Method for identifying DNS spoofing attack packet and detecting DNS spoofing attack
A technology for DNS spoofing and attack packets, applied in the field of identifying DNS spoofing attack packets and detecting DNS spoofing attacks, can solve problems such as spoofing attacks, and achieve the effect of improving attack resistance and high practical value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
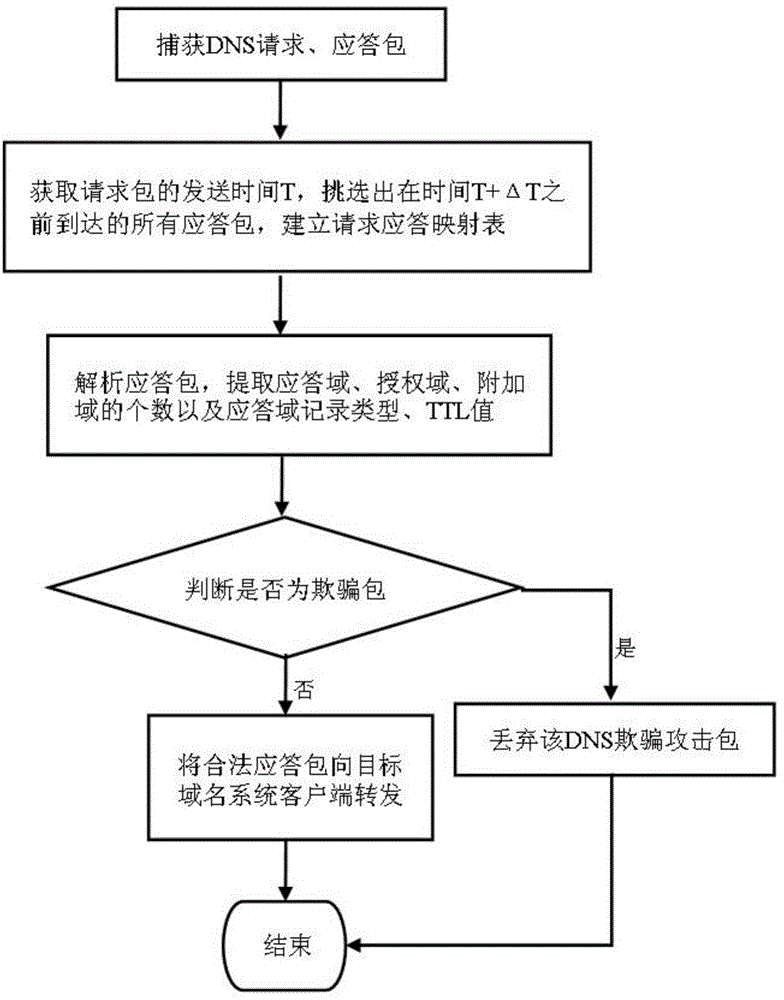
[0020] In order to make the above objects, features and advantages of the present invention more obvious and understandable, the present invention will be further described below through specific embodiments and accompanying drawings.
[0021] Normally, after receiving the response message returned by the upper-level DNS server, the local DNS server will process the message as follows:
[0022] Check whether the destination port of the response message is equal to the source port of the DNS request message. If not, it means that it is not a response to the request, and the protocol stack will discard the data message;
[0023] Check the problem domain of the response message, that is, make sure that the domain name of the request in the response packet is consistent with the domain name in the request packet;
[0024] Check the transaction ID (TID) of the response message. A TID will be included in the query request sent by the DNS server to identify a certain query. The TID w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com