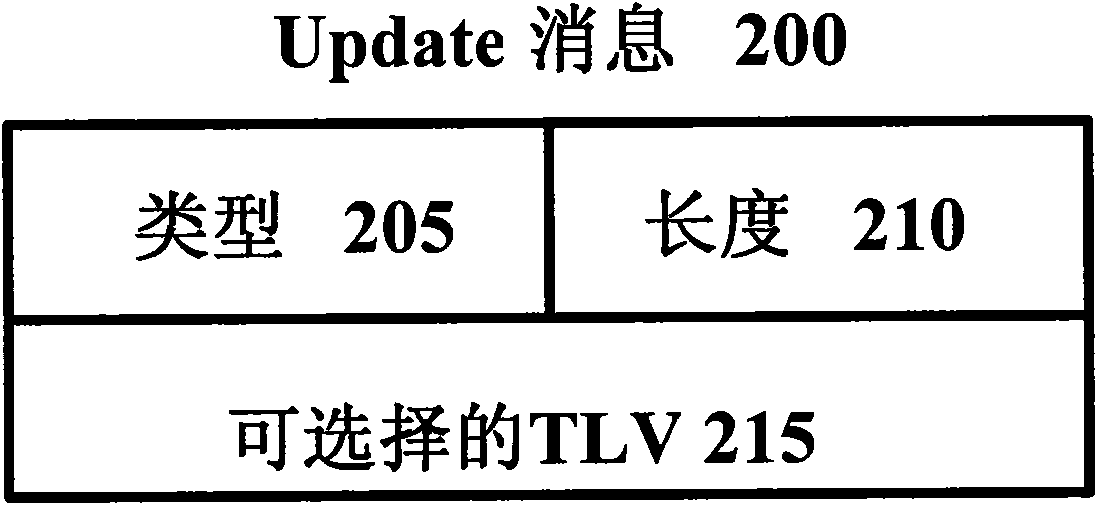
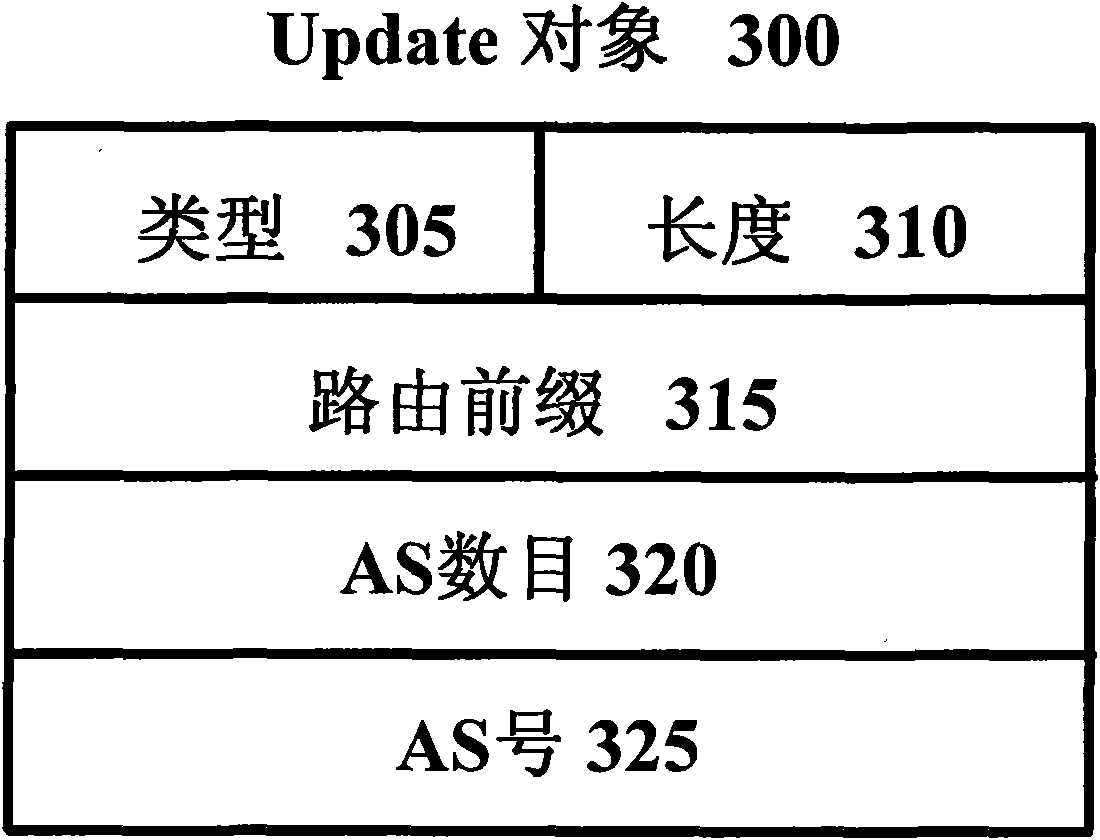
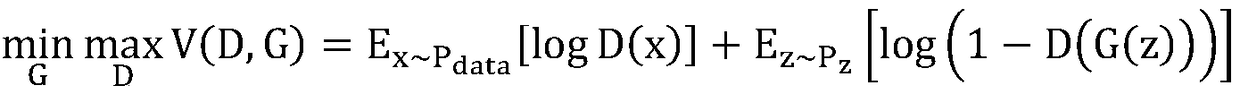Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
143 results about "Base domain" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
For categorization purposes, the base domain is assigned an appropriate category value that is representative of all pages and files contained within the website. The base domain and it’s respective category value can then be committed to a URL database, which can be cached on a device—in a data center, on a computer, or accessible via the cloud.
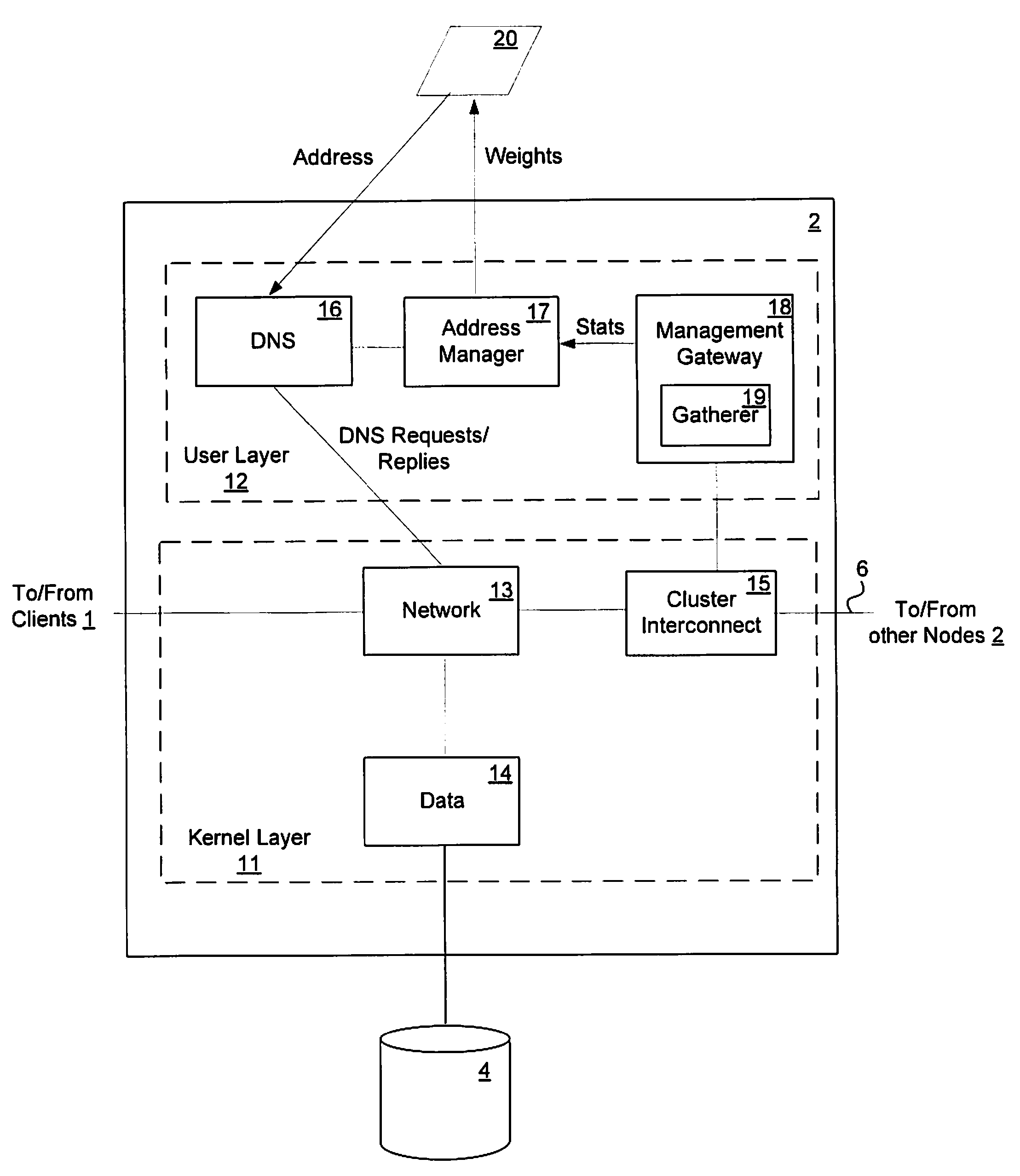
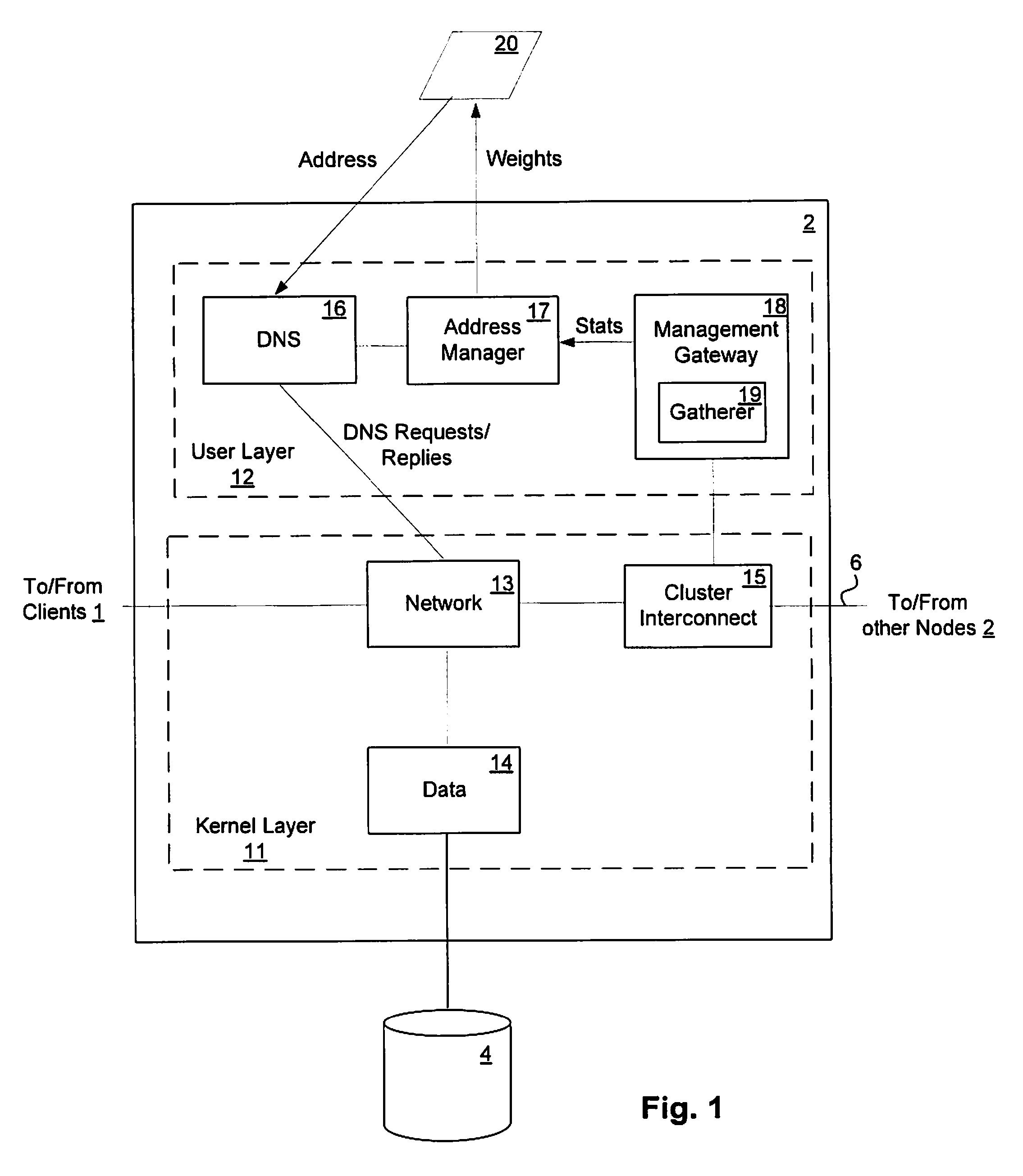
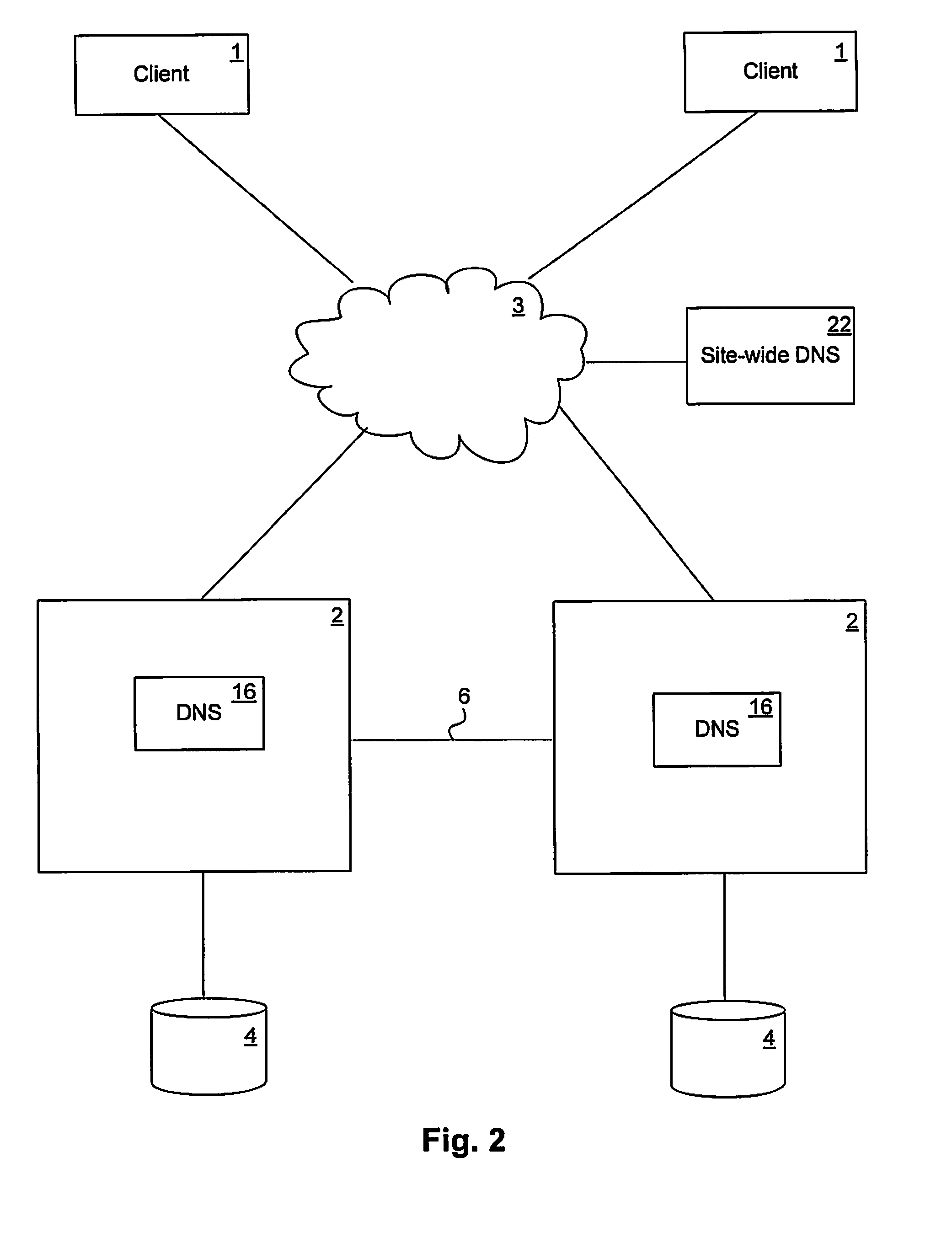
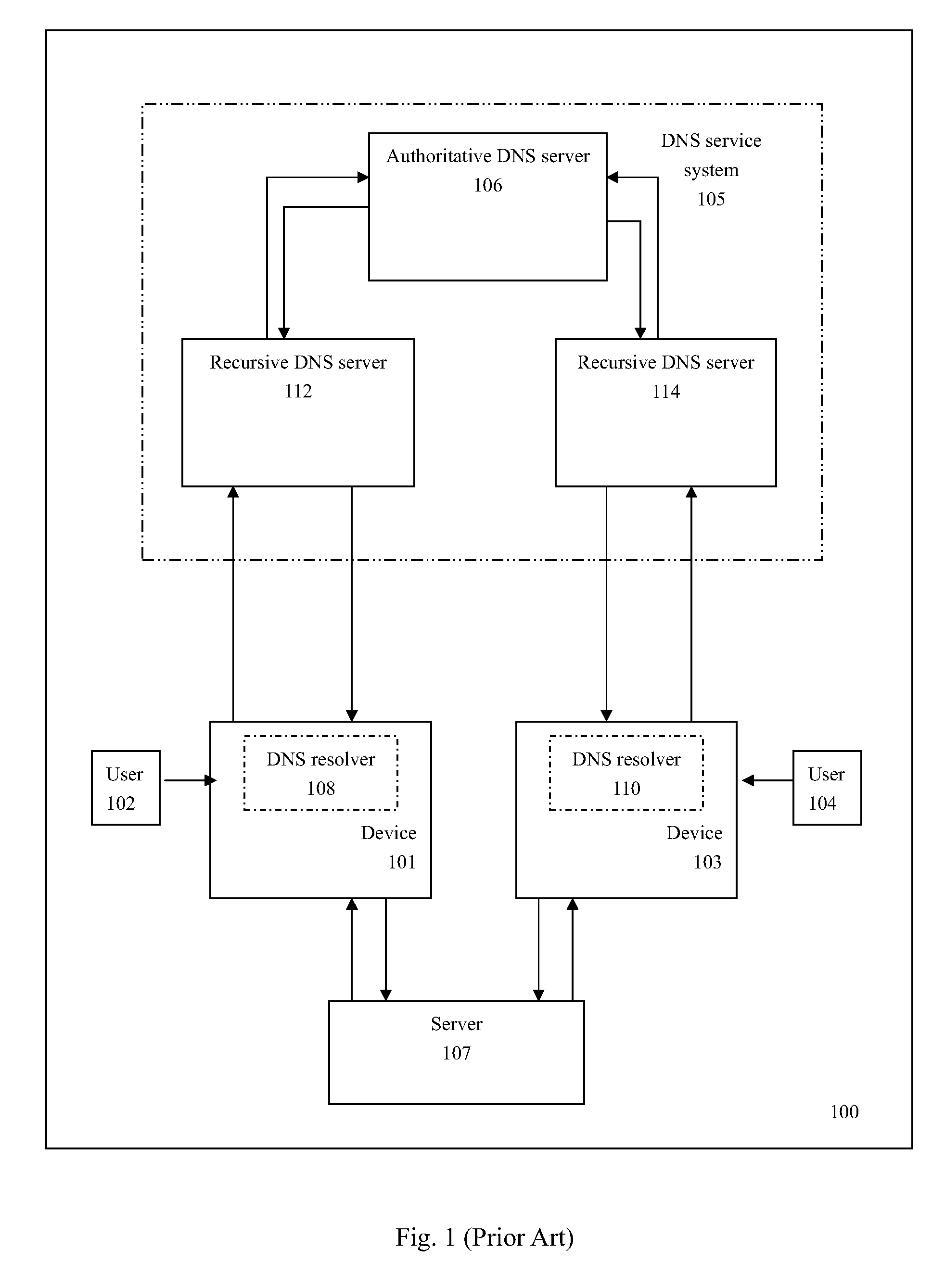
Load-derived probability-based domain name service in a network storage cluster
ActiveUS20100023621A1Multiprogramming arrangementsMultiple digital computer combinationsDomain nameIp address
DNS name resolution is integrated into each node in a network storage cluster, to allow load balancing of network addresses, using a weighted random distribution to resolve DNS requests. A node in the cluster gathers statistics on utilization of resources, such as CPU utilization and throughput, on nodes in the cluster and distributes those statistics to all other nodes. Each node uses the same algorithm to generate weights for the various IP addresses of the cluster, based on the statistics distributed to it. The weights are used to generate a weighted list of available network addresses. In response to a DNS request, a DNS in a given node randomly indexes into the weighted address list to resolve requests to a network address. The weights are chosen so that the DNS is likely to pick an IP address which has a low load, to balance port and node usage over time.
Owner:NETWORK APPLIANCE INC
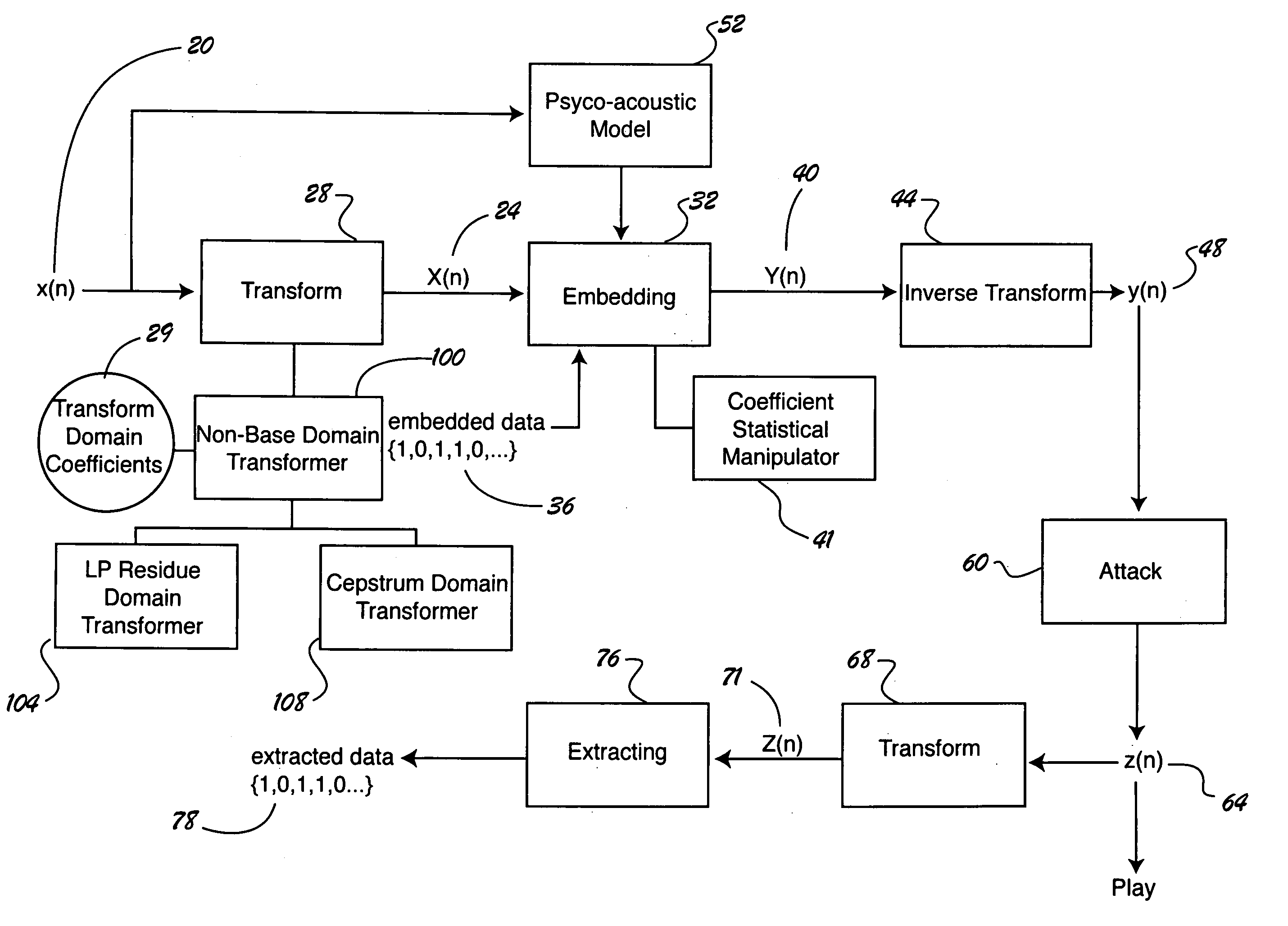
Computer-implemented method and apparatus for audio data hiding
InactiveUS7058570B1Maximize survivabilityLittle changeSpeech analysisSound producing devicesHidden dataSurvivability
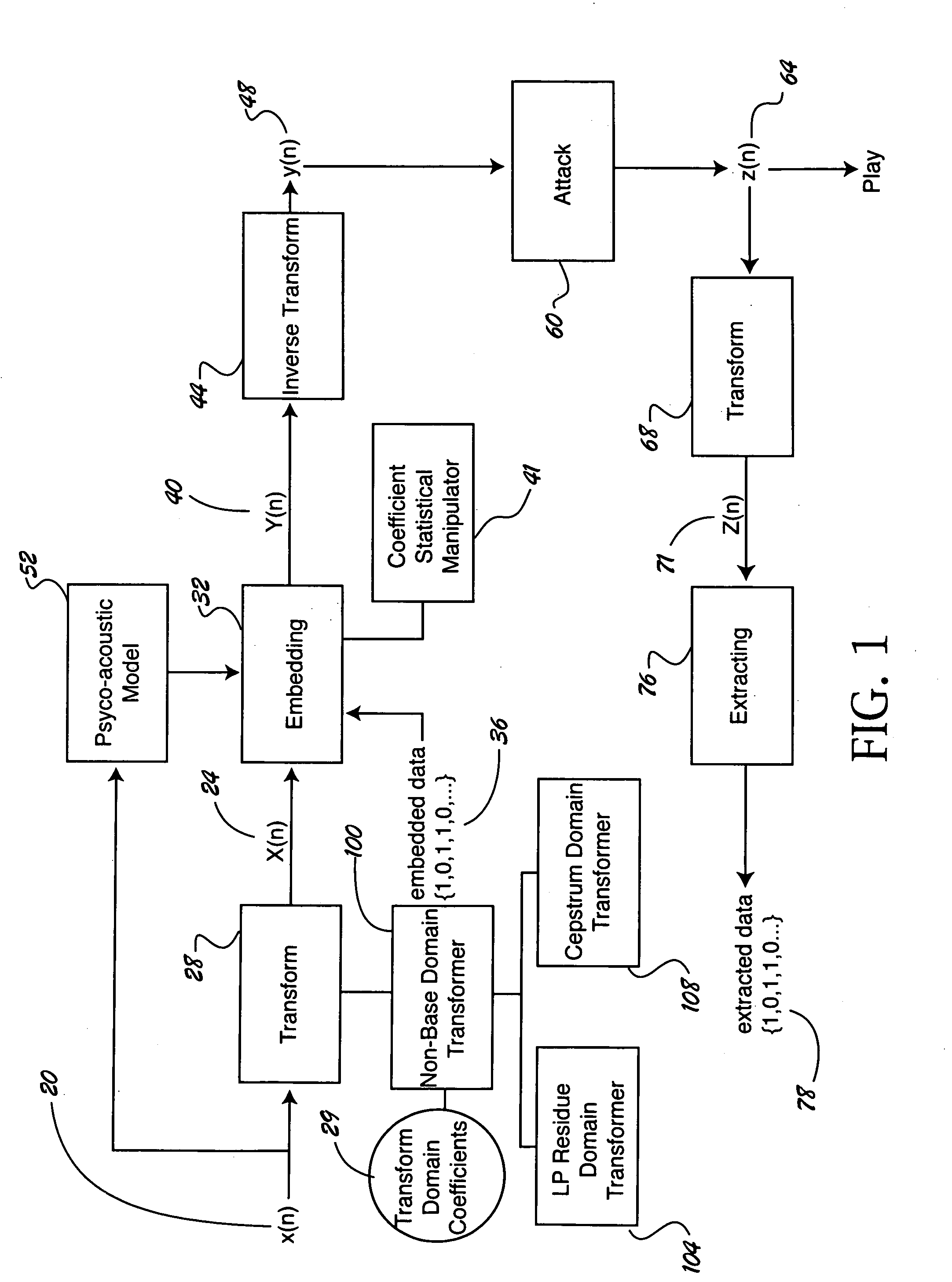
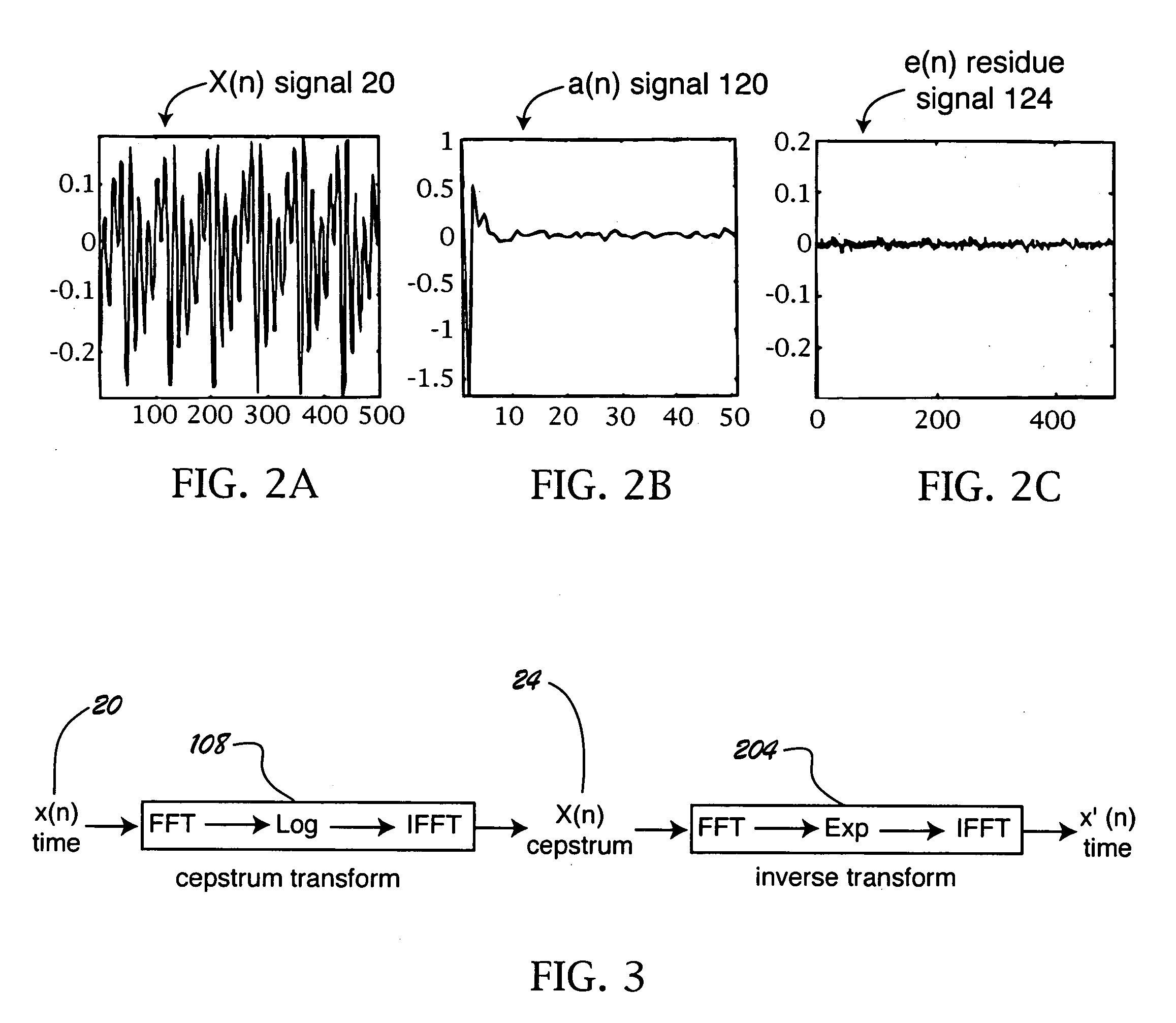
A computer-implemented method and apparatus for embedding hidden data in an audio signal. An audio signal is received in a base domain and then transformed into a non-base domain, such as cepstrum domain or LP residue domain. The statistical mean manipulation is employed on selected transform coefficients to embed hidden data. The introduced distortion is controlled by psychoacoustic model to ensure the imperceptibility of the embedded hidden data. Scrambling techniques can be plugged in to further increase the security of the data hiding system. The present new audio data hiding scheme provides transparent audio quality, sufficient embedding capacity, and high survivability over a wide range of common signal processing attacks.
Owner:PANASONIC CORP
Systems and methods for cognitive testing
InactiveUS20180055434A1Improve motor functionImprove efficiencyAnimal housingMedical report generationSpecific testModularity
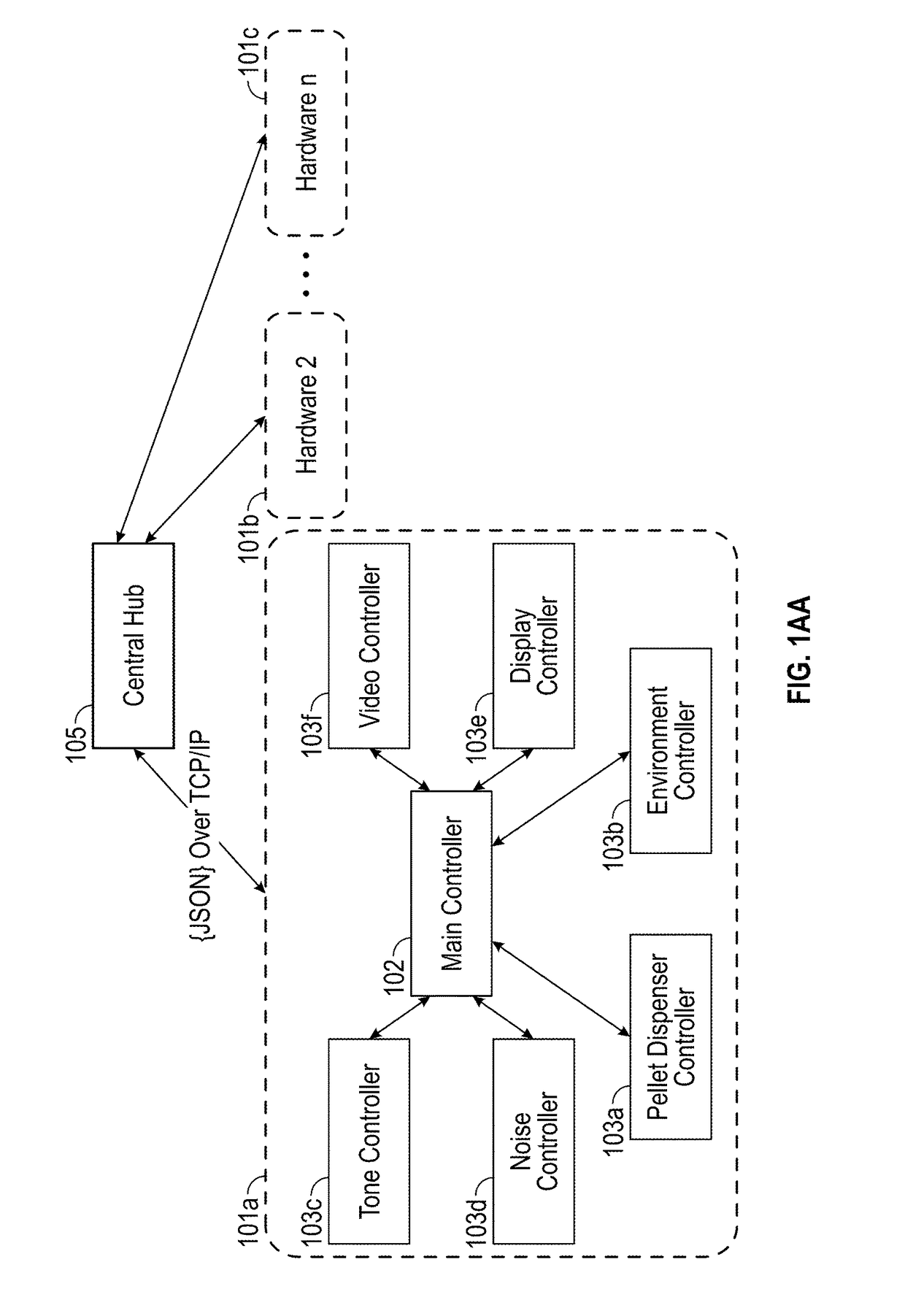
Systems, apparatuses, devices, networks, and methods for testing of animals, and, in particular, cognitive testing. Testing can include a modular hardware controller configured to include at least two modular interfaces, allowing interconnection of one or more child controller circuit boards. The child controller boards may collectively control an environment within the testing chamber, and receive input from or provide output to a testing chamber of an animal testing enclosure. Features are provided to execute testing protocols and collect results, including those using a script-based domain specific language, as well as to adjust a specific test execution using feedback from the testing system to ensure compliance with testing protocols.
Owner:DART NEUROSCIENCES LLC
Communication Method and System Using User ID-Based Domain Name
InactiveUS20100121954A1Digital data processing detailsUser identity/authority verificationDomain nameIp address
A method of communication is provided, which comprises assigning a first domain name by a server to a first user when the first user logs onto the server using a first device, the first domain name being associated with a first device identifier of the first device and a first user identifier of the first user; and negotiating communication for the first device based on the first domain name despite of the IP address of the first device. Other embodiments are disclosed. By way of the present invention, a secure and convenient resource sharing and access control may be achieved.
Owner:YANG ZHENG +1
Distributed database system by sharing or replicating the meta information on memory caches
InactiveUS20100293140A1High speed synchronizationInformation securityDigital data processing detailsDatabase distribution/replicationLarge scale dataDistributed database
It is a purpose of this invention to achieve Scale-Out of the distributed database system that assumes a real-time update to be a requirement and which is achieved by dividing the database system into two or more database domains. This is to achieve handling of even larger scale databases while providing even higher performance. Assuming that the large-scale database system has been distributed to two or more of above-mentioned data base domains, in multi transaction processing with real-time update of the database object across two or more of above-mentioned database domain, this invention is achieved by executing the above-mentioned multi transaction processing to the database meta information storage management part in the database meta information management repository device by applying partition topology technology or replication topology technology for exchange and synchronization of meta information such as status information etc. at even higher speeds.
Owner:NISHIYAMA SHUHEI
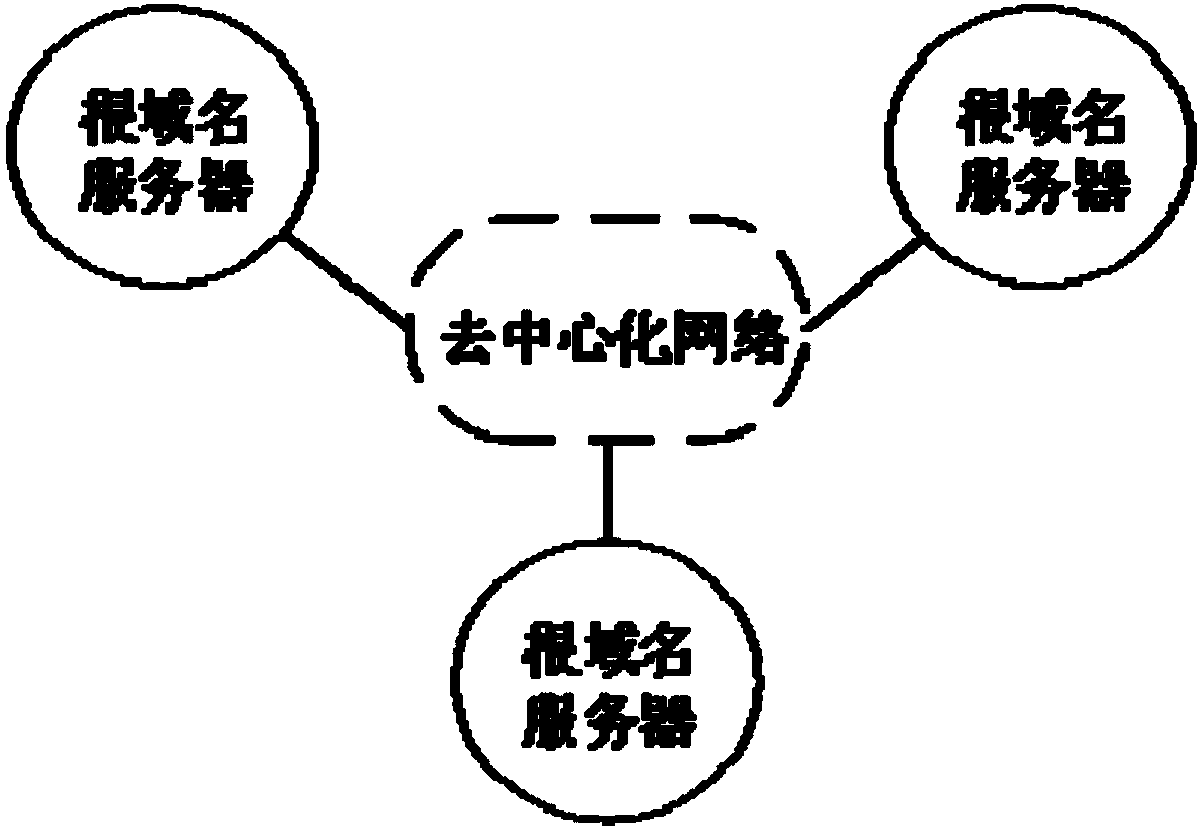
Blockchain-based domain name resolution system
ActiveCN108064444AImprove management efficiencyEfficient managementSecuring communicationChain networkChain link
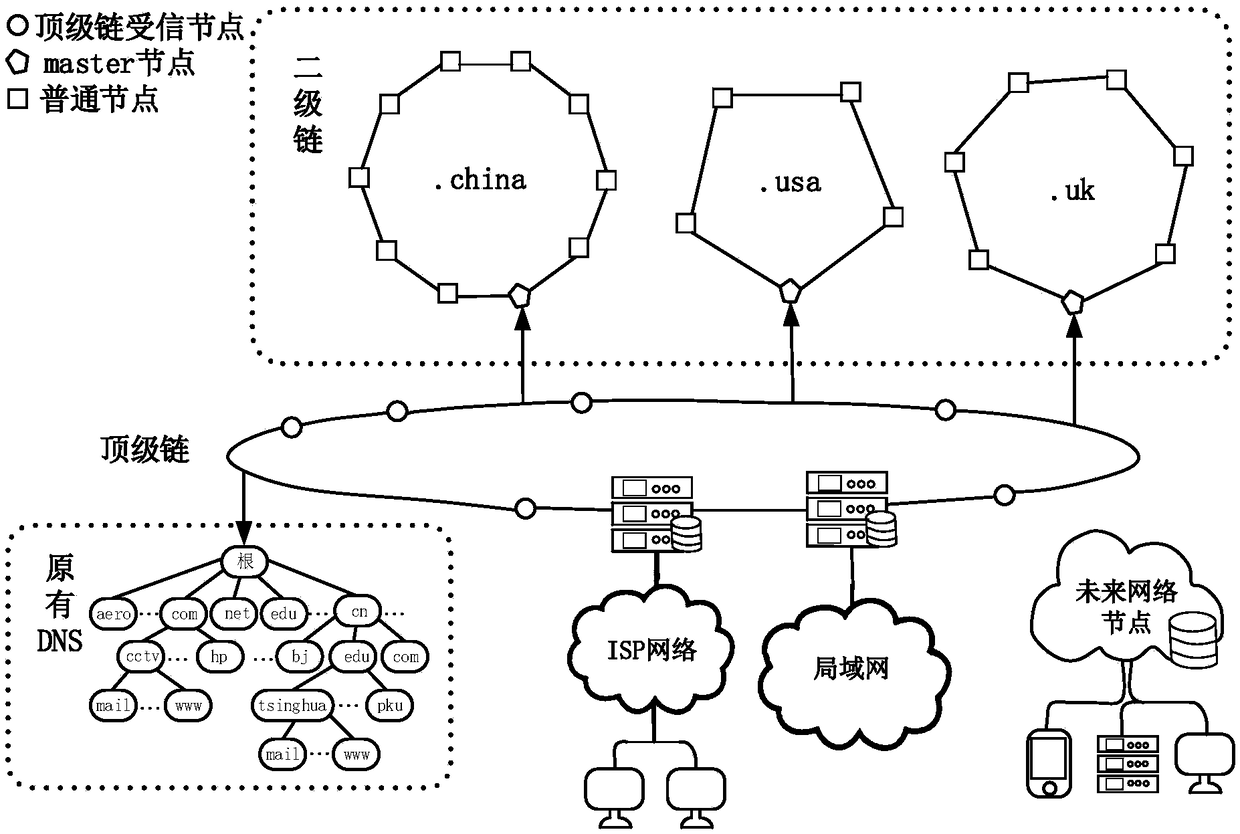
The invention relates to a blockchain-based domain name resolution system. The domain name resolution system adopts a hierarchical structure, including a top-level domain name chain network, a second-level domain name chain network, a future network node and an original DNS system network, and the top-level domain name chain links the second-level domain name chain network, the future network nodeand the original DNS system network; the top-level domain name chain network is used for each professional organization to deploy reliable server nodes to form an allied blockchain network, each nodeserver records information about all current top-level domain names, second-level domain name chain nodes, future network nodes, and existing DNS system root nodes; the second-level domain name chainnetwork is used for domain name registration and management, and records a record of all second-level domain names and subdomain names to which they belong; the future network node is used for storing metadata and indexes thereof in the future network. The resolution request is reduced and the efficiency of domain name resolution is effectively improved.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL
Generalized parity stripe data storage array
InactiveUS20050086575A1Increased Hamming distanceIncrease distanceNon-binary linear block codesError detection/correctionOn columnTheoretical computer science
The Hamming distance of an array of storage devices is increased by generating a parity check matrix based on column equations that are formed using an orthogonal parity code and includes a higher-order multiplier that changes each column. The higher order multiplier is selected to generate a finite basic field of a predetermined number of elements. The array has M rows and N columns, such that M is greater than or equal to three and N is greater than or equal to three. Row 1 through row M-2 of the array each have n-p data storage devices and p parity storage devices. Row M-1 of the array has n-(p+1) data storage devices and (p+1) parity storage devices. Lastly, row M of the array has N parity storage devices.
Owner:IBM CORP
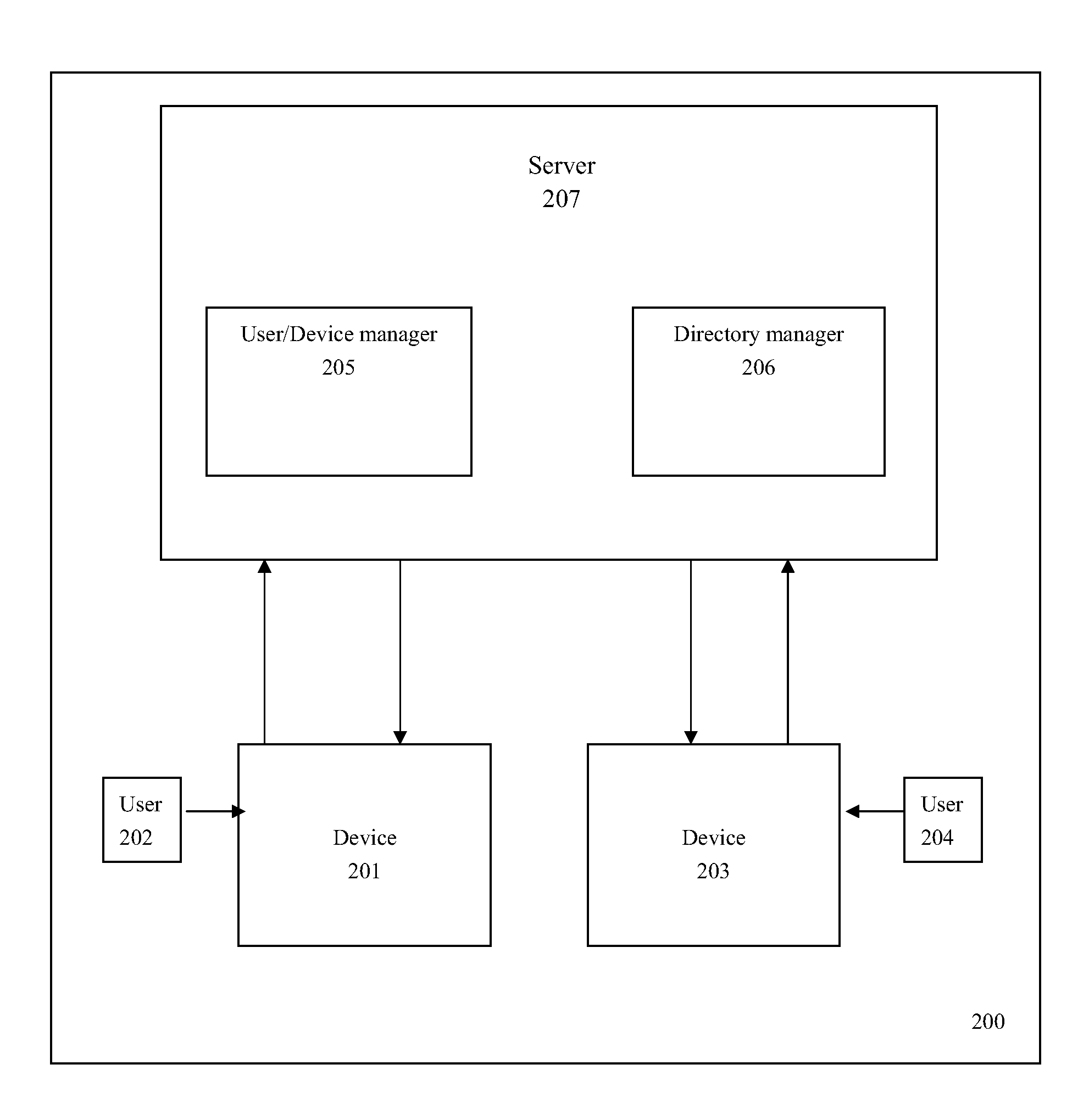
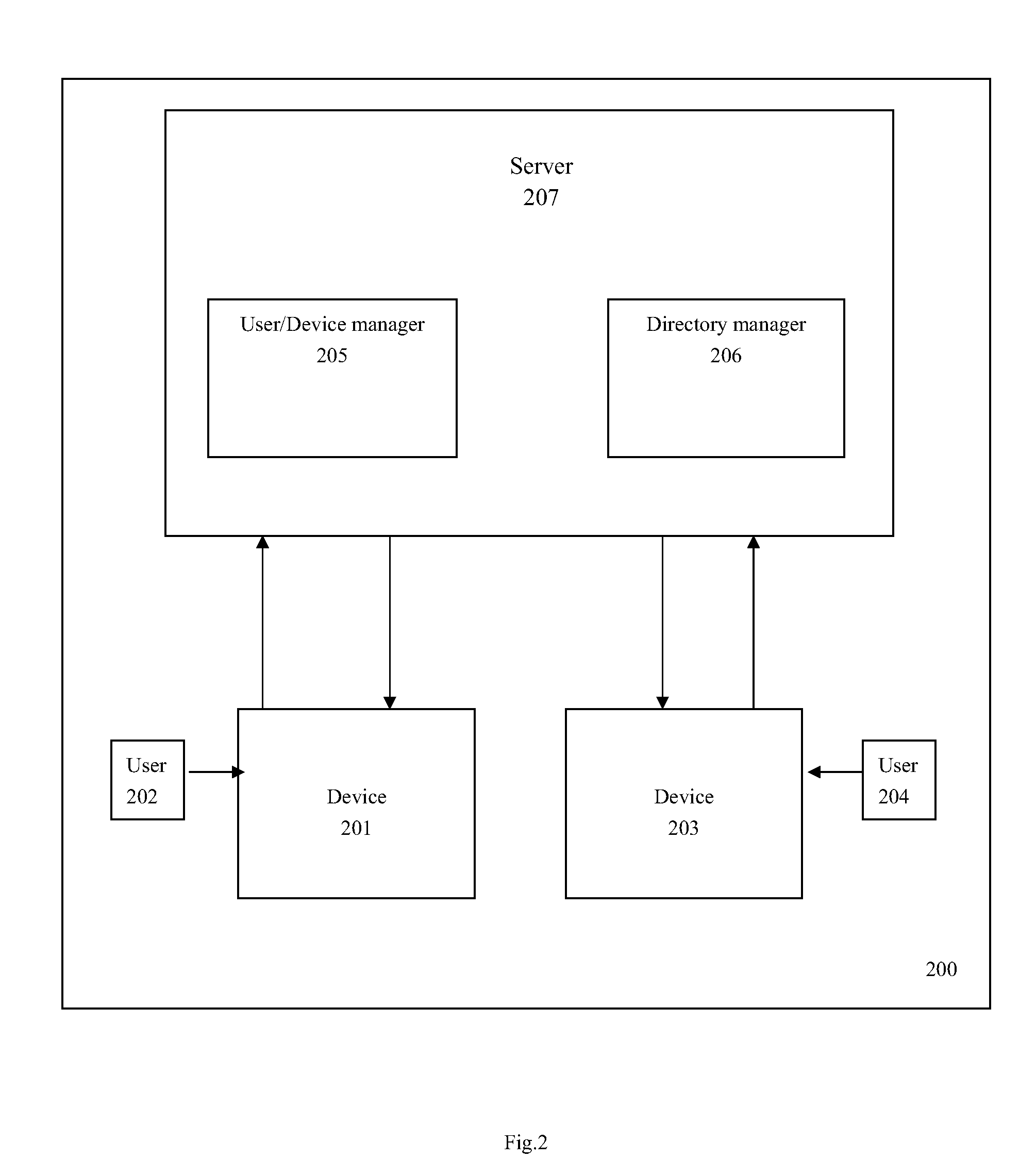
Domain management method and domain context of users and devices based domain system
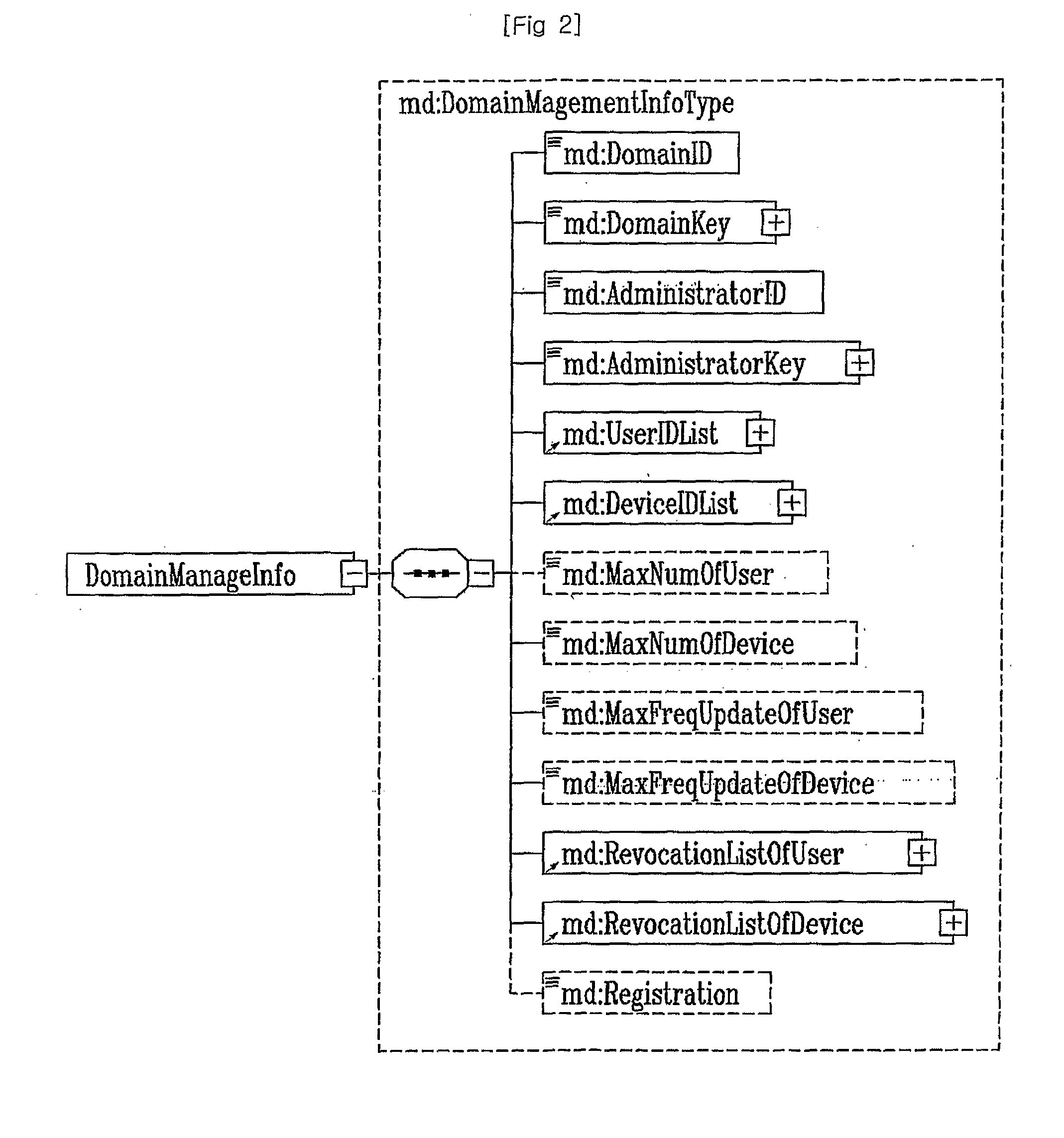
ActiveUS20090235330A1Satisfy the demandReduce administrative burdenDigital data processing detailsMultiple digital computer combinationsDigital contentInternet privacy
Provided are domain contexts indicating user and device based domain systems for being applied to a new digital content protection / management system, and management methods thereof. A concept of “domain” is introduced in the present invention so that various business models can be obtained in accordance with content use of one home or small-sized group. The domain refers to as a group of user and device SAV and PAV indicating a context for being applied to the domain system includes: a domain identifier for specifying a domain as a region containing at least one content execution device and at least one content user; domain authentication information for guaranteeing authenticity of the domain; a user list containing information of users belonging to the domain; and a device list containing devices belonging to the domain.
Owner:ELECTRONICS & TELECOMM RES INST
Spin oscillator device
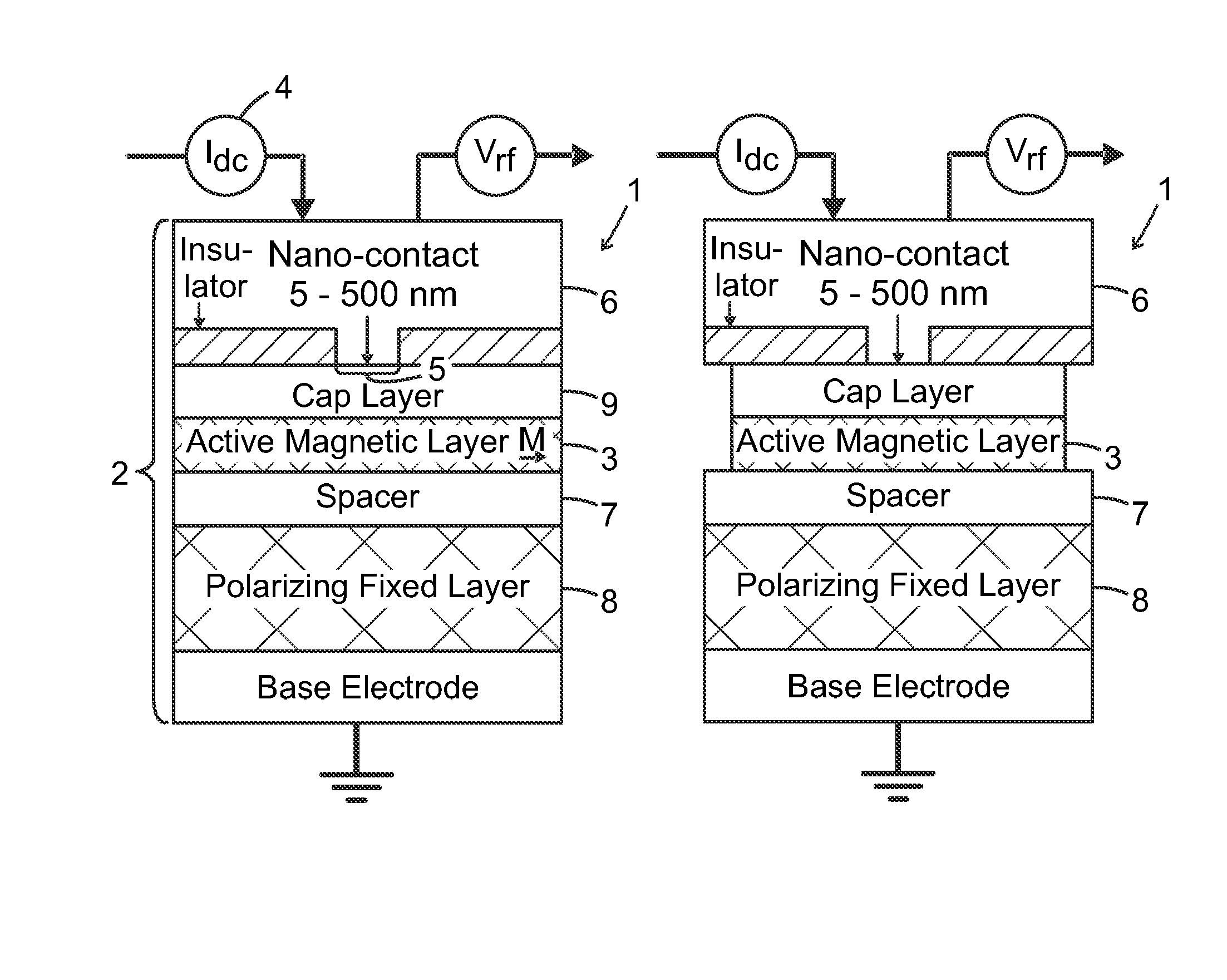
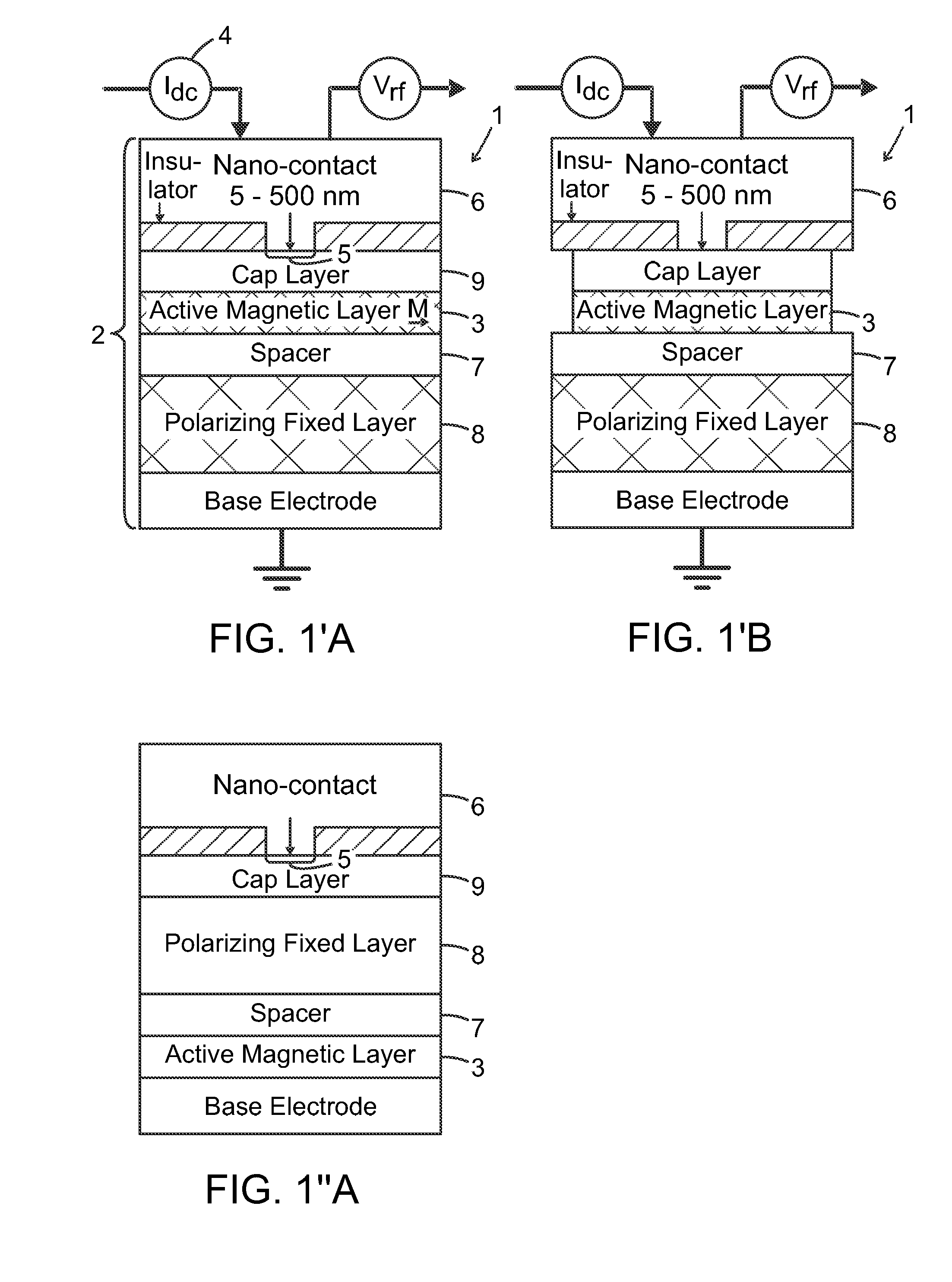
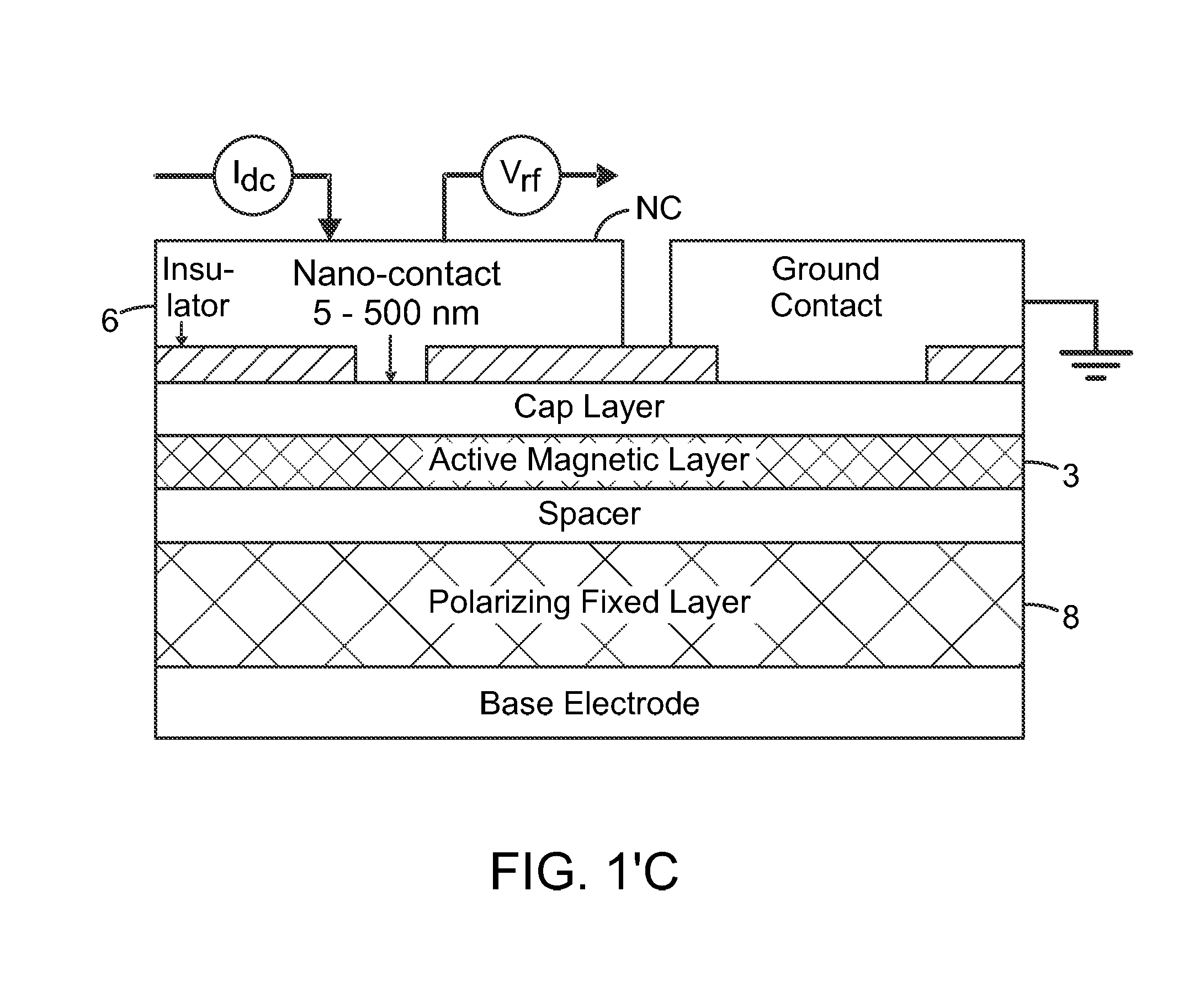
ActiveUS20170033742A1Detection is limitedPulse automatic controlMagnetic-field-controlled resistorsSpin-transfer torqueMagnetic memory
The present invention relates to using spin transfer torque underneath a nanocontact on a magnetic thin film with perpendicular magnetic anisotropy (PMA), provides generation of dissipative magnetic droplet solitons and magnetic droplet-skyrmions and report on their rich dynamical properties. Micromagnetic simulations identify the conditions necessary to nucleate and drive droplet-skyrmions over a wide range of currents and fields. Micromagnetic simulations also demonstrate how droplets and droplet-skyrmions can be used as skyrmion injectors and detectors in skyrmion-based magnetic memories. The droplet-skyrmion can be controlled using both current and magnetic fields, and is expected to have applications in spintronics, magnonics, skyrmionics, and PMA-based domain-wall devices.
Owner:NANOSC AB
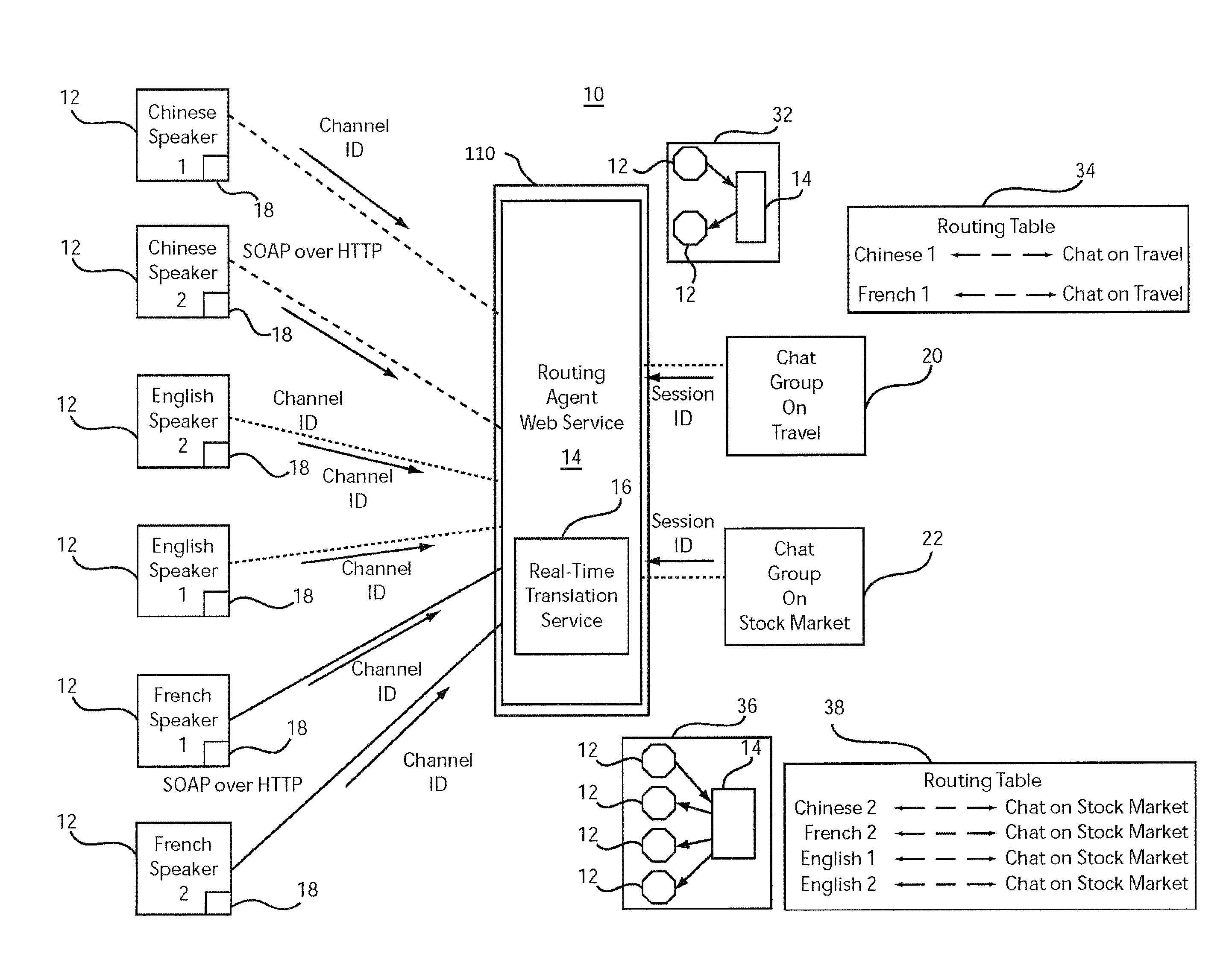
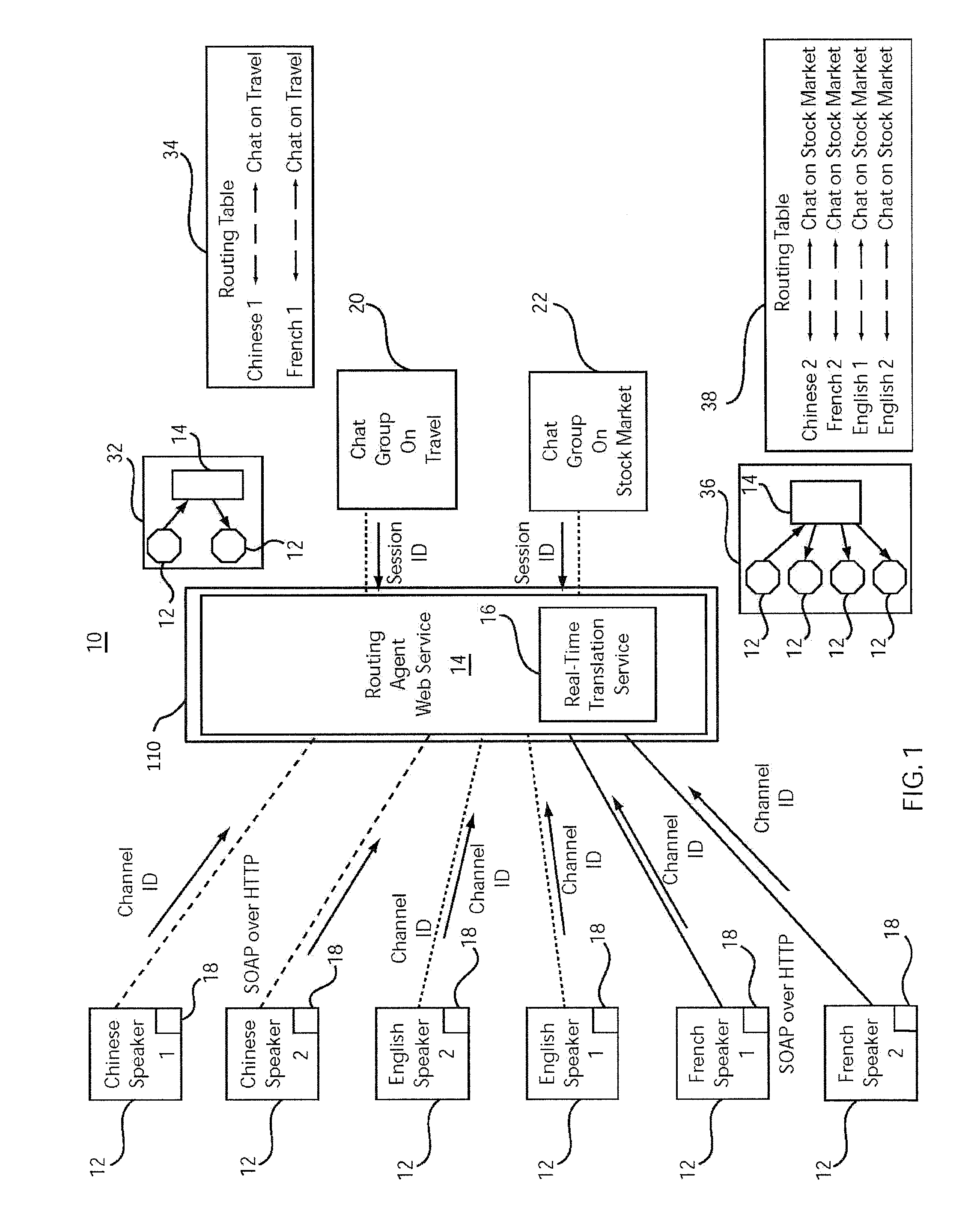
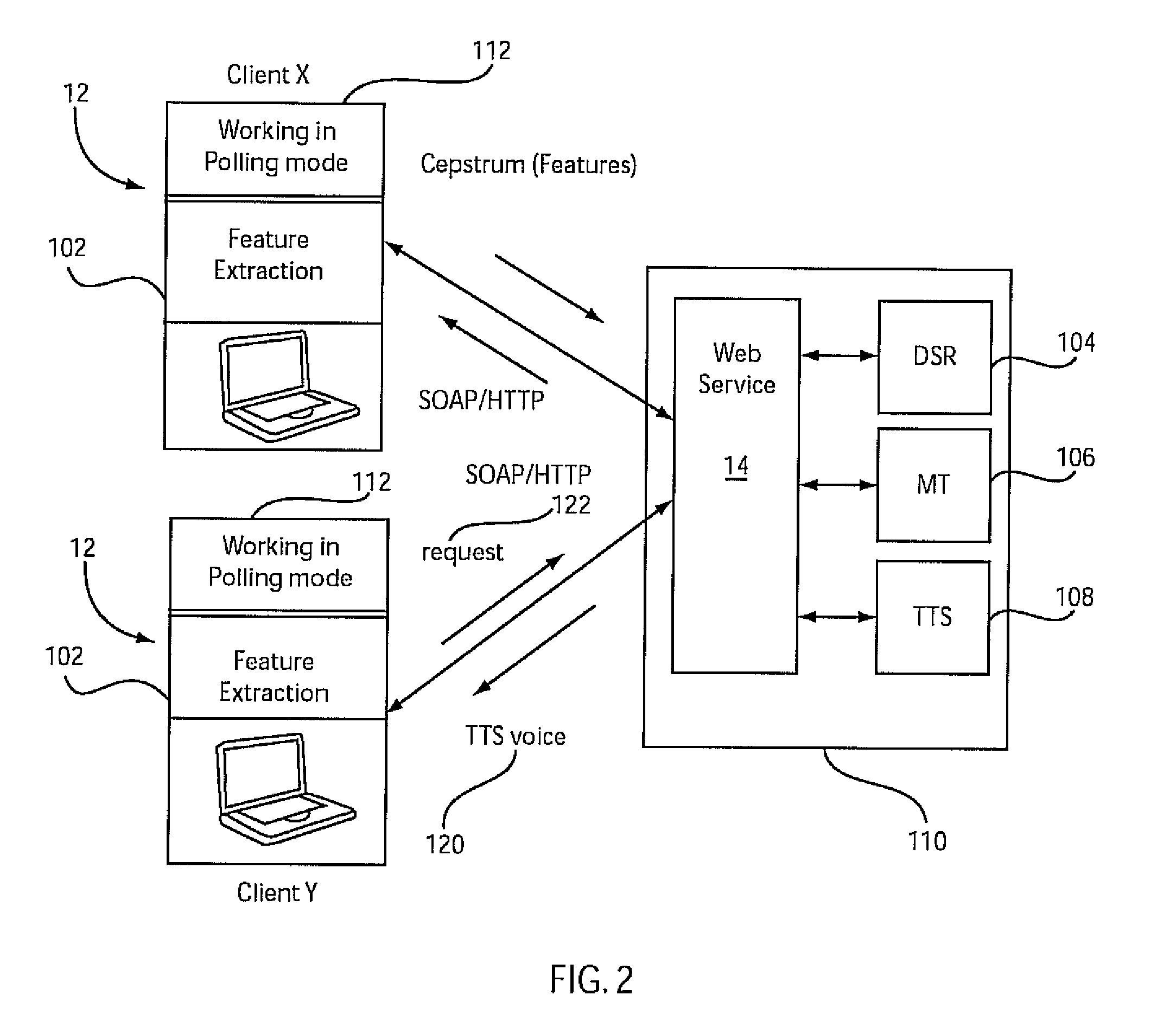
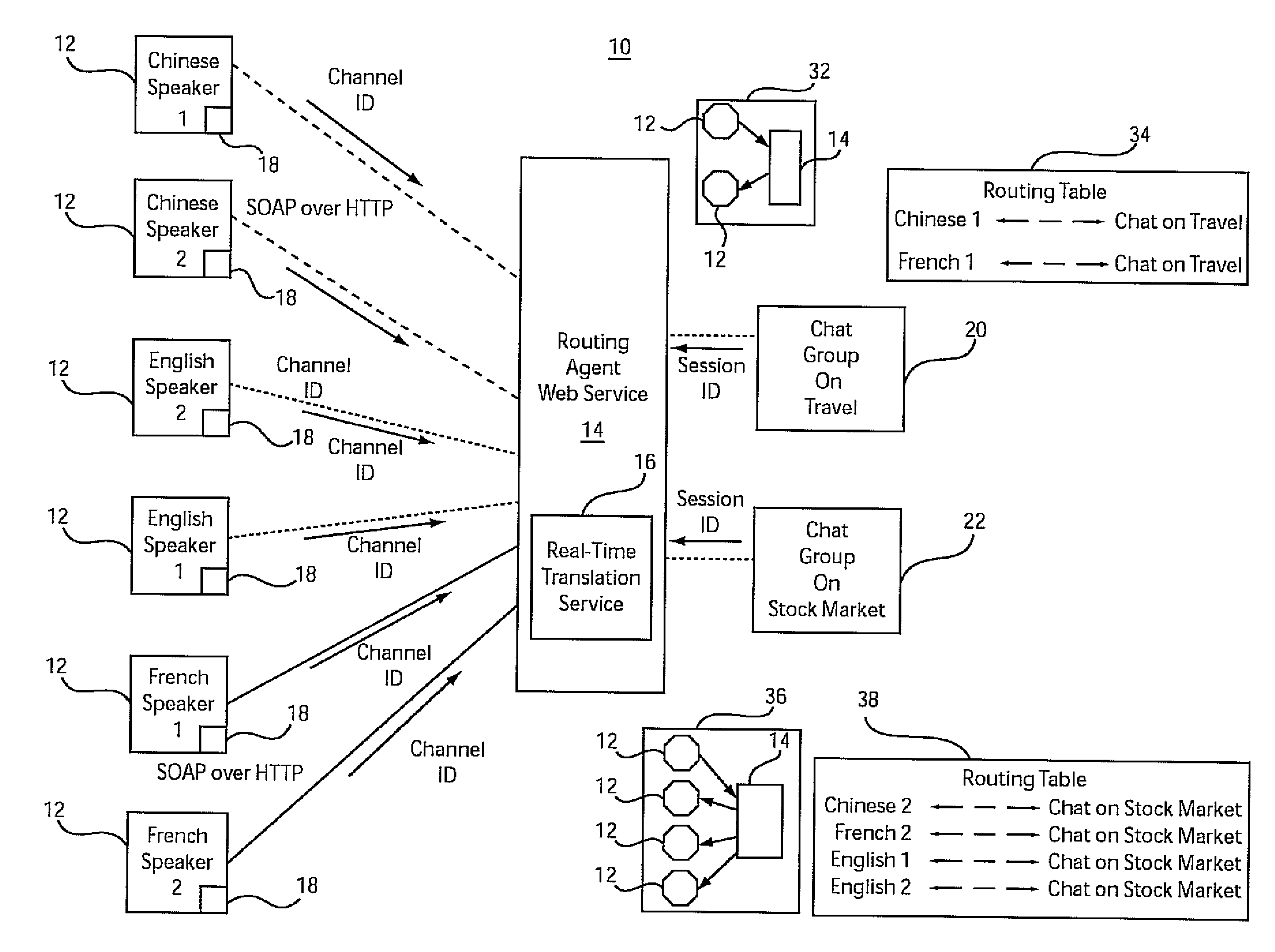
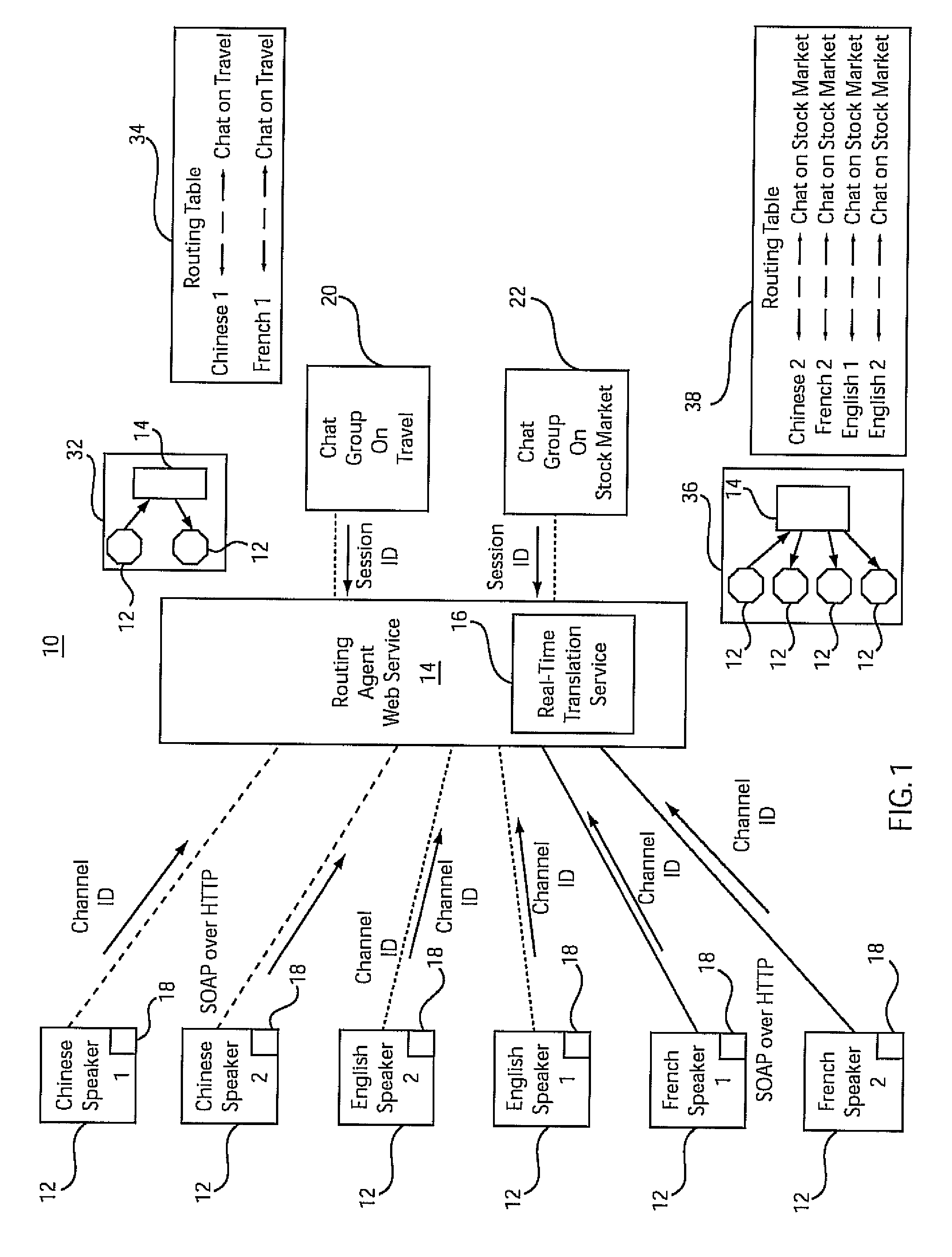
Open architecture based domain dependent real time multi-lingual communication service
InactiveUS8270606B2Natural language translationDigital data processing detailsReal-time webInternet communication
A system and method for real-time network communications provides a session identifier as a public key for group communication between clients, and provides a channel identifier representing a private key for each of a plurality of clients. The channel identifier includes client-specific attributes, which function to indicate grouping criteria for the group communication. A dynamic communication link is created over a network between a client and a service based upon the public and private key combination such that group communication is enabled based upon the attributes of the private key and the public key. Communications are translated using a translation service which employs the attributes associated with the private key and the public key combination to provide response information in a designated language to enable multi-lingual real-time communications.
Owner:IBM CORP
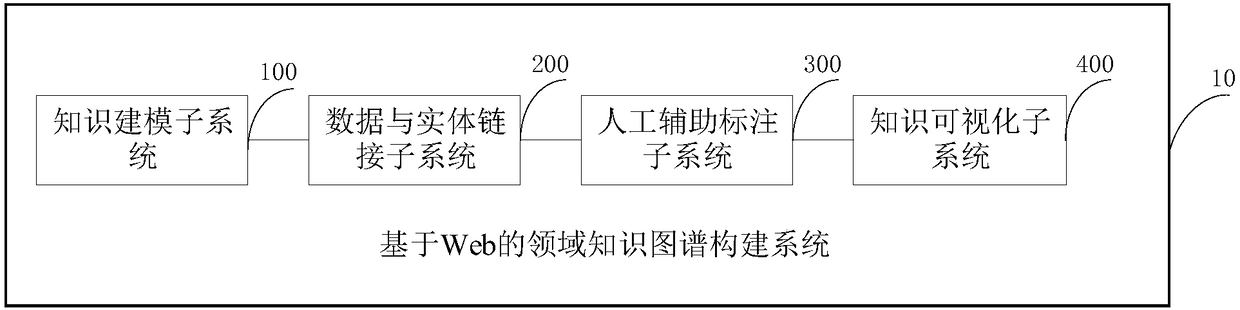
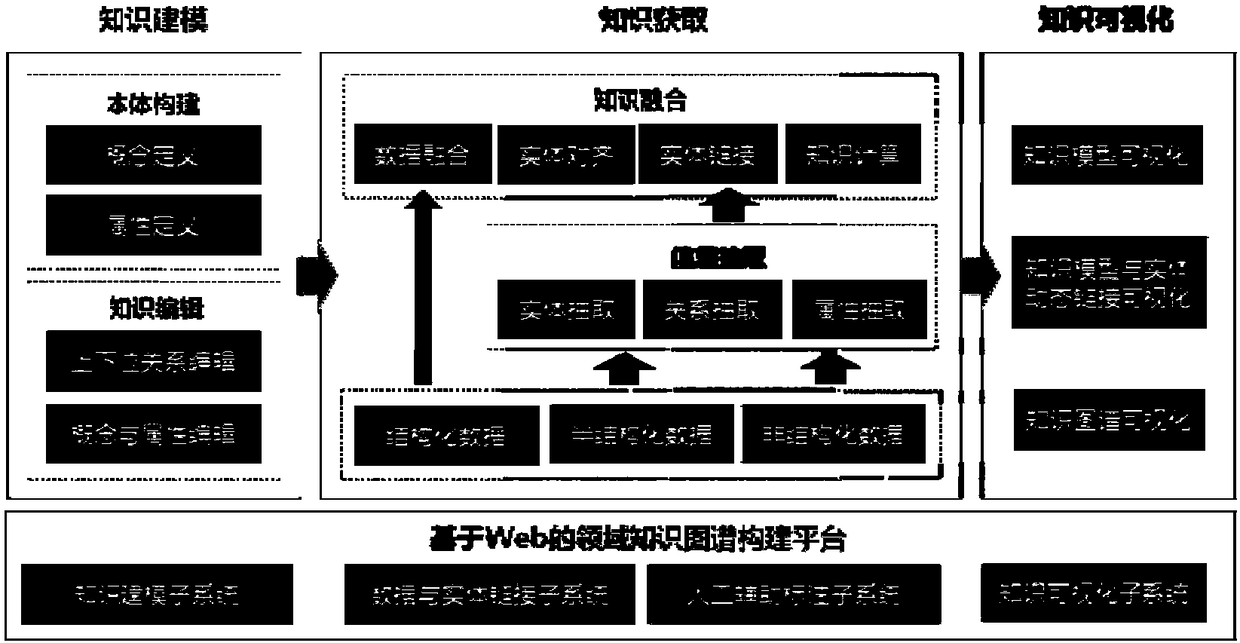
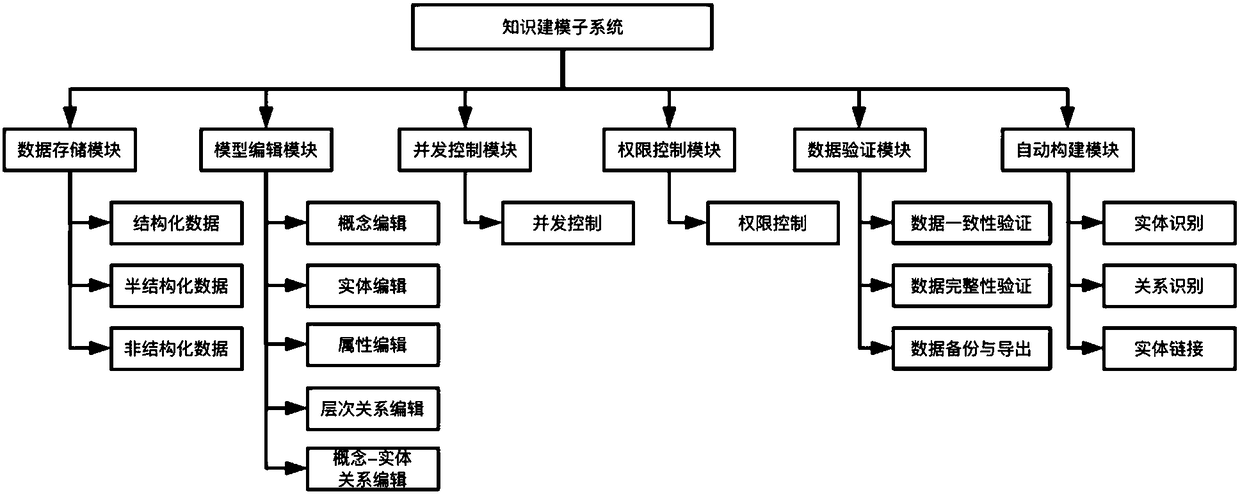
Web-based domain knowledge map construction system and method
ActiveCN108345647AReduce difficultyHigh precisionSpecial data processing applicationsEntity linkingData ingestion
The invention discloses a Web-based domain knowledge map construction system and method. The system comprises a knowledge modeling subsystem, a data and entity link subsystem, a human assisted labeling subsystem and a knowledge visualization subsystem, wherein the knowledge modeling subsystem is sued for obtaining an original knowledge model according to a preset data resource, and receiving an operation instruction of an operation interface so as to construct a data mode of a knowledge map to obtain a knowledge model; the data and entity link subsystem is used for extracting knowledges according to multiple types of data and storing the extracted knowledges into the knowledge map; the human assisted labeling subsystem is used for receiving a user labeling instruction so as to change the knowledge map according to the user labeling instruction; and the knowledge visualization subsystem is used for visually displaying the knowledge model, a dynamic link between the knowledge model and an entity and the changed knowledge map. The system is capable of simply and conveniently completing the work such as knowledge modeling, knowledge obtaining and knowledge visualization, so that the domain knowledge map construction difficulty is greatly reduced and benefit is brought to enhance the accuracy of domain knowledge maps.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Blockchain-based domain name resolution system
InactiveUS20190166085A1Improve management efficiencyImprove analysis efficiencyEncryption apparatus with shift registers/memoriesChain networkBase domain
The invention relates to a blockchain-based domain name resolution system, characterized in that the domain name resolution system adopts a layered structure comprising a top-level domain name chain network, a second-level domain name chain network, a future network node and an existing DNS system network; the top-level domain name chain network links the second-level domain name chain network, the future network node and the existing DNS system network respectively, and the top-level domain name chain network is used for each professional organization to deploy the server nodes having a reliable performance respectively to form a union blockchain network, wherein each node server records the information of all the current top-level domain names, the second-level domain name chain nodes, the future network nodes and the root nodes of the existing DNS system; the second-level domain name chain network is used for the registration and management of domain names, and recording of all the second-level domain names and their subdomain names; the future network node is used for the storage of the metadata and index in the future network. The invention reduces the resolution request, thus effectively improving the efficiency of domain name resolution.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL
Open architecture based domain dependent real time multi-lingual communication service
InactiveUS20090274299A1Natural language translationDigital data processing detailsReal-time webCommunication link
A system and method for real-time network communications provides a session identifier as a public key for group communication between clients, and provides a channel identifier representing a private key for each of a plurality of clients. The channel identifier includes client-specific attributes, which function to indicate grouping criteria for the group communication. A dynamic communication link is created over a network between a client and a service based upon the public and private key combination such that group communication is enabled based upon the attributes of the private key and the public key. Communications are translated using a translation service which employs the attributes associated with the private key and the public key combination to provide response information in a designated language to enable multi-lingual real-time communications.
Owner:IBM CORP
Suggesting concept-based domain names
ActiveUS20090248734A1Improve relationshipKnowledge representationSpecial data processing applicationsDomain nameBase domain
Methods and systems of the present invention allow for displaying suggested concept-based results. An exemplary method may comprise the steps of receiving a domain name, determining from ontological calculations suggested domain names related to the concept of the domain name and displaying the suggested domain names.
Owner:GO DADDY OPERATING
An information security management platform
InactiveCN101056198ADynamic and flexible security managementImplement security task managementData switching networksSecure stateInformation security management
The invention discloses an information safety management platform, which includes: safety base domain, for monitoring the network safety status, generating and sending the safety report to the safety management domain; safety management domain, for receiving the safety report from the safety base domain, and extract the safety information from the safety information domain, according to the analysis for the safety report received from the relevant safety information, acquire the network safety alarm and network safety configuration suggestions; the safety information domain, used for saving the safety information and output to the safety management domain. The invention may realize the automatic management of dynamic network information safety.
Owner:HUAWEI TECH CO LTD
Method for realizing self surrogate function for mobile node
ActiveCN1589060ASafe roamingPrevent eavesdroppingRadio/inductive link selection arrangementsTransmissionEncryption decryptionComputer science
A method for making a mobile nod to realize self agent function is camed out by getting a legal configuration transmit address after panning in the expanding network domain then starting the register rule: certifying to the base domain management entity and informing it the acquired configuration transmit address, getting the ARP agent to the base domain network host to automatically respond the access request of the upper layer protocol stock and determine the path communicated with its host setting up a background service frame to integrate the ciphering and deciphering module and tunnel module and enter into the frame carrying out tunnel packaging and de-packaging operation data, negotiating on dynamic session cipher key and ciphering and de-ciphering user actual transmission data done before dellvery.
Owner:CHINA IWNCOMM
Process-based domain isolation
InactiveUS8910277B1Secure browsing environmentEnvironment safetySpecific access rightsResource allocationBase domainIsolation system
Owner:GOOGLE LLC
Binary coding-based domain name system (DNS) data compression and decompression methods and systems
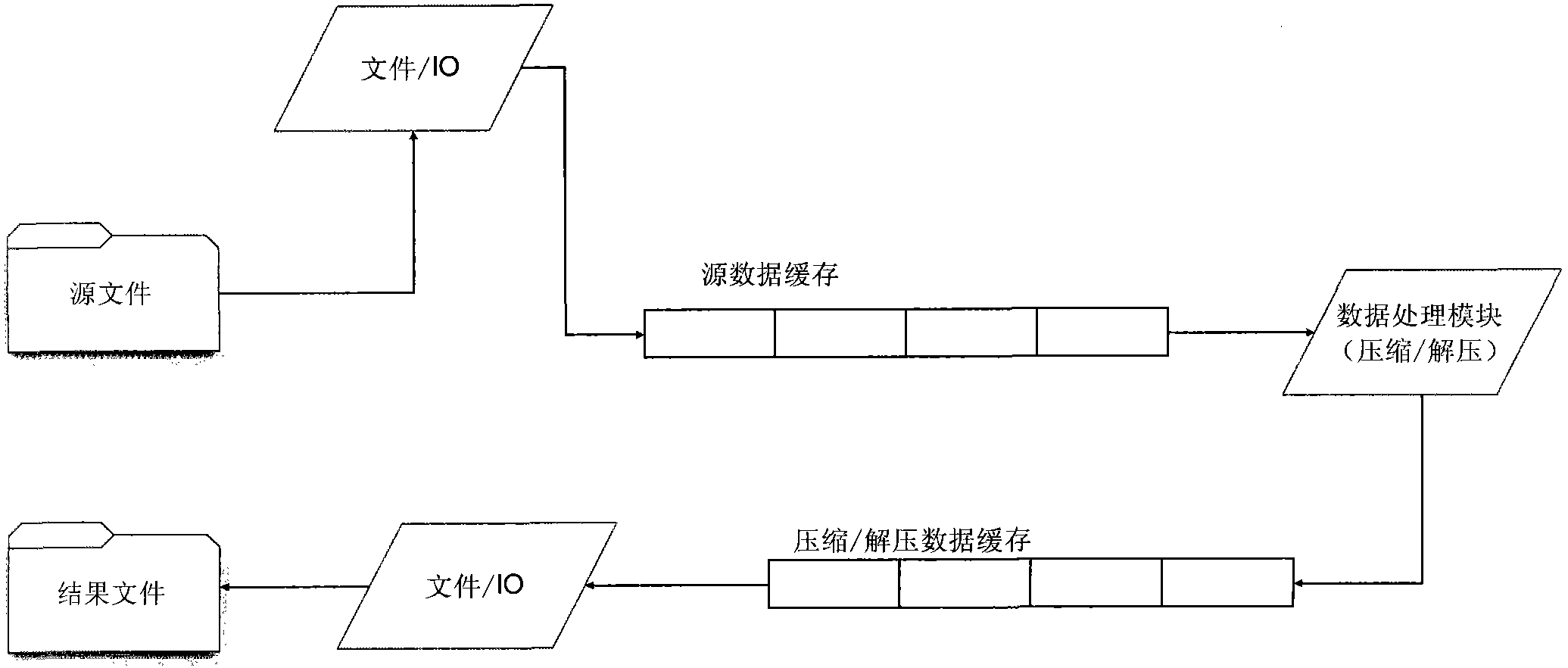
ActiveCN103685589AEfficient designGuaranteed enterprise-level applicationsTransmissionSpecial data processing applicationsData compressionComputer network technology
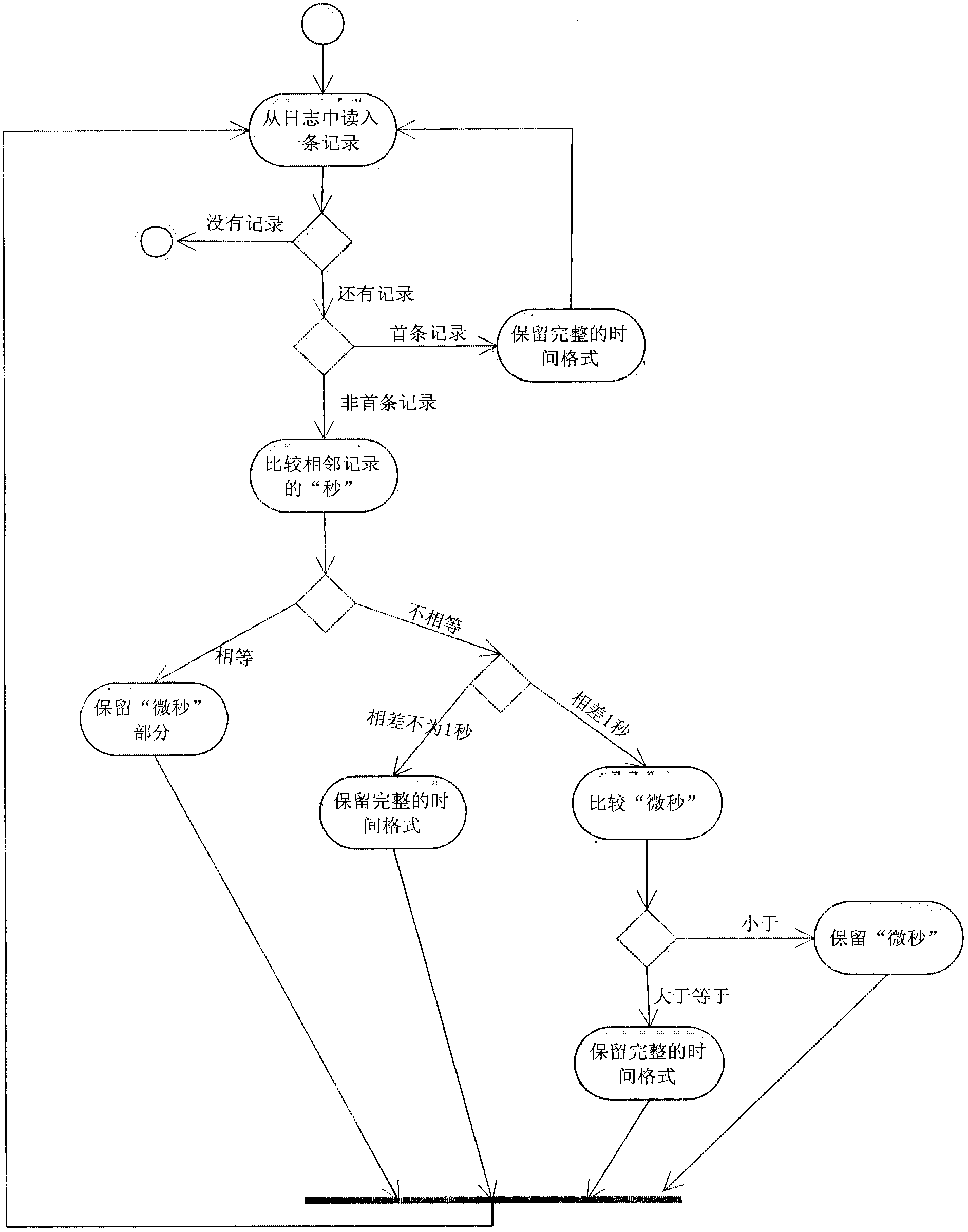
The invention discloses binary coding-based domain name system (DNS) data compression and decompression methods and systems, and belongs to the field of computer network technologies. The DNS data compression method comprises the following steps: 1) reading log information from a data source file, and then packing the data into a cache queue; 2) taking out the data from a data cache queue and compressing the data through a data compression module, and storing into a compression information cache; 3) taking out the data from the compression information cache, carrying out binary encoding, and then storing in a result file. The decompression method comprises the following steps: (1) carrying out binary encoding decompression on binary encoding compression log information in a result file, and then storing in the compression information cache; 2) taking out the data from the cache, and storing into a decompression information cache; 3) taking out the data from the decompression information cache and decompressing to obtain log record information. By adopting the methods, high-ratio compression of the log is achieved, and the compressed file can be further compressed by gzip.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
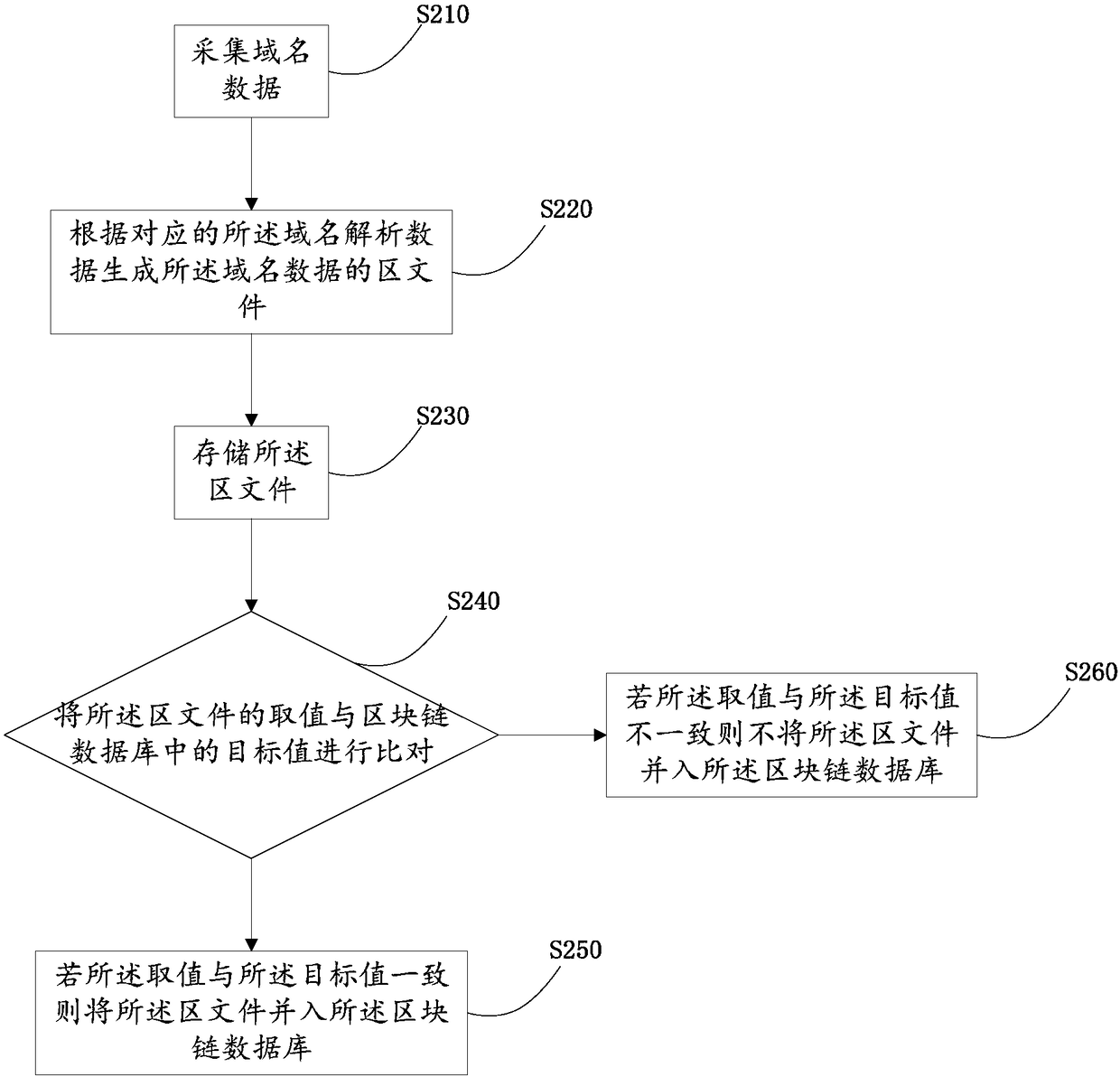
Blockchain-based domain name resolution data management method, system and storage system
InactiveCN108566449APrevent tamperingImprove resistance to attackEncryption apparatus with shift registers/memoriesUser identity/authority verificationDomain nameApproaches of management
The invention relates to the technical field of domain name systems, and discloses a blockchain-based domain name resolution data management method, system and storage system. The management method includes the following steps: collecting domain name data; generating a zone file of domain name resolution data corresponding to the domain name data; storing the zone file; comparing a value of the zone file with a target value in a blockchain database, and if the value is consistent with the target value, merging the zone file into the blockchain database. According to the scheme of the invention, the zone file of the domain name resolution data is generated, the domain name resolution data is stored and managed in the form of a blockchain, so that the domain name resolution data can be prevented from being tampered with, a decentralized domain name resolution data storage system based on a blockchain technology can be realized, and the anti-attack capability of a domain name system can be enhanced.
Owner:GUANGZHOU UNIVERSITY
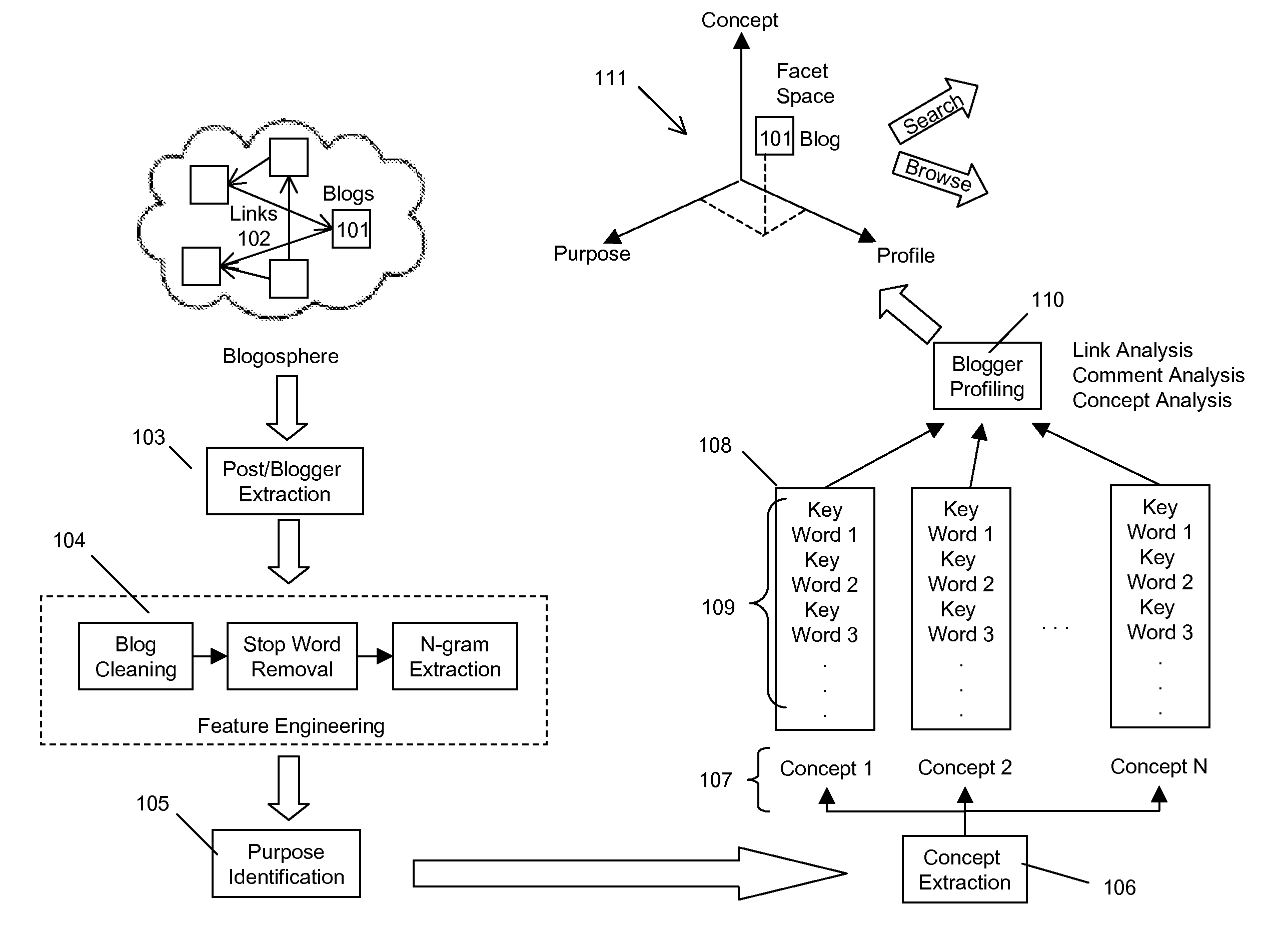
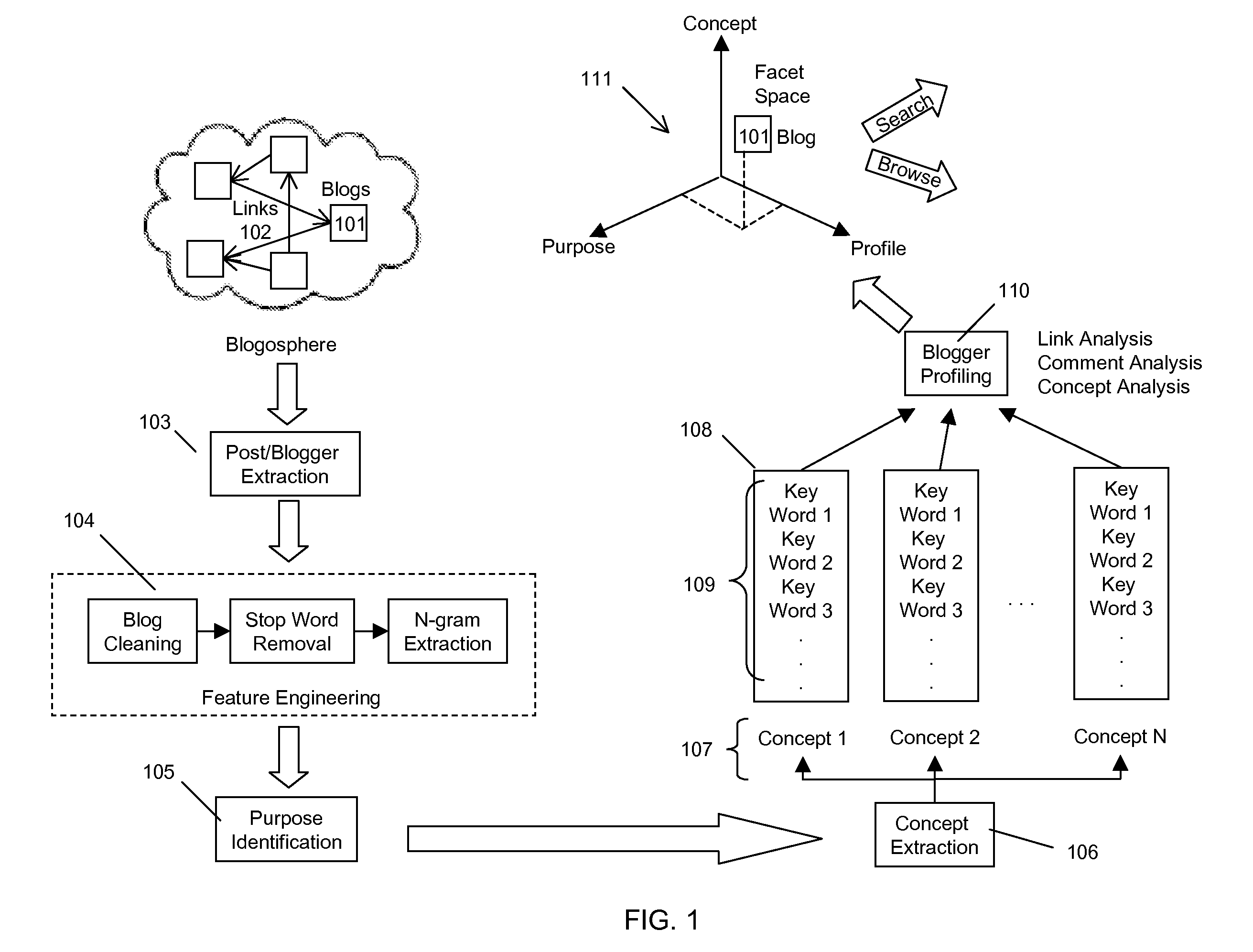
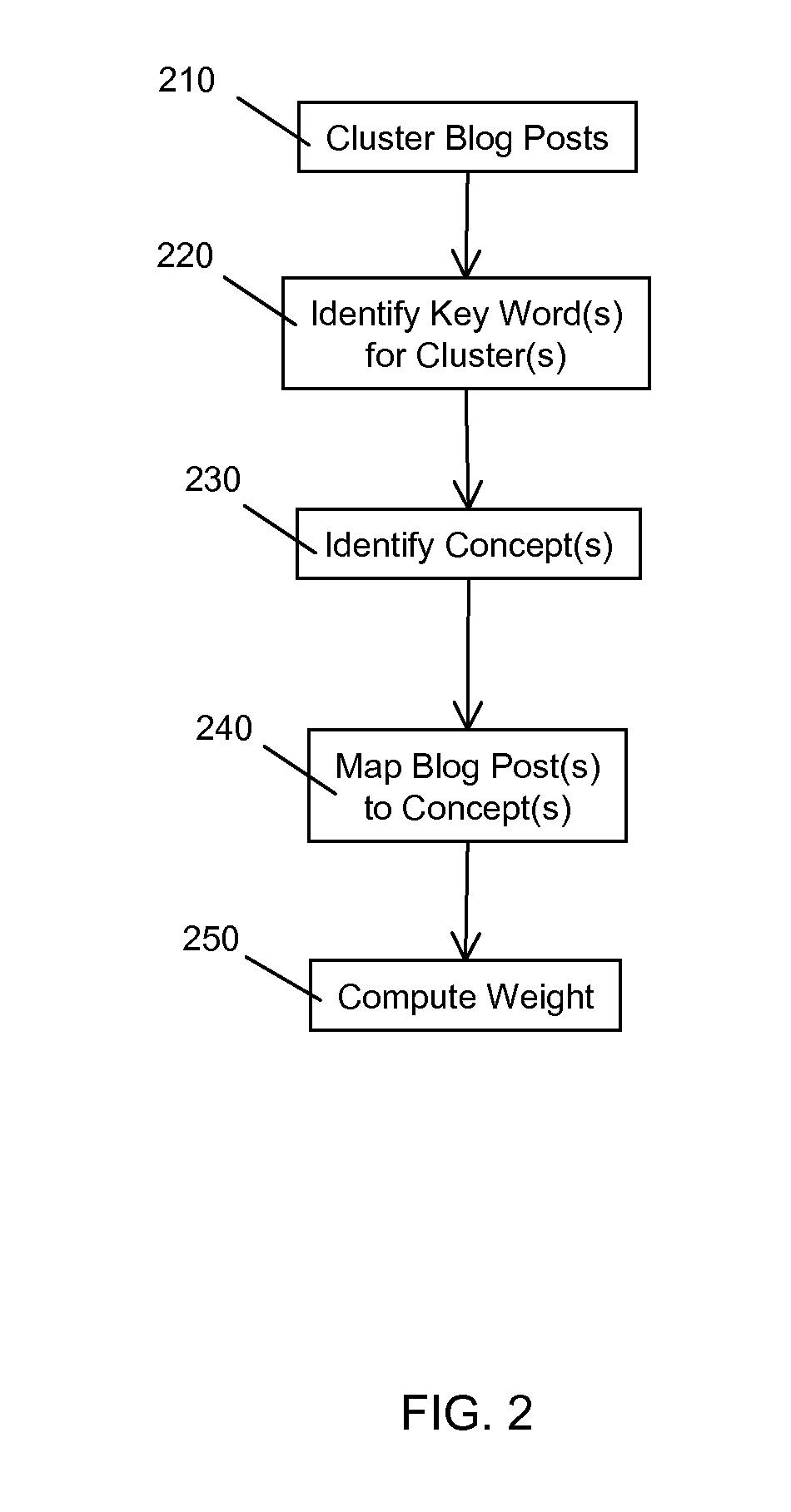
Systems and Methods for Semantics Based Domain Independent Faceted Navigation Over Documents
InactiveUS20110320442A1Easy to analyzeAutomatically determines the weight of the relationshipDigital data processing detailsWebsite content managementSemanticsDocumentation
Systems and associated methods providing a document corpus navigation interface including domain independent facets are described. Embodiments provide a list of domain independent facets, extract facet values from the document corpus, learn the facet values from the corpus, map each document to one of the values of each of the facets, and automatically determine a weight of the relationship.
Owner:IBM CORP
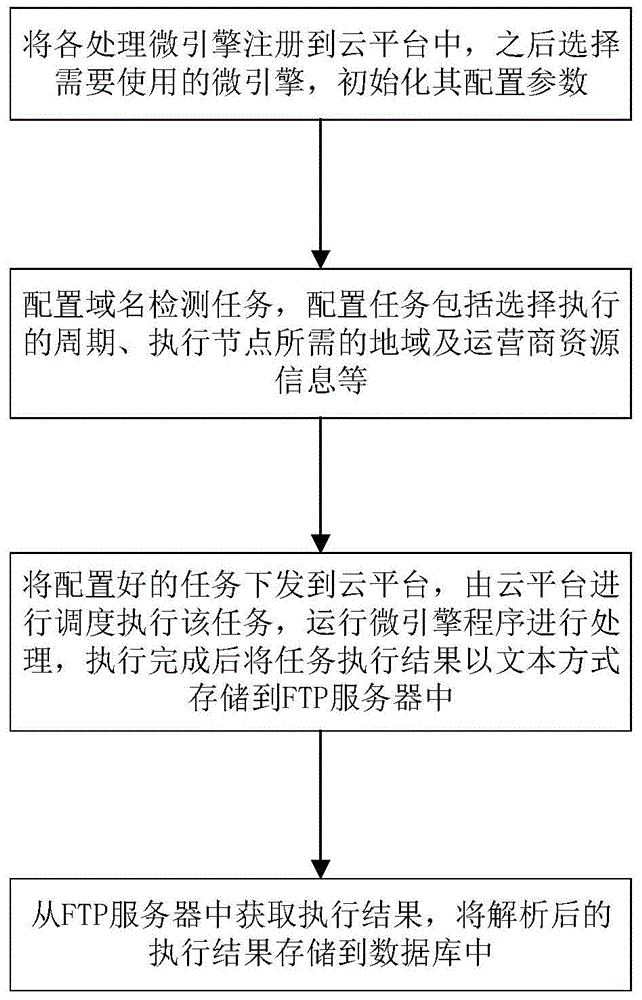
Cloud-platform-based domain name active detecting method and system
The invention provides a cloud-platform-based domain name active detecting method and system. The method includes (1) registering all processing micro engines in a cloud platform and initiating configuration parameters of the micro engines; (2) configuring and generating a domain name detection task and sending the task to the cloud platform; (3) scheduling the domain name detection task to a determined micro engine program and saving a task execution result to a FTP server in a text format after the program is implemented; (4) acquiring an execution result file from the FTP server and saving the analyzed execution result file to a data base. The active detecting system is constructed based on the method. According to the invention, cloud platform resources are employed for active detection of domain name security for operators in different regions and IPv4 segment DNS server determination can be implemented efficiently.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
Image restoration from transformed component data
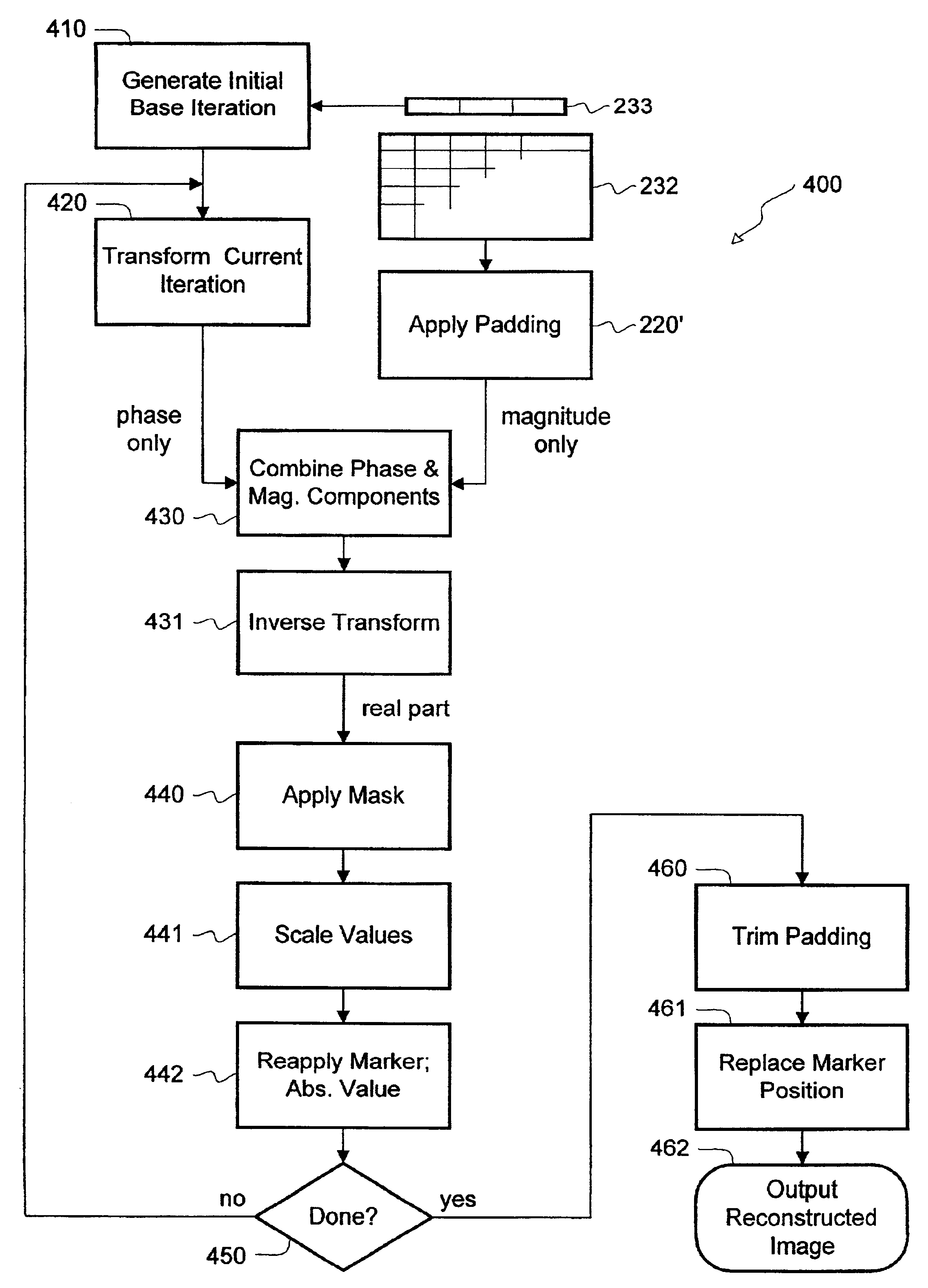
InactiveUS6873744B2Fast convergenceCharacter and pattern recognitionImage codingPattern recognitionImage restoration
An image in a base domain (e.g., spatial) is restored from only one component (e.g., magnitude) of a transform-domain (e.g., Fourier) image by combining this component with a complementary component (e.g., phase) of a transformed previous iteration. Every iteration is converted to the base domain, and predefined known marker and padding data is reapplied to the iteration during every iteration, for convergence purposes. The restored image can be scaled and trimmed, and the marker position interpolated. The original image to be restored is modified to contain the known marker and known padding at known locations. These may be inserted in the base domain or in the transform domain.
Owner:RGT UNIV OF MINNESOTA
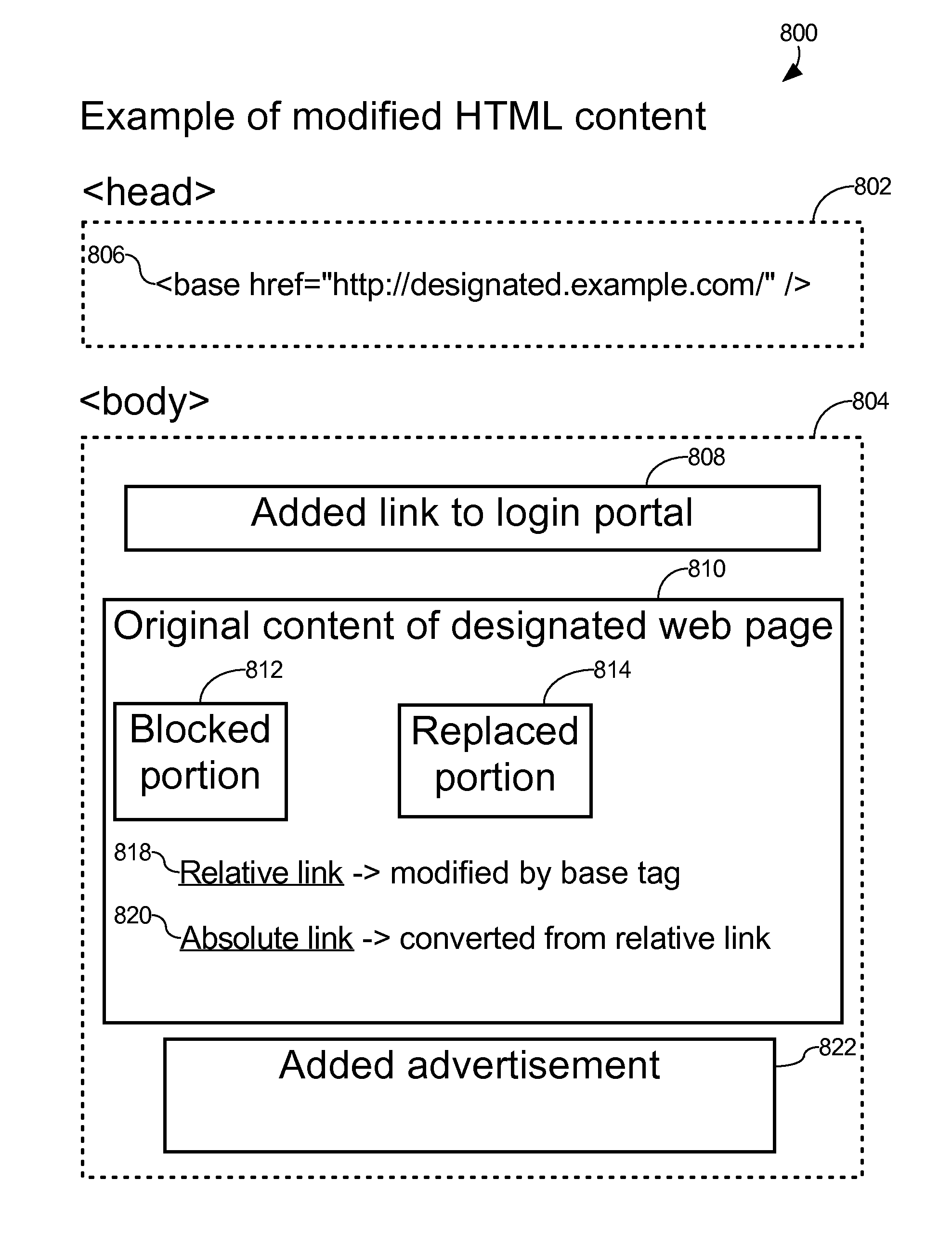
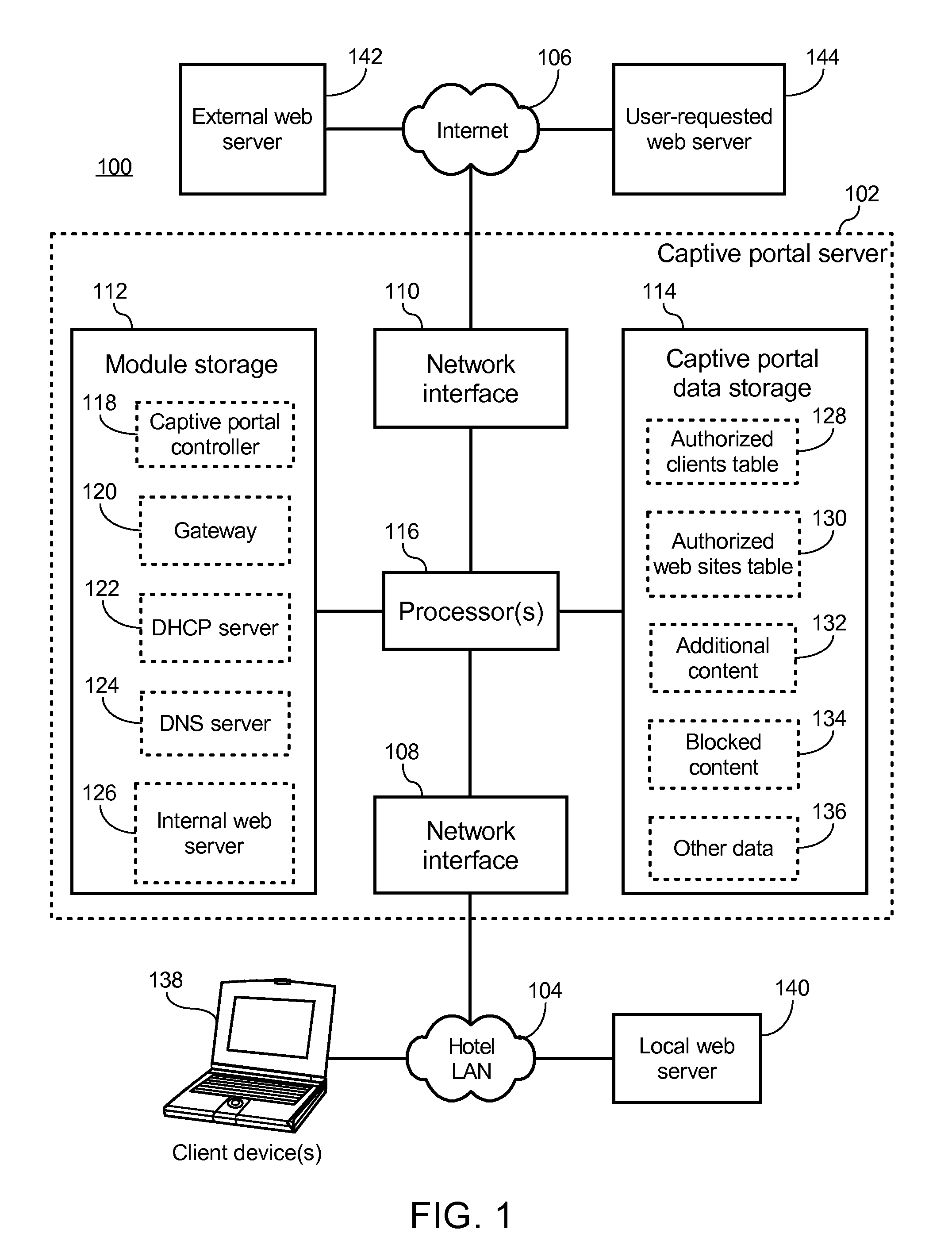
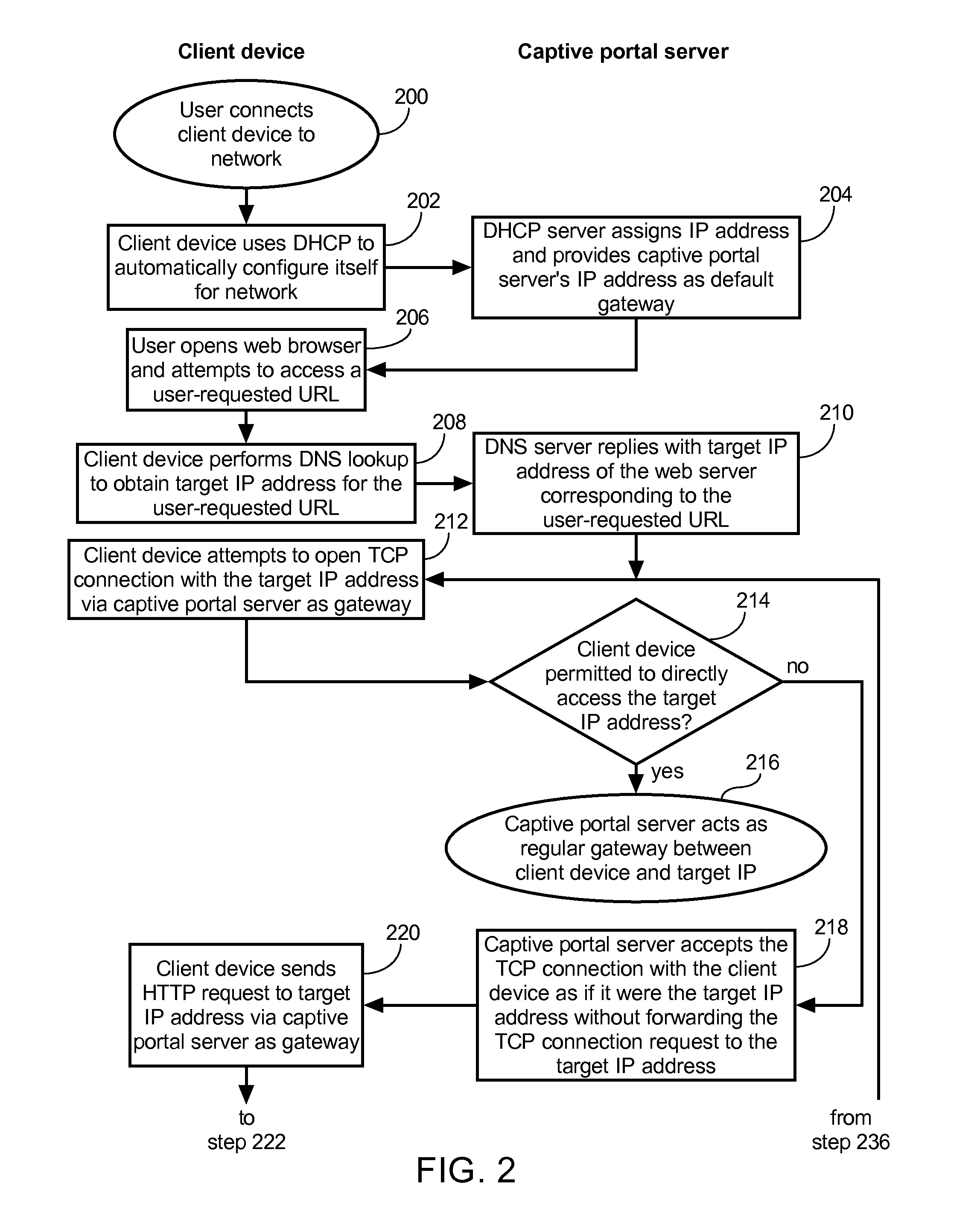
Captive portal that modifies content retrieved from designated web page to specify base domain for relative link and sends to client in response to request from client for unauthorized web page
ActiveUS8650495B2Digital data information retrievalComputer security arrangementsWeb browserWeb service
The described captive portal techniques cause client devices to render and display designated web pages. One designated web page may be different than a requested web page such as when a client is not authorized to access the requested page and is instead caused to display a login portal. The captive portal may modify the designated web page to ensure that relative links lacking base domains now have specified base domains pointing to an authorized web server. The modified content is sent from the captive portal to the client device for display. Client web browser security measures related to redirection messages are thereby bypassed and load on the captive portal is minimal. Another designated web page may be the same as the requested web page such as when the requested page is an authorized page even for non-logged in clients. Authorized pages may be modified to add a login link.
Owner:GUEST TEK INTERACTIVE ENTERTAINMENT
Reservoir simulation with scalable grid computing
ActiveUS20130325419A1SeismologyComputation using non-denominational number representationComputational sciencePerformance computing
Larger, expandable high performance computing (HPC) clusters which are of different generations and performance speeds are provided for reservoir simulation. This provides scalability and flexibility for running computation-intensive reservoir simulation jobs on HPC machines. Availability of larger numbers of processors in a processor pool makes simulation of giant models possible and also reduces fragmentation when multiple jobs are run. A hardware performance based domain decomposition is performed which results in computation load balancing. The reservoir domain is decomposed efficiently to reduce communication overhead. Adaptive detection of the available mix of computation resources is performed, and reservoir simulation decomposition methodology adjusts the distribution of load based on the available hardware and different processor generation resources to minimize the reservoir simulation runtime.
Owner:SAUDI ARABIAN OIL CO
Method and device for controlling access security
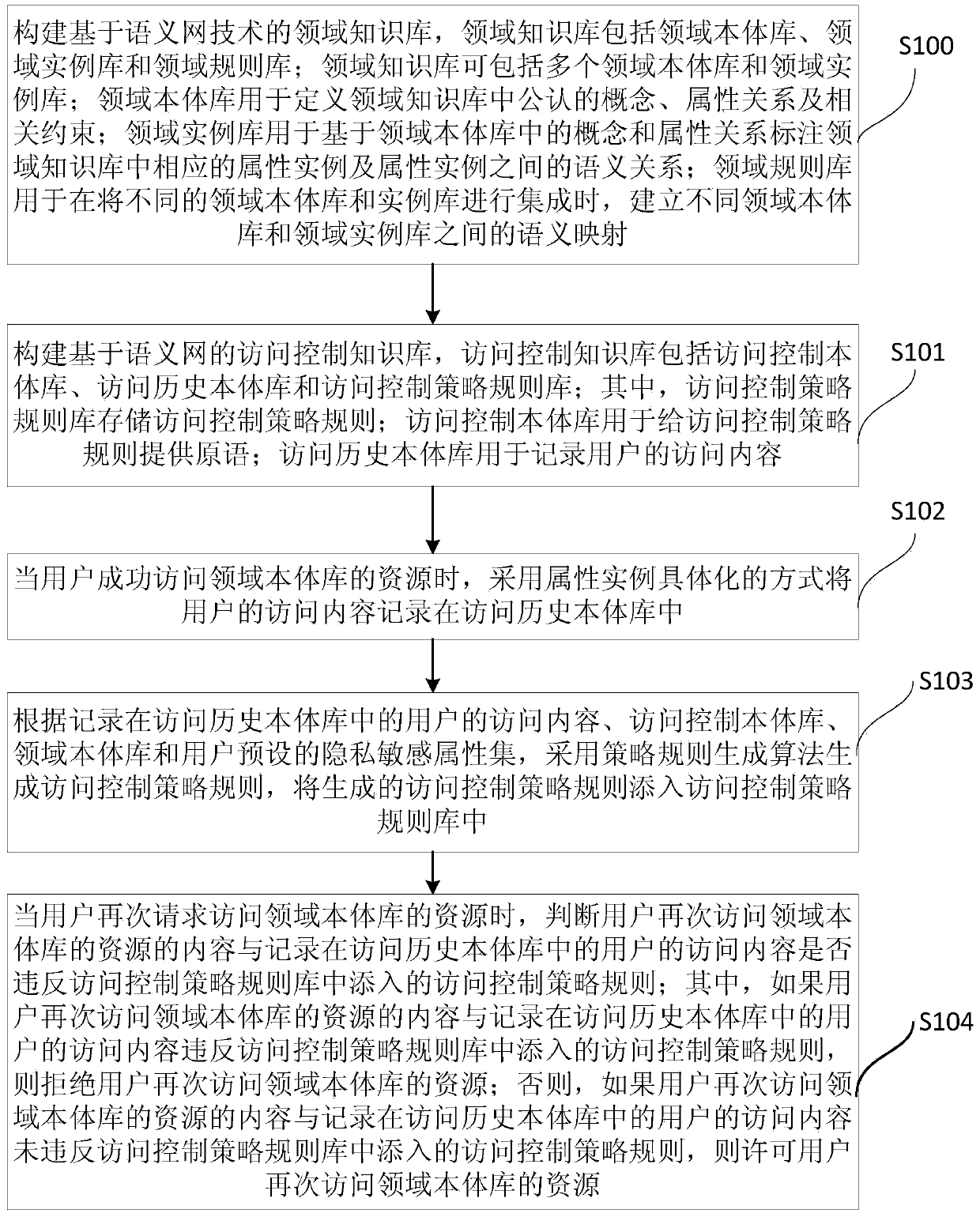
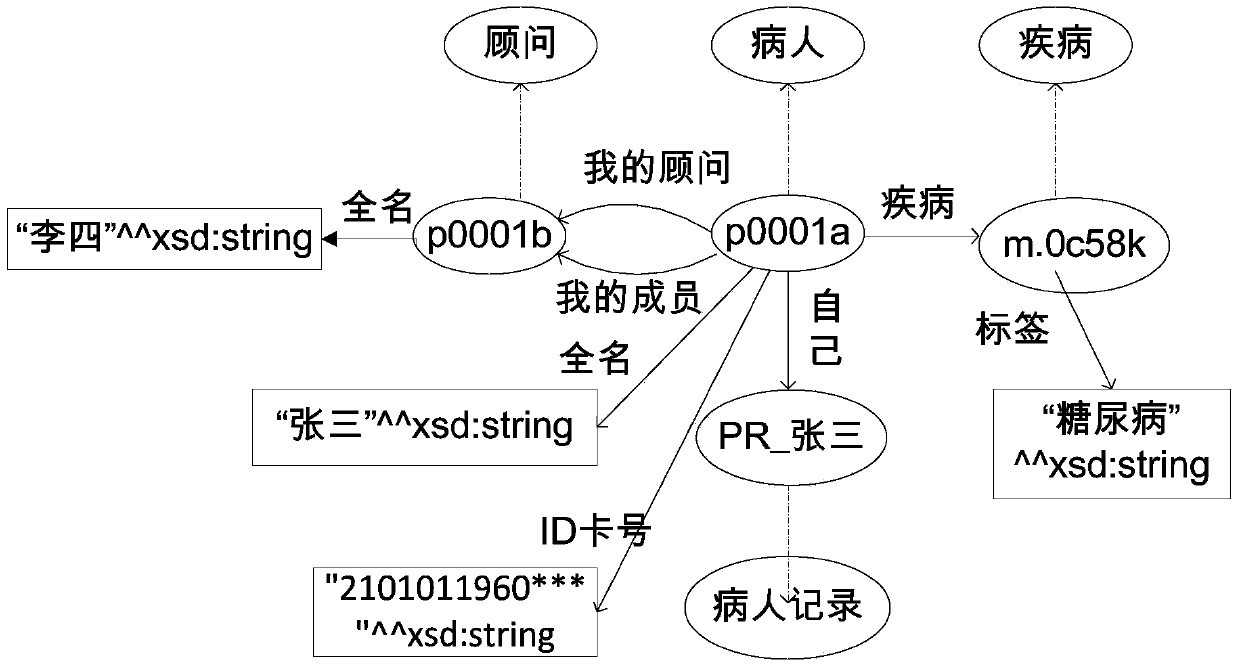
ActiveCN103745161AIncrease flexibilityImprove robustnessDigital data protectionTransmissionAccess historyA domain
The invention provides a method and a device for controlling access security, wherein the method comprises the steps of establishing semantic web technology-based domain knowledge bases (including a domain ontology base, a domain example base and a domain rule base) and access control knowledge bases (including an access control ontology base, an access history ontology base and an access control policy rule base), when a user succeeds in accessing resources in the domain knowledge bases, recording the historical contents accessed by the user by an attribute example embodying method and generating an access control policy rule simultaneously, when the same user requests for accessing to the resources in the domain knowledge bases again, determining whether the access content of the user at the present time and the historical content accessed by the user previously break the made access policy rule, and if breaking the made access policy rule, rejecting the access request of the user at the present time, otherwise, allowing the access request of the user at the present time. The method and the device can be used for solving the security and privacy disclosure problems caused by context linkage between the contents accessed a plurality of times by the same user.
Owner:NEUSOFT CORP
Method, system and gateway device for enabling interworking between IP and CS networks
InactiveUS7898990B2Improve abilitiesMultiplex system selection arrangementsSpecial service provision for substationCircuit switchingBase domain
A method, system and gateway device enables interworking between an IP-based network and a circuit-switched network. A first address information of a first connection end located in the circuit-switched network is routed in a trigger message from the IP-based network to a gateway control function. The first and second call legs are established in parallel towards the first connection end based on the first address information, and towards a second connection end located in the IP-based network based on a second address information obtained from the trigger message. A single connection between the two connection ends is then established by connecting the first and second call legs. Thereby, IP-based signaling functionality can be used to add capability for subscribers located in the CS domain to be invited into conferences or calls with subscribers located in an IP-based domain, e.g. the IMS domain.
Owner:INTELLECTUAL VENTURES I LLC
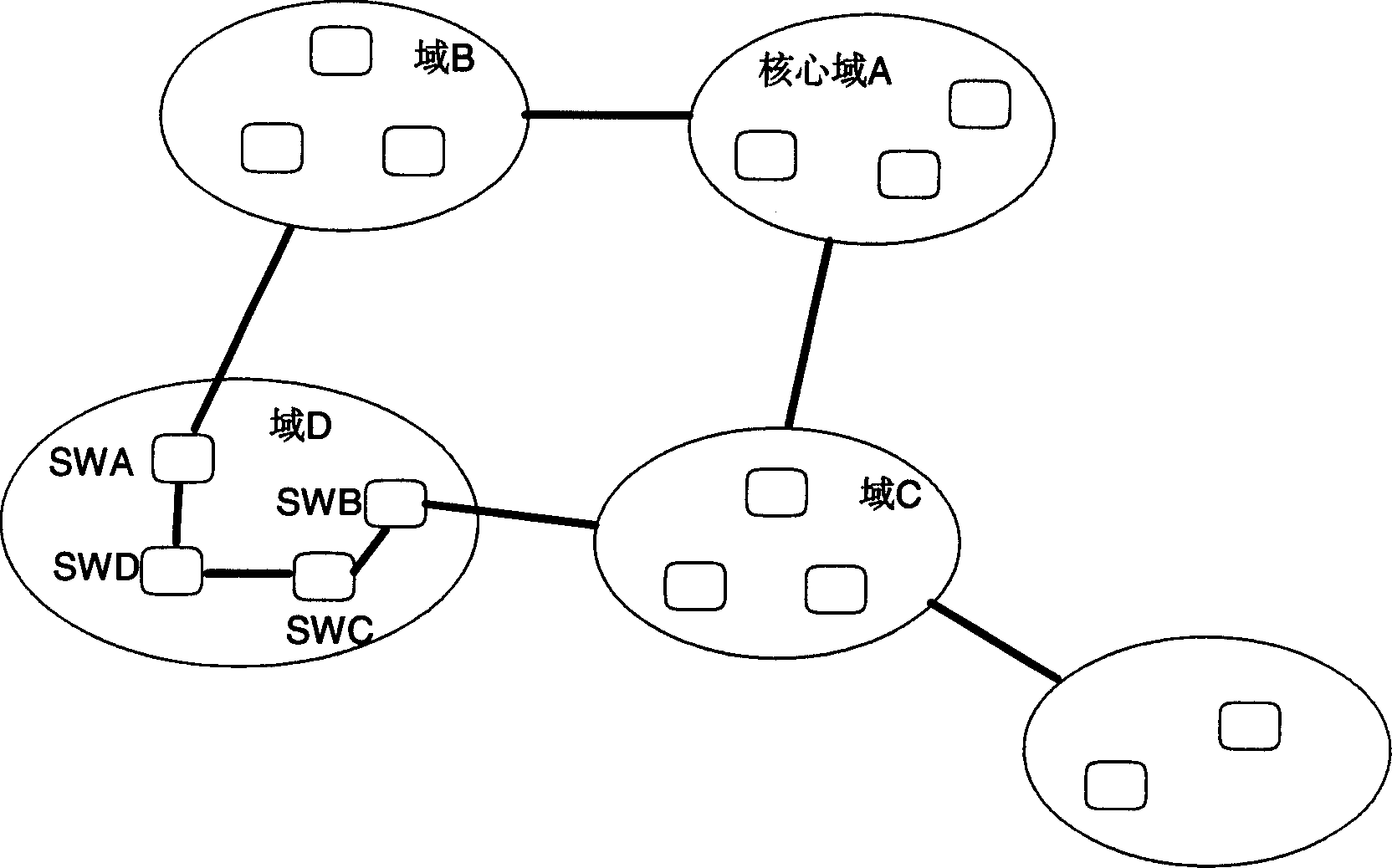
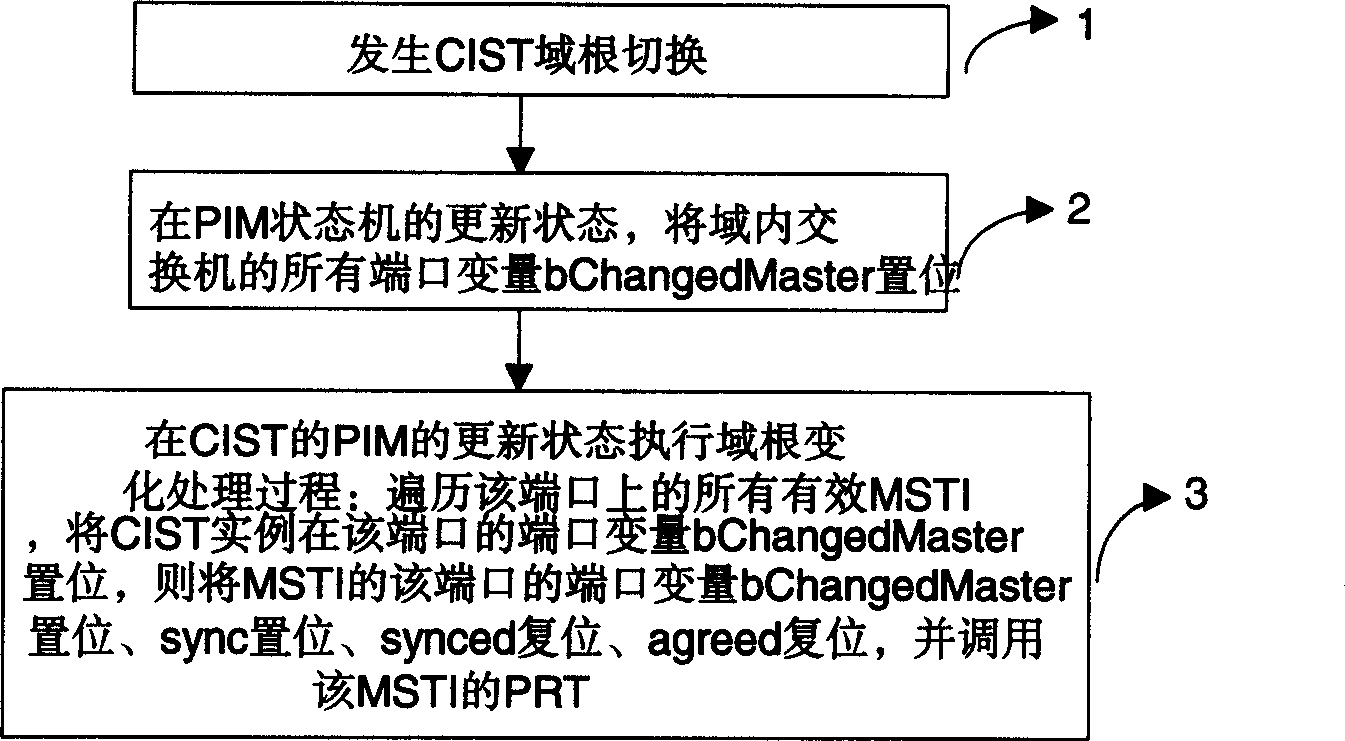
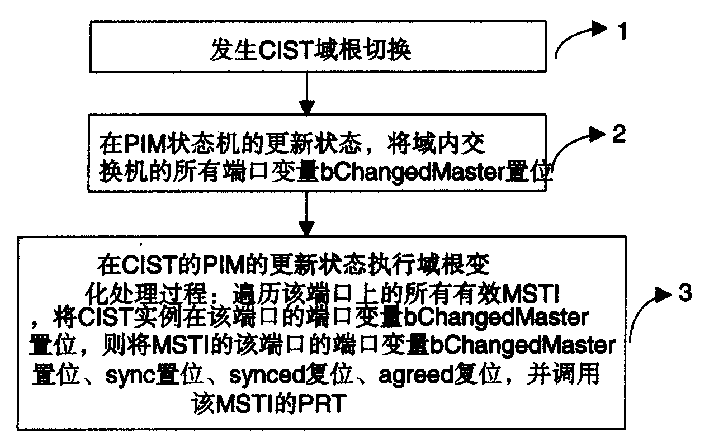
Multiple generation tree protocol based domain roots switching method
InactiveCN1510873AAvoid formingGuaranteed to understandData switching by path configurationComing outComputer science
An implement method for domain root switching based on Multiple Spanning Tree Protocol (MSTP), this method is: when taking CIST domain to switch, after the precedence information of each port in the exchanger renews by PIM, trigger the switching procedure of handling CIST domain root corresponding to MSTI, to ensure each of MSTI in MST domain knows the information about CIST domain root switching. This method can avoid MSTI comes out temporary loop circuit due to CIST domain root changing.
Owner:HUAWEI TECH CO LTD
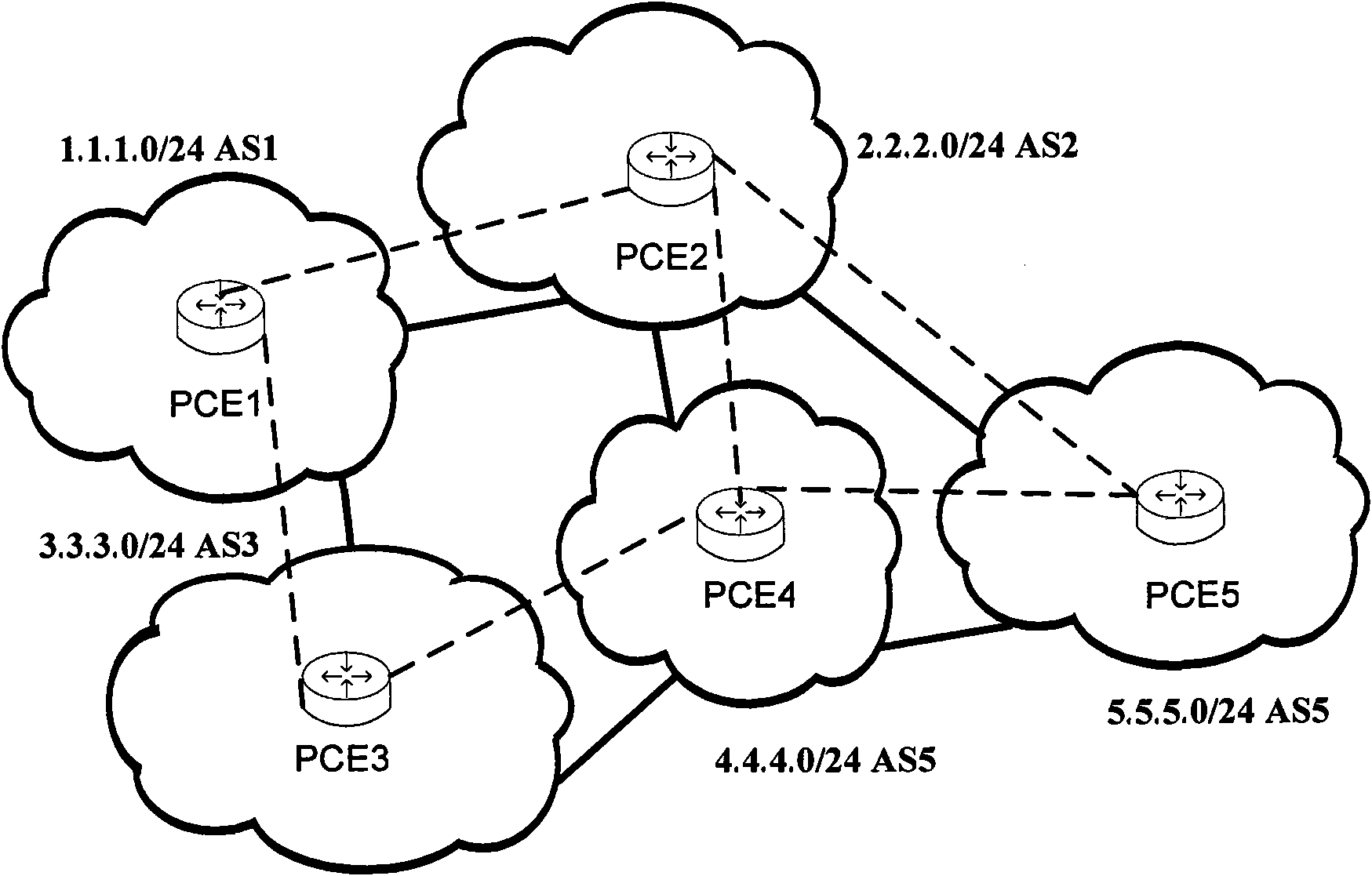
Domain routing information generation method and device, path computation method and device
The invention discloses a path computation element-based domain routing information generation method, a path computation element-based domain routing information generation device, a path computation element-based path computation method and a path computation element-based path computation device. The domain routing information generation method comprises the following steps of: mutually noticing a route updating message between route computation elements and directly forwarding the received route updating message for a path computation element without cross-domain computation capacity; adding a domain identifier of a domain where the to-be-forwarded route updating message is positioned into the to-be-forwarded route updating message and continuously forwarding the message for the path computation element with the cross-domain computation capacity; wherein all domain identifiers added into the route updating message in the entire forwarding process form a domain sequence under a routing prefix; and generating domain routing information by each path computation element according to the received route updating message, wherein the domain routing information indicates at least one domain sequence under each routing prefix. The methods and the devices are suitable for a boarder gateway protocol (BGP) protocol network, networks which do not use the BGP protocol and expand situational application of path computation.
Owner:ZTE CORP
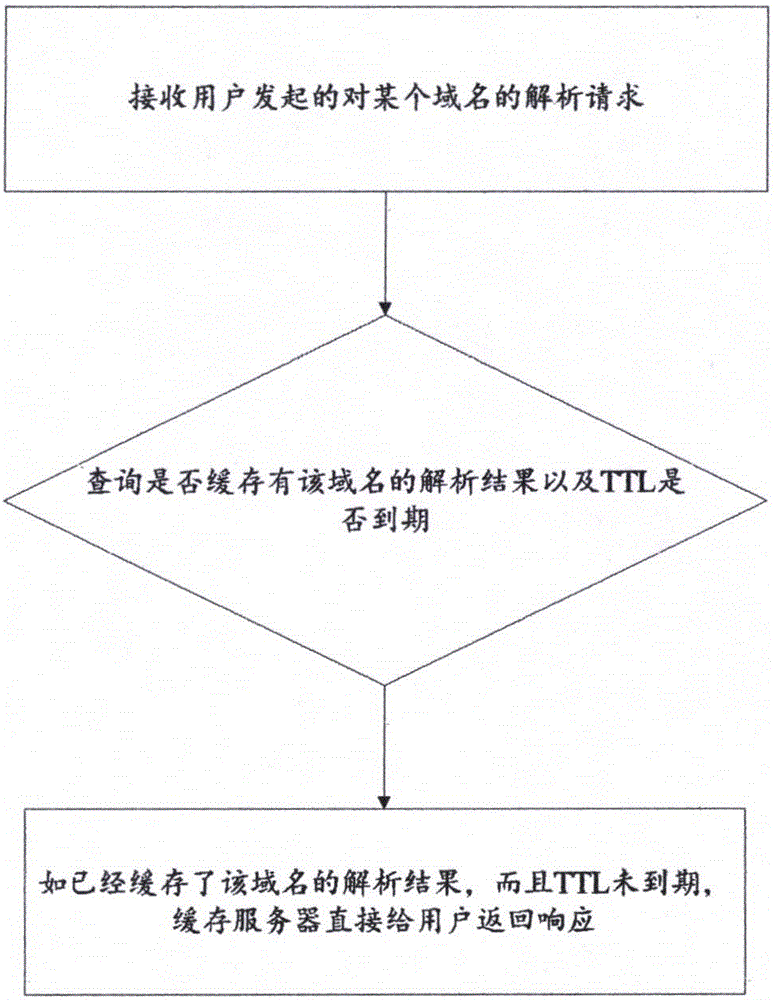
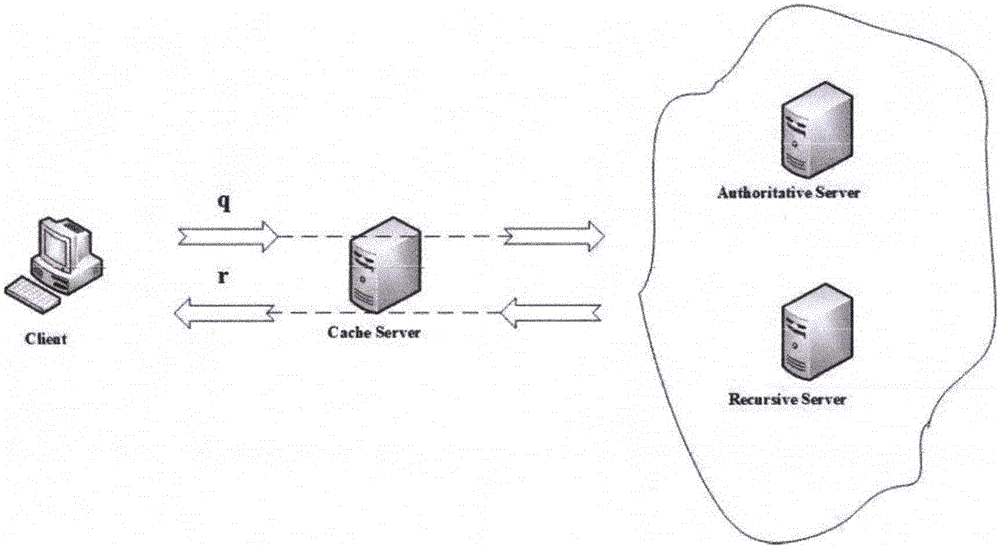
Domain name server (DNS) cache camping-based domain name resolution method and system
The present invention discloses a domain name server (DNS) cache camping-based domain name resolution method and system. The method comprises the steps of receiving a user-initiated request to resolve a domain name; inquiring whether a resolution result of the domain name is cached in a cache server and whether an TTL is expired; and if the resolution result of the domain name is cached in the cache server and the TTL is not expired, directly returning, by the cache server, a response to the user. According to the method, DNS cache based on the cache server improves the resolution speed; further, when an authoritative server or a recursive server resolves abnormally, the cache server makes the cache resided and waits to update a domain name record until the authoritative server or the recursive server resolves normally, so that the technical effect is better.
Owner:BEIJING RUNSTONE TECH
Generative adversarial learning network-based domain learning method
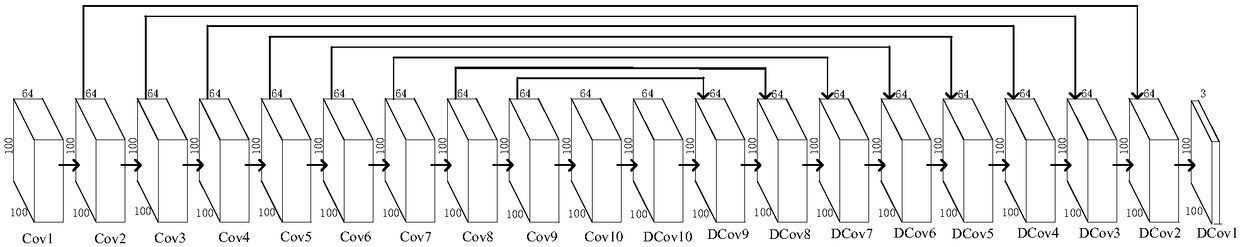
ActiveCN108710896ALow costHigh similarityCharacter and pattern recognitionFace detectionImage resolution
The invention discloses a generative adversarial learning network-based domain learning method. The method comprises the following steps of 1) collecting a human face image set of a source domain, positioning human face positions by using a human face detector and extracting human face images; 2) constructing a generative neural network G, wherein input and output are the human face images with the same resolution, the input is the collected specific application scene human face image, and the output is the converted image; 3) constructing a classification neural network D, and applying neurons of a convolutional neural network, wherein the input is an output image of the generative neural network and a training image of a human face classifier, and the output is classification of two types of input images; 4) iteratively training the generative neural network G and the classification neural network D in an asynchronous mode; 5) when the human face recognition is carried out in a specified scene, performing conversion G(I) on the input human face image I, and inputting the converted human face image into a human face recognition module to obtain a human face recognition result. Themethod is relatively high in adaptability to a universal human face recognizer and relatively low in data cost.
Owner:ZHEJIANG UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com