Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
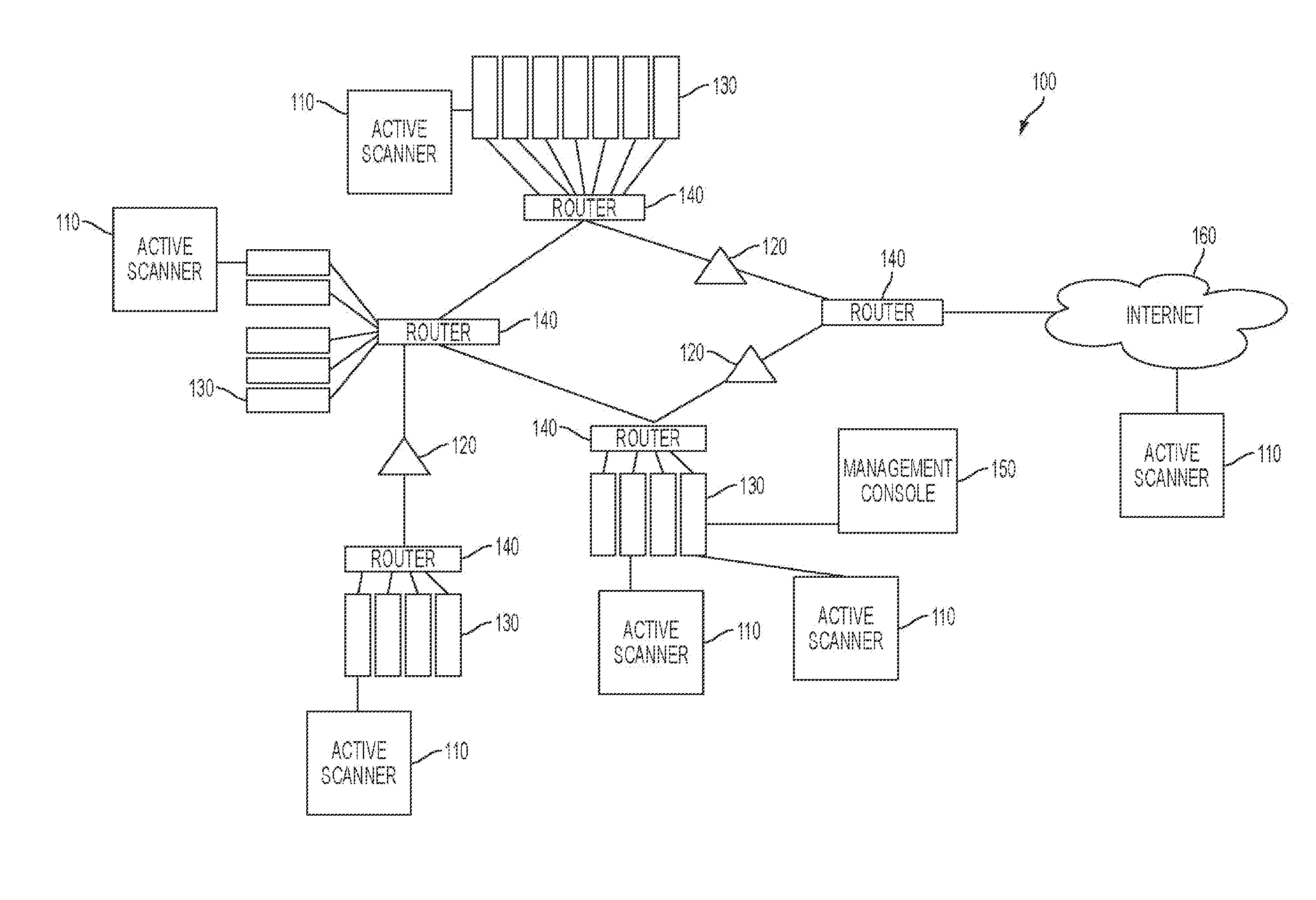
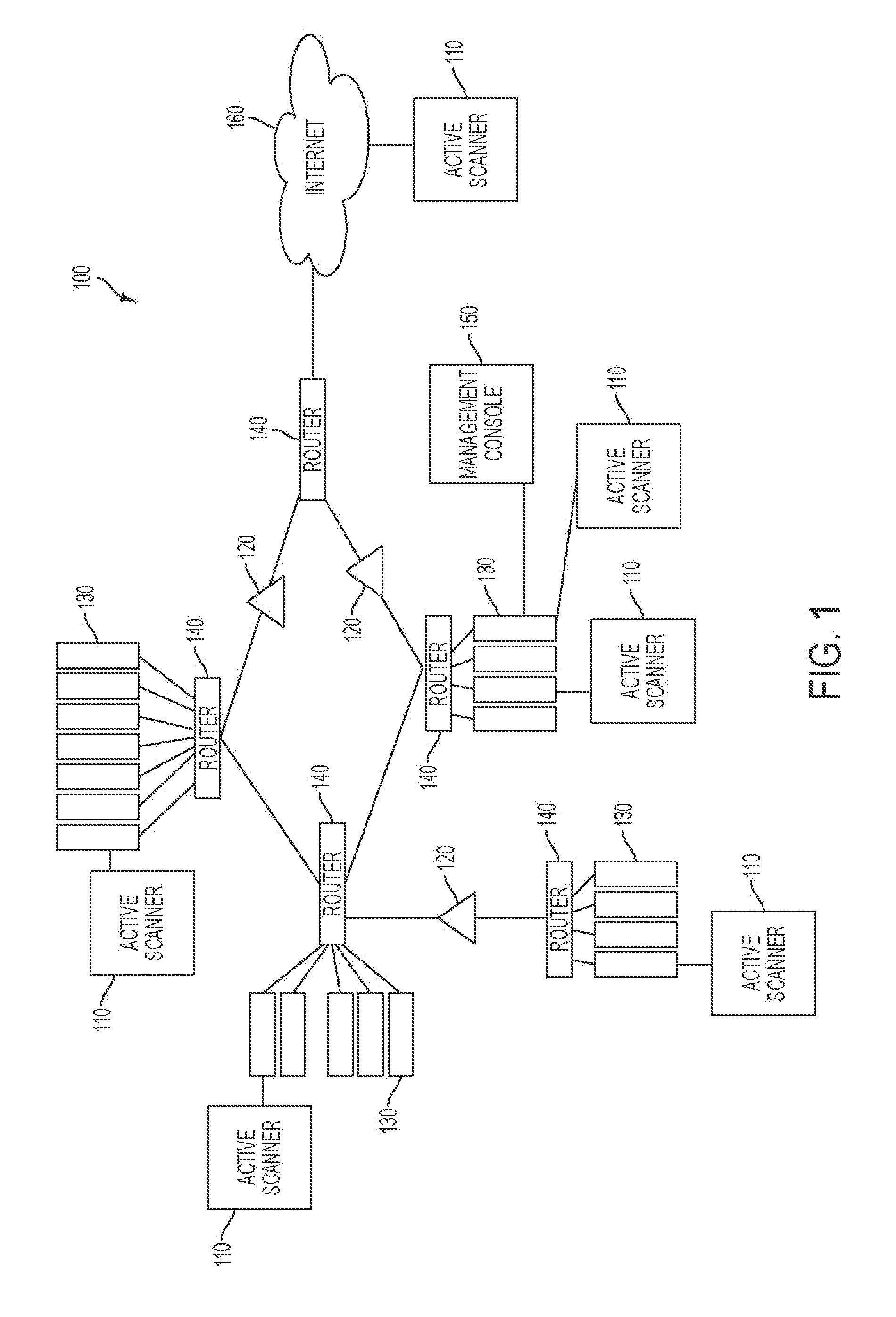
322 results about "Botnet" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
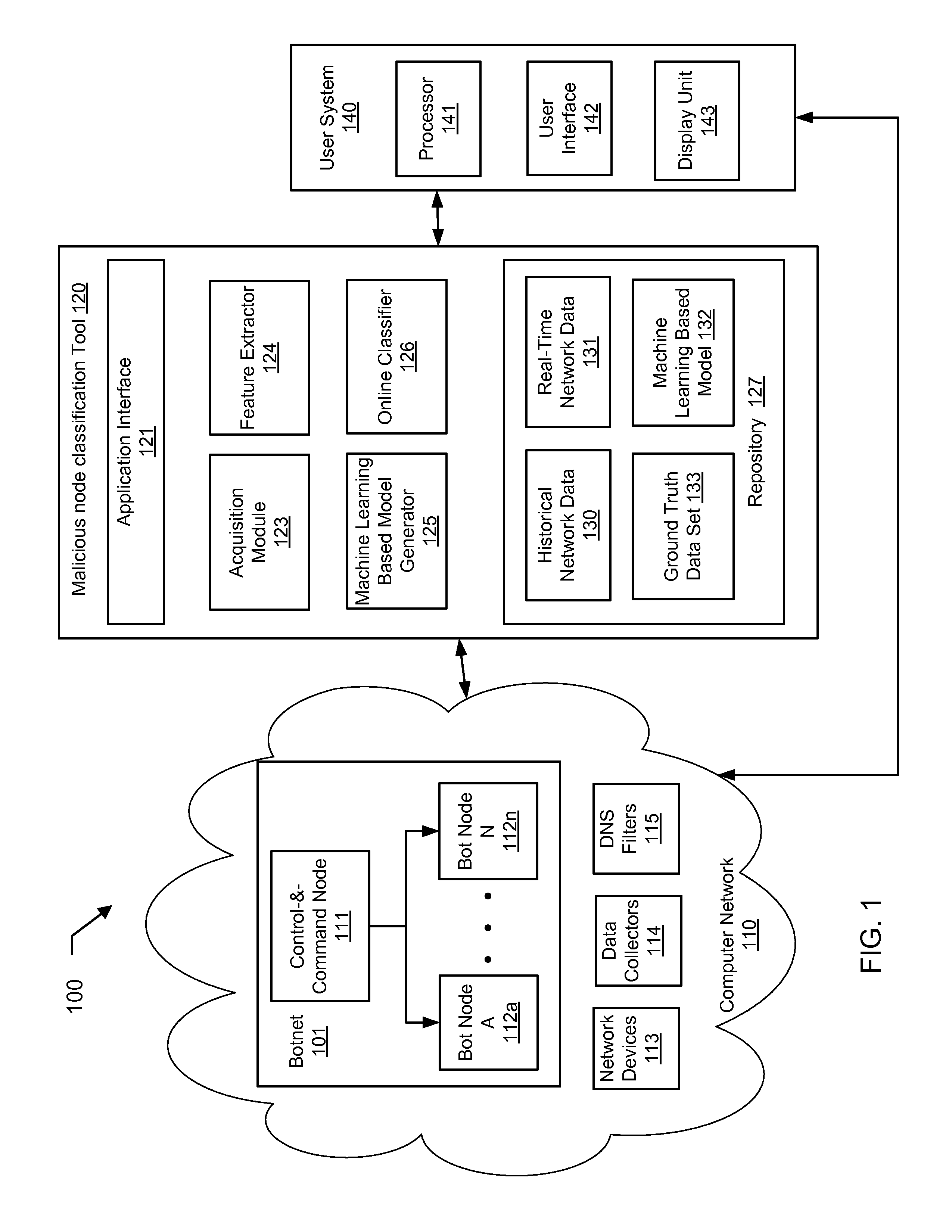
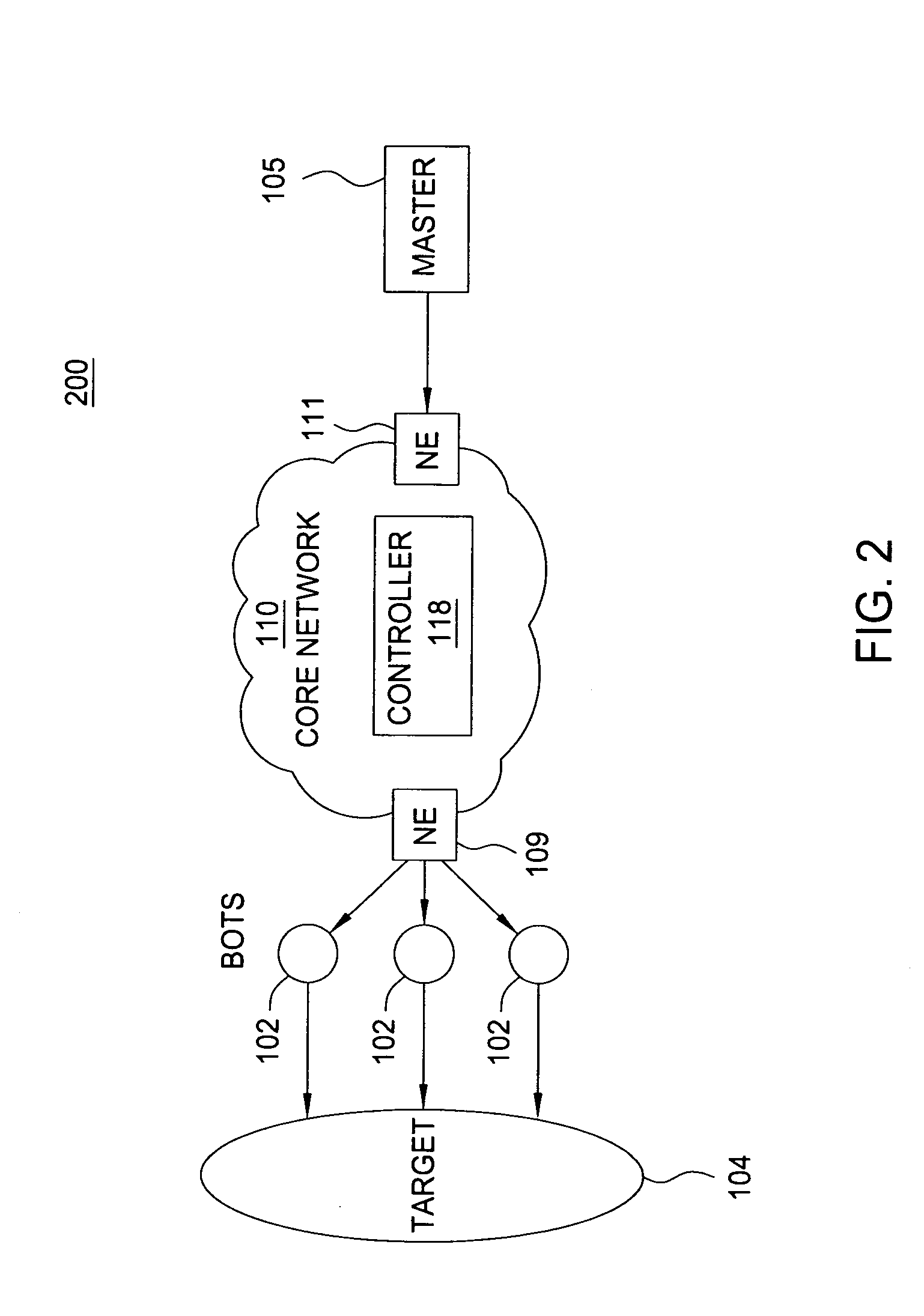
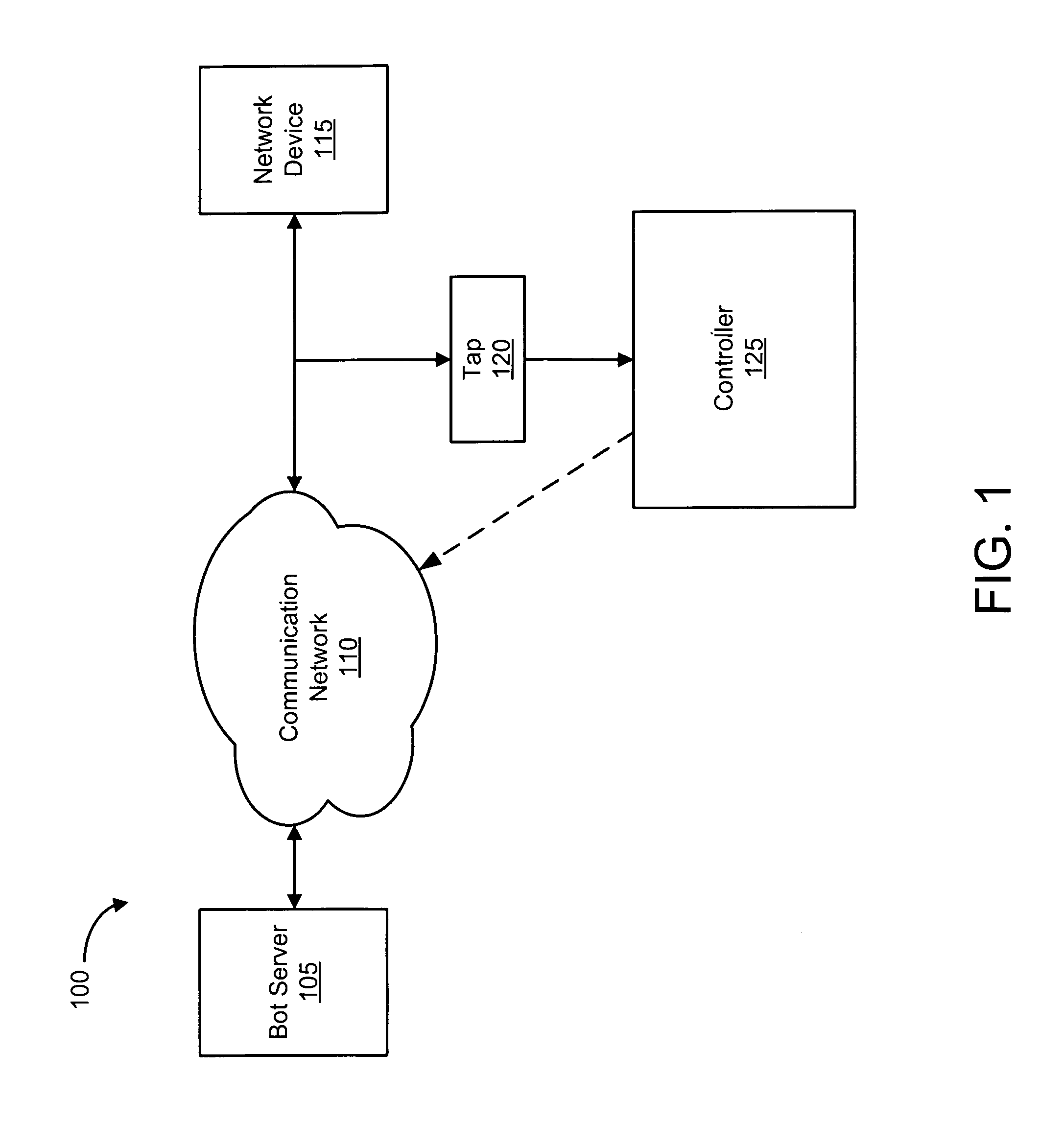
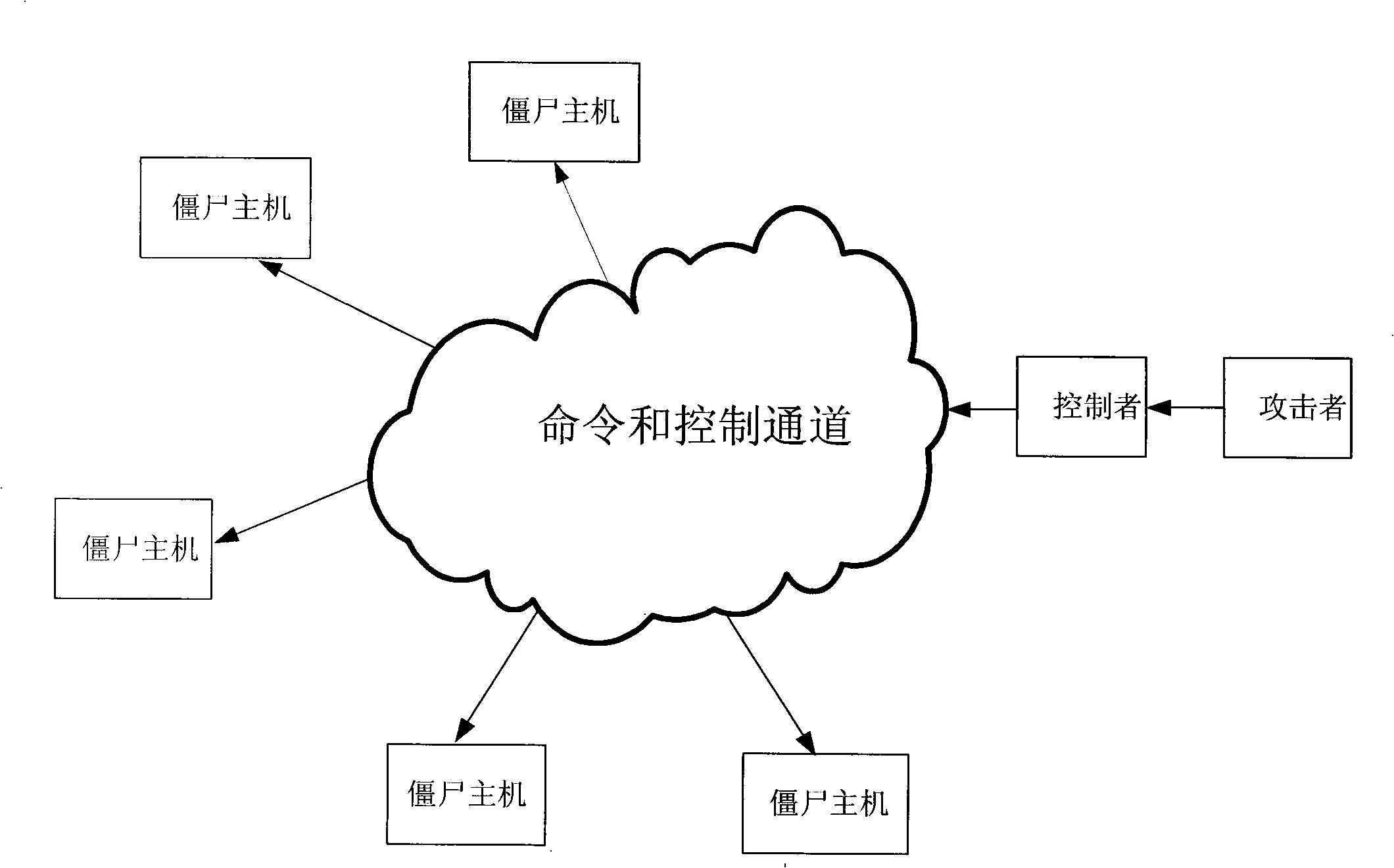
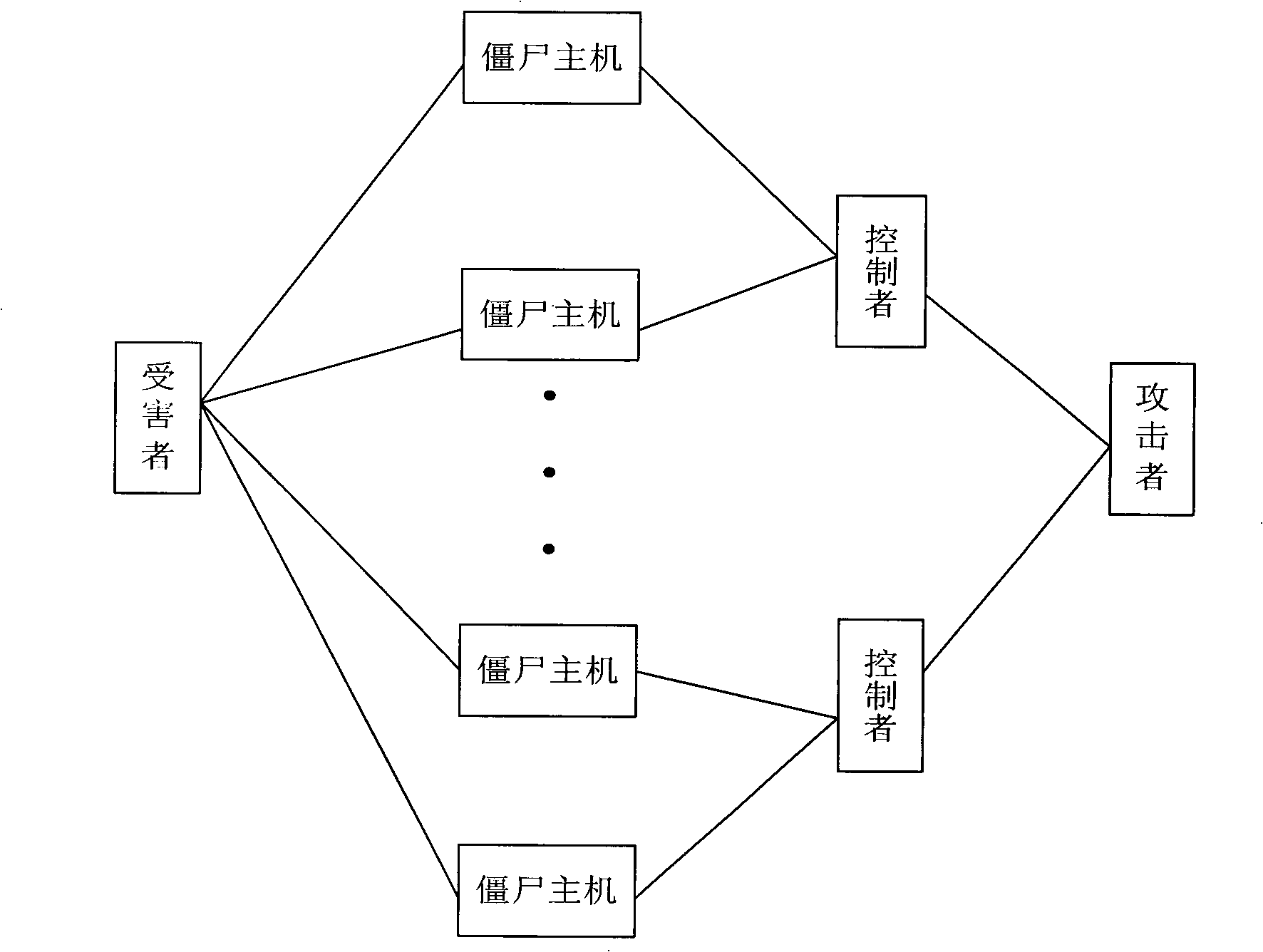
A botnet is a number of Internet-connected devices, each of which is running one or more bots. Botnets can be used to perform distributed denial-of-service attack (DDoS attack), steal data, send spam, and allows the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a combination of the words "robot" and "network". The term is usually used with a negative or malicious connotation.
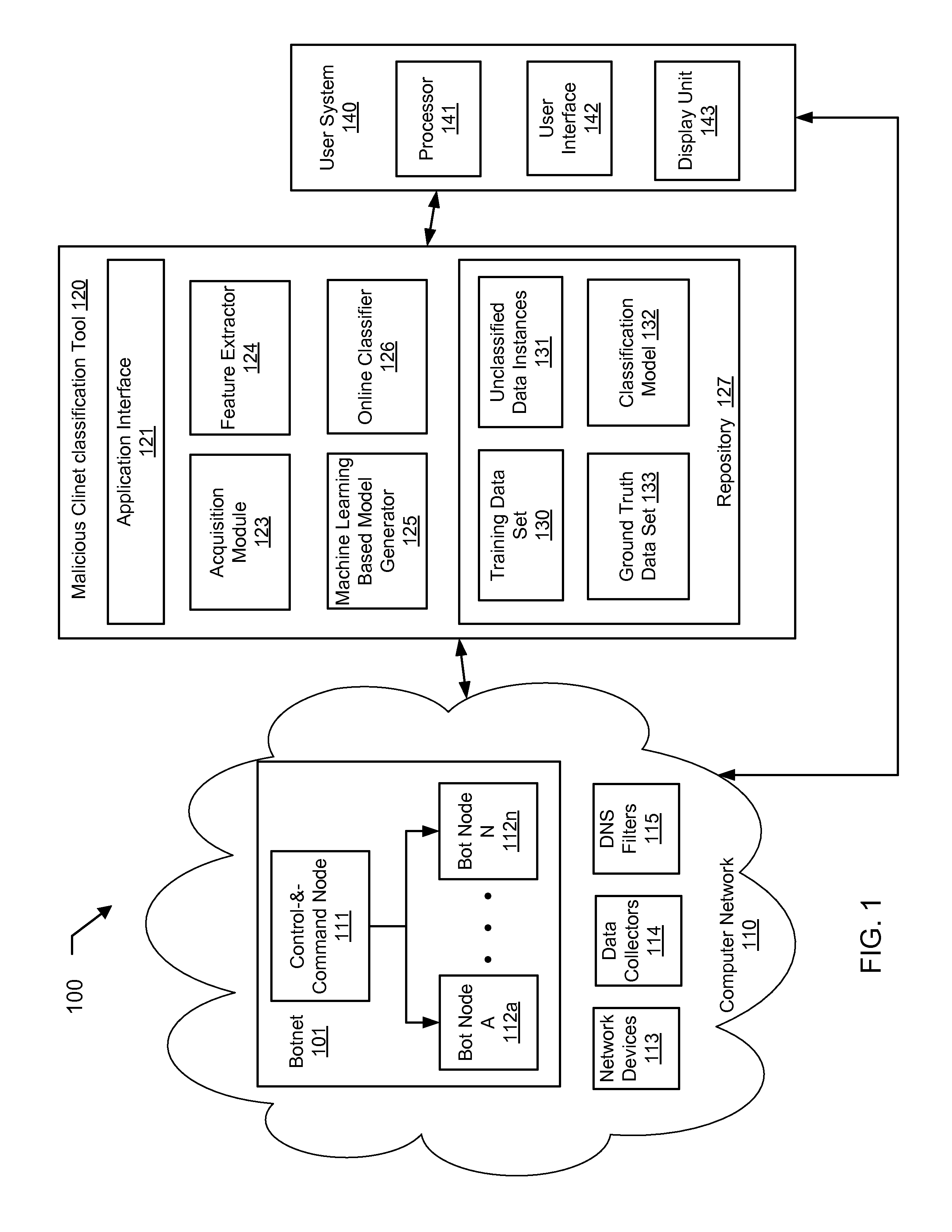
Machine learning based botnet detection using real-time extracted traffic features
ActiveUS8682812B1Digital computer detailsComputer security arrangementsLearning basedTraffic capacity
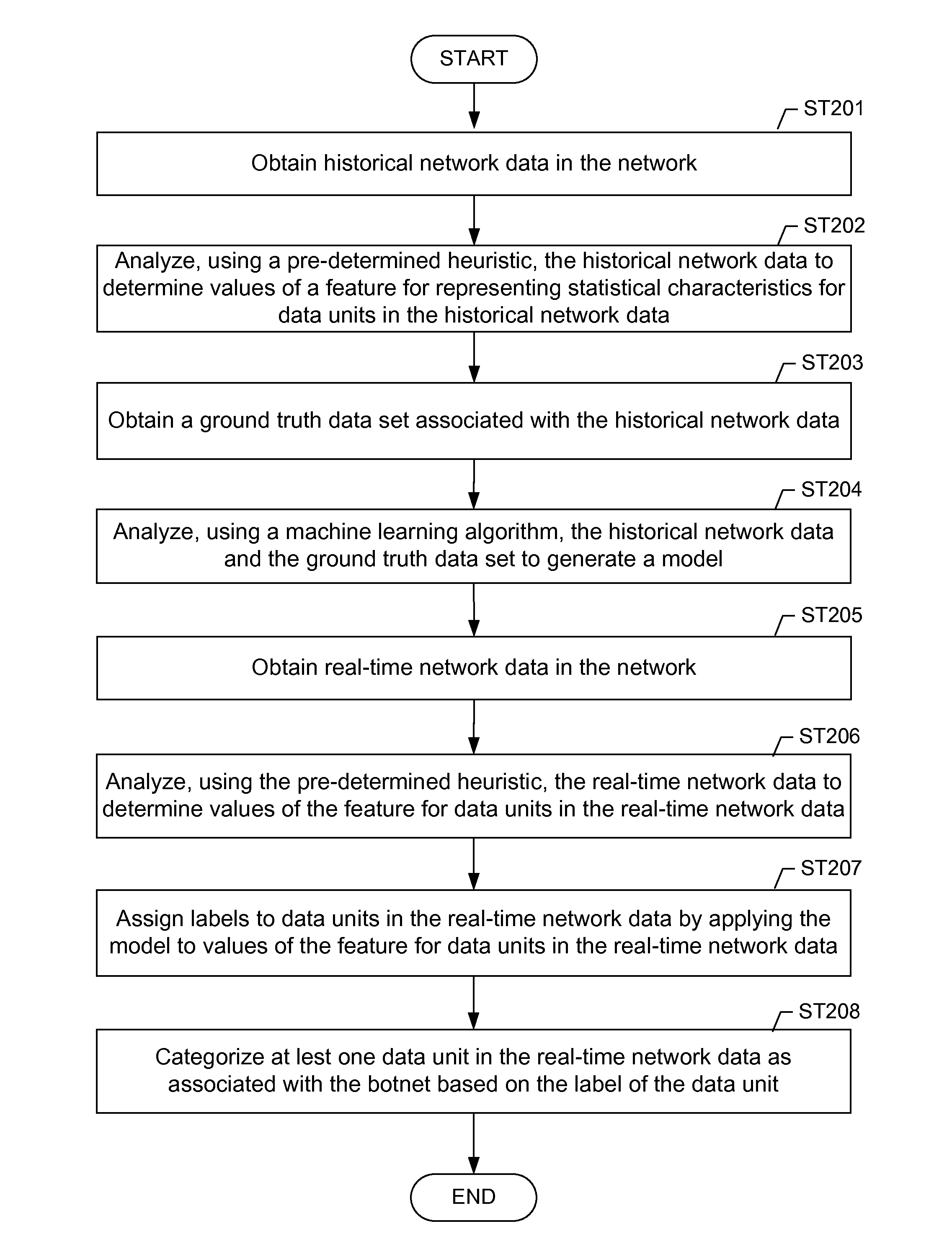
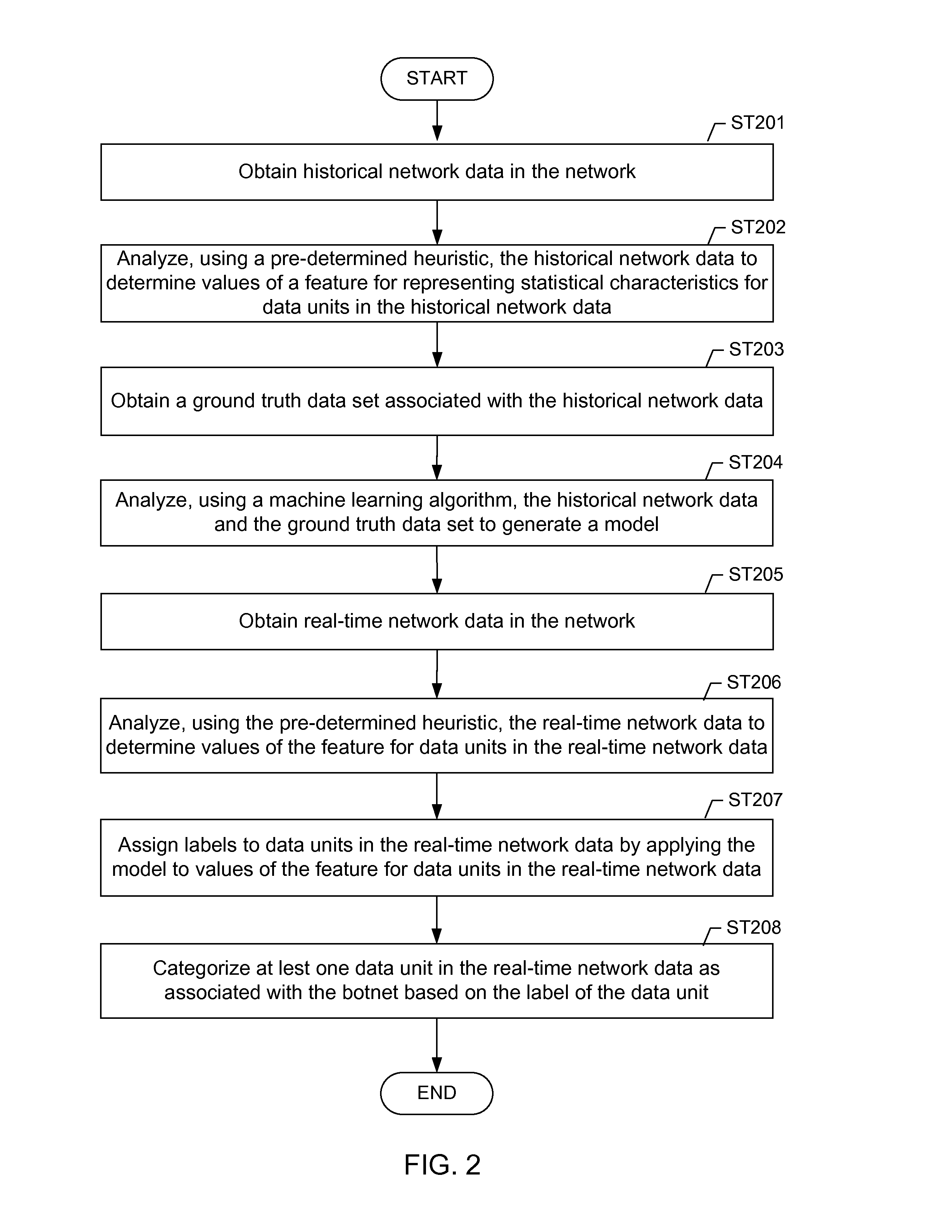
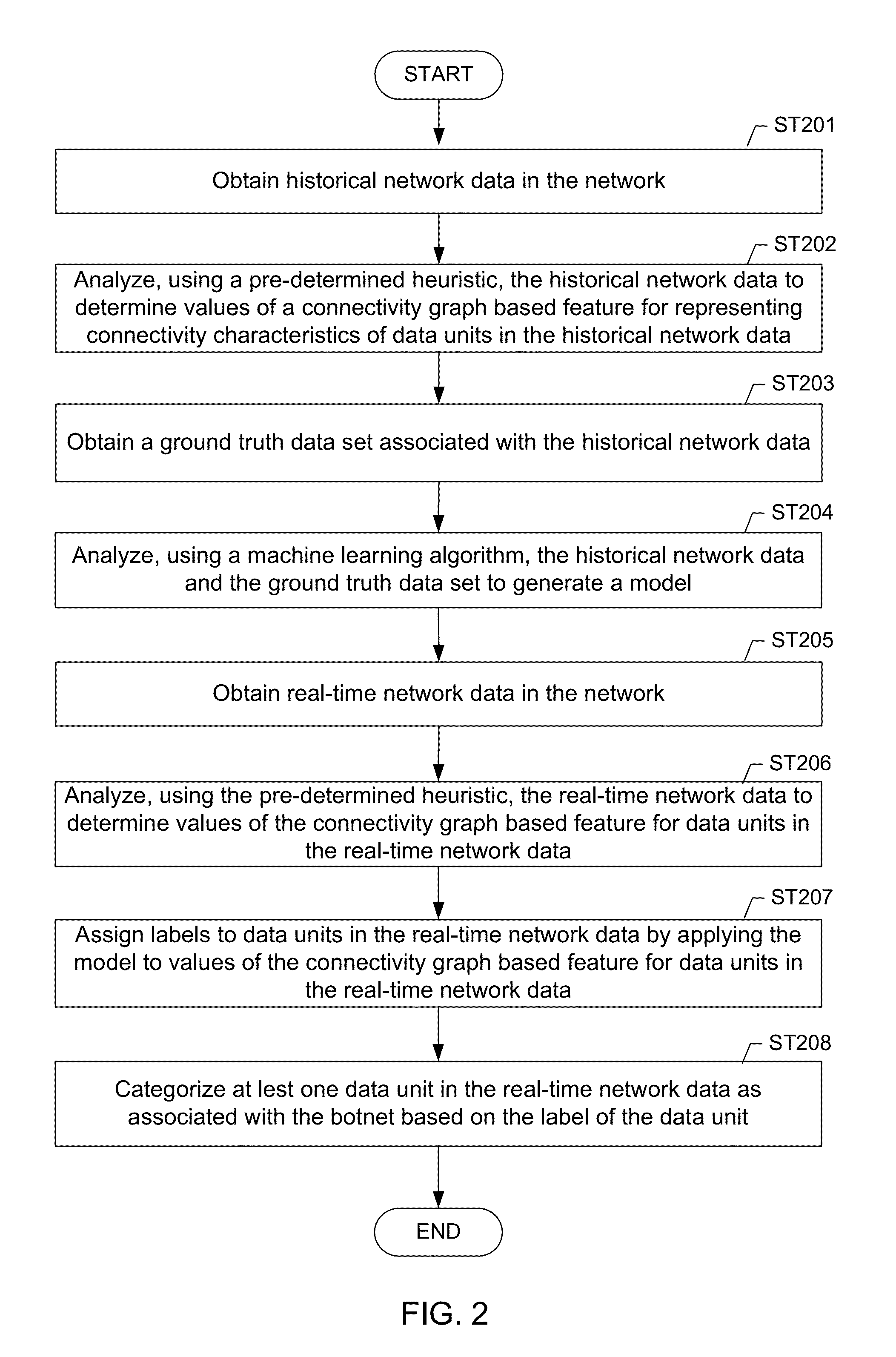
A method for identifying a botnet in a network, including analyzing historical network data using a pre-determined heuristic to determine values of a feature in the historical network data, obtaining a ground truth data set having labels assigned to data units in the historical network data identifying known malicious nodes in the network, analyzing the historical network data and the ground truth data set using a machine learning algorithm to generate a model representing the labels as a function of the values of the feature, analyzing real-time network data using the pre-determined heuristic to determine a value of the feature for a data unit in the real-time network data, assigning a label to the data unit by applying the model to the value of the feature, and categorizing the data unit as associated with the botnet based on the label.
Owner:THE BOEING CO
Method and apparatus for detecting compromised host computers
A method and apparatus for detecting compromised host computers (e.g., Bots) are disclosed. For example, the method identifies a plurality of suspicious hosts. Once identified, the method analyzes network traffic of the plurality suspicious hosts to identify a plurality suspicious hub-servers. The method then classifies the plurality of candidate Bots into at least one group. The method then identifies members of each of the at least one group that are connected to a same controller from the plurality suspicious controllers, where the members are identified to be part of a Botnet.
Owner:AT&T INTPROP II L P
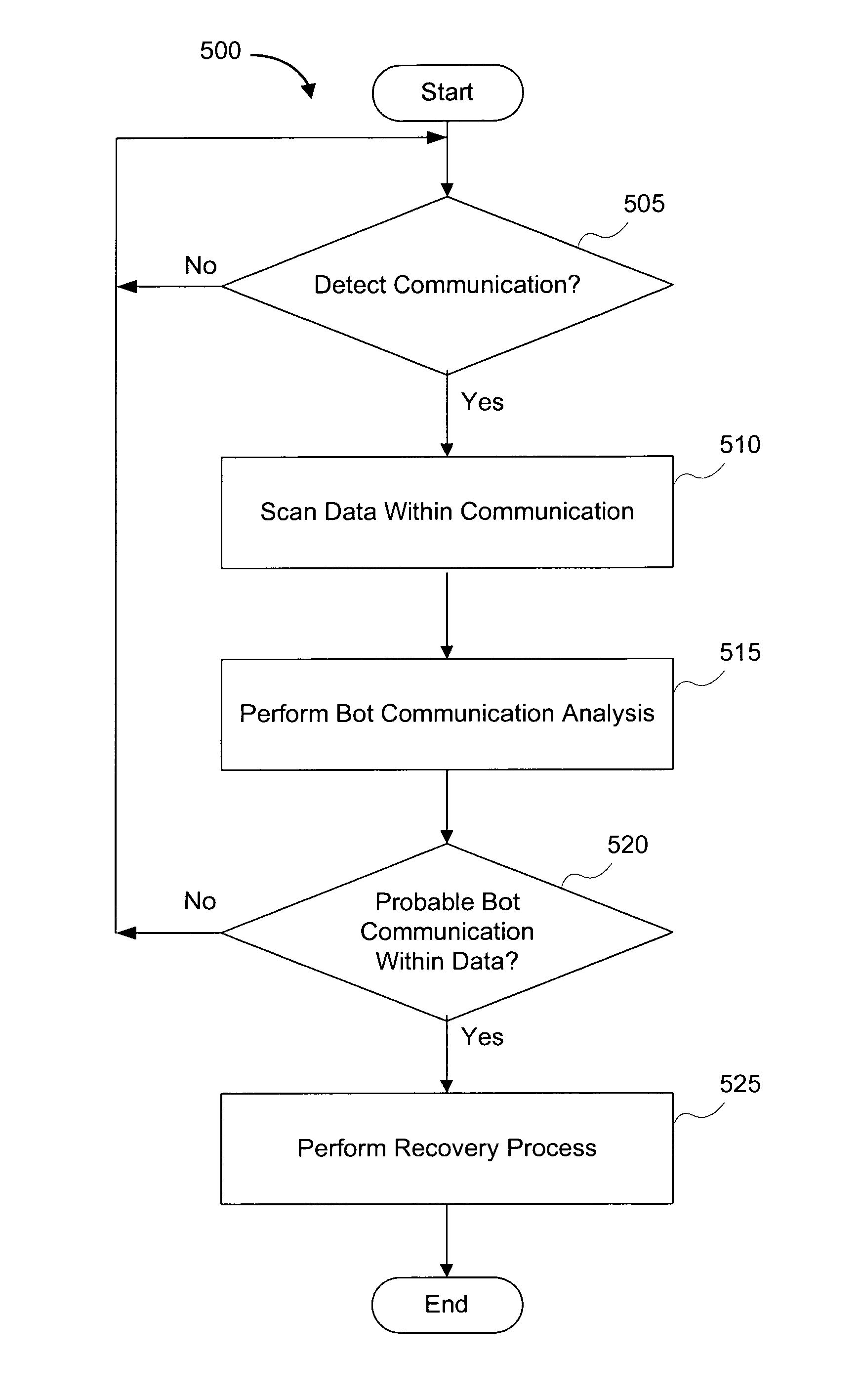
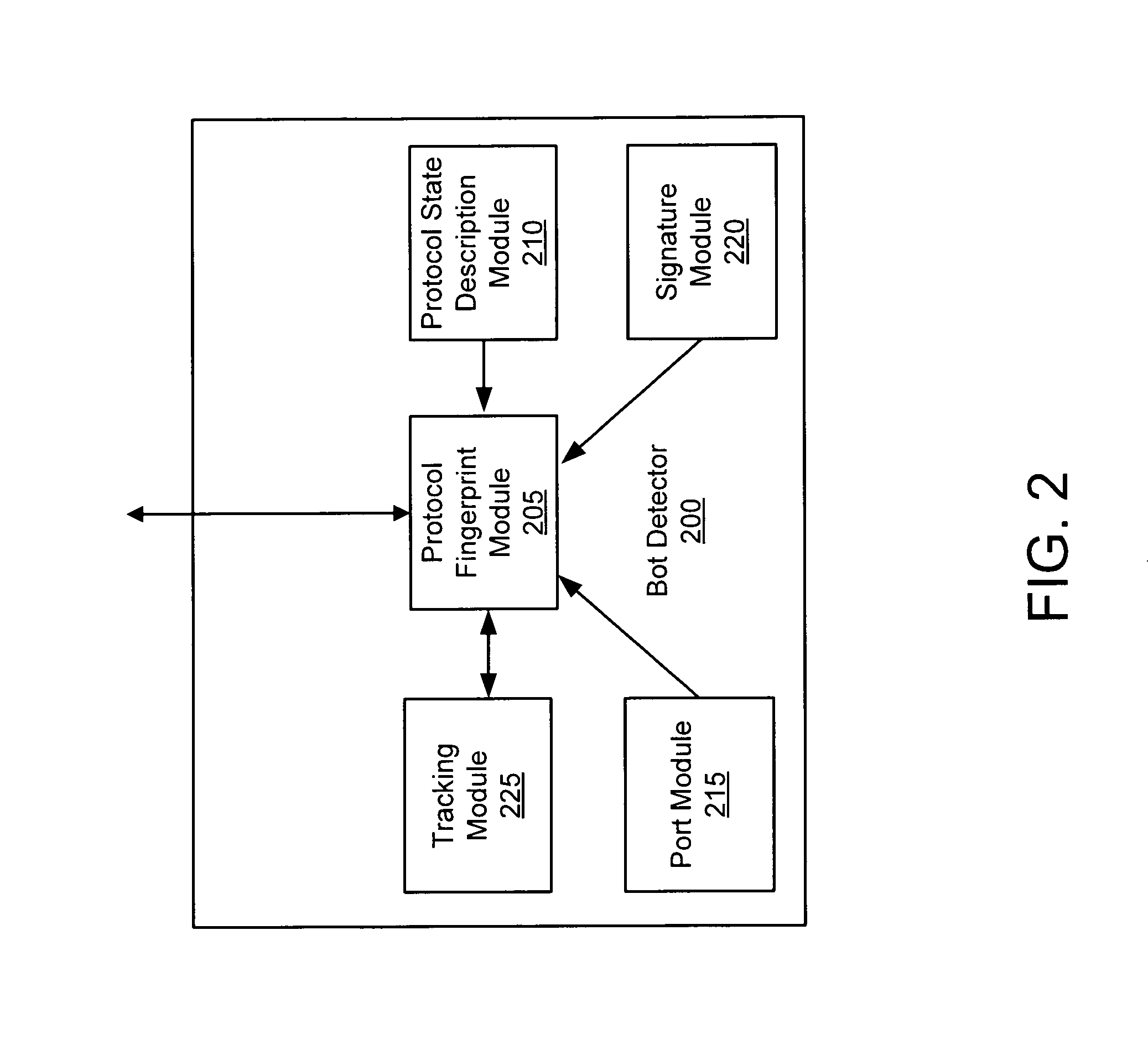
Systems and methods for detecting communication channels of bots
ActiveUS8561177B1Detect presenceMemory loss protectionError detection/correctionBotnetComputer security
Exemplary systems and methods for detecting a communication channel of a bot. In exemplary embodiments, presence of a communication channel between a first network device and a second network device is detected. Data from the communication channel is scanned and used to determine if a suspected bot communication exists. If a bot communication is detected, then a recovery process may be initiated.
Owner:FIREEYE SECURITY HLDG US LLC
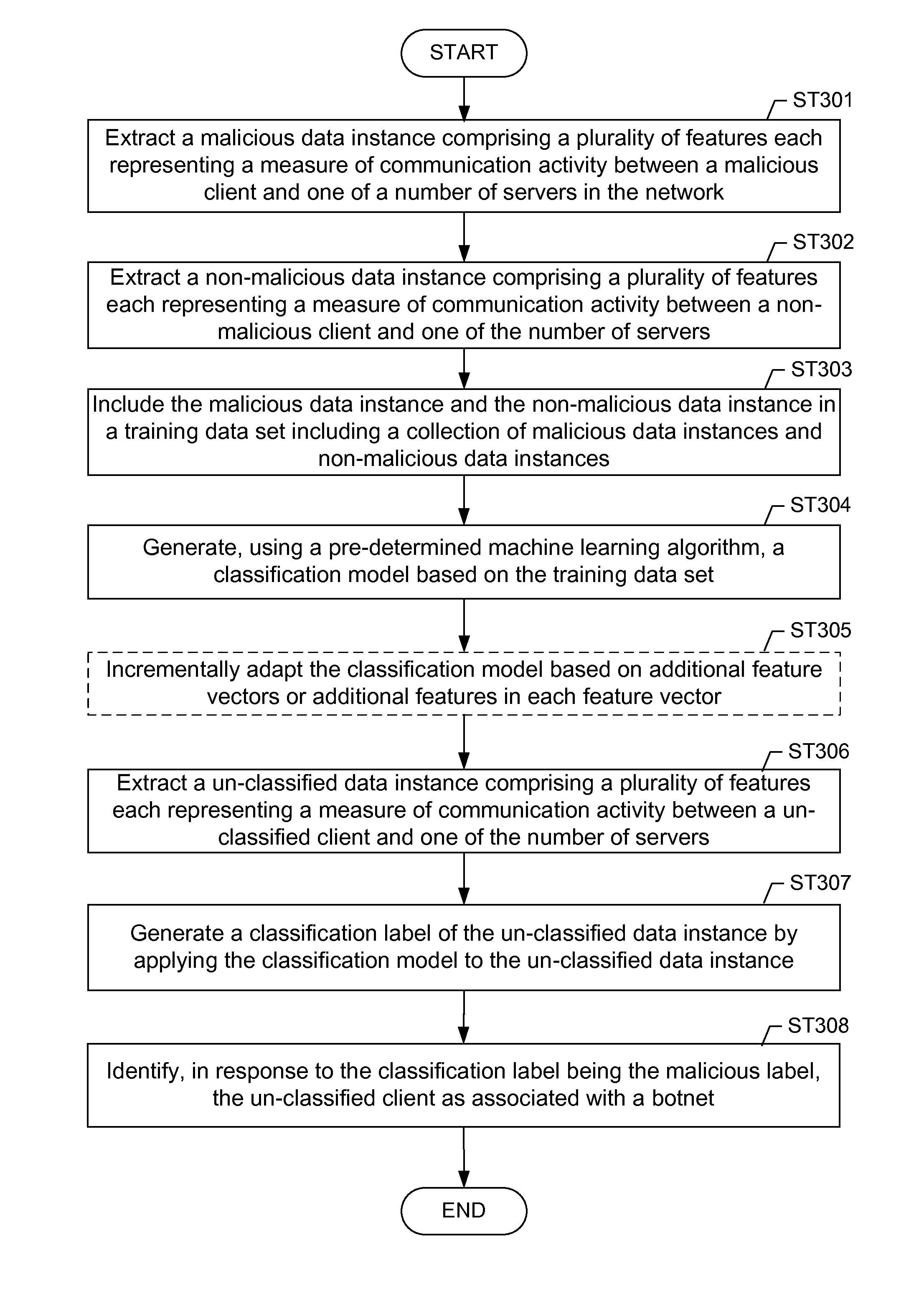
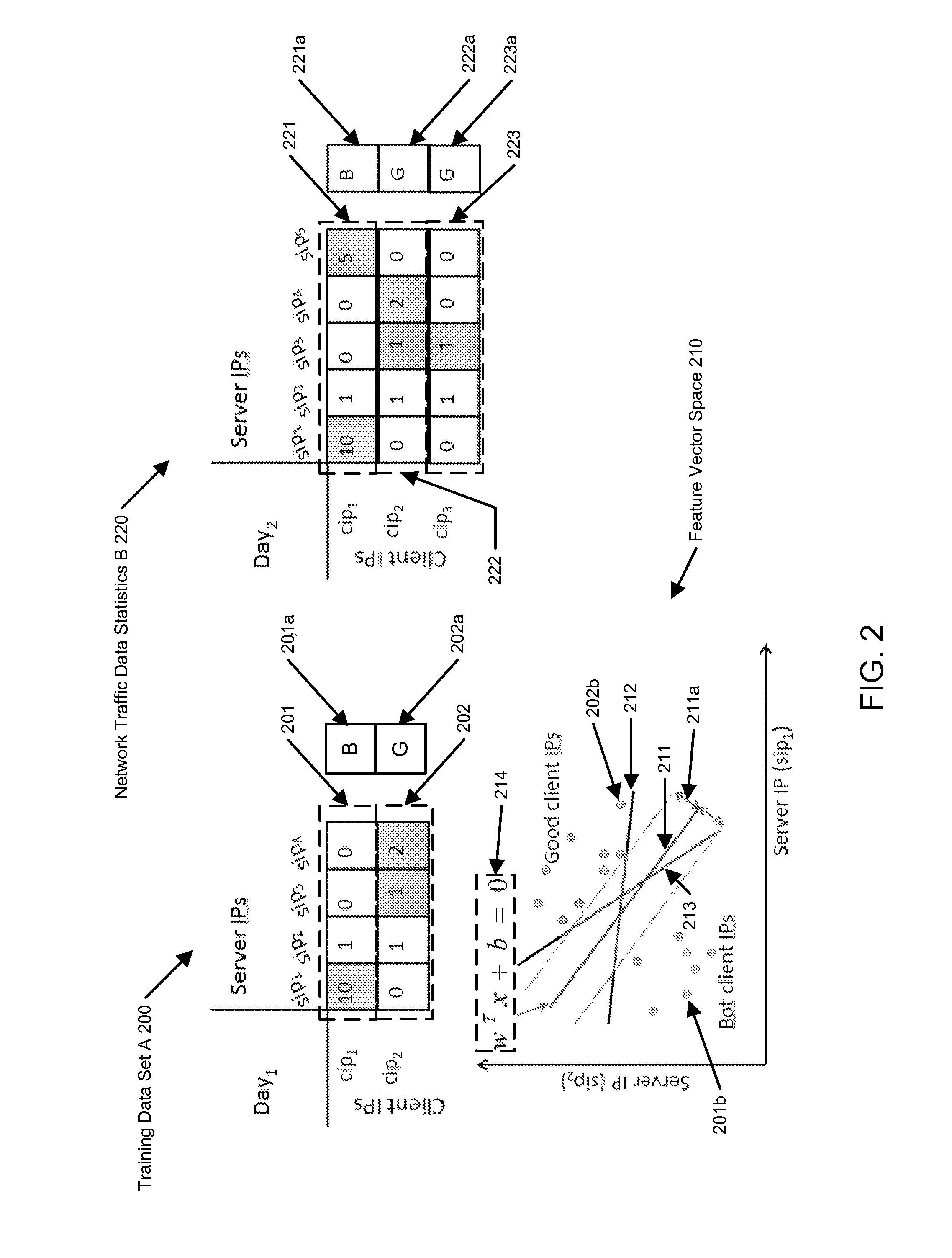
Machine learning based botnet detection with dynamic adaptation
Embodiments of the invention address the problem of detecting bots in network traffic based on a classification model learned during a training phase using machine learning algorithms based on features extracted from network data associated with either known malicious or known non-malicious client and applying the learned classification model to features extracted in real-time from current network data. The features represent communication activities between the known malicious or known non-malicious client and a number of servers in the network.
Owner:THE BOEING CO
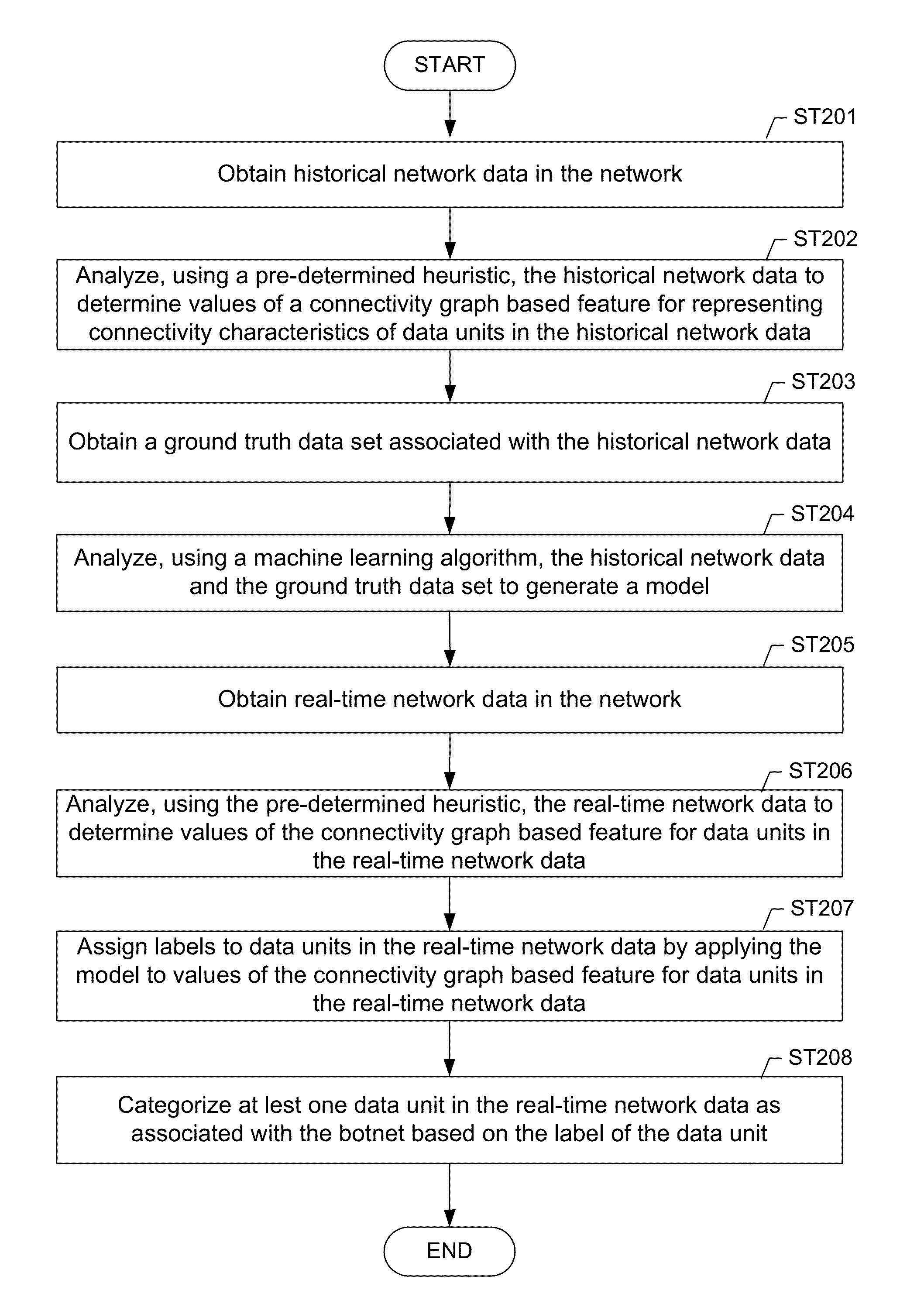
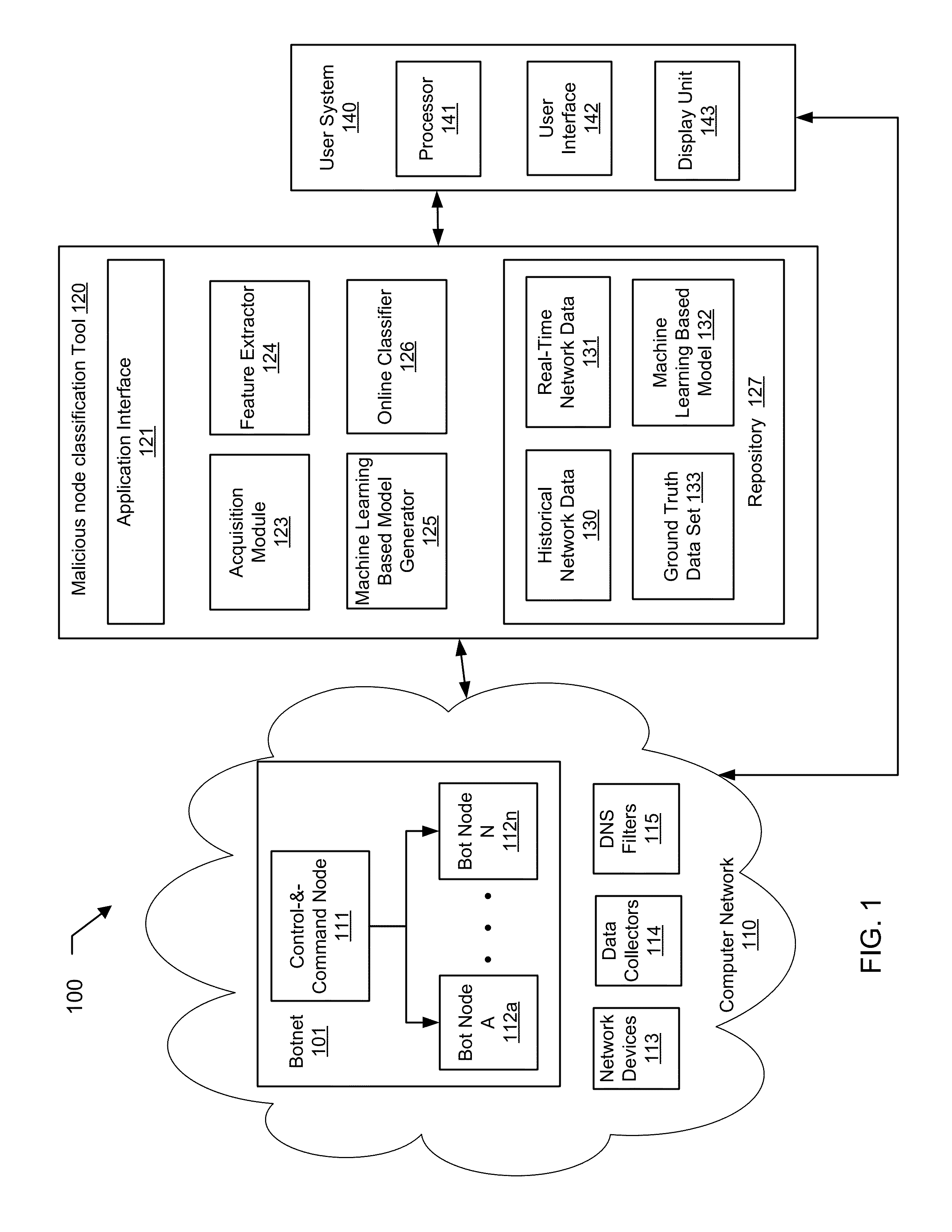
Machine learning based botnet detection using real-time connectivity graph based traffic features
A method for identifying a botnet in a network, including analyzing historical network data using a pre-determined heuristic to determine values of a connectivity graph based feature in the historical network data, obtaining a ground truth data set having labels assigned to data units in the historical network data identifying known malicious nodes in the network, analyzing the historical network data and the ground truth data set using a machine learning algorithm to generate a model representing the labels as a function of the values of the connectivity graph based feature, analyzing real-time network data using the pre-determined heuristic to determine a value of the connectivity graph based feature for a data unit in the real-time network data, assigning a label to the data unit by applying the model to the value of the connectivity graph based feature, and categorizing the data unit as associated with the botnet based on the label.
Owner:THE BOEING CO
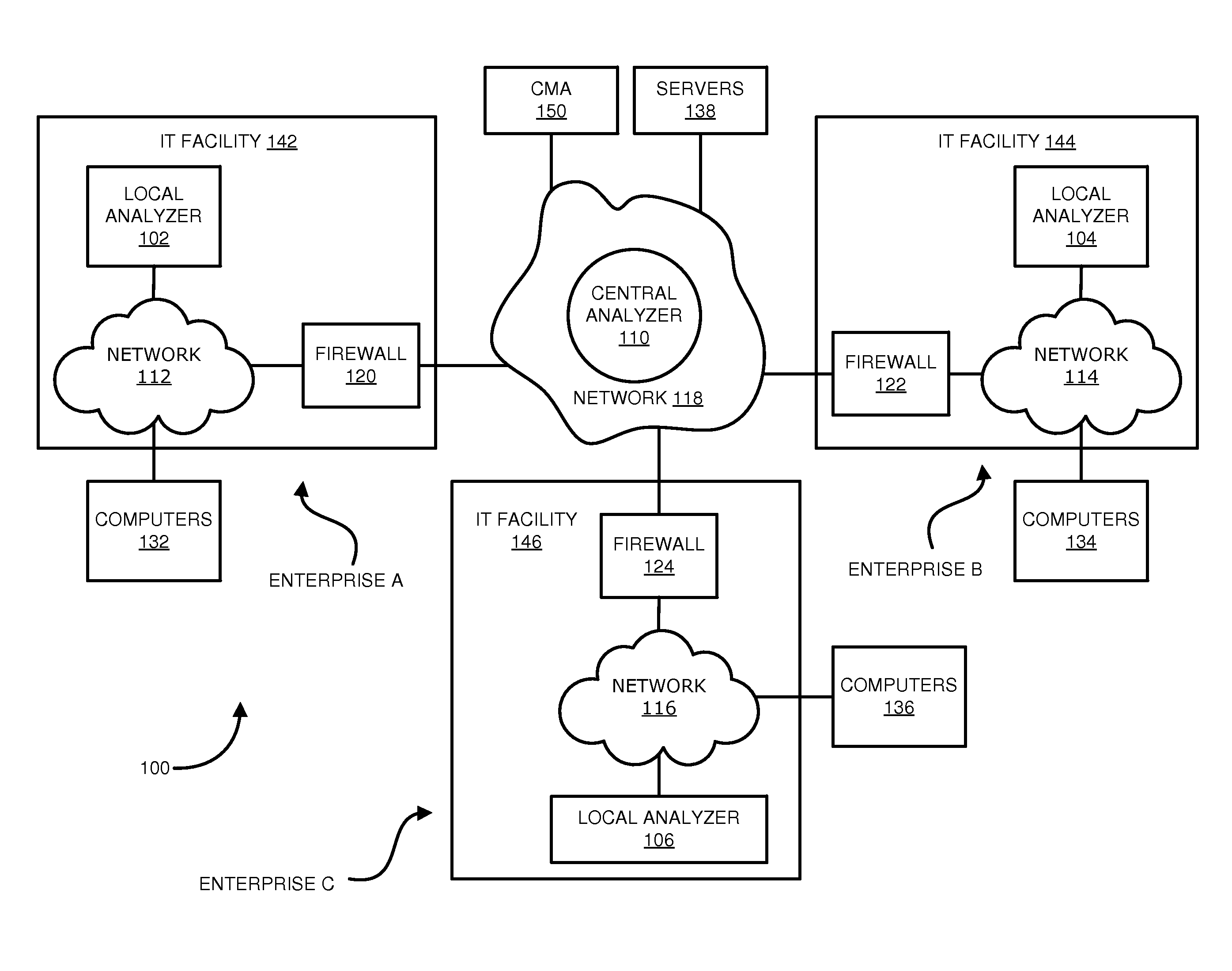
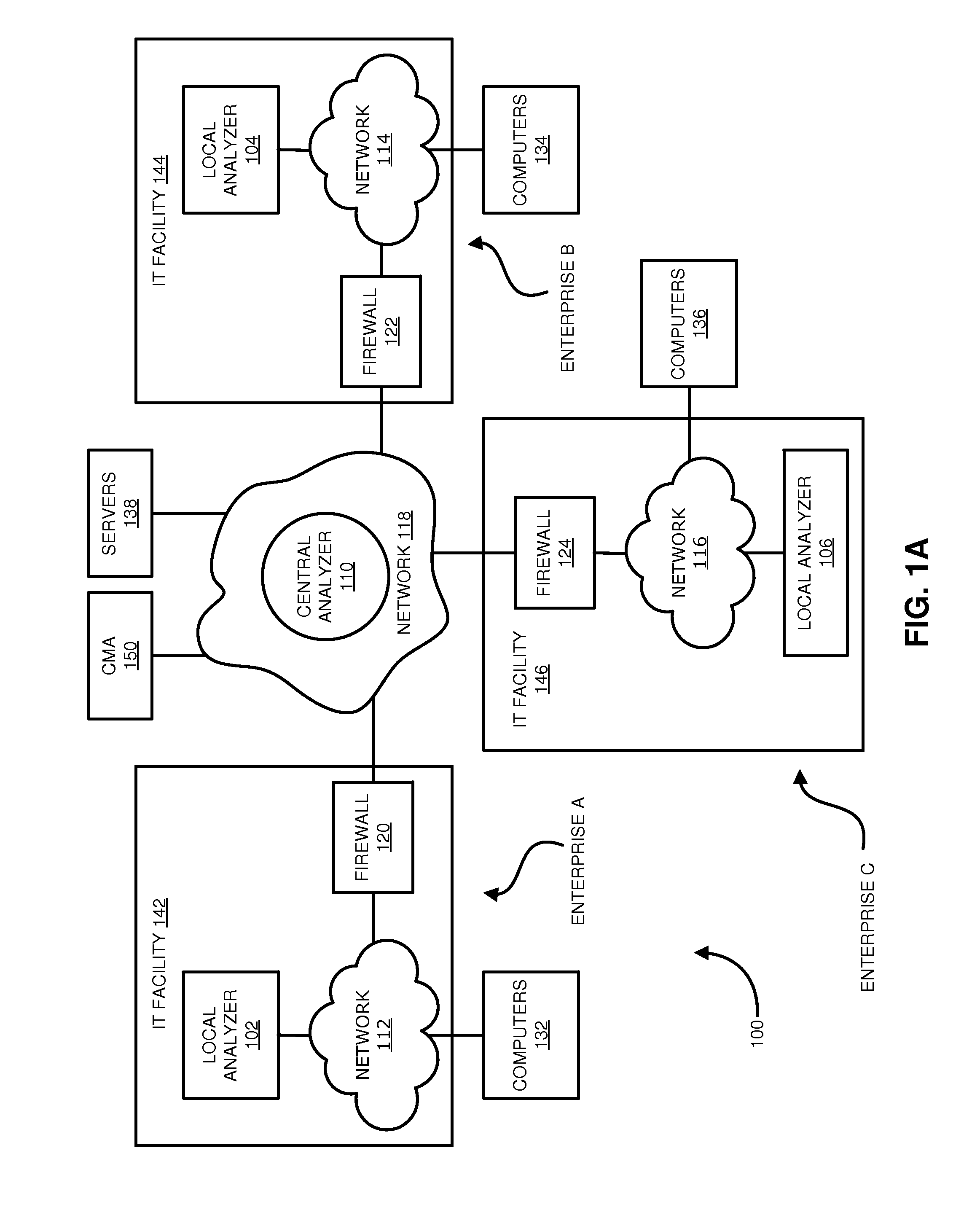
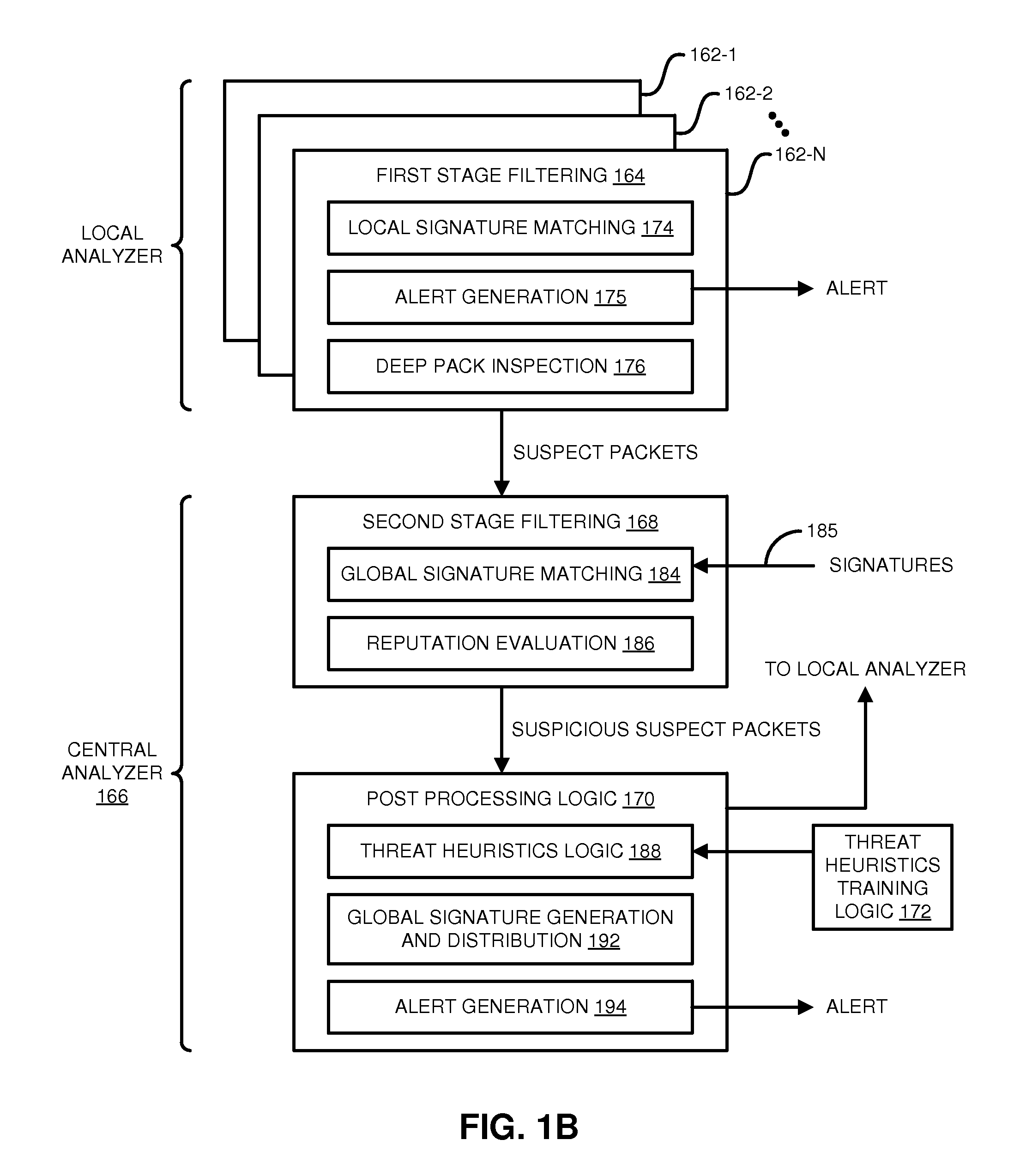
Distributed systems and methods for automatically detecting unknown bots and botnets
ActiveUS9430646B1Error detection/correctionPlatform integrity maintainanceOutbound communicationCommand and control
Techniques may automatically detect bots or botnets running in a computer or other digital device by detecting command and control communications, called “call-backs,” from malicious code that has previously gained entry into the digital device. Callbacks are detected using a distributed approach employing one or more local analyzers and a central analyzer. The local analyzers capture packets of outbound communications, generate header signatures, and analyze the captured packets using various techniques. The techniques may include packet header signature matching against verified callback signatures, deep packet inspection. The central analyzer receives the header signatures and related header information from the local analyzers, may perform further analysis (for example, on-line host reputation analysis); determines using a heuristics analysis whether the signatures correspond to callbacks; and generally coordinates among the local analyzers.
Owner:FIREEYE SECURITY HLDG US LLC
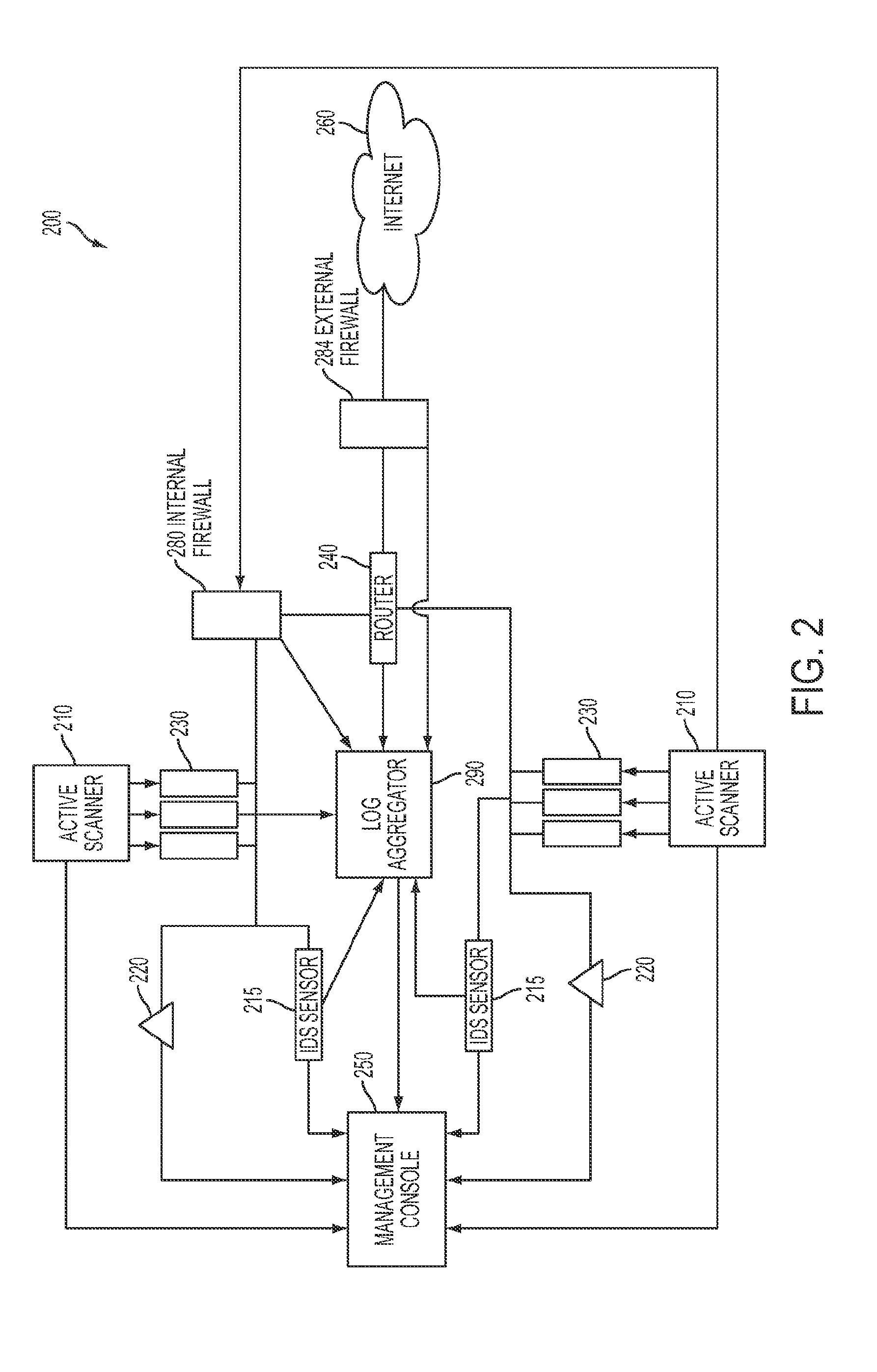
System and method for strategic Anti-malware monitoring
ActiveUS20140013434A1Mitigate and manage governanceMitigate and manage and riskMemory loss protectionError detection/correctionAnti virusFile system
The system and method described herein may leverage active network scanning and passive network monitoring to provide strategic anti-malware monitoring in a network. In particular, the system and method described herein may remotely connect to managed hosts in a network to compute hashes or other signatures associated with processes running thereon and suspicious files hosted thereon, wherein the hashes may communicated to a cloud database that aggregates all known virus or malware signatures that various anti-virus vendors have catalogued to detect malware infections without requiring the hosts to have a local or resident anti-virus agent. Furthermore, running processes and file system activity may be monitored in the network to further detect malware infections. Additionally, the network scanning and network monitoring may be used to detect hosts that may potentially be participating in an active botnet or hosting botnet content and audit anti-virus strategies deployed in the network.
Owner:TENABLE INC
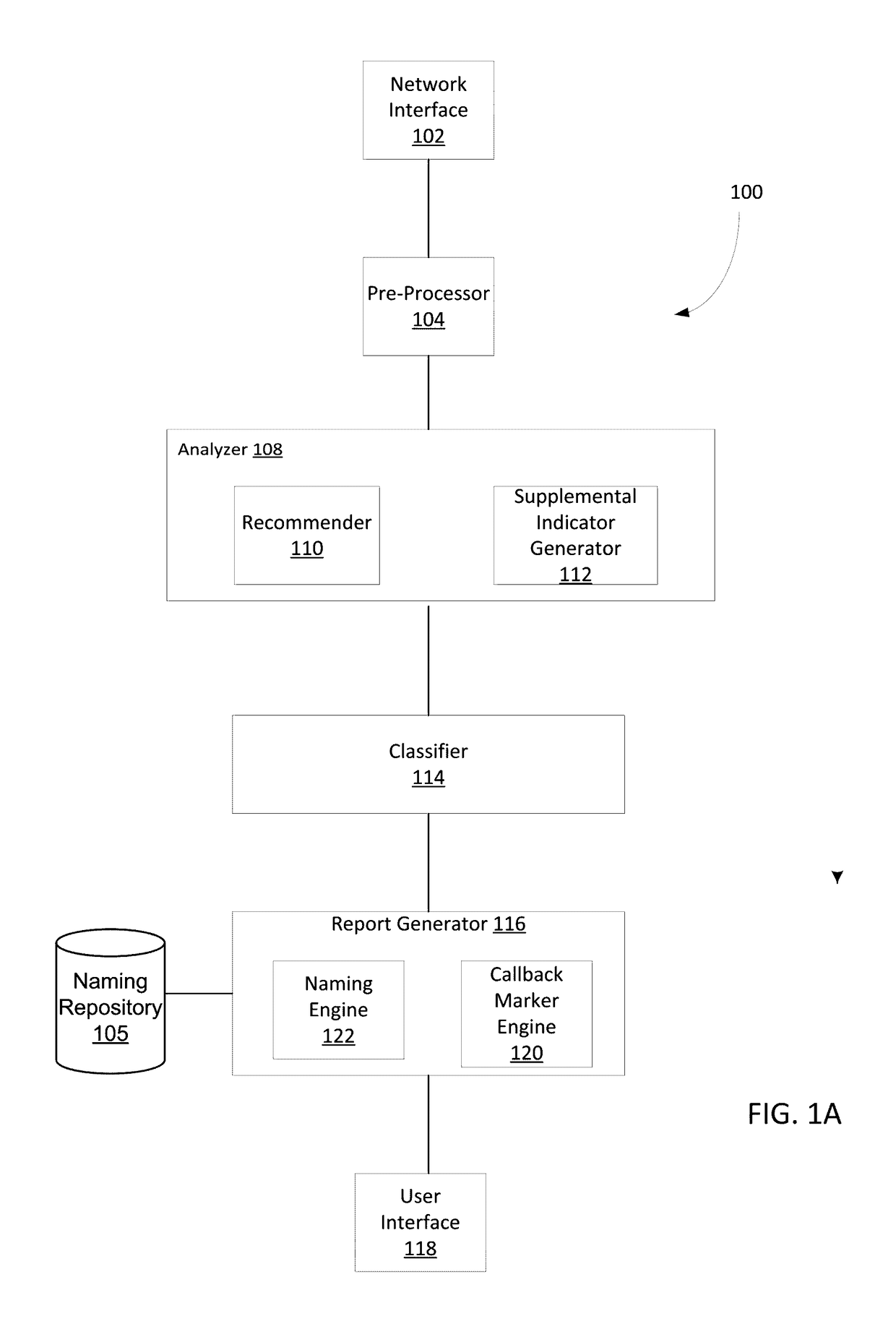
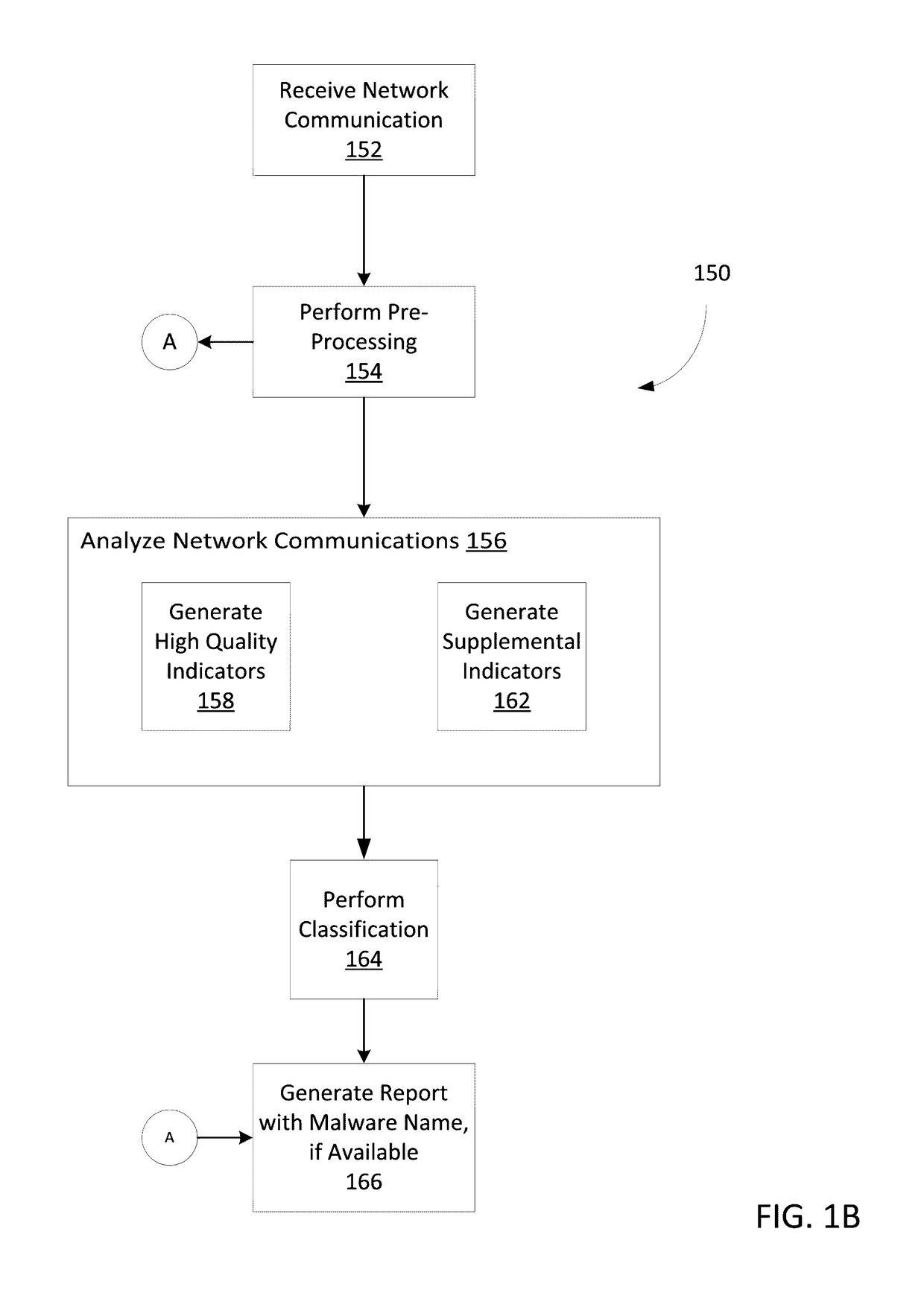
Classifying sets of malicious indicators for detecting command and control communications associated with malware
ActiveUS9635039B1Platform integrity maintainanceTransmissionOutbound communicationCommand and control
Techniques may automatically detect bots or botnets running in a computer or other digital device by detecting command and control communications, called “call-backs,” from malicious code that has previously gained entry into the digital device. Callbacks are detected using an approach employing both a set of high quality indicators and a set of supplemental indicators. The high quality indicators are selected since they provide a strong correlation with callbacks, and may be sufficient for the techniques to determine that the network outbound communications actually constitute callbacks. If not, the supplemental indicators may be used in conjunction with the high quality indicators to declare the outbound communications as callbacks.
Owner:FIREEYE SECURITY HLDG US LLC
System and method for modeling activity patterns of network traffic to detect botnets
InactiveUS20110153811A1Efficient detectionDigital computer detailsTransmissionNetwork activityActivity classification
The invention relates to a system and method that can detect botnets by classifying the communication activities for each client according to destination or based on similarity between the groups of collected traffic. According to certain aspects of the invention, the communication activities for each client can be classified to model network activity by differentiating the protocols of the collected network traffic based on destination and patterning the subgroups for the respective protocols. Those servers that are estimated to be C&C servers can be classified into download and upload, spam servers and command control servers, within a botnet group detected by modeling network activity, i.e. analyzing network-based activity patterns. Also, botnet groups can be detected by way of a group information management function, for generating an activity pattern-based group matrix based on group data, and a mutual similarity analysis, performed on groups suspected to be botnets from the group information.
Owner:KOREA INTERNET & SECURITY AGENCY
Distributed systems and methods for automatically detecting unknown bots and botnets
A system and method for detecting malicious activity through one or more local analyzers and a central analyzer. The local analyzer captures packets that are part of communications over a network, generates a signature from information obtained from one or more of the captured packets, and determines whether the signature matches any signature of a first plurality of signatures stored in a first storage device that is accessible to the first local analyzer. The central analyzer remotely receives a portion of the information and the signature from the first local analyzer in response to the signature failing to match any of the signatures stored in the first storage device. The central analyzer determines whether the signature matches any global signature stored within a second storage device that is accessible to the central analyzer.
Owner:FIREEYE SECURITY HLDG US LLC +1
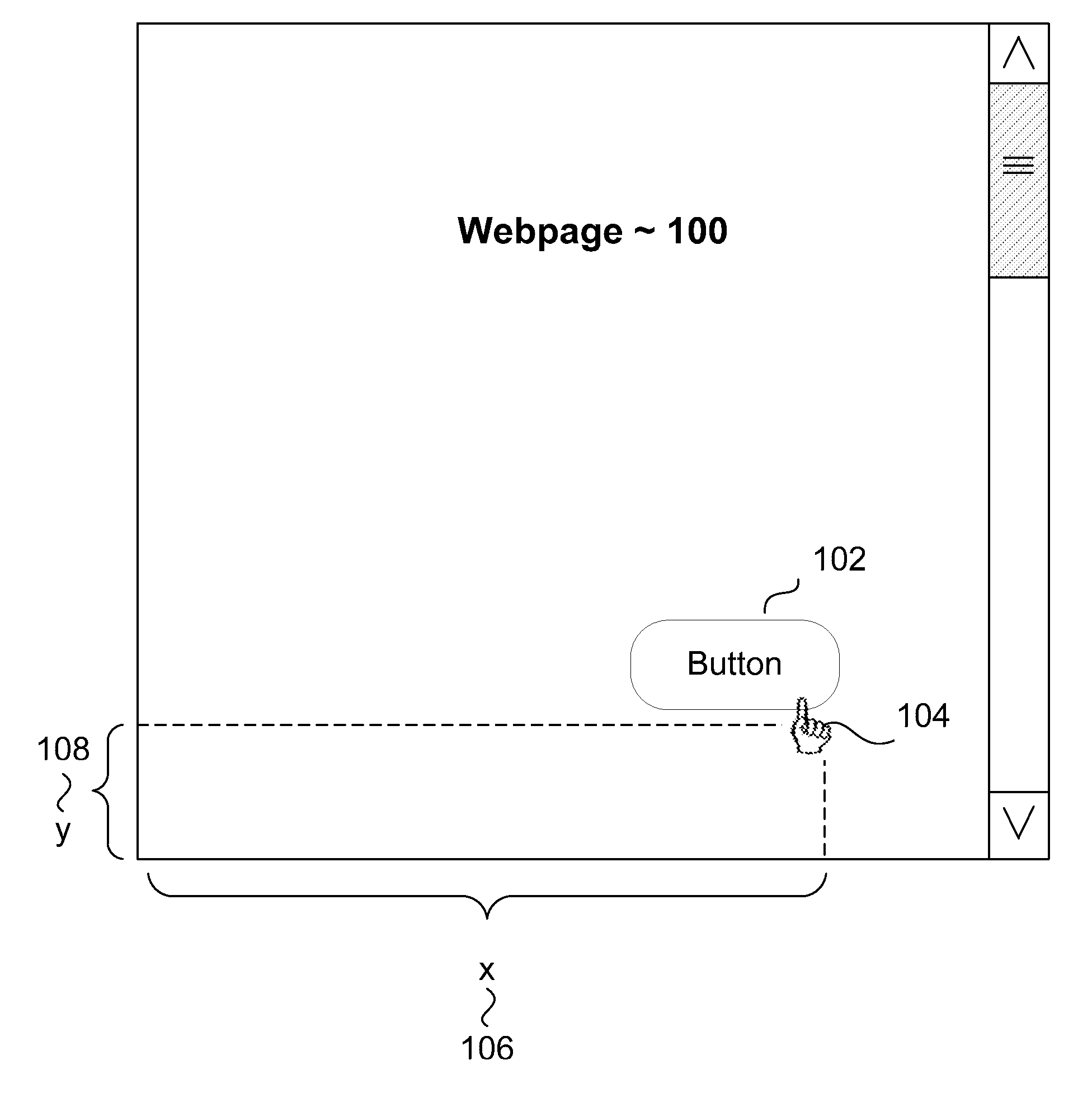
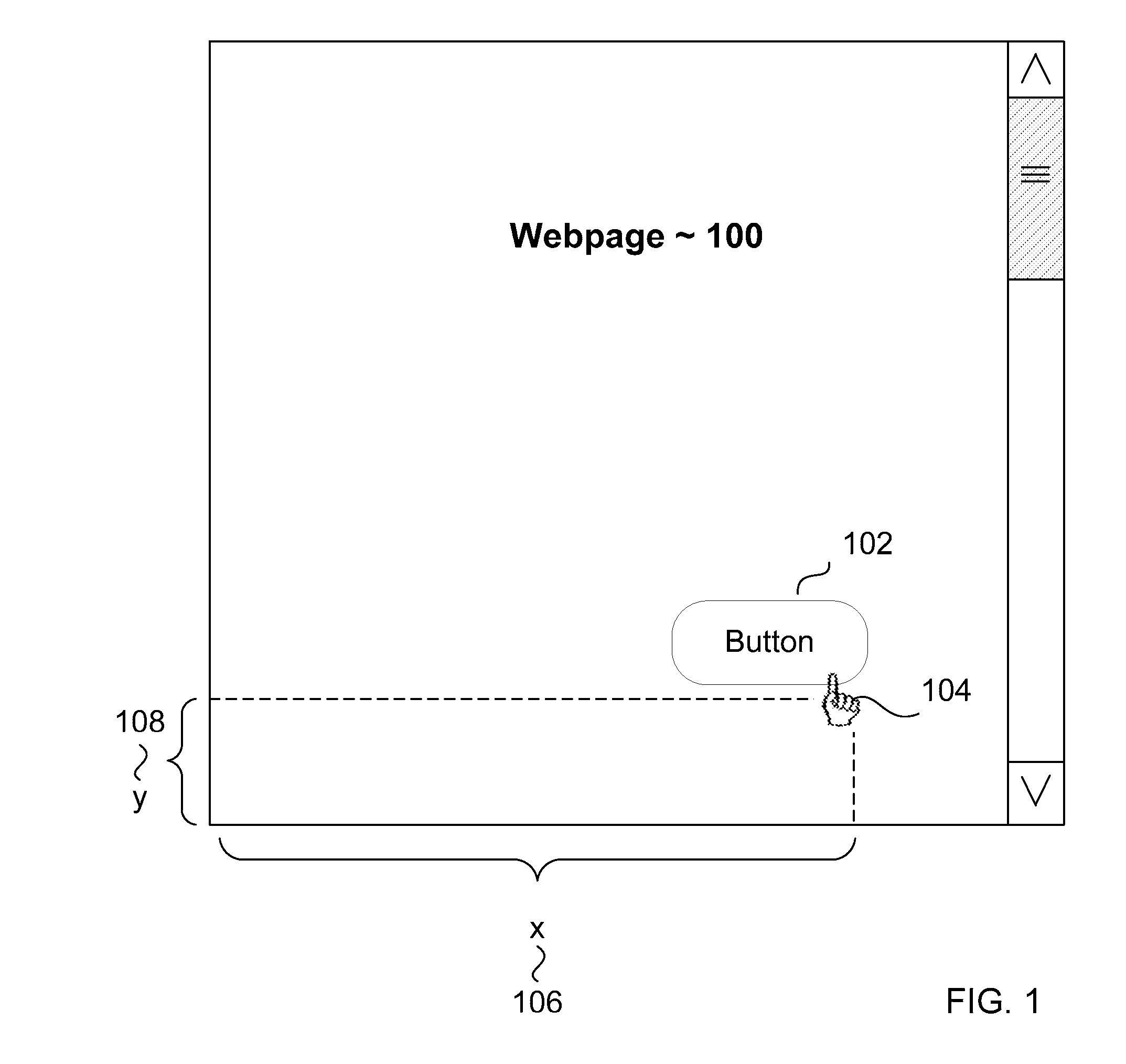
Systems and methods for security management based on cursor events
ActiveUS20110113388A1Digital data authenticationInput/output processes for data processingSafety management systemsData mining
Systems and methods for security management based on cursor events. Click coordinates on a webpage of user's activity are logged in order to detect multiple or repeated transactions that bare the same exact coordinates. Such multiple or repeated activity may be helpful in detecting scripted attacks or bot net activity in a variety of environments and transactions. Further, the invention may also capture the coordinates of the location of submit buttons, and similar buttons, on a webpage to analyze whether a click action or other pointer action occurred within the button's parameters.
Owner:THE 41ST PARAMETER
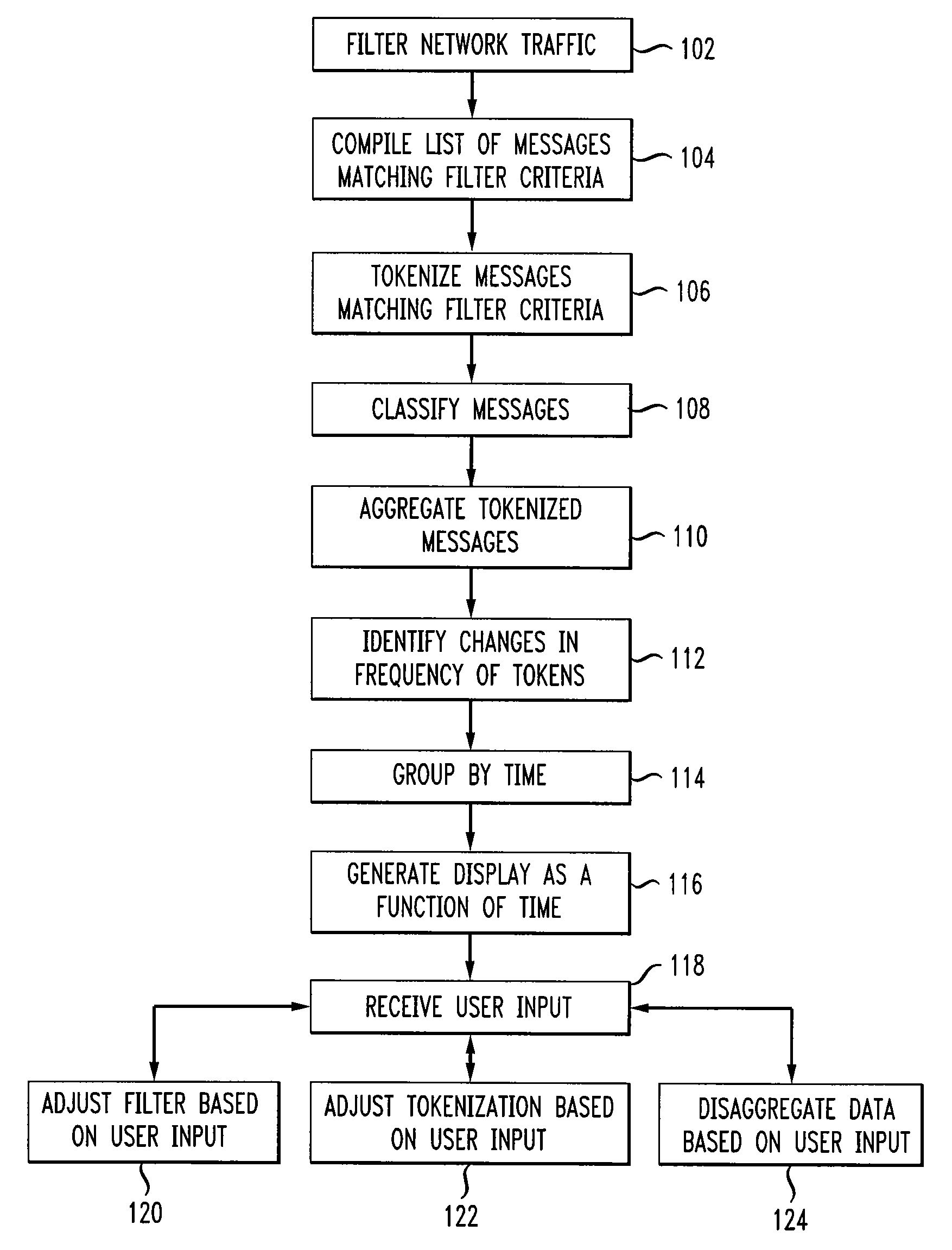
Method and Apparatus for Botnet Analysis and Visualization
A method and apparatus for botnet analysis and visualization. Network traffic is filtered to compile a list of messages. The identified messages are tokenized, classified, and aggregated and changes in the frequency of tokenized messages are identified. A display of the tokenized messages is generated and displayed via a user interface. The user interface is configured to a allow a user to review data generated based on the filtered network traffic in order to detect potential botnet activity. User input may be used to adjust filtering and tokenization of the messages.
Owner:AT&T INTPROP I L P
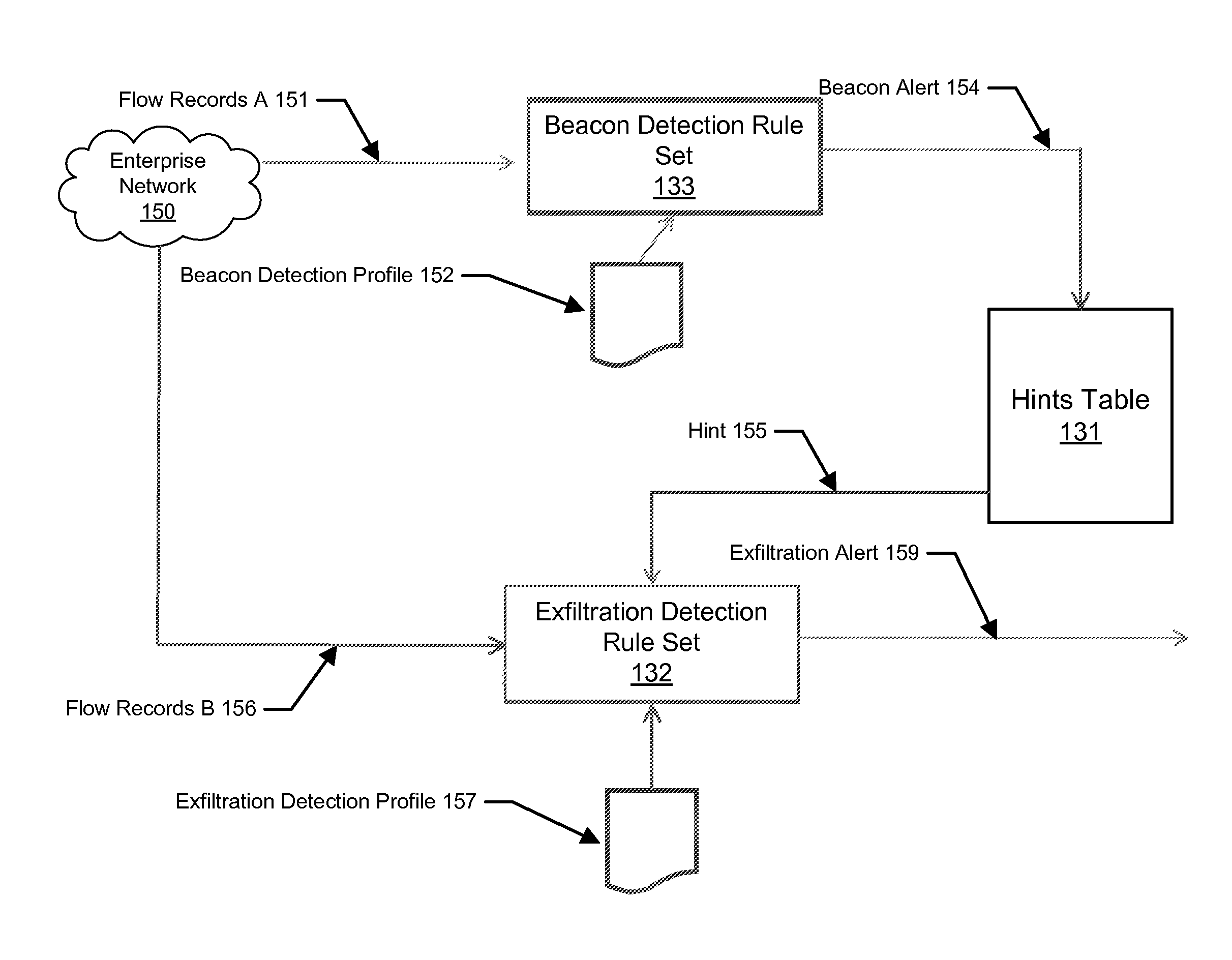
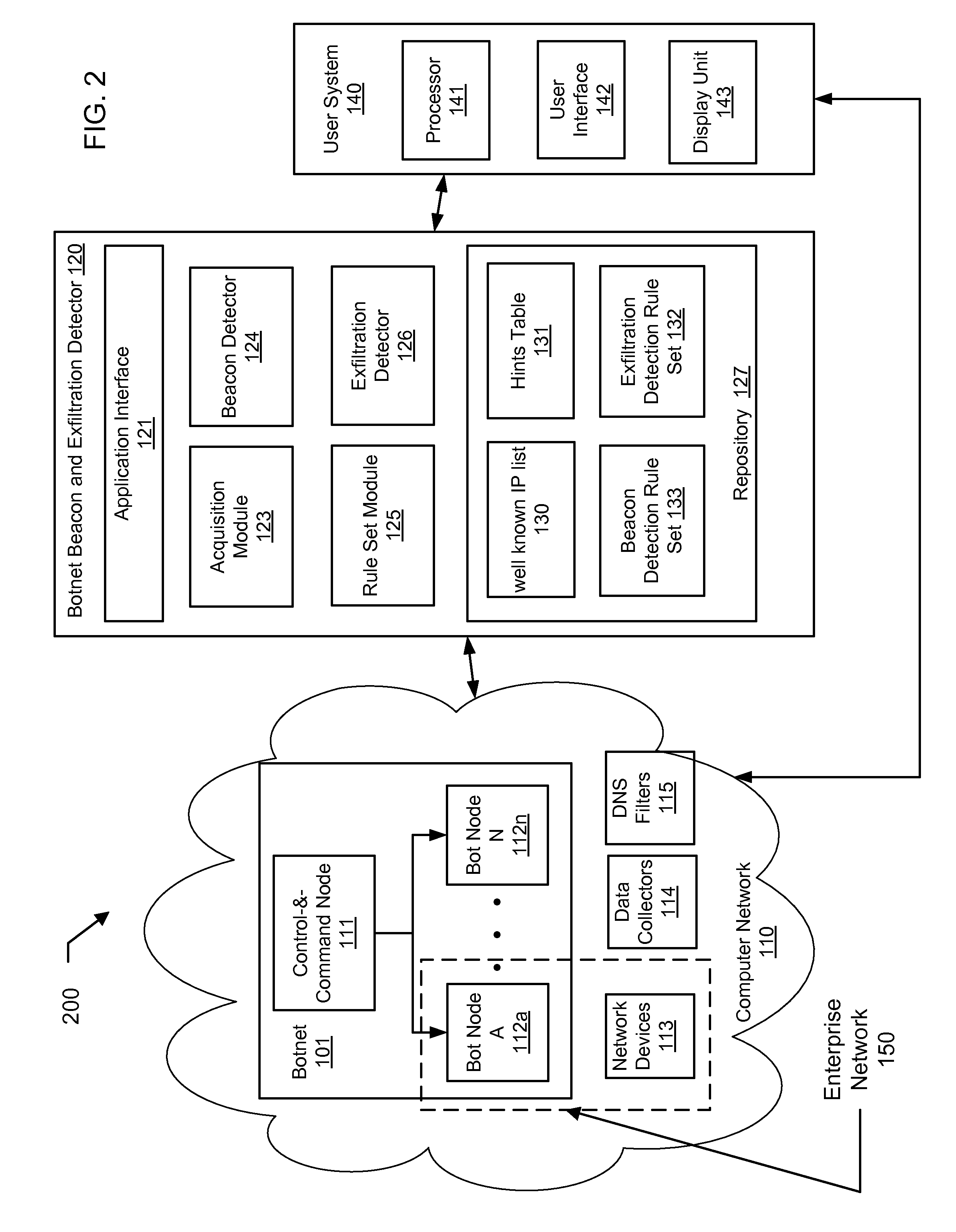
Botnet beacon detection
A method and system to detect botnet beaconing event based on a beacon detection rule set to generate a beacon alert, which is in turn used to trigger an elevated exfiltration detection activity by reducing various thresholds in an exfiltration detection rule set.
Owner:THE BOEING CO
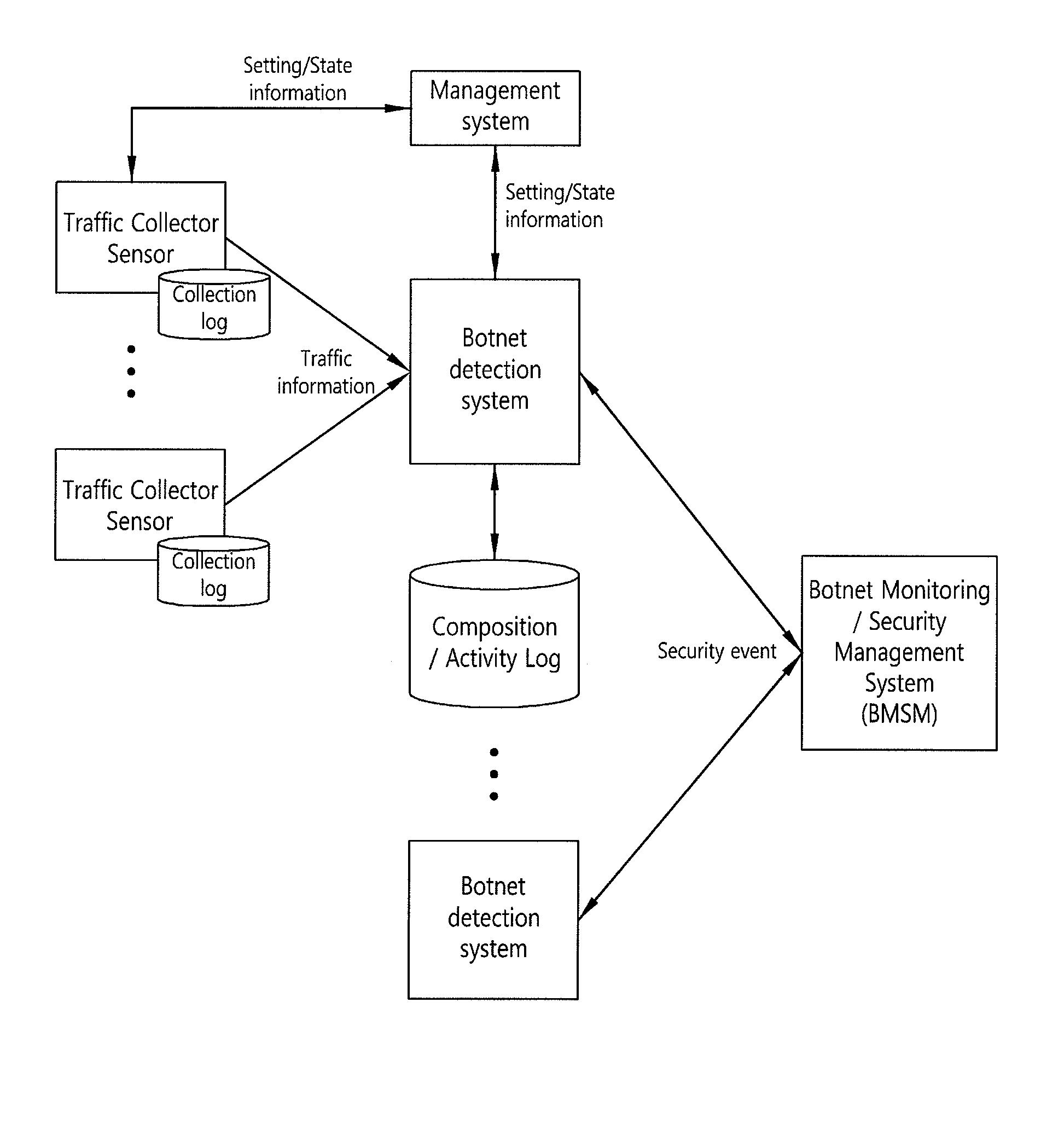
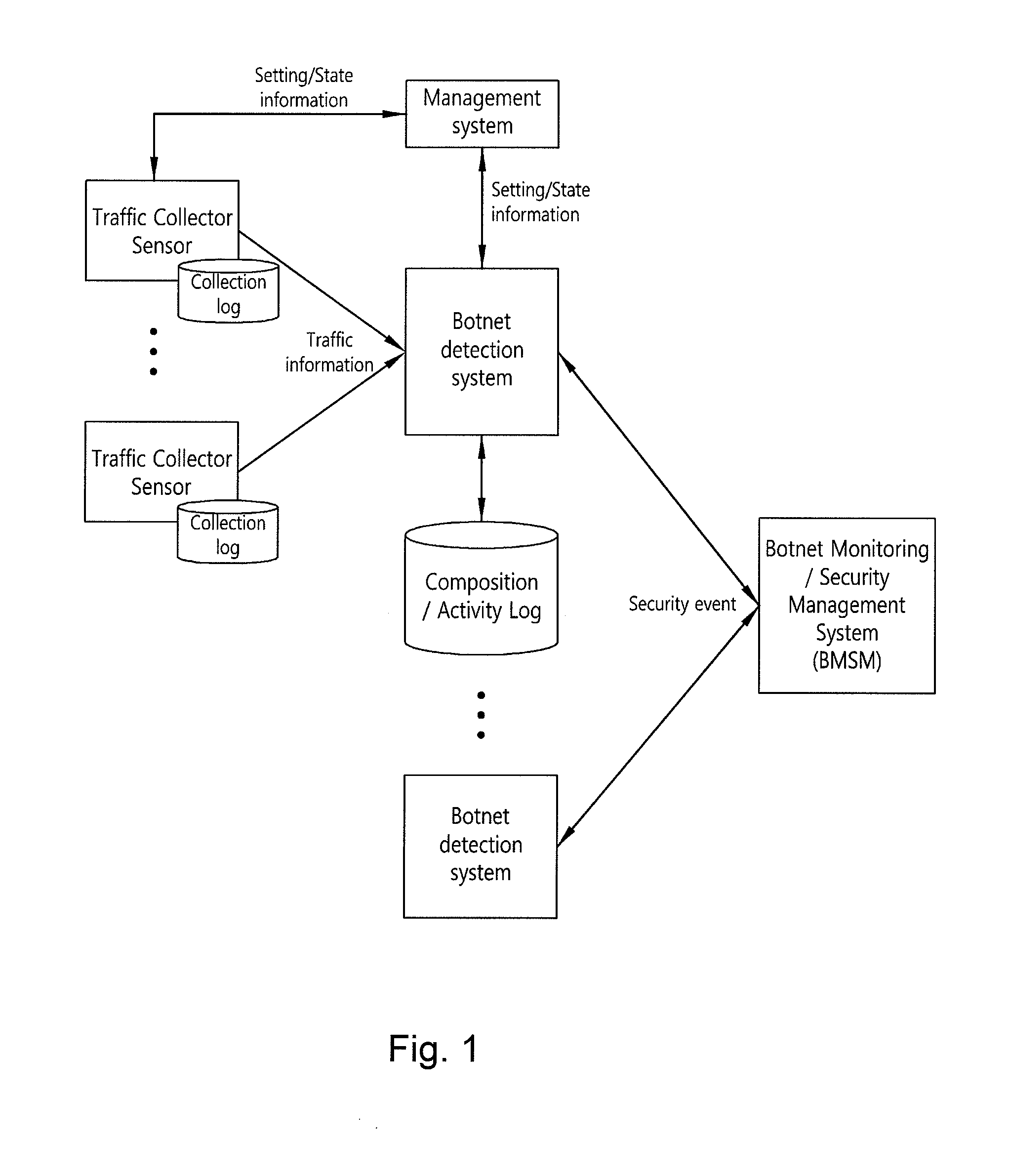
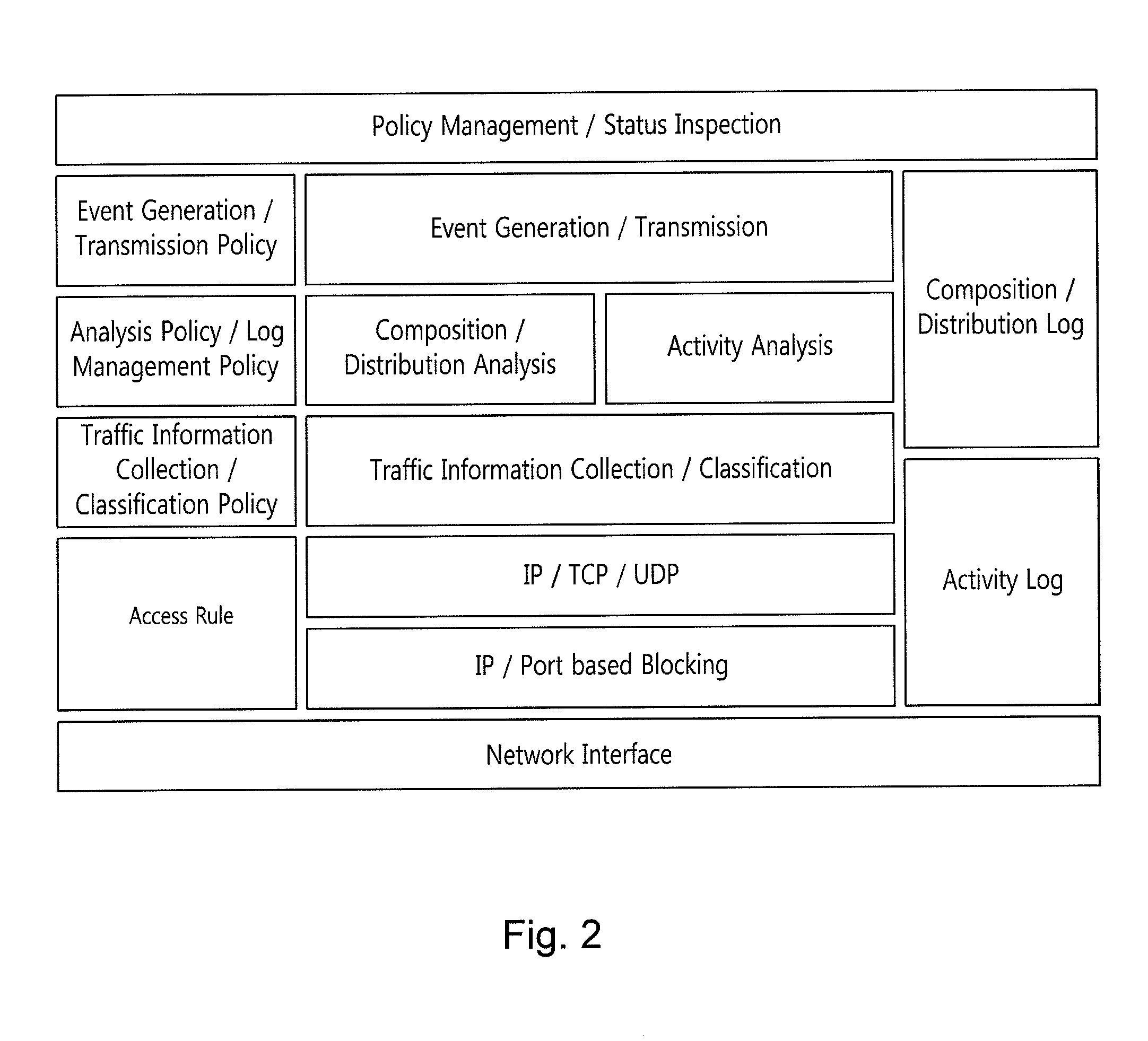
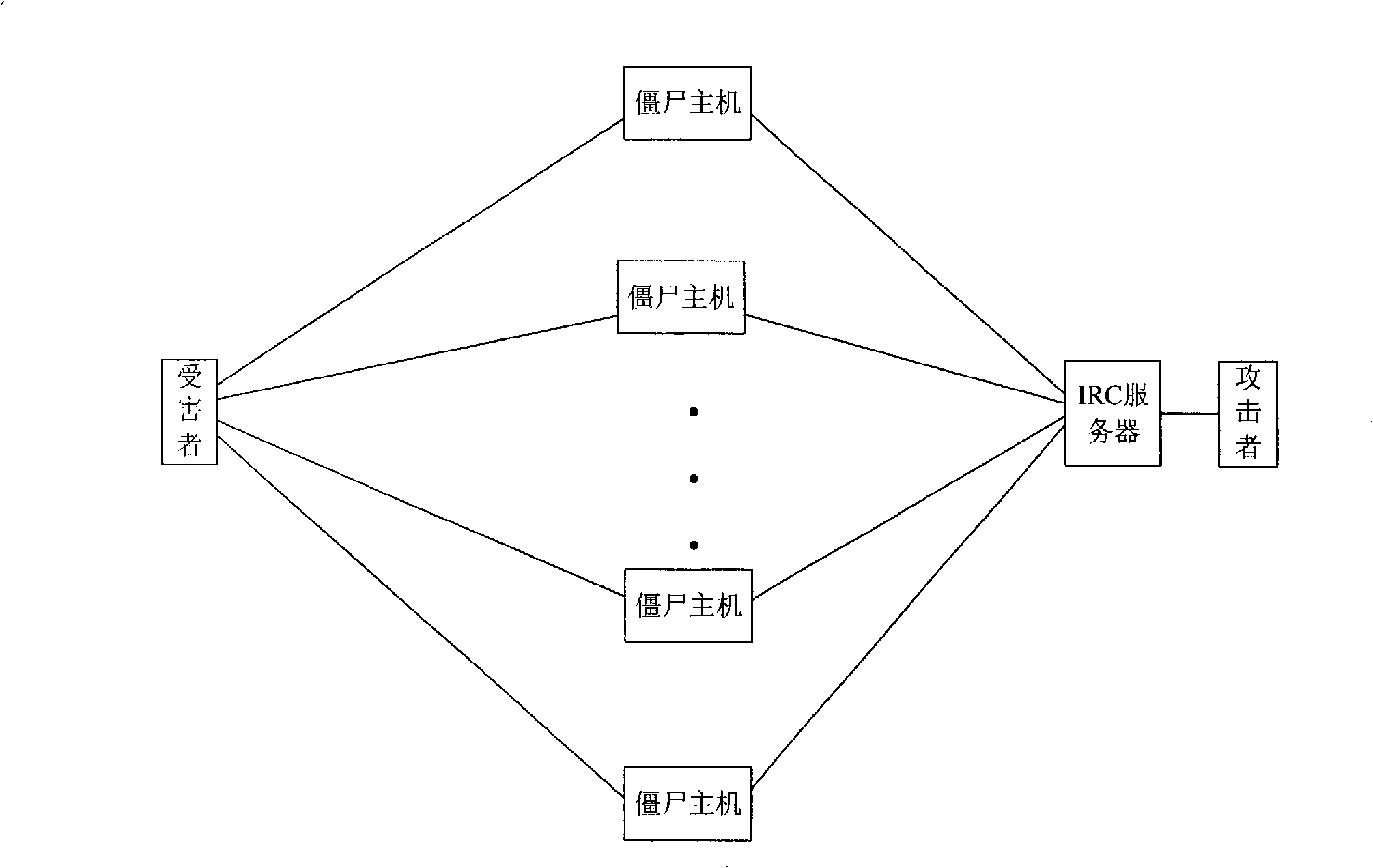
Security system of managing irc and HTTP botnets, and method therefor
InactiveUS20100162350A1Efficient Safety ManagementData taking preventionSpecial data processing applicationsService provisionBotnet
The present invention relates to a security system of managing IRC and HTTP botnets and a method therefor. More specifically, the present invention relates to a system and a method that detects a botnet in an Internet service provider network to store information related to the detected botnet in a database and performs security management of IRC and HTTP botnets, including a botnet management security management (BMSM) system, configured to visualize the information related to the detected botnet and establish an against policy related to the detected botnet. Accordingly, the present invention provides a security system of managing IRC and HTTP botnets that can efficiently performs the security management of IRC and HTTP botnets by using the BMSM system
Owner:KOREA INTERNET & SECURITY AGENCY
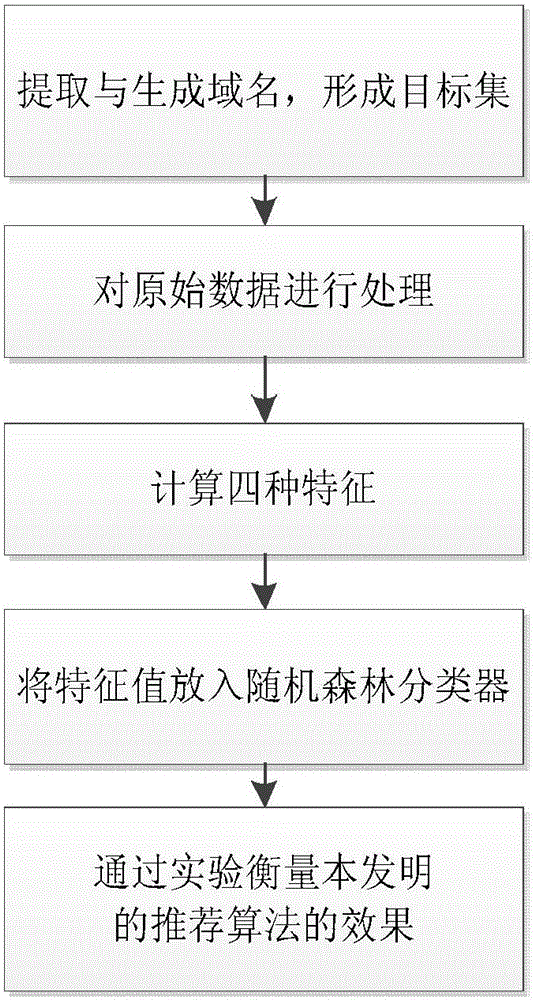
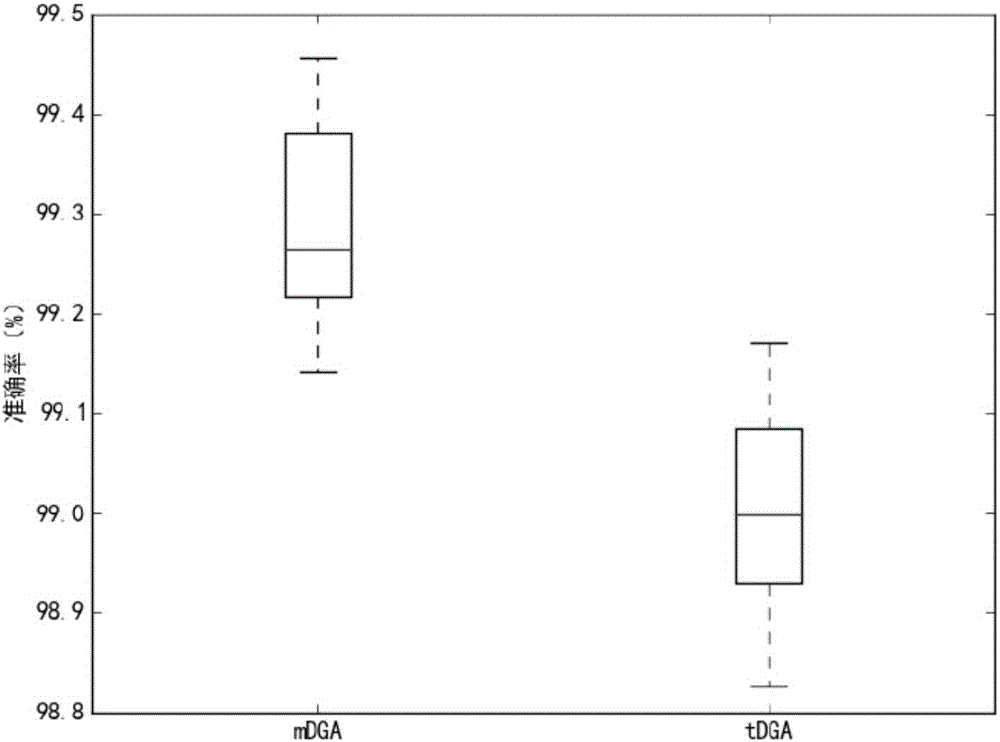
Botnet detection method based on DNS (Domain Name System) flow characteristics
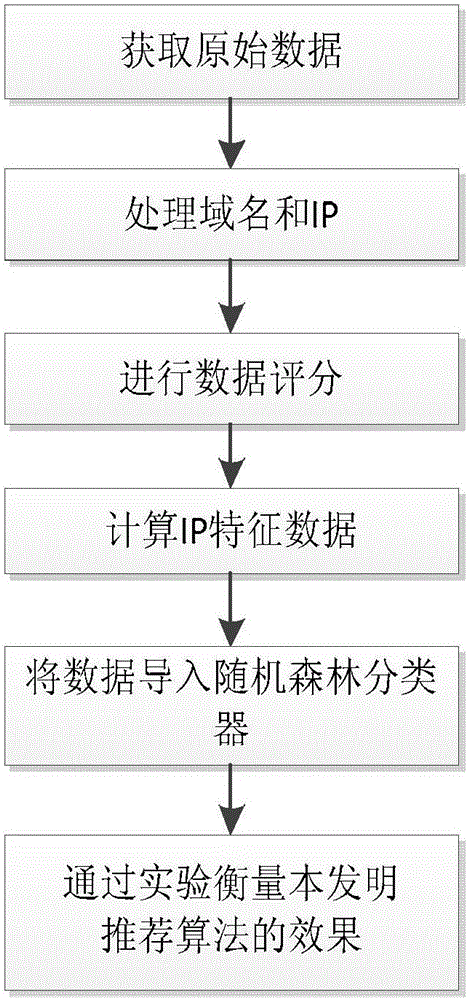
The invention discloses a botnet detection method based on DNS (Domain Name System) flow characteristics. The method of the invention comprises a Domain-Flux botnet detection method based on DNS flow characteristics. The method comprises steps: legal main domain names and illegal main domain names are combined to form a target set; a domain name whose length is larger than 6 is extracted and processed as a research target; the domain name entropy, word formation characteristics, phonetic characteristics and grouped characteristics are calculated respectively; and the above is put in a random forest classifier to obtain a training model. A Fast-Flux botnet detection method based on the Domain-Flux botnet detection method comprises steps: the original data of a DNS server are processed; the training model obtained before is used for evaluating a to-be-processed domain name, and a score for a DGA condition is acquired; a white list, a black list and a grey list are used for scoring the domain name and an IP; time characteristics of the IP address are calculated; the stability of the IP address is calculated; and the above is put in the random forest classifier to obtain a training model SFF. The experiment accuracy is high.
Owner:宁波知微瑞驰信息科技有限公司
Method to perform botnet detection
A method and a system for monitoring network activities associated with a computer connected to a network are provided. The method may include detecting a bot activity associated with the computer; attributing a bot status to the computer, based on a bot activity type associated with the bot activity, prior detections of bot activities, and considering time stamps. The method may also include updating the bot status attributed to the computer, based upon detection of subsequent bot activities associated with the computer, the bot activity types associated with the subsequent bot activities, and one or more other criteria. In one example embodiment, the network activities may include network transmissions and behavioral patterns. According to example embodiments, the system may include a network monitor, a bot activity detection module, a bot status module, and a bot status update module.
Owner:SYMANTEC CORP
Detection method, system and apparatus of zombie network
ActiveCN101360019AAvoid harmResolve detectionData switching networksCommunications securityAnalysis center
Embodiments of the invention disclose a method, a system and a device for detecting botnet, belonging to the network communication security field. The method comprises: receiving a communication message of the network under test; picking up a botnet information message of the communication message according to the communication message; picking up a bot host IP and a controller IP according to the botnet information message; and inquiring about account numbers corresponding to the bot host IP and the controller IP according to the picked bot host IP and the controller IP. The system comprises: a network probe, a monitoring and analysis center and an authentication server. The device includes a monitoring and analysis center. The botnet detection method can detect the botnet in real time, and can also respond to the botnet in real time, thereby solving the problem that the prior art based on the ex post analysis can not detect and respond to the botnet in real time, avoiding the harm of botnet, and making the network communications more secure.
Owner:CHENGDU HUAWEI TECH
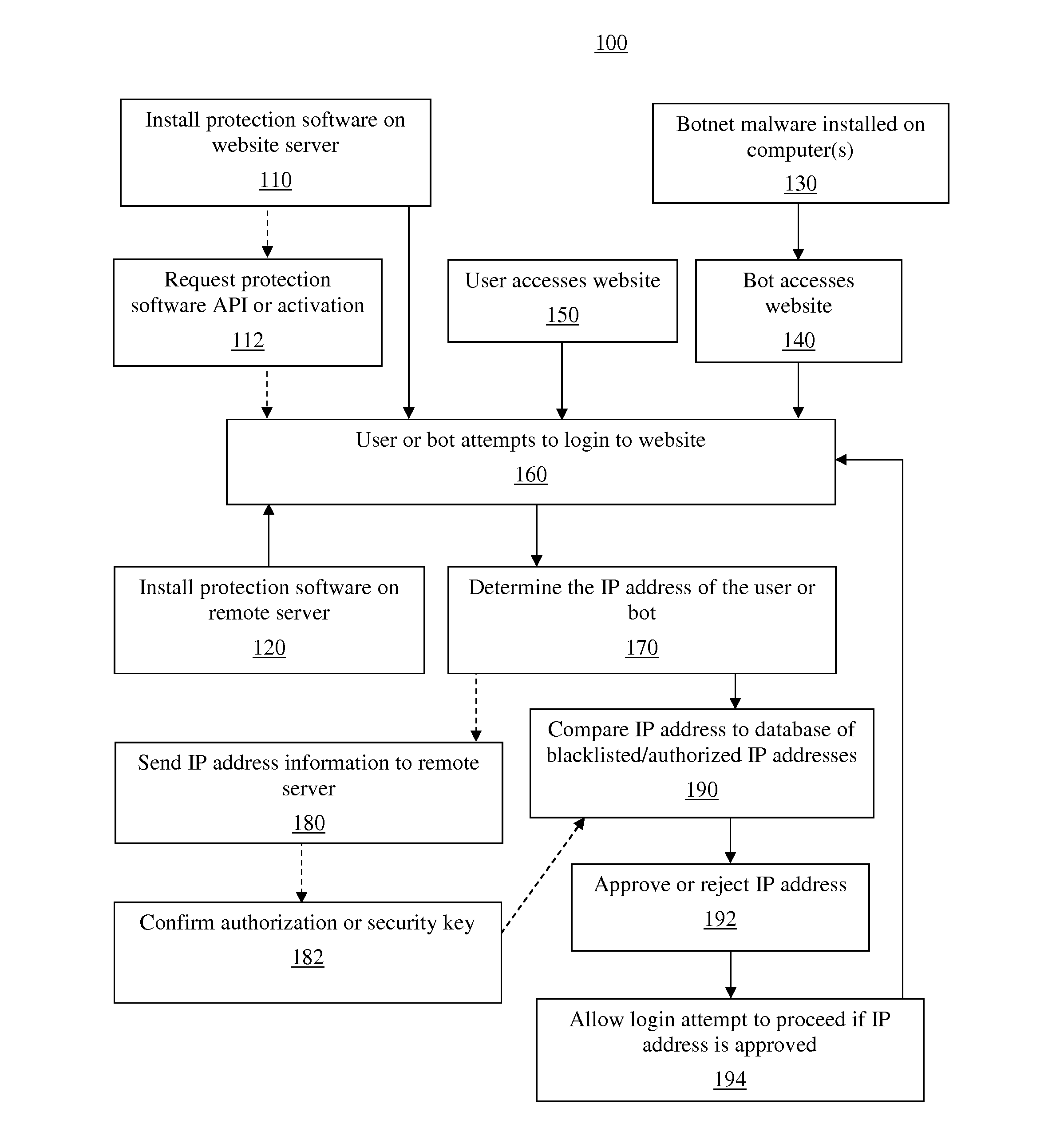
Systems And Methods For Protecting Websites From Botnet Attacks
InactiveUS20150288715A1Readily apparentDigital data processing detailsMultiple digital computer combinationsIp addressBlack list
A computer-implemented method for preventing an unauthorized login attempt includes the steps of: (i) receiving, at a central server in communication with a plurality of servers in a distributed computing network, a first communication comprising a security key and an IP address associated with an entity attempting to login to a website hosted by a server; (ii) comparing, by the central server, the received security key to a stored list of security keys; (iii) authenticating the first communication if the received security key matches one of the stored security keys; (iv) comparing, by the central server, the received IP address to blacklisted IP addresses; (v) determining whether the received IP address is one of the blacklisted IP addresses; and (vi) providing, to the server, an indication of whether the IP address is one of the blacklisted IP addresses.
Owner:AUTOMATTIC
Method and apparatus for security-risk based admission control
A method and apparatus is disclosed herein for security risk-based admission control. In one embodiment, the method comprises: receiving a request from the user device to access the network; determining whether to admit the user device based on a security-based admission control policy that admits user devices based on a constraint optimization that attempts to maximize the sum utility of the currently admitted user devices in view of a security assessment of the user device and security risk imposed on the network and already admitted user devices if the user device is admitted to the network, wherein the constraint optimization is based on a utility associated with admitting the user device to the network, a reputation value associated with the user device, and a botnet damage estimation on the network associated with the user device; and admitting the user device to the network based on results of determining whether to admit the user device.
Owner:NTT DOCOMO INC
Method and system for detecting bot network
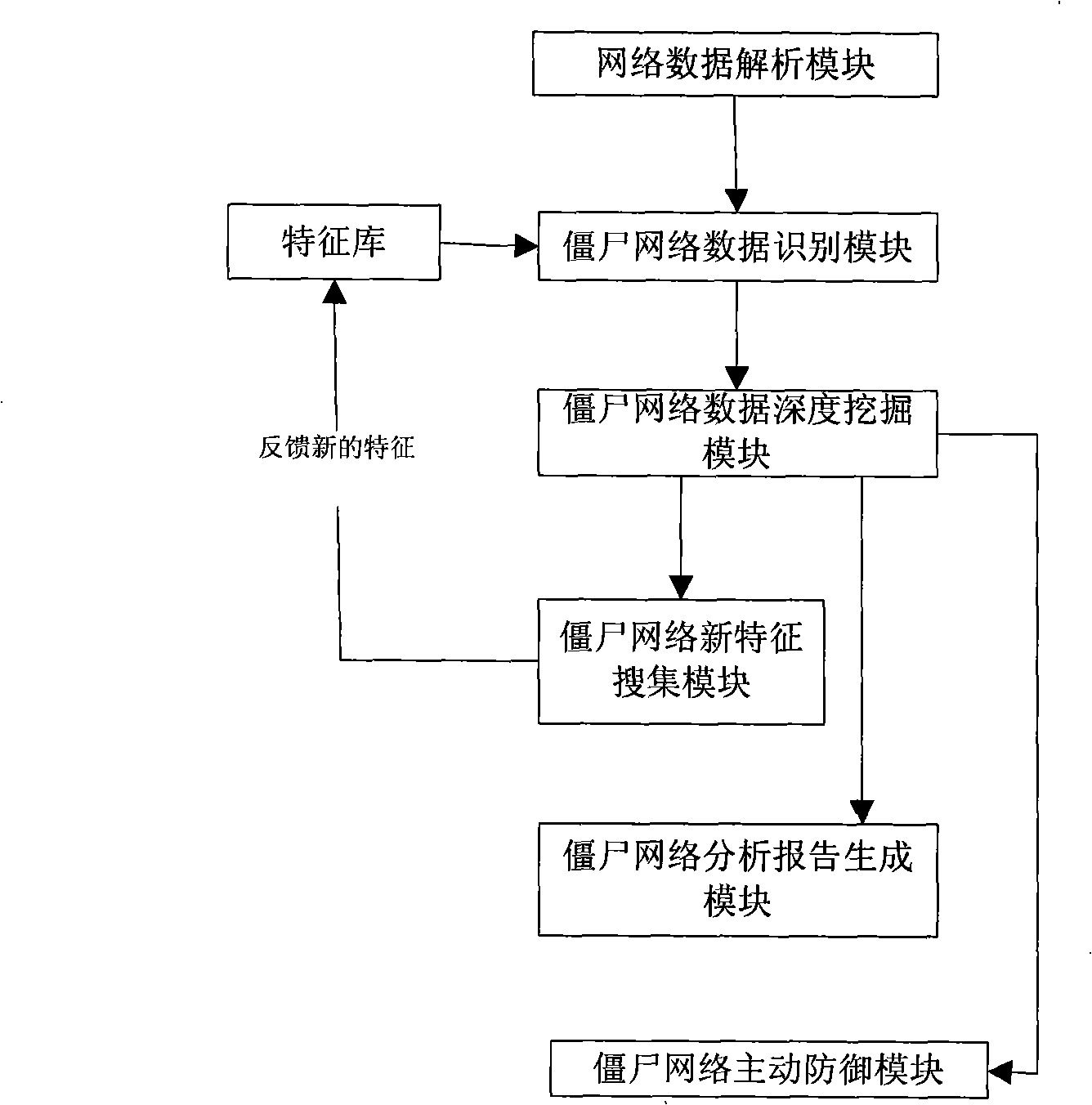
InactiveCN101404658AImprove defenseWide range of defenseData switching networksSpecial data processing applicationsNetwork packetNetwork control
The invention discloses a method for detecting a bot network and a system thereof, which belong to the field of computer security. The method comprises the following steps: first, extracting IRC protocol data from a network data packet; then, matching the protocol data with feature codes in a data feature bank to acquire a bot network data packet; dividing the bot network data packet, and linking the bot network data packets from the same bot network; finally, determining a control server, a bot computer and a bot network control computer from the same bot network according to the divided bot network data packets, thereby describing the topology of the bot network. The system comprises a network data analysis module, a bot network data identification module and a bot network data deep dig module. Compared with the prior art, the invention can analyze and defense the whole bot network integrally, and has the advantages of better defense effect, wider defense range, higher efficiency and better traceability.
Owner:RUN TECH CO LTD BEIJING
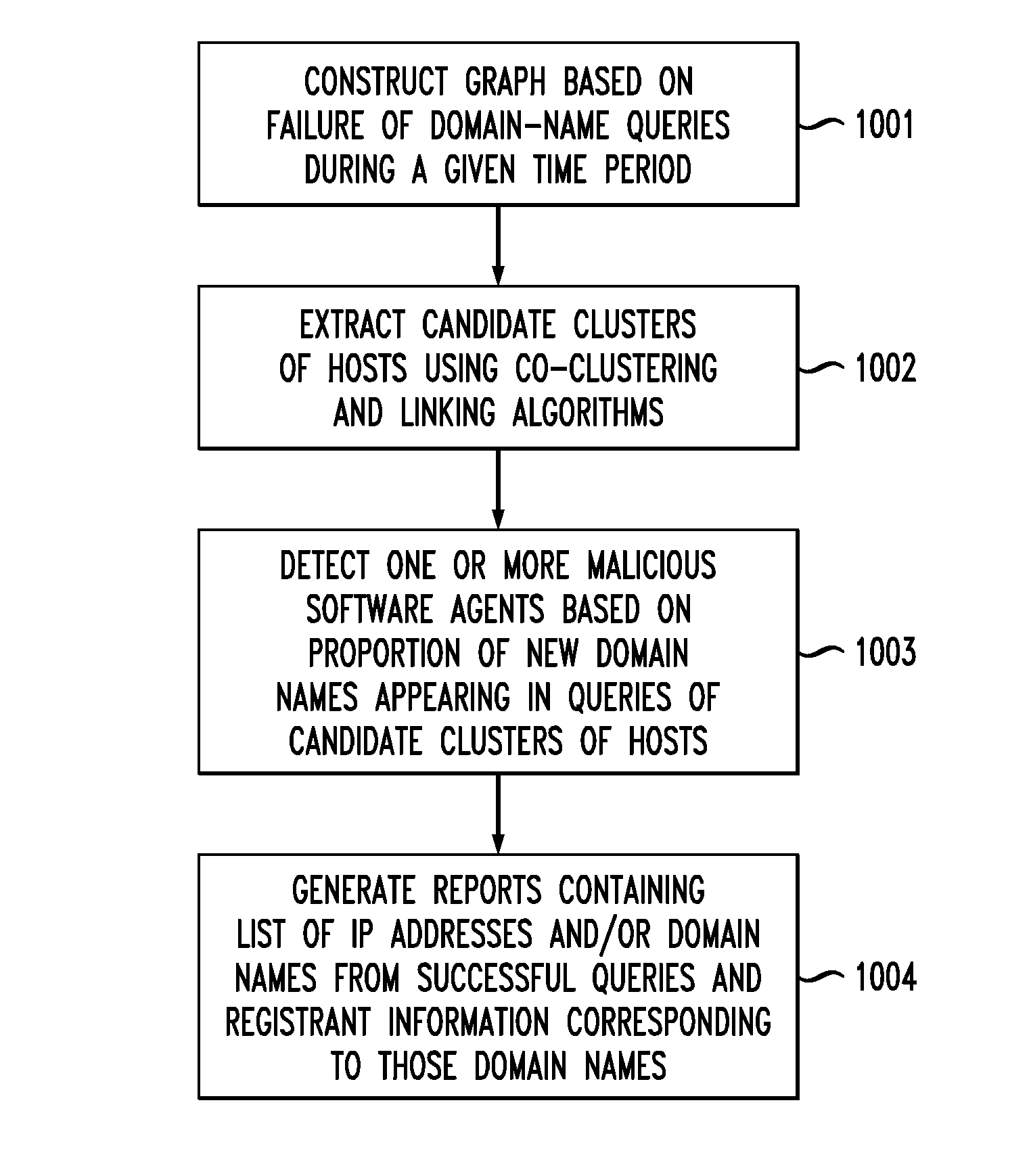
System and method for detection of domain-flux botnets and the like
ActiveUS8516585B2Memory loss protectionUnauthorized memory use protectionCluster algorithmDomain name
In one embodiment, a method for detecting malicious software agents, such as domain-flux botnets. The method applies a co-clustering algorithm on a domain-name query failure graph, to generate a hierarchical grouping of hosts based on similarities between domain names queried by those hosts, and divides that hierarchical structure into candidate clusters based on percentages of failed queries having at least first- and second-level domain names in common, thereby identifying hosts having correlated queries as possibly being infected with malicious software agents. A linking algorithm is used to correlate the co-clustering results generated at different time periods to differentiate actual domain-flux bots from other domain-name failure anomalies by identifying candidate clusters that persist for relatively long periods of time. Persistent candidate clusters are analyzed to identify which clusters have malicious software agents, based on a freshness metric that characterizes whether the candidate clusters continually generate failed queries having new domain names.
Owner:RPX CORP
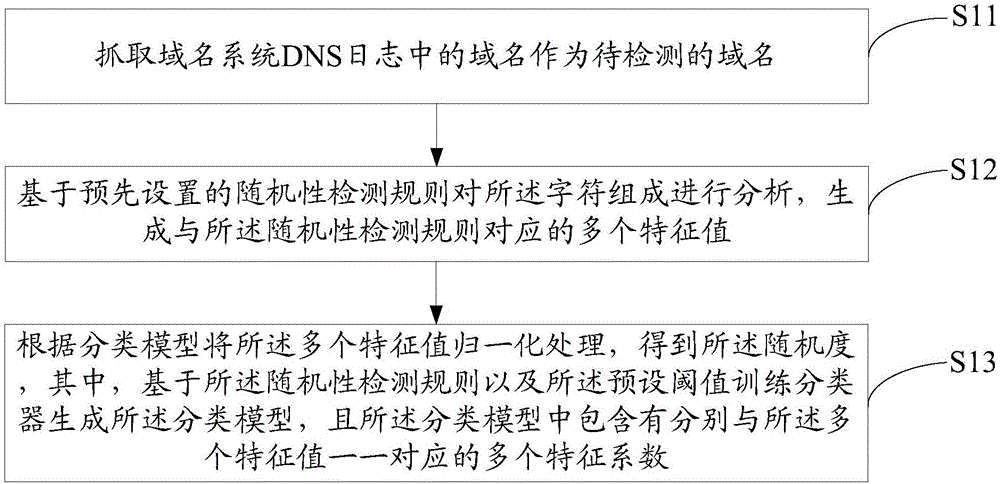
Method and device for detecting illegal domain name
The invention discloses a method and device for detecting an illegal domain name. The method includes the following steps that: a domain name to be detected is obtained, character composition in the domain name is analyzed, so that the feature value of the domain name can be obtained, and the degree of randomness of the domain name is obtained according to the feature value; and if the degree of randomness of the domain name is larger than a preset threshold value, it is determined that the domain name is an illegal domain name. The present invention also provides a device for detecting an illegal domain name. With the method and device for detecting the illegal domain name of the invention adopted, the technical problem that an existing botnet monitoring technology cannot detect newly-emerging illegal domain names can be solved, and the accuracy rate of the detection of illegal domain names can be improved.
Owner:SANGFOR TECH INC
Method, apparatus and system for detecting botnet
A method, an apparatus, and a system for detecting Botnet are disclosed. The method for detecting Botnet includes: obtaining an address information about a control host in a Bot sample by using an auto breakout environment; sending a query request message to a traffic analysis device to obtain an address information of a Bot host connected with the control host, in which the query request message carries the address information about the control host; and receiving a query response message returned by the traffic analysis device, in which the query response message carries the address information of the Bot host connected with the control host. The method for detecting Botnet can obtain the Botnet information in real time and construct a topology of the Botnet.
Owner:HUAWEI TECH CO LTD
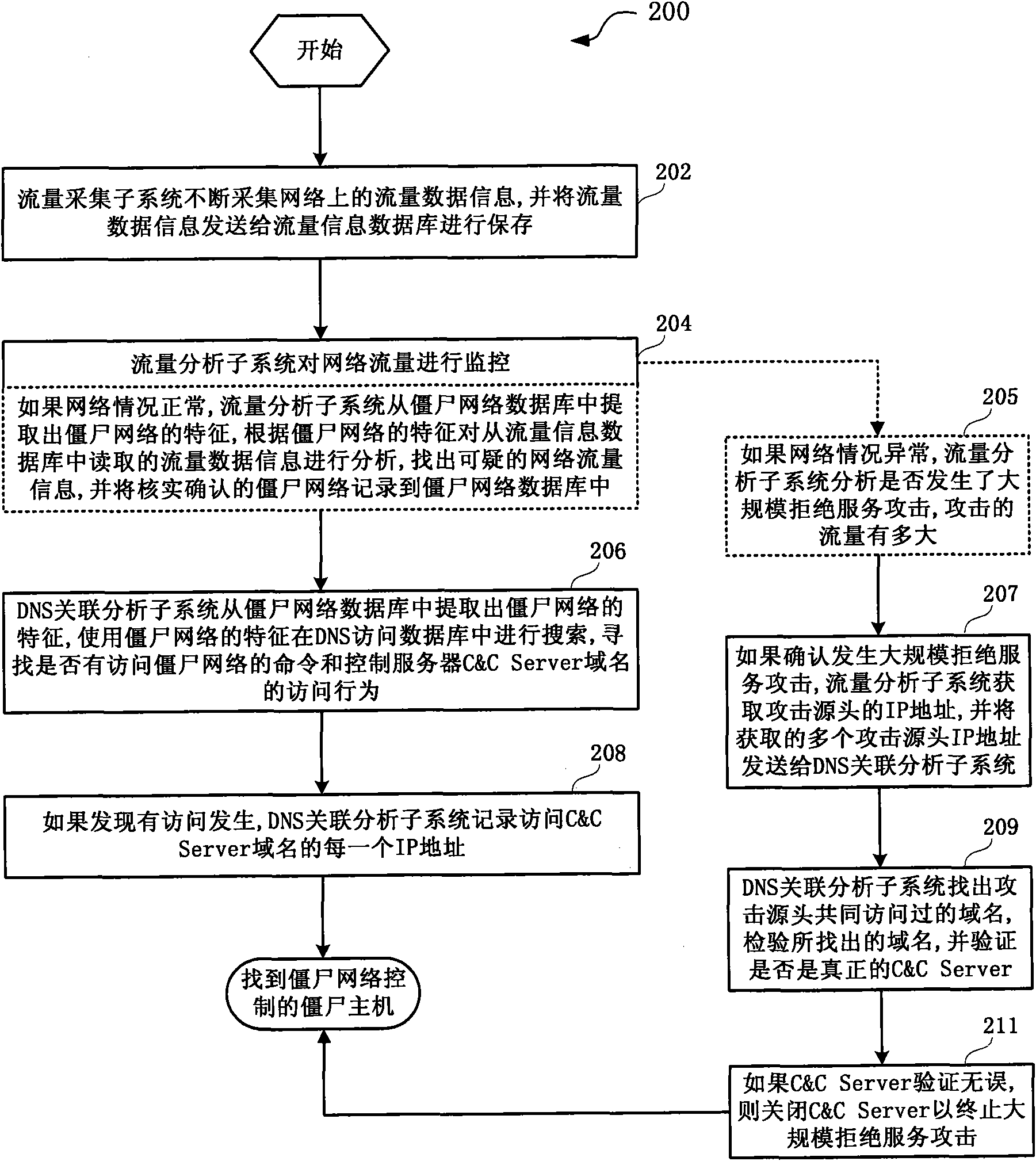
Method and system for reviewing Botnet
The invention discloses a method and a system for reviewing Botnet. The method comprises the steps of: continuously collecting flow data information on a network through a flow collecting sub-system and sending the flow data information to a flow information database to store, monitoring the network flow through a flow analyzing sub-system, taking out the feature of the Botnet from a Botnet database by a DNS correlation analysis sub-system, searching in the database accessed by DNS with the feature of the Botnet, finding if exist the Botnet accessing order and an access of a control server C&C Server domain name, and if yes, recording each IP address of the C&C Server domain name through the DNS correlation analysis sub-system. The method and system of the invention can find out Botnet and the host computer controlling the Botnet by analyzing and verifying the access request of DNS and the network flow feature, and can perform precautionary measures to the corresponding server and Botnet host computer like refusing service, close the server, and the like, so as to further ensure the safety of the network.
Owner:CHINA TELECOM CORP LTD
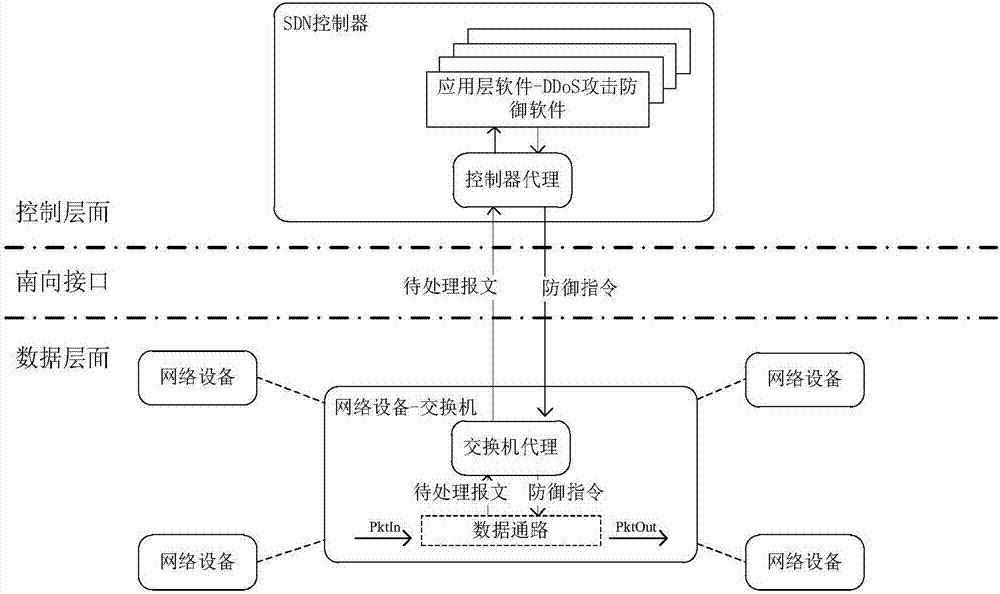
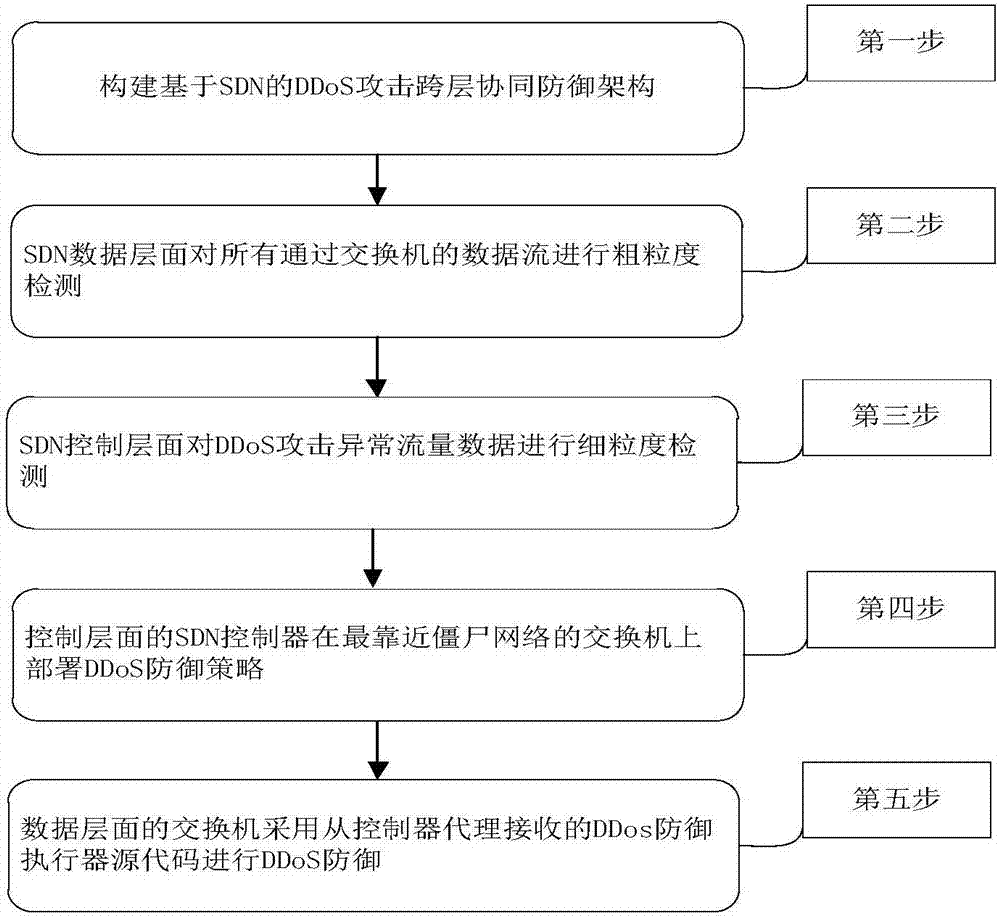
Software defined network-based DDoS attack cross-layer cooperative defense method
The invention discloses a software defined network-based DDoS attack cross-layer cooperative defense method and aims to solve the problems of over high communication pressure of a southbound interfaceand a control plane as well as over high calculation pressure of an SDN controller. According to the technical scheme, the method comprises the following steps: constructing an SDN-based DDoS attackcross-layer cooperative defense framework comprising a data plane and a control plane, performing coarse-grained detection on data flow by the data plane to acquire DDoS attack abnormal flow data, andperforming fine-grained detection on the DDoS attack abnormal flow data by the control plane to acquire an exchanger closest to a bot network; deploying a DDoS defense strategy on the exchanger closest to the bot network by the SDN controller of the control plane, and performing DDoS defense according to the DDoS defense strategy by the SDN exchanger of the data plane. Through cooperation of thedata plane and the control plane, the cooperative defense advantage of the SDN is completely utilized and the problems of high pressure of the SDN southbound interface and too large burden of the SDNcontroller are solved, so that the exchanger can perform automatic defense intelligently.
Owner:NAT UNIV OF DEFENSE TECH
Malicious traffic isolation system and method using botnet information
InactiveUS20110154492A1Effective trafficMemory loss protectionData taking preventionTraffic capacityClient-side
The present invention relates to a malicious traffic isolation system and method using botnet information, and more particularly, to a malicious traffic isolation system and method using botnet information, in which traffics for a set of clients having the same destination are routed to the isolation system based on a destination IP / Port, and botnet traffics are isolated using botnet information based on similarity among groups of the routed and flowed in traffics. The present invention may provide a malicious traffic isolation method using botnet information, which can accommodate traffics received from a PC or a C&C server infected with a bot into a quarantine area, isolate traffics generated by normal users from traffics transmitted from malicious bots, and block the malicious traffics. In addition, the present invention may provide a malicious traffic isolation method using botnet information, which can provide a function of mitigating DDoS attacks of a botnet.
Owner:KOREA INTERNET & SECURITY AGENCY
System, method and computer program product for collusion detection
ActiveUS8533825B1Easy to liftPractical solutionMemory loss protectionError detection/correctionClient-sideBotnet
Embodiments disclosed herein provide a practical solution for click fraud detection. One embodiment of a method may comprise constructing representations of entities via a graph network framework. The representations, graphs or vector spaces, may capture information pertaining to clicks by botnets / click farms. To detect click fraud, each representation may be analyzed in the context of clustering, resulting in large data sets with respect to time, frequency, or gap between clicks. Highly accurate and highly scalable heuristics may be developed / applied to identify IP addresses that indicate potential collusion. One embodiment of a system having a computer program product implementing such a click fraud detection method may operate to receive a client file containing clicks gathered at the client side, construct representations of entities utilizing the graph framework described herein, perform clustering on the representations thus constructed, identify IP addresses of interest, and return a list containing same to the client.
Owner:GOOGLE LLC
Method and apparatus for identifying members of a peer-to-peer botnet
A peer-to-peer (P2P) bot(s) in a network is identified using an already identified P2P bot. More specifically, such embodiments may facilitate determining a candidate set of computers, which may be potential P2P bots, by identifying computers in a network that have a private mutual contact with a seed bot, which is a computer identified as a P2P bot, and identifying additional computers that have private mutual contacts with the identified computers. Further, a confidence level indicative of a certainty of a membership of each of the candidate computers in the P2P botnet is determined and responsive to a determination that the confidence level of the candidate computer exceeds a determined threshold confidence level, the candidate computer is identified as a P2P bot.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
Command and control channel detection with query string signature
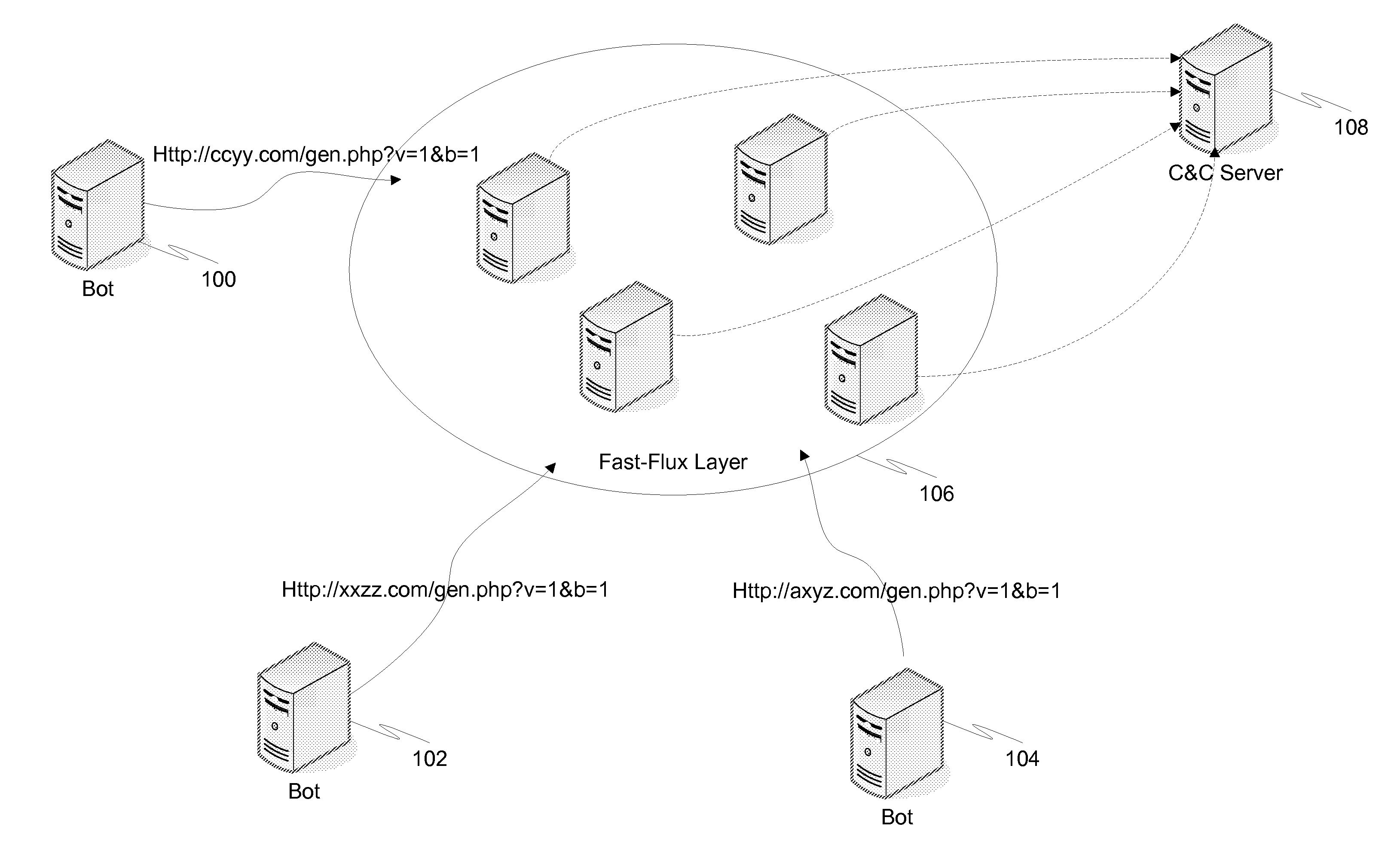
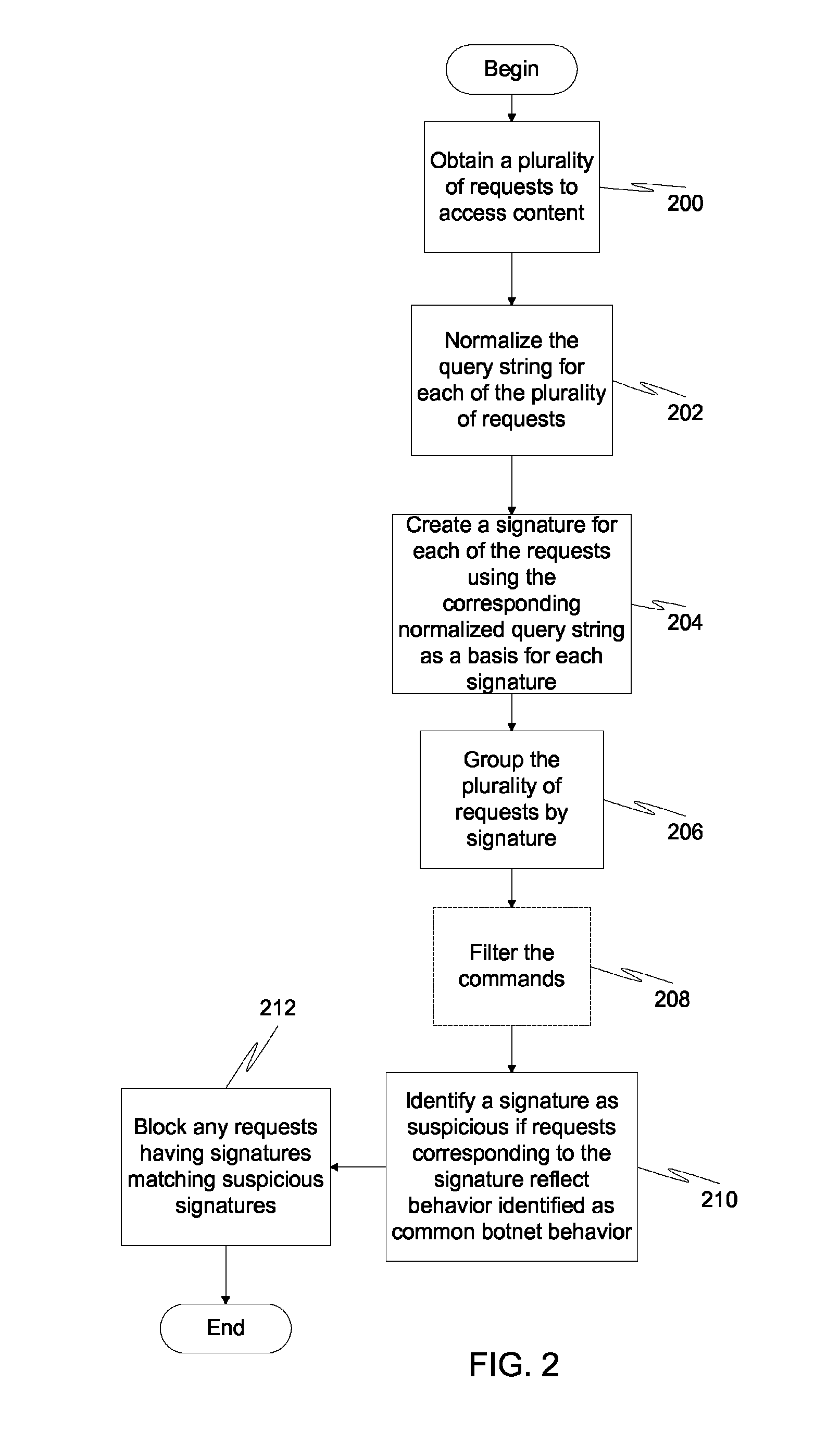
Detection and prevention of botnet behavior is accomplished by monitoring access request in a network. Each request includes a domain of content to access and a path of content to access, and each path includes a file name and query string. Once obtained, the query strings for each of these requests are normalized. A signature is then created for each of the normalized query strings. The obtained requests can then be grouped by signature. Once the requests have been grouped by signature, each grouping is examined to identify suspicious signatures based on common botnet behavior. Suspicious requests are used in back-end and front-end defenses against botnets.
Owner:TREND MICRO INC
Domain name server (DNS) data packet-based bot-net domain name discovery method
The invention discloses a domain name server (DNS) data packet-based bot-net domain name discovery method. A DNS data packet is taken as a basic data source in a network layer, and a domain name co-occurrence scoring method is used for tracking and discovering a plurality of bot-net domain names under the condition that a part of bot-net domain names are known by utilizing the two key features of groupment and persistence of a bot-net. Known local features (manifesting as bot-net domain names) of the bot-net are updated or changed into unknown domain names along with time, the unknown domain names are discovered, and the dynamic variations of access behaviors of a specified bio-net are discovered, mastered and tracked, so that the shortcomings of the conventional bio-net detection method are overcome. According to the method, domain names are taken as features, so that the limitation caused by bio-net protocol diversity, information encryption and the like when feature codes are used for detection can be avoided; and an object is observed according to the co-occurrence behaviors of the domain names, so that the unknown bio-net domain names can be discovered by fully utilizing the features of groupment and persistence of the bio-net.
Owner:XI AN JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com