Method and system for reviewing Botnet
A botnet and subsystem technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as inability to suppress botnets, inability to find zombie hosts, difficulty in locating zombie hosts and botnets, etc., to achieve The effect of ensuring network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be described more fully hereinafter with reference to the accompanying drawings, in which exemplary embodiments of the invention are illustrated.
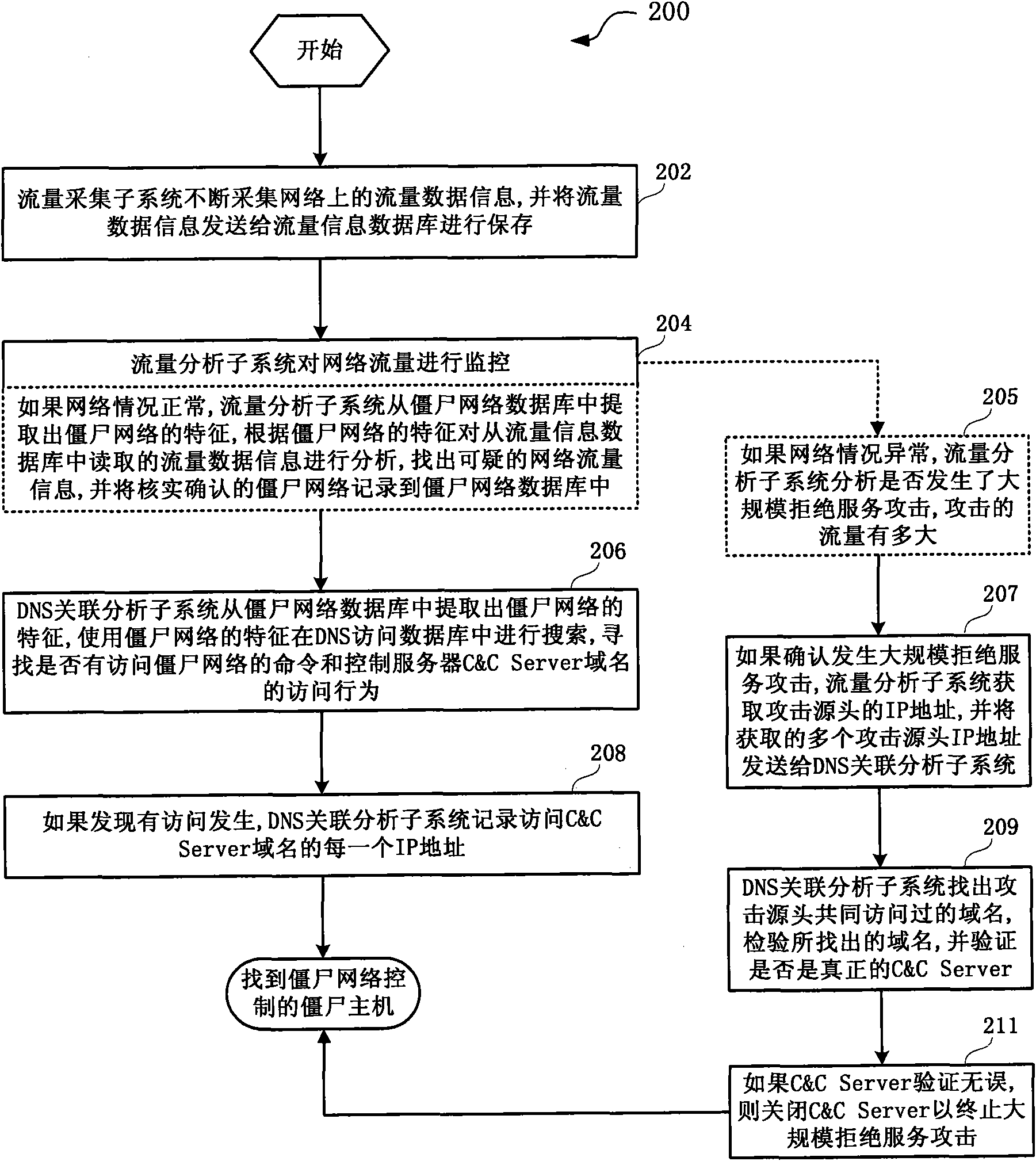
[0030] figure 1 A flowchart showing a method for tracing a botnet provided by an embodiment of the present invention.
[0031] like figure 1As shown, the method 100 for tracing a botnet includes: Step 102, the traffic collection subsystem continuously collects traffic data information on the network, and sends the traffic data information to a traffic information database for storage. For example, the traffic collection subsystem is a system for collecting network traffic information, which can adopt a coarse force collection module, a fine-grained force collection module, or a structure with two parts: a coarse force collection module and a fine force collection module; The traffic collection method performed by the coarse module can use the traffic sampling function that comes with the current ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com