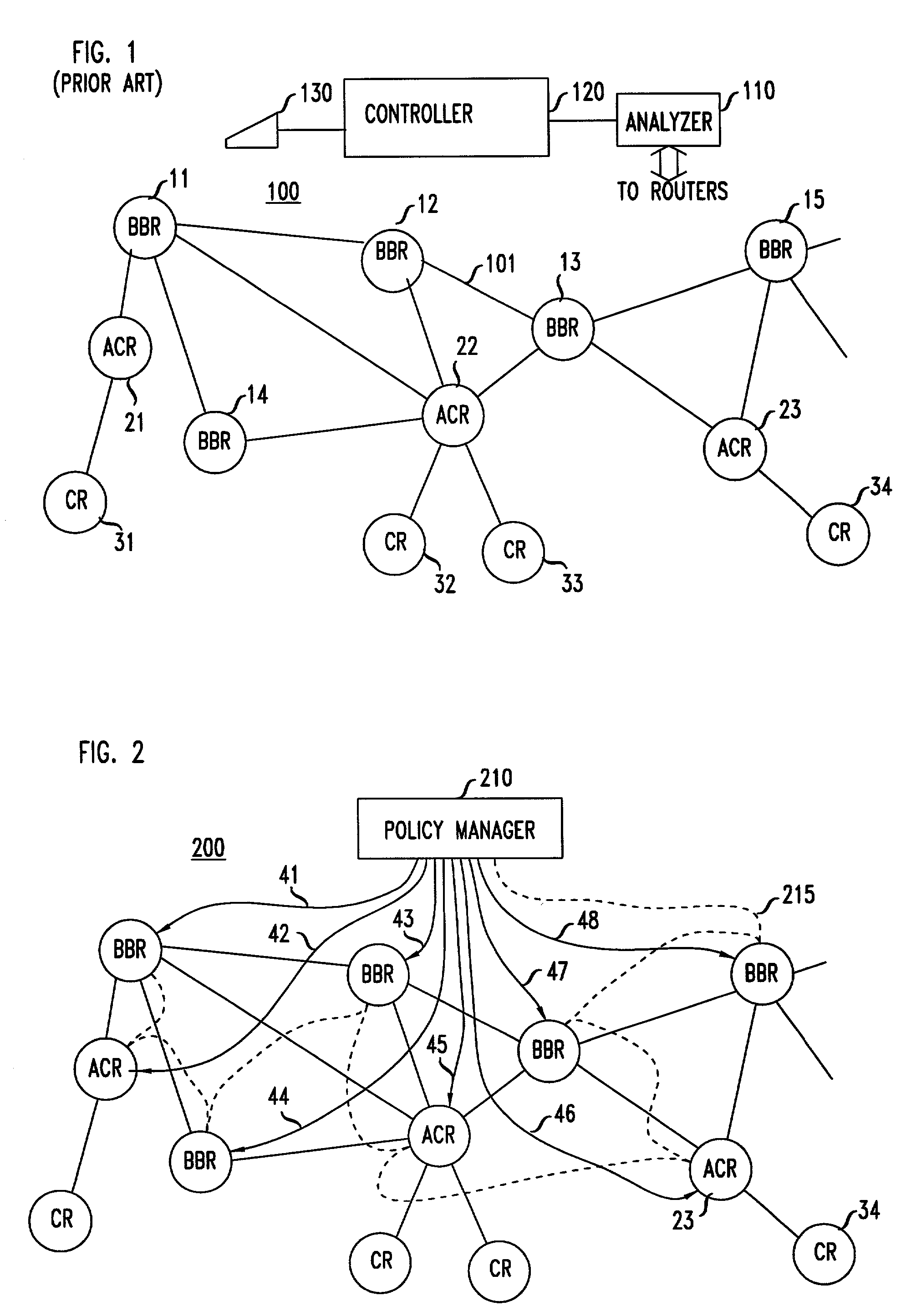
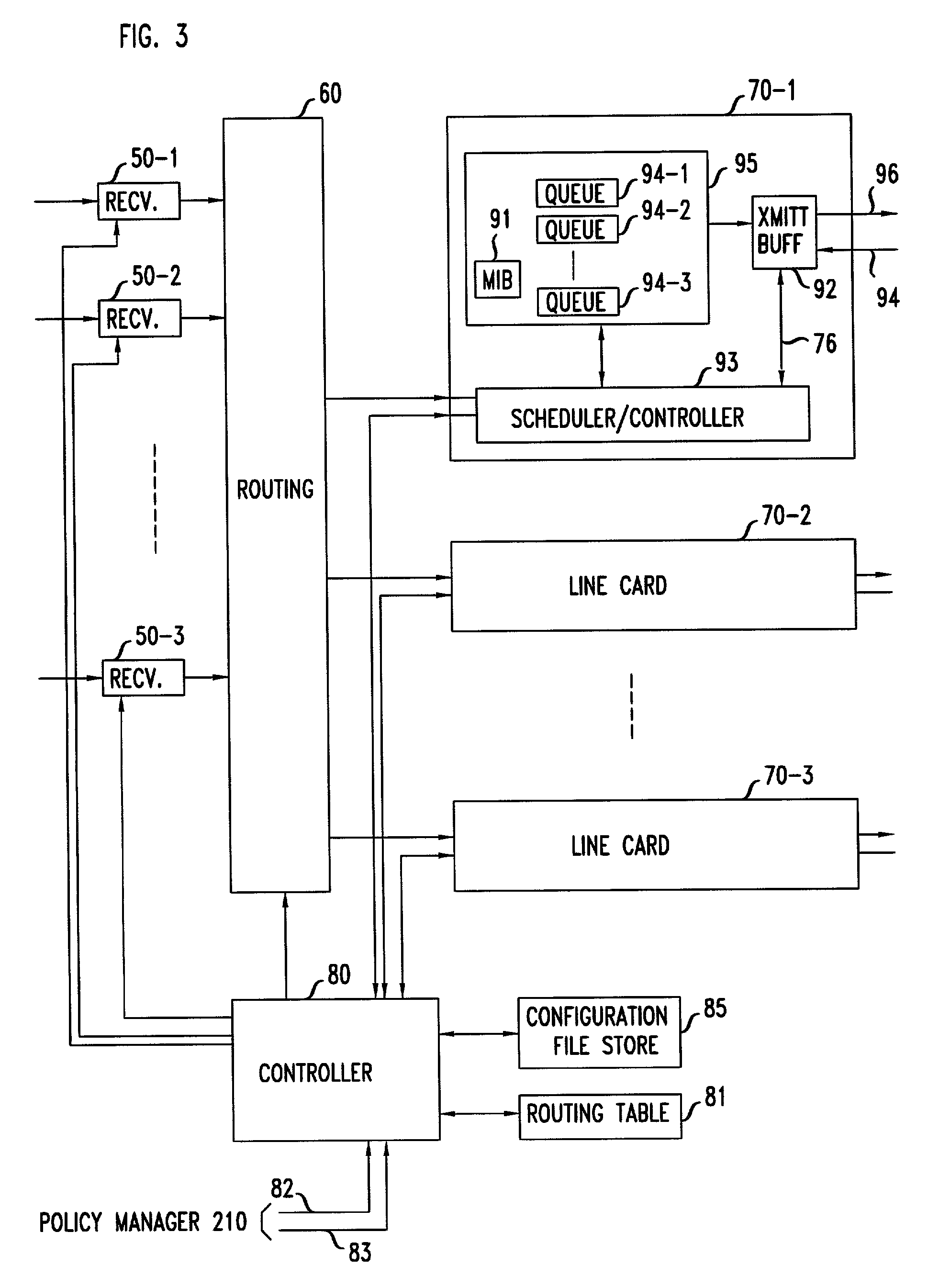
Automatic router configuration based on traffic and service level agreements
An arrangement where a policy manager automatically generates configuration file updates for the routers in the network, as necessary, sends those updates to the appropriate routers, and causes the routers to install the configuration file updates in real-time. The automatic generation of configuration file updates is carried out in response to information that is delivered to the policy manager from a traffic measurement and flow analysis system that replaces the prior art analyzer system. The information that is generated by the traffic measurement and flow analysis system is sensitive to thresholds that the policy manager installs in the traffic measurement and flow analysis system.
Owner:SERVICENOW INC
Performance and flow analysis method for communication networks
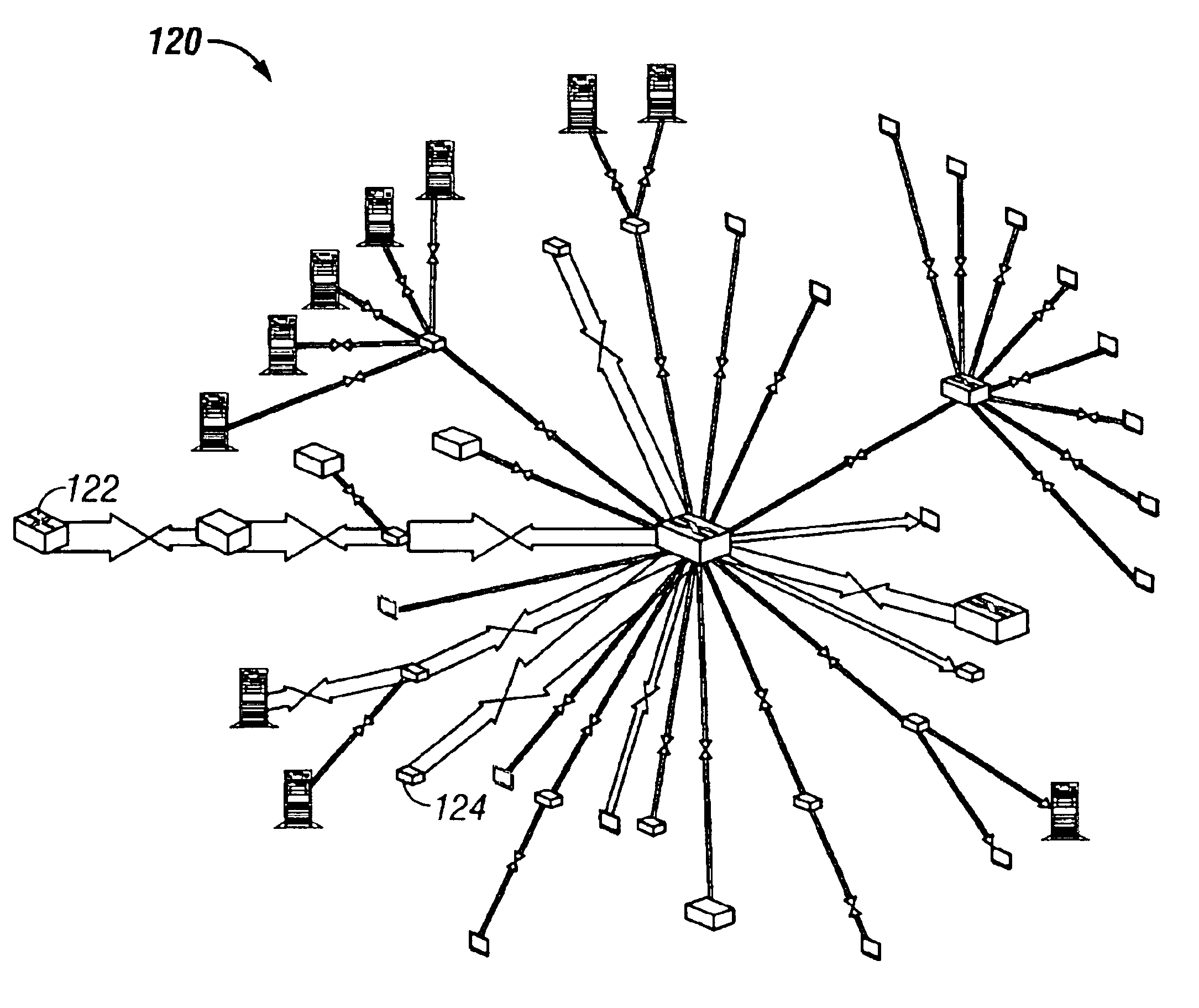
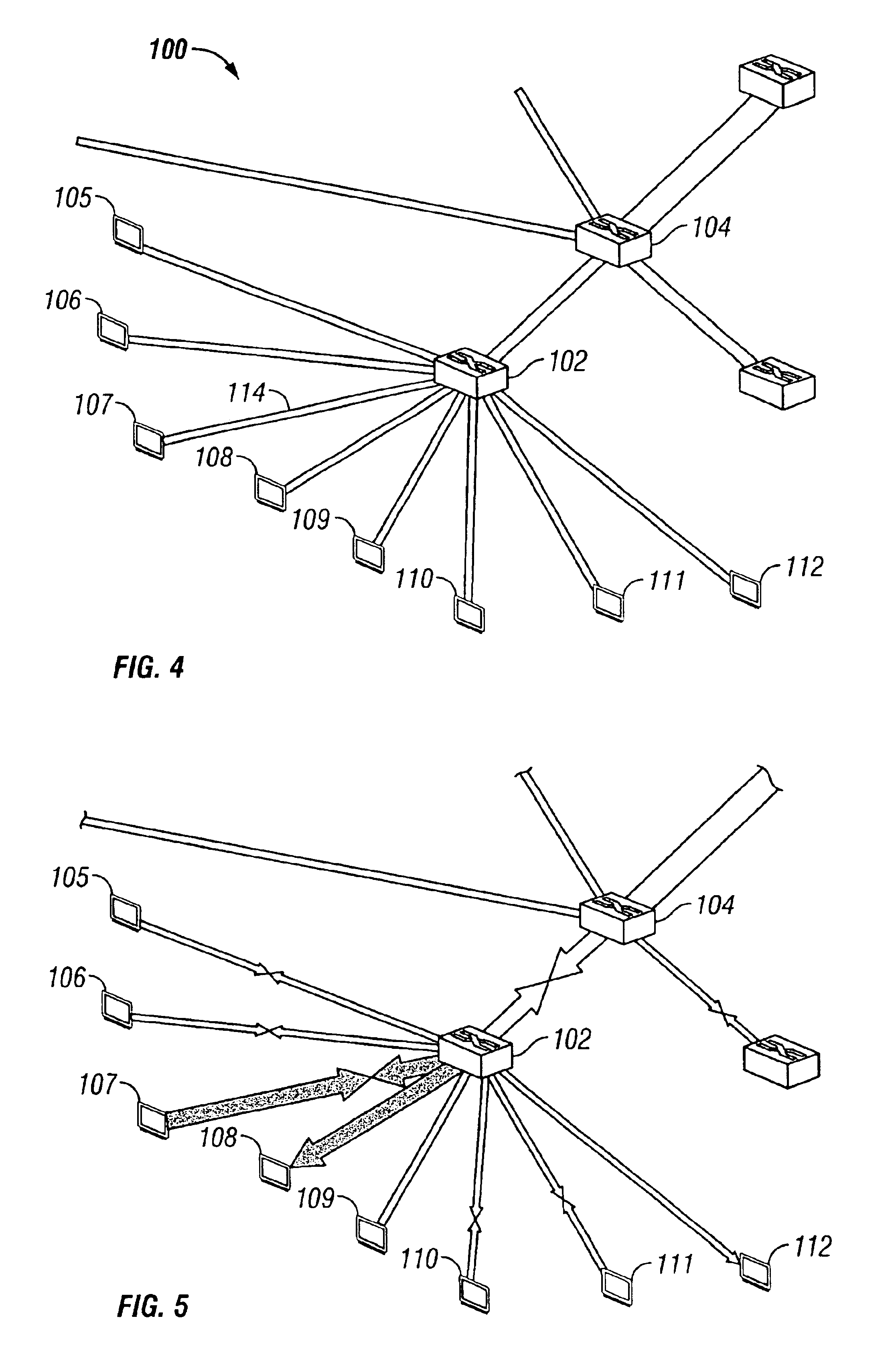
A system and method are used for visually representing performance and flow analysis of a communication network having devices connected by links. The system includes a first memory for storing a graphical representation of the communication network and showing the devices connected by links and a second memory storing data representing performance and flows in the communication network. A processing system is operatively connected to the first and the second memory and to a display. The processing system selectively maps the data on the graphical representation of the communication network by varying visual characteristics of the devices and the links for viewing on the display.
Owner:BMC SOFTWARE
System, method and apparatus for preventing transmission of data on a network
InactiveUS20010039623A1Interfere operationInterfere useEnergy efficient ICTMemory loss protectionTraffic capacityTraffic flow analysis
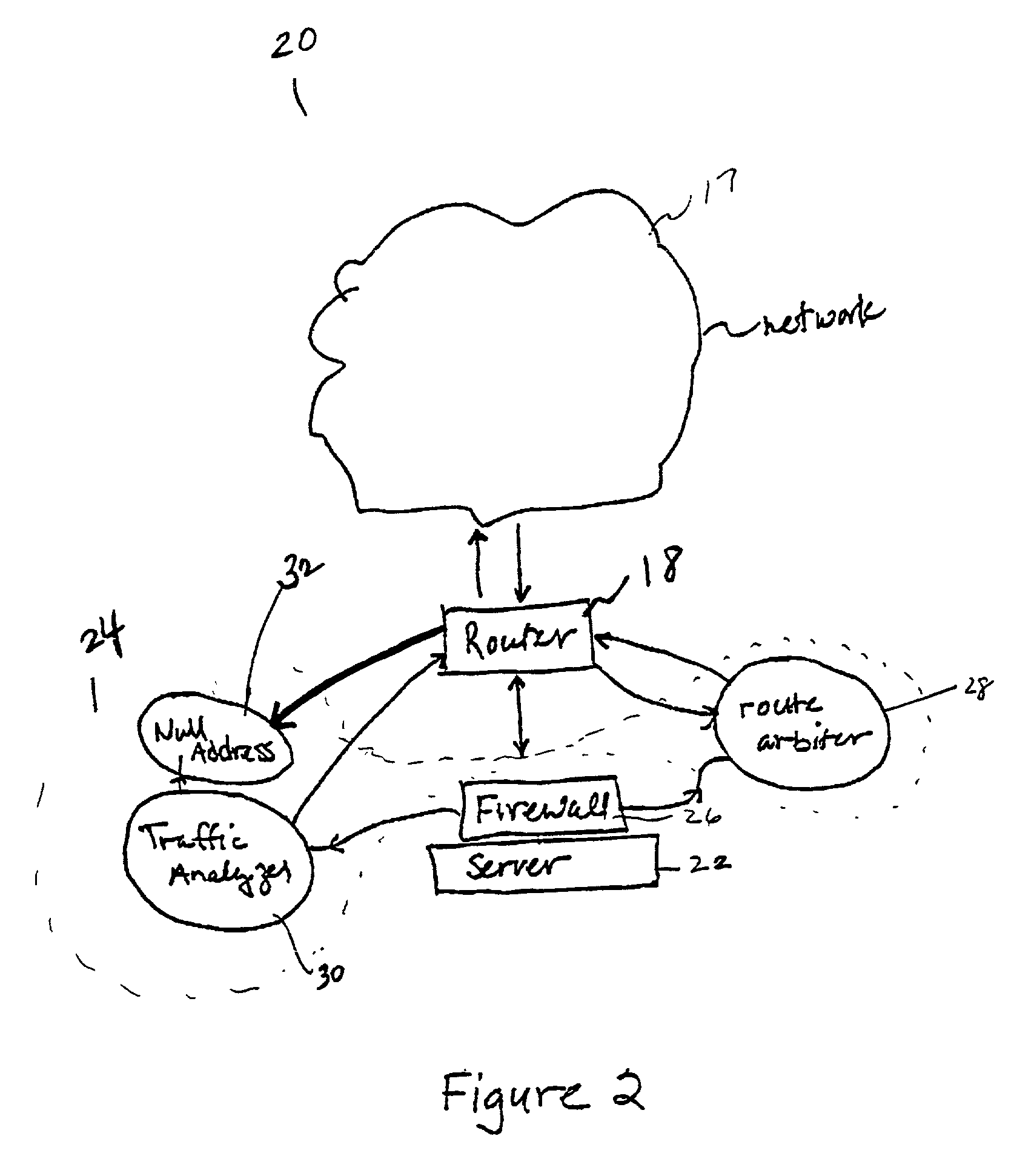
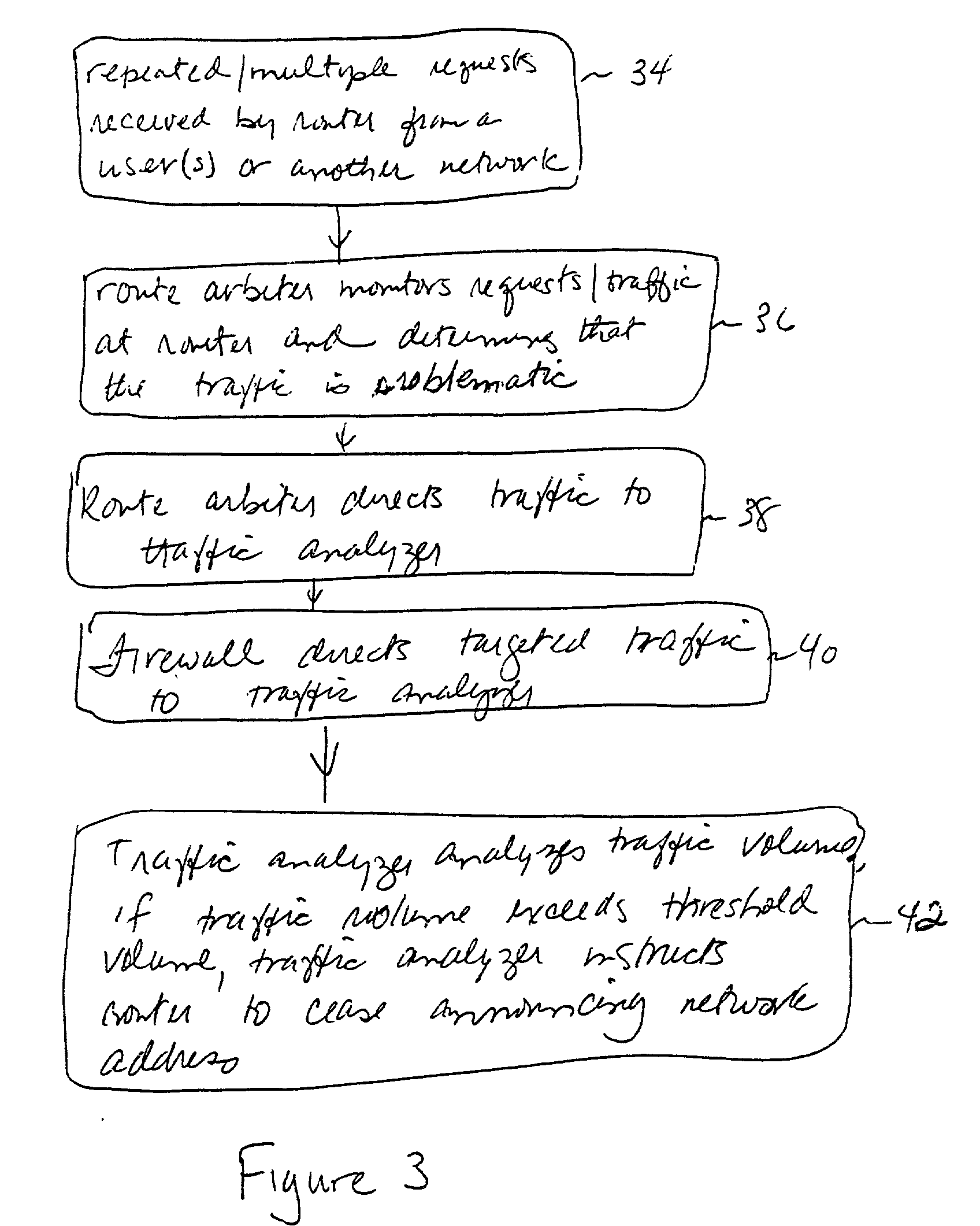
Embodiments of the invention are directed to a detection system, method and apparatus that identifies and eradicates fraudulent requests on a network. Embodiments of the detection system comprise at least one router, a server, and an activity monitoring system. The activity monitoring system comprises a route arbiter and a traffic analyzer, wherein the route arbiter monitors the activity on the router. The route arbiter continuously monitors the router and firewall device to determine if abnormal activity or traffic patterns are emerging. If a determination is made that abnormal activity or abnormal traffic patterns exist, the activity monitoring system responds by blocking the activity or redirecting the traffic.
Owner:IRDETO USA
Traffic flow surveying and handling method based on unmanned aerial vehicle high-definition video
ActiveCN103413444AHigh precisionOvercome inherent difficultiesImage analysisDetection of traffic movementHigh-definition videoSignal timing
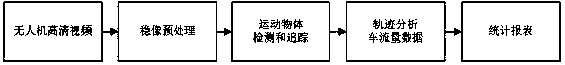
The invention provides a traffic flow surveying and handling method based on an unmanned aerial vehicle high-definition video. The method comprises the steps of video capture, wherein an unmanned aerial vehicle is made to hover over a selected urban road intersection for high-definition video shooting; image stabilization and pre-processing, wherein the high-definition video is copied, stabilization and pre-processing are carried out on images, and then an image sequence is output; detection and tracking, wherein detection and tracking are carried out on moving objects with the image sequence treated with image stabilization as source data; analysis and statistics, wherein traffic flow analysis and statistics are carried out on a target ID which is tracked down and the current coordinates of motion; output, wherein traffic flow statistical data are transmitted to a client-side graphical interface for display, and then data and statements are generated. The traffic flow surveying and handling method based on the unmanned aerial vehicle high-definition video is capable of obtaining various high-accuracy traffic data, reducing the workload of field survey remarkably, preventing the traffic from being affected, obtaining statistic data of all traffic flows in twelve directions of the intersection, and providing data support for congestion control such as intersection signal timing optimization and traffic channeling improvement.
Owner:SHENZHEN WISESOFT TECH DEV
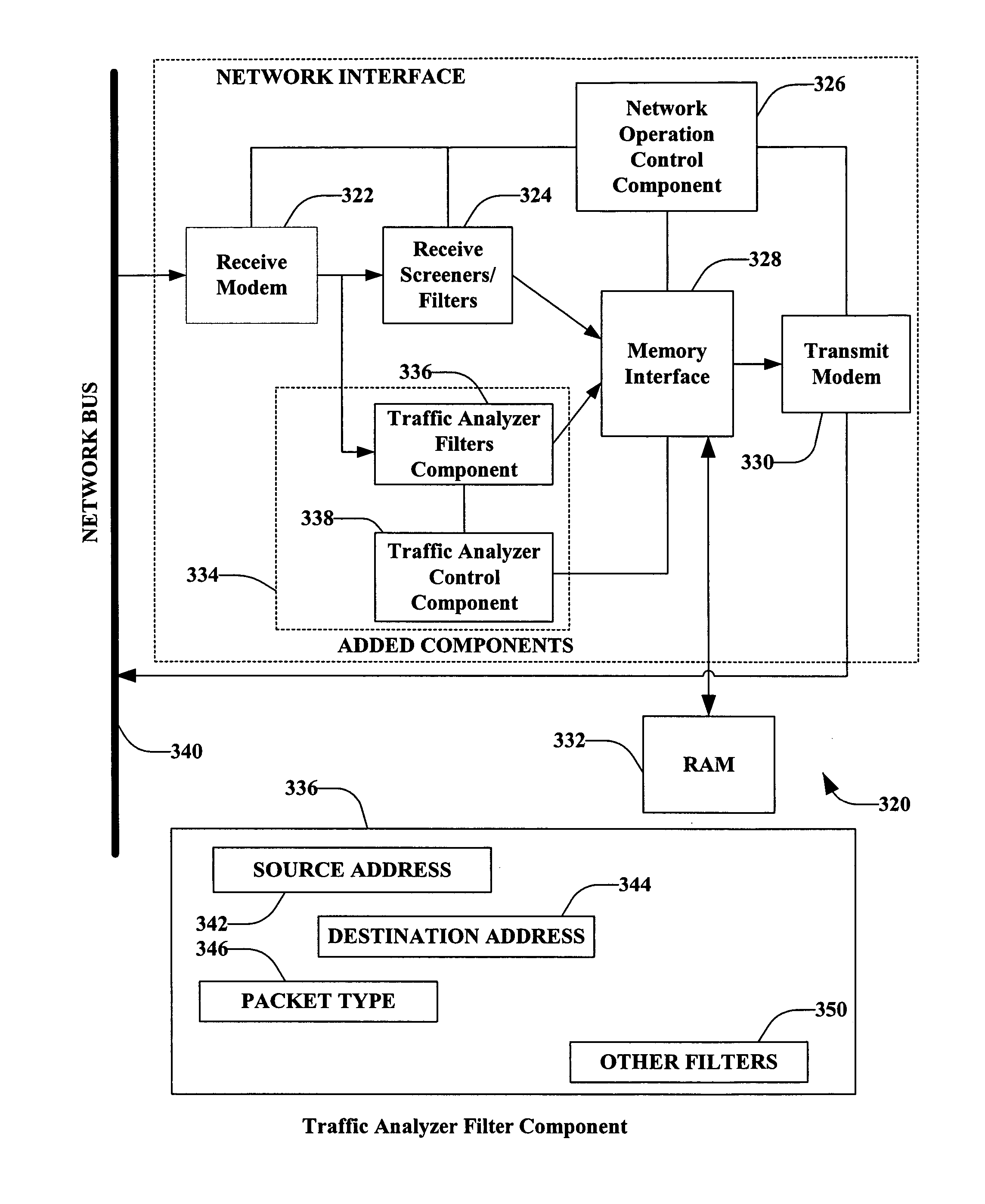
Embedded network traffic analyzer
InactiveUS20050071445A1Simple interfaceReduce disadvantagesError preventionFrequency-division multiplex detailsTraffic capacityTraffic flow analysis
The present invention provides a system and method for interfacing to a network. The system includes a network interface comprising an embedded network traffic analyzer (NTA) capable of network traffic analyzer filter and capture capabilities. The NTA also includes an artificial intelligence component that facilitates diagnosing and / or prognosing state and / or health of the network (and / or components thereof).
Owner:ROCKWELL AUTOMATION TECH
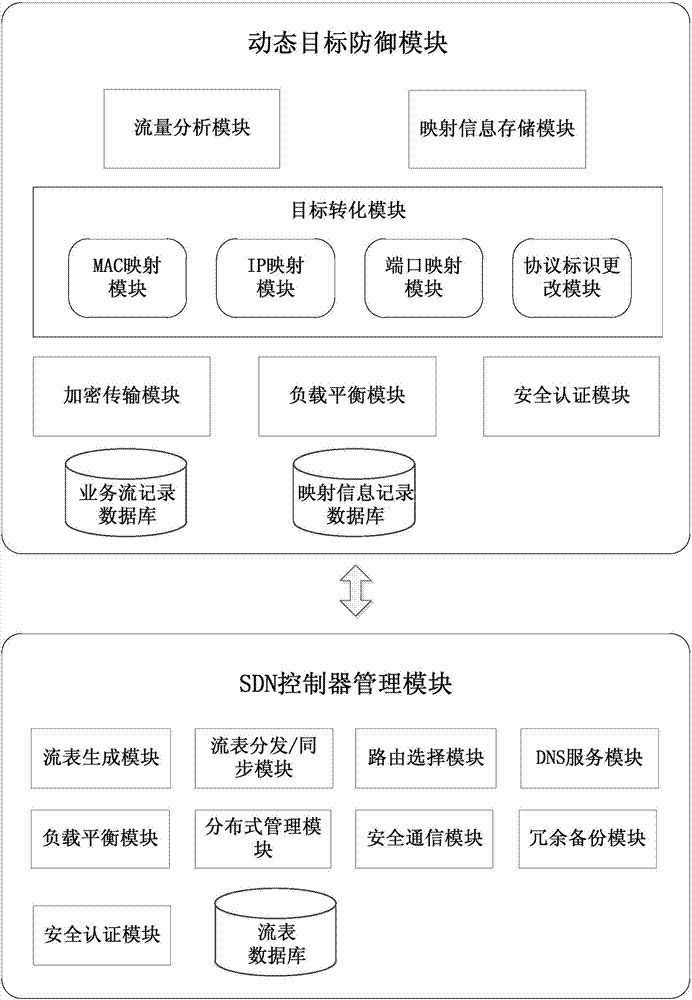
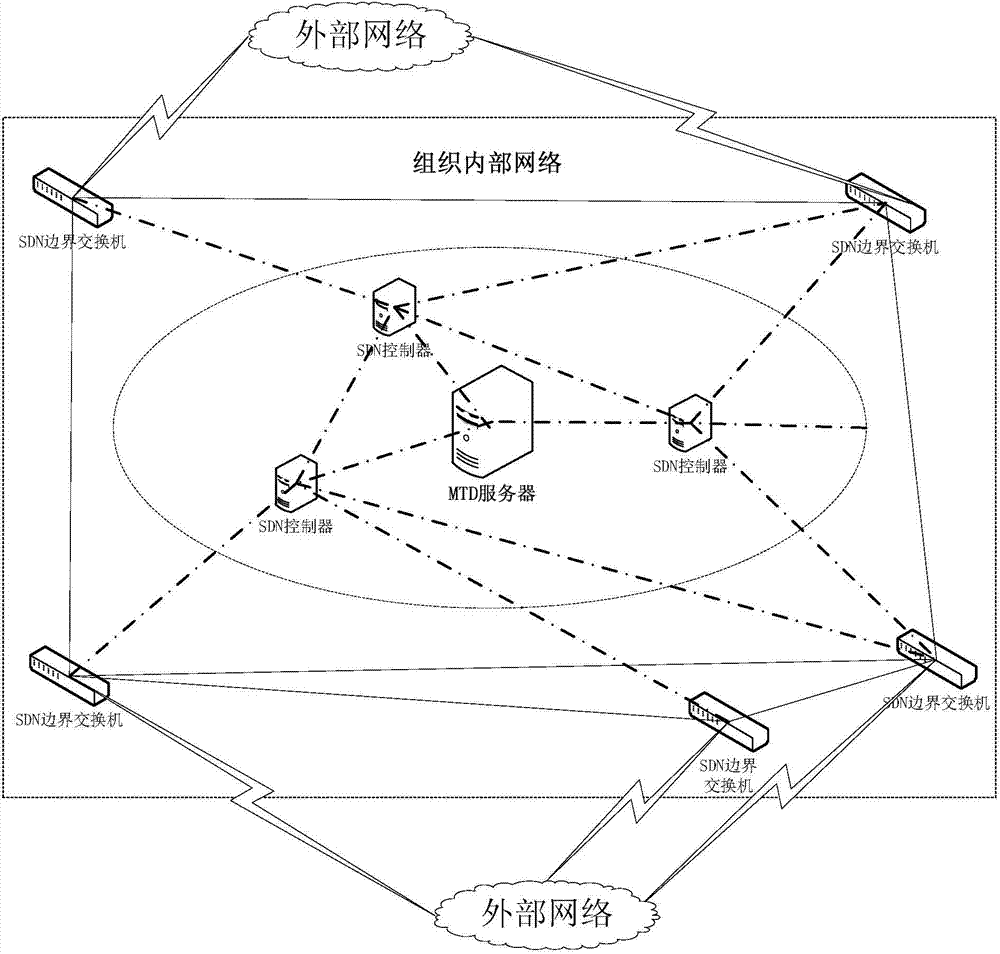
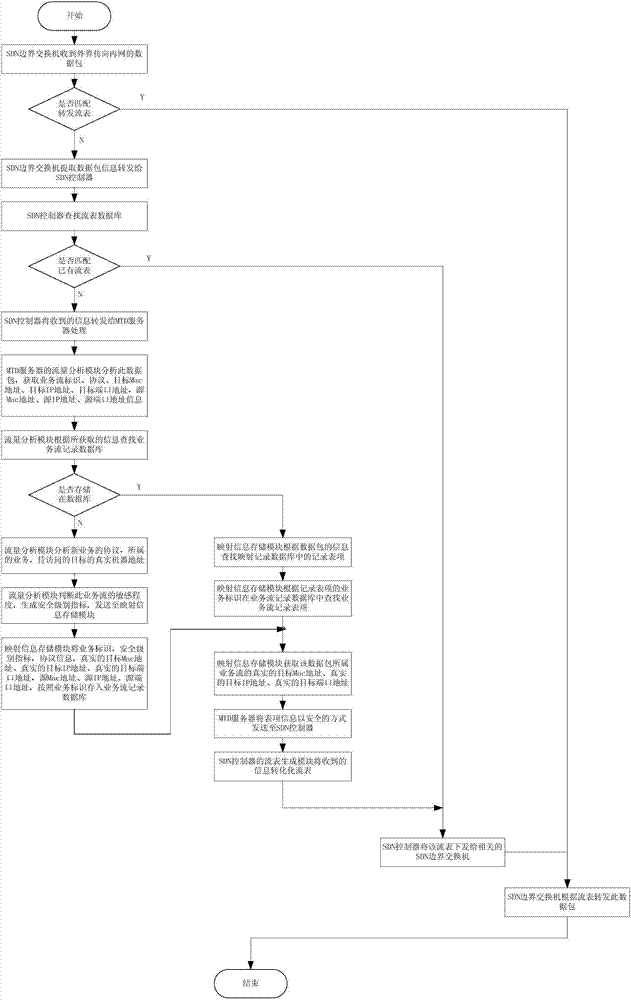
Moving target defense system and moving target defense method for SDN (self-defending network)
InactiveCN104506511AProtection securityIncrease the difficultyTransmissionTraffic flow analysisSafety Communications
The invention discloses a moving target defense system for an SDN (self-defending network). The system consists of a moving target defense module and an SDN controller management module; the moving target defense module comprises a flow analysis module, a mapping information storage module, a target conversion module, an encryption transmission module, a load balance module, a safety authentication module, a business flow recording database and a mapping information recording database; the SDN controller management module comprises a flow table generation module, a flow table distribution / synchronization module, a route selection module, a DNS service module, a load balance module, a distributed management module, a safety communication module, a redundant backup module, a safety authentication module and a flow table database; furthermore, the invention also discloses a moving target defense method for the SDN. Through the moving target defense system and the moving target defense method disclosed by the invention, the difficulty of an attacker to detect a target is increased further, and therefore the safety of an intranet is comprehensively protected.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
Distributed Flow Analysis
ActiveUS20090310491A1Error preventionFrequency-division multiplex detailsTraffic flow analysisStreamflow
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
Method and system for recommending mobile video based on flow analysis and user behavior analysis
ActiveCN103051930ASolve the recommendation is not smart enoughSolve the real problemSelective content distributionSpecial data processing applicationsBehavioral analyticsTraffic flow analysis
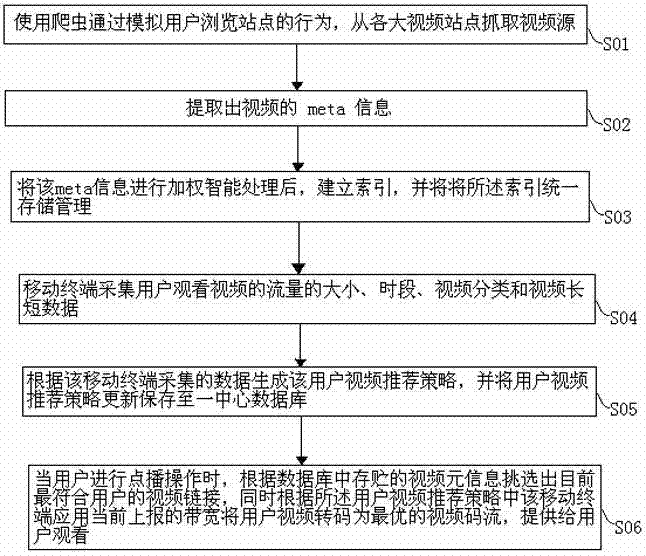
The invention relates to a method and a system for recommending a mobile video based on flow analysis and user behavior analysis. The method comprises the following steps of: capturing a video source from major video stations by simulating a station browsing behavior of a user by using a crawler; extracting the meta information of a video; intelligently weighting the meta information, and establishing an index; generating a user video recommendation policy according to data acquired by a mobile terminal; and when the user performs on-demand operation, transcoding a user video into an optimum video code stream according to a reported bandwidth applied by the mobile terminal in the user video recommendation policy, and providing the video code stream for the user for watching. The invention has the advantages that the optimum video code stream can be obtained by real-time transcoding according to the flow using habit of the user, a dynamic change video recommendation policy of a video on-demand behavior and the current customization flow package of the user, and then provided for the user for watching, so the problem of over-high flow cost for watching stream media by the user in the prior art is solved to a certain extent, and user experience is improved.
Owner:CHINA YOUKE COMM TECH
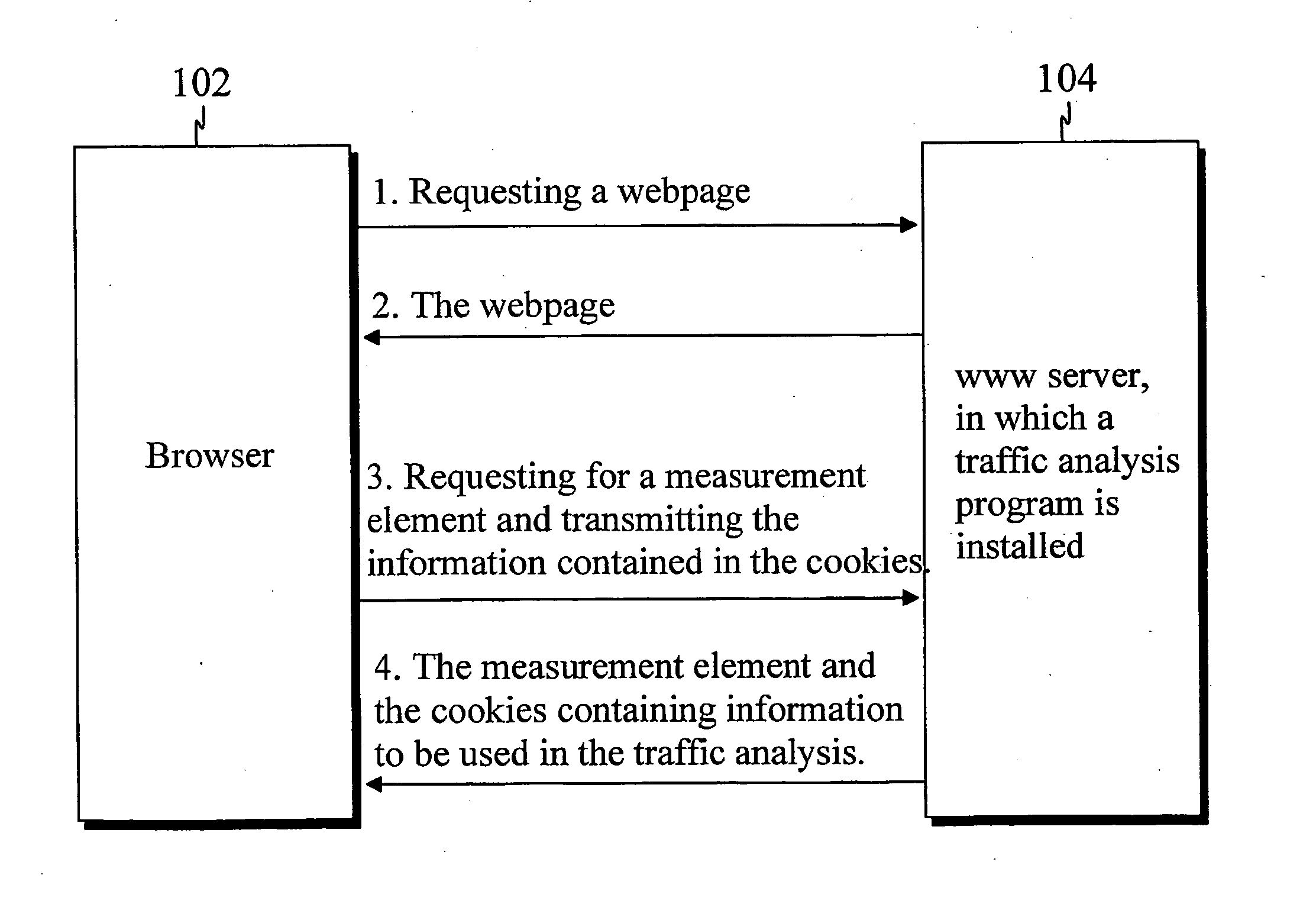
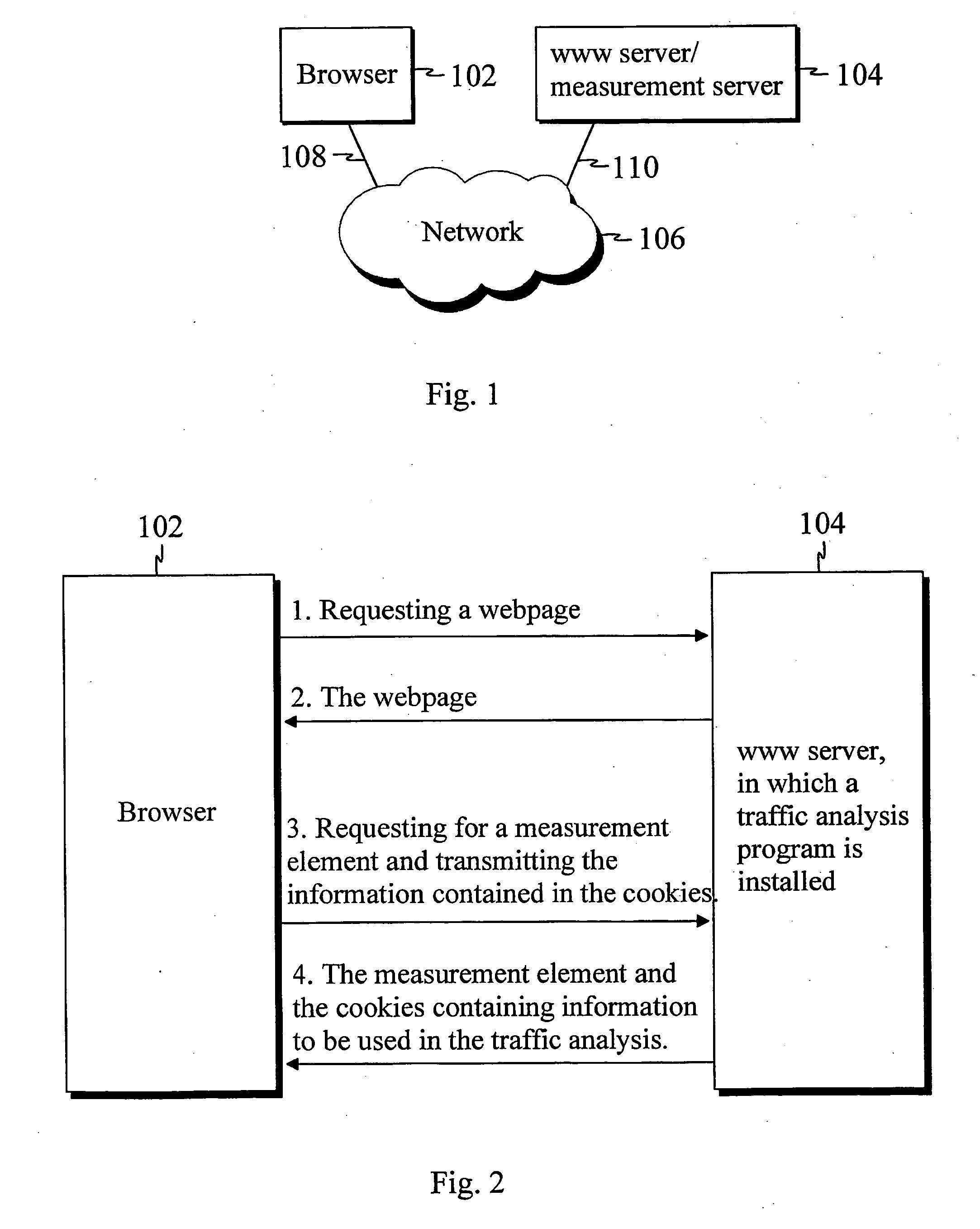
Traffic flow analysis method
InactiveUS20050021731A1Improve measurement reliabilityFast and reliableMultiple digital computer combinationsData switching networksTraffic flow analysisInterpreted language
The present invention describes a method for collecting visitor information in a distributed browser-based traffic analysis system. The method comprises the steps of: receiving a request with a content server from a network element for an interpreted language page content; receiving the interpreted language page content, the interpreted language page content having at least one measurement code comprising a measurement element source attribute specifying a measurement program; receiving a request for the source data of the measurement element, the request comprising at least one data structure including at least one of at least one page ID and at least one category ID and at least one time stamp and other relevant data; comparing the content of the fields of the data structure(s) to a predefined set of rules in the measurement program; updating the counters or other programming structures in the measurement program based on the comparison; updating the data structure(s), and providing the network element with the updated data structure(s) and the source data for the measurement element.
Owner:INTERQUEST
Method for detecting and monitoring gusty abnormal network flow
InactiveCN1764126ASolve the blockageImprove stabilityData switching networksTraffic flow analysisMonitor equipment
The detection and monitor method for burst abnormal network flow comprises: simulating and realizing the worm attack on NS-2 network simulator platform and DDoS distributed denial service attack, gathering the network flow information by Net Flow protocol, determining the behavior character of abnormal source, and taking control measures to interrupt attack. This invention originates to integrates character comparison and flow self-learning, overcomes the problem that SNMP protocol is lack for analysis and hard to determine flow abnormal threshold, and improves efficiency and practicality of monitor flow greatly. The experiment shows: this method is very well in real-time, and lays the foundation of inverse track well.
Owner:SHANGHAI JIAO TONG UNIV
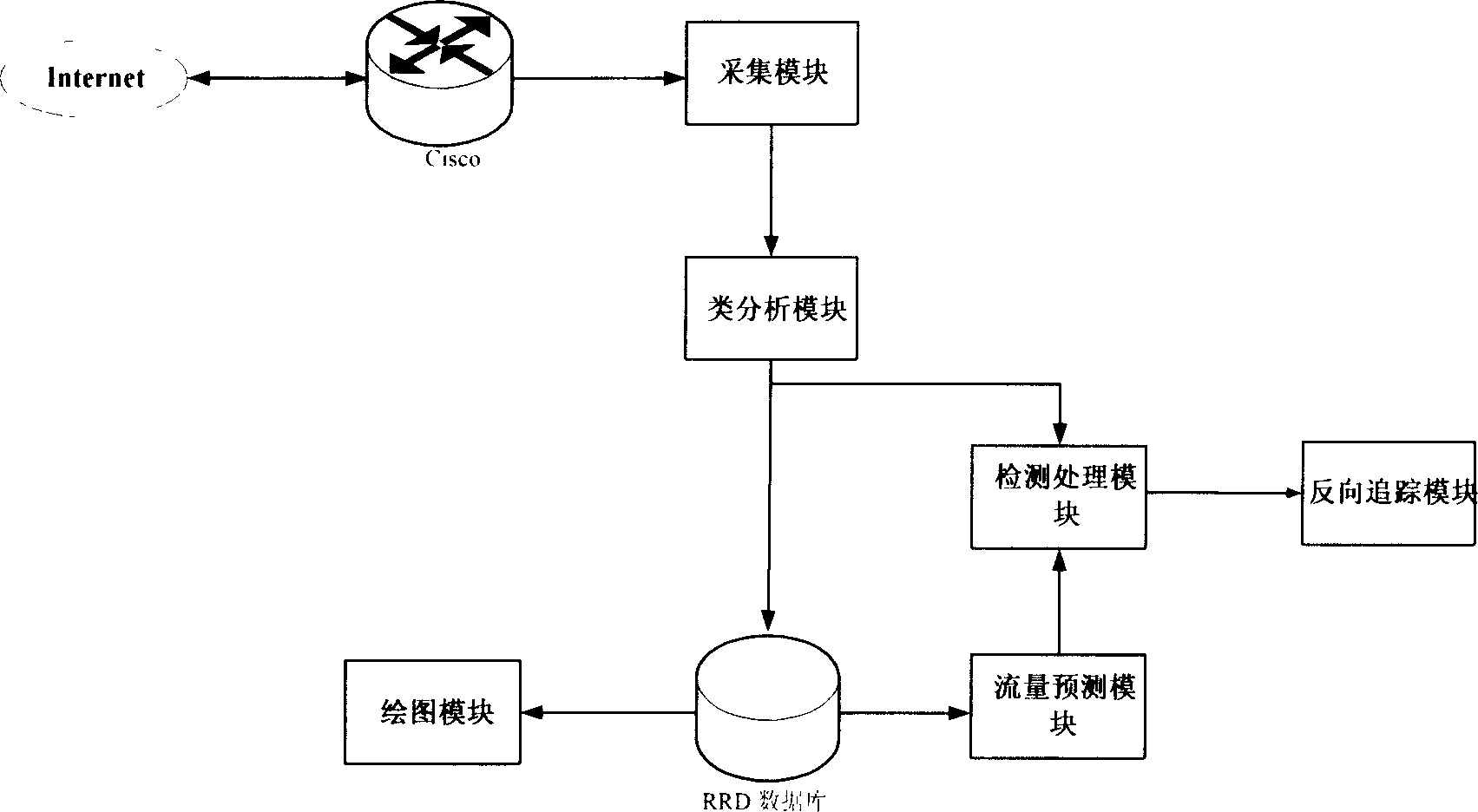
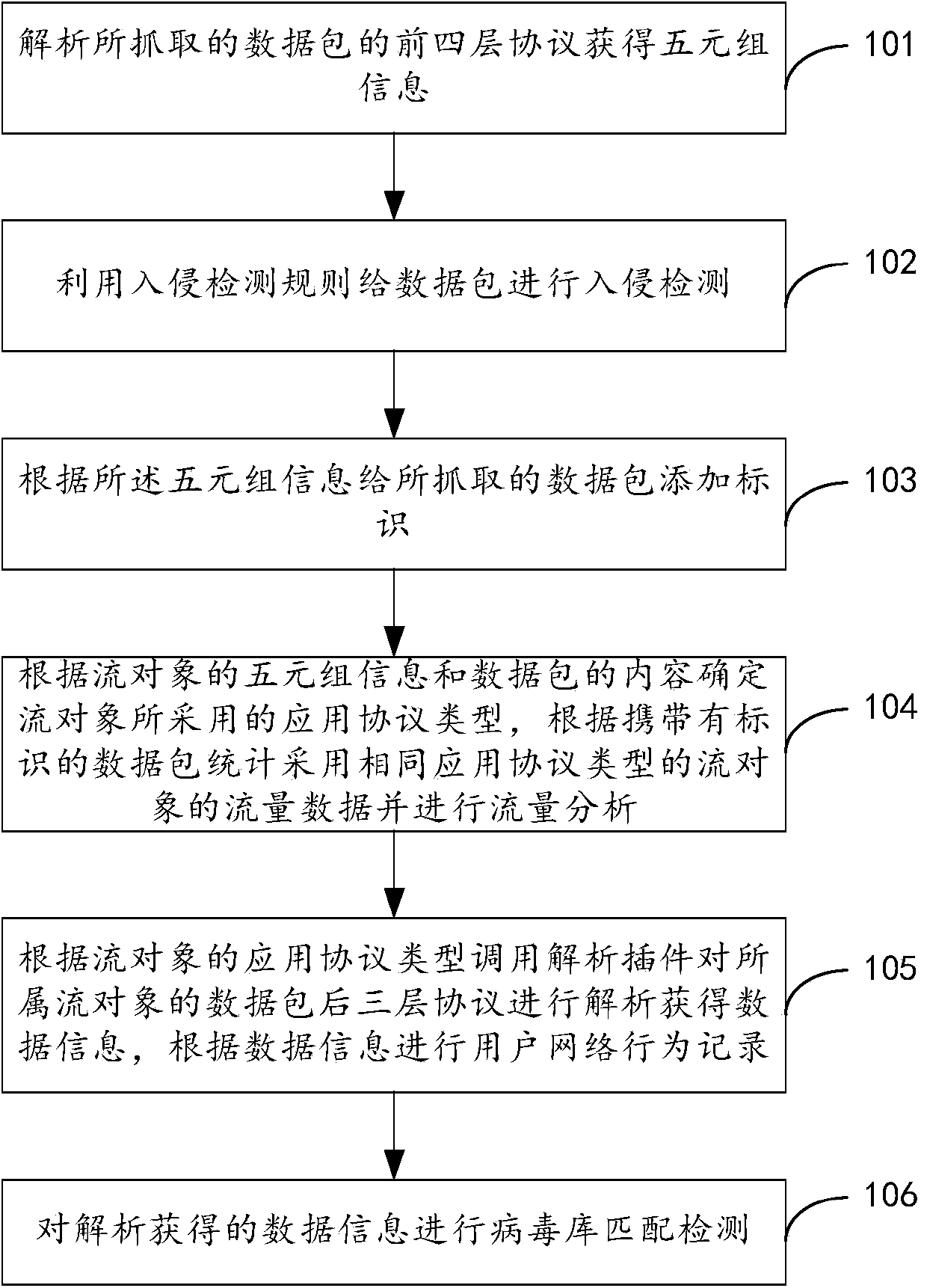
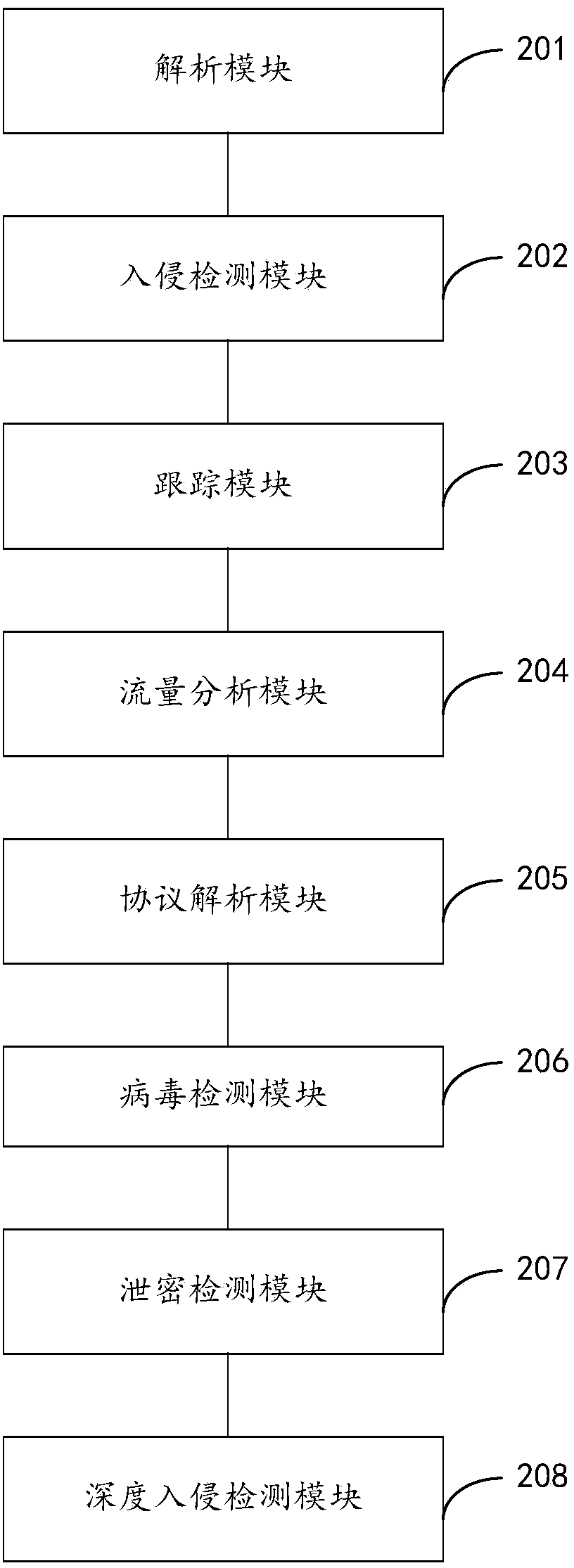
Network security detection method and system
The invention provides a network security detection method and system. First four layers of a protocol of a capture data packet are analyzed to obtain quintuple information; an intrusion detection rule is used to carry out intrusion detection to the data packet; the quintuple information is used to add an identifier to the captured data packet; according to quintuple information of a stream object and a content of the data package, an application protocol type applied in the stream object is determined; according to the data packet with the identifier, flow data of the stream object using the same application protocol type is calculated and undergoes flow analysis; according to the application protocol type of the stream object, an analysis plug-in is used to analyze a data packet application layer protocol of the corresponding stream object so as to obtain data information; according to the data information, a user network behavior record is carried out; and the obtained data information obtained by analyzing is detected by matching a virus database. The intrusion detection, the network behavior detection, the abnormal flow analysis and the virus detection are integrated in one system, and only one interface is needed to realize multiple detection methods of the network access.
Owner:BEIJING TOPSEC SOFTWARE +3
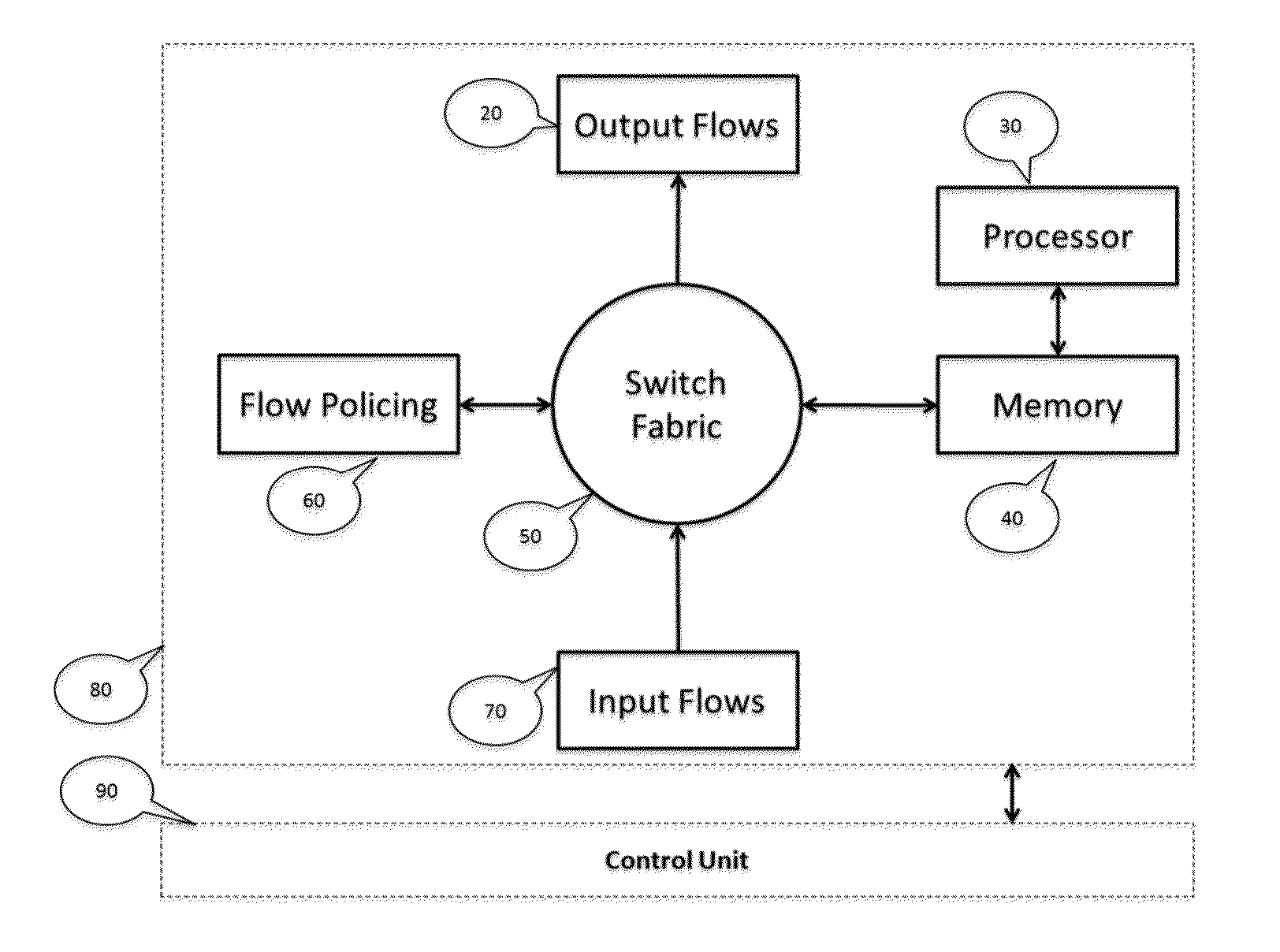
Programmable switching engine with storage, analytic and processing capabilities
InactiveUS20150063349A1Good varietyEasy to manageMultiplex system selection arrangementsCircuit switching systemsStructure of Management InformationMulti dimensional
An improvement to the prior-art extends an intelligent solution beyond simple IP packet switching. It intersects with computing, analytics, storage and performs delivery diversity in an efficient intelligent manner. A flexible programmable network is enabled that can store, time shift, deliver, process, analyze, map, optimize and switch flows at hardware speed. Multi-layer functions are enabled in the same node by scaling for diversified data delivery, scheduling, storing, and processing at much lower cost to enable multi-dimensional optimization options and time shift delivery, protocol optimization, traffic profiling, load balancing, and traffic classification and traffic engineering. An integrated high performance flexible switching fabric has integrated computing, memory storage, programmable control, integrated self-organizing flow control and switching.
Owner:ARDALAN SHAHAB +1
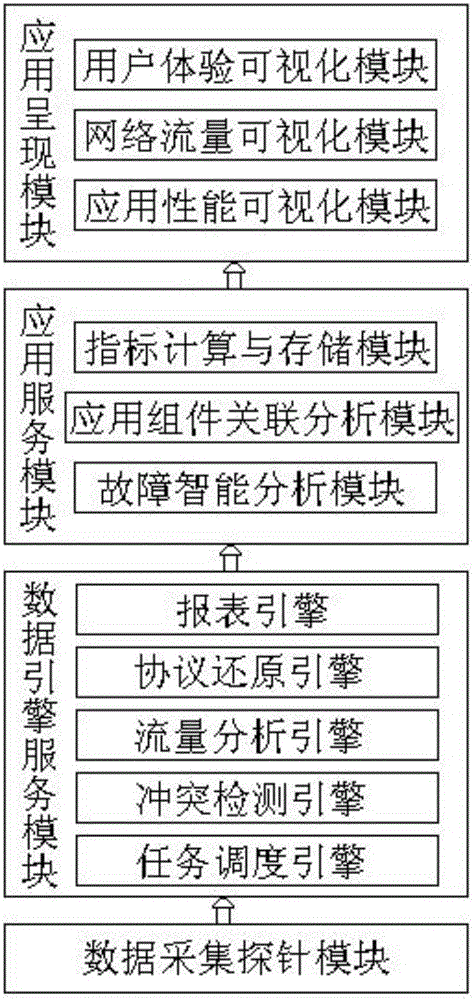
Electric power application performance monitoring system based on flow analysis
ActiveCN106301971ARealize monitoringAchieve positioningData switching networksData acquisitionPerformance index
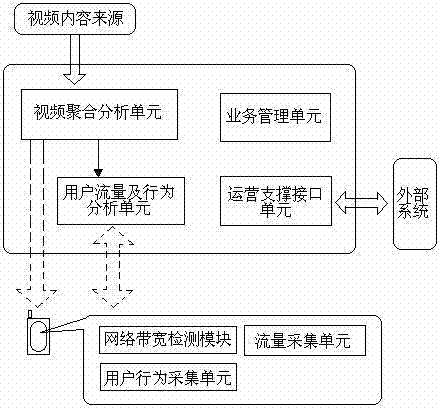
The invention relates to an electric power application performance monitoring system based on flow analysis. The system comprises a data acquisition probe module, a data engine service module, an application service module and an application presentation module, wherein the data acquisition probe module comprises a plurality of data acquisition probes and is used for mirroring network flow data of a business system to a host in a data acquisition probe, and extracting, computing and presenting the application performance indexes of the business system; the data engine service module is used for performing management and task scheduling on the data acquisition probe and performing network flow analytical processing and protocol reassembling processing on the network flow data; the application service module is used for performing correlation analysis on the data processed by the data engine service module; and the application presentation module is used for comprehensively presenting the application performance of the business system according to the data analyzing result summarized by the application service module. The design not only can realize data acquisition, monitoring and analysis and help to solve faults timely, but also is simple and convenient in operation and high in reliability.
Owner:STATE GRID CORP OF CHINA +1
High-efficiency visible monitoring analysis system for large-scale traffic data
InactiveCN103309964AQuick comprehension comparisonLowering the Barrier to AnalysisDetection of traffic movementSpecial data processing applicationsData streamDensity based
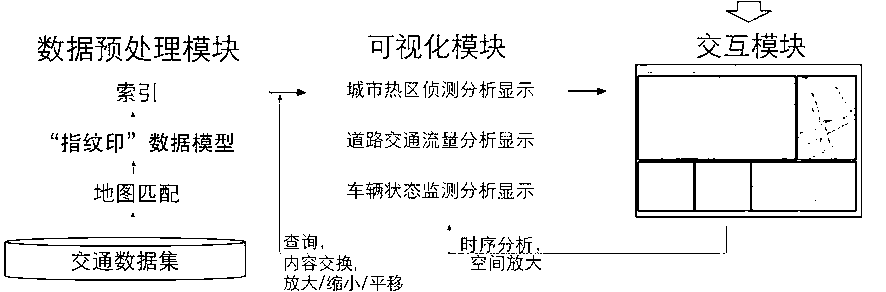
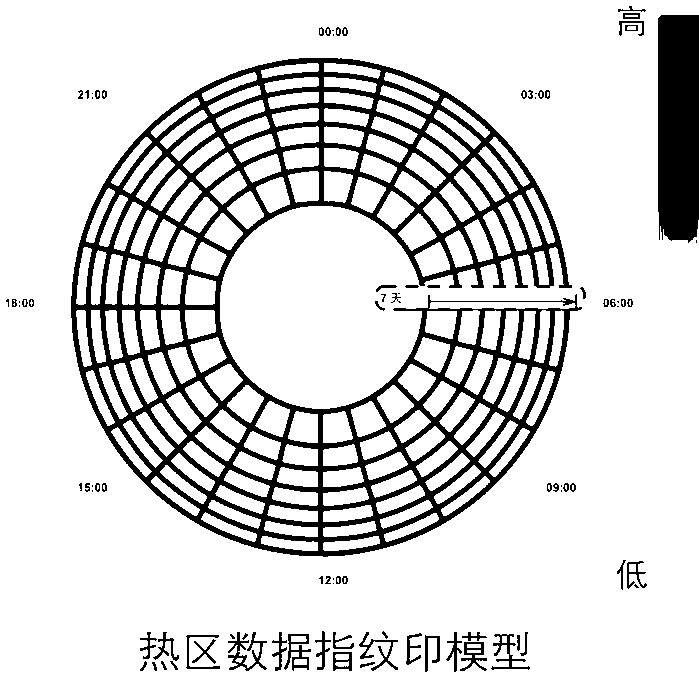
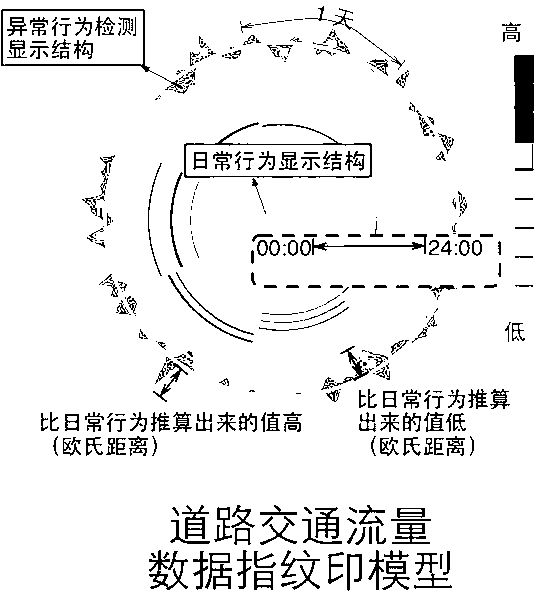
The invention relates to a high-efficiency visible monitoring analysis system for large-scale traffic data. The system is mainly based on a visible 'fingerprint' data model previously proposed by an inventor; the collected original traffic data is converted into the visible 'fingerprint' data model through a data conversion module under large-scale real-time data flow; and complex abstract conceptions such as periodic flow changes, track exceptions and hidden data errors in the traffic data can be visualized into simple and intuitional visual effects so as to provide automatic detection and analysis of city hot spot regions based on density, road traffic flow analysis based on historical traffic flow dynamic properties and real-time monitoring analysis of the traffic track exceptions based on vehicle historical data and statistic information for a user. The periodical flow change properties in the large-scale traffic data are analyzed in real time based on the historical data and the statistic information to find hidden rules and errors so as to provide analysis and support for the decision of the user. Therefore, the convenience is provided for an analyzer to quickly understand the data and the information, the analysis threshold is reduced, the application range is expanded, and the analysis efficiency and accuracy are improved.
Owner:GUANGZHOU HKUST FOK YING TUNG RES INST
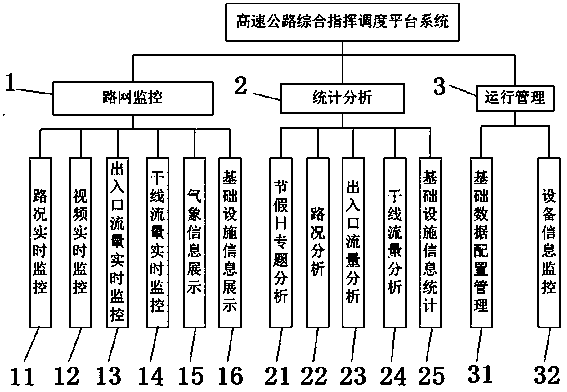
Comprehensive commanding and dispatching platform system of expressway
InactiveCN104240011AImprove work efficiencyEasy to displayResourcesTraffic capacityTraffic flow analysis
The invention provides a comprehensive commanding and dispatching platform system of an expressway. The system comprises a road network monitoring sub system, a statistic analysis sub system and an operation management sub system, wherein the road network monitoring sub system comprises a road condition real-time monitoring module, a video real-time monitoring module, an exit and entry traffic flow real-time monitoring module, a trunk traffic flow real-time monitoring module, a weather information showing module and an infrastructure information showing module; the statistic analysis sub system comprises a holiday specific analysis module, a road condition analysis module, an exist and entry traffic flow analysis module, a trunk traffic flow analysis module and an infrastructure information statistic module; the operation management sub system comprises a basic data configuration management module and an equipment information monitoring module. A user can visually learn about dynamic conditions of a road network, the operation conditions of the road network can be conveniently and accurately mastered, comprehensive commanding and dispatching efficiency of the expressway is improved and operation safety of the expressway is well guaranteed.
Owner:ANHUI WANTONG TECH
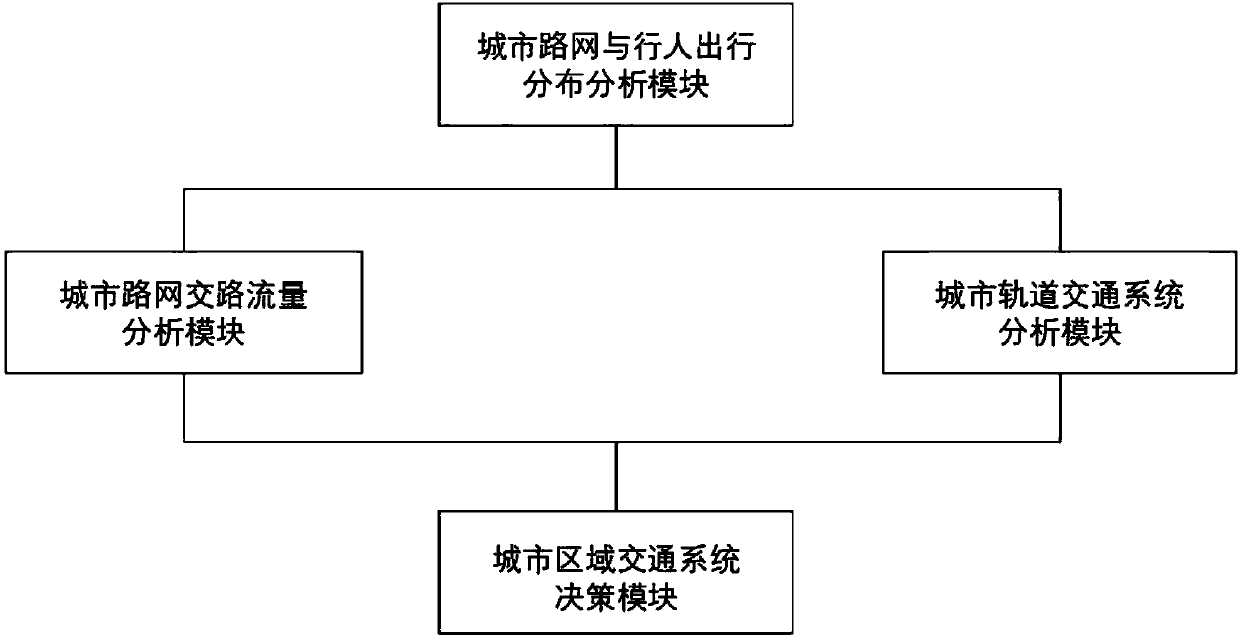
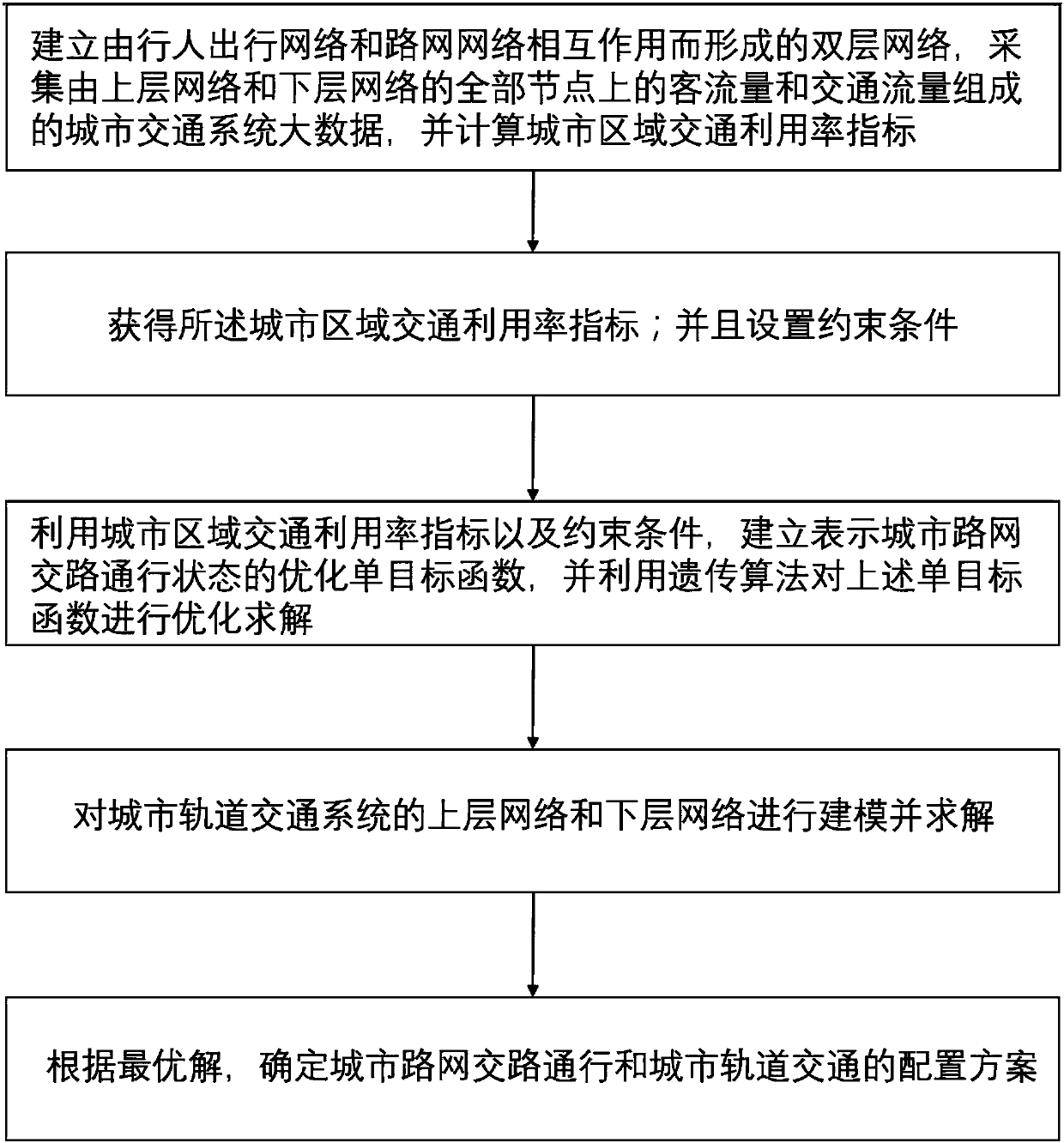
Genetic-algorithm-optimization-based big data analysis system and method of urban regional traffic
ActiveCN108470444AImprove decision makingDetection of traffic movementEngineeringData analysis system
The invention, which belongs to the field of urban traffic design, particularly relates to a genetic-algorithm-optimization-based big data analysis system and method of urban regional traffic. The system is composed of an urban road network and pedestrian travel distribution analysis module, an urban road network traffic flow analysis module, an urban rail transit system analysis module, and an urban regional transportation system decision module. According to the invention, with urban road network and resident travel distribution as an object, a genetic-algorithm-based urban-road-network optimized dual-layer planning model is established by using a dual-layer planning model in a continuous network design and introducing the urban road network and resident travel distribution index into urban road network optimization; an optimal solution is calculated by using a genetic algorithm; and the decision-making configuration of the transportation system is realized based on the optimal solution. Therefore, the data analysis ability and decision-making ability of the urban regional traffic are enhanced substantially.
Owner:TERMINUSBEIJING TECH CO LTD
Historical radar data based air traffic flow analysis system and method
InactiveCN102074126ALong-term period-by-time statisticsQuantitative Basis for Effective BillingAircraft traffic controlStatistical analysisFlow management
The invention discloses a historical radar data based air traffic flow analysis system and method. Aiming at the defects of air traffic flow analysis mainly, the system is designed. The system comprises a server and at least one client, wherein the server is in communication connection with the client and is used for maintaining a database, carrying out statistical analysis of external data received by the client, and storing the statistical analysis results in the database, and the client is used for providing an interface of user interaction and an interface of the external data and the database. The historical radar data is used as a data source, the long-term time segment statistics of historical flow can be actually carried out, and the playback of a historical track and the statistics of instantaneous flow can be carried out; based on the schedule flight property and the airspace property, the combined query of a specific spatial unit can be carried out, and thus the decision support of flow management and the air traffic control service billing are provided to air traffic controllers, and the quantitative basis is provided to airspace capacity assessment and navigation precision checkout.
Owner:TSINGHUA UNIV
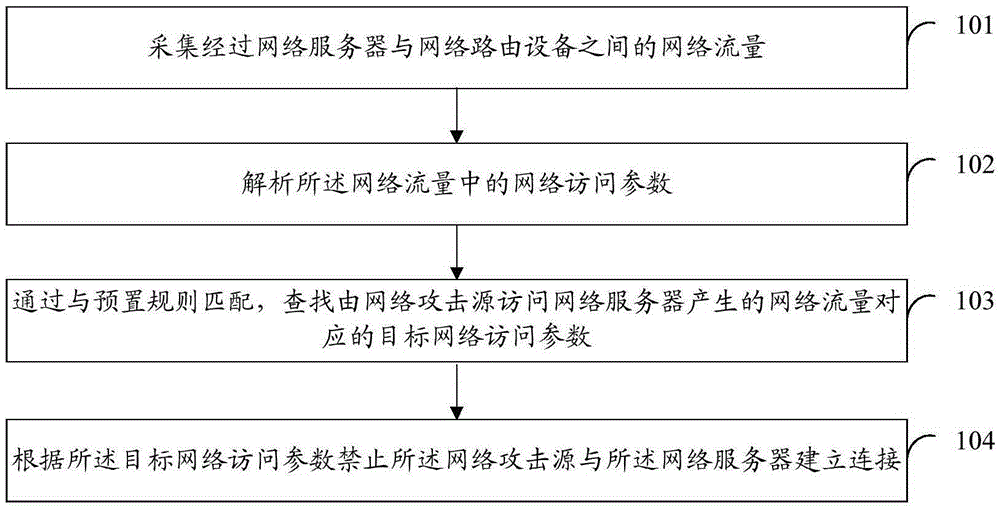
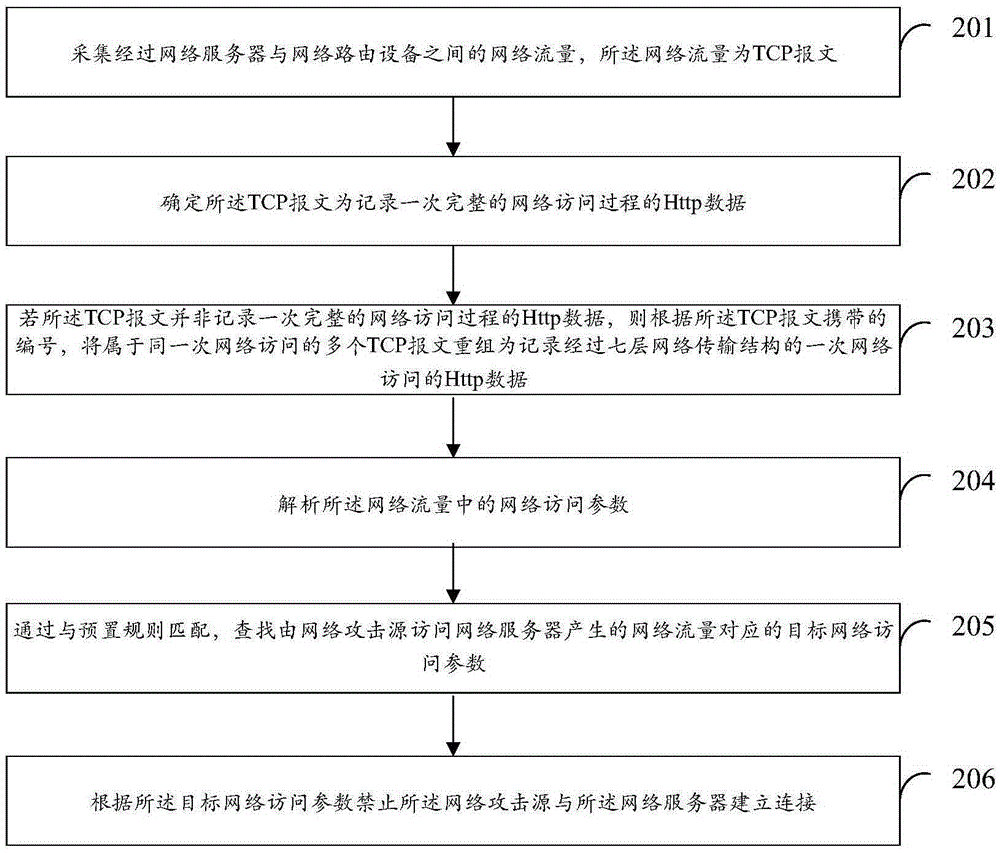
Flow analysis based protective method and device against network attack
InactiveCN106656922AReduce learning costsImprove securityTransmissionAccess networkTraffic flow analysis
The invention discloses a flow analysis based protective method against a network attack. The method comprises that a network flow between a network server and a network router is collected; a network access parameter in the network flow is analyzed; a target network access parameter corresponding to the network flow generated when a network attack source accesses the network server is searched by matching a preset rule; and according to the target network access parameter, the network attack source is forbidden establishing connection to the network server. According to schemes of the invention, no operation needs to be carried out on a client or an external server, and the learning cost of a user is reduced; and compared with a traditional manner in which an WAF server needs to be connected, the method and device aim at clients or external servers of all access network servers, safety detection can be carried out needless of connecting the WAF server, 100% safety protection is provided for the network server, and the total safety of the cloud computing network is improved.
Owner:ALIBABA GRP HLDG LTD
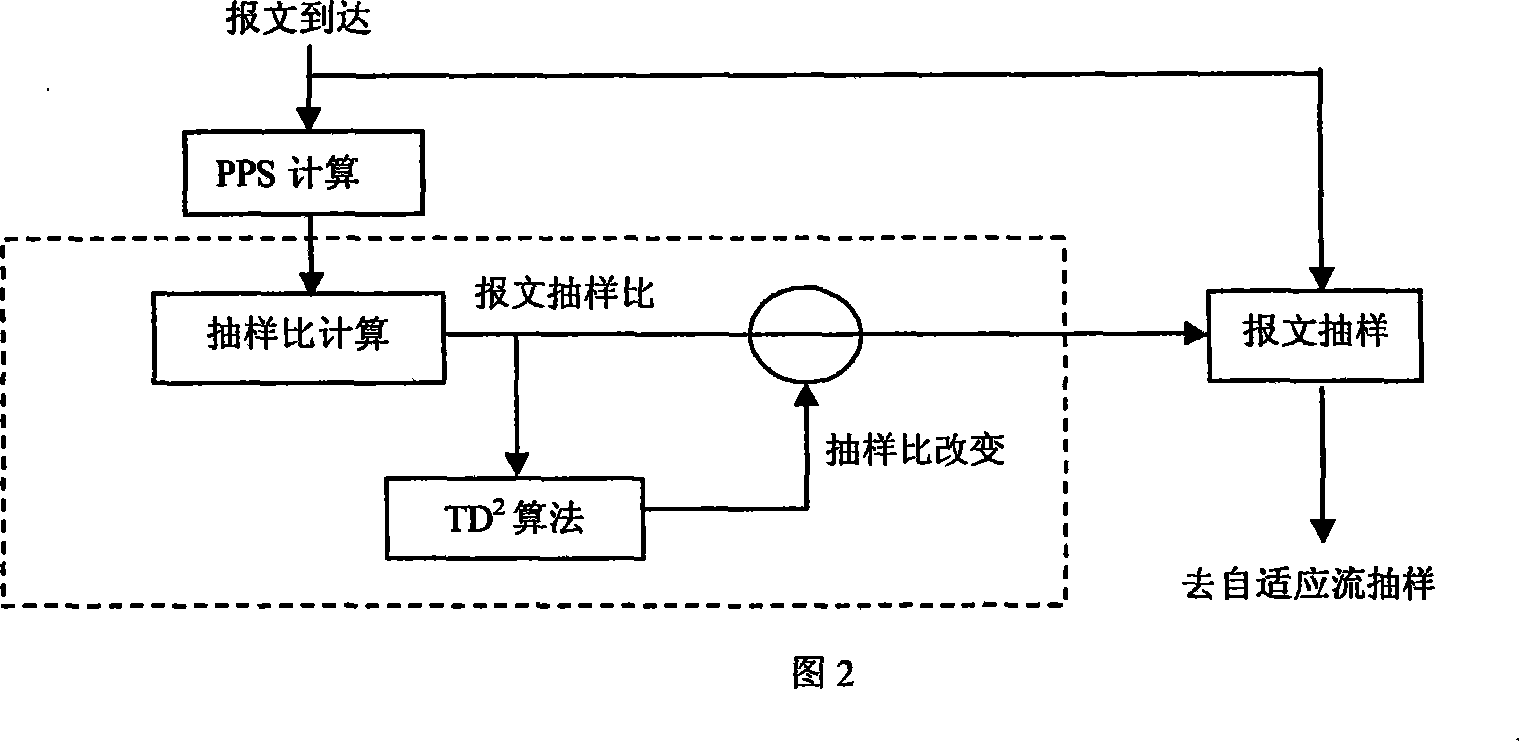
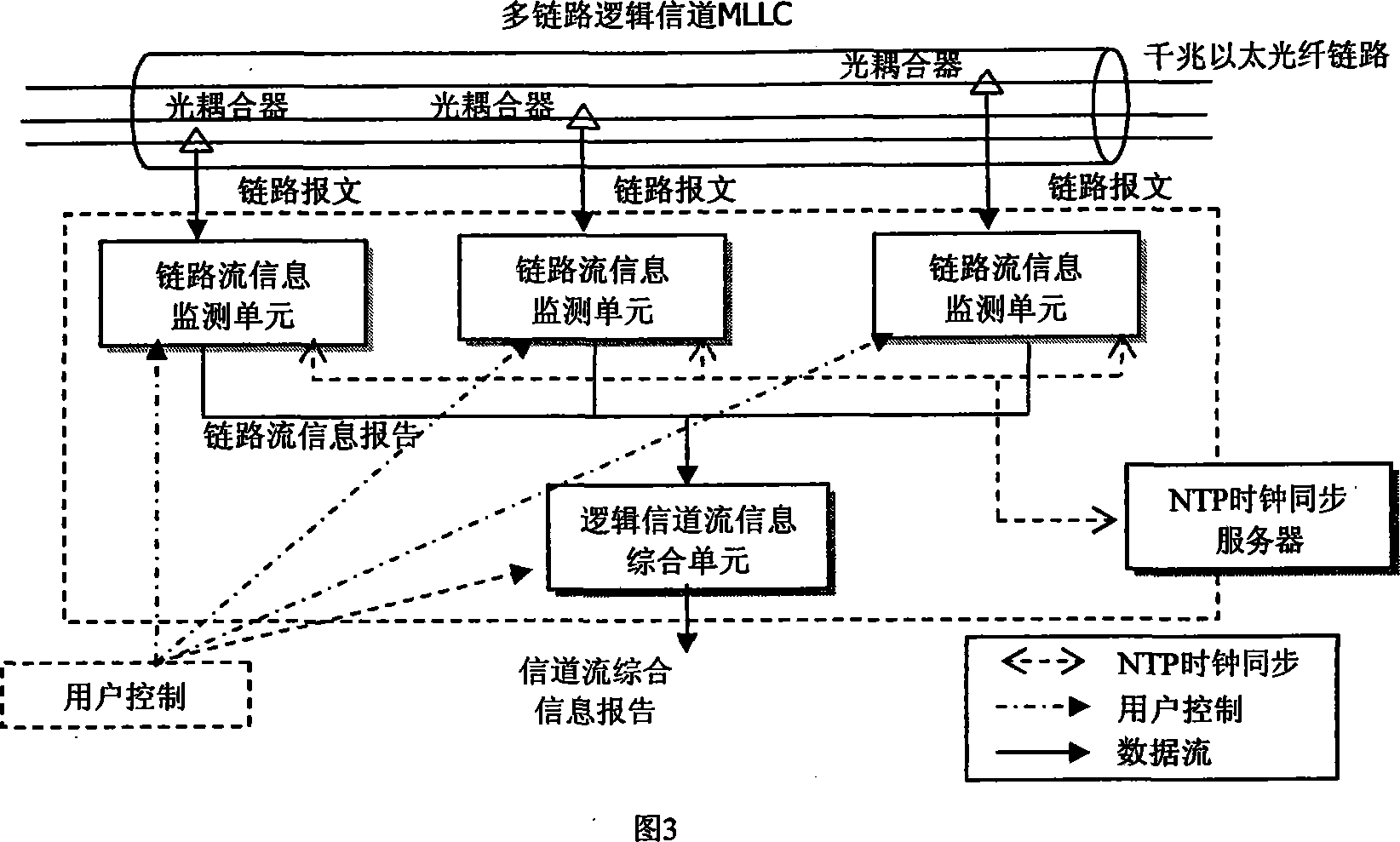
Self adaption sampling stream measuring method under high speed multilink logic channel environment
The method is designed based on NetraMet and NetFlow system. It uses a sampling ratio supporting a high-speed multi-link logical channel network traffic measurement, which can makes self-adaption to the message sampling ratio and the traffic sampling ratio according to the network traffic state and supports to use time slice approach to output the stream message. It uses a general approach to monitor the traffic in any channels.
Owner:SOUTHEAST UNIV
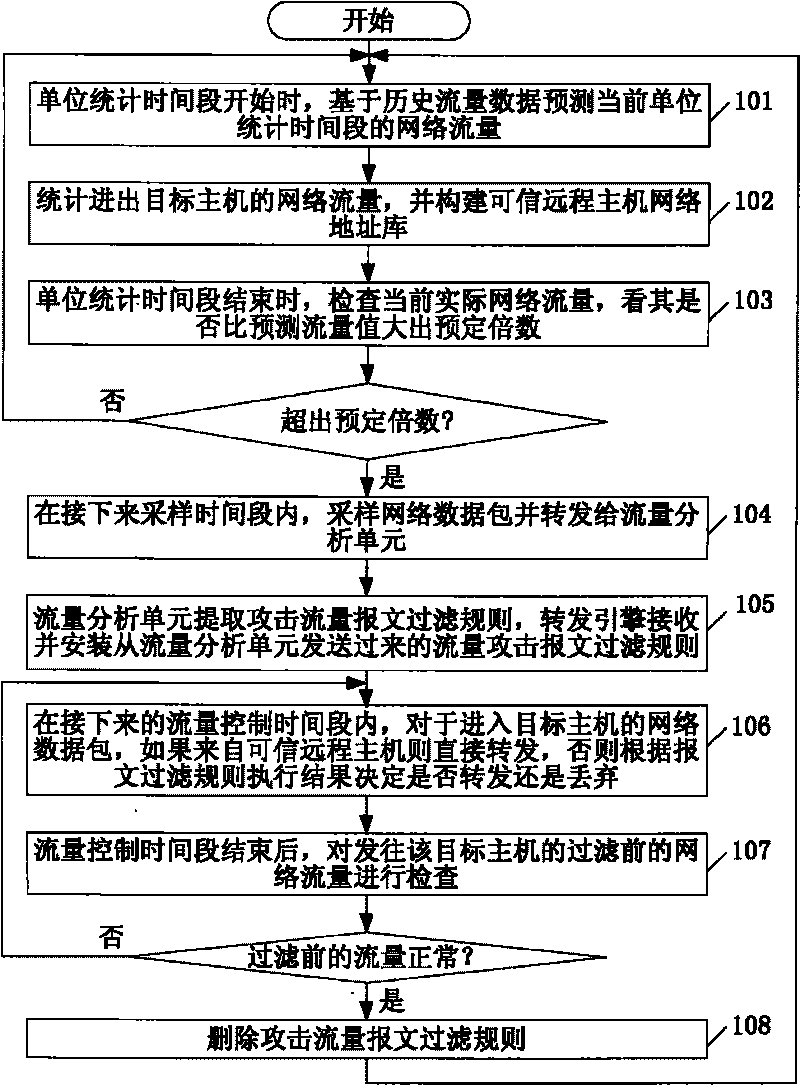
Flow control device and method based on flow prediction and trusted network address learning
InactiveCN101729389AFor real-time analysisEasy to collectData switching networksTraffic capacityTraffic flow analysis
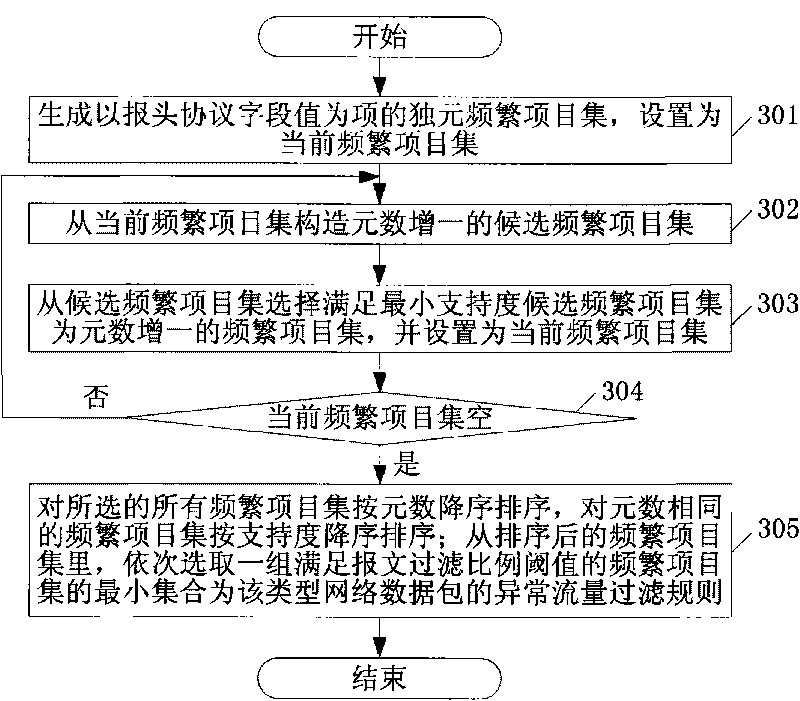
The invention discloses a flow control device and a method based on flow prediction and trusted network address learning. The device comprises a forwarding engine and a flow analysis unit, wherein the forwarding engine is used for forwarding a network packet and calculating the network flow entering and leaving each target host, and reliable network addresses are collected from the network packet sent by each target host; when attack flow is detected, the network packet of the target host with attack flow is sampled, and the sample is sent to the flow analysis unit; according to the collected reliable network address and the attack flow filtering rule returned by the flow analysis unit, flow control is carried out to the network packet sent to the target host; according to the received network packet sample, the flow analysis unit takes each TCP / IP protocol packet head field value as an item to extract a frequent item set satisfying preset minimum support to serve as an attack flow filtering rule applied to the target host corresponding to the network packet sample.
Owner:BEIJING VENUS INFORMATION TECH +1
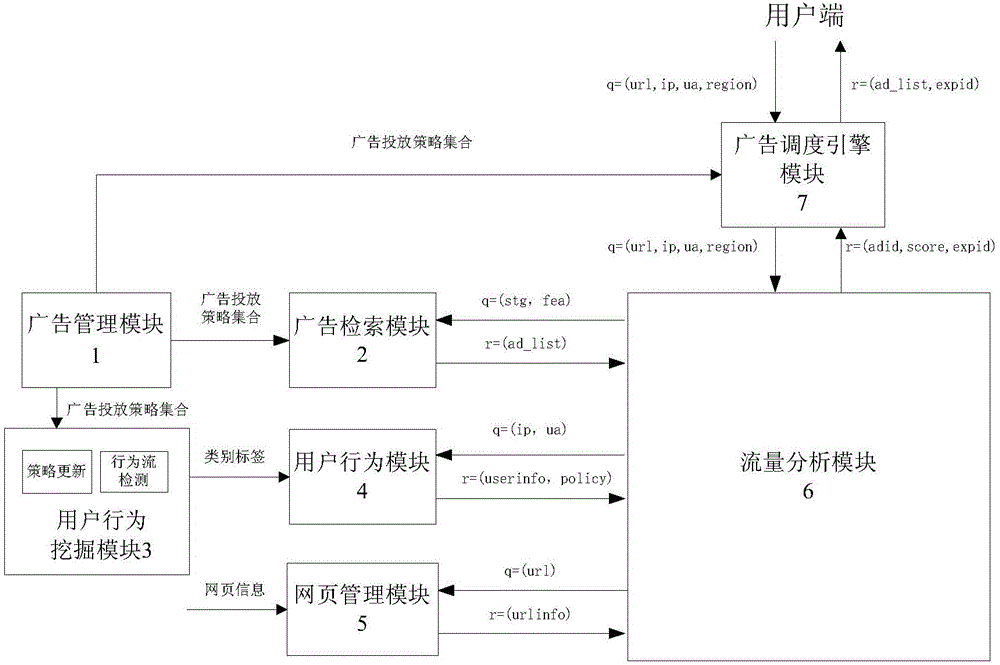
Online advertisement recommending system and method for large-scale medium data
ActiveCN103955842AImprove self-learning abilityImprove intelligenceSpecial data processing applicationsMarketingTraffic flow analysisLarge scale data
The invention provides an online advertisement recommending system and method for large-scale medium data and relates to the technical field of the calculation advertisement science. An advertisement dispatch engine module in the online advertisement recommending system is respectively connected with a user side, an advertisement management module and a flow analysis module. Parameter exchange is carried out between the flow analysis module and an advertisement searching module, a user behavior inquiry module and a webpage management module. A user behavior mining module is respectively connected with the advertisement management module and the user behavior inquiry module. The advertisement management module is connected with the advertisement searching module. According to the online advertisement recommending method, when a user finish accessing a webpage, the user is identified according to user information, user interests are inquired, user behaviors are learned, matched advertisements are searched for according to the predicted user behaviors, and finally the online advertisements are recommended to the user. The system has the good self-learning ability, can effectively improve the intelligent level of advertisement recommendation, and is suitable for online advertisement recommendation under the background with the large-scale data.
Owner:武汉烽火普天信息技术有限公司
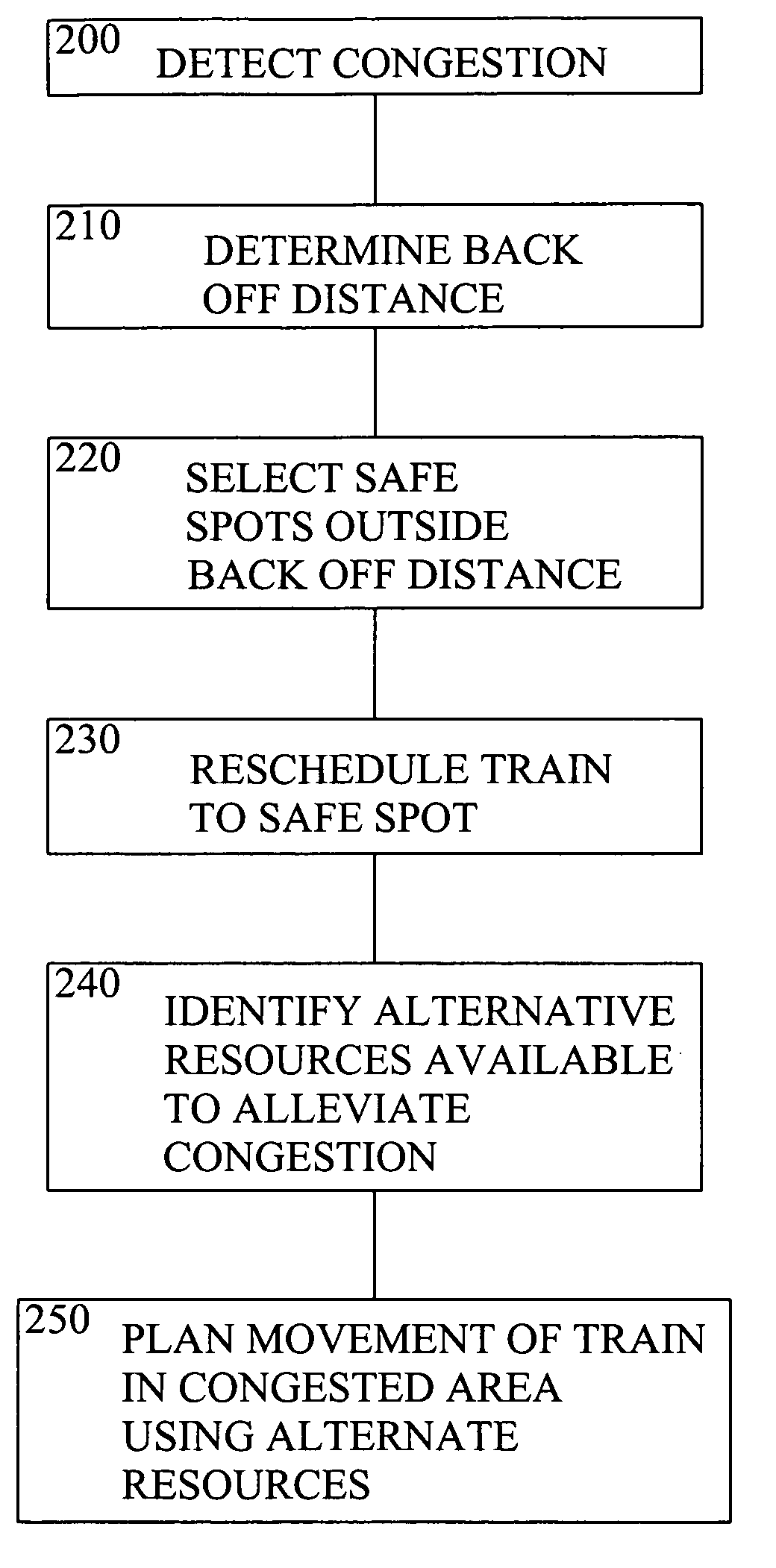
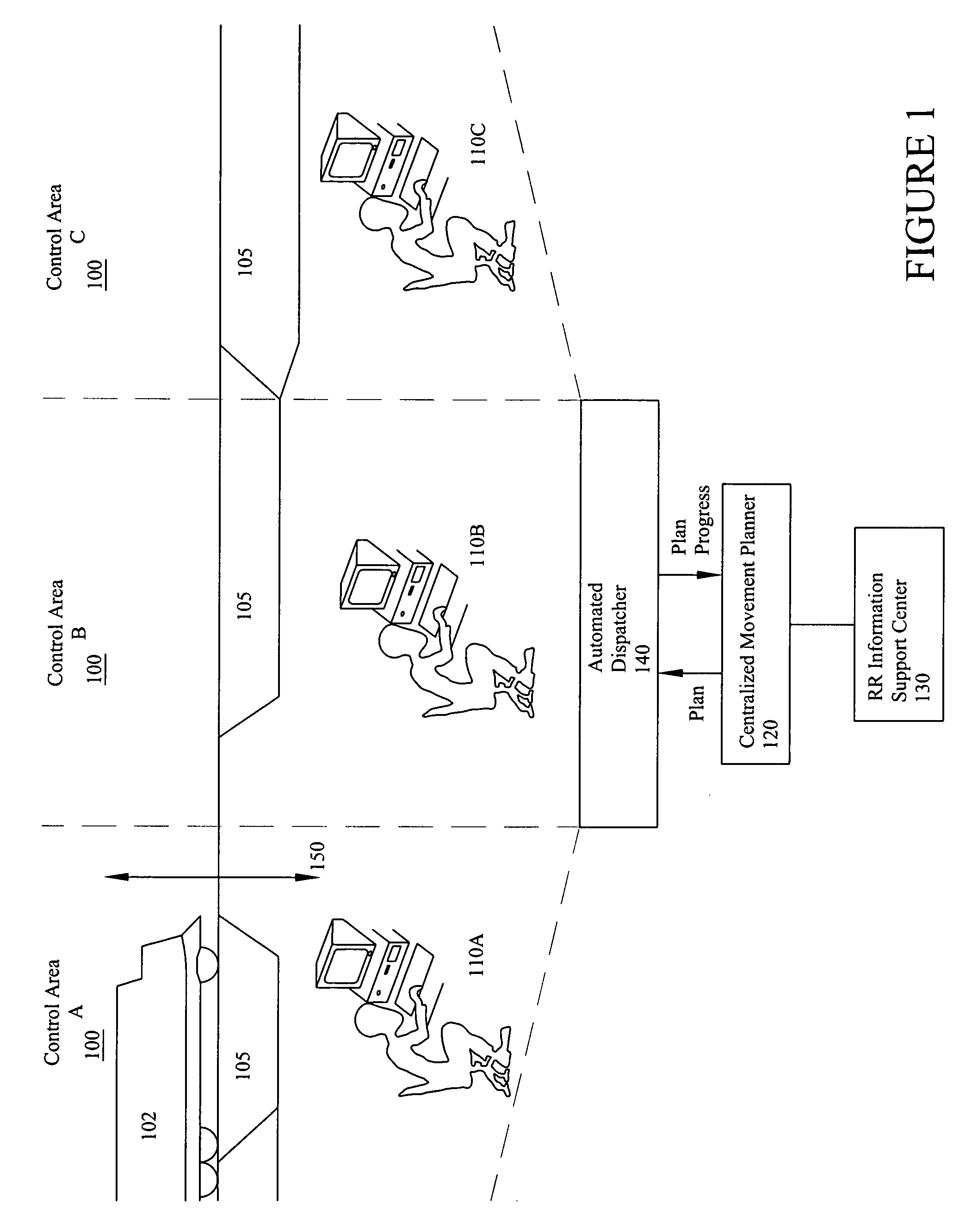
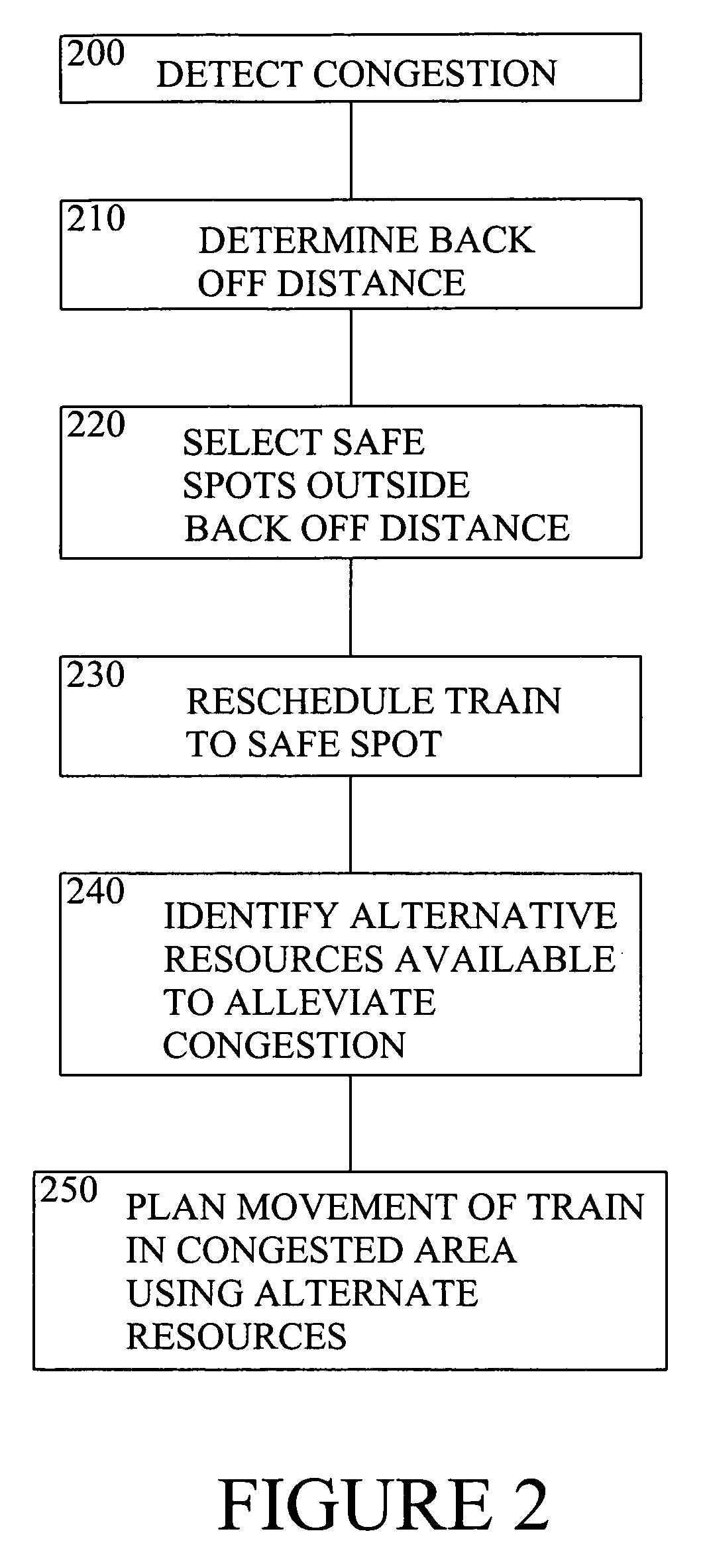
Method and apparatus for congestion management
InactiveUS7725249B2Analogue computers for vehiclesInstruments for road network navigationAutomatic controlTraffic flow analysis
A scheduling system and method for moving plural objects through a multipath system described as a freight railway scheduling system. The scheduling system utilizes a cost reactive resource scheduler to minimize resource exception while at the same time minimizing the global costs associated with the solution. The achievable movement plan can be used to assist in the control of, or to automatically control, the movement of trains through the system. Deadlock is avoided by controlling the entry of trains into congested areas, and may be automatically implemented by the use of traffic flow analysis algorithms.
Owner:GENERAL ELECTRIC CO
Flow monitoring system based on software definition network and flow monitoring method
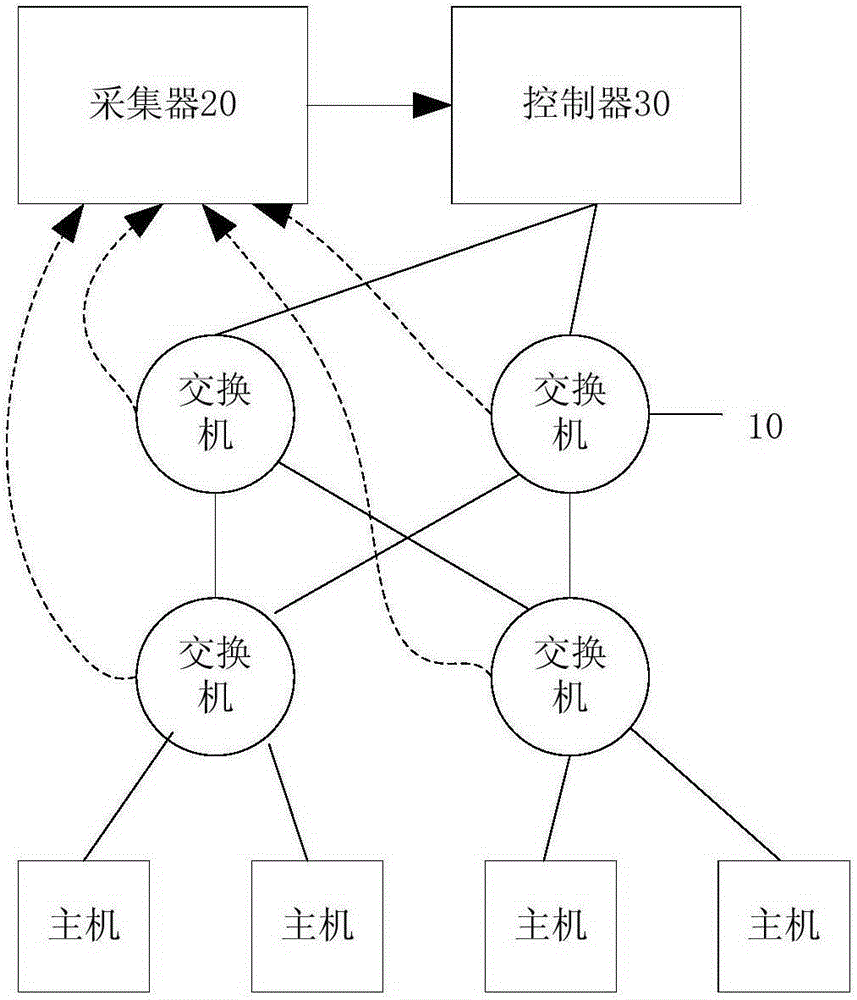
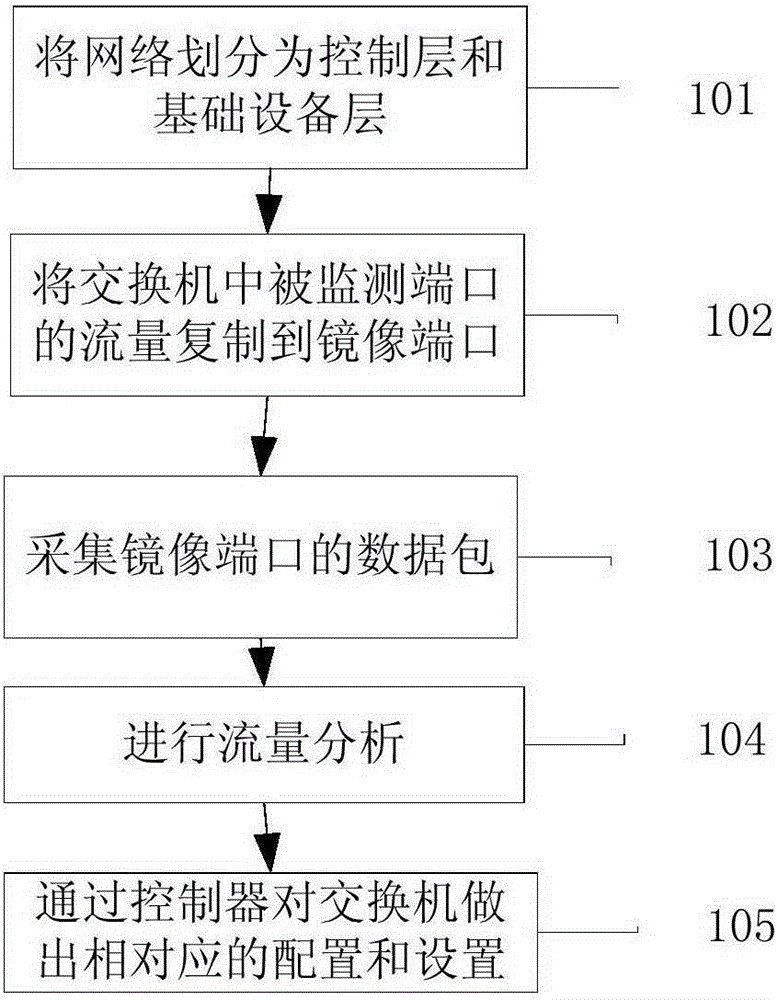
ActiveCN105357075AEffective monitoringQuick monitoringData switching networksControl layerRouting table
The invention discloses a flow monitoring system based on the software definition network and a flow monitoring method. The flow monitoring method comprises steps that, the software definition network method is employed to divide the network into a control layer and a basic equipment layer, the control layer is provided with a controller, has a complete routing table and a forwarding table and is used for managing and configuring networks and deploying protocols, the basic equipment layer only has a simple data forwarding function, flows of multiple monitored ports of the network equipment in the basic equipment layer are copied to a mirror image port of the network equipment, a data packet is acquired through the mirror image port, flow analysis is further carried out, and configuration and setting for the network equipment are correspondingly carried out through the controller according to the flow analysis result. According to the flow monitoring method, the mirror image port of the network equipment is utilized as an acquisition port, direct interconnection between the mirror image port and the acquisition device port is realized, data transmission time delay is greatly reduced, and data transmission performance and time are improved.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
P2P botnet detection device and method based on flow analysis
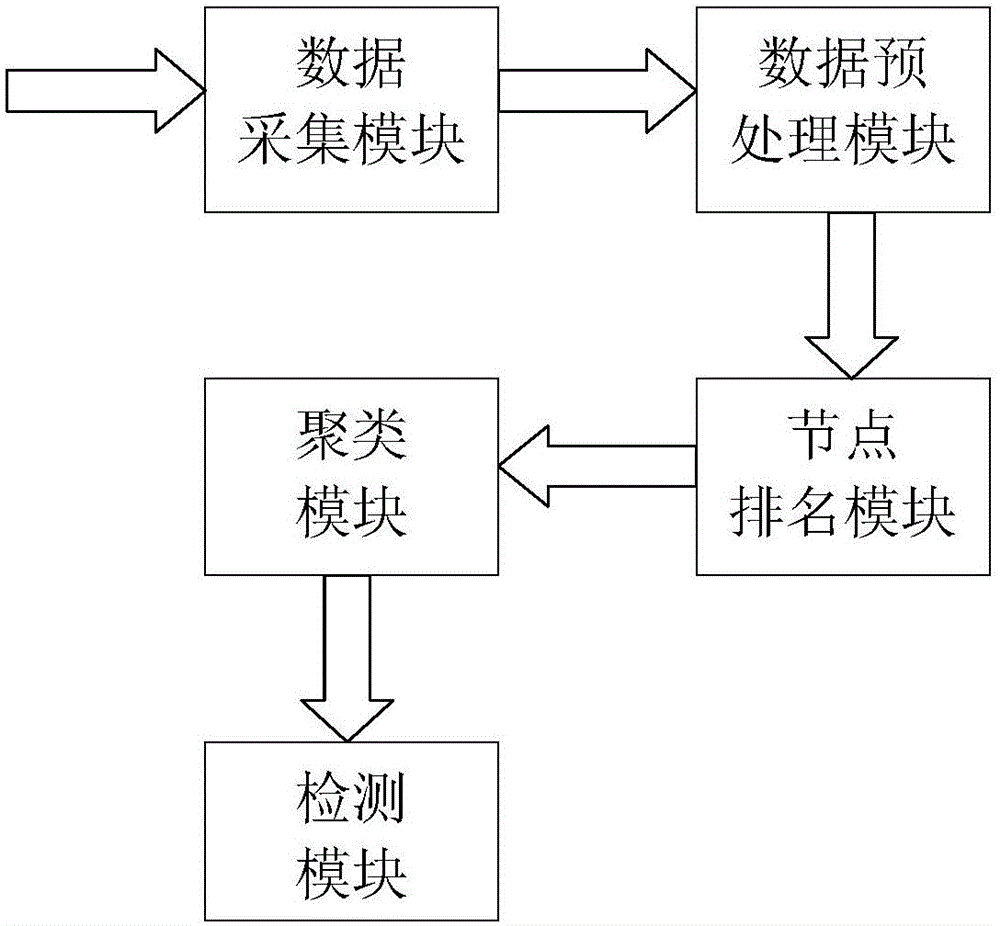
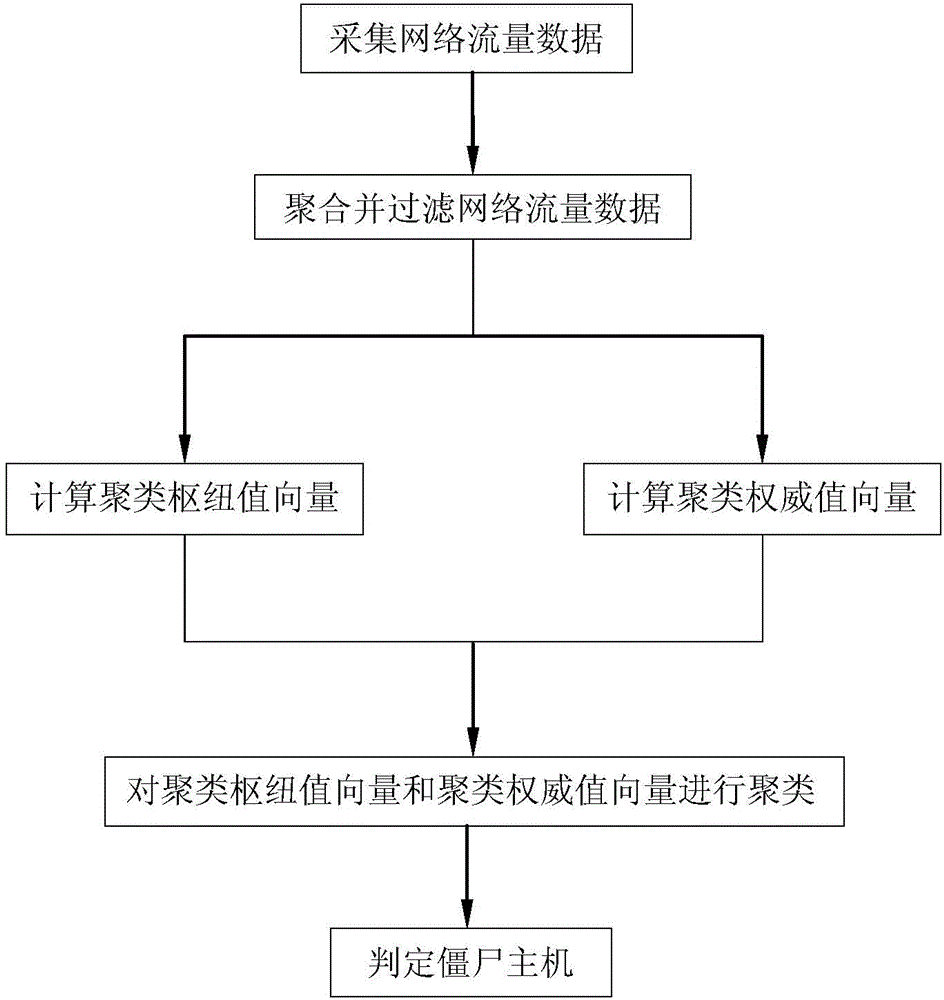
InactiveCN104683346AOvercome the disadvantage of easy accumulation at the data acquisition moduleIncrease speedTransmissionExtensibilityTraffic flow analysis
The invention discloses a P2P botnet detection device and method based on flow analysis and mainly solves the problems of low detection rate and no expandability in the prior art. The P2P botnet detection device comprises a data acquisition module, a data preprocessing module, a node ranking module, a clustering module and a detection module. The method comprises the following steps: (1) acquiring network traffic data; (2) clustering and filtering the network traffic data; (3) calculating a clustering hub value vector; (4) calculating a clustering authority value vector; (5) clustering the clustering hub value vector and the clustering authority value vector; (6) judging detection results. According to the P2P botnet detection device and method, the data preprocessing module is added behind the data acquisition module, the network traffic data is analyzed through calculating the hub value vector and the authority value vector, and the defects of low detection efficiency and no expandability in the prior art are overcome.
Owner:XIDIAN UNIV
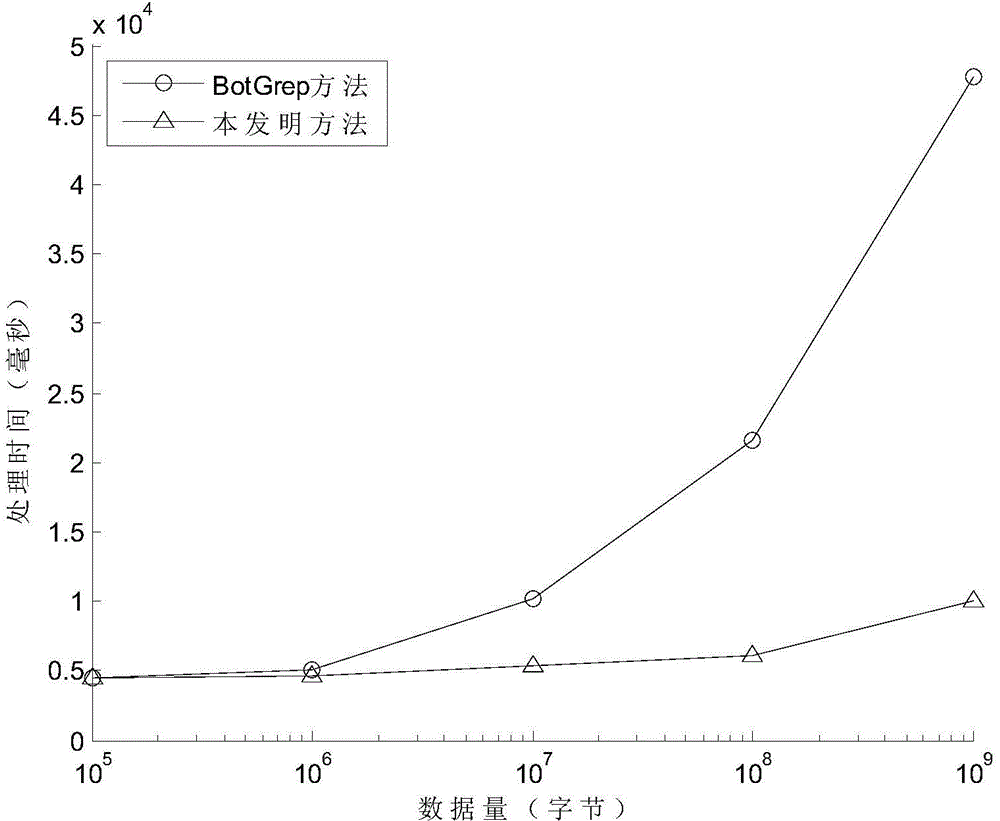
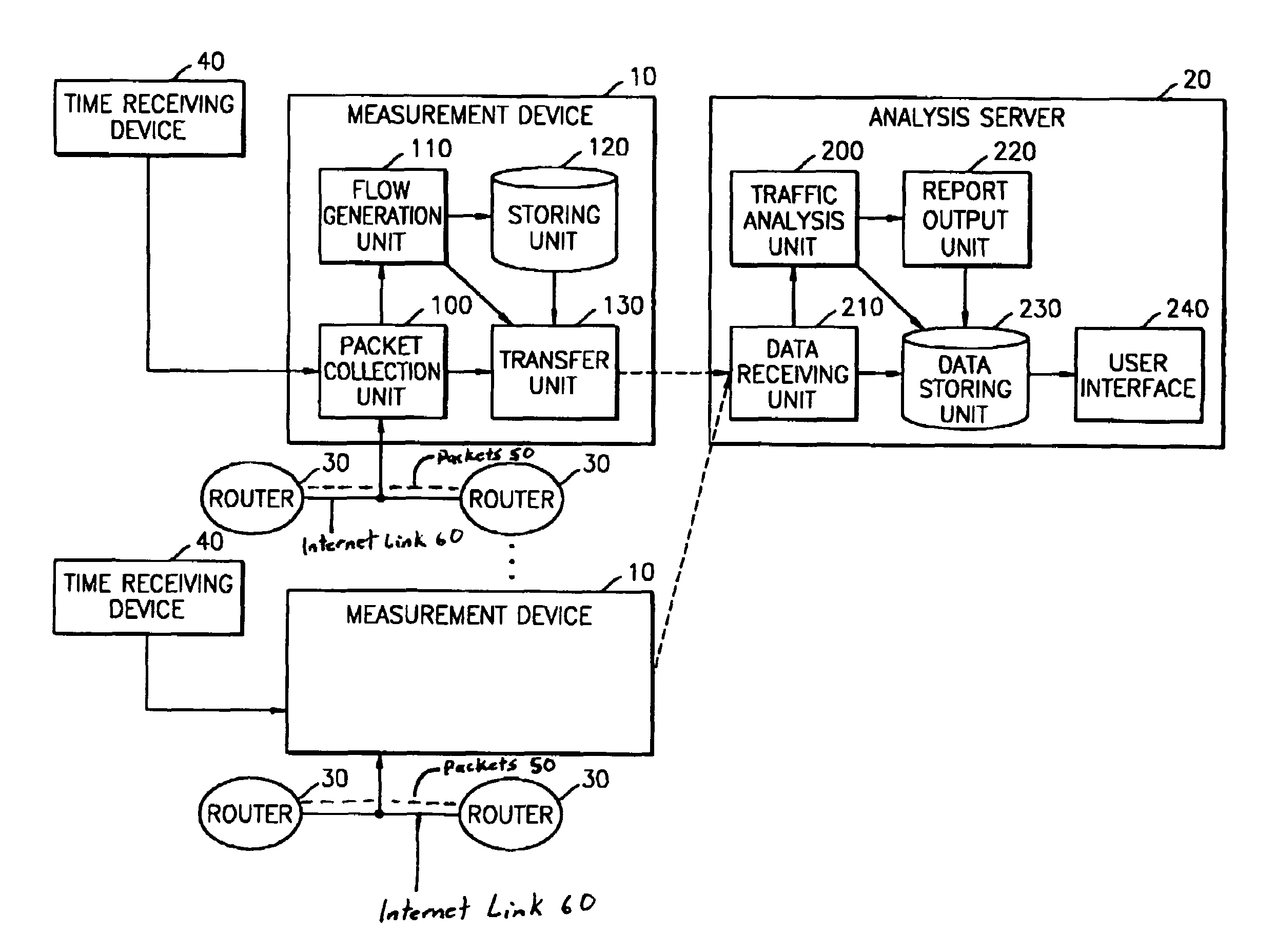
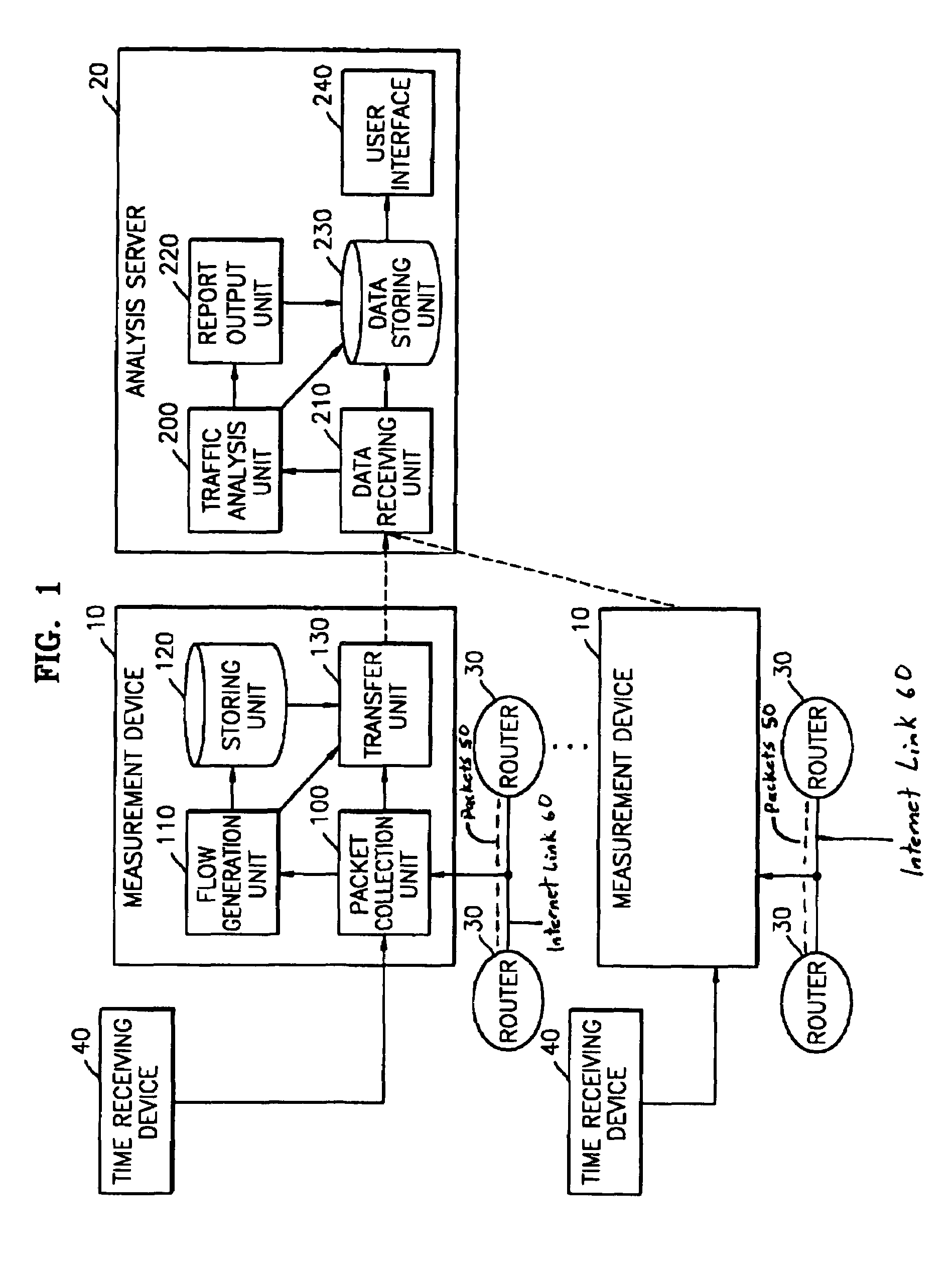
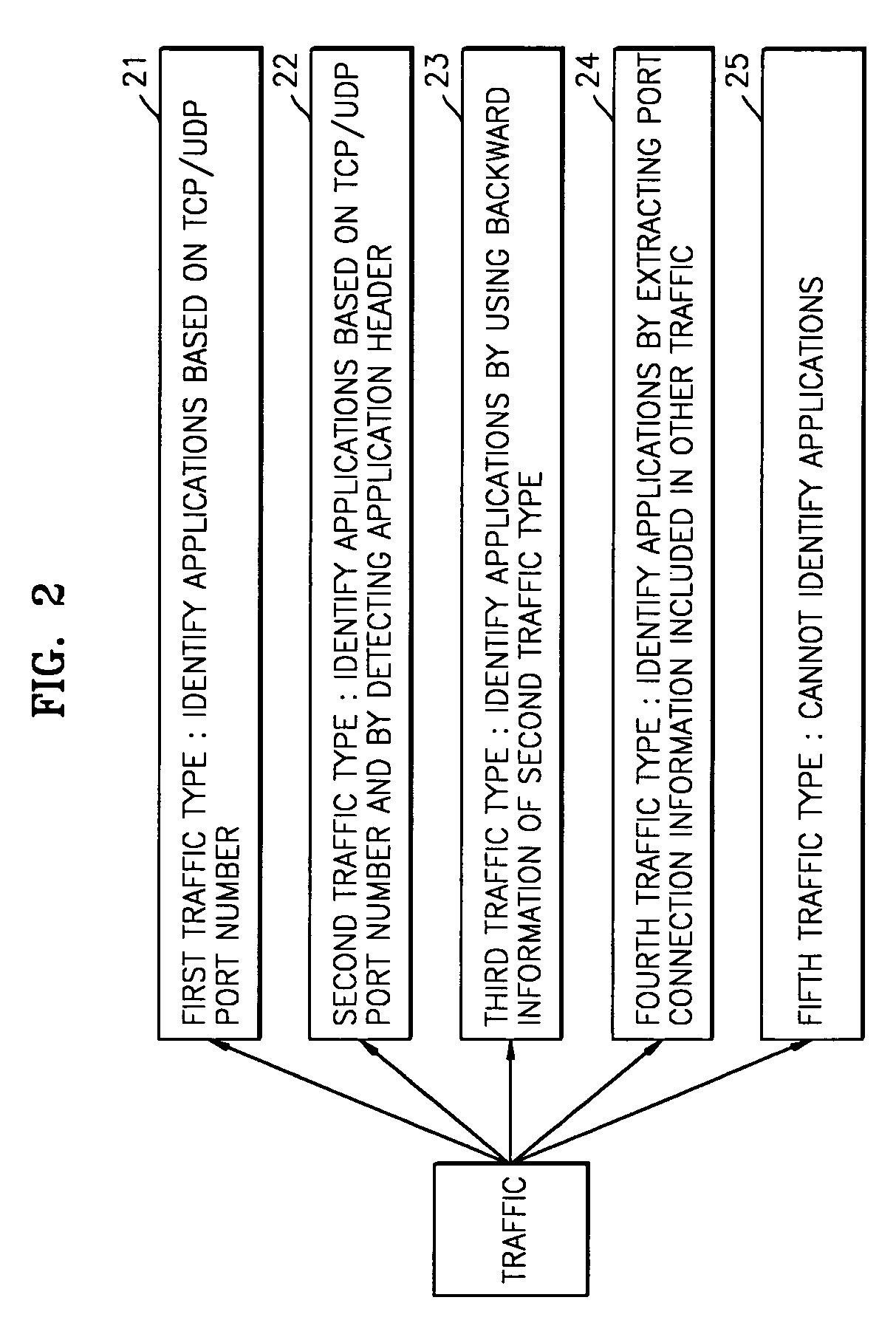
Traffic measurement system and traffic analysis method thereof
A traffic measurement system and a traffic analysis method are provided. The traffic measurement system includes a plurality of measurement devices that collect all of packets flowing through Internet links, extract traffic data required to analyze traffic from the collected packets, and process the extracted data into predetermined flow types, and an analysis server that identifies applications of traffic by analyzing the traffic data transferred from the plurality of measurement devices as a whole, classifies the identified applications into predetermined traffic types, and outputs the classification result. The traffic measurement system measures the traffics in the Internet network and processes the measured traffics to generate detailed traffic statistical data according to applications. In particular, the traffics are analyzed considering measurement data from various points, and the data for identifying the applications are extracted from headers of the applications included in payloads of IP packets in real time. Accordingly, detailed traffic analysis result is provided.
Owner:ELECTRONICS & TELECOMM RES INST
Network traffic analyzer
InactiveUS7039577B1Facilitate trend analysisEasy to identifyMultiplex system selection arrangementsError preventionTraffic capacityTraffic flow analysis
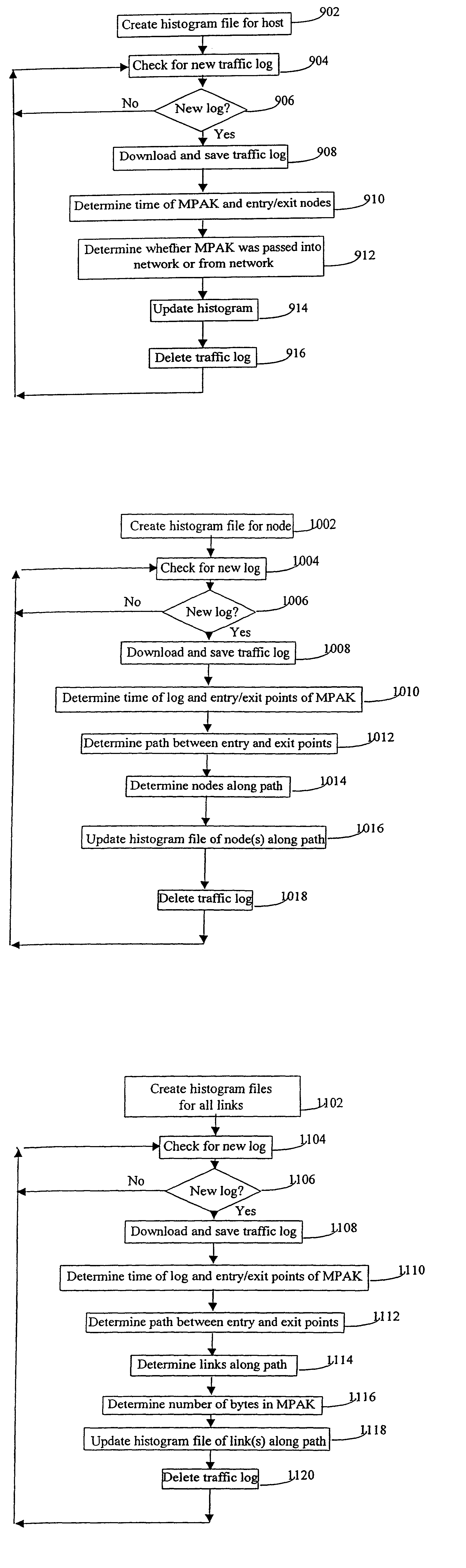
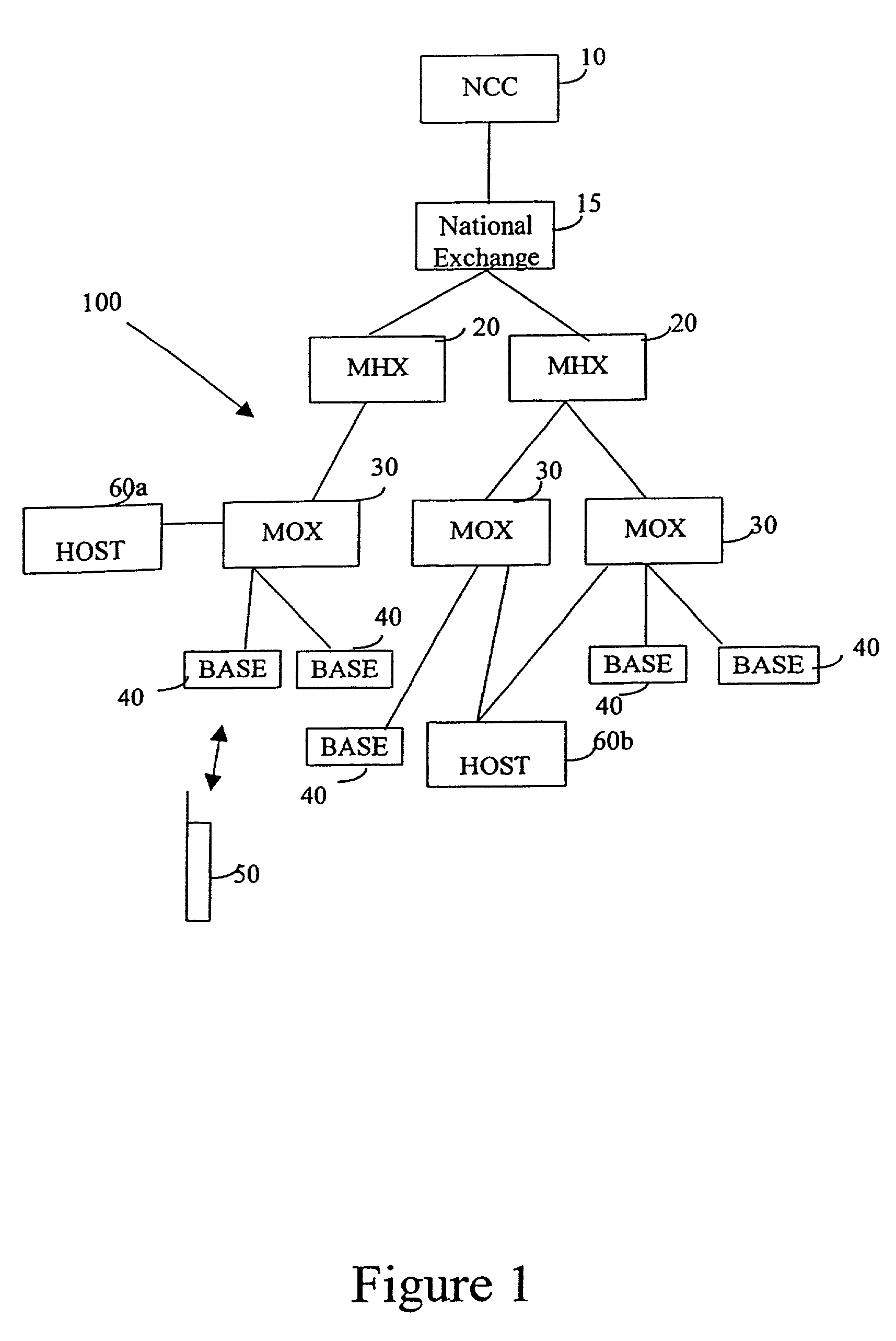
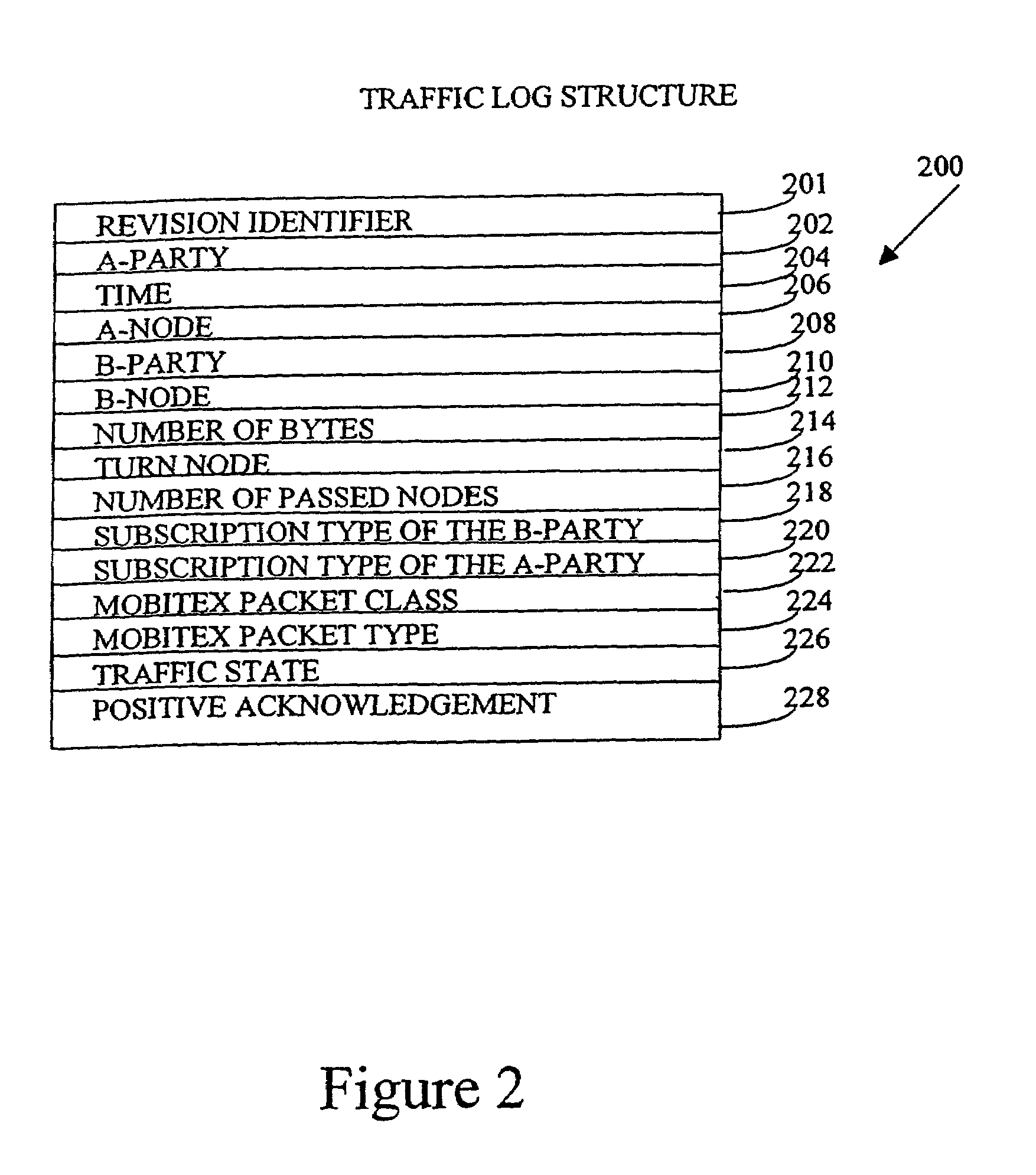
A system for and method of analyzing packet traffic in a packet-switched network, including collecting traffic logs from a network operations center, wherein the traffic logs are representative of packet traffic passing through an actual configuration of the network, and wherein each traffic log includes the time the traffic log was created and an associated packet's network entry and exit points. The collected traffic logs are stored in a computer such that the traffic logs can be replayed. A computer file is thereafter created and is representative of a modified network configuration that is different from the actual configuration of the network. The traffic logs are replayed in coordination with the modified network configuration to generate a histogram file representative of packet traffic passing through or via at least one of a host, node or link in the modified network configuration.
Owner:BELLSOUTH INTPROP COR
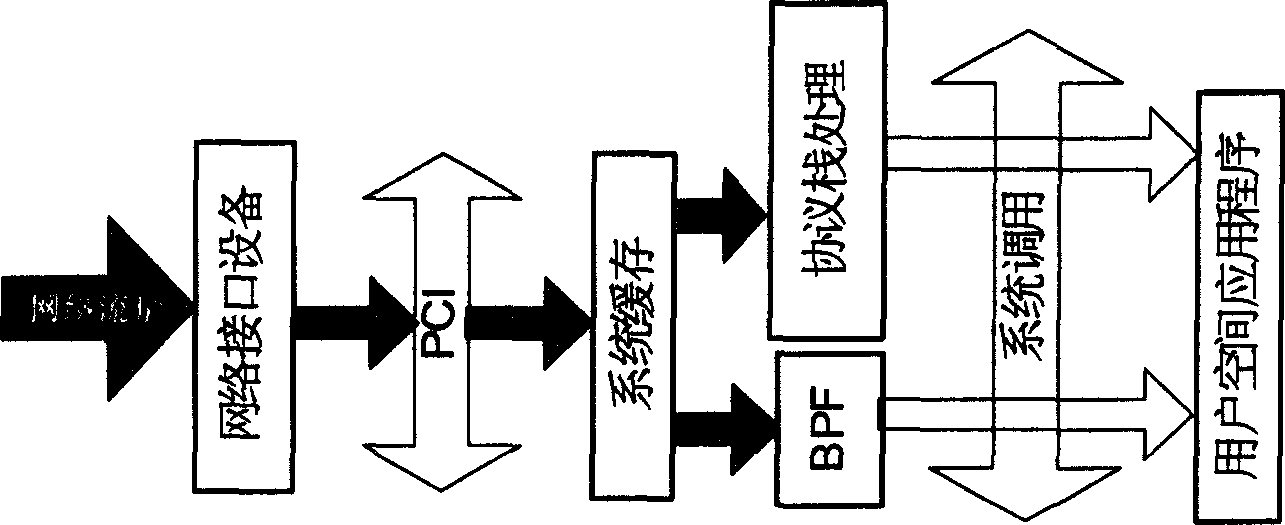
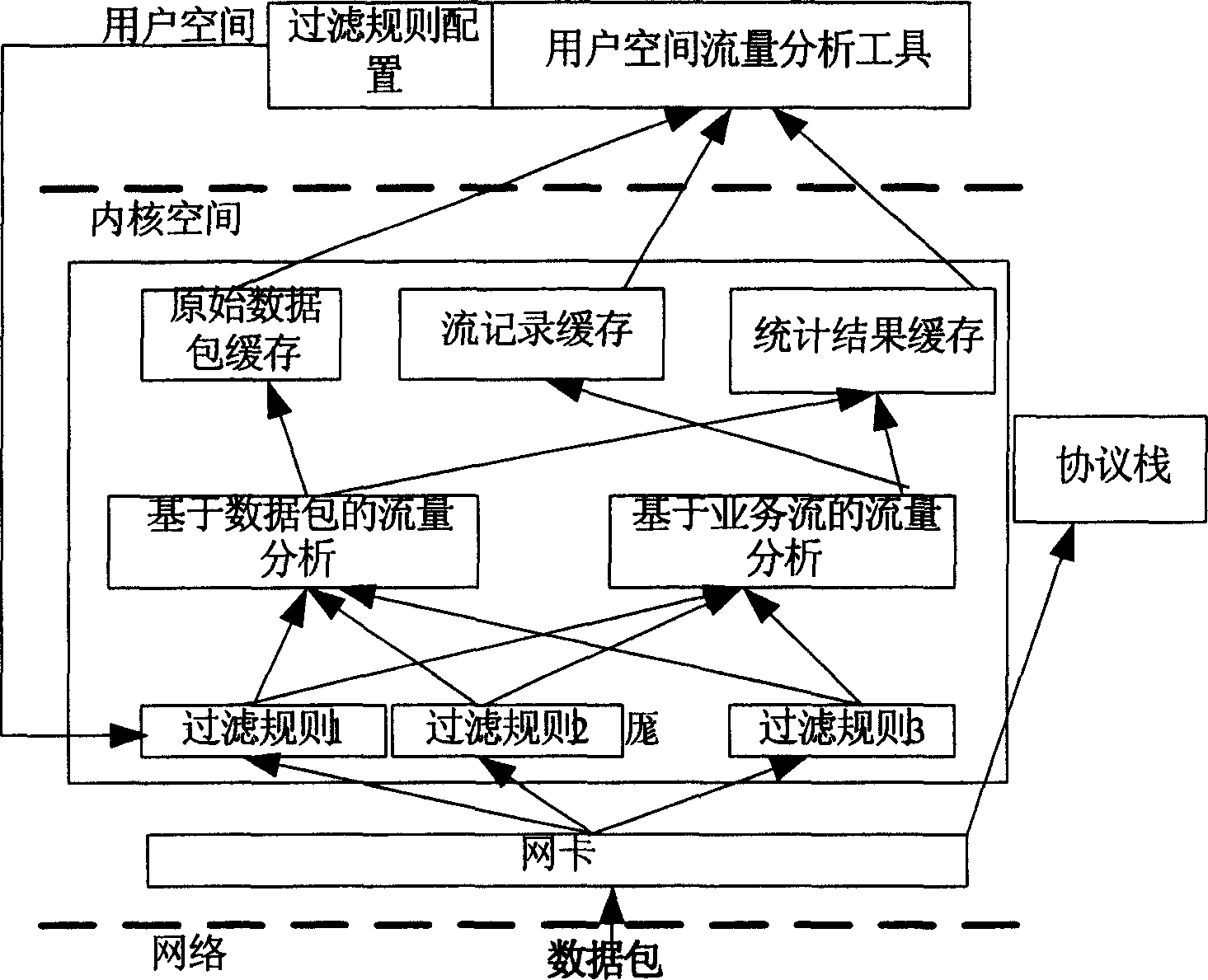
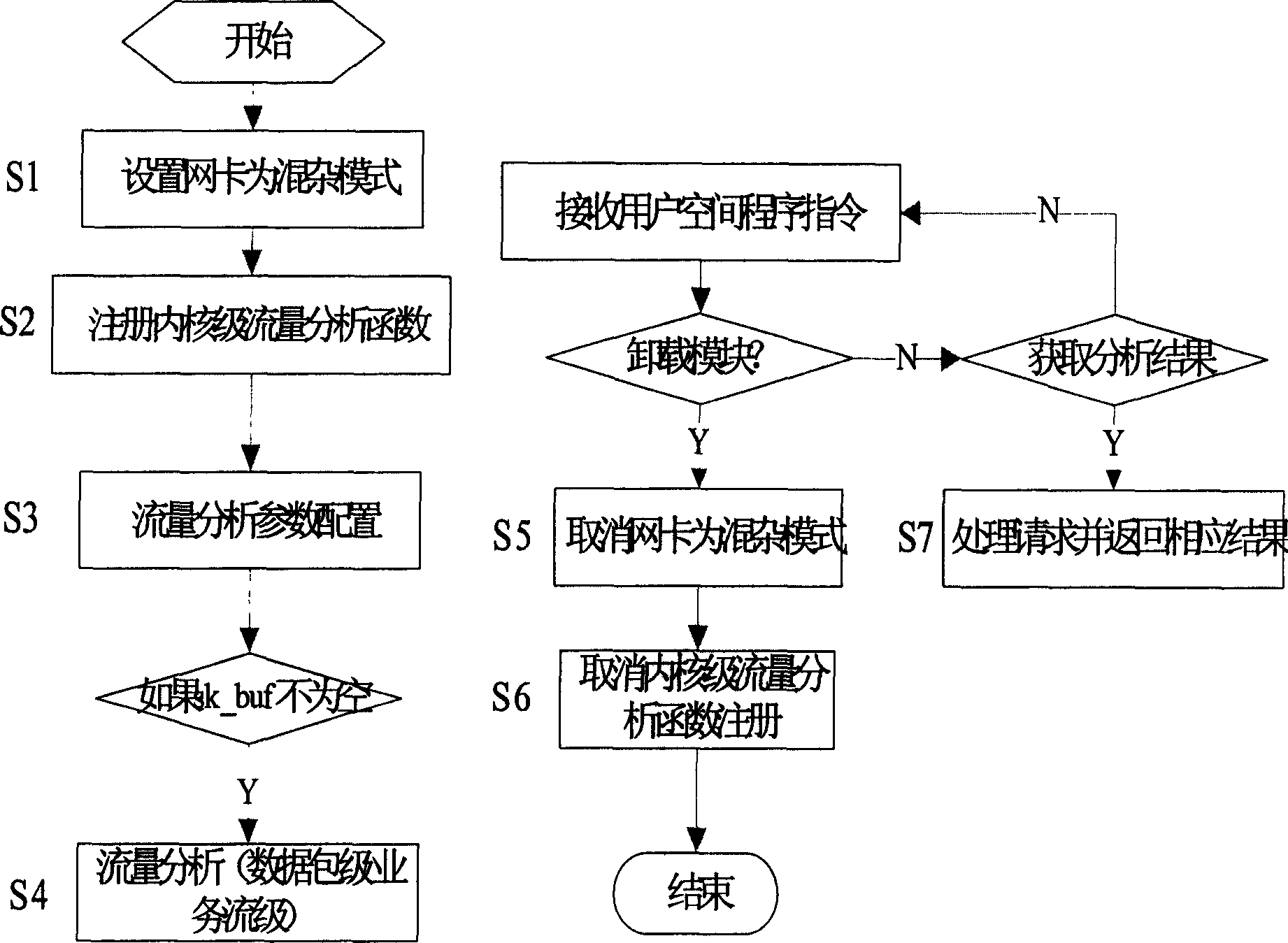
Flow analysis method based on Linux core
InactiveCN1633110AImprove the efficiency of monitoring analysisShorten call timeData switching networksTraffic flow analysisGNU/Linux
A flow analysis method based on Linux kernel is realized by the way of loading the kernel in Linux. The provided monitoring analysis target includes flow rate, link usability, 2-7 layer protocol distribution, rate of different protocols, packets distribution, which can monitor specific kind flows based on the definition rules of different flows and provide related statistic results.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
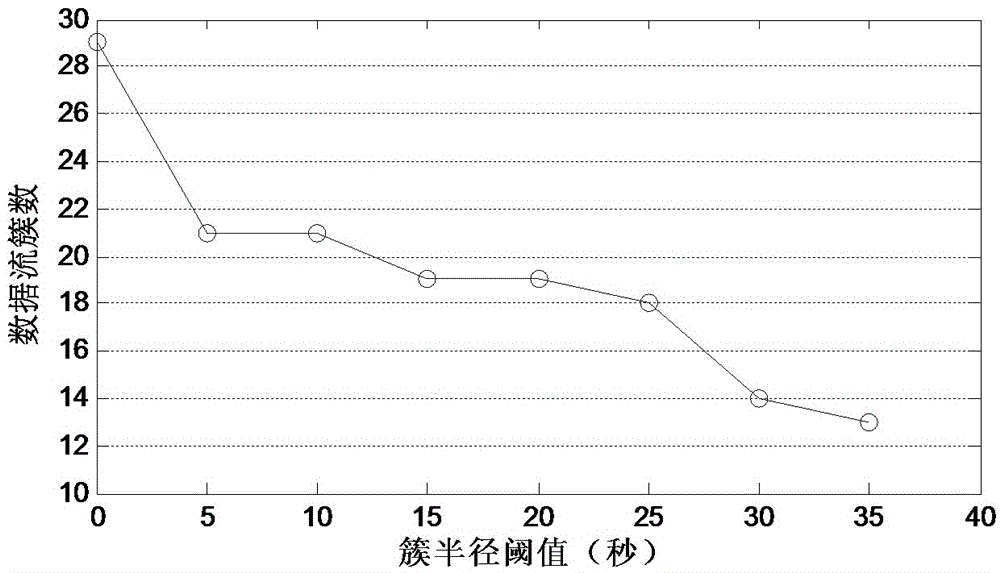
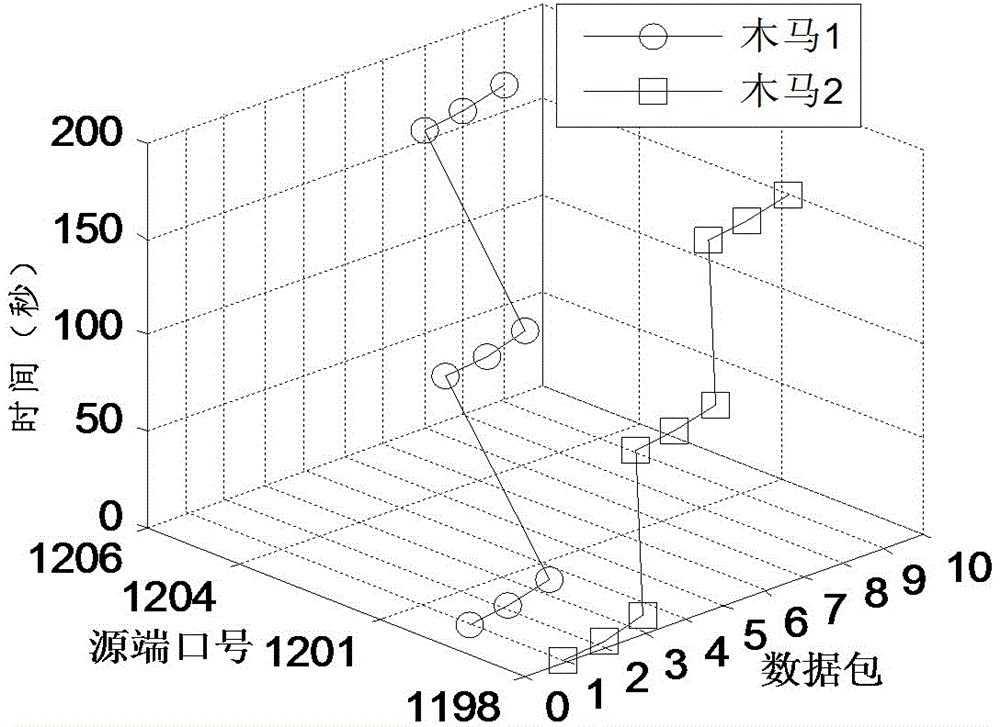
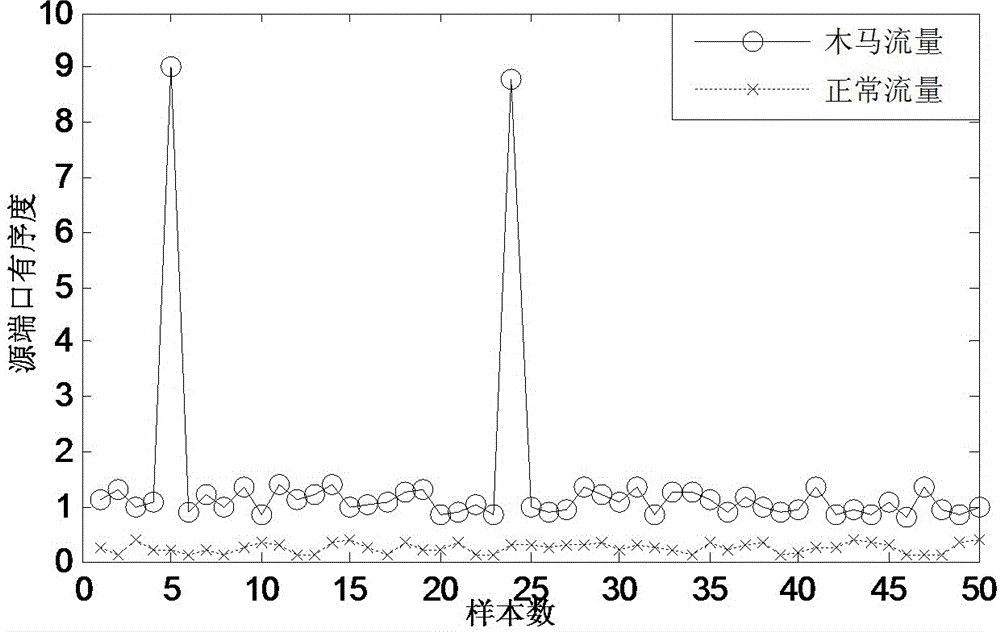
Torjan detection method based on uncontrolled end flow analysis
The invention discloses a torjan detection method based on uncontrolled end flow analysis. The method includes the steps that firstly, a captured network data package is processed; secondly, the network data package is organized into data flows according to quintuple information and requirements of protocol specifications; then, the data flows are classified according to equivalent tetrads to form data flow sets identified by the tetrads; finally the data flows in the data flow sets are clustered to form data flow clusters by the adoption of a data flow clustering algorithm based on timestamps. According to the torjan detection method based on the uncontrolled end flow analysis, on the basis of carrying out clustering on the network data flows to form the data flow clusters, the data flows are processed with the data flow cluster as a unit to analyze the difference between torjan communication behaviors and normal network communication behaviors, in addition, the difference between the torjan communication behaviors and the normal network communication behaviors are deeply dug in combination with the technologies of statistic analysis and data mining, and therefore uncontrolled end torjan flow in a network can be detected.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com