Industrial control network security protection method and system
An industrial control network and security protection technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as high requirements for software virus databases, inability to meet industrial control network requirements, and complex monitoring equipment. The effect of anti-attack ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
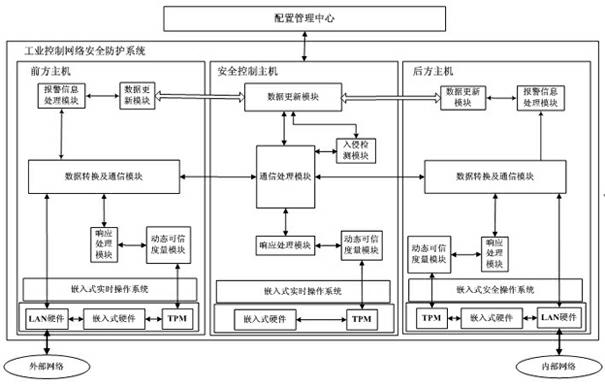
[0032] Embodiments of the present invention: an industrial control network security protection method adopts a 3-host structure and a three-layer protection strategy, comprising the following steps:
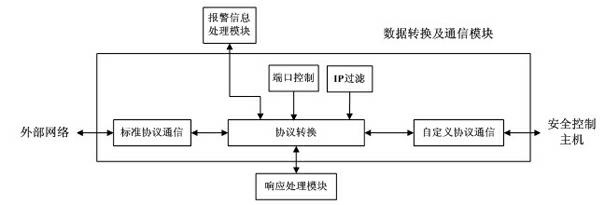
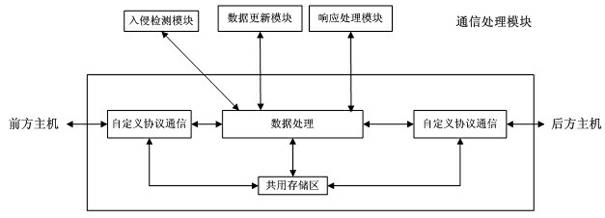
[0033] In response to external network attacks, the front host performs first-level data filtering and access control on external network communication data, and filters illegal access. Alarm and notify the hosts on both sides, the rear host performs in-depth filtering and access control on the data, and legal data enters the internal network;
[0034] In response to internal network attacks, the rear host performs first-level data filtering and access control on internal network communication data to filter access by illegal identities. The security control host caches data through a shared storage area, detects intrusion of data, and timely monitors illegal data. Alarm and notify the hosts on both sides, the front host performs in-depth filtering and access control on the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com