Method for detecting user to make malicious IP scanning
A user, malicious technology, applied in the direction of digital transmission system, data exchange network, electrical components, etc., can solve the problem of not detecting malicious users and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
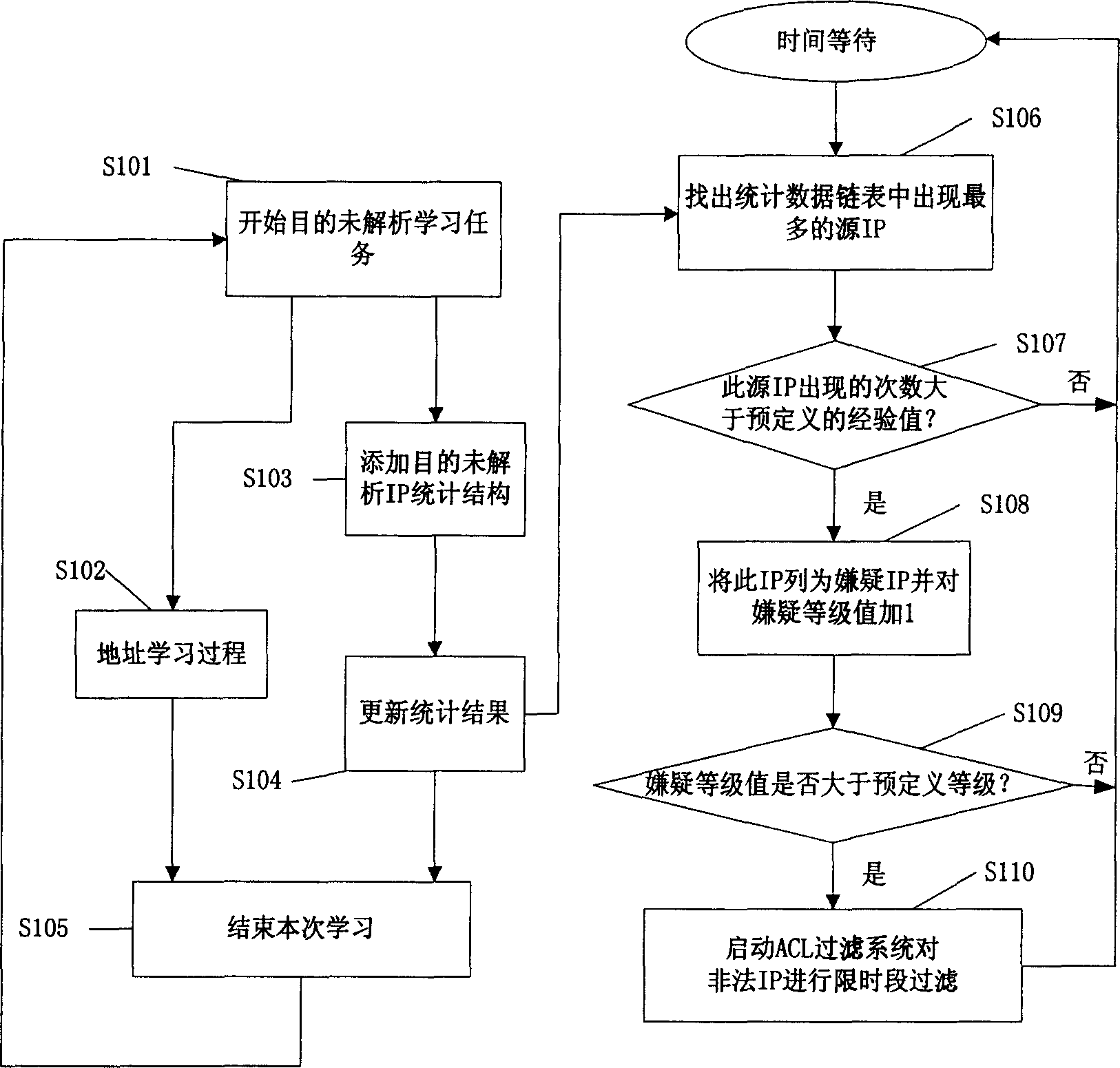
[0017] figure 1 It is a flow chart of a method for detecting users who scan malicious IP addresses according to a preferred embodiment of the present invention. like figure 1 As shown, in a preferred embodiment of the method for detecting and scanning users with malicious IP addresses according to the present invention, in order to detect malicious attacks, the process of learning the destination IP is firstly modified. The traditional purpose IP address learning task is only after starting the purpose unresolved learning task (step s101), after simply performing IP address learning (step s102), and then ending the current learning task (step s105).
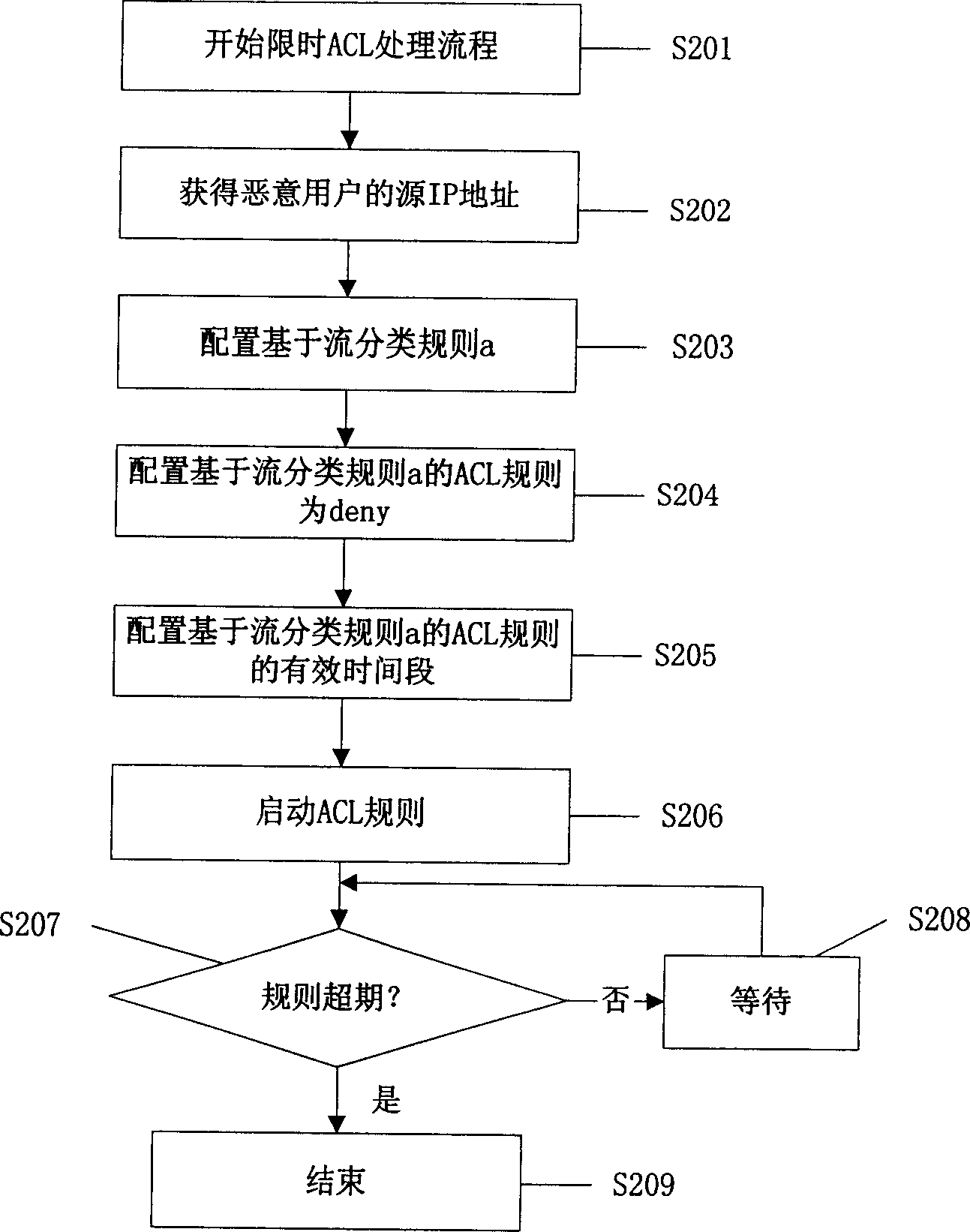
[0018] In order to detect the attack, it is necessary to collect statistics on the IP addresses in the current specified time slice while learning the IP addresses, so as to find the IP address...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com