Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
87results about How to "Information security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
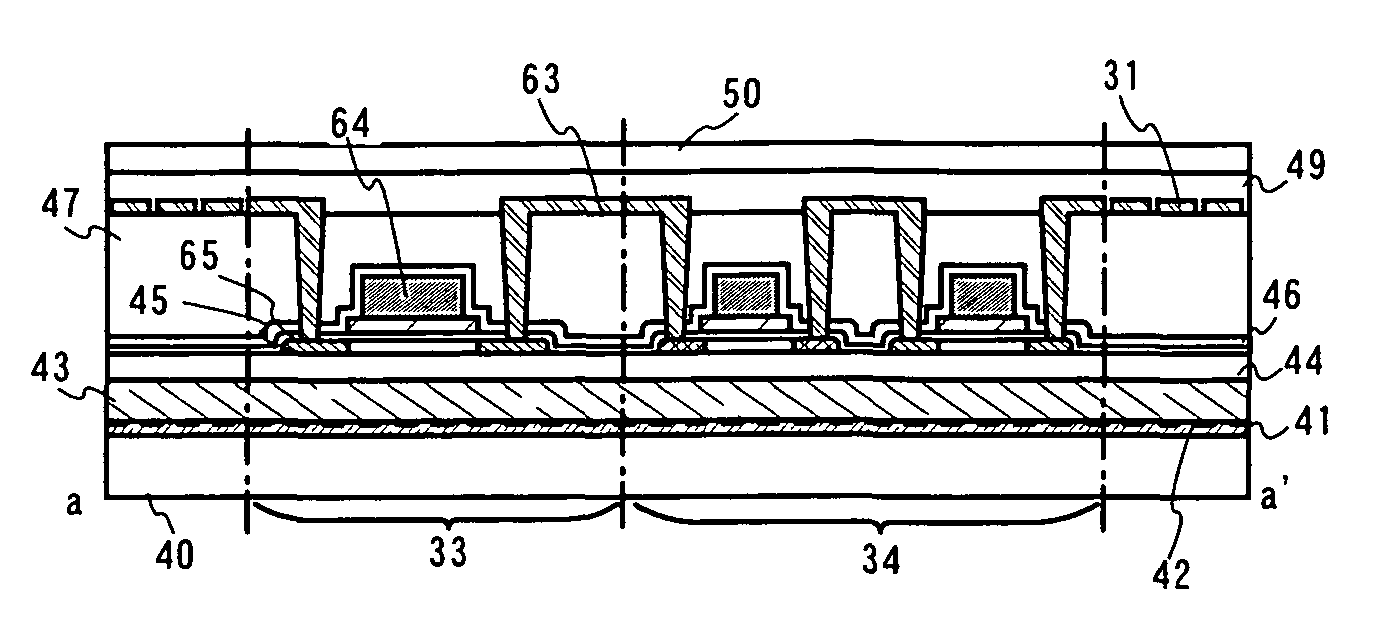
Embedded device, control method therefor, program for implementing the control method, and storage medium storing the program
InactiveUS20060059462A1Easily and flexibly expandableSecuring privacy and securityWeb data retrievalNatural language data processingImaging processingWeb browser
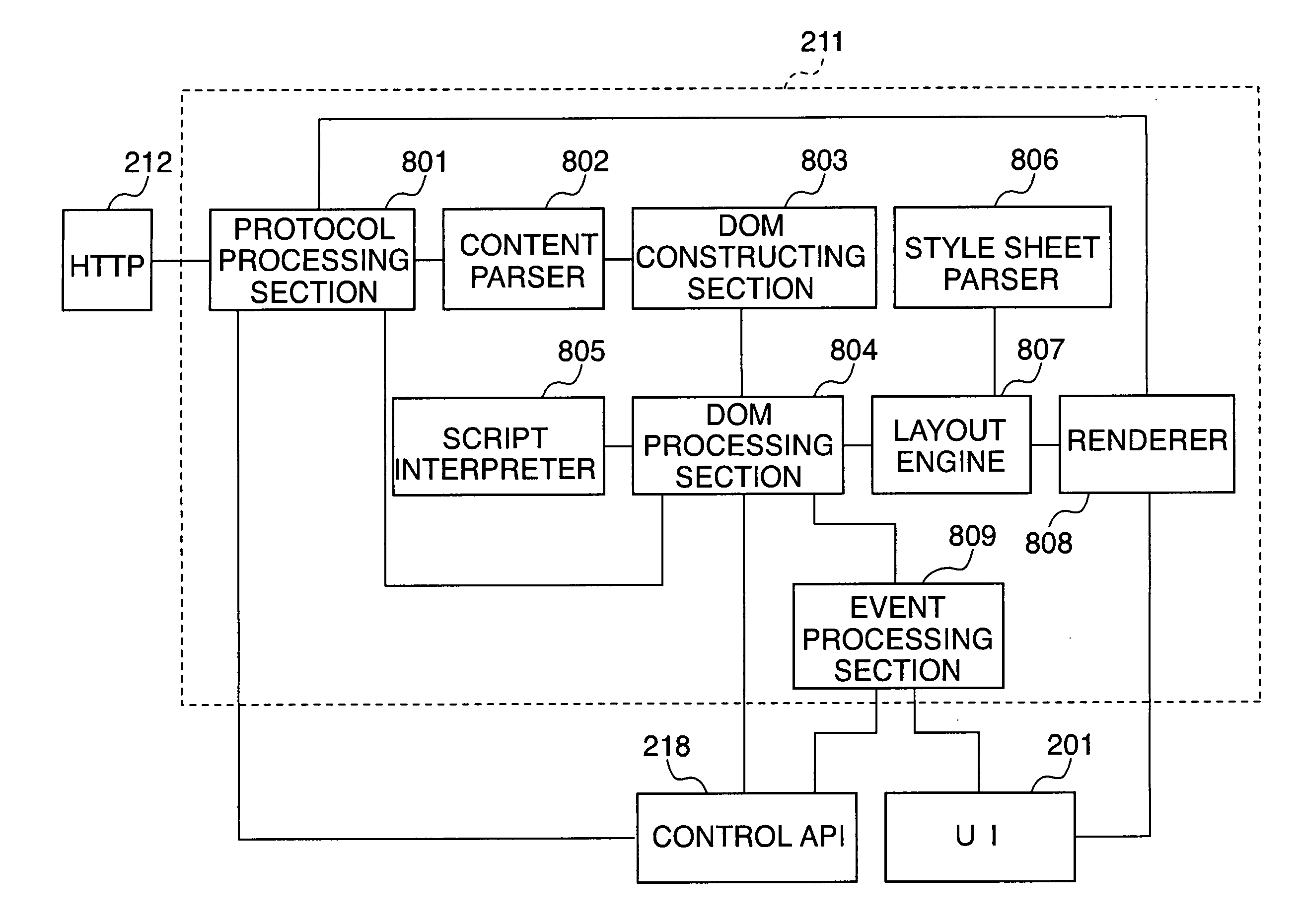
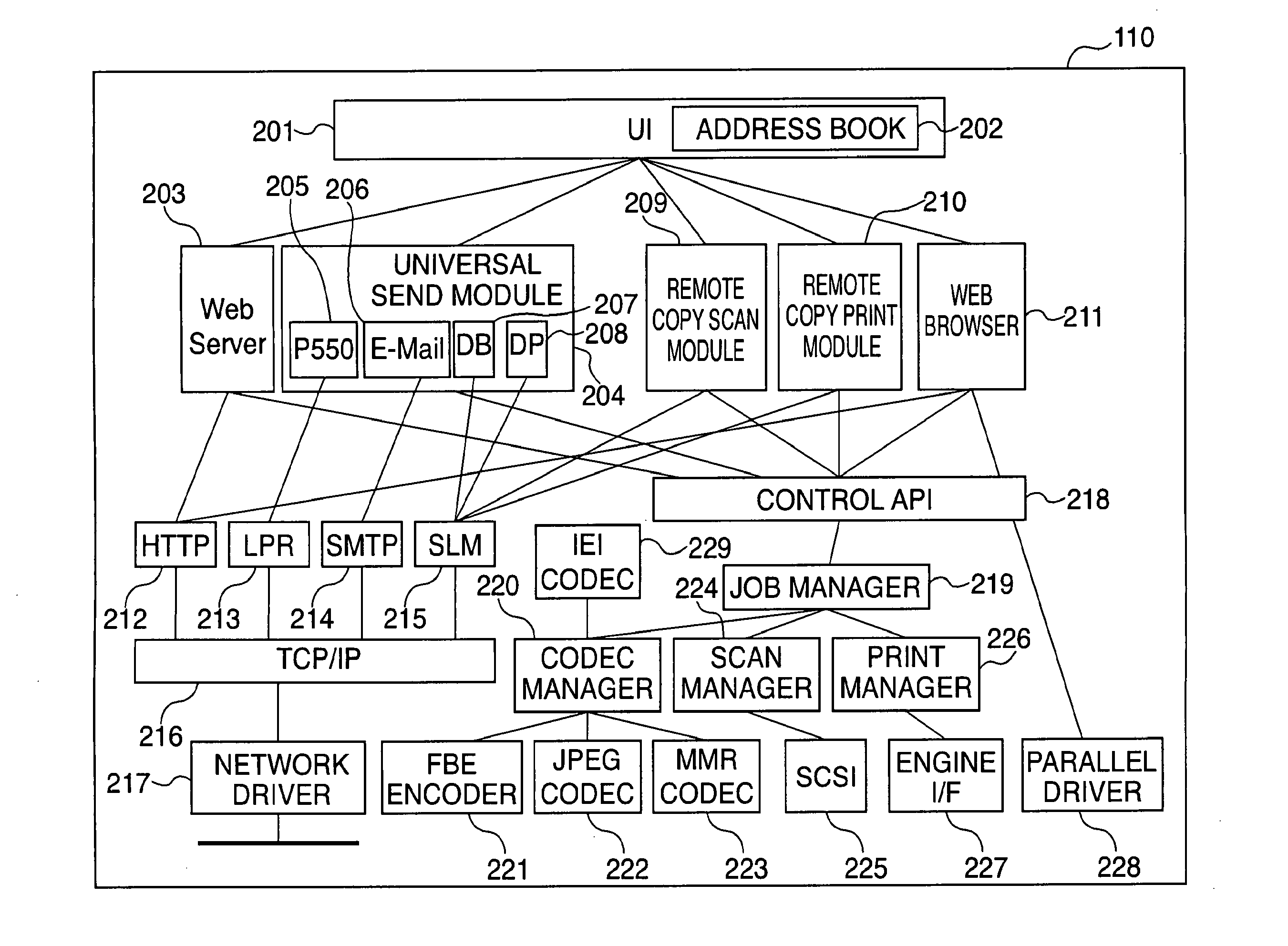
An embedded device incorporating a Web browser, which enables a server to provide a dynamic content adapted and linked to a function specific to the embedded device and a status of the same, as an easily and flexibly expandable service in response to access from the embedded browser, and enables securing privacy and security of information on a client. In an image processing apparatus (110) implementing the embedded device, a Web browser module (211) loads Web content data containing at least document data which is described in a markup language and has a script or information for reference to a script embedded therein, and performs presentation based on the loaded Web content data. A controller unit (111) controls information and operation of the image processing apparatus. A script interpreter (805) incorporated in the Web browser module interprets the document data contained in the loaded Web content data and processes the script or the information for reference to a script embedded in the document data. A control API module (218) provides an interface via which the script interpreter gains access, based on the processing of the script, to a DOM managed in the Web browser module. Further, the control API module provides an interface via which the script interpreter gains access, based on the processing of the script, to the information and operation of the embedded device, controlled by the controller unit.
Owner:CANON KK
Securing sensitive information with a trusted proxy frame
InactiveUS20120089481A1Rapid deploymentInformation securityDigital data processing detailsUser identity/authority verificationThird partyInternet privacy
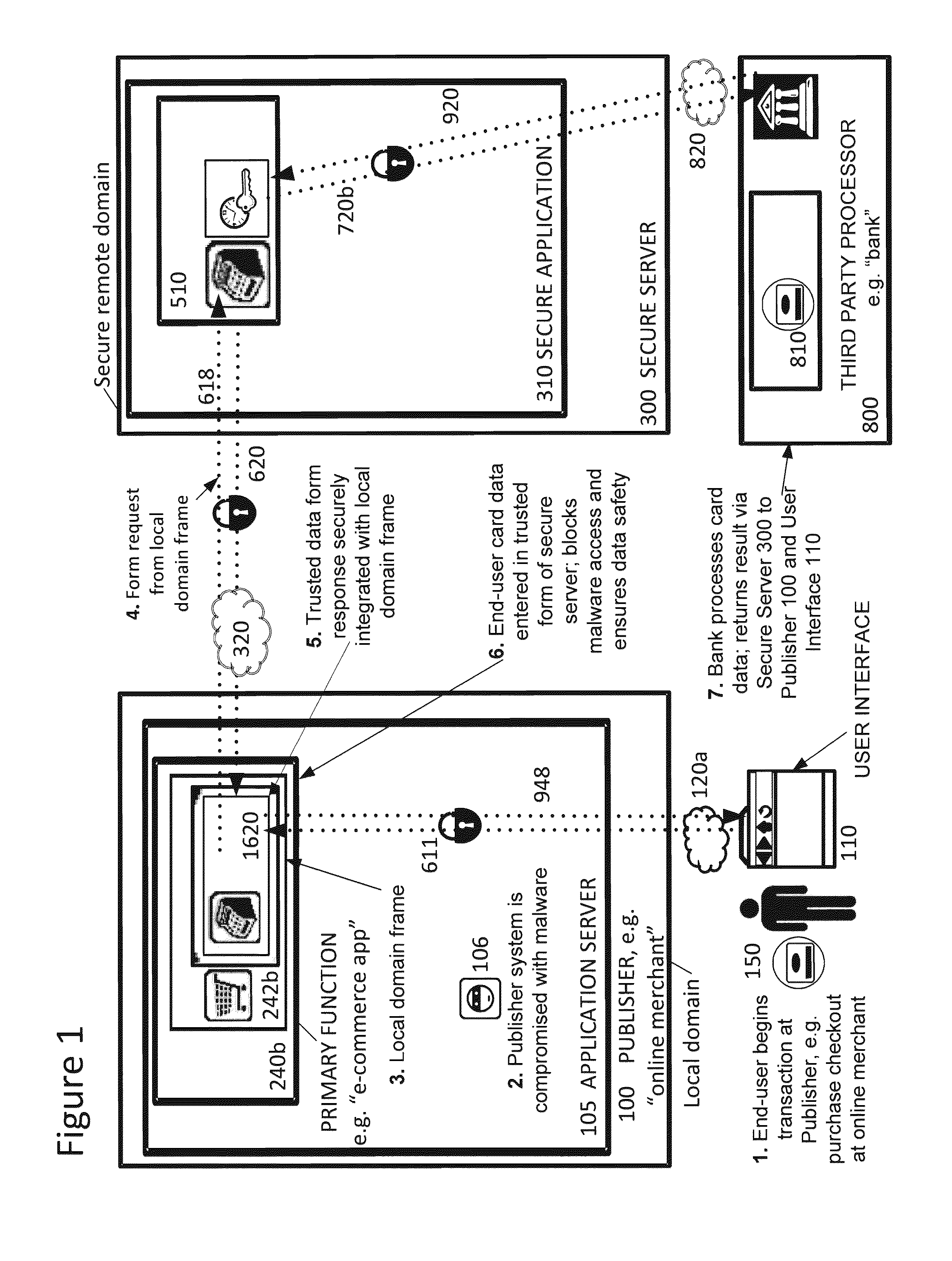
A system and method for secure transmission of sensitive end user information from an Internet portal operated by a publisher to a third party data processor. The publisher provides a content portal such as an e-commerce or healthcare information site. A third party data processor such as a bank or healthcare organization requires the sensitive information for a data processing function. In response to the requirement for sensitive information, a trusted proxy frame is invoked from a secure server operative to securely communicate the sensitive information. The trusted proxy frame is displayed in a secure context in the end user's browser and receives input of the sensitive information. The sensitive information is encrypted and communicated through the secure server to the third party data processor. Results of this processing are transmitted to the publisher through a novel callback process that enables the publisher to execute its data processing functions, as if it was in possession of the sensitive information, but without actual access to the sensitive information. The third party data processor returns an acknowledgement of processing of the sensitive information.
Owner:CHAIN REACTION ECOMMERCE
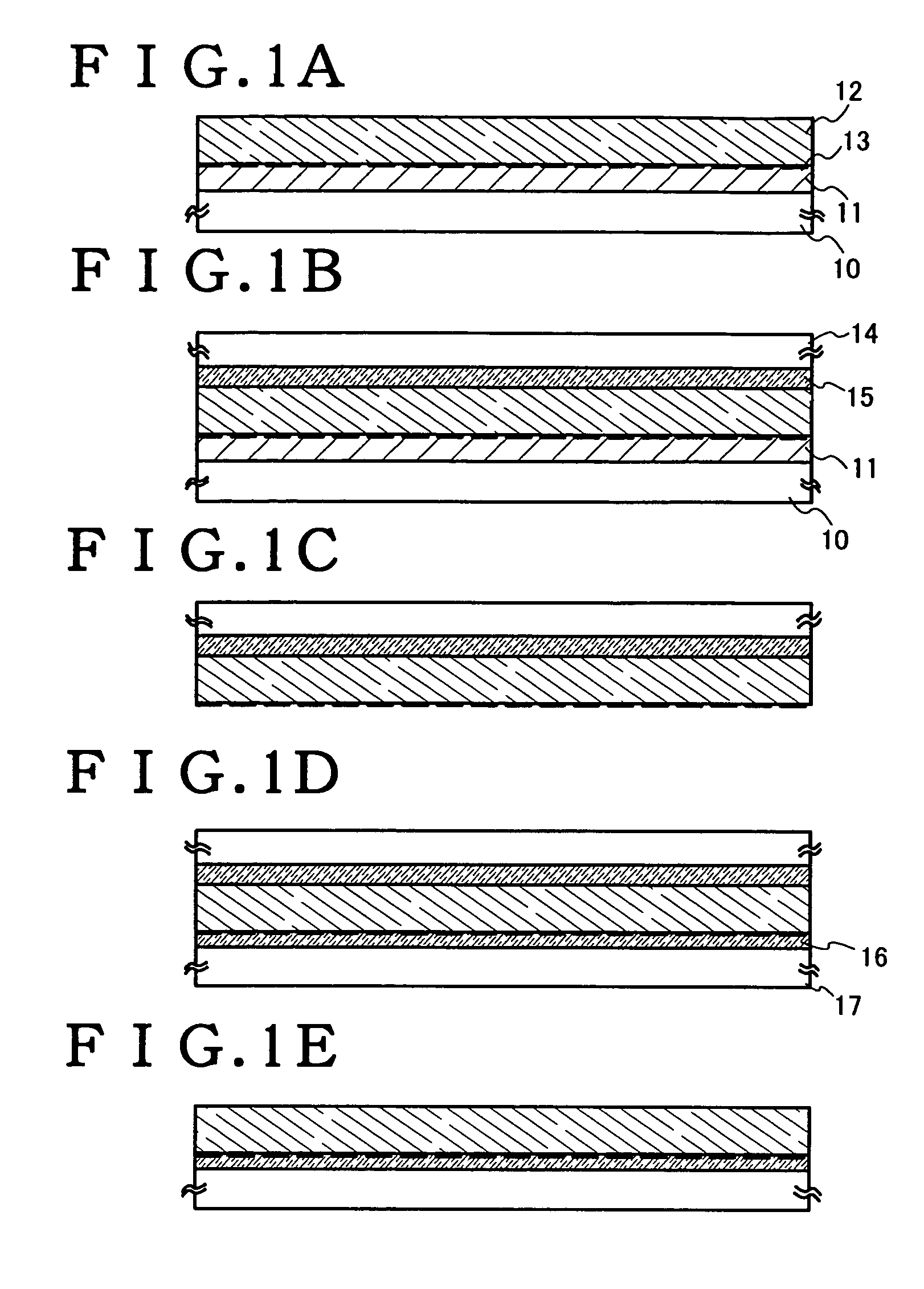
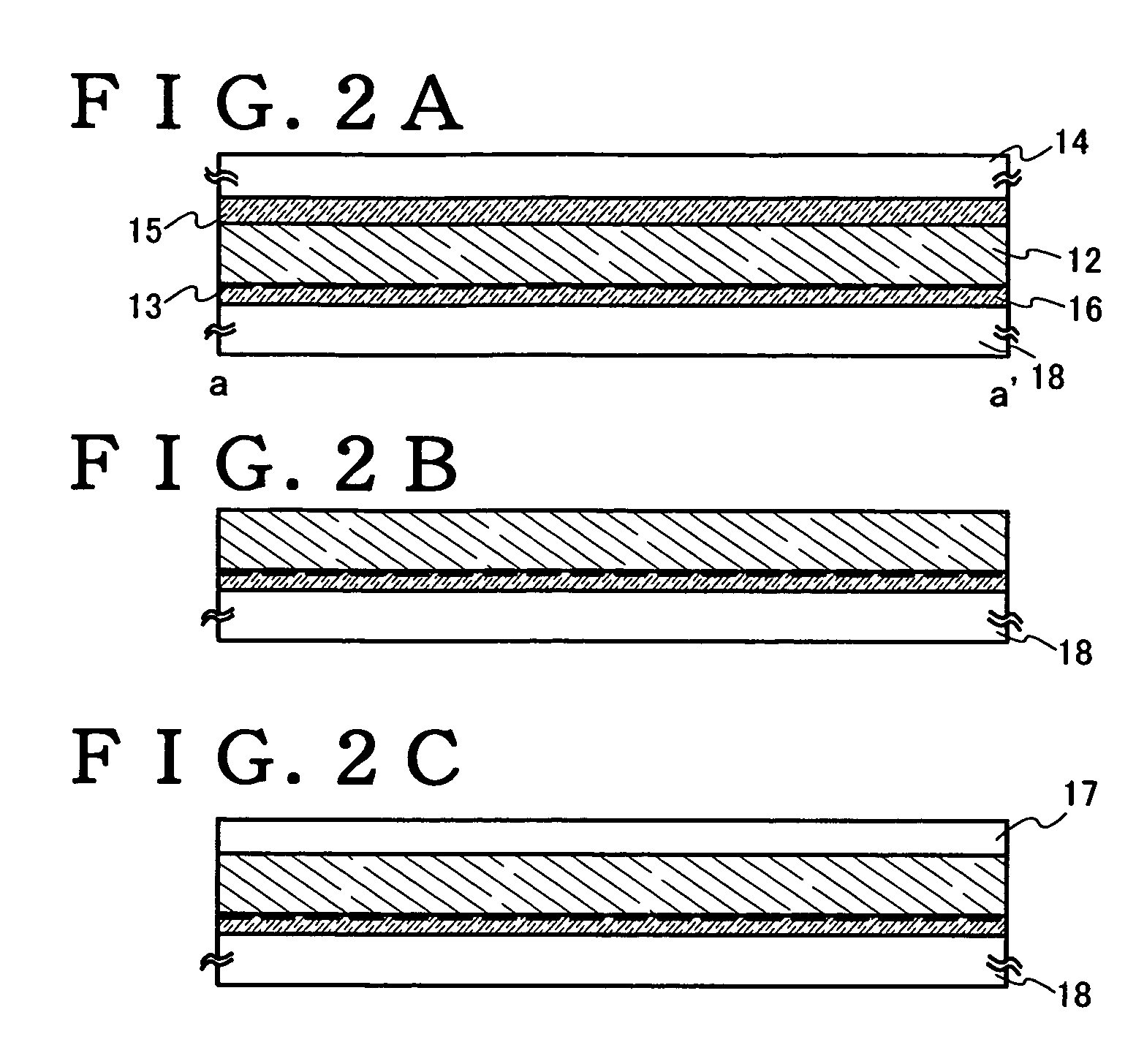
Thin film integrated circuit device, IC label, container comprising the thin film integrated circuit, manufacturing method of the thin film integrated circuit device, manufacturing method of the container, and management method of product having the container
InactiveUS7973313B2Efficiency of information managementIncrease capacitanceTransistorSolid-state devicesSiliconSemiconductor
The present invention provides an ultrathin thin film integrated circuit and a thin film integrated circuit device including the thin film integrated circuit device. Accordingly, the design of a product is not spoilt while an integrated circuit formed from a silicon wafer, which is thick and produces irregularities on the surface of the product container. The thin film integrated circuit according to the present invention includes a semiconductor film as an active region (for example a channel region in a thin film transistor), unlike an integrated circuit formed from a conventional silicon wafer. The thin film integrated circuit according to the present invention is thin enough that the design is not spoilt even when a product such as a card or a container is equipped with the thin film integrated circuit.
Owner:SEMICON ENERGY LAB CO LTD
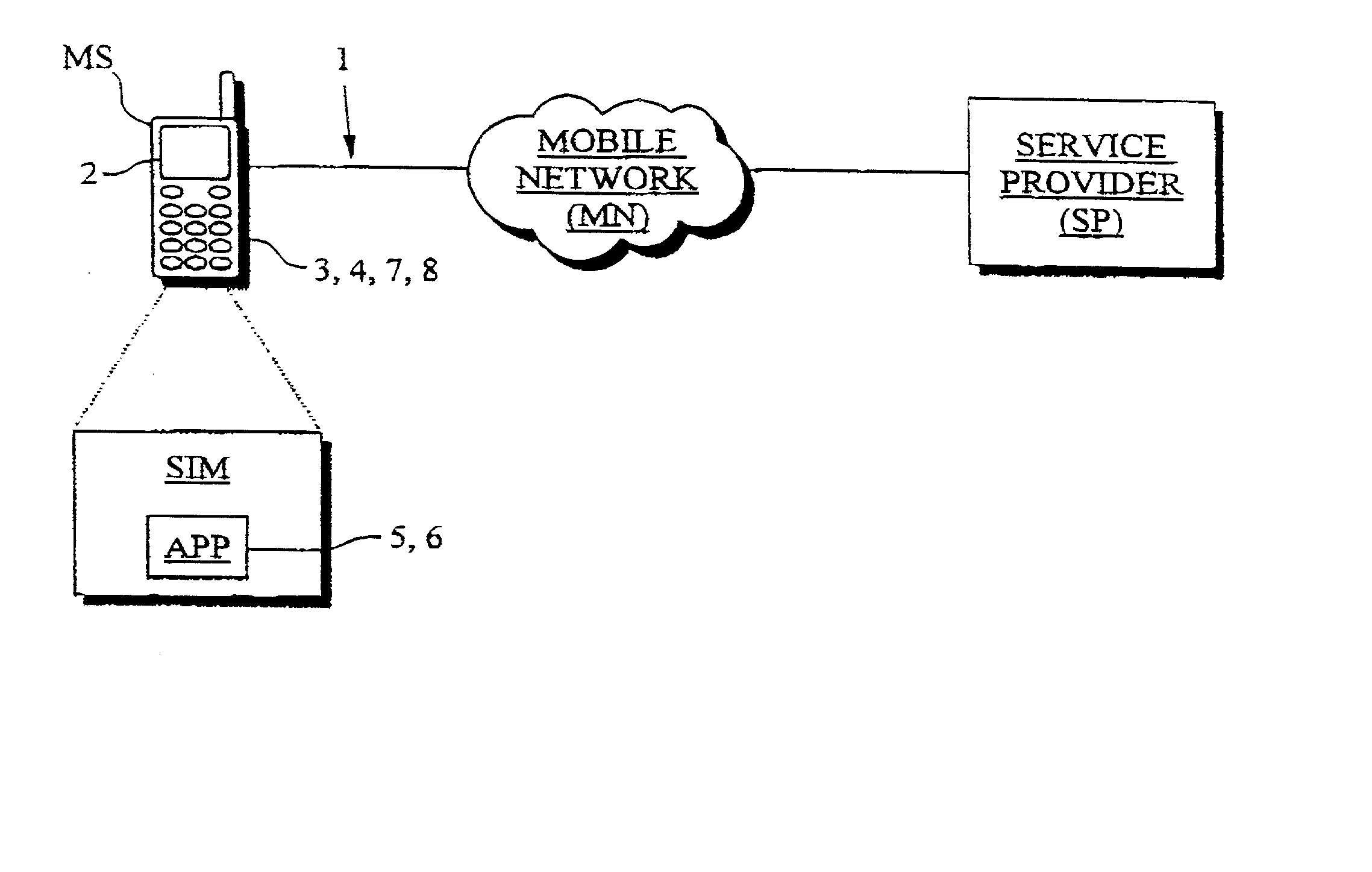
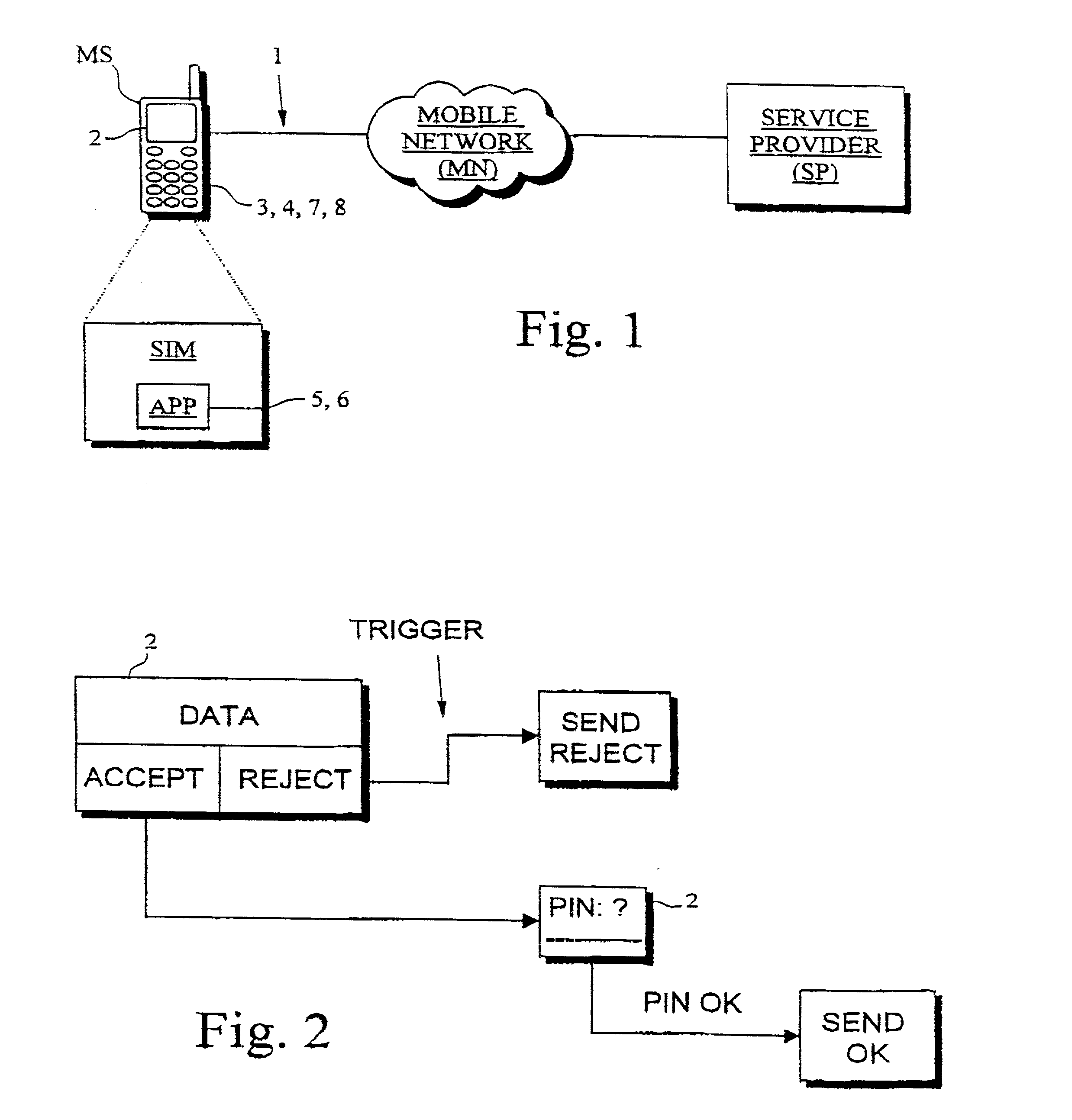
System and method for implementing secure mobile-based transactions in a telecommunication system
InactiveUS20030008637A1Easy to implement payment applicationSimplify verification operationsUnauthorised/fraudulent call preventionEavesdropping prevention circuitsUser inputDigital signature
A system for implementing secure transactions includes a mobile communication network, a service provider communicating with the mobile communication network and a mobile station communicating with the mobile network and, through the network, with the service provider. A subscriber identity module, in which an executable service application is stored, is associated with the mobile station. The system further includes means for transferring the material needed in implementing the transaction into the mobile station, means in the mobile station for presenting the transferred material to the user, means for requesting the user's acceptance of the presented material for digital signing, means for activating a PIN inquiry if the user accepts the material, means for checking, in the subscriber identity module, the correctness of the PIN code entered by the user, and means for encrypting and / or digitally signing the transmitted material using the service application stored in the subscriber identity module if the PIN code entered by the user is correct.
Owner:SONERA SMARTTRUST LTD
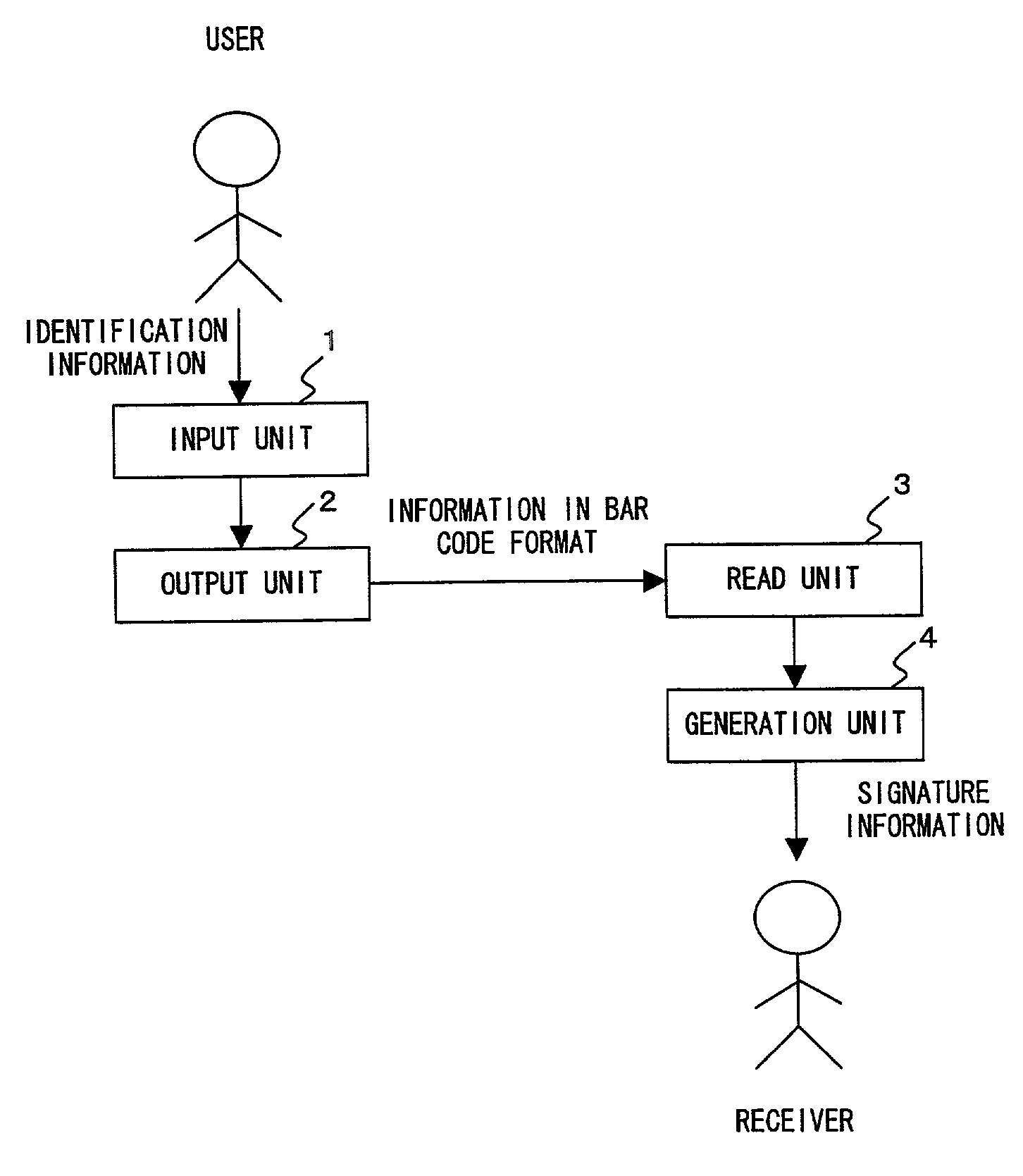
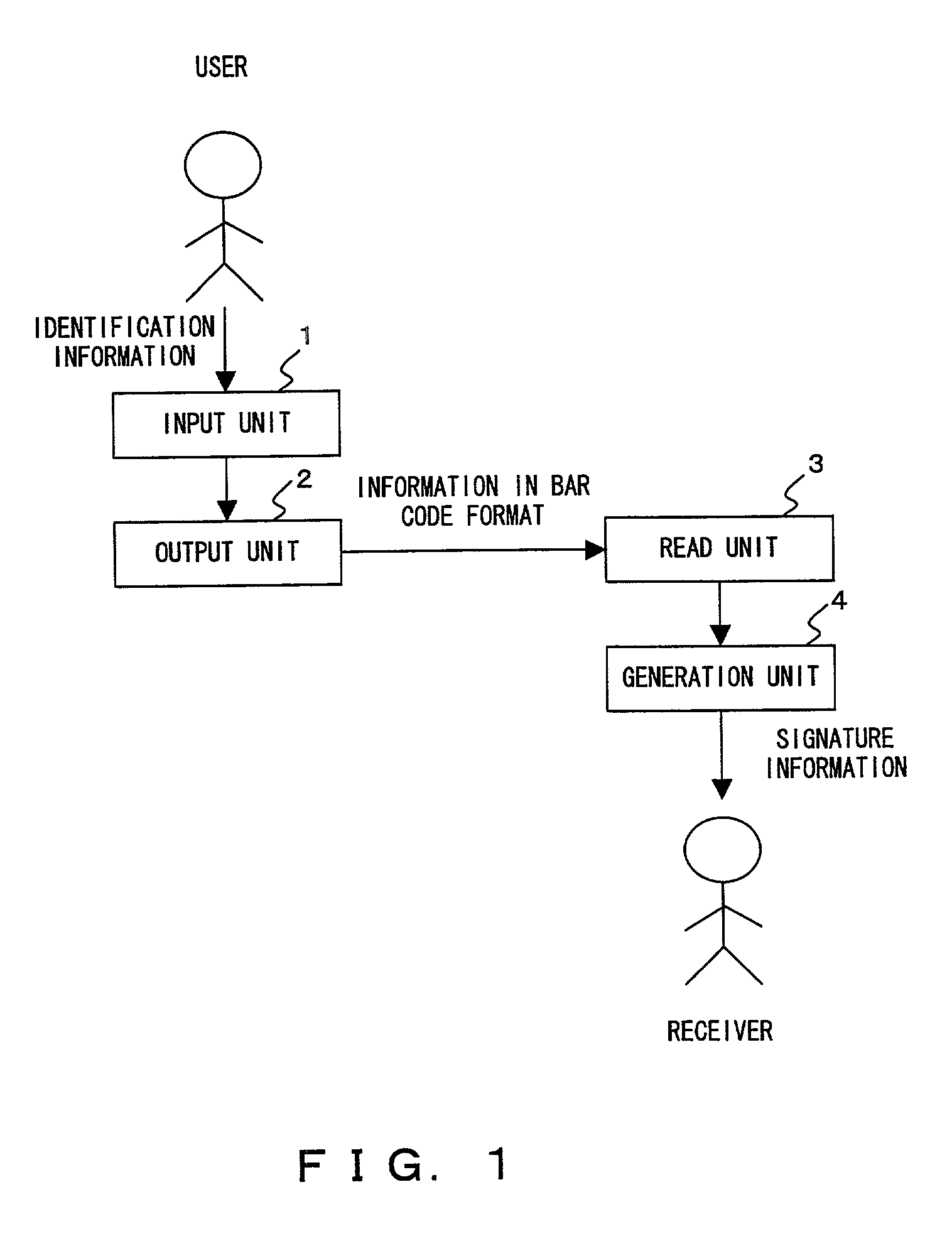
Signature system presenting user signature information
InactiveUS7107454B2Information securityDigital data processing detailsUser identity/authority verificationBarcodeComputer terminal
A user inputs identification information in a terminal, and generates identification information and bar code information about a signature program. A receiver reads the bar code information of the user using a bar code reader. The bar code reader executes a signature program, generates signature information containing the identification information of the user, and requests a certification device to verify the signature information.
Owner:SAKURA BANK LIMITED THE +1
Thin film integrated circuit device, IC label, container comprising the thin film integrated circuit, manufacturing method of the thin film integrated circuit device, manufacturing method of the container, and management method of product having the container
InactiveUS8193532B2Efficiency of information managementIncrease capacitanceTransistorSolid-state devicesSiliconSemiconductor
Owner:SEMICON ENERGY LAB CO LTD
Thin film integrated circuit device, IC label, container comprising the thin film integrated circuit, manufacturing method of the thin film integrated circuit device, manufacturing method of the container, and management method of product having the container
ActiveUS20110223966A1Efficiency of information managementIncrease capacitanceTransistorSolid-state devicesSiliconSemiconductor
The present invention provides an ultrathin thin film integrated circuit and a thin film integrated circuit device including the thin film integrated circuit device. Accordingly, the design of a product is not spoilt while an integrated circuit formed from a silicon wafer, which is thick and produces irregularities on the surface of the product container. The thin film integrated circuit according to the present invention includes a semiconductor film as an active region (for example a channel region in a thin film transistor), unlike an integrated circuit formed from a conventional silicon wafer. The thin film integrated circuit according to the present invention is thin enough that the design is not spoilt even when a product such as a card or a container is equipped with the thin film integrated circuit.
Owner:SEMICON ENERGY LAB CO LTD
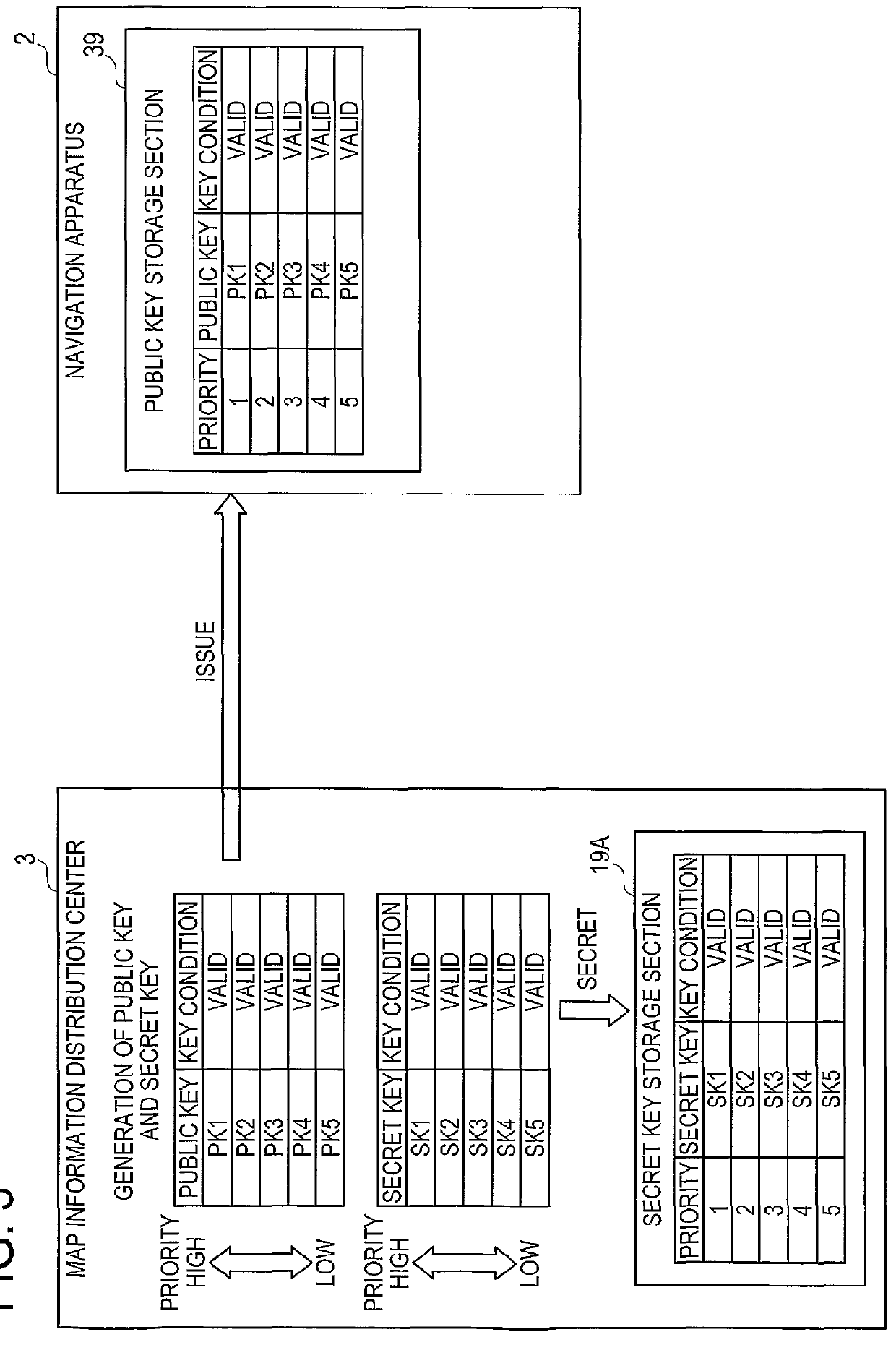
Navigation apparatus and information distribution system
ActiveUS20100070772A1Ensure safetyQuick verificationInstruments for road network navigationRoad vehicles traffic controlDistribution systemKey storage
A CPU of a navigation apparatus stores public keys to which priorities are set and which are published by an information distribution center in a public key storage section. The CPU of the navigation apparatus extracts an electronic signature of distribution data which is distributed from the information distribution center and verifies the electronic signature by using only ‘valid’ public keys among the public keys in order of the priorities. The CPU of the navigation apparatus determines that the distribution data is valid information which is distributed from the information distribution center when the electronic signature passes verification.
Owner:AISIN AW CO LTD +1
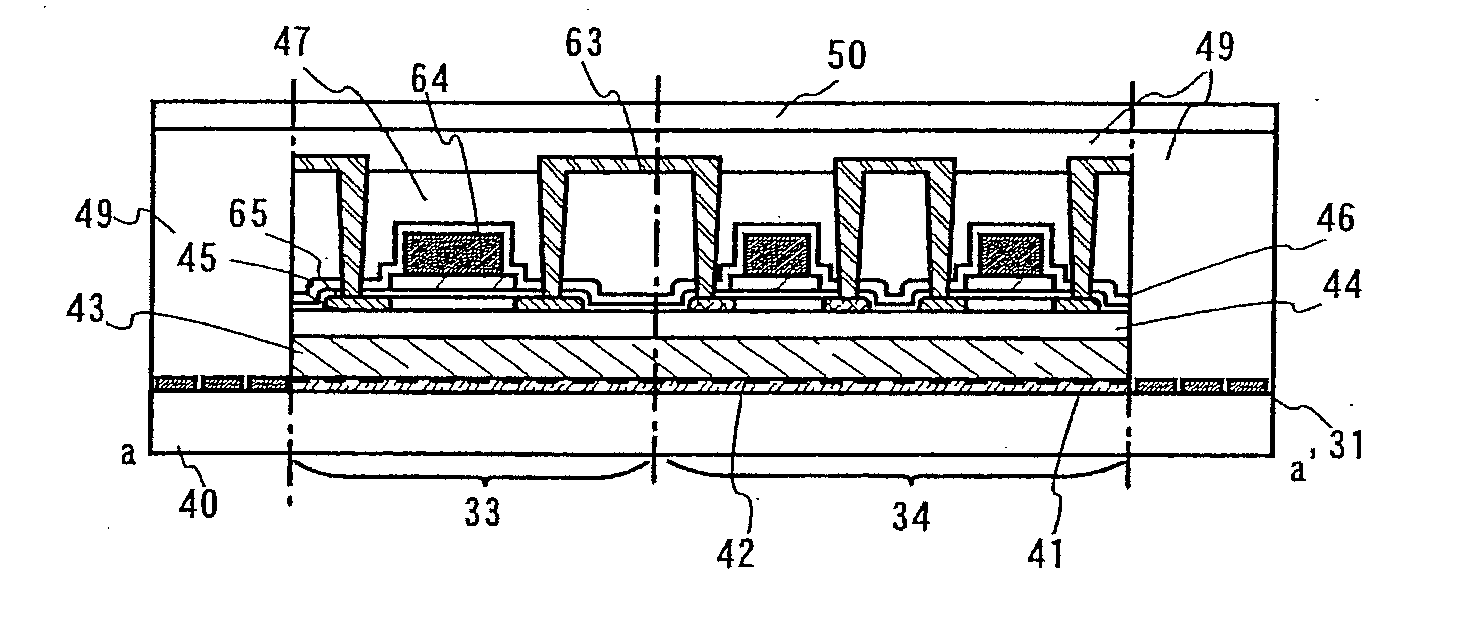
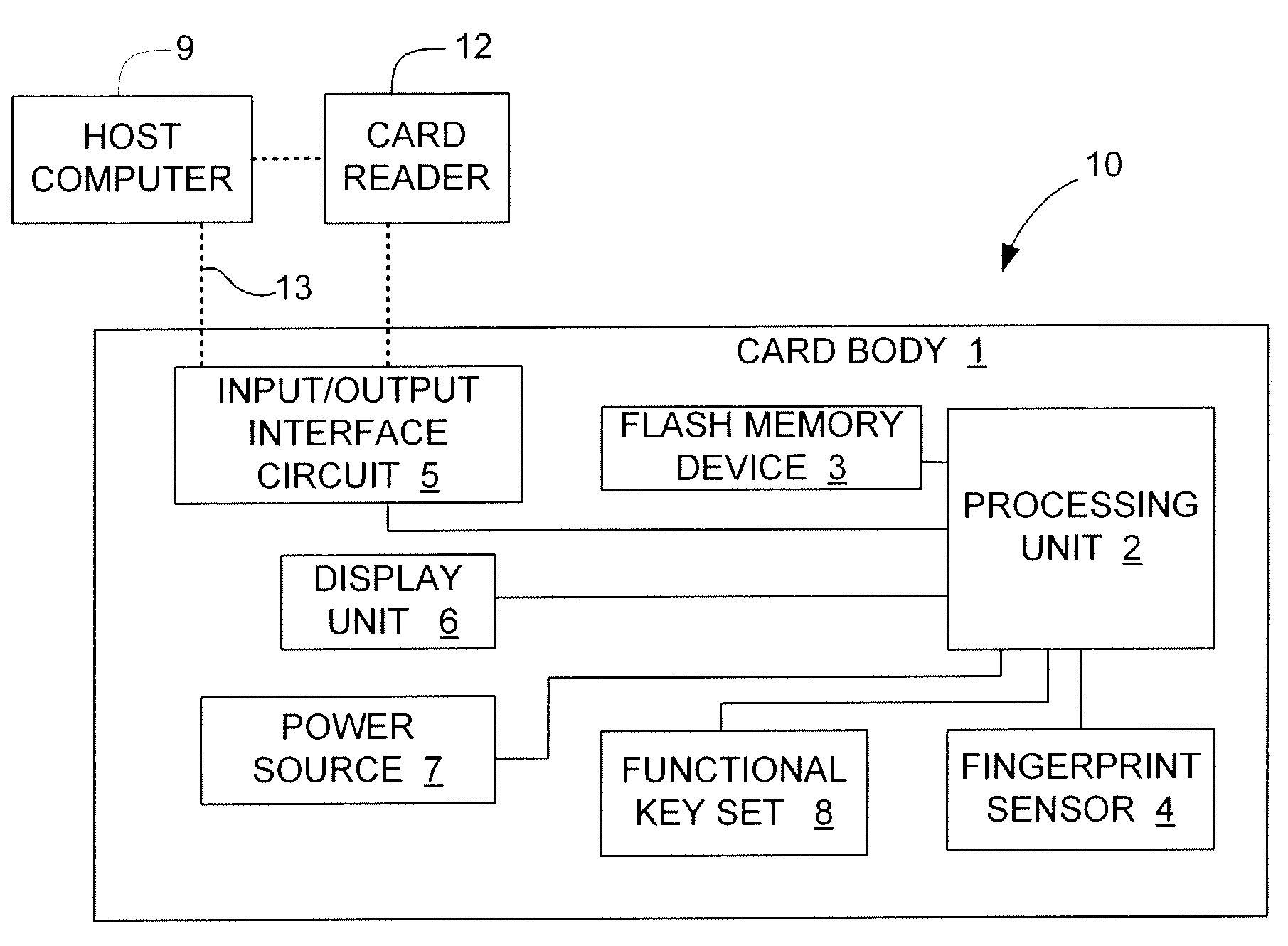
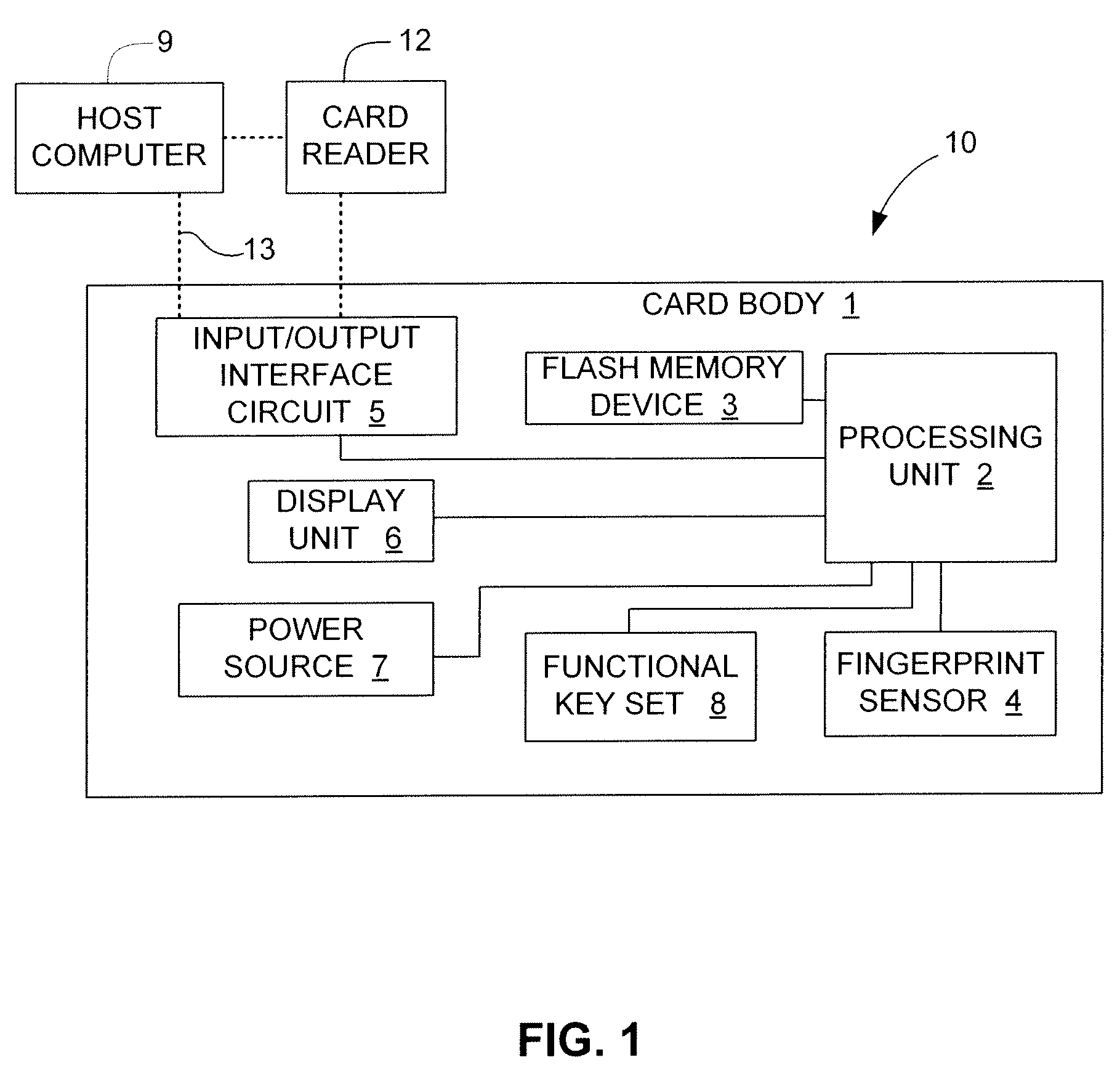
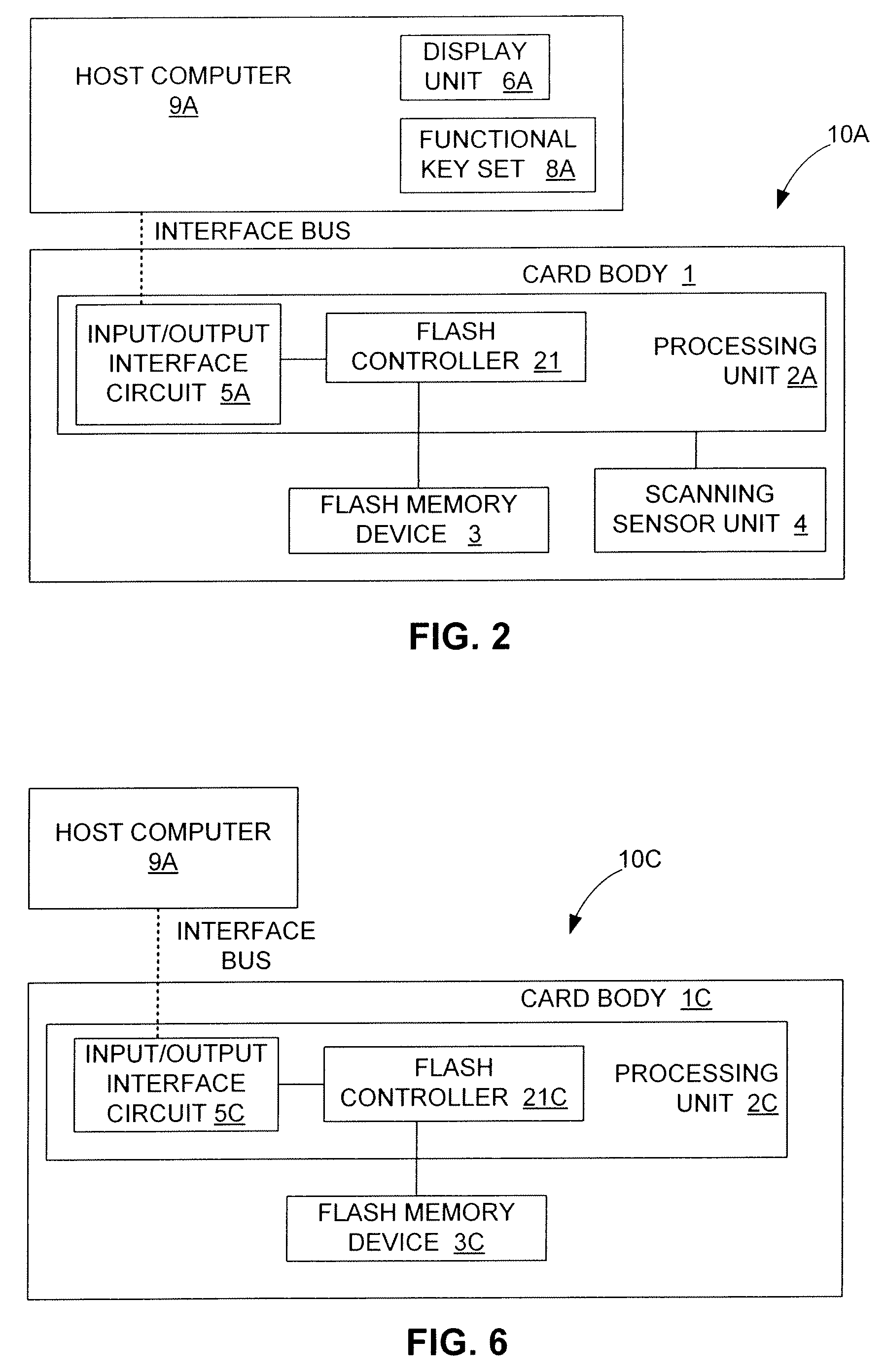
Electronic data flash card with fingerprint verification capability
InactiveUS7690030B1Easily carryDurable for ruggednessDigital data processing detailsUser identity/authority verificationData fileFingerprint
An electronic data flash card with fingerprint capability is accessible by an host computer, and includes a processing unit connected to a flash memory device that stores a data file and reference fingerprint data of a person authorized to access the data file, a fingerprint sensor for scanning the fingerprint of a user and for generating input fingerprint data that can be compared with the stored reference fingerprint data, and an input-output interface circuit activated so as to establish a communication with the host computer. In an embodiment, the electronic data flash card uses a USB input / output interface circuit for communication with the host computer.
Owner:SUPER TALENT TECH CORP
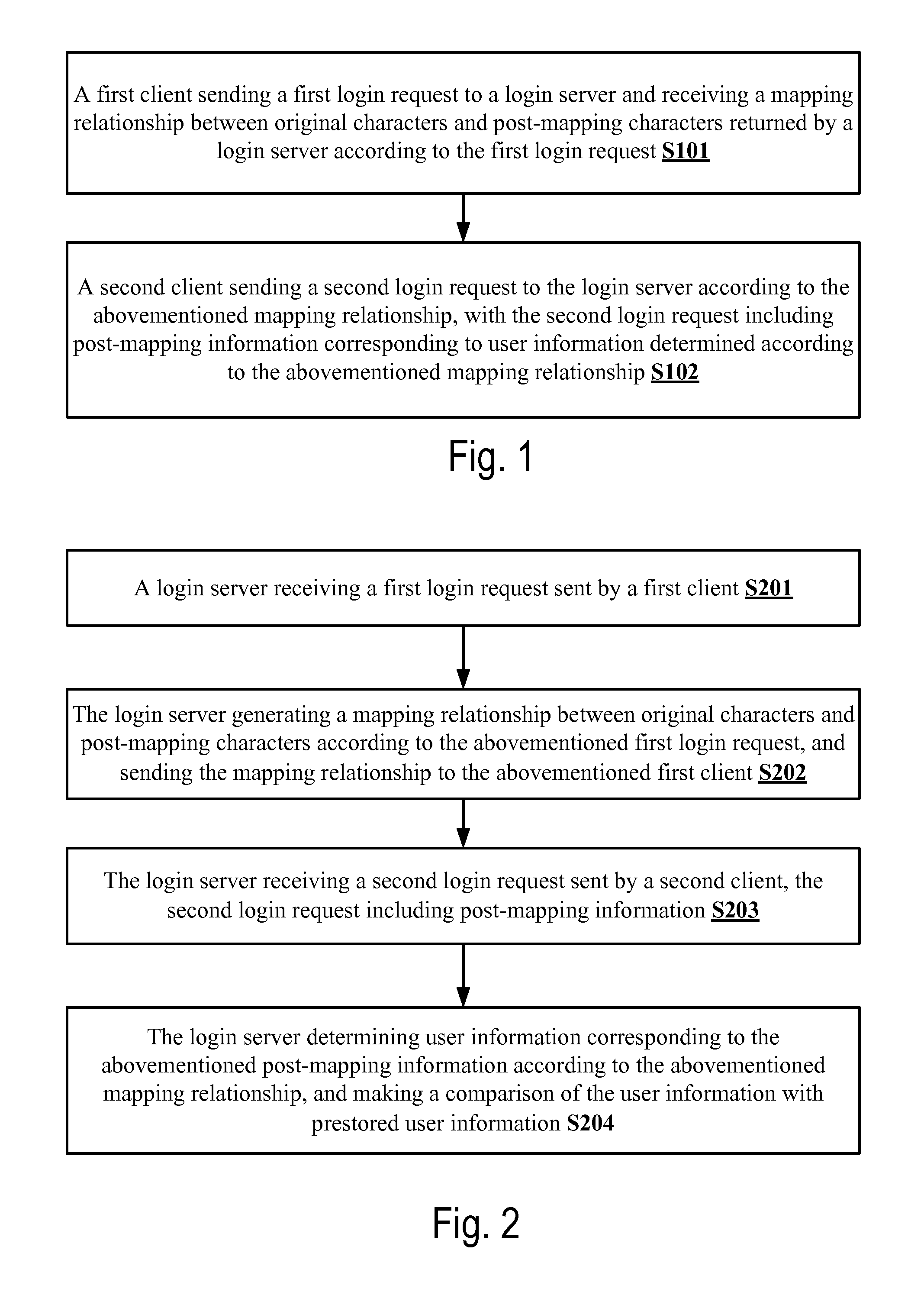
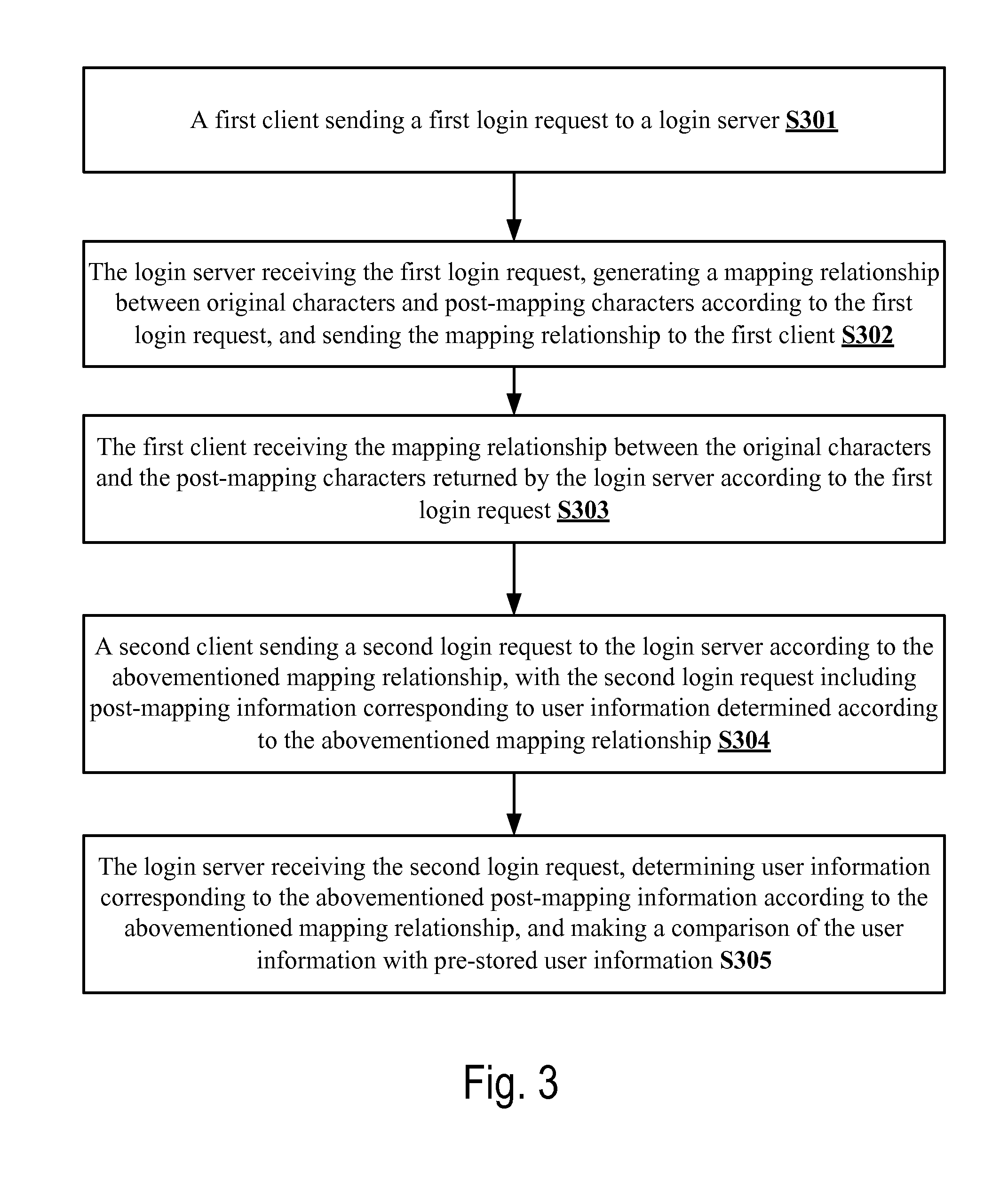
Method and system of login authentication
ActiveUS20140041005A1Improve safetySecurity of user informationDigital data processing detailsUser identity/authority verificationClient-sideComputer virus
A method and system for login authentication is disclosed. The method comprises the steps of: sending, by a first client, a first login request to a login server and receiving a mapping relationship between original characters and post-mapping characters returned by the login server according to the first login request; and sending, by a second client, a second login request to the login server according to the mapping relationship, with the second login request including post-mapping information corresponding to user information determined according to the mapping relationship. The solution in the present invention is to realize joint login by two clients, such that even if one of the clients is infected with a computer virus, no particular user information can be obtained through the infected client. Thus, the security of login authentication and the security of user information can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
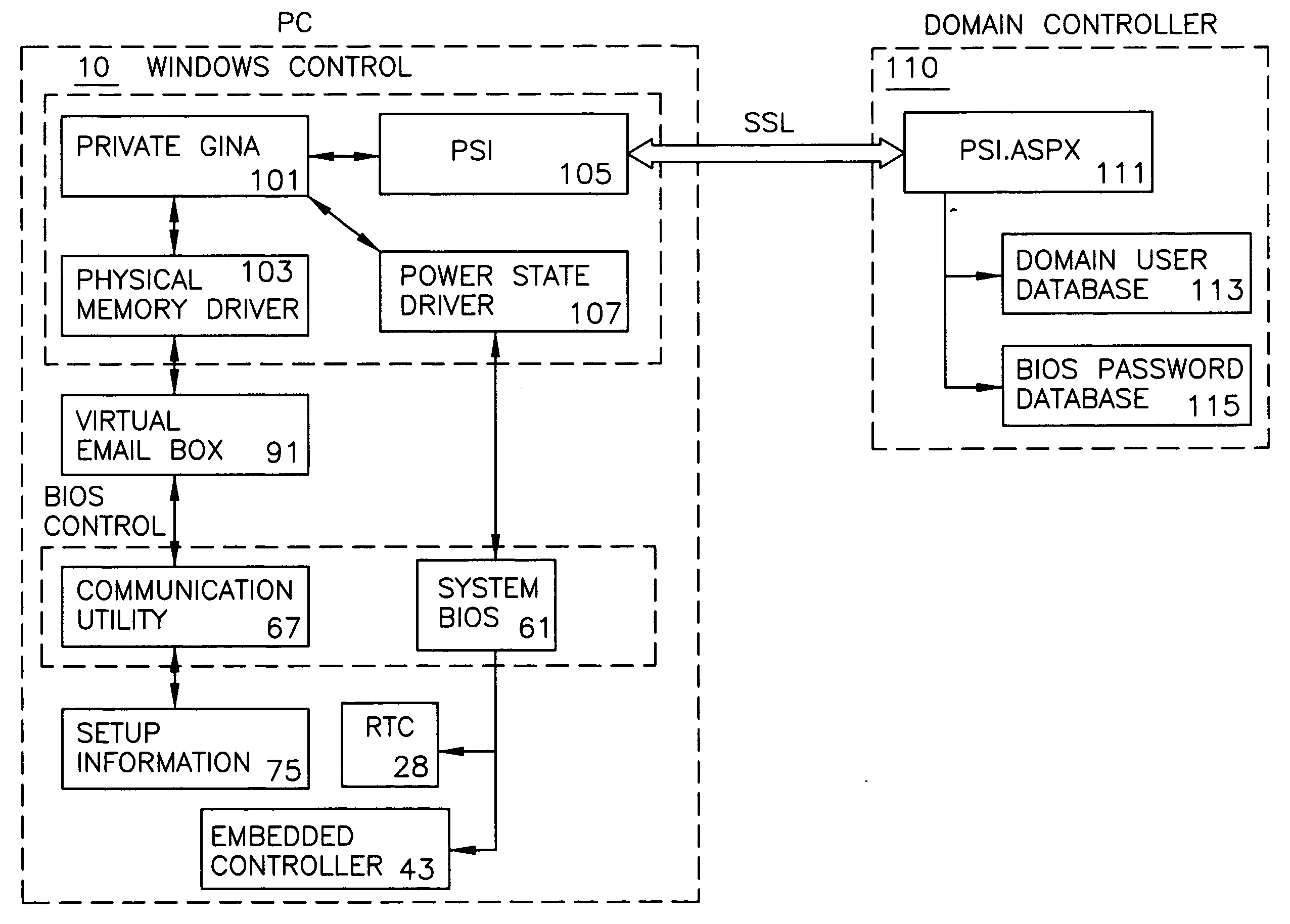
Information transfer
ActiveUS20080022099A1Losses in performanceLosses in usabilityUser identity/authority verificationDigital data protectionOperational systemMalware
Methods and apparatus are provided for securely inputting highly confidential information, exchanging the information via a network, and securely reflecting the information in a computer, without the information being stolen by malicious software. Upon a transfer of encrypted information from a server to a computer, the transferred information is stored in a memory of the computer and the computer is switched to a suspended state and immediately thereafter returns-to the previous state to be shifted to under the control of a BIOS. The information stored in the memory is decrypted and processed there. Processing information generated based on the processed information is then encrypted and it is transferred to the server after the computer is switched to under the control of the operating system.
Owner:IBM CORP +1
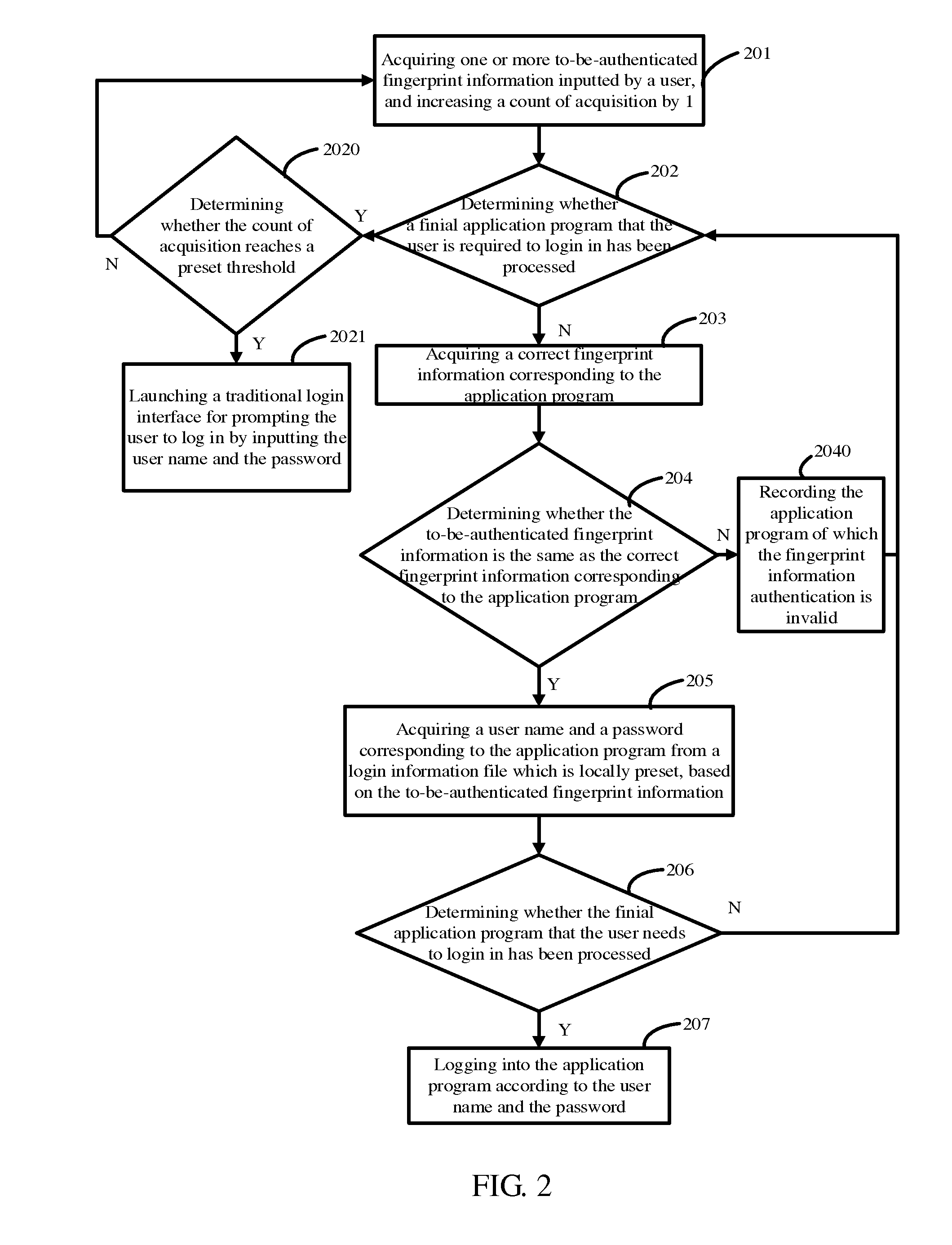
Mobile terminal and application program login method thereof
ActiveUS20140013424A1Quickly log into application programImprove user experienceUnauthorised/fraudulent call preventionDigital data processing detailsPasswordUser input
The present invention discloses a mobile terminal and an application program login method thereof. The method includes acquiring the to-be-authenticated fingerprint information inputted by a user when the user is required to log into an application program; determining whether the to-be-authenticated fingerprint information is the same as a correct fingerprint information which is locally preset and corresponds to the application program; if yes, then acquiring, according to the identifying fingerprint information, a user name and a password corresponding to the application program from a login information file which is locally preset; and logging into the application program according to the user name and the password. By logging into the application program via fingerprint, the present invention not only ensures the security of personal information, but also allows the user to quickly log into the application program, thereby improving user experience.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
Authentication method of mobile intelligent terminal and POS terminal
ActiveCN105530241AImprove the level ofInformation securityPayment architectureTransmissionMutual authenticationEngineering
The invention relates to the field of communication authentication, and particularly relates to an authentication method of a mobile intelligent terminal and a POS terminal. The mobile intelligent terminal generates a first time authentication code via a shared key and a random number to carry out first time authentication with the POS terminal, and the POS terminal generates a new key, encrypts the new key, generates a second time authentication code via the encrypted new key and the random number, and returns the second time authentication code to the mobile intelligent terminal to carry out second time authentication, and the new key generated by the POS terminal is completely transmitted to the mobile intelligent terminal during the second time authentication. After decryption, the both parties splice the two keys into the new key and use the spliced key for encryption or decryption in subsequent communication. By means of the twice mutual authentication of the mobile intelligent terminal and the POS terminal, the shared encryption and decryption key is smartly obtained in the authentication process, the communication security grade of the mobile intelligent terminal and the POS terminal is improved, and the information in the transaction of mobile payment is safer.
Owner:咪付(深圳)网络技术有限公司
Method for mobile terminal to access wireless access point and wireless access point
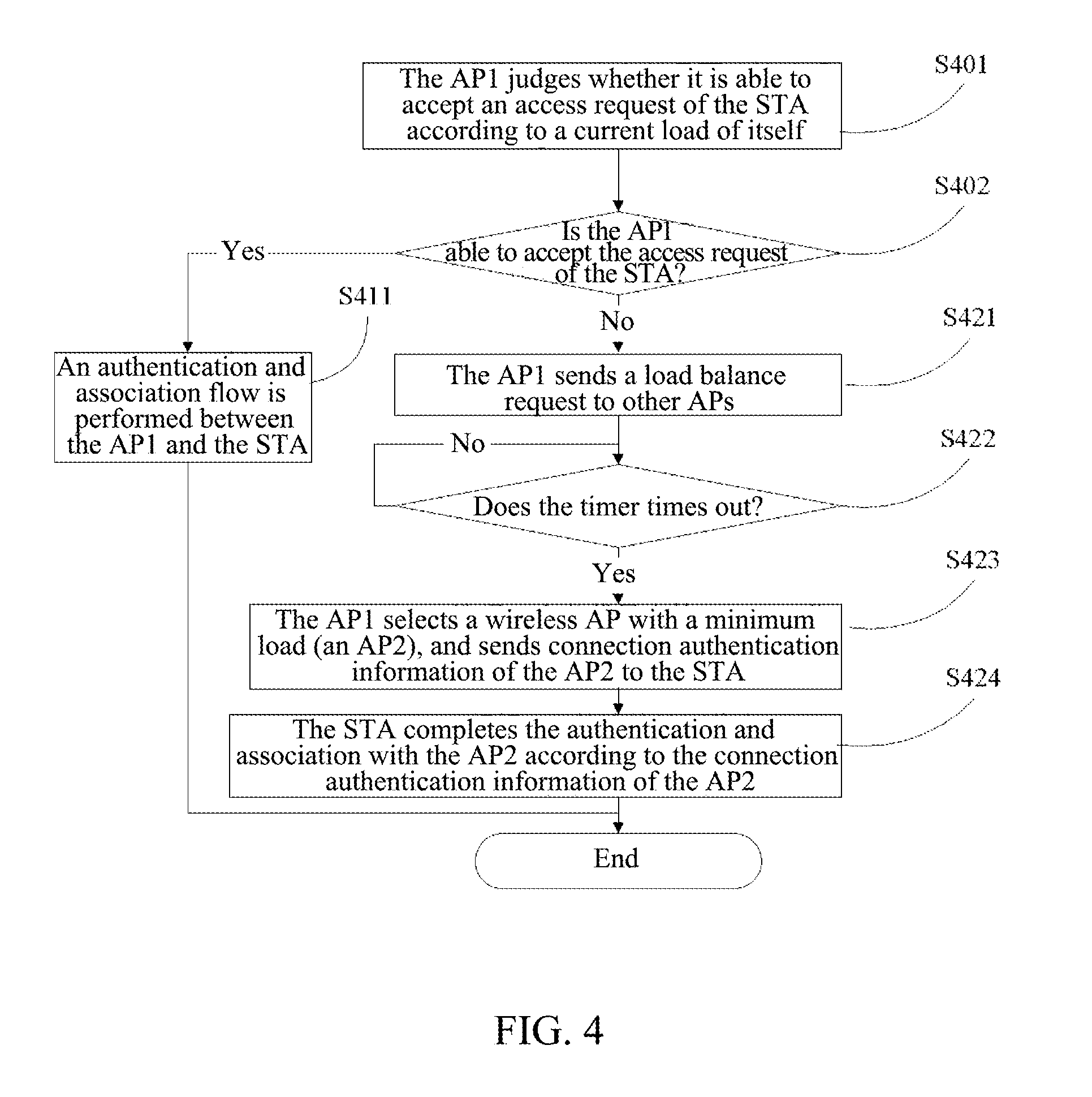
ActiveUS20150109912A1Small amount of system overheadSecurity of authentication informationError preventionFrequency-division multiplex detailsTelecommunicationsMobile station
A method for a mobile terminal accessing wireless access points and a wireless access point are disclosed. The method includes: after acquiring an access request of a mobile station, when determining that its load exceeds a preset first load upper limit, according to acquired connection information of other wireless access points, a first wireless access point sends a load balance request to all the other wireless access points; a wireless access point receiving the request sends a load balance feedback message to the first wireless access point, carrying its load and connection authentication information required; the first wireless access point selects a load balance feedback message carrying a minimum load from all received messages, and then sends the connection authentication information carried in the selected message to the mobile station; and the mobile station initiates an access flow to a corresponding wireless access point according to the received information.
Owner:ZTE CORP
User interface dynamic generation model of household electric apparatus integrated with universal protocol
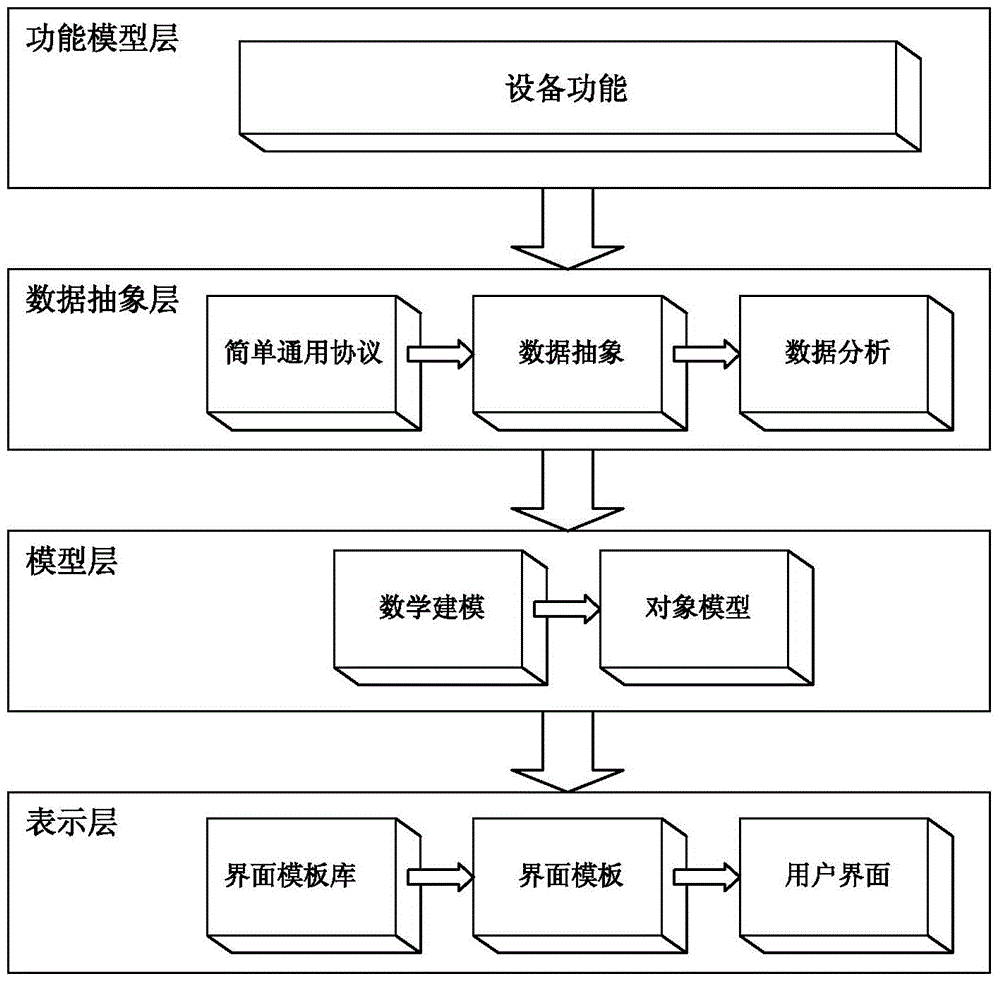
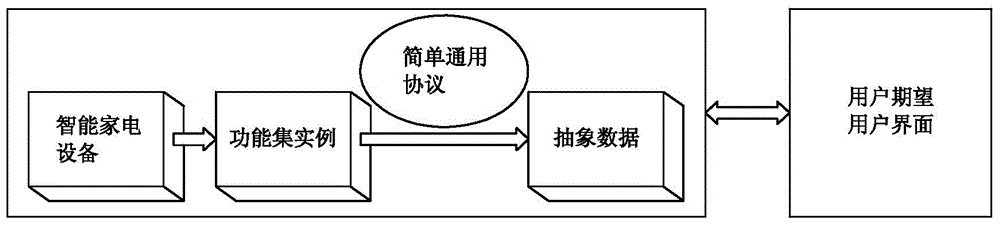
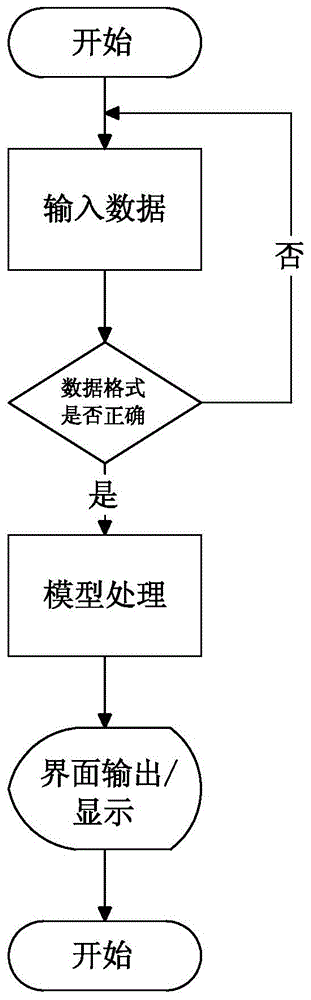
InactiveCN104991764ASimple structureImprove stabilityComputer controlSpecific program execution arrangementsIntelligent control systemEmbedded system
The invention discloses a user interface dynamic generation model of a household electric apparatus integrated with a universal protocol. By abstracting a household electric apparatus function set into a set of data set based on a simple universal protocol and by combining an expected user control interface of a user to the household electric apparatus, and based on an FMP model, the data set is analyzed and a model is established; and at last, according to the model, the user control interface dynamic generation of the household electric apparatus is realized. The technical solution of the invention provides a design and the dynamic generation to a control system interface of smart household apparatuses; by adopting the model, the work load of a develop engineer of a system front end is greatly decreased; the code quantity of the system development is reduced; with the data driving features of the interface, the update frequency to the smart control system is also reduced; and lastly, the user interface is combined with the control protocol based on the simple universal protocol of the smart household apparatuses, thus the smart control to the household apparatuses is realized conveniently.
Owner:GUANGDONG CANBO ELECTRICAL +1
System and method for secure wall
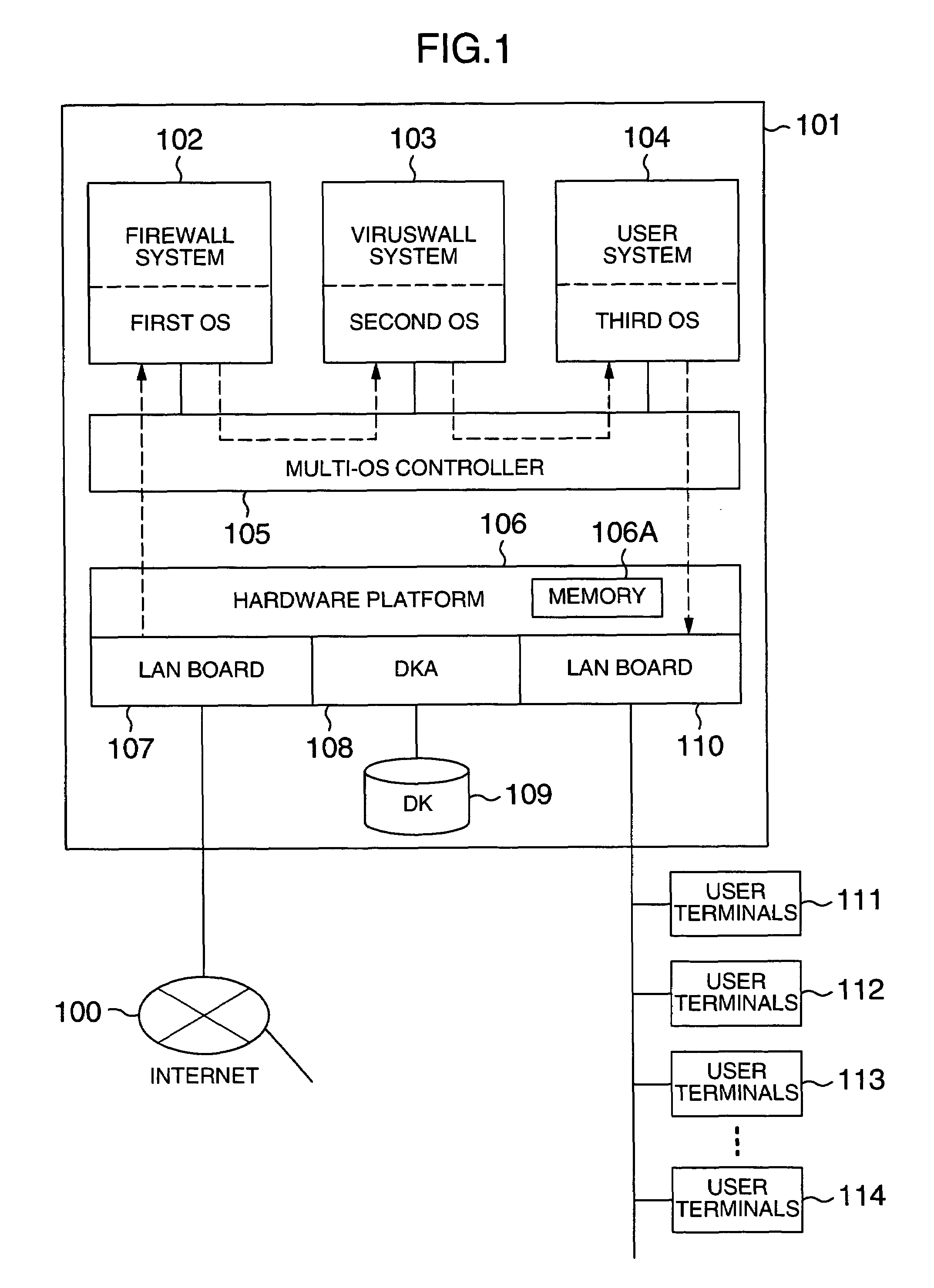
InactiveUS7260839B2Strengthen securityPrevent be damageMemory loss protectionError detection/correctionComputer hardwareInformation processing
A security wall, such as a firewall and a viruswall, is built easily which does not require firewall-dedicated hardware or viruswall-dedicated hardware nor, in a mobile information processing device, mobile terminal-dedicated hardware. For this purpose, on a single information processing device, a plurality of separate LAN segments are realized and data from an external network such as the Internet is forced to pass through the multiple LAN segments before it reaches a user system in order to reinforce the system against external attacks. The security wall system is made portable so that the firewall and the viruswall can be executed at the same time, strengthening the security of the mobile information processing device.
Owner:HITACHI LTD
Embedded device, control method therefor, program for implementing the control method, and storage medium storing the program
ActiveUS20140304591A1Securing privacy and securityEasy maintenanceWeb data retrievalNatural language data processingWeb browserClient-side
An embedded device incorporating a Web browser, which enables a server to provide a dynamic content adapted and linked to a function specific to the embedded device and a status of the same, as an easily and flexibly expandable service in response to access from the embedded browser, and enables securing privacy and security of information on a client. In an image processing apparatus (110) implementing the embedded device, a Web browser module (211) loads Web content data containing at least document data which is described in a markup language and has a script or information for reference to a script embedded therein, and performs presentation based on the loaded Web content data. A controller unit (111) controls information and operation of the image processing apparatus. A script interpreter (805) incorporated in the Web browser module interprets the document data contained in the loaded Web content data and processes the script or the information for reference to a script embedded in the document data. A control API module (218) provides an interface via which the script interpreter gains access, based on the processing of the script, to a DOM managed in the Web browser module. Further, the control API module provides an interface via which the script interpreter gains access, based on the processing of the script, to the information and operation of the embedded device, controlled by the controller unit.
Owner:CANON KK
Visual electronic license plate system
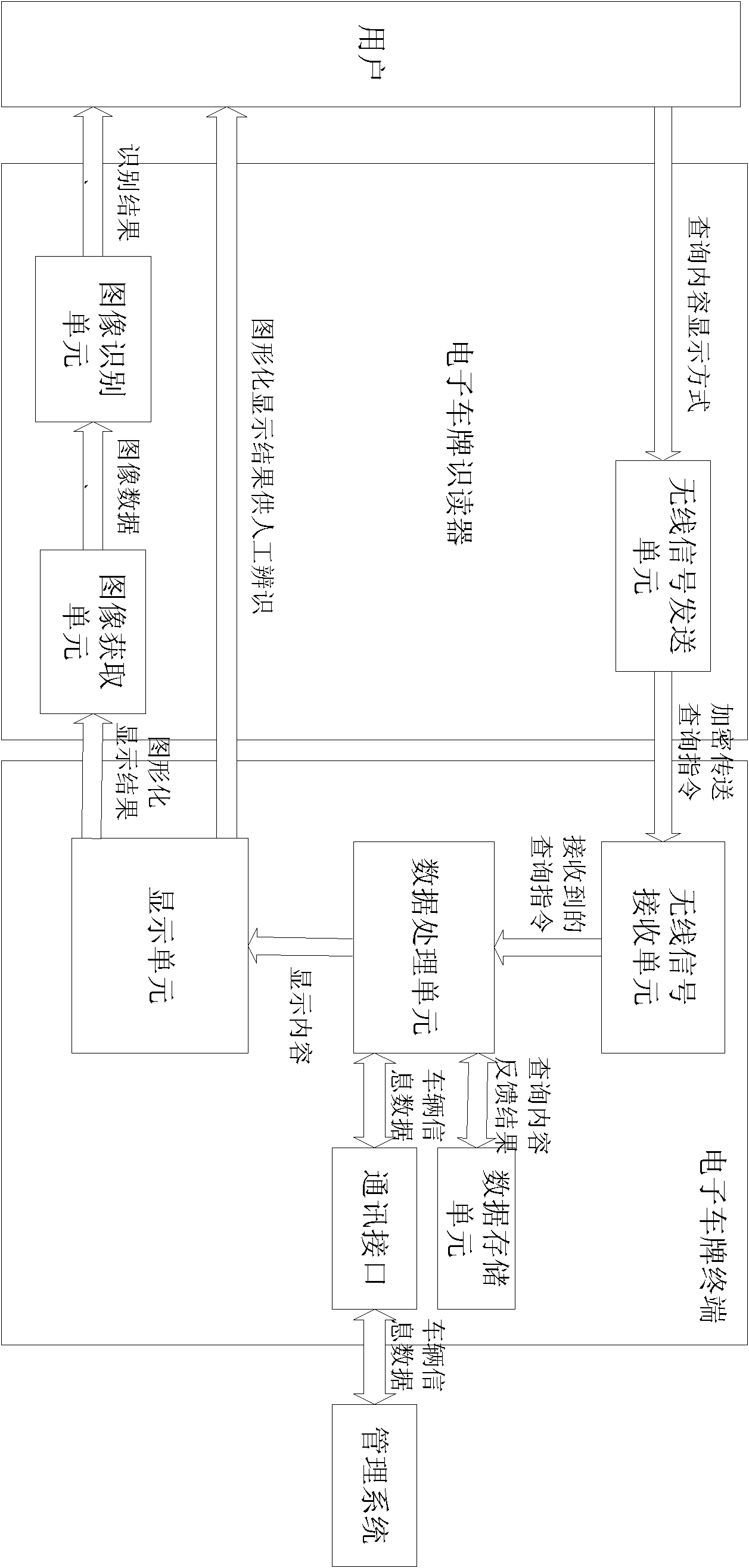
ActiveCN102152764AImprove securityInformation securityCo-operative working arrangementsVehicle componentsPlate readerData processing
The invention discloses a visual electronic license plate system which is characterized in that the visual electronic license plate system comprises an electronic license plate terminal and an electronic license plate reader; the electronic license plate terminal comprises a wireless signal receiving unit, a data processing unit, a data storage unit and a display unit; the wireless signal receiving unit is used for sending a received inquiry instruction to the data processing unit; the data processing unit is used for reading out data in the data storage unit, obtaining a processing result and sending the processing result to the display unit to display; the electronic license plate reader comprises a wireless signal transmission unit, an image acquisition unit and an image identification unit; the wireless signal transmission unit is used for transmitting the inquiry instruction to the electronic license plate terminal; the electronic license plate terminal has corresponding display on the display unit; the image acquisition unit is used for acquiring a result image displayed by the electronic license plate terminal; and the image identification unit is used for automatically identifying the result. The visual electronic license plate system has high safety and strong anti-falsification property, is visualized and visual and has high accuracy rate of automatic identification.
Owner:SUZHOU GOLD MANTIS YIHE TECH
Heating cooker for commercial use
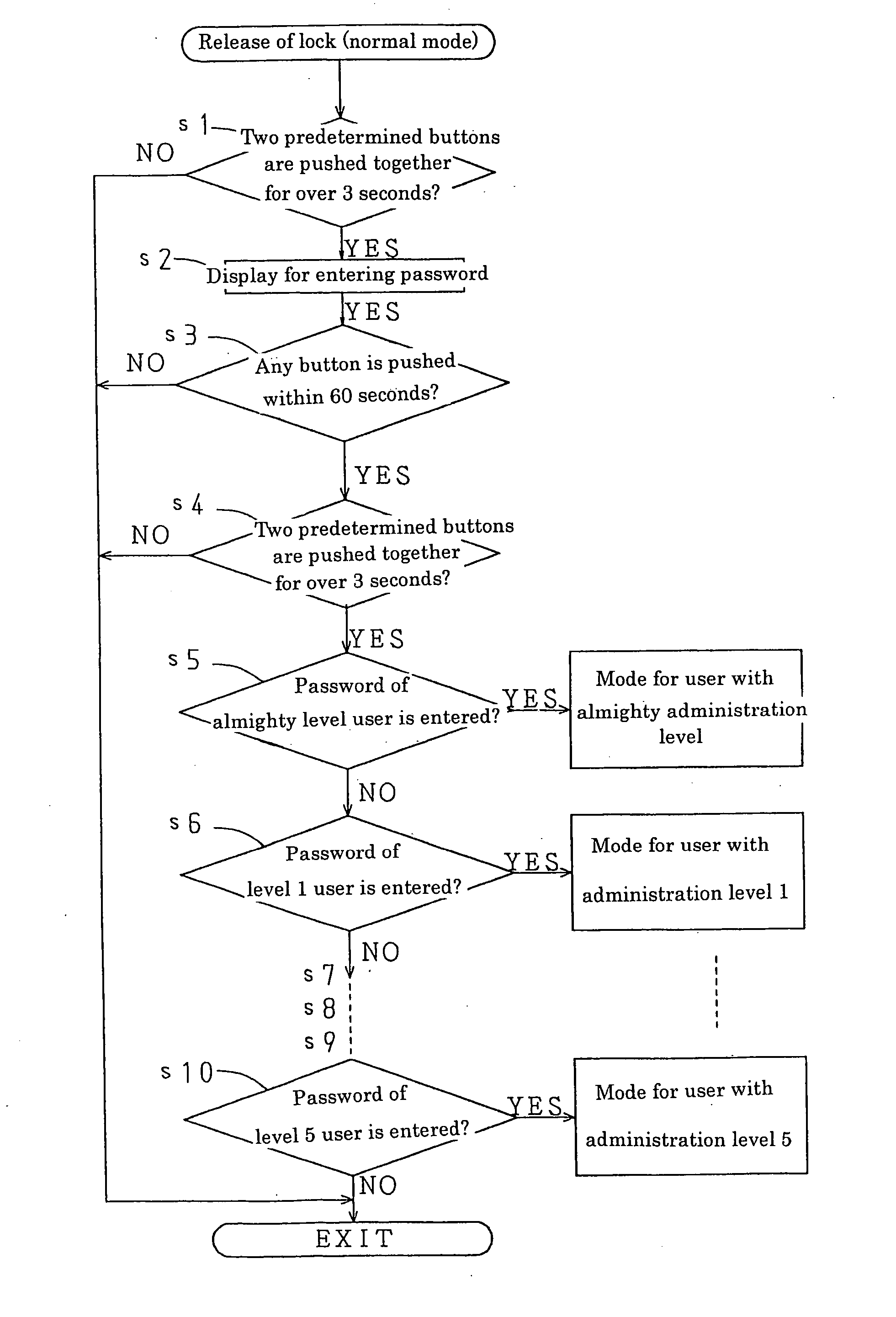
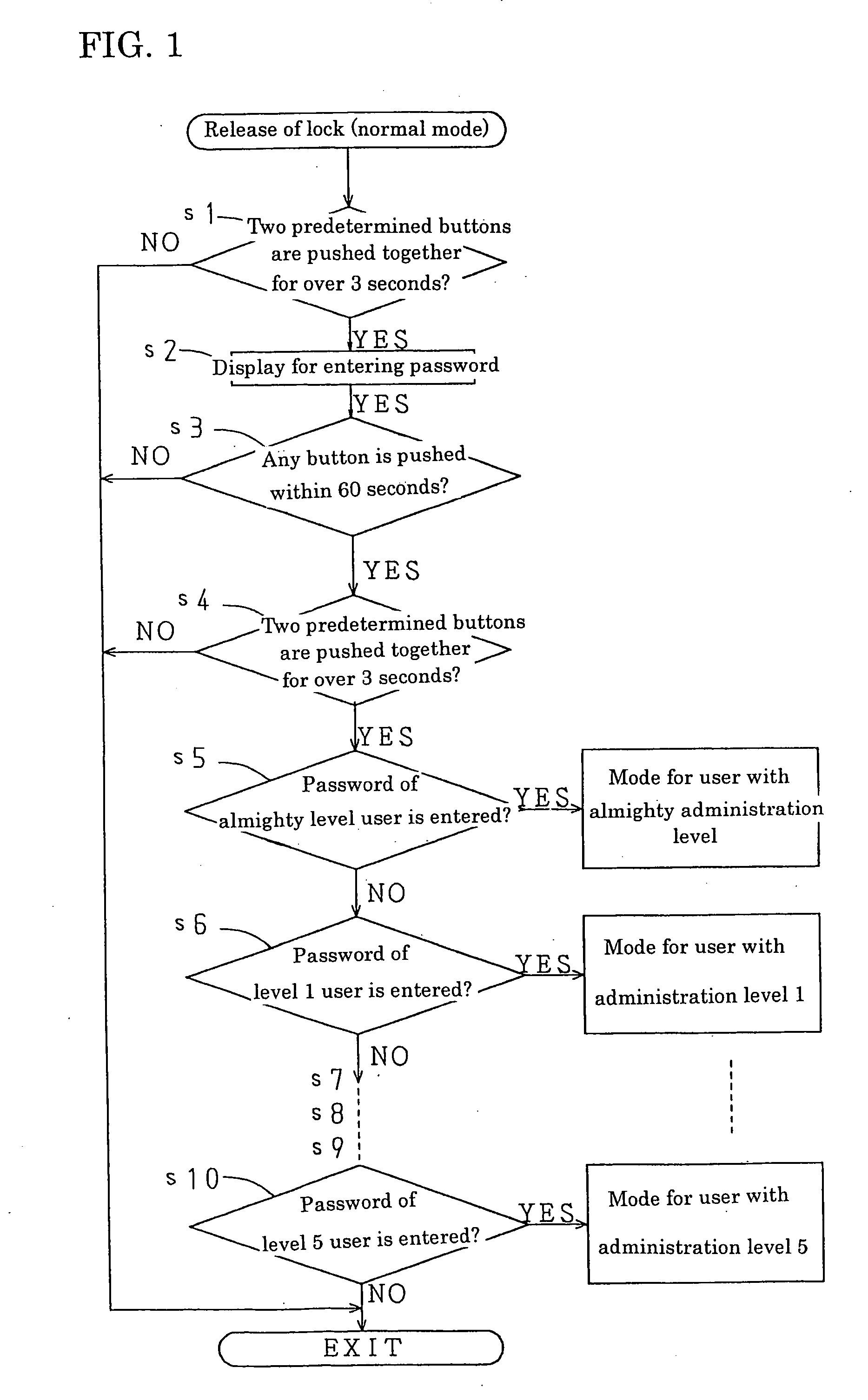
ActiveUS20050011881A1Improve securityInformation leakageElectric heatingCooking vesselsPasswordMonitoring system
A heating cooker for commercial use is provided in which heating control is conducted based on cooking parameter according to each cooking menu and an unauthorized user is prevented from changing the cooking parameter easily. In the heating cooker, cooking parameter can be changed only when a password is entered. Moreover, a user's administration level is determined by the entered password and information which can be changed is selected according to the user's administration level. The password entry can be carried out not only in an operation display panel provided with the heating cooker but in a remote central monitoring system which operates the heating cooker from a distant place.
Owner:PALOMA
Human-computer interaction method and human-computer interaction equipment
ActiveCN104714645APracticalDifficult to observeInput/output for user-computer interactionGraph readingMuscle groupHuman–robot interaction
The embodiment of the invention discloses a human-computer interaction method and human-computer interaction equipment. The method comprises the steps that a first strength signal relevant to strength is analyzed out of a first surface myoelectricity signal, and the first surface myoelectricity signal is obtained from a second surface myoelectricity signal collected from a muscle group expected to be controlled by a user; the strength of the user is determined according to the first strength signal; when the duration time of the strength belonging to a preset strength range meets preset time, a preset instruction of controlling the human-computer interaction equipment to act is triggered; the human-computer interaction equipment is controlled to act according to the preset instruction. In the whole process, the user only needs to control the strength applied to the muscle group, and high practicality is achieved. In addition, due to the fact that specific gestures or specific hand shapes do not need to be obviously made, based on the hidden property, the situation that the process is observed by other people, and information leakage is caused is not likely to happen, and the function of information safety is achieved to a certain degree.
Owner:HUAWEI TECH CO LTD +1
Recording medium holder having one or more recording mediums
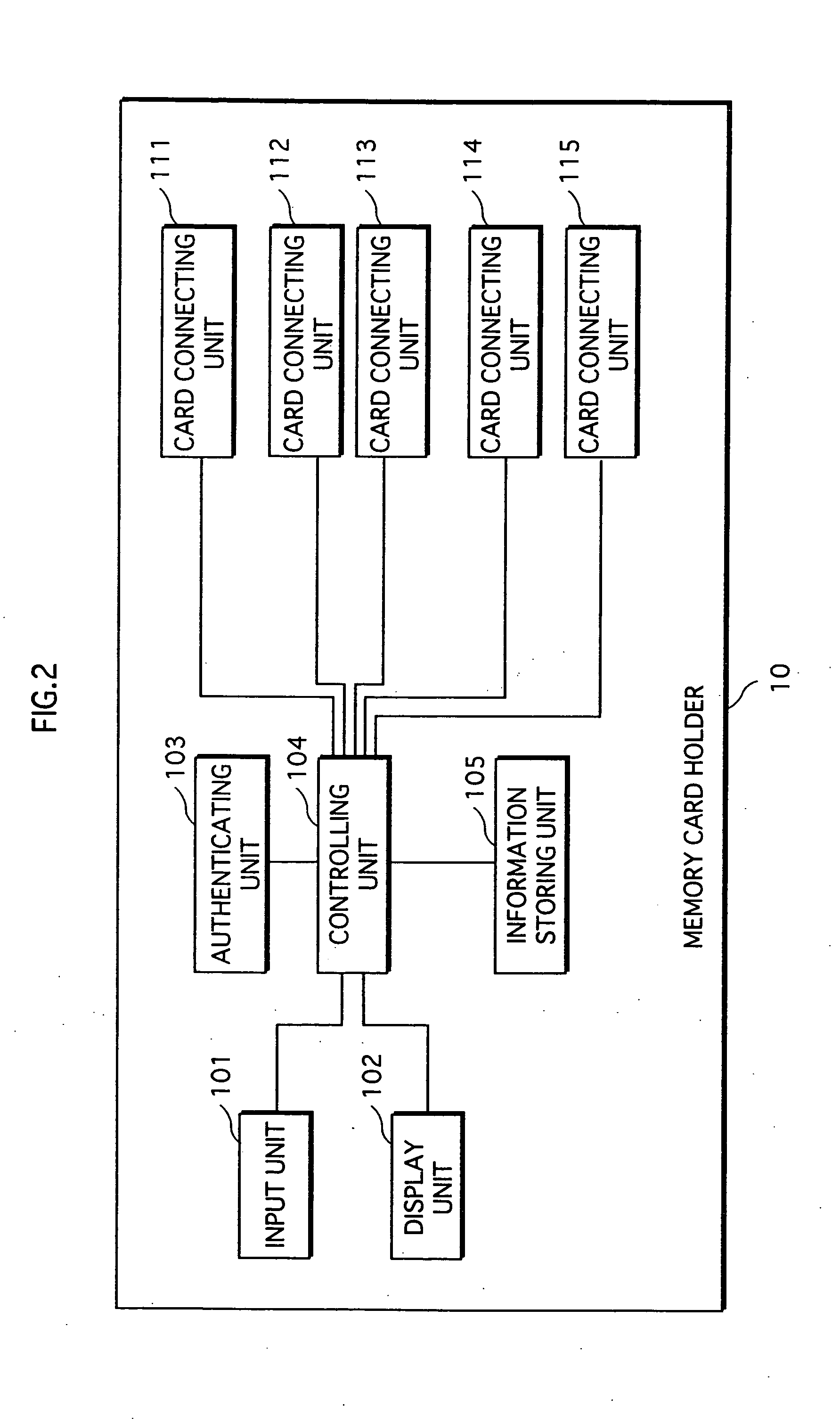
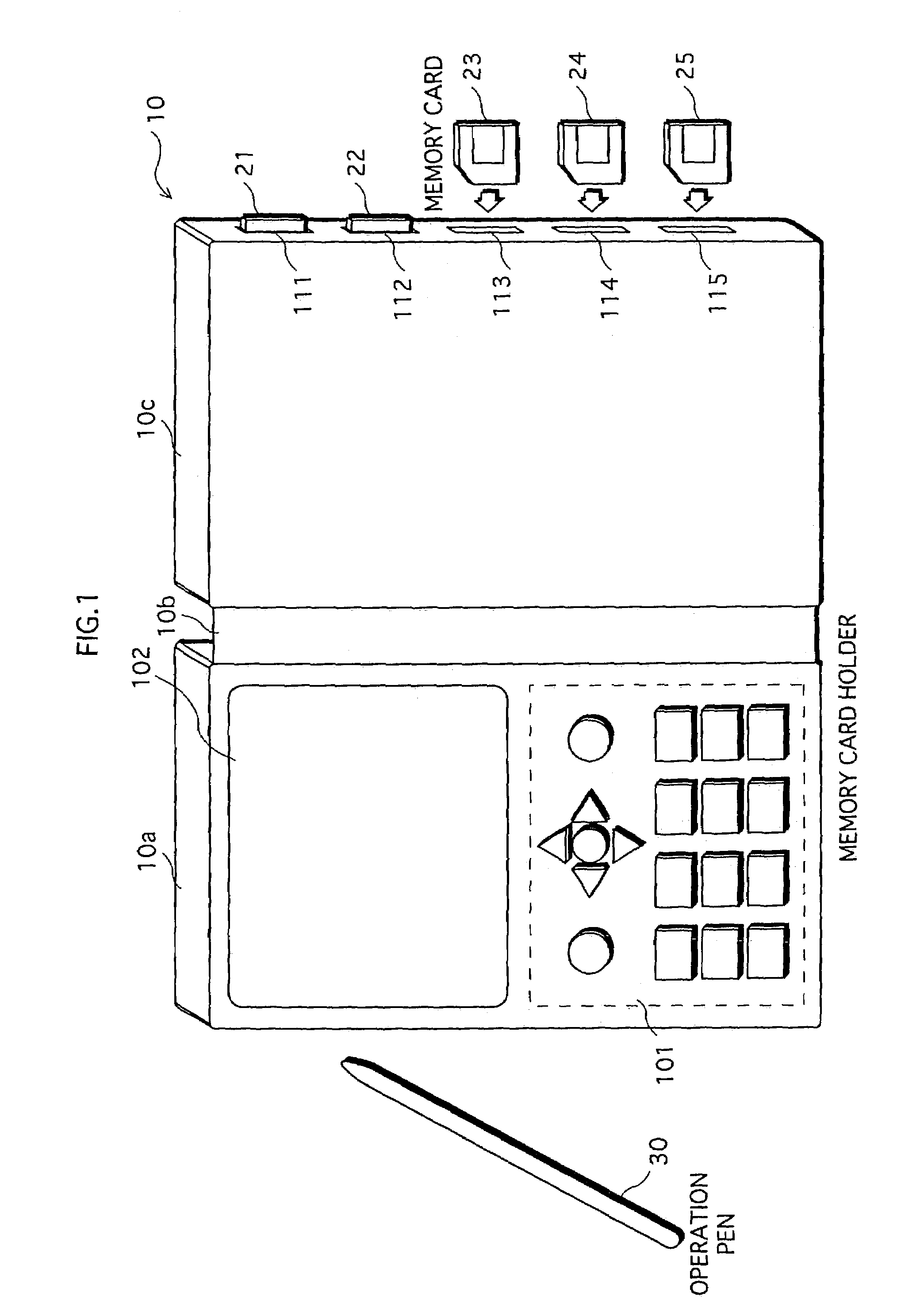
InactiveUS20060253652A1Easy searchSafe and efficient managementDigital data protectionInternal/peripheral component protectionComputer hardwareLiquid-crystal display
A recording medium holder enables a user to easily find a desired recording medium from recording mediums that the user manages. The recording medium holder includes a recording medium holding unit for holding a plurality of recording mediums, a liquid crystal displaying unit for displaying each of the plurality of recording mediums held in the recording medium holding unit by an icon, and an information displaying unit for displaying information of a recording medium that corresponds to an icon clicked in the liquid crystal displaying unit, the information including ID information, title information, index information, and other information. The information is read out from the recording medium at a first click, and from a storing unit at a second click and after.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
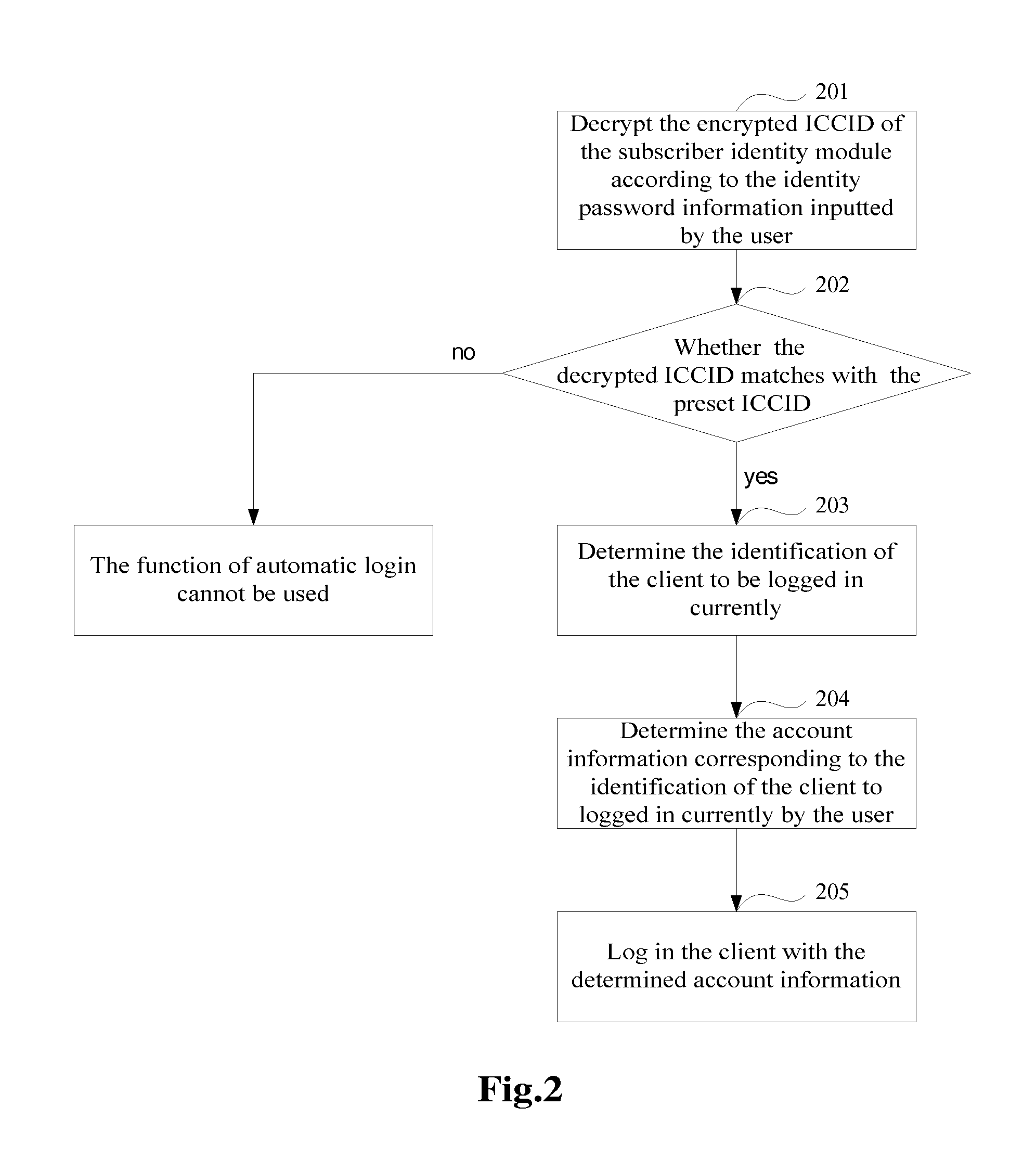
Method and system for automatically logging in a client
ActiveUS20120233462A1Security of account informationEasy to manageUser identity/authority verificationRecord information storagePasswordEngineering
A method and system for automatically logging in a client is disclosed in the present invention, mainly comprising: use encrypted ICCID for the authentification of user's identity during automatic login; when authentification is passed, determine the account information corresponding to the identification of the client to be logged in currently by the user, and log in the client automatically with the determined account information, so that the user can conveniently manage the account information corresponding to each client when he guarantees the security of the account information simultaneously, avoiding the troublesome inputting of username and password of the account and achieving the purpose of automatically logging in a client.
Owner:DRNC HLDG INC
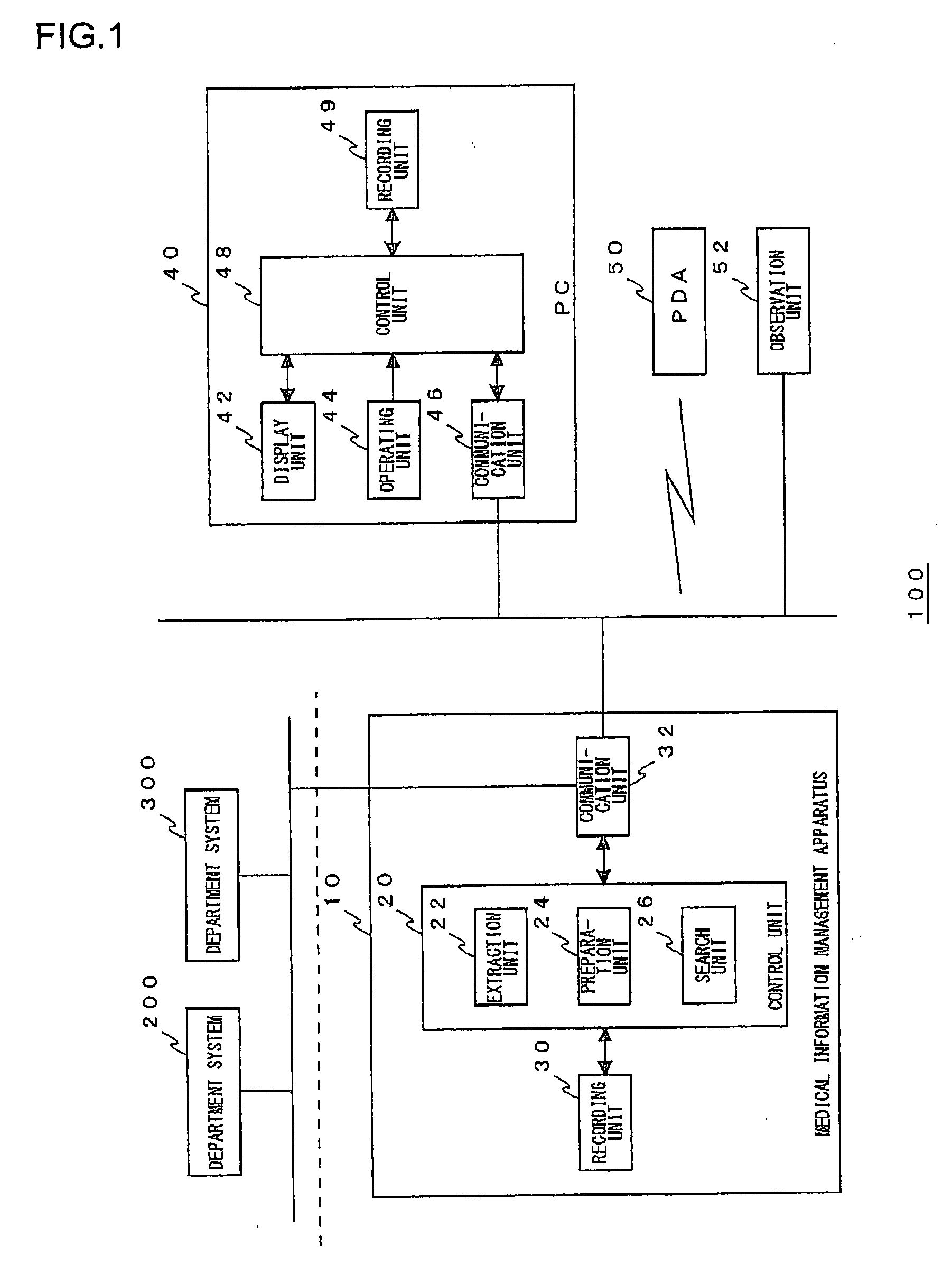
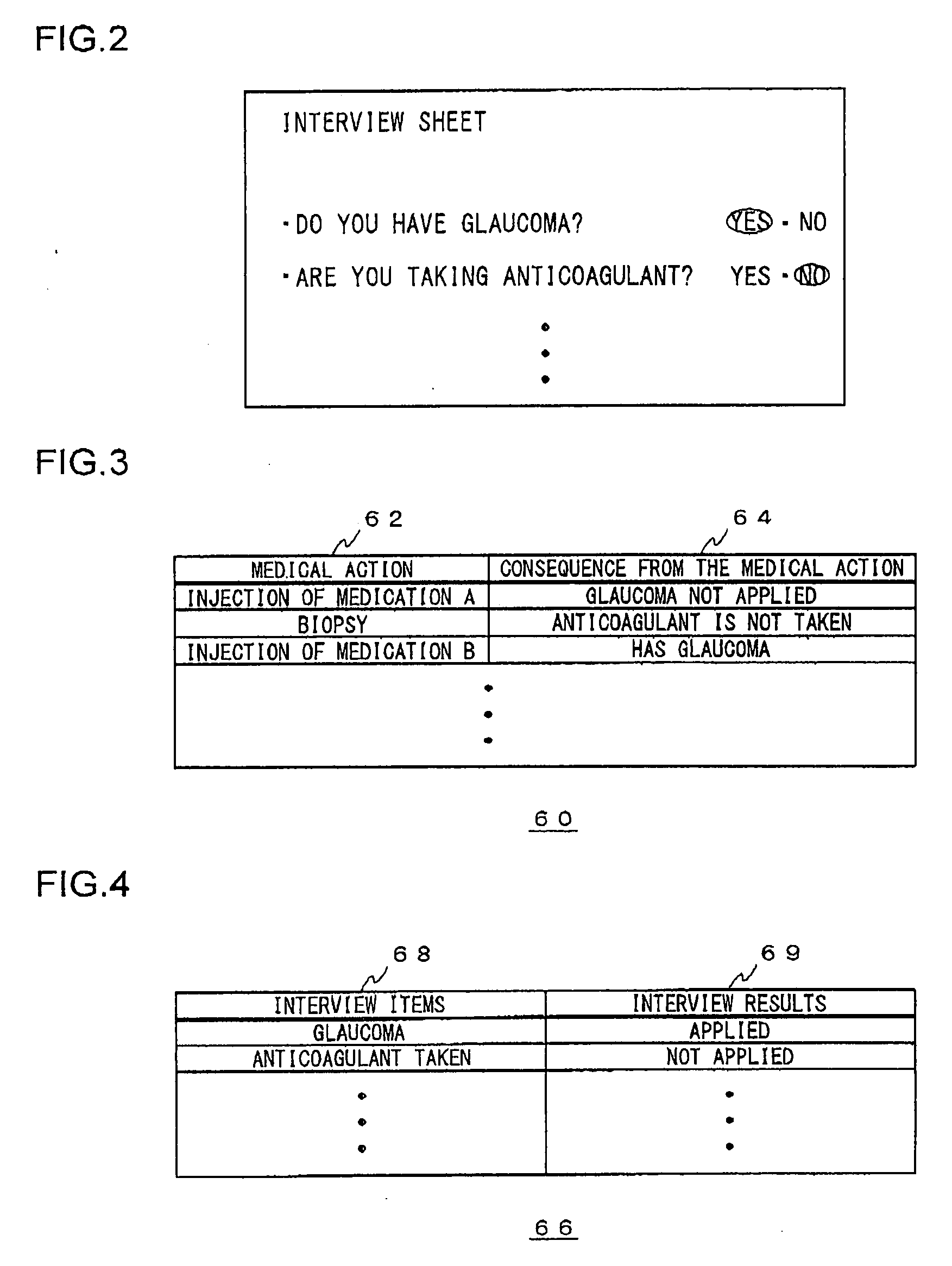
Medical information management apparatus for managing interview sheet data
InactiveUS20070299696A1Reduce troubleReliable dataData processing applicationsComputer-assisted medical data acquisitionLibrary scienceMedical treatment
A recording unit records implementation information on a medical treatment performed on a patient. An extraction unit extracts information necessary to prepare an interview result of an interview item for the patient, from the implementation information recorded in the recording unit. A preparation unit prepares the interview result by referring to the information extracted by the extraction unit, and prepares interview sheet data from the interview result and the interview item corresponding to the interview result.
Owner:OLYMPUS MEDICAL SYST CORP
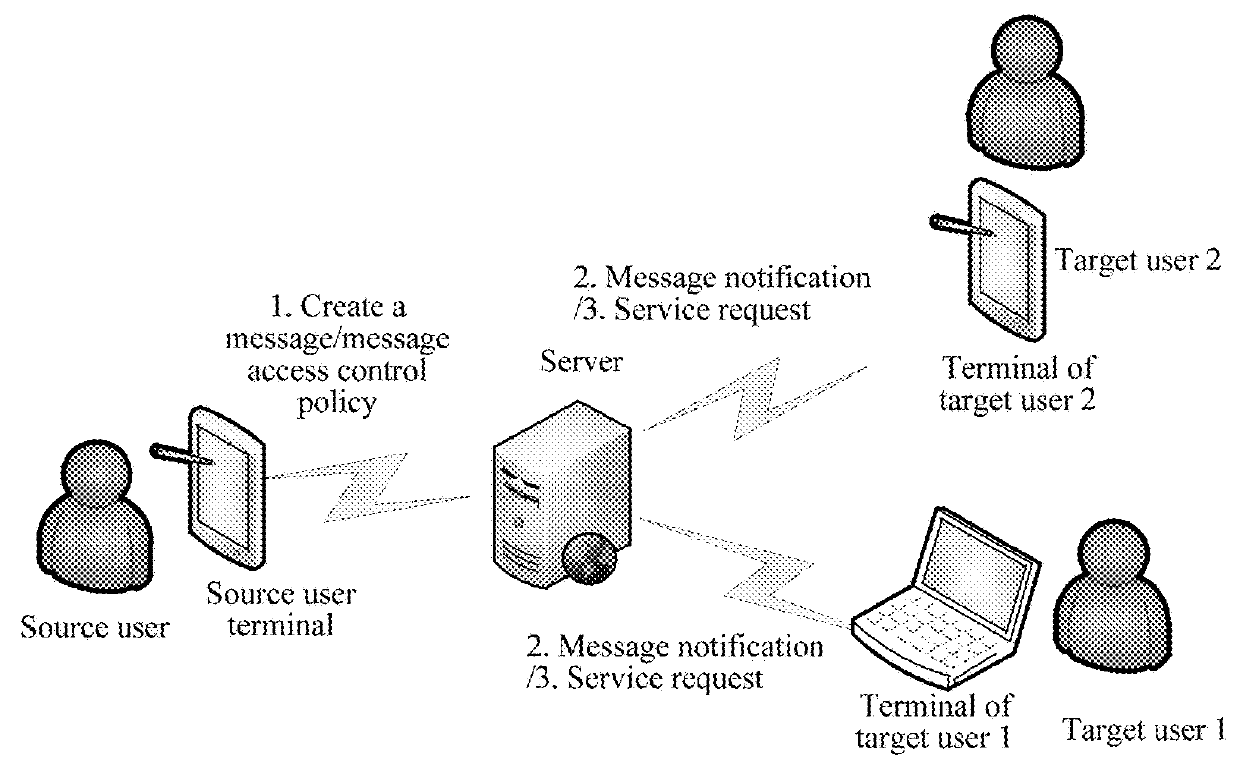
Message right management method, device and storage medium
ActiveUS20180270217A1Ensure information securityInformation securityServices signallingDigital data authenticationMessage passingWorld Wide Web
A message right management method, and a device and storage medium for implementing the method, are provided. The message right management method includes obtaining a message created by a source user, and sending a message notification to a target user in a social platform. The method further includes verifying the target user when receiving a request for logging onto a message page from the target user, and controlling logon of the target user to the message page on the basis of a verification result. The method further includes, when receiving a service request of the target user with respect to the message, determining, based on a message right control policy, whether the target user has a right corresponding to a service requested by the service request, and controlling a response to the service request according to a determining result.
Owner:TENCENT TECH (SHENZHEN) CO LTD
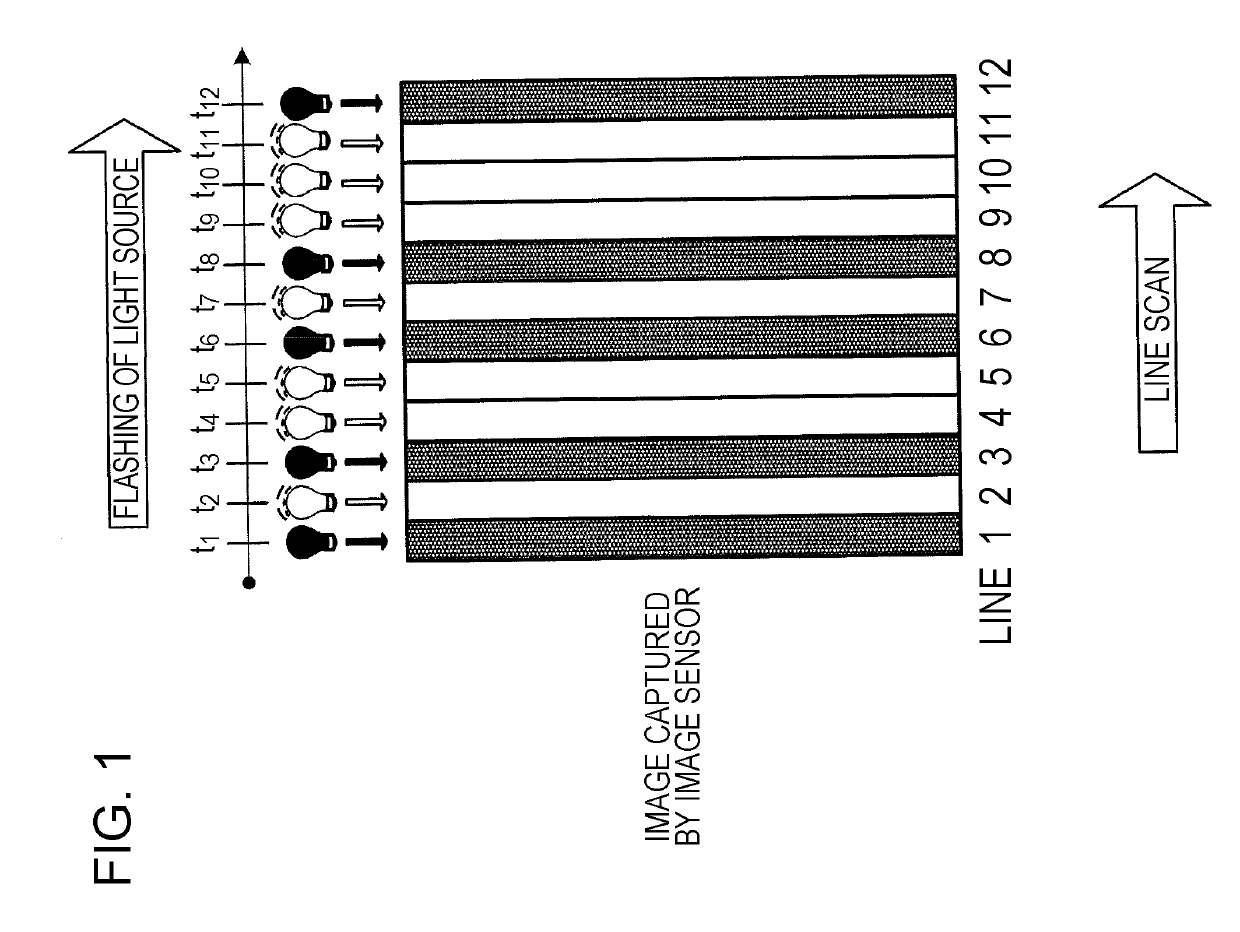
Terminal and communication method
ActiveUS20190223232A1Safely obtain informationInformation securityAssess restrictionNetwork topologiesRadio equipmentComputer terminal
A terminal (1050) includes a light receiver (151) that receives a light signal emitted by an apparatus (1000), the light signal including an identifier (SSID) of at least one base station (470); a receiver receiver (153) that performs a reception process on the received light signal to output reception data; a data analyzer (155) that selects one base station based on the identifier of the at least one base station that is included in the reception data; and a radio device (453) that establishes a wireless connection with the selected base station (470) by using the identifier of the base station (470) and wirelessly communicates with the base station (470).
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Method and system for information recording
ActiveUS20160092850A1Reduce consumptionReduce loadPayment circuitsCommerceTerminal equipmentComputer terminal
Embodiments of the present application disclose a method and system for recording purchase data performed by a first terminal device and a second terminal device. During operation, the first terminal device receives a command to record purchase data. In response to receiving the command to record purchase data, the first terminal device scans a digital object identifier generated by the second terminal device. The digital object identifier includes purchase data acquired by the second terminal device. The first terminal device then extracts and records the purchase data from the digital object identifier.
Owner:ADVANCED NEW TECH CO LTD
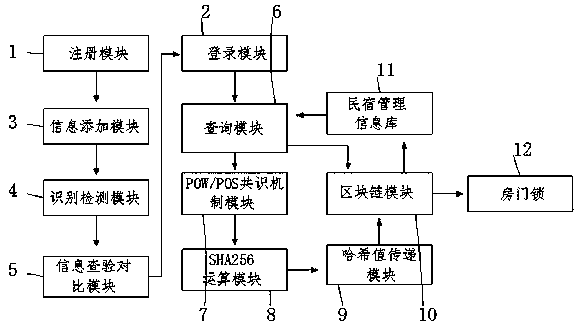
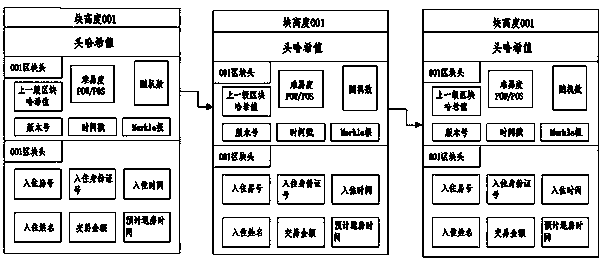
A method for realizing a home lodging management system based on a block chain
InactiveCN109190349AInformation securityEasy to search for dataData processing applicationsDigital data protectionManagement systemManagement information base
The invention relates to the technical field of artificial intelligence and block chain, and discloses a method for realizing a home lodging management system based on a block chain, which includes aregistration module, a login module, an information adding module, an identification detection module, an information checking and comparing module, a query module, a POW / POS consensus mechanism module, a SHA operation module, a Hash value, a block chain module, a home lodging management system and a room door lock. The output end of the registration module is electrically connected with the inputend of the information addition module, and the output end of the information addition module is electrically connected with the input end of the identification and detection module. The invention utilizes the decentralization technology in the block chain technology, According to the non-tampering and non-forgery technical characteristics of the block chain, through the compulsory identificationauthentication of the Internet lock authentication of identity information, to ensure the real name system to stay in the lodging, so that the information is more secure and reliable, so as to createa more convenient, fast, safe and efficient lodging management system.
Owner:安云印(天津)大数据科技有限公司
Navigation apparatus and information distribution system
ActiveUS8261083B2Ensure safetyQuick verificationInstruments for road network navigationKey distribution for secure communicationDistribution systemKey storage
A CPU of a navigation apparatus stores public keys to which priorities are set and which are published by an information distribution center in a public key storage section. The CPU of the navigation apparatus extracts an electronic signature of distribution data which is distributed from the information distribution center and verifies the electronic signature by using only ‘valid’ public keys among the public keys in order of the priorities. The CPU of the navigation apparatus determines that the distribution data is valid information which is distributed from the information distribution center when the electronic signature passes verification.
Owner:AISIN AW CO LTD +1
Recording medium holder having one or more recording mediums
ActiveUS7093049B2Easy searchSafe and efficient managementUser identity/authority verificationMemory adressing/allocation/relocationLiquid-crystal displayLiquid crystal
A recording medium holder enables a user to easily find a desired recording medium from recording mediums that the user manages. The recording medium holder includes a recording medium holding unit for holding a plurality of recording mediums, a liquid crystal displaying unit for displaying each of the plurality of recording mediums held in the recording medium holding unit by an icon, and an information displaying unit for displaying information of a recording medium that corresponds to an icon clicked in the liquid crystal displaying unit, the information including ID information, title information, index information, and other information. The information is read out from the recording medium at a first click, and from a storing unit at a second click and after.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
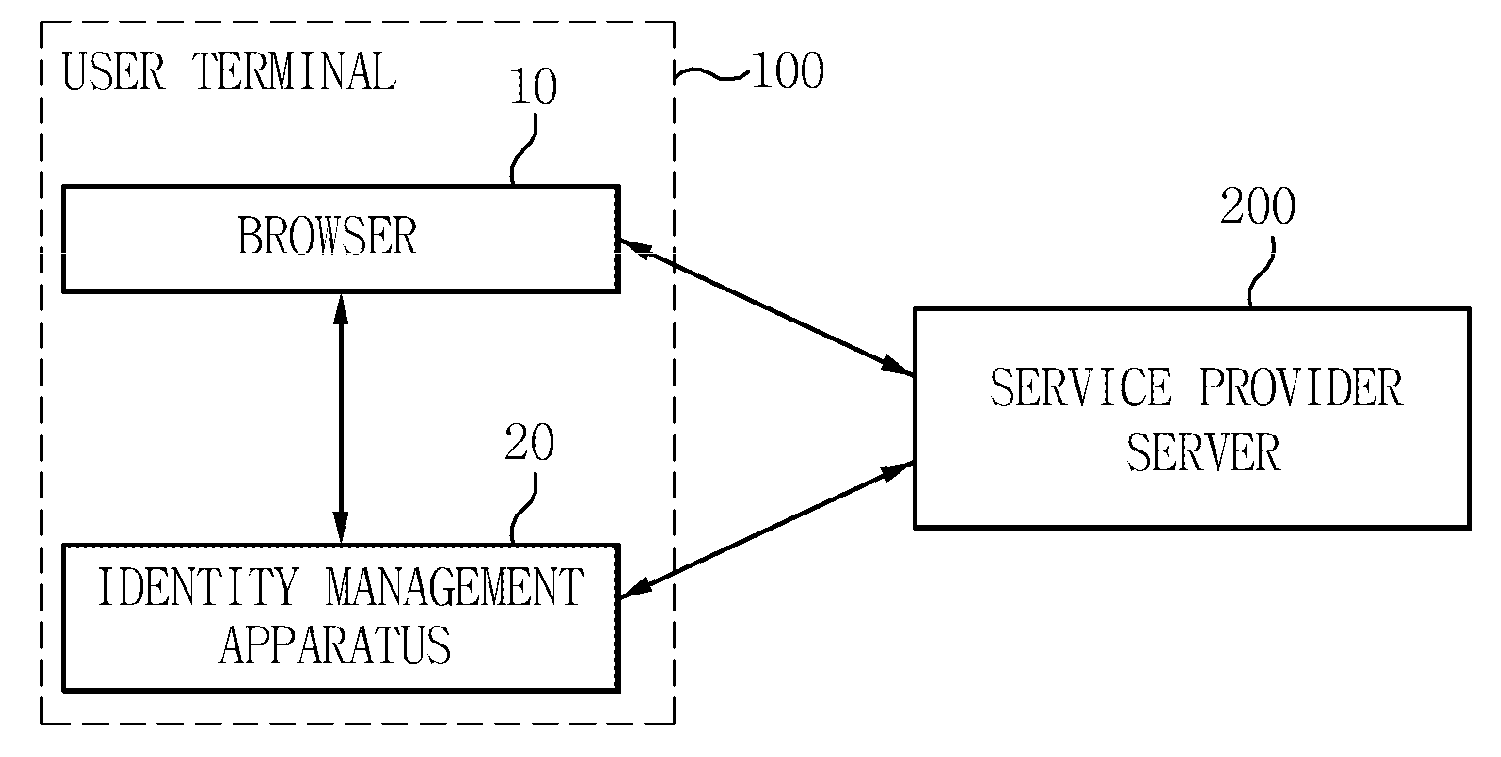
System for user-centric identity management and method thereof
InactiveUS20100310078A1Reduce harmConvenientlyKey distribution for secure communicationPublic key for secure communicationService protocolComputer terminal
A user terminal for a user-centric identity management system includes: a browser that requests a service to the service provider server and receives a service parameter in which a plurality of selectable protocol parameters corresponding to the service are recorded from the service provider server; an interaction unit that selects any one protocol parameter among the plurality of protocol parameters by receiving the service parameter through the browser; and a service processing unit that performs a service protocol with the service provider server on the basis of the protocol parameter selected through the interaction unit, and receives token information required to receive the service from the service provider server and transfers the token information to the browser.
Owner:ELECTRONICS & TELECOMM RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com