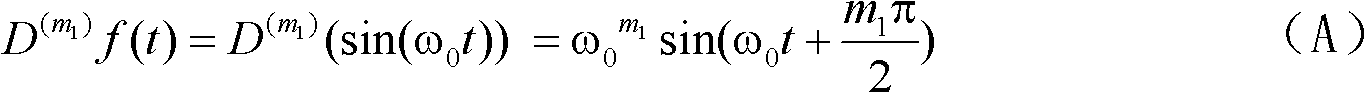Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
326results about How to "Improve resistance to attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
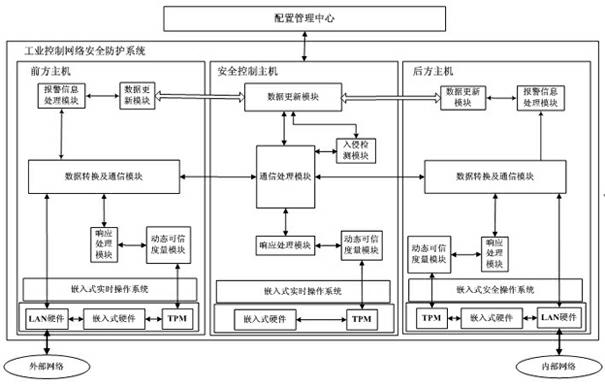
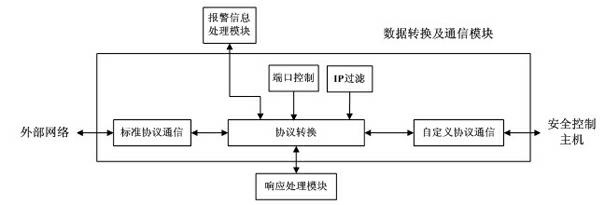
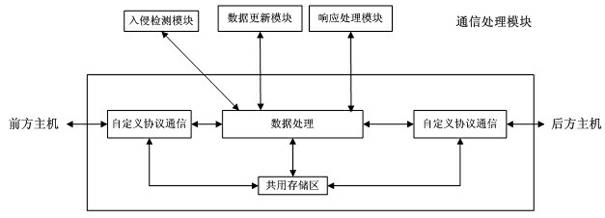
Industrial control network security protection method and system
InactiveCN102438026AImprove resistance to attackImprove securityUser identity/authority verificationData switching networksSystem transformationNetwork attack
The invention discloses an industrial control network security protection method and an industrial control network security protection system. The method comprises the following steps that: aiming at an external network attack, a front host performs first layer data filter and access control on external network data; a security control host caches data through a common storage region, performs intrusion detection on the data, timely alarms illegal data and informs hosts on two sides; a rear host performs deep filter and access control on the data and causes the legal data to enter an internal network; aiming at an internal network attack, the rear host performs the first data filter and access control on internal network data; the security control host caches the data through the common storage region, performs the intrusion detection on the data, timely alarms the illegal data and informs the hosts on the two sides; and the front host performs the deep filter and access control on the data and causes the legal data to enter an external network. By the method and the system, the network security level of an industrial control system is increased, and the cost on investment, system transformation and management is reduced.
Owner:AUTOMATION RES & DESIGN INST OF METALLURGICAL IND
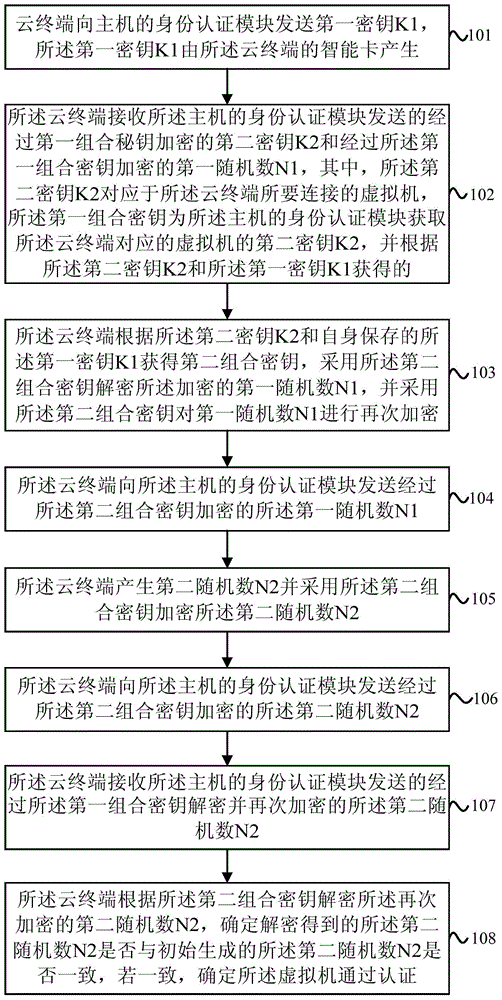
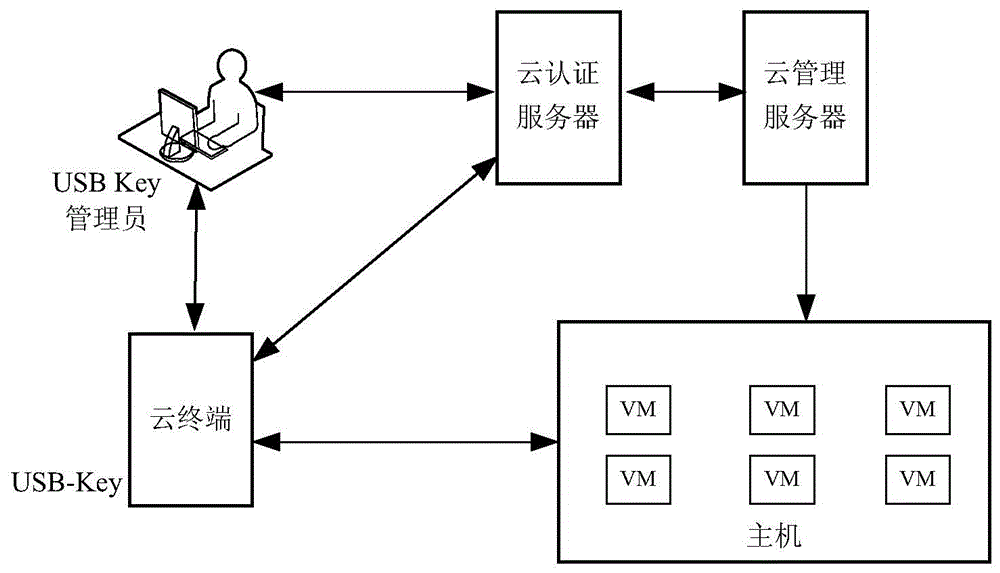
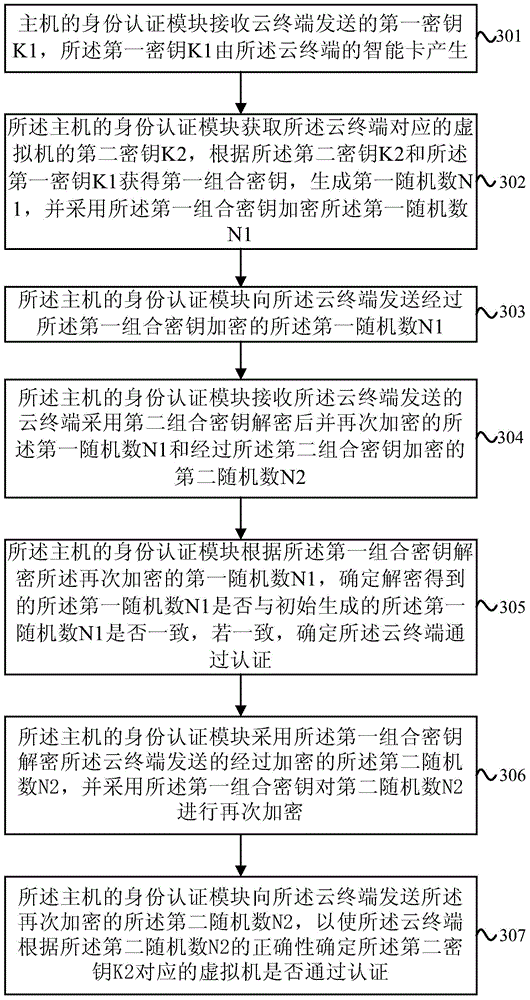
Method, equipment and system for authenticating identities
ActiveCN104639516AImprove resistance to attackImprove securityUser identity/authority verificationComputer scienceVirtual machine
An embodiment of the invention provides a method, equipment and a system for authenticating identities. The method includes enabling a cloud terminal to transmit first secret key K1 to a host; enabling the host to acquire second secret keys K2 corresponding to virtual machines, acquiring first combined secret keys according to the secret keys K2 and the secret keys K1, generating first random numbers N1, encrypting the first random numbers N1 by the aid of the first combined secret keys and then transmitting the encrypted first random numbers N1 to the cloud terminal; enabling the cloud terminal to acquire second combined secret keys according to the secret keys K2 transmitted by the host and the secret keys K1 stored in the cloud terminal, decrypting the first random numbers N1 by the aid of the second combined secret keys, then encrypting the first random numbers N1 again, generating second random numbers N2, encrypting the second random numbers N2 by the aid of the second combined secret keys and transmitting the second random numbers N2 and the first random numbers N1 to the host; enabling the host to decrypt the first random numbers N1 by the aid of the first combined secret keys, and determining whether the cloud terminal is successfully authenticated or not according to the correctness of the first random numbers N1; enabling the host to decrypt the second random numbers N2 by the aid of the first combined secret keys again, decrypting the second random numbers N2 again and then transmitting the second random numbers N2 to the cloud terminal; enabling the cloud terminal to decrypt the second random numbers N2 by the aid of the second combined secret keys and determining whether the virtual machines are successfully authenticated or not according to the correctness of the second random numbers N2.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
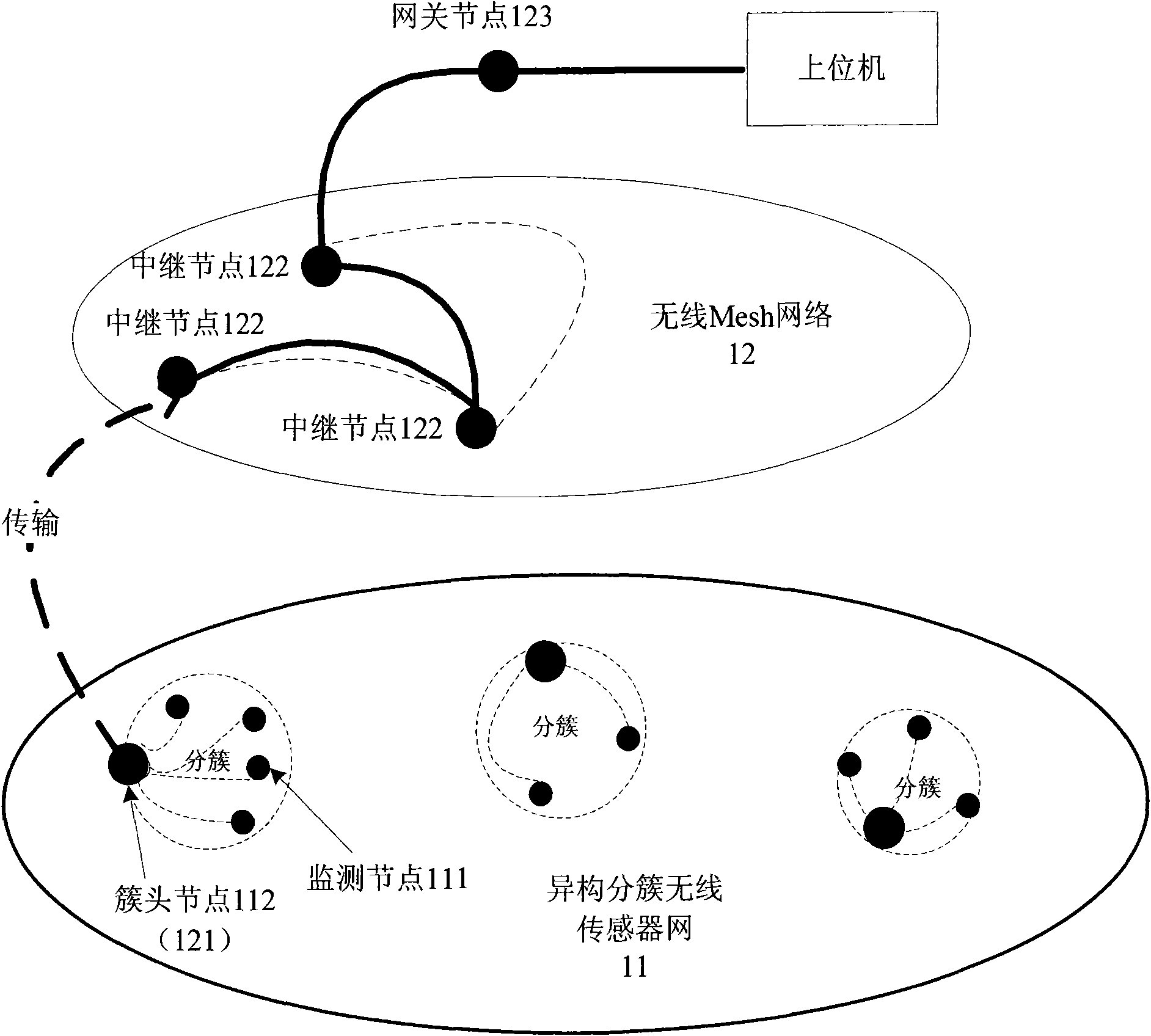
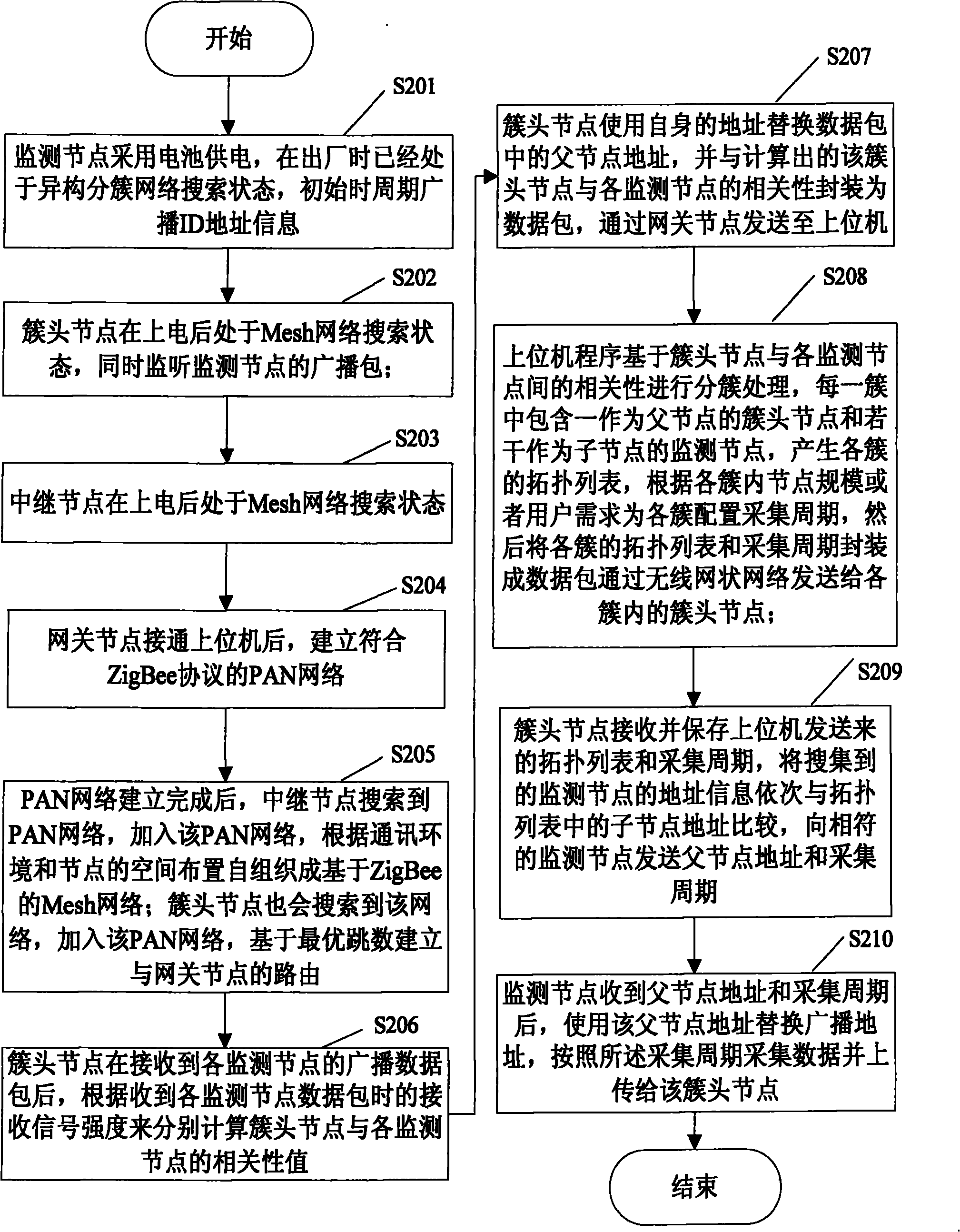
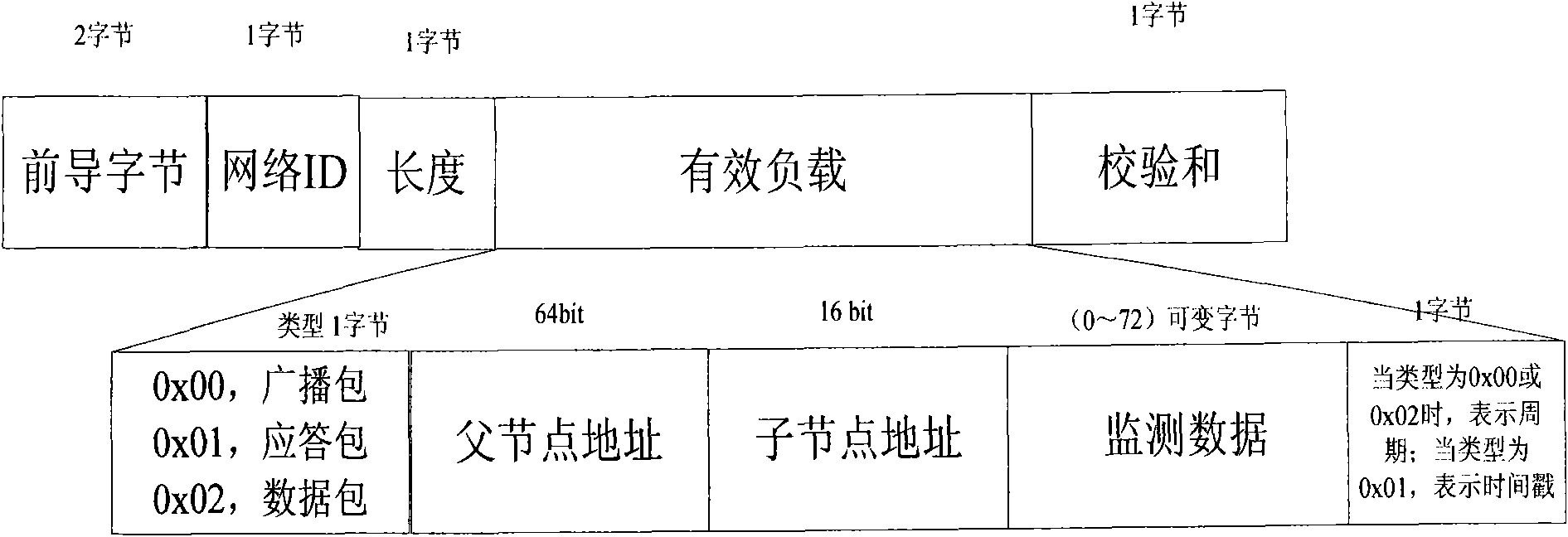
Method and system for fusion of multi-source monitoring data based on heterogeneous clustering wireless sensor network
ActiveCN101902772AFacilitate communicationEasy to deployNetwork topologiesMobile wireless sensor networkBroadcast packet
Owner:BEIJING LOIT TECH
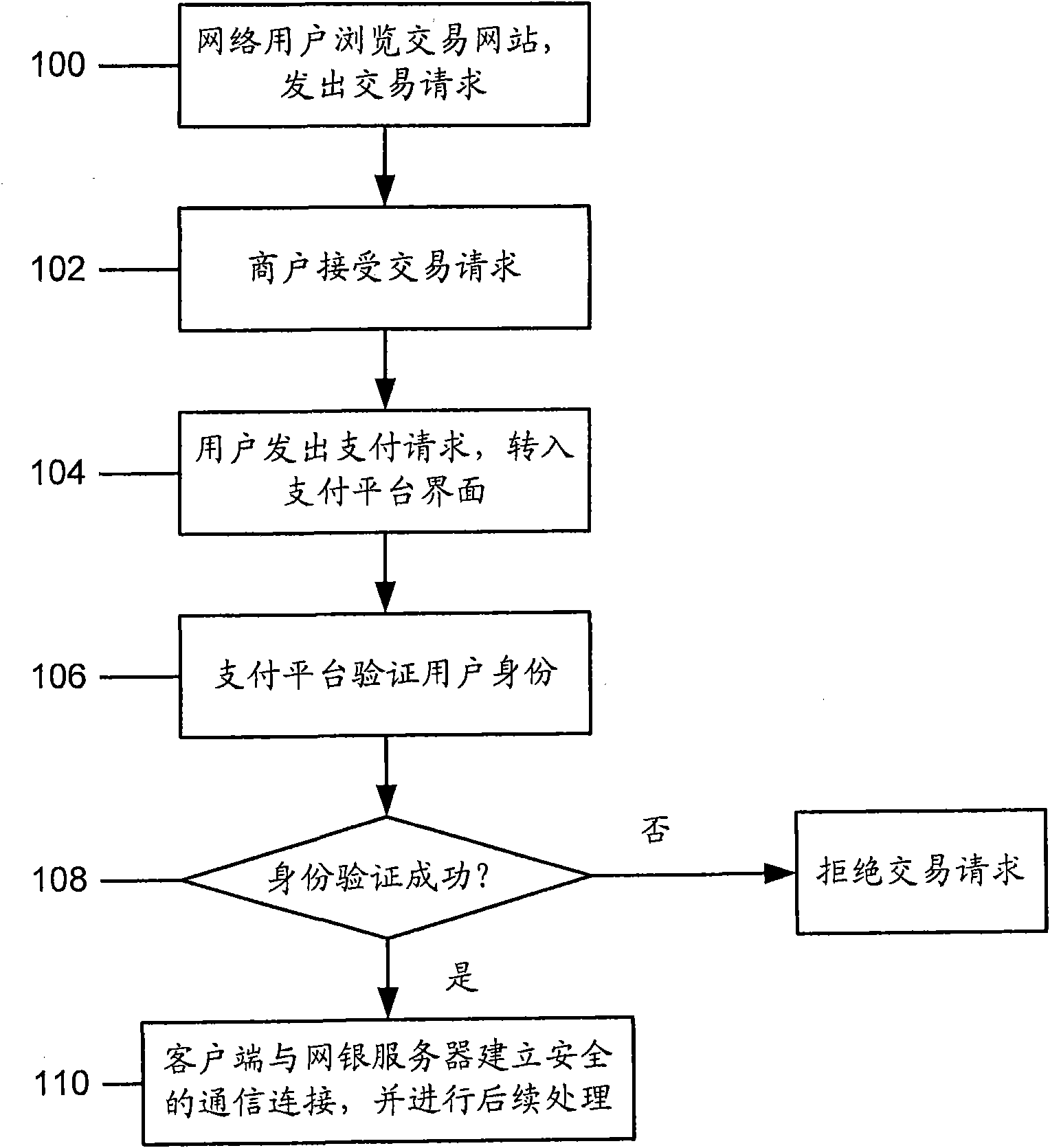
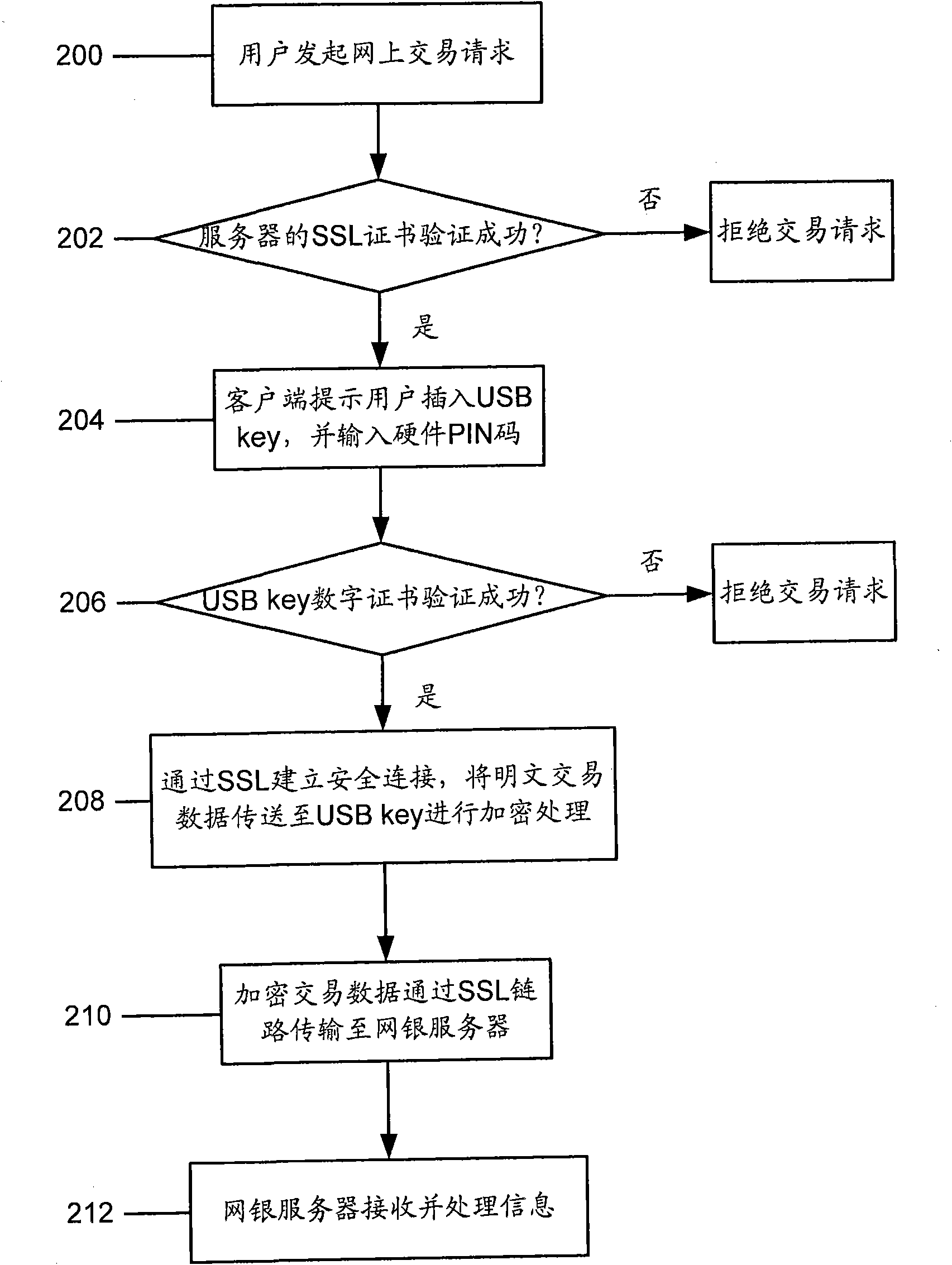
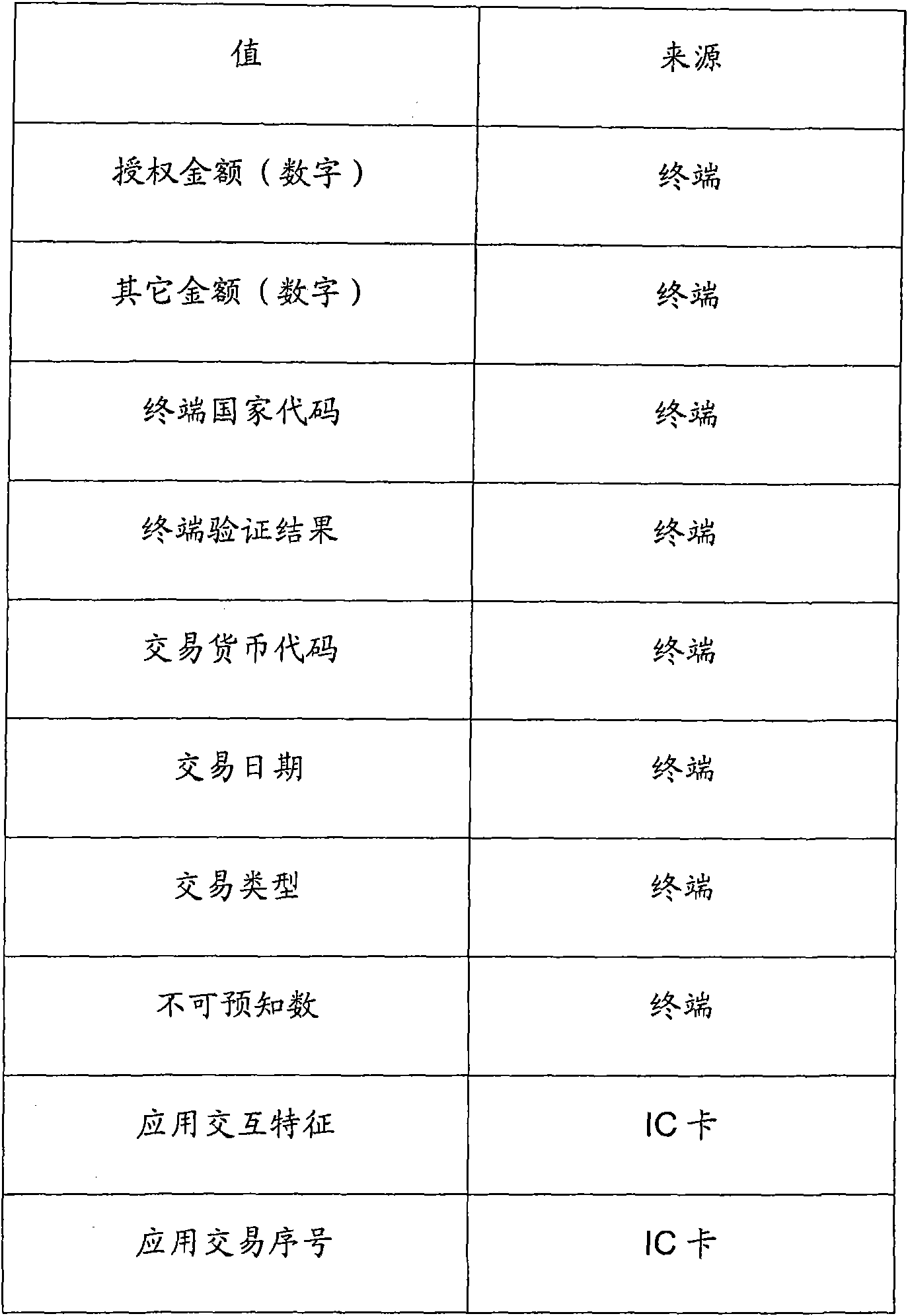
Multiple-factor authentication method for online payment and authentication system
InactiveCN101770619AEnsure safetyImprove resistance to attackPayment architectureTransmissionPlaintextCommunications security
The invention discloses a multiple-factor authentication method; wherein an authentication USB key digital certificate comprises a client side and a server two-way verification digital certificate; the USB key is inserted and hardware PIN code is input, transaction data information is transferred to the USB key to carry out encryption processing; the transaction ciphertext of an authentication bank IC card comprises the following steps: part source data is input; ARQC is generated by the bank IC card and is transferred to the server for verification; the ARQC is decrypted by the server; the contents of first cleartest transaction data and second cleartest transaction data are compared and authorized transaction can be carried out under the condition that the first cleartest transaction data and second cleartest transaction data are completely consistent. The invention further discloses a multiple-factor authentication system, comprising a device for authenticating the USB key digital certificate, a device for authenticating the transaction ciphertext of the authentication bank IC card, a comparison unit for comparing the first cleartest transaction data and second cleartest transaction data, and an authorization unit; in the authentication method and the system, communication safety between the client side and the server can be not only ensured, and the transaction data source safety can be ensured.
Owner:CHINA UNIONPAY
DCT domain video watermark treatment method based on texture features
InactiveCN101662686AImprove resistance to attackImprove robustnessTelevision systemsDigital video signal modificationPattern recognitionAc coefficient
The invention relates to a video watermark treatment method, in particular to a DCT domain video watermark treatment method based on texture features, which belongs to technologies of information safety. The method comprises the steps of scrambling a watermark; calculating the brightness sum of a video image according to the color value of RGB of the video image, sequencing the brightness sum, selecting a frame for embedding, determining the middle position and the lower position of AC coefficients for embedding the watermark after the scrambling into the video image according to the texture distribution of the video image, carrying out distortion compensation on the video image with the embedded watermark by introducing motion compensation, reducing the video distortion caused during thewatermark embedding, and extracting and detecting the video image with the embedded watermark by utilizing the correlation of the watermark. The method has the advantages of good invisibility, stronganti-attack ability, good safety and real-time property and large capacity of embedded information.
Owner:WUXI CINSEC INFORMATION TECH
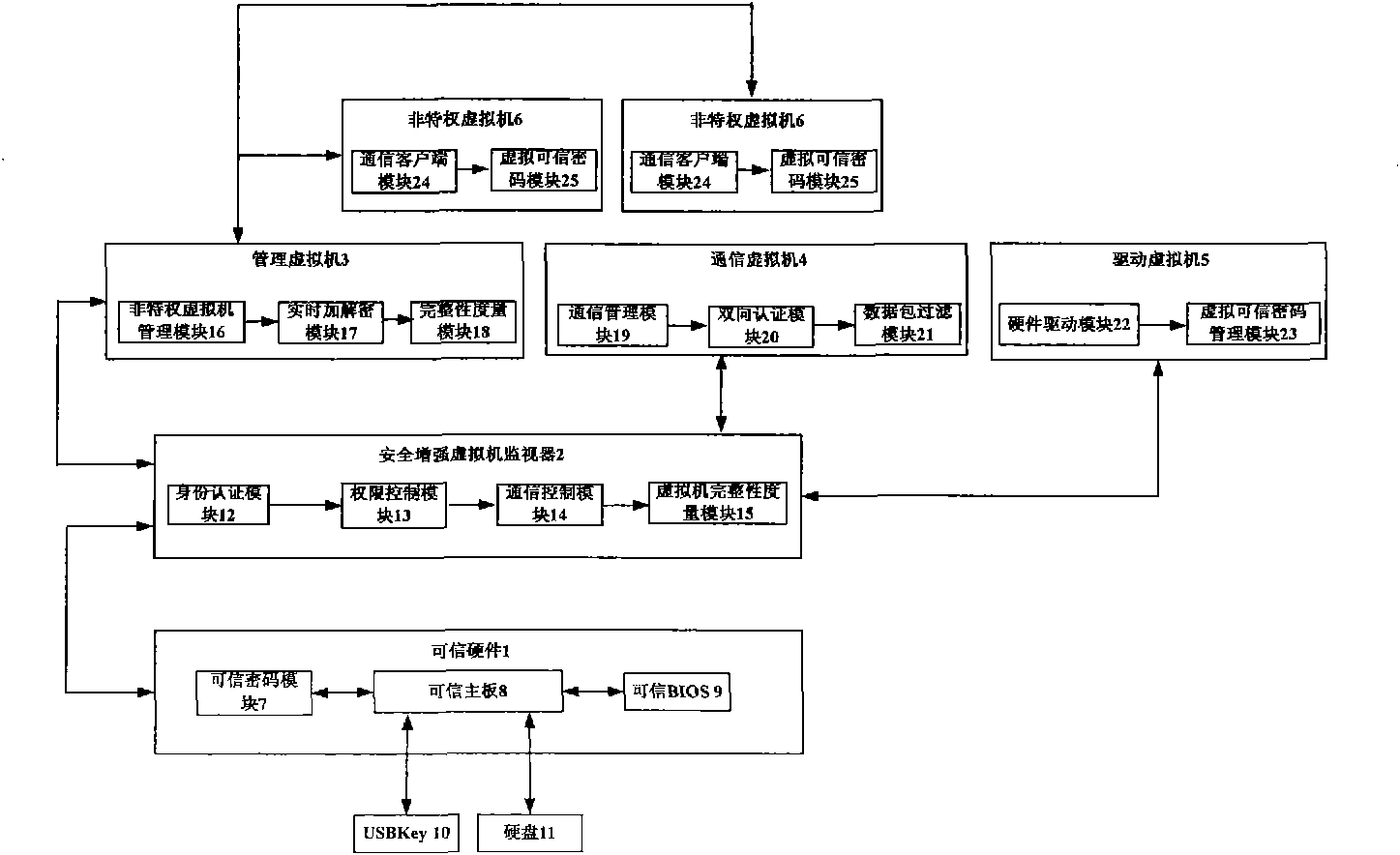
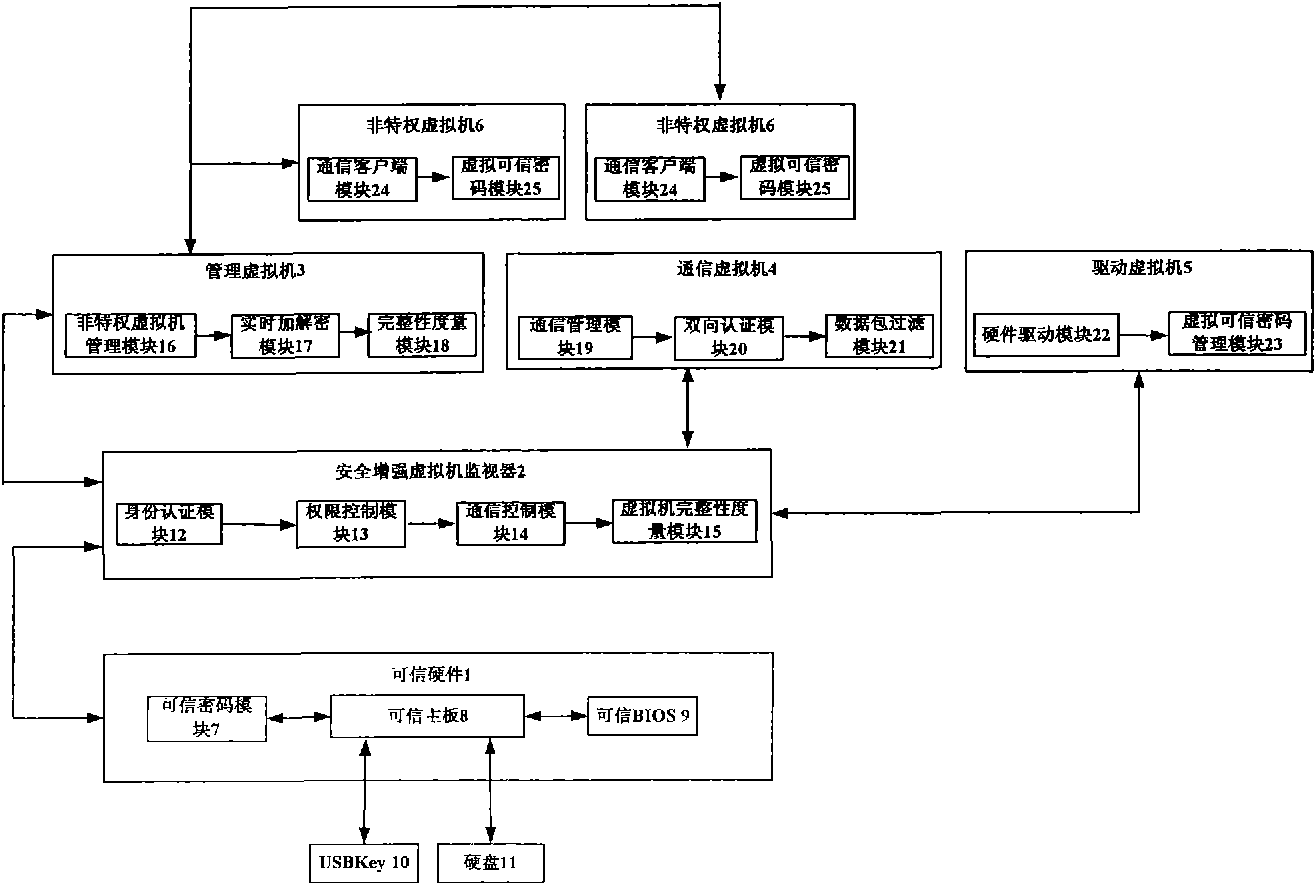
Credible virtual machine platform
InactiveCN101957900AImprove stability and attack resistanceImprove securityInternal/peripheral component protectionVirtual machineOperating environment
The invention discloses a credible virtual machine platform, which comprises a hard disk (11), a USB Key (10) and a nonprivileged virtual machine (6), and also comprises credible hardware (1), a security enhancement virtual machine monitor (2), a management virtual machine (3), a communication virtual machine (4) and a driving virtual machine (5). The security enhancement virtual machine monitor (2) is bidirectionally connected with the credible hardware (1) and the management virtual machine (3) respectively; the management virtual machine (3), the driving virtual machine (5) and the communication virtual machine (4) are privileged virtual machines; the management virtual machine (3) creates, manages, destroys and transfers other virtual machines; the driving virtual machine (5) provides driving needed by the operation of the virtual machine and management of a virtual credible password module; and the communication virtual machine (4) takes charge of communication between inner virtual machines and a virtual machine platform. The credible virtual machine platform has the advantages of effectively guaranteeing the safety and credibility of an operating environment of the virtual machine platform and realizing effective management and control of communication between virtual domains.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
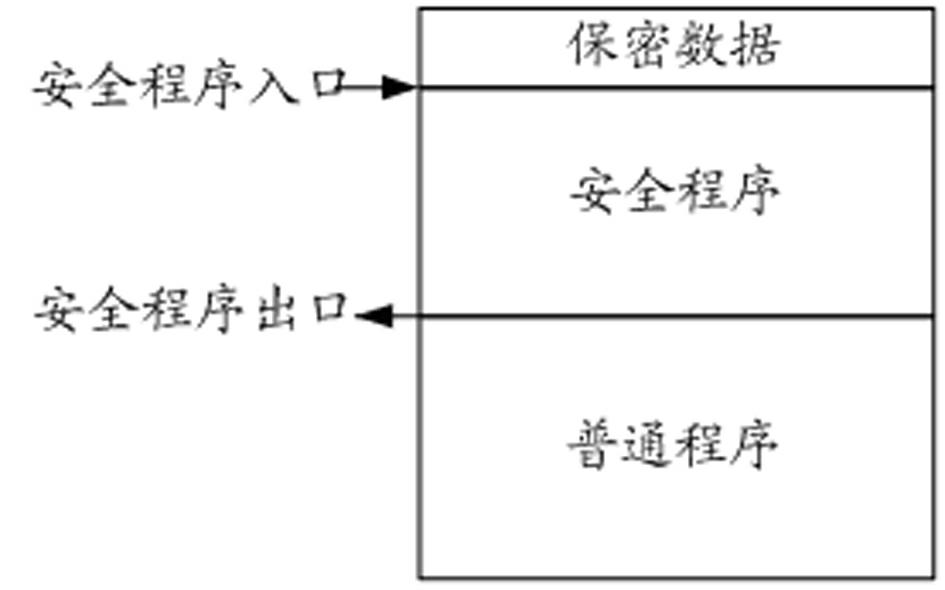
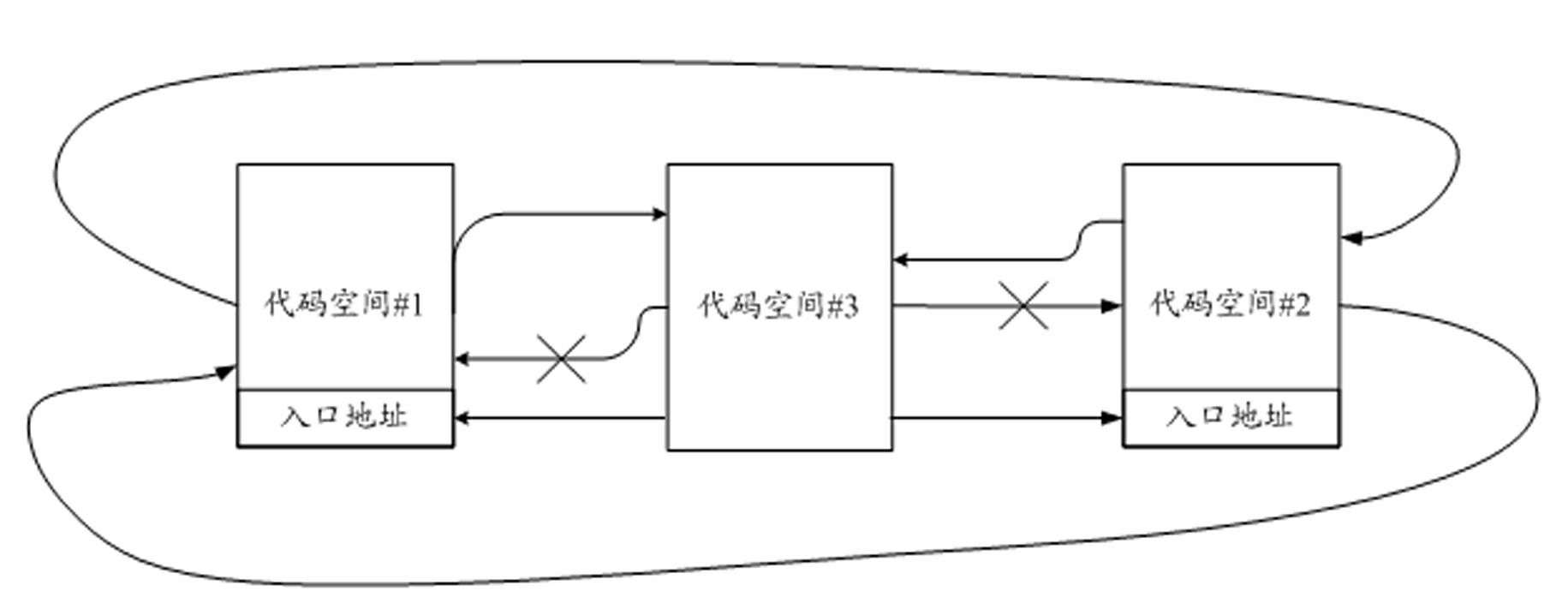
Storage protecting controller and method for improving safety of SOC (system on chip)
ActiveCN102592083AImprove resistance to attackImprove securityUnauthorized memory use protectionInternal/peripheral component protectionCode spaceSpace partitioning
The invention discloses a storage protecting controller and a method for improving safety of an SOC (system on chip). The method includes the steps: dividing a program code space of a processor into a plurality of code spaces, and setting an entry address corresponding to each code space; dividing a storage space into a plurality of storage protecting areas, individually setting access authority attributes of the processor to the storage protecting areas when each code space executes program codes; judging whether a program pointer of the processor skips or not and whether skip is abnormal or not, and generating skip abnormal indication if the skip is abnormal; and monitoring whether access of a current bus to the storage space is abnormal or not, and stopping access of the bus if access of the current bus to the storage space is abnormal, so that the program pointer of the processor is prevented from skipping from one code space to another code space to execute a program, and abnormal access to the storage protecting areas is prevented. The storage protecting controller can effectively improve program code running safety, and can be widely applied to SOC chips of various types.
Owner:SHENZHEN STATE MICRO TECH CO LTD
Safe positioning method for wireless sensor
ActiveCN101309151AImprove resistance to attackEffective against known attacksRadio/inductive link selection arrangementsSecuring communicationLine sensorWireless sensor networking
The invention discloses a safe positioning method for a wireless sensor; the safe positioning method adopts two safe positioning methods which are the malicious beacon detection based on the checkpoint and the malicious beacon detection algorithm based on the regional voting mechanism to solve the positioning safety problem of the sensor network nodes. The positioning method improves the anti-attack capability of the system through filtering the malicious beacons directly so that not only the known attacks can be defended, but also the unknown attacks can be defended; the corresponding defending measurement for every possible specific attack is avoided; the implementation of the safety strategy of the positioning system is simplified; the two detection methods are combined effectively to adjust the defending strategy automatically according to the attack types; the safe positioning is guaranteed and the computation cost is reduced effectively; the neighbor communication authentication technique based on the unidirectional key chain is adopted to avoid the support of other network safety protocols so that the storage cost of the sensor nodes is reduced; the neighbor communication authentication technique can be compatible and used together with the present wireless sensor network protocol; the safety target of the positioning system of the sensor network nodes is realized.
Owner:XIDIAN UNIV
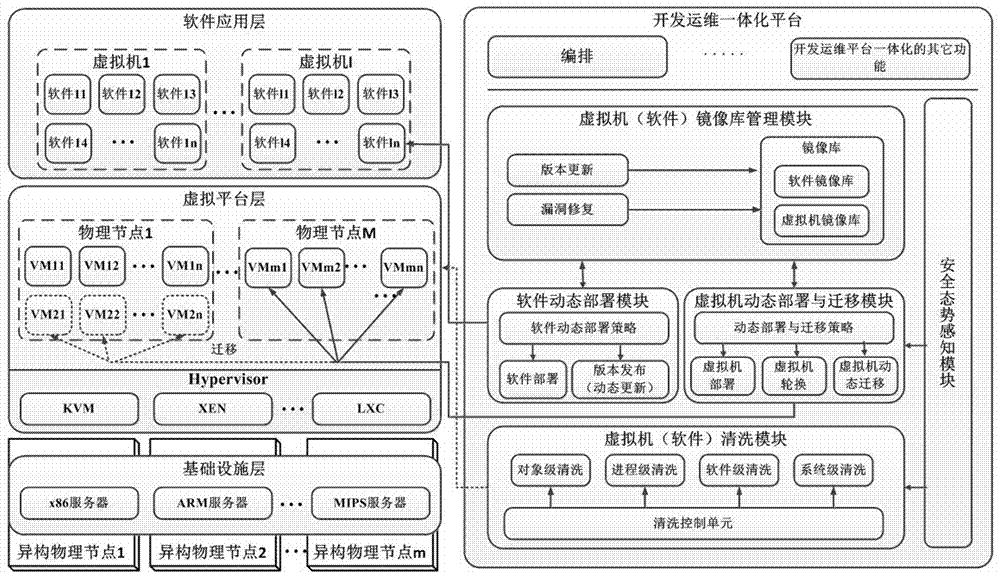
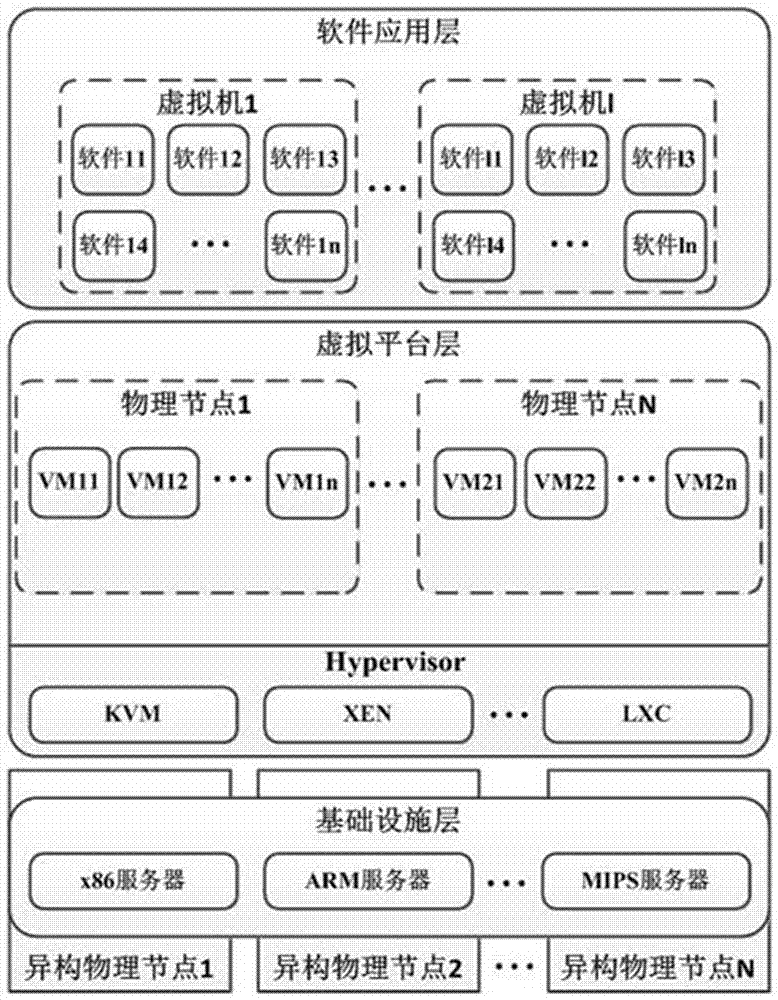
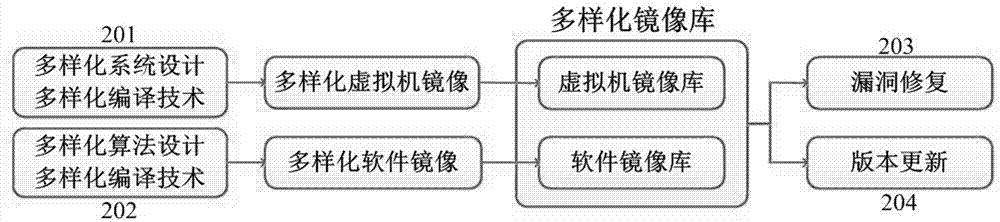
Dynamic generation and maintenance method of heterogeneous cloud host
ActiveCN107196803AImprove resistance to attackMeet security needsData switching networksSoftware simulation/interpretation/emulationIsomerismsCloud data center
The invention relates to the technical field of network security, and especially relates to a dynamic generation and maintenance method of a heterogeneous cloud host. The method comprises the following steps: 1) a heterogeneous cloud host node whose isomerism is embodied by the diversified physical facilities, virtual machines and software; 2) a mirror image library management system comprising creating diversified virtual machines and software mirror images; 3) dynamic deployment of a heterogeneous virtual machines and software: when the virtual machine or the software is instantiated, generating virtual machines or software of different versions according to physical nodes and application attributes, and deploying the virtual machines or software on the physical nodes; 4) dynamic virtual machine migration mechanism: a development operation and maintenance unit performs security posture estimation on the current virtual machine and its operation environment, and performs initiative migration on the virtual machine according to a strategy; and 5) a dynamic virtual machine and software cleaning mechanism: cleaning the online virtual machines according to the security posture or periodically. By adoption of the method, the anti-attack ability of a cloud data center is improved, and higher security requirements of users and providers for cloud services and infrastructure are satisfied.
Owner:THE PLA INFORMATION ENG UNIV
Compressive sensing-based adaptive video information hiding method
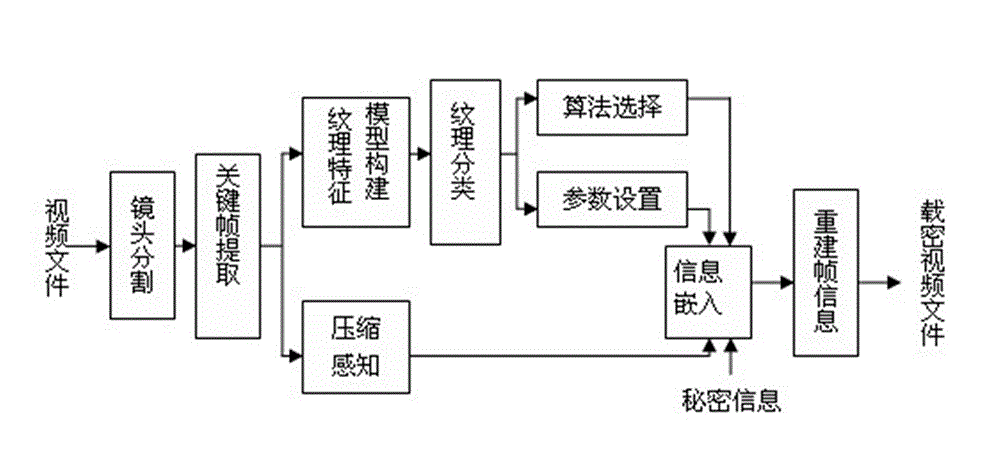
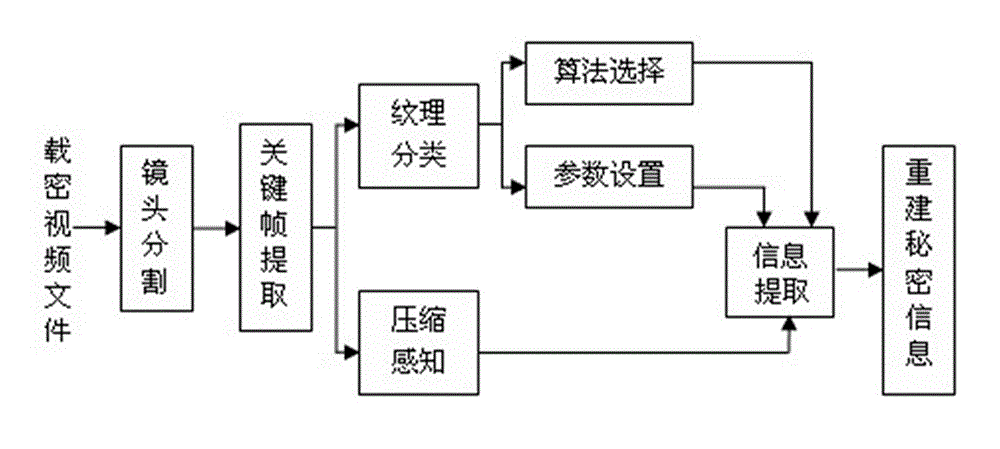
InactiveCN102917227AOrnamental effectSmall amount of calculationTelevision systemsDigital video signal modificationPattern recognitionKey frame
The invention discloses a compressive sensing-based adaptive video information hiding method, which is characterized by comprising the following steps of: a, framing a video file by using shot as a unit; b, taking the first frame of each shot as a key frame; c, establishing an image texture classification model to obtain a texture classification model mark of each key frame; d, determining a texture category of each key frame and determining whether the key frame is a texture region, or a smooth region or between the texture region and the smooth region; e, selecting an algorithm and determining insert depth; f, inserting secret information, i.e., inserting the secret information in a coefficient matrix; and g, synthesizing a video file. According to the video information hiding method, the secret information can be adaptively inserted under the condition that the entire video file is not required to be decompressed, so that the ornamental value of the video is not affected, and the method has the advantages of small amount of calculation, high information steganography efficiency, small influence on the video and good secret information safety. The method can be widely applied to various fields such as copyright authentication, pirate tracking and secure communication.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Memory controller for system on chip (SOC) chip system and method for implementing memory controller
ActiveCN102567245AReduce dependenceSimplify storage protection structureUnauthorized memory use protectionMemory interfaceControl store
The invention discloses a memory controller for a system on chip (SOC) chip system and a method for implementing the memory controller. The memory controller comprises a bus interface module, a memory interface module connected with a nonvolatile memory, and a safety protection subunit module connected between the bus interface module and the memory interface module, wherein the safety protection subunit module comprises a plurality of safety protection subunits of which the safety attributes can be independently configured; each safety protection subunit is used for performing access protection on one safety memory space in the nonvolatile memory; and by setting different safety attributes of the safety protection subunits, each piece of main equipment on a bus has different access authority on each safety memory space. The memory controller can effectively protect the safety information of the nonvolatile memory and is particularly suitable for an SOC chip which is needed to divide a memory space into different blocks with different sizes and ensure that the access attributes of the blocks are different.
Owner:SHENZHEN STATE MICRO TECH CO LTD
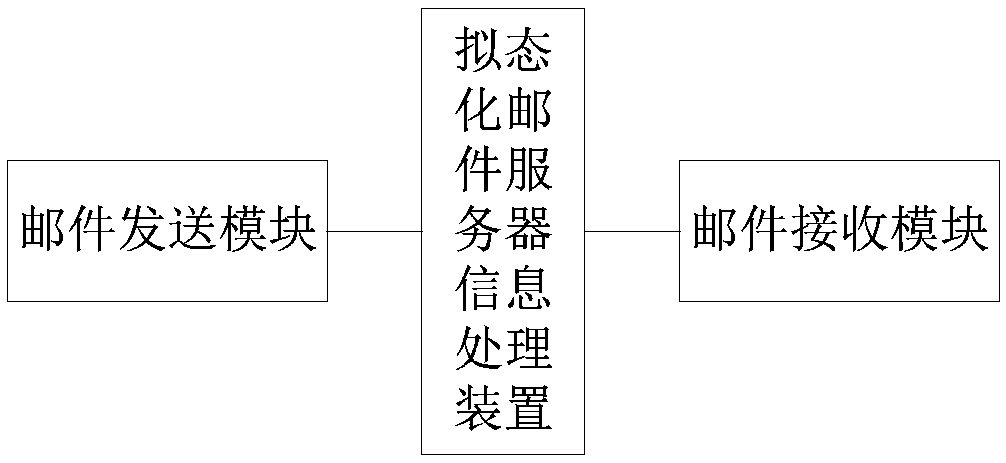
Mimetic mail server information processing device and mail service processing method, device and mail system
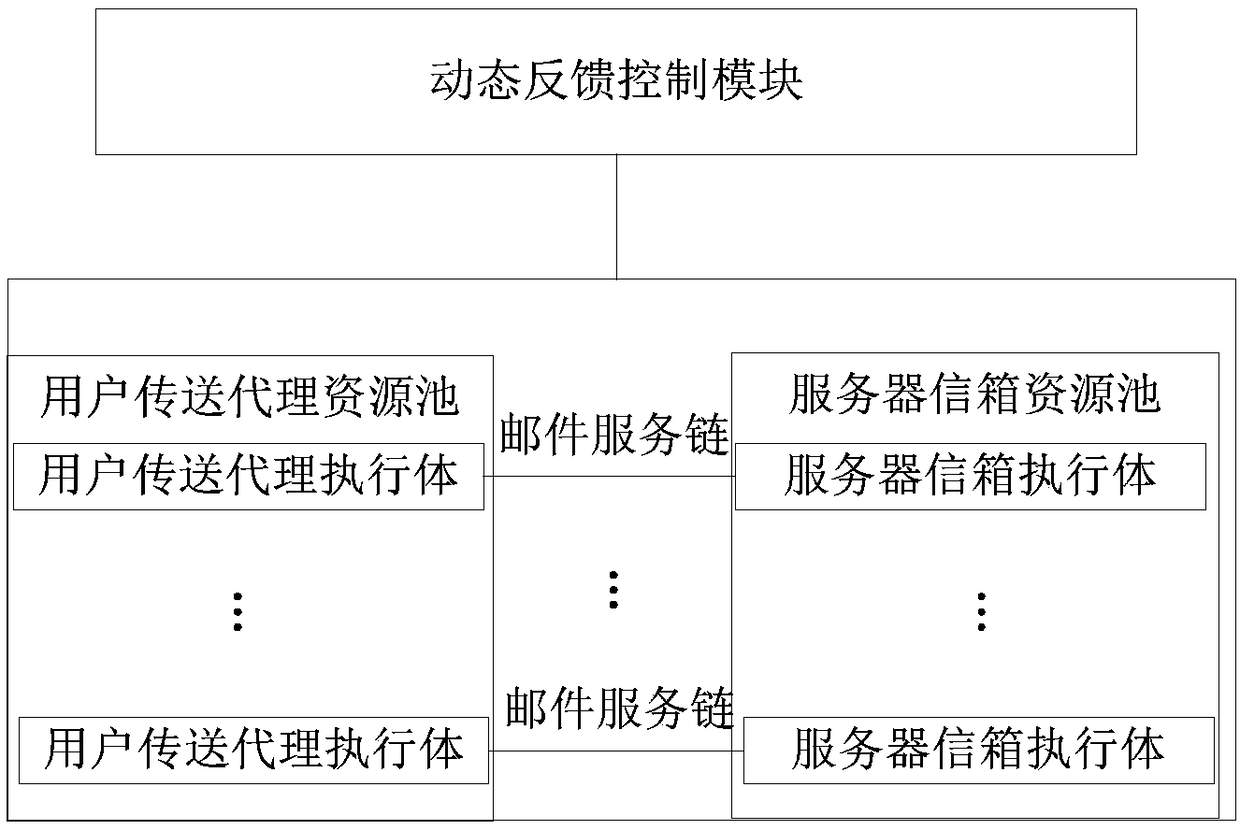
ActiveCN108833417AMeet security needsSolve the problem of building homogeneityData switching networksResource poolInformation processing
The invention relates to a mimetic mail server information processing device and a mail service processing method, device and a mail system. The information processing device comprises a resource poolcomposed of a user transfer proxy component and a server mailbox component, multiple parallel heterogeneous mail service chains composed of various components randomly selected from the resource pool, and a dynamic feedback control module, wherein the user transfer proxy component includes a number of heterogeneous user transfer proxy executors, and the server mailbox component includes a numberof server mailbox executors; and the dynamic feedback control module is used to monitor the operation of each executor and perform dynamic scheduling on various components. According to the scheme ofthe invention, the diversified executors are created, multiple processing results are subjected to mimetic decision output, the security performance of the mail system services can be improved, the initiative, variability and randomness of the mail system defense capability can be improved, the problem of privacy protection can be effectively solved, a more secure mail server solution can be provided, and the important guiding significance can be provided for the mail system security technologies.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Image digital copyright protecting method and image digital copyright protecting system based on frequency domain digital watermarking algorithm
InactiveCN106384328AGood clipping resistanceImprove translationImage data processing detailsProgram/content distribution protectionWavelet transformFrequency domain
The invention provides an image digital copyright protecting method based on a frequency domain digital watermarking algorithm. The method comprises the steps of performing coding of character information which comprises copyright information for obtaining an image sequence that is obtained through combining definite-number binary-value image templates, and embedding the binary-value image sequence into an image according to image characteristic points and a wavelet transform technique; calculating the size of the image sequence for keeping robustness of the algorithm, and generating an alarm when the size of the image sequence is overlarge; and for resisting rotation and scaling attacks, embedding pre-arranged template linear points in an annular Fourier transform area of SIFT characteristic points of the image. In extraction, a rotation and scaling deformation parameter which is bear by the image is estimated through analyzing distribution of the template linear points; the parameter is used for restoring the image and then extraction is performed; a extracted watermarking binary-value image is restored to a watermarking character sequence through matching with a preset template image according to an encoding algorithm; and whether the watermarking sequence is totally extracted is checked by means of a CRC32 algorithm. The image digital copyright protecting method has high robustness and settles a problem of incapability of simultaneously resisting multiple kinds of attacks in an existing image algorithm, particularly cutting and rotation scaling geometric attacks.
Owner:武汉圆周率软件科技有限公司
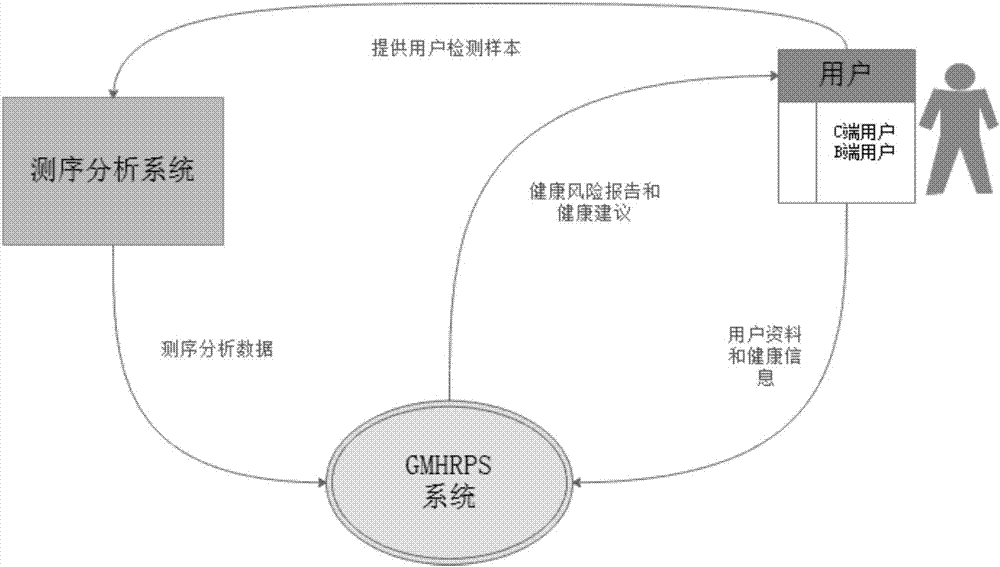
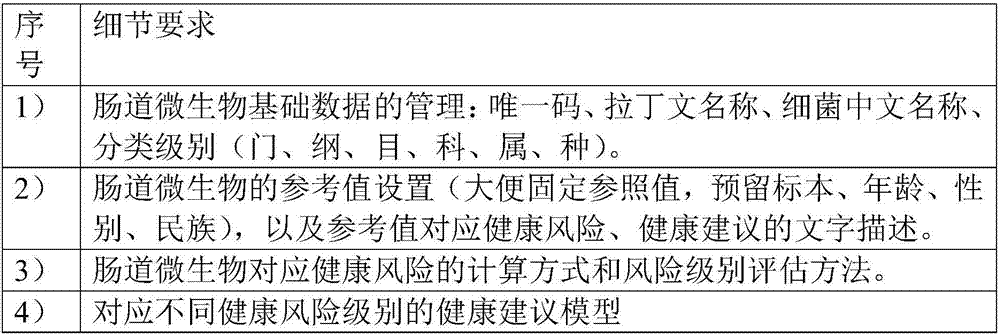
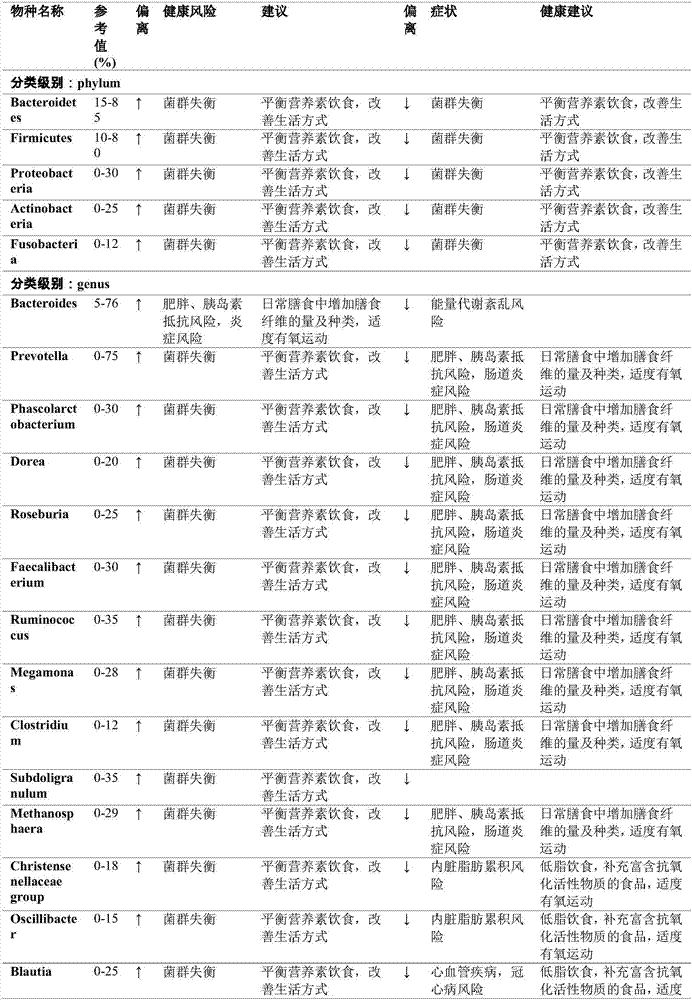
Enteric microorganism-based health risk prediction system
PendingCN107506582AManagement scienceStandardized managementSequence analysisSpecial data processing applicationsInformatizationHuman body
Owner:周礼红
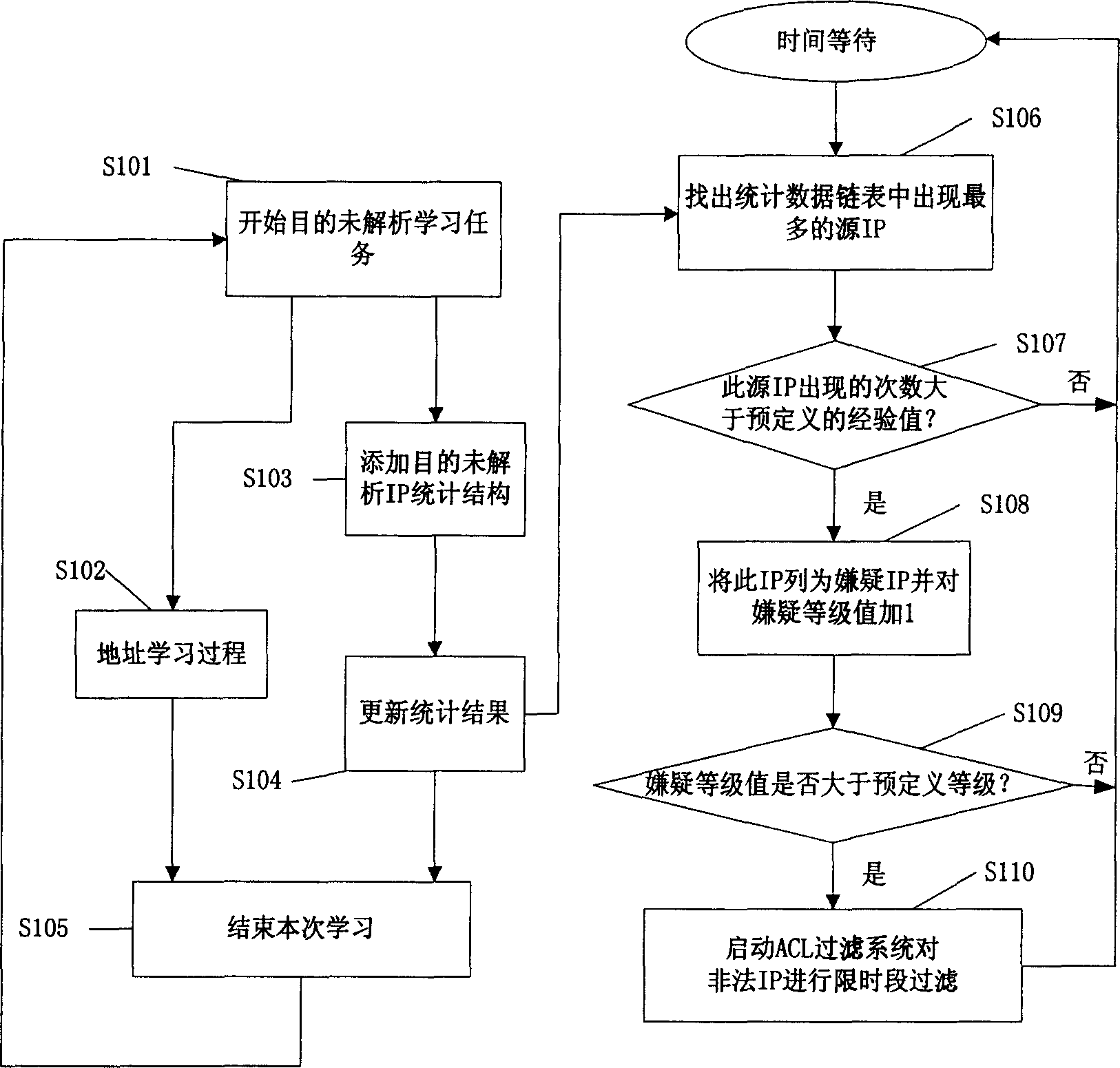
Method for detecting user to make malicious IP scanning
A method for detecting out user carrying on vicious IP scanning includes counting up all source IP address of received messages , finding out source IP address being occurred most frequently in statistic value , judging whether source IP address being occurred most frequently is IP address of user carrying in vicious IP scanning or not and controlling confirmed IP address of user carrying on vicious IP scanning .
Owner:GLOBAL INNOVATION AGGREGATORS LLC
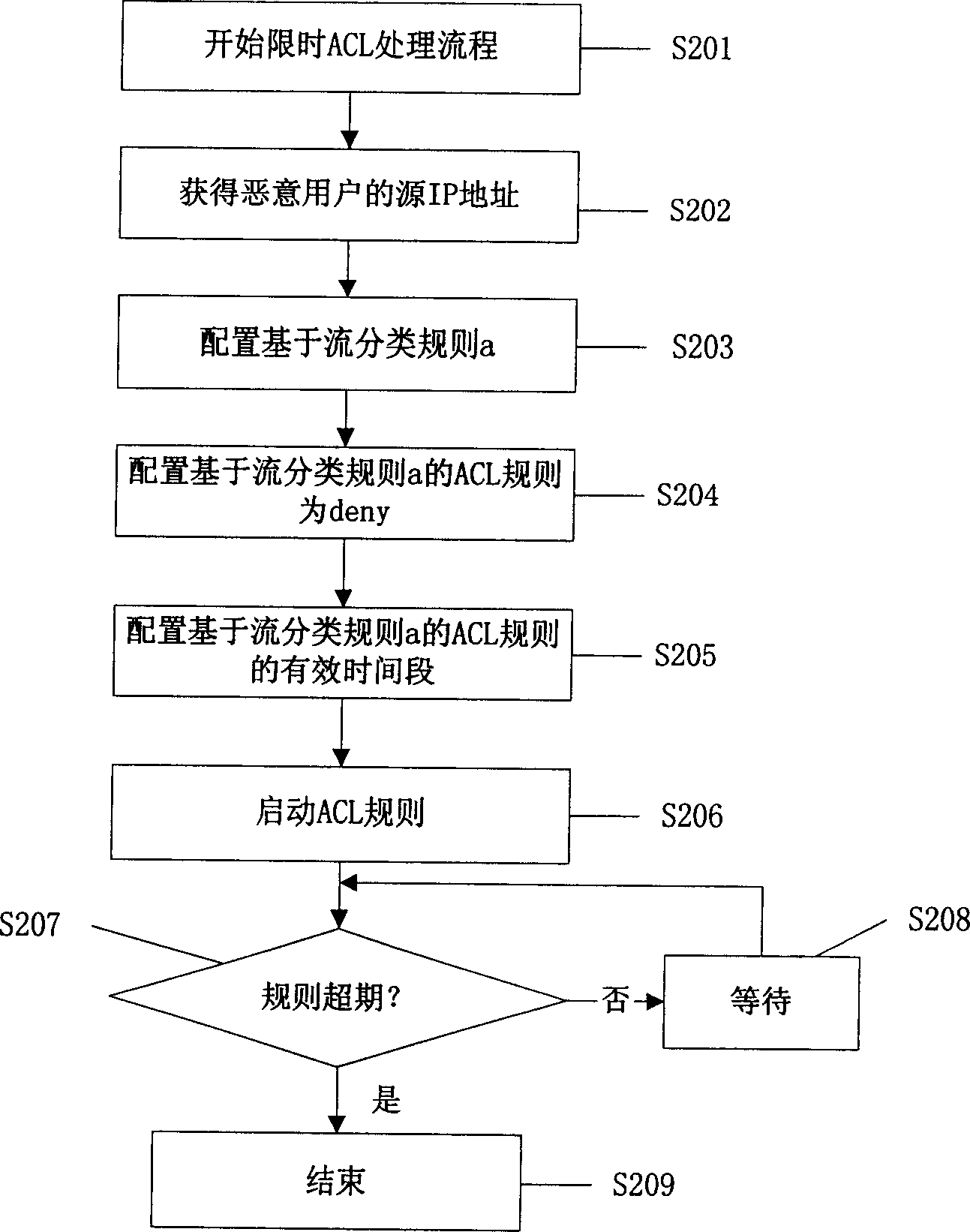
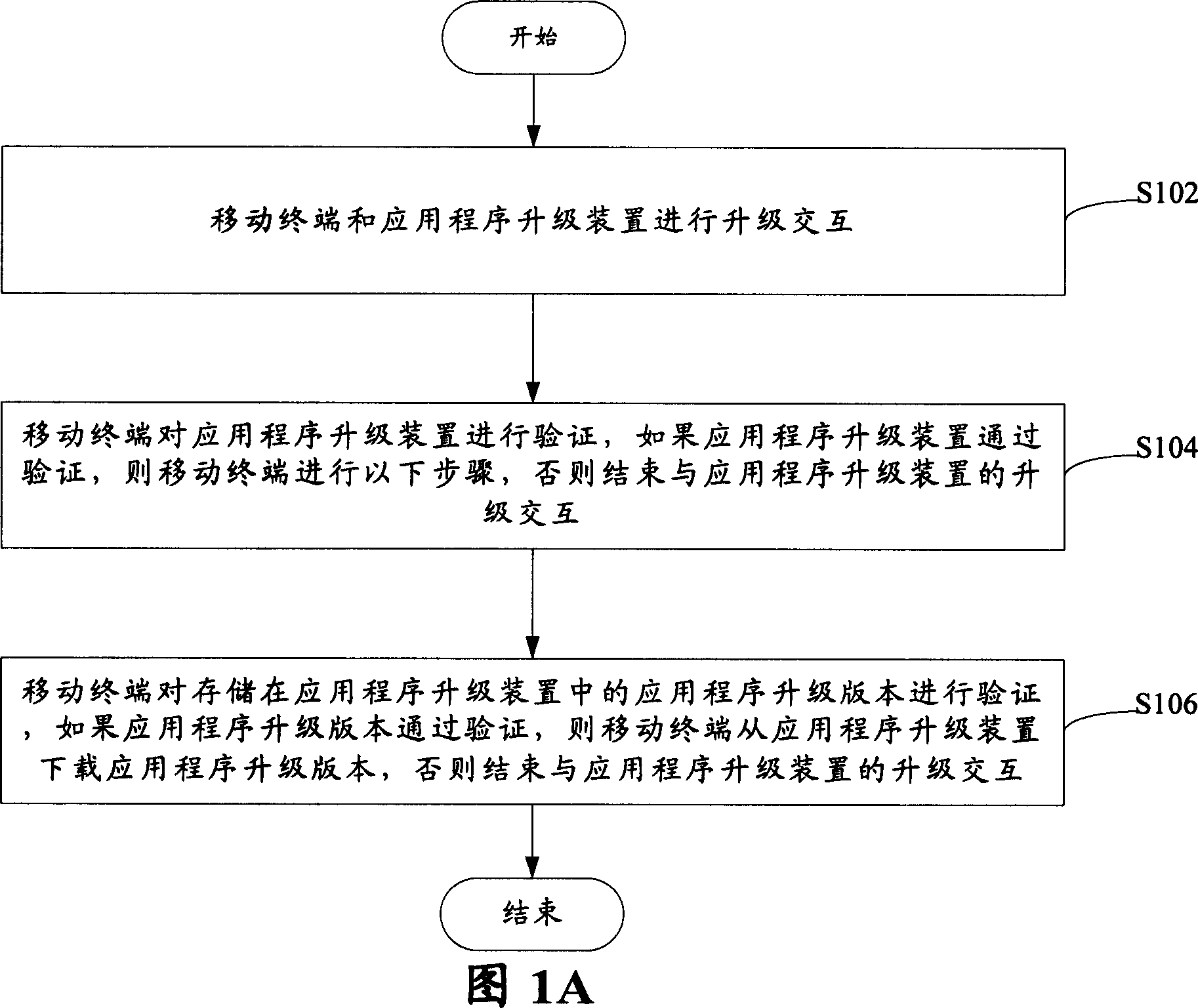
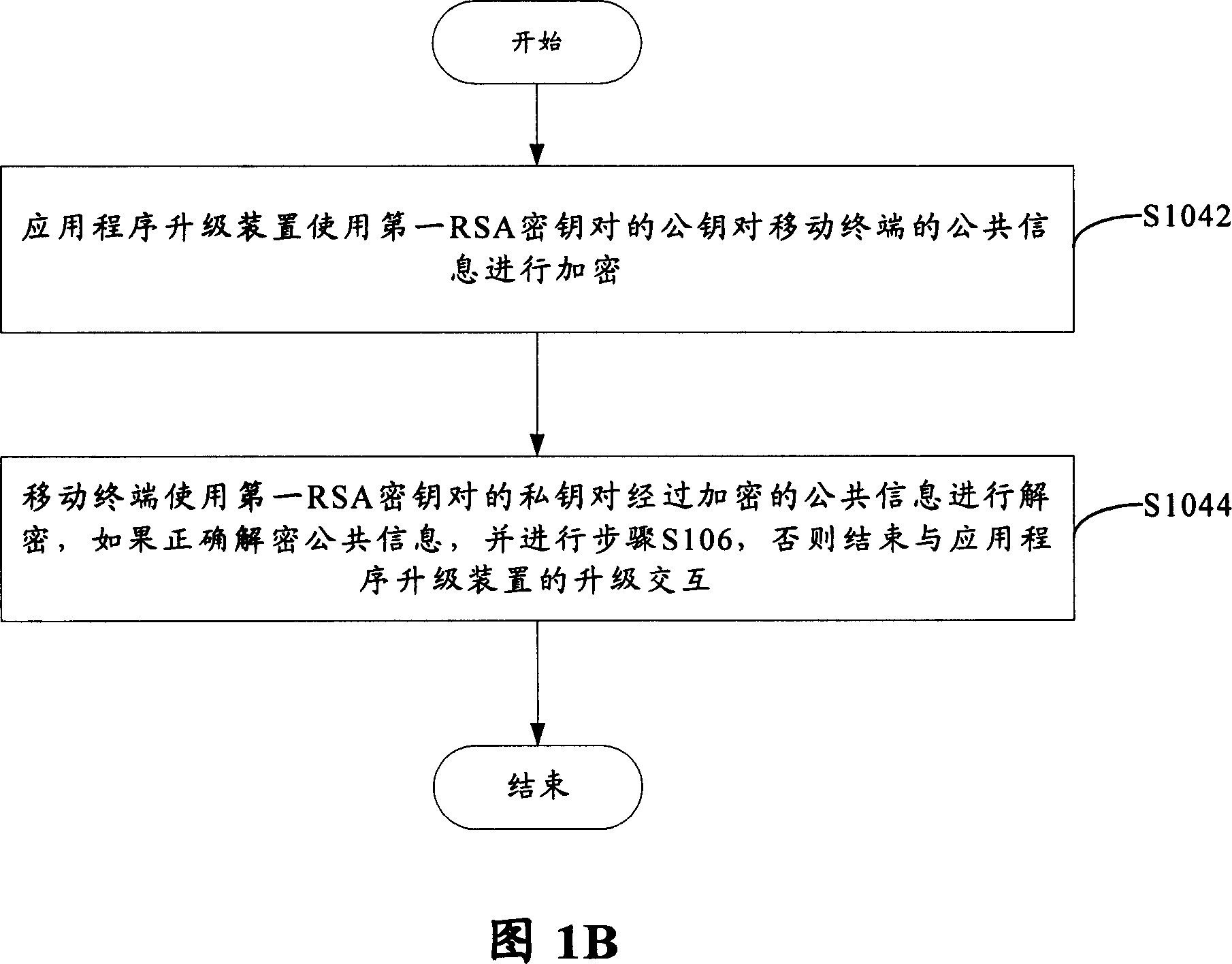
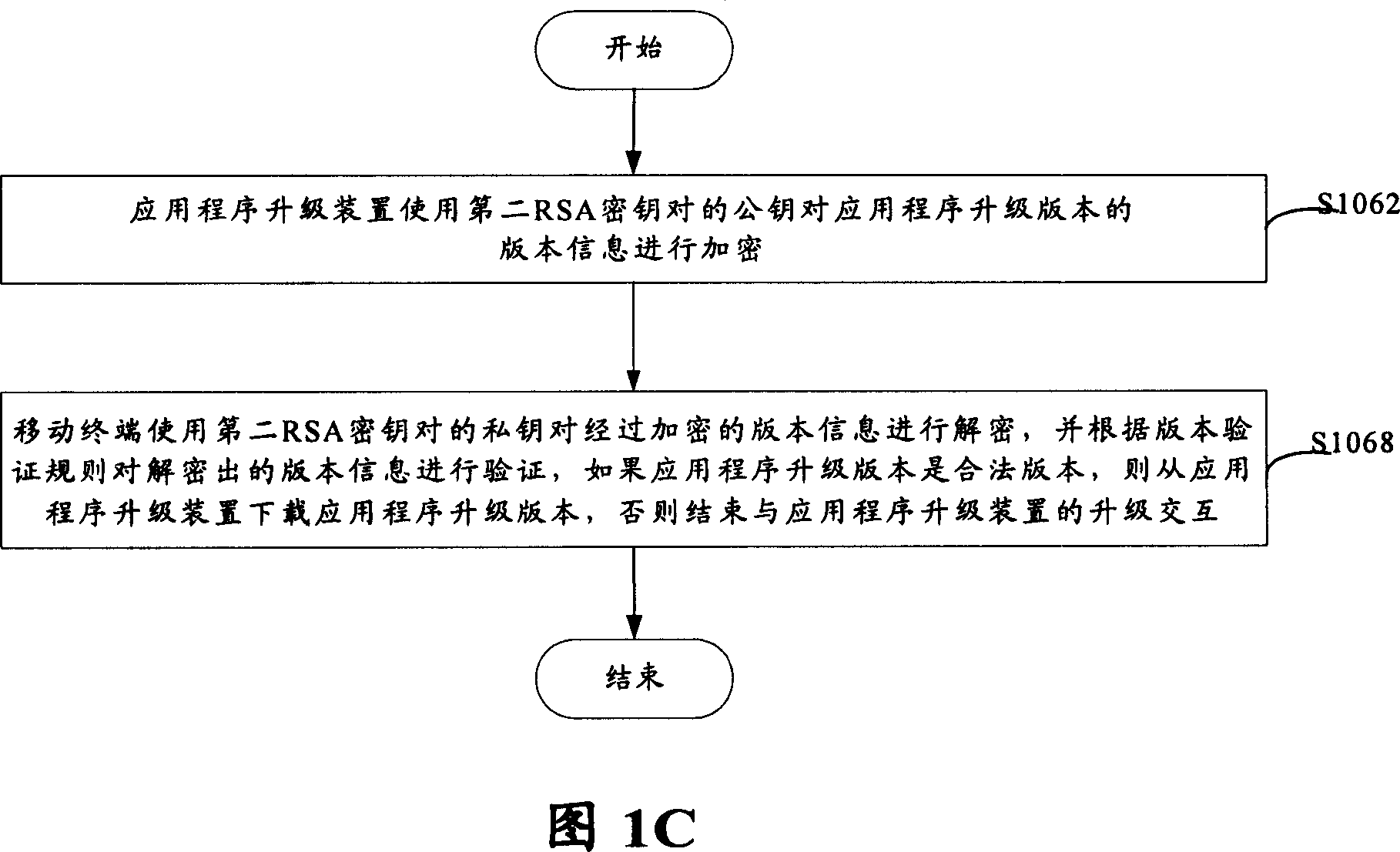
Method of application program for prevention illegal update mobile terminal
InactiveCN101043680AEnsure safetyWide versatilityUser identity/authority verificationRadio/inductive link selection arrangementsComputer terminalApplication software
The disclosed method for preventing illegal upgrading the mobile terminal application program comprises: S102, the mobile terminal and the upgrade device take interaction for upgrading; S1104, the terminal identifies the upgrade device, if the device passes the identification, goes to next step, or lese finishes the process; and S106, the mobile terminal validates the upgrade version program, if the version passes the validating, the terminal downloads the program for upgrading, or else finishes the process. This invention is efficient.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
Finger print structure in digital products, its authentication and digital products issue system
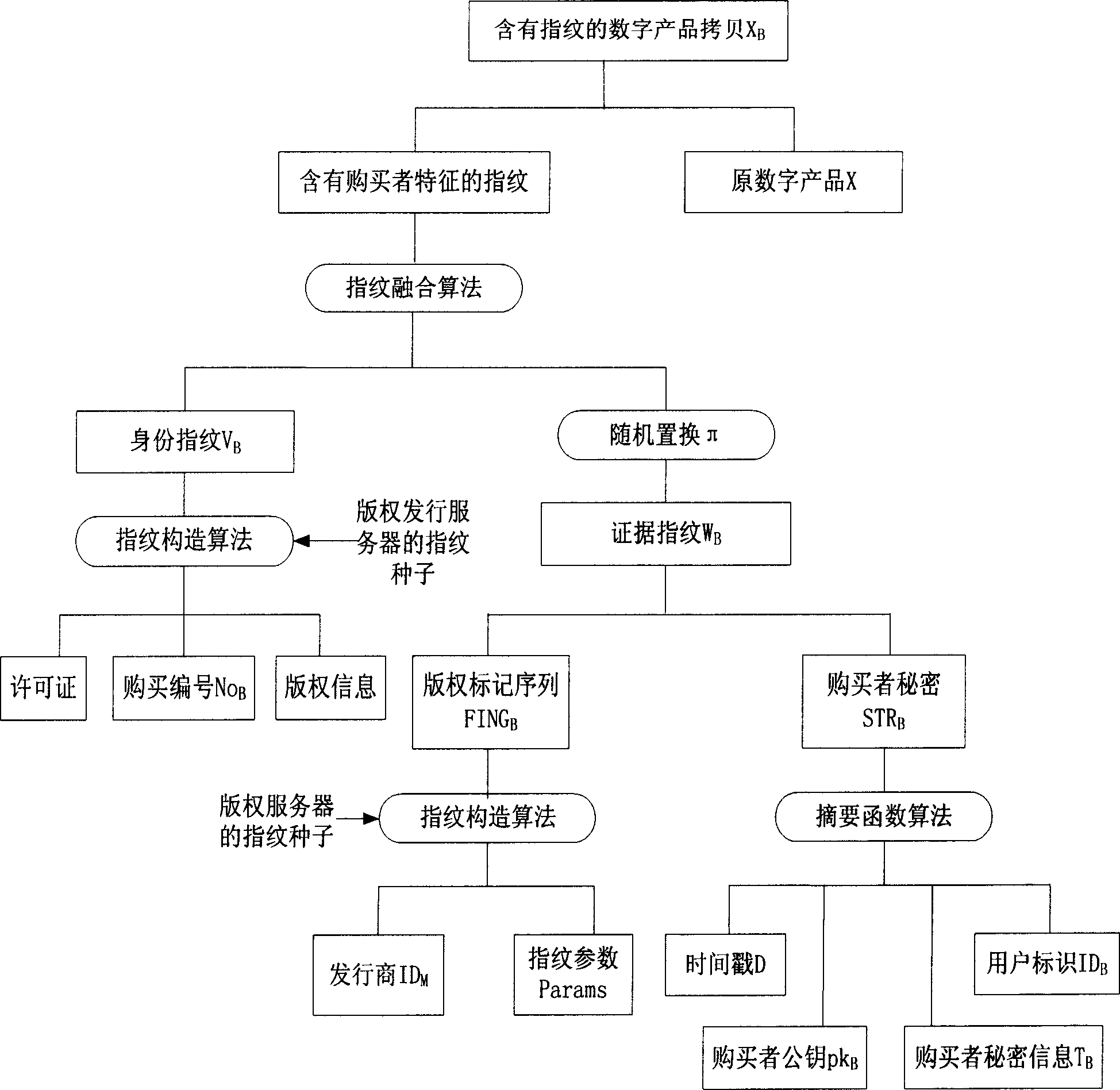
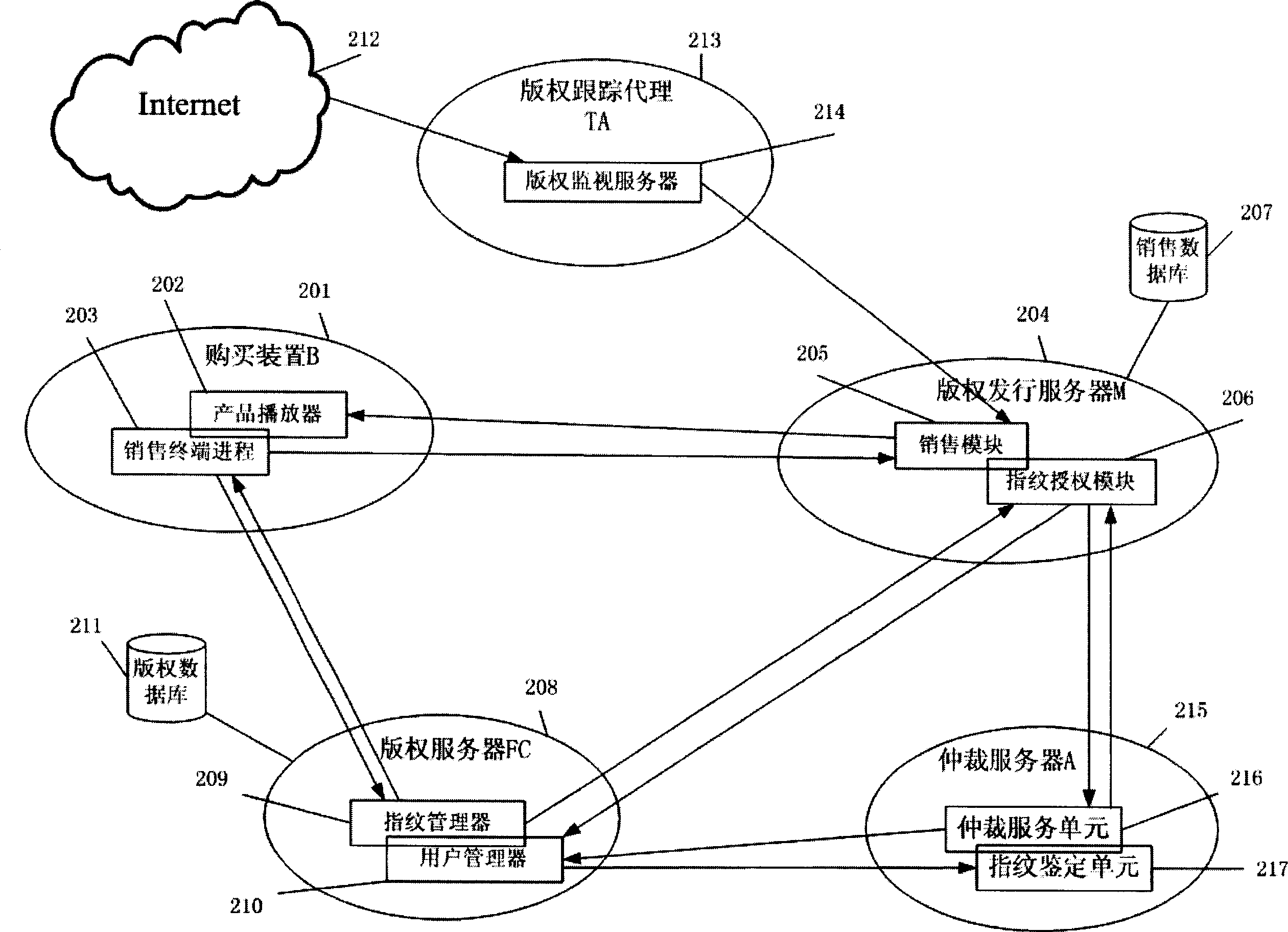
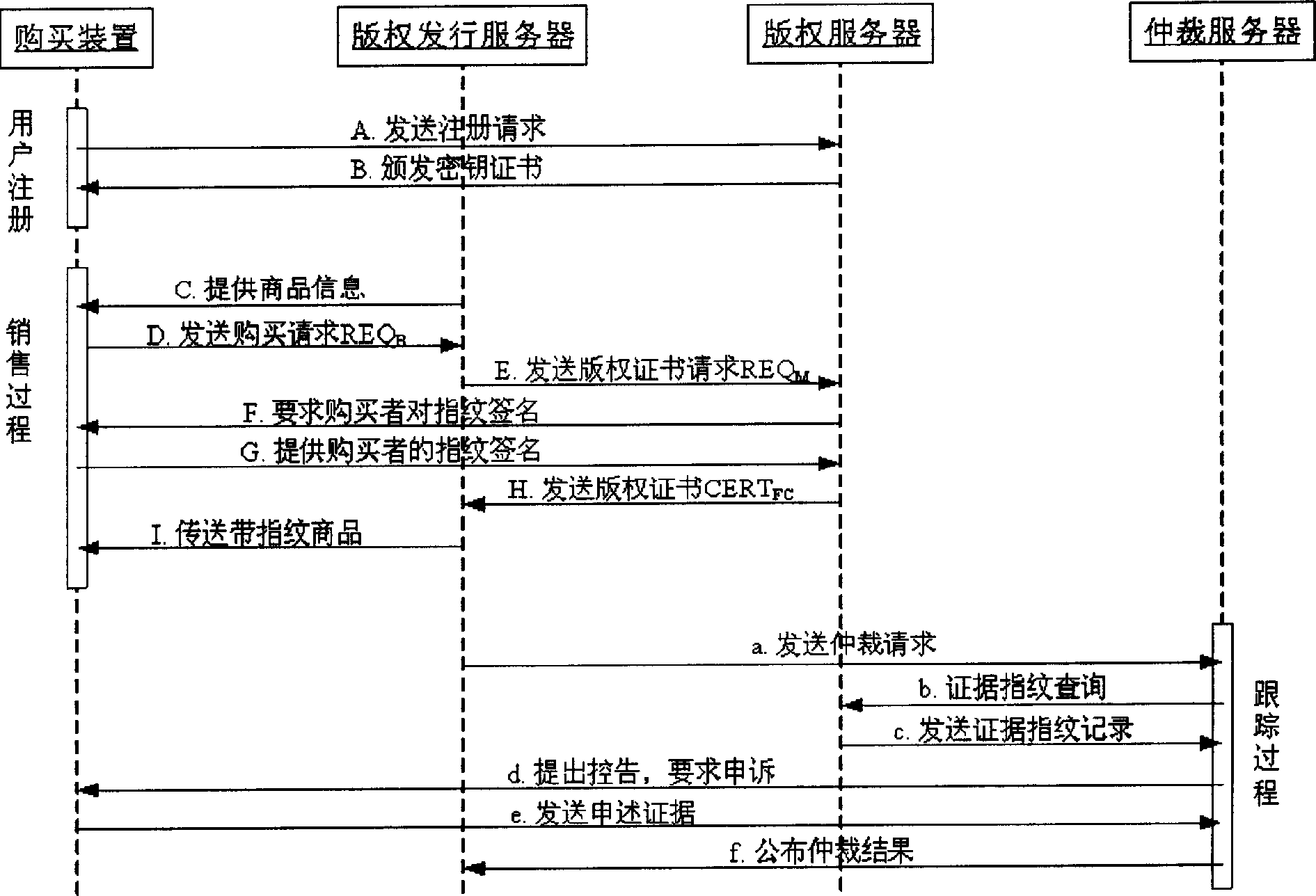
InactiveCN1834973AEnhanced construction flexibility and fingerprint security and robustnessImprove reliabilityProgram/content distribution protectionMarketingSystem safetyFingerprint
The invention relates to an in-digital product fingerprint constructing and verifying method, and the constructing method obtains purchase secret information from a purchaser, and uses a copyright server to construct an evidence fingerprint unable to be forged, and then uses a copyright issuing server to construct an ID fingerprint with license issued by the copyright server and sale information, and finally adopts fusion technique to construct a fingerprint-containing copy. And the verifying method extracts the ID fingerprint stored in the digital product to check the product license and identify the ID of the purchaser, and then checks and confirms the belonging relation by comparability of the evidence fingerprint. Correspondingly, the invention provides a digital product issuing system, comprising purchasing device, copyright issuing server and copyright server. And it provides a user-friendly and simple-to-apply method, largely improving safety and extendibility of the existing system.
Owner:PEKING UNIV
Method and device for generating three-dimensional dynamic verification code
InactiveCN101739720AImprove resistance to attackEasy to identifyDigital data authentication3D modellingGeometric primitiveAnimation
The invention provides a method and a device for generating a three-dimensional dynamic verification code. The invention adopts a technical scheme which comprises the following steps: randomly generating the verification code and determining the position at which the verification code is displayed in a screen; generating a three-dimensional geometric primitive and judging whether the positions of the three-dimensional geometric primitive and the verification code information displayed in the screen are the same or not; if so, changing a designated changed attribute of the three-dimensional geometric primitive; otherwise not changing the designated changed attribute of the three-dimensional geometric primitive; and moving the designated changed attribute of the three-dimensional geometric primitive according to a motion trail to realize the three-dimensional dynamic verification code. In the invention, the content of the verification code is displayed by changing the attribute of the geometric primitive and each frame does not reveal the verification code information out, so that the traditional two-dimensional image verification code attack means cannot separate the content of the verification code from a single-frame image; and at the same time, because different motion trail of each geometric primitive is set by a special method, the identification and attack difficulties of the traditional technology tracing a moving object in a video are increased and anti-attack capability of the verification code finally is improved effectively.
Owner:WUHAN UNIV
Blockchain-based domain name resolution data management method, system and storage system
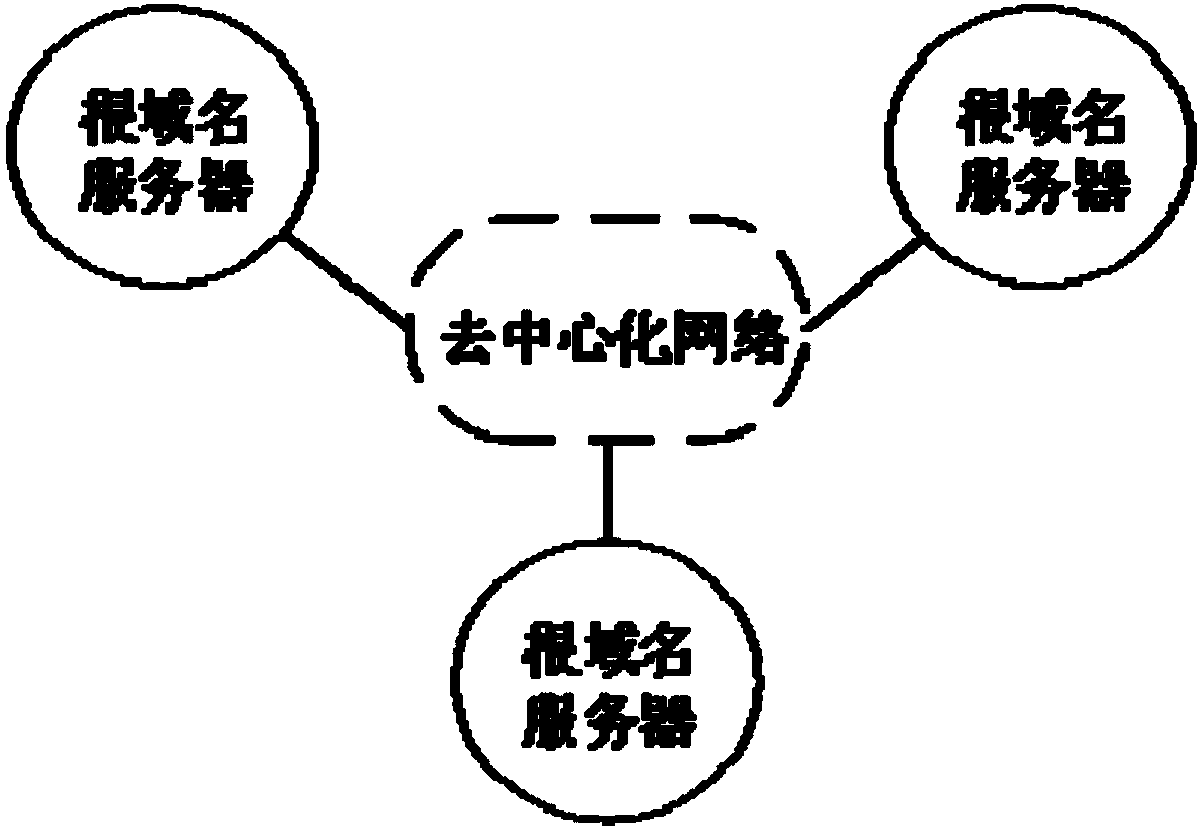
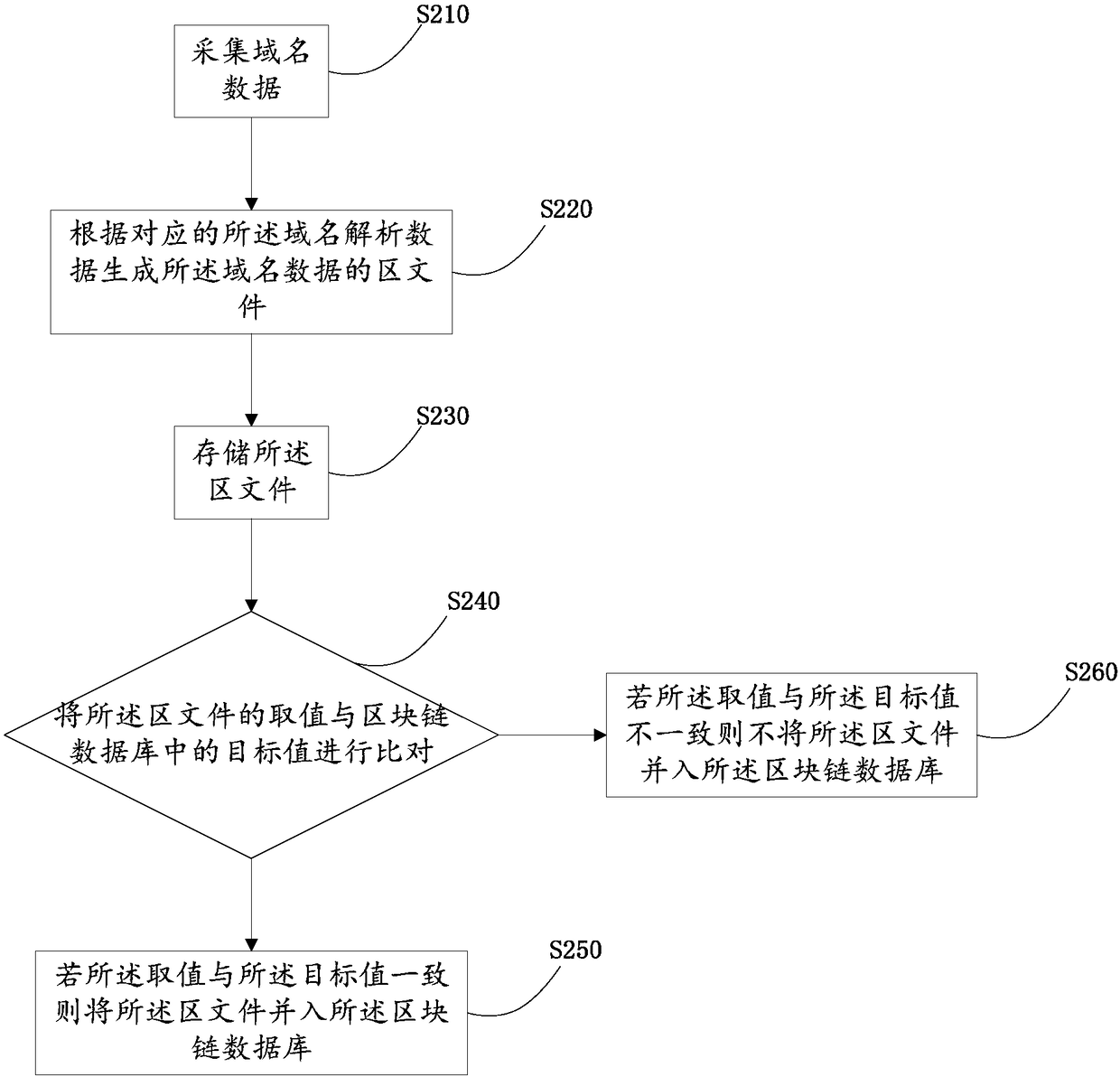
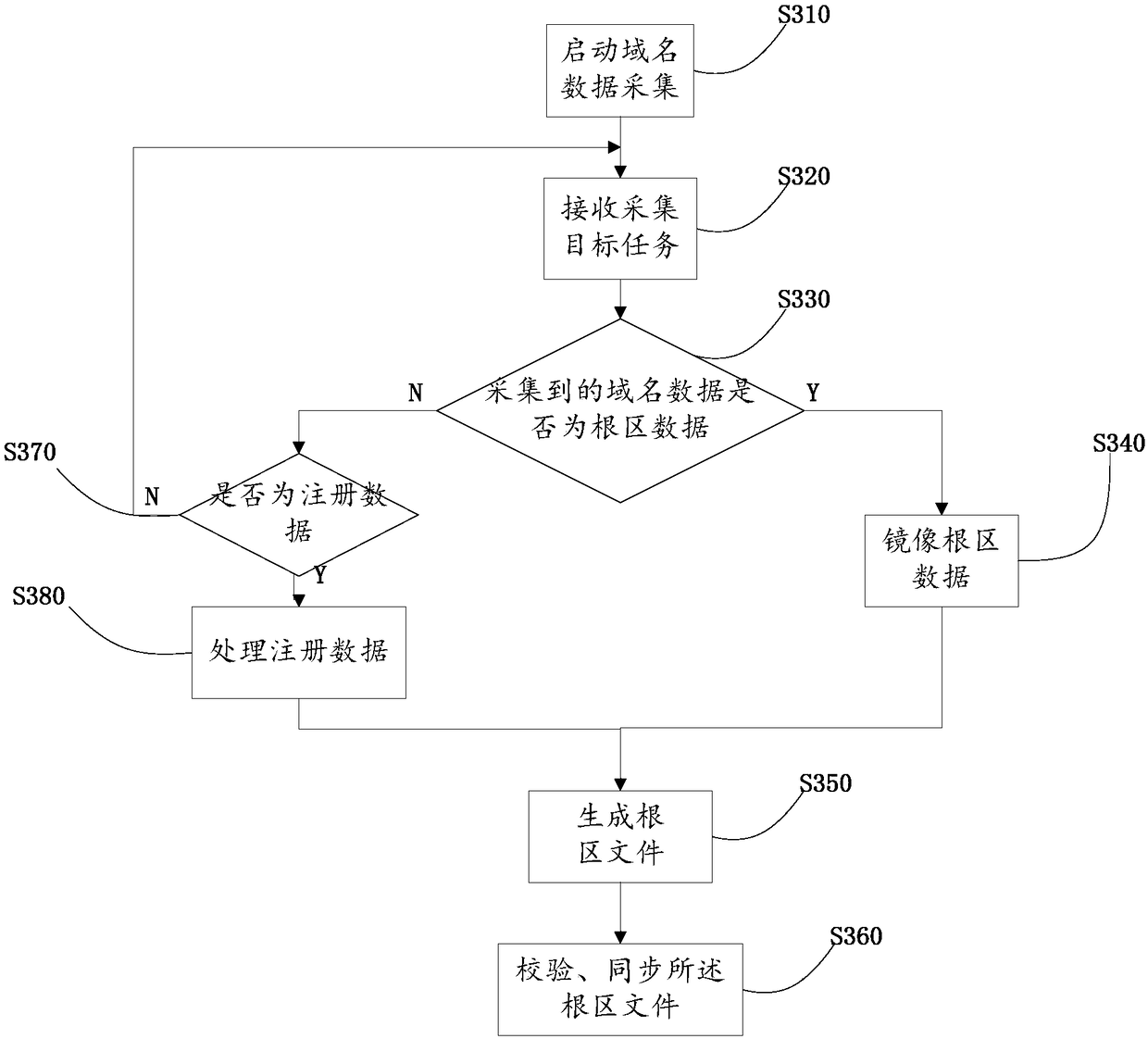
InactiveCN108566449APrevent tamperingImprove resistance to attackEncryption apparatus with shift registers/memoriesUser identity/authority verificationDomain nameApproaches of management
The invention relates to the technical field of domain name systems, and discloses a blockchain-based domain name resolution data management method, system and storage system. The management method includes the following steps: collecting domain name data; generating a zone file of domain name resolution data corresponding to the domain name data; storing the zone file; comparing a value of the zone file with a target value in a blockchain database, and if the value is consistent with the target value, merging the zone file into the blockchain database. According to the scheme of the invention, the zone file of the domain name resolution data is generated, the domain name resolution data is stored and managed in the form of a blockchain, so that the domain name resolution data can be prevented from being tampered with, a decentralized domain name resolution data storage system based on a blockchain technology can be realized, and the anti-attack capability of a domain name system can be enhanced.
Owner:GUANGZHOU UNIVERSITY
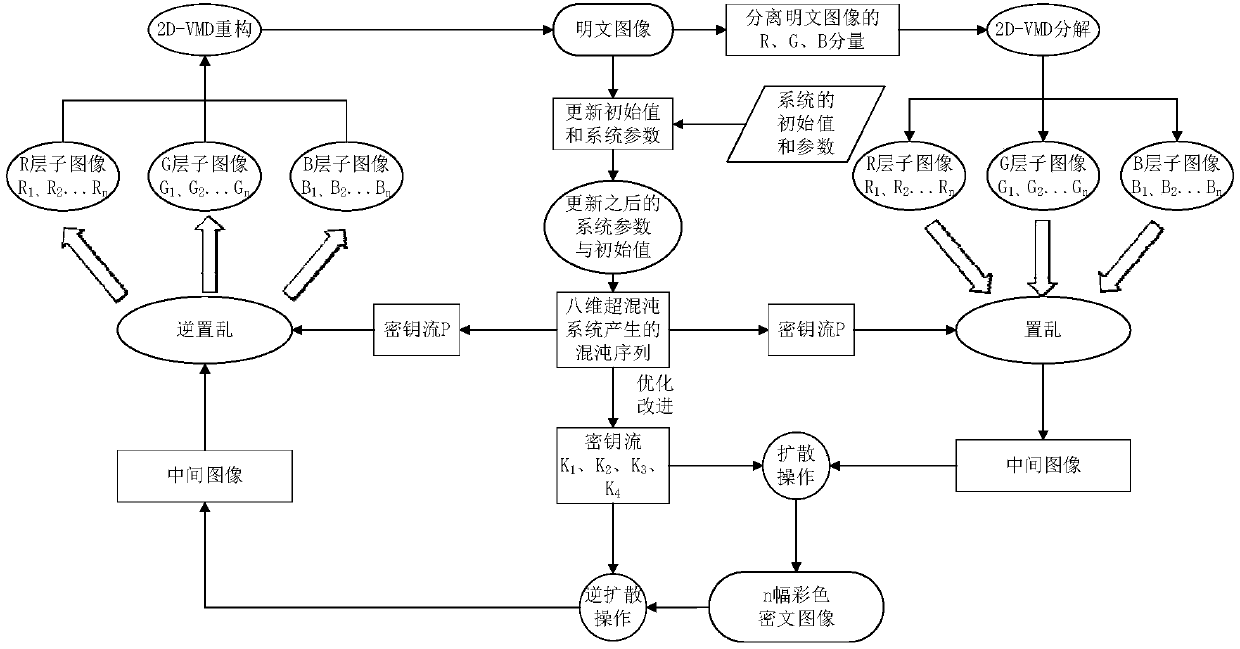
Color digital image encryption method based on 2D-VMD and eight-dimensional hyperchaotic system
ActiveCN108322622AIncreased sensitivityExpand the key spacePictoral communicationComputer visionMultiple attack
The invention provides a color digital image encryption method based on 2D-VMD and an eight-dimensional hyperchaotic system, and belongs to the technical field of information security. The problems ofpoor security, small key space and breaking easiness of the existing color digital image encryption methods are solved. The technical points are as follows: separating red, green and blue componentsof a color plaintext image; randomly selecting an initial value of the system, updating and calculating parameters and the initial value of the eight-dimensional hyperchaotic system by using the colorplaintext image, performing iteration on the hyperchaotic system to generate two key sequences with high randomness; separately decomposing the red, green and blue components by using a 2D-VMD method, separately performing pixel position scrambling and pixel value diffusion encryption on sub-images obtained by decompression, finally obtaining color ciphertext images of corresponding decompositionlayers, and decrypting the color ciphertext images. Compared with the existing encryption methods, the color image encryption algorithm provided by the invention has a significant increase in key space and can effectively resist multiple attacks.
Owner:HARBIN UNIV OF SCI & TECH
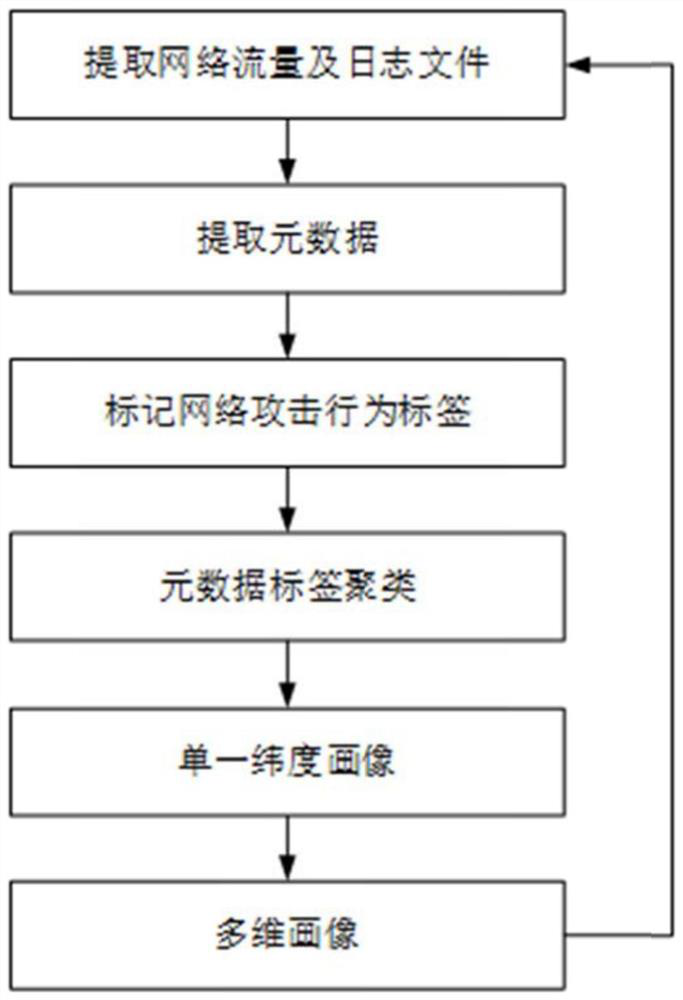
Network attack tracing method based on behavior portraits
ActiveCN111988285AIncreased depth of analysisImprove resistance to attackTransmissionHigh level techniquesNetwork behaviorInternet traffic
The invention provides a network attack tracing method based on a behavior portrait. The network attack tracing method comprises the following steps: 1) extracting network traffic and a log file in real time; 2) extracting metadata in the network flow and the log file; 3) counting and analyzing the key fields in the metadata of the same network behavior main body, and marking security labels for the network behaviors according to the security events corresponding to different key fields; 4) according to the network attack model, clustering the security tags describing the same network attack latitude to form a structured tag, namely a network attack behavior single latitude portrait; 5) aggregating and correlating portrait results of a plurality of latitudes to form a network attack behavior portrait, and 6) repeating the steps 1) to 5) to continuously extract real-time traffic and log information and enrich the network behavior portrait. The method improves the perception ability of the network security situation, enhances the analysis and defense ability of an attacker, and is used for network security.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
Data encryption method
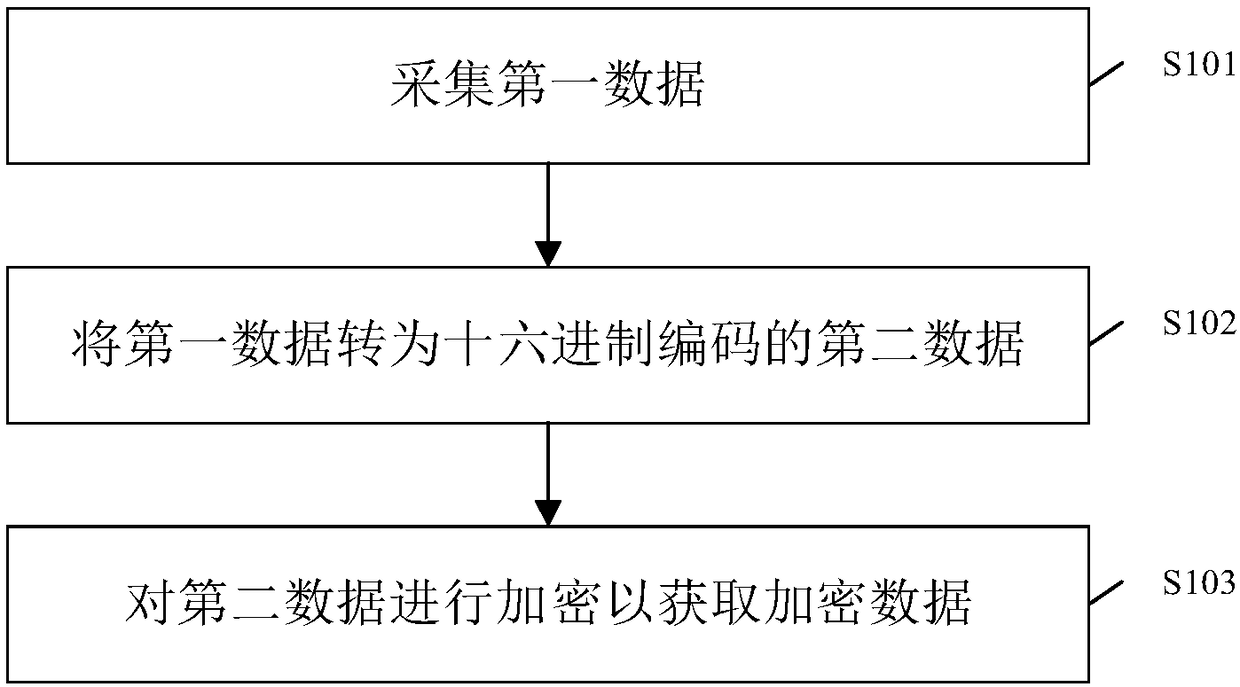
InactiveCN108429735AEnsure safetyIncrease the difficultyKey distribution for secure communicationMultiple keys/algorithms usageIntel HEXComputer hardware
The invention provides a data encryption method. The data encryption method comprises the following steps that first data is acquired, wherein the first data is fingerprint data, identity card data, adigital cipher and / or MF card data; the first data is converted into hexadecimal coded second data; and the second data is subjected to a hardware encryption mechanism and a software encryption mechanism to acquire encrypted data. According to the data encryption method, by means of the process that the first data is acquired and converted into the hexadecimal coded second data, and then the second data is encrypted to acquire the encrypted data, the security of the data can be guaranteed.
Owner:陈柱
Method for identifying DNS spoofing attack packet and detecting DNS spoofing attack
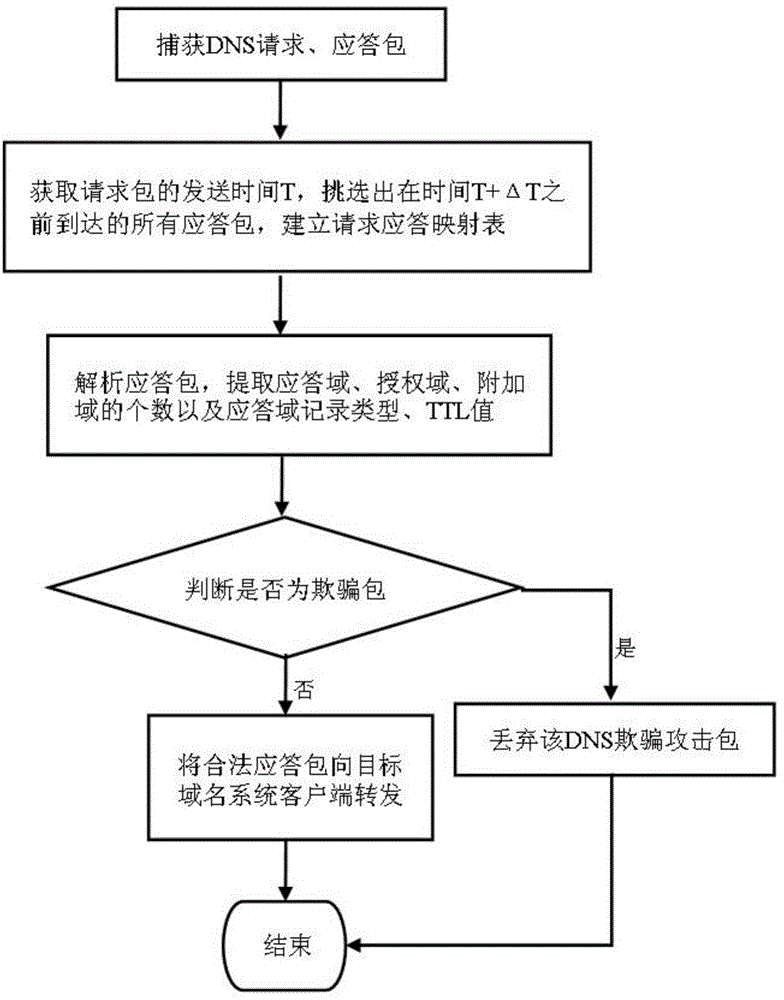
The invention relates to a method for identifying DNS spoofing attack packet and detecting DNS spoofing attack. For a plurality of DSN response packets with identical quintuple (business identifier, source IP address, destination IP address, source port number, destination port number), the one which concurrently accords to the following four characteristics is a DNS spoofing packet: having only one acknowledge field, one IP address is inside the acknowledge field; the acknowledge field does not contain Cname type records; the TTL values corresponding to class A records in acknowledge packets are not reasonable; the acknowledge packets do not contain authorized fields or additional fields. When detecting the DNS spoofing attack, firstly all DNS packets between a client terminal and a domain name server are captured; and then each acknowledge packet is judged whether to be the DNS spoofing packet based on the method above. The method for identifying DNS spoofing attack packet and detecting DNS spoofing attack is able to effectively identify DNS spoofing packets and timely detect DNS spoofing attack, thus the method has a high practical value in increasing the anti-attack ability of DNS system as well as protecting DNS service system.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Color image encryption method based on Latin square scrambling
ActiveCN108696666AImprove resistance to attackReduce strong correlationSecuring communication by chaotic signalsPictoral communicationPlaintextComputer hardware
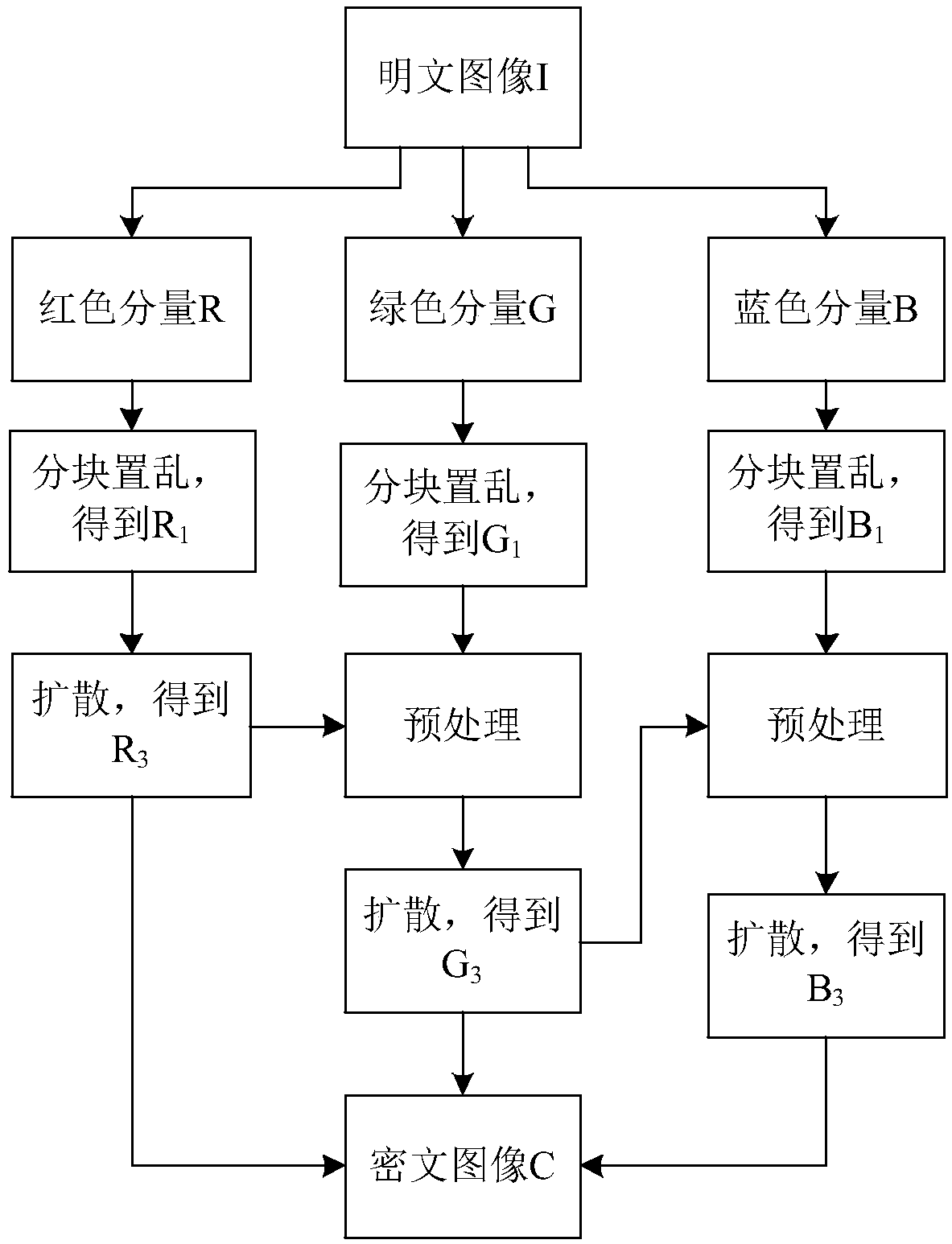
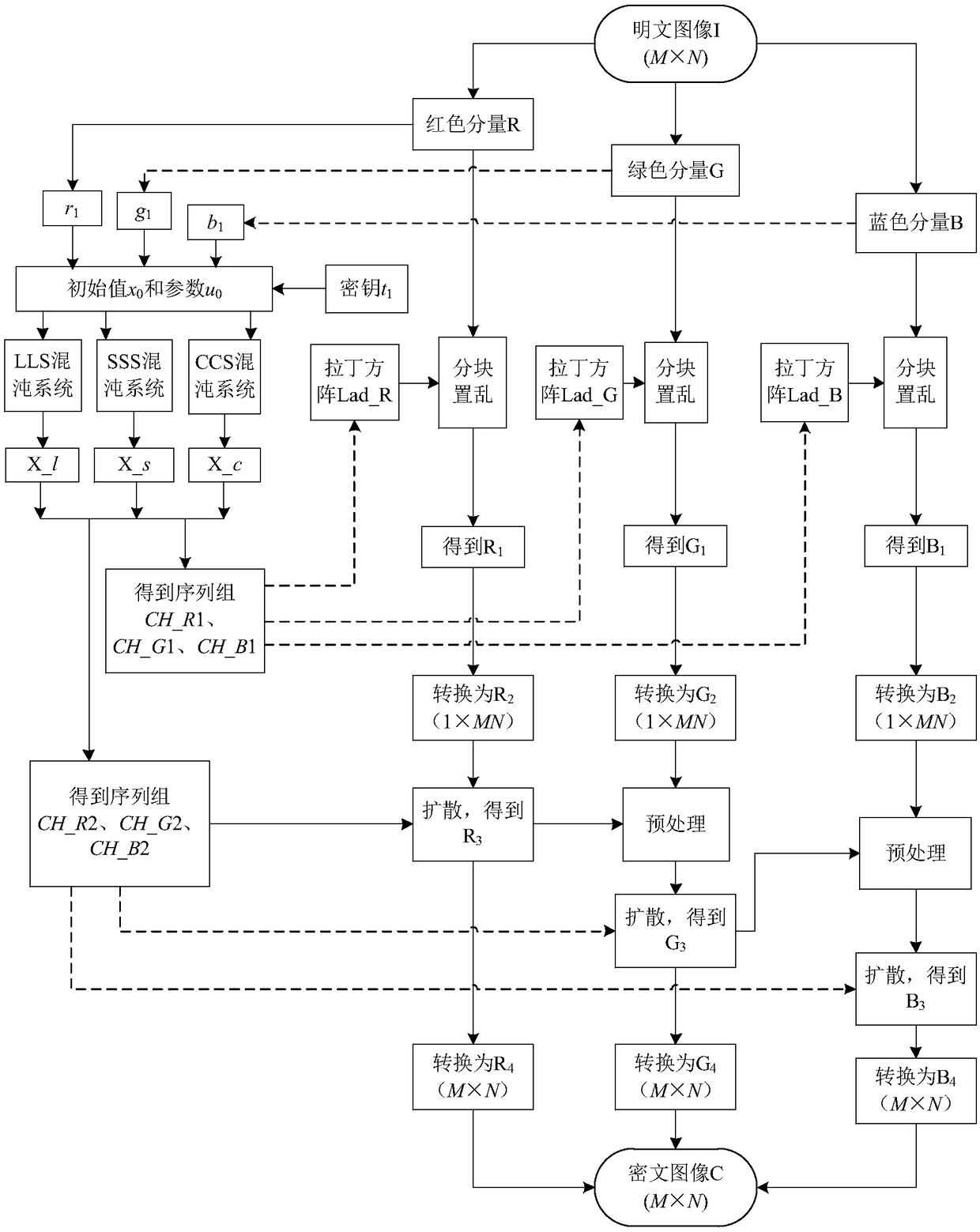
The invention relates to a color image encryption method based on Latin square scrambling. Plaintext keys r1, g1 and b1 are calculated through utilization of R, G and B components of a color plaintextimage, an initial value and a parameter obtained through calculation based on the keys are substituted into a chaotic system, and three groups of chaotic sequences are generated; the chaotic sequences for scrambling and diffusion are selected through utilization of a chaotic sequence selection mechanism based on the plaintext and digital arrangement; and a final ciphertext image is obtained through adoption of a block scrambling policy based on a Latin square and the chaotic sequences, and diffusion operation based on the plaintext and a scrambled image. The encryption method is closely related to the plaintext, so the plaintext attack resistance is improved. The employed chaotic system is an improved chaotic system, a chaotic characteristic is good, the randomness is high and a key spaceis great, so a security level is further improved. A simulation result and safety analysis show that according to the encryption provided by the invention, an image complete encryption demand can besatisfied, the encryption efficiency is high, and the robustness is high.
Owner:HENAN UNIVERSITY
Block chain distributed dynamic network key generation and encryption method
ActiveCN110719165AFew stepsEnsure safetyKey distribution for secure communicationFinanceProtocol for Carrying Authentication for Network AccessKey generation
The invention discloses a block chain distributed dynamic network key generation, encryption and decryption method, which comprises the following steps of: (1) generating and encrypting a key, initializing a network, and starting a key management protocol of a distributed dynamic self-organizing network; (2) after the key management protocol is started, counting the key encryption times, startingto accumulate the key generation and encryption times, updating a key encryption algorithm after the specified times are reached, and waiting for a new round of key generation and encryption operation; and (3) after the secret key is generated and encrypted, broadcasting a message generated by the secret key to the whole network for verification. In order to solve the problem that potential safetyhazards exist due to dynamic changes of a blockchain distributed network, a secret key management protocol is designed, generation and encryption of a secret key are managed, the efficiency of secretkey generation and encryption and decryption processes is guaranteed, an encryption method of an iterative encryption algorithm is designed for attackers to forcibly crack the secret key or launch replay attacks, secret key loss is reduced, and transaction information transmission safety is guaranteed.
Owner:HANGZHOU YUNXIANG NETWORK TECH
Quantum image encryption method based on image association dissection
InactiveCN103778593AImplement encryptionImprove securityImage codingImage data processing detailsArray data structureBinary tree
Disclosed is a quantum image encryption method based on image association dissection. A quantum-state superposition and measurement principle is used to establish correlation between image pixels. An image is dissected into superposition of a series of characteristic sub-images. Conversion operations are performed on the characteristic sub-images stored in a complete binary-tree digit group through use of a random phase door and a quantum rotating door and then a plurality of superpositions are performed on all the images through quantum-state superposition so as to obtain a cipher image. Schmidt orthogonal dissection is performed on the quantum random phase door, the quantum rotating door, a coefficient matrix and the cipher image so as to obtain a standard orthogonal ground state which is then used as a key. The quantum image encryption method based on the image association dissection has a larger key space so that strong attacks can be resisted and combination of a quantum-mechanical theory and an image encryption technology is realized. The method has classical information theory security and quantum information theory security so that quantum image encryption surpasses restriction of classical image encryption and compared with classical images, quantum images are higher in security.
Owner:NANCHANG UNIV
Method for generating verification codes as well as method and detection for verification
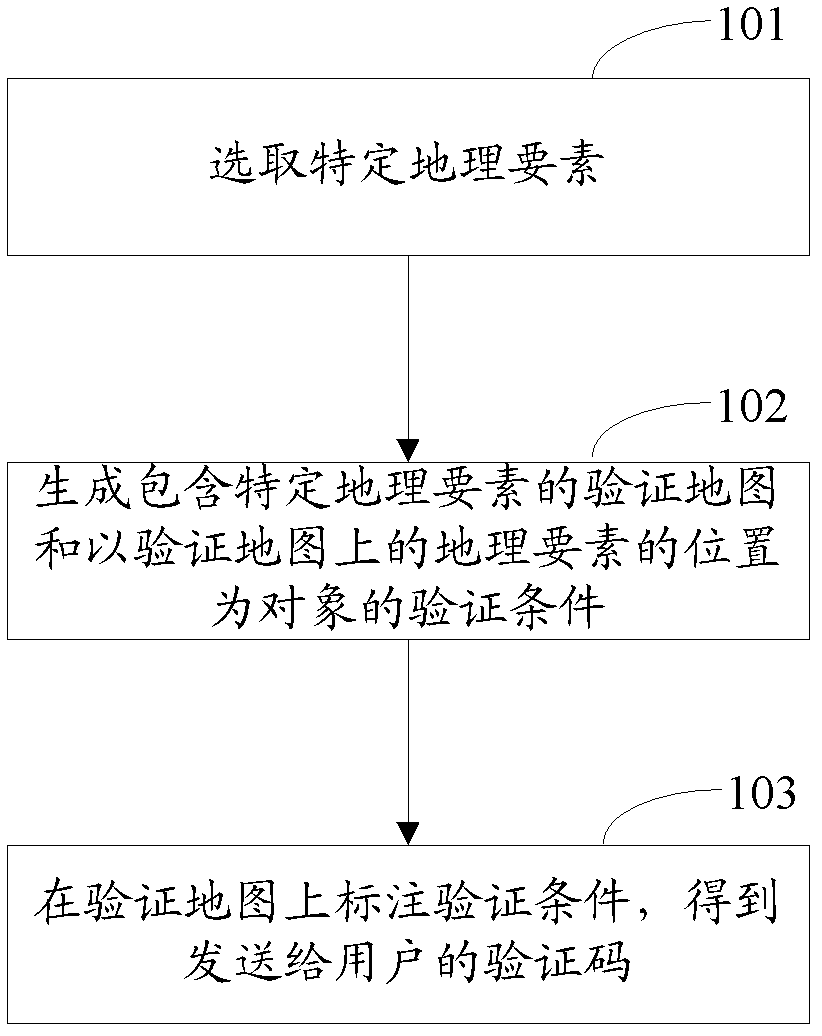
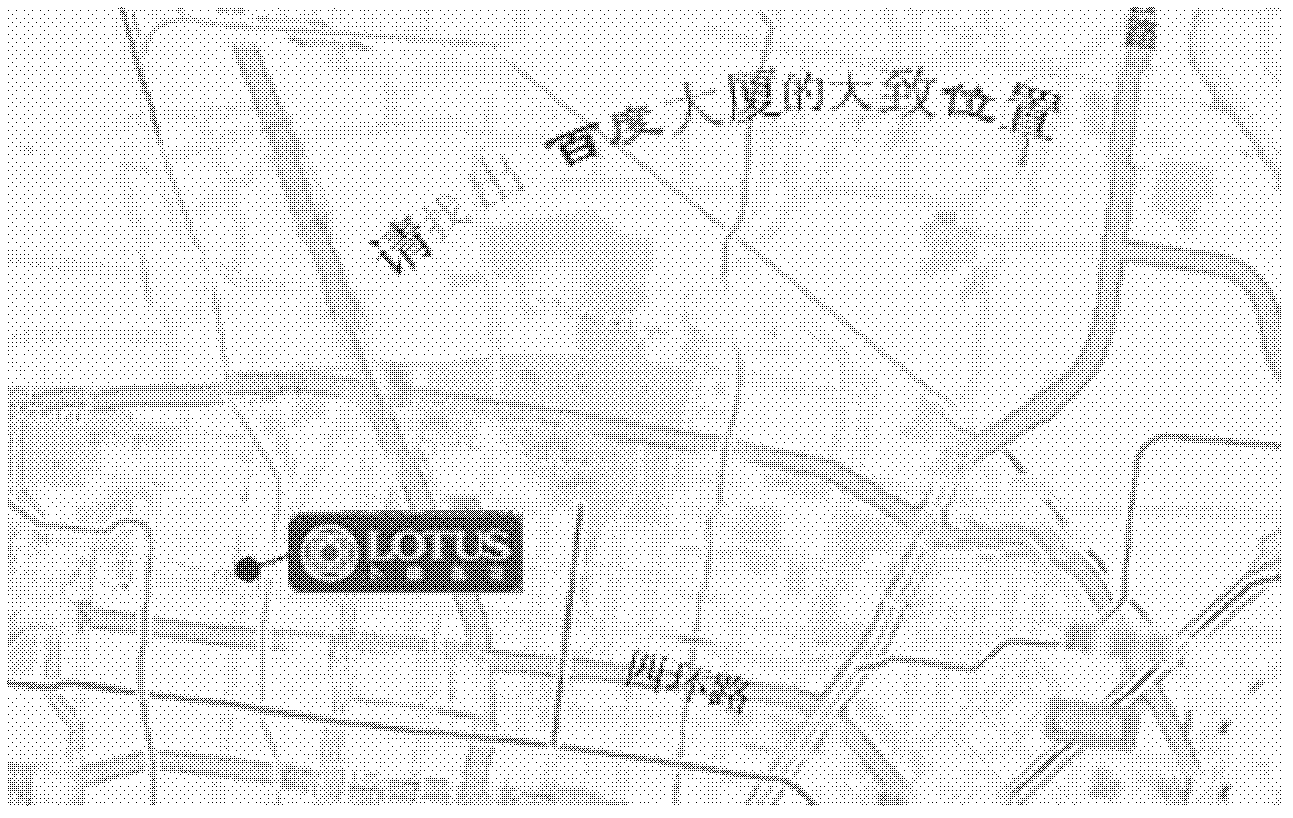
ActiveCN102360409AIncrease the difficultyImprove resistance to attack2D-image generationDigital data authenticationComputer science
The invention provides a method for generating verification codes as well as a method and device for verification, wherein the method for generating the verification codes comprises the following steps of: selecting specific geographic elements; generating a verification map containing specific geographic elements and a verification condition taking the positions of the geographic elements on the verification map as an object; and obtaining the verification codes sent to a user by labeling the verification condition on the verification map. By virtue of the mode, the attack resistance of the verification codes can be effectively enhanced.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Wavelet domain-based method for weighting fractional differential image digital watermark
InactiveCN102129655AOvercoming cracking problemsImprove securityImage data processing detailsFractional differentialImaging processing
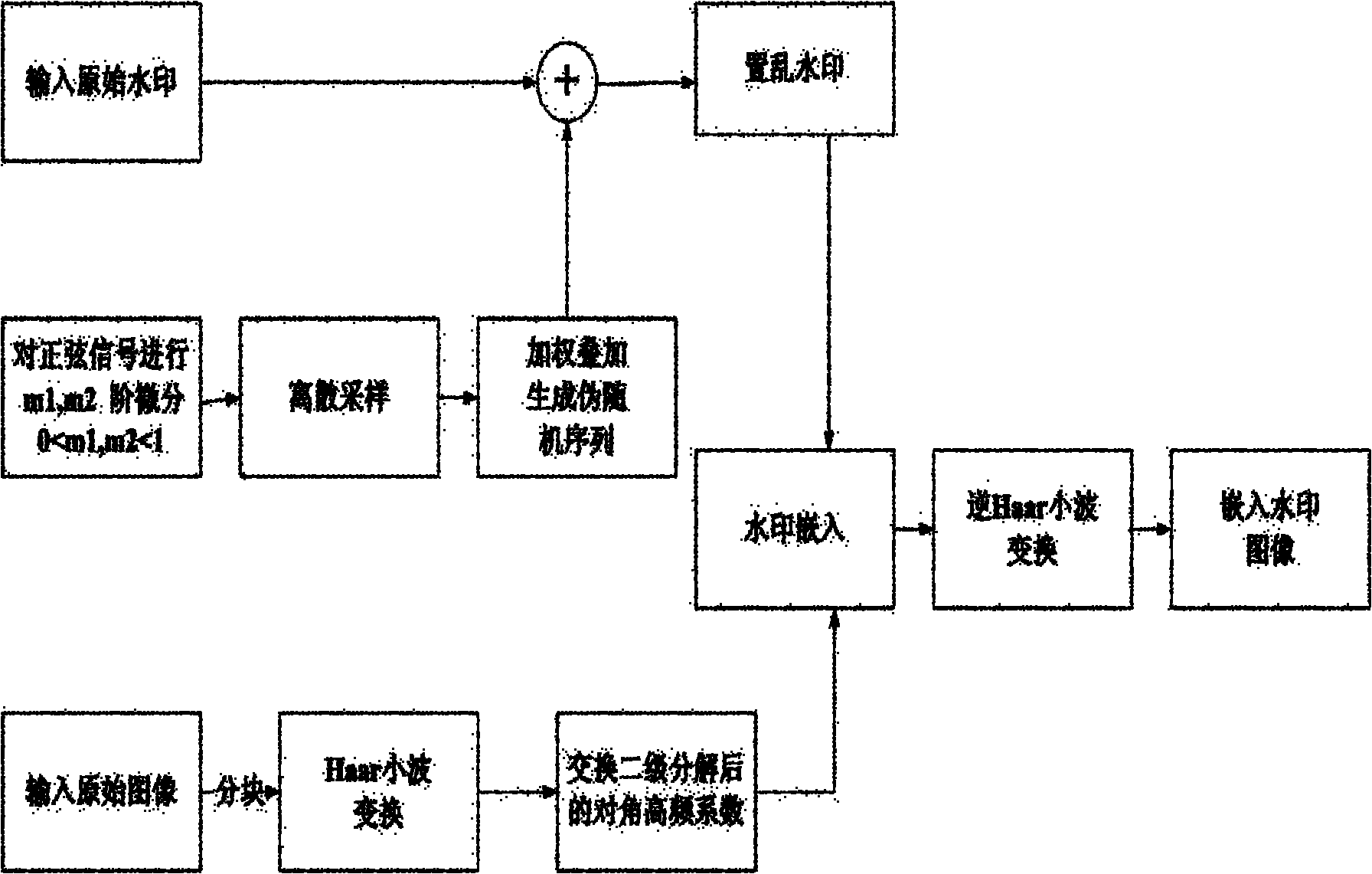
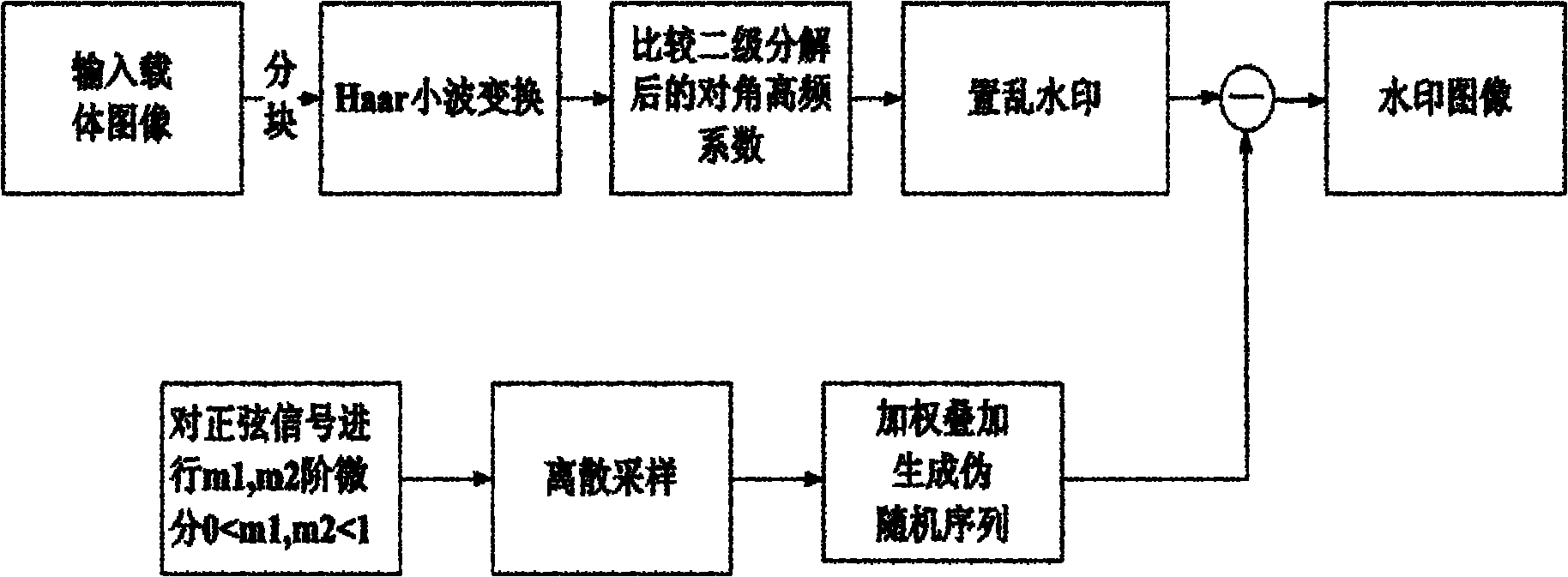
The invention provides a wavelet domain-based method for weighting a fractional differential image digital watermark, which mainly solves the problem that the high-frequency coefficient of an image undergoing wavelet decomposition is susceptible to extraneous noises and conventional image processing. The method comprises the implementation steps of: doing two different orders of differentials for a sinusoidal signal by utilizing a fractional order Cauchy formula; respectively carrying out discrete sampling and superposing by utilizing a given weight to generate a pseudorandom sequence and adding the pseudorandom sequence with a watermark pixel value to realize watermark scrambling; carrying out two-stage decomposition on a carrier image by utilizing a Haar wavelet and embedding the scrambled watermark information in the carrier image through the exchanged and decomposed high-frequency coefficient; and through comparing the high-frequency coefficient undergoing the two-stage decomposition by utilizing the Haar wavelet, extracting the scrambled watermark and subtracting the pseudorandom sequence to realize watermark recovery. The method provided by the invention has the advantages of strong anti-attack ability and good safety of the image, and can be applied to copyright protection, restriction of illegally spreading audiovisual products, individual privacy protection, identification hiding and high-tech crime prevention.
Owner:XIDIAN UNIV
Method implementing conditional reception and conditional receiving apparatus
InactiveCN101335579AAchieve descramblingEnsure safetyBroadcast systems controlComputer hardwareConditional access systems
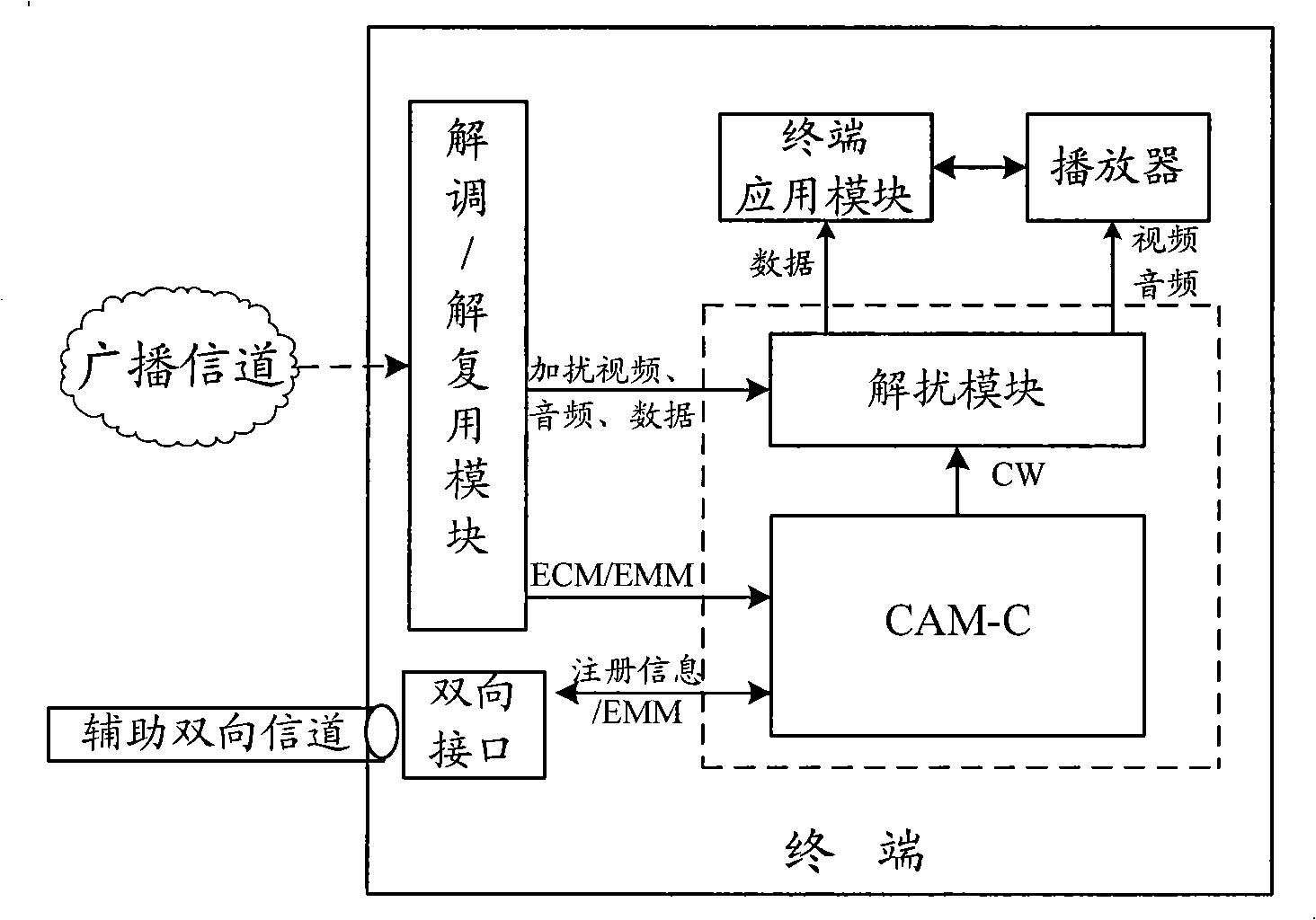
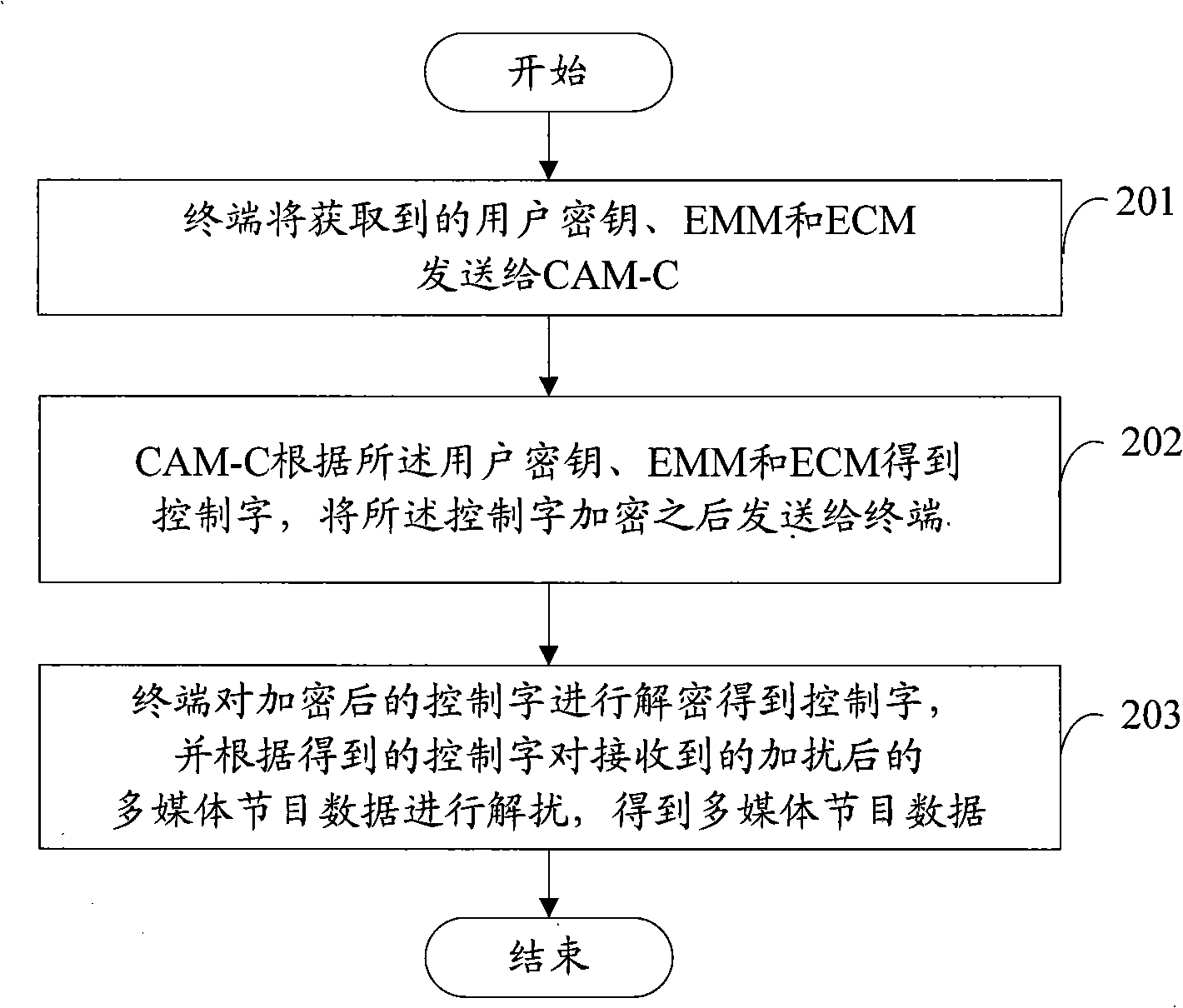
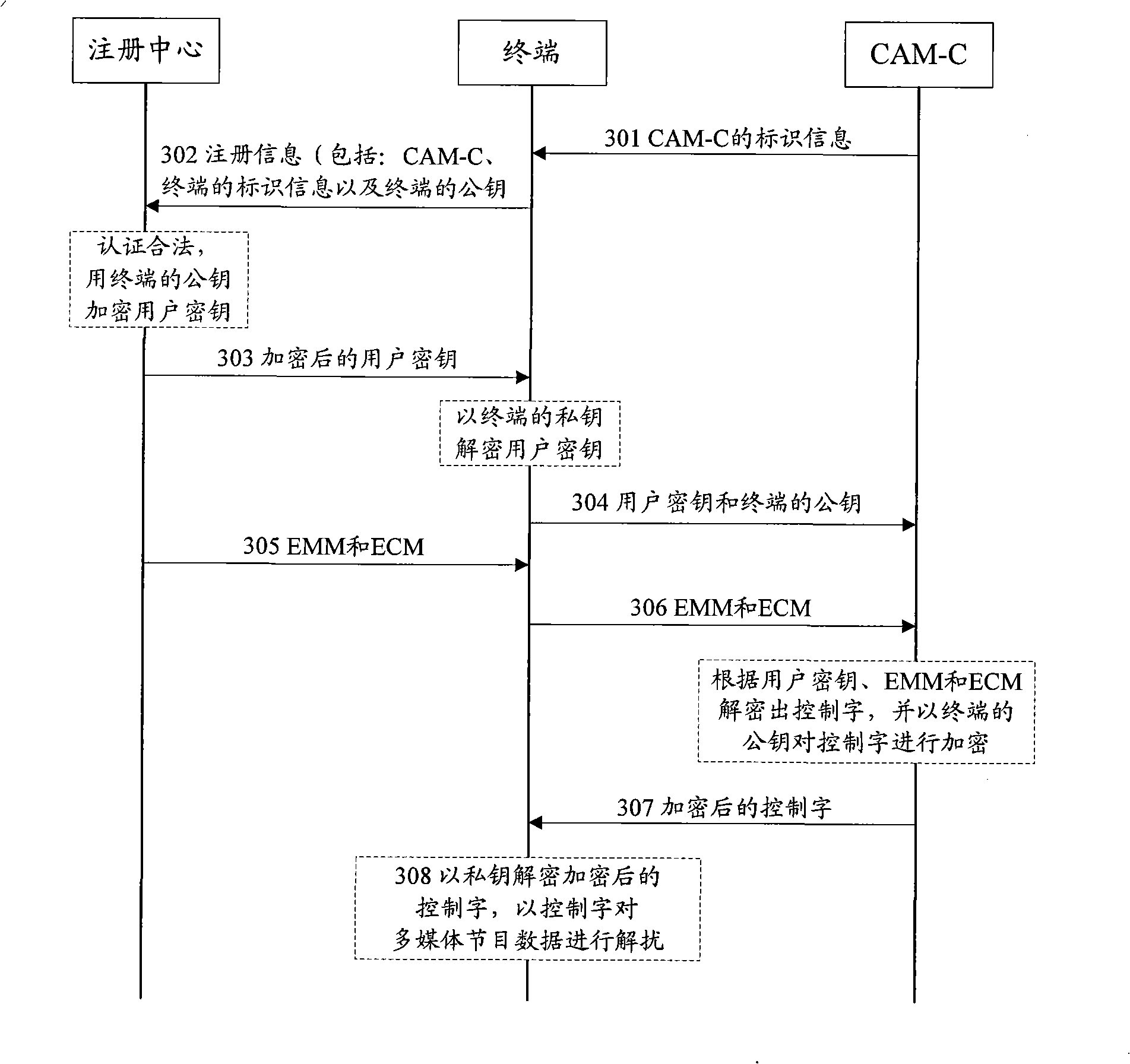
The invention discloses a method of realizing conditional access. The method includes the following steps: a terminal sends an acquired user key, an entitlement management message (EMM) and an entitlement control message (ECM) to a Conditional Access Module-Card (CAM-C); the CAM-C acquires a control word according to the user key, EMM and ECM, and sends the encrypted control word to the terminal after encrypting the control word; the terminal decrypts the encrypted control word to acquire the control word, and carries out descramble to the received scrambled multimedia program data according to the control word to obtain the multimedia program data. The invention also discloses a conditional access device. The use of the invention can realize the function of conditional access, and ensure the safety of conditional access system.
Owner:INNOFIDEI TECHNOLOGIES INC
Intelligent control water meter
InactiveCN101963520AChange classic modeEliminate troubleVolume meteringMagnetic tension forceElectricity
The invention relates to an intelligent quantitative control water meter. When a valve in the water meter is opened by separating magnets which attract with each other, energy required by closing a valve is registered in the displacement of the magnets generated when the valve is opened; magnetic force is used for quantitative control when the magnets are far away from each other and magnetic attraction force is weak, and the magnetic attraction force is used as power for closing the valve when the magnets are close to each other and the magnetic force is strong; the water meter has a unified measurement reading which conforms to the purpose of legislation of the metrology law; water supply and power supply are alternately performed, normal water supply is performed without the power supply, and the valve is automatically closed without electric energy when a quota is finished; a circuit is electrified for short time to intelligently judge, a motor in the meter is conditionally started and the valve is opened to recover the water supply; and the water meter is provided with an internal locking device for preventing the water meter from being illegally and nondestructively opened or disassembled. The intelligent quantitative control water meter has the advantages of simpleness, stability and reliability. The problems of the measurement, charging, management and measurement law of the intelligent water meter and a remote water meter caused by the conventional non-electrical quantity electrical testing technology are radically solved in a mechanical quantization and electronic equipment power-off working mode.
Owner:杨启梁
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com