Method of application program for prevention illegal update mobile terminal
An application program and mobile terminal technology, applied in the field of communication, can solve the problems of harming the mobile phone market, destroying mobile phones, etc., and achieve the effects of increasing anti-attack capabilities, ensuring security, and broad versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The specific implementation manners of the present invention will be described in detail below with reference to the accompanying drawings.
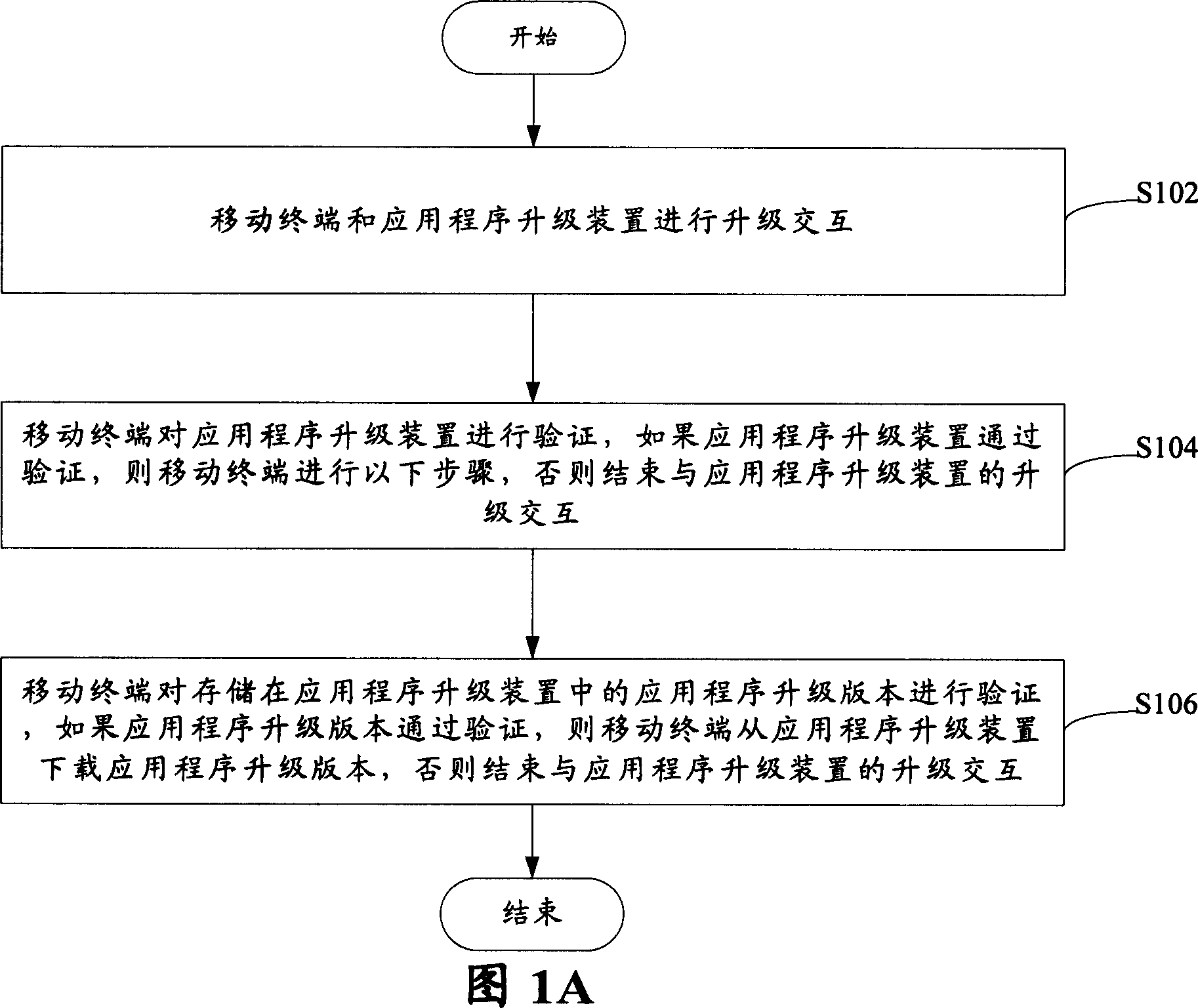
[0018] The invention adopts the encryption algorithm and combines the communication ability of the mobile phone to propose a new method for preventing the application program of the mobile terminal from being illegally upgraded.
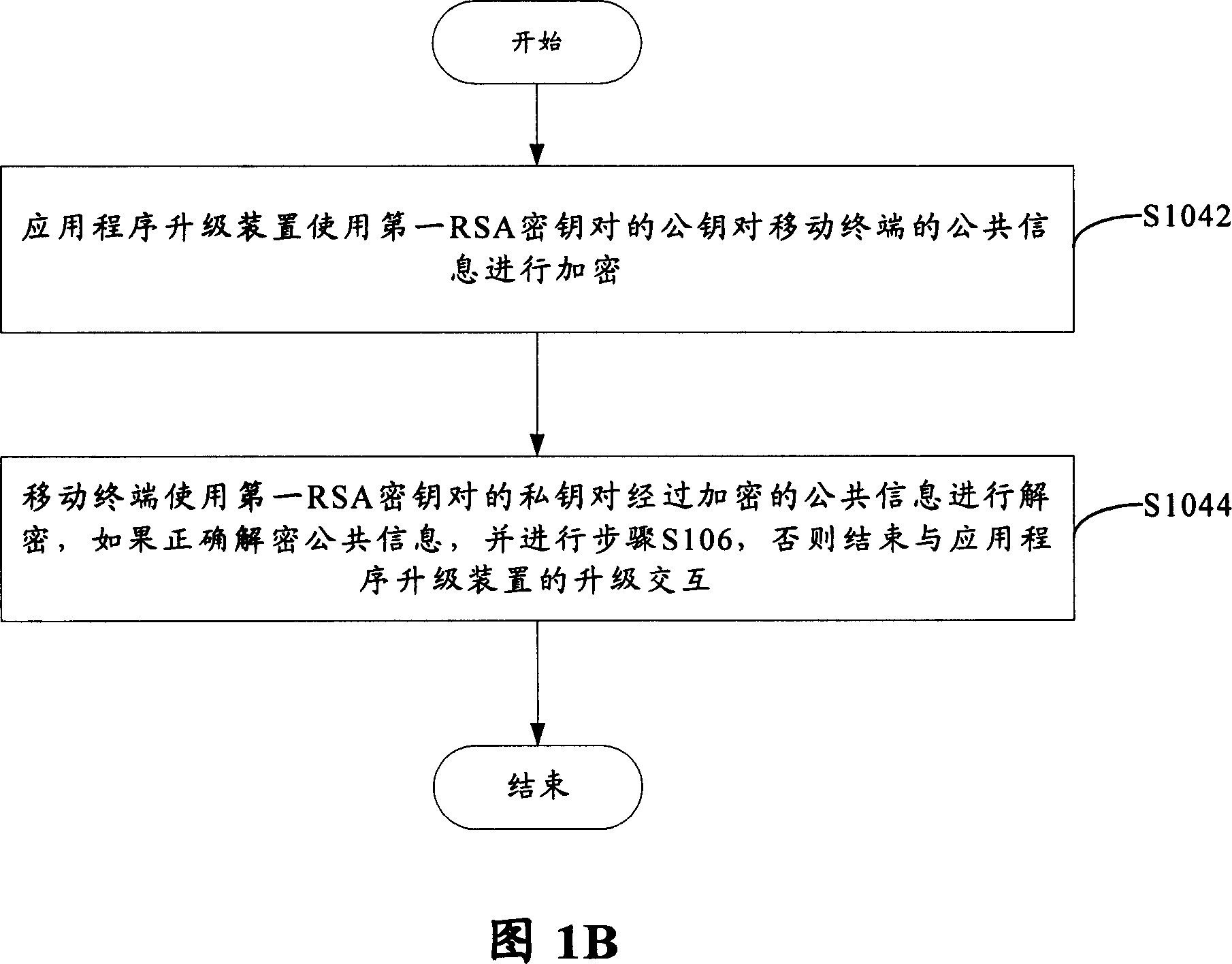
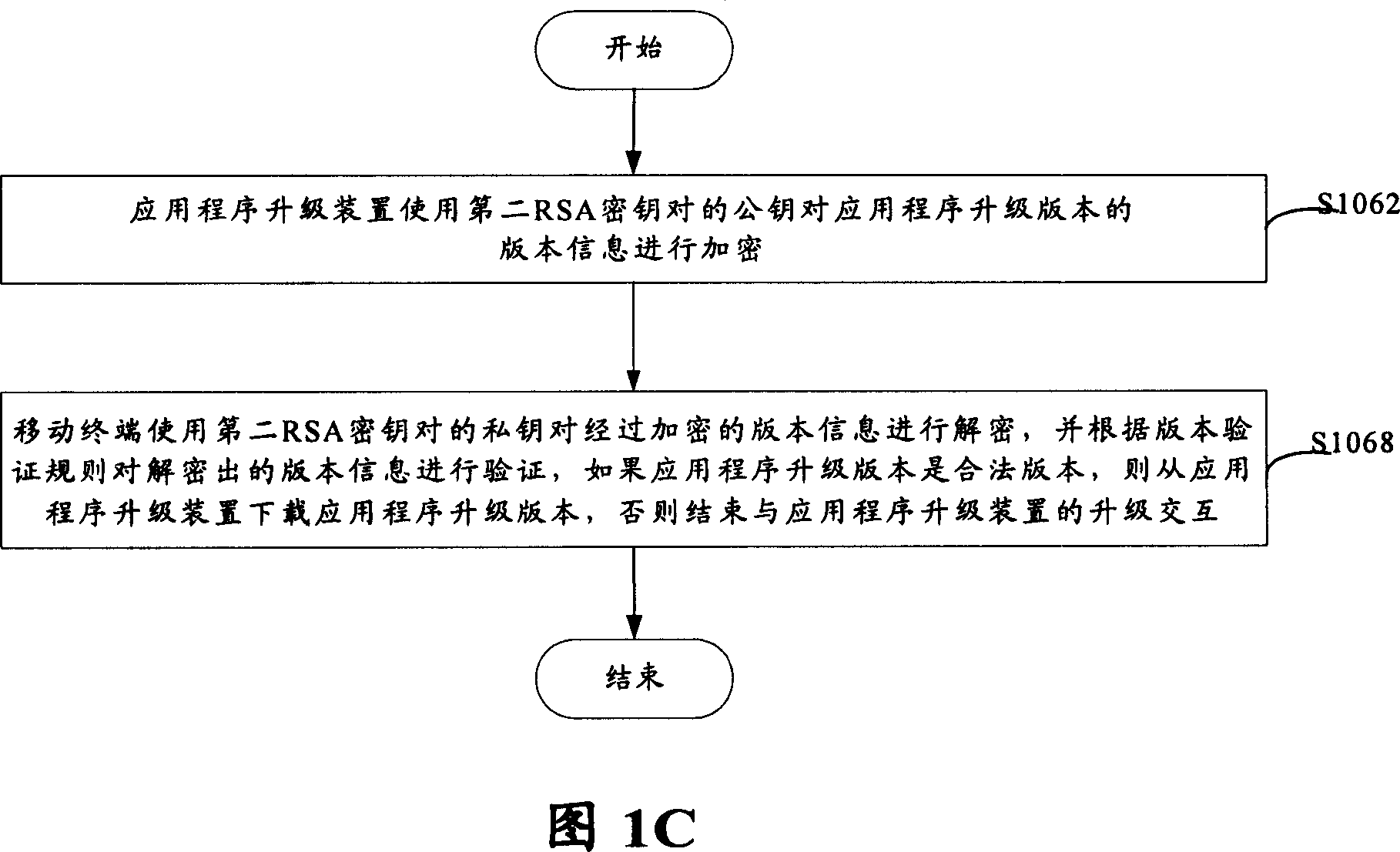
[0019] The RSA encryption algorithm is a public key infrastructure (PKI for short) technology, which is an asymmetric algorithm based on a public key, which uses two very large prime numbers to generate completely different public keys (ie , the encryption key) and the private key (ie, the decryption key). Using the RSA algorithm for encryption and identity verification has a high ability to resist attacks. Introducing this algorithm into the mobile phone for security design can greatly improve the security performance of the mobile phone.
[0020] FIG. 1A to FIG. 1C show a flow chart of a method for pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com