Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
201results about How to "Difficult to forge" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
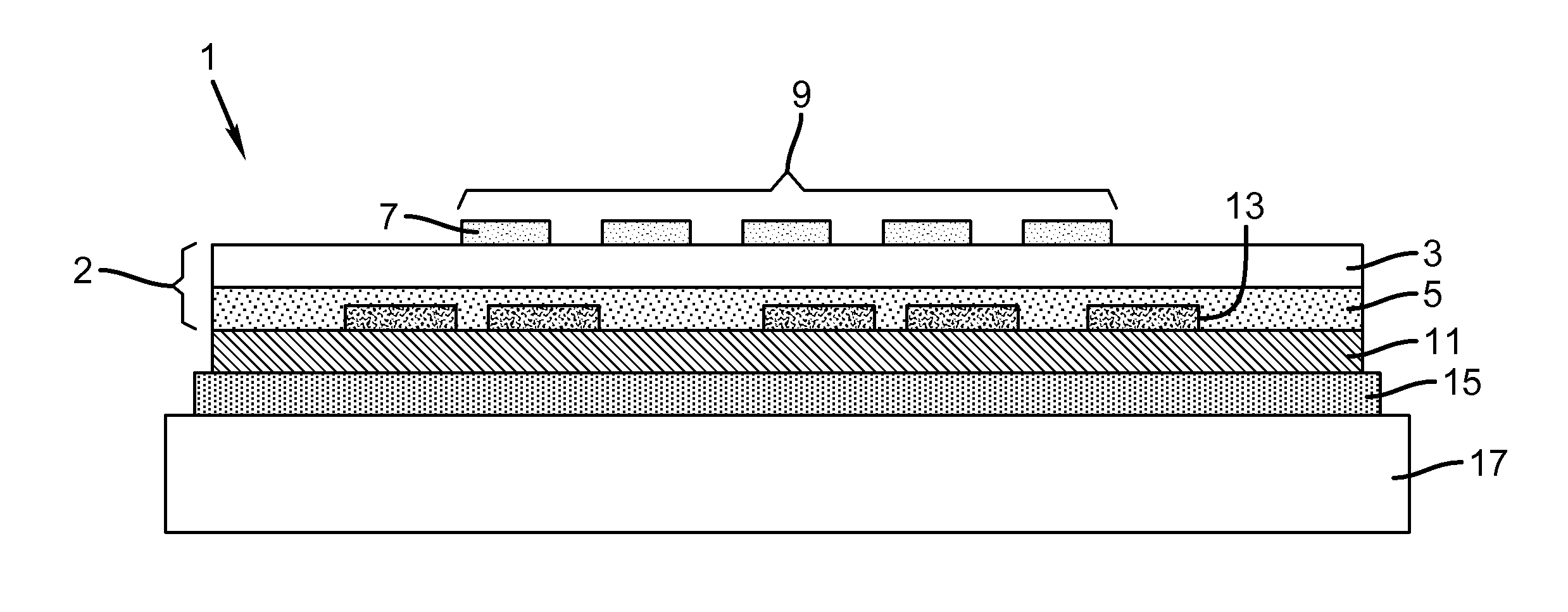
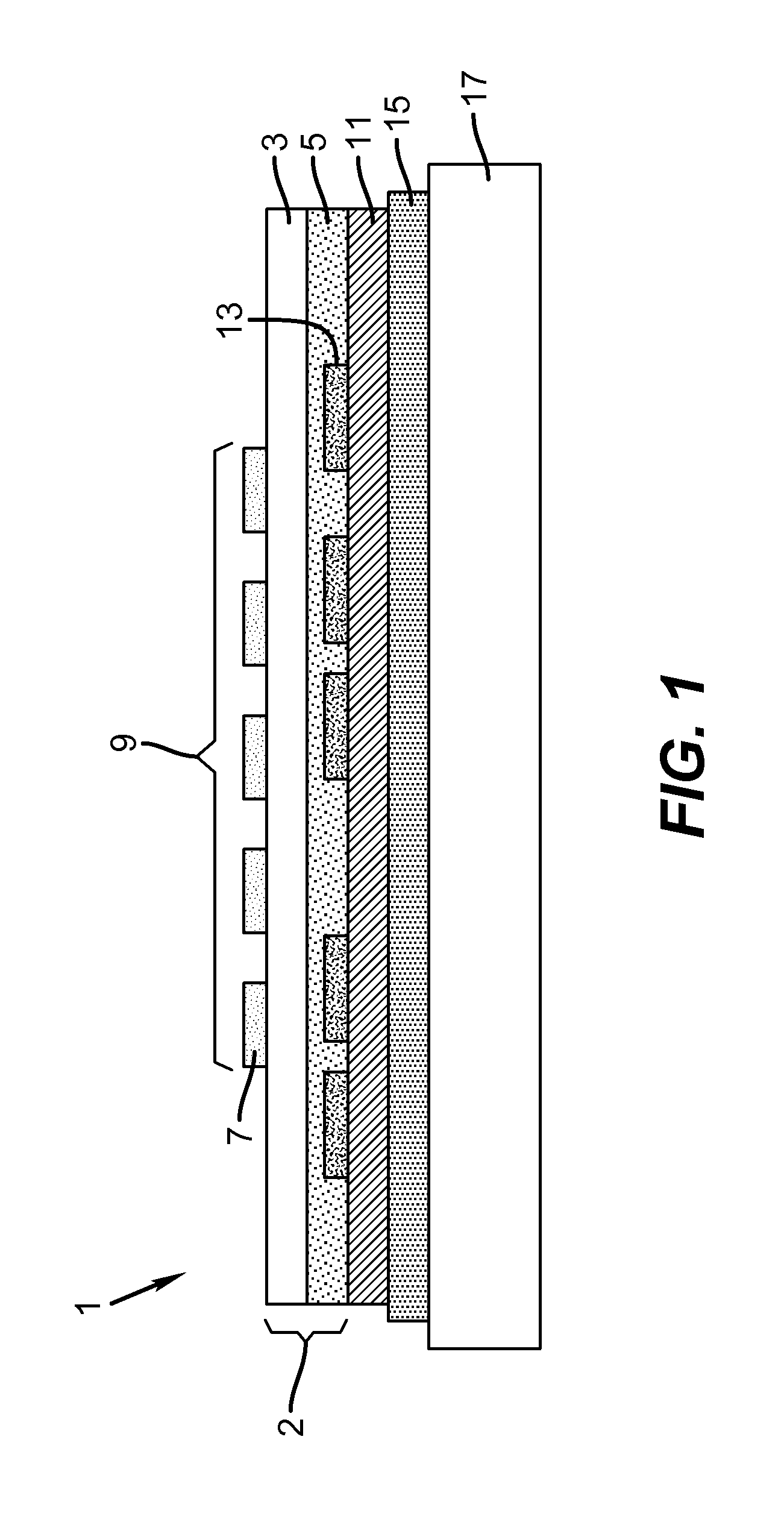
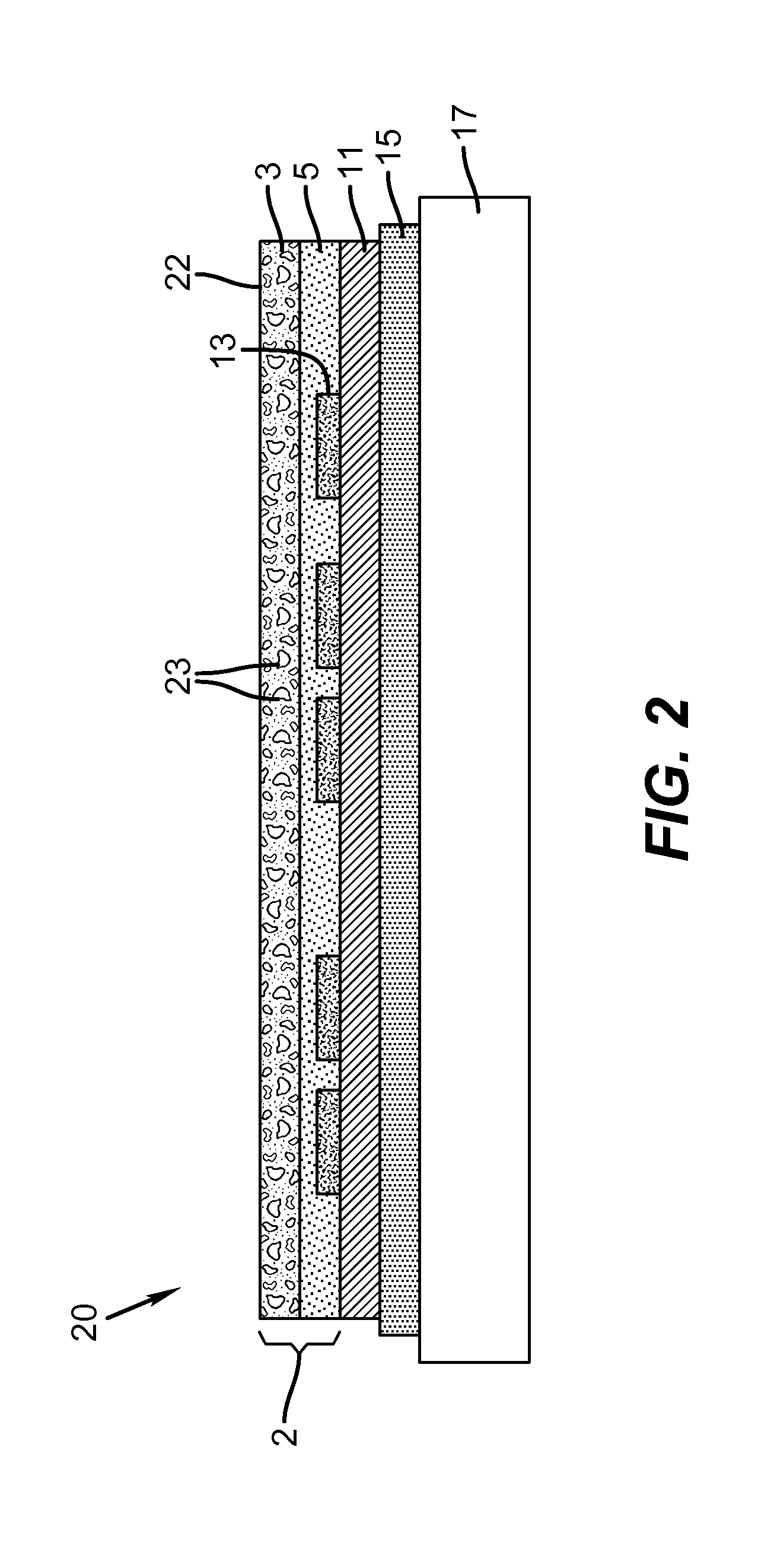
Methods and systems for processing assets
InactiveUS20170331896A1Improve securityRemoving reliance on a central authoritySynchronising transmission/receiving encryption devicesUser identity/authority verificationDistributed computingAuthentication
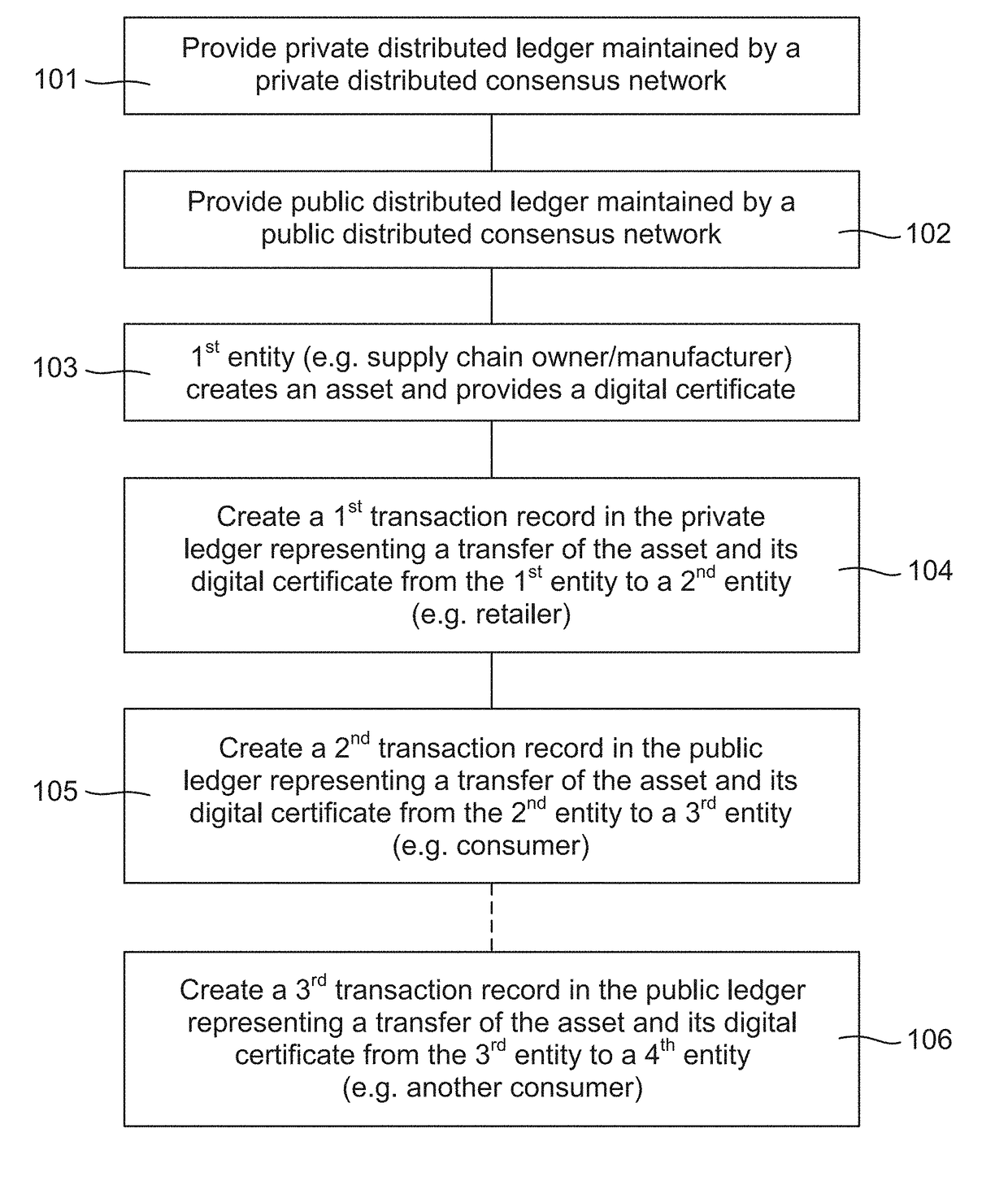
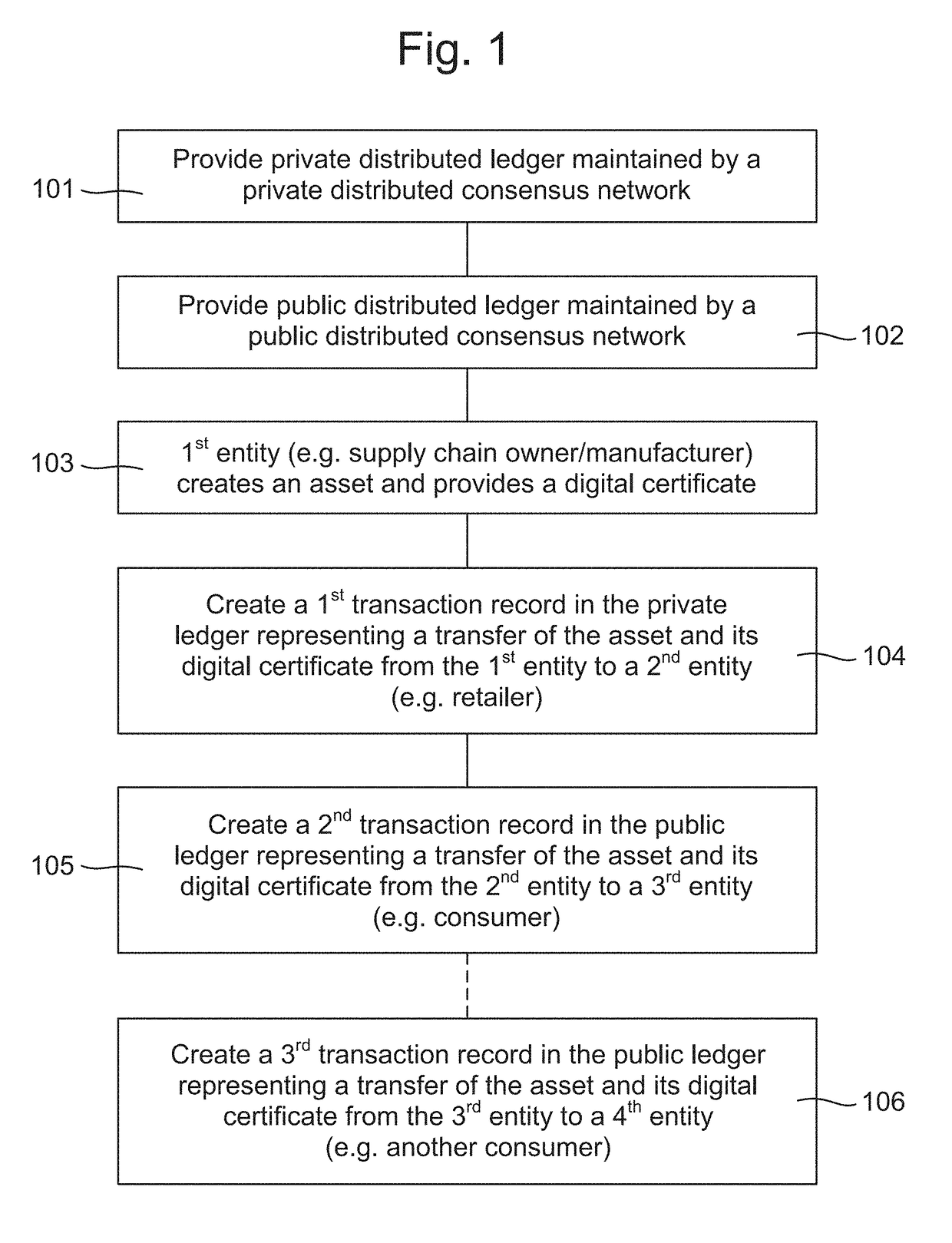
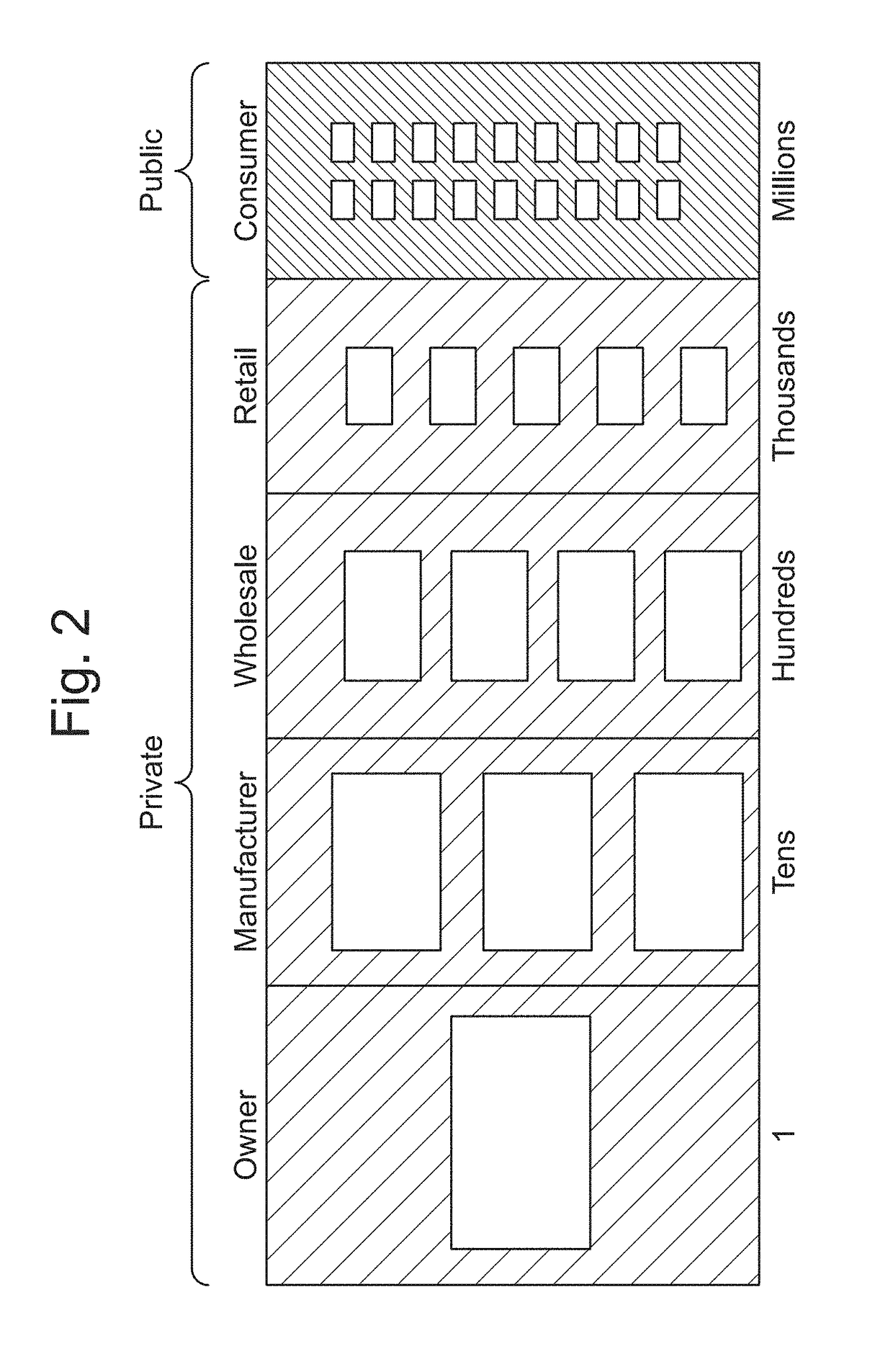
A computer-implemented method for processing an asset within a supply chain includes: providing a first distributed ledger maintained by nodes within a first distributed consensus network; providing a second distributed ledger maintained by nodes within a second distributed consensus network; creating the asset by a supply chain first entity associated with at least one node within the first network, and providing a digital certificate uniquely associated with the asset for authentication; creating a first transaction record in the first distributed ledger representing an asset transfer and its associated digital certificate from the first entity to a supply chain second entity associated with at least one node within the first network; and creating a second transaction record in the second distributed ledge representing an asset transfer and its associated digital certificate from the second entity to a supply chain third entity associated with at least one node within the second network.
Owner:DE LA RUE INT LTD
Methods and apparatus for protecting against IP address assignments based on a false MAC address
ActiveUS7320070B2Remove the burdenCollect revenueTime-division multiplexMultiple digital computer combinationsIp addressCAC protocol
Methods and apparatus detecting attempts to obtain IP addresses by faking a MAC address in a data portion of an IP address request message are described. In accordance with the present invention, rather than use standard address allocation protocols, e.g., ARP, the DNS DCHP contacts the requesting edge router via a private secure network. The MAC address received in the address request is compared to the MAC addresses stored in the edge routers port / MAC address resolution table. If the MAC address received in the request message cannot be found in the edge router's table which was created from the MAC address included in the message's header, a fraudulent attempt to obtain a MAC address is declared. The fraudulent attempt to obtain an IP address can be reported and steps taken to identify the perpetrator of the fraud.
Owner:VERIZON PATENT & LICENSING INC
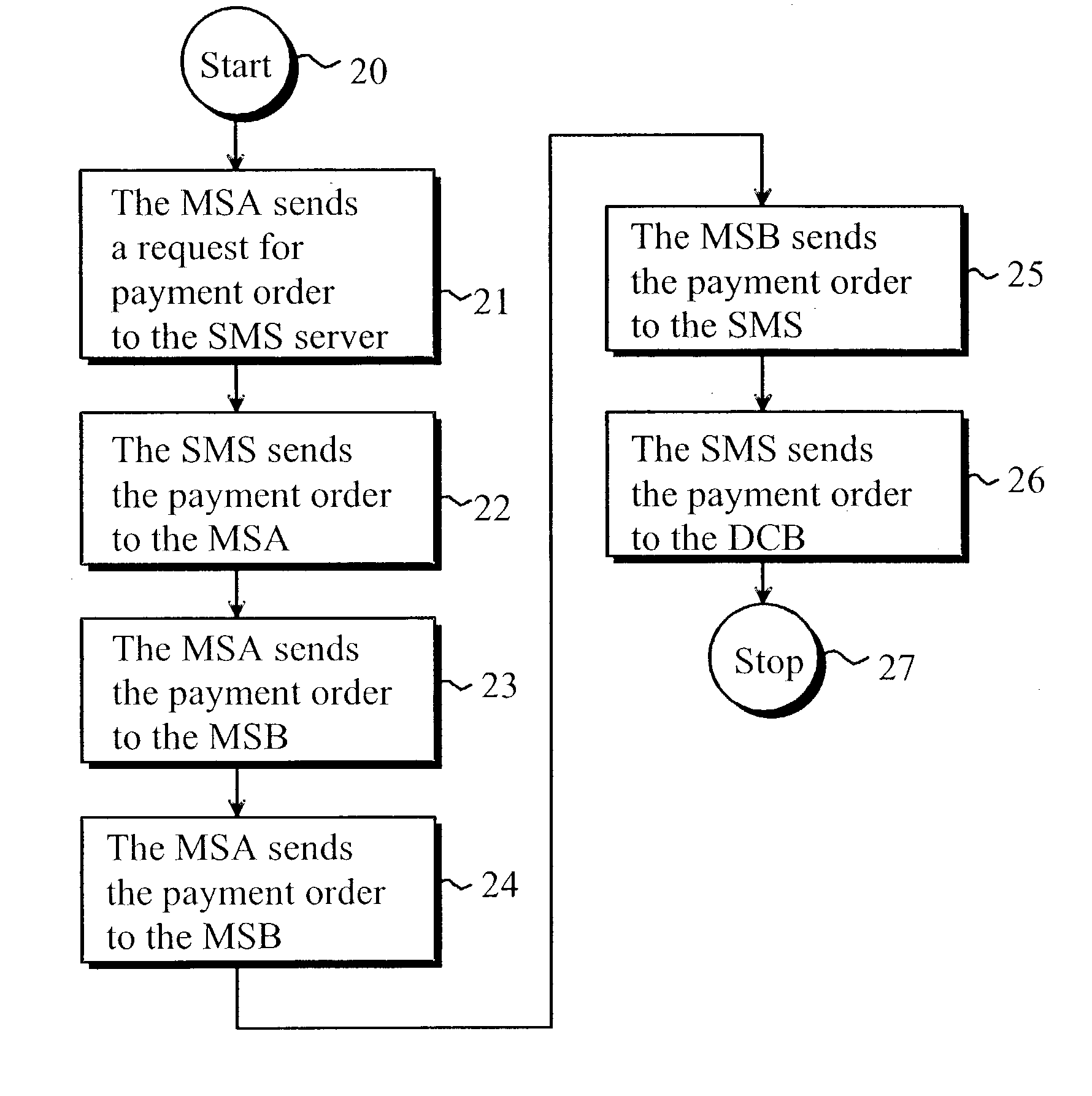
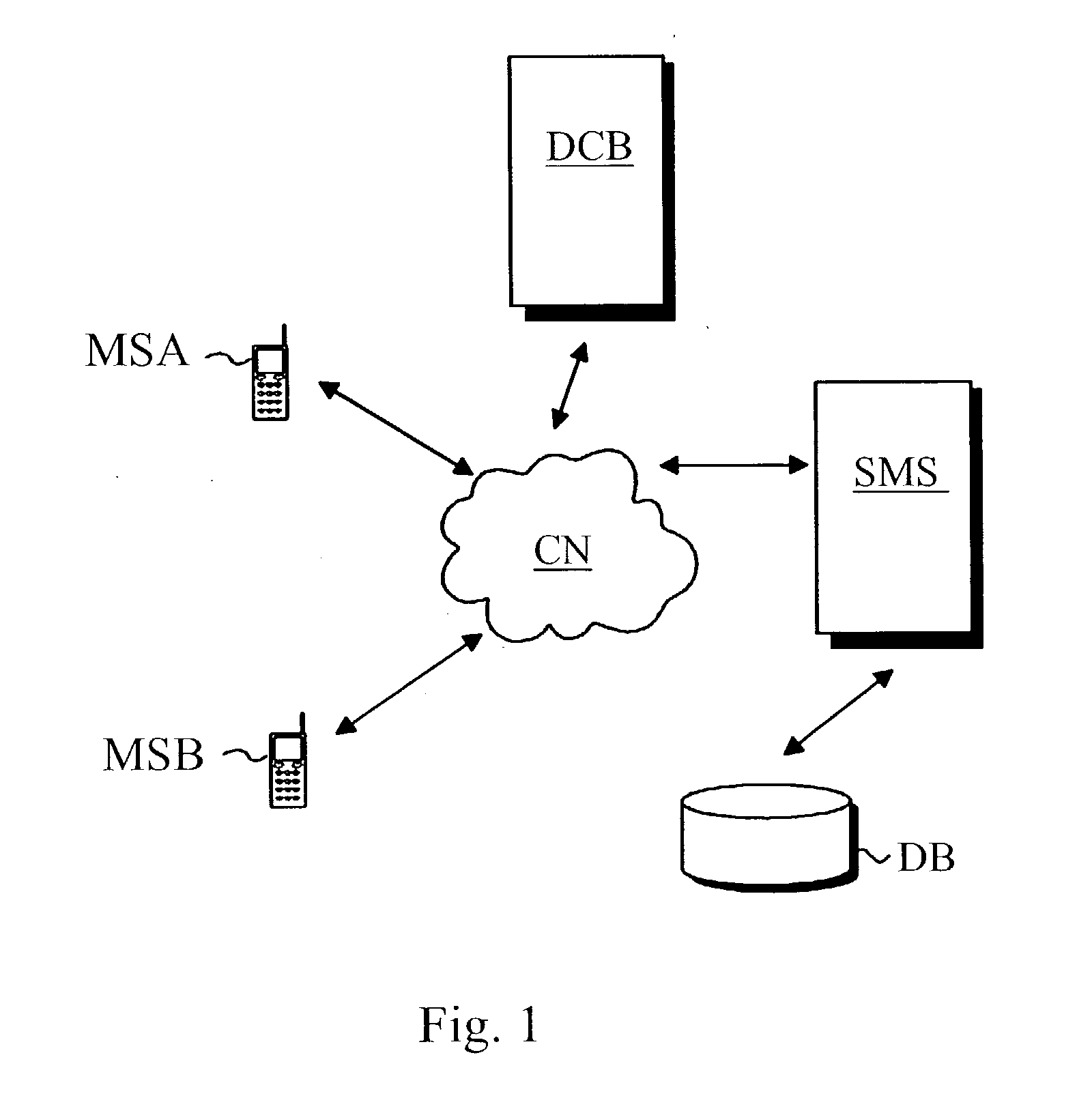
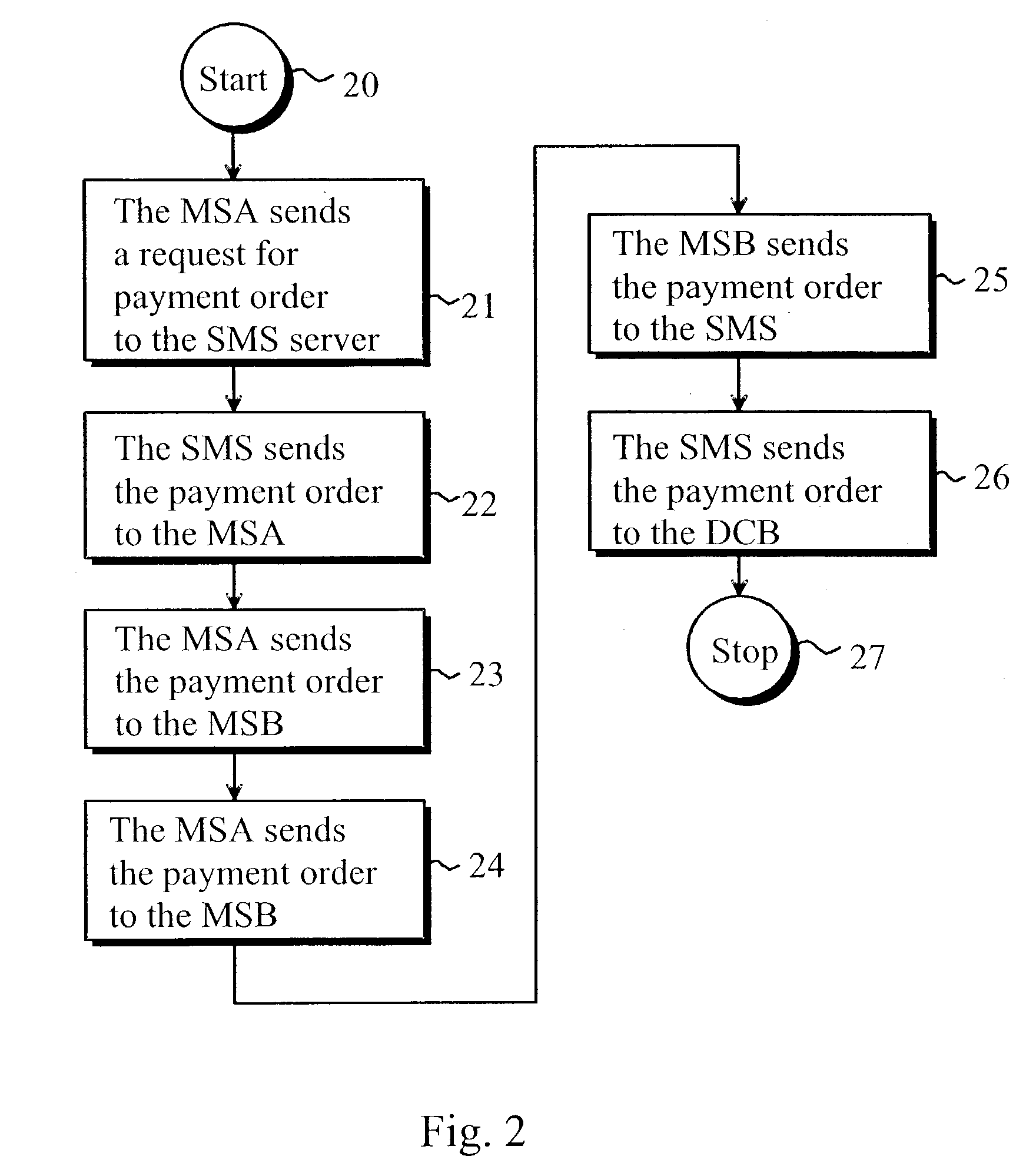
Method of implementing digital payments
ActiveUS20030126078A1Eliminate, orAlleviate, the drawbacks and deficienciesFinanceComputer security arrangementsPaymentTerminal equipment
A method for transferring a digital payment order from a first terminal device to a second terminal device, and for saving the payment order on a payment order server. A payment order request is sent from the first terminal device to the payment order server and, in response, the requested payment order is sent from the payment order server to the first terminal device. The payment order is thereafter transmitted from the first terminal device to the second terminal device, and the payment order is then transferred from the second terminal device to the payment order server to be honored. A message confirming the honoring of the payment order is sent to the second terminal device.
Owner:MIND FUSION LLC
Kinematic images formed by orienting alignable flakes
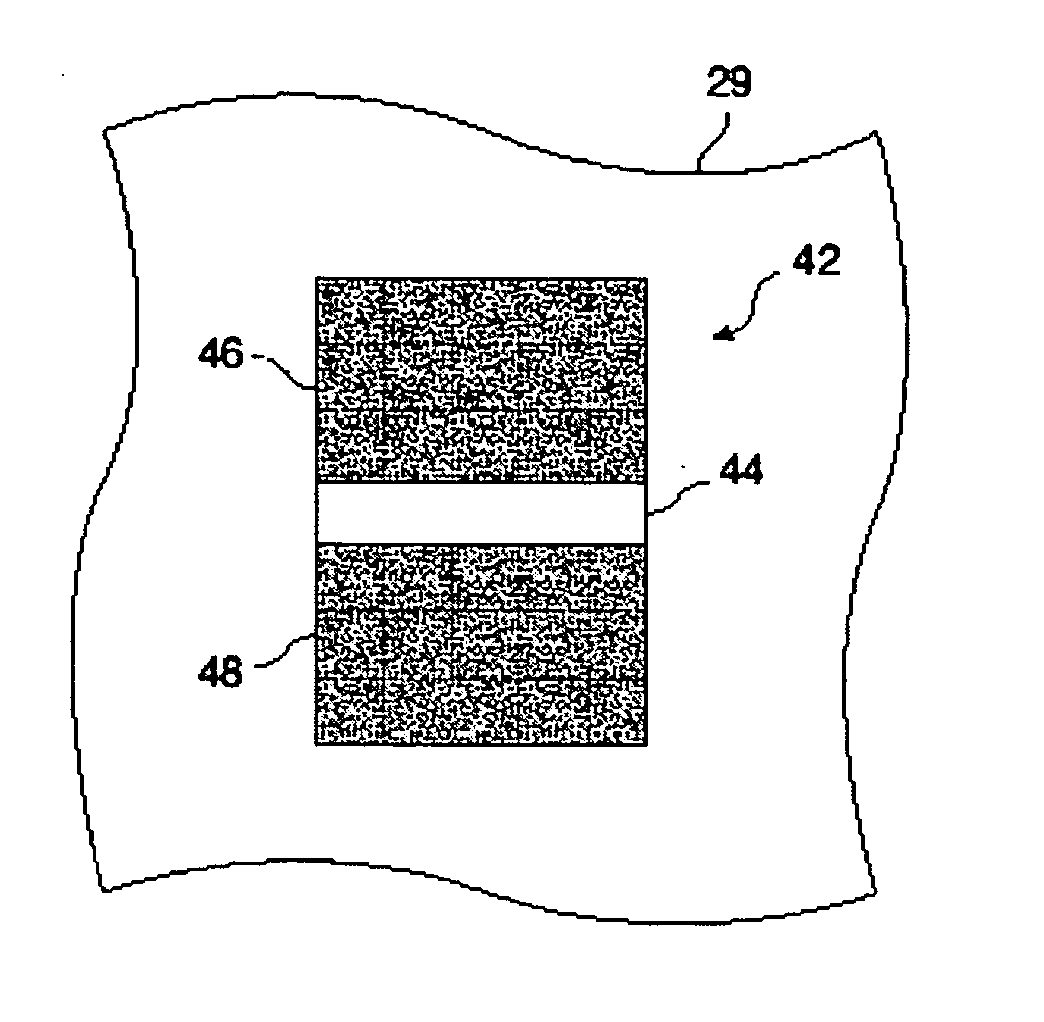
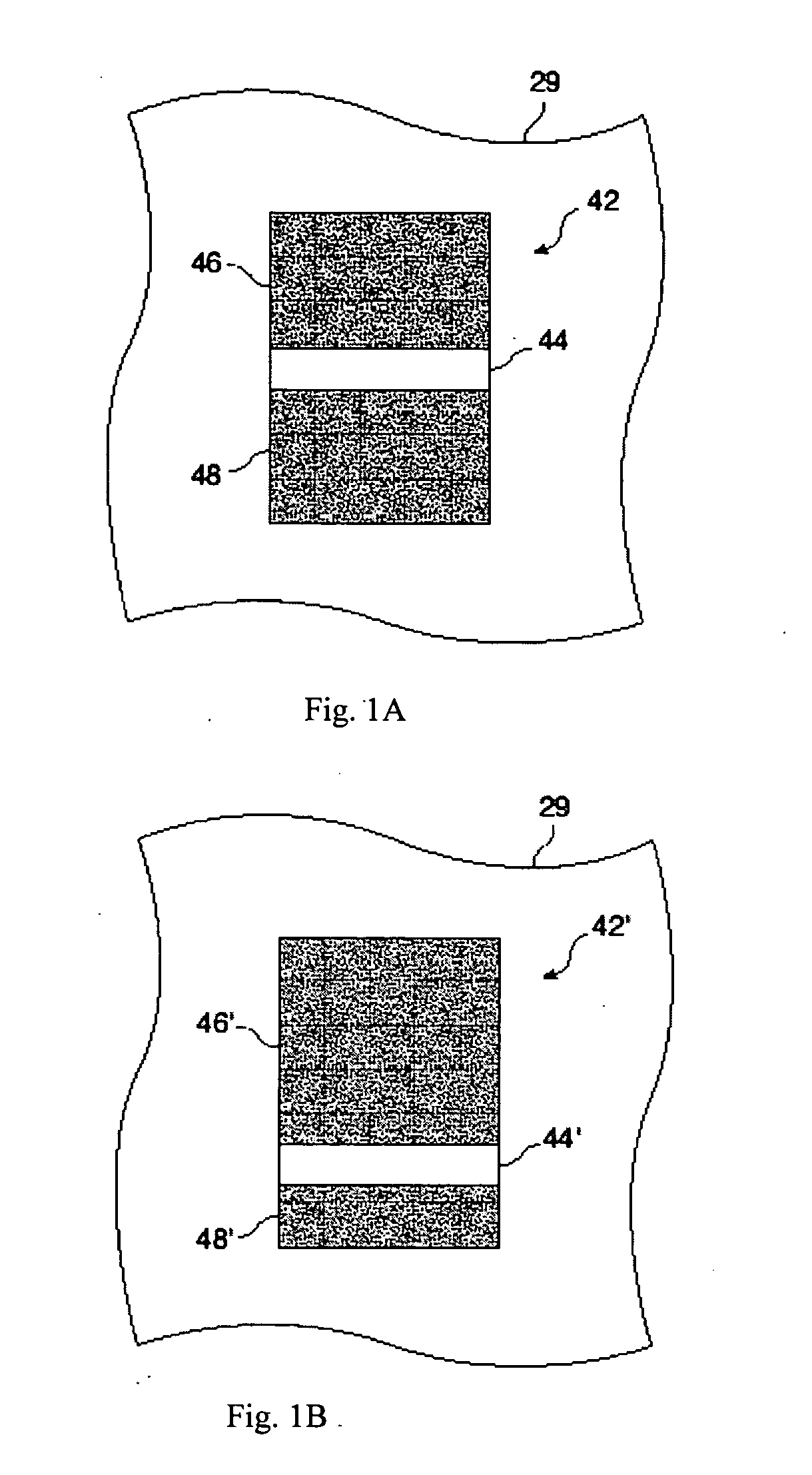
ActiveUS20060097515A1Difficult to counterfeitEasily identifiableDecorative surface effectsPattern printingEngineeringBank note
An image is disclosed comprised of flakes in a carrier, such as an ink vehicle or a paint that can be aligned in a magnetic field. The flakes are aligned so as to produce one or more kinematic features such as a rolling bar that appears to move as the image is tilted. These images can provide security features on high-value documents, such as bank notes.
Owner:VIAVI SOLUTIONS INC
Collectible item and code for interactive games
InactiveUS20050287925A1Improvement is requiredHigh manufacturing costDecorative surface effectsCard gamesEngineeringLaser etching
Owner:MATTEL INC
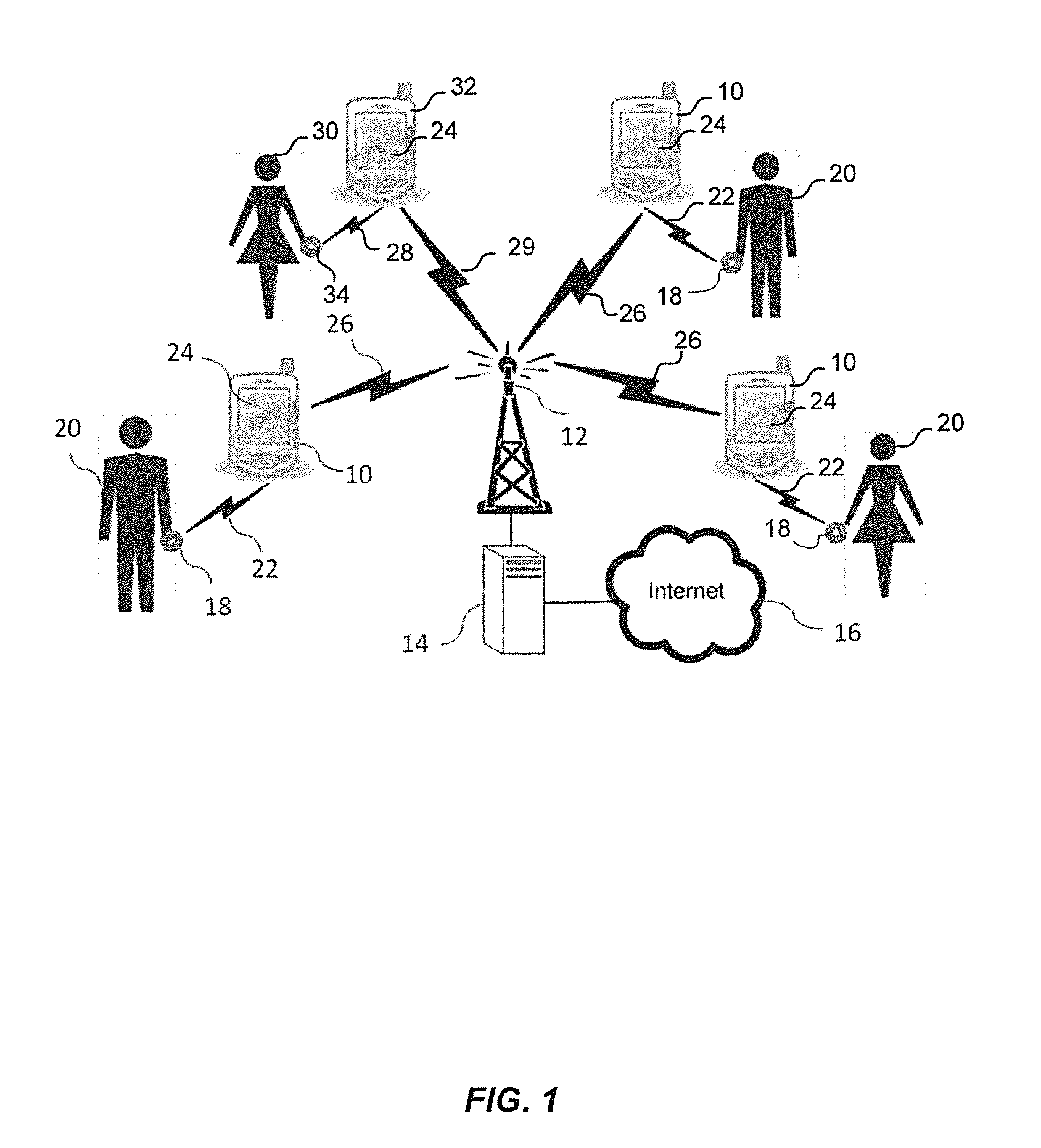
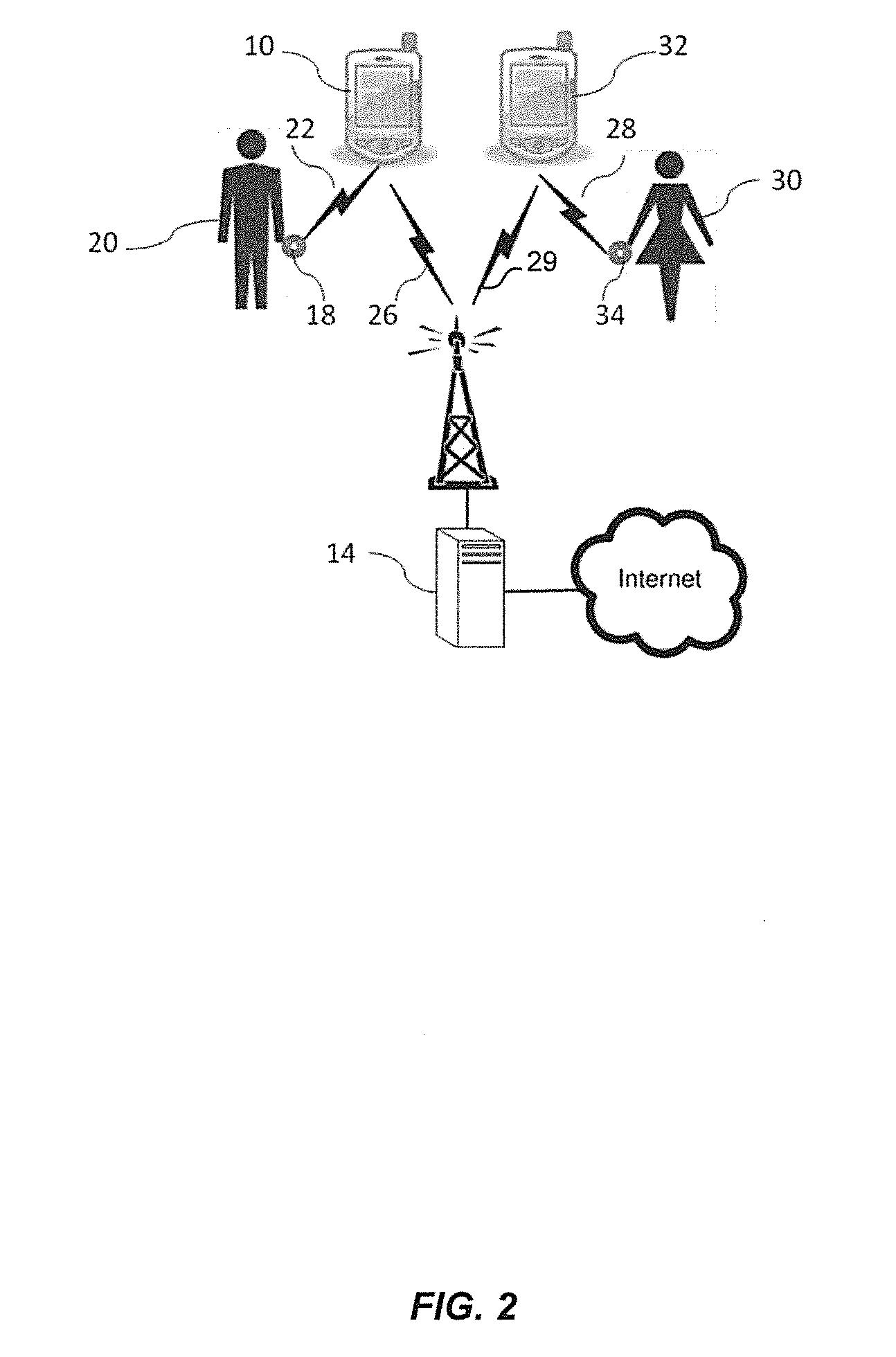
Method and apparatus for monitoring emotional compatibility in online dating
InactiveUS20140221866A1Difficult to forgeObjective emotional profileElectroencephalographyServices signallingComputer compatibilityHuman–computer interaction
Methods, devices, and systems provide for capturing and sharing emotion data to determine the emotional compatibility of couples for online dating or longer-term relationships. An emotion monitoring device (EMD) measures physiological signals obtained from biosensors and computes an emotion profile in response to standardized stimuli displayed to the user. The emotion profile for each user is transmitted to an internet server. The emotion profiles are correlated with other variables measuring successful dating or marital relationships to enhance the selection of suitable partners from the pool of users. In an alternative embodiment, emotion data are captured from a couple during a face-to-face or online dating interaction. Each person shares their emotion data with the other during the interaction. In an embodiment for face-to-face or virtual dating games the emotion data of a group of users, each equipped with an EMD, are captured, displayed, and shared.
Owner:THE VISTA GRP LLC
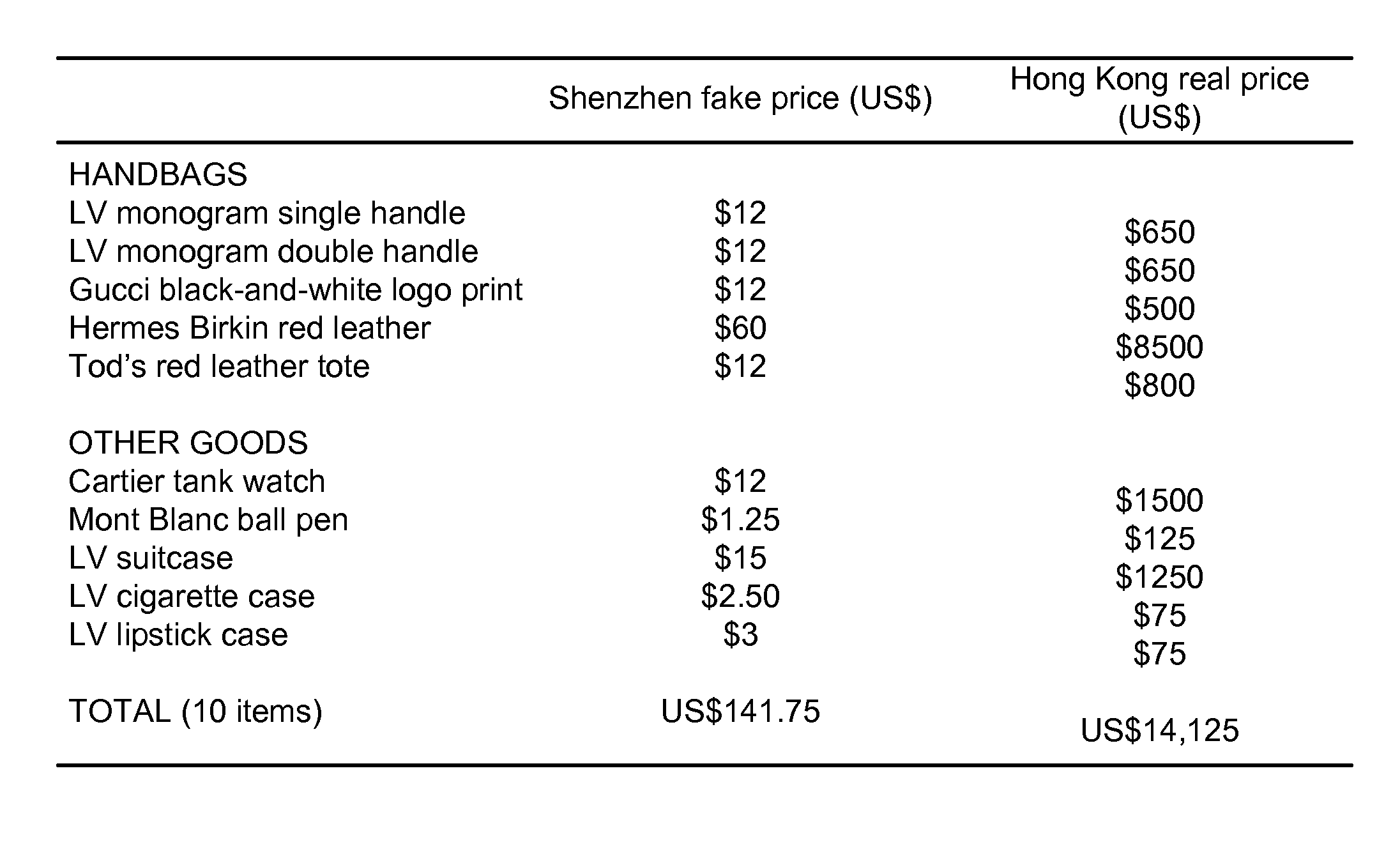
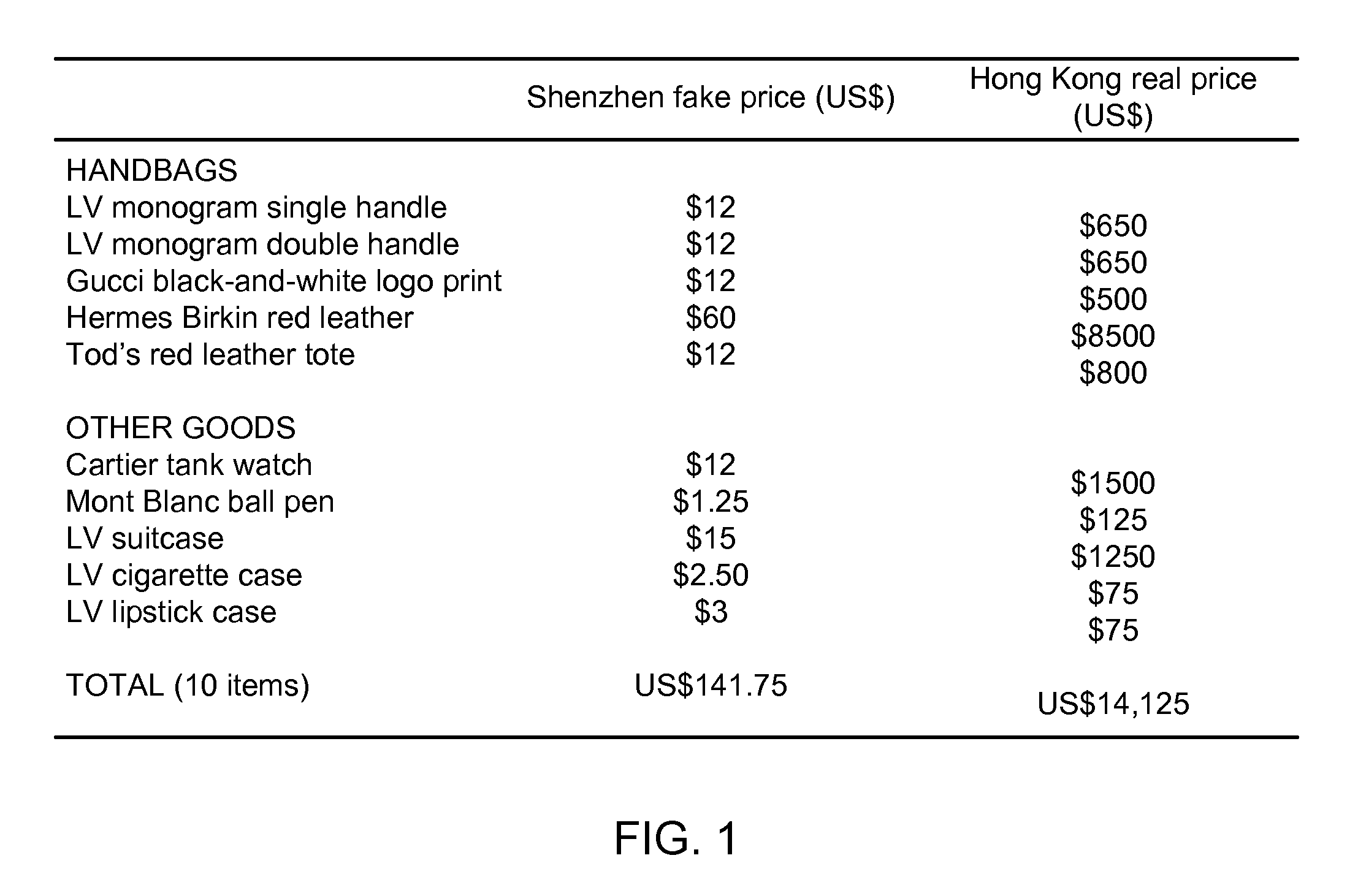
Protecting a manufactured item from counterfeiting
InactiveUS8108309B2Easy to manageDifficult to forgeHand manipulated computer devicesComputer security arrangementsProgramming languageSerial code
A method and system are described for protecting a manufactured item from counterfeiting. The manufactured item, which is marked with an identifier, such as a serial number, is associated with a code generator that has secret functions and data for generating verification codes. The manufactured item is then supplied along with the corresponding code generator. Thereafter, the identifier from the manufactured item and the verification code generated by the code generator are used to verify authenticity of the manufactured item.
Owner:PROVALIDATE
Report system and method using context-sensitive prompt objects
InactiveUS20060026122A1Enhance protectionCreate efficientlyDigital data information retrievalDigital data processing detailsBusiness intelligenceReporting system
A reporting system that incorporates a context sensitive prompt object in a report definition to enable questions to be answered automatically by the reporting system (e.g., decision support system, business intelligence and OLAP) at report execution time. The context sensitive prompt object is an object separate from the report such that the context sensitive prompt object may be used by a plurality of different reports. The answer is defined at least in part by a contextual feature of the report execution.
Owner:MICROSTRATEGY
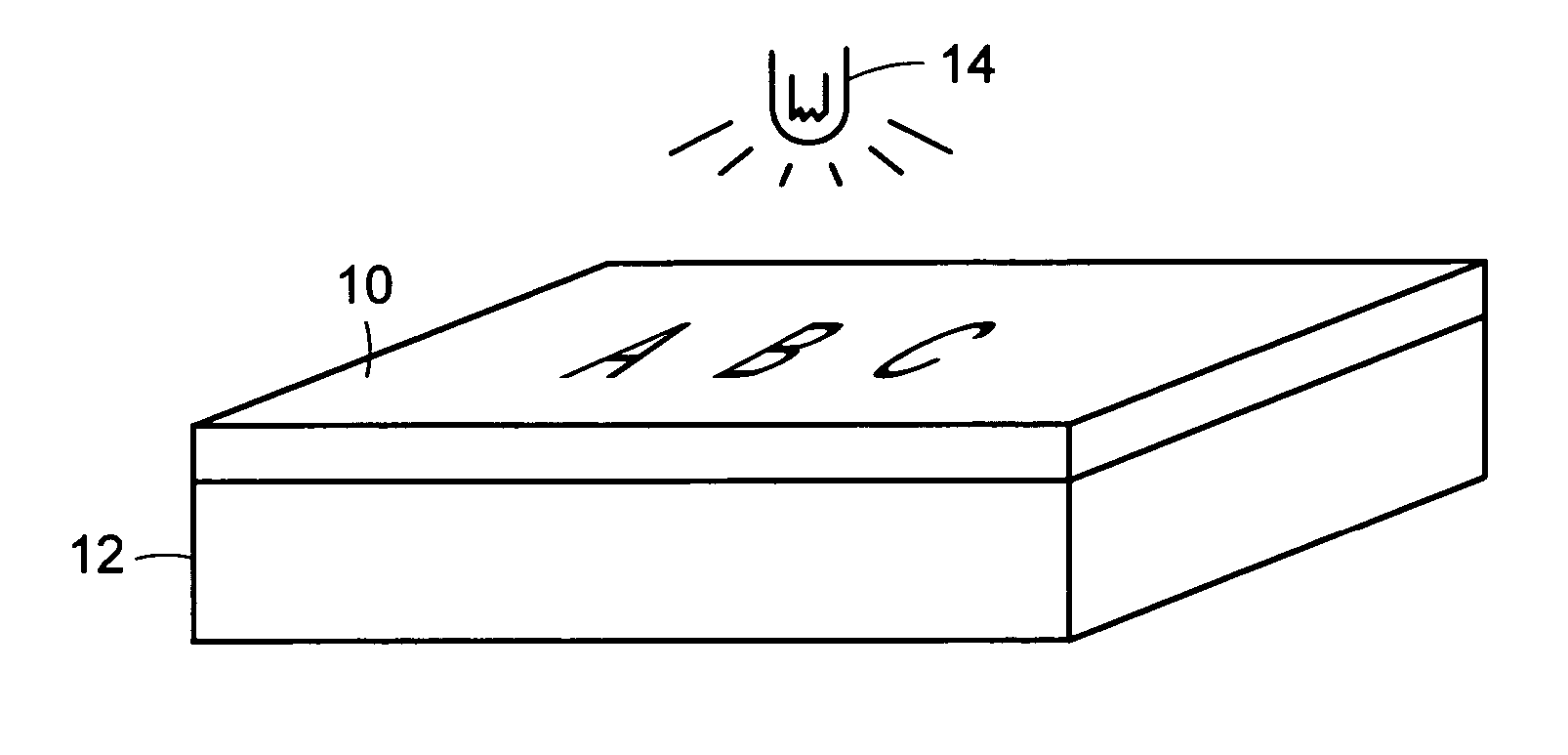
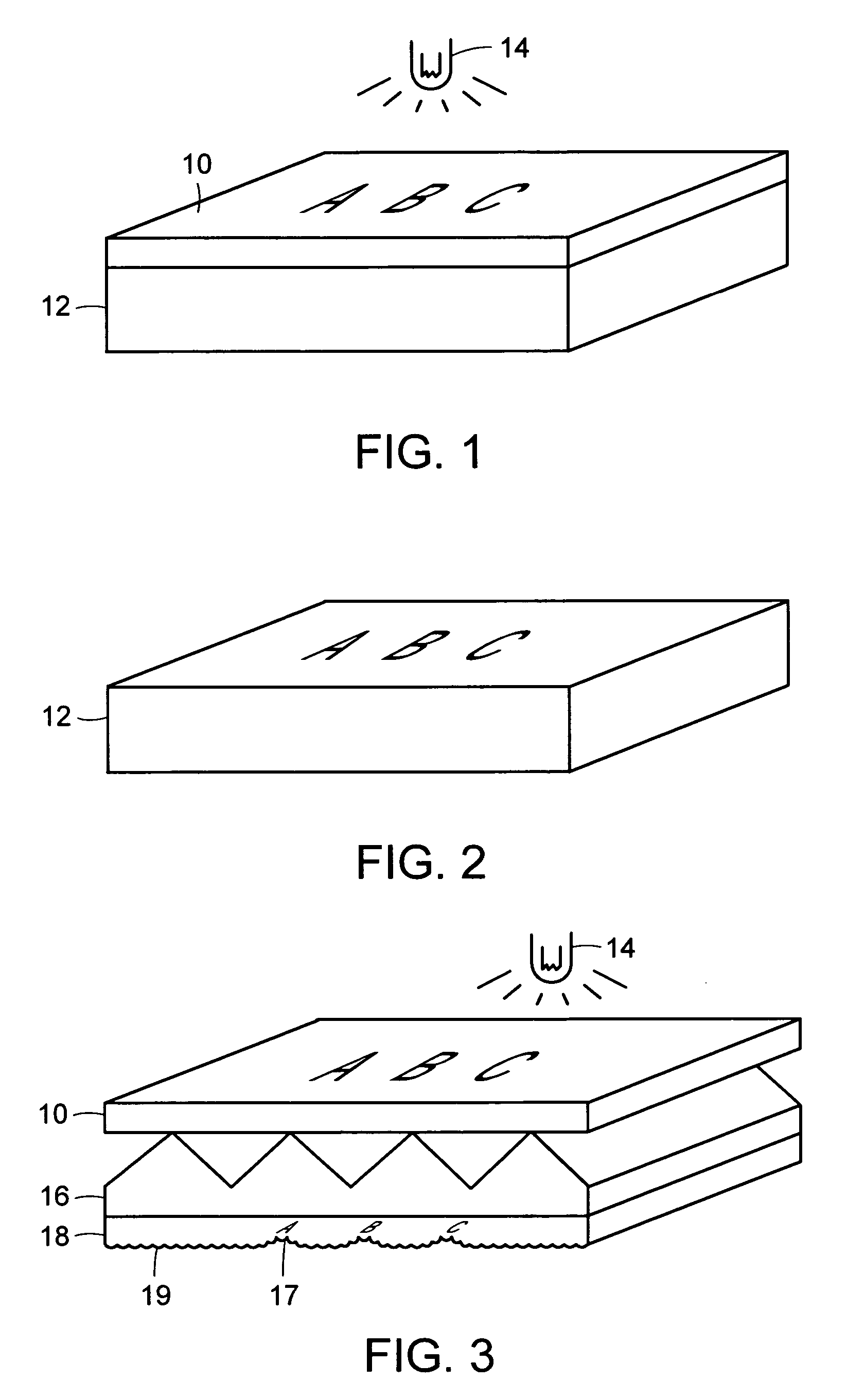
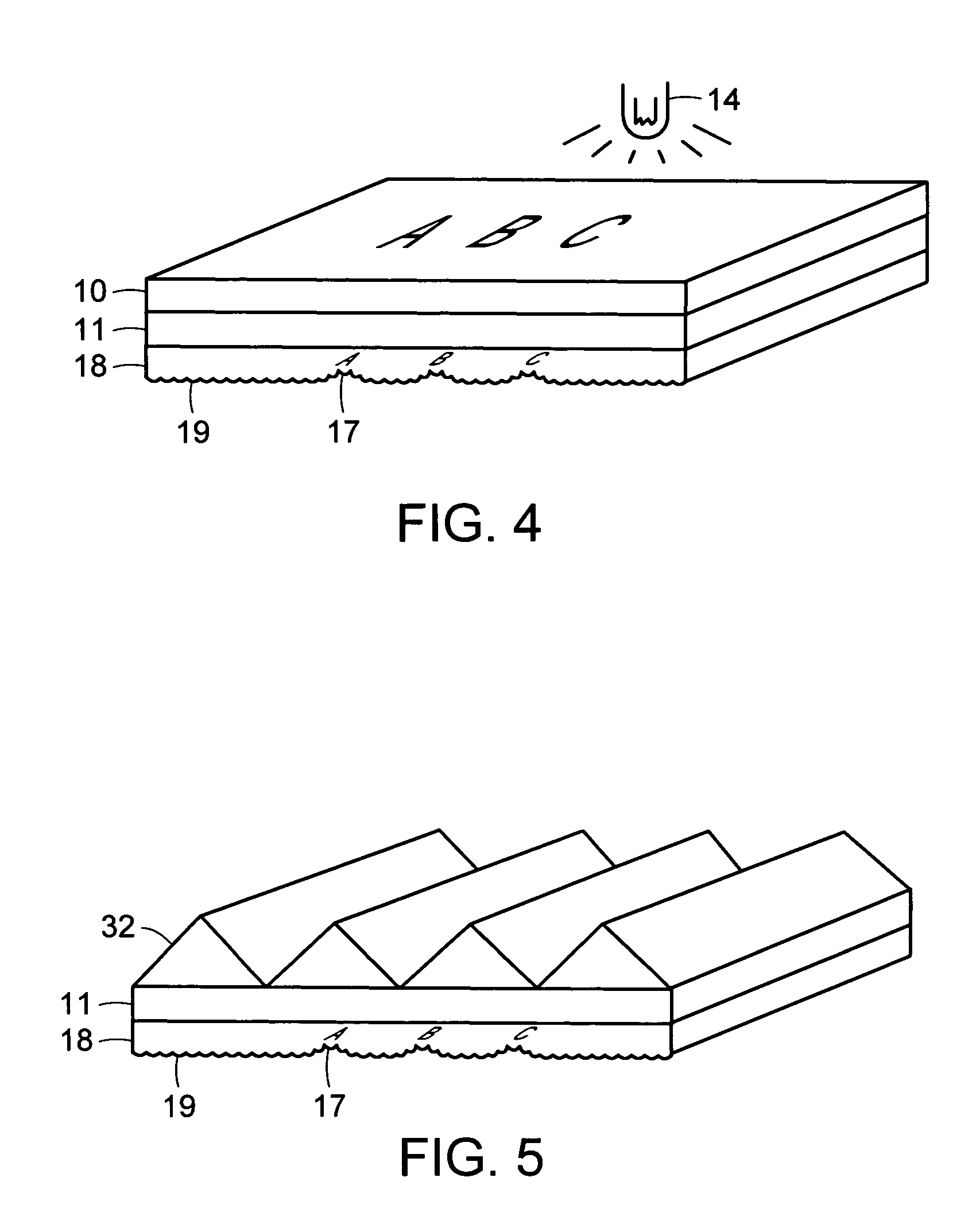
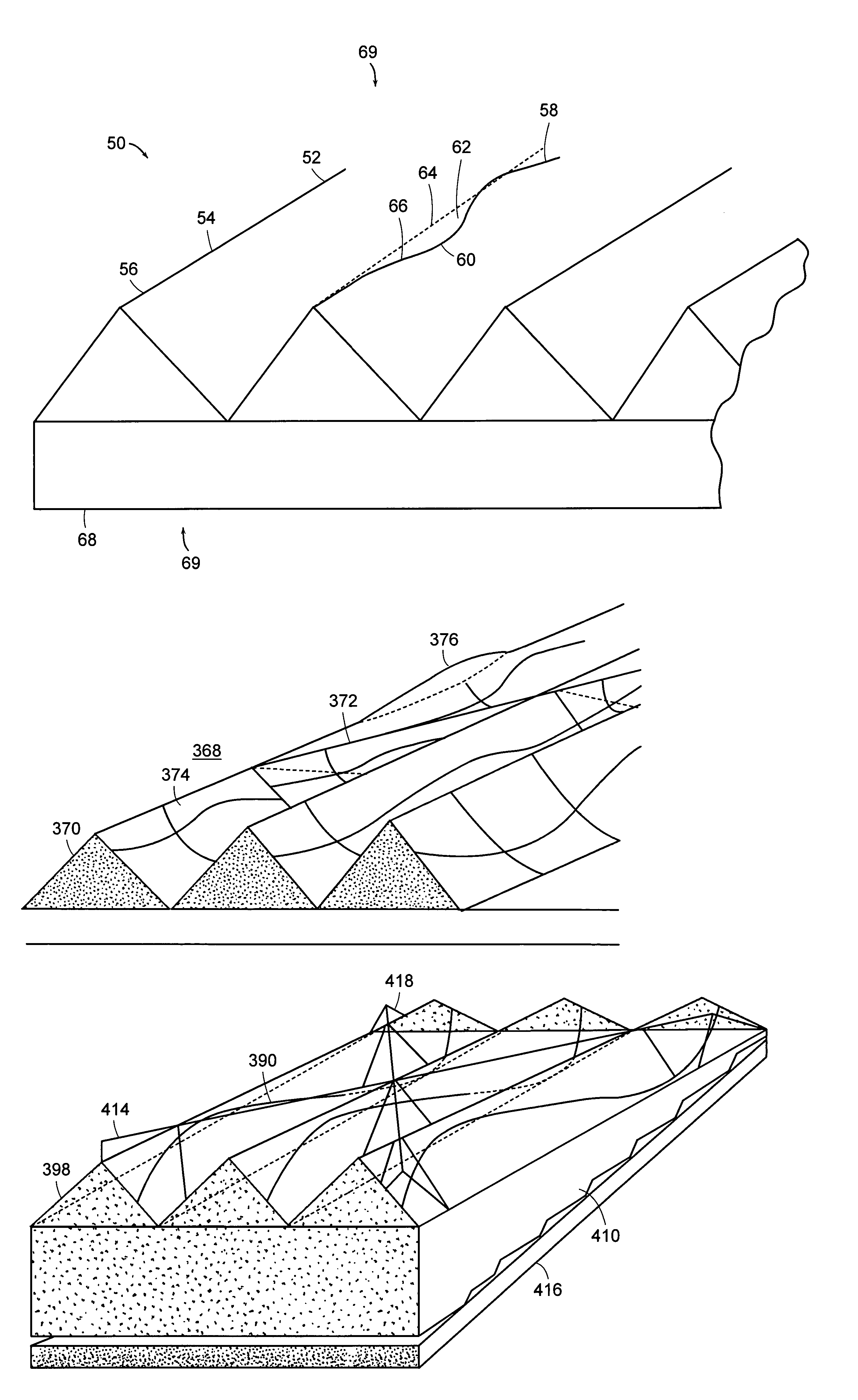
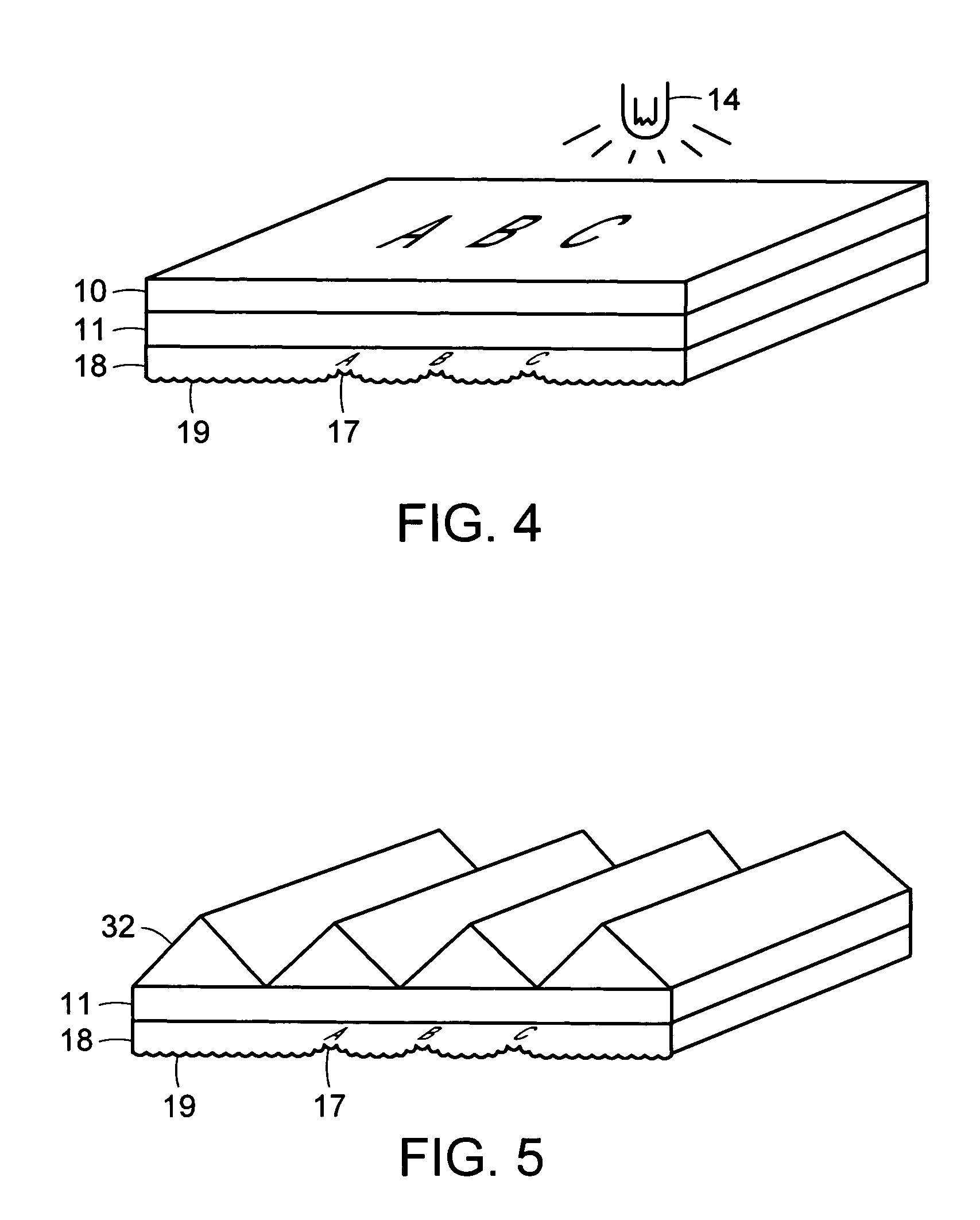
Differentially-cured materials and process for forming same
A light-redirecting optical structure includes a first side and a second side, the first side including plurality of linear prisms having a visibly random shaped surface on the prisms and a plurality of cross-cut prisms on first side which are oriented at an angle such that it is greater than zero degrees but less than 180 degrees. A backlight wedge includes a stepped structure on a bottom side that decreases in size traversing the wedge away from a light source which is positioned at an end and having a visibly random shaped surface on said wedge.
Owner:ORAFOL AMERICAS
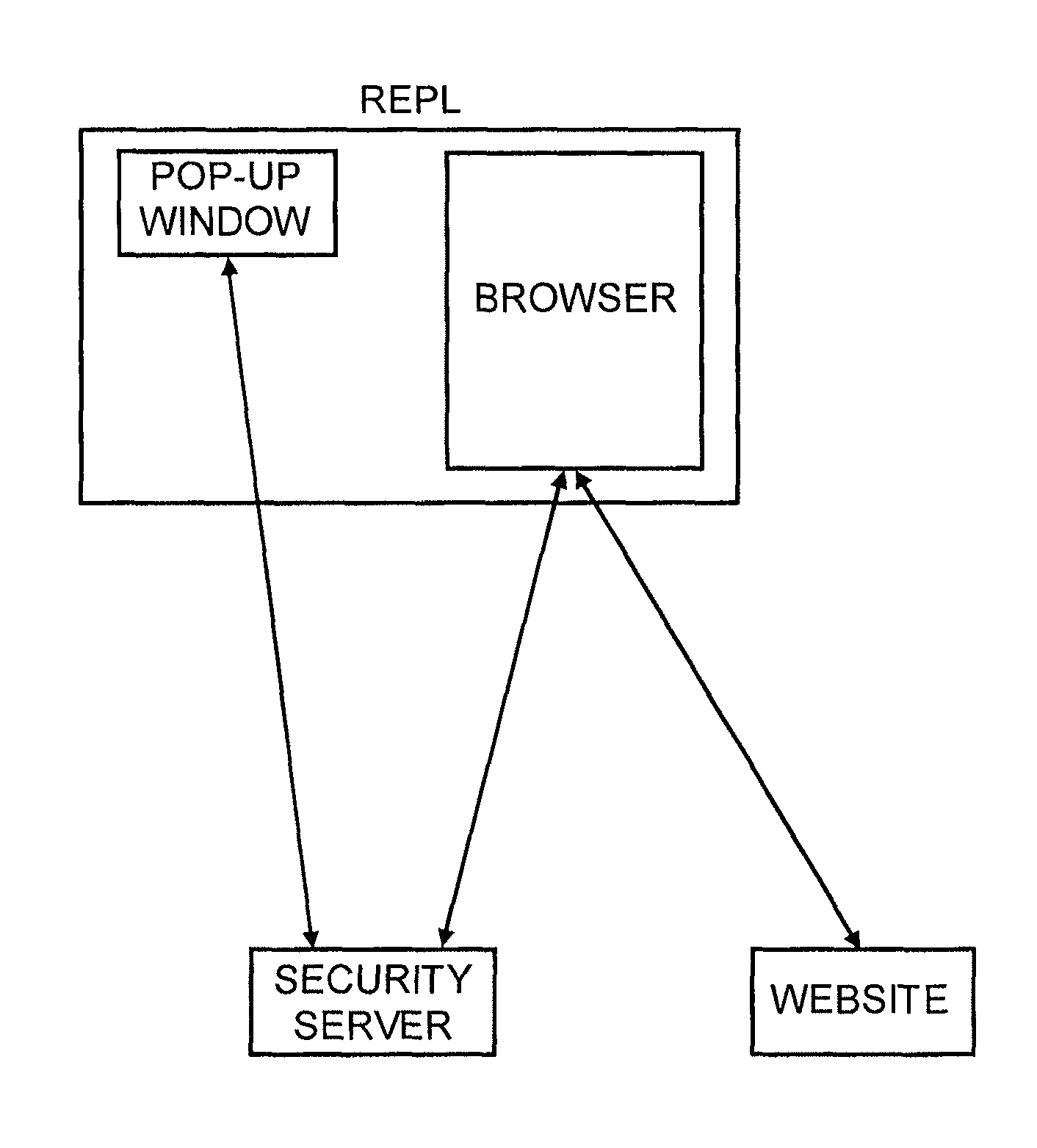
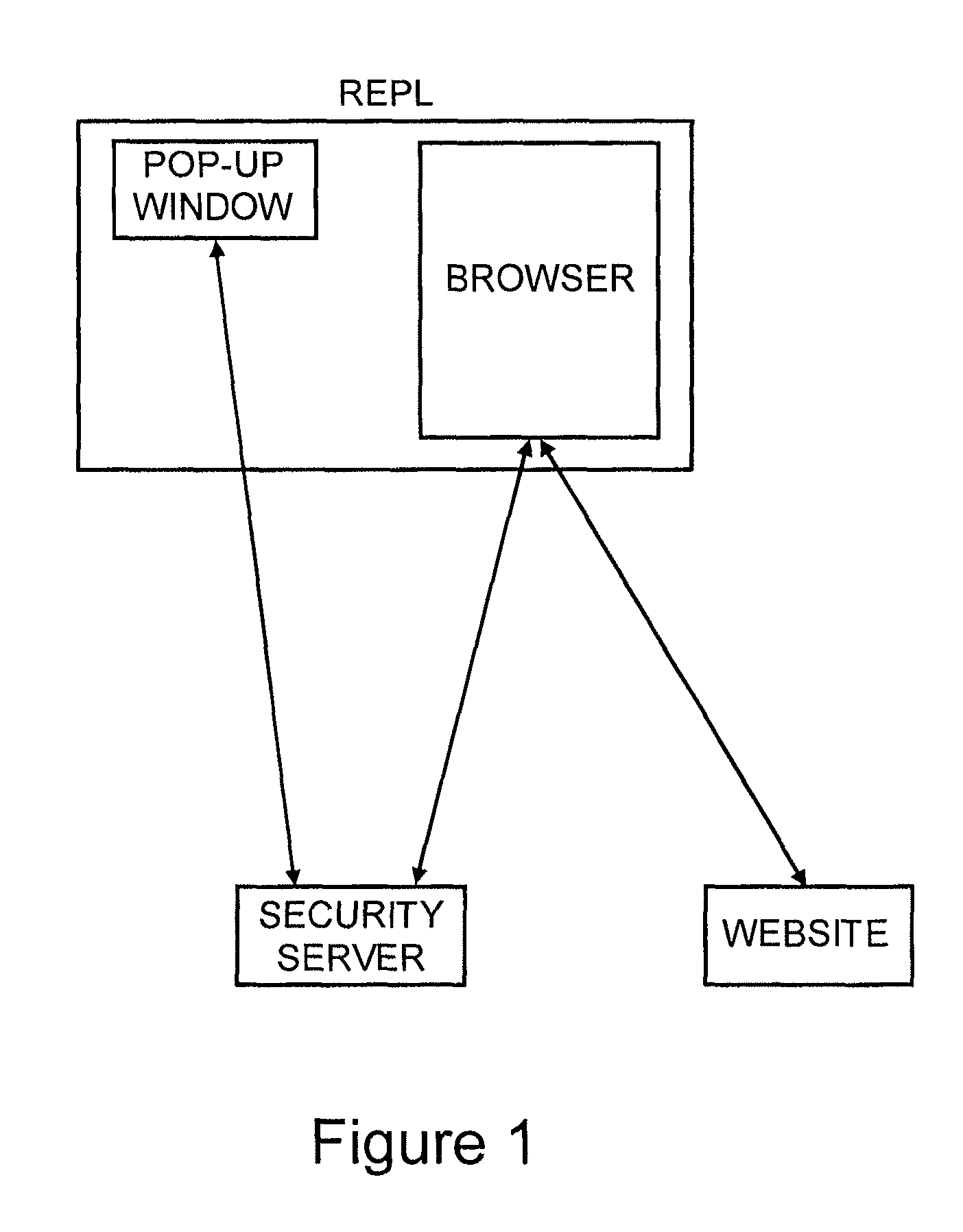
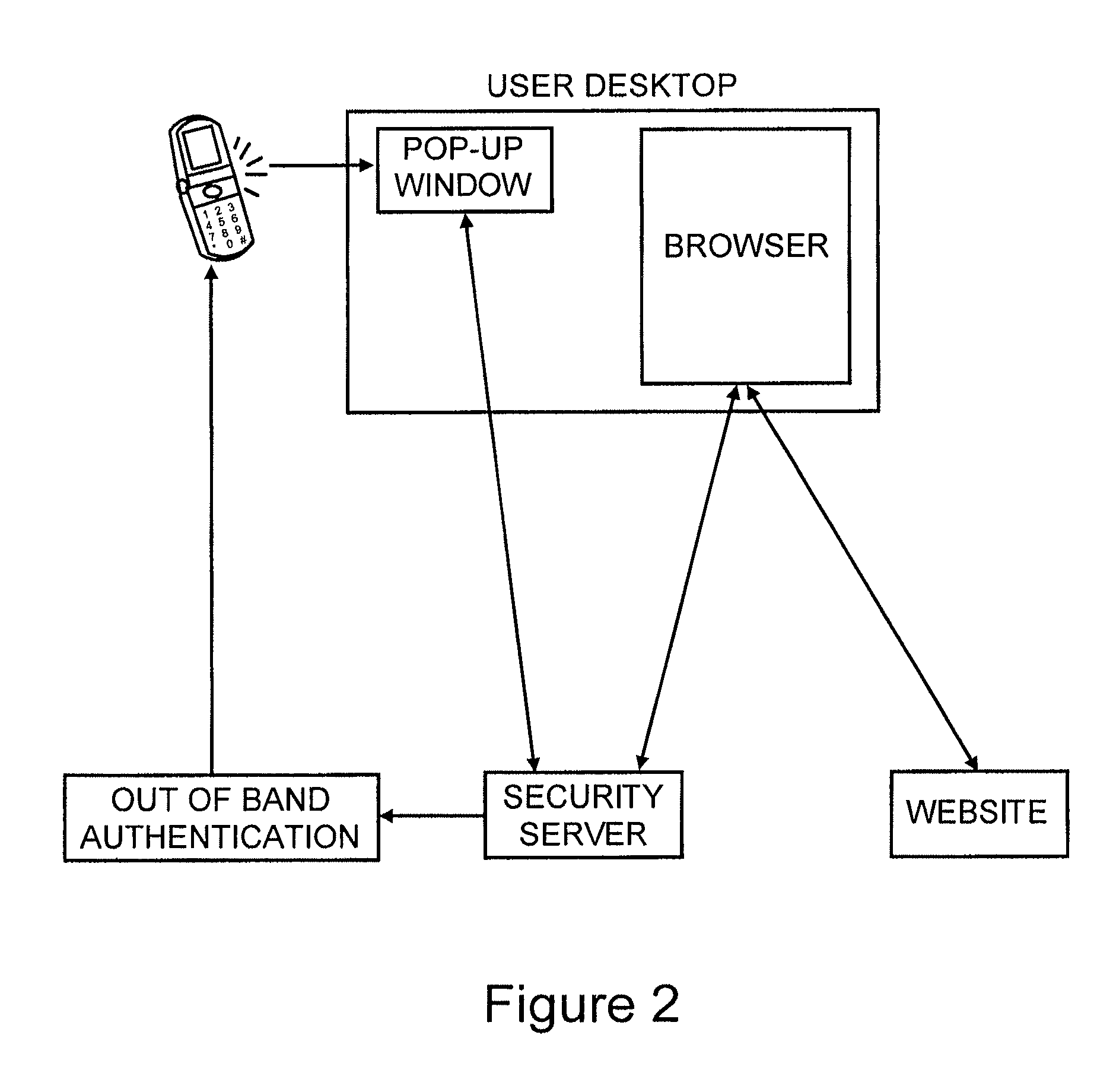
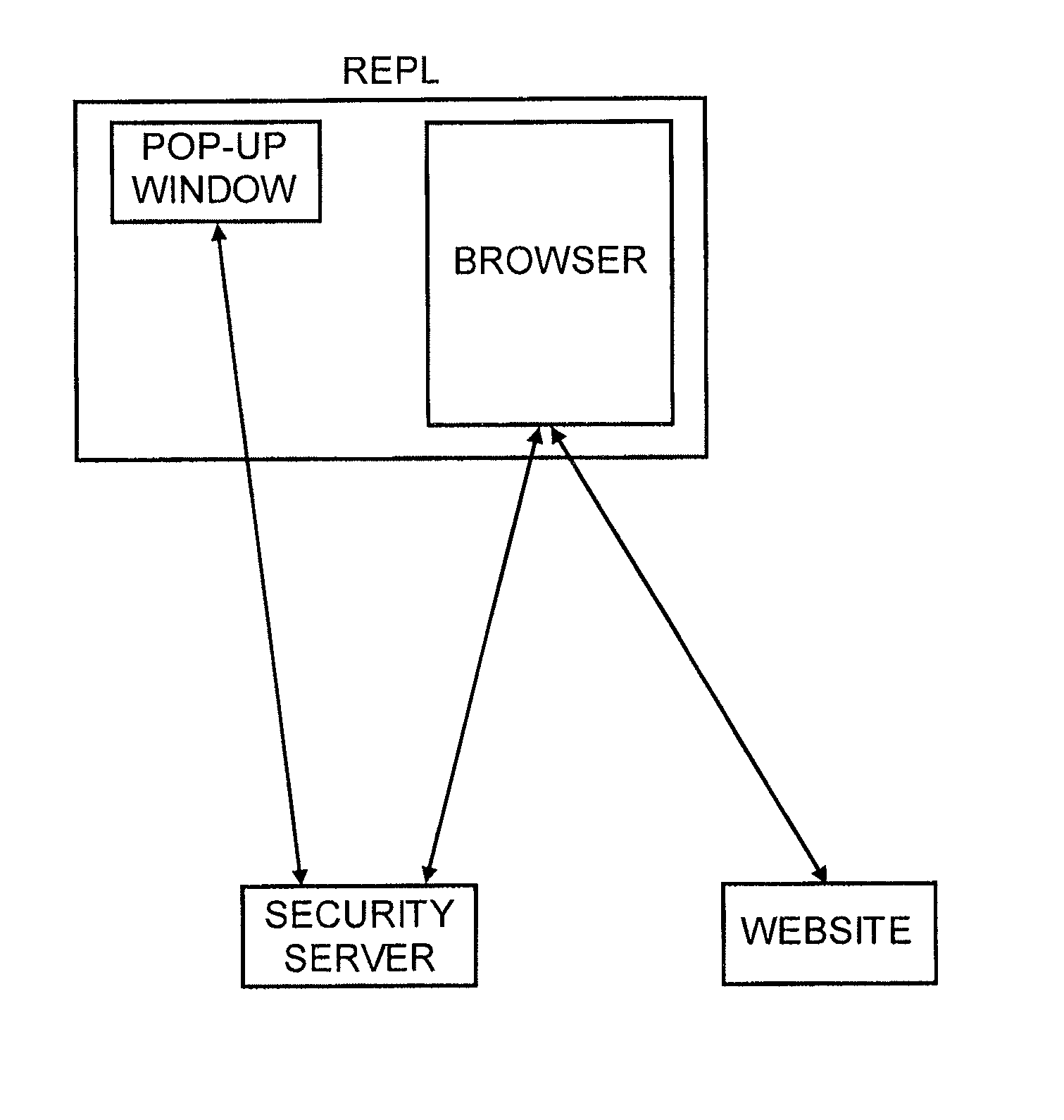
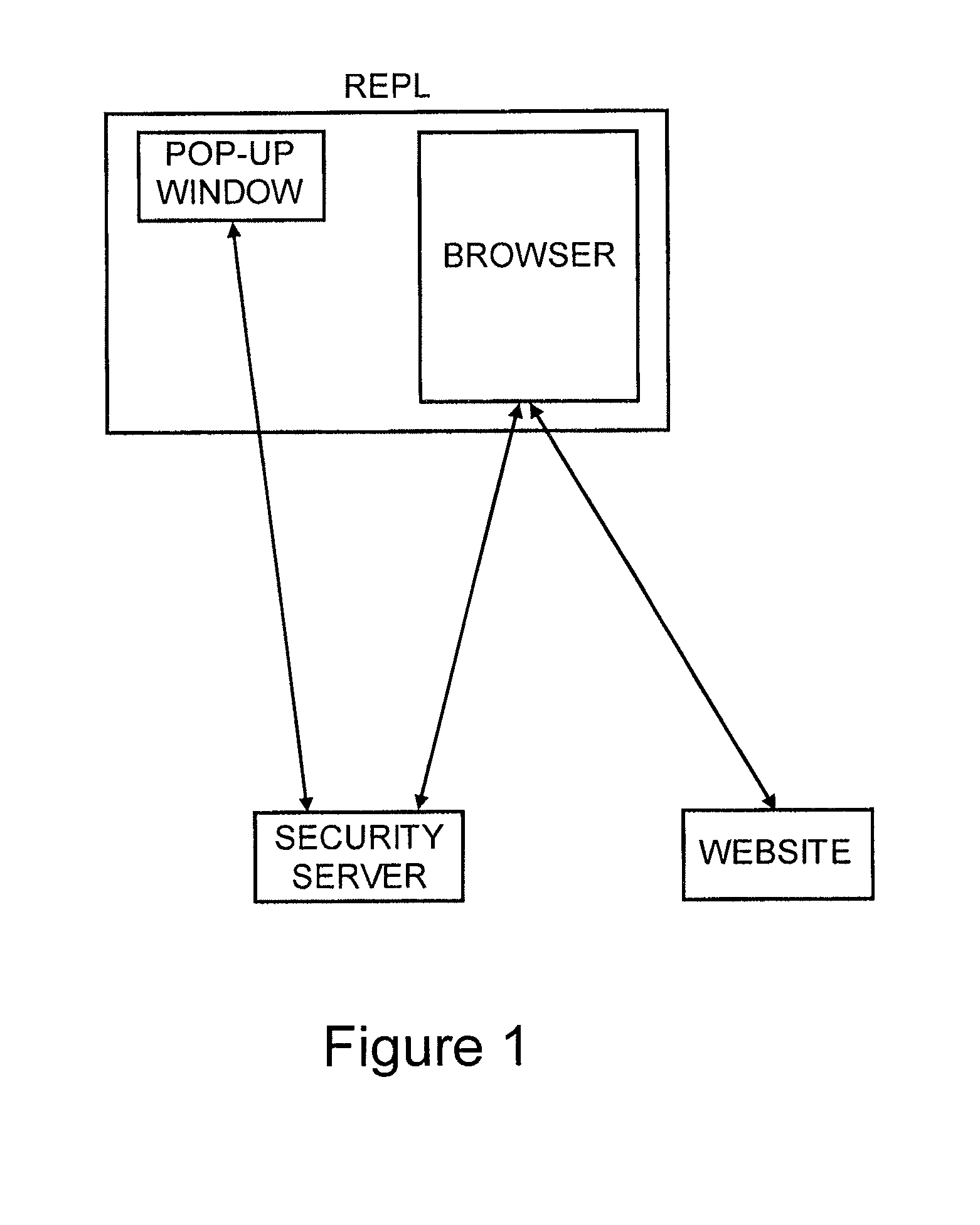
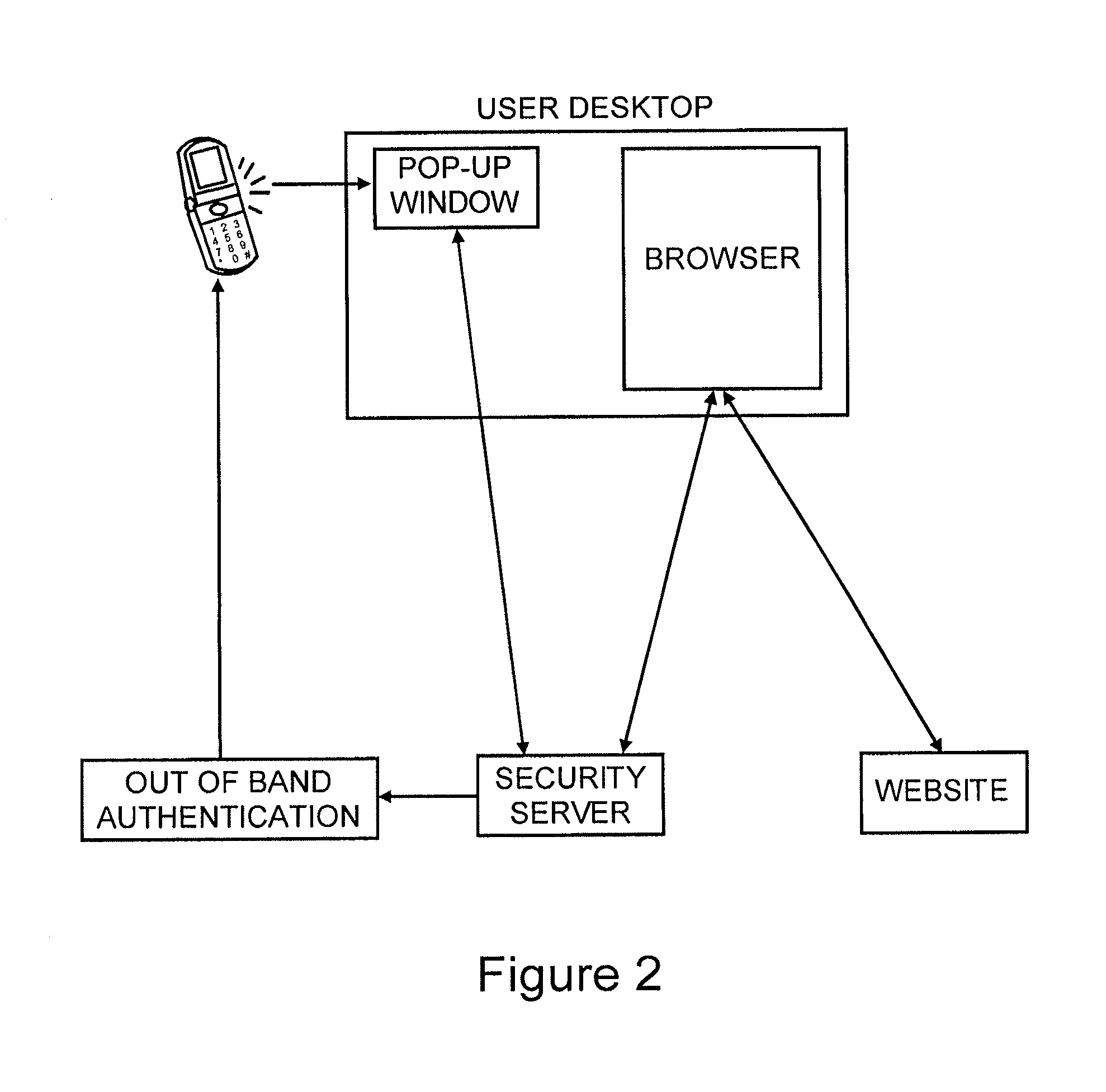
Method for secure user and site authentication
ActiveUS8549601B2Not easily defeatedImprove securityDigital data processing detailsMultiple digital computer combinationsUser authenticationOne-time password
User authentication is achieved by creating a window on the user's PC that is in communication with a security server, where this communication channel is separate from the communication channel between the user's browser and whichever web site they are at. A legitimate web site embeds code in the web page which communicates to the security server from the user's desktop. The security server signals both the web page on the user's browser and the window to which it has a separate channel. If user authentication is requested by the web site, the security server computes a one time password based on a secret which it shares with the web site, but not with the user, and which is not associated with any particular user, and the web site can re-compute the one time password to authenticate the user.
Owner:PAYFONE
Differentially-cured materials and process for forming same
A light-redirecting optical structure includes a first side and a second side, the first side including plurality of linear prisms having a visibly random shaped surface on the prisms and a plurality of cross-cut prisms on first side which are oriented at an angle such that it is greater than zero degrees but less than 180 degrees.A backlight wedge includes a stepped structure on a bottom side that decreases in size traversing the wedge away from a light source which is positioned at an end and having a visibly random shaped surface on said wedge.
Owner:ORAFOL AMERICAS
Security label laminate and method of labeling
ActiveUS8360323B2Reduce the amount requiredMaximize detectabilityStampsRecord carriers used with machinesAdhesiveLength wave
Owner:AUTHENTIX INC
Method for identifying persons and system for carrying out said method
ActiveUS7583822B2Easy accessDifficult to forgeProgramme controlElectric signal transmission systemsPattern recognitionSkin crease
The present invention provides a process and system for identifying a person. According to the inventive method, and with the aid of the system, a sensor is used to capture biometric characteristics of a person to be identified. Identification data is extracted and the identification data of the person to be identified is compared to reference data in a database. In a preferred embodiment, an image is taken of creases in the skin of the person to be identified, reference crease data having been taken beforehand and stored in a database, and a first recognition is effected by means of the skin crease image in a filtering stage. After this first recognition, the reference data of the database may be filtered using other biometric characteristics, with continuing recognition using these other characteristics.
Owner:IDEMIA IDENTITY & SECURITY FRANCE
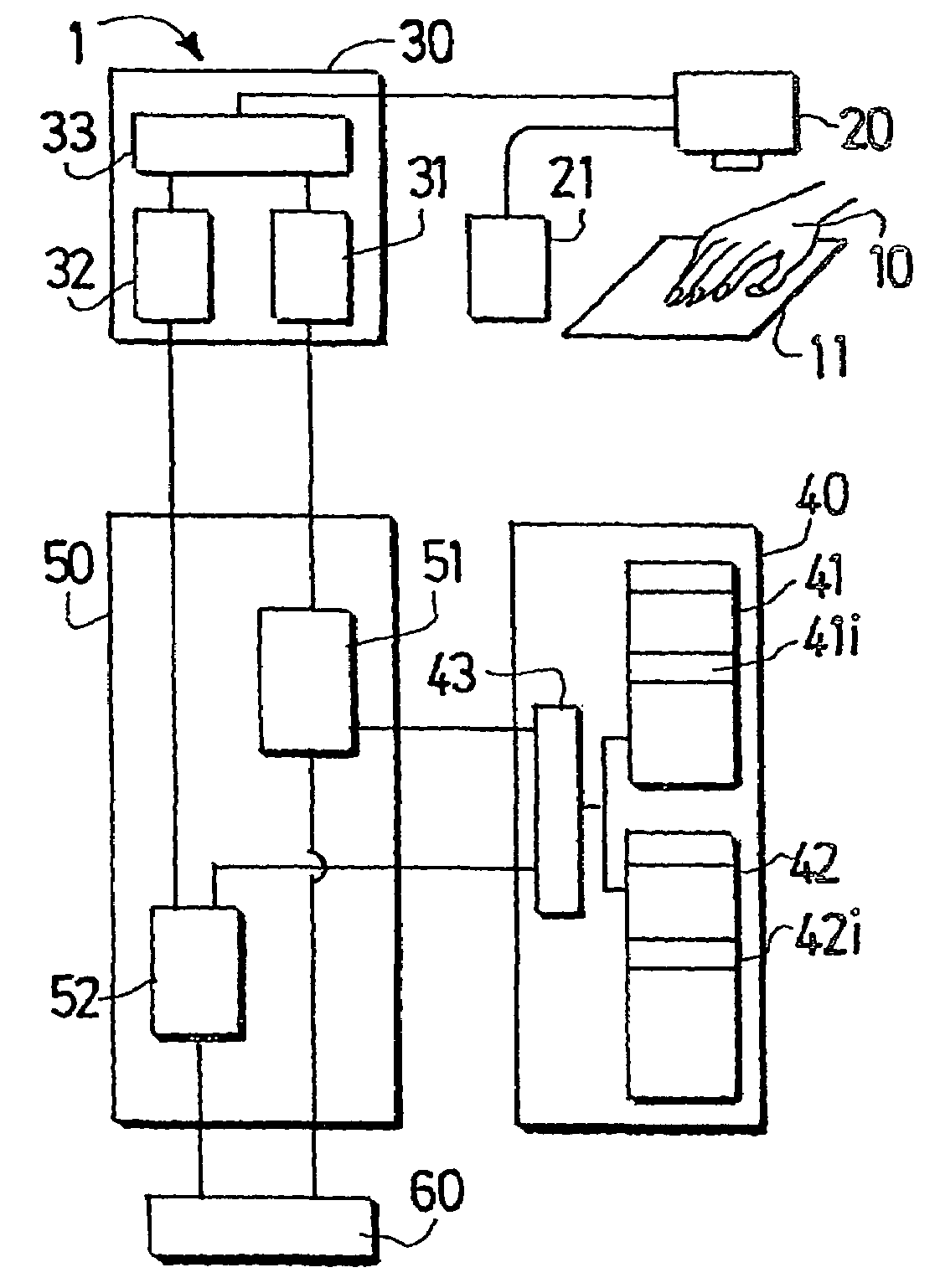
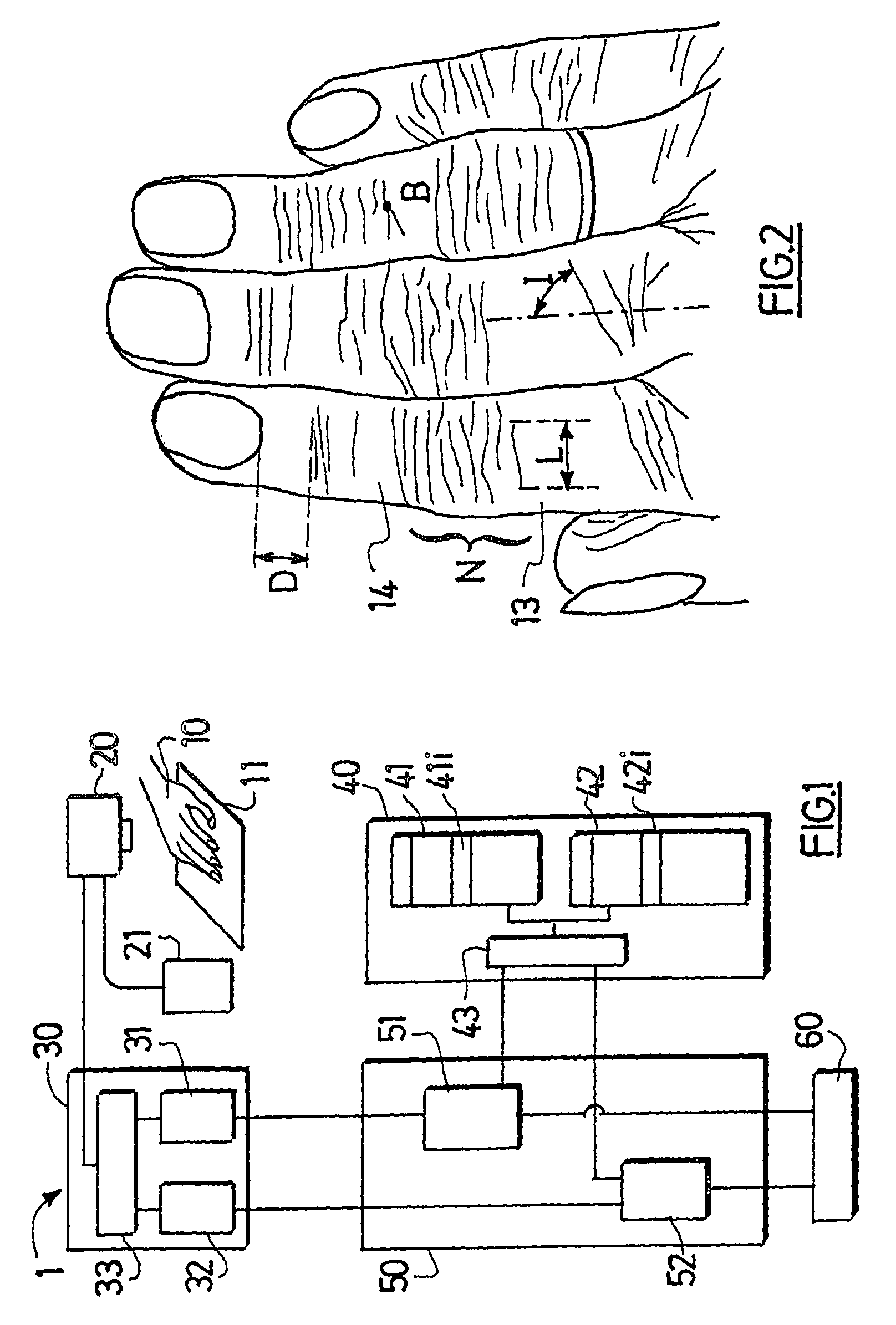
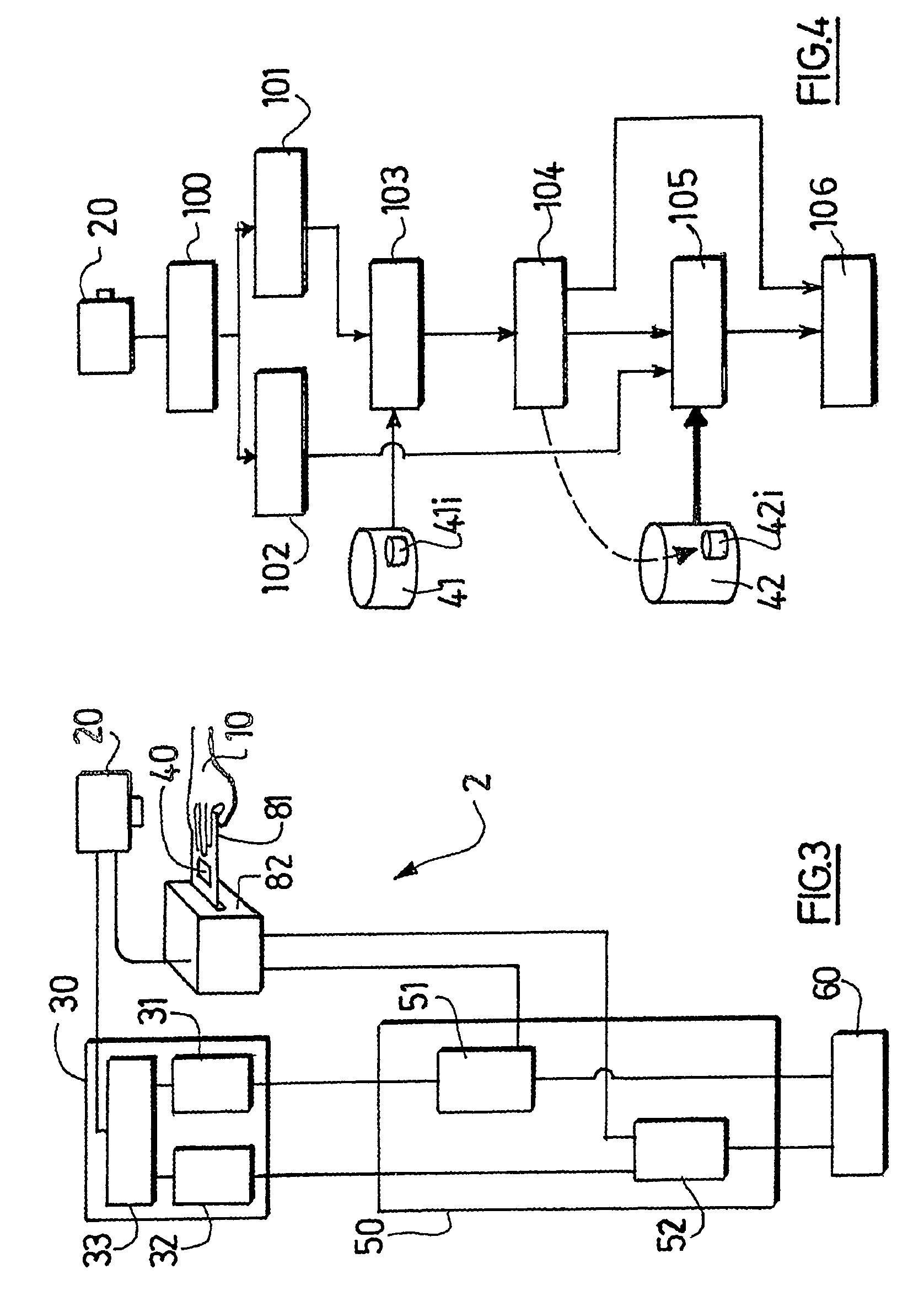
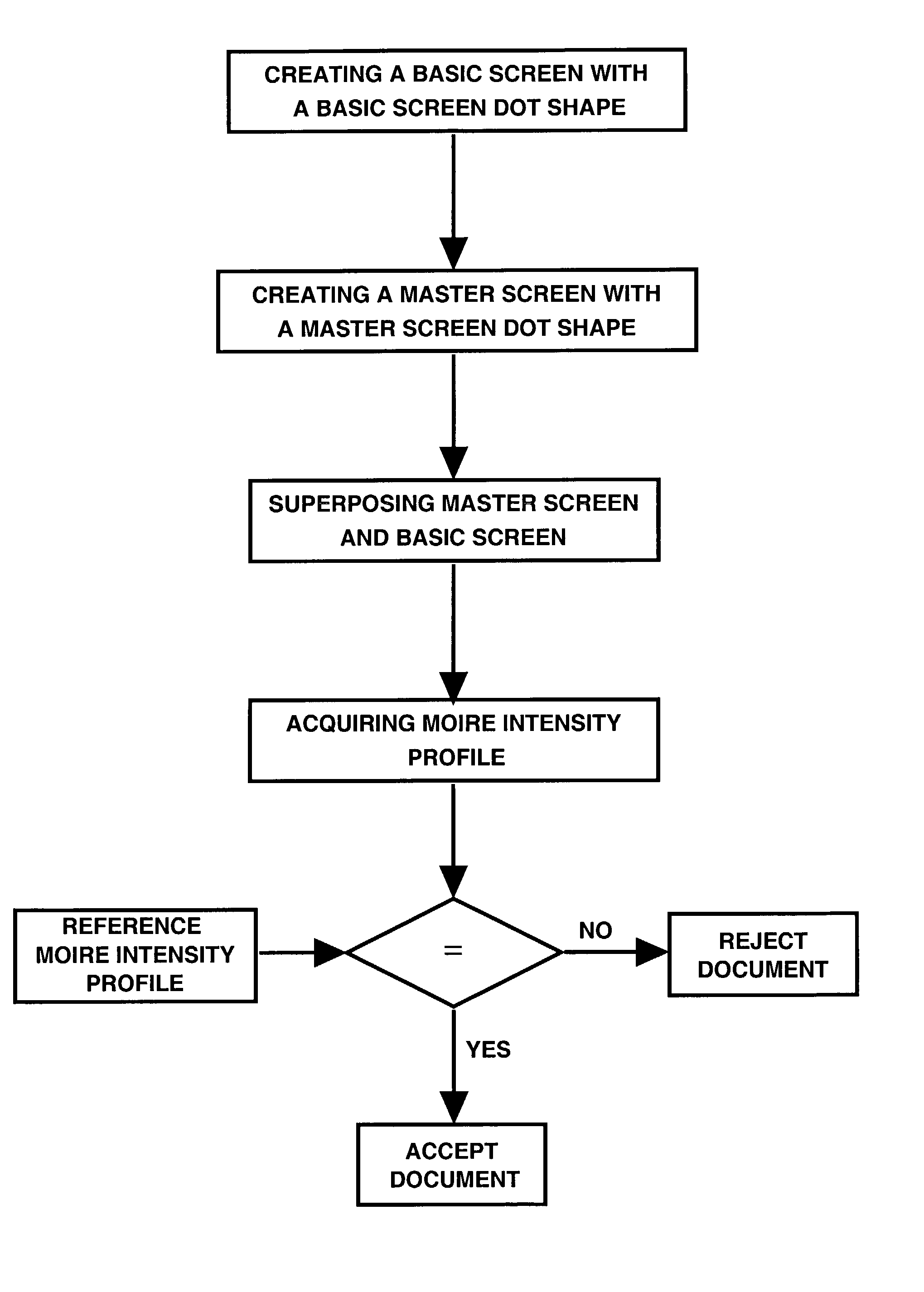
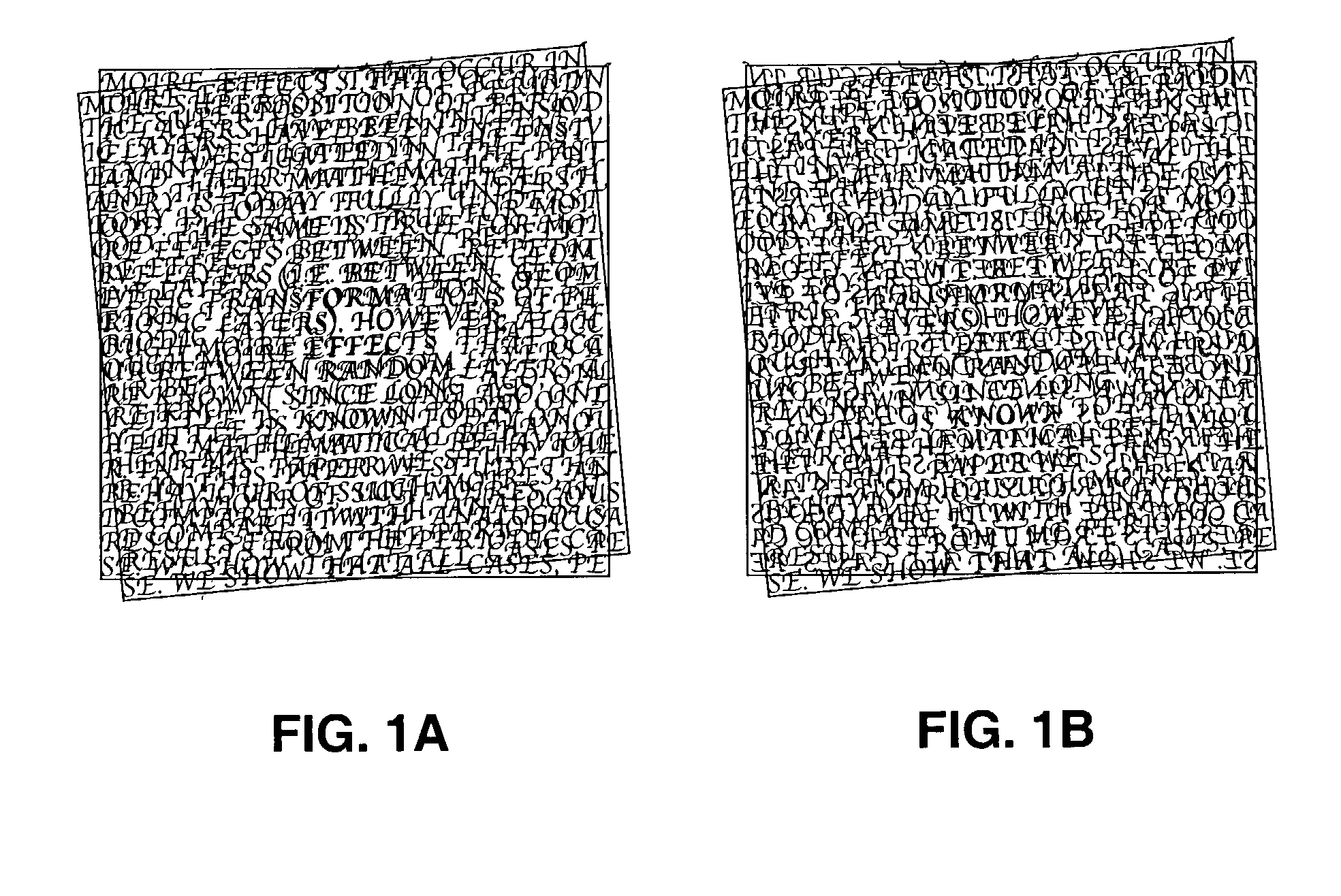
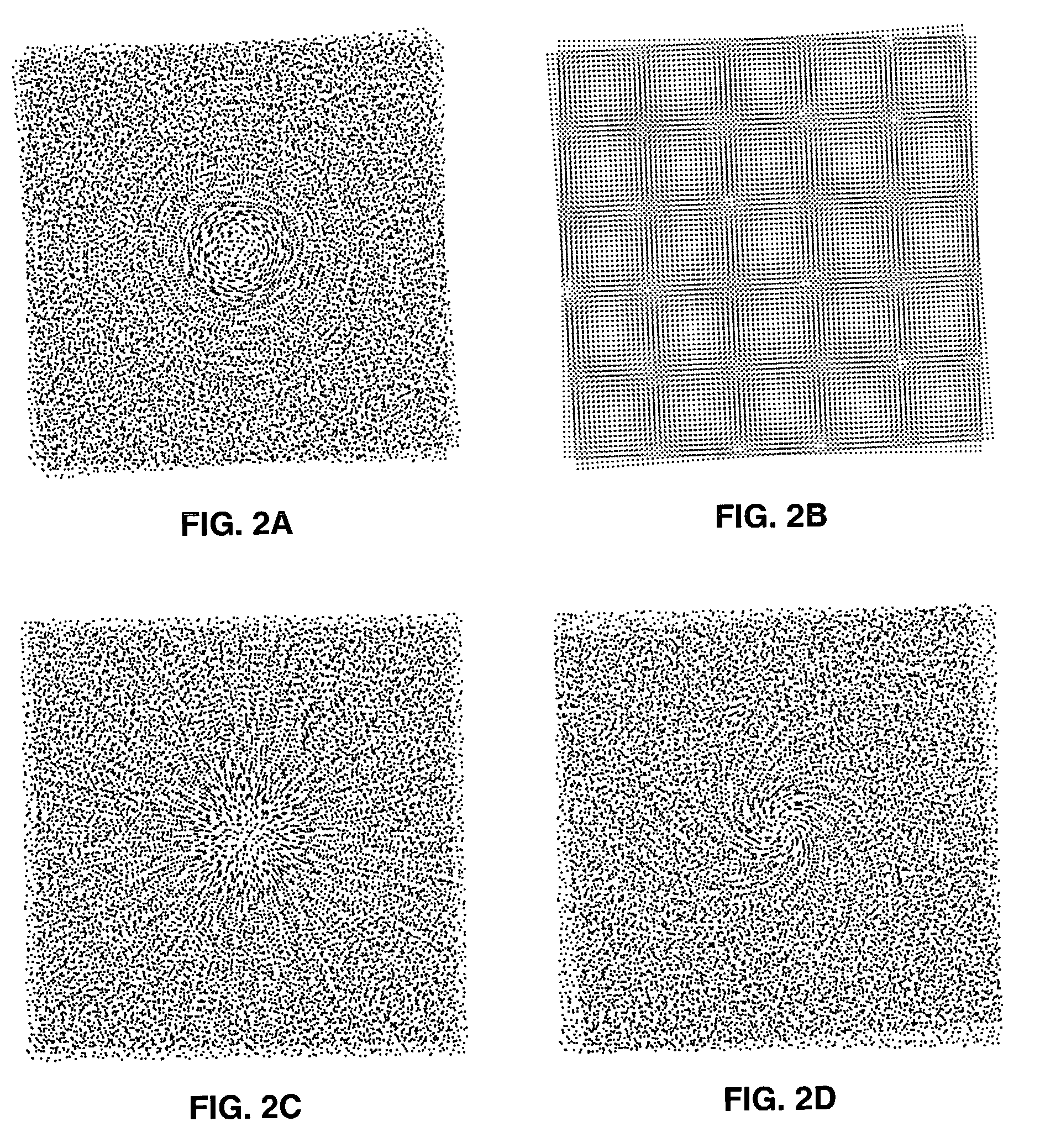
Authentication with built-in encryption by using moire intensity profiles between random layers
ActiveUS7058202B2Difficult to forgeOther printing matterPaper-money testing devicesStandard stateSynthetic materials
This invention discloses new methods, security devices and apparatuses for authenticating documents and valuable articles which may be applied to any support, including transparent synthetic materials and traditional opaque materials such as paper. The invention relates to moire intensity profiles which occur in the superposition of specially designed random structures. By using specially designed random basic screen and random master screen, where at least the basic screen is comprised in the document, a moire intensity profile of a chosen shape becomes visible in their superposition, thereby allowing the authentication of the document. An important advantage of the present invention is that it can be incorporated into the standard document printing process, so that it offers high security at the same cost as standard state of the art document production. Another major advantage of the present invention is in its intrinsically incorporated encryption system due to the arbitrary choice of the random number sequences for the generation of the specially designed random dot screens that are used in this invention.
Owner:ECOLE POLYTECHNIQUE FEDERALE DE LAUSANNE (EPFL)
Security label laminate and method of labeling
ActiveUS20100025476A1Reduce the amount requiredMaximize detectabilityStampsRecord carriers used with machinesAdhesiveWavelength
A labeling method for marking a product with invisible information. The label includes a removable laminate formed from a light transmissive layer, and a light transmissive adhesive that detachably affixes the label to a product. The label includes an invisible marker that contains information, detectable by light of selected wavelength. The amount of marker selected is sufficient to allow information in the marker to be detected only when the laminate is affixed over a surface with a selected optical background. The label laminate is removed from the surface of the product and affixed to a surface having the selected optical background and is exposed to light that renders the information in the marker detectable. The method allows covert information in the label laminate to be reliably detected and read with the use of minimal quantities of marker material.
Owner:AUTHENTIX INC
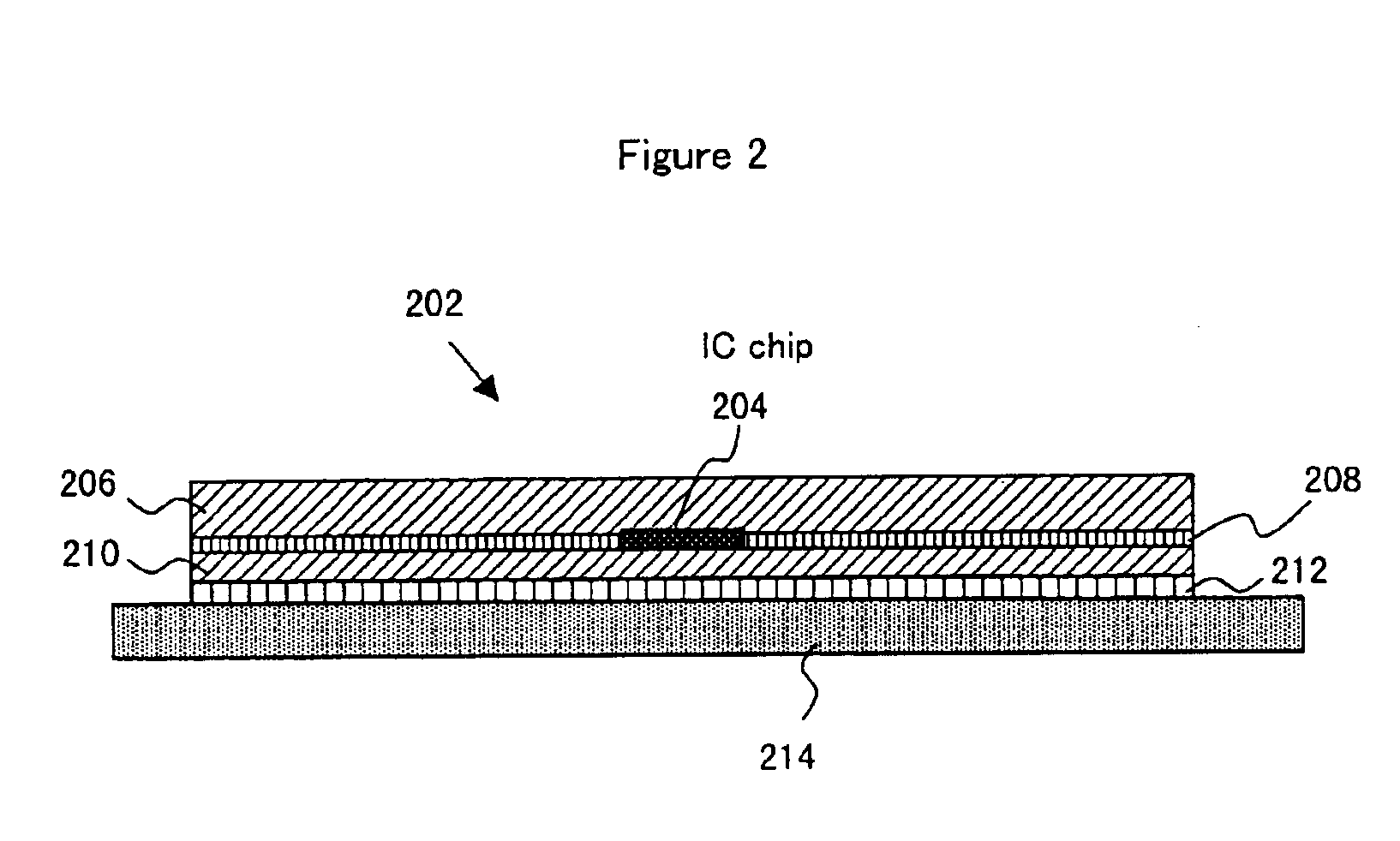
Service system, information processing system and interrogator
InactiveUS7119662B1Difficult to forgeEasy to produceElectric signal transmission systemsDigital data processing detailsInformation processingDigital signature
A contactless IC chip is mounted or adhered on a certificate and used in a service system having an interrogator and a computer system. The interrogator and the computer system are interconnected via a network such as the Internet. The IC chip is used as an electronic tag and the interrogator receives first information by reading information printed on the certificate including a digital signature and by receiving second information from the electronic tag through an antenna of the interrogator. Then, the first information from the certificate and the digital signature are used by the computer to calculate third information that is compared with the second information received from the electronic tag. If the comparison results in a match, then the certificate is deemed authentic.
Owner:HITACHI LTD
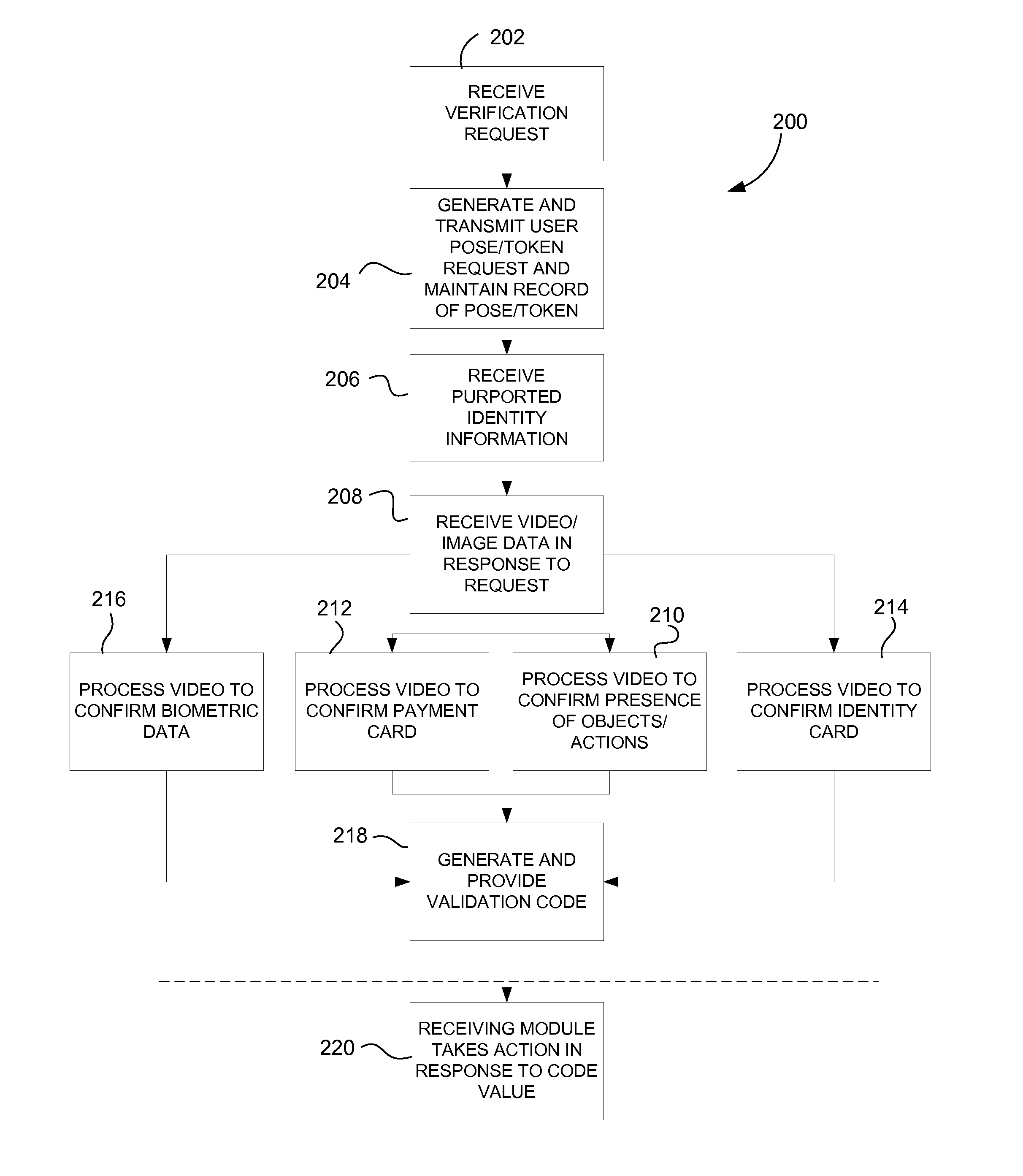
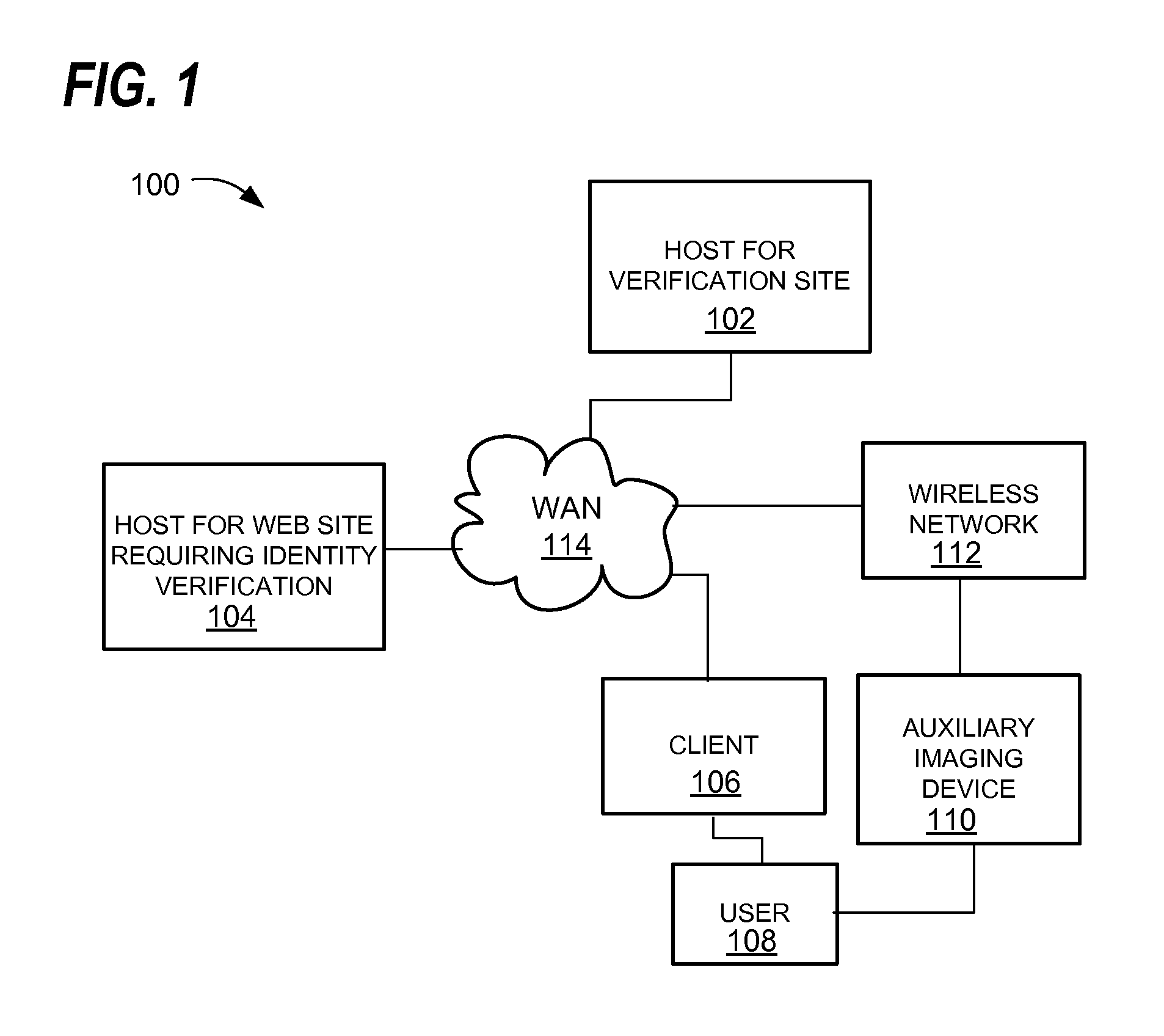
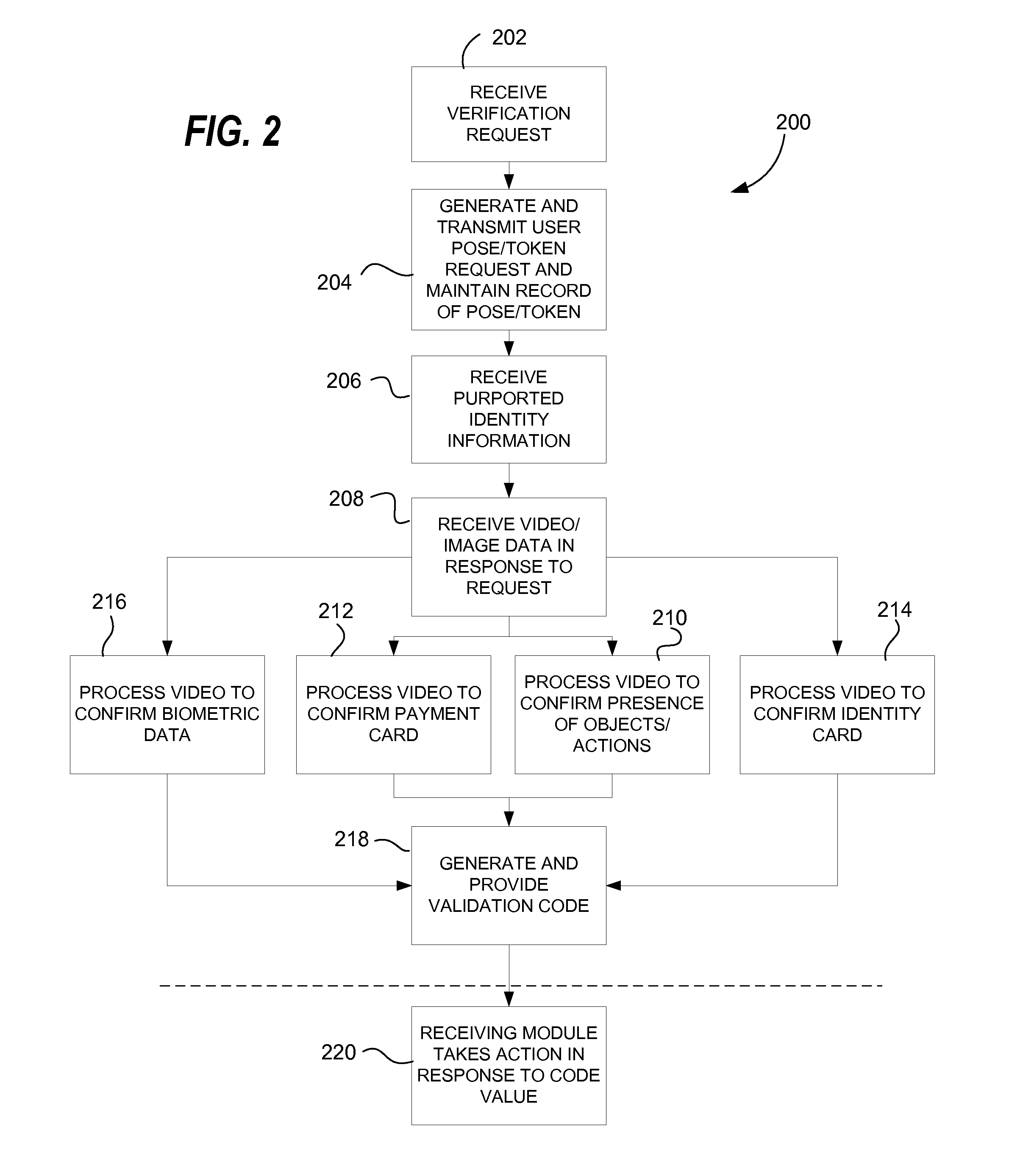
Online identity verification
ActiveUS20120106805A1Increase the number ofDifficult to forgeCharacter and pattern recognitionClient-sideAuthentication protocol
A method for verifying an identity attribute of a remote user includes providing pose instructions to a remote client from a host during an authentication session. The pose instructions may reference a specific physical token associated with the user, for example a government ID card, credit card, household object or printed or displayed image provided from an authentication host. The host receives an image from the client and may analyze the image to determine if the pose instructions were followed and if the physical token appears in the image. Based on this determination, and optionally using other factors, the host verifies an identity attribute of the user.
Owner:SHUSTER GARY S
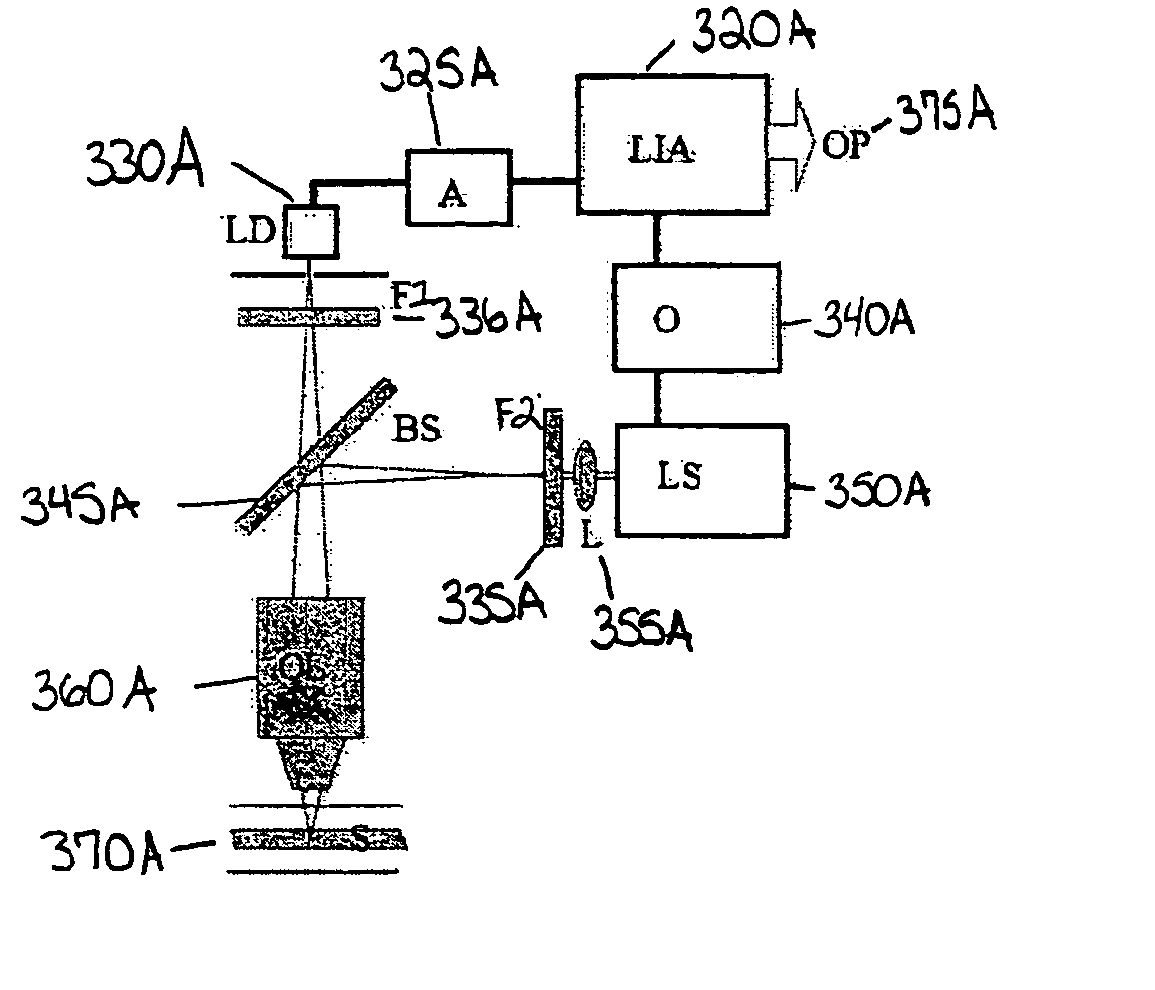
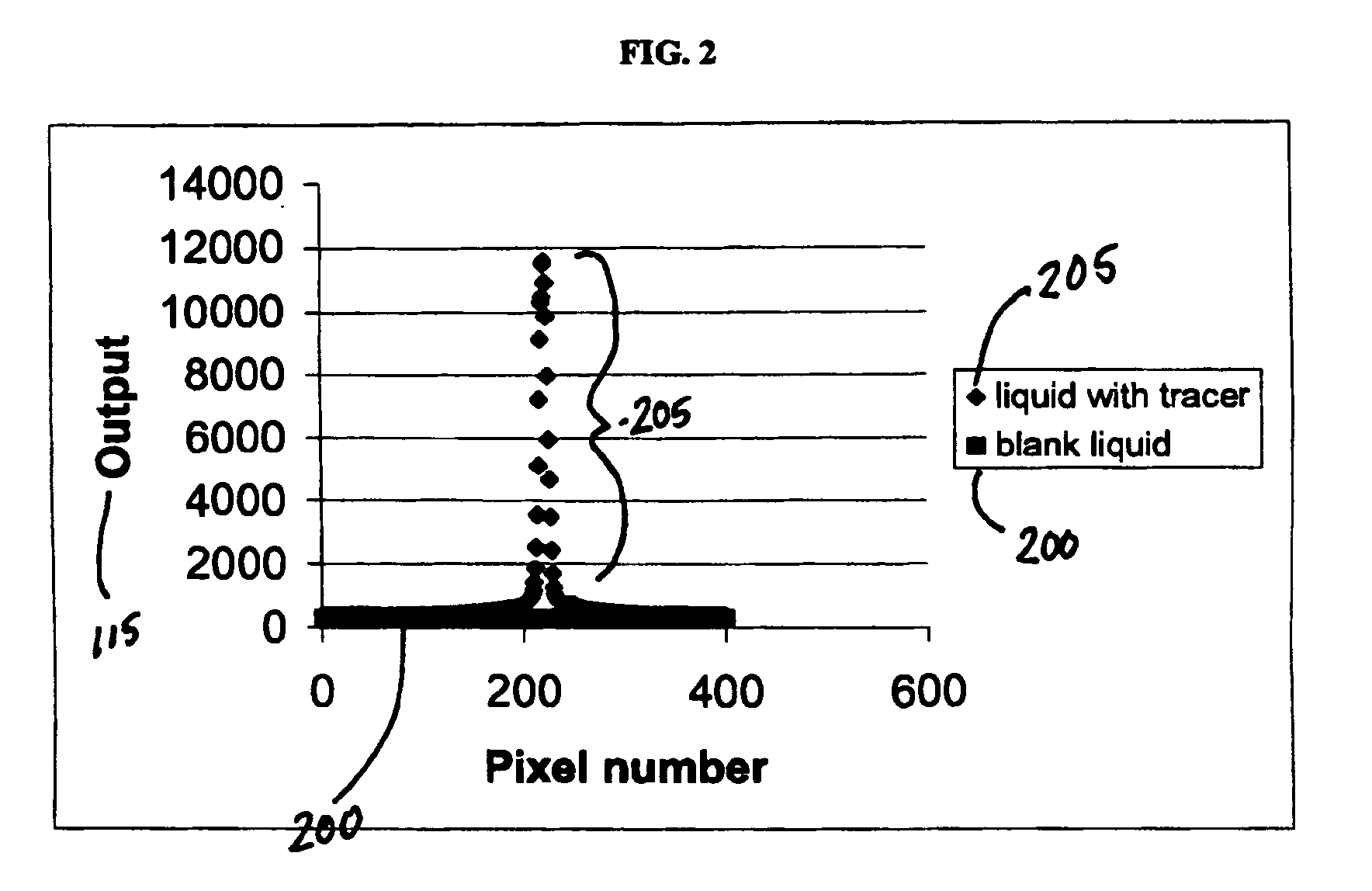
Method and apparatus for monitoring liquid for the presence of an additive
ActiveUS20050260764A1Minimize background signalDifficult to counterfeitChemiluminescene/bioluminescenceAnalysis by electrical excitationPhysicsLight source
The present invention relates to an apparatus and methods for the identification or authentication of liquid products by the addition of an anti-Stokes marker. The invention features an apparatus and method for the identification of a liquid, dynamic or static, that includes adding an anti-Stokes luminescent marker compound to the liquid followed by exposing the compound to a light source of a known wavelength or known wavelengths and then detecting one or more shorter wavelength emissions from the marker, where the identity of the liquid is confirmed by the emission wavelength or wavelengths that are detected and quantified. The irradiating source of light includes, but is not limited to, a laser and other conventional light sources.
Owner:AUTHENTIX INC
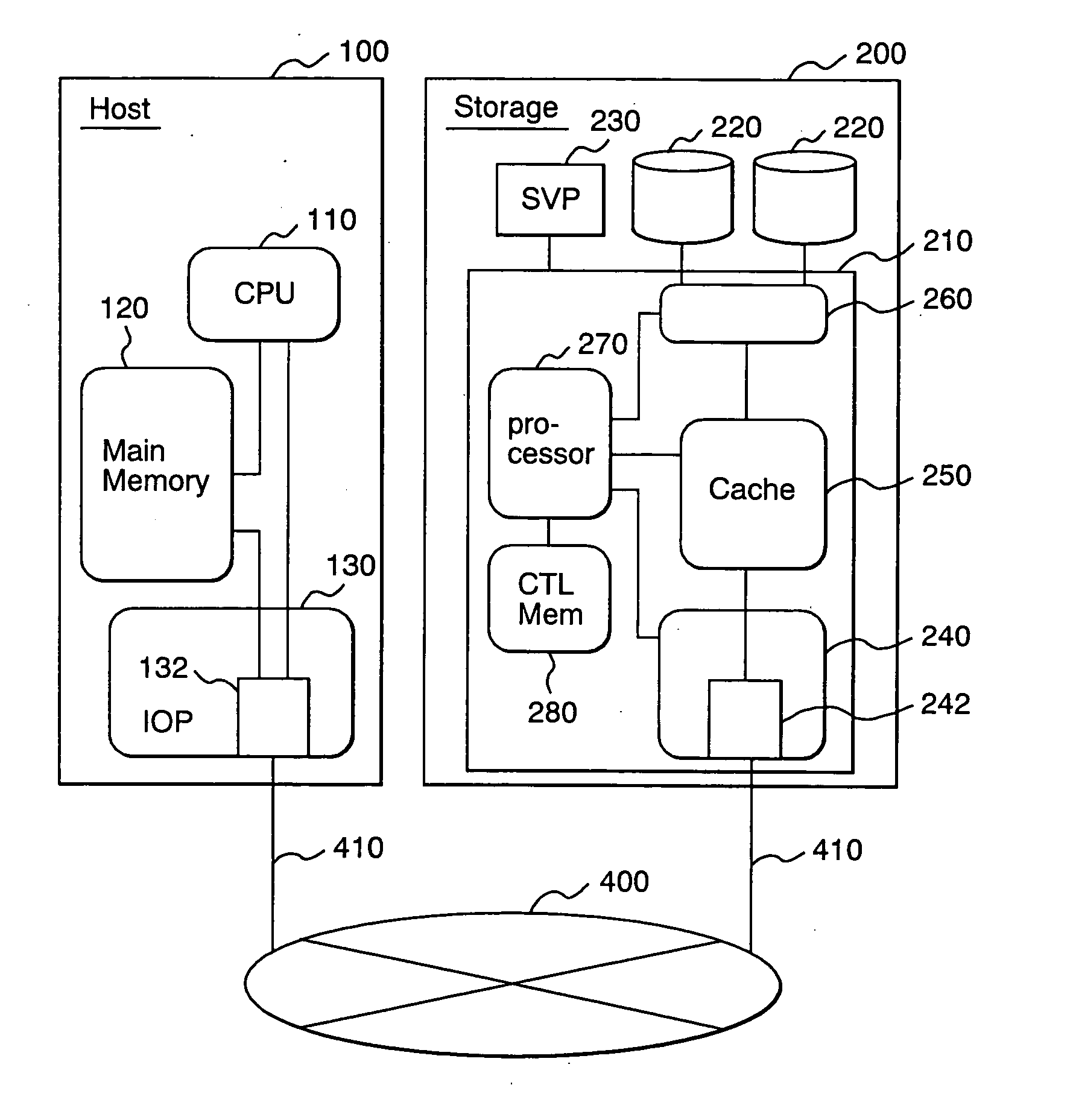
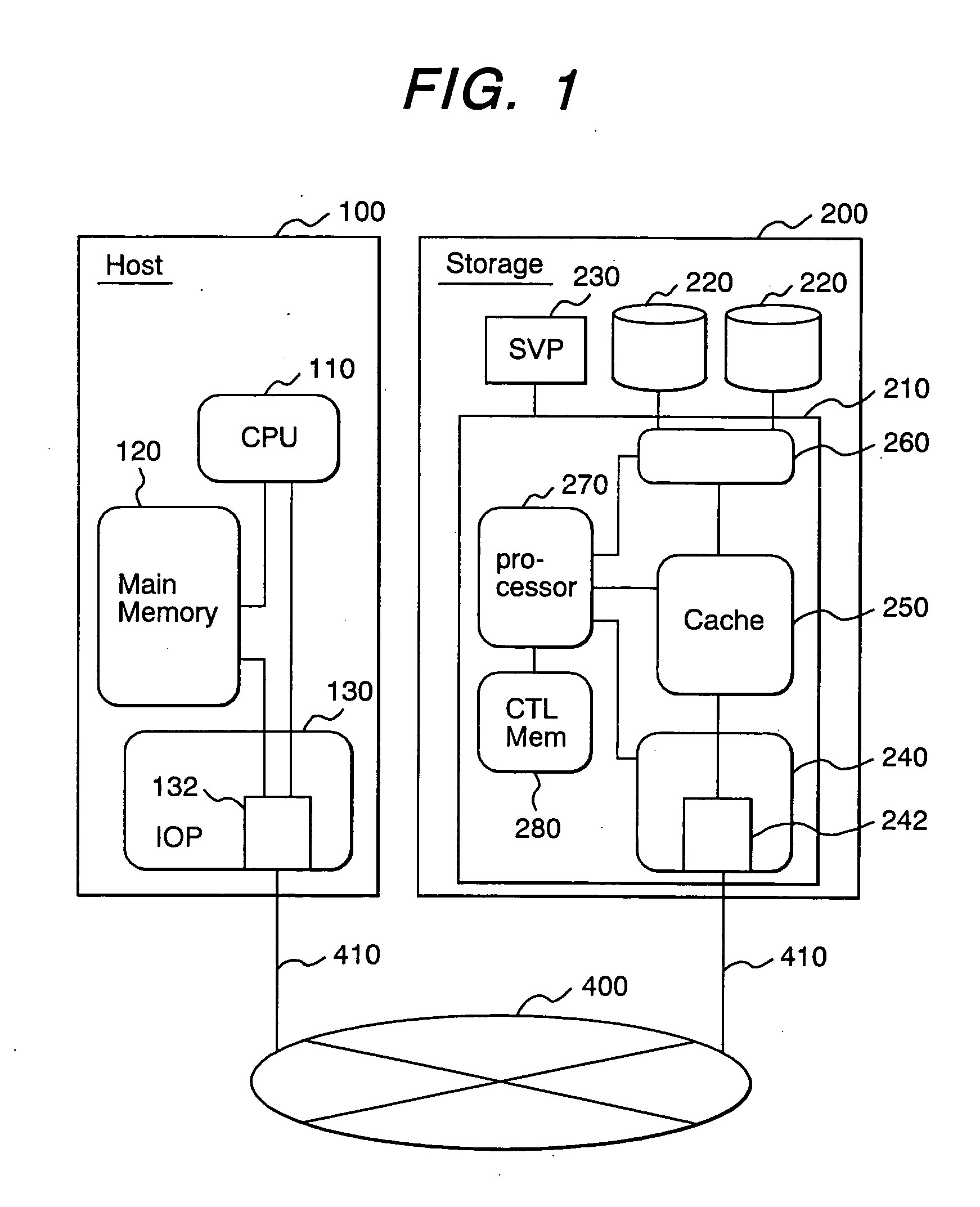
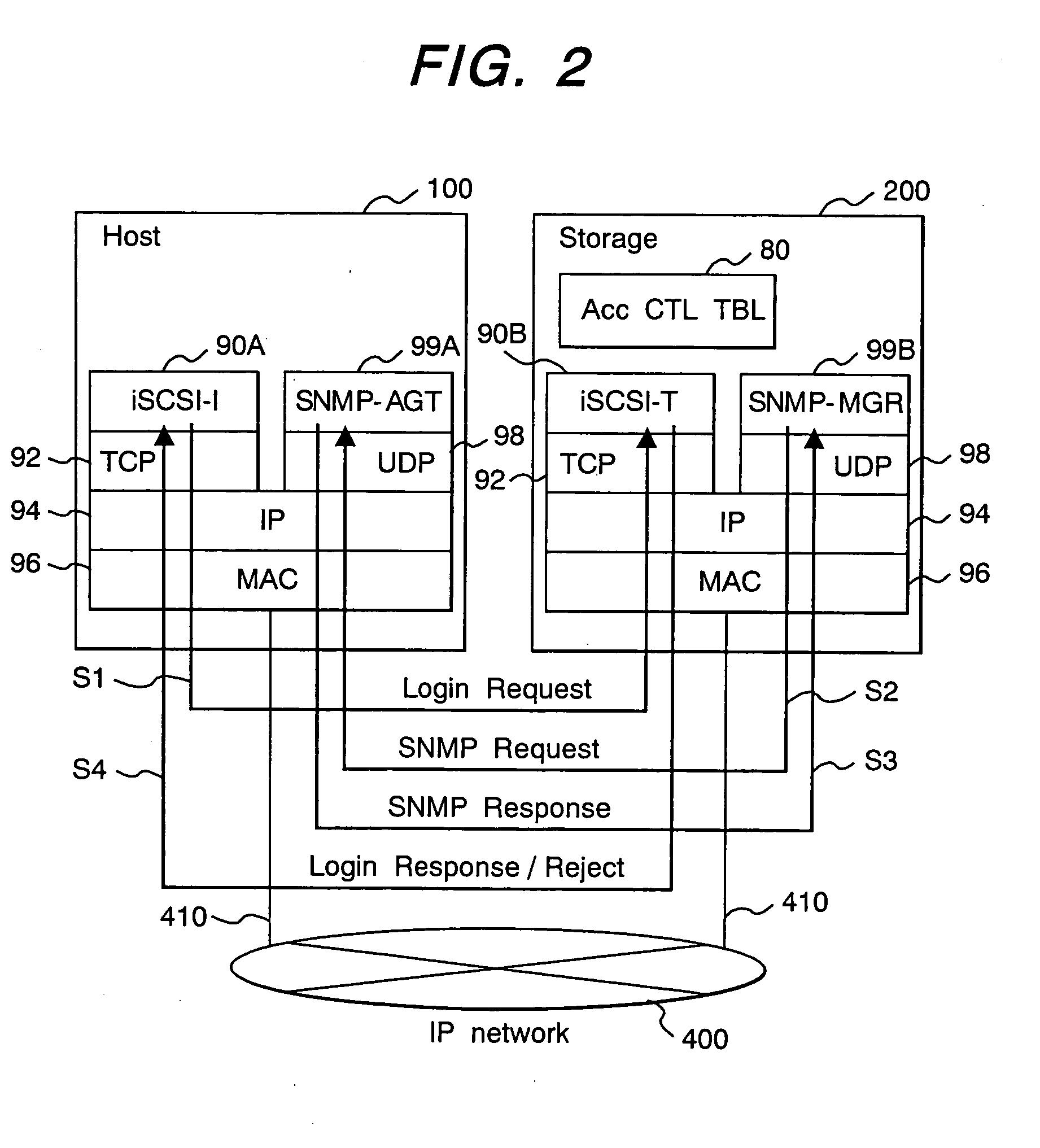
Storage apparatus and access management method therefor
InactiveUS20050091504A1Increase rangeSafety is assuredInput/output to record carriersUnauthorized memory use protectionAccess managementISCSI
An access control management method is provided for managing access permits for access requests transmitted by an external apparatus to a storage apparatus by way of a network. The storage apparatus receives a frame of a login request from the external apparatus and determines whether or not the received frame includes second information for identifying the external apparatus (first determination process). In a case where a result of the first determination process indicates that the frame does not include the second information, acquisition of first information for identifying the external apparatus from the external apparatus is requested and the acquired first information is checked in order to determine whether or not an access permit should be given to the external apparatus (second determination process). In a case where a result of the second determination process indicates that an access permit should be given to the external apparatus, an access request made by the external apparatus as a request for an access to the storage apparatus is approved. As a result, it is possible to improve security of an access request made by the external apparatus serving as a host computer by adoption of an iSCSI protocol as a request for an access to the storage apparatus.
Owner:HITACHI LTD
Method for the determination of soundness of a sheet-shaped medium, and method for the verification of data of a sheet-shaped medium
InactiveUS7159241B1Difficult to forgeEasy to carryDigital data processing detailsAnalogue secracy/subscription systemsOperating systemService system
The present invention provides a service system using a certificate which is easily portable and difficult to counterfeit. The feature of the invention is to use a contactless IC chip as a portable certificate. An IC chip-attached seal is thin and small, and therefore is easily portable and distributable to a user. By integrating or attaching (or sticking) the IC chip into or on a certificate 3910, the counterfeiting of the certificate 3910 becomes difficult.
Owner:HITACHI LTD
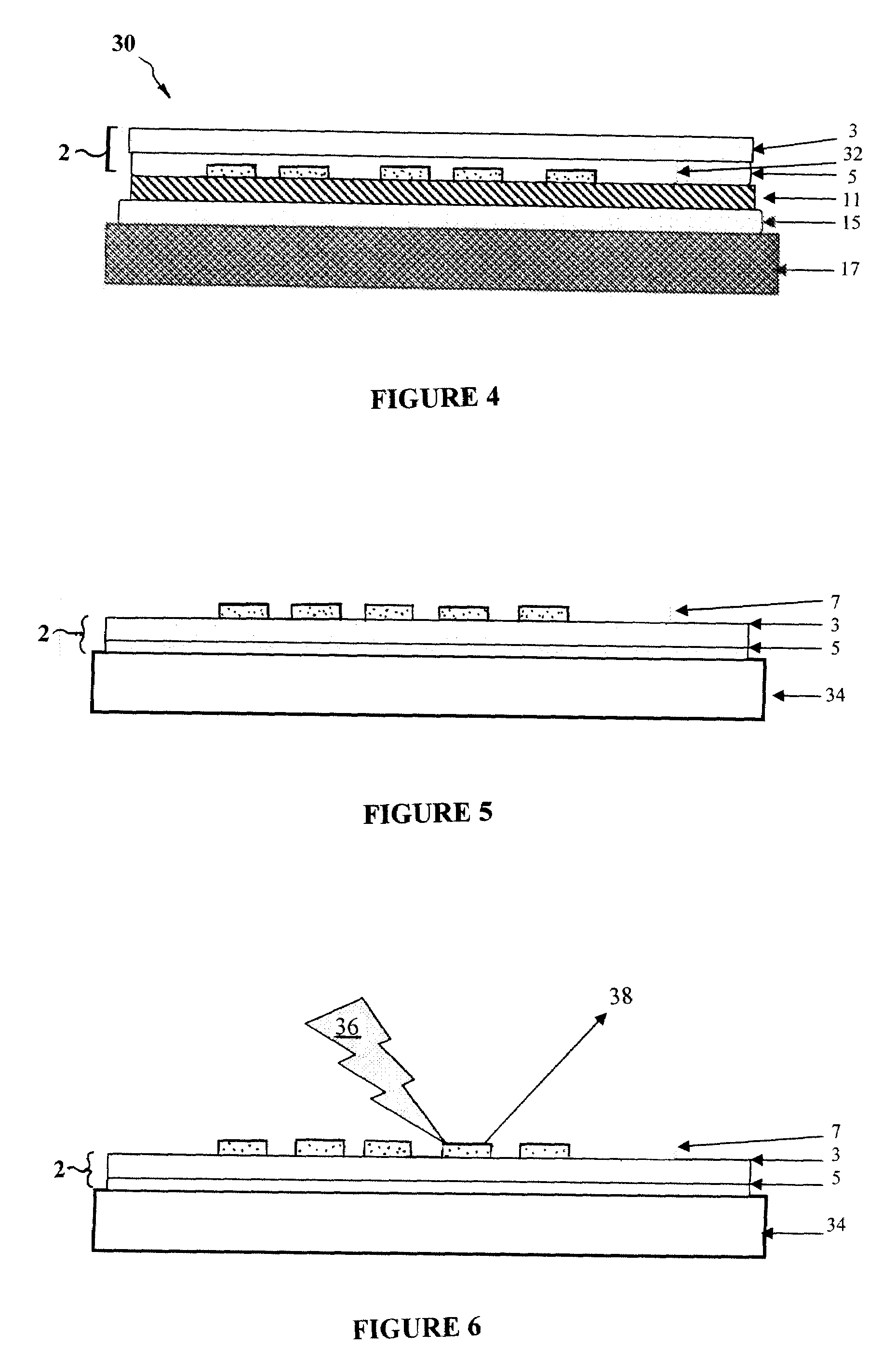
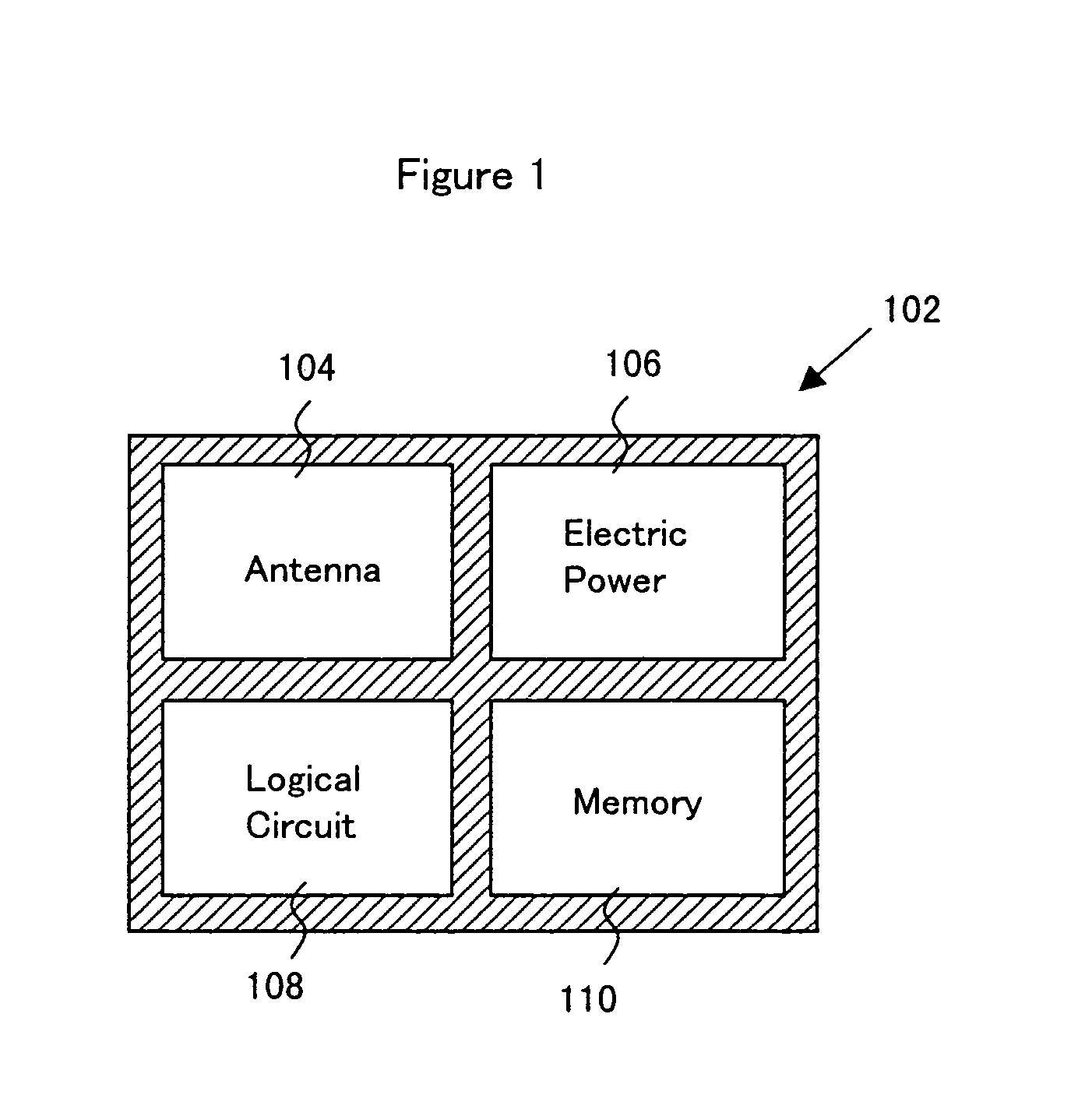
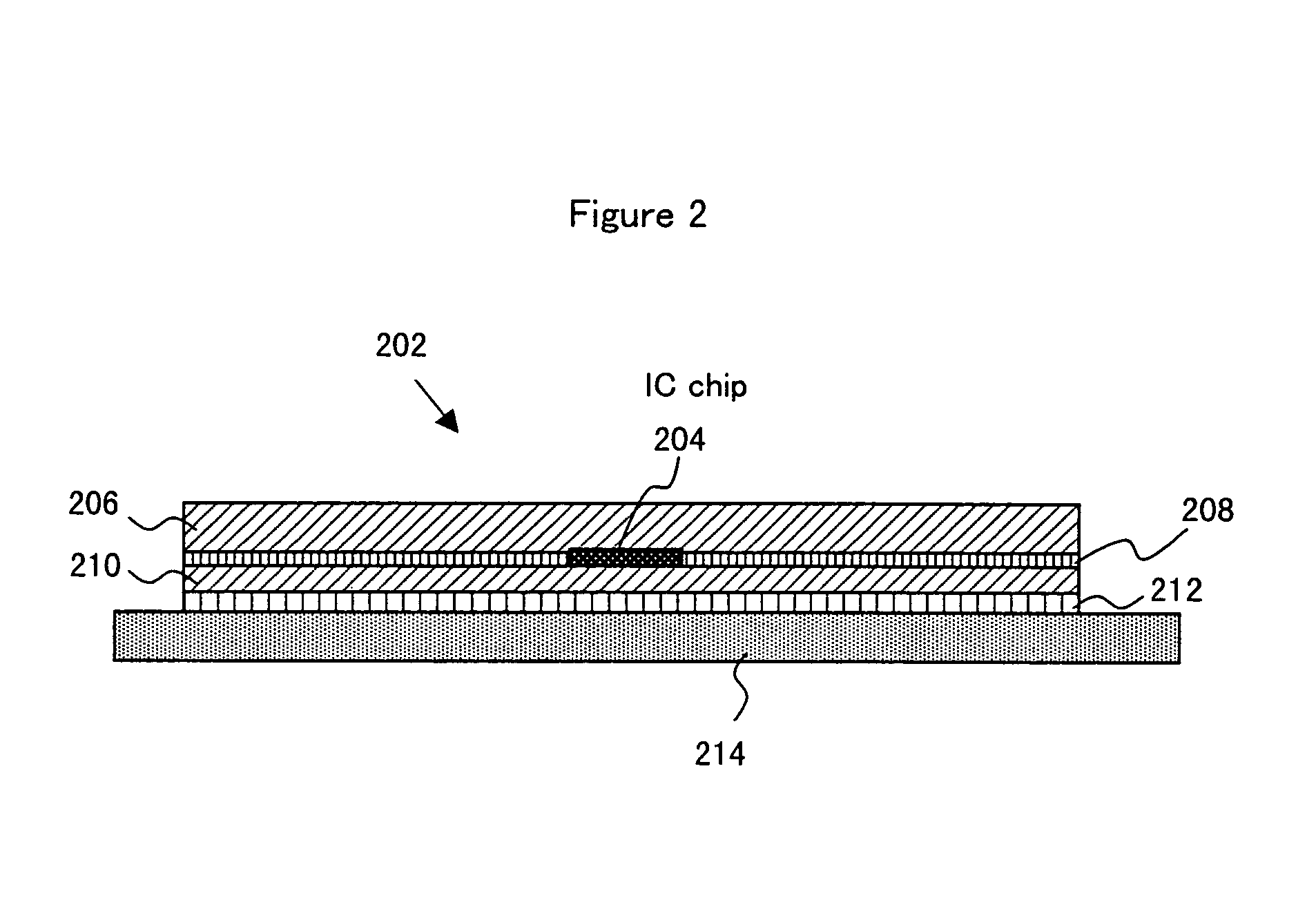
Thin film integrated circuit device, IC label, container comprising the thin film integrated circuit, manufacturing method of the thin film integrated circuit device, manufacturing method of the container, and management method of product having the container
InactiveUS7973313B2Efficiency of information managementIncrease capacitanceTransistorSolid-state devicesSiliconSemiconductor
The present invention provides an ultrathin thin film integrated circuit and a thin film integrated circuit device including the thin film integrated circuit device. Accordingly, the design of a product is not spoilt while an integrated circuit formed from a silicon wafer, which is thick and produces irregularities on the surface of the product container. The thin film integrated circuit according to the present invention includes a semiconductor film as an active region (for example a channel region in a thin film transistor), unlike an integrated circuit formed from a conventional silicon wafer. The thin film integrated circuit according to the present invention is thin enough that the design is not spoilt even when a product such as a card or a container is equipped with the thin film integrated circuit.
Owner:SEMICON ENERGY LAB CO LTD
Kinematic images formed by orienting alignable flakes
ActiveUS7604855B2Difficult to forgeEasy to identifyDecorative surface effectsPretreated surfacesKinematicsEngineering
Owner:VIAVI SOLUTIONS INC
Optical recording medium and optical recording medium recording device
InactiveUS20060098559A1Difficult to forgeEffective protectionOptical overwritingRecord information storageOptical recordingData recording
An optical recording medium such as DVD has a data recording area (103) in which data can be rewritten and a write-once area (104) in which data can be written only once and not be erased. A medium specific ID (105) which is specific to an optical recording medium is recorded in the write-once area (104). In the data recording area (103), a reflectance ratio of a part where the data is recorded is different from a reflectance ratio in a part where the data is not recorded. A reflectance ratio of a recording pit formed in the write-once area (104) is higher than the higher one of the reflectance ratios in the part where the data is recorded and in the part where the data is not recorded in the data recording area (103). Data recoding in the write-once area (104) is performed by irradiating to the write-once area (104) a laser beam with heat amount of three to 25 times heat amount necessary for recording rewritable data in the data recording area (103).
Owner:PANASONIC CORP
IP based security applications using location, port and/or device identifier information
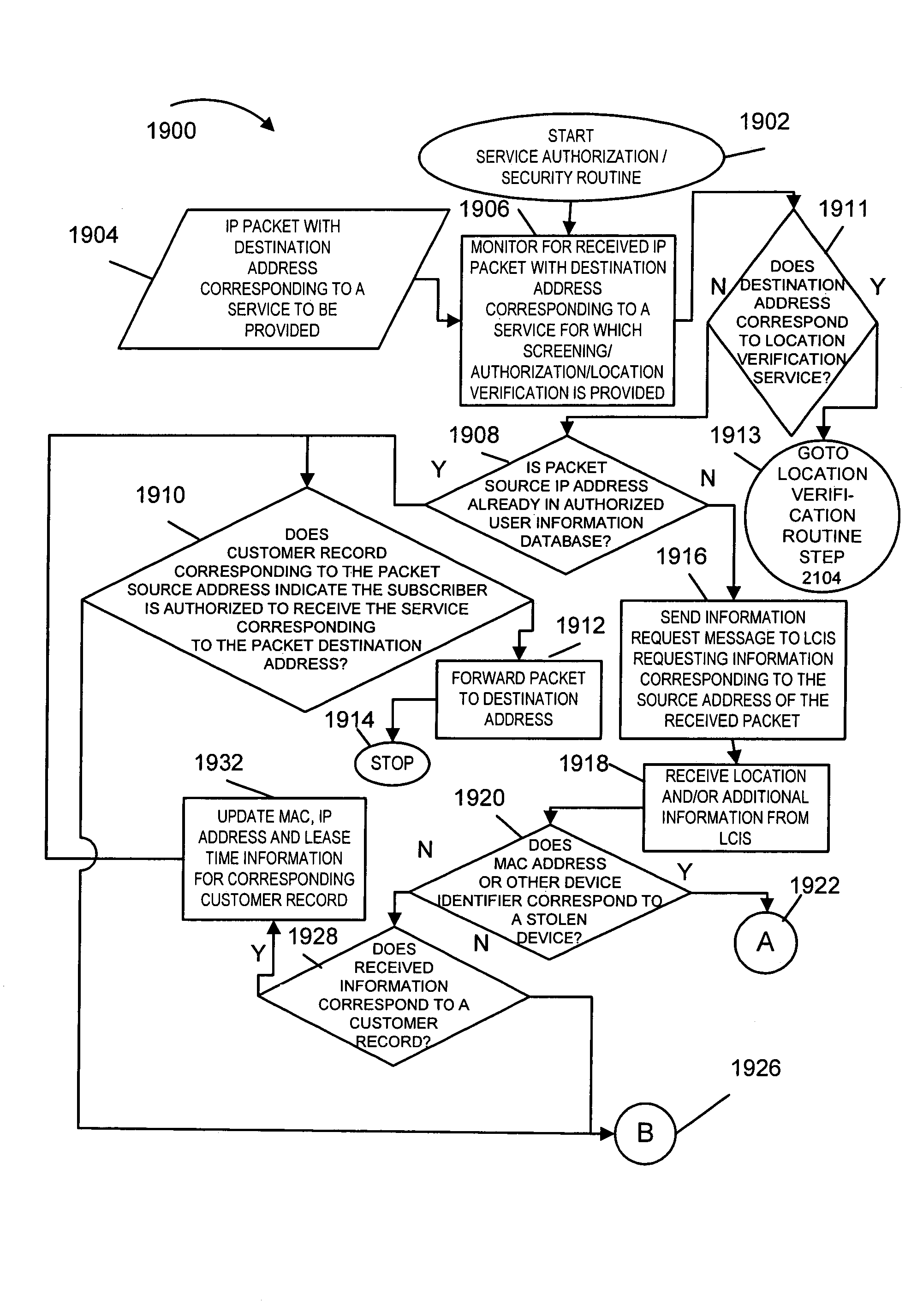
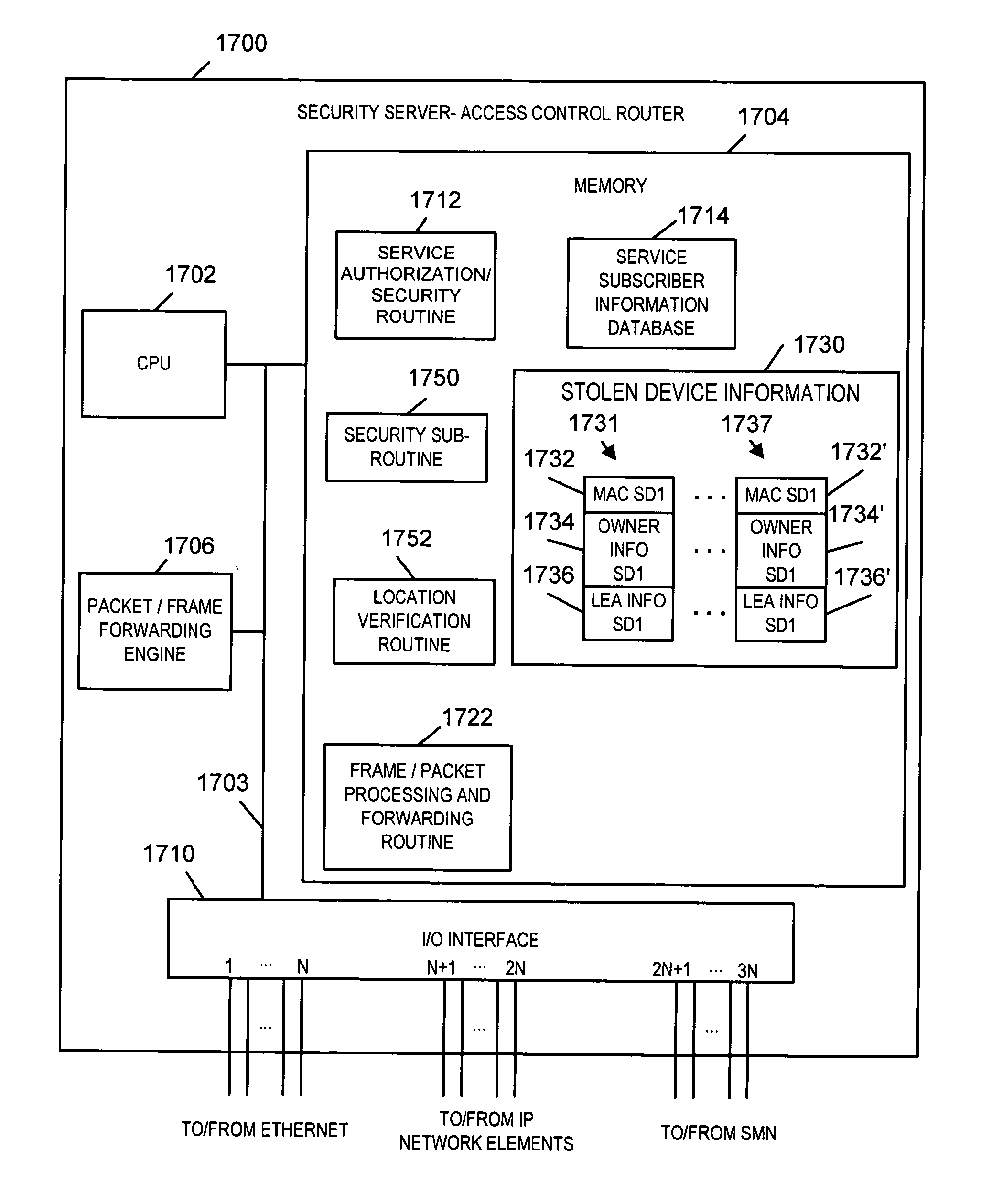
InactiveUS20110067119A1Quick checkDifficult to forgeVolume/mass flow measurementTime-division multiplexInternet privacyIp address
Methods and apparatus for determining, in a reliable manner, a port, physical location and / or device identifier, such as a MAC address, associated with a device using an IP address and for using such information, e.g., to support one or more security applications is described. Supported security applications include restricting access to services based on the location of a device seeking access to a service, determining the location of stolen devices, and verifying the location of the source of a message or other IP signal, e.g., to determine if a prisoner is contacting a monitoring service from a predetermined location.
Owner:VERIZON PATENT & LICENSING INC
Methods and apparatus for protecting against IP address assignments based on a false MAC address
InactiveUS20080092228A1Quick checkDifficult to forgeTime-division multiplexMultiple digital computer combinationsIp addressProtocol for Carrying Authentication for Network Access
Methods and apparatus detecting attempts to obtain IP addresses by faking a MAC address in a data portion of an IP address request message are described. In accordance with the present invention, rather than use standard address allocation protocols, e.g., ARP, the DNS DCHP contacts the requesting edge router via a private secure network. The MAC address received in the address request is compared to the MAC addresses stored in the edge routers port / MAC address resolution table. If the MAC address received in the request message cannot be found in the edge router's table which was created from the MAC address included in the message's header, a fraudulent attempt to obtain a MAC address is declared. The fraudulent attempt to obtain an IP address can be reported and steps taken to identify the perpetrator of the fraud.
Owner:VERIZON PATENT & LICENSING INC
System for producing secure toner-based images and methods of forming and using the same
ActiveUS6998211B2Easy to visually assesSimple methodDecorative surface effectsDuplicating/marking methodsComputer scienceColoring agents
Owner:TROY GRP INC
Method for secure site and user authentication
ActiveUS8458774B2Not easily defeatedImprove securityDigital data processing detailsMultiple digital computer combinationsCommunications securityWeb site
Owner:PAYFONE
IP based security applications using location, port and/or device identifier information
ActiveUS7873985B2Remove the burdenCollect revenueDigital data processing detailsTime-division multiplexIp addressDevice Identifiers
Methods and apparatus for determining, in a reliable manner, a port, physical location and / or device identifier, such as a MAC address, associated with a device using an IP address and for using such information, e.g., to support one or more security applications is described. Supported security applications include restricting access to services based on the location of a device seeking access to a service, determining the location of stolen devices, and verifying the location of the source of a message or other IP signal, e.g., to determine if a prisoner is contacting a monitoring service from a predetermined location.
Owner:VERIZON PATENT & LICENSING INC
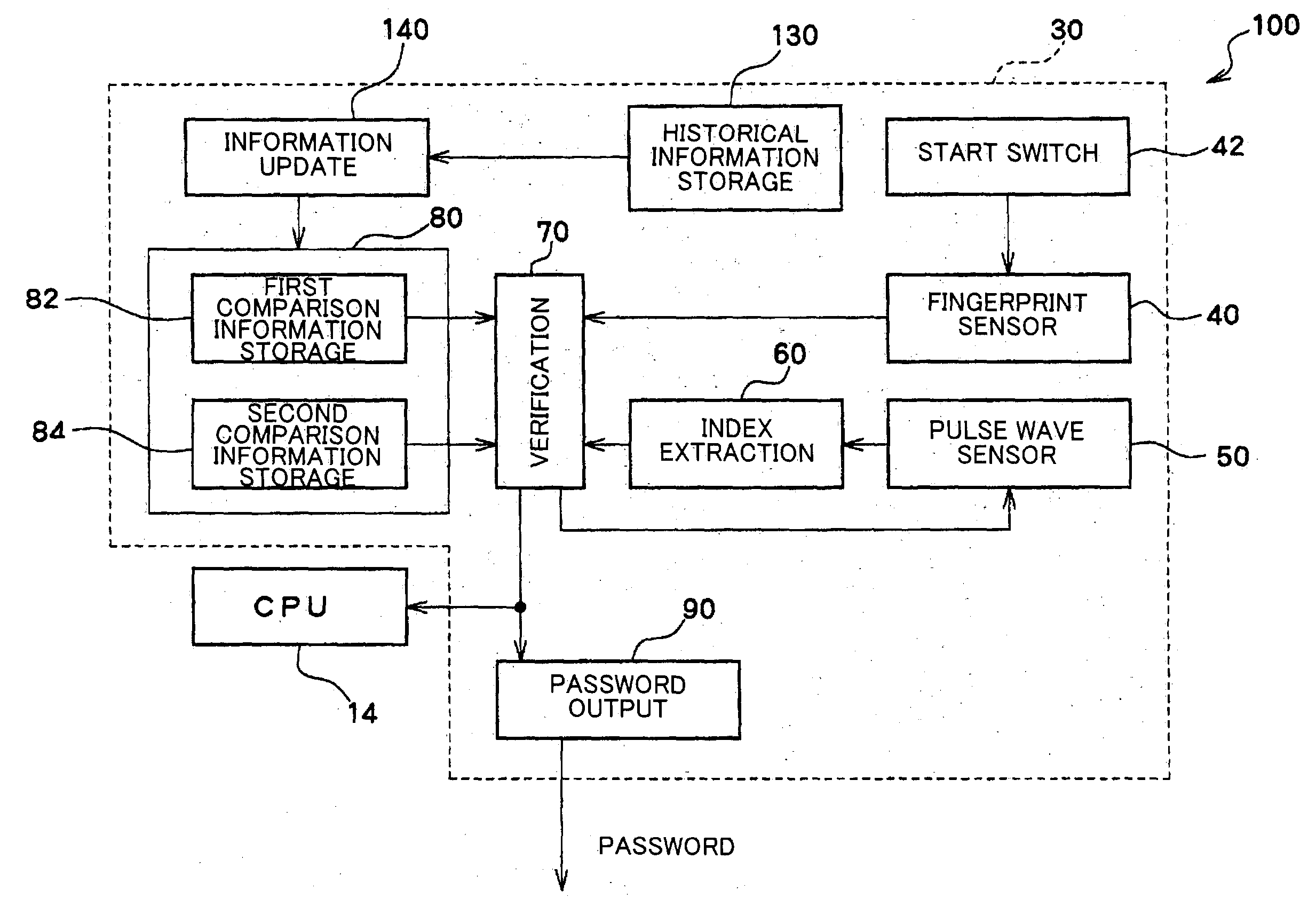
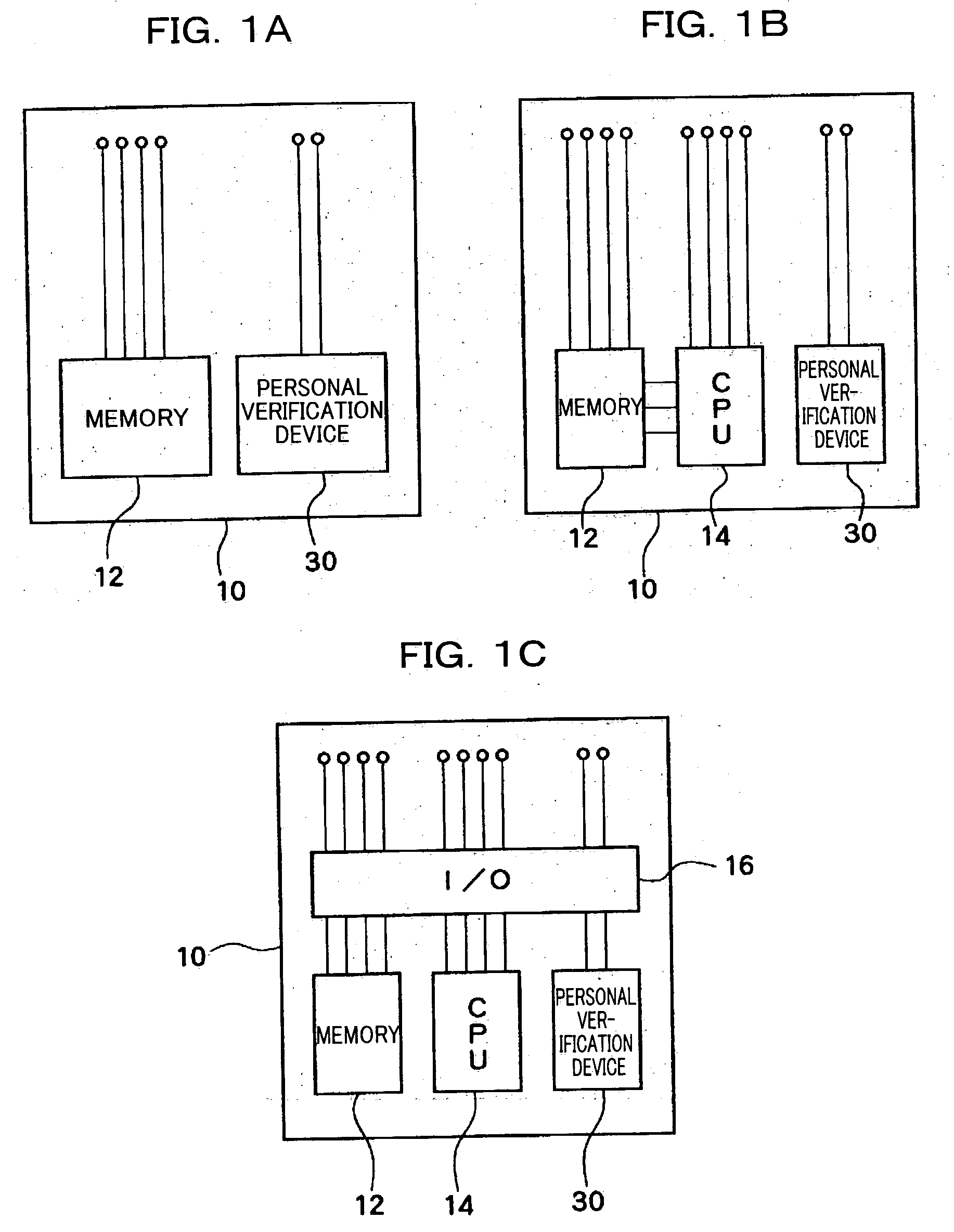
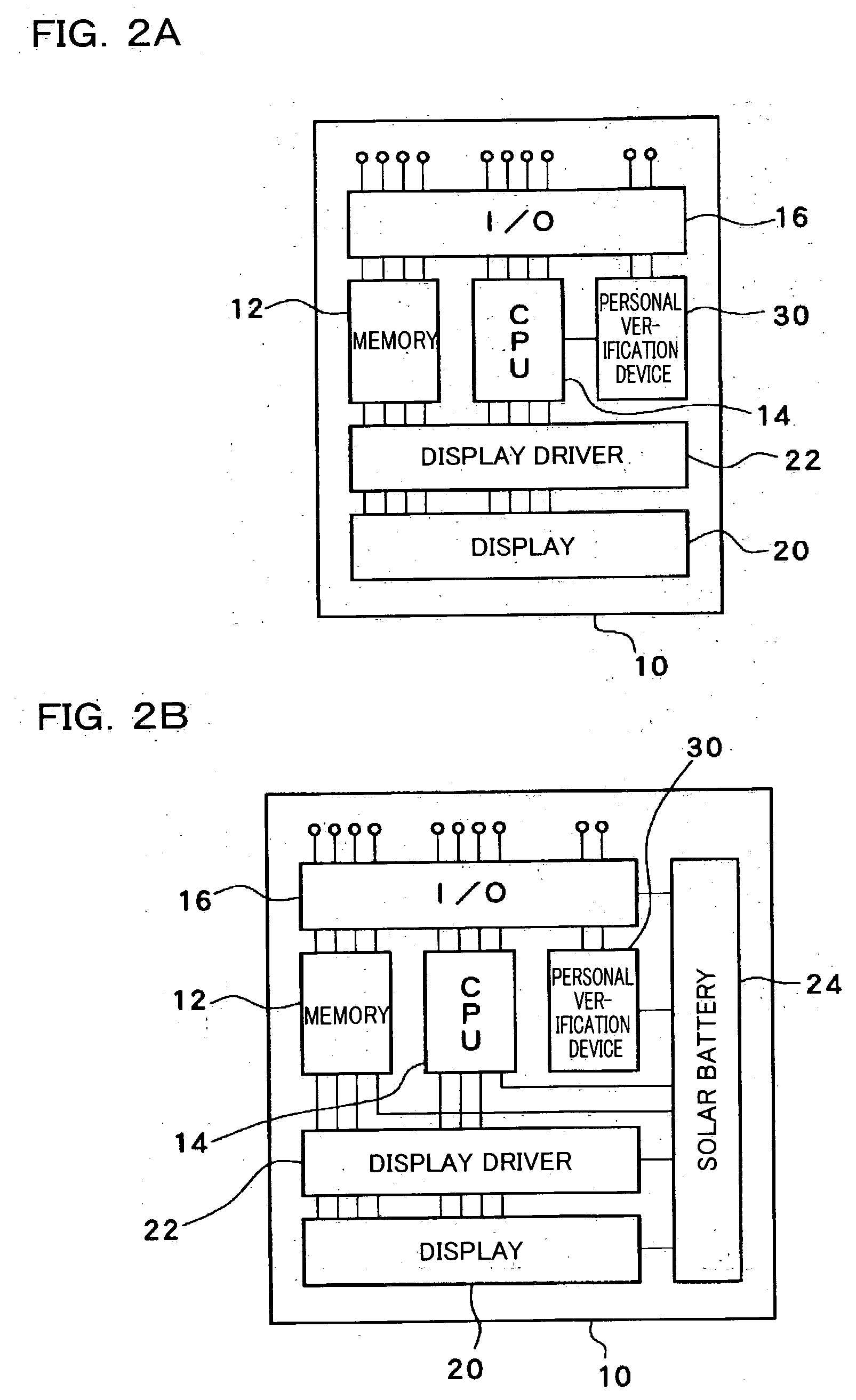
Personal verification device, card-type information storage medium, and information processing system using the same
ActiveUS20050053264A1Highly accurateDifficult to verifyPerson identificationComputer security arrangementsFingerprintInformation handling system
A personal verification device includes a fingerprint sensor which detects a fingerprint of an operator, and a pulse wave sensor which detects a pulse wave of the operator. An index extraction section processes the pulse wave detected by the pulse wave sensor and extracts at least one index. First reference information which is compared with a fingerprint is stored in a first reference information storage section. Second reference information which is compared with the at least one index is stored in a second reference information storage section. A verification section outputs a signal indicating that the operator is true when it is determined that the operator is a registered person based on the result of comparison between the fingerprint and the first reference information, and it is determined that the operator is alive based on the result of comparison between the at least one index and the second reference information.
Owner:138 EAST LCD ADVANCEMENTS LTD
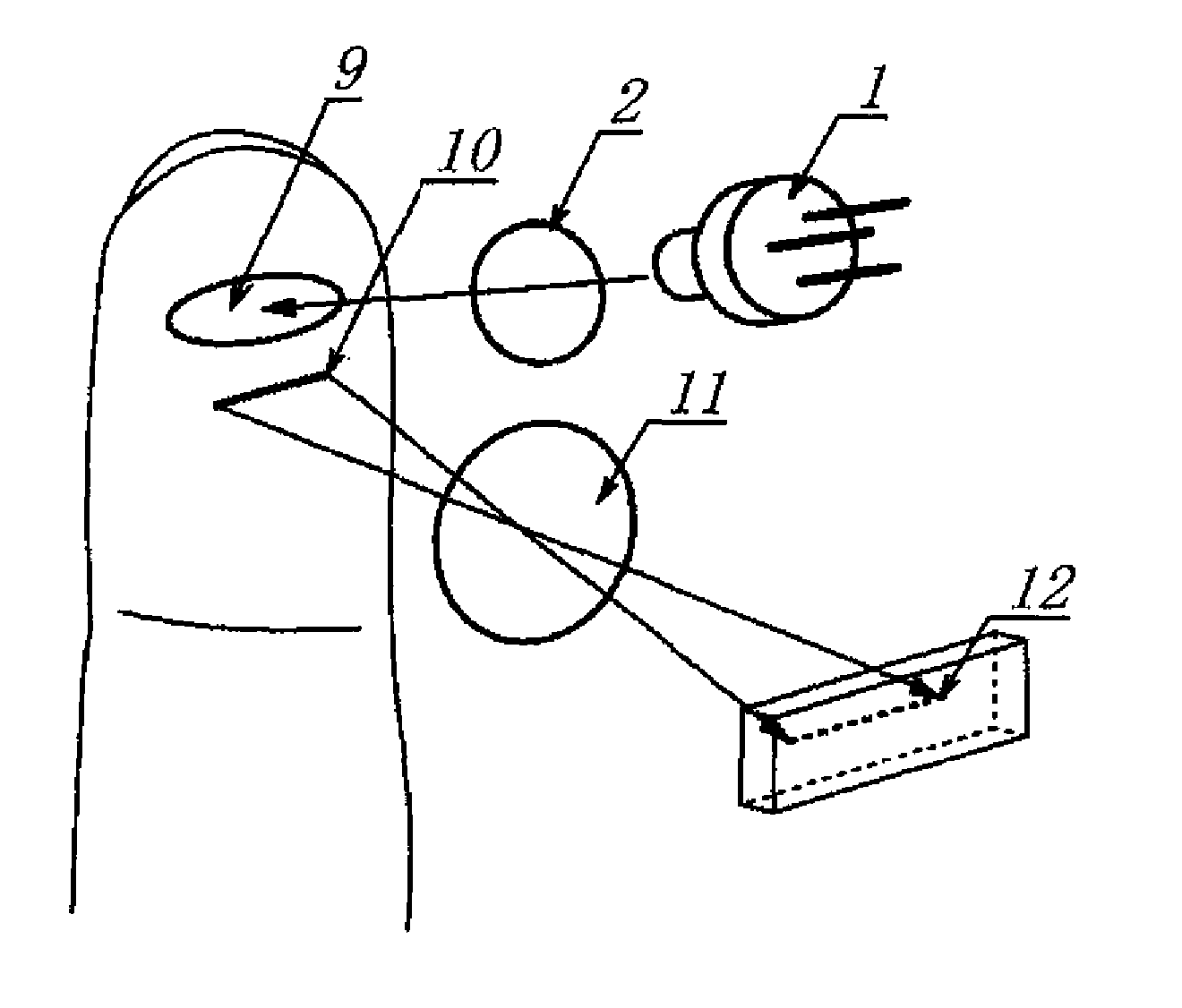
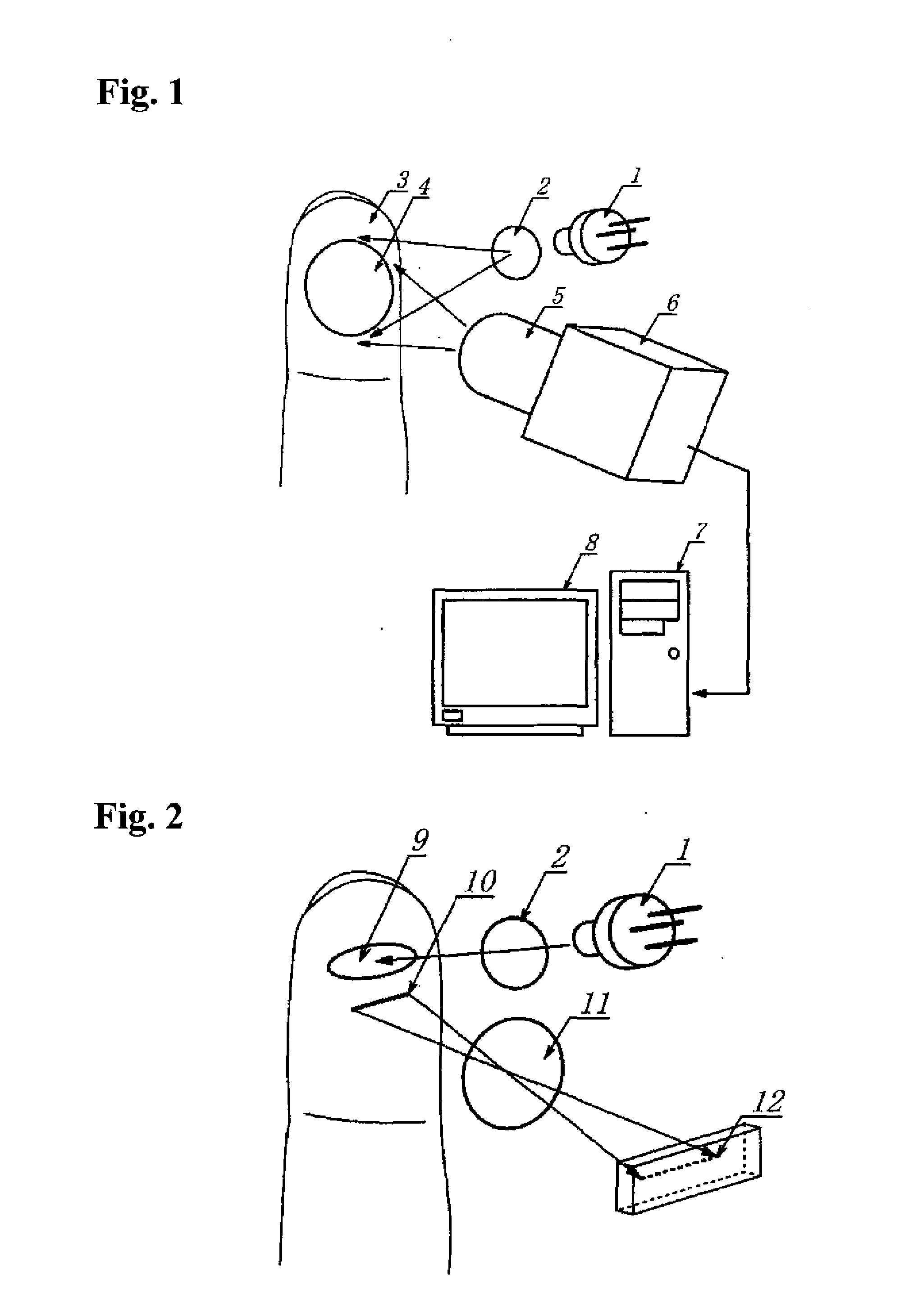
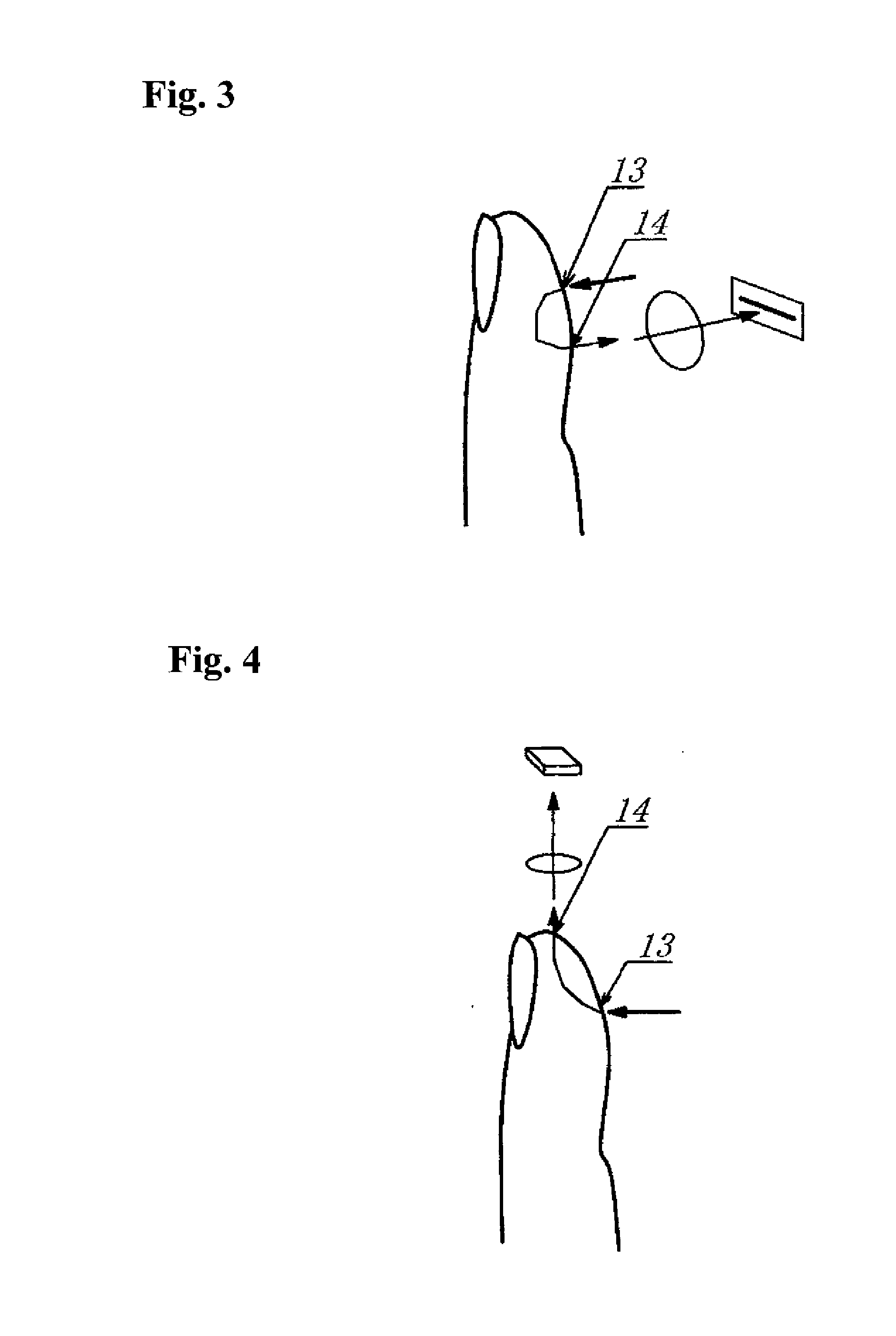
Personal authentication method using subcutaneous bloodstream measurement and personal authentication device
ActiveUS20110026783A1Difficult to forgeDistinguish clearlyPerson identificationDigital data authenticationImage sensorLaser beams
In a personal authentication method using the subcutaneous bloodstream measurement where an expanded laser beam is irradiated onto a finger pad, light reflected from a subcutaneous blood vessel layer is imaged on an image sensor as a laser speckle using an optical system, a quantity that represents the rate of change with respect to time of the amount of light received for each pixel of the laser speckle is calculated, the values are used as a two-dimensional map to obtain a map showing the bloodstream of the finger pad, and the bloodstream map is comparison-checked against pre-registered data of individuals, the laser speckle is imaged on the image sensor using a region separate from a region irradiated by the laser beam as an observation region of the image sensor. A device for use in the method is also provided. Relating to a method and device for authentication using, e.g., a finger print pattern on the basis of the laser speckle, an improved technique capable of extracting, e.g., the finger print pattern accurately is provided.
Owner:NAT UNIV CORP KYUSHU INST OF TECH (JP) +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com