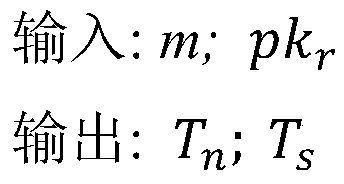Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
346 results about "Hidden data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
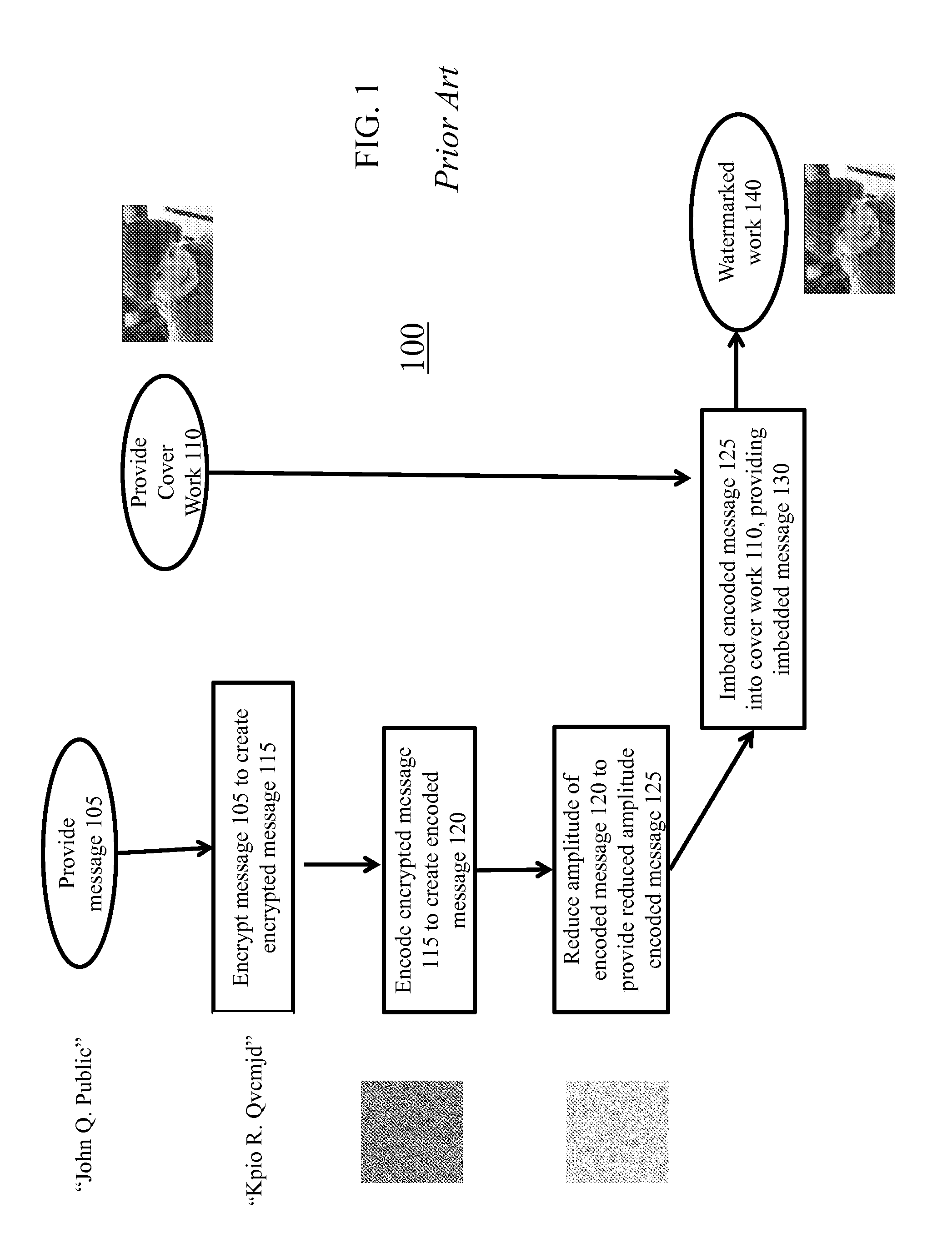
Method and apparatus for embedding data, including watermarks, in human perceptible images
InactiveUS6031914AGood autocorrelationPromote generationElectric signal transmission systemsCharacter and pattern recognitionPattern recognitionFrequency spectrum
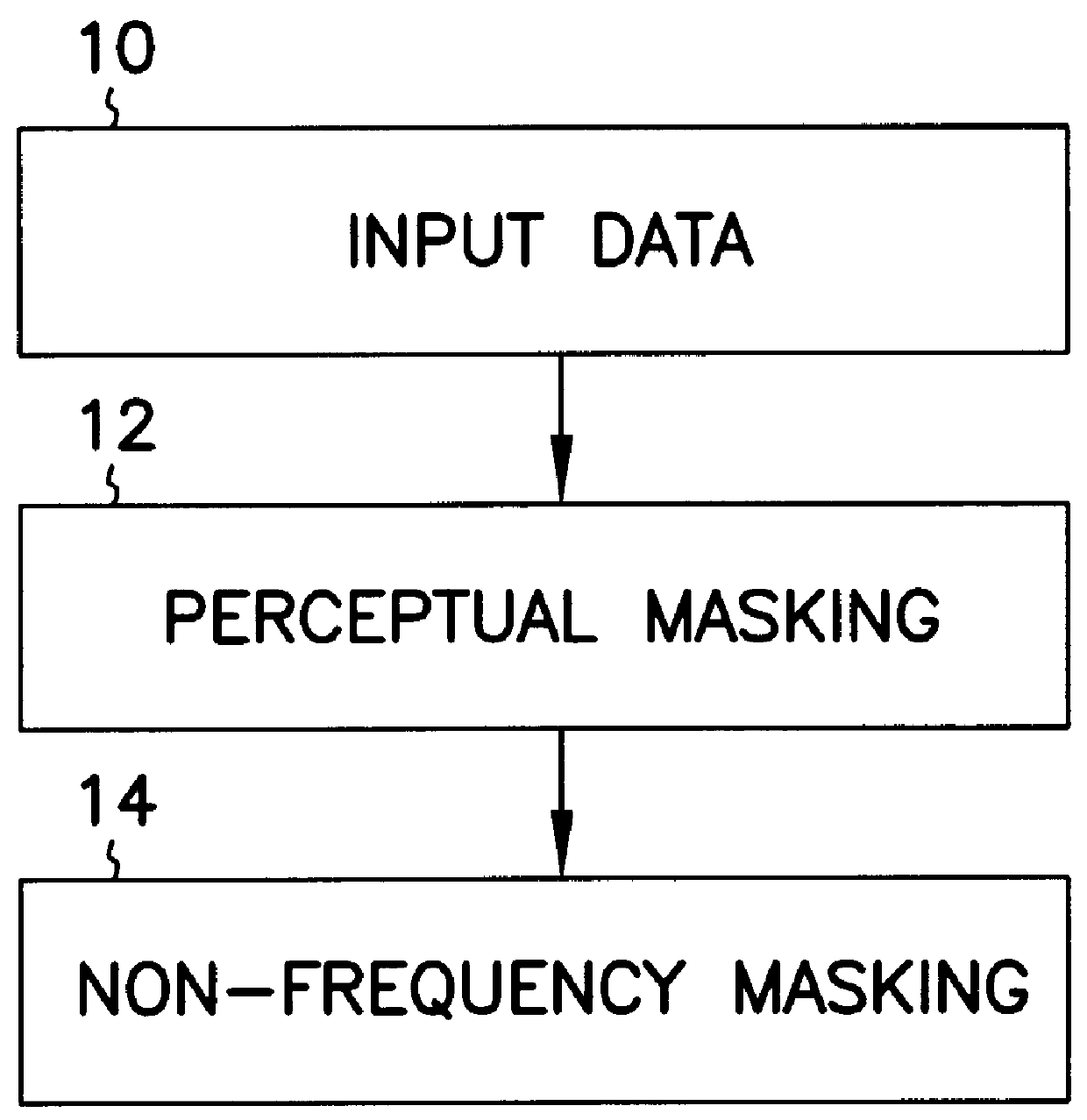
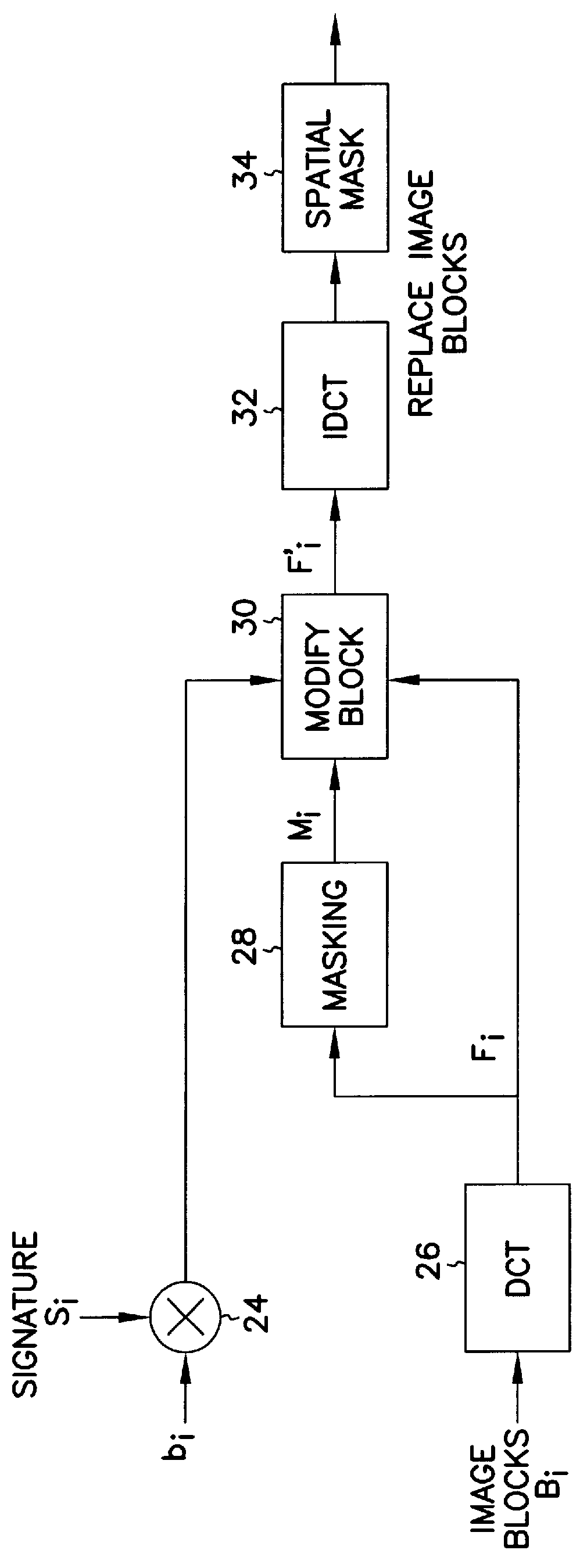
A technique for hiding of data, including watermarks, in human-perceptible images, that is, image host data, is disclosed. In one embodiment a method comprises three steps. In the first step, data to be embedded is inputted. In the case of a watermark, this data is a unique signature, and may be a pseudo-noise (PN) code. In the case of hidden data to be embedded in the host data, this data is the hidden data itself, or the hidden data as spread against the frequency spectrum by a pseudo-noise (PN) code. In the second step, the inputted data is embedded within the host data, in accordance with a perceptual mask of the host data. The perceptual mask determines the optimal locations within the host data to insert the inputted data. In the case of images, these optimal locations are determined by reference to the human visual system. In the third step, the host data, with the embedded data, is further masked by a non-frequency mask. In the case of image data, the non-frequency mask is a spatial mask.
Owner:MINNESOTA RGT UNIV OF A CORP OF MN
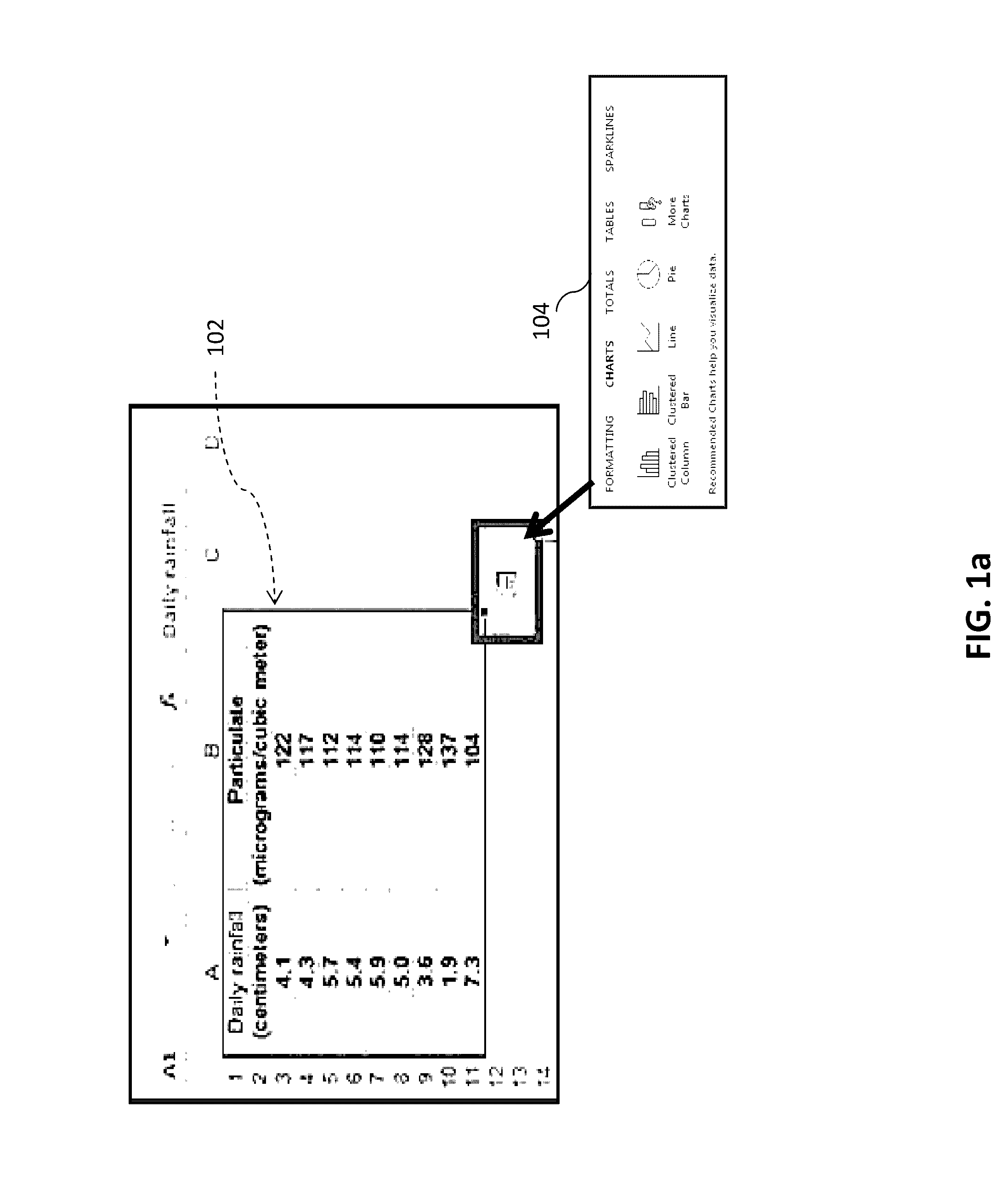
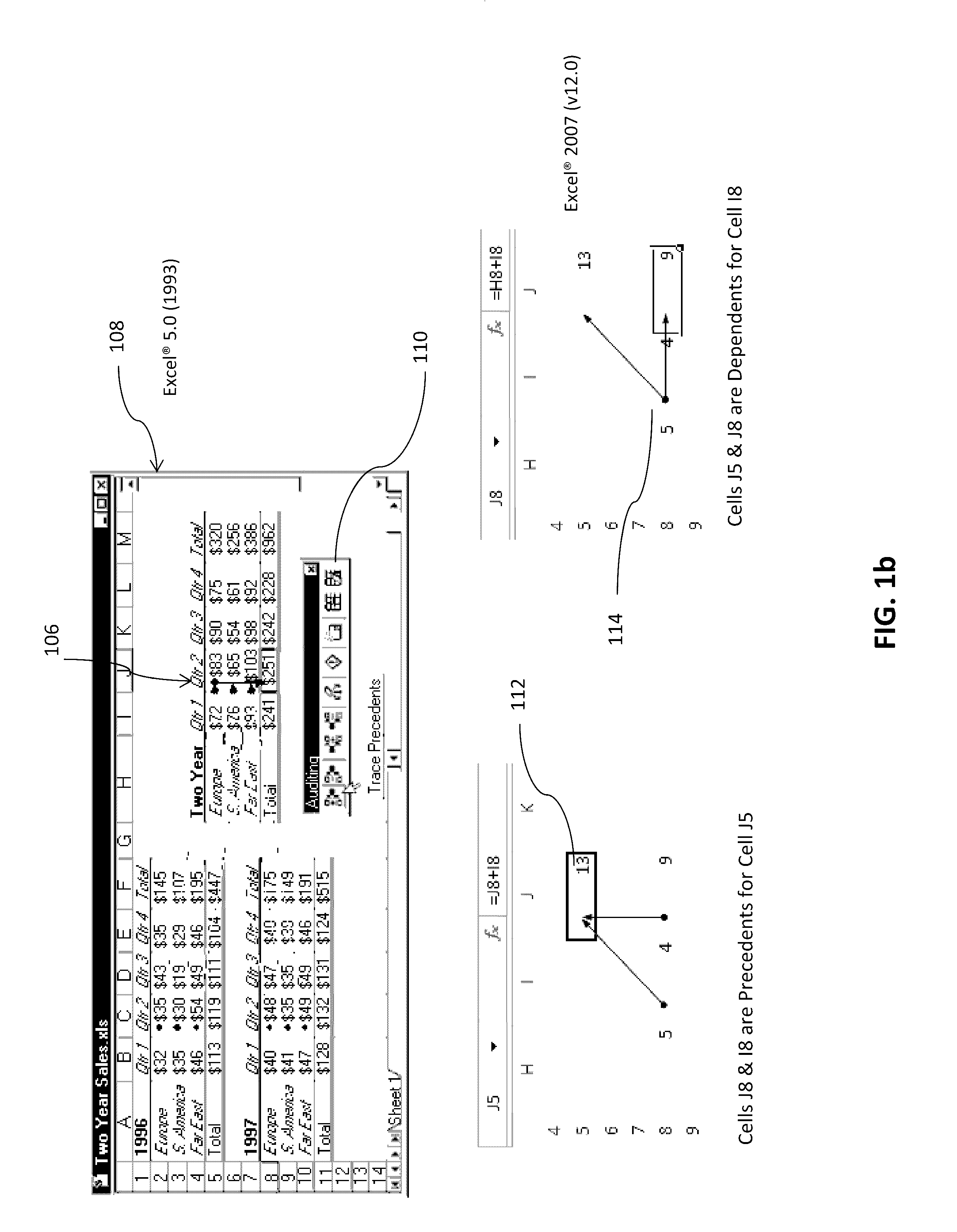
Methods and Systems for Dynamic Graph Generating
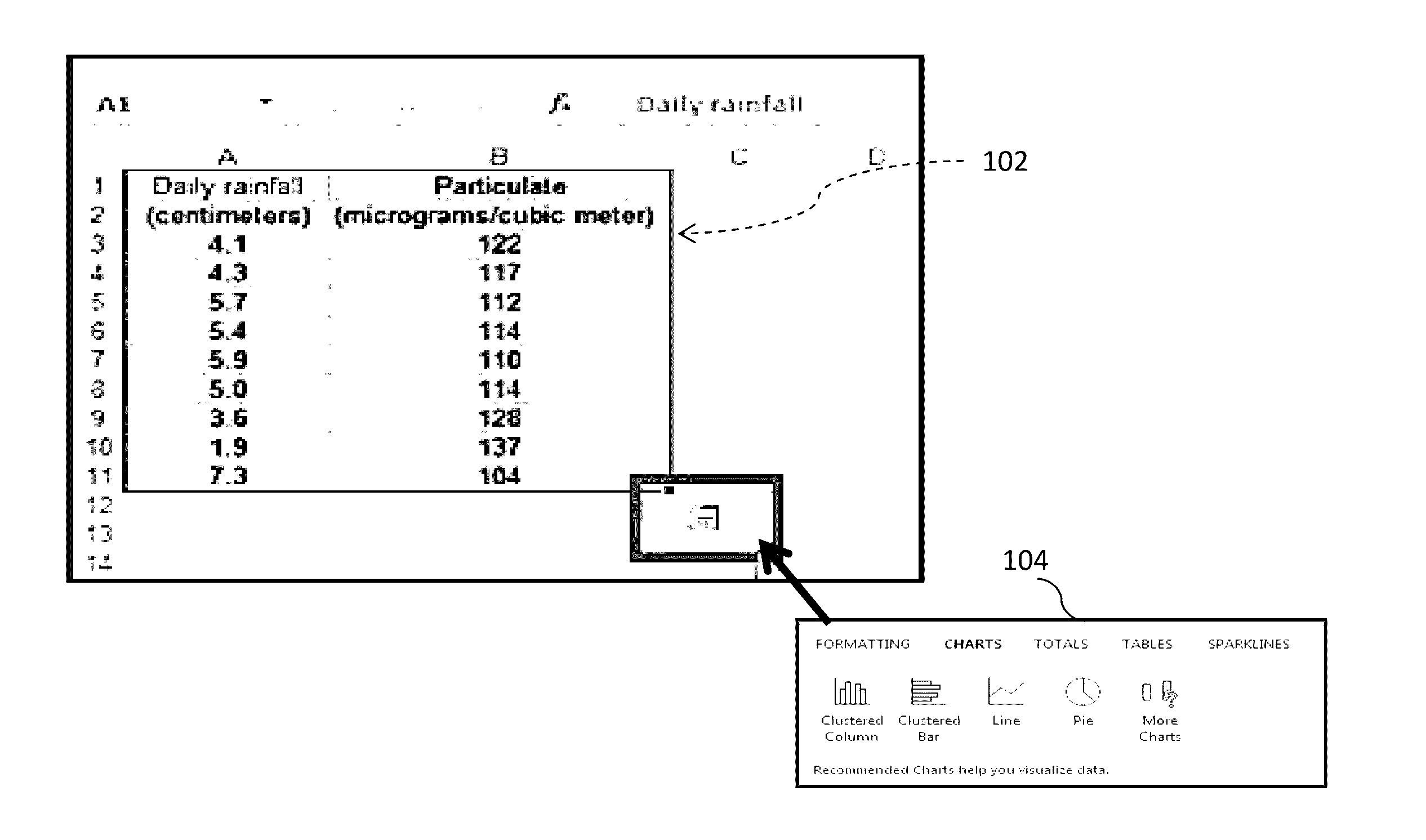
A computer system and method for interrogating and analyzing data. The system may recognize the software application containing data and will search for visible and hidden data including Headers and Labels; and may further interrogate and analyze visible data. The system will preferably create graphical representations based on the analyzed data instantaneously. The graphical representation is configured to be generated dynamically as the selection of data changes; hence it will eliminate the need of selecting data and changing graph types while moving from one data set to other data sets. The data set may be a single point data, a block of data, a highlighted area, a screen grab, tabular, graphical, or textual formatted data. The system and method may analyze the data from various formats and applications such as spreadsheet, PDF file, remote data sources and web based databases etc.
Owner:RITCHIE COLIN FREDERICK +1
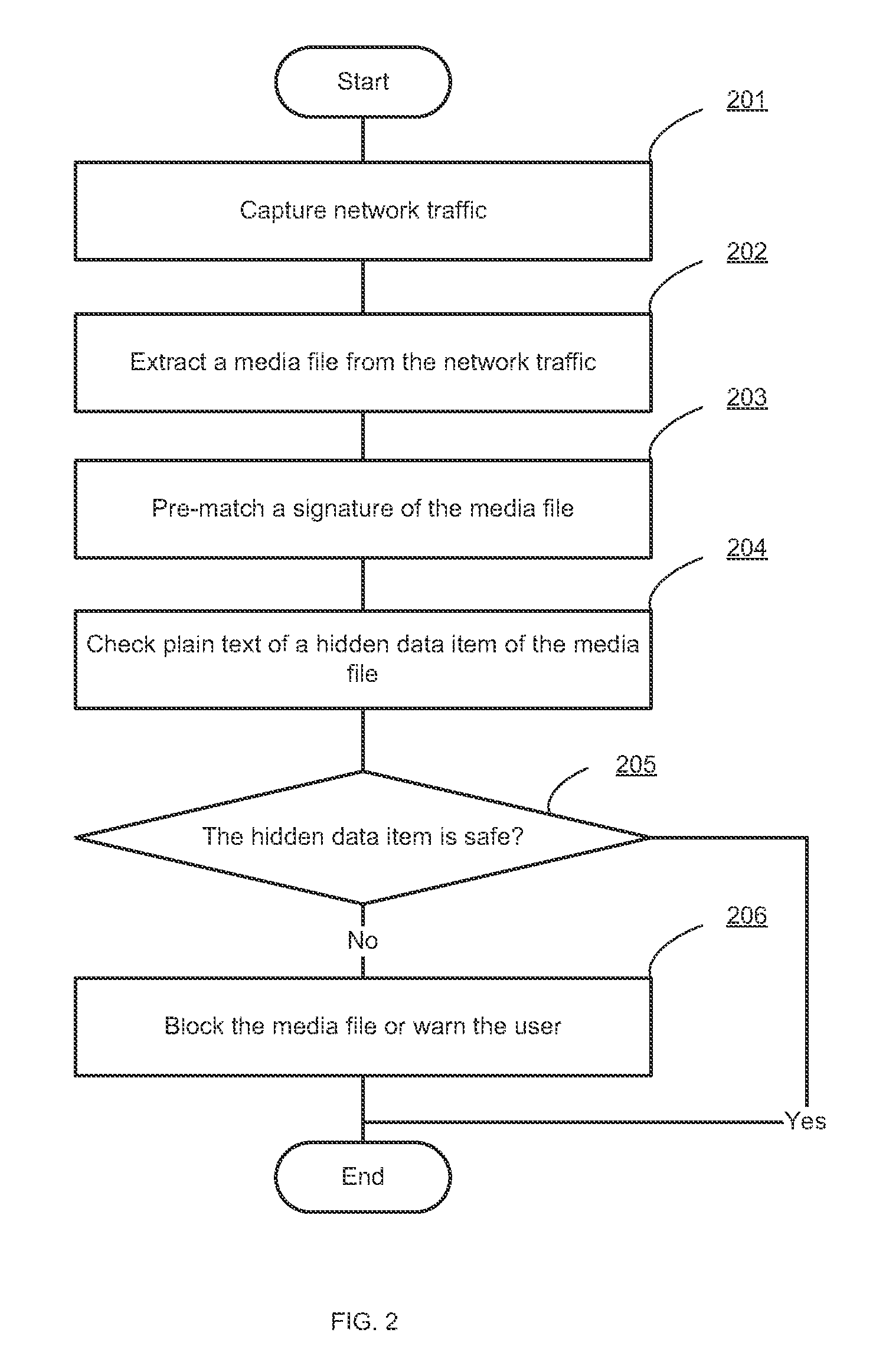
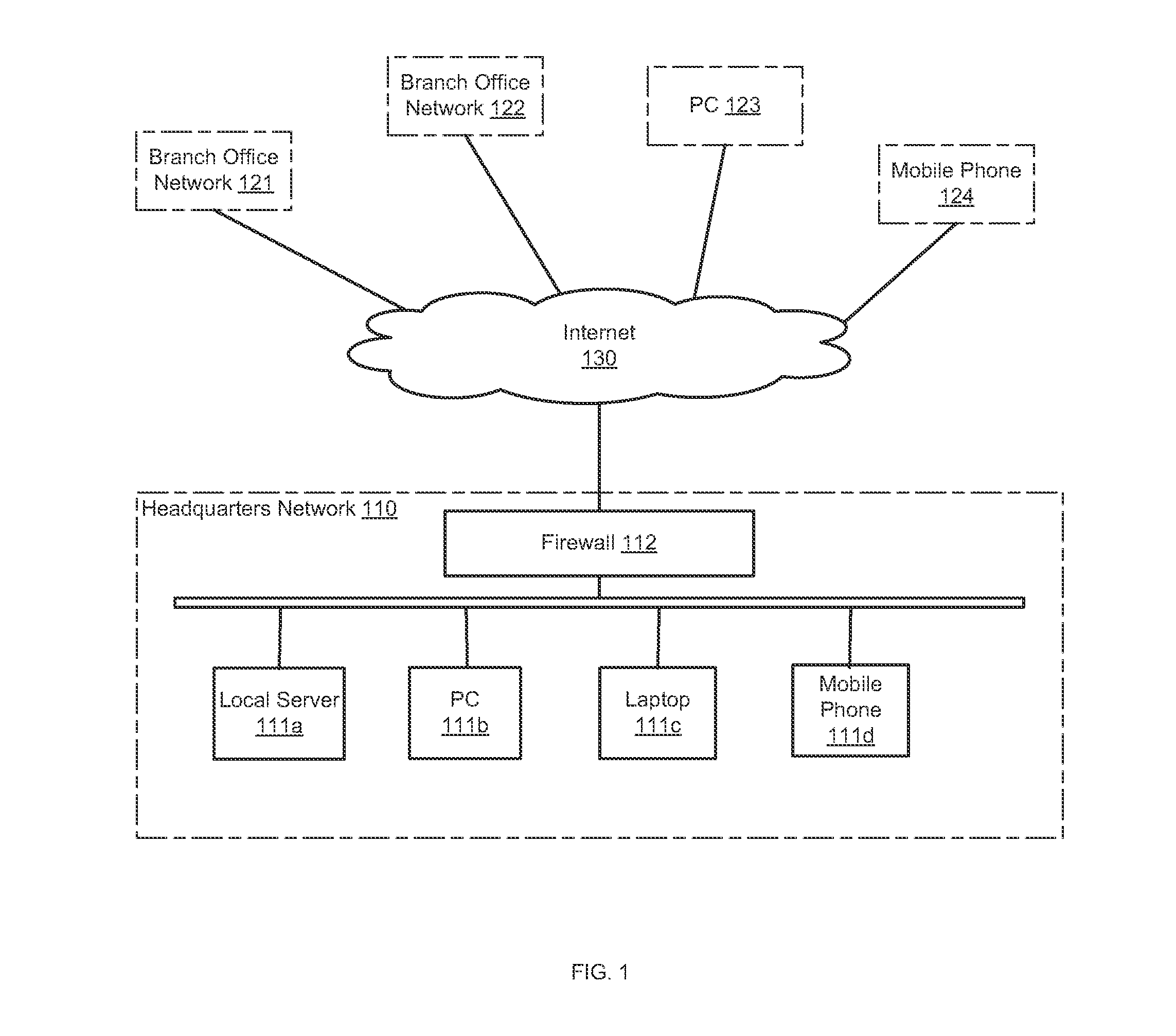
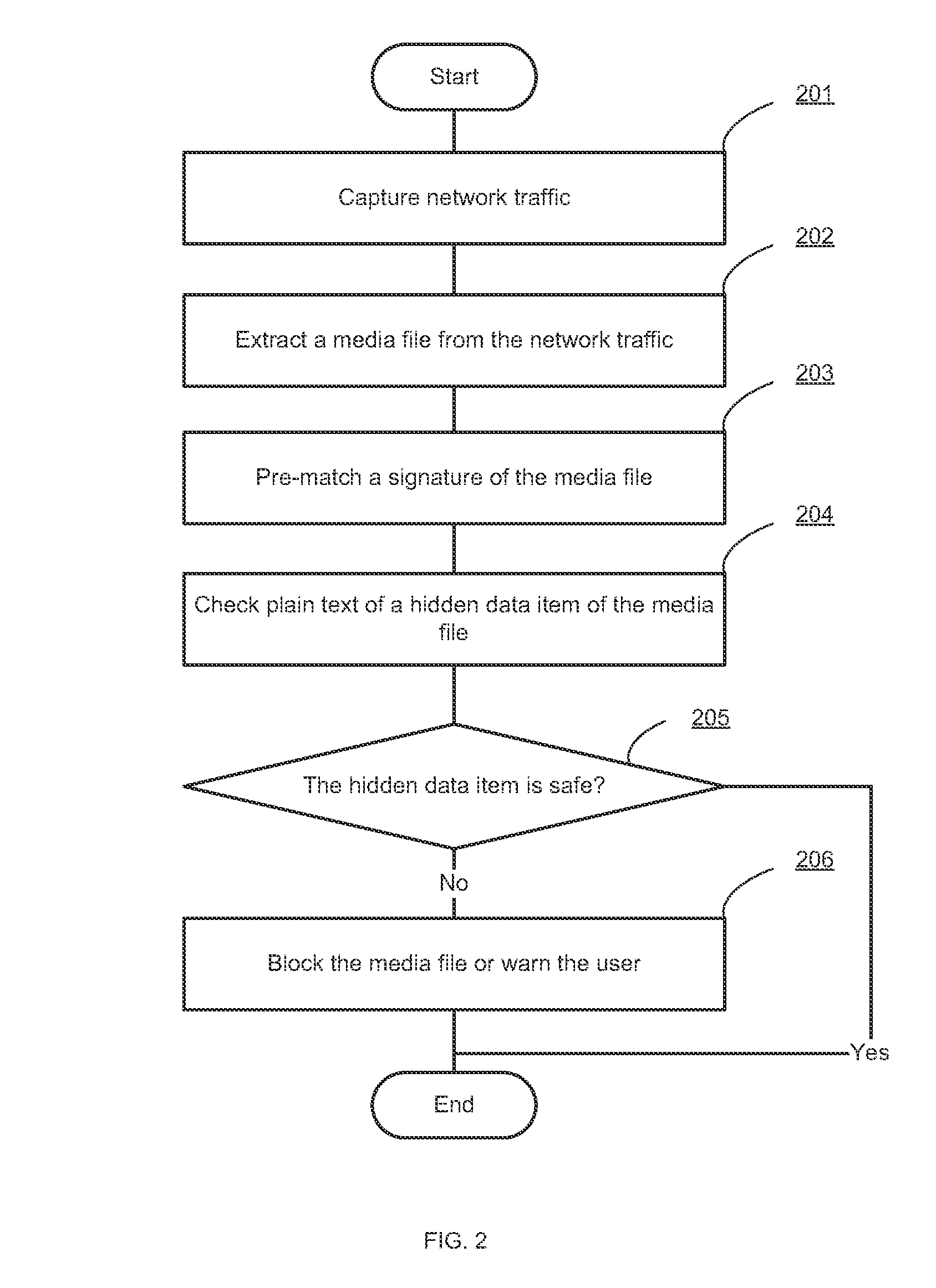
Filtering hidden data embedded in media files
Systems and methods for filtering unsafe content at a network security appliance are provided. According to one embodiment, a network security appliance captures network traffic and extracts a media file from the network traffic. The network security appliance then determines the presence of a hidden data item embedded in the media file in a machine-readable form. When such a hidden data item is identified, the network security appliance performs one or more actions on the media file based on a predefined security policy.
Owner:FORTINET
Data hiding through arrangement of objects
InactiveUS7321667B2User identity/authority verificationCharacter and pattern recognitionHidden dataComputer graphics (images)
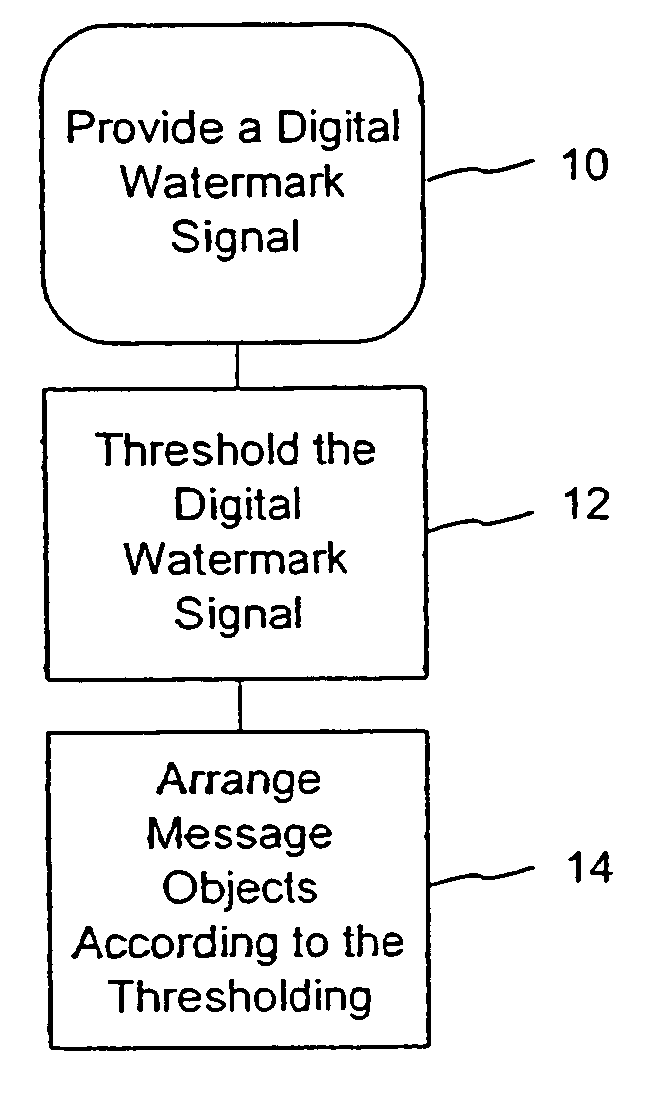
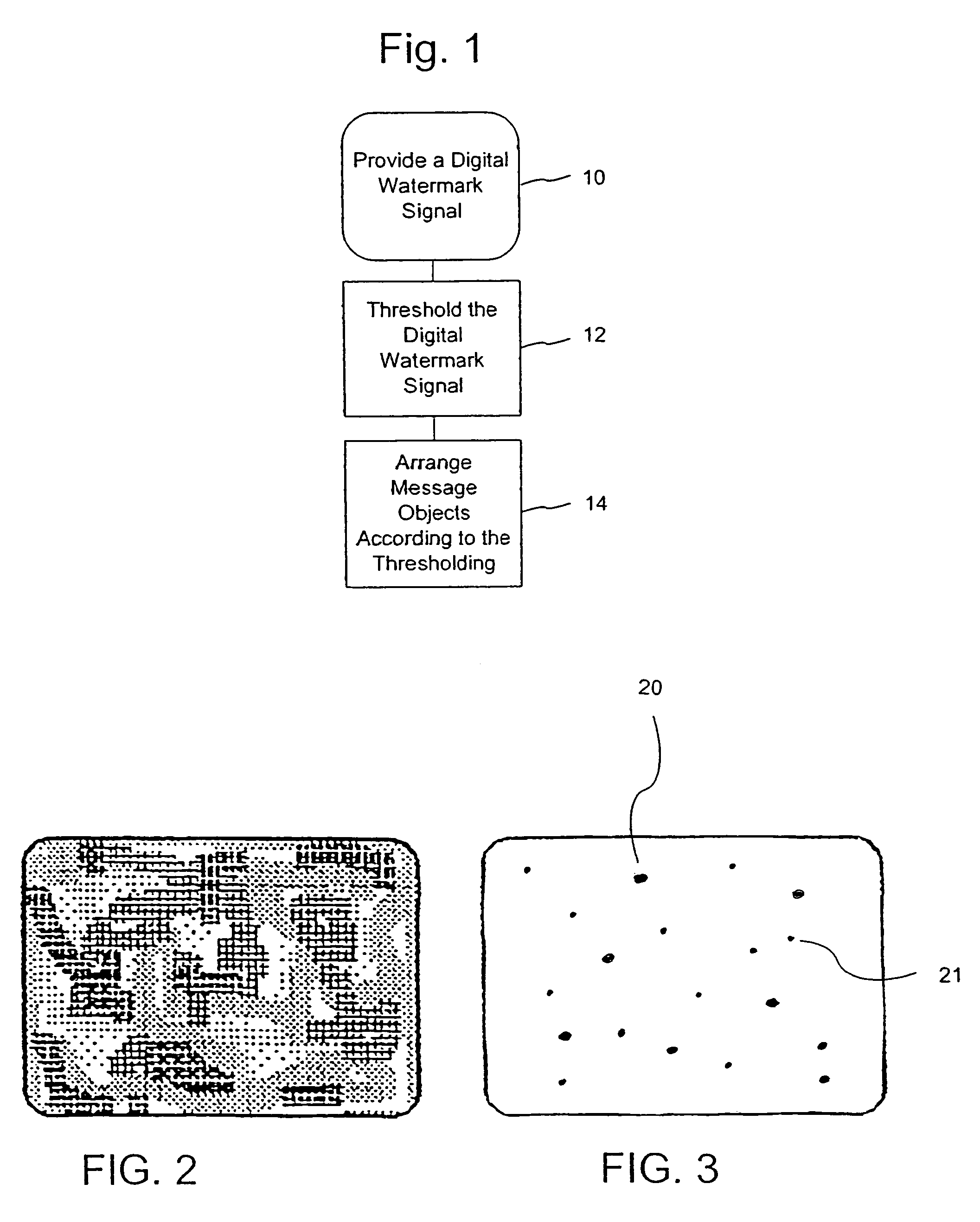
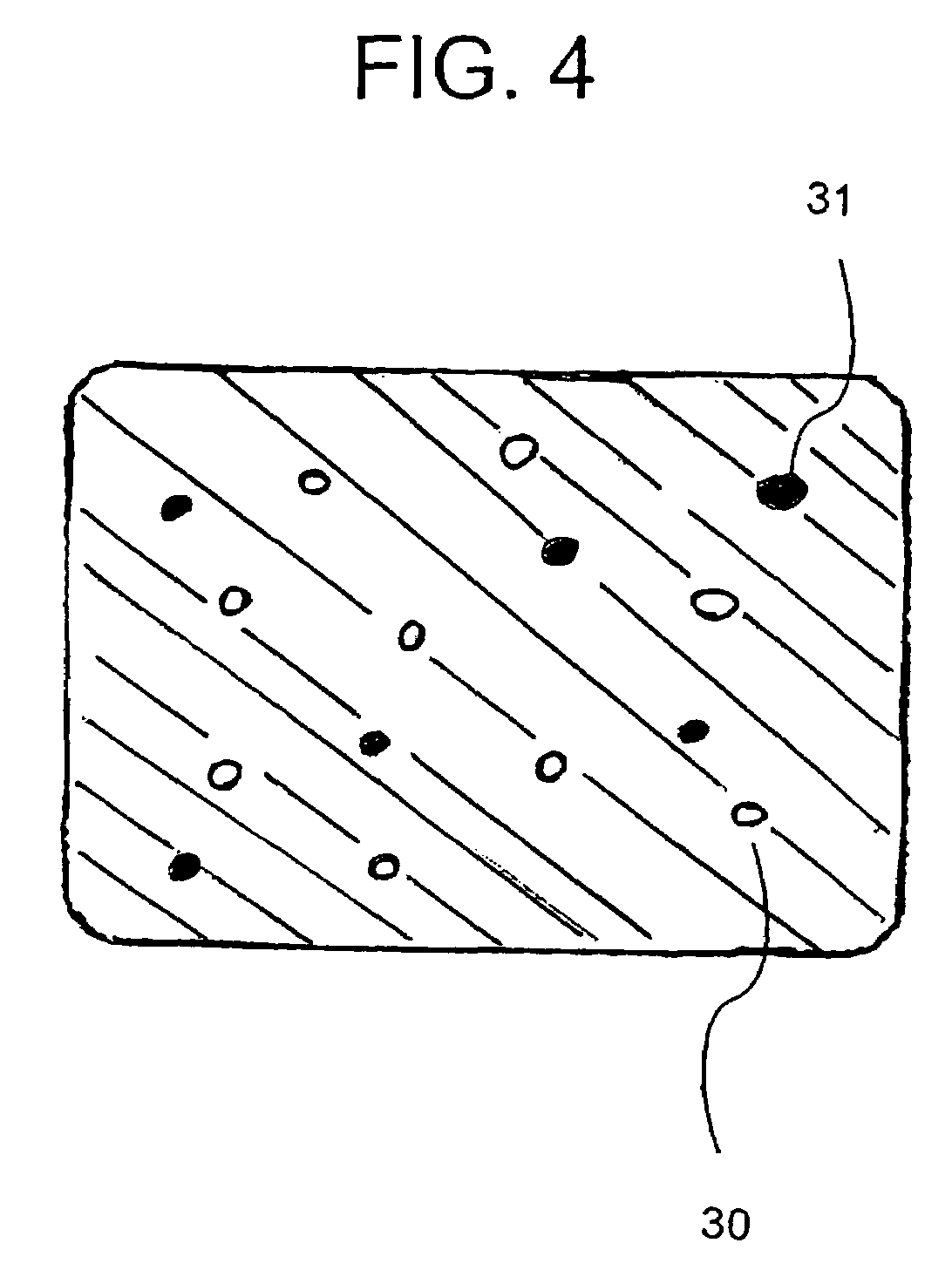
The present invention provides steganographic embedding techniques. A digital watermark signal is reduced to a set of spatial positions. The set of spatial positions sufficiently conveys the digital watermark signal. Message objects are positioned according to the set of spatial positions. Non-message objects are combined with the message objects to form an image or design. The message objects include distinguishable characteristics, e.g., via color, contrast, gray-scale level or luminance, in comparison to the non-message objects. The digital watermark signal is detected by distinguishing the message objects from the non-message objects (e.g., via color or contrast differences) and analyzing the relative placement of the message objects within the image or design.
Owner:DIGIMARC CORP
Computer-implemented method and apparatus for audio data hiding
InactiveUS7058570B1Maximize survivabilityLittle changeSpeech analysisSound producing devicesHidden dataSurvivability
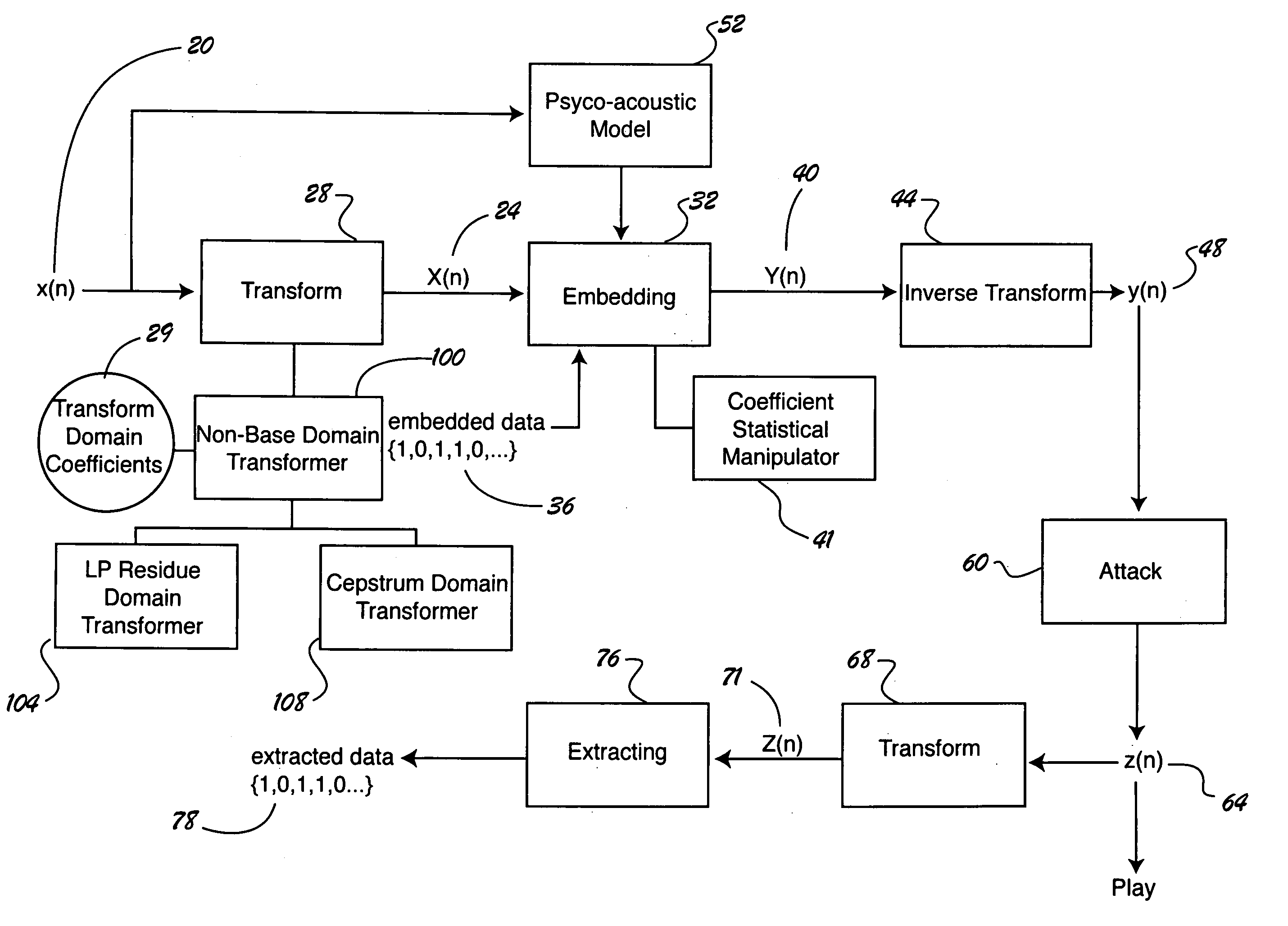
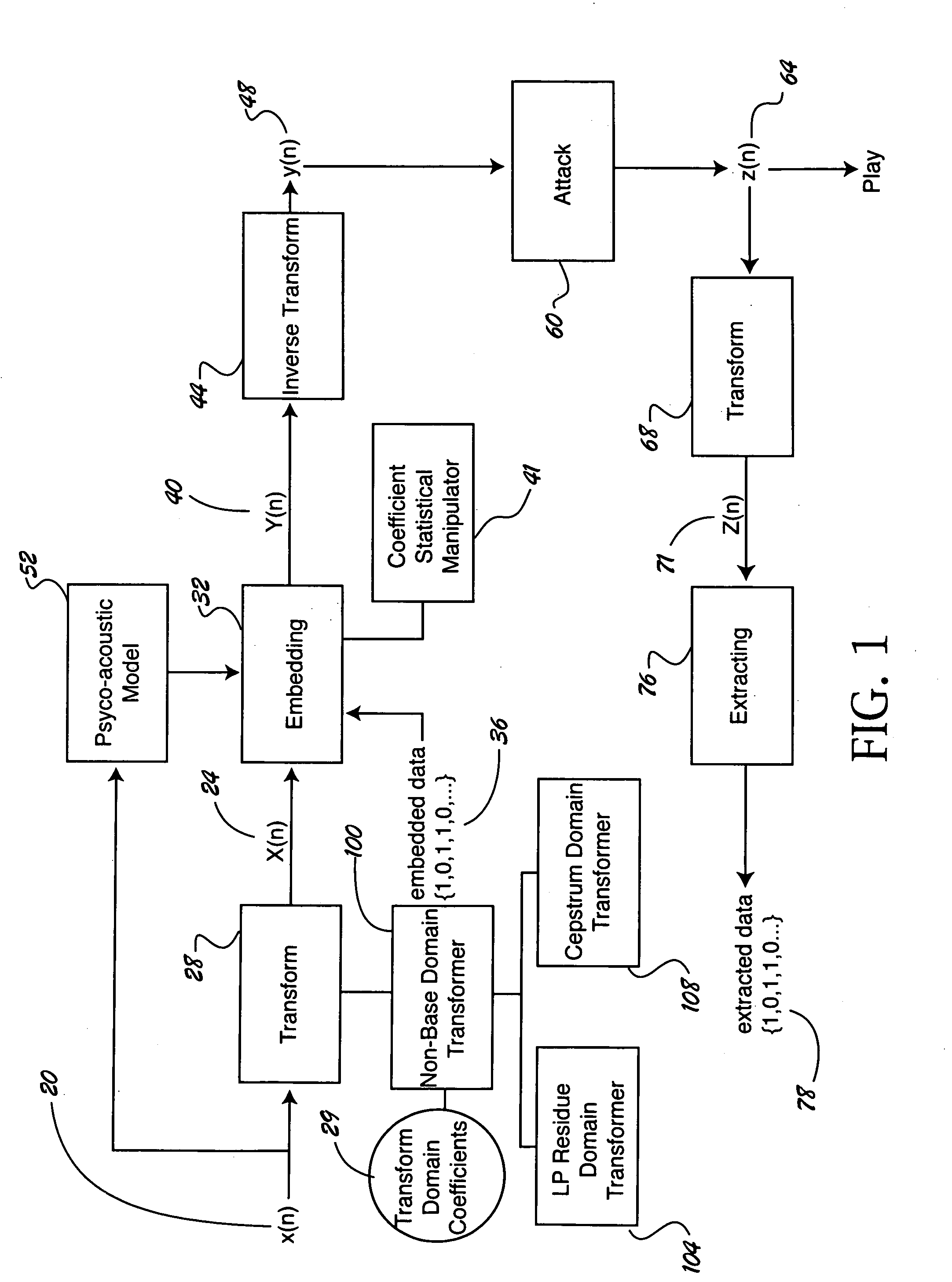
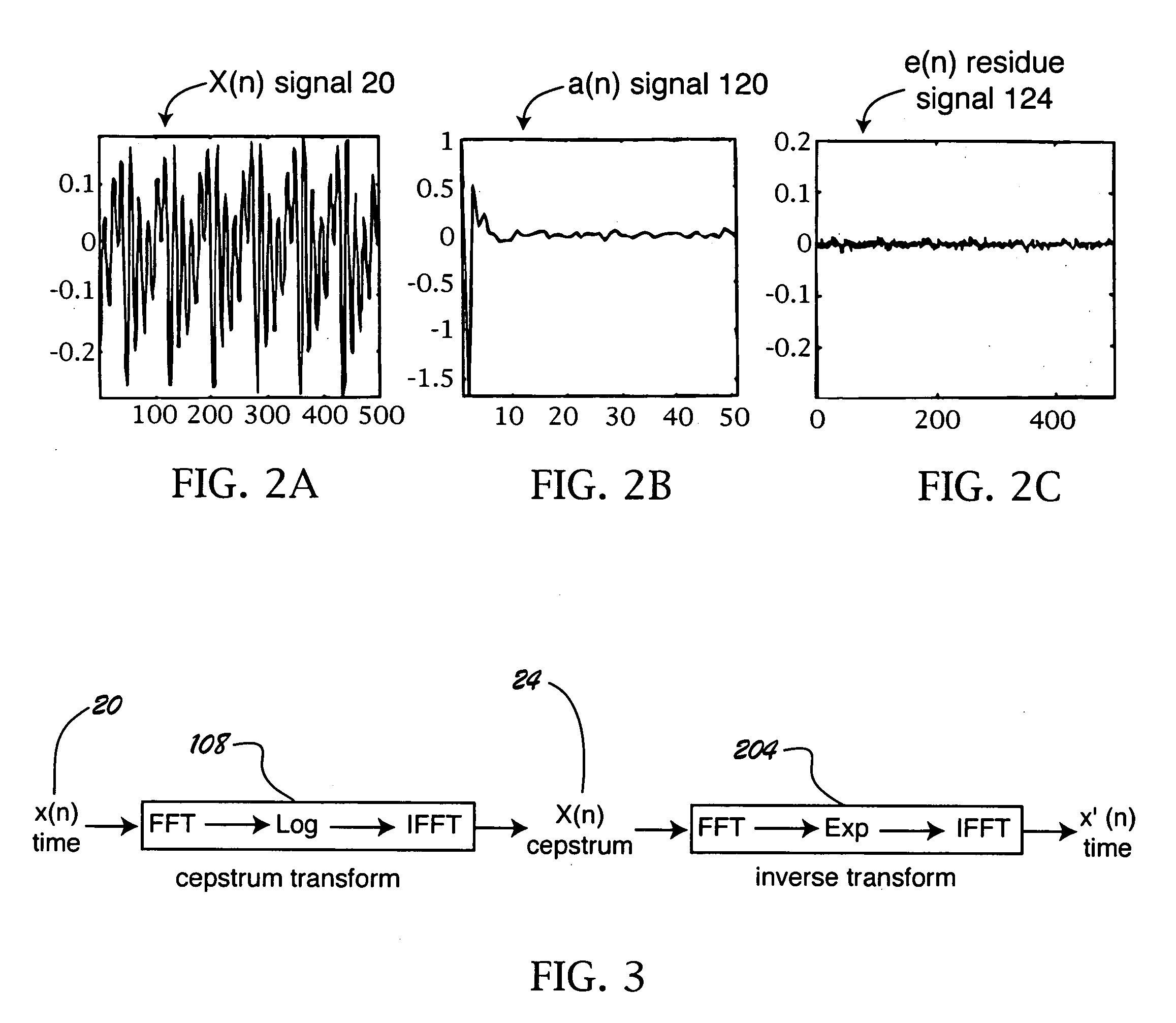
A computer-implemented method and apparatus for embedding hidden data in an audio signal. An audio signal is received in a base domain and then transformed into a non-base domain, such as cepstrum domain or LP residue domain. The statistical mean manipulation is employed on selected transform coefficients to embed hidden data. The introduced distortion is controlled by psychoacoustic model to ensure the imperceptibility of the embedded hidden data. Scrambling techniques can be plugged in to further increase the security of the data hiding system. The present new audio data hiding scheme provides transparent audio quality, sufficient embedding capacity, and high survivability over a wide range of common signal processing attacks.
Owner:PANASONIC CORP
Stealth packet switching
InactiveUS20050094640A1Low probability of interceptReduce probabilityTime-division multiplexData switching by path configurationHidden dataNetwork architecture
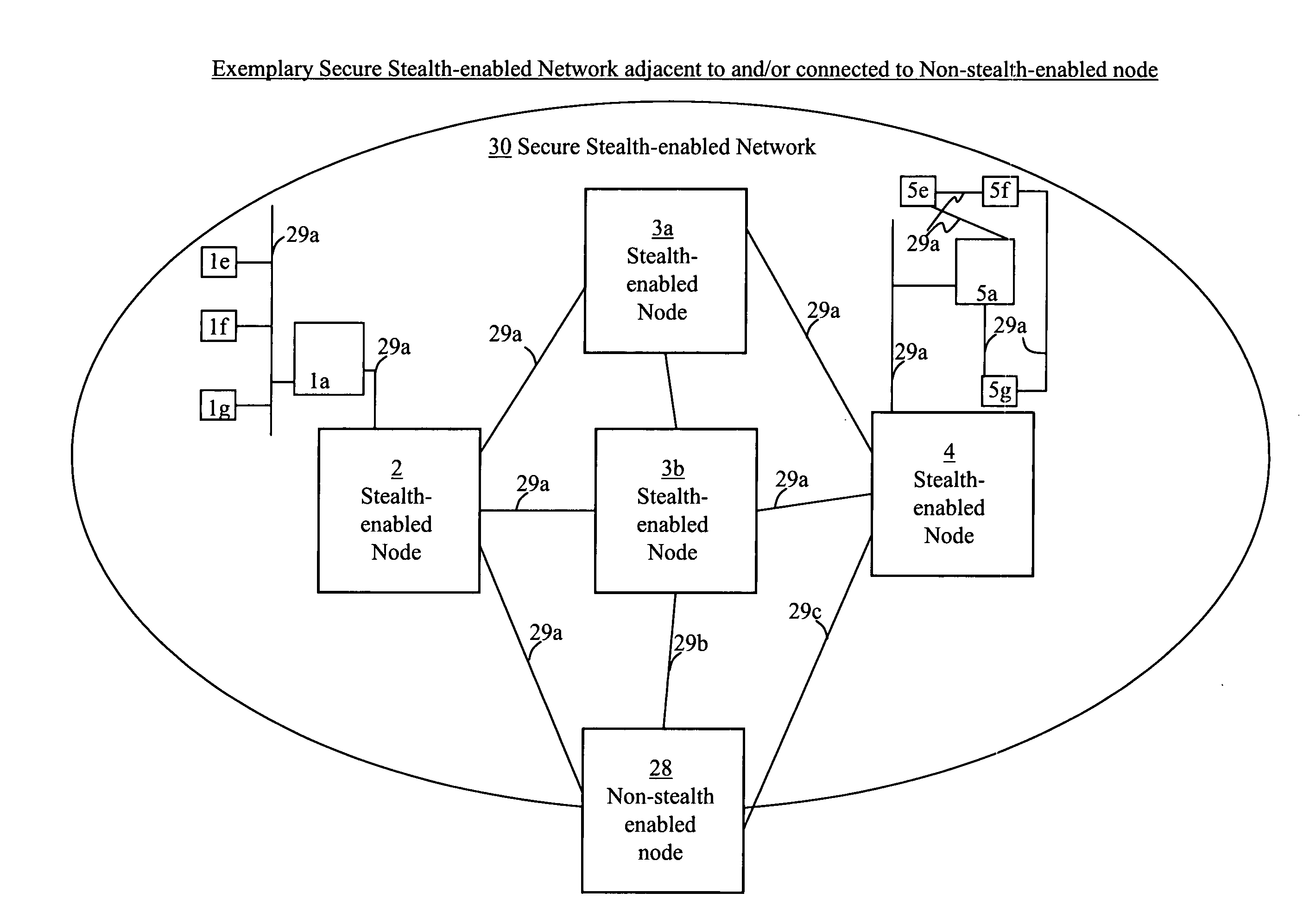
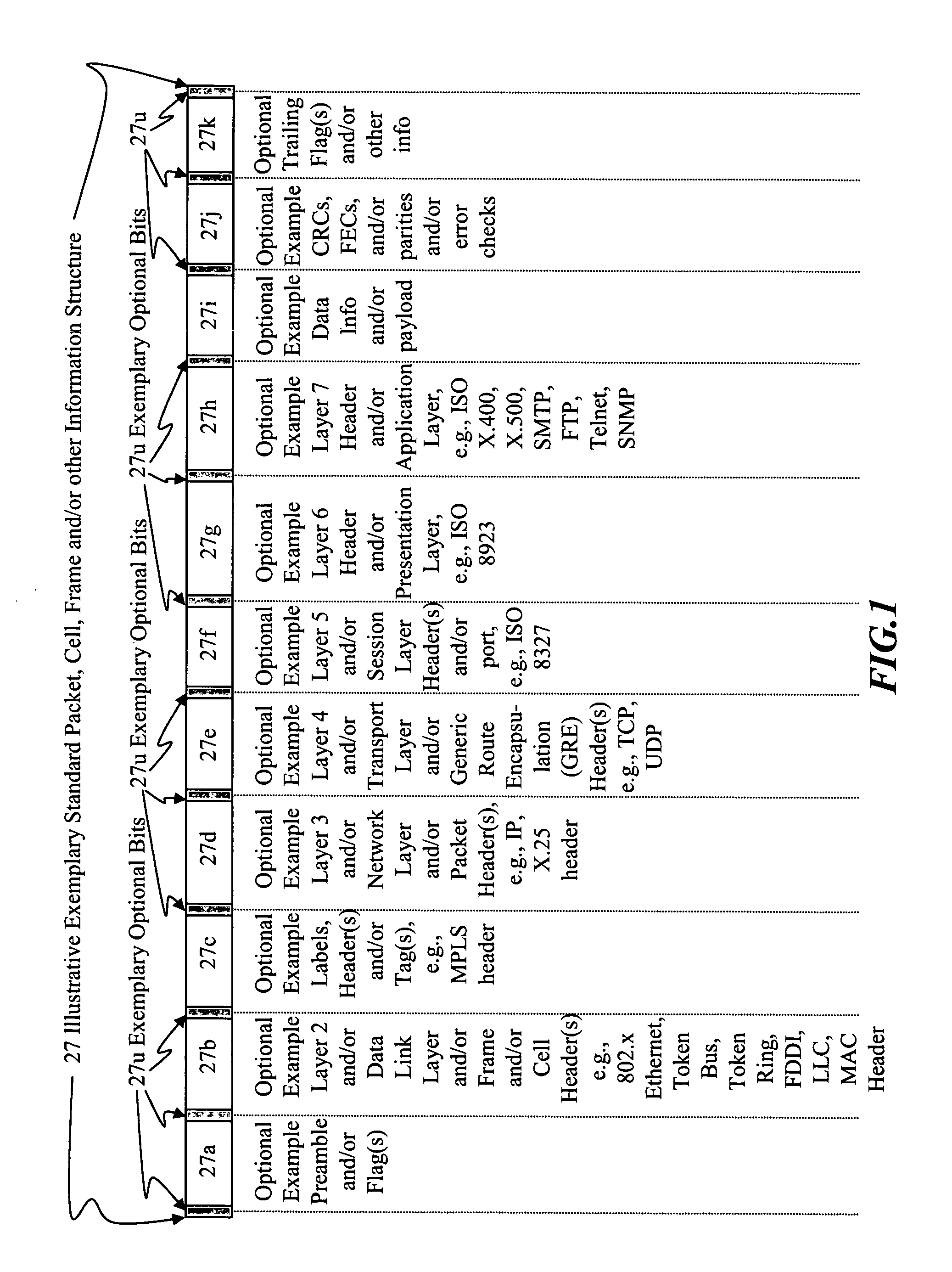
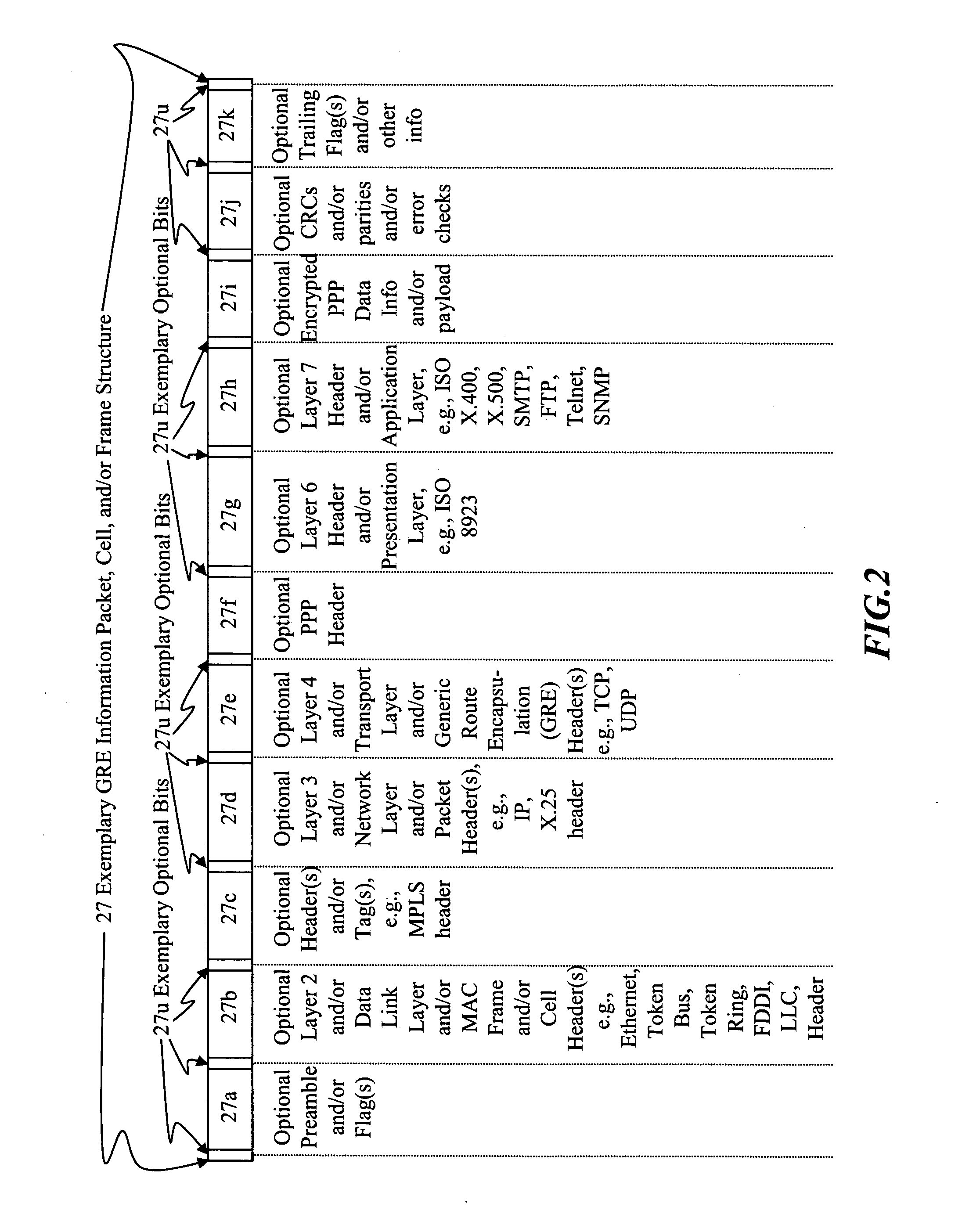
Systems, methods, devices, and network architectures are disclosed for creating and implementing secure wireless, wired, and / or optical stealth-enabled networks using specially modified packets, cells, frames, and / or other “stealth” information structures. This enables stealth packets to have a low probability of detection, a low probability of interception, and a low probability of interpretation. Stealth packets are only detected, intercepted, and correctly interpreted by stealth-enabled network equipment. In its simplest form, stealth packet switching modifies the packet structure, protocols, timing, synchronization, and other elements through various rule-violations. This creates stealth packets, which normal equipment cannot receive correctly, and hence normal equipment discards the stealth packets. Stealth packets may be further enhanced with encryption techniques which focus on encrypting the packet structure itself, as opposed to merely encrypting the data. Using encryption to modify the packet structure itself adds an entirely new level of encryption complexity, thus making the stealth communications orders of magnitude more difficult to decrypt than standard decryption techniques. Combining stealth packets with time-based reservation packet switching enables total encryption of the packet (including header and preamble encryption) capable of routing through multiple hops without decryption of headers and preamble at each hop. Time-based reservation packet switching can also guarantee real-time stealth packet delivery through a network that is totally congested from data storms, virus caused congestion, and / or denial of service attacks.
Owner:HOWE WAYNE RICHARD
Data hiding and extraction methods
InactiveUS6512835B1Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningComputer hardwareArray data structure
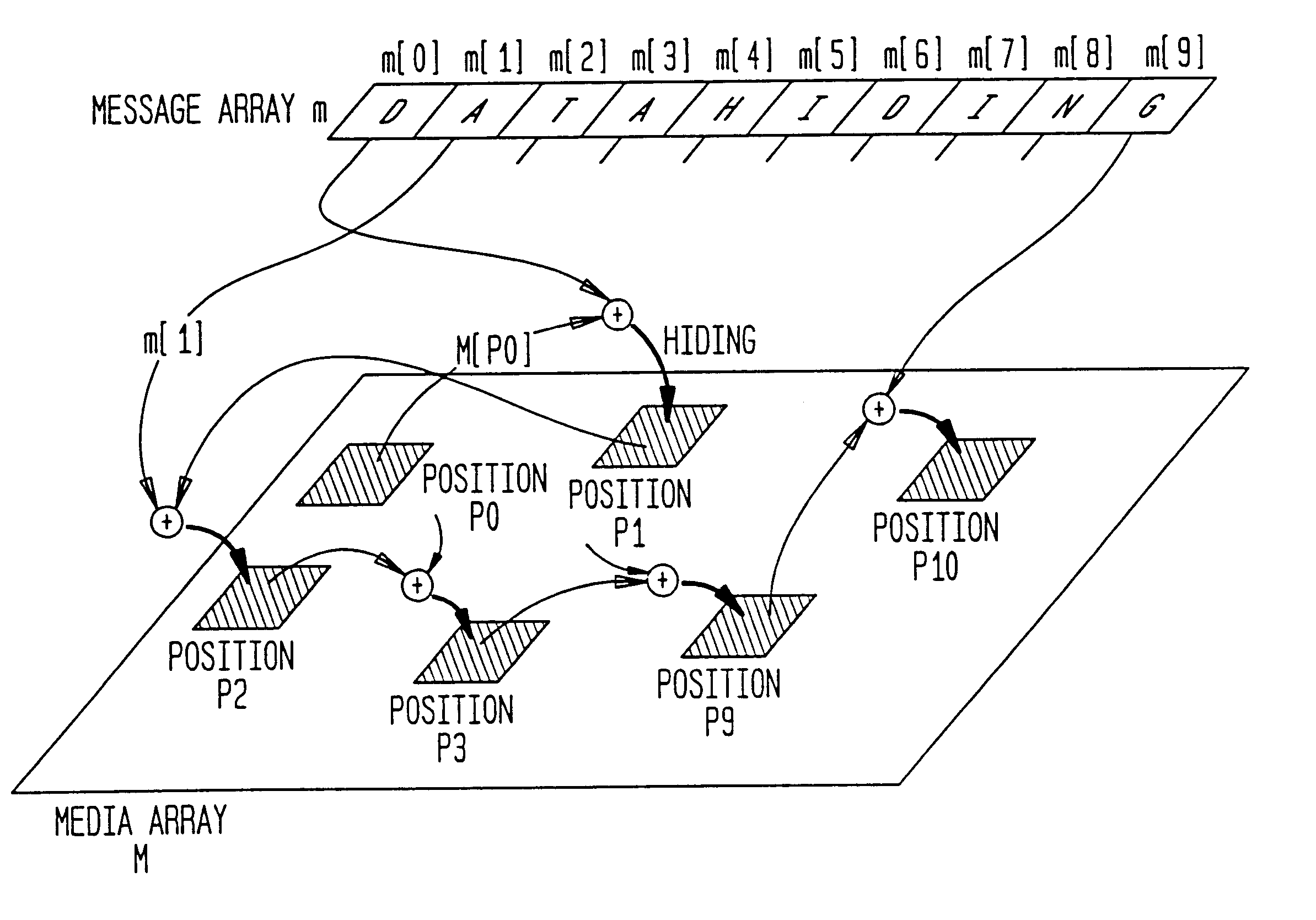
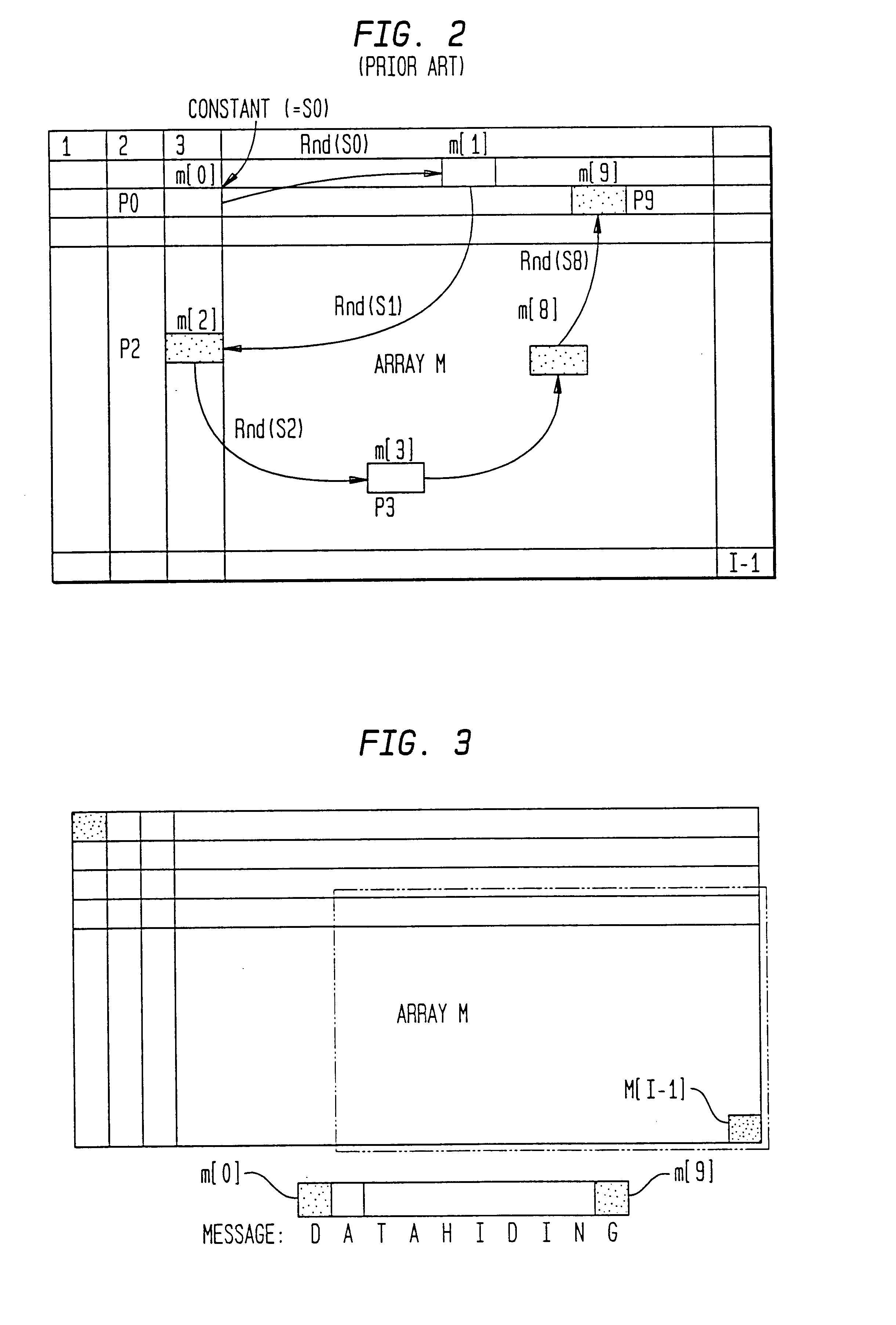
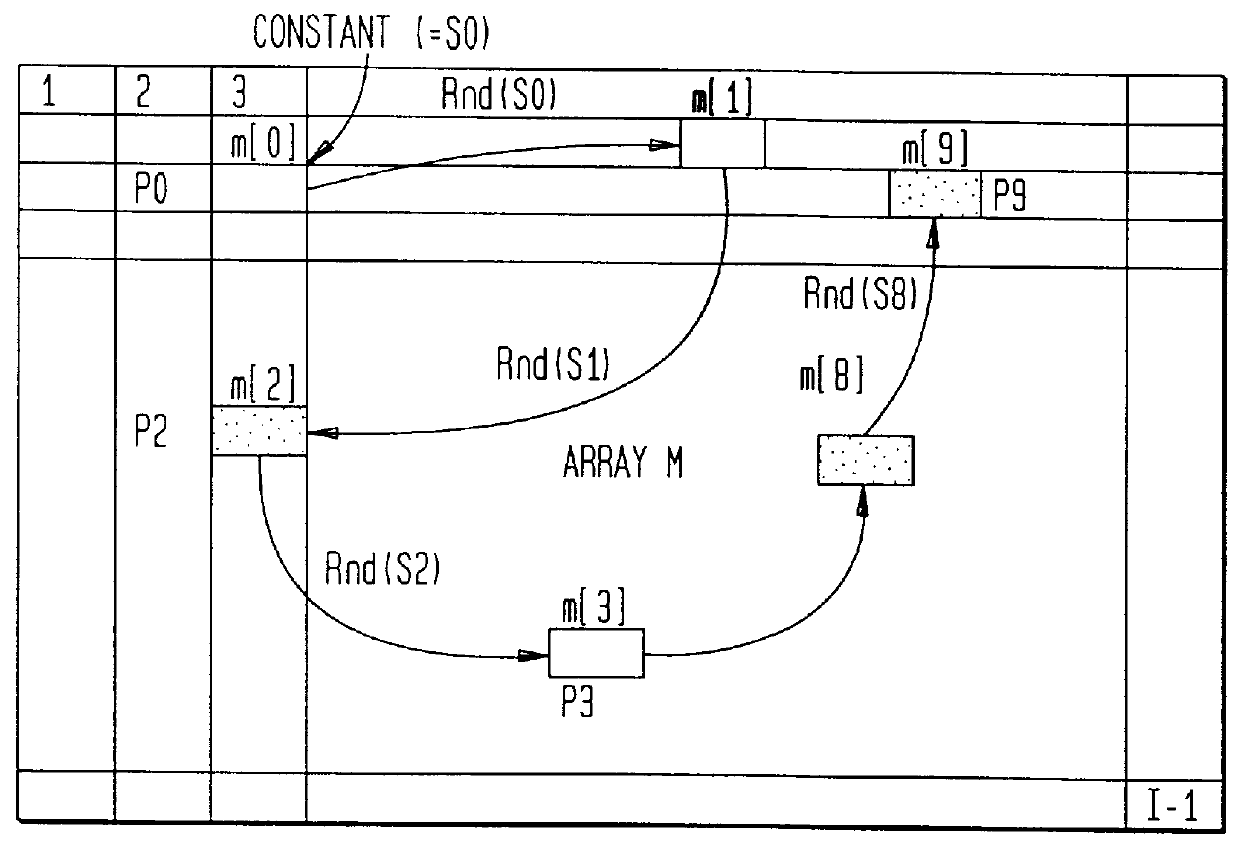
The present invention provides a data hiding method of hiding media data in message data and a data extraction method of extracting the hidden data wherein message data is dispersively hidden in media data such as an image or sound to prevent a third person from modifying the message data easily.More specifically, the present invention relates to a data hiding method in which media data is expressed as a media array while message data is expressed as a message array so that the array elements of the message array can be dispersively hidden in the message array based on a state values specifying a particular array element of the media array, comprising the steps of:(a) determining the j-th (j>=0) state value Sj;(b) determining (j+1)-th state value Sj+1 based on the j-th state value, the array element of the media array indicated by the j-th state value, and the array element of the message array; and(c) hiding data with respect to the array element of the media array indicated by the (j+1)-th state value Sj+1.
Owner:IBM CORP
Just-in-time analytics on large file systems and hidden databases
ActiveUS9244976B1Easy to issueAccurate aggregate estimationDigital data information retrievalSpecial data processing applicationsHidden dataFile system
A just-in-time sampling-based system can, after consuming a small number of disk accesses or queries, produce extremely accurate answers for a broad class of aggregate and top-k queries over a file system or database without the requirement of prior knowledge. The system is efficient, accurate, and scalable. The system performs aggregate estimations of a hidden database through its web interface by employing techniques that use a small number of queries to produce unbiased estimates with small variance. It conducts domain discovery over a hidden database through its web interface by employing techniques which provide effective guarantees on the effectiveness of domain discovery. Systems and methods enhance forms used by mobile devices to access hidden databases. It employs data analytics to improve the usage of form fields, including providing context-sensitive auto-completion suggestions, highlighting selections in drop-down boxes and eliminating suggestions in drop-down boxes.
Owner:GEORGE WASHINGTON UNIVERSITY +1
Method for protecting mobile phone private data
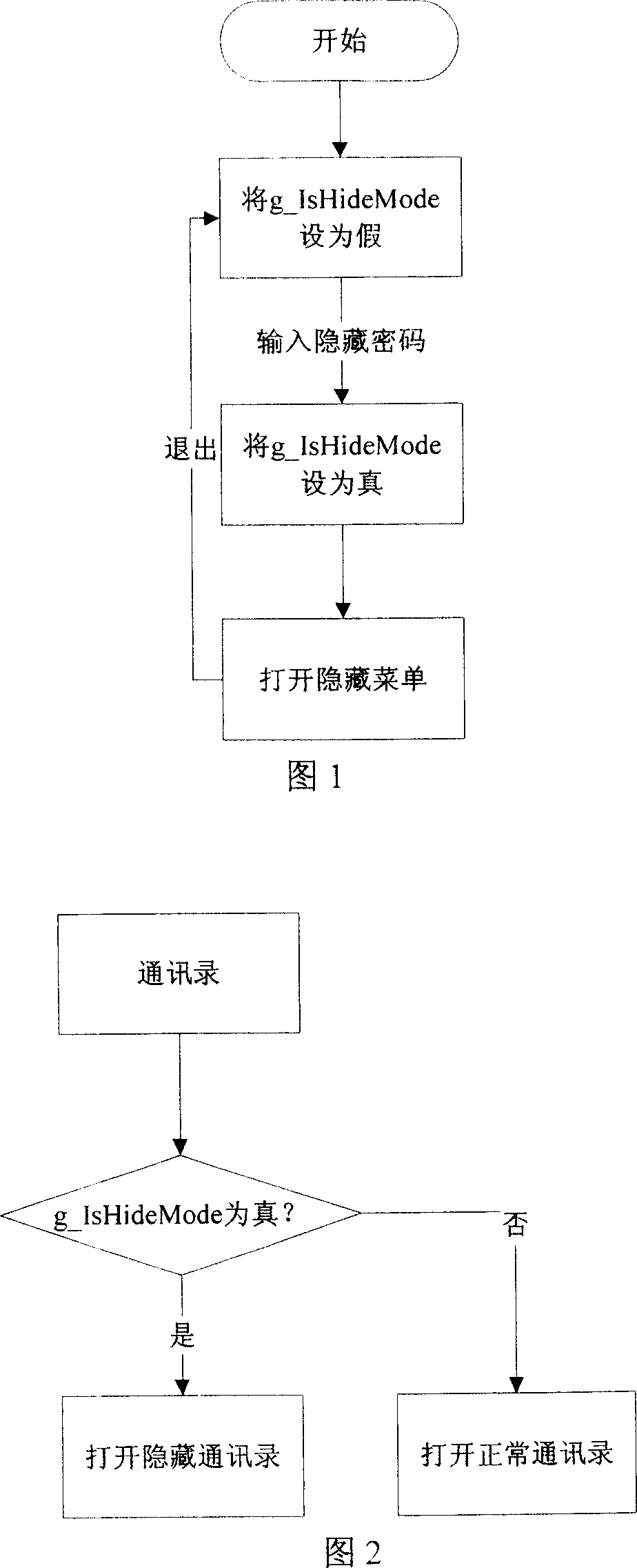
InactiveCN101026822AImprove protectionFeel free to viewDigital data processing detailsDigital data protectionComputer hardwareHidden data
Interfaces of handset are divided into two modes: hidden and normal. A global variable parameter is setup. When being as 1, 2, n or true, the value of the parameter denotes that current mode is hidden; when being as 0, or false, the value of the parameter denotes that current mode is normal. Moreover, a parameter variable of file is set up. When being as 1, 2, n or true, the file is marked as hidden attribute; when being as 0, or false, the file is marked as normal attribute in order to save and display private data or normal data. Key in hidden cipher of handset makes switch between hidden mode and normal mode. Thus, owner of handset can look normal data and hidden data, and non-owner can only look normal data so as to protect all private data. Features are: simple operation and smart method for setting up cipher.
Owner:江苏高通科技实业有限公司
System and method for hiding and extracting message data in multimedia data
The present invention provides a data hiding method of hiding media data in message data and a data extraction method of extracting the hidden data wherein message data is dispersively hidden in media data such as an image or sound to prevent a third person from modifying the message data easily. More specifically, the present invention relates to a data hiding method in which media data is expressed as a media array while message data is expressed as a message array so that the array elements of the message array can be dispersively hidden in the message array based on a state values specifying a particular array element of the media array, comprising the steps of: (a) determining the j-th (j> / =0) state value Sj; (b) determining (j+1)-th state value Sj+1 based on the j-th state value, the array element of the media array indicated by the j-th state value, and the array element of the message array; and (c) hiding data with respect to the array element of the media array indicated by the (j+1)-th state value Sj+1.
Owner:IBM CORP
High bandwidth memory management using multi-bank DRAM devices
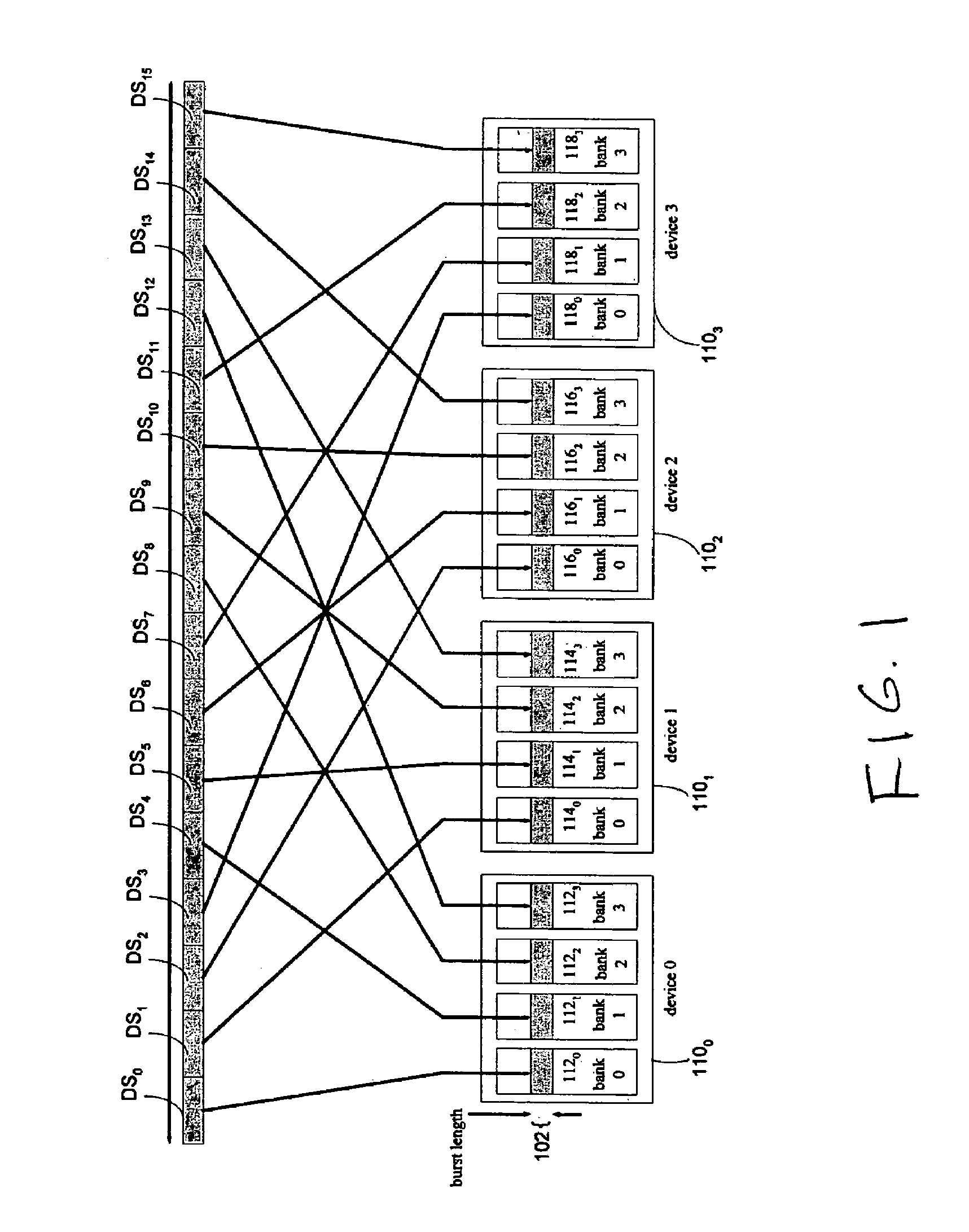
InactiveUS7296112B1Performance maximizationHigh bandwidthMemory adressing/allocation/relocationHidden dataData segment
The disclosure describes implementations for accessing in parallel a plurality of banks across a plurality of DRAM devices. These implementations are suited for operation within a parallel packet processor. A data word in partitioned into data segments which are stored in the plurality of banks in accordance with an access scheme that hides pre-charging of rows behind data transfers. A storage distribution control module is communicatively coupled to a memory comprising a plurality of storage request queues, and a retrieval control module is communicatively coupled to a memory comprising a plurality of retrieval request queues. In one example, each request queue may be implemented as a first-in-first-out (FIFO) memory buffer. The plurality of storage request queues are subdivided into sets as are the plurality of retrieval queues. Each is set is associated with a respective DRAM device. A scheduler for each respective DRAM device schedules data transfer between its respective storage queue set and the DRAM device and between its retrieval queue set and the DRAM device independently of the scheduling of the other devices, but based on a shared criteria for queue service.
Owner:CISCO TECH INC
Spectral edge marking for steganography or watermarking
InactiveUS20130335783A1Massive absorptionVisual presentation using printersRecord carriers used with machinesPrint mediaSpectral edge
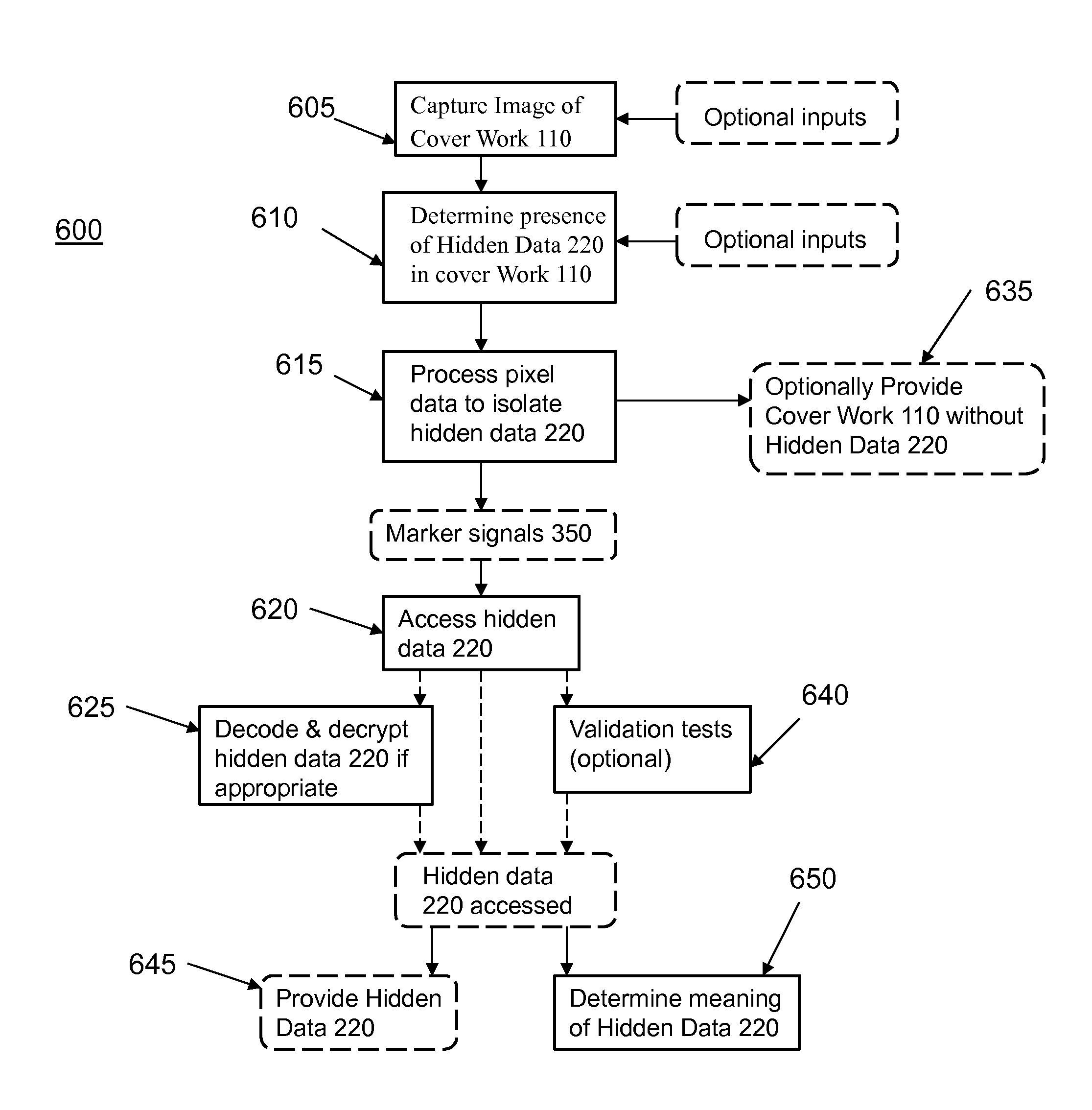
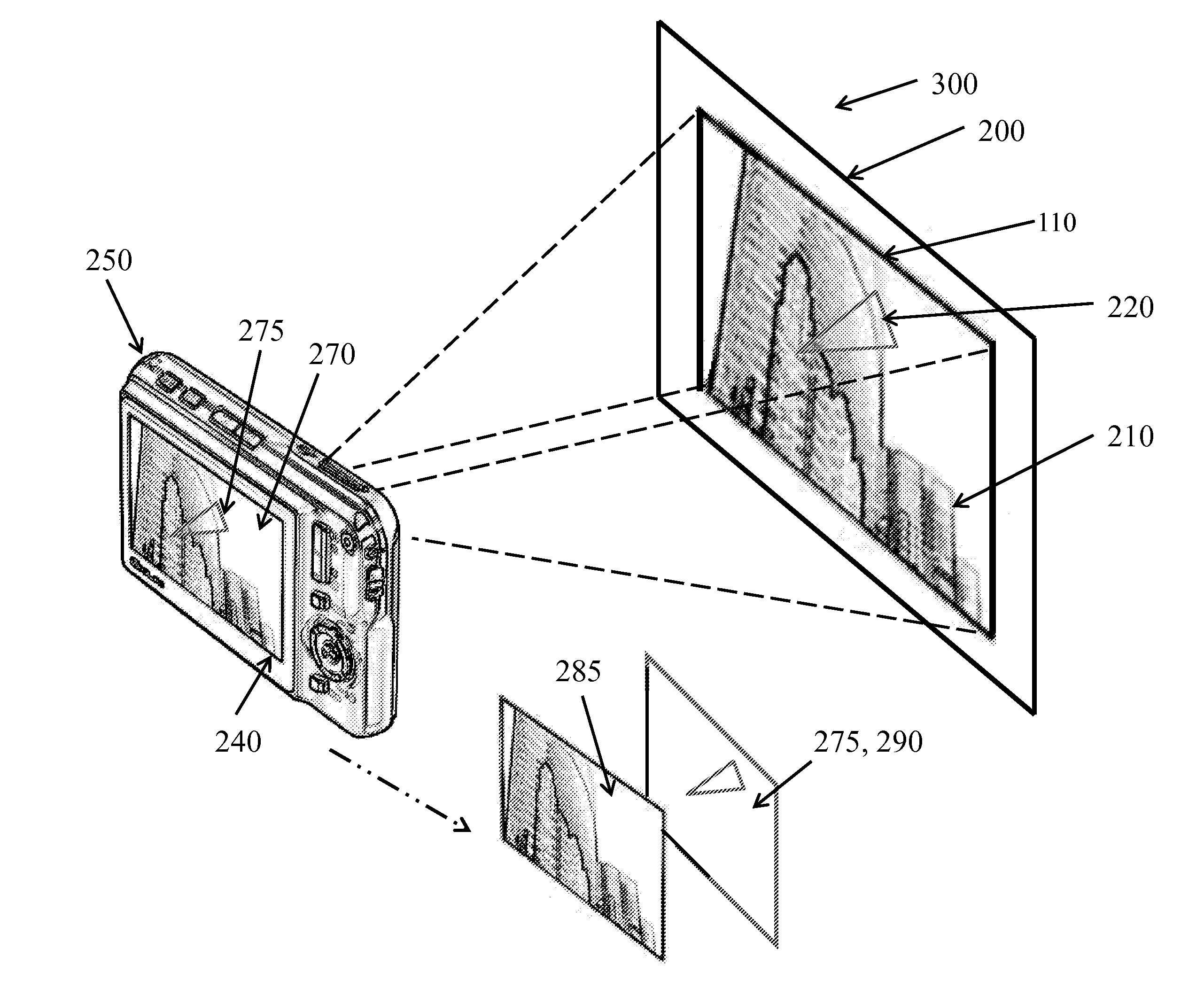
A print media (200) comprises paper or other substrate, on which image content, whether text or images are printed with accompanying hidden data (220). The image content is printed with one or more normal printing process visible colorants (340), while the hidden data (220) is printed with spectral edge markers (320). The spectral edge marker materials (320) have a substantial spectral absorption just outside the human visible spectrum, and only slight visible absorption, which is masked by the visible colorants (340). Although the hidden data is nominally visually imperceptible, an image capture device (250) having a visible spectral response that extends into a spectral region just outside the visible spectrum where the spectral edge marker absorption occurs, can then detect the hidden data.
Owner:EASTMAN KODAK CO
Spectral edge marking for steganography or watermarking
InactiveUS20130336525A1Massive absorptionPaper-money testing devicesPattern printingSpectral edgePrint media
A system for detecting visibly hidden content on a print media (200) in which image content is printed with one or more normal printing process visible colorants (340), and which further includes embedded hidden data (220) printed with spectral edge markers (320). These spectral edge marker materials (320) have a substantial spectral absorption just outside the human visible spectrum, either at the UV edge or IR edge, but only slight visible absorption which is masked by the visible colorants (340). Although the hidden data is nominally visually imperceptible, an image capture device (250) having a visible spectral response from at least one spectrally distinct color imaging channel that extends into a spectral region just outside the visible spectrum where the spectral edge marker absorption occurs, can then detect the hidden data.
Owner:EASTMAN KODAK CO
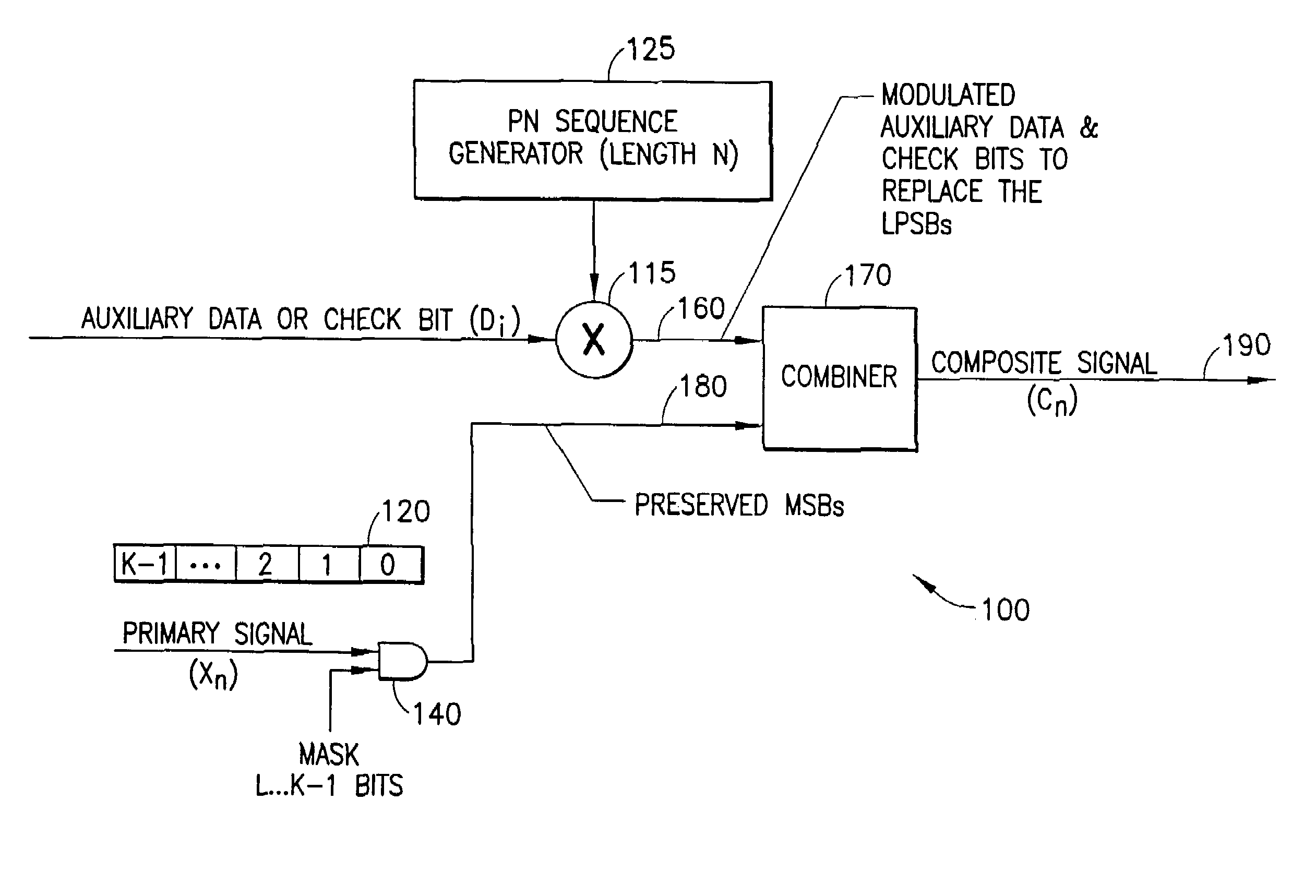
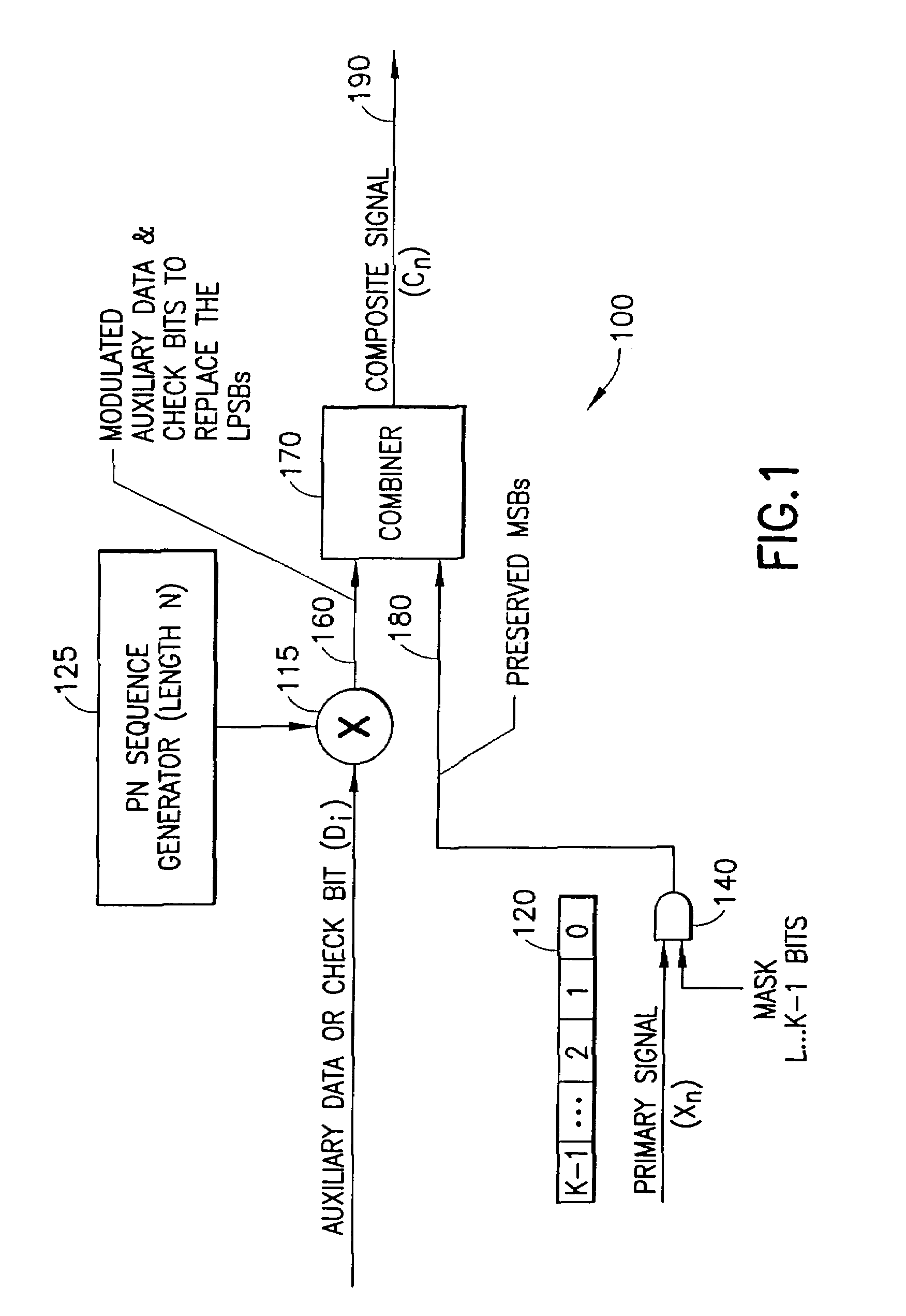
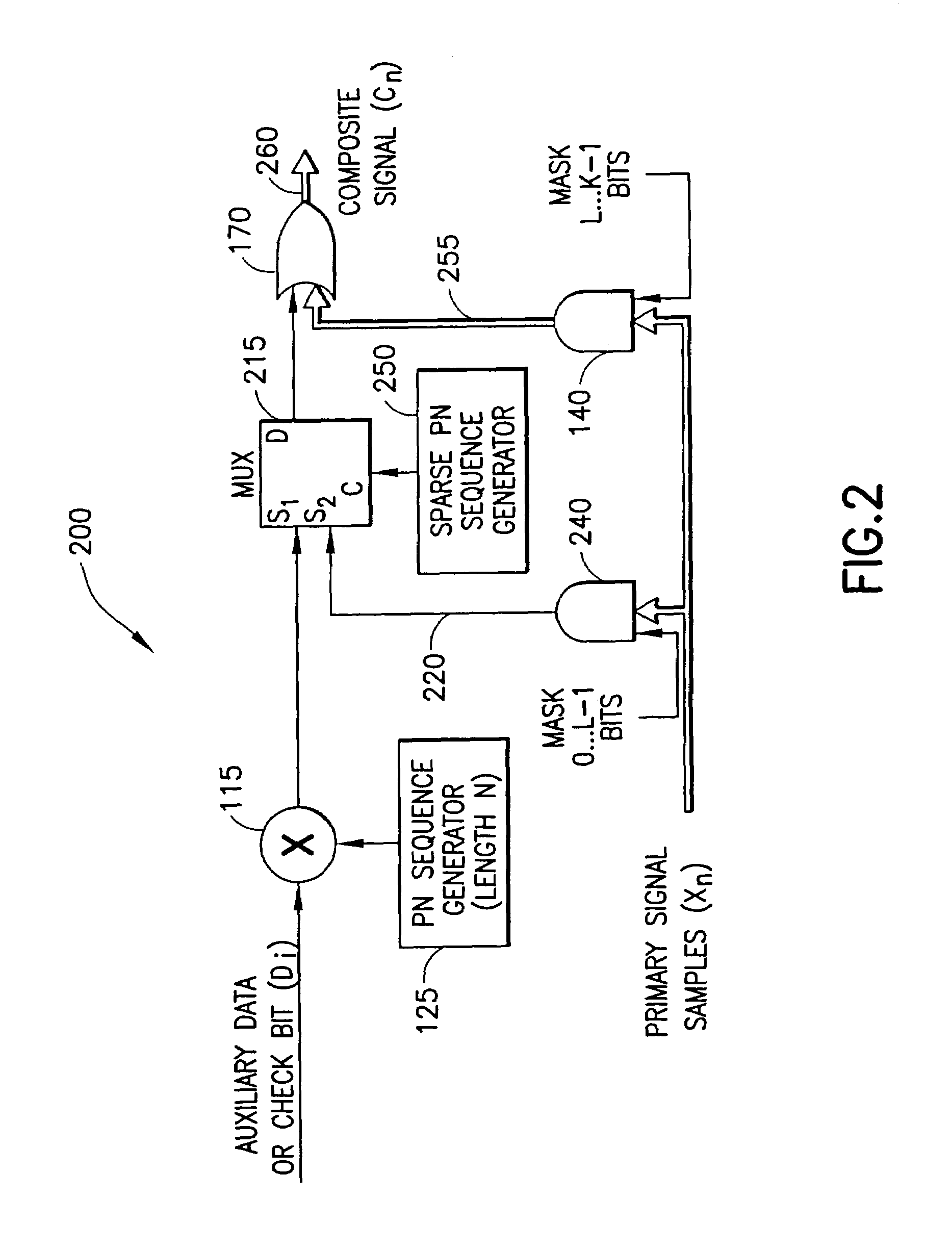
Digital hidden data transport (DHDT)
InactiveUS7460667B2Manipulation can be minimizedReliable dataSpeech analysisRecord information storageHidden dataNoise level
A system for embedding auxiliary digital information into a primary digital signal to form a composite digital signal. Auxiliary data bits modulate a pseudo-random (e.g., PN) sequence to provide an auxiliary data sequence used to modify the Least Perceptually Significant Bits (LPSBs) of successive multi-bit samples of the primary signal. In a cross-term compensation embodiment, a correlation between the PN sequence and the sample bits is determined, and compared to the auxiliary data bits to determine whether there is a desired correspondence. The LPSBs in the samples are toggled, if necessary, to provide the desired correspondence. The selection of LPSBs to modify accounts for a desired noise level of the auxiliary data in the primary signal. LPSBs may be modified based on a sparse PN sequence to achieve the desired noise level and conceal the presence of the auxiliary data.
Owner:VERANCE
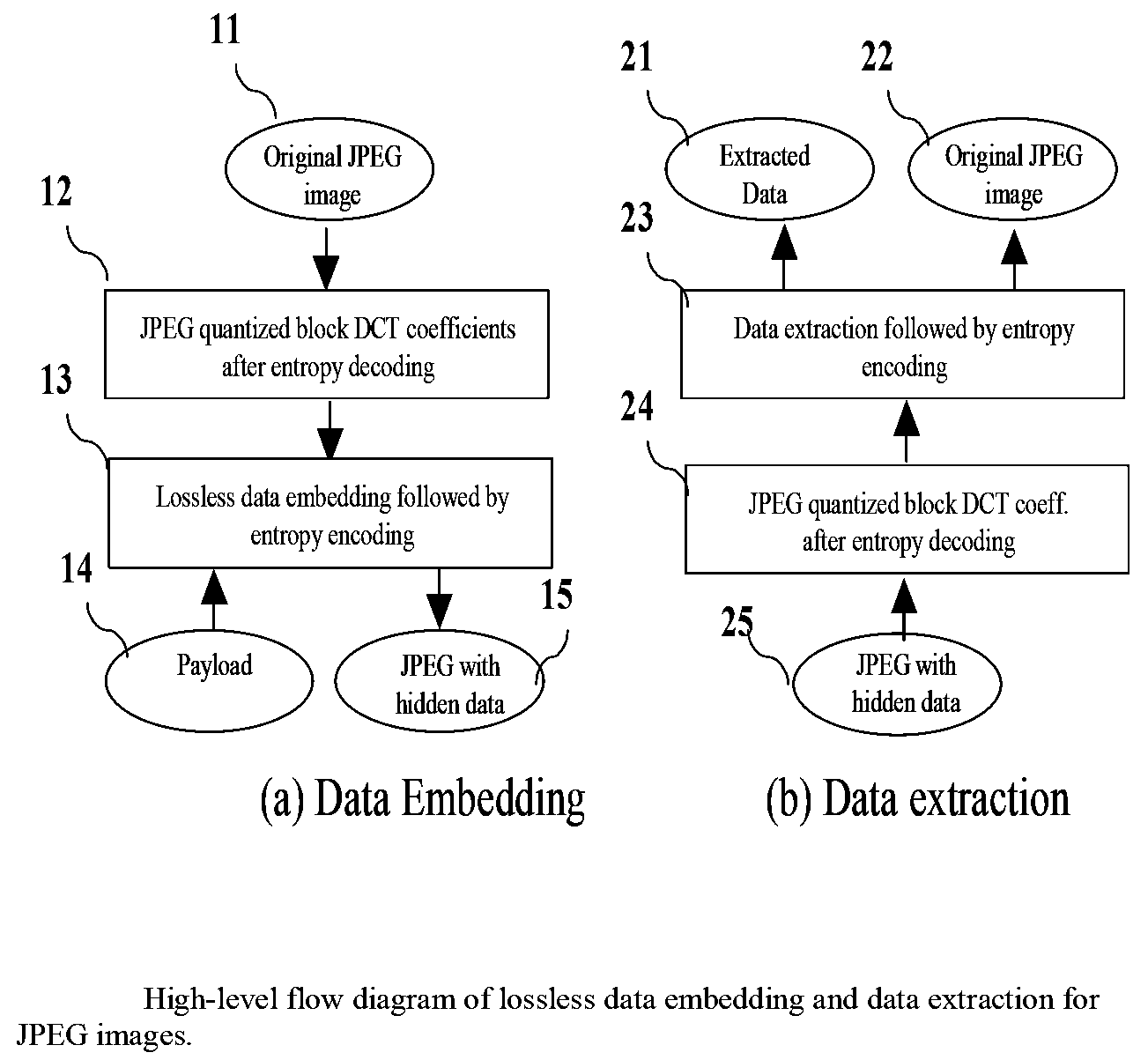
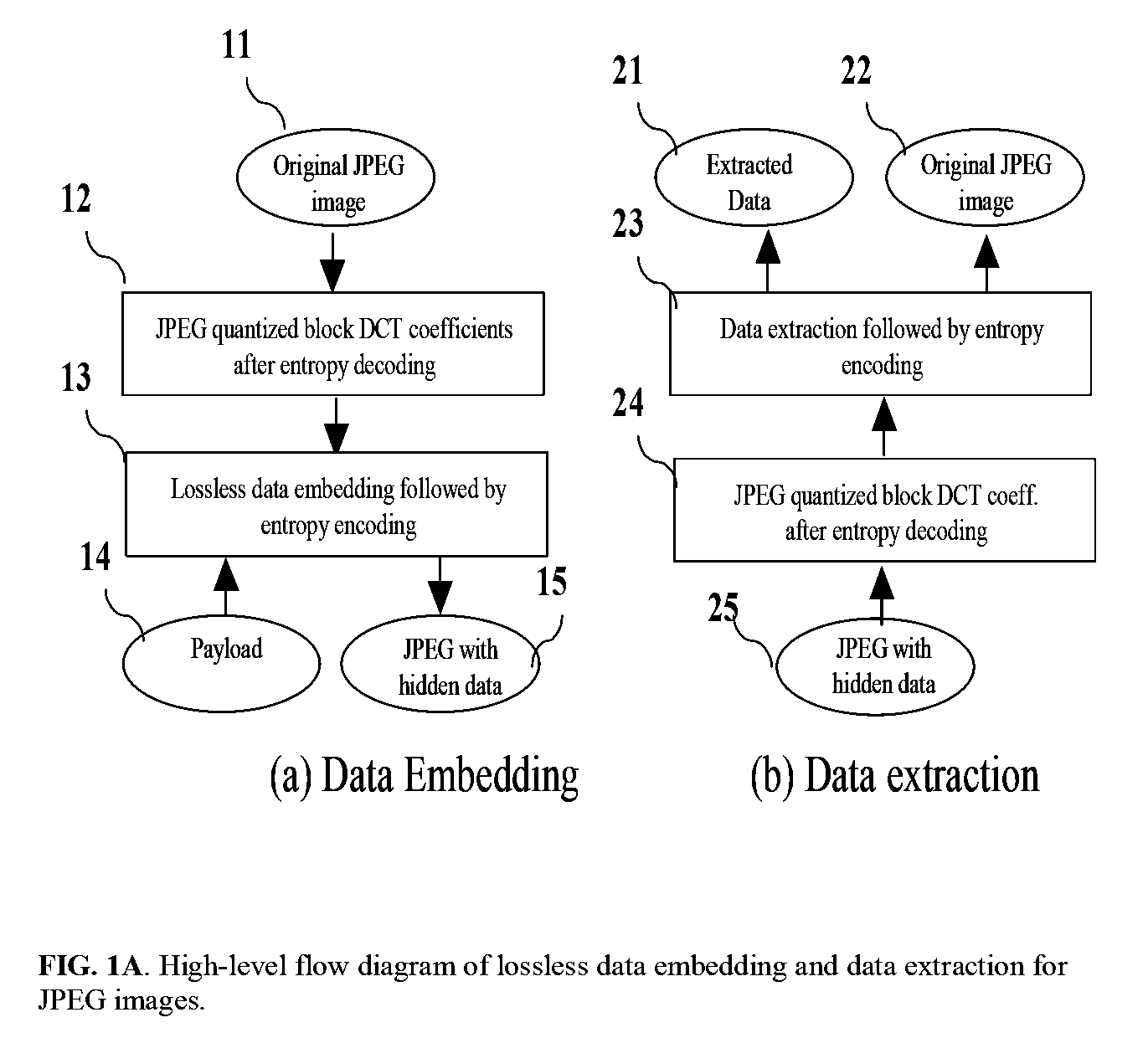
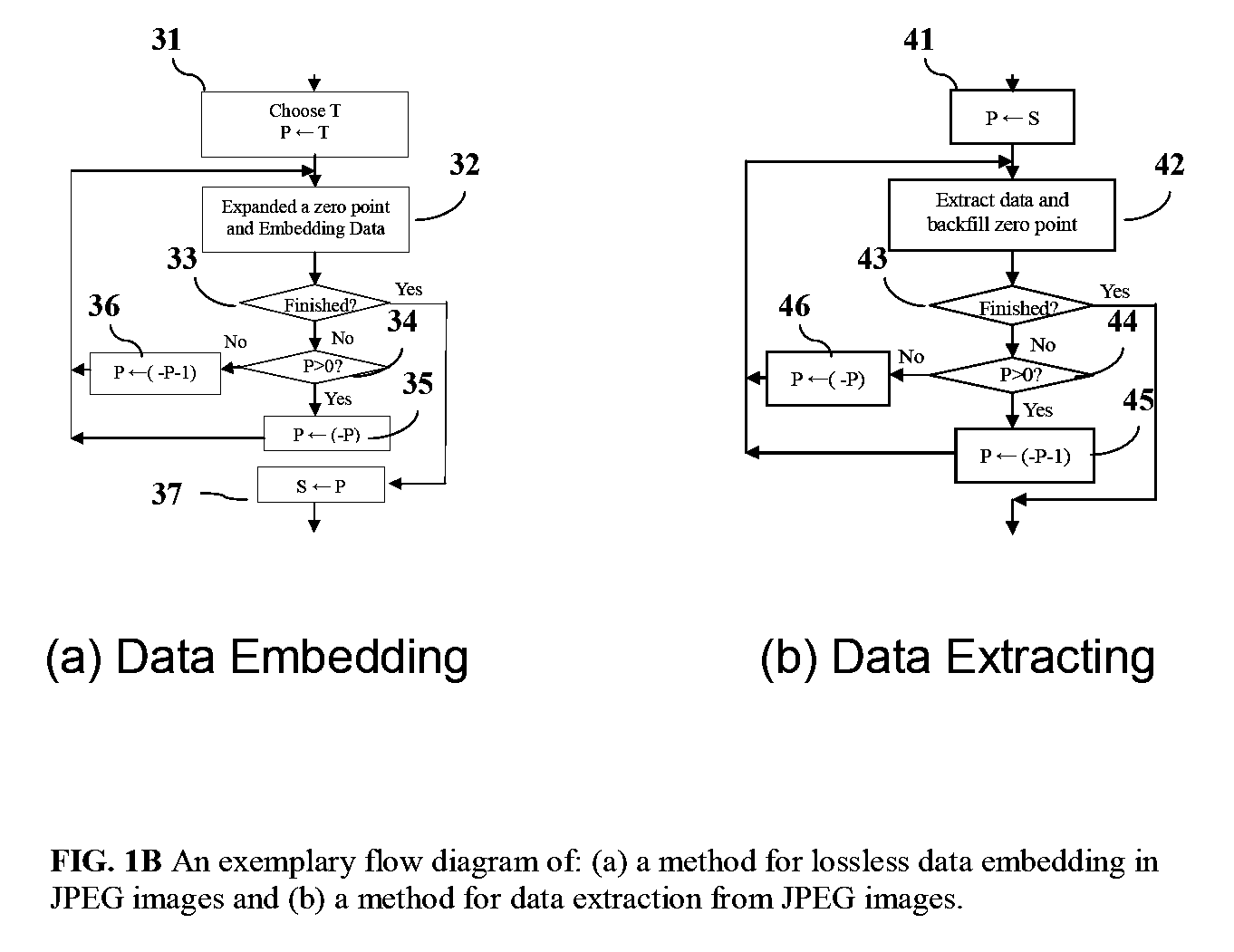
Appratus and method for reversible data hiding for JPEG images
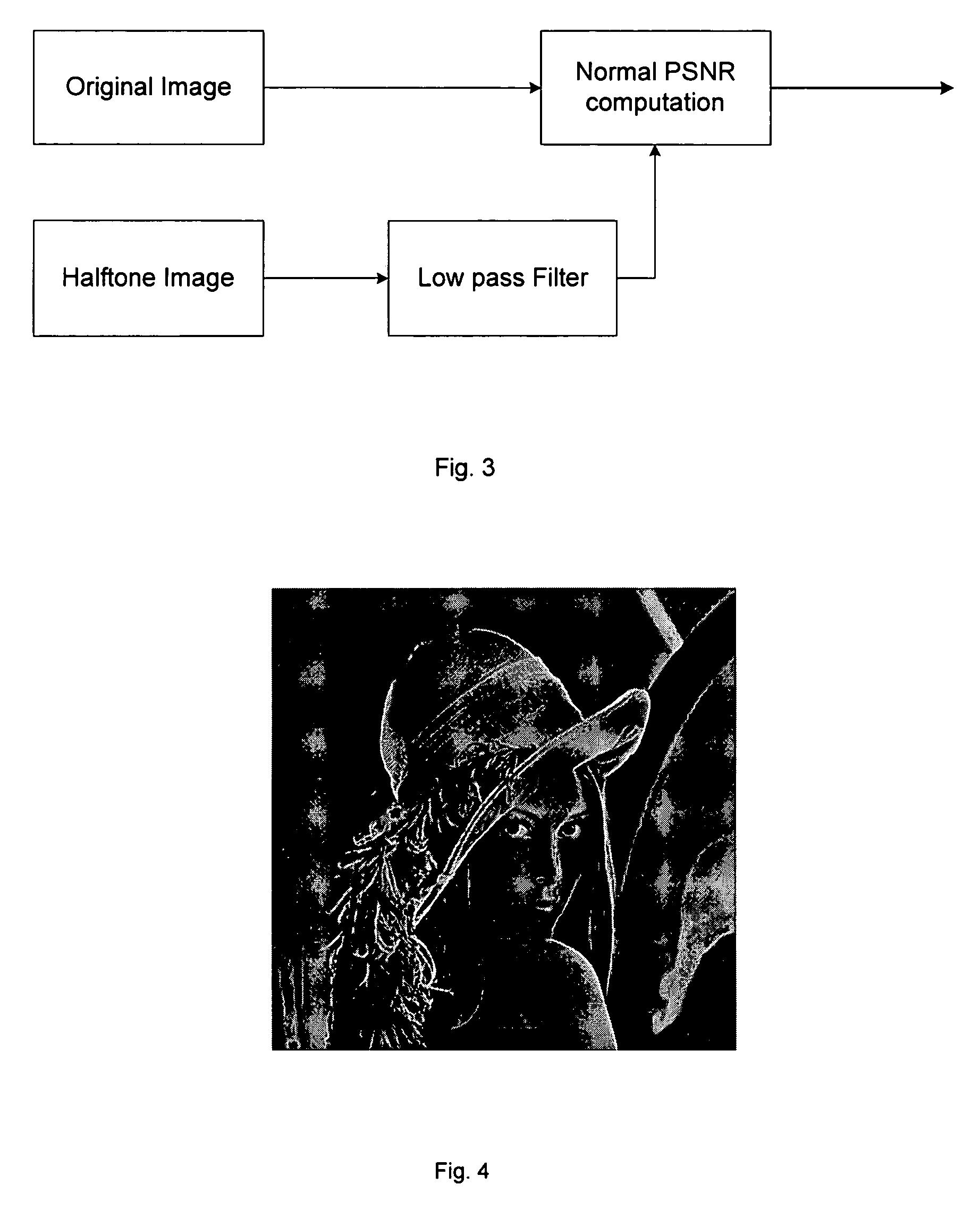
ActiveUS20080199093A1Visual qualityIncrease in sizeCharacter and pattern recognitionImage data processing detailsJPEGImaging data
Embodiments of the invention are directed toward reversible / invertible and lossless, image data hiding that can imperceptibly hide data into digital images and can reconstruct the original image without any distortion after the hidden data have been extracted in various digital image formats including, but not limited to Joint Photographic Experts Group (JPEG). In particular, embodiments of the invention provide a lossless data hiding technique for JPEG images based on histogram pairs. that embeds data into the JPEG quantized 8×8 block DCT coefficients and achieves good performance in terms of peak signal-to-noise ratio (PSNR) versus payload through manipulating histogram pairs with optimum threshold and optimum region of the JPEG DCT coefficients. Furthermore, the invented technology is expected to be able to apply to the I-frame of Motion Picture Experts Group (MPEG) video for various applications including annotation, authentication, and forensics.
Owner:NEW JERSEY INSTITUTE OF TECHNOLOGY
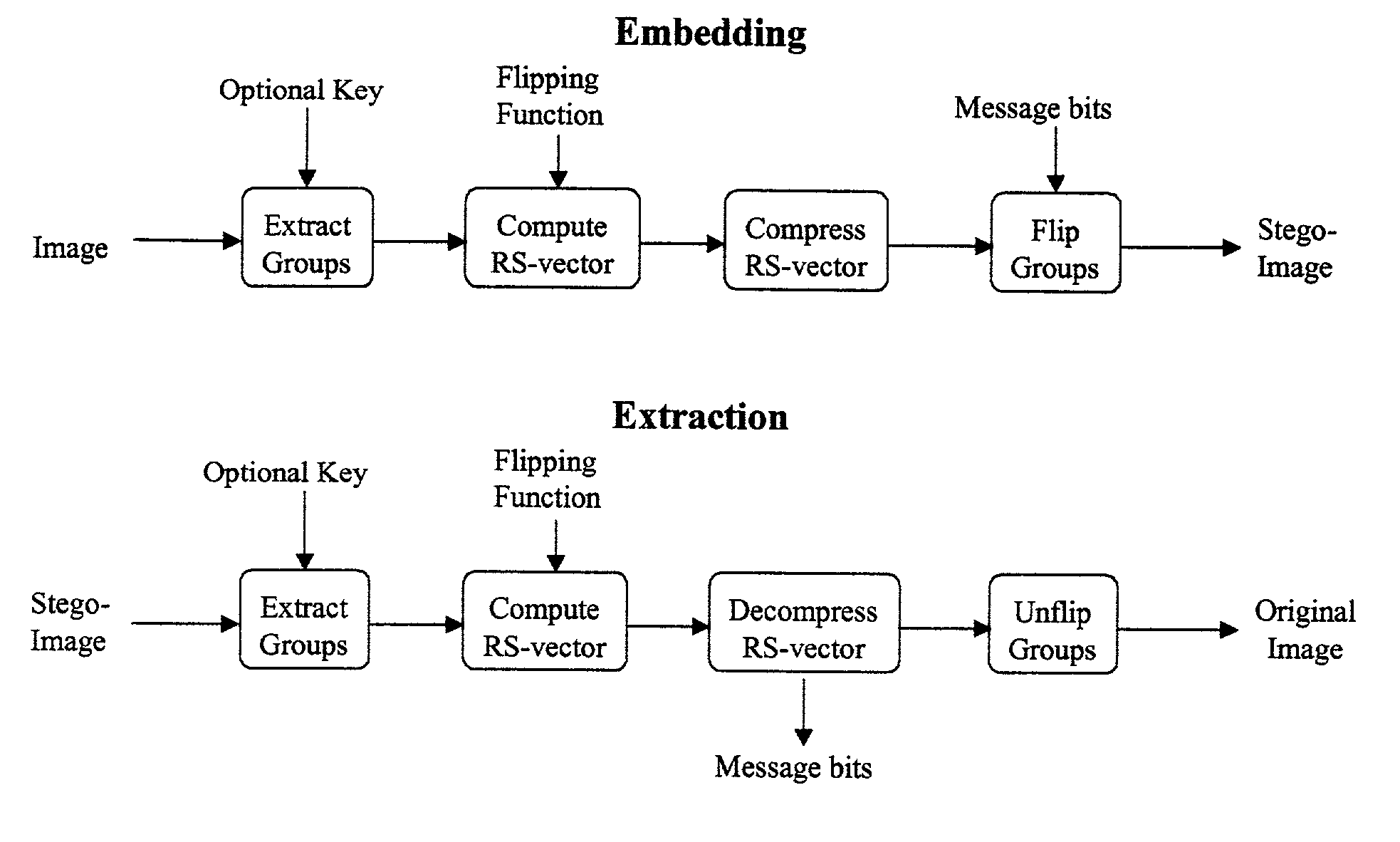
Lossless embedding of data in digital objects
ActiveUS7006656B2Simple and elegant lossless techniqueHeavy loadUser identity/authority verificationCharacter and pattern recognitionSteganalysisHidden data
Current methods of embedding hidden data in an image inevitably distort the original image by noise. This distortion cannot generally be removed completely because of quantization, bit-replacement, or truncation at the grayscales 0 and 255. The distortion, though often small, may make the original image unacceptable for medical applications, or for military and law enforcement applications where an image must be inspected under unusual viewing conditions (e.g., after filtering or extreme zoom). The present invention provides high-capacity embedding of data that is lossless (or distortion-free) because, after embedded information is extracted from a cover image, we revert to an exact copy of the original image before the embedding took place. This new technique is a powerful tool for a variety of tasks, including lossless robust watermarking, lossless authentication with fragile watermarks, and steganalysis. The technique is applicable to raw, uncompressed formats (e.g., BMP, PCX, PGM, RAS, etc.), lossy image formats (JPEG, JPEG2000, wavelet), and palette formats (GIF, PNG).
Owner:RES FOUND OF SUNY THE +1
Method, software, and device for hiding data in binary image, while preserving image quality
InactiveUS20050259844A1Time-division multiplexCharacter and pattern recognitionHidden dataImaging quality
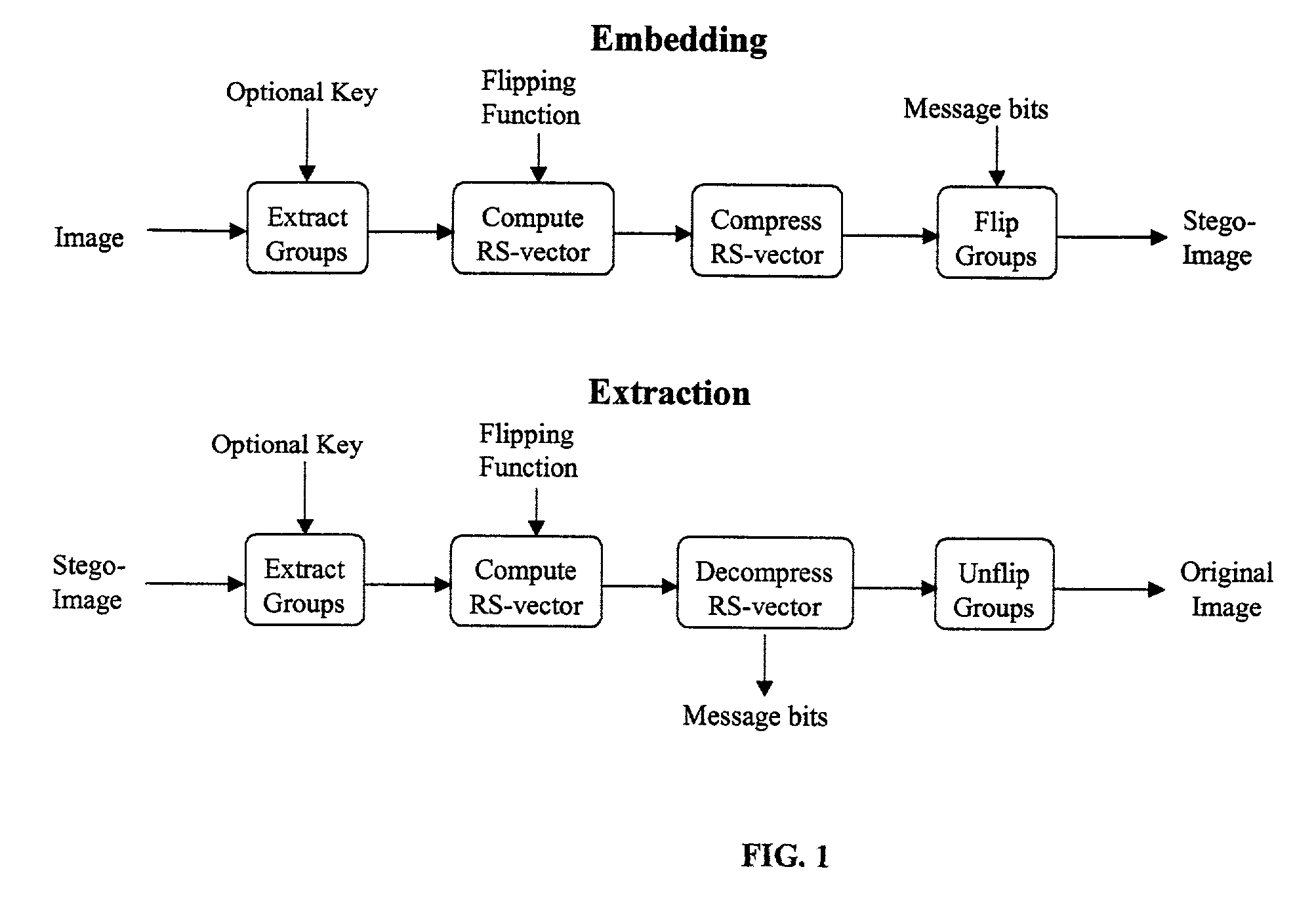
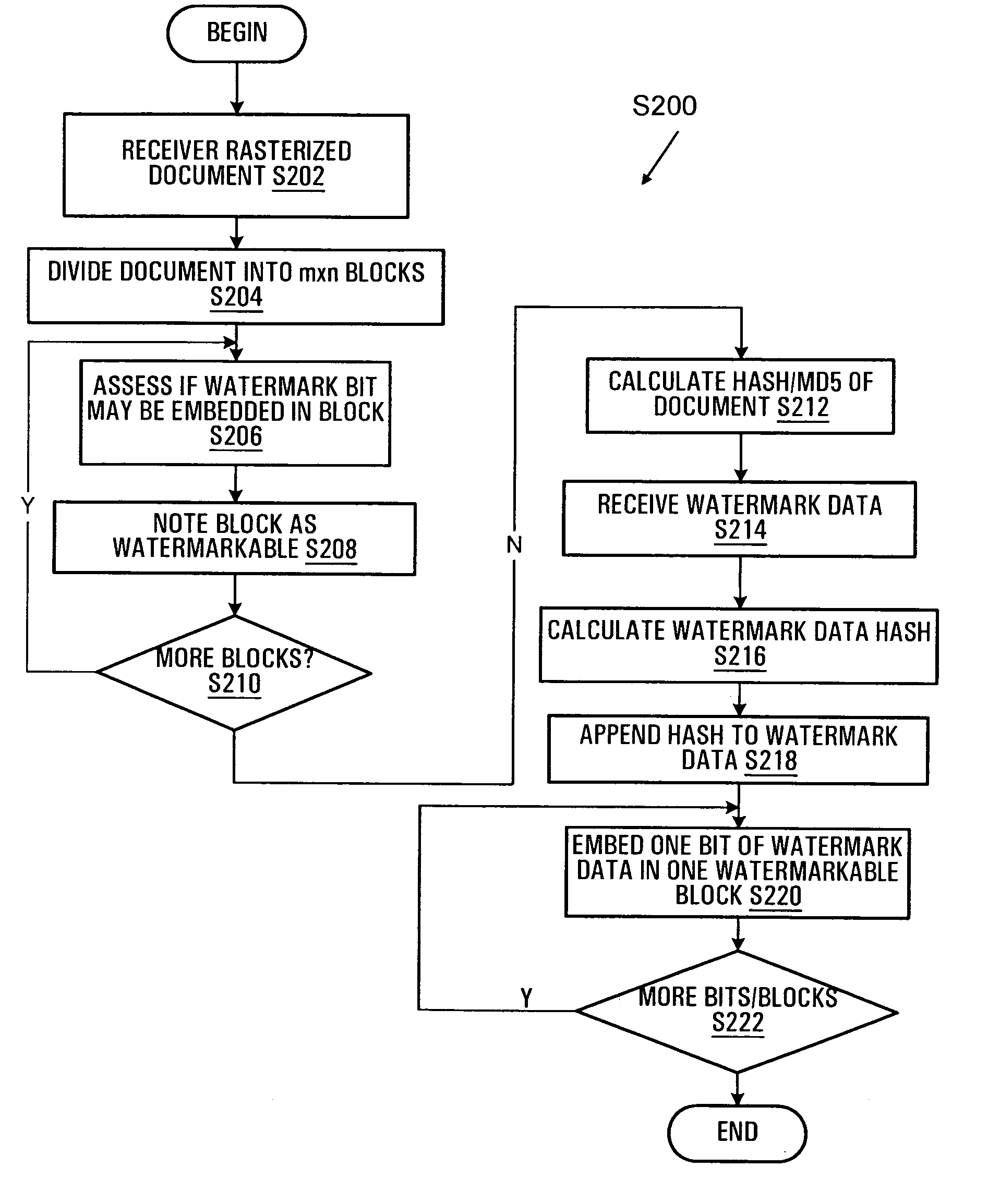
A method of embedding watermark data into a two-colour (binary) image includes dividing the image into blocks and assessing the suitability of each block to embed a bit of watermark data by assessing whether or not the flipping of a defined pixel in each block affects the visual attributes of said block in manner to be perceptible by the human eye. Data is only embedded in those blocks determined to be suitable for data embedding, by flipping the defined pixel, as required. A recipient of the document may similarly assess which blocks contain watermark data, by assessing the suitability of each block in the document to embed such data. Conveniently, watermark data may be extracted without further information about the data's location within a document.
Owner:NANYANG TECH UNIV
Filtering hidden data embedded in media files
ActiveUS20150319138A1Multiple digital computer combinationsProgram controlTraffic capacityHidden data
Systems and methods for filtering unsafe content at a network security appliance are provided. According to one embodiment, a network security appliance captures network traffic and extracts a media file from the network traffic. The network security appliance then determines the presence of a hidden data item embedded in the media file in a machine-readable form. When such a hidden data item is identified, the network security appliance performs one or more actions on the media file based on a predefined security policy.
Owner:FORTINET
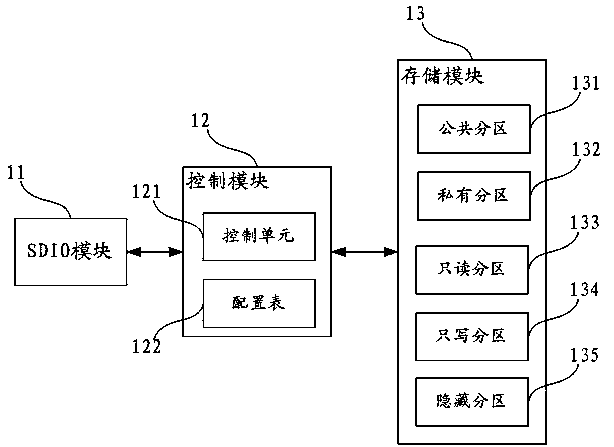
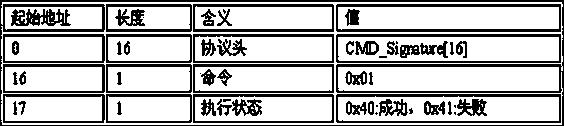
Storing device of safety partitions
InactiveCN103617404AImprove securityUnauthorized memory use protectionInternal/peripheral component protectionComputer hardwareHidden data
Owner:天津赢达信科技有限公司
System and method for secret communication
InactiveUS7177441B2Key distribution for secure communicationCharacter and pattern recognitionData setHidden data
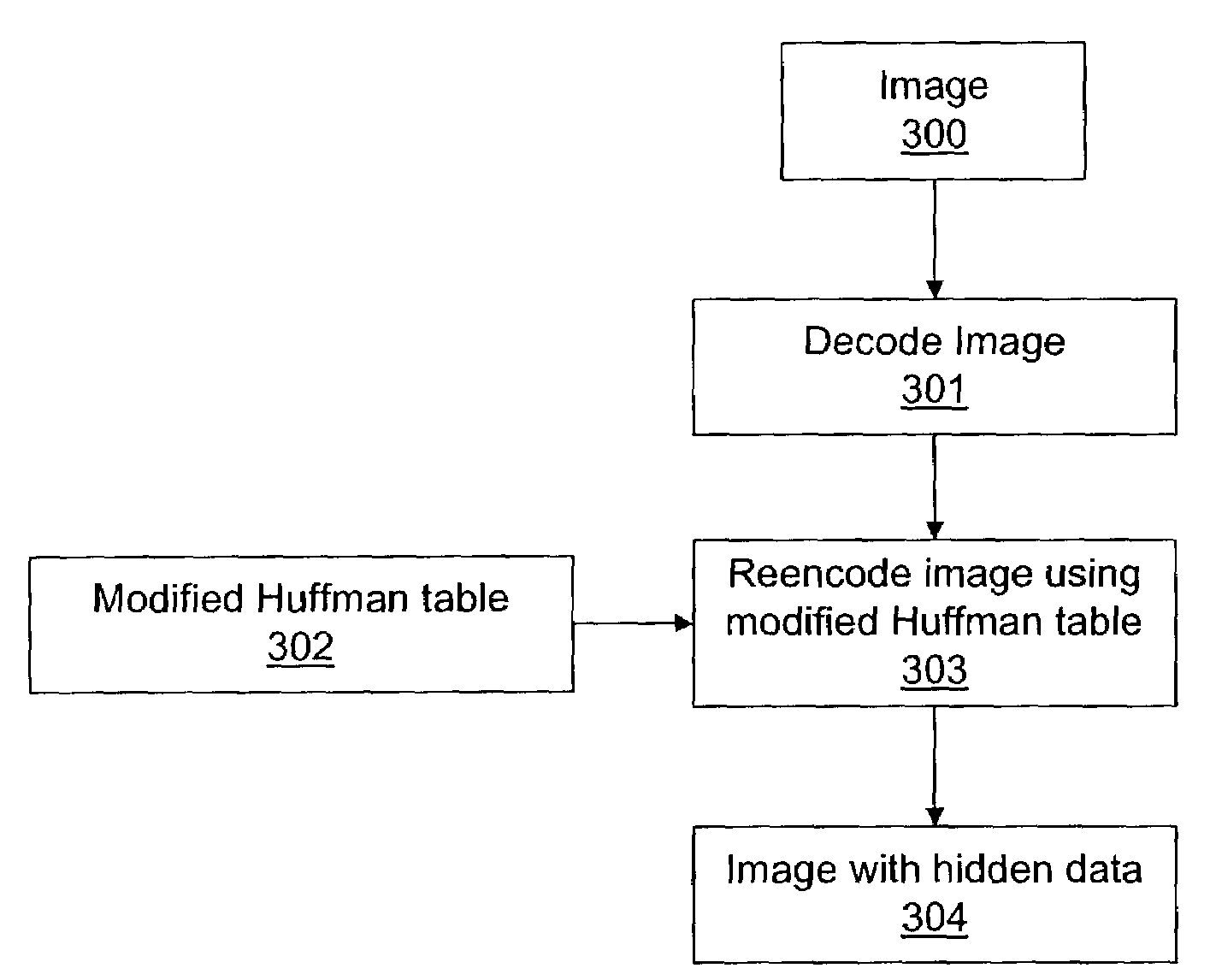
We present a communication system which enables two or more parties to secretly communicate through an existing digital channel which has a primary function other than this secret communication. A first party receives a series of cover data sets, hides a certain amount of auxiliary data in the cover data sets, and then relays these cover data sets containing hidden data to a second party, aware of the hidden data. This second party may then extract the hidden data and either restore it to its original state (the state it was in before the first party received it) and send it along to its original intended destination, or may just simply extract the hidden auxiliary data. There exist a plethora of techniques for hiding auxiliary data in cover data, and any of these can be used for the hiding phase of the system. For example, in a JPEG cover data set, a Huffman table may be modified in such a way as to have no impact on the observable nature of the image, and several such schemes are presented here. Since there are so many ways in which to exploit a particular cover data set for secret communication, it is necessary that the first and second parties have pre-established a set of rules by which they will communicate. There must be agreement on the hiding technique, cover data type and location of the hidden data within the cover.
Owner:IBM CORP
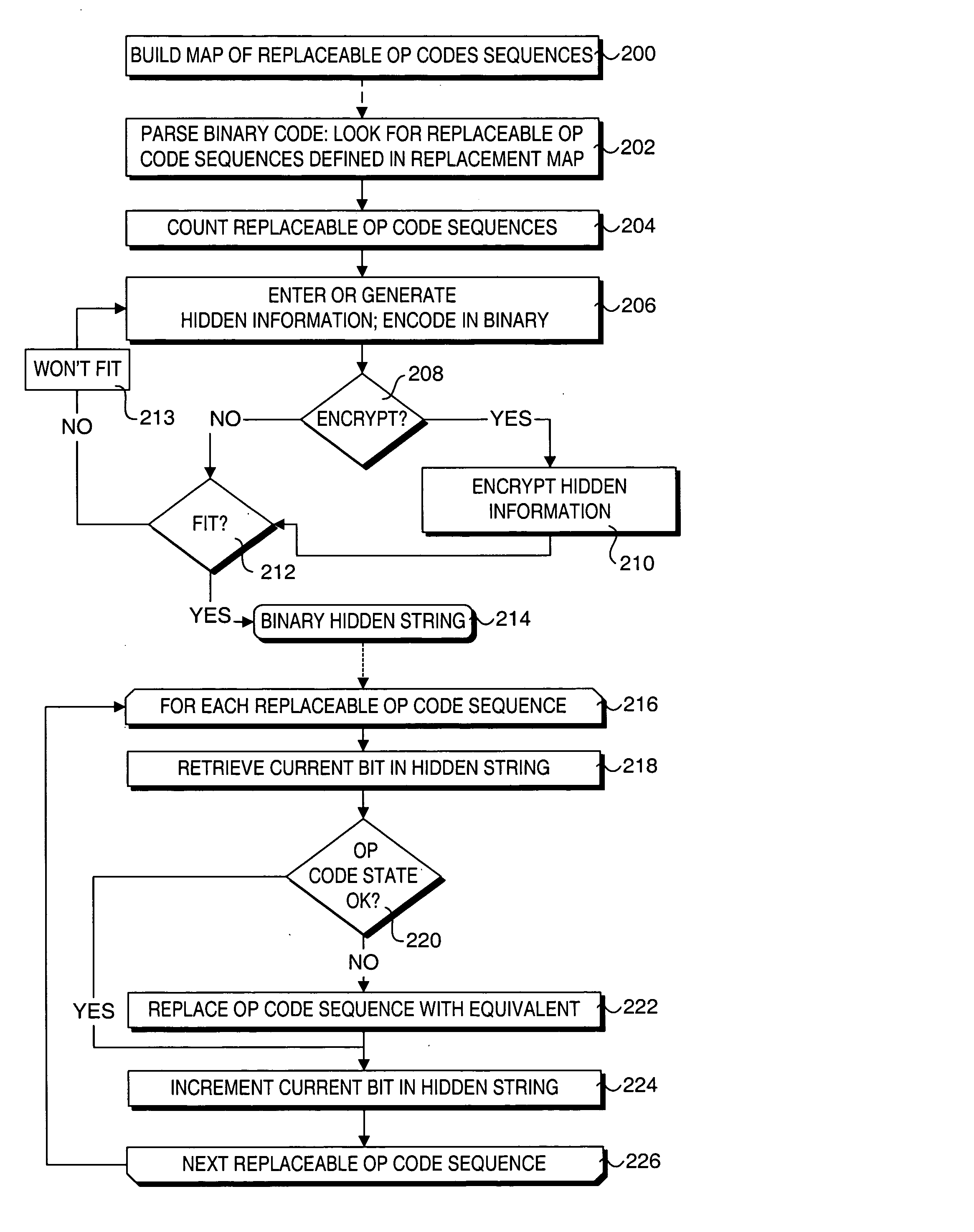
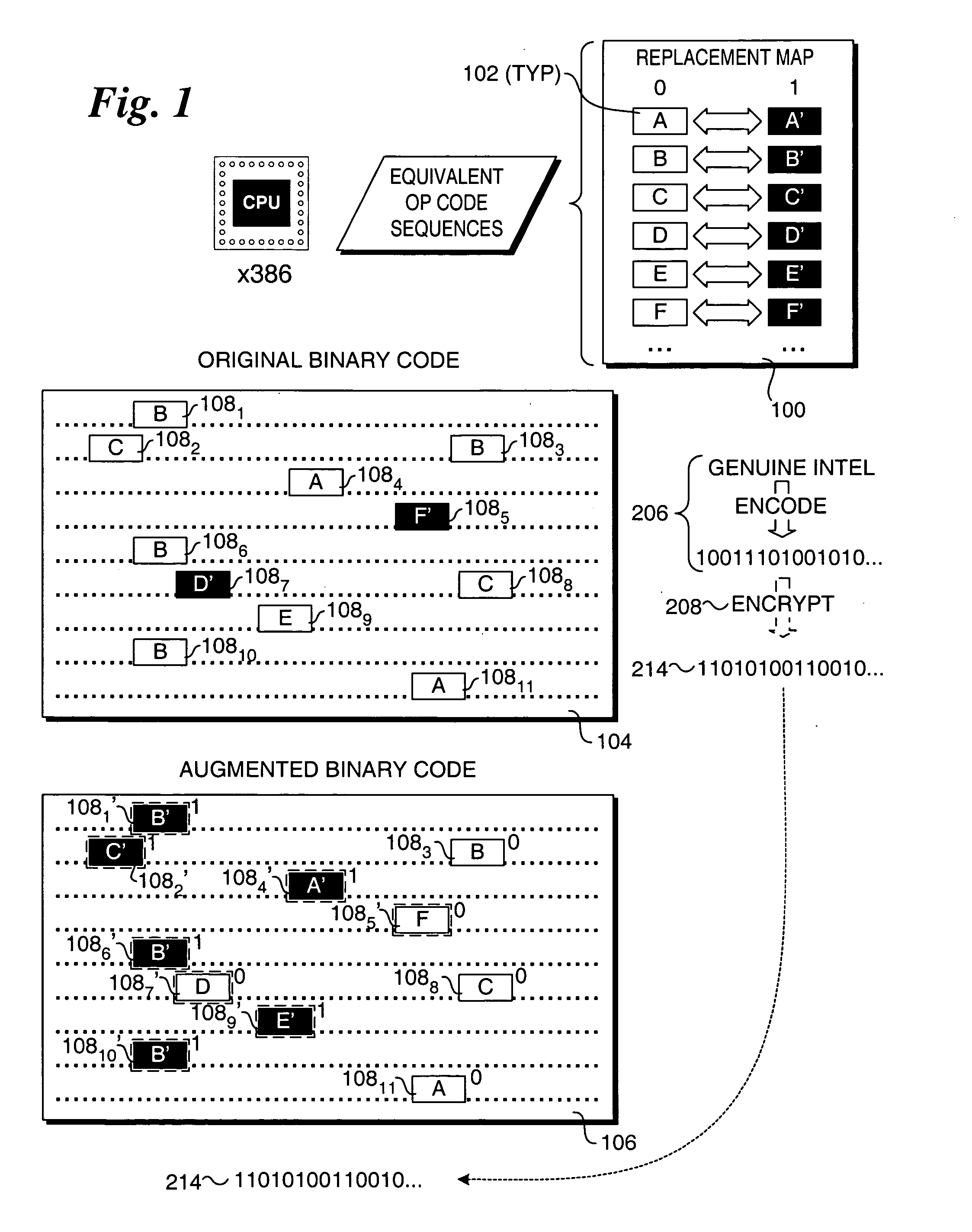
Method to provide transparent information in binary drivers via steganographic techniques
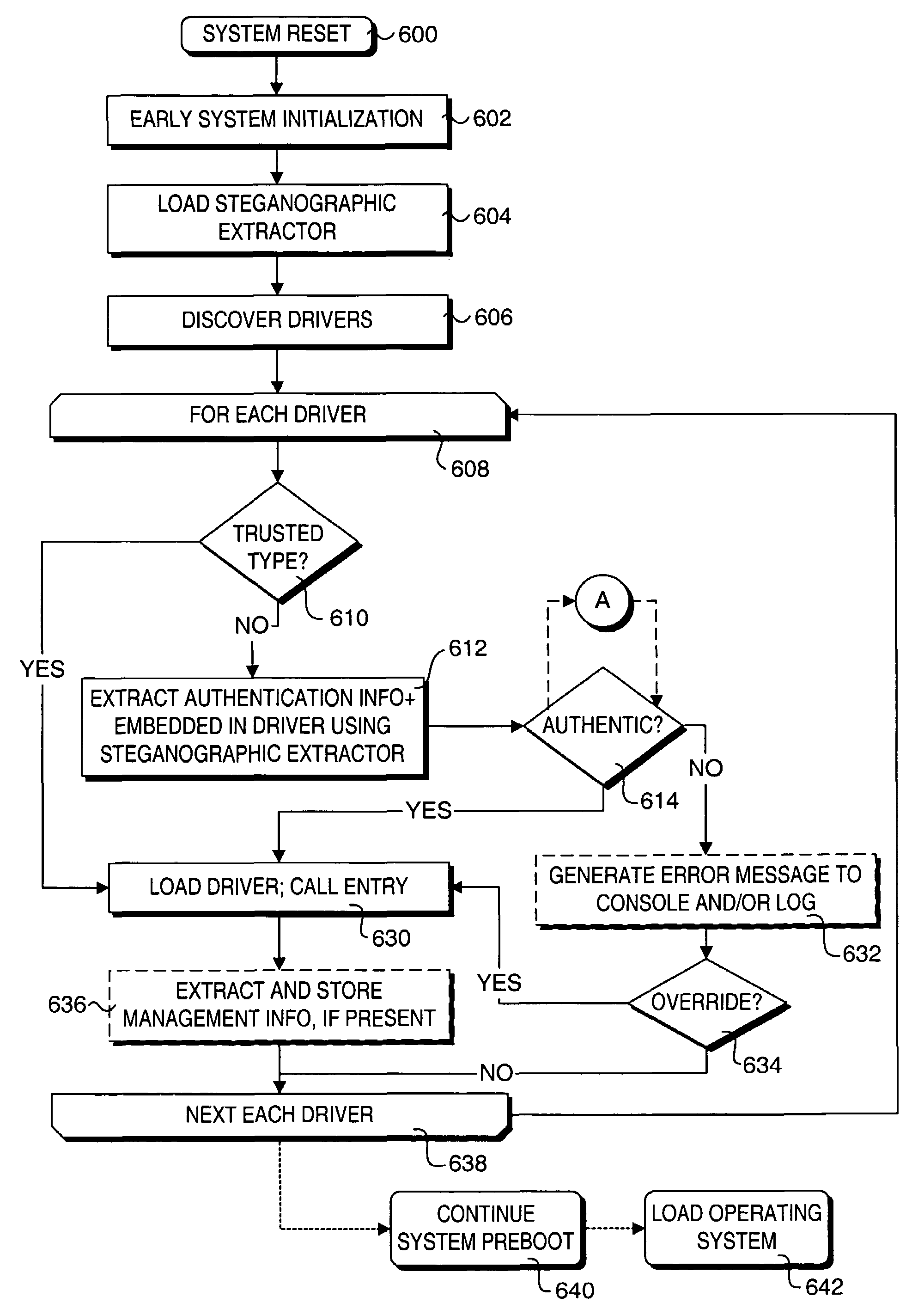
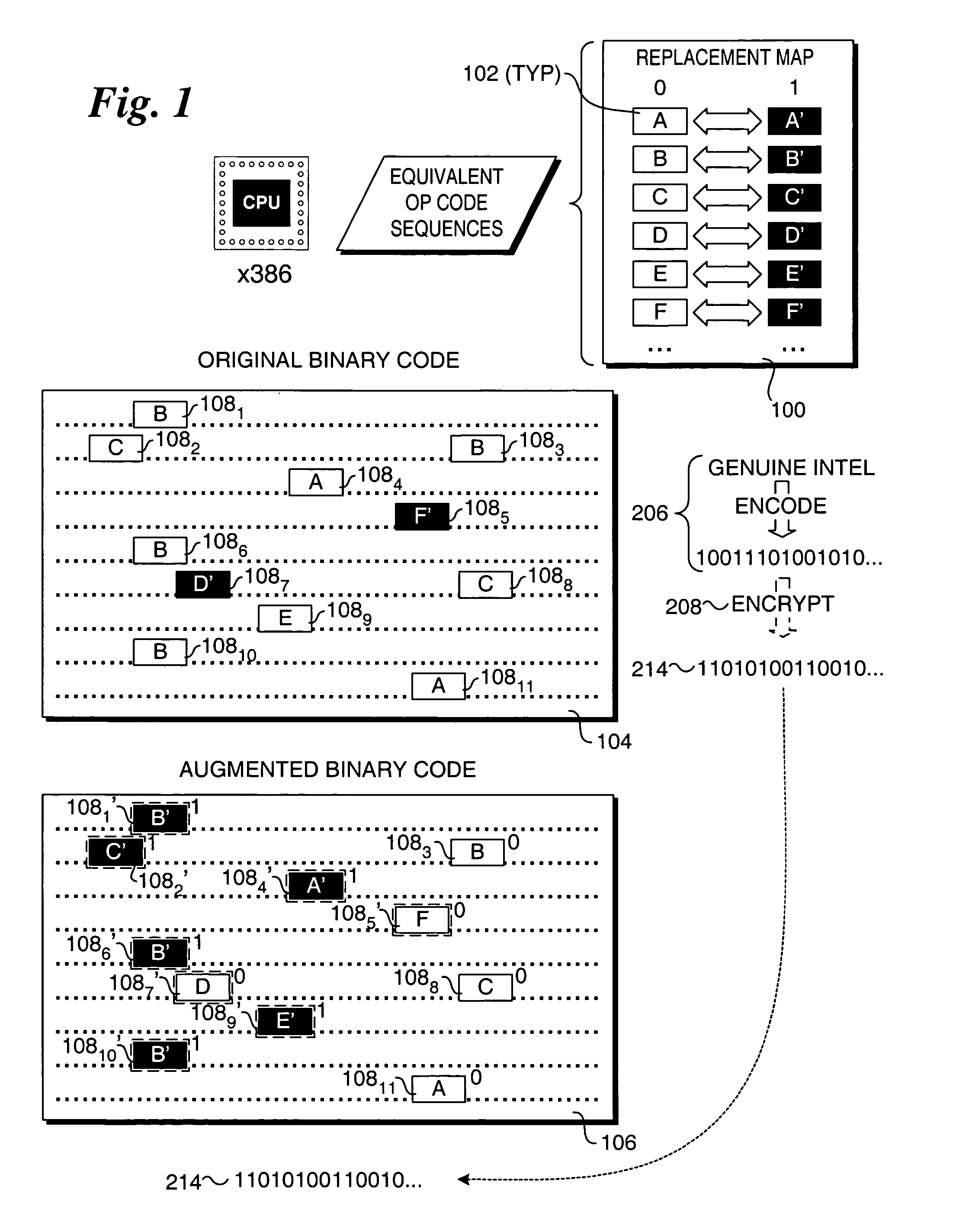
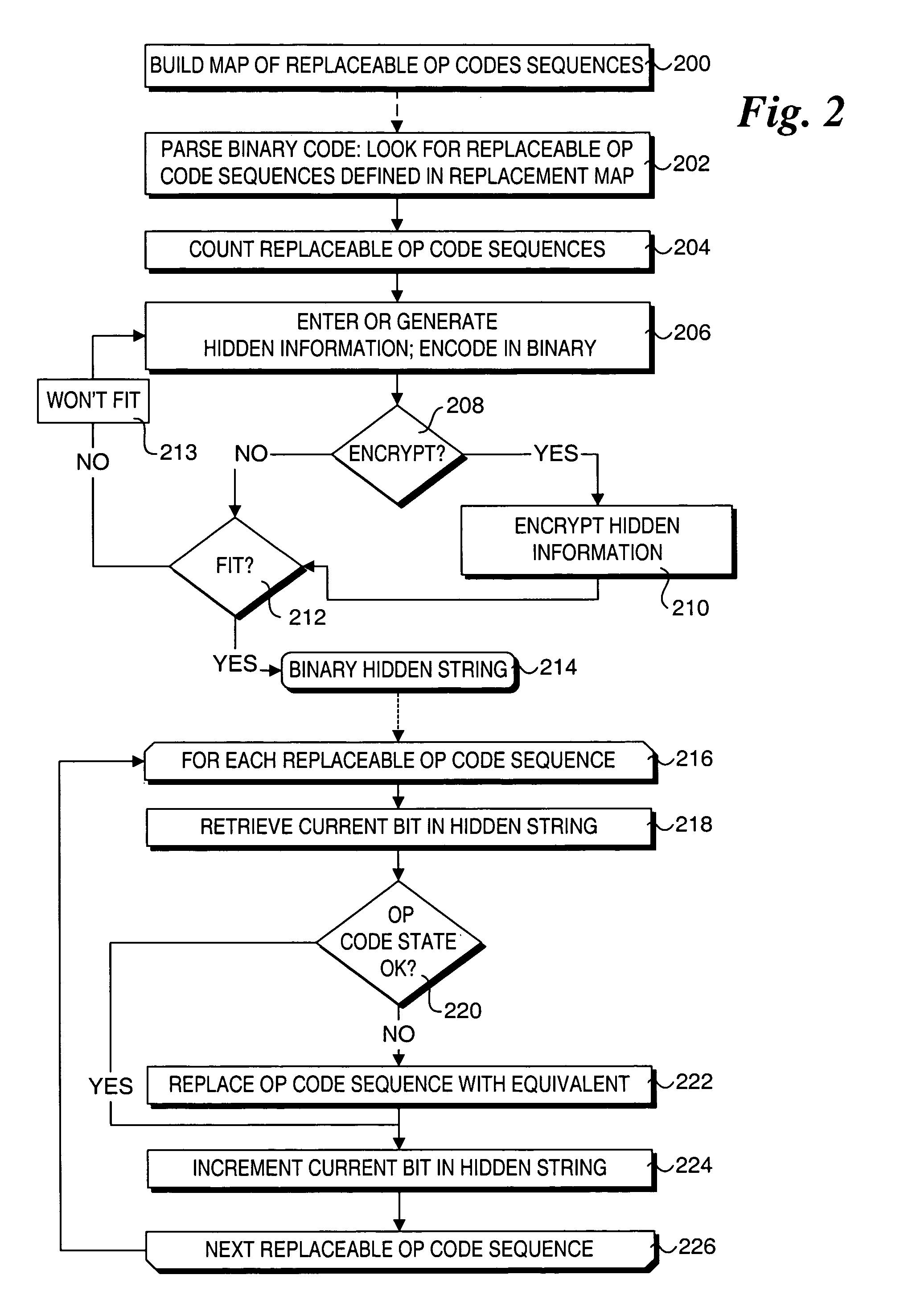
ActiveUS7751584B2User identity/authority verificationCharacter and pattern recognitionComputer hardwareHidden data
Methods for providing and extracting hidden information in firmware images using steganographic processes. Information is hidden in binary firmware images, such as drivers, using a steganographic process in which the functionality of the binaries do not change, and the size is not increased. During a pre-boot phase of a computer system, binary firmware drivers containing hidden steganographic data are identified, and a steganographic extraction process is performed to extract the hidden data. In one embodiment, a hash is employed on an authentic binary image to uniquely identify the op code content. The digest from the hash is stored in the steganographic data. In one embodiment, a vendor's private key and optional signature is used to encrypt the hash. A similar hash is performed on the binary image of a discovered binary firmware driver, and the authentic hash digest is extracted from the steganographic data. The hash digests are compared to authenticate the binary firmware driver.
Owner:INTEL CORP
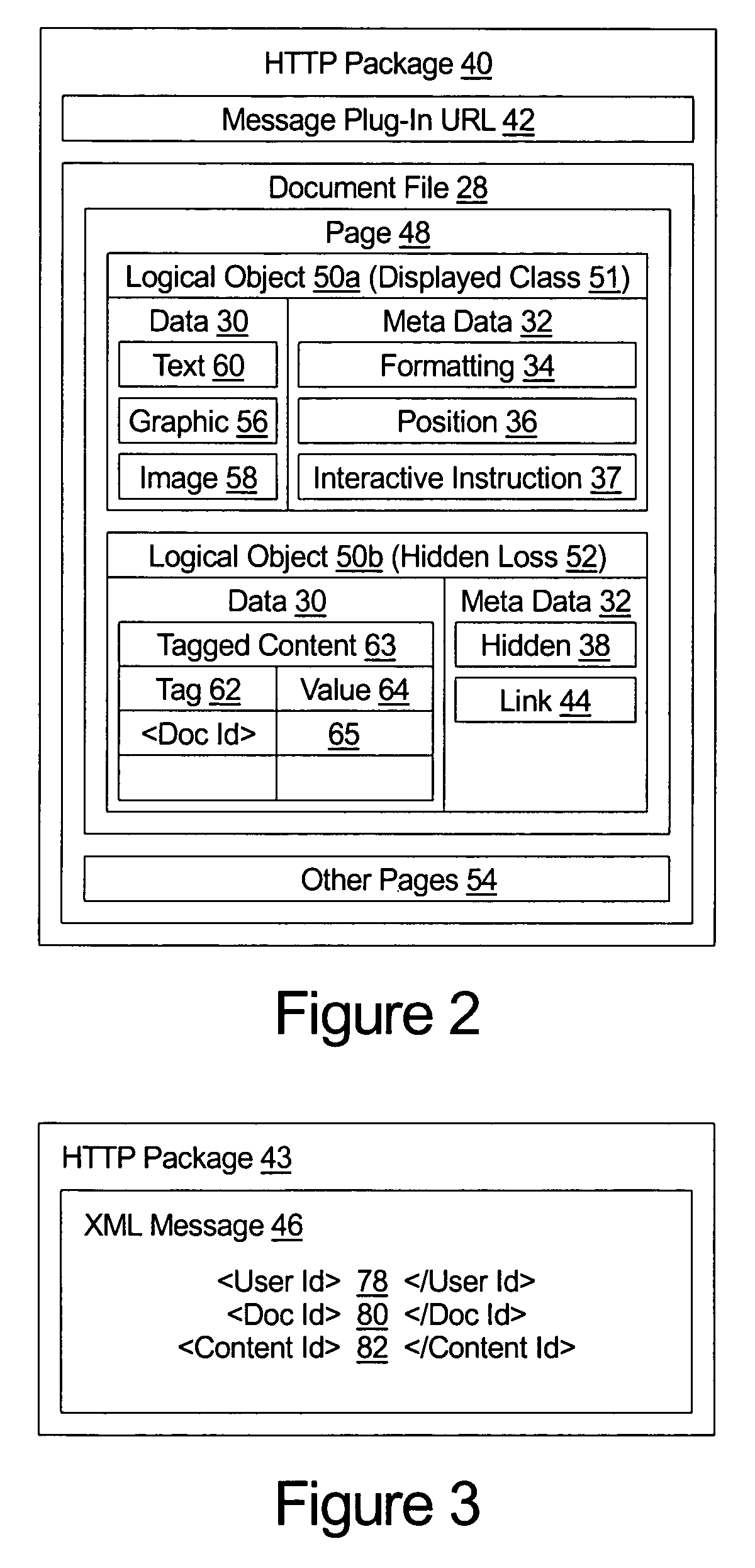
System and method for dynamically linking data within a portable document file with related data content stored in a database
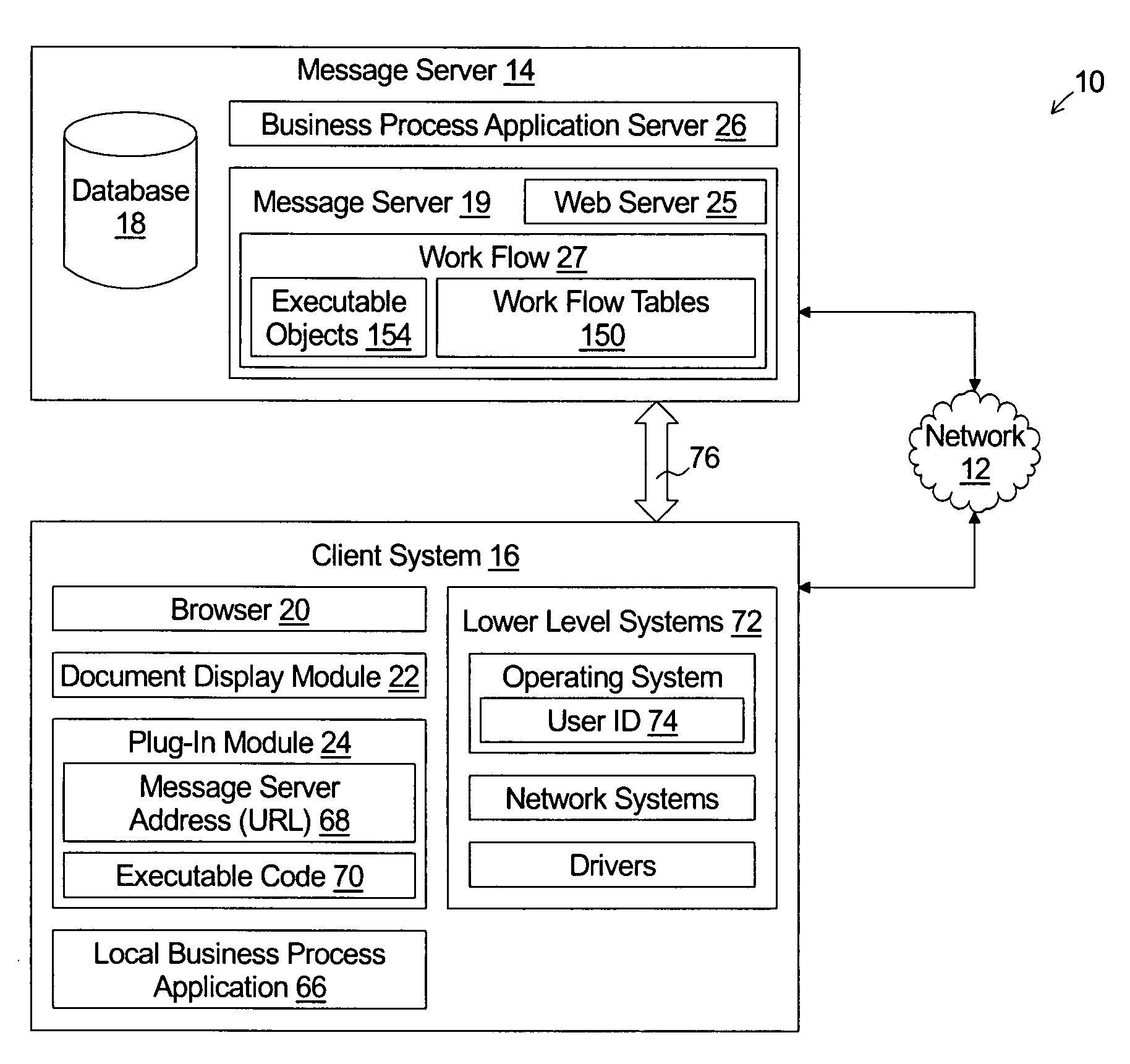
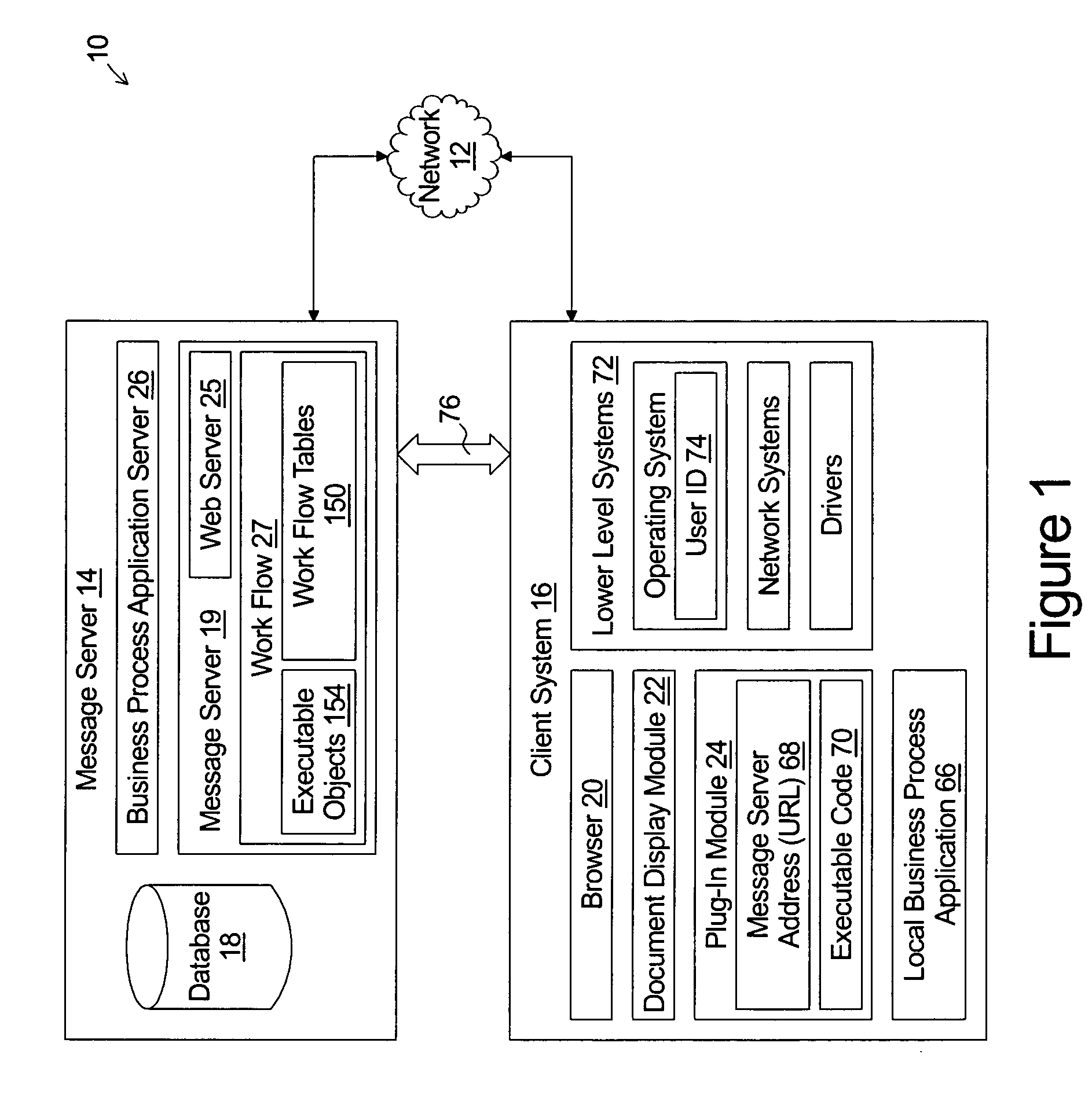
A message server comprises web server systems for sending a first portable document file to a client system. The first portable document file comprises displayed data content selectable by the user and associated hidden data content. The hidden data content may be in a tagged data content format. The message server receives a message from the client system. The message comprises both: i) identification of the first portable document file; and ii) identification of the displayed data content selected by the user. The message sever uses the identification of the first portable document file and the identification of the displayed data content selected by the user to locate and provide a second portable document file that is related to the content selected by the user.
Owner:BOTTOMLINE TECH
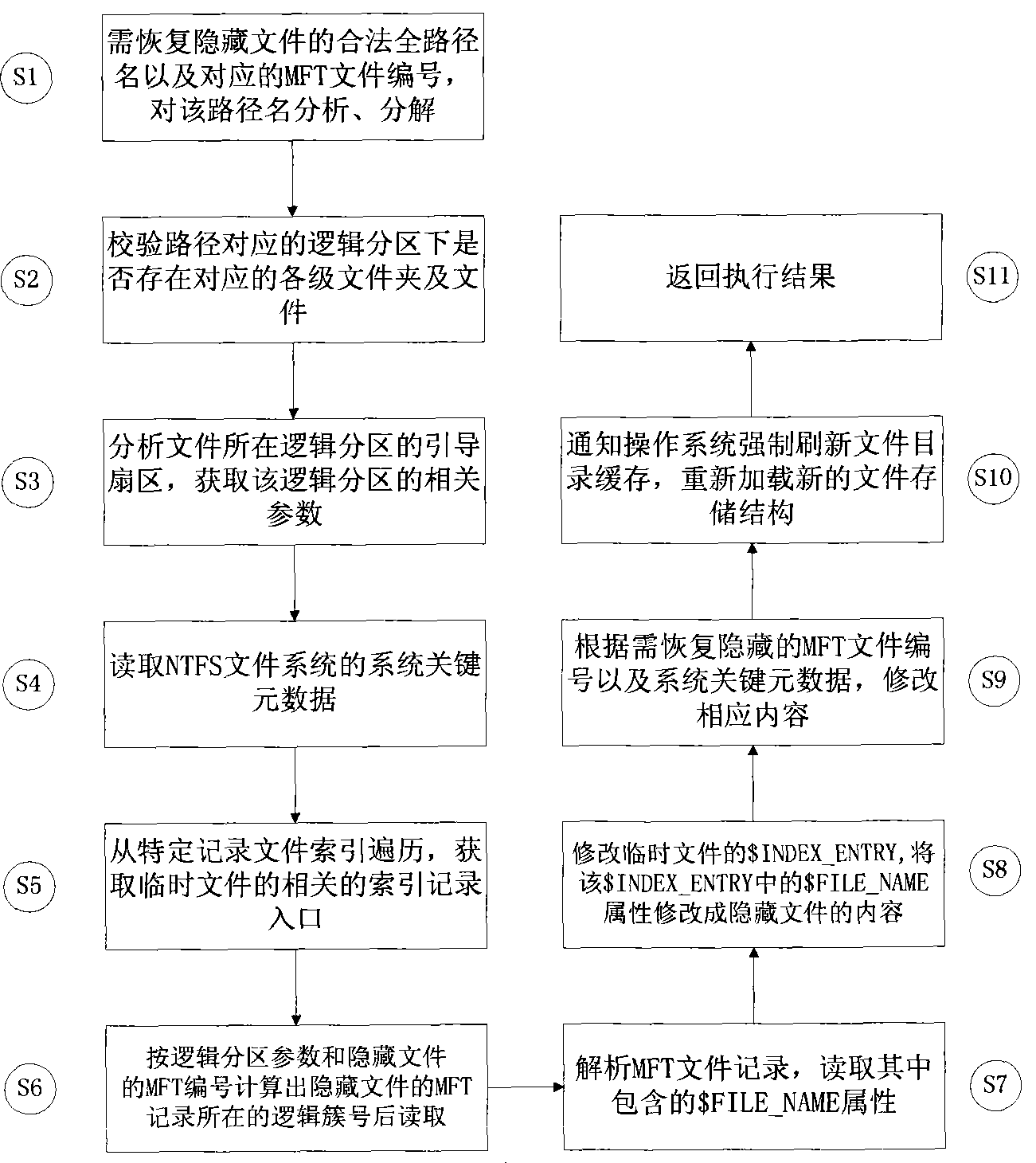
Light file hiding method in NTFS file system
InactiveCN101464900AWill not increase the waiting time for executionImprove integritySpecial data processing applicationsData integrityHidden data
The invention discloses a method for hiding light-weight files under an NTFS file system, which belongs to the technical field of computer network information. The method comprises a data hiding method and a hidden data recovering method, wherein, the data hiding method is characterized in that metadata of the file system referred according to the legal file path traverses index record entries of special files, thereby achieving the purpose of hiding file data. The hidden data recovering method is characterized in that the hidden data is redisplayed and added into the file system by altering the index record entry of a temporary file according to the legal file path and the record number of the hidden files, thereby achieving the purpose of recovering the hidden data. By adopting the invention, the confidentiality of confidential data and the transparency for other users can be realized through data hiding. Meanwhile, data exchange and operation expenditure during the execution process of hidden data are minimized, and data integrity and reliability are protected to the greatest extent.
Owner:SHANGHAI JIAO TONG UNIV
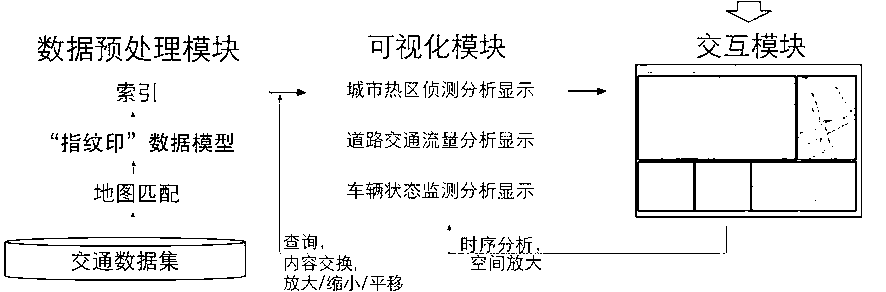
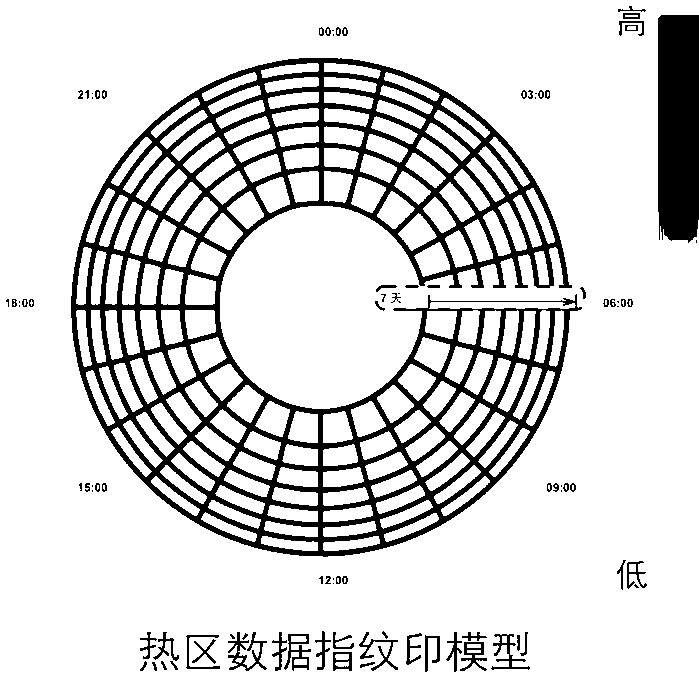
High-efficiency visible monitoring analysis system for large-scale traffic data
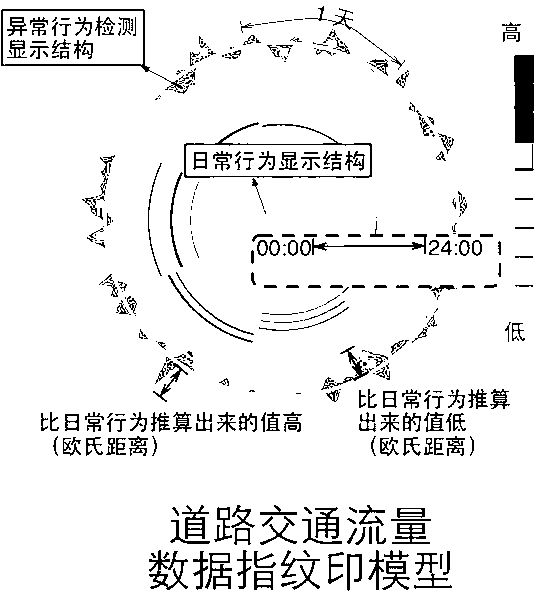
InactiveCN103309964AQuick comprehension comparisonLowering the Barrier to AnalysisDetection of traffic movementSpecial data processing applicationsData streamDensity based
The invention relates to a high-efficiency visible monitoring analysis system for large-scale traffic data. The system is mainly based on a visible 'fingerprint' data model previously proposed by an inventor; the collected original traffic data is converted into the visible 'fingerprint' data model through a data conversion module under large-scale real-time data flow; and complex abstract conceptions such as periodic flow changes, track exceptions and hidden data errors in the traffic data can be visualized into simple and intuitional visual effects so as to provide automatic detection and analysis of city hot spot regions based on density, road traffic flow analysis based on historical traffic flow dynamic properties and real-time monitoring analysis of the traffic track exceptions based on vehicle historical data and statistic information for a user. The periodical flow change properties in the large-scale traffic data are analyzed in real time based on the historical data and the statistic information to find hidden rules and errors so as to provide analysis and support for the decision of the user. Therefore, the convenience is provided for an analyzer to quickly understand the data and the information, the analysis threshold is reduced, the application range is expanded, and the analysis efficiency and accuracy are improved.
Owner:GUANGZHOU HKUST FOK YING TUNG RES INST
Data covert transmission method based on block chain network
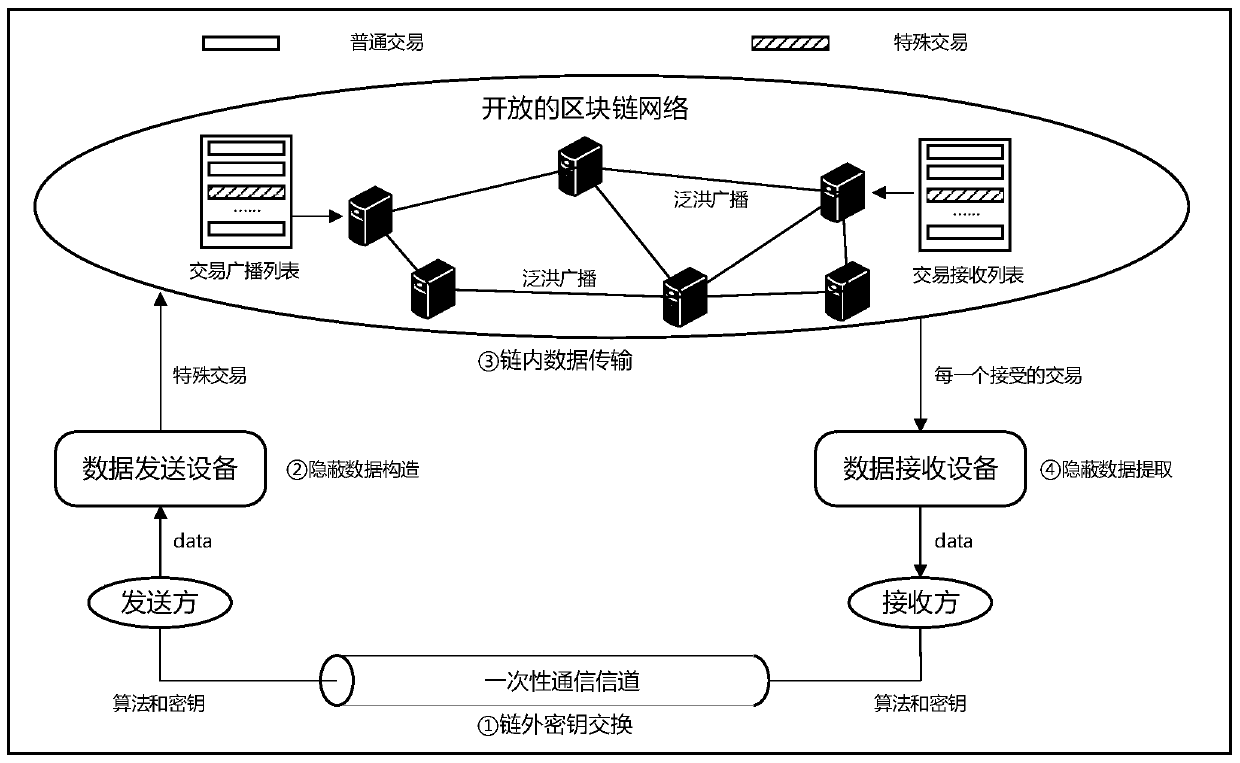
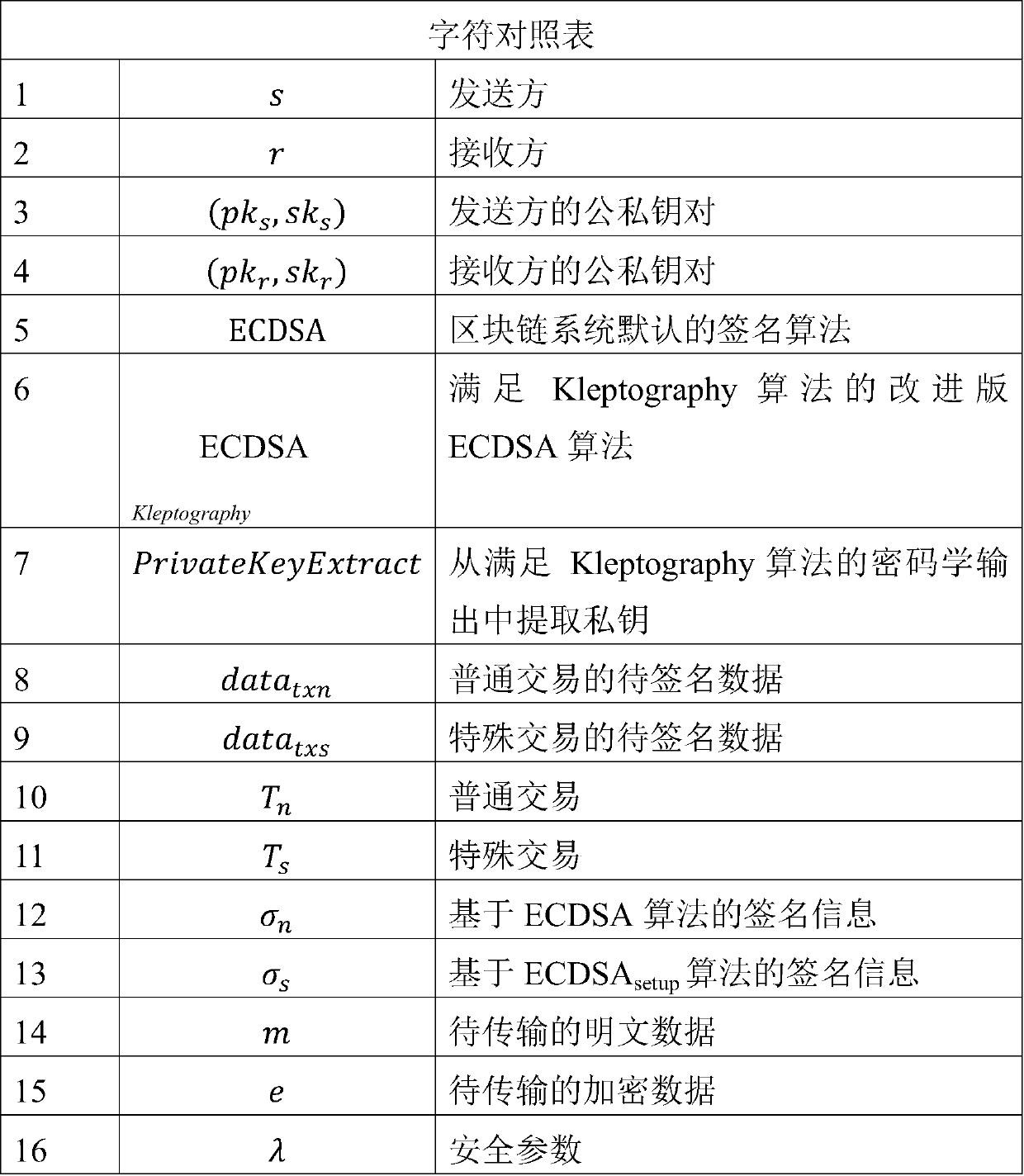
ActiveCN110225016AImprove concealmentAvoid Statistical LawsFinanceMultiple keys/algorithms usageKey exchangeCovert communication
The invention relates to a data covert transmission method based on a block chain network, and belongs to the technical field of data covert transmission. According to the method, a public key servingas a certificate of covert communication is exchanged through an out-of-chain key exchange stage; then constructing a special transaction which contains a message encrypted by a sender private key and can leak signature information of the sender private key and is generated by using a Kleptography technology through a covert data construction stage; then, the special transaction is propagated through an in-chain data transmission stage; and finally, reading and detecting each block chain transaction propagated in the block chain network one by one by a receiver in a hidden data extraction stage, and if the signature data in the transaction can extract a private key by using a Kleptograpy technology, indicating that the transaction is a special transaction carrying encrypted data. And thereceiver decrypts the original text by using the extracted private key. Compared with the prior art, the method has the characteristic of high concealment, and an enemy cannot identify a concealed channel according to account characteristics.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Method for hiding message data into media data and a method for extracting that hidden data
InactiveUS6286100B1Static indicating devicesUser identity/authority verificationHidden dataHigh resistance
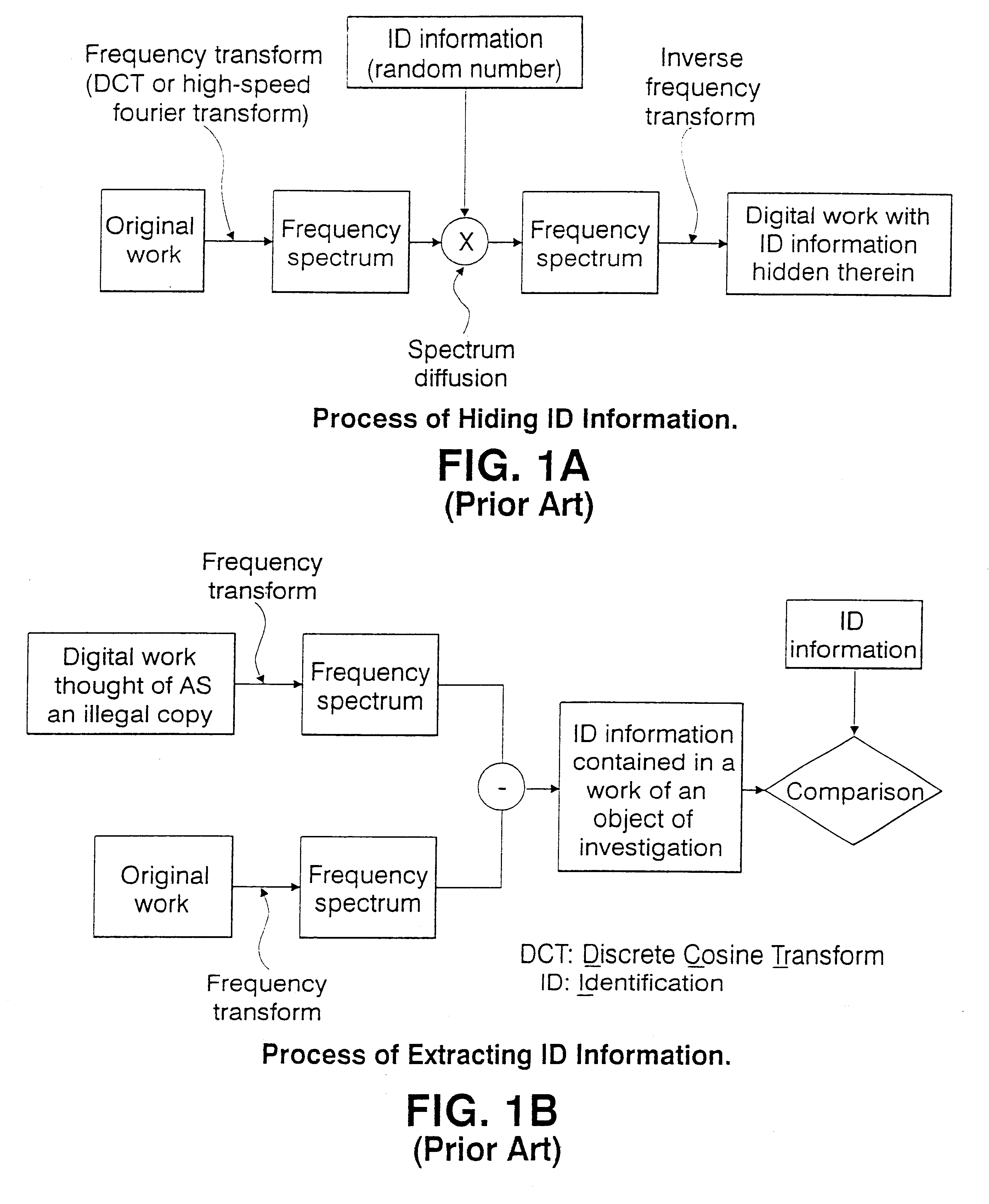
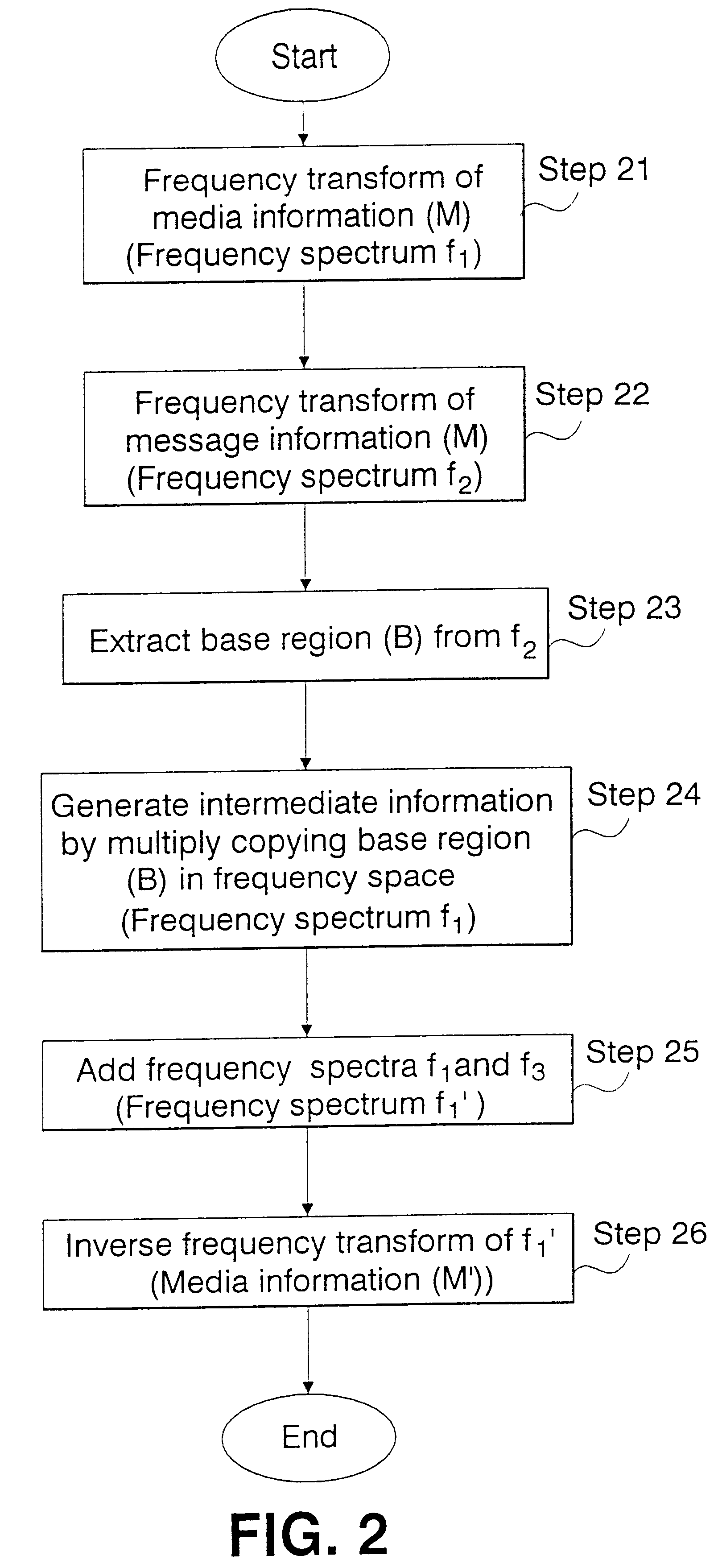
A method for hiding message information into media information in frequency space. The data hiding method has high resistance to removal or change of message information embedded into media information and effectively maintain hidden message information even when signal processing is performed by employing a frequency filter. More specifically, in order to hide message information (m) into media information (M), the frequency transform of the message information (m) and the media information (M) are performed, and frequency spectra f1 and f2 are obtained. Next, from the frequency spectrum f2 of the message information (m), a region containing feature frequency components representative of the features of the message information (m) in real space is extracted as the base region B. Then, n copies of the base region B are generated, and in frequency space, the n copies are dispersedly arranged.
Owner:IBM CORP
Method for realizing computer software intruder preventing edition based on confidence computation module chip
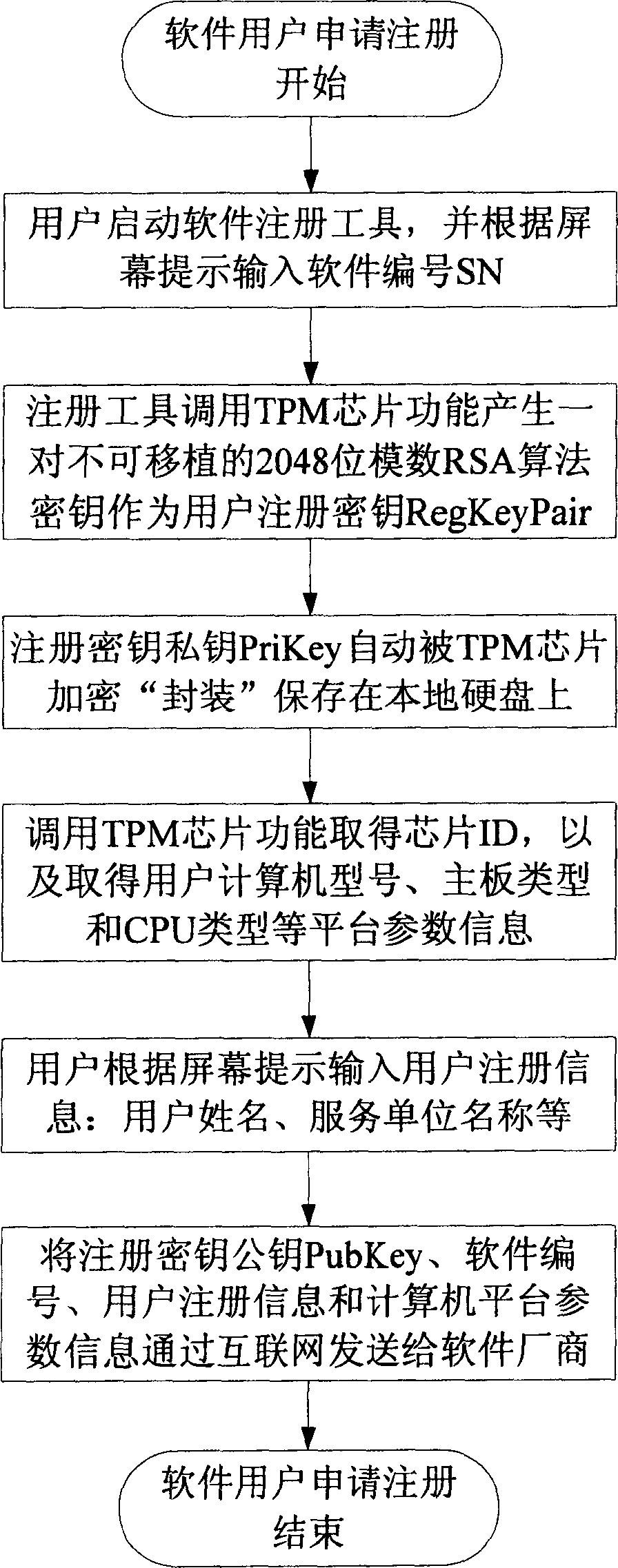
ActiveCN1740940AEnsure legal useAccurately informedDigital data processing detailsProgram/content distribution protectionHidden dataSoftware engineering
The invented method includes the following measures: firstly, mounting trusted computing module chip and its supporting software on the software user computer and implementing chip initialization; hiding key data selected from on part or several parts of protected software product by software copyright proprietor and transferring the software product containing no hidden data to legal software user; and proving a software registration tool software for user, so that it can effectively prevent computer bootleg.
Owner:SHENZHEN SINOSUN TECH
Power system transient stability evaluation method based on deep learning technology
InactiveCN107846012AGuaranteed Evaluation PerformanceReduce false positive rateNeural architecturesNeural learning methodsTransient stateTime domain
The invention relates to a power system transient stability evaluation method based on a deep learning technology. Firstly, a time domain simulation method is used to generate a sample set {x<0>, y<0>}; characteristic variable vectors are then extracted according to the sample set, and a training set {x<1>, y<0>} is formed, wherein the training set is the characteristic variable vector set; training parameters are determined, a stacked automatic encoder is trained based on the training set, characteristic extraction is carried out on the training set to generate a calculation set {x<2>, y<0>};and finally, based on the calculation set, classification model training is carried out on a convolution neural network, and a power system transient stability evaluation model is formed. The stackedautomatic encoder is used to carry out layer-by-layer characteristic extraction on the characteristic variable vectors, a hidden data mode is mined, high-order characteristics more facilitating transient stability evaluation are formed, the convolution neural network is further used to build a stable classification model, the evaluation performance of the model is thus ensured, the misjudgement rate of unstable samples can be reduced, noise interference in a wide area measurement system of the power system can be effectively overcome, and an important significance is provided for online safeand stable evaluation on the power system.
Owner:STATE GRID HUBEI ELECTRIC POWER COMPANY +1
Methods and apparatus for hiding data in halftone images
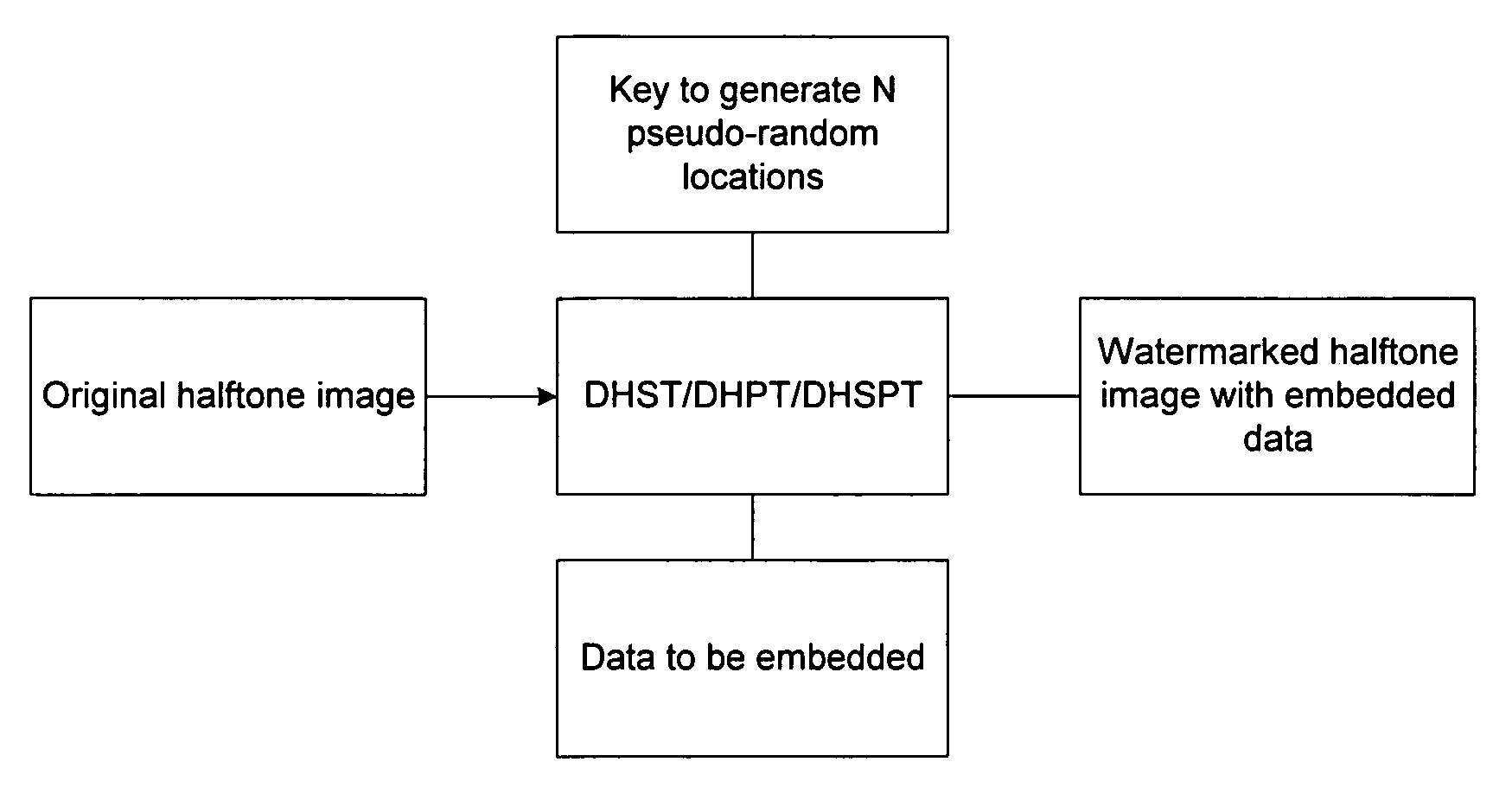
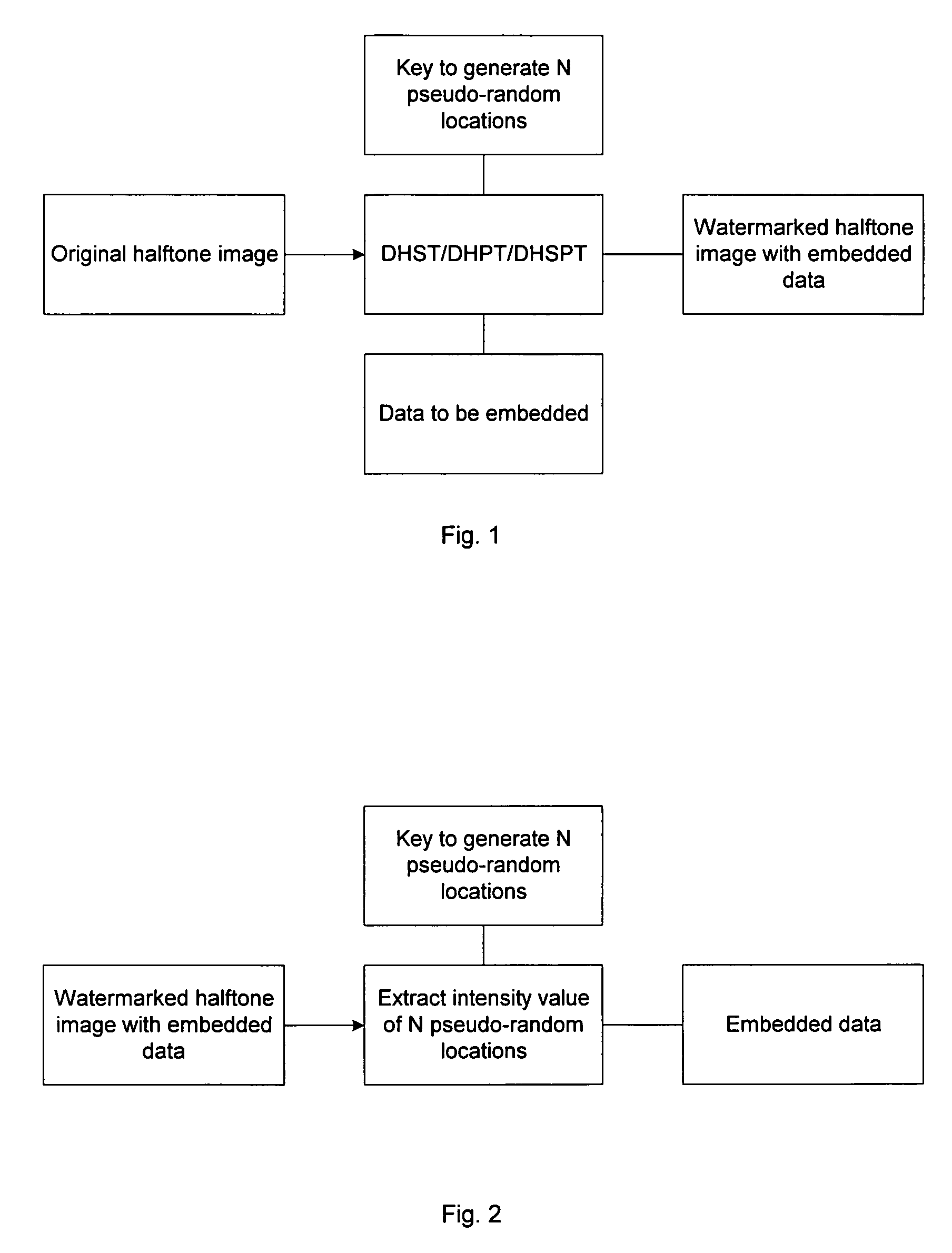
InactiveUS7058199B1A large amountPreserving the local average intensityCharacter and pattern recognitionVisual presentationPattern recognitionHidden data
We propose methods for generating a halftone image, in which each pixel takes one of two tone values. The generated image contains hidden data, which is present at data storage pixels chosen using a pseudo-random number generator. In a first case, the data is hidden within an existing halftone image by reversing the tone value at certain of the data storage pixels, and at pixels neighboring the data storage pixels. In a second case, the halftone image is generated from a grey-scale image, and data is hidden during this conversion process.
Owner:SCI & TECH HONG KONG UNIV OF THE
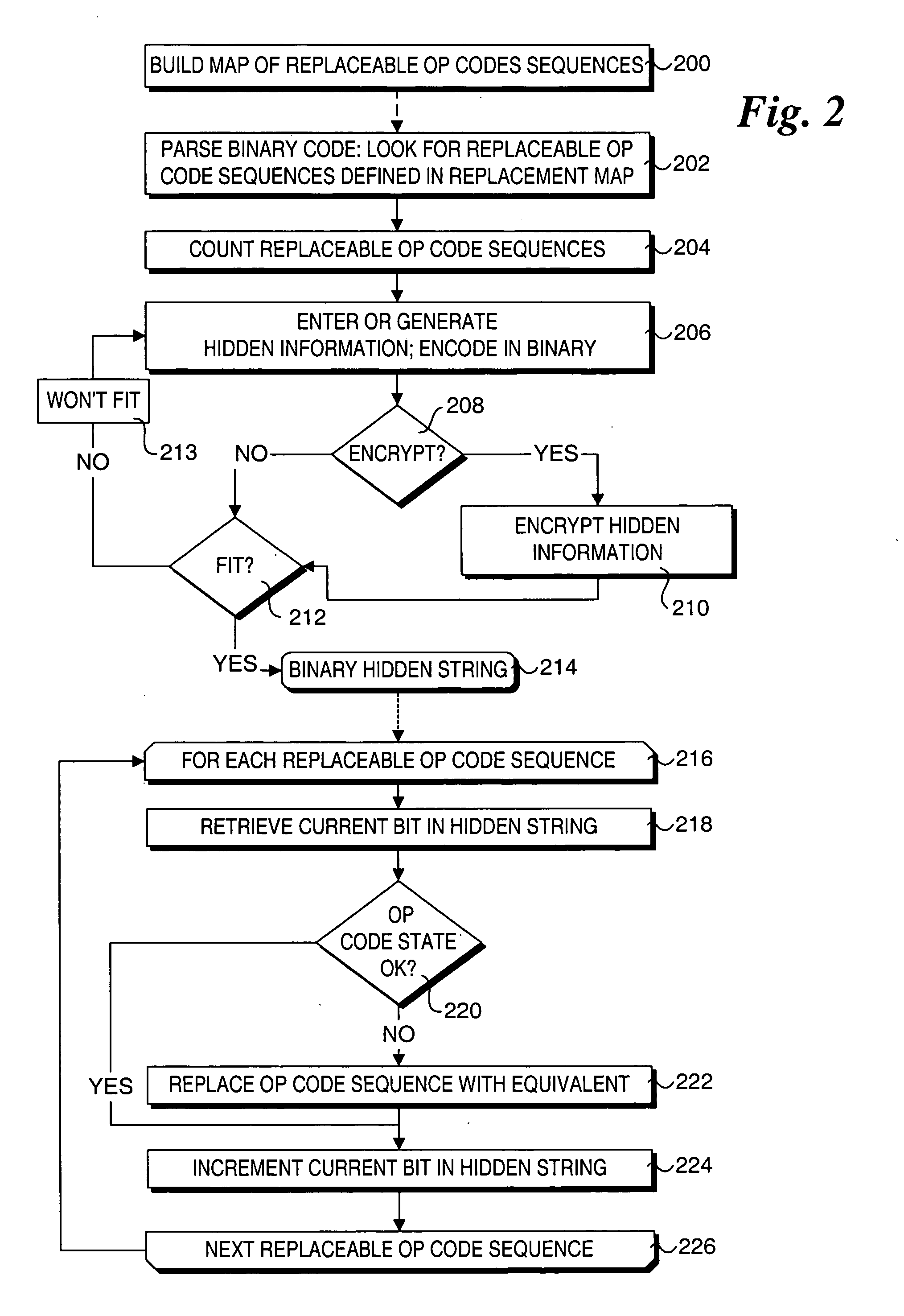
Method to provide transparent information in binary drivers via steganographic techniques
ActiveUS20050105761A1User identity/authority verificationCharacter and pattern recognitionComputer hardwareHidden data
Methods for providing and extracting hidden information in firmware images using steganographic processes. Information is hidden in binary firmware images, such as drivers, using a steganographic process in which the functionality of the binaries do not change, and the size is not increased. During a pre-boot phase of a computer system, binary firmware drivers containing hidden steganographic data are identified, and a steganographic extraction process is performed to extract the hidden data. In one embodiment, a hash is employed on an authentic binary image to uniquely identify the op code content. The digest from the hash is stored in the steganographic data. In one embodiment, a vendor's private key and optional signature is used to encrypt the hash. A similar hash is performed on the binary image of a discovered binary firmware driver, and the authentic hash digest is extracted from the steganographic data. The hash digests are compared to authenticate the binary firmware driver.
Owner:INTEL CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com