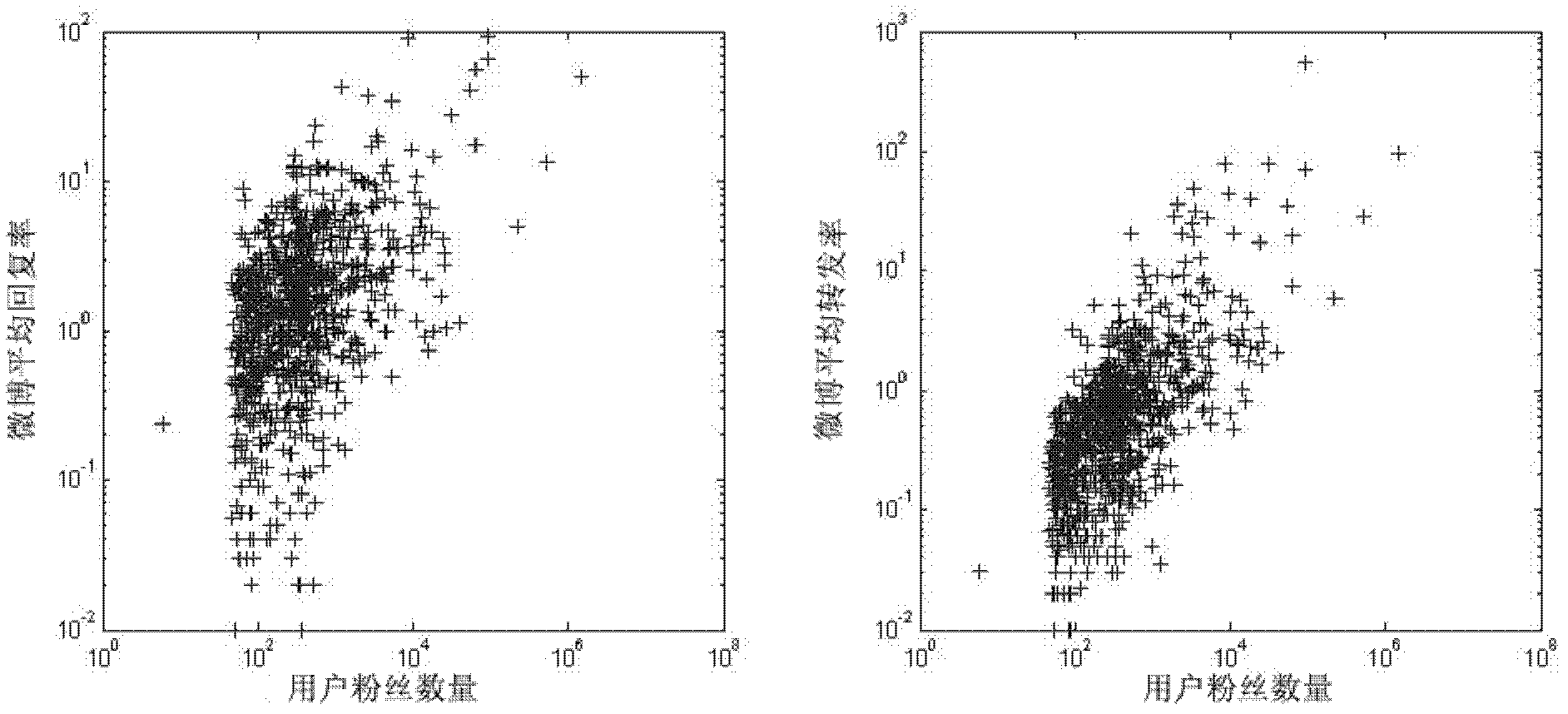
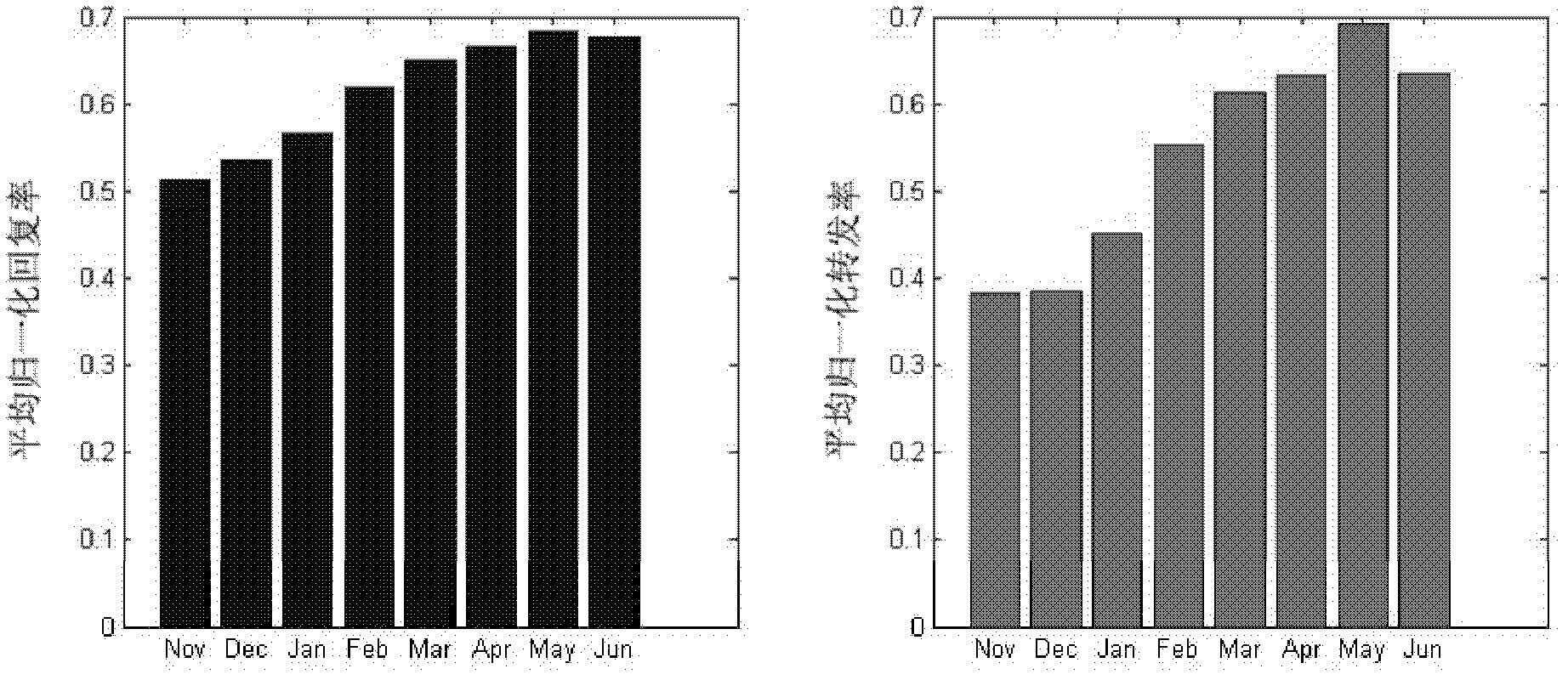
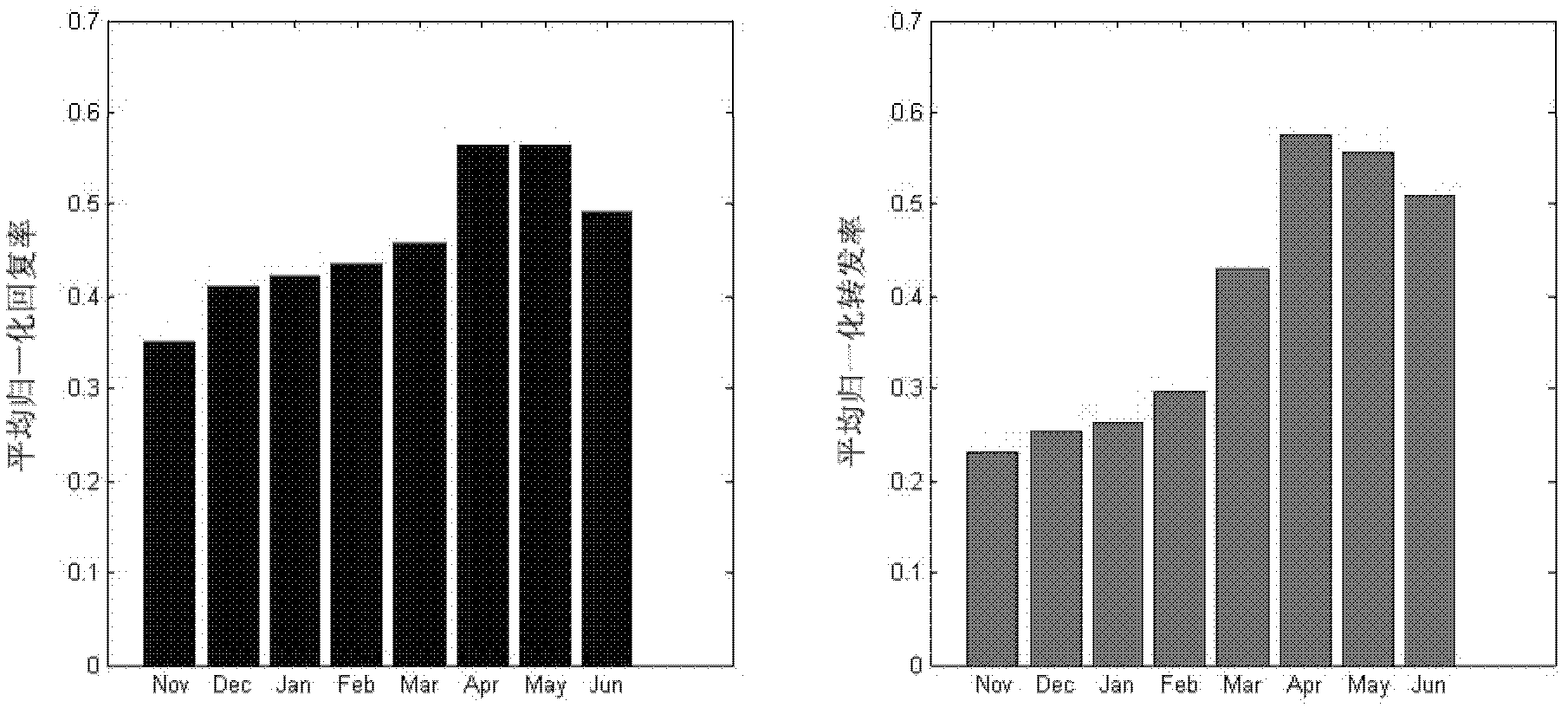
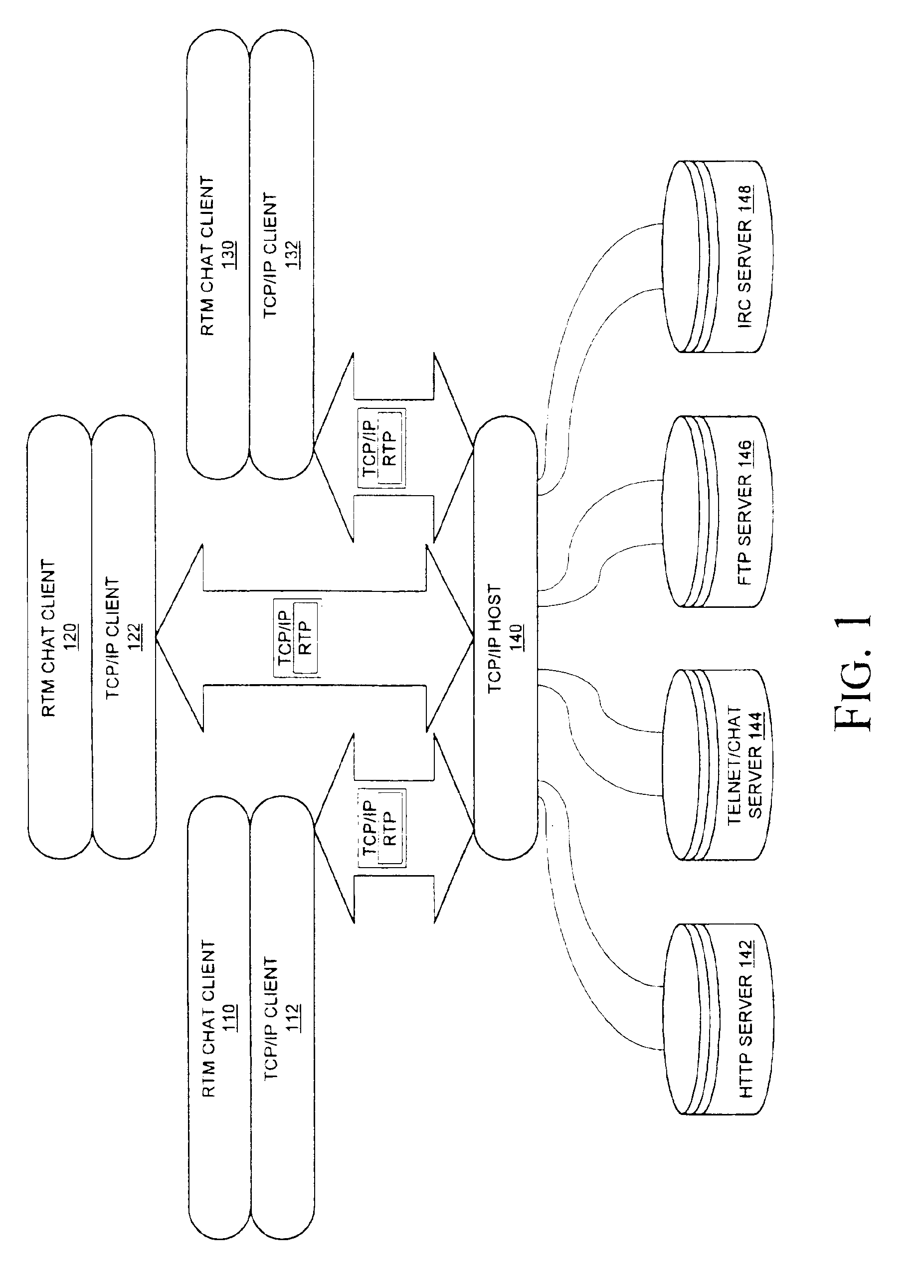
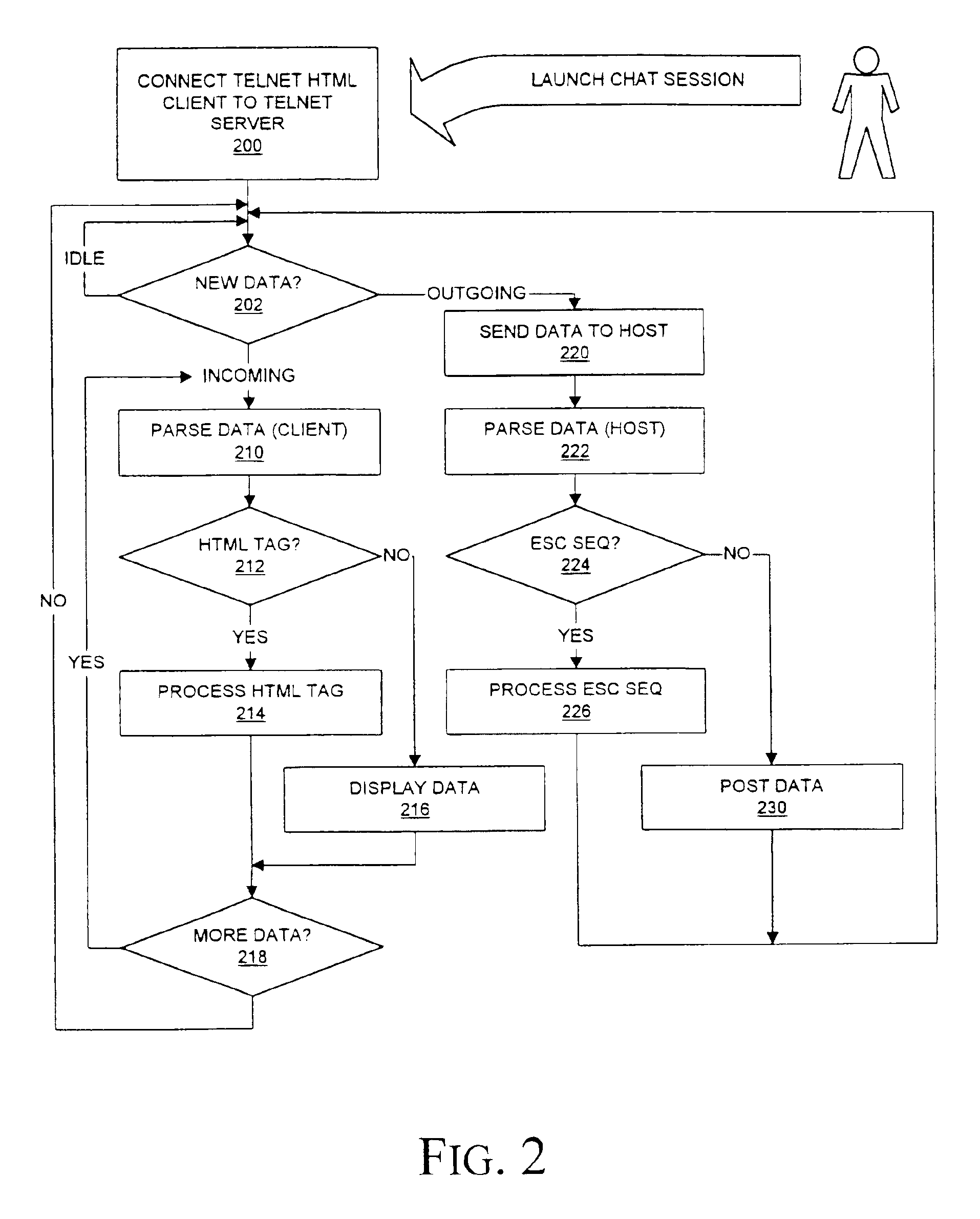
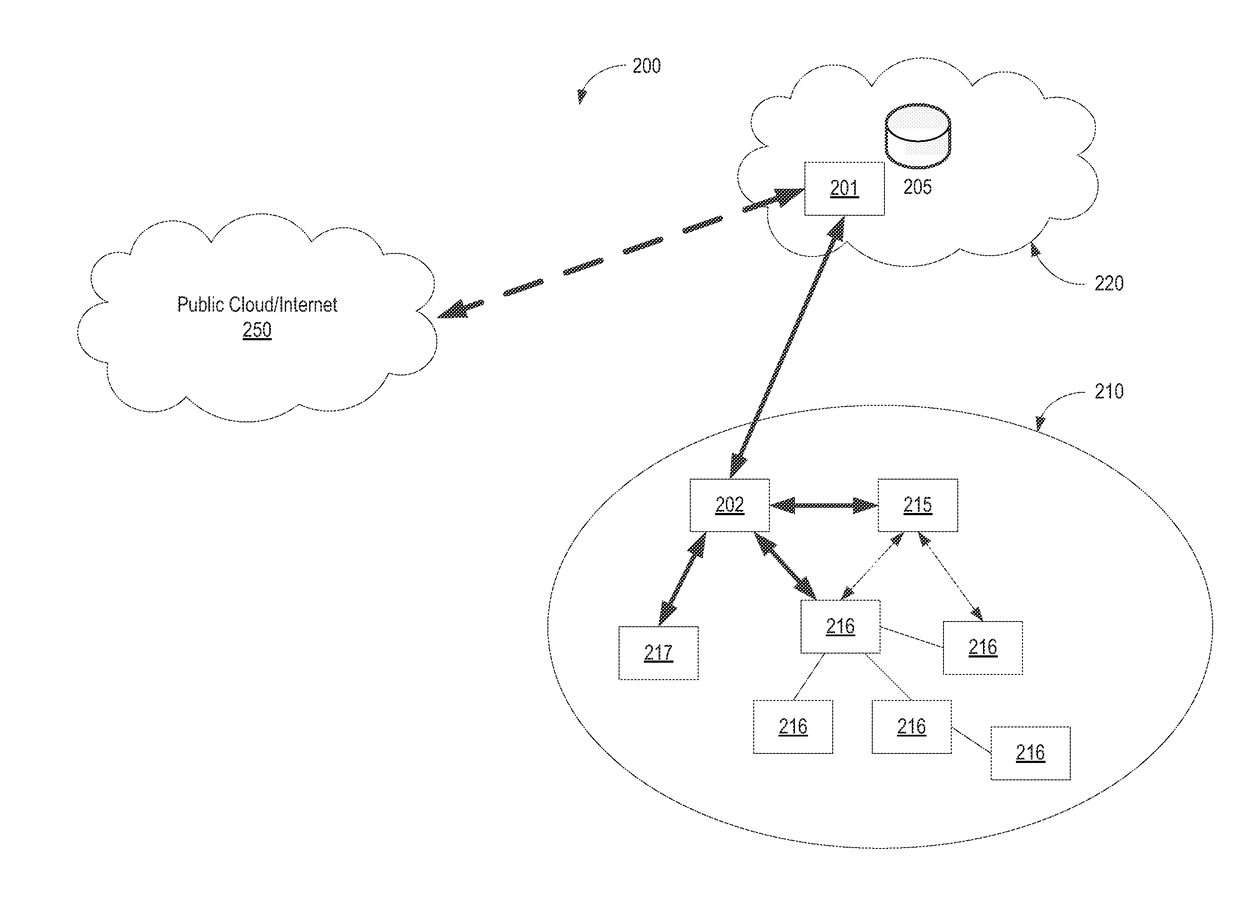
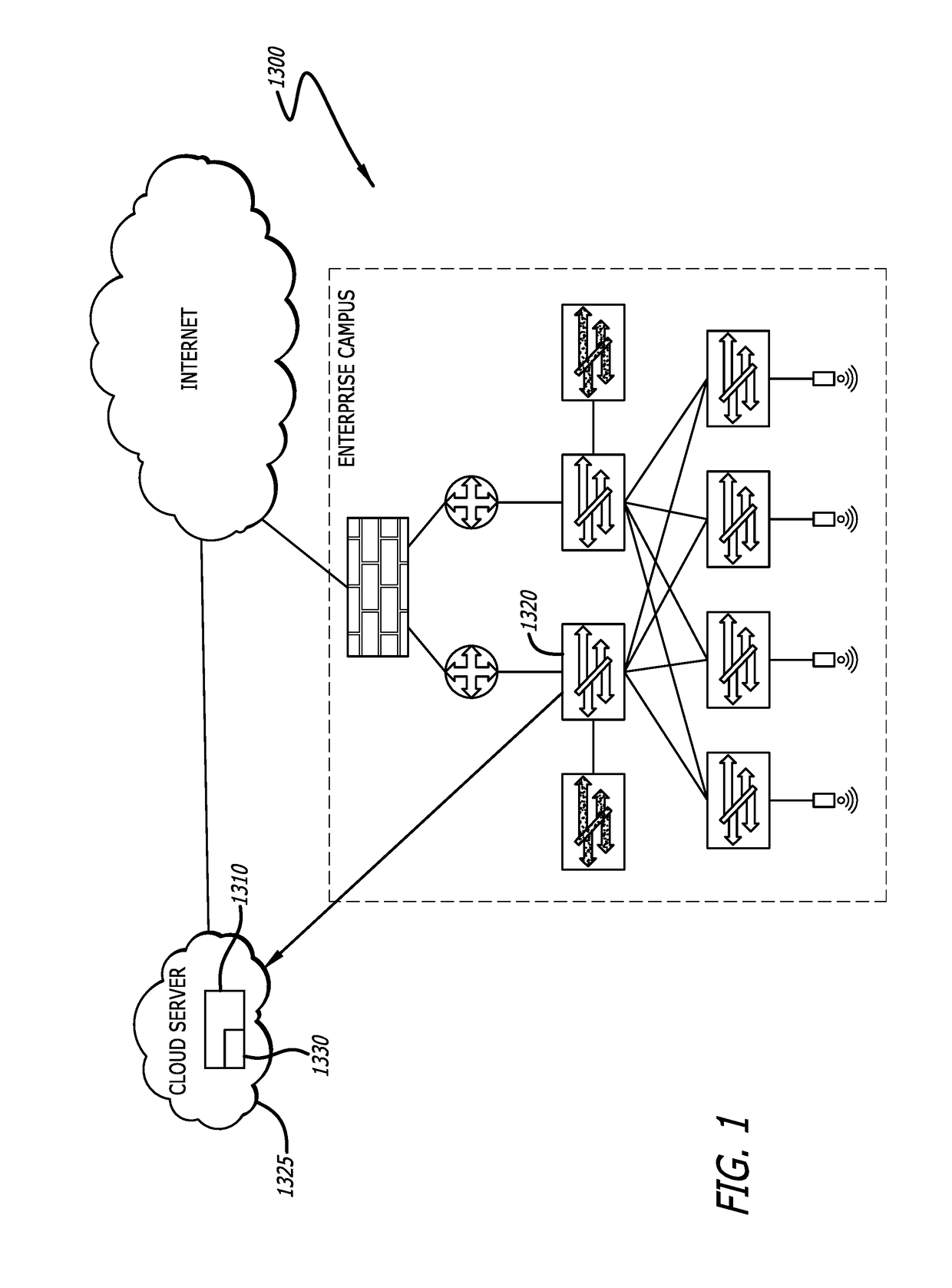
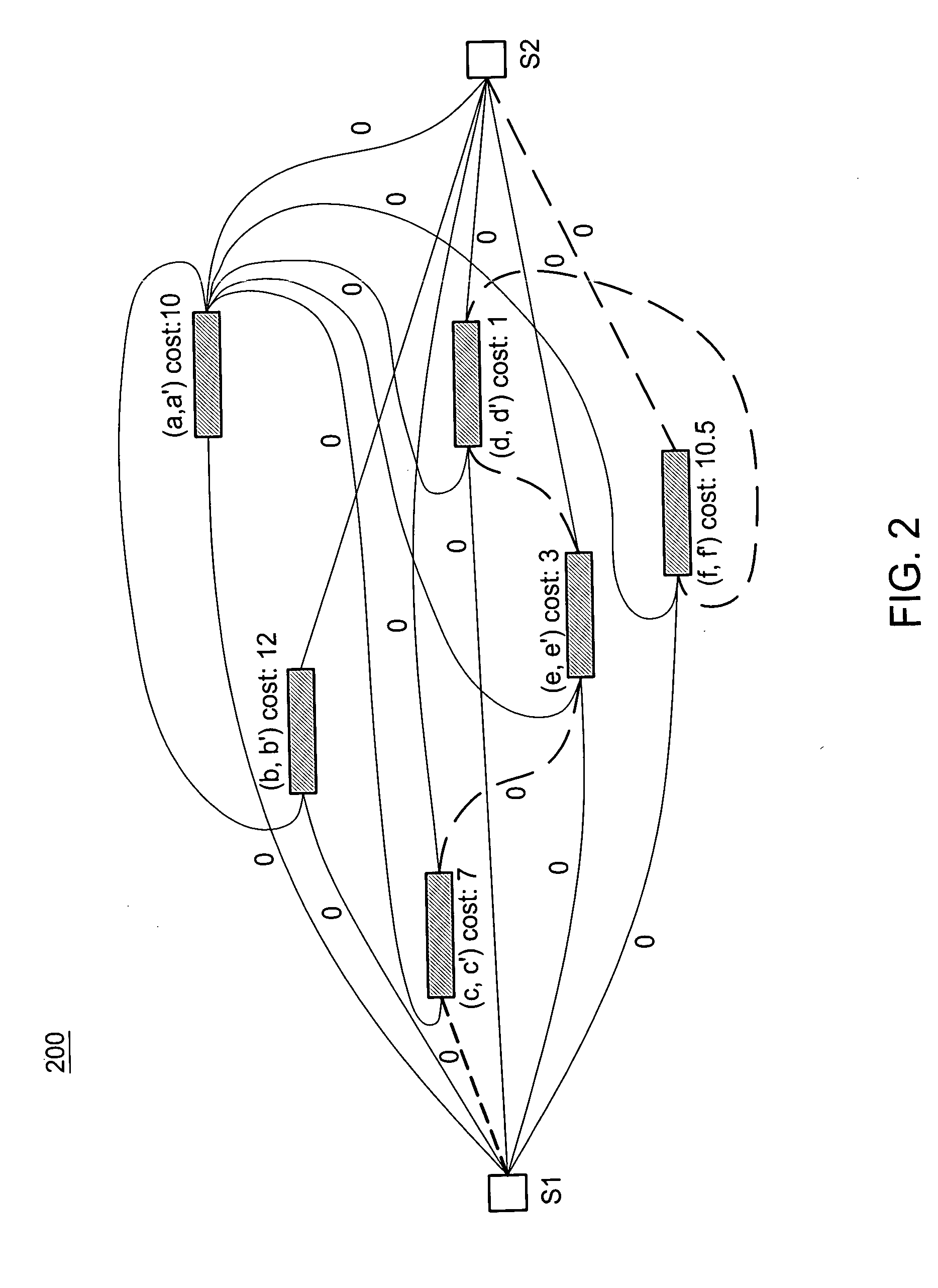
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
769 results about "Real time networks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Real-Time Networks. Real-time network (RTN) users demand high quality data available around the clock. Trimble supports enterprises all over the world to design, build and operate real-time networks for any industry.
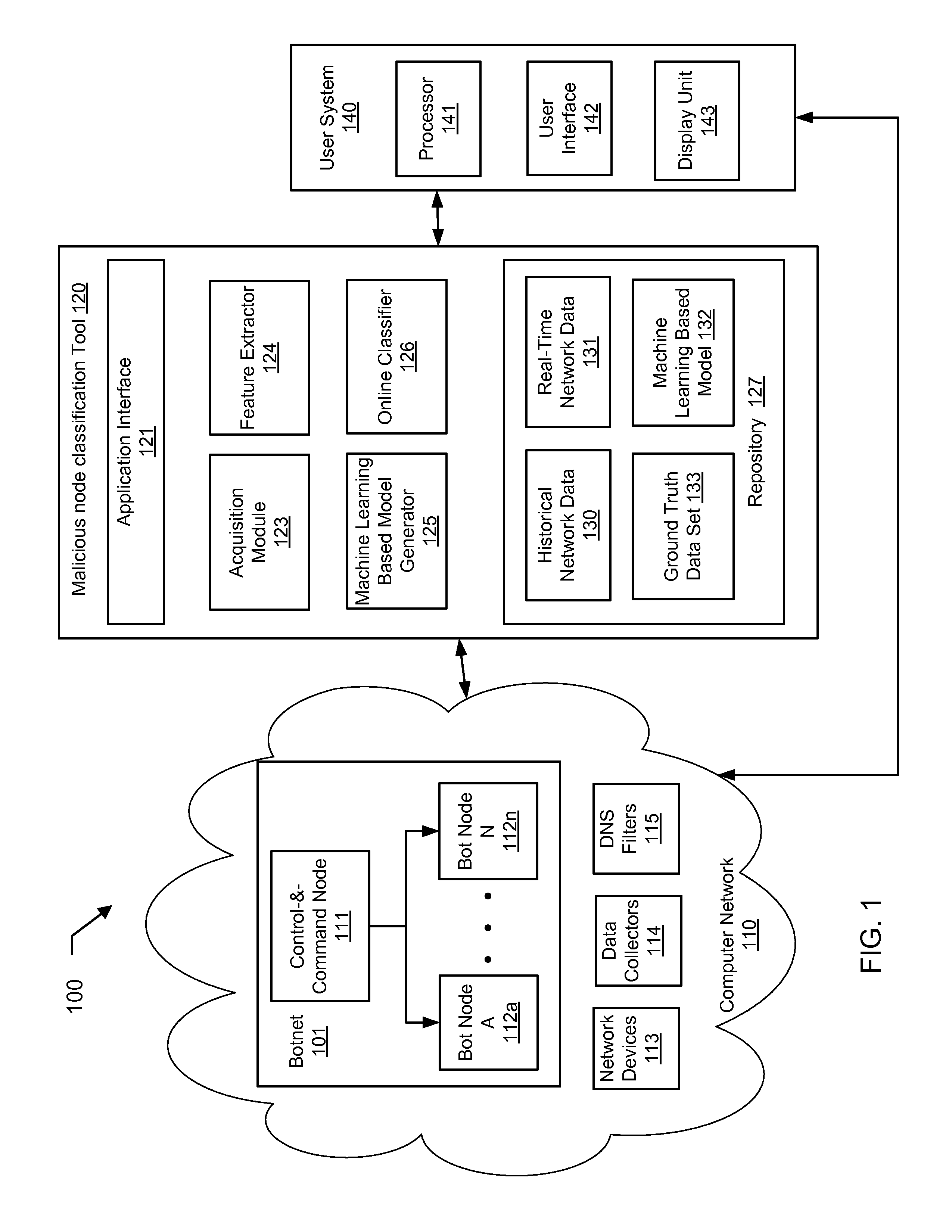
Machine learning based botnet detection using real-time extracted traffic features
ActiveUS8682812B1Digital computer detailsComputer security arrangementsLearning basedTraffic capacity
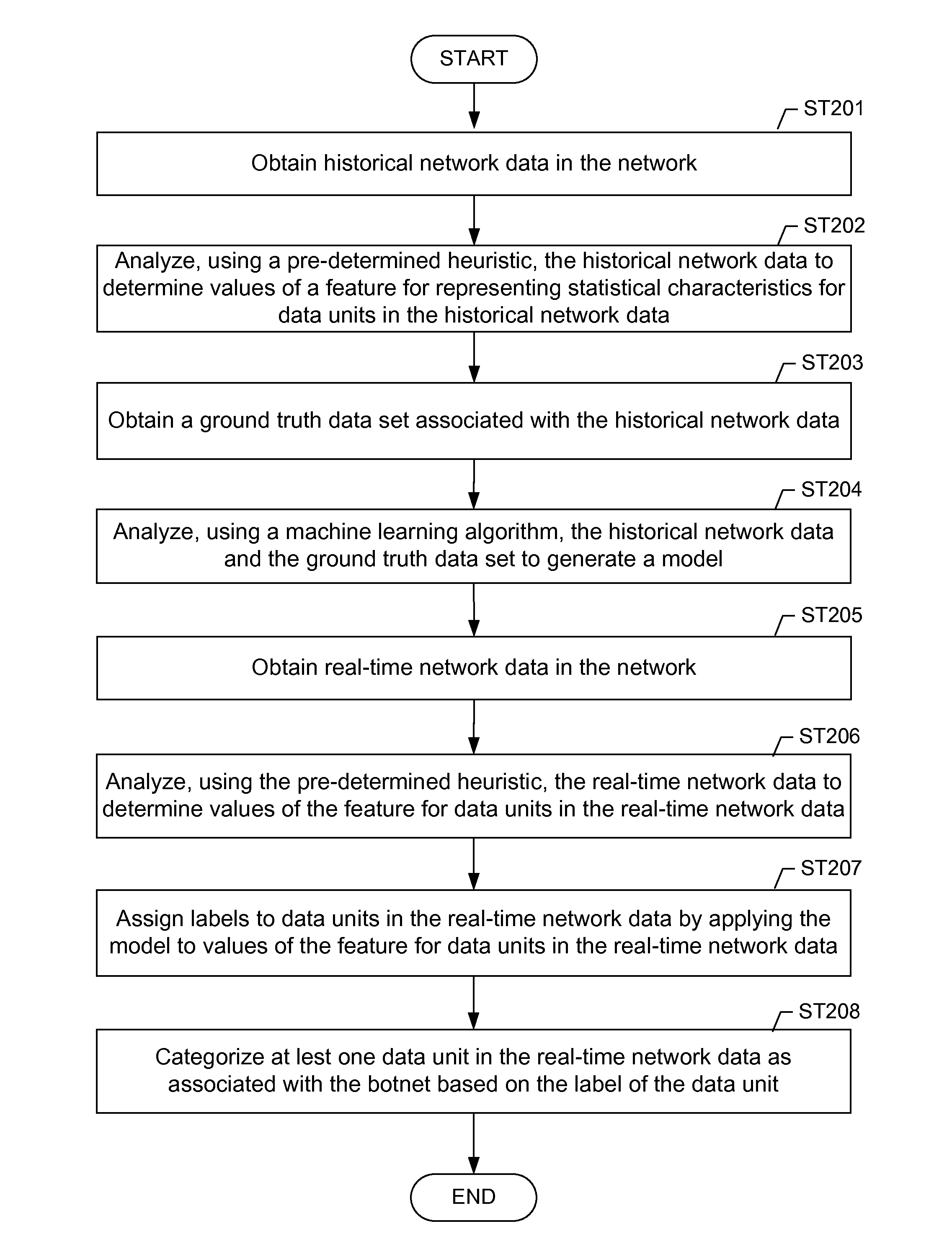
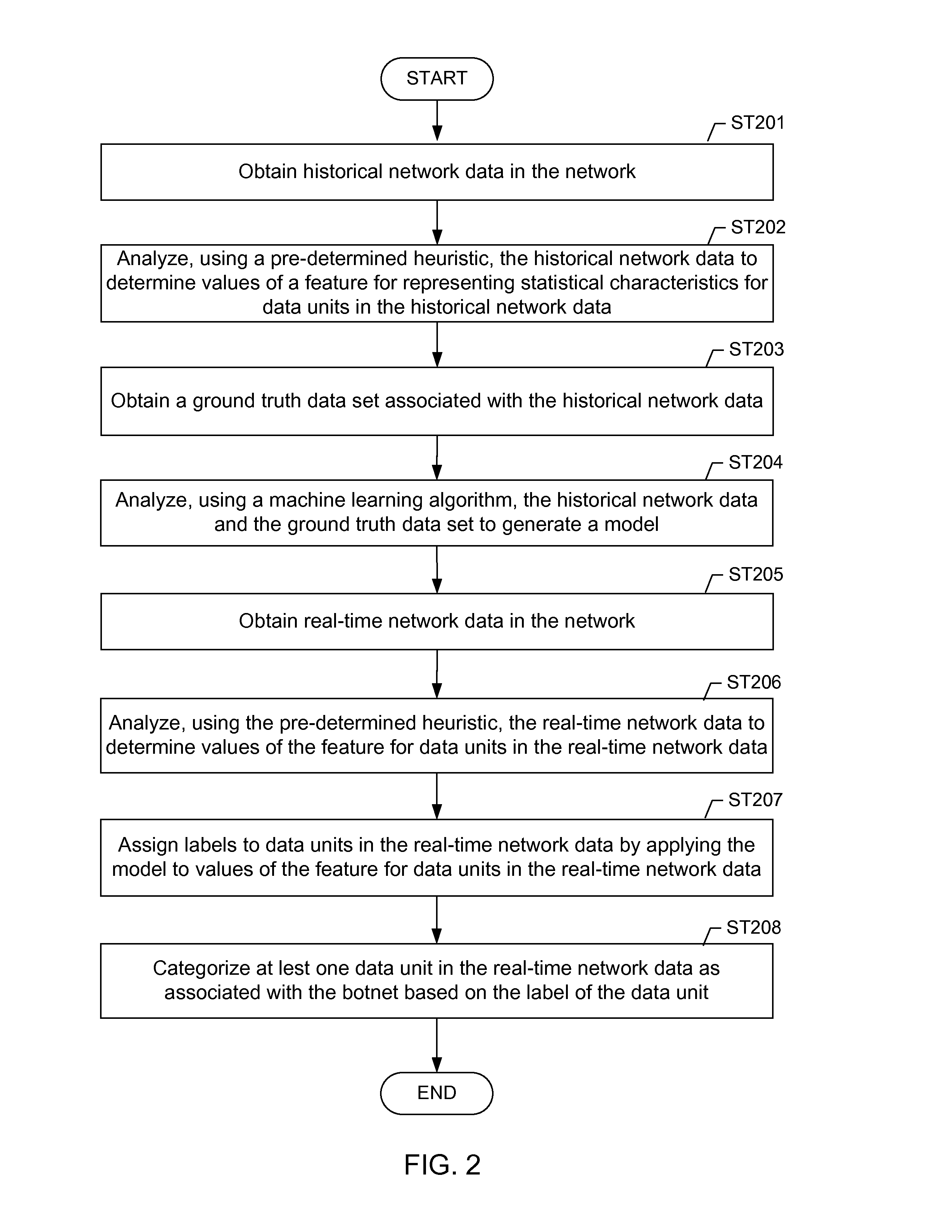
A method for identifying a botnet in a network, including analyzing historical network data using a pre-determined heuristic to determine values of a feature in the historical network data, obtaining a ground truth data set having labels assigned to data units in the historical network data identifying known malicious nodes in the network, analyzing the historical network data and the ground truth data set using a machine learning algorithm to generate a model representing the labels as a function of the values of the feature, analyzing real-time network data using the pre-determined heuristic to determine a value of the feature for a data unit in the real-time network data, assigning a label to the data unit by applying the model to the value of the feature, and categorizing the data unit as associated with the botnet based on the label.
Owner:THE BOEING CO
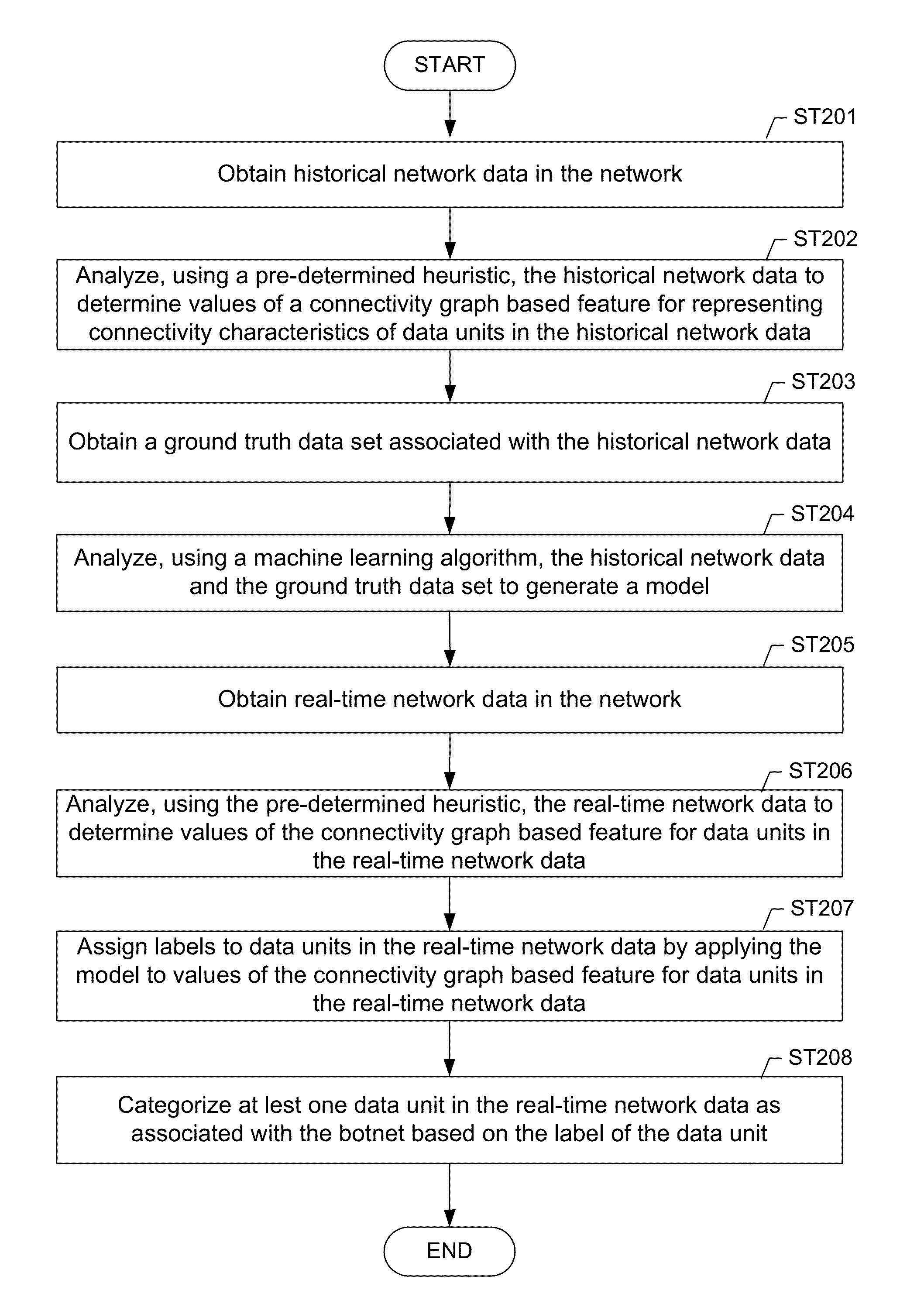
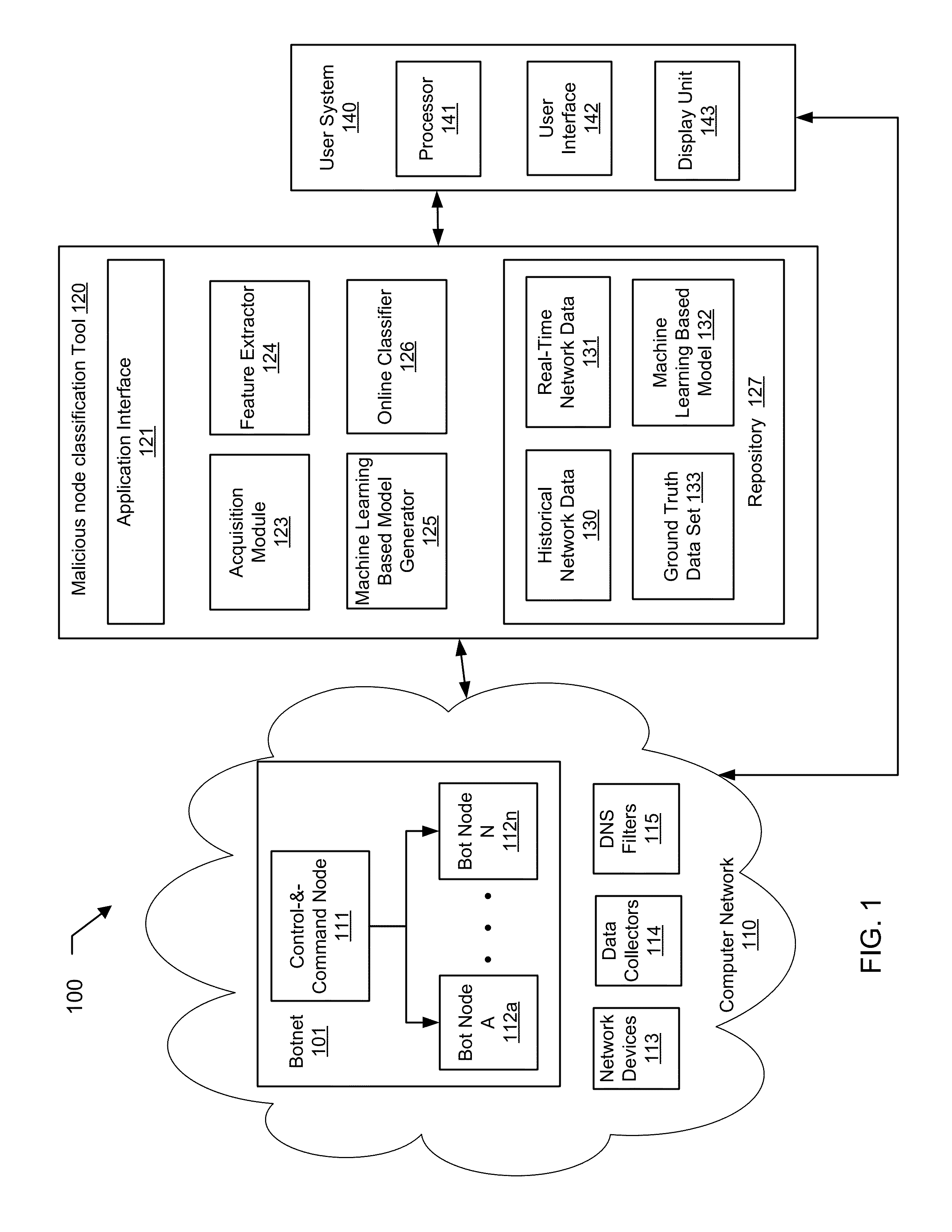
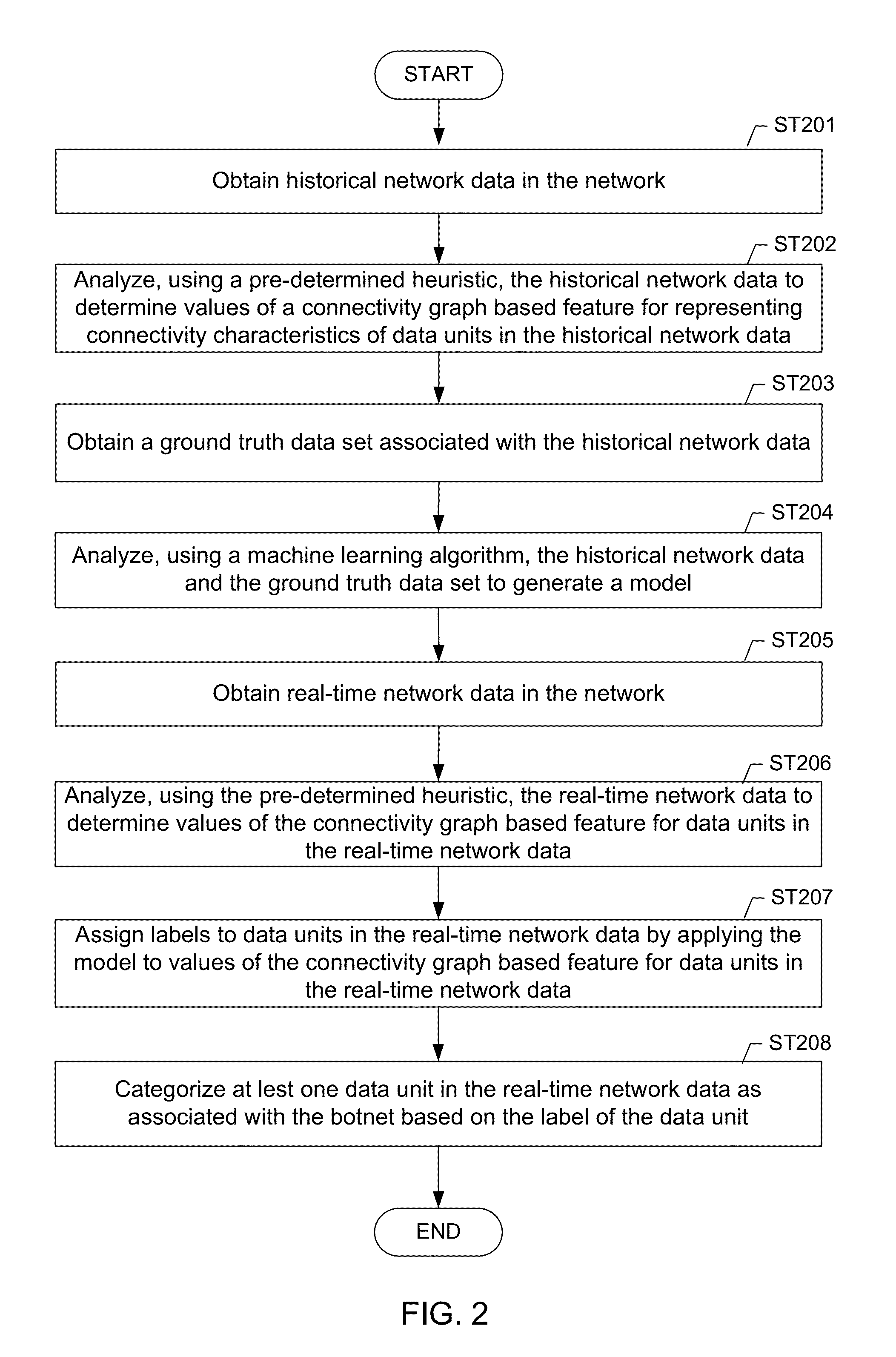
Machine learning based botnet detection using real-time connectivity graph based traffic features
A method for identifying a botnet in a network, including analyzing historical network data using a pre-determined heuristic to determine values of a connectivity graph based feature in the historical network data, obtaining a ground truth data set having labels assigned to data units in the historical network data identifying known malicious nodes in the network, analyzing the historical network data and the ground truth data set using a machine learning algorithm to generate a model representing the labels as a function of the values of the connectivity graph based feature, analyzing real-time network data using the pre-determined heuristic to determine a value of the connectivity graph based feature for a data unit in the real-time network data, assigning a label to the data unit by applying the model to the value of the connectivity graph based feature, and categorizing the data unit as associated with the botnet based on the label.
Owner:THE BOEING CO
Diagnostic access system
InactiveUS7975184B2Reduce user costsEasy to useError detection/correctionDigital computer detailsData processing systemDiagnostic data
Owner:GOFF DONALD +2
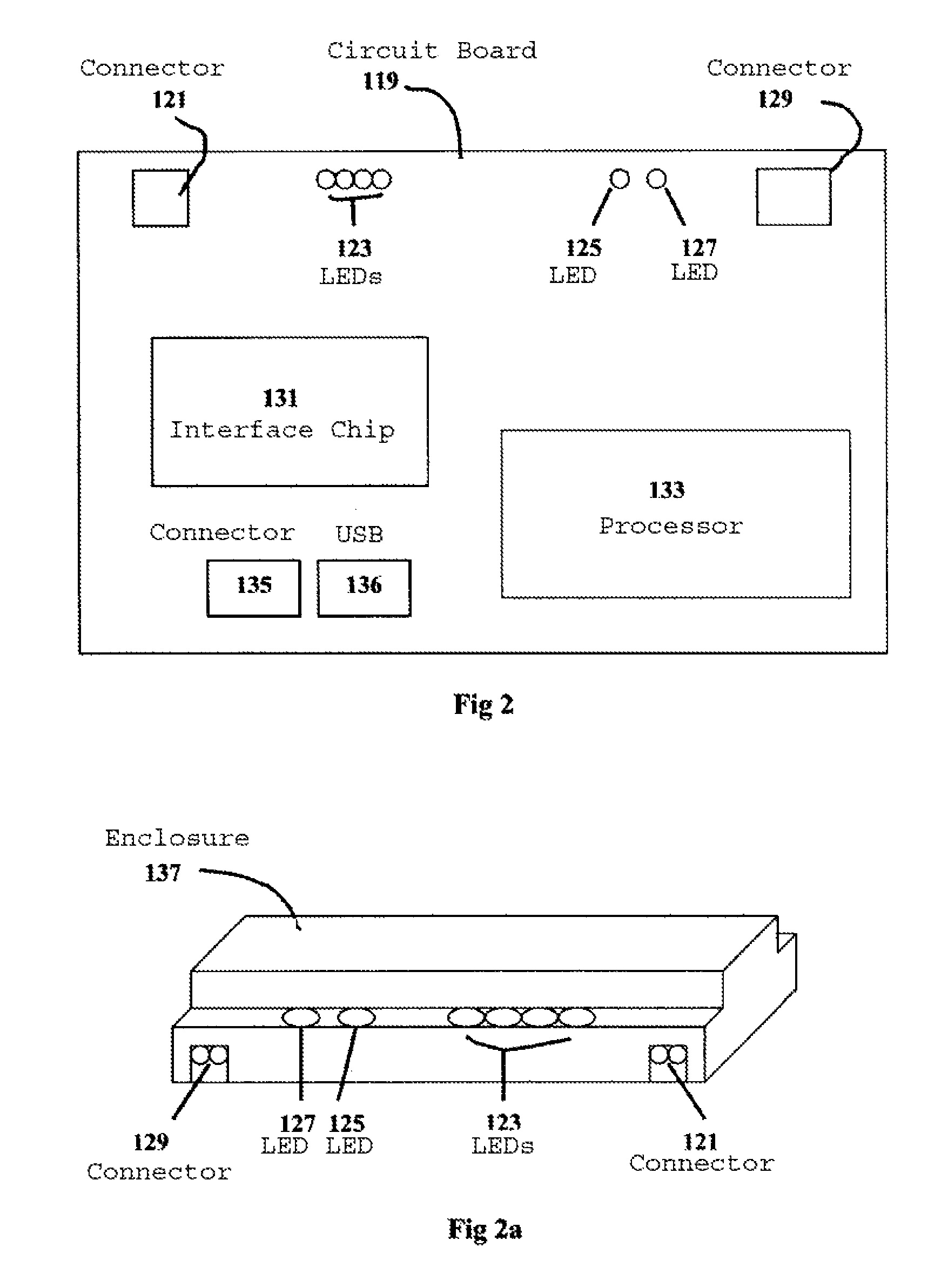
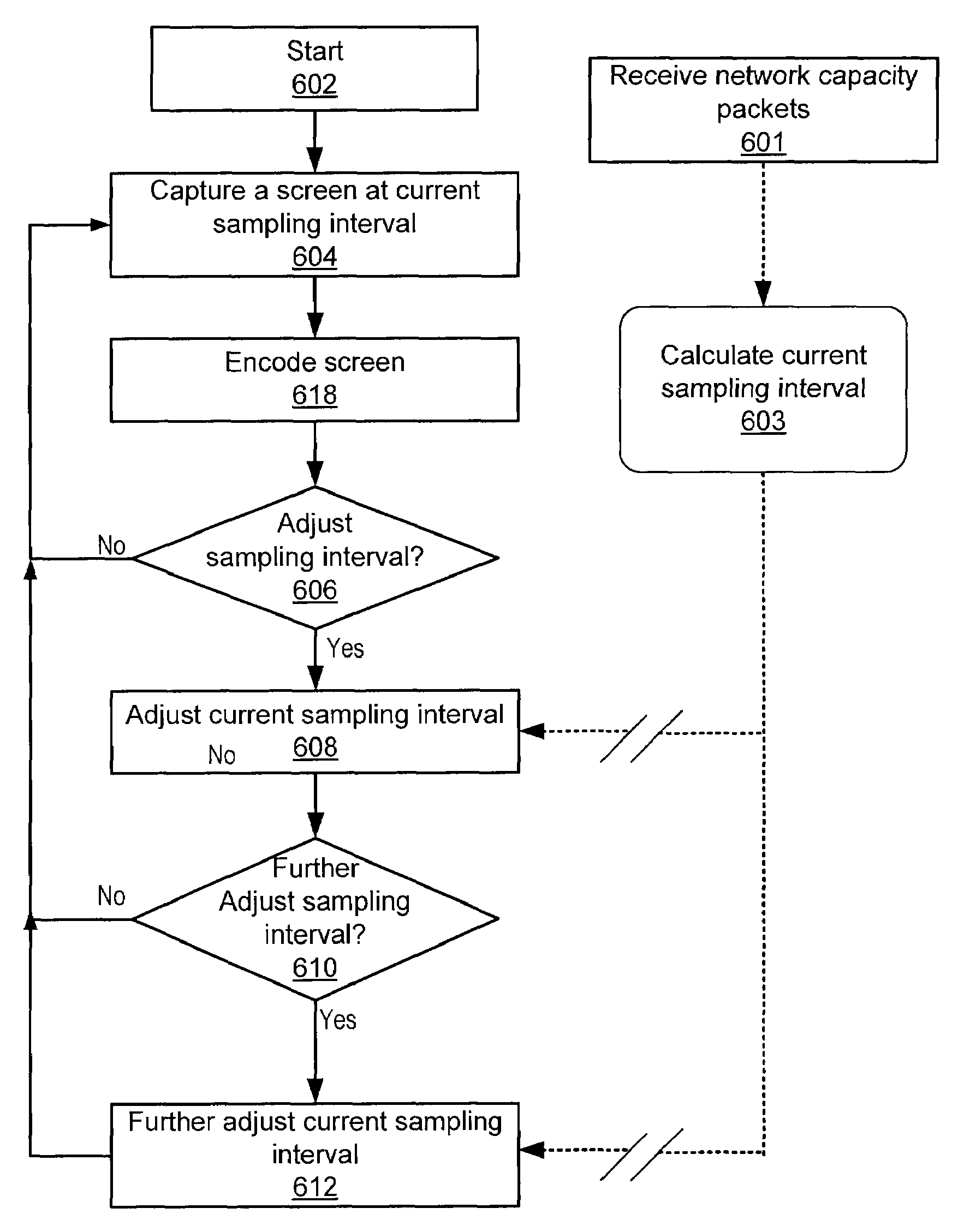
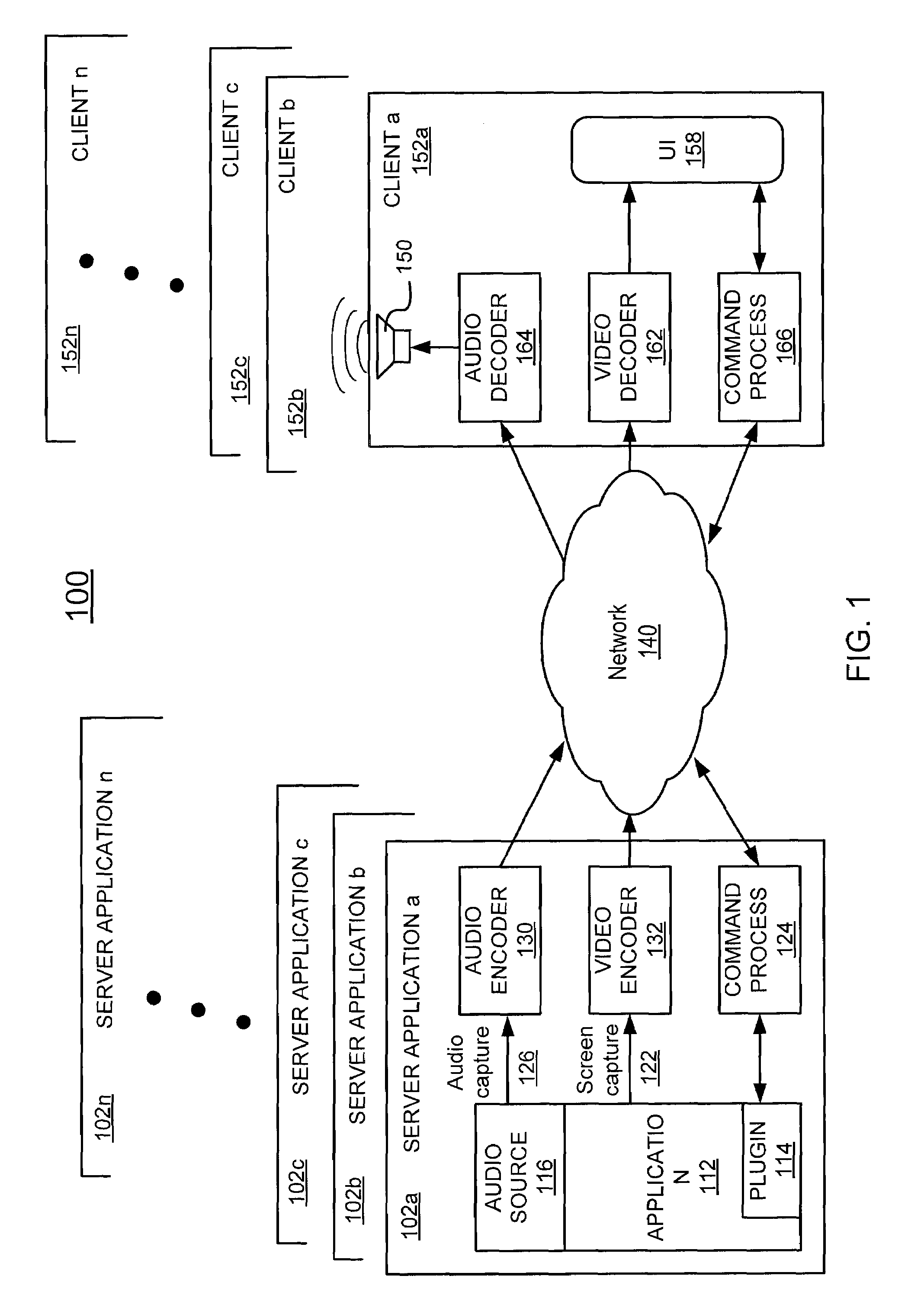
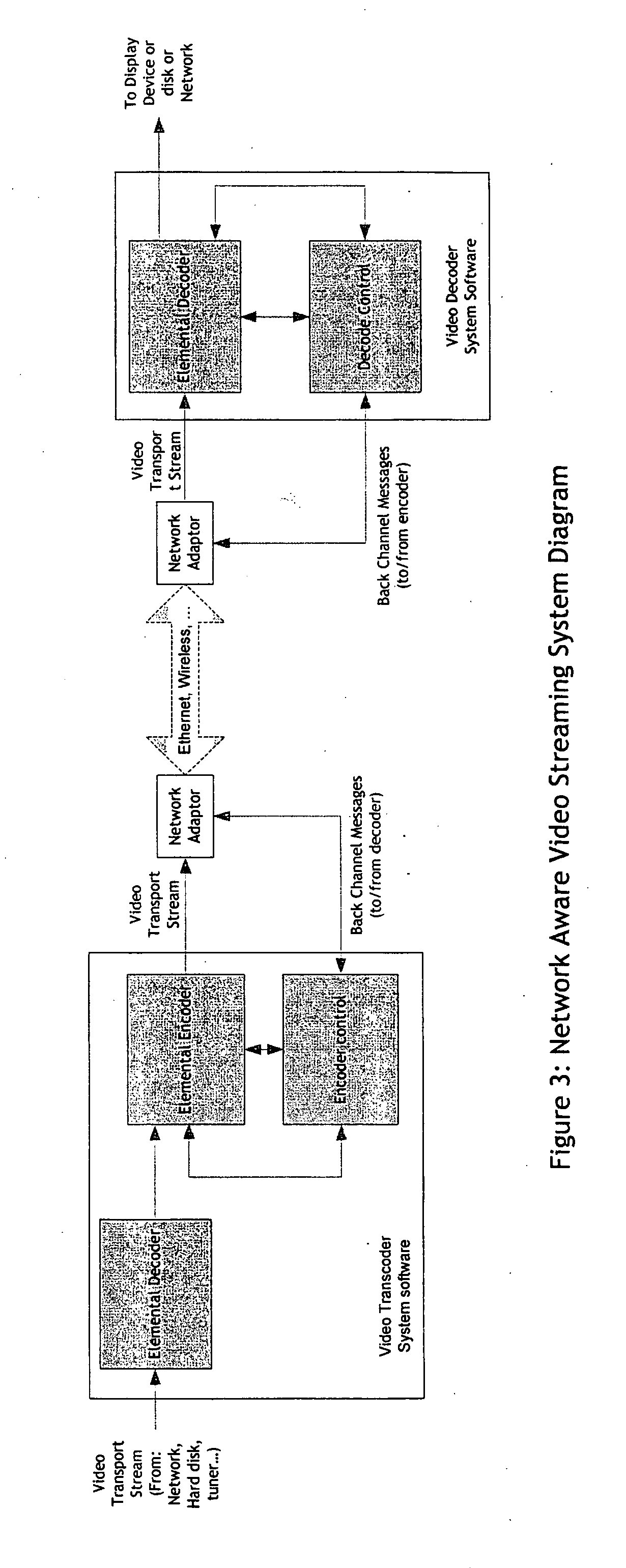
Network-Based Dynamic Encoding
ActiveUS20080101466A1Color television with pulse code modulationPulse modulation television signal transmissionVideo encodingIntra-frame
A network-based video encoding and decoding system encodes and decodes remotely displayed user application data on a centralized desktop computer. Remotely displayed user application data are screen captures of a browsing application run by the centralized desktop computer on user's behalf. The encoding system optimizes its encoding performance using back channel information which includes real time network capacity information and decoder feedback. The encoding system consults a back channel information manager to dynamically adjust encoding parameters. Based on the real time network capacity information received, the encoding system adjusts its capturing sampling rate. Based on encoding errors identified by the decoding system, the encoding system selectively re-send previously encoded frames / blocks, or send intra frames on demand to allow the decoding system to correct encoding errors. In response to encoding customization requests from the decoding system, the encoding system adjusts its encoding parameters to meet such requests.
Owner:OTELLO CORP ASA
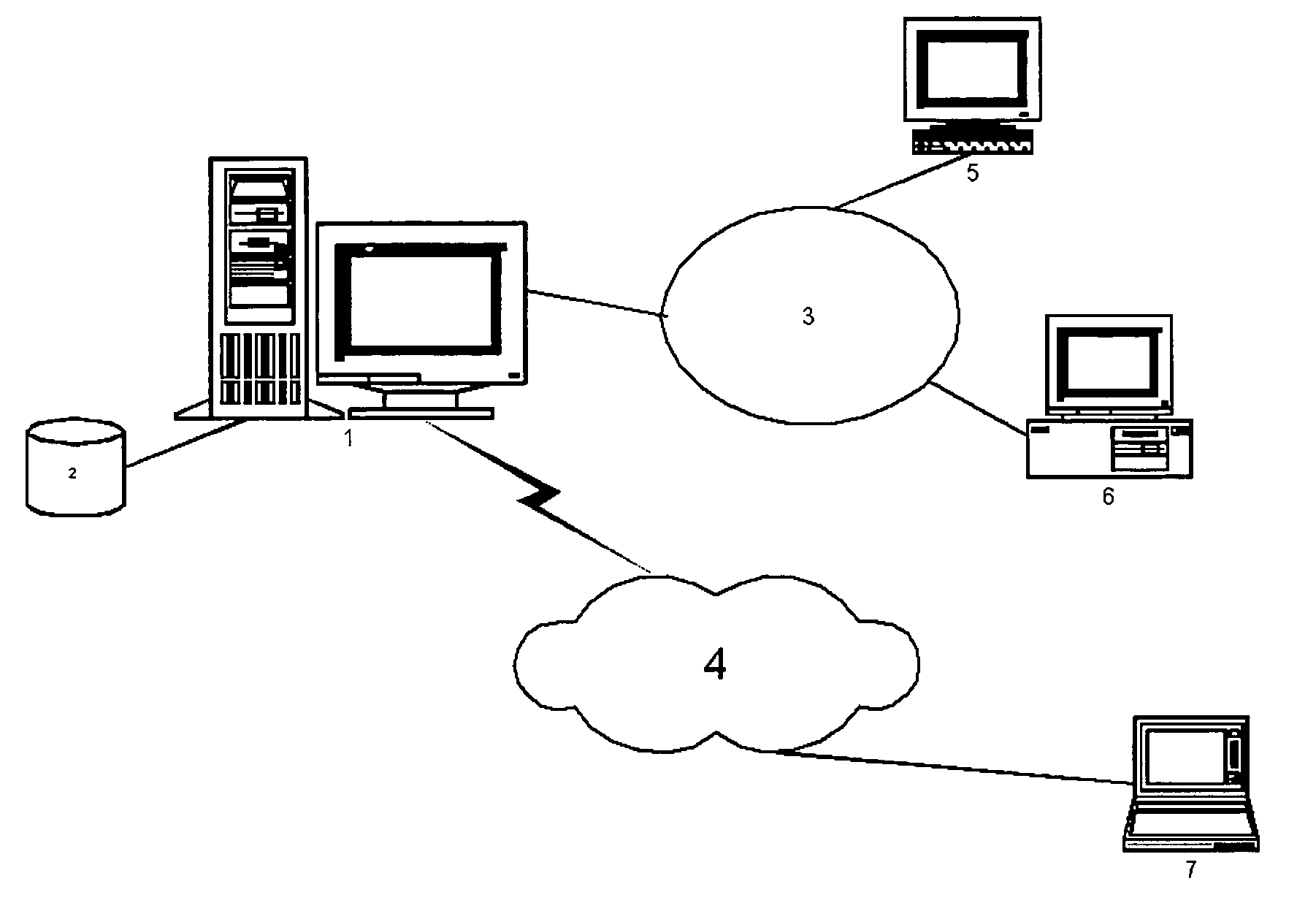
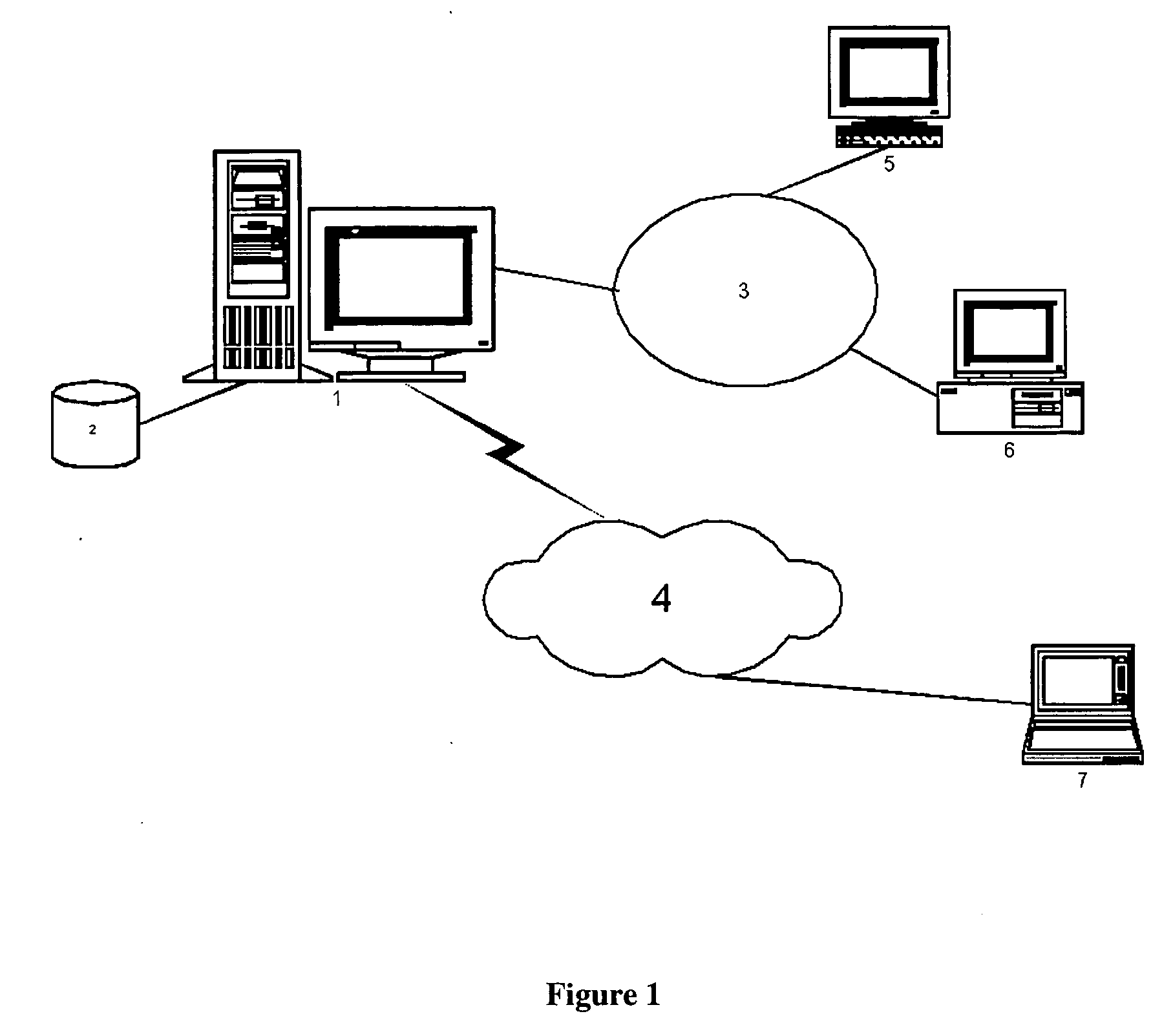
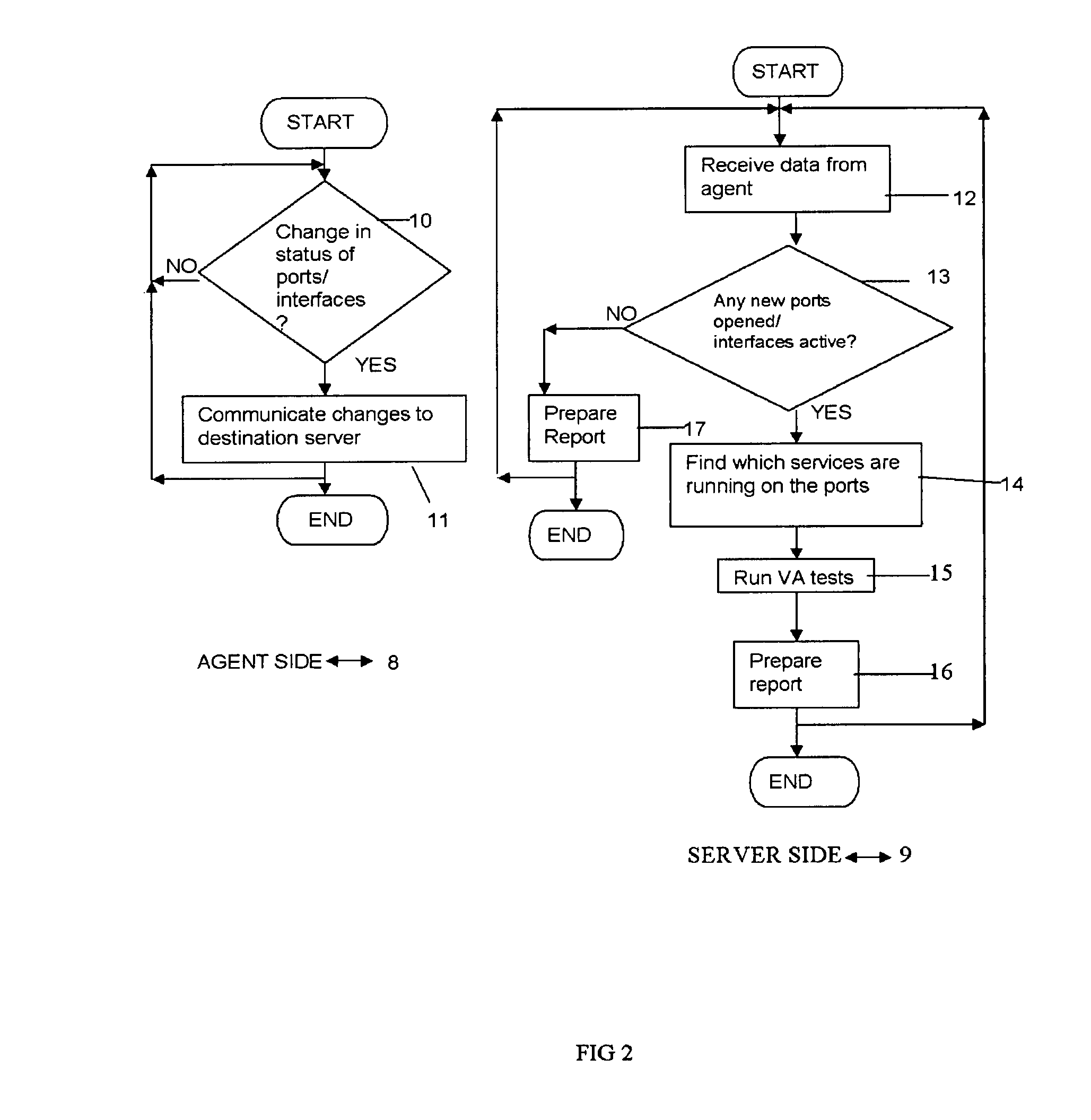
System for real-time network-based vulnerability assessment of a host/device via real-time tracking, vulnerability assessment of services and a method thereof
ActiveUS20050005169A1Not consuming high bandwidth and other resourceError preventionFrequency-division multiplex detailsComputer hardwareState variation
A system for real-time vulnerability assessment of a host / device, said system comprising an agent running on the host / device. The agent includes a a first data structure for storing the status of interfaces and ports on the interfaces of the host / device. An n executable agent module is coupled to the first data structure to track the status of interfaces and ports on the interfaces of the host / device and to store the information, as entries in said first data structure. The executable agent module compares the entries to determine a change in the status of interfaces and / or of ports on the interfaces of the host / device. A remote destination server is provided that includes a second data structure for storing the status of interfaces and the ports on the interfaces of the host / device. An executable server module is coupled to the second data structure to receive the information communicated by the agent executable module of the agent on the host / device. The executable server module stores the received information as entries in the second data structure wherein the entries indicate the state of each of the ports on each of the active interfaces of the host / device as received. The executable server module compares the entries in said data structures to determine the change in the status of interfaces and ports on the interfaces of the host / device. The executable server module runs vulnerability assessment tests on the host / device in the event of a change in the status of interface / ports.
Owner:RPX CORP
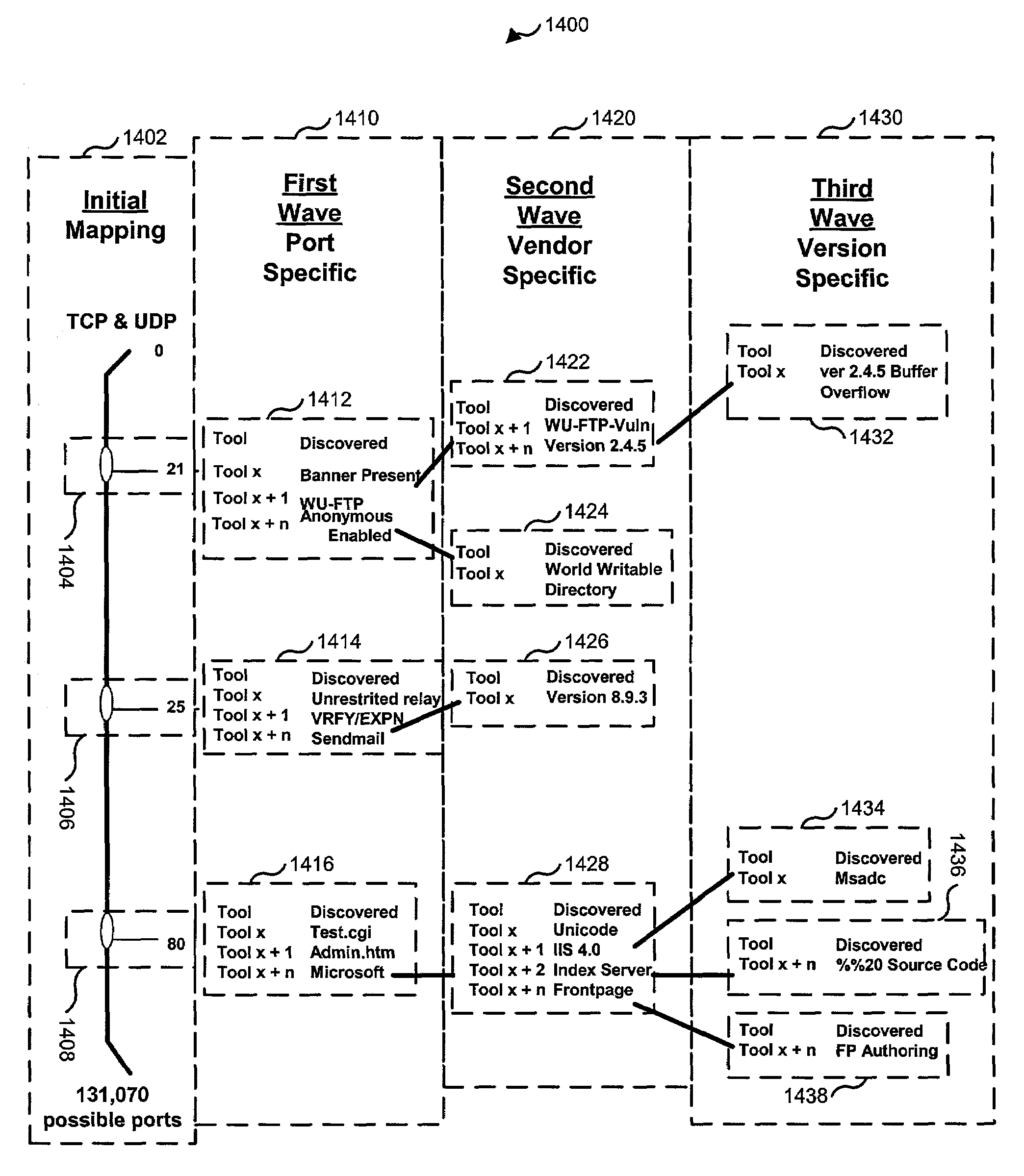
Network security testing
ActiveUS7325252B2Improve viewing effectShort working hoursMemory loss protectionError detection/correctionSecurity solutionWork period
To answer the security needs of the market, a preferred embodiment was developed. A preferred embodiment provides real-time network security vulnerability assessment tests, possibly complete with recommended security solutions. External vulnerability assessment tests can emulate hacker methodology in a safe way and enable study of a network for security openings, thereby gaining a true view of risk level without affecting customer operations. Because this assessment can be performed over the Internet, both domestic and worldwide corporations benefit. A preferred embodiment's physical subsystems combine to form a scalable holistic system that can be able to conduct tests for thousands of customers any place in the world. The security skills of experts can be embedded into a preferred embodiment systems and automated the test process to enable the security vulnerability test to be conducted on a continuous basis for multiple customers at the same time. A preferred embodiment can reduce the work time required for security practices of companies from three weeks to less than a day, as well as significantly increase their capacity. Component subsystems typically include a Database, Command Engine, Gateway, multiple Testers, Report Generator, and an RMCT.
Owner:ALERT LOGIC
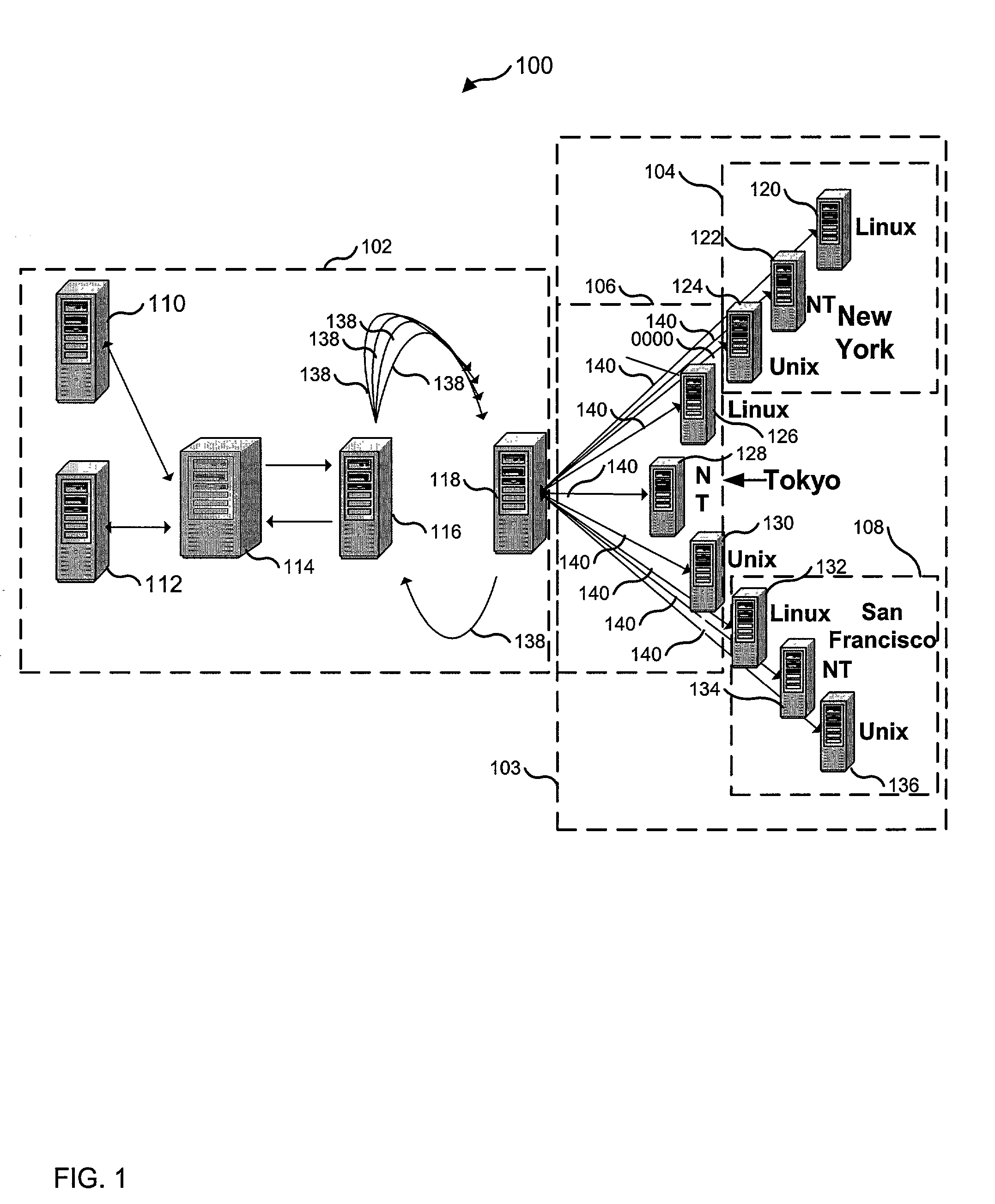
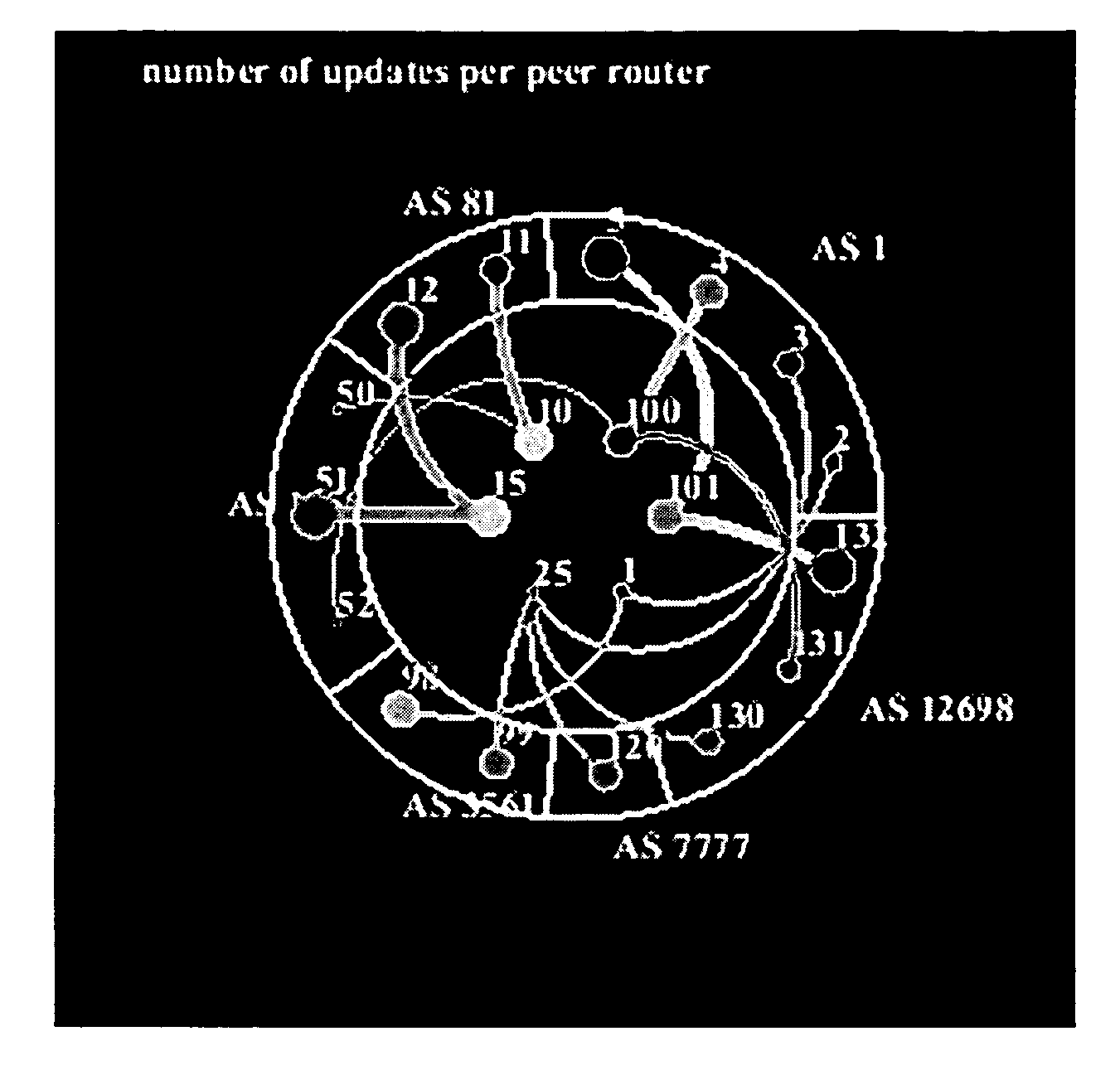
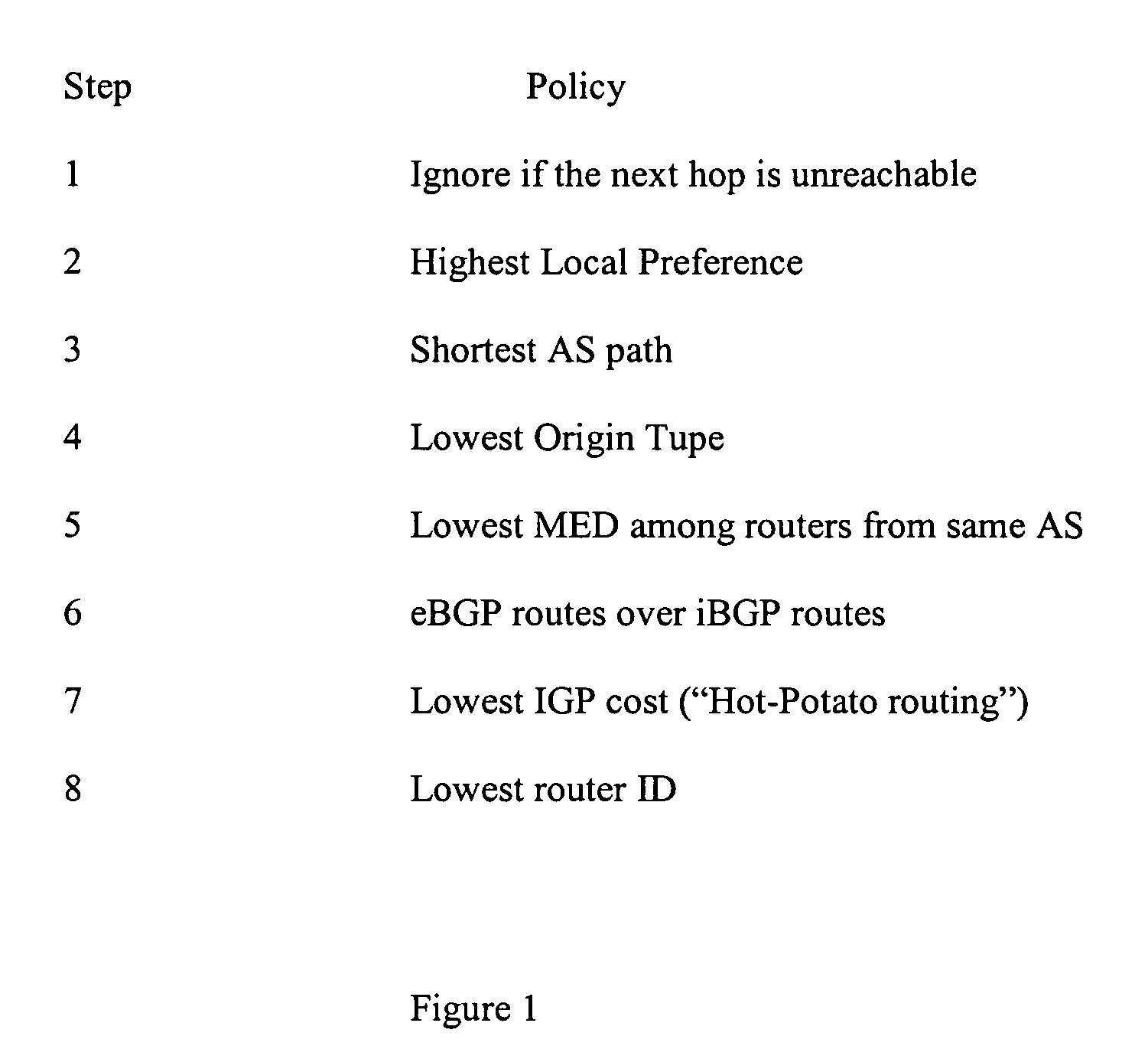
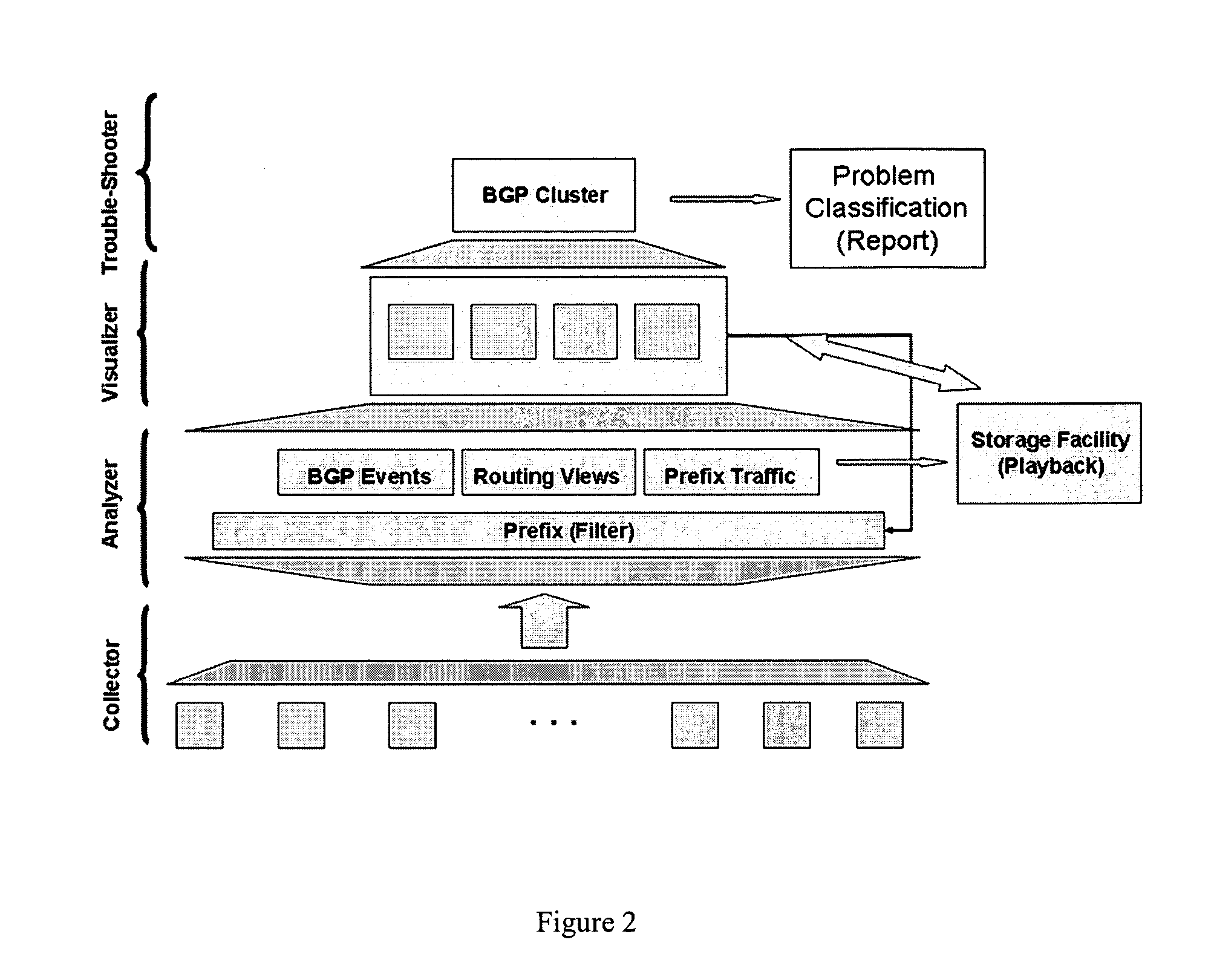
Method for real-time visualization of BGP analysis and trouble-shooting
InactiveUS7945658B1Efficient identificationEfficient reportingError preventionTransmission systemsThe InternetProblem identification
The present invention comprises a multi-tier system. Major goals of the system are to 1) clearly visualize BGP dynamics and alert / report important deviation of BGP dynamics to avoid overwhelming the operators with too much information and 2) analyze the root cause of the problems by using a multi-tier approach, with a light-computational analysis and high-level classification for a real-time problem identification followed by a more rigorous off-line analysis for a further and more detailed trouble shooting. An example embodiment is provided that comprises four modules. The first module comprises a distributed family of collectors in charge of collecting real-time network information. The second module filters out non-relevant prefixes and extracts and profiles key features of the network information. The third module monitors BGP activity from both an Internet-AS and single-AS perspectives by displaying the data in real time and highlighting major shifts or divergence from historical baselines with comprehensive layouts. The forth module is run off-line to focus on a few relevant events that are selected through the first three modules. This is usually a time-consuming phase of the process due to the different temporal and / or spatial correlation that must be run across several sets of data. During this phase, the system can spend more time to better identify the real cause of the problem.
Owner:THE BOEING CO
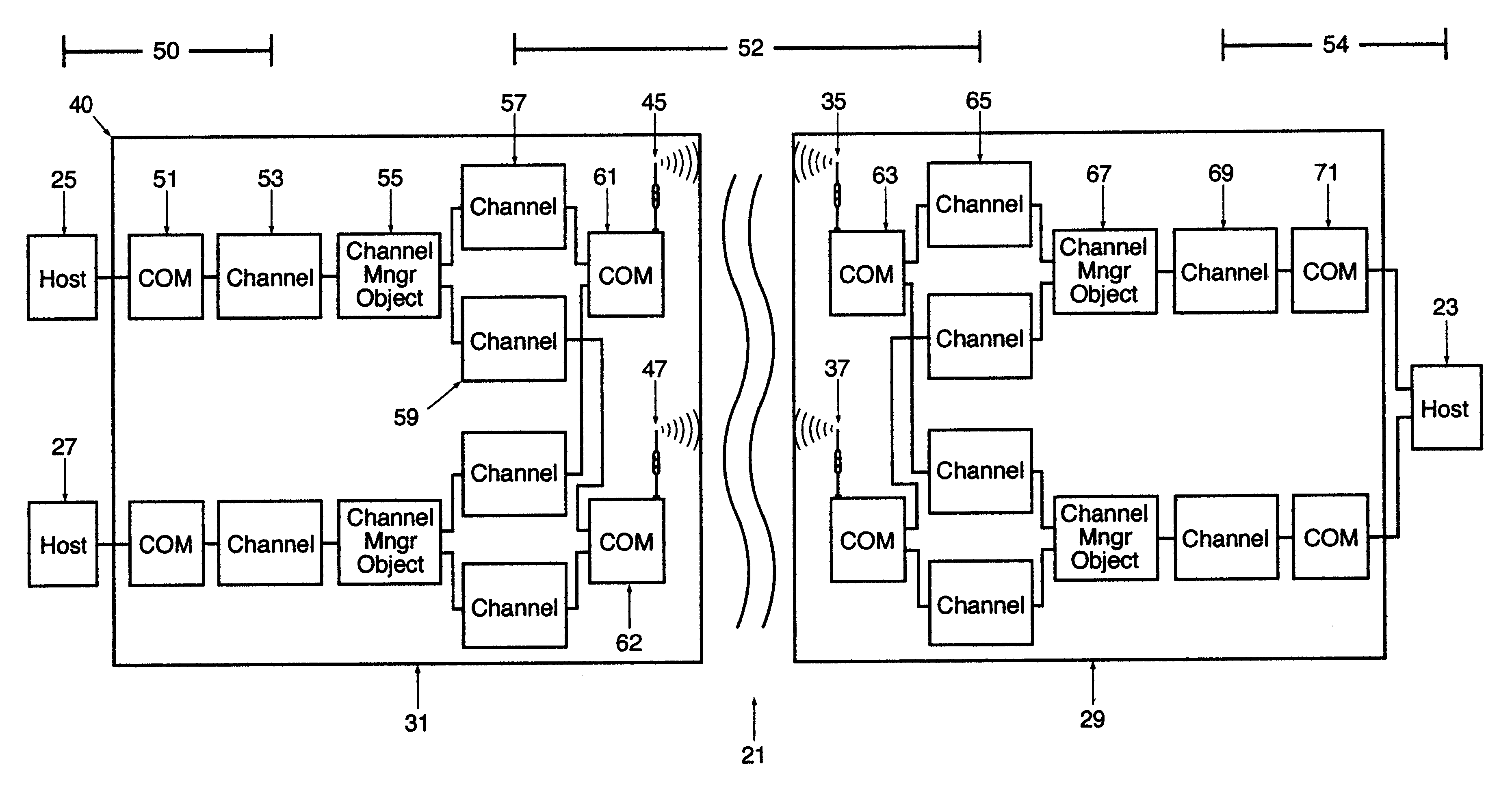
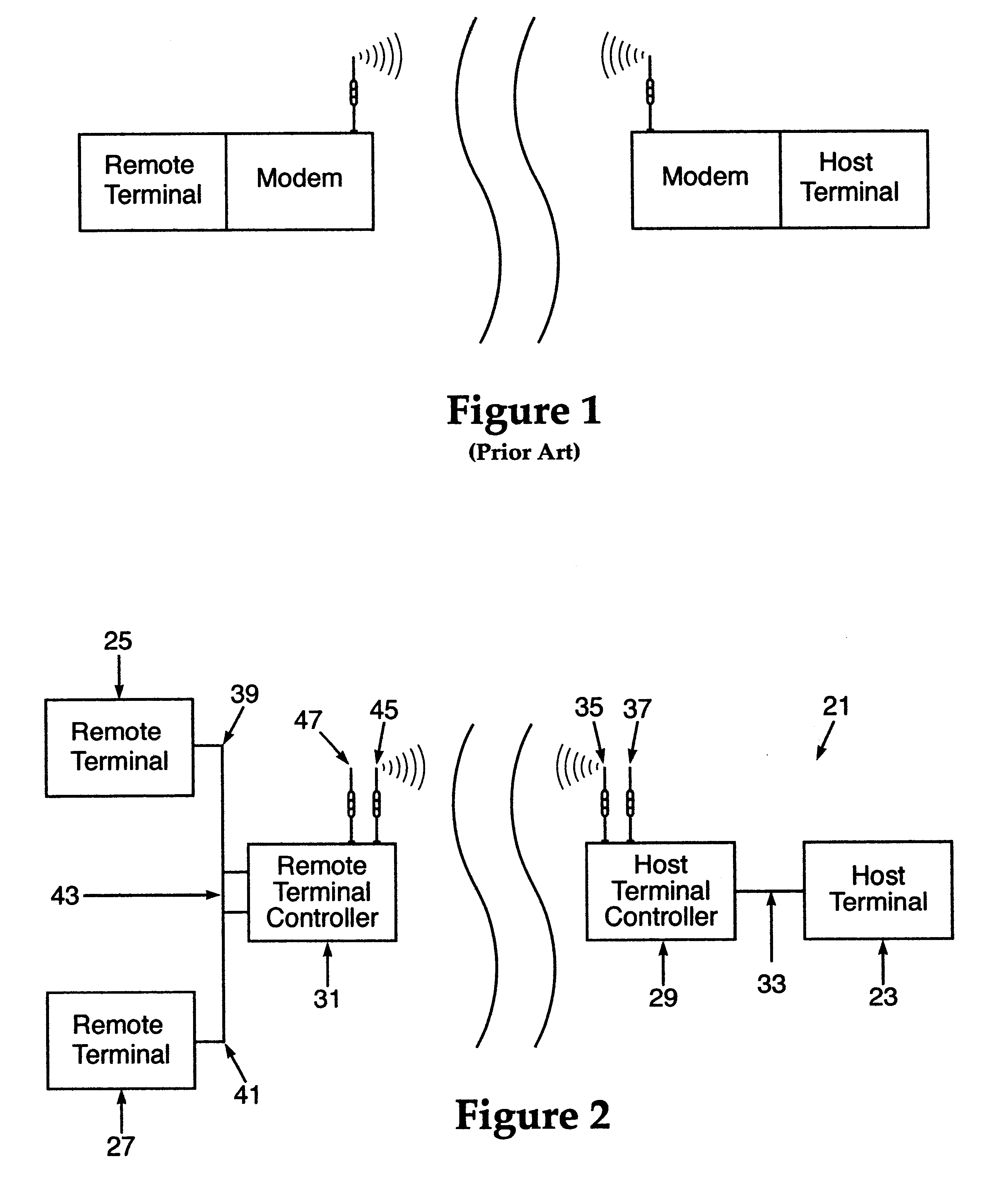
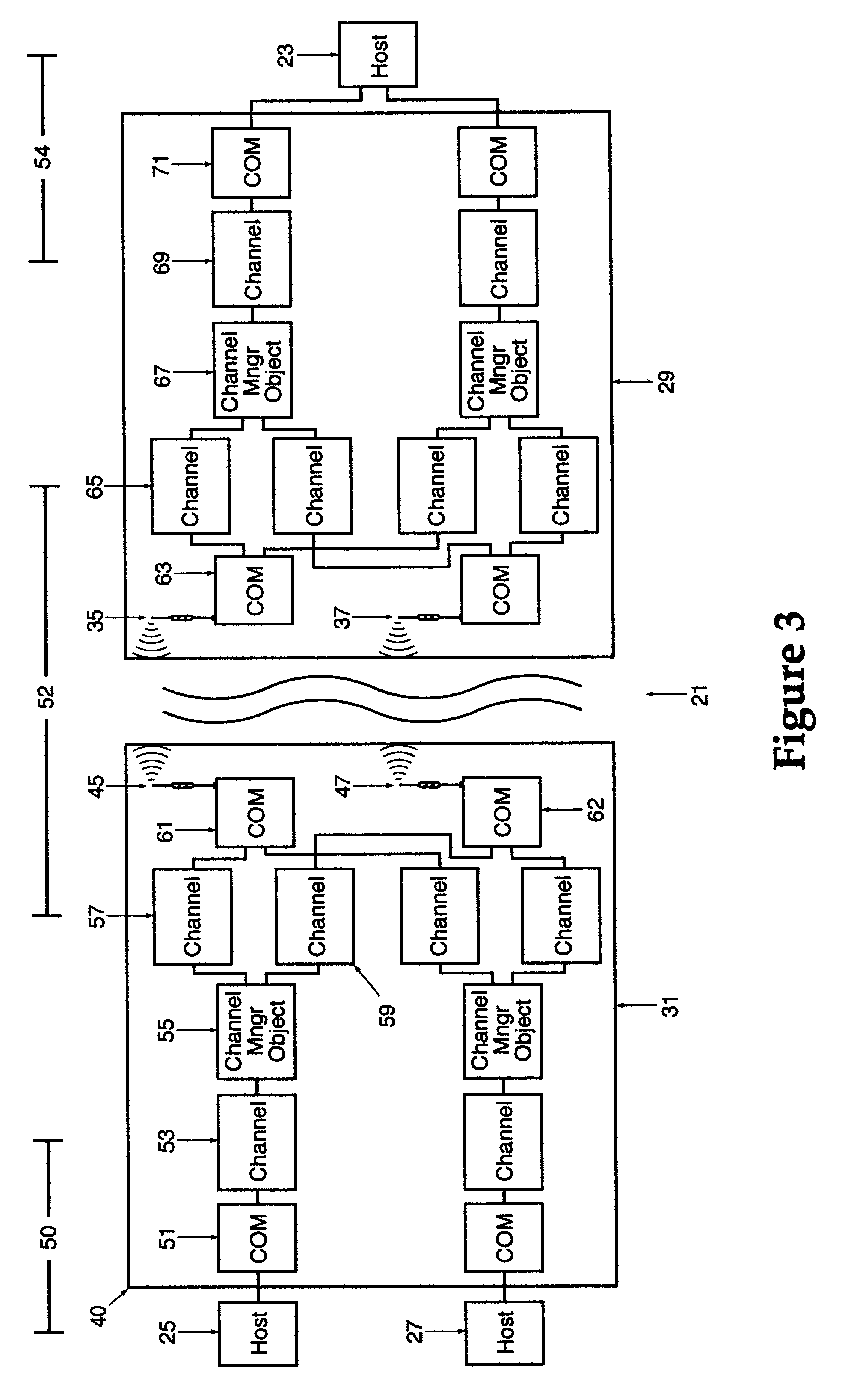
Method and apparatus for transportation of data over a managed wireless network using unique communication protocol
InactiveUS6587441B1Multiplex system selection arrangementsError prevention/detection by using return channelWireless controlWireless mesh network
A wireless, redundant, secure, real-time, network for a proprietary interactive data transfer system having a remote terminal and a host data center, such as an automated teller banking system, is disclosed. Controllers for the remote terminal and the host data center receive the proprietary language messages and packetize and encrypt the messages for sending over the best wireless carrier among the plurality of wireless carriers the controllers are connected to. The wireless control protocol monitors the communications to provide for selection of the most reliable communication carrier for any part of a transmission. Each network segment of the signal path has at least one state-controlled gate which reports the status of that signal path. Real time transmission and acknowledgment of securely packetized messages on wireless communications carriers via an object oriented coding control application provides for reliable datagram transfer independent of the reliability of any one signal path.
Owner:MAYFAIR WIRELESS
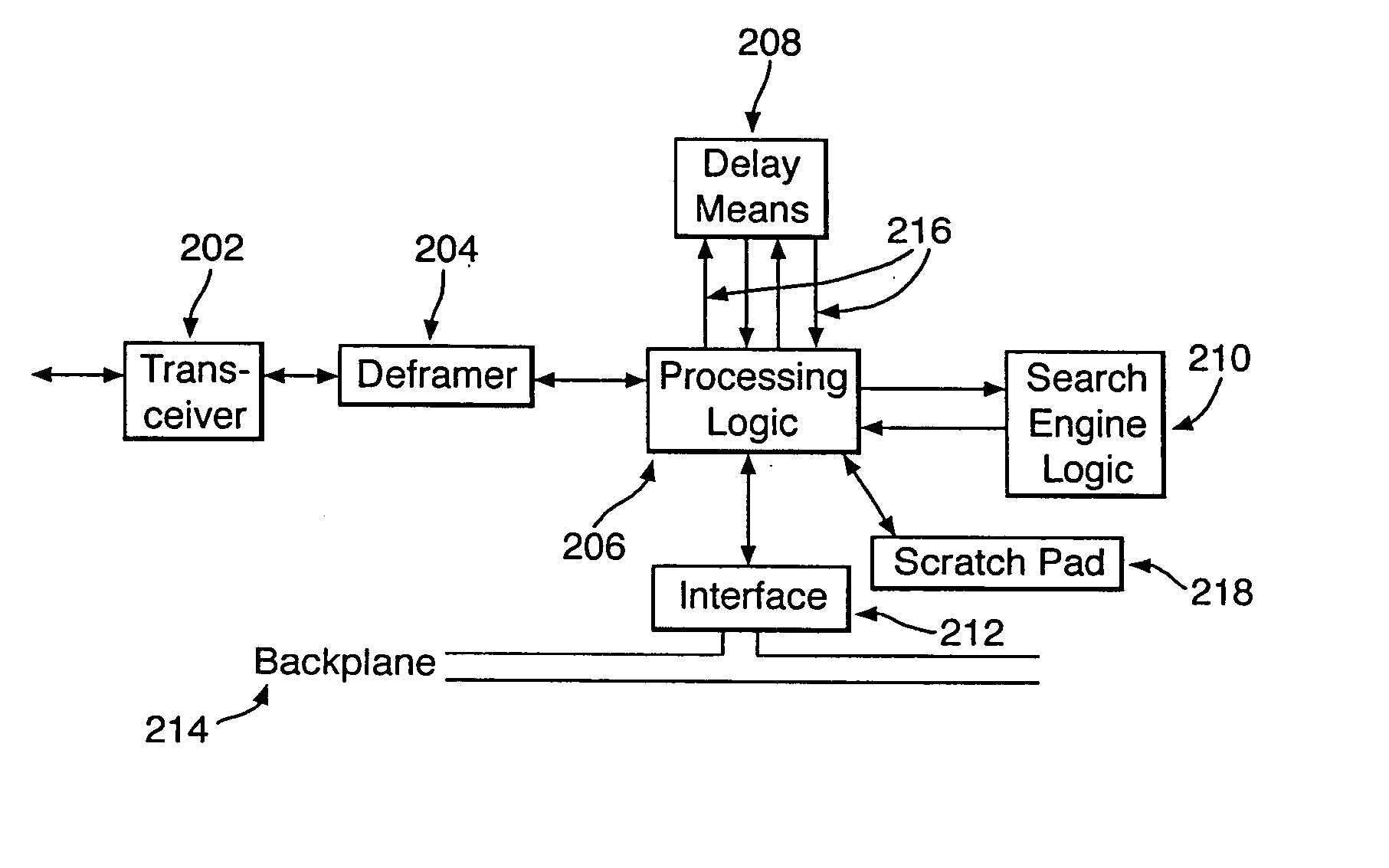
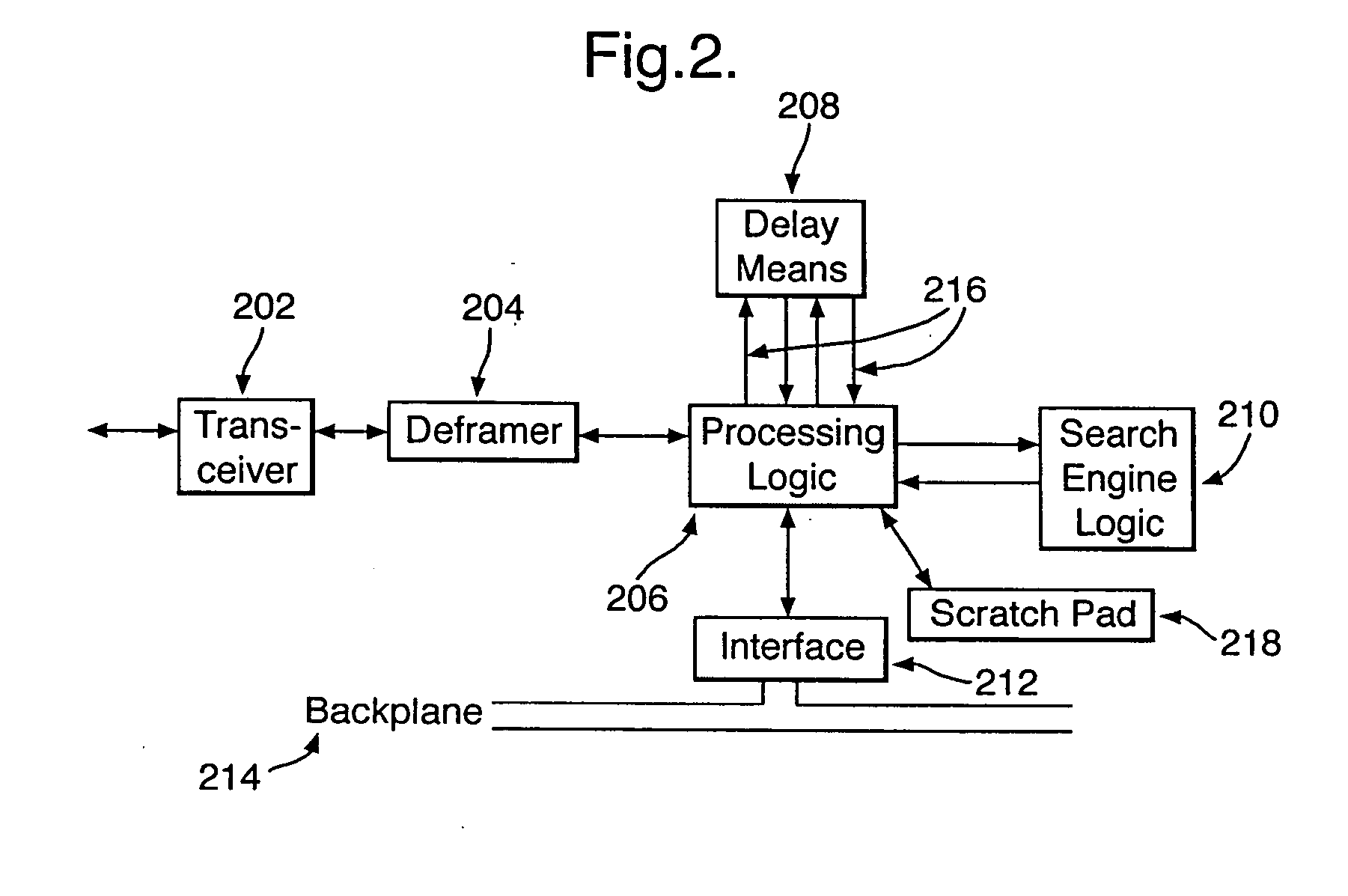
Real-time network monitoring and security
ActiveUS20050108573A1Easy programmingEasy maintenanceWeb data indexingMemory loss protectionHigh bandwidthWire speed
There is provided a hardware device for monitoring and intercepting data packetized data traffic at full line rate. In preferred high bandwidth embodiments, full line rate corresponds to rates that exceed 100 Mbytes / s and in some cases 1000 Mbytes / s. Monitoring and intercepting software, alone, is not able to operate on such volumes of data in real-time. A preferred embodiment comprises: a data delay buffer (208) with multiple delay outputs (216); a search engine logic (210) for implementing a set of basic search tools that operate in real-time on the data traffic; a programmable gate array (206); an interface (212) for passing data quickly to software sub-systems; and control means for implementing software control of the operation of the search tools. The programmable gate array (206) inserts the data packets into the delay buffer (208), extracts them for searching at the delay outputs and formats and schedules the operation of the search engine logic (210). One preferred embodiment uses an IP co-processor as the search engine logic.
Owner:BAE SYSTEMS PLC
Apparatus and methods for real-time multimedia network traffic management and control in wireless networks
InactiveUS8868725B2Multiple digital computer combinationsData switching networksWireless mesh networkNetwork management
Owner:KENT STATE UNIV
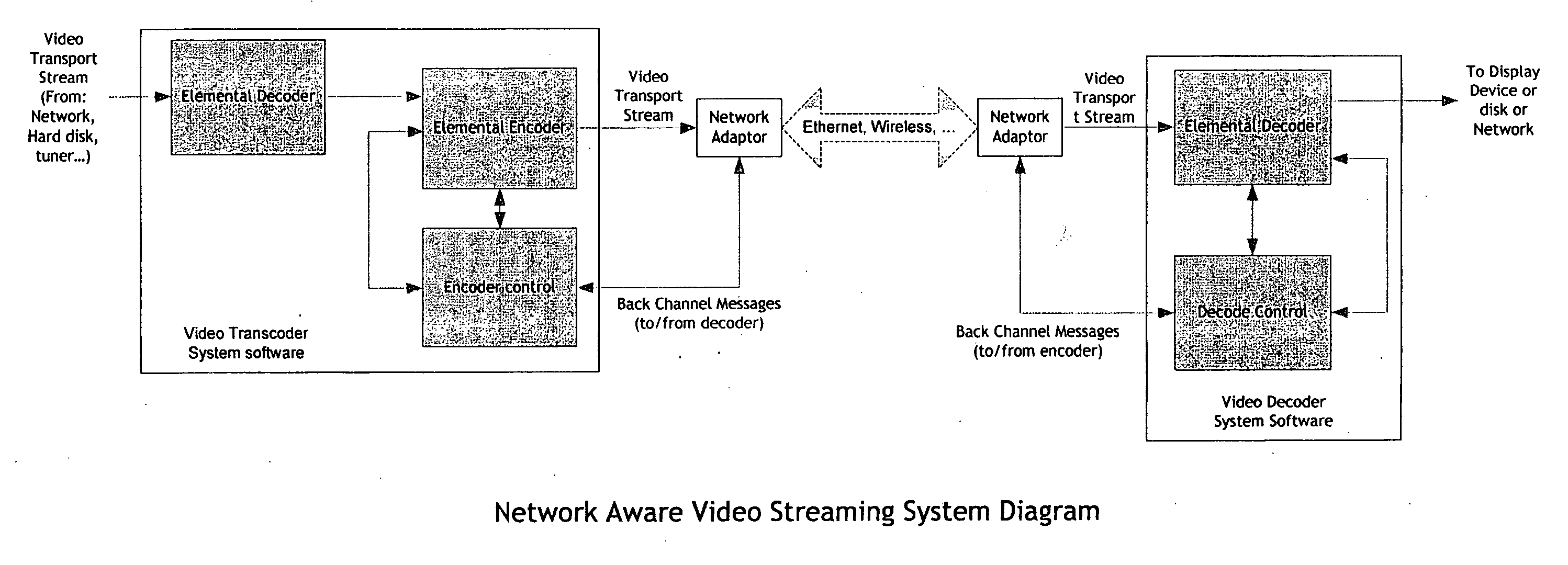
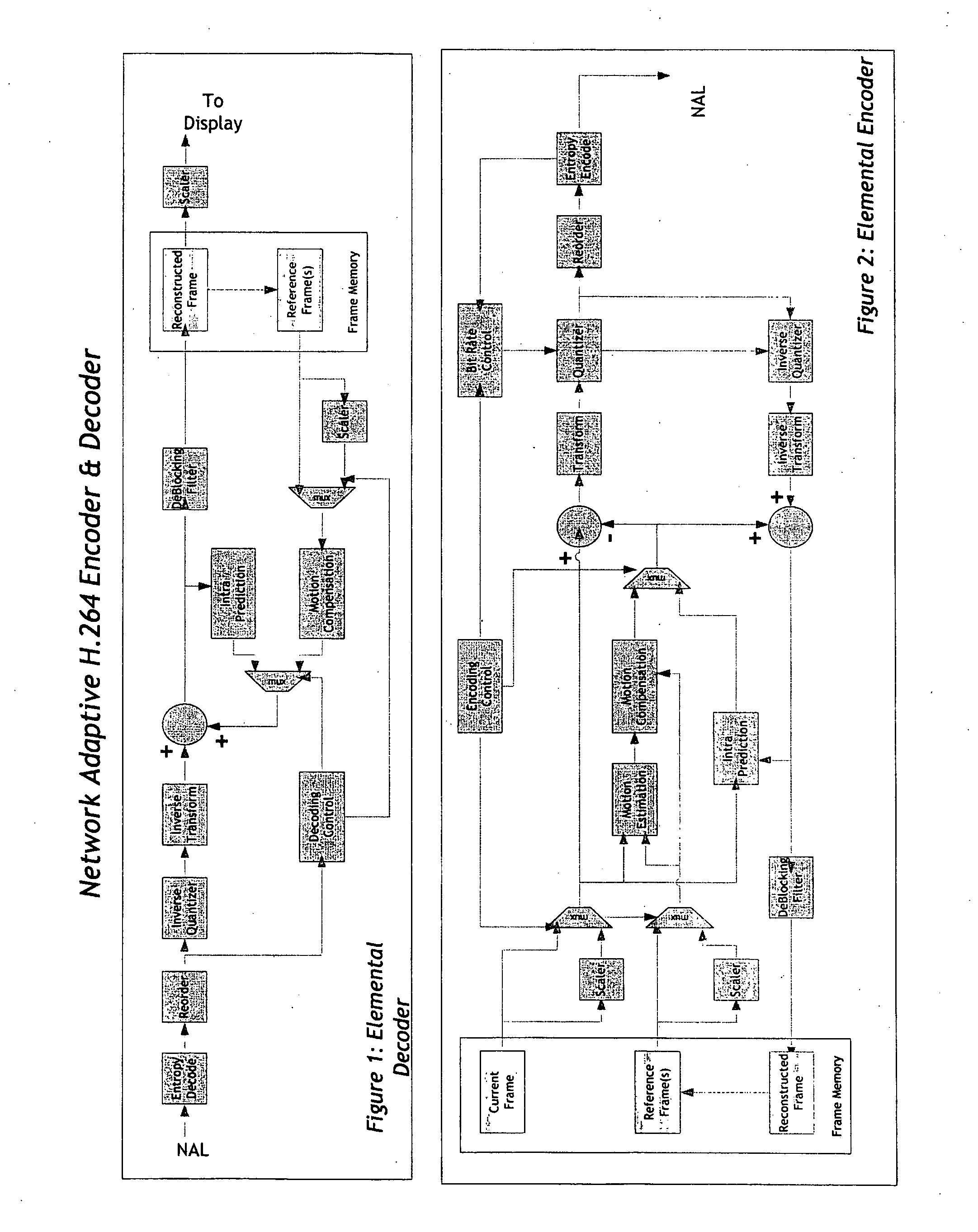
Real-time network adaptive digital video encoding/decoding
ActiveUS20080084927A1Lowering scale factorLow data ratePulse modulation television signal transmissionPicture reproducers using cathode ray tubesDigital videoImaging quality
A method for real time video transmission over networks with varying bandwidth is described. Image quality is maintained even under degrading network performance conditions through the use of image scaling in conjunction with block based motion compensated video coding (MPEG2 / 4, H.264, et. Al.). The ability to quickly switch resolutions without decreasing reference frame correlation is shown enabling a fast switch to reduce the required bandwidth for stable image quality.
Owner:ELEMENTAL TECH LLC
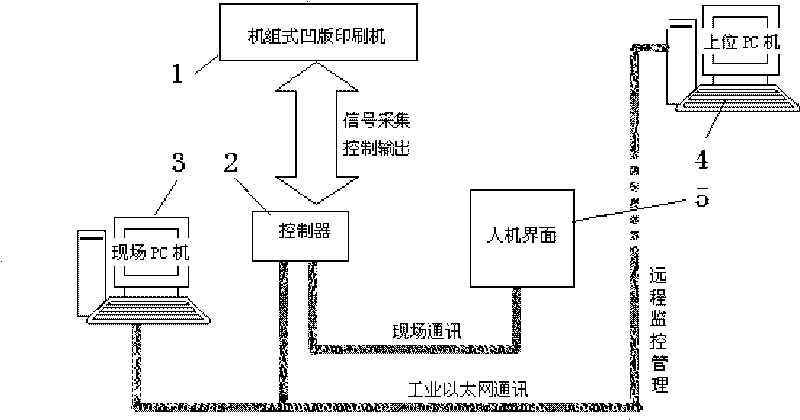
Information management system for on-line production of printing machine and method thereof
ActiveCN101713994AImprove efficiencyChange efficiencyData switching by path configurationTotal factory controlEmbedded systemReal time networks
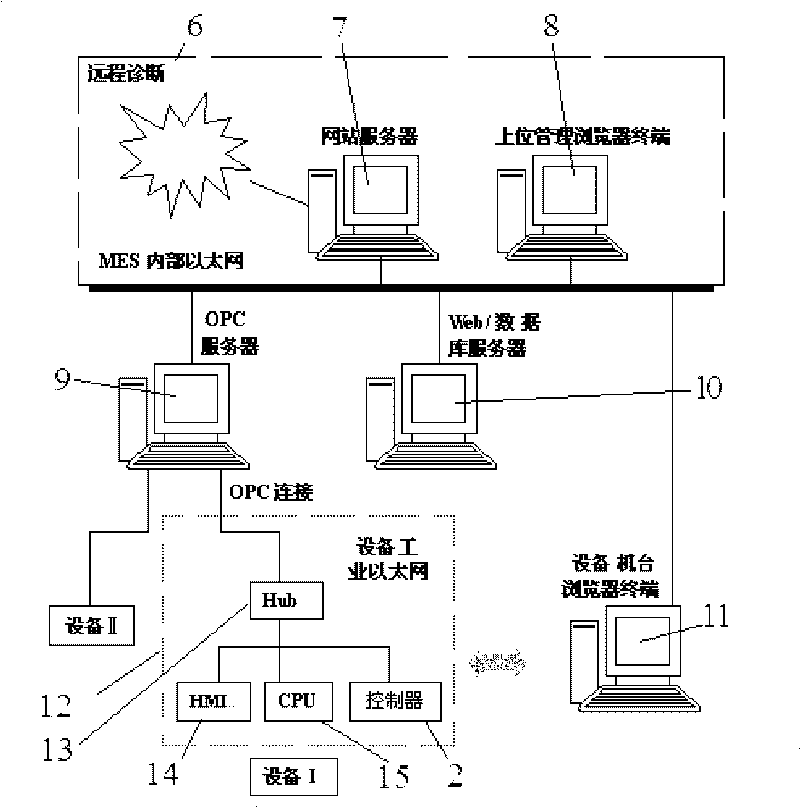
The invention discloses an information management system for on-line production of a printing machine, which is characterized in that a web server and an upper management browser terminal which are mutually connected are arranged in an MES internal Ethernet to be used for realizing on-line remote diagnosis and maintenance; the MES internal Ethernet is respectively connected with an OPC server and an equipment station browser terminal, and the MES internal Ethernet is also connected with an equipment industrial Ethernet of a plurality of printing machine units through the OPC server; an Hub, an HMI, a CPU and a controller are arranged in the equipment industrial Ethernet; the Hub is externally connected with the OPC server; the Hub is respectively connected with the HMI, the CPU and the controller; and the controller is connected with a PLC control system in the printing machine equipment. The invention also discloses a method of on-line control and real-time data acquisition of the control system. The invention realizes the real-time network monitoring, parameter reporting, production management and analytic statistics under the B / S structure in an Ethernet communication mode, and realizes multi-browser and multi-user operation.
Owner:SHAANXI BEIREN PRINTING MACHINERY
Intelligent garbage recycling bin
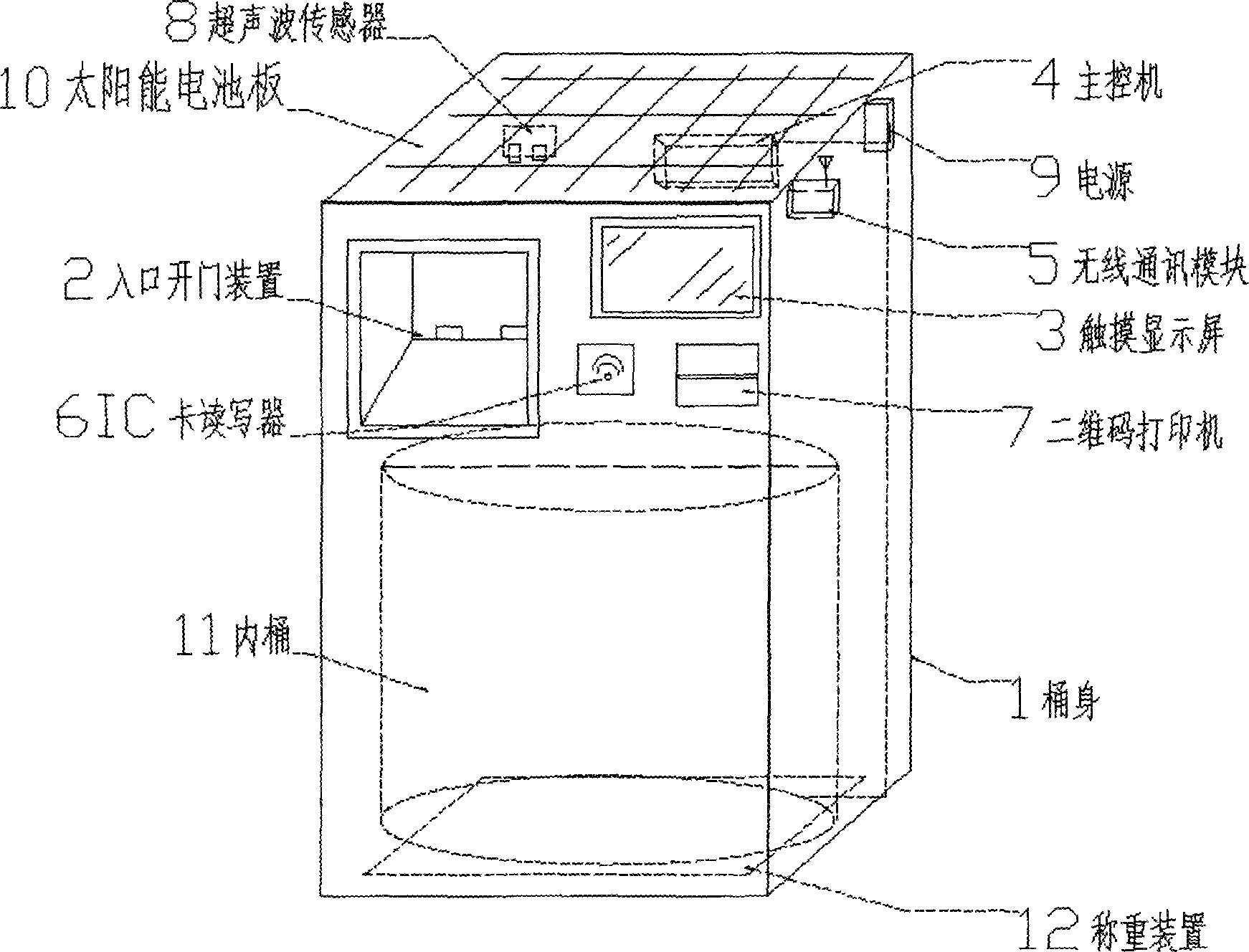
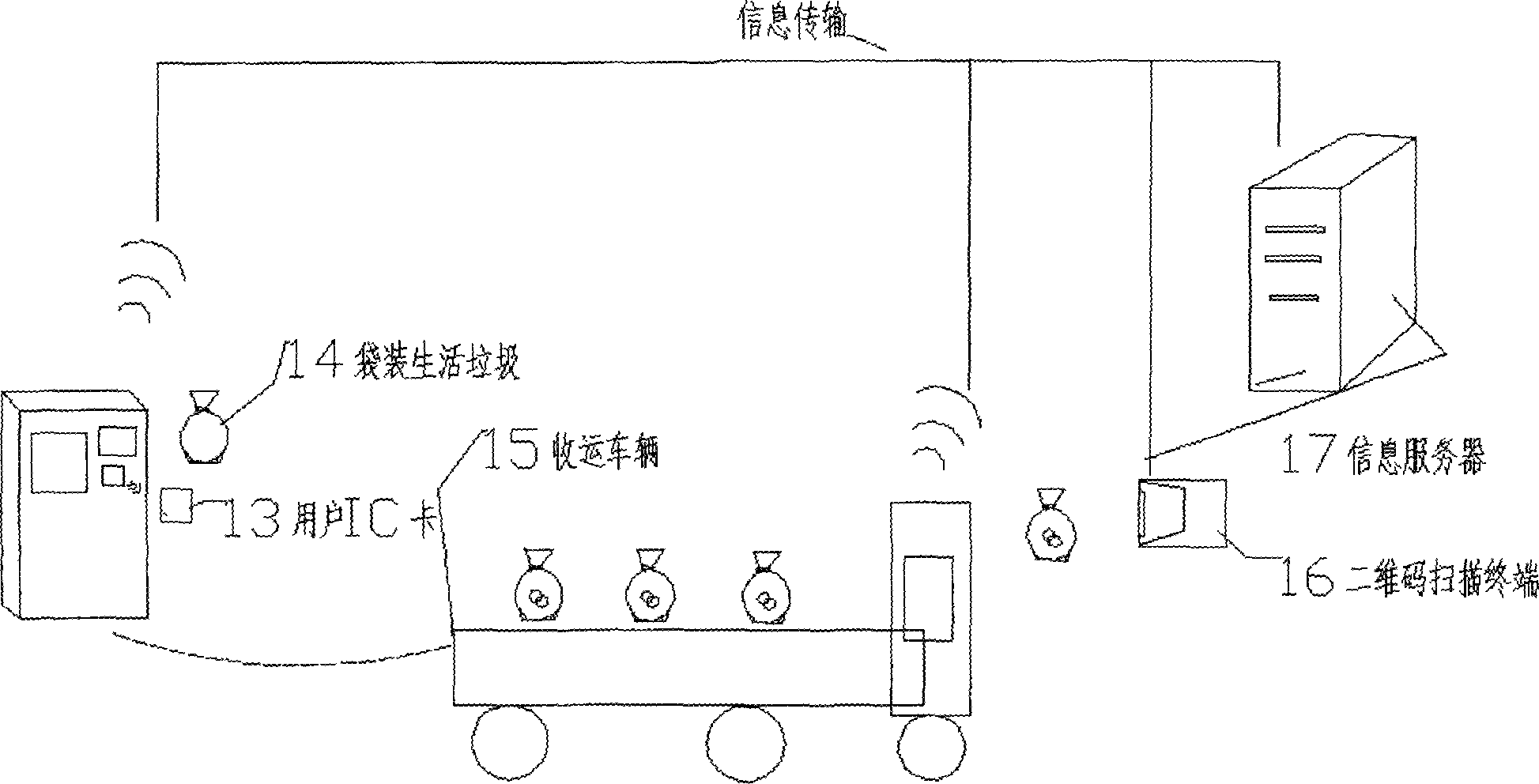
The invention discloses an intelligent garbage classified recycling bin, which is provided with a closed garbage entrance door shield, wherein the closed garbage entrance door shield is capable of identifying an RFID card or bar codes for indicating a membership, and is also capable of automatically closing a recycling bin door shield, and the garbage bin is networked with a center system in real time, and can instantly realize member point conversion input according to the weight of the garbage, and can also automatically inform the center system of assigning a recycling vehicle to carry out garbage bin cleaning before the capacity of the garbage bin reaches the upper limit. The intelligent garbage classified recycling bin belongs to application of internet of things in the field of environment protection. The intelligent garbage classified recycling bin mainly consists of six parts which are respectively an identity identifying module, a garbage weighing module, a garbage bin capacity detecting module, a display and input and output module, a wireless networking module and an energy supply module. The recycle of classified garbage becomes orderly and convenient due to excellent human-machine interacting interface and experience and real-time networking state monitoring.
Owner:郑皓元 +1
Sina microblog-based user grade sequencing algorithm
InactiveCN102663101AEfficient acquisitionImprove rationalitySpecial data processing applicationsReference modelReal-time data
The invention discloses a Sina microblog-based user grade sequencing algorithm. The Sina microblog-based user grade sequencing algorithm comprises the following steps: a) capturing real-time data in Sina microblogs; b) determining restraining factors which affect user grade sequencing in the Sina microblogs through data analysis; c) establishing a user influence power reference model in the user grade sequencing; d) establishing a user liveness reference model in the user grade sequencing; and e) getting a user weight calculation model by weighting the user influence power and the user liveness models, and realizing the user grade sequencing of the Sina microblogs by utilizing the model. The Sina microblog-based user grade sequencing algorithm can be used in the field of research of social networks. The Sina microblog-based user grade sequencing algorithm disclosed by the invention has higher rationality and smaller time loss, and is suitable for real-time network environments.
Owner:BEIJING JIAOTONG UNIV +1
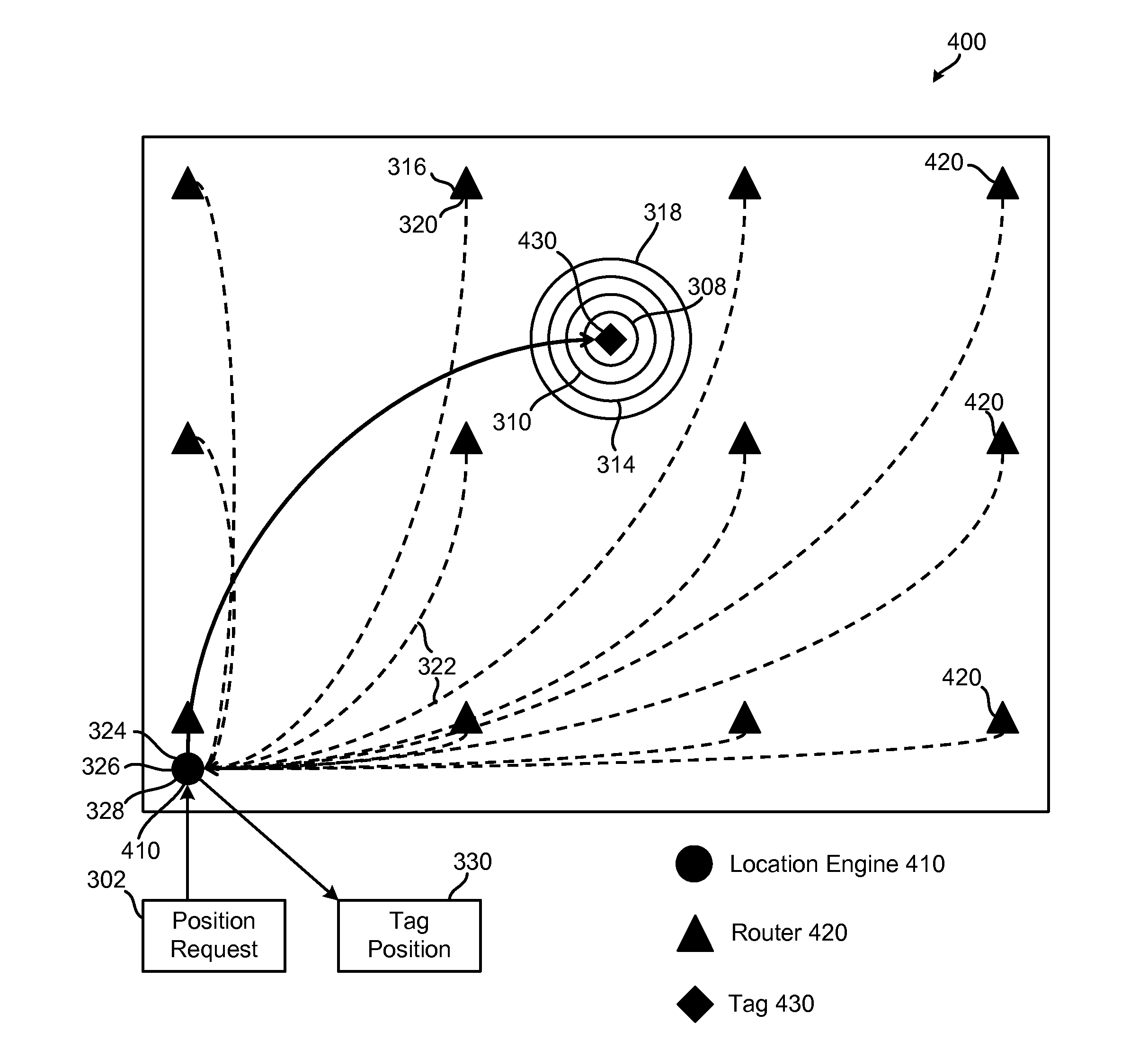
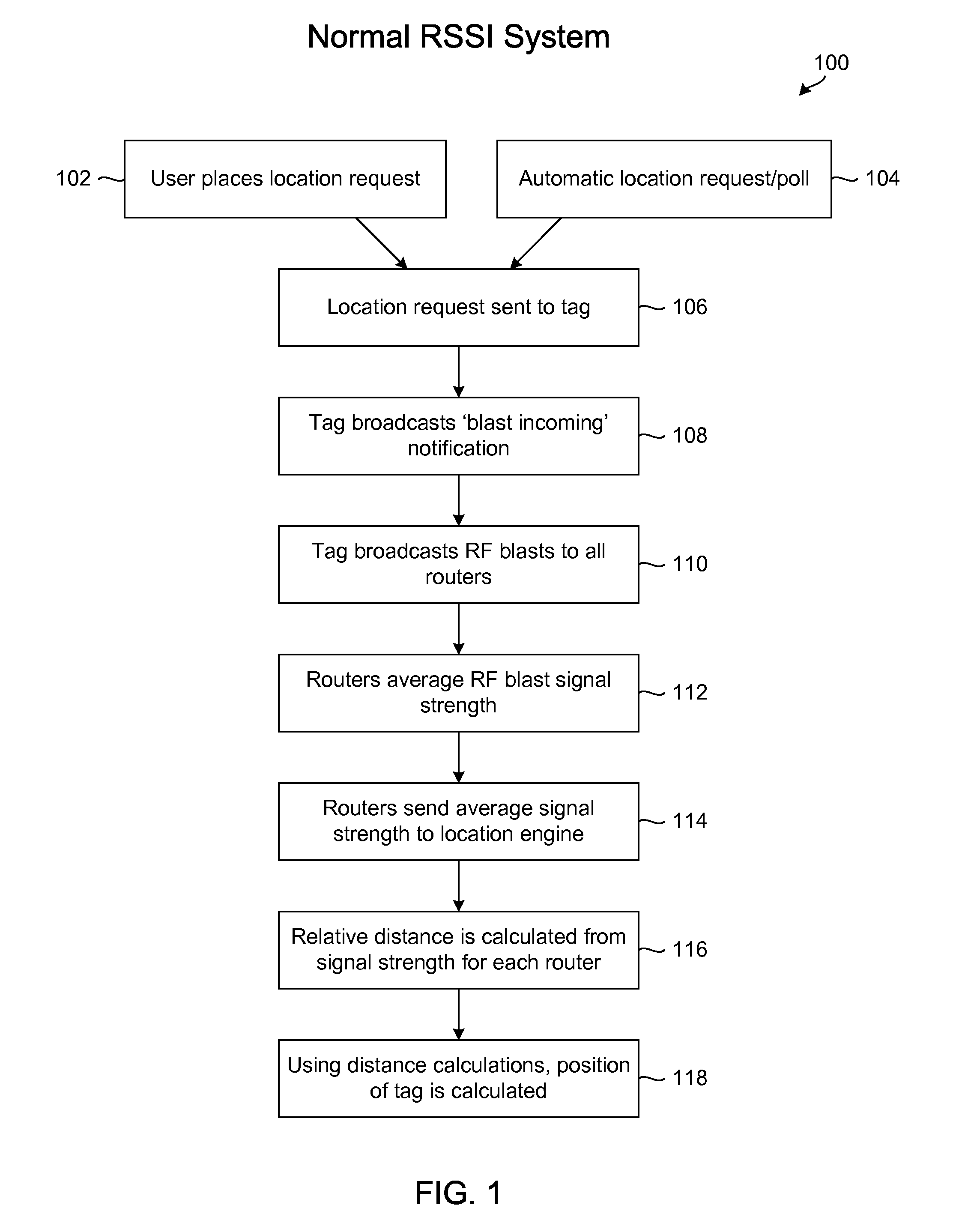
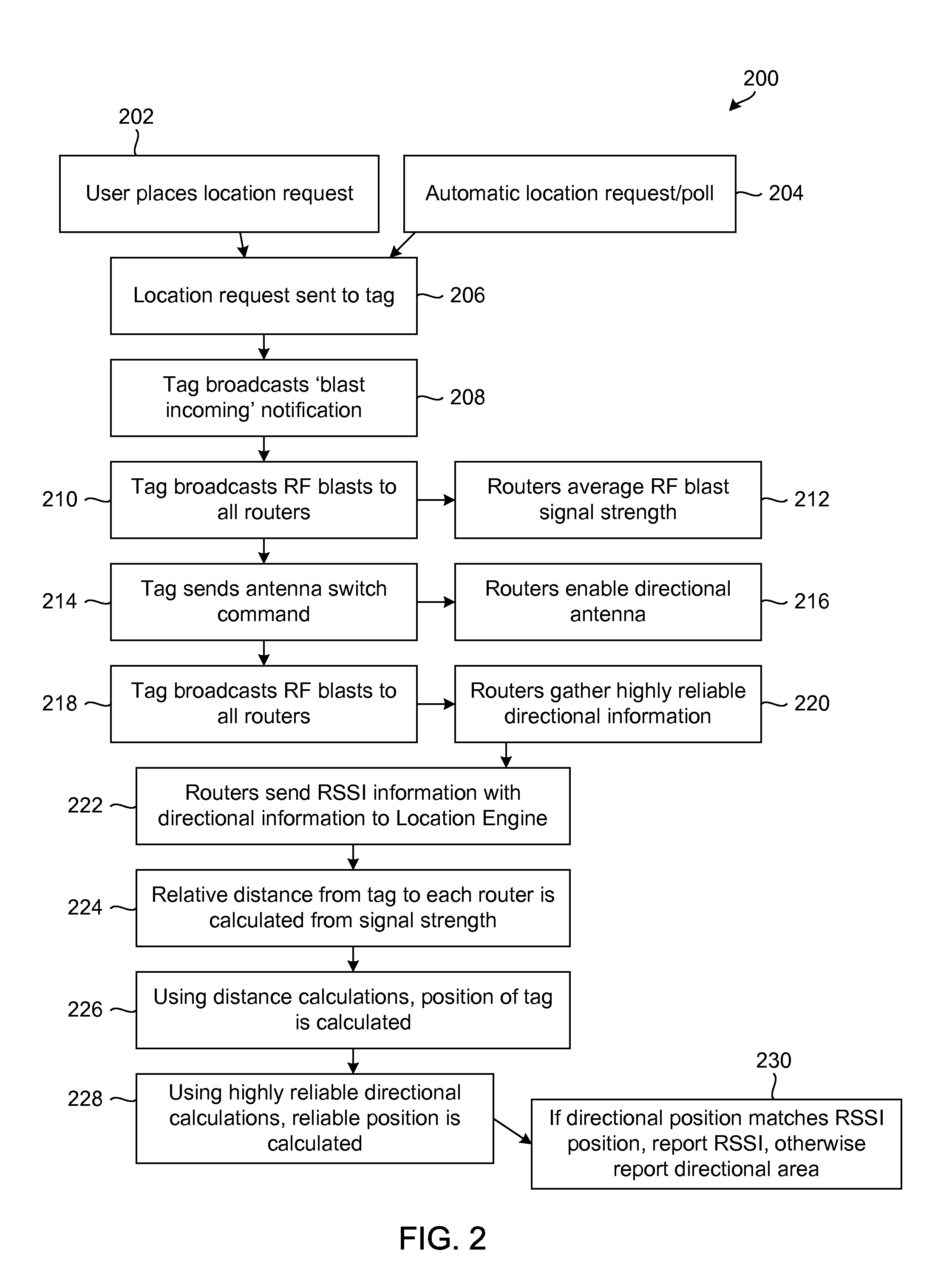
Real-time network node location system and method
InactiveUS20100238862A1Position fixationWireless commuication servicesReceived signal strength indicationDirectional antenna
A real-time location system and method for a wireless network includes, in one embodiment: (a) obtaining received signal-strength indicator measurements between stationary routers and mobile devices; (b) determining the relative angles of mobile devices from stationary routers using directional antenna systems; and (c) using signal strength and angle information to calculate the location of mobile devices.
Owner:BUZBY NETWORKS
Systems and methods for real-time network-based vulnerability assessment
A system for real-time vulnerability assessment of a host / device, said system comprising an agent running on the host / device. The agent includes a a first data structure for storing the status of interfaces and ports on the interfaces of the host / device. An n executable agent module is coupled to the first data structure to track the status of interfaces and ports on the interfaces of the host / device and to store the information, as entries in said first data structure. The executable agent module compares the entries to determine a change in the status of interfaces and / or of ports on the interfaces of the host / device. A remote destination server is provided that includes a second data structure for storing the status of interfaces and the ports on the interfaces of the host / device. An executable server module is coupled to the second data structure to receive the information communicated by the agent executable module of the agent on the host / device. The executable server module stores the received information as entries in the second data structure wherein the entries indicate the state of each of the ports on each of the active interfaces of the host / device as received. The executable server module compares the entries in said data structures to determine the change in the status of interfaces and ports on the interfaces of the host / device. The executable server module runs vulnerability assessment tests on the host / device in the event of a change in the status of interface / ports.
Owner:RPX CORP
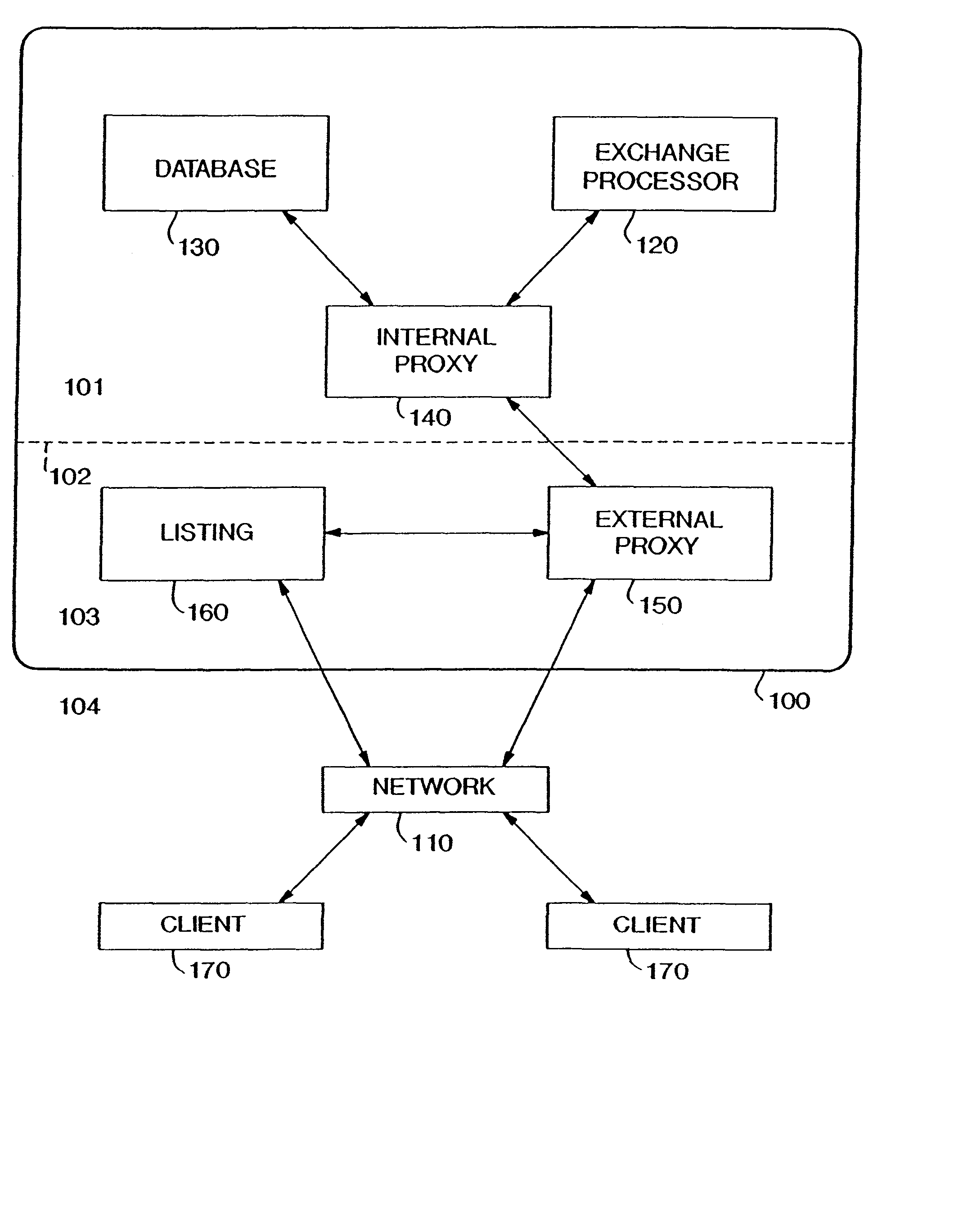
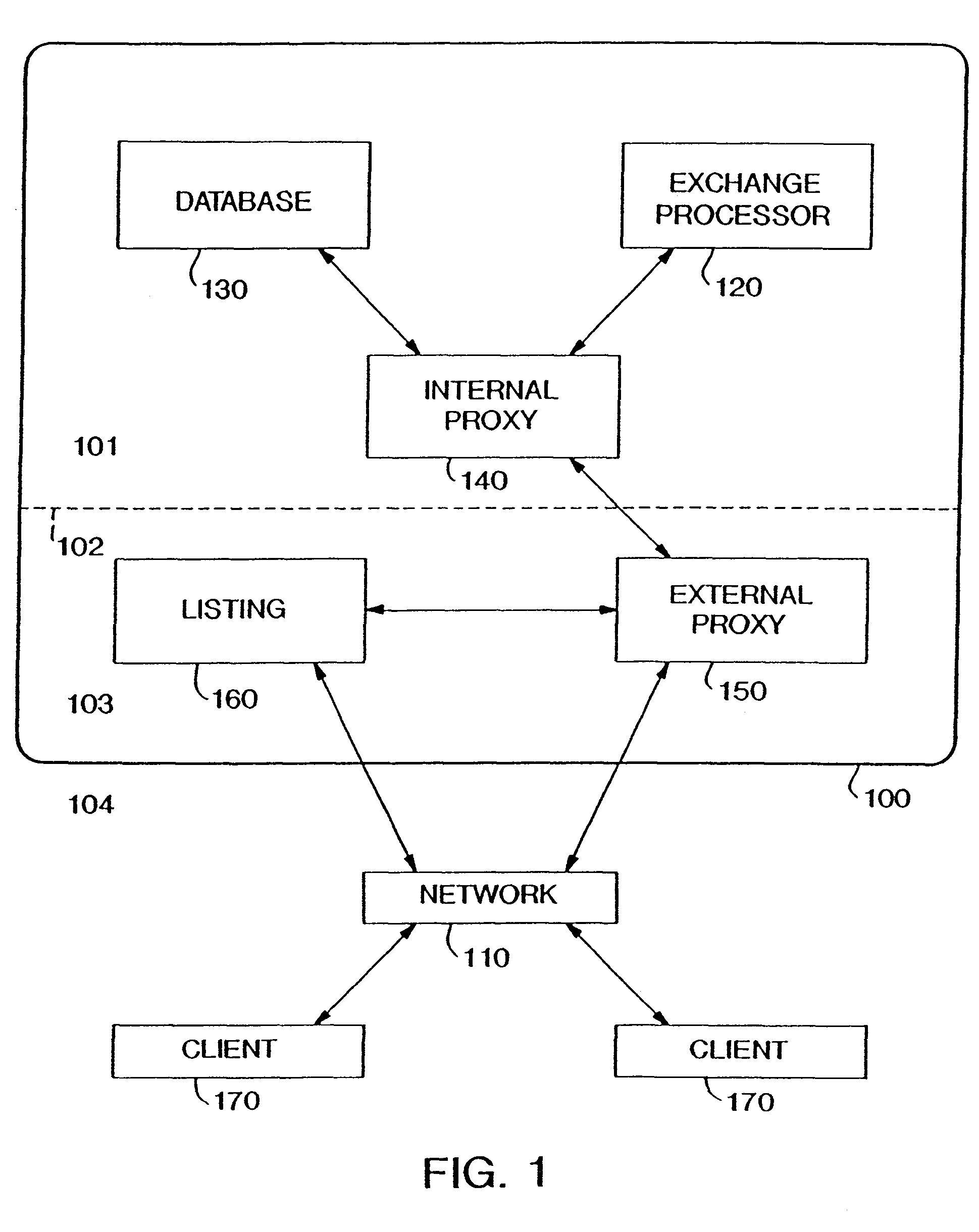
Real time network exchange with seller specified exchange parameters and interactive seller participation
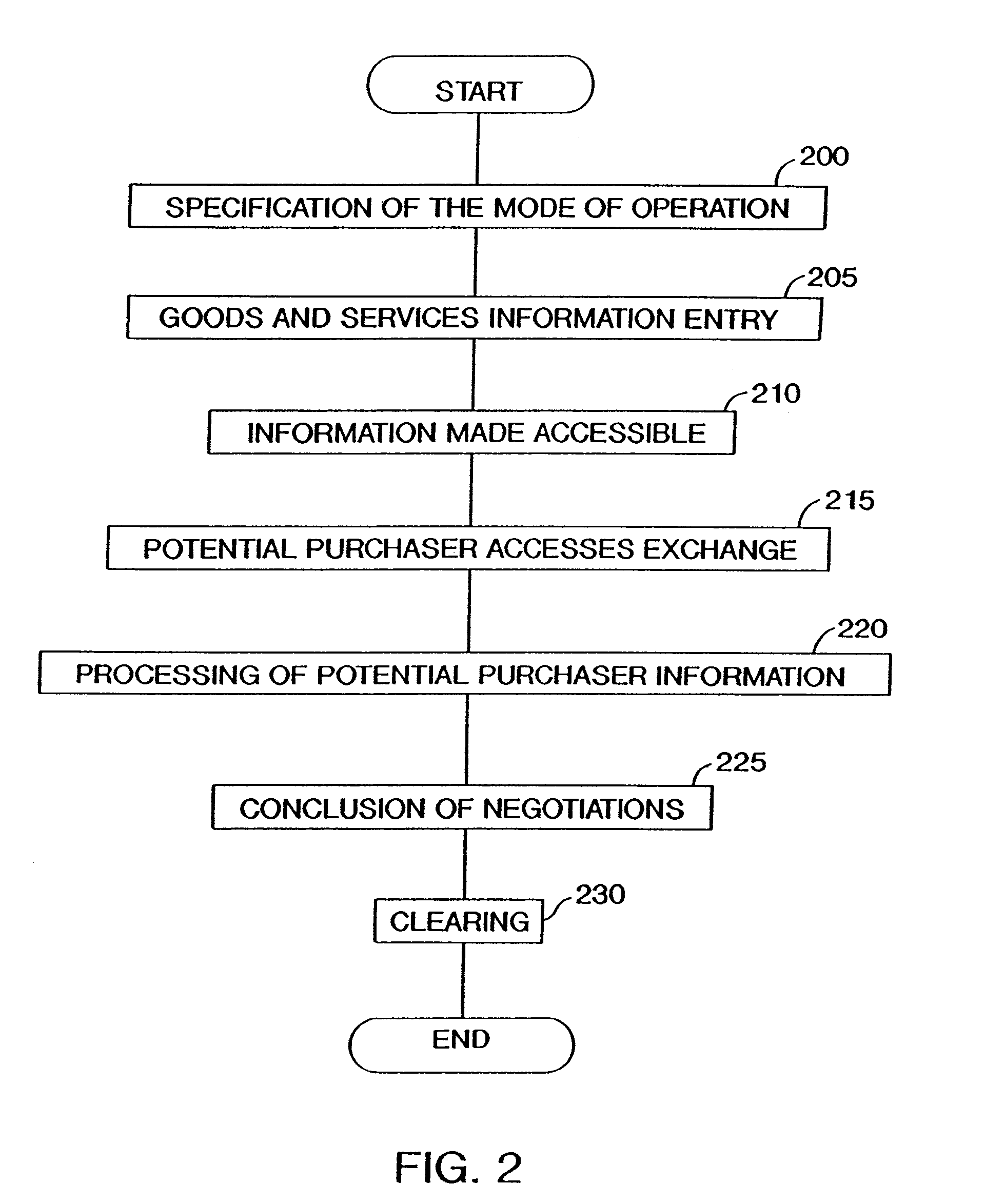
<heading lvl="0">Abstract of Disclosure< / heading> A system and method for networked exchange are disclosed. A system for networked exchange comprises an internal proxy (140); an exchange processor (120) in communication with the internal proxy (140); a database (130) in communication with the internal proxy (140); an external proxy (150) in communication with the internal proxy (140); and, a communications network (110) connected to the external proxy. A method for networked exchange comprises 8 steps. Those steps are (1) specifying a mode of operations for an exchange; (2) identifying a commodity for the exchange; (3) listing information about the commodity; (4) accessing of the listing by a potential purchaser; (5) accessing the network-based exchange by the potential purchaser; (6) processing information generated by the potential purchaser, the information comprising a negotiation; (7) concluding the negotiation; and, (8) clearing the concluded negotiation.
Owner:HANGER SOLUTIONS LLC +1
A malicious traffic detection implementation method and device based on deep learning
ActiveCN108985361ASolve the characteristicsAddress privacy breachesCharacter and pattern recognitionNeural architecturesFeature extractionManual extraction
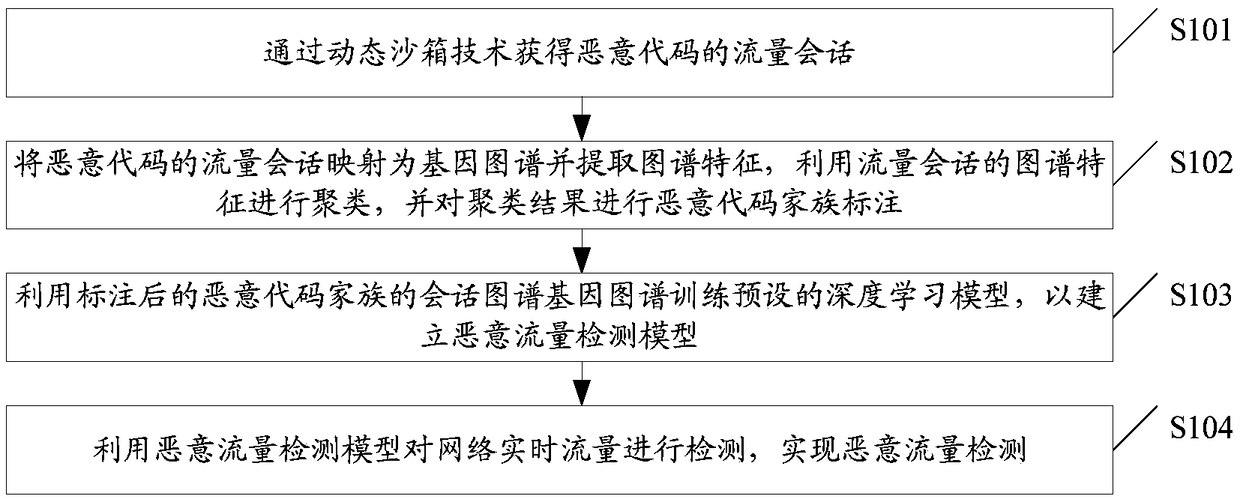
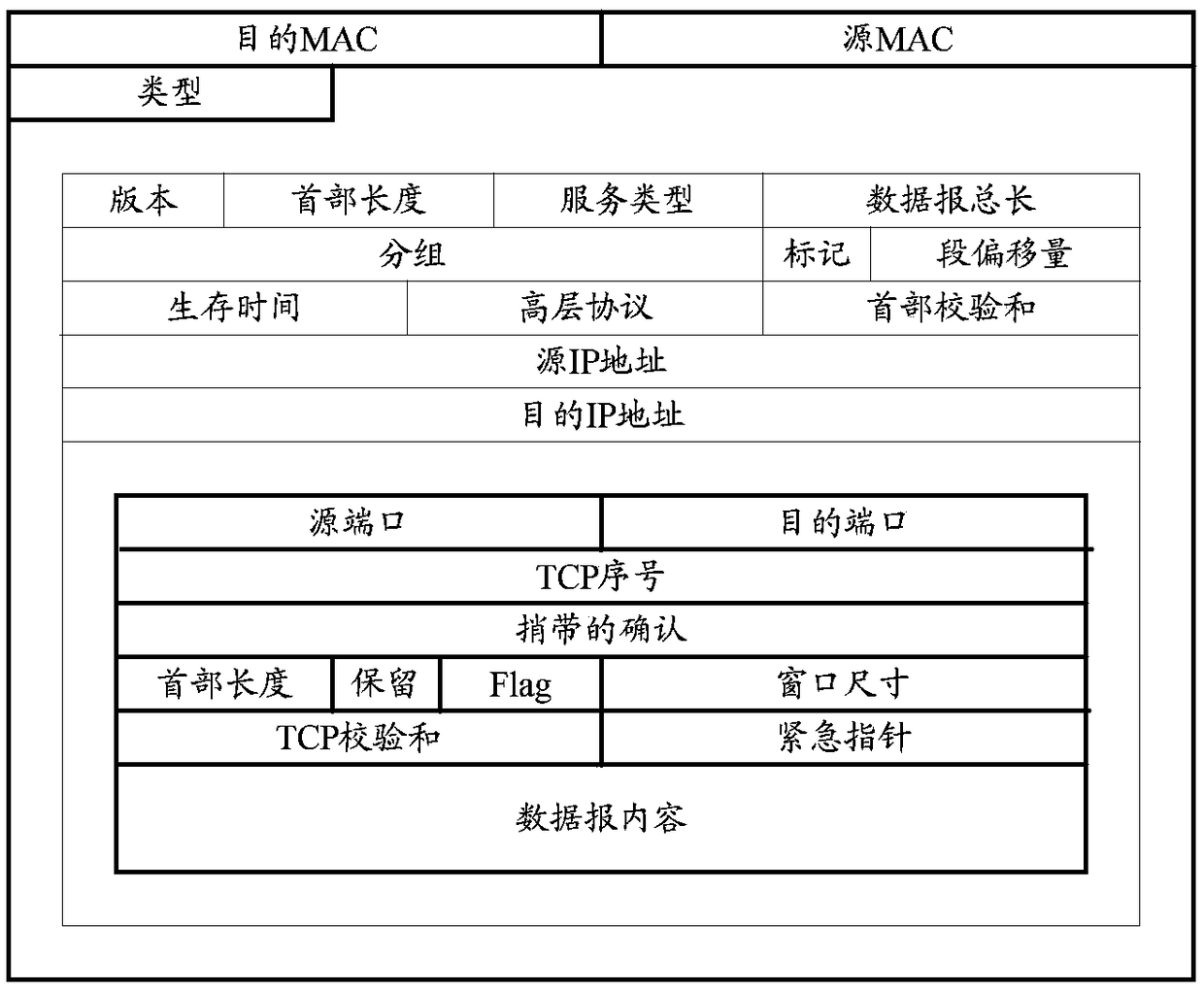
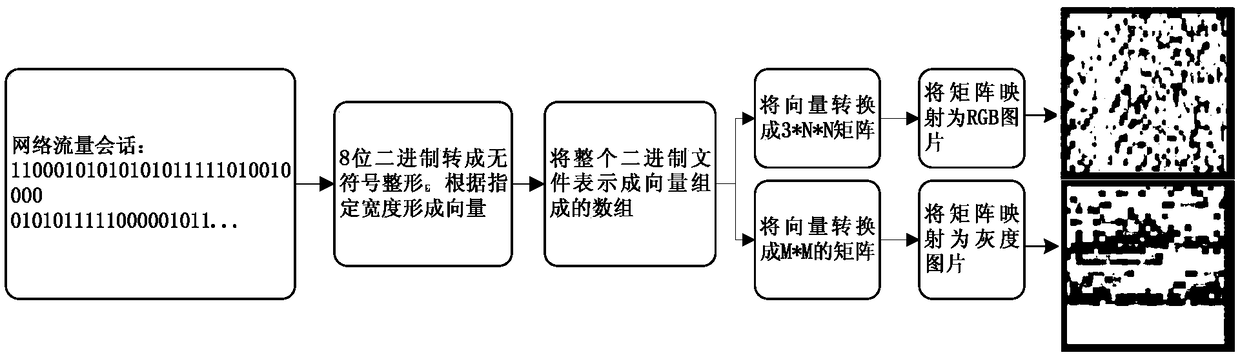
The embodiment of the invention discloses a malicious traffic detection implementation method and device based on deep learning. The method can include: obtaining the flow session of malicious code through dynamic sandbox technology; mapping the traffic session of malicious code to a gene map and extracting the map features; using the map features of traffic session for clustering and marking theclustering results by a malicious code family; training the preset depth learning model by using the tagged gene map of the malicious code family to establish the malicious traffic detection model; using the malicious traffic detection model to detect real-time network traffic, and realizing malicious traffic detection. Through the embodiment, many problems existing in the conventional detection technology such as artificial feature extraction difficulty, privacy disclosure, encryption and confusion difficult to identify, machine learning feature manual extraction and the like are solved to acertain extent, and the method has the characteristics of high robustness, high speed, high accuracy, low false alarm rate, cross-platform detection and the like.
Owner:北京金睛云华科技有限公司
Machine Learning Model Evaluation in Cyber Defense
ActiveUS20180165597A1Computer security arrangementsProbabilistic networksCyber defenseMachine learning
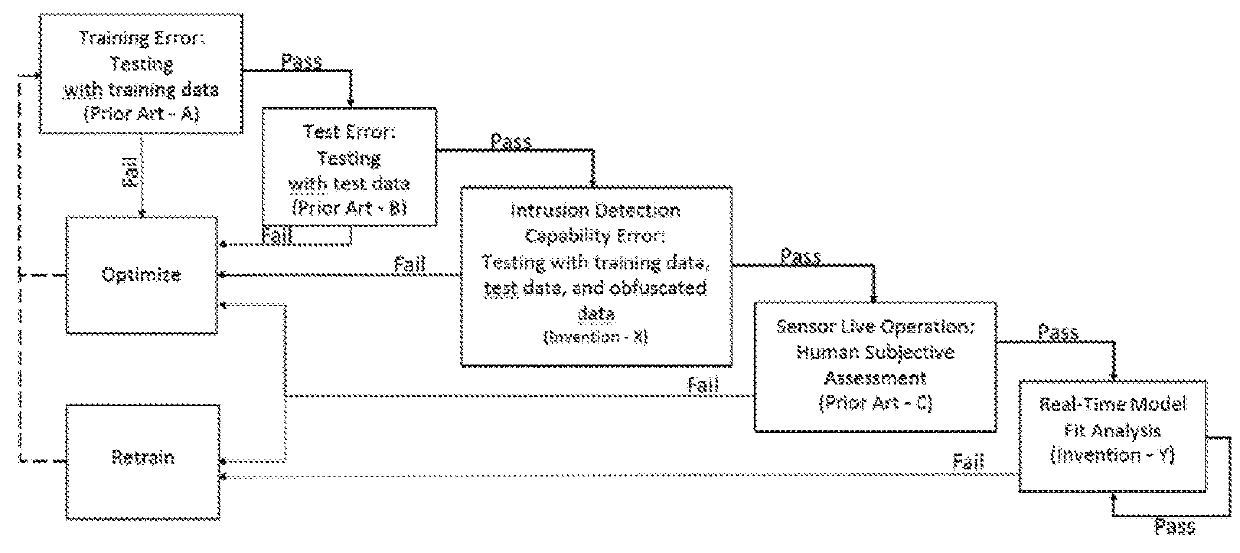
Testing machine learning sensors by adding obfuscated training data to test data, and performing real time model fit analysis on live network traffic to determine whether to retrain.
Owner:RESURGO
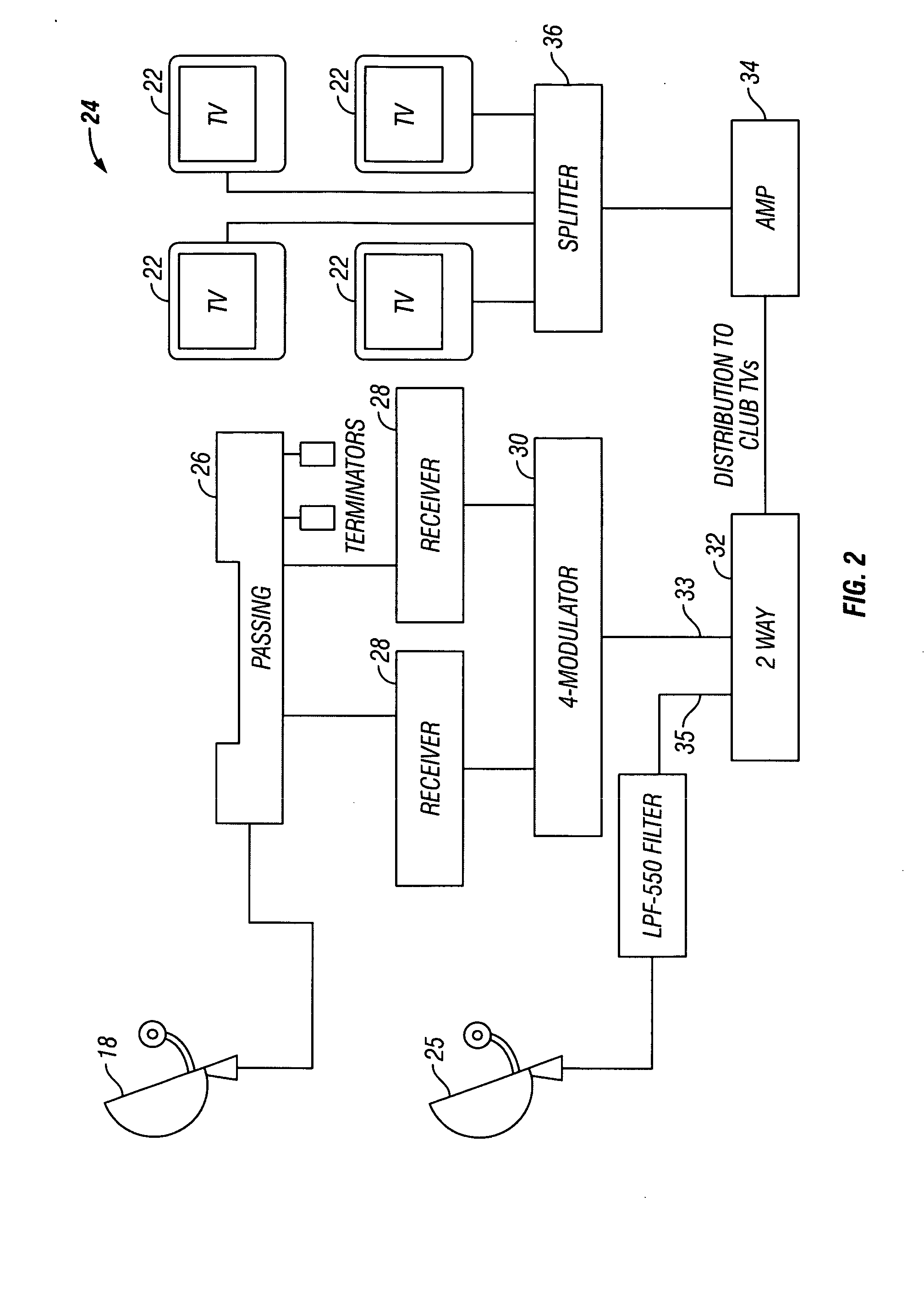
System and methods for network TV broadcasts for out-of-home viewing with targeted advertising
InactiveUS20090044217A1Accurate abilityMaximize effectivenessReceiver side switchingBroadcast transmission systemsThe InternetTargeted advertising
A television broadcasting system and methods that manages the insertion of targeted advertisements and other messages into live satellite or Internet broadcasts or other types of broadcasts into out-of-home locations such as health clubs. The insertion of targeted advertisement and other messages are accomplished by a satellite service provider purchasing live network broadcasting feeds with a license to strip out existing commercial advertisements and replace them with targeted advertisements to match the demographics of the viewing audience at health clubs and other non-home locations nationally, regionally and locally where the viewer is unable to change or delete the targeted advertisements while viewing the live broadcast programming from the networks.
Owner:IDEACAST +1
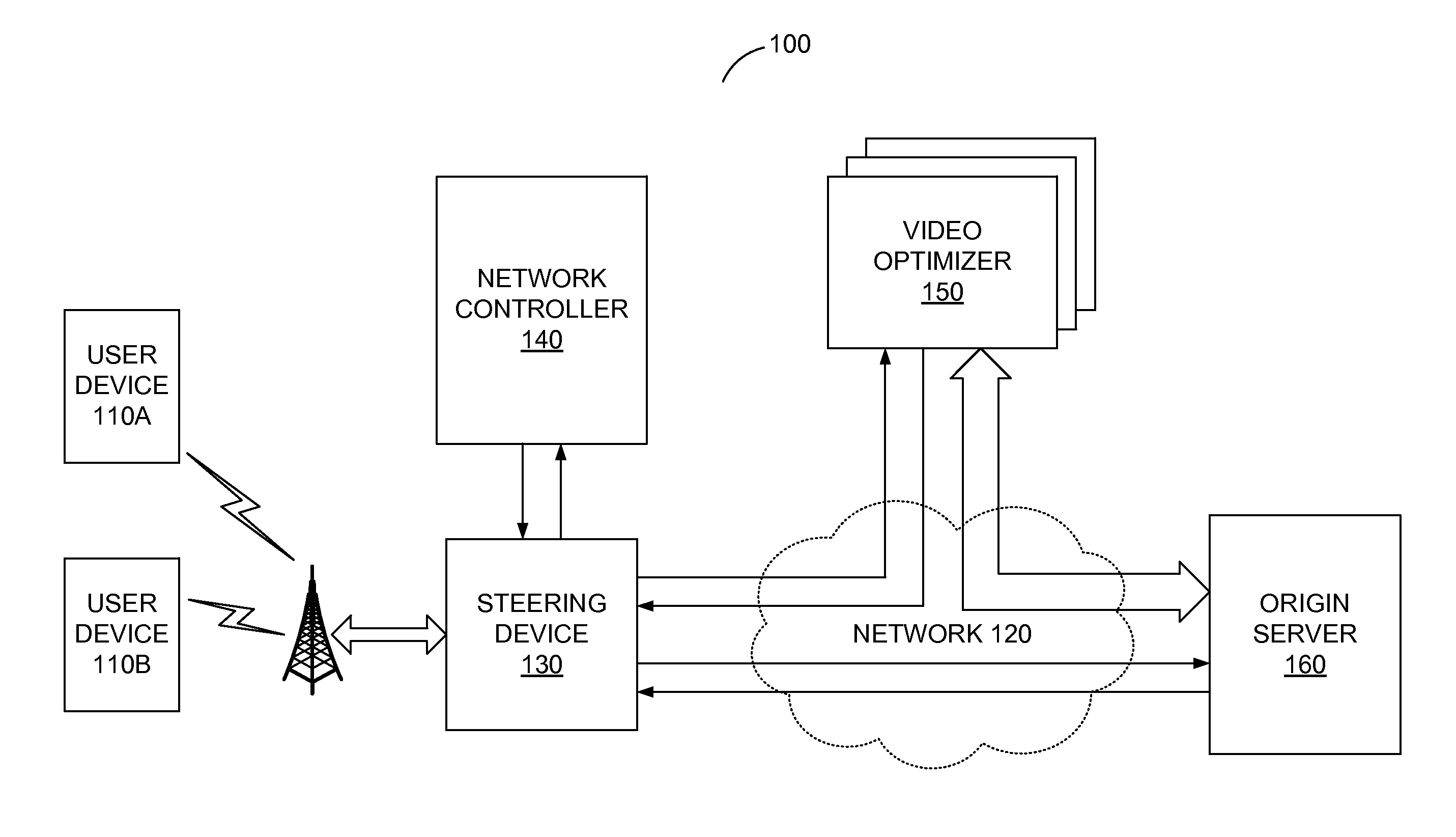
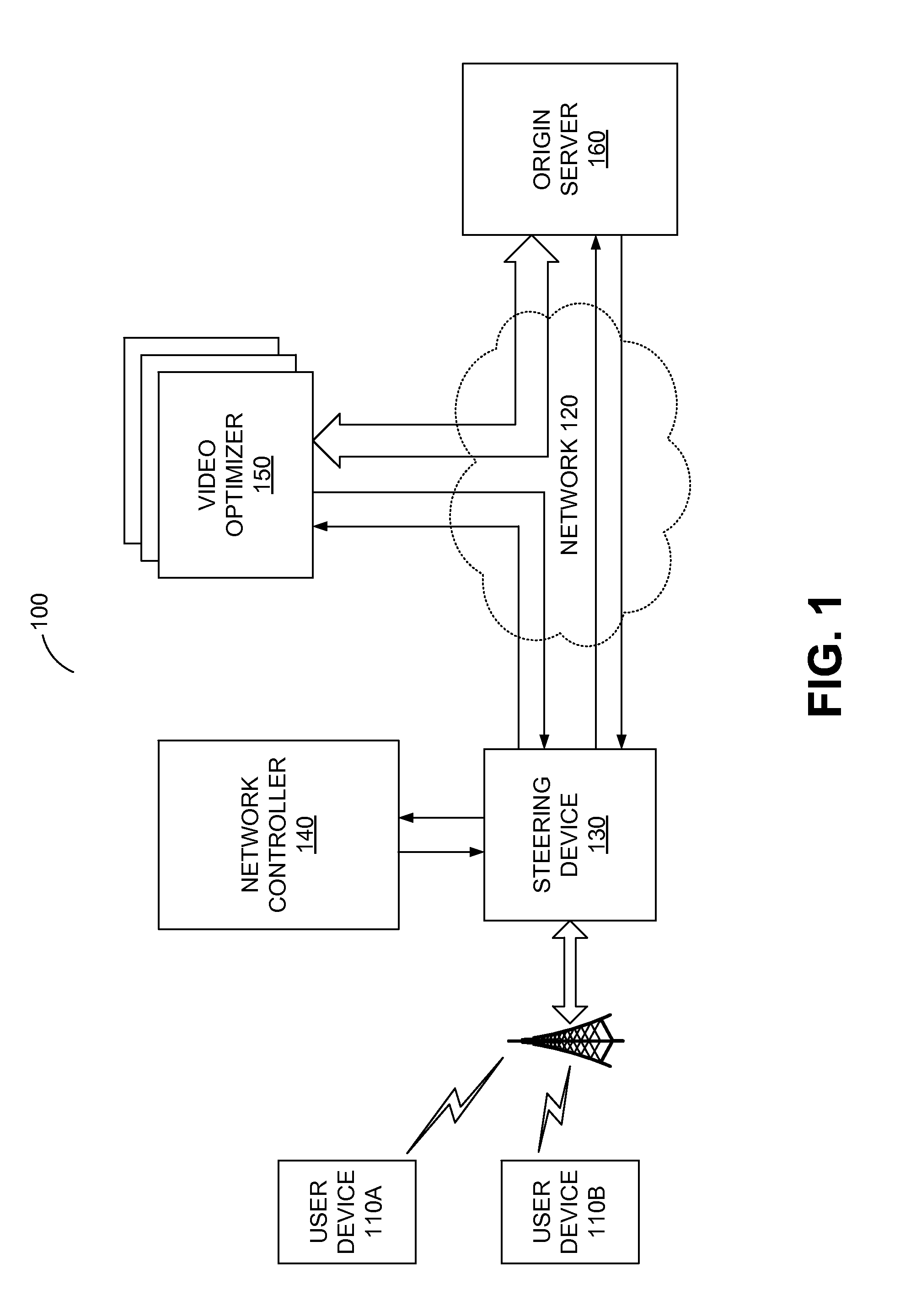
Real-Time Network Monitoring and Subscriber Identification with an On-Demand Appliance
A system and a method are disclosed for selectively monitoring traffic in a service provider network. The system receives a notice for a beginning of a network data flow, which responds to a request from a user device for content at an origin server. The system then determines whether to monitor the data flow from the origin server to the user device. If so determined, the system collects statistic information of the data flow and stores the statistic information to a flow record in a database. The system also maps the flow record to a subscriber of the service provider network by analyzing the statistic information of the data flow and estimates bandwidth provided to the data flow by the service provider's network based on the analysis of the statistic information of the data flow.
Owner:OTELLO CORP ASA
Real-time web sharing system
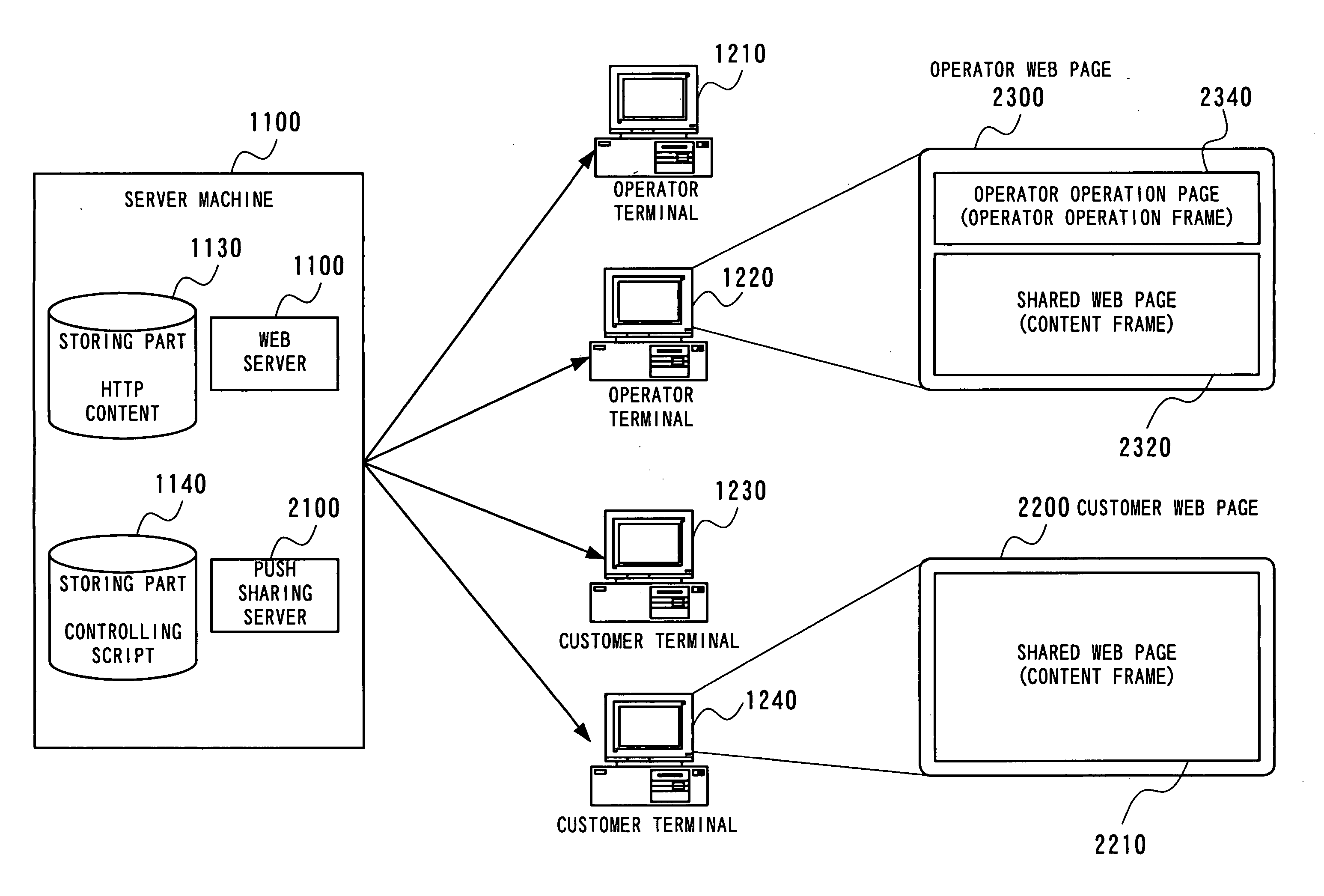
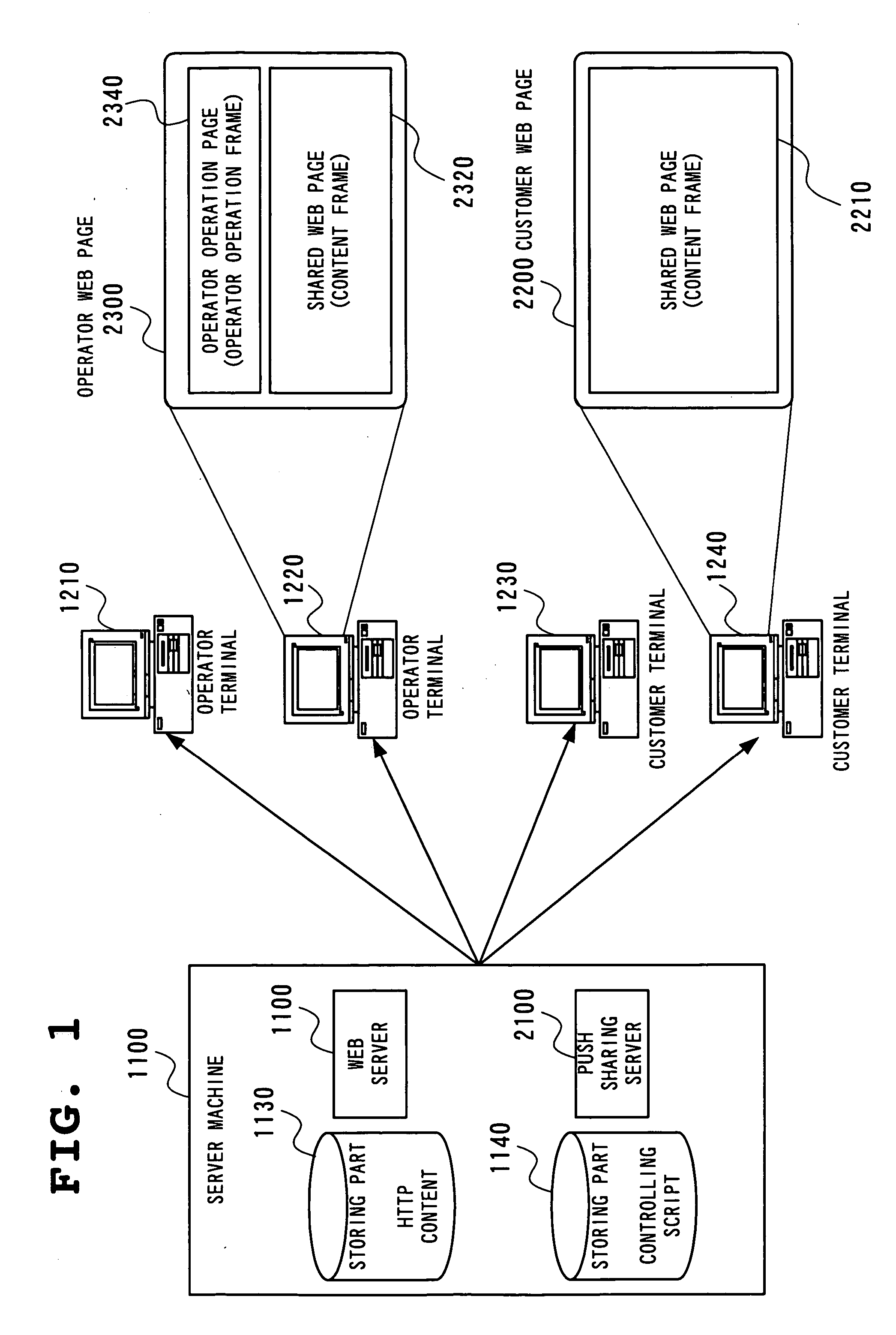
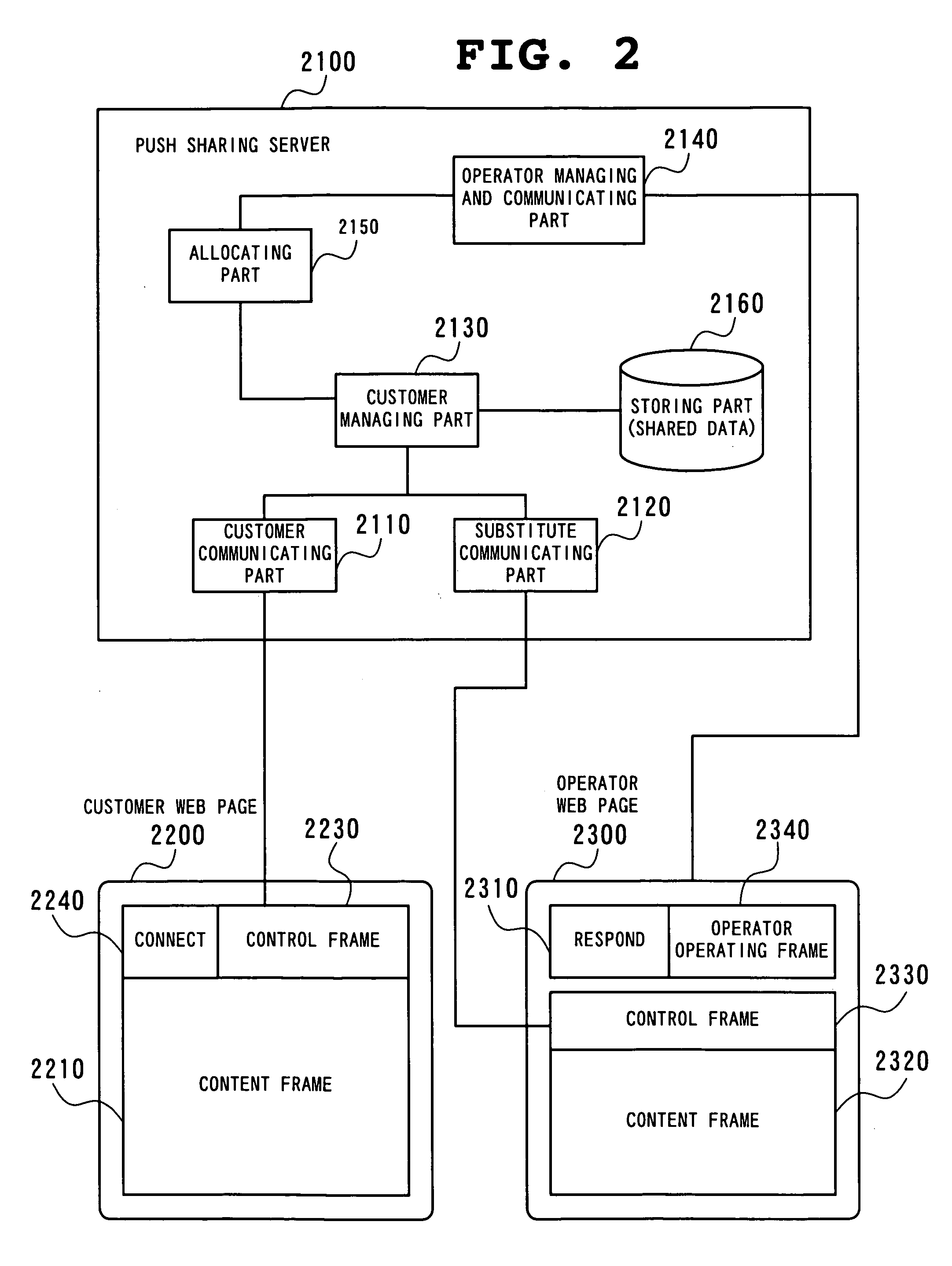
ActiveUS20060015763A1Error detection/correctionMultiple digital computer combinationsComputer hardwareWeb page
The customer presses the Connect button (2240) on the customer terminal (1230). By this, a connection request to an operator terminal is notified to an operator terminal (1210) via the push sharing server (2100). On receiving this notification, the operator terminal (1210) changes the Respond button (2310) to the Incoming button. When the operator presses the Respond button (2310) on the operator web page (2300), the push sharing server (2100) transmits a difference notification command to the operator terminal (1210), and the operator terminal displays the same web page as the web page on the customer terminals (1230).
Owner:ASTRAZEMECA +1
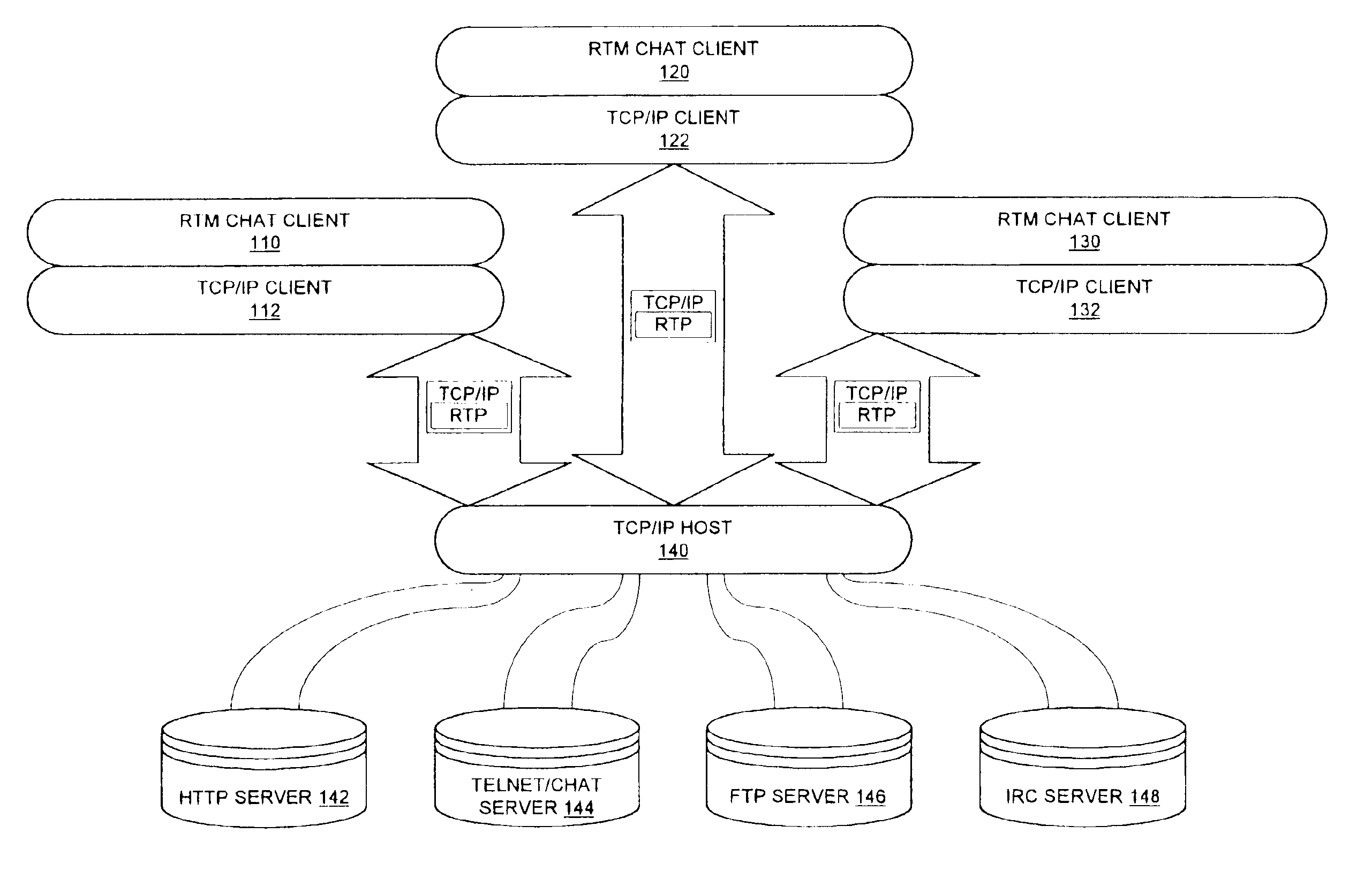
Method and apparatus for real time network communication
InactiveUS6862625B1Function increaseSpecial service provision for substationMultiple digital computer combinationsNetwork Communication ProtocolsNetwork communication
A real time communications protocol connection is formed over a network communications connection. A markup language instruction is embedded in a message. The message is sent on the real time communications protocol connection.
Owner:NYTELL SOFTWARE LLC
System and method for using real-time packet data to detect and manage network issues
A system and method is disclosed of extracting information from real-time network packet data to analyze connectivity data for client devices in a network. The method includes: detecting when client devices initiate a connectivity event; after detecting a connectivity event, waiting a period of time for the client device to either reach or fail to reach a network connected state; after waiting a period of time, recording connectivity event information; and sending the recorded connectivity event information to an analytics system for network incident and / or network congestion analysis.
Owner:VMWARE INC
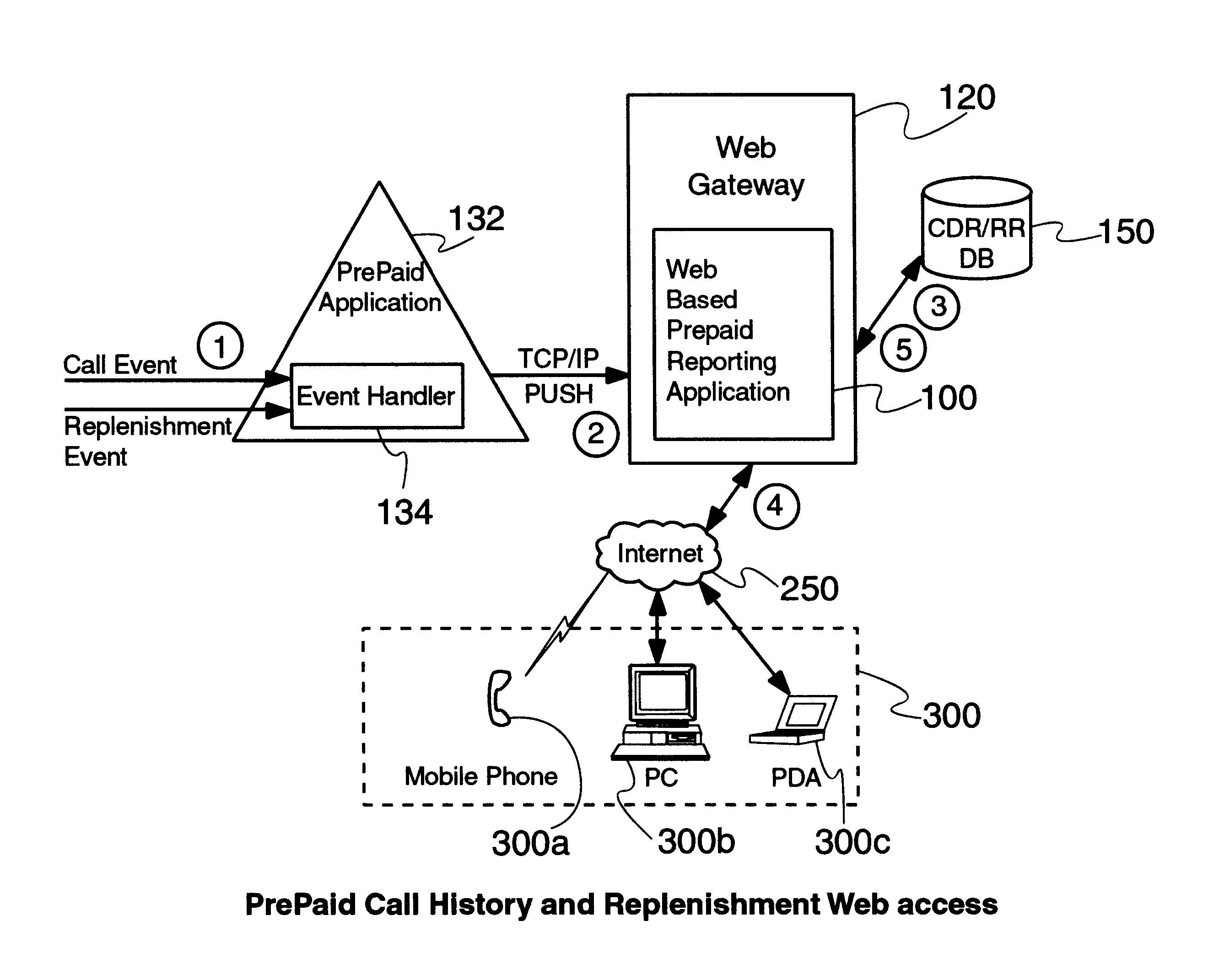
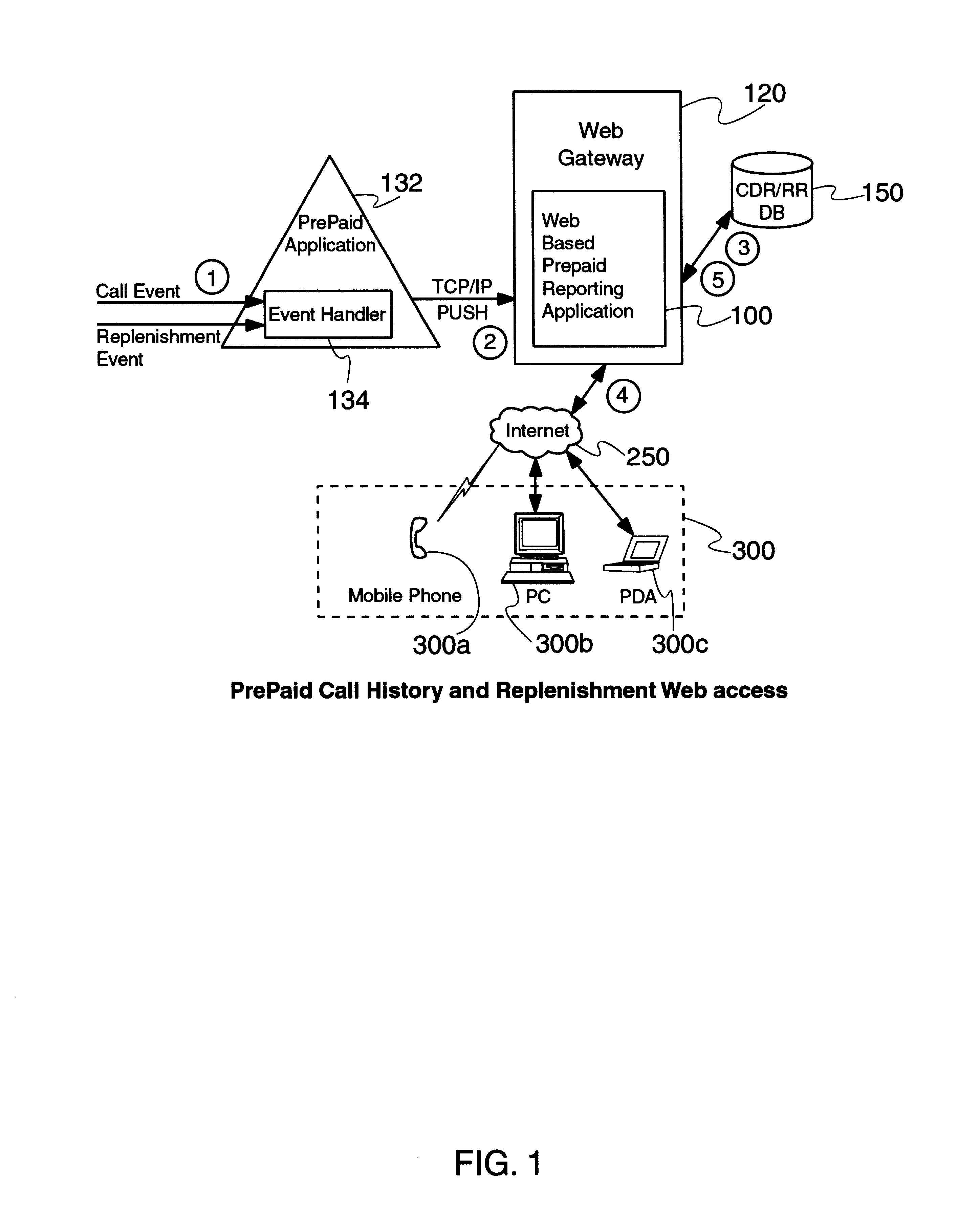
Prepaid real-time web based reporting
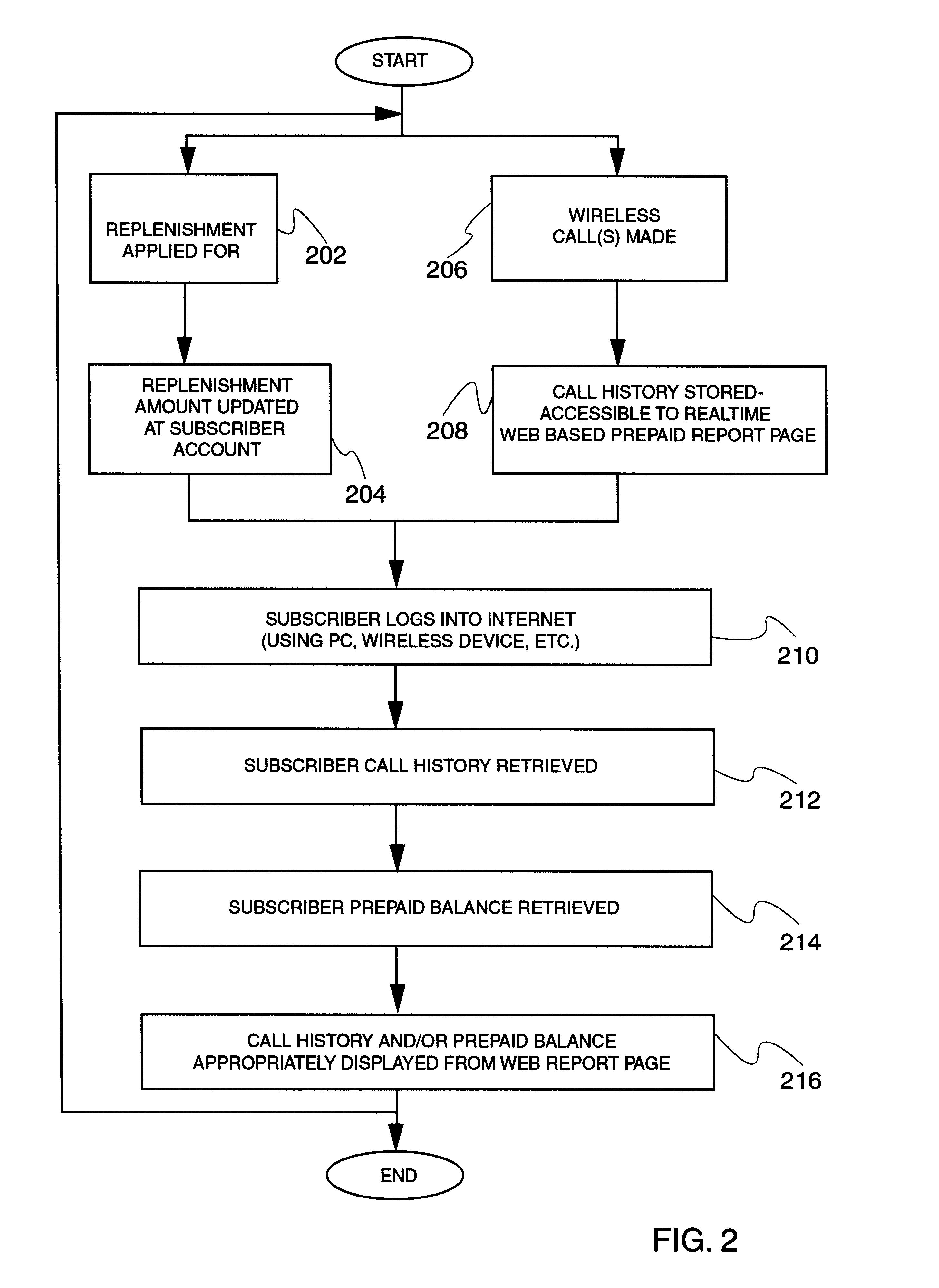
InactiveUS20030069816A1Complete banking machinesPrepayment with on-line account/card rechargingWeb browserPassword
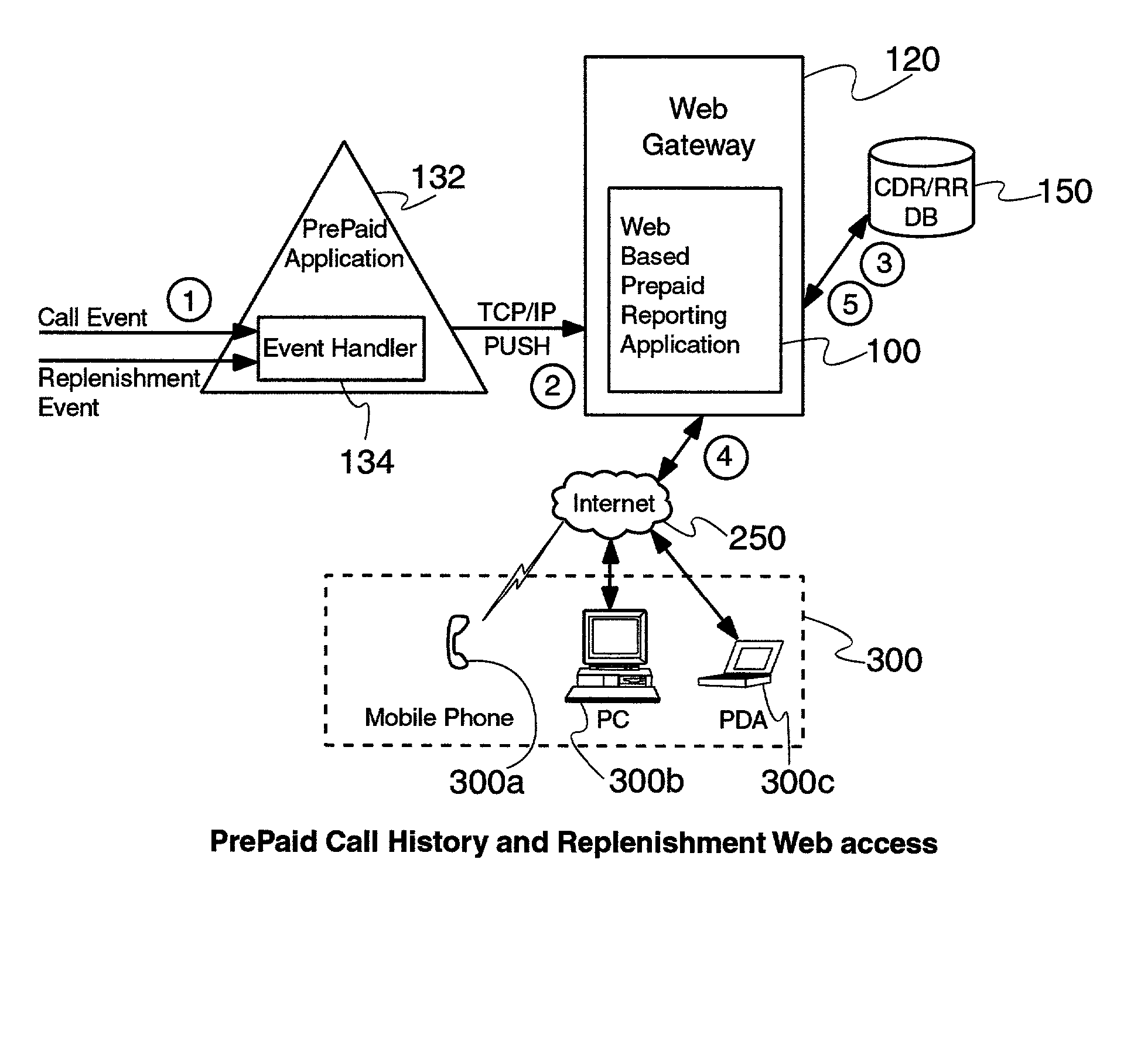
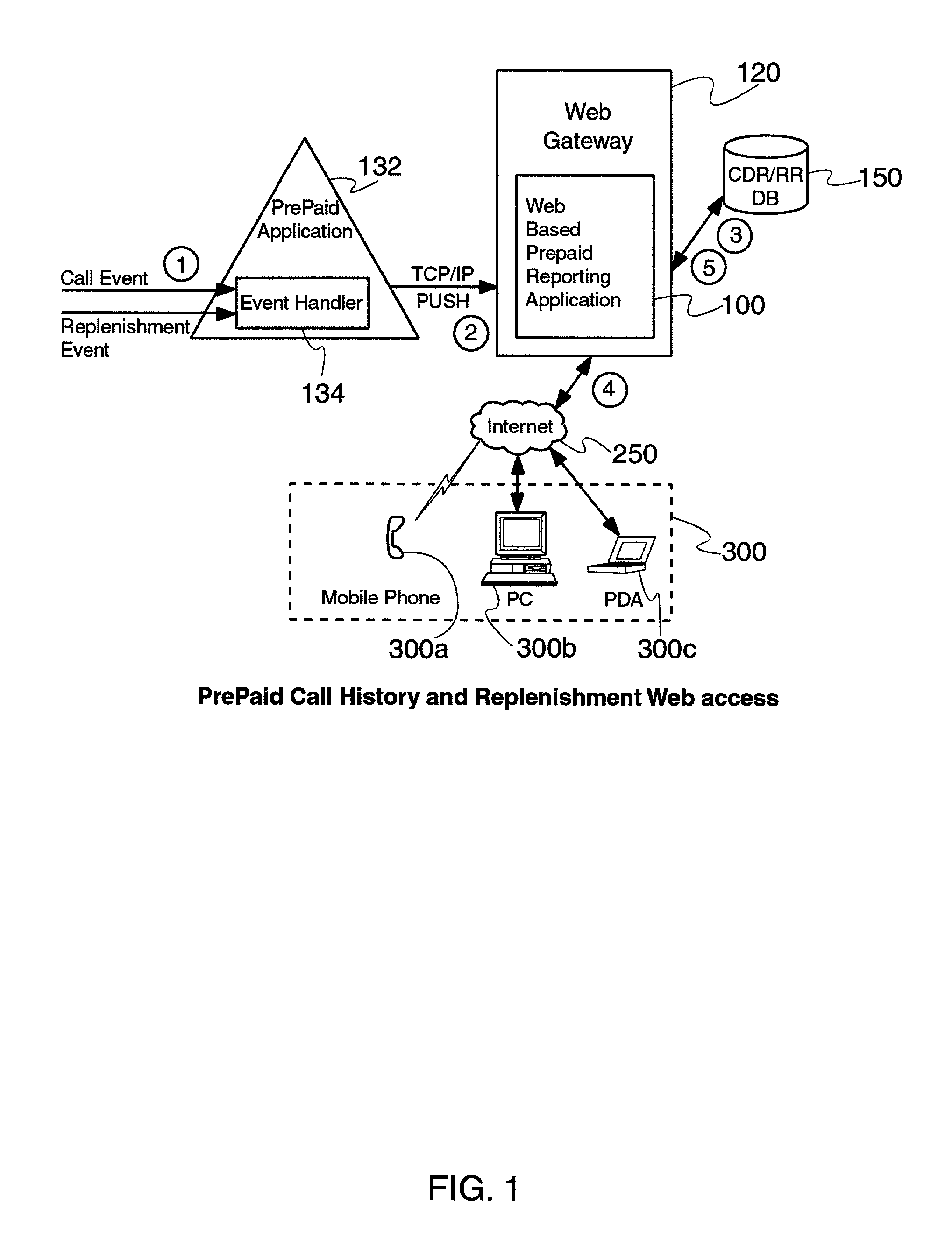
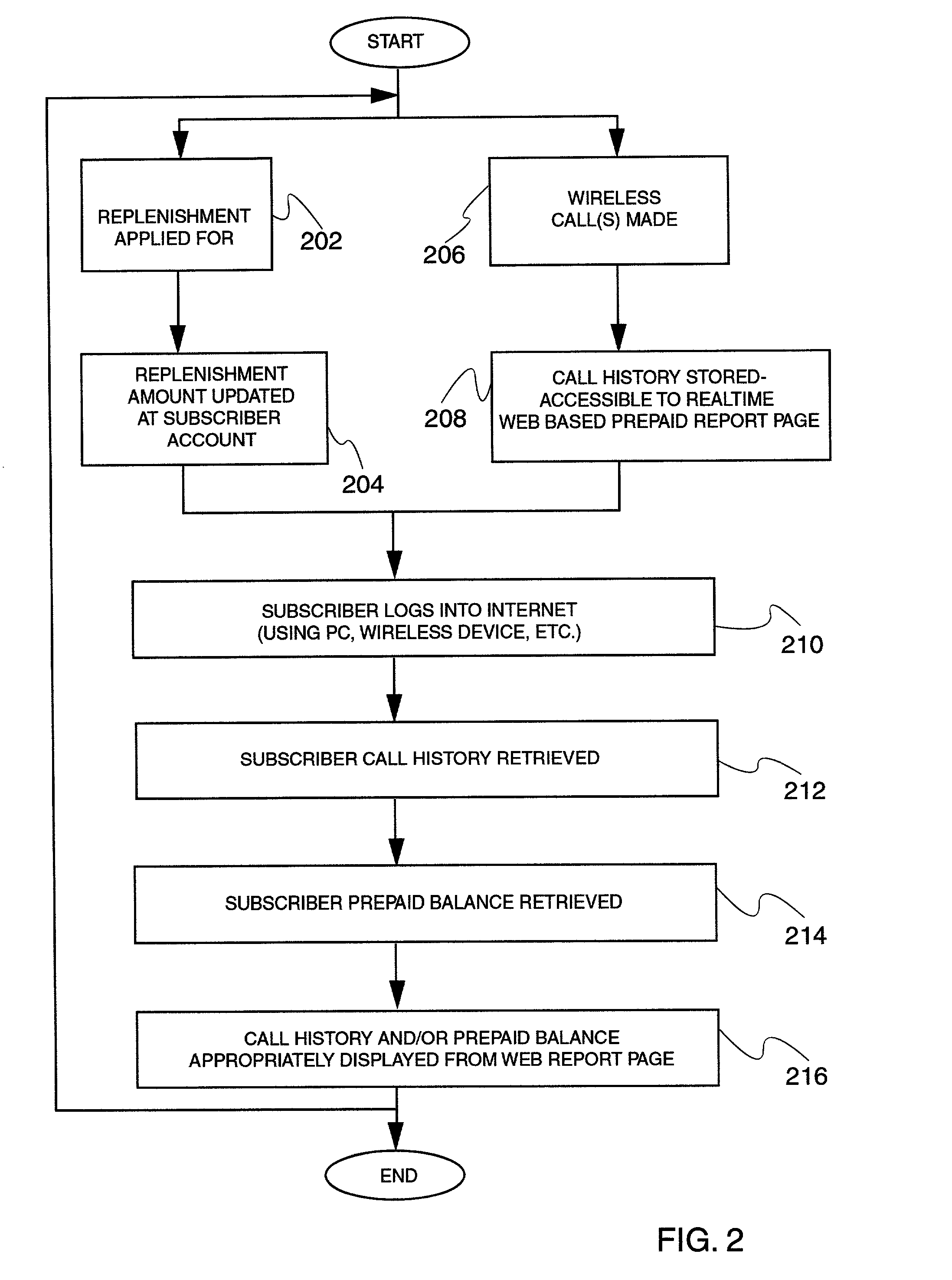
Near real time Internet access of prepaid call history and replenishment data is provided via an Internet browser separate from the prepaid device to a user (e.g., the subscriber), allowing a subscriber to access call history and / or replenishment information nearly in real time (e.g., within a minute of the expense / credit) without requiring assistance from a customer service representative. A web based prepaid report page retrieves call history and / or replenishment information from the subscriber's service provider, and displays the same through a web browser for review by the subscriber. The requested call history and / or replenishment information may be bounded by date, date and time, or even within specific time range(s) within each day in a given range of days. The web based prepaid report page may also link the user to a replenishment application for the subscriber, to assist the subscriber in replenishing their account after having reviewed their call history and prepaid account status in near real time. The call history and account balance information is preferably updated in near real time after the completion of a call, which is then accessed by the web based prepaid report page. Substantially immediately after a prepaid call is ended, the web based prepaid reporting application formulates a Call Detail Record (CDR) and sends it over a TCP / IP link to the web based prepaid reporting application, which stores the CDR in a local database. Then, a user may access this CDR / RR information in near real time, after appropriate log-in with, e.g., a user ID of the subscriber (e.g., MIN number based), and perhaps a password. Once the requested information is entered, the web based prepaid reporting application queries its local database, formats an appropriate response to the user's request, and presents the call history and / or replenishment information to the web browser of the user.
Owner:SLINGSHOT TECH LLC
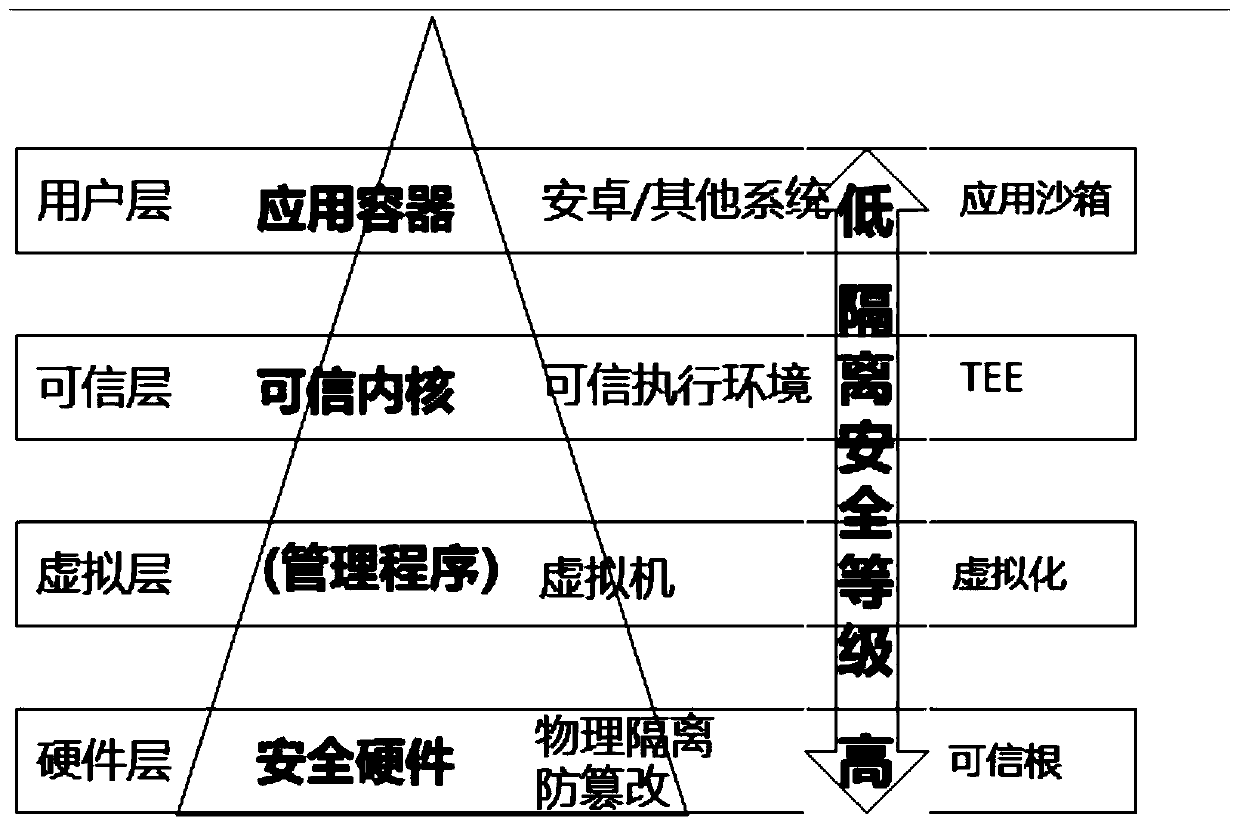
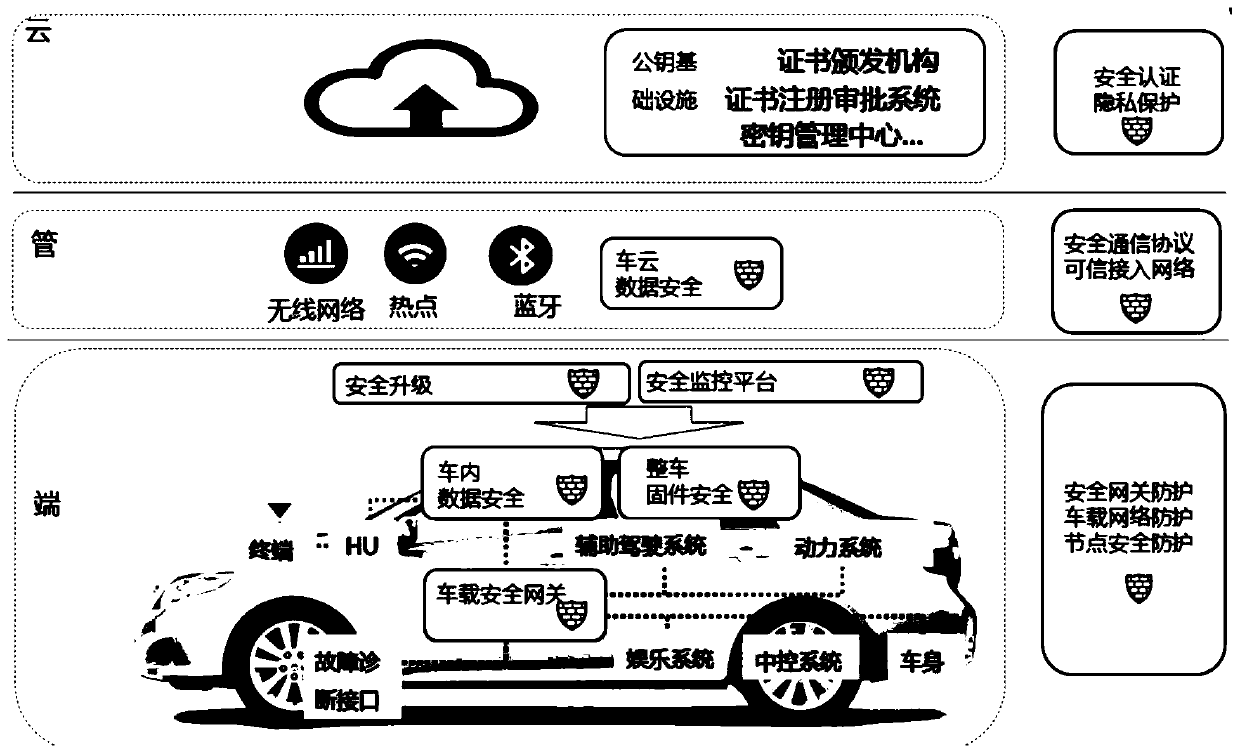
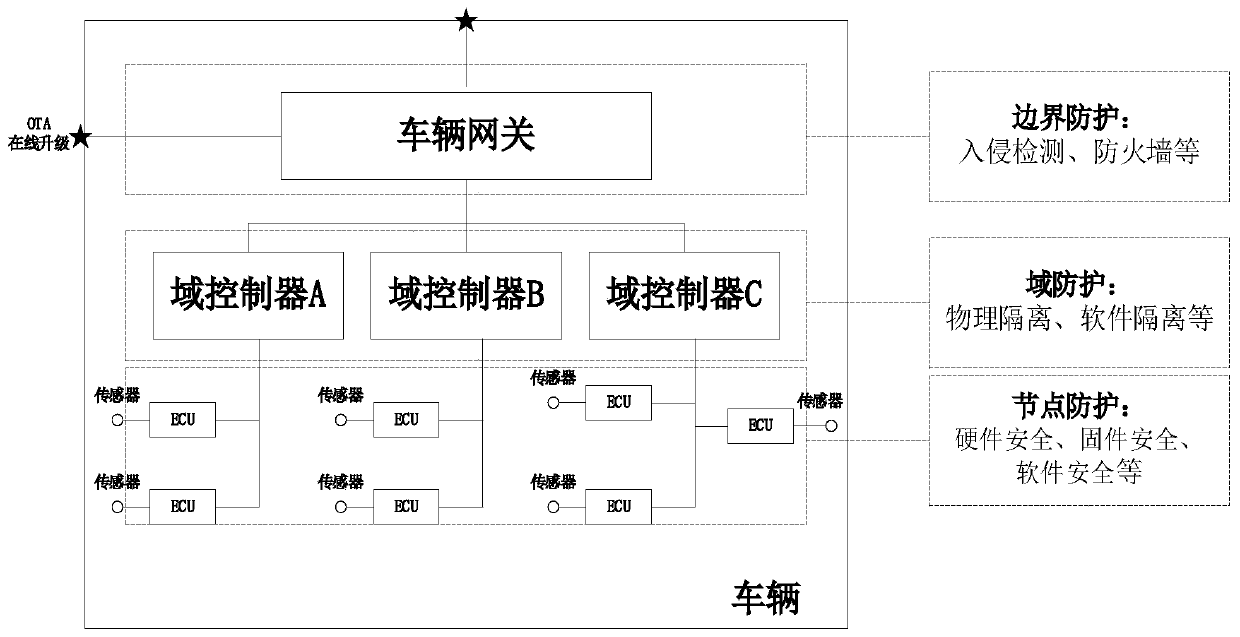
Intelligent network connection automobile information safety platform based on end-pipe-cloud
ActiveCN109714344AImprove the working mechanism of safety managementPromote the development of social securityKey distribution for secure communicationData life cycleThe Internet
The invention discloses an intelligent networked automobile information security platform based on end-pipe-cloud, and the platform carries out the security protection for a vehicle end, a cloud platform, and an Internet, and a trusted execution environment and a security level for the domain isolation, the deep defense, and the software and hardware integration are built at the vehicle end. Nodeverification, file layer encryption protection and key management service are established at the cloud end, and SSL / TLS secure communication is used between the nodes and between the nodes and the application program. For a communication network, a PKI-based communication encryption mechanism, a real-time network abnormal flow monitoring mechanism, an end-pipe-cloud integrated intrusion detectionmechanism, a national vulnerability perception and early warning mechanism and a multi-stage collaborative emergency response and online upgrading mechanism are established. And a data life cycle management mechanism, a key security storage management mechanism and a key data security storage management mechanism are established for data of the vehicle end and the cloud end. The establishment of the information security platform is the first example in the field of intelligent connected automobiles at present, and lays a foundation for the construction of national security systems.
Owner:CHINA INTELLIGENT & CONNECTED VEHICLES (BEIJING) RES INST CO LTD +1
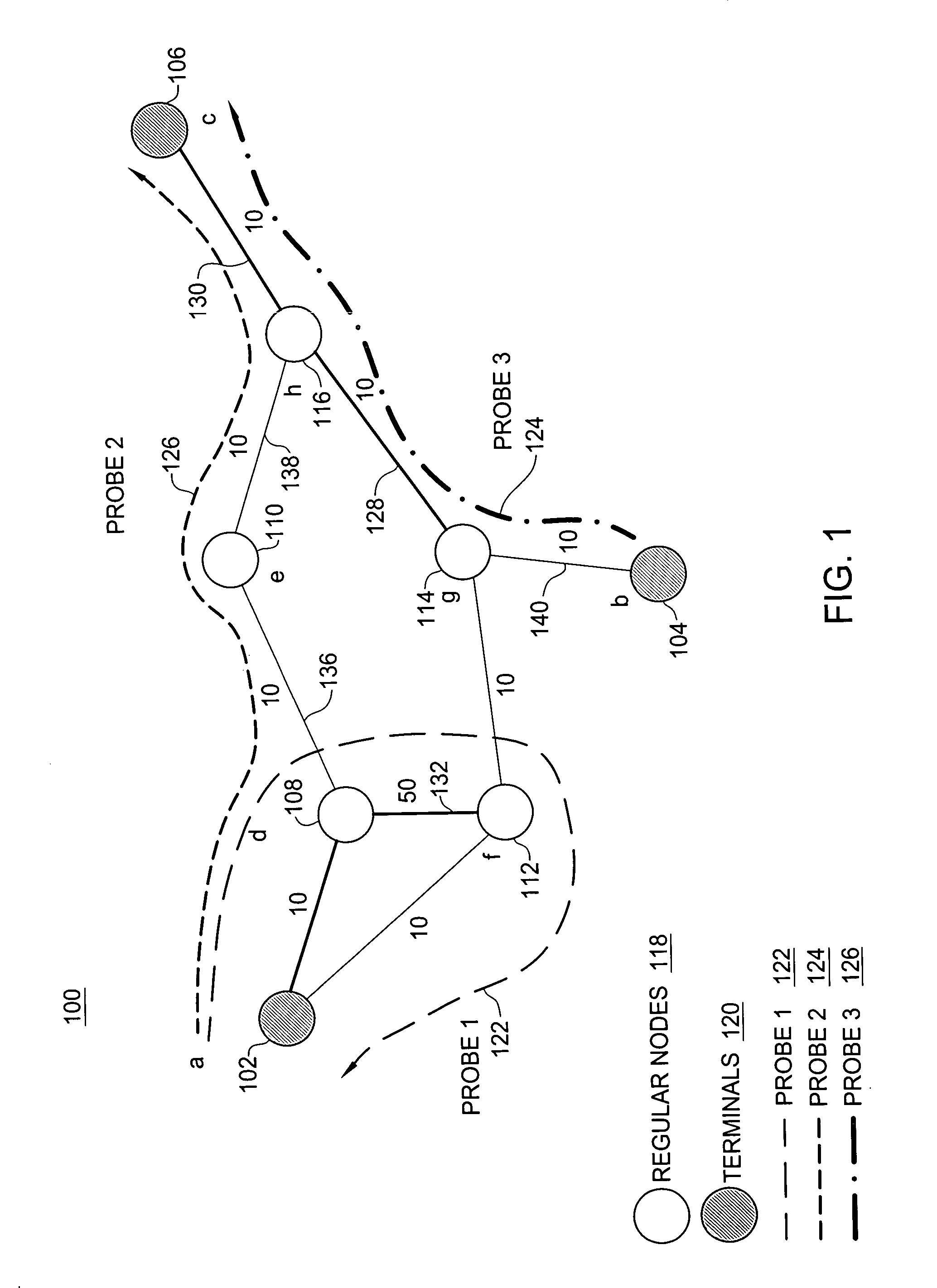
End-to-end service quality using source-routed probes
InactiveUS20070177518A1Low costError preventionTransmission systemsQuality of serviceTraffic capacity
The need to monitor real time network services has prompted service providers to use new measurement technologies, such as service-specific probes. A service-specific probe is an active probe that closely mimics the service traffic so that it receives the same treatment from the network as the actual service traffic. Service-specific probes are end-to-end and their deployment depends on solutions that address questions such as minimizing probe traffic, while still obtaining maximum coverage of all the links in the network. A polynomial-time probe-path computation algorithm is provided as well as a 2-approximate solution for merging probe paths when the number of probes exceeds a required bound k. The algorithms are evaluated using ISP topologies generated via Rocketfuel. For most topologies, it is possible to cover more than about 98% of the edges using just about 5% of the nodes as terminals.
Owner:ALCATEL LUCENT SAS
Online examination method of relay protection setting value based on dynamic short-circuit current
InactiveCN102074939ASafe and stable operationThe calculation result is accurateEmergency protective circuit arrangementsPower gridComputer science
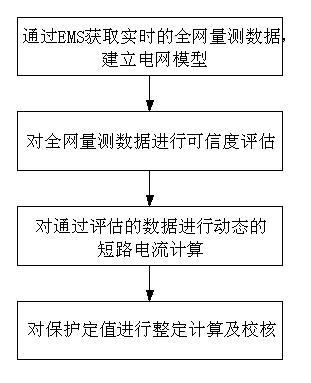
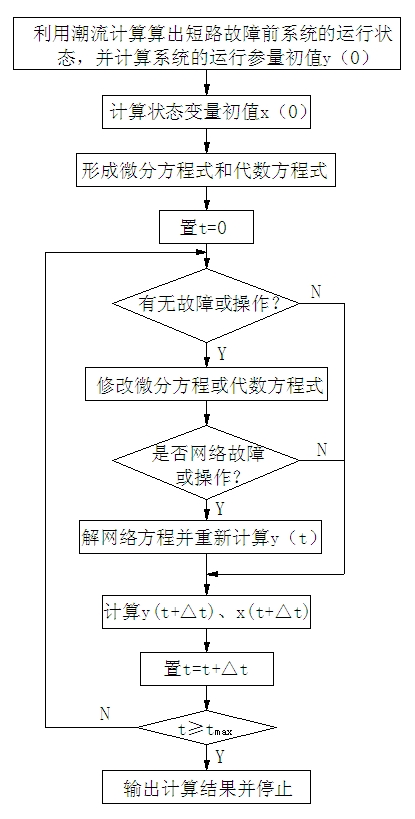
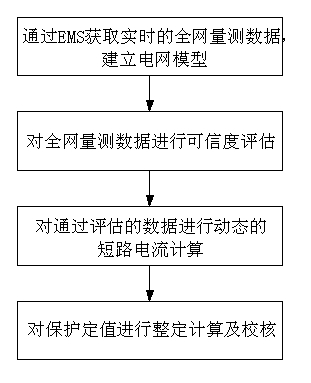
The present invention discloses an online examination method of relay protection setting value based on dynamic short-circuit current, which includes the following steps of: (1) obtaining real-time network-wide measurement data through EMS to establish an electrical network model; (2) carrying out a credibility assessment to the network-wide measurement data and to obtain the data which passes the assessment; (3) carrying out a dynamic short-circuit current calculation to the data passing the credibility assessment; (4) carrying out a setting calculation and examination of the protection setting value. The method enhances the accuracy of the short-circuit calculation result, realizes the online examination and real-time early warning of the relay protection setting value, and improves the automation degree of the protection setting value work.
Owner:NORTH CHINA GRID +1
IPhone smart phone based robot human-machine interactive system
InactiveCN101977240AImprove control convenienceConvenience for future lifeTelephonic communicationTransmissionSimulationInteraction technology
The invention relates to an iPhone smart phone based robot human-machine interactive system. The system comprises an iPhone console (1), a server (2), a controller (4), a robot (5), a network video module (6) and a CAN bus (3). The system breaks specific complexity and closure of the traditional robot control, various hardware resources such as iPhone smart phone and advanced interactive techniques (such as MULTI-TOUCH, accelerometer and the like) are innovatively combined with robot technology, and high usability human-machine interface (HMI) having novel human motion control analyzing function based on HMM is realized. 3G technology is utilized to access Internet, so as to construct a remote robot control platform with real-time network video feedback, and a high friendly robot human-machine interactive system with carrying convenience, flexible control and no distance restriction is developed.
Owner:NANKAI UNIV
Prepaid real-time web based reporting
InactiveUS6694000B2Prepayment with on-line account/card rechargingBilling/invoicingWeb browserPassword
Near real time Internet access of prepaid call history and replenishment data is provided via an Internet browser separate from the prepaid device to a user (e.g., the subscriber), allowing a subscriber to access call history and / or replenishment information nearly in real time (e.g., within a minute of the expense / credit) without requiring assistance from a customer service representative. A web based prepaid report page retrieves call history and / or replenishment information from the subscriber's service provider, and displays the same through a web browser for review by the subscriber. The requested call history and / or replenishment information may be bounded by date, date and time, or even within specific time range(s) within each day in a given range of days. The web based prepaid report page may also link the user to a replenishment application for the subscriber, to assist the subscriber in replenishing their account after having reviewed their call history and prepaid account status in near real time. The call history and account balance information is preferably updated in near real time after the completion of a call, which is then accessed by the web based prepaid report page. Substantially immediately after a prepaid call is ended, the web based prepaid reporting application formulates a Call Detail Record (CDR) and sends it over a TCP / IP link to the web based prepaid reporting application, which stores the CDR in a local database. Then, a user may access this CDR / RR information in near real time, after appropriate log-in with, e.g., a user ID of the subscriber (e.g., MIN number based), and perhaps a password. Once the requested information is entered, the web based prepaid reporting application queries its local database, formats an appropriate response to the user's request, and presents the call history and / or replenishment information to the web browser of the user.
Owner:SLINGSHOT TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com