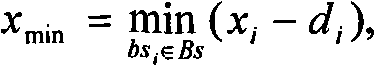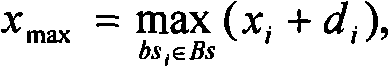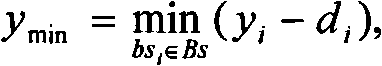Safe positioning method for wireless sensor
A wireless sensor and secure positioning technology, applied in radio/inductive link selection arrangement, secure communication device, transmission system, etc., to achieve the effect of improving anti-attack capability, no need for key management, and resisting known attacks
Active Publication Date: 2008-11-19
XIDIAN UNIV
View PDF0 Cites 31 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
The purpose of the present invention is to solve the deficiencies of the existing security positioning methods, fully investigate the characteristics of the sensor network and node positioning mechanism, and propose a wireless sensor security positioning method, which improves the anti-attack ability of the sensor itself by filtering out malicious beacons
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention discloses a safe positioning method for a wireless sensor; the safe positioning method adopts two safe positioning methods which are the malicious beacon detection based on the checkpoint and the malicious beacon detection algorithm based on the regional voting mechanism to solve the positioning safety problem of the sensor network nodes. The positioning method improves the anti-attack capability of the system through filtering the malicious beacons directly so that not only the known attacks can be defended, but also the unknown attacks can be defended; the corresponding defending measurement for every possible specific attack is avoided; the implementation of the safety strategy of the positioning system is simplified; the two detection methods are combined effectively to adjust the defending strategy automatically according to the attack types; the safe positioning is guaranteed and the computation cost is reduced effectively; the neighbor communication authentication technique based on the unidirectional key chain is adopted to avoid the support of other network safety protocols so that the storage cost of the sensor nodes is reduced; the neighbor communication authentication technique can be compatible and used together with the present wireless sensor network protocol; the safety target of the positioning system of the sensor network nodes is realized.
Description
technical field The invention belongs to the technical field of network communication, and relates to wireless self-organizing network security technology. Specifically, based on the verification of internal and external consistency of beacons, a secure wireless sensor network node positioning method is proposed to solve the security problem of node positioning in sensor networks. , that is, how the node can correctly obtain its own geographic location information after being randomly deployed to prevent various internal and external attacks against the node positioning system. Background technique Wireless sensor network is a wireless multi-hop network composed of a large number of micro, low-cost, low-power sensor nodes deployed in the monitoring area, which realizes the collection, processing and publishing of sensitive data in the monitoring area. Sensor networks have many advantages such as rapid deployment, cooperative perception, and high fault tolerance, so they have...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): H04L9/36H04Q7/38
Inventor 马建峰叶阿勇裴庆祺沈玉龙庞辽军赵锟曾勇刘家佳李兴华王超杨力毛立强杨超
Owner XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com