Method for protecting mobile phone private data
A data and privacy technology, applied in the fields of digital data protection, computer security devices, telephone communication, etc., can solve the problems of narrow application of encryption mode, inability to enable the functions related to the address book and address book, and affecting the use of mobile phones.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0045] Embodiment 1: a method for protecting mobile phone privacy data.
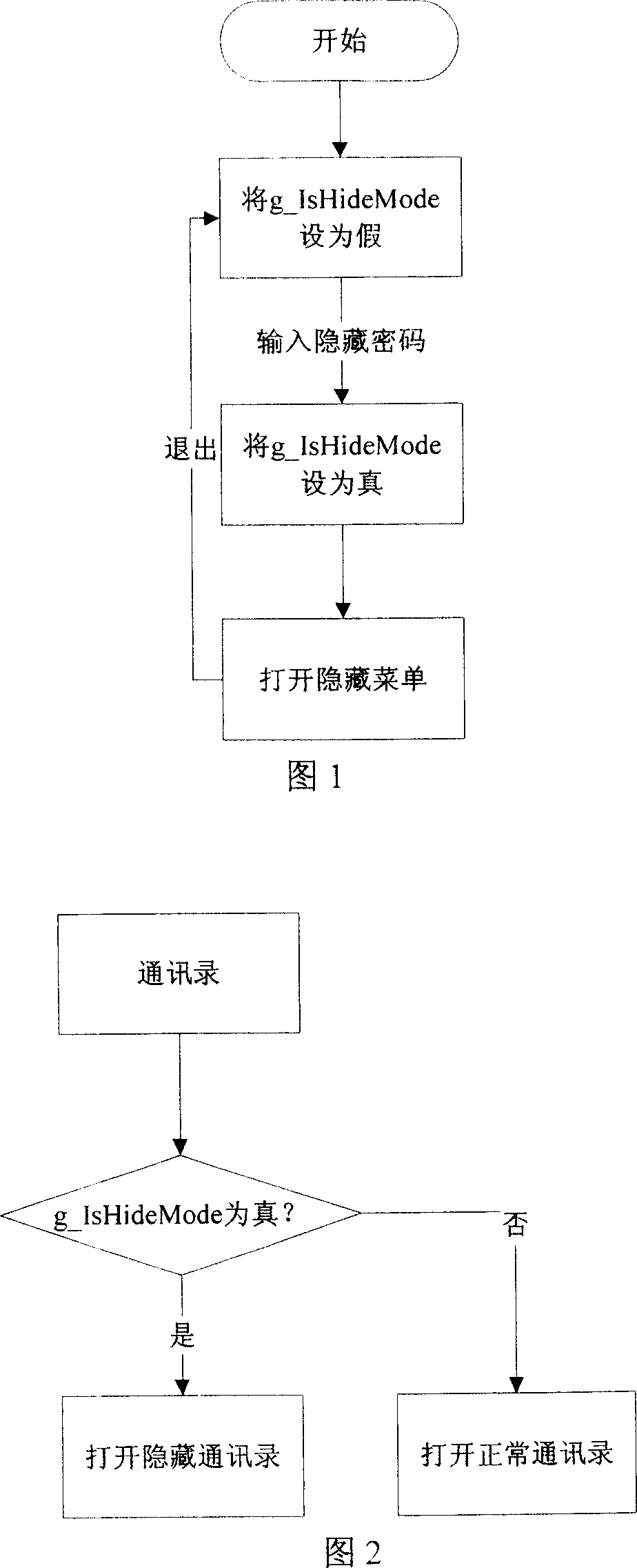
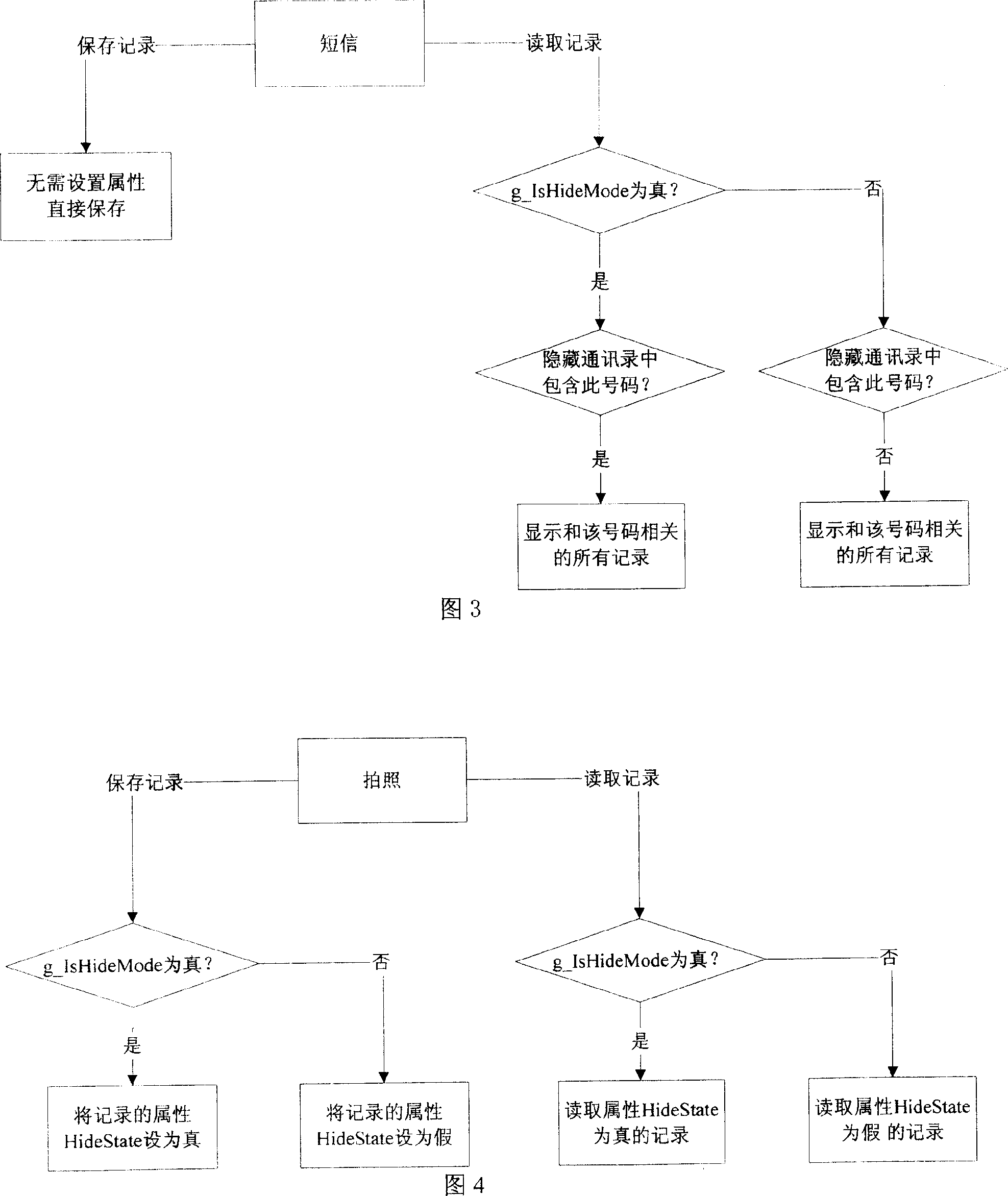
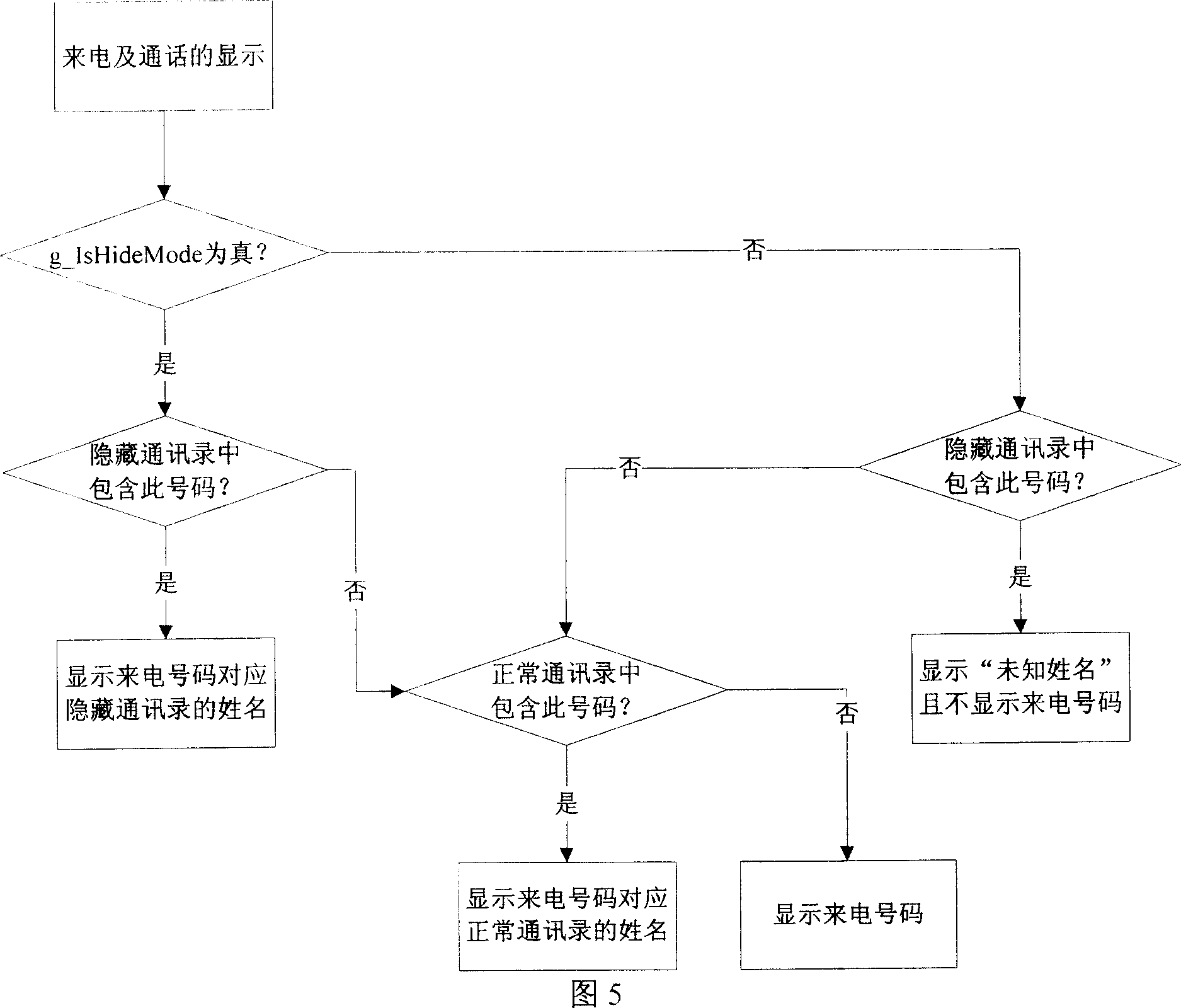
[0046] The functional modules of the mobile phone that may contain the private information of the organic owner include: address book, call records, SMS, MMS, photo taking, video recording, recording, notepad, schedule, etc. For the data related to the number, the private data can be distinguished from the normal data by setting the hidden number. The normal mode provides any user with standard mobile phone functions, and can view the normal information of all mobile phones; the hidden mode is a special function provided to the owner of the mobile phone, which realizes the storage and reading of the private data of the mobile phone, and is used to monitor the private data of the owner. protection of. The switch between normal and hidden mode can be realized by encrypting the hidden menu or encrypting the interface of entering the hidden mode.
[0047] Applying the above method, the main steps of the me...
Embodiment 2
[0071] Embodiment 2: a method for protecting mobile phone privacy data.
[0072] According to the method of embodiment 1, when using the hidden function of the mobile phone, the owner may need to set the privacy data to different levels to be disclosed to different people, which is impossible for the method of embodiment 1. Multiple hidden modes can be set according to the idea of Embodiment 1, and the passwords of each hidden mode are different, and different hidden passwords are announced to different people, so that the function of classifying private data can be realized.
[0073] Applying the above points of view, the main steps of the method are as follows:
[0074] (1) The mobile phone interface is divided into multiple hidden modes and a normal mode, each hidden mode is used to store different levels of private data, and the normal mode is used to store normal data. Set an integer global variable g_IsHideMode and save it in the EEPROM of the mobile phone. When the ...
Embodiment 3
[0077] Embodiment 3: a method for protecting mobile phone privacy data.
[0078] According to the method of Embodiment 1, the switch between the normal mode and the hidden mode is realized by encrypting the hidden menu, and of course it can also be realized by encrypting the interface of entering the hidden mode.
[0079] Applying the above method, the main steps of the method are as follows:
[0080](1) Divide the mobile phone interface into two modes: hidden and normal, and store all data (hidden data and normal data) and normal data respectively. Set a Boolean global variable g_IsHideMode and save it in the EEPROM of the mobile phone. When the value of g_IsHideMode is true, it means that the current mode is hidden; when the value of g_IsHideMode is false, it means that the current mode is normal; then set a parameter variable HideState of a file, and when the value of HideState is true, it means that the file is marked as a hidden attribute ; When the value of HideState i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com