Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
49 results about "Ddos defense" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
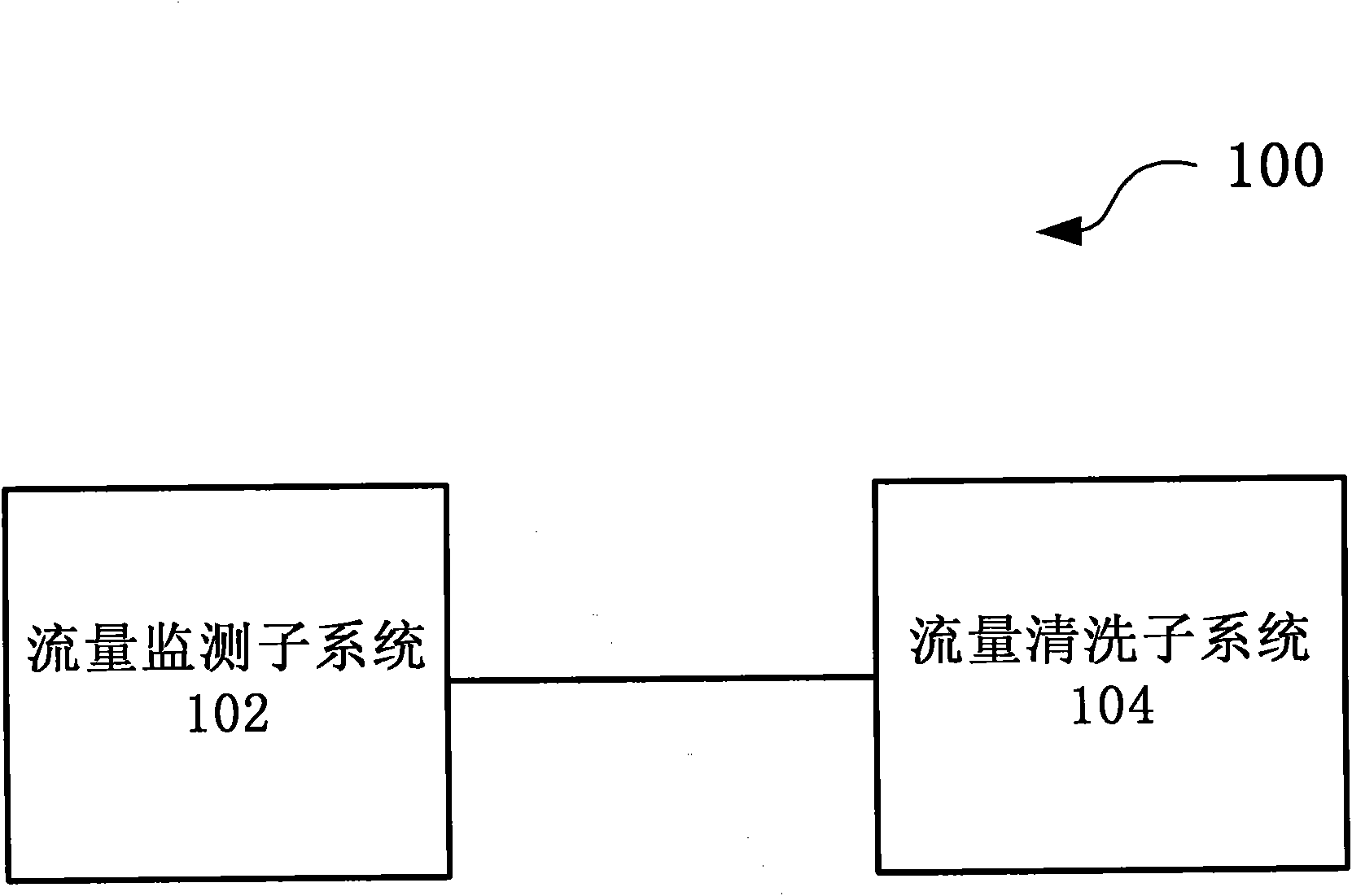
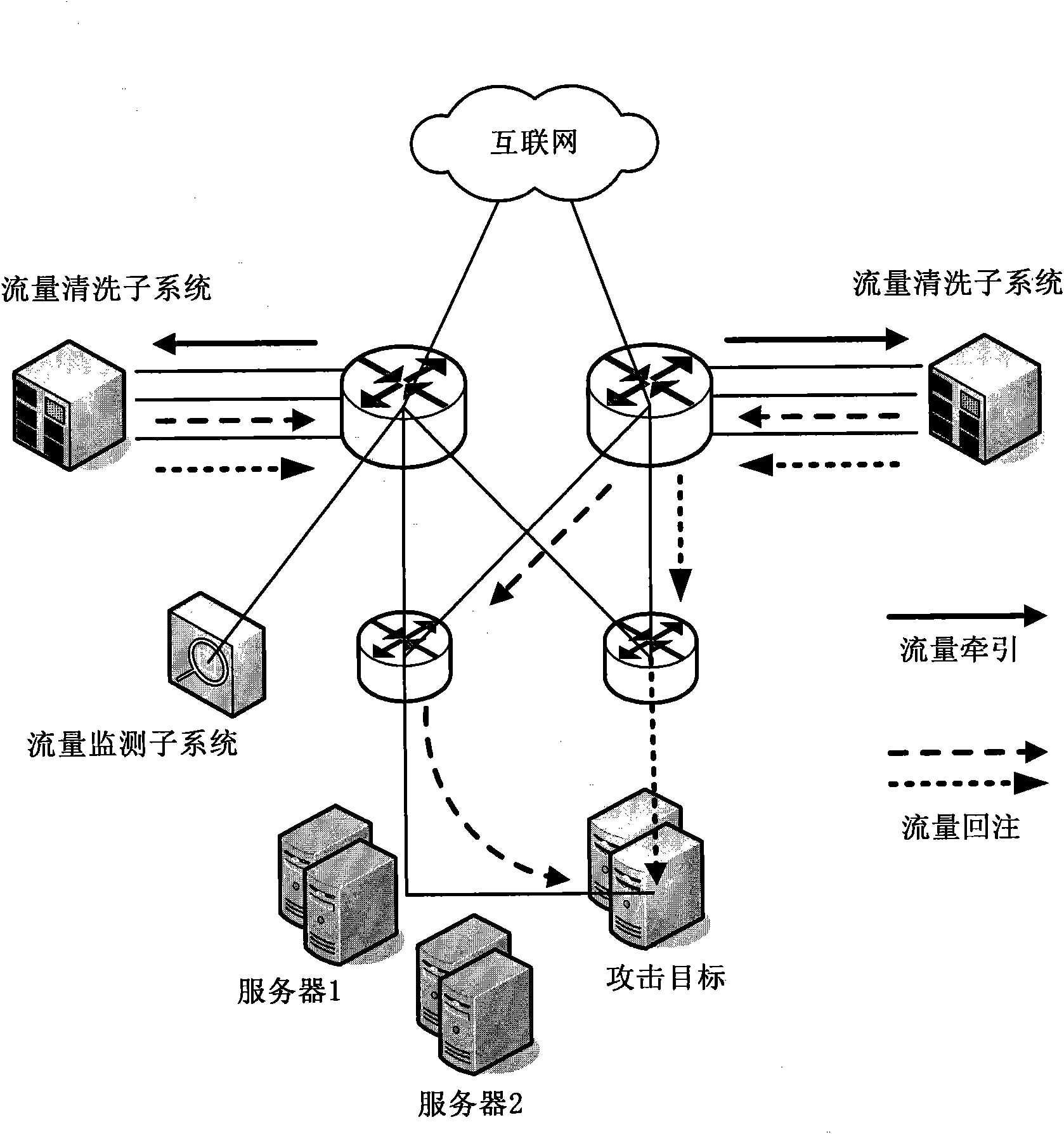
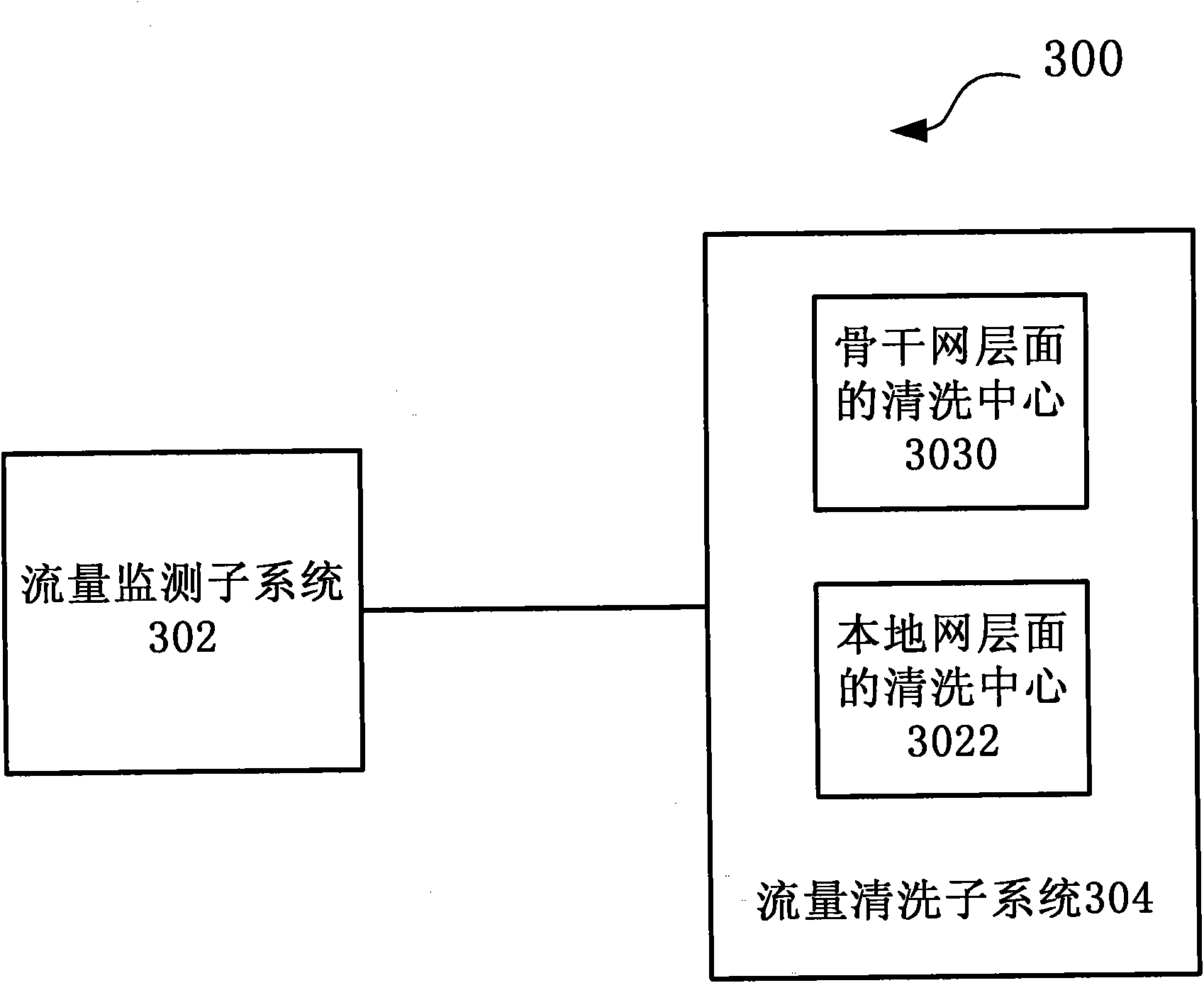
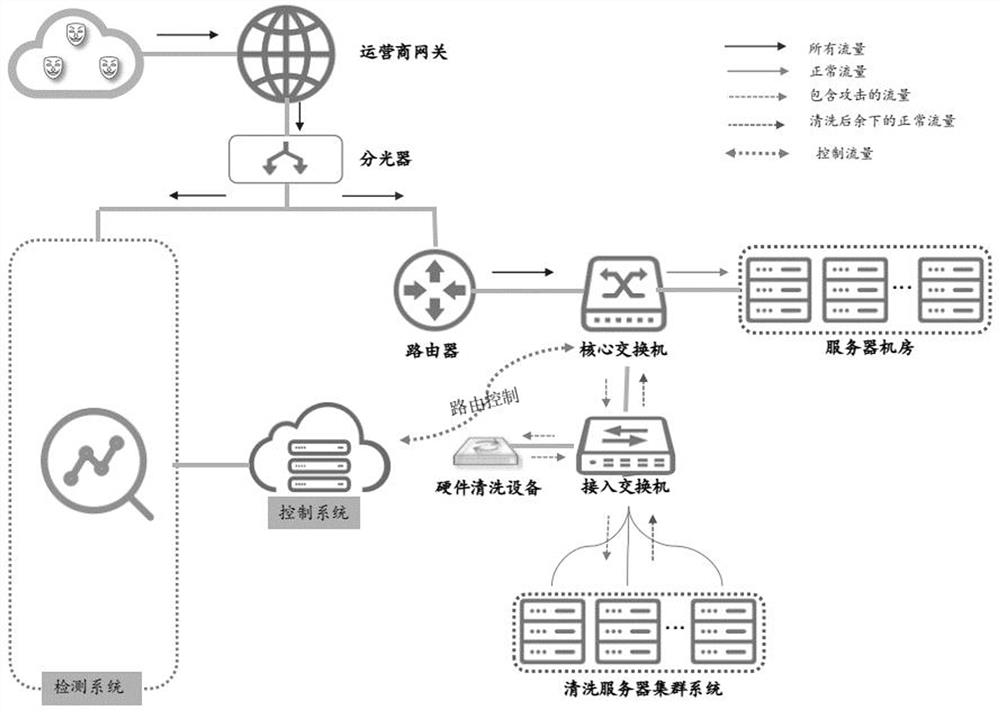
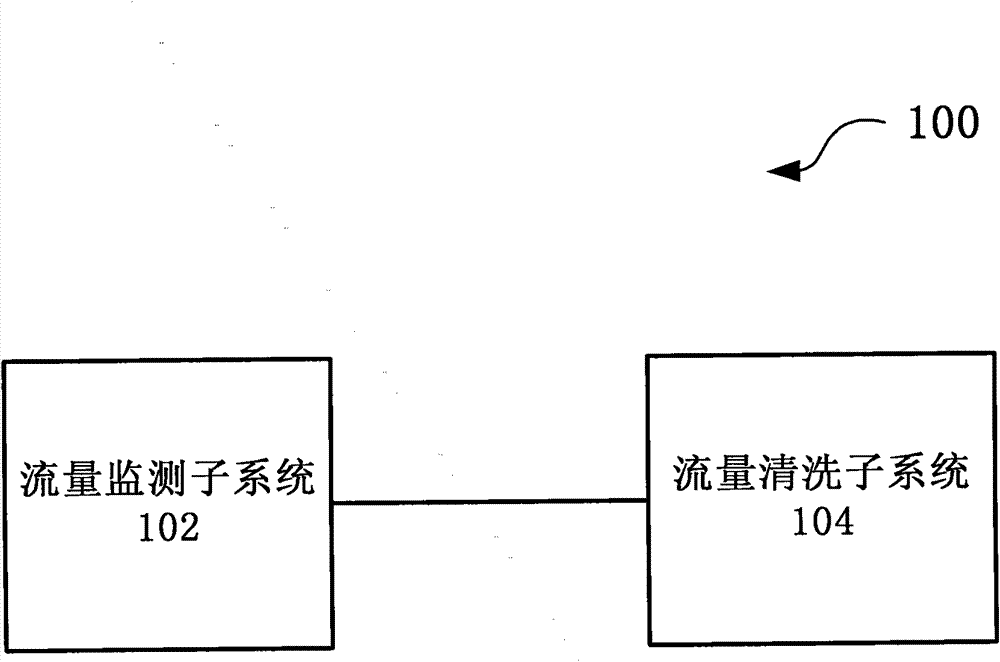
Large-scale DDoS (Distributed Denial of Service) attack defense system and method based on two-level linkage mechanism
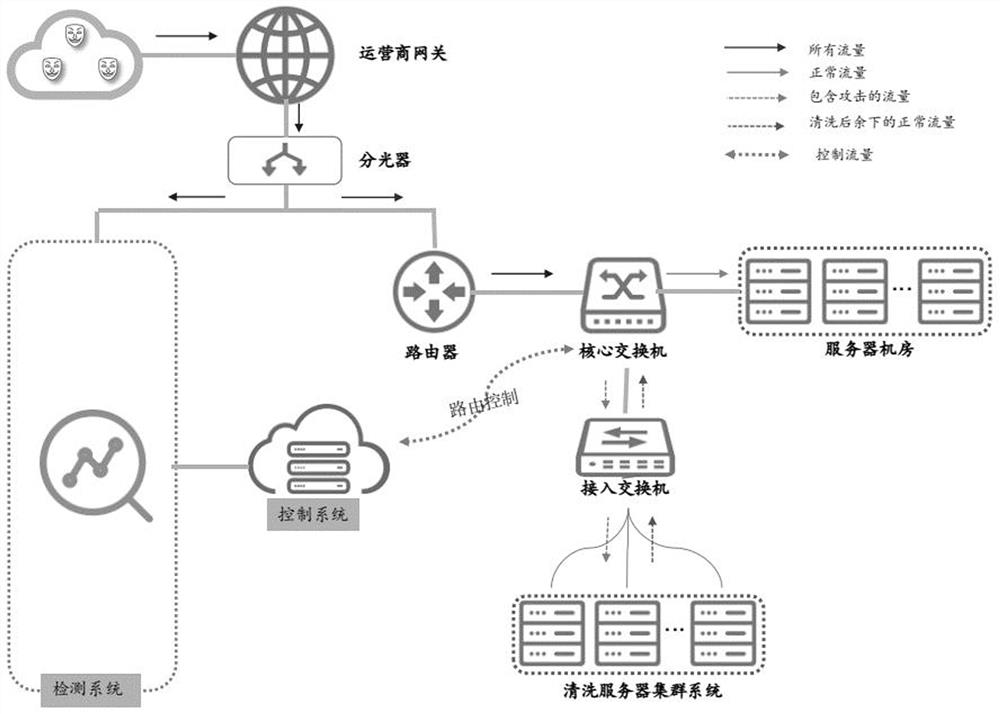
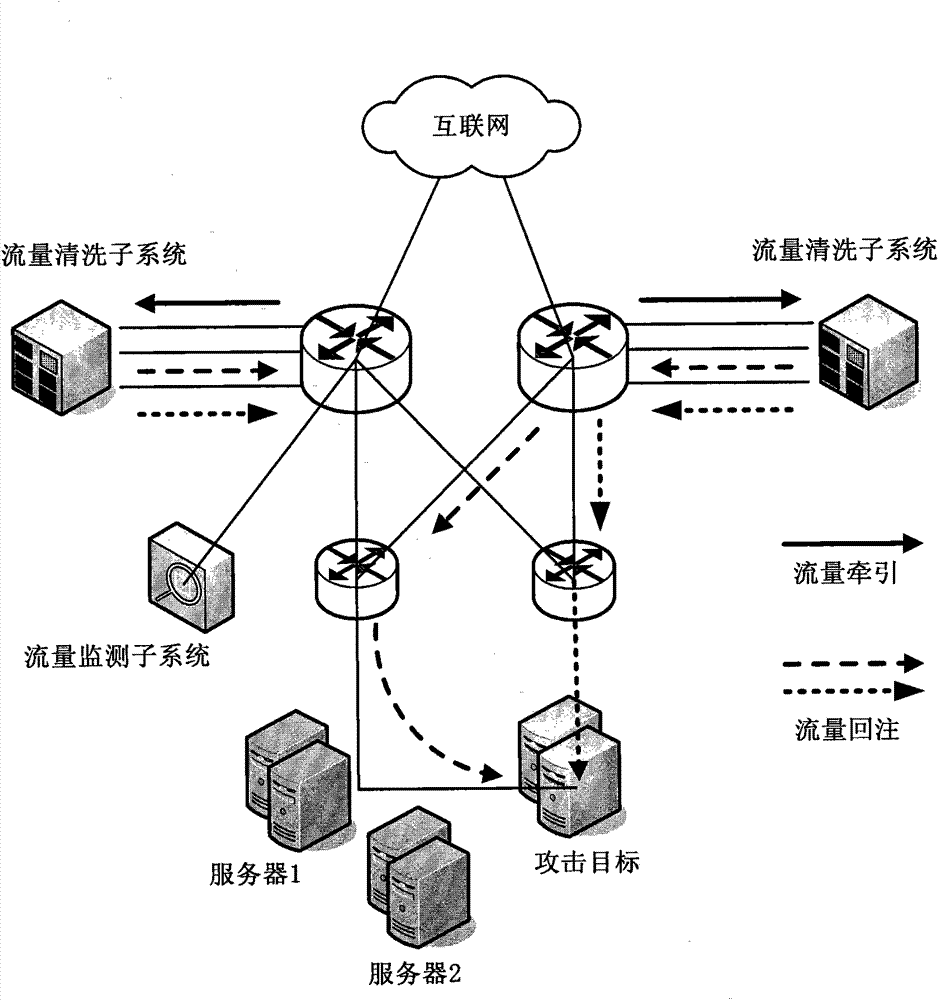
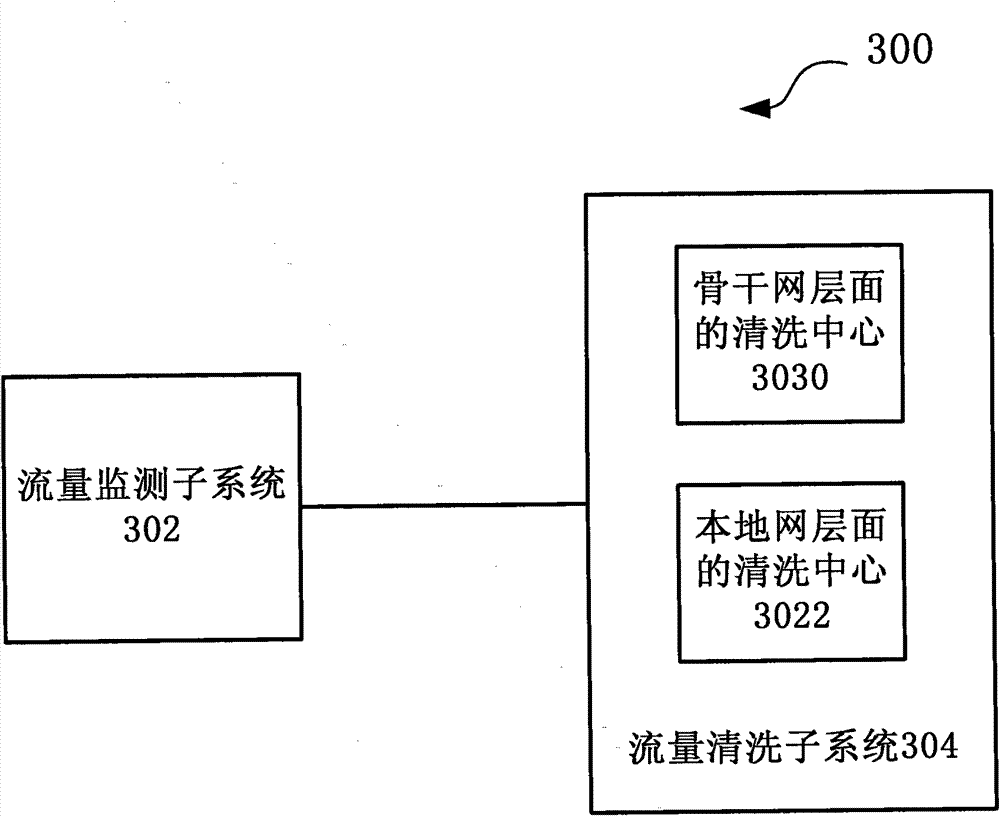
The invention discloses large-scale DDoS (Distributed Denial of Service) attack defense system and method based on a two-level linkage mechanism. The method comprises the following steps of: monitoring the flow of a total network by a flow monitoring subsystem in real time, and searching and confirming a DDoS attack behavior; sending an alarm message for triggering a cleaning operation to a flow cleaning subsystem, and guiding the abnormal flow of the DDoS attach behavior to the flow cleaning subsystem; receiving the abnormal flow guided by the flow monitoring subsystem by the flow cleaning subsystem, cleaning the abnormal flow according to the cleaning operation triggered by the alarm message, (wherein the flow cleaning subsystem adopts the two-level architecture of a backbone network plus a local network defense system, and the two levels of cleaning system work cooperatively and clean synchronously), and injecting the cleaned cleaning flow back to a target customer network. The large-scale DDoS attack defense system and method based on the two-level linkage mechanism solve the problems of cleaning capacity, cleaning precision, and the like existing in the traditional DDoS defense technology; and on the basis of reducing the deployment cost of service scale, the large-scale DDoS attach defense capability of the total network is greatly improved, and the cleaning precision ofthe attack flow is increased.
Owner:CHINA TELECOM CORP LTD
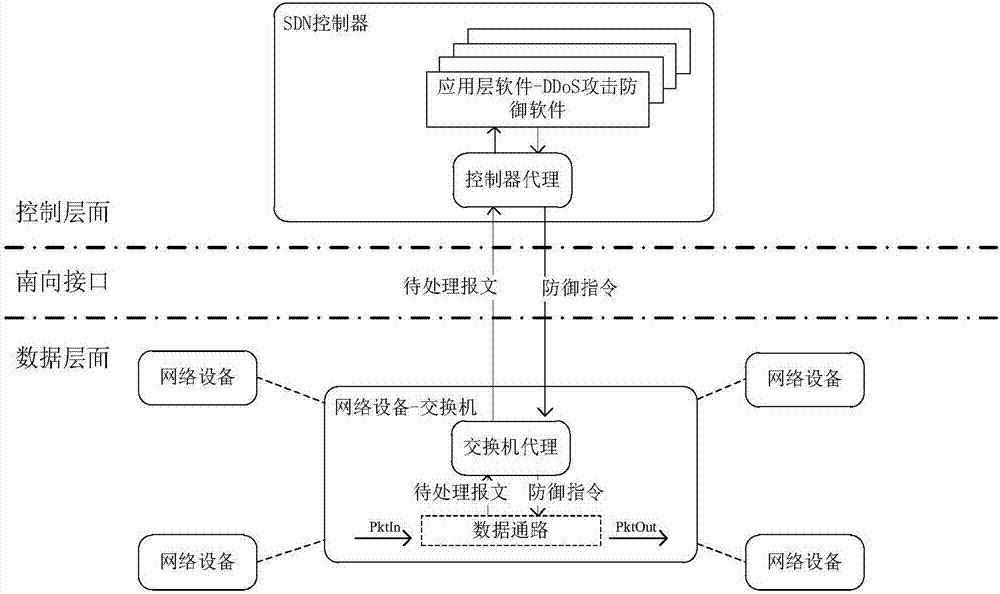
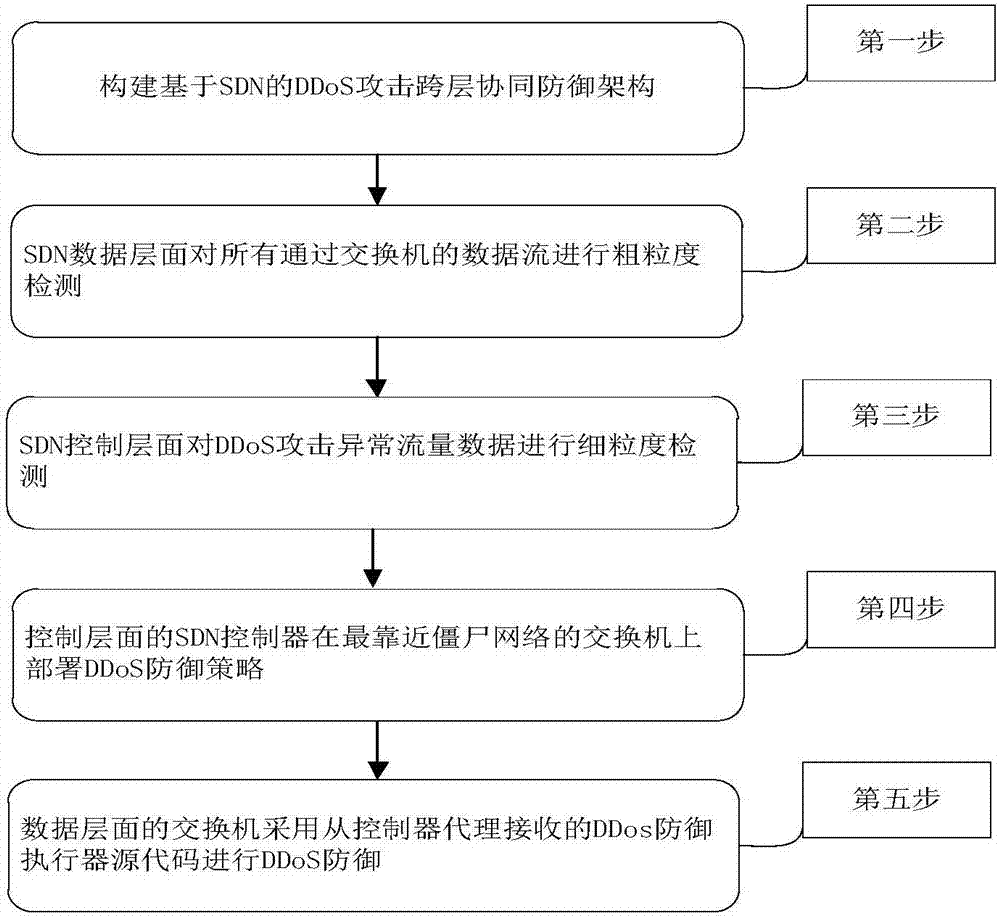
Software defined network-based DDoS attack cross-layer cooperative defense method
The invention discloses a software defined network-based DDoS attack cross-layer cooperative defense method and aims to solve the problems of over high communication pressure of a southbound interfaceand a control plane as well as over high calculation pressure of an SDN controller. According to the technical scheme, the method comprises the following steps: constructing an SDN-based DDoS attackcross-layer cooperative defense framework comprising a data plane and a control plane, performing coarse-grained detection on data flow by the data plane to acquire DDoS attack abnormal flow data, andperforming fine-grained detection on the DDoS attack abnormal flow data by the control plane to acquire an exchanger closest to a bot network; deploying a DDoS defense strategy on the exchanger closest to the bot network by the SDN controller of the control plane, and performing DDoS defense according to the DDoS defense strategy by the SDN exchanger of the data plane. Through cooperation of thedata plane and the control plane, the cooperative defense advantage of the SDN is completely utilized and the problems of high pressure of the SDN southbound interface and too large burden of the SDNcontroller are solved, so that the exchanger can perform automatic defense intelligently.
Owner:NAT UNIV OF DEFENSE TECH
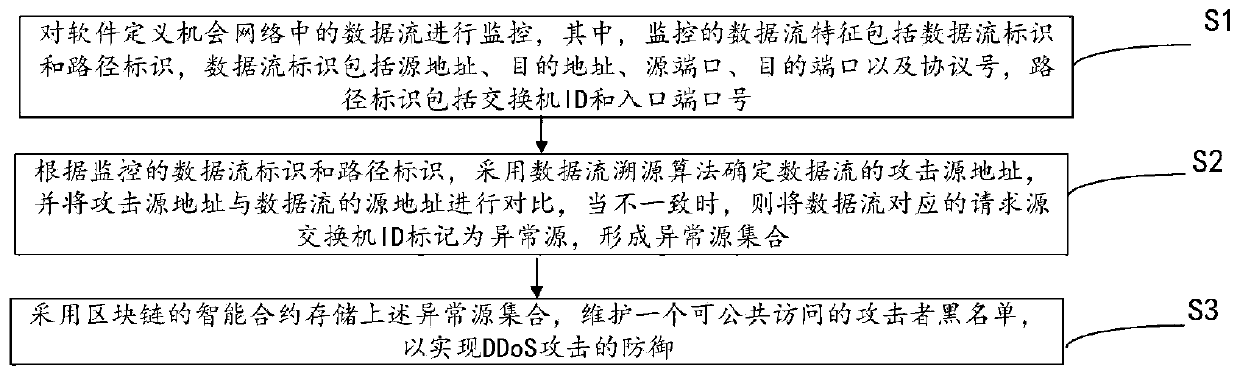
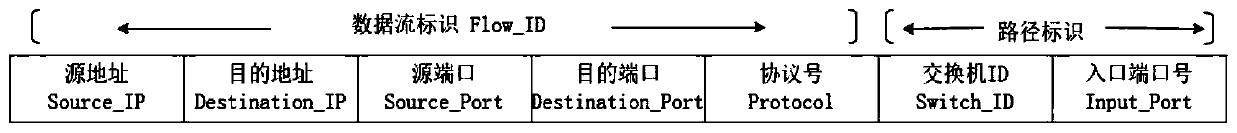
Software defined opportunity network DDoS defense method based on block chain
ActiveCN110113328AGuaranteed reliabilityPrevent tamperingTransmissionTraffic characteristicControl layer
The invention discloses a software defined opportunity network DDoS defense method based on a block chain. Firstly, the characteristic that the SDN can perform logic centralized management and controlon a control layer is utilized; the network state is dynamically monitored in real time; then, the possibility of existence of a DDoS amplification attack is analyzed by analyzing the traffic characteristics obtained by monitoring, an attacker address is determined according to a traceability algorithm, and finally, a public accessible attacker blacklist is maintained by using a block chain architecture to assist an application layer in malicious traffic filtering so as to realize defense of the DDoS attack. According to the method, the attack source tracking accuracy is improved, the storage of the attack source blacklist address is realized in combination with the block chain architecture, and the attack source storage architecture based on the distributed account book technology can effectively prevent the data from being tampered or damaged while maintaining the data reliability. The whole network can perform filtering in a data packet receiving stage by inquiring a blacklist address, so that the DDoS attack is prevented from the source.
Owner:WUHAN UNIV OF TECH
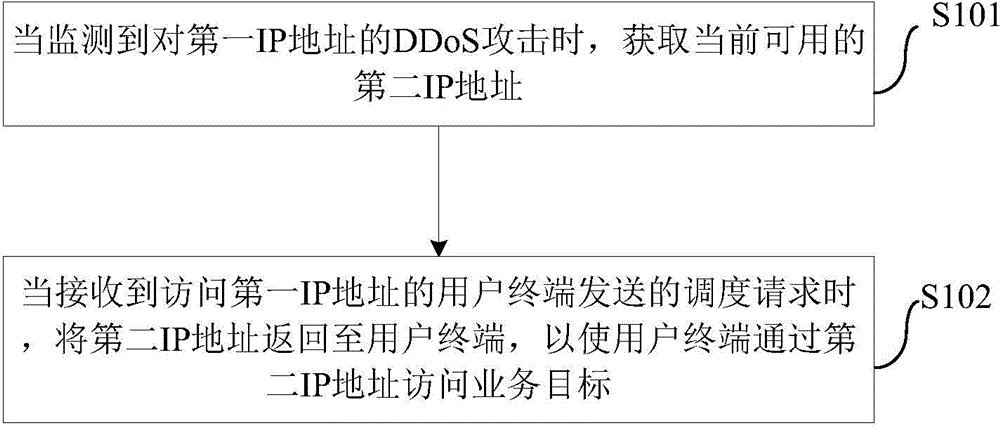
Dispatching system-based DDoS (distributed denial of service) defense method and DDoS (distributed denial of service) defense system
The present invention provides a dispatching system-based DDoS (distributed denial of service) defense method and a DDoS (distributed denial of service) defense system. The method includes the following steps that: when a DDoS attack to a first IP address is monitored, a currently available second IP address is obtained; and when a dispatching request sent by a user terminal which accesses the first IP address is received, the second IP address is sent to the user terminal, so that the user terminal can access a service target through the second IP address. With the dispatching system-based DDoS (distributed denial of service) defense method provided by the embodiments of the present invention adopted, influences of the DDoS attack can be reduced to a controllable range, defense cost can be reduced, influence on the service target accessed by a user which is caused by wrong attack killing can be greatly reduced, and the experience of a user subjected to attacks can be improved.
Owner:ALIBABA GRP HLDG LTD
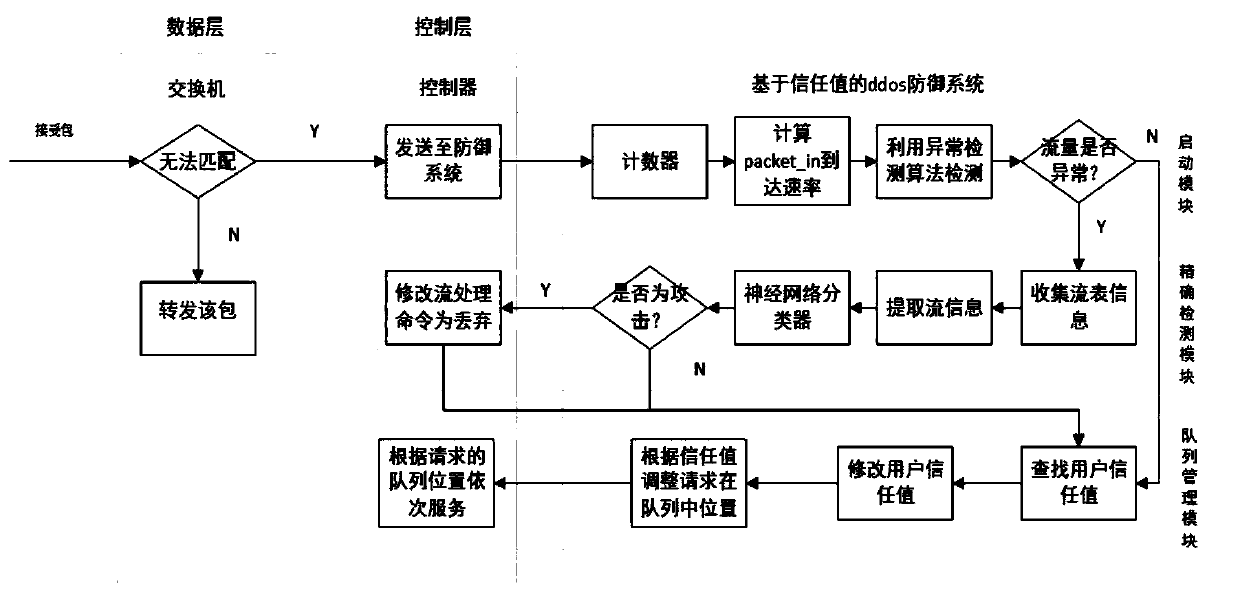
Self-adaptively started ddos defense method and system based on trust value in SDN
ActiveCN106657107AReduce resource usageGuaranteed detection accuracyTransmissionTraffic capacityControl layer
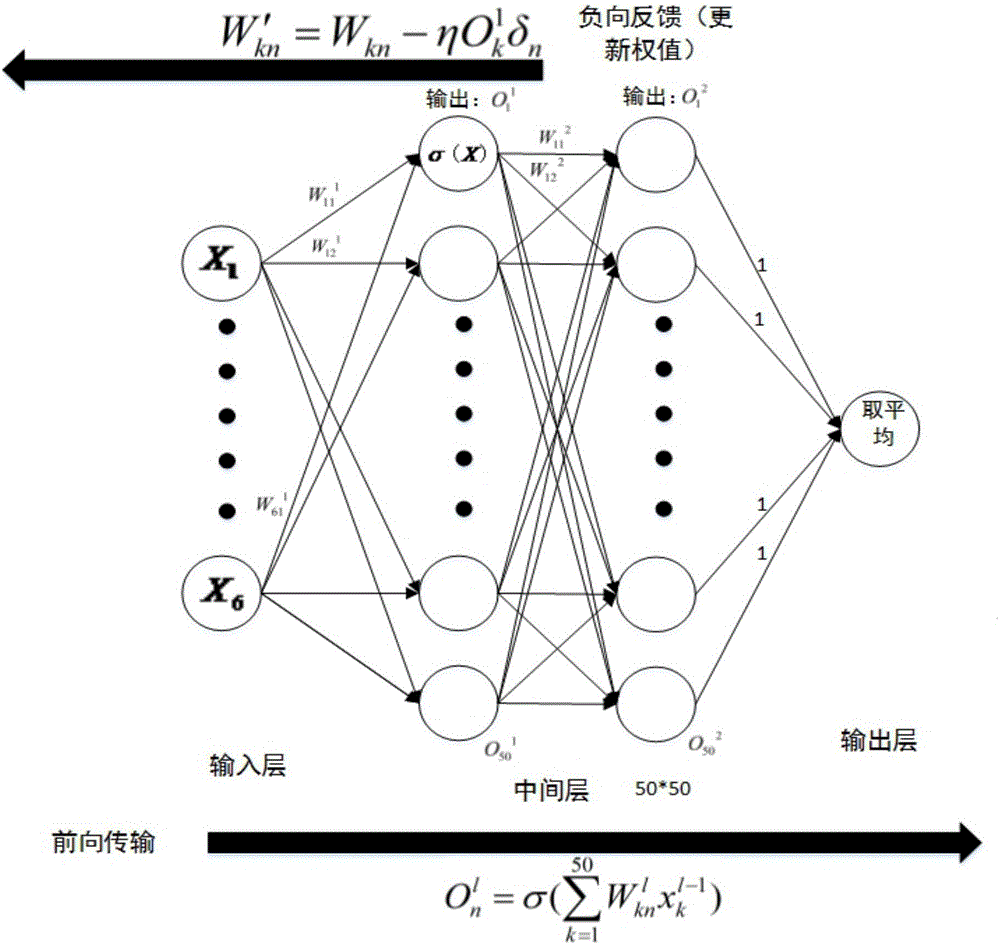
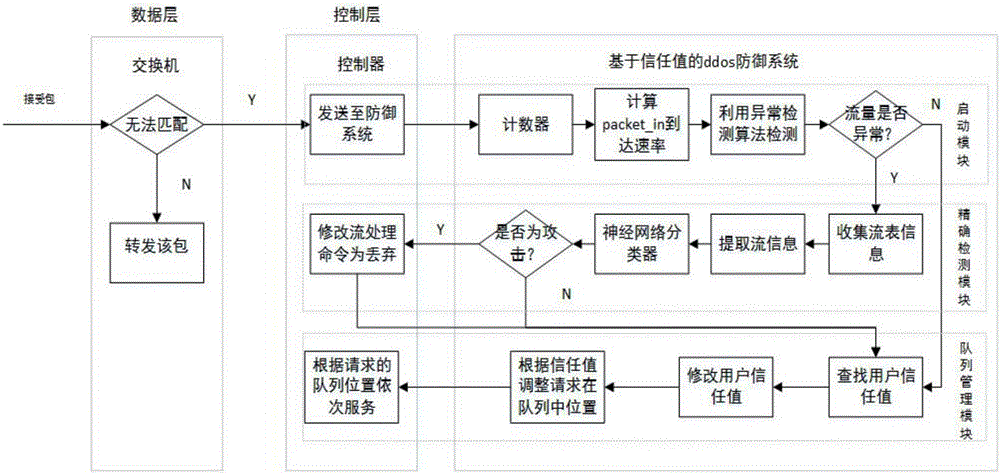
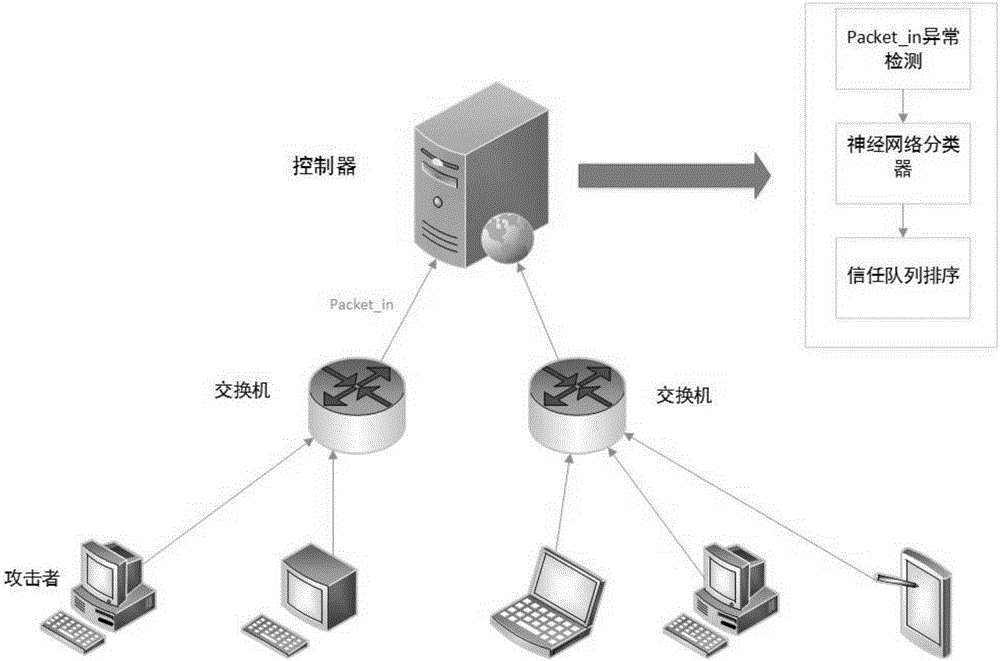
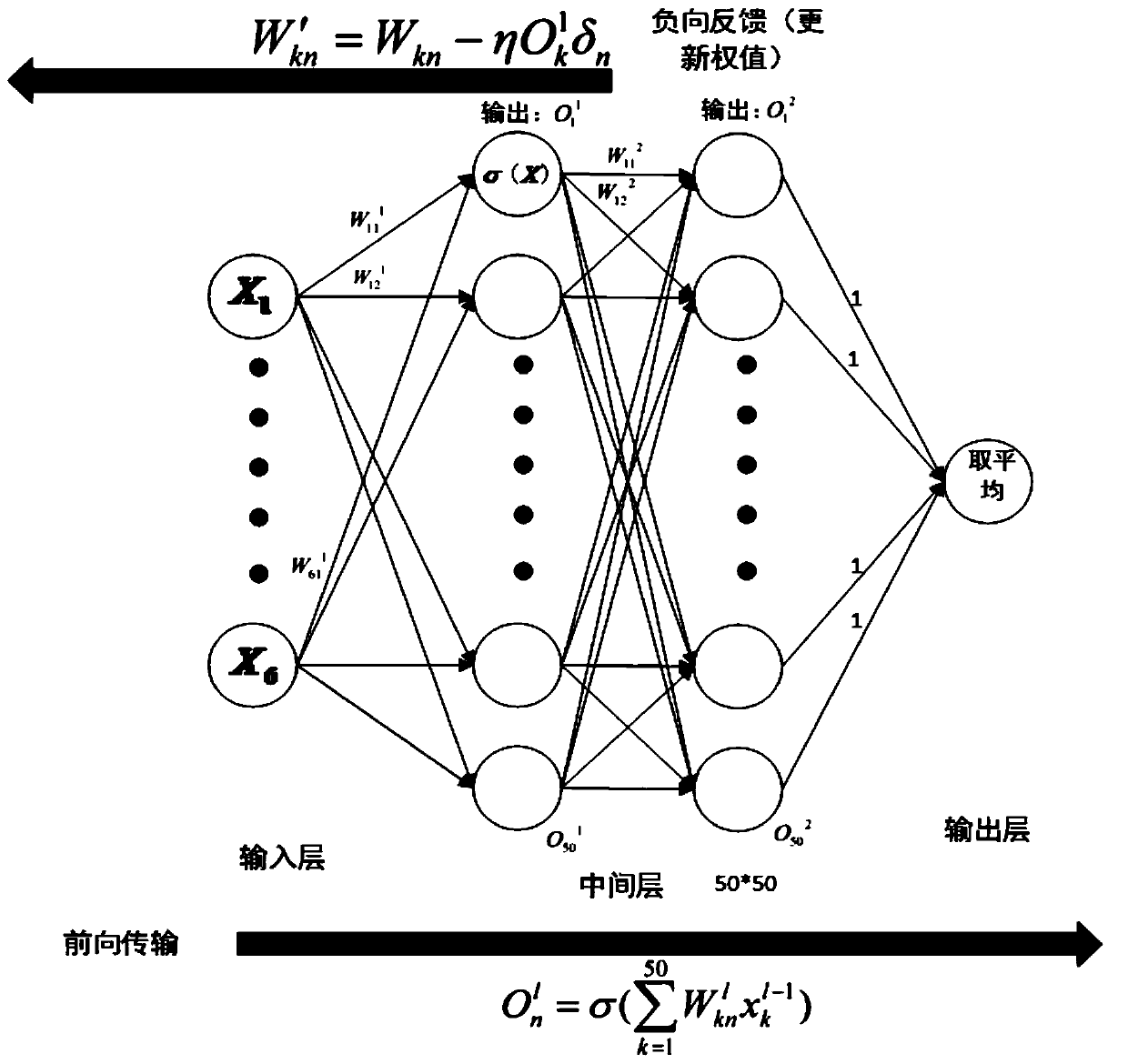
The invention discloses a self-adaptively started ddos defense method based on a trust value in an SDN. The self-adaptively started ddos defense method comprises the following steps: a switch receives an unmatched packet, and sends a packet_in data packet to a controller; a counter is deployed in an SDN controller; the counter pre-sets a packet_in number value; when an arrival packet_in number is equal to a set value every time, the packet_in arrival rate in the time period is calculated; then, whether the packet_in arrival rate is abnormal or not is judged; the flow on the switch corresponding to packet_in is precisely detected by utilization of a reverse neural network classifier; a neural network, an intermediate layer of which is 50*50, is established; six characteristic values are calculated; training is carried out by taking the six characteristic values as input of the classifier; and, if the output value of the neural network is between 0.5 and 1, the fact that the flow is a ddos attack is determined. By means of the self-adaptively started ddos defense method and system based on the trust value in the SDN disclosed by the invention, the characteristics of the SDN, such as flow table information of a data layer and control of the controller in a control layer to the whole network, are sufficiently utilized; and thus, the ddos attack in the SDN can be effectively defensed.
Owner:NANJING UNIV OF POSTS & TELECOMM
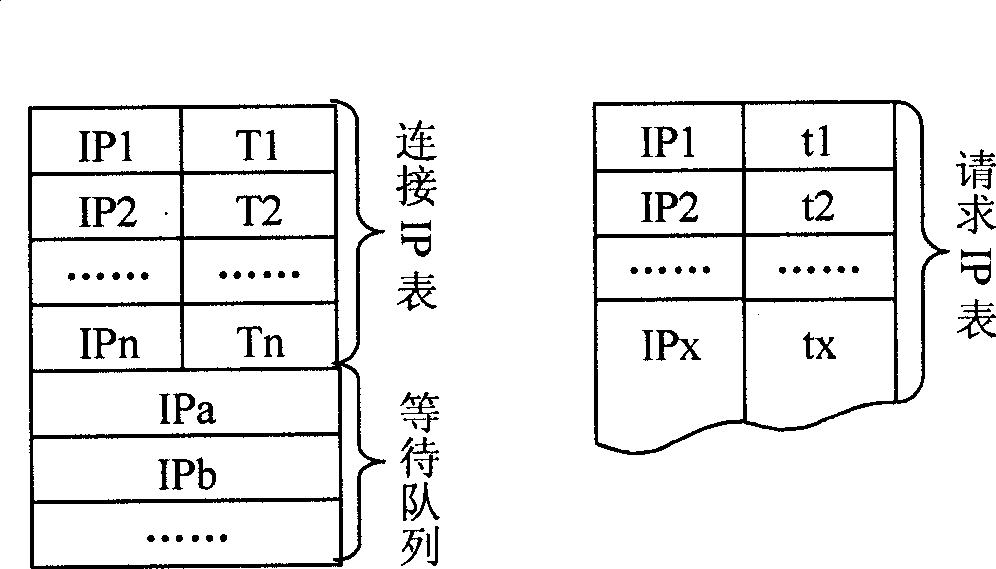
IP spoofing DDoS attack defense method based on active IP record
InactiveCN101383812ABreak down the pressure of attack defenseNetwork connectionsTraffic capacityData stream
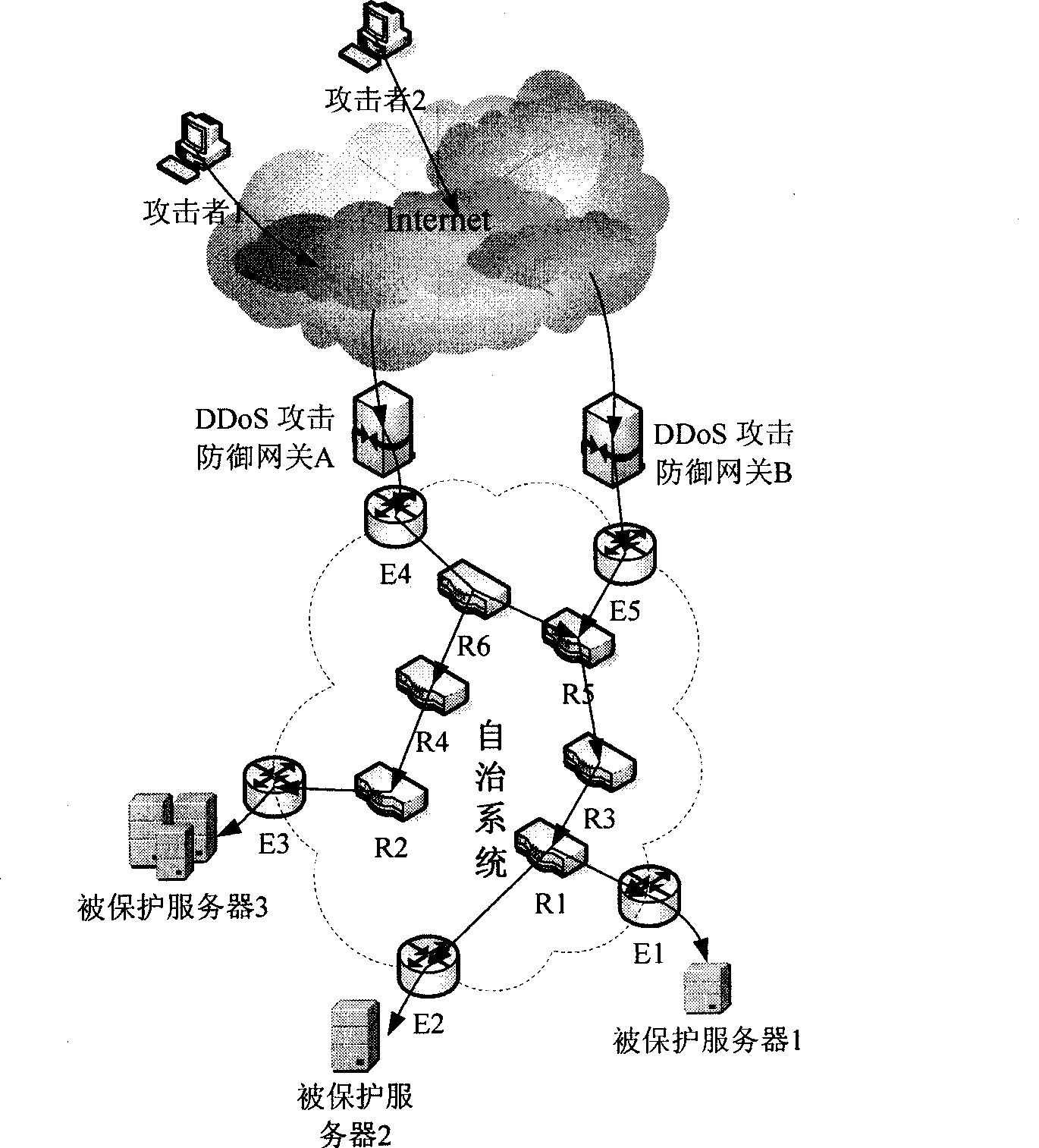
The invention discloses a defense method aiming at IP deception DDoS (Distributed Denial of Service) attack. The method is based on active IP records; the active IP is a source IP address which has established or is establishing connection with a system, the IP deception DDoS attack generally uses a randomly generated IP as a data stream source address, the IP is a non-active IP, a data stream from the active IP according to the principle can be regarded as a legal stream flow and a network stream from the non-active IP is regarded as a suspicious stream flow, therefore, a DDoS defense gateway which is positioned at the boundary of an autonomous system can use an active IP record form to carry out the matching process to data packets of the autonomous system, the network stream from the active IP passes through directly, the IP data packets without active records are discarded by a router at the boundary of the autonomous system or a router near the boundary and sends an ICMP time out error message to notify source nodes. The data packet of the IP deception DDoS attack with the non-active IP can not reach victimized nodes. The discarded data packet carries out retransmission by the upper layer protocol or application of the source nodes.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
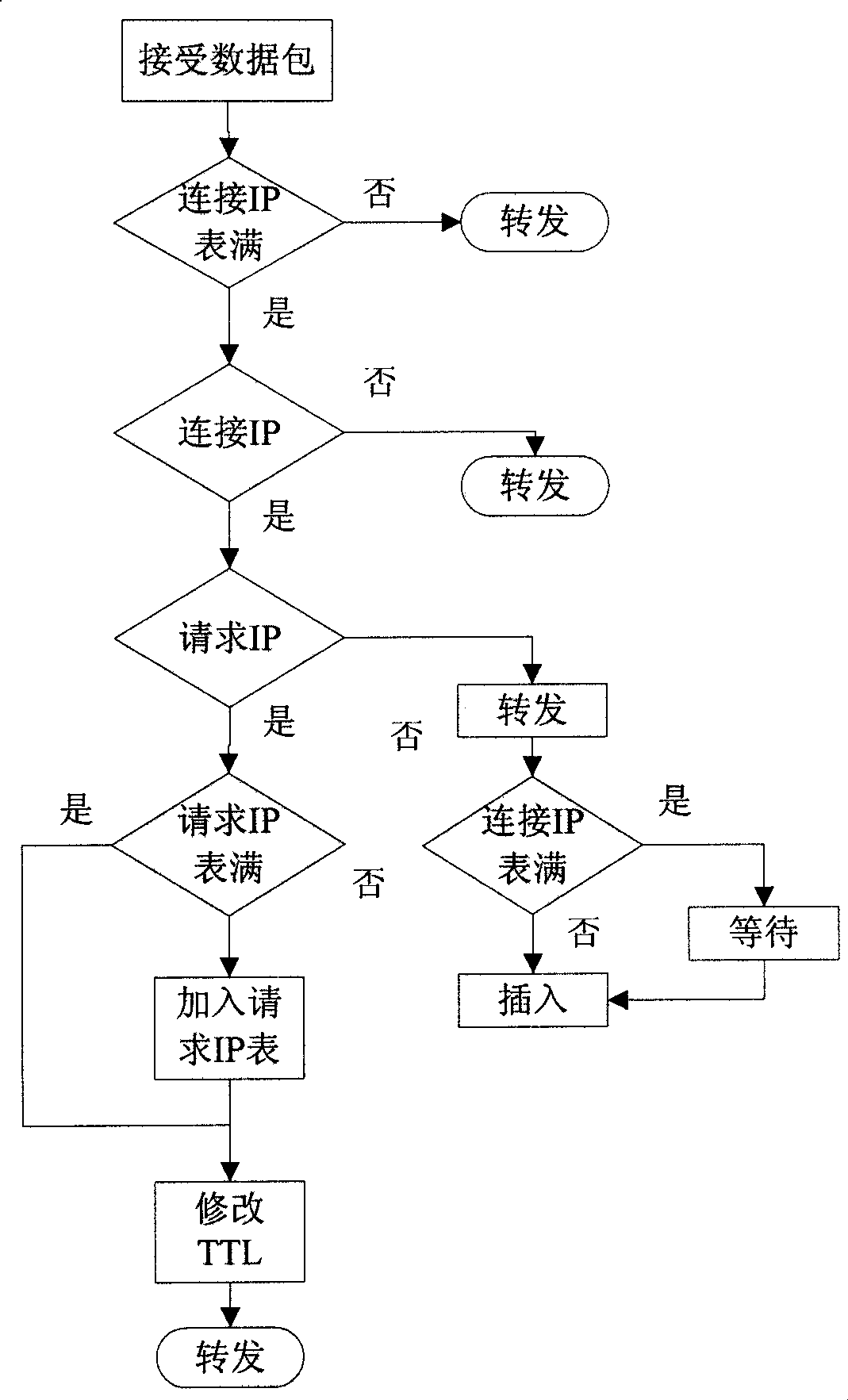
Link type DDoS defense method and system based on migration of forward path
The invention provides a link type DDoS defense method based on migration of a forward path, applied to SDN. The method comprises the steps of 1, constructing a network flow matrix and positioning a congested link by collecting LLDP messages; 2, judging whether the congested link forms a link flooding attack; 3, if the link flooding attack exists, recognizing a suspicious network flow in the congested link; and 4, selecting a migrating link set not close to the congested link according to a constraint condition, selecting the network flow to be migrated and a migration interval, and generating migration rule information; and migrating the suspicious work flow according to the migration rule information. The method is implemented in the software definition network based on OpenFlow. According to the method provided by the invention, deployment of a link type DDoS defense system is achieved by using components easy to maintain and migrate. Meanwhile the system for implementing the method is provided.
Owner:INST OF INFORMATION ENG CAS
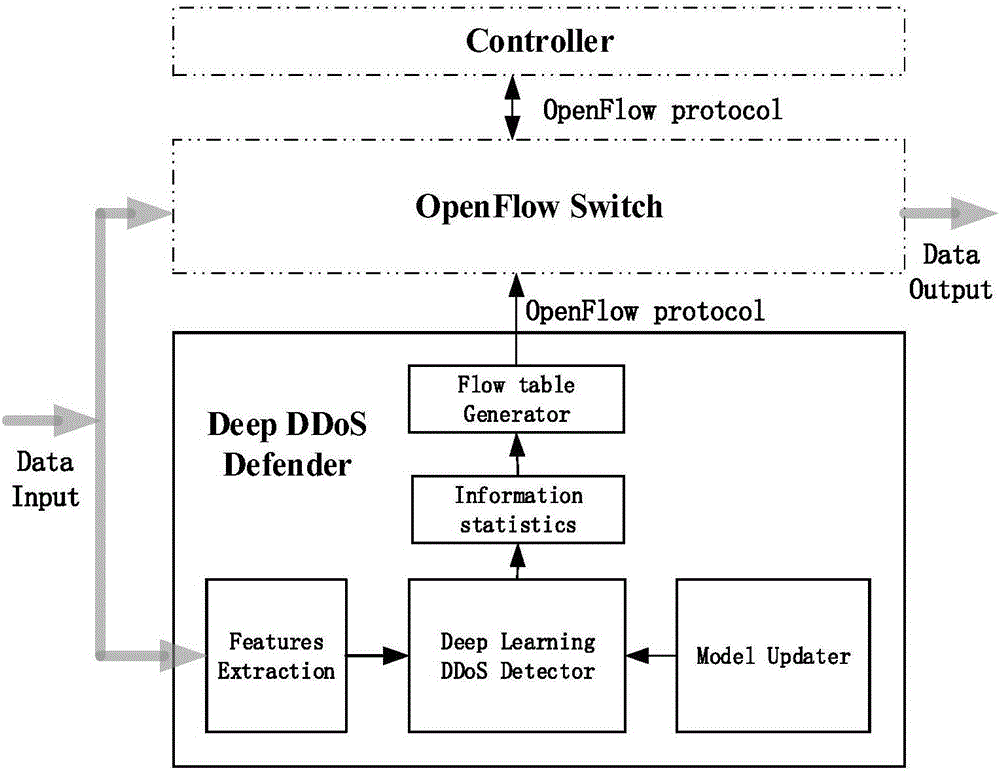
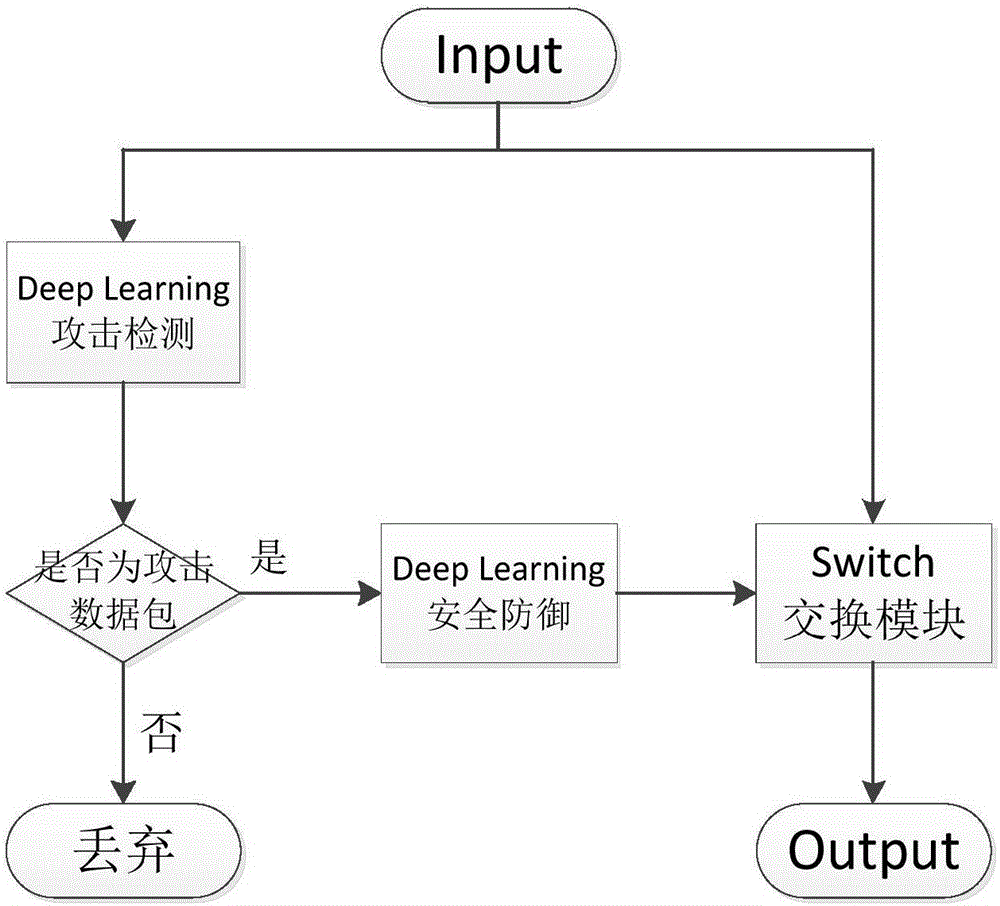
Deep learning based DDOS defensive device and method in SDN
ActiveCN106534133AImprove detection efficiencyImprove accuracyTransmissionLearning basedNetwork packet
The invention discloses a deep learning based DDOS defensive device and method in SDN. The device comprises a feature extraction module, a deep learning DDOS detection module, a Model Updater module, an information statistics module and a flow table generation module. The feature extraction module extracts features of an input data packet in the system to construct a feature matrix, processed features are input to the deep learning DDOS detection module, and the deep learning DDOS detection module uses a learned model to determine whether the input data packet in the present system is an attack packet. According to the invention, deep learning is used to detect the data packet input to the system, and compared with a traditional DDOS attack invasion detection method, the detection efficiency and the accuracy are improved greatly.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
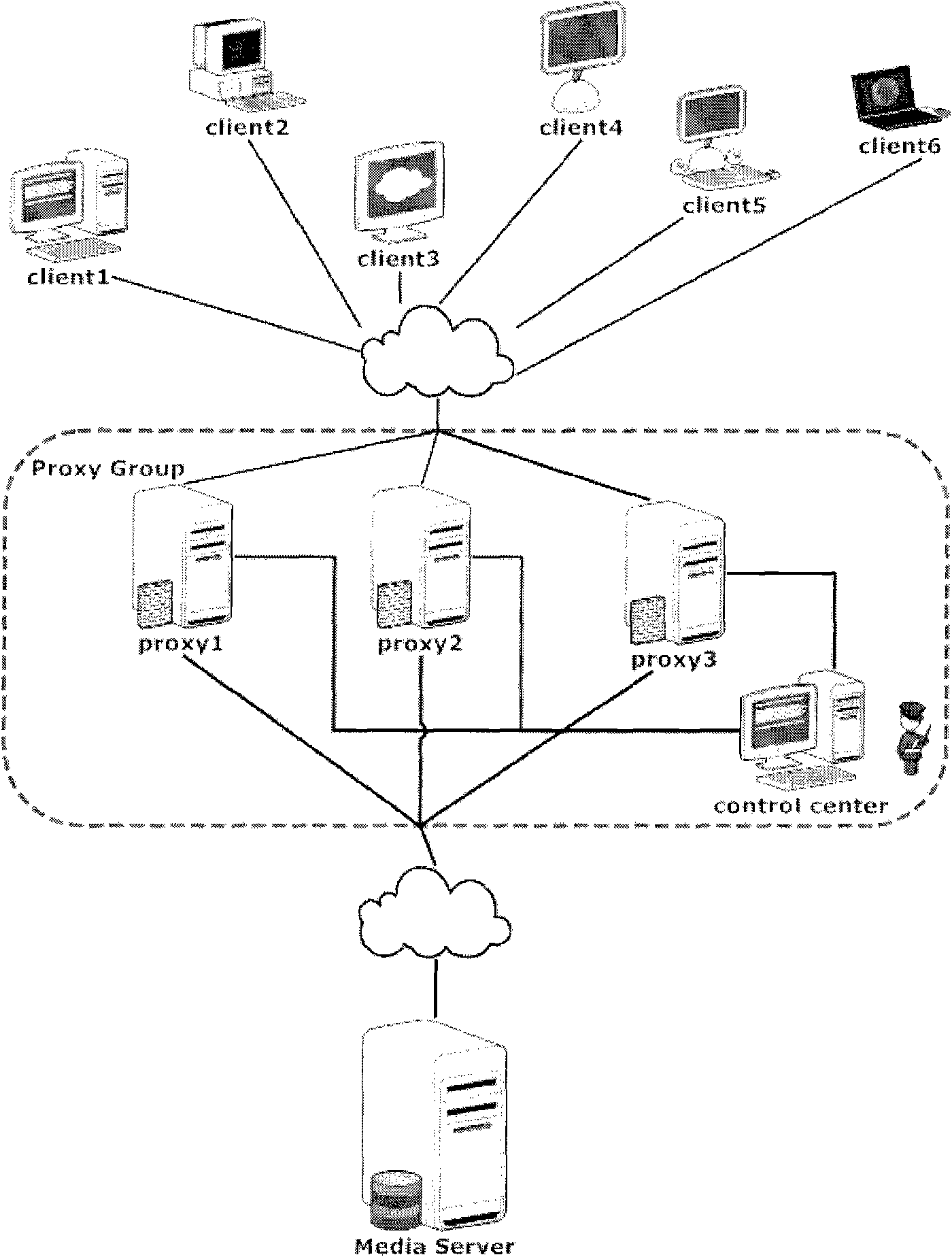
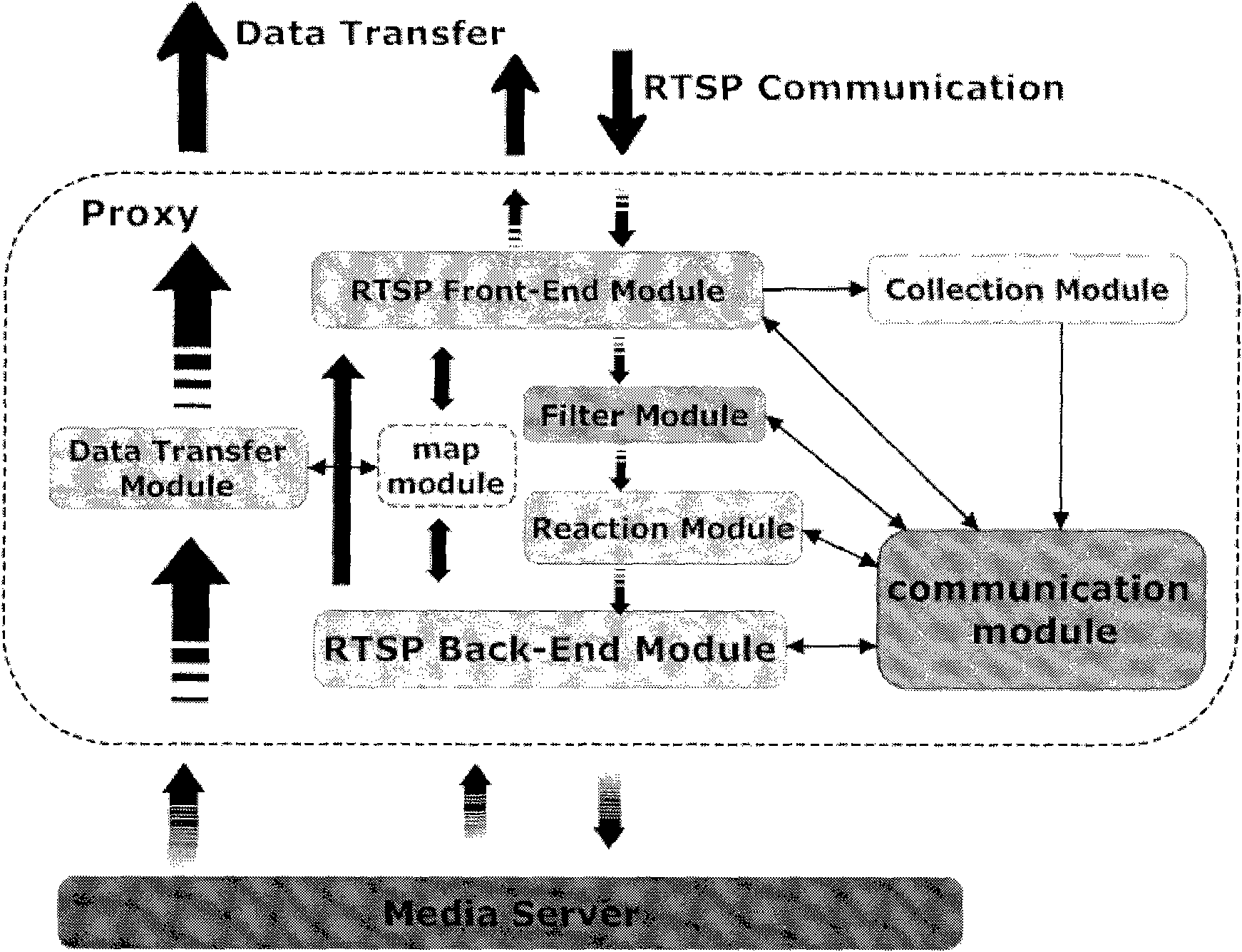
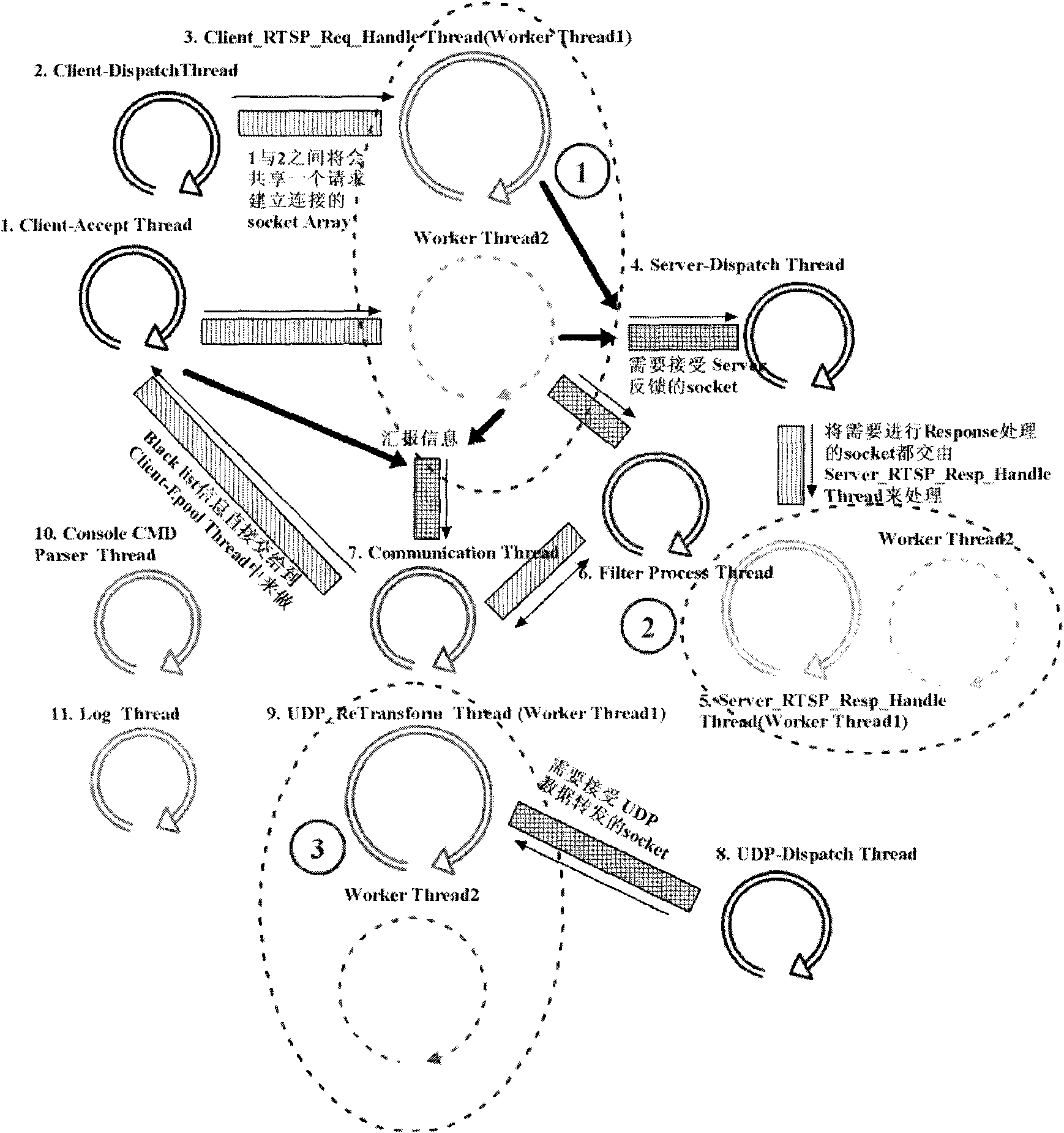
DDOS attack defense system and method for streaming media server application layer
The invention discloses a DDOS attack defense system and a method for a streaming media server application layer, the attack defense system is used for defending against DoS and DDoS attacks of a streaming media server system; the streaming media server system comprises a server host and at least one client; and the defense system is connected with the server host and the client. The attack defense system comprises at least one streaming media service proxy module and a control central module. The streaming media service proxy module is responsible for forwarding of streaming media control information and data information, collection of a variety of statistical information and final implementation of a defense decision; and the control central module is used for overall monitoring of the current state of the whole streaming media server system and emitting a command to a proxy for carrying out defense. The prospective study is based on various DDOS attacks of the streaming media RTSP, and a set of streaming media DDOS defense system based on a PROXY GROUP is designed, thereby effectively ensuring the safety of streaming media service on Internet without authorization.
Owner:SHANGHAI CLEARTV CORP LTD
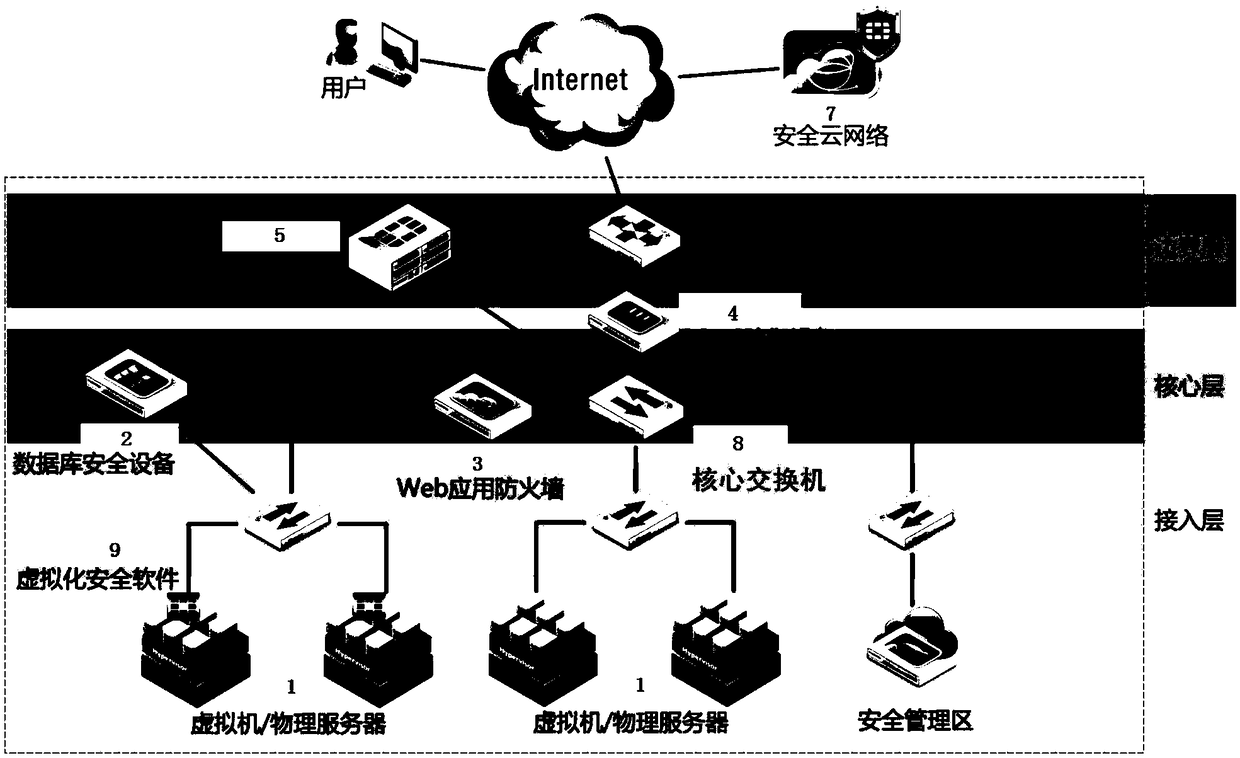
Smart city information security guarantee system
InactiveCN109347847AOpen flexibleClose flexibleDigital data protectionData switching networksWeb applicationData center
The invention discloses a smart city information security guarantee system. The system comprises a plurality of groups of virtual machines / physical servers which are deployed at a cloud computing datacenter, database security equipment, a Web application firewall, DDos defense equipment, security gateways and a plurality of core switches. The security gateways are hanged beside the core switchesof the cloud computing data center through adoption of single arms. Two security gateways form a group and are connected with different core switches, and a hot standby HA cluster is formed. The DDosdefense equipment is connected between the boundary of the cloud computing data center and the core switches serially in an online mode. The Web application firewall is connected between a security Web service area and the core switches serially in a transparent mode. Important database server virtual machines are migrated to a security data service area through vMotion. The database security equipment is deployed on bypasses of an access layer switch of the security data service area. According to the system, cloud computing security is greatly improved, and smart city information security isguaranteed.
Owner:广东粤迪厚创科技发展有限公司 +1
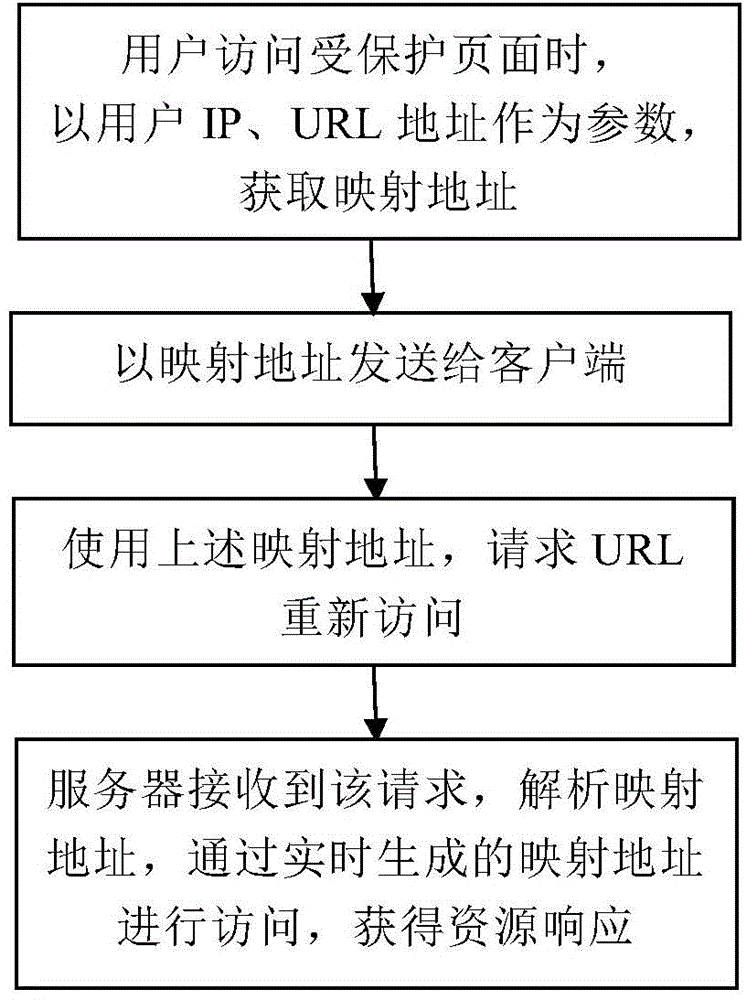
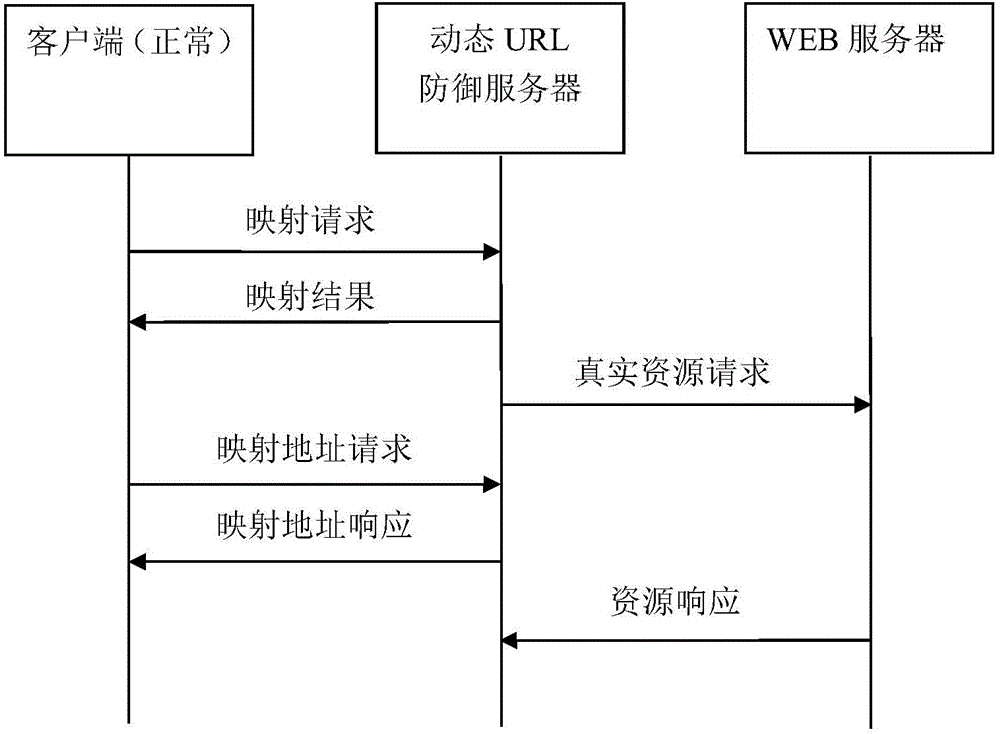
HTTP DDOS defense method based on URL dynamic mapping
The invention discloses an HTTP DDOS defense method based on URL dynamic mapping. The HTTP DDOS defense method comprises the following steps: when a user visits a protected page, the IP and URL addresses are taken as parameters, real-time interaction with a database is carried out, and the mapping address is obtained from the database; the mapping address is sent to the client; the client uses the mapping address to request a dynamic URL defense server to re-visit; a WEB server receives the request, analyzes the mapping address, visits through the mapping address generated in real time, and the resource response is acquired if the mapping address corresponds. Compared with the prior art, through the URL dynamic mapping technology, when an attacker attacks, the attack resource cannot be accurately located, so that a normal user can effectively visit the application-level source, and the attack resistance of application-level HTTP service is improved; the attacker is prevented from attacking through a unitary code.
Owner:TIANJIN UNIV
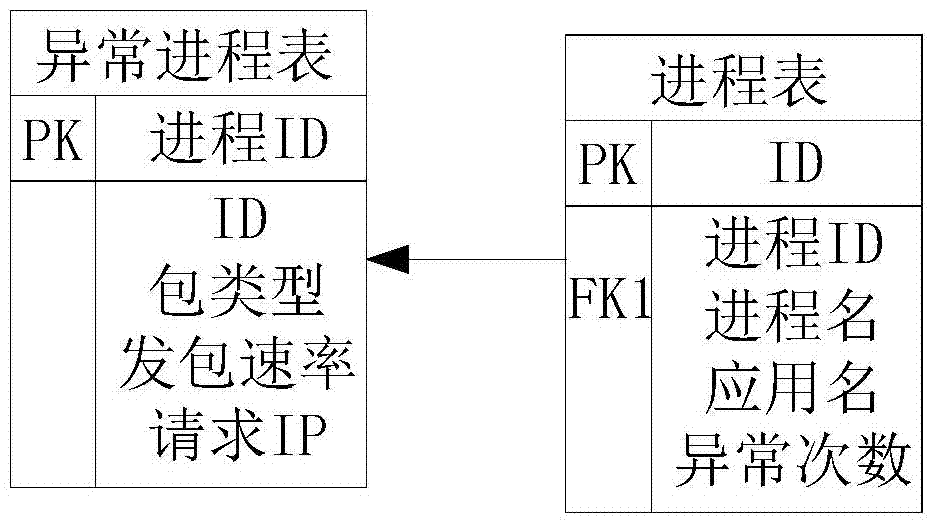
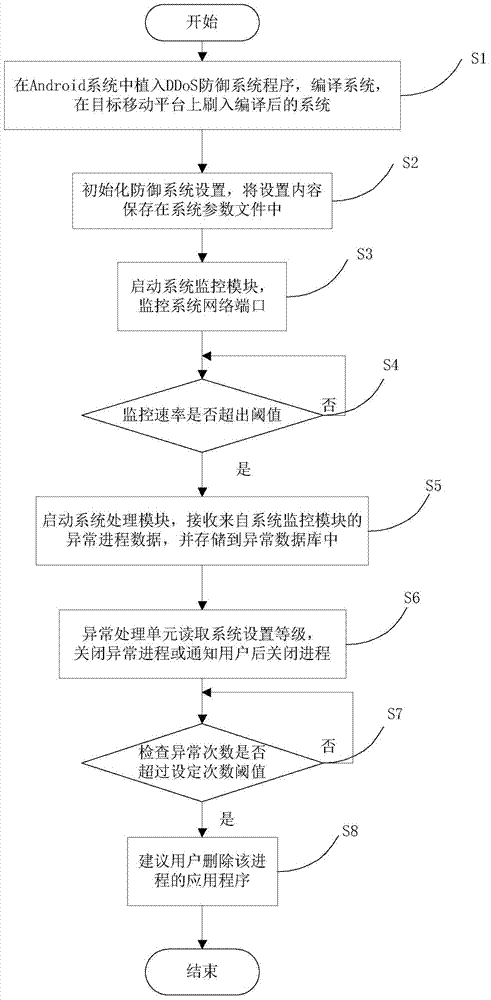
Android system-based distributed denial of service attack (DDoS) defense system and method
The invention provides an android system-based distributed denial of service attack (DDoS) defense system and method. Programs of the defense system are installed in an android system of a mobile platform, whether the rate of a synchronize (SYN) request, ACK-SYN response or user datagram protocol (UDP) package which is sent to the same port of the same internet protocol (IP) address in a current process exceeds a set threshold value or not is subjected to timing detection through a network port of a monitoring system, an abnormal process of sending data packages is tracked, recorded and stopped, and defense against DDoS on the mobile platform can be achieved. According to the android system-based DDoS defense system and method, the DDoS defense system is easy to install, network flow and system costs are extremely low, normal usage of the mobile platform is not affected, and technical problems that existing DDoS defense methods are complicated in deployment and implementation, high in resource costs and not suitable for the mobile platform can be solved.
Owner:重庆蓝岸科技股份有限公司
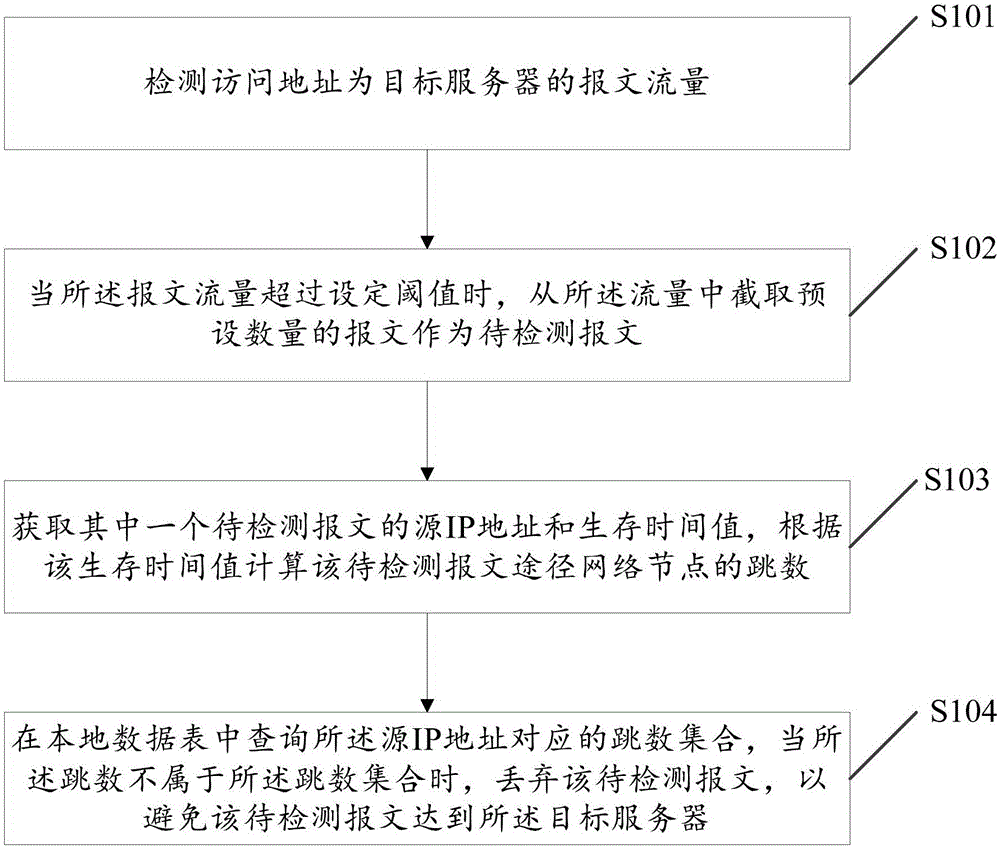
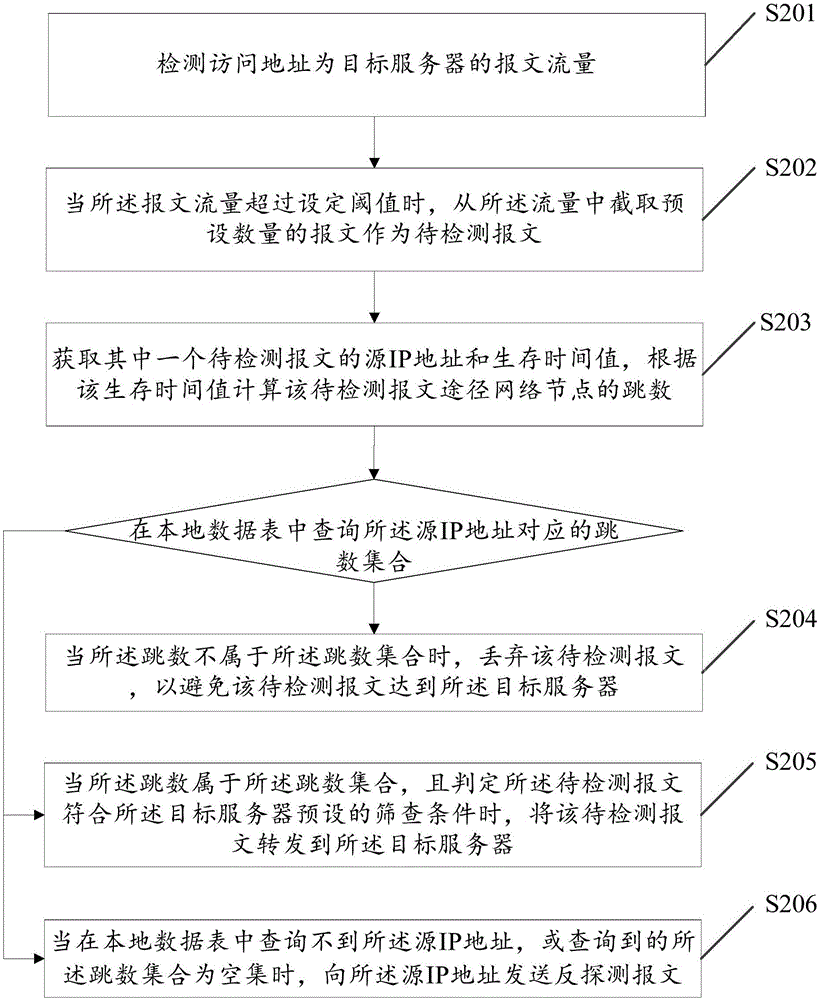
Method and device for cleaning forged source IP in DDOS (Distributed Denial of Service) defense system
The invention discloses a method and a device for cleaning a forged source IP in a DDOS (Distributed Denial of Service) defense system. The method comprises steps: a message flow with an access address to be a target server is detected; when the message flow exceeds a set threshold, a preset number of messages are intercepted from the flow as to-be-detected messages; the source IP address and the survival time value of one to-be-detected message are acquired, and according to the survival time value, the hop number when the to-be-detected message passes through a network node is calculated; and a hop set corresponding to the source IP address is queried in a local data sheet, when the hop number does not belong to the hop set, the to-be-detected message is discarded, and thus, the to-be-detected message can be prevented from arriving at the target server. Thus, the forged flow can be effectively and accurately cleaned.
Owner:GUANGZHOU HUADUO NETWORK TECH
Application level DDoS defense method and system
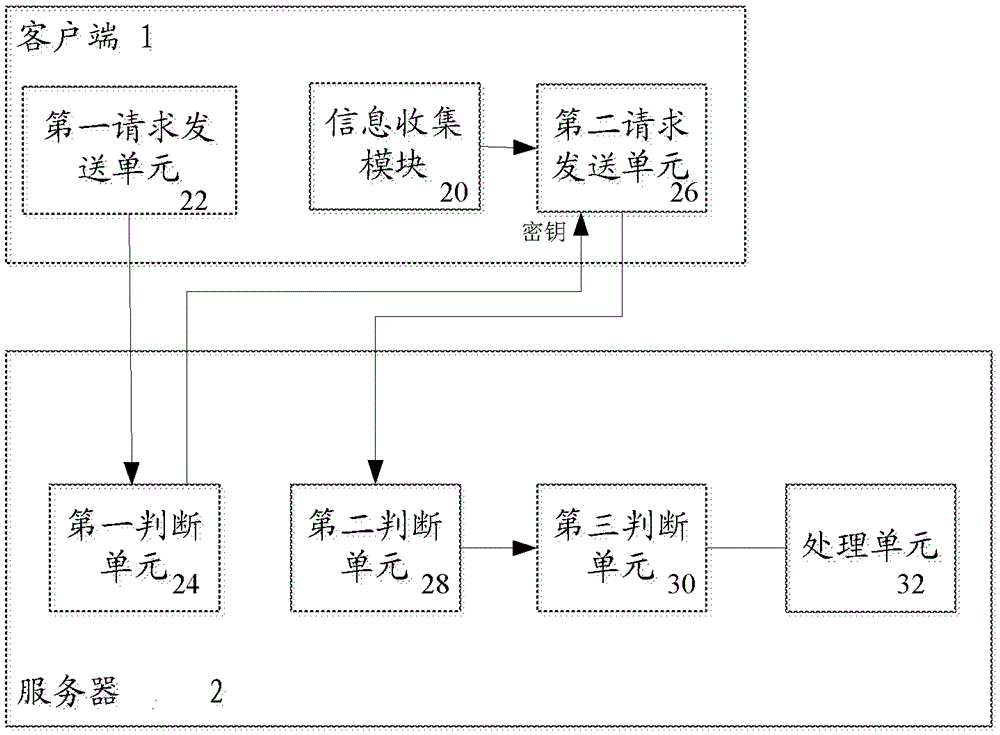
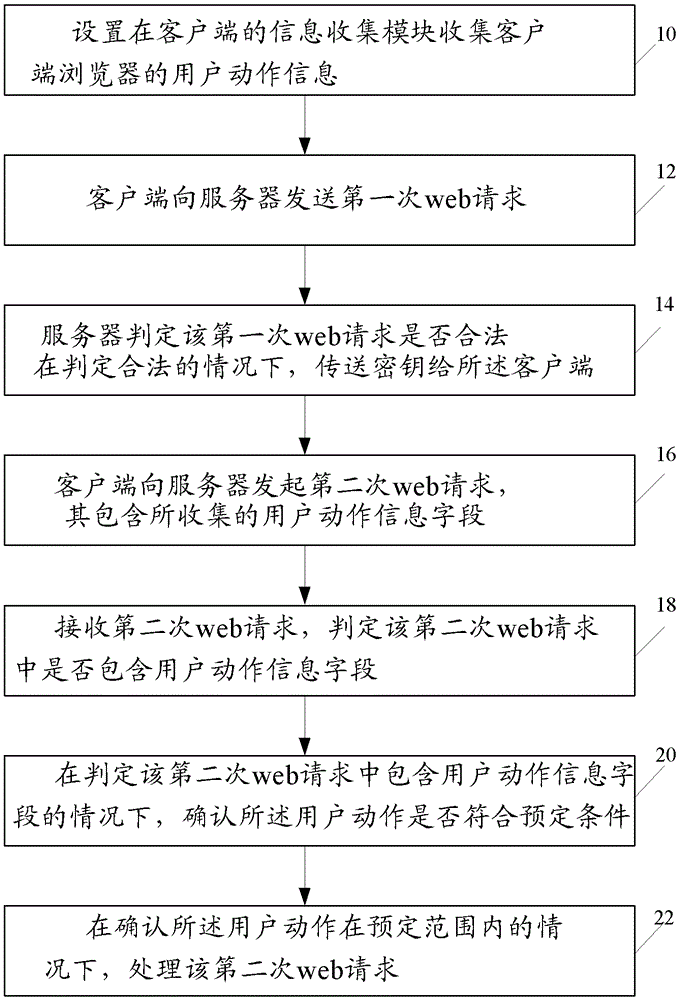
The present invention provides an application level DDoS defense method. The method comprises: a) an information collection module arranged at a client collects user motion information of a client web browser: b) the client sends a first web request to a server to require a secret key; c) the server determines whether the first web request is legal or not, and if the first web request is legal, the secret key is transmitted to the client; d) the client initiates a second web request to the server, and the second web request is encrypted by the secret key and includes collected user motion information fields; e) the server receives the second web request and determines whether the second web request includes the user motion information yield or not; f) if the second web request includes the user motion information yield, it is determined whether the user motion accords with a preset condition; and g) the second web request is processed in the condition that it is determined the user motion is in the preset range. The present invention further provides an application level DDoS defense system.
Owner:CHINA UNIONPAY
http flow defense method and system for resisting DDoS attack
ActiveCN112003873AGuaranteed recognition functionSolve traffic problemsTransmissionInternet privacyAttack
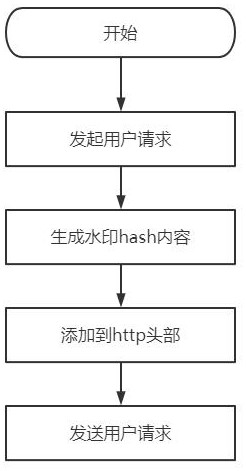
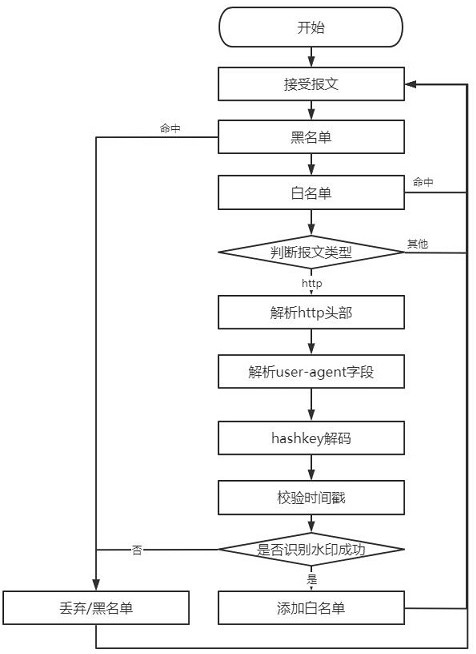
The invention provides an http flow defense method and system for resisting DDoS attack. A dynamic watermark generation module is arranged in a mobile client, a dynamic watermark is generated when anHTTP request is initiated to a server, when the message passes through a DDoS defense device, the correctness and integrity of the watermark in the HTTP protocol header are quickly checked to identifywhether the message belongs to the flow of a normal client or the attack flow initiated by a zombie host controlled by an attacker, and a cleaning action is performed through the defense device. Through the arrangement, the identification function of the mobile client is ensured, and the flow problem that a normal client and an illegal attacker cannot be distinguished is effectively solved; and the HTTP attack identification and performance processing capabilities of the DDoS defense device are improved.
Owner:CHENGDU DBAPP SECURITY
Method and system for achieving DDoS defense based on technology of dynamic tunnels
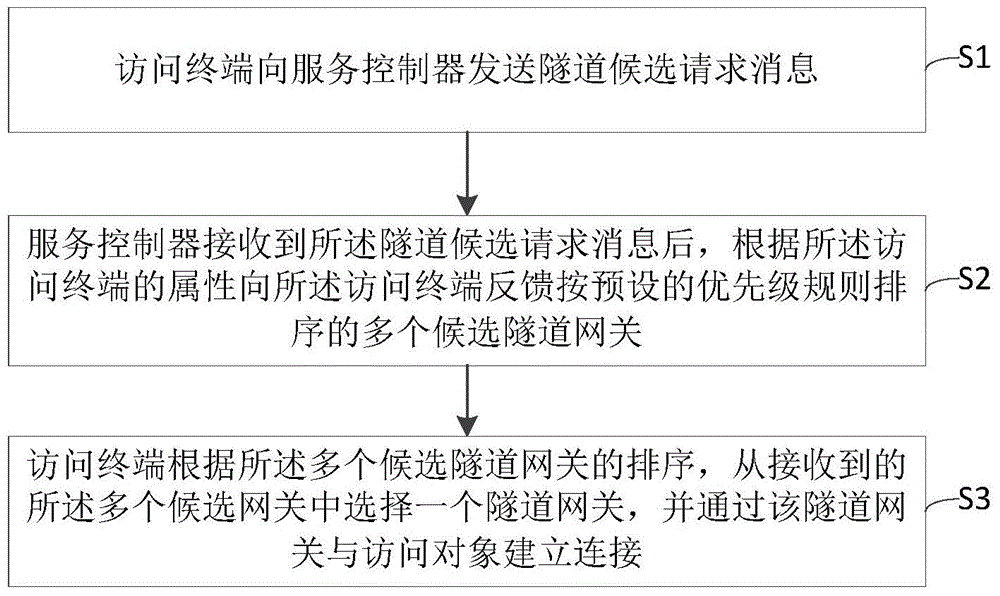
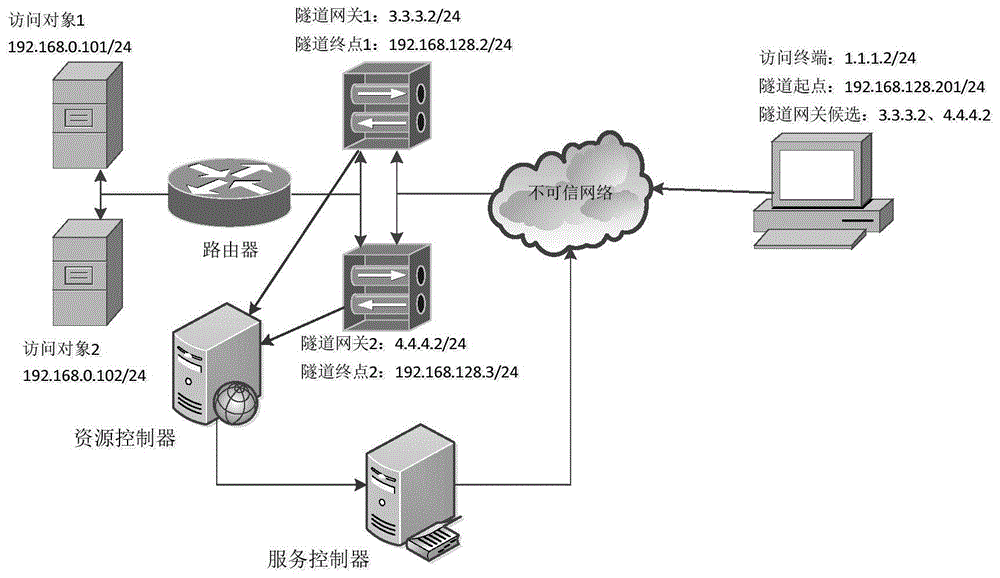
ActiveCN104869118AReduce redundancyGuaranteed reliabilityTransmissionTelecommunicationsComputer terminal
The invention provides a method for achieving DDoS defense based on the technology of dynamic tunnels, and the method comprises the steps: an access terminal transmits a tunnel candidate request message to a service controller; the service controller feeds back a plurality of candidate tunnel gateways, which are arranged according to a preset priority rule, to the access terminal according to the property of the access terminal after the service controller receives the tunnel candidate request message; the access terminal selects one tunnel gateway from the plurality of received candidate tunnel gateways according to the sequence of the plurality of candidate tunnel gateways, and is connected with an access object through the tunnel gateway. The invention also provides a system for achieving DDoS defense based on the technology of dynamic tunnels, and the system comprises the access terminal, the service controller, a source controller, and a plurality of tunnel gateways. The method and system achieves the security defense against attack, can reduce the link redundancy, and guarantee the reliability of core business.
Owner:北京云杉世纪网络科技有限公司
Network security isolation method and apparatus
InactiveCN107948209ARealize safe and isolated data transmissionVersatileTransmissionIPsecDdos defense
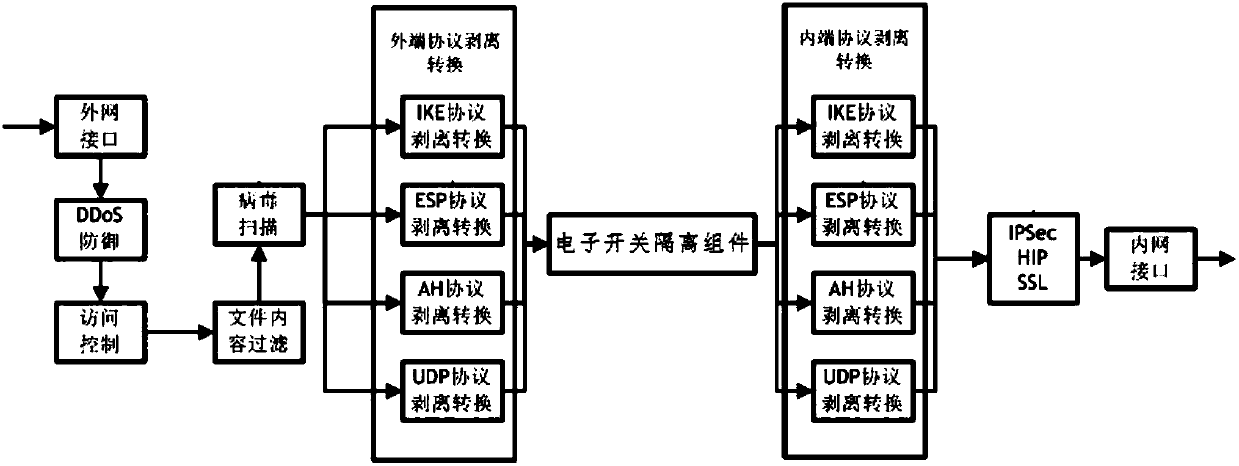
The invention provides a network security isolation method and apparatus. The apparatus comprises an outer end machine, an isolation card and an inner end machine; the outer end machine, the isolationcard and the inner end machine are connected in sequence; an external network interface module, an access control module, a file content filtering module, a virus scanning module and an outer end protocol stripping conversion module connected in sequence are arranged in the outer end machine; an electronic isolation component module is arranged in the isolation card; and an inner end protocol stripping conversion module, an IPSec / HIP / SSL module and an inner network interface module connected in sequence are arranged in the inner end machine. According to the network security isolation methodand apparatus, DDoS defense, access control, file content filtering, virus scanning, protocol stripping conversion and IPSec / HIP / SSL decryption are cooperatively used; and security isolation data transmission of different levels of networks can be achieved, and the network security isolation method and apparatus have the advantages of wide application range, rich functions and reliable effect.
Owner:宝牧科技(天津)有限公司
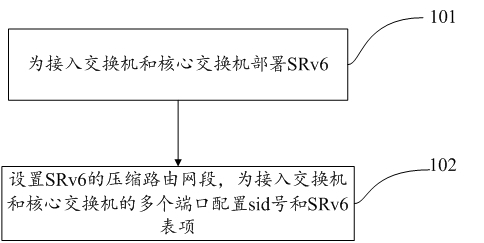
Extensible DDoS defense method and system
ActiveCN112272194AIncrease the number of nodesReduce duplication of workTransmissionEngineeringDdos defense
The invention discloses an extensible DDoS (Distributed Denial of Service) defense method and system, the method is applied to the DDoS defense system, the DDoS defense system comprises an access switch, a core switch and a cleaning server which are controlled by routing, and the method comprises the following steps: deploying SRv6 for the access switch and the core switch; and setting a compressed routing network segment of the SRv6, and configuring sid numbers and SRv6 table entries for a plurality of ports of the access switch and the core switch. According to another aspect of the invention, the invention also discloses the extensible DDoS defense method and system, which can compile sid numbers for corresponding interfaces through the SRv6 technology used by the core switch and the access switch so as to realize centralized control of all routes and reduce repeated workload when other defense devices are newly added.
Owner:GUANGDONG COMM & NETWORKS INST
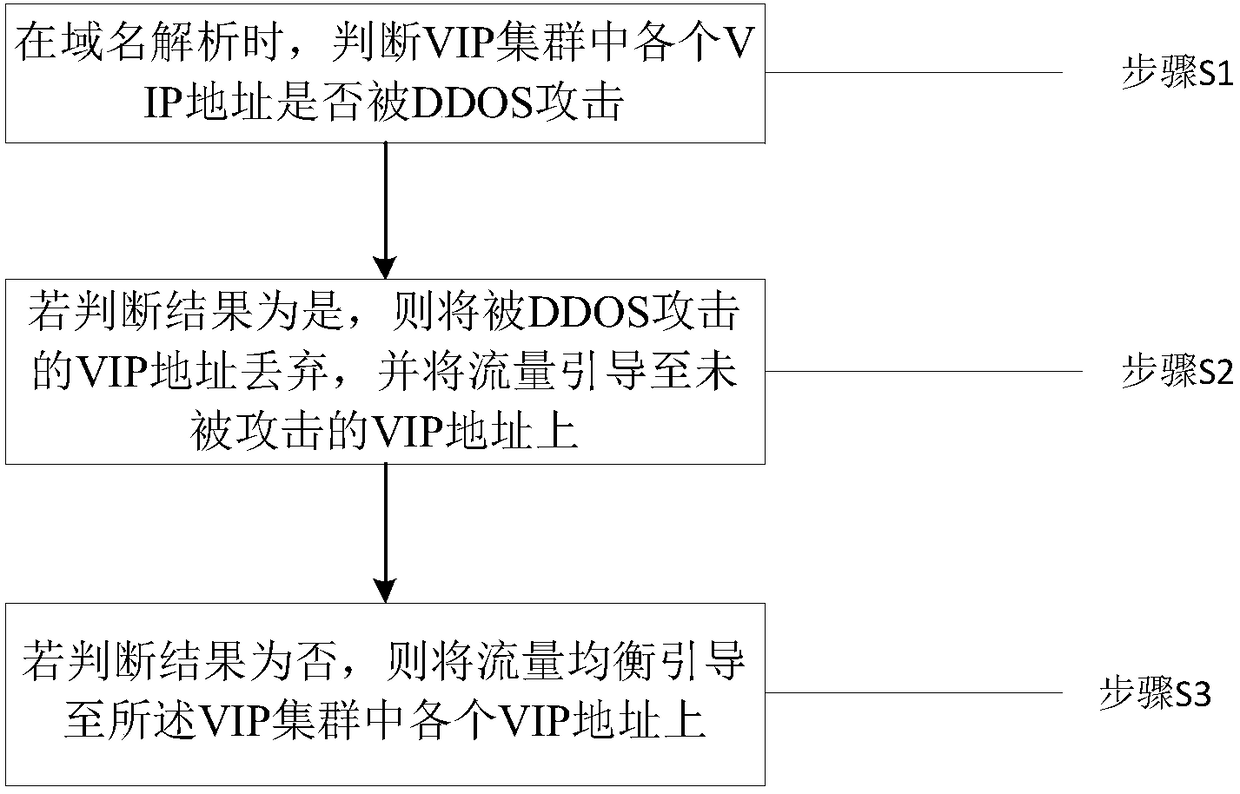
DDOS defense method and system based on fault automatic migration system
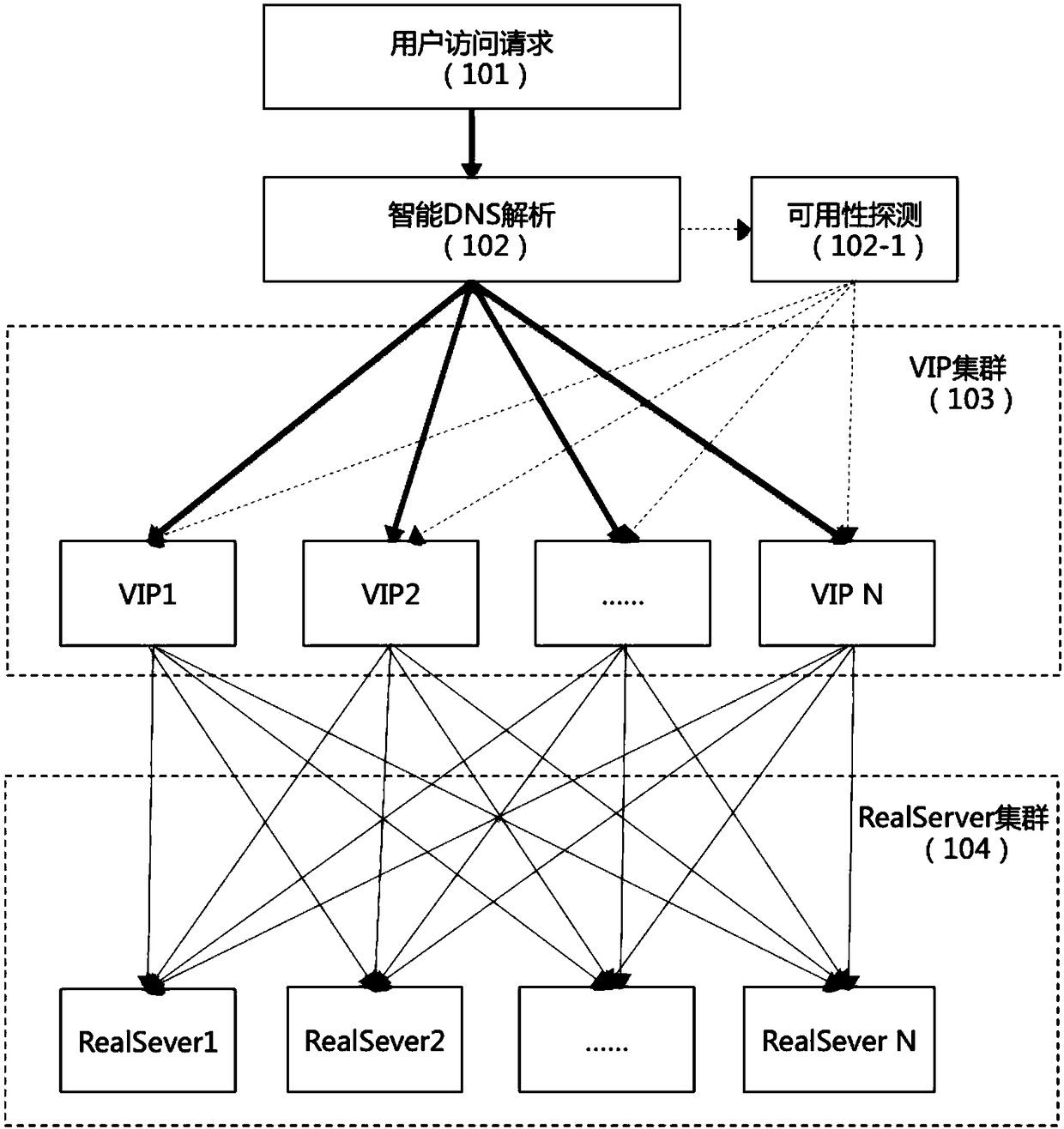
InactiveCN109218250ASolve the problem of attackAvoid attackData switching networksDomain nameDdos defense
The present invention relates to the technical field of network security and in particular to a DDOS defense method and system based on a fault automatic migration system, wherein the DDOS defense method includes: determining whether each VIP address in a VIP cluster is attacked by DDOS during domain name resolution; if so, discarding the VIP addresses attacked by the DDOS, and guiding the trafficto the VIP addresses that are not attacked; and if not, uniformly guiding the traffic to each VIP address in the VIP cluster. The technical solution of the present invention realizes the avoidance ofattack traffic by the automatic migration. An attacker generally attacks the VIPs, and the DDOS attacked VIPs are automatically discarded, and the normal traffic is guided to other VIPs that are notattacked, thereby preventing the server from being attacked, solving the problem of DDOS attack, and greatly reducing the cost and the difficulty of use.
Owner:BEIJING DUODIAN ONLINE SCI & TECH CO LTD
Method for defending against DDos in address disjunction mapping network
InactiveCN101702727AHigh practical valueGuarantee opennessPublic key for secure communicationUser identity/authority verificationTraffic capacityNetwork packet
The invention relates to a method for defending against DDos in an address disjunction mapping network, which belongs to the technical field of networks. In the method, a data packet access mechanism and a flow control mechanism for giving a token are included. The method provides the data packet access mechanism to defend against DDos attacks on an access router, launched by malicious nodes, thereby ensuring the safety of the network; and on such a basis, by designing the flow control mechanism based on the token in the address disjunction mapping network the purpose that a data source end can transmit data to a receiving end for fundamentally preventing the probability of the DDoS attacks only after obtaining the permission of the receiving end can be effectively ensured. According to a border router and the access router deployed in the method, the distributed denial of service (DDoS) attack can be effectively defended even though the network is in an environment of an asymmetric roundtrip path.
Owner:BEIJING JIAOTONG UNIV
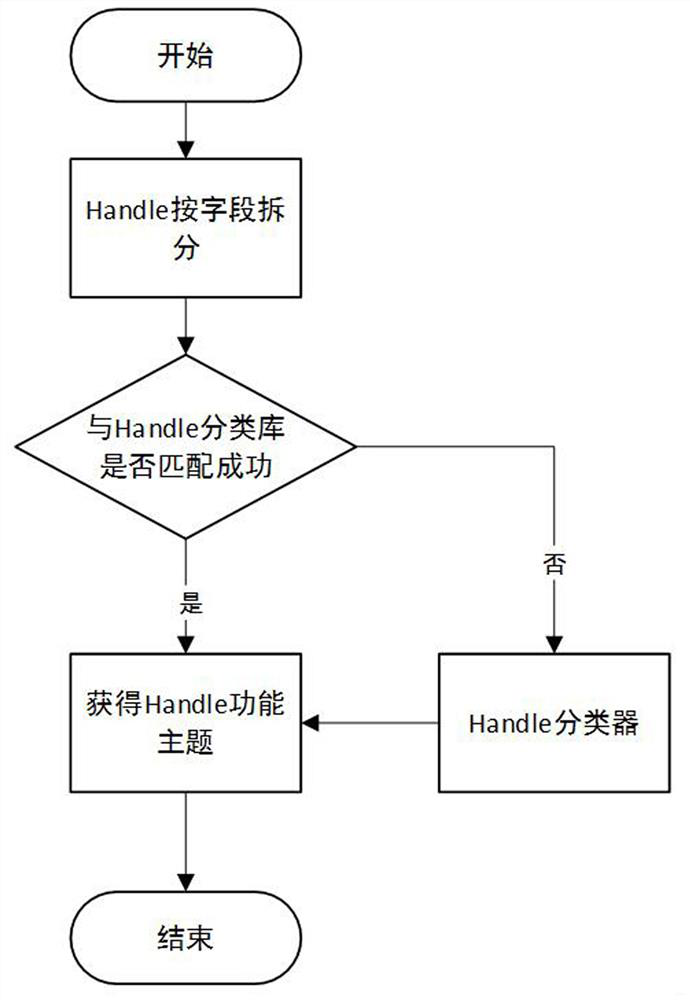
Handle identification system-oriented DDoS defense method
ActiveCN113645238ANormal query requestAvoid compromising functional propertiesCharacter and pattern recognitionTransmissionAttackThe Internet
The invention discloses a Handle identification system-oriented DDoS defense method. The method comprises the following steps of: analyzing Handle analysis logs, mining characteristics of a query end through a method in a data mining technology, calculating deviation according to clustering and statistical results, taking the deviation as an index for detecting DDoS attacks, and carrying out multilayer speed-limiting processing on abnormal Handle query requests. The detection module and the processing module are respectively deployed on a sub-node server at a Handle client and a local Handle Service (LHS) access point, the detection of the distributed denial of service attack is realized on a Handle identification analysis system, and the security of the industrial internet identification analysis system is improved.
Owner:码客工场工业科技北京有限公司
Large-scale DDoS (Distributed Denial of Service) attack defense system and method based on two-level linkage mechanism
ActiveCN101924764BSolve the accuracy problemLower deployment costsTransmissionAlarm messageDdos defense
The invention discloses large-scale DDoS (Distributed Denial of Service) attack defense system and method based on a two-level linkage mechanism. The method comprises the following steps of: monitoring the flow of a total network by a flow monitoring subsystem in real time, and searching and confirming a DDoS attack behavior; sending an alarm message for triggering a cleaning operation to a flow cleaning subsystem, and guiding the abnormal flow of the DDoS attach behavior to the flow cleaning subsystem; receiving the abnormal flow guided by the flow monitoring subsystem by the flow cleaning subsystem, cleaning the abnormal flow according to the cleaning operation triggered by the alarm message, (wherein the flow cleaning subsystem adopts the two-level architecture of a backbone network plus a local network defense system, and the two levels of cleaning system work cooperatively and clean synchronously), and injecting the cleaned cleaning flow back to a target customer network. The large-scale DDoS attack defense system and method based on the two-level linkage mechanism solve the problems of cleaning capacity, cleaning precision, and the like existing in the traditional DDoS defense technology; and on the basis of reducing the deployment cost of service scale, the large-scale DDoS attach defense capability of the total network is greatly improved, and the cleaning precision ofthe attack flow is increased.
Owner:CHINA TELECOM CORP LTD
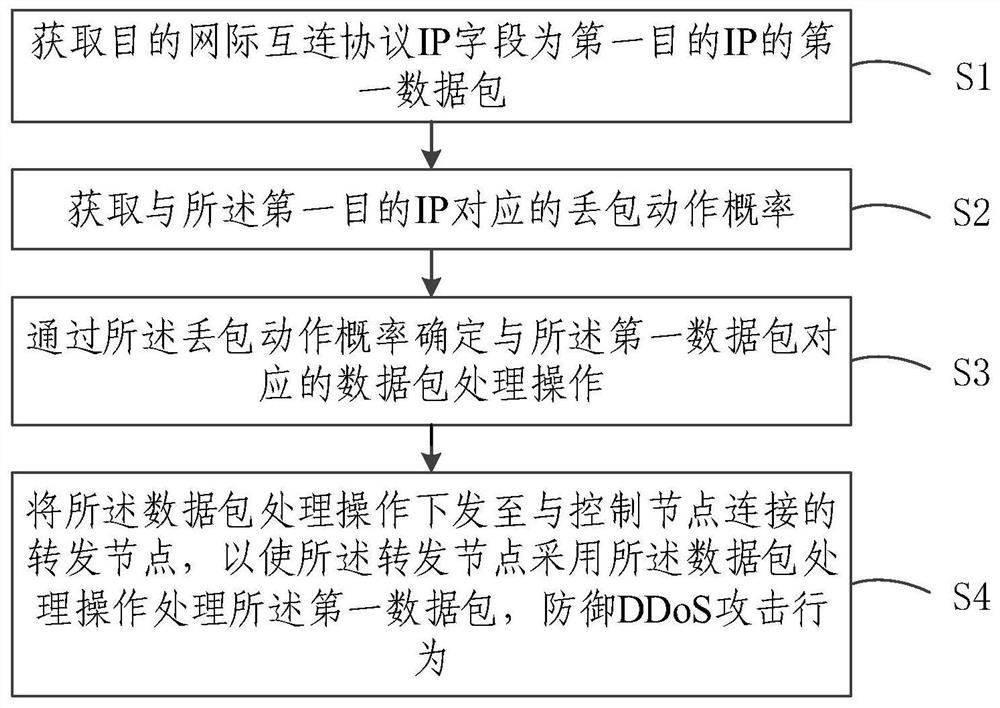
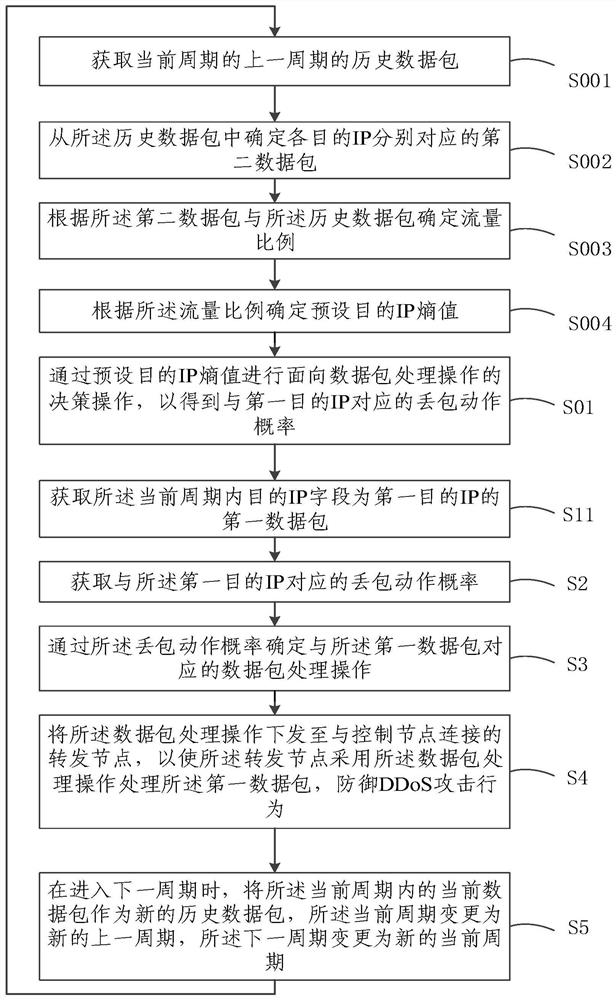
DDoS attack defense method and system, node and storage medium
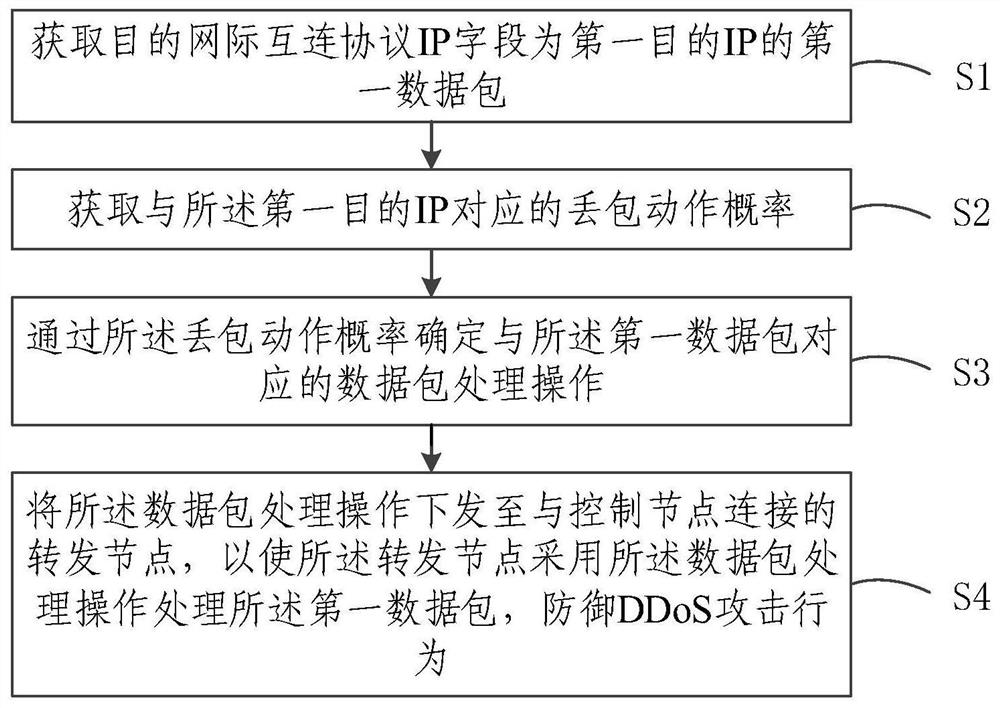
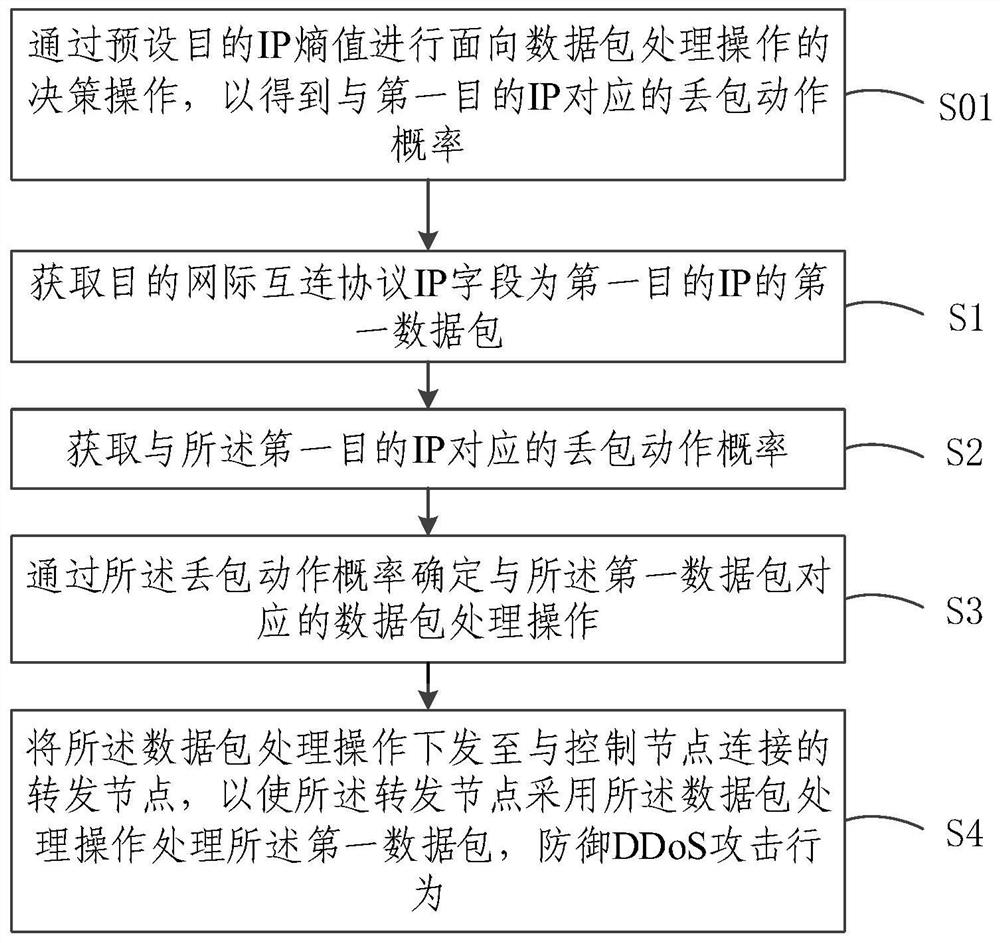
ActiveCN111786967AImprove accuracySolve technical problems that are difficult to deal with DDoS attacksData switching networksData packPacket loss
The embodiment of the invention relates to the technical field of network security, and discloses a DDoS attack defense method and system, a node and a storage medium. According to the embodiment of the invention, the method comprises the steps: firstly obtaining a first data package with a first destination IP as a destination IP field; obtaining a packet loss action probability corresponding tothe first destination IP; determining a data packet processing operation corresponding to the first data packet through the packet loss action probability; and issuing the data packet processing operation to a forwarding node connected with a control node, so that the forwarding node processes the first data packet by the data packet processing operation to defend a DDoS attack behavior. Obviously, according to the embodiment of the invention, the number of the data packets sent to the specific destination IP is limited; therefore, the traffic restriction behavior based on the destination IPis realized, dynamic real-time traffic restriction can be performed on the suspicious traffic, the accuracy of the DDoS defense behavior is improved, and the technical problem that the SDN control entity is difficult to deal with the DDoS attack is solved.
Owner:TSINGHUA UNIV
DDoS prevention method and system based on user level shunting
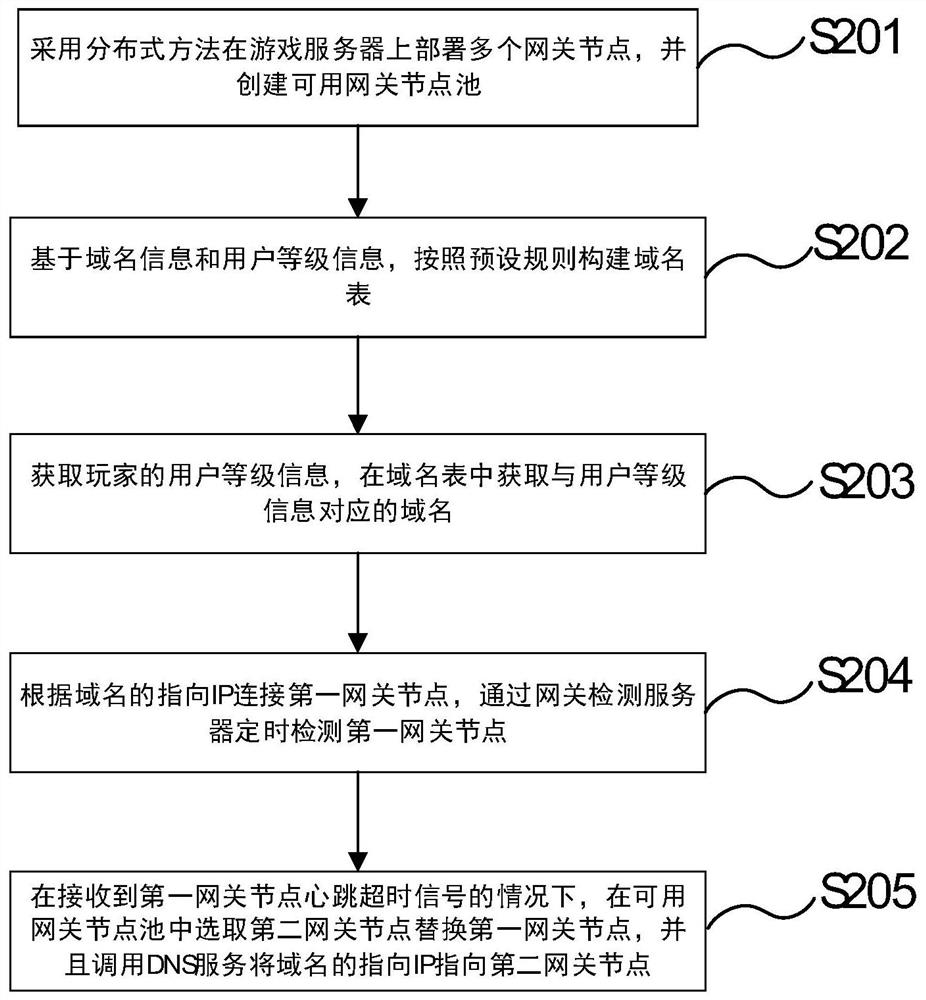
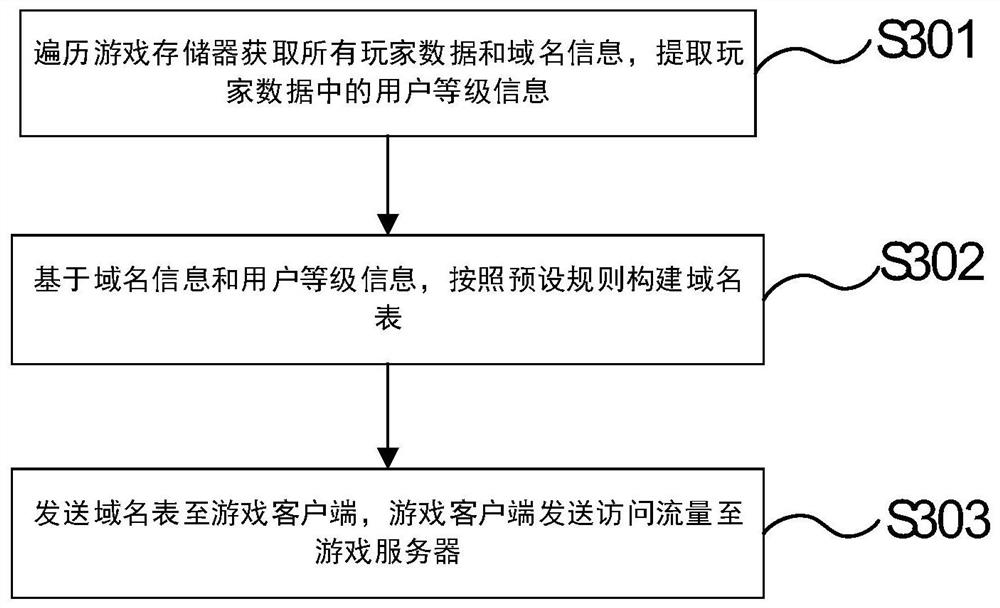
ActiveCN113242210ASolve the problem of low defenseIncrease the difficultyData switching networksDomain nameInternet privacy
The invention relates to an anti-DDoS method and system based on user level shunting, and the method comprises the steps: obtaining the user level information of a player, and obtaining a domain name corresponding to the user level information in a domain name list; connecting a first gateway node according to a pointing IP of the domain name, and detecting the first gateway node regularly through a gateway detection server; under the condition that a heartbeat timeout signal of the first gateway node is received, selecting a second gateway node from the available gateway node pool to replace the first gateway node, and calling the DNS service to point the pointing IP of the domain name to the second gateway node. Through the application of the method and the device, the problem that the defense capability of related DDoS defense methods is lower due to the fact that available gateway nodes are exposed to the outside in related technologies is solved, and the attack duration and the attack difficulty of attackers are increased, so the defense capability of a DDoS defense system is improved.
Owner:杭州闪电玩网络科技有限公司
DDOS mass flow defense architecture
The invention relates to the technical field of network safety protection, and provides a router. The invention discloses a DDOS large-flow defense architecture. The protection platform comprises a main server, a micro server and a hidden server. The method comprises the following steps: establishing a connection pool by a plurality of micro servers, mapping IPs and ports connected with a main server to IPs and ports of hidden servers on the micro servers through load balancing, carrying out real-time anomaly monitoring on the connection pool, and quickly switching to new IPs and ports when anabnormal IP is monitored; the DDOS defense system solves the problems that a DDOS defense system in the prior art is poor in universality, high in price and not suitable for small and medium-sized enterprise applications, and cannot locate an attack source.
Owner:上海来三网络科技有限公司
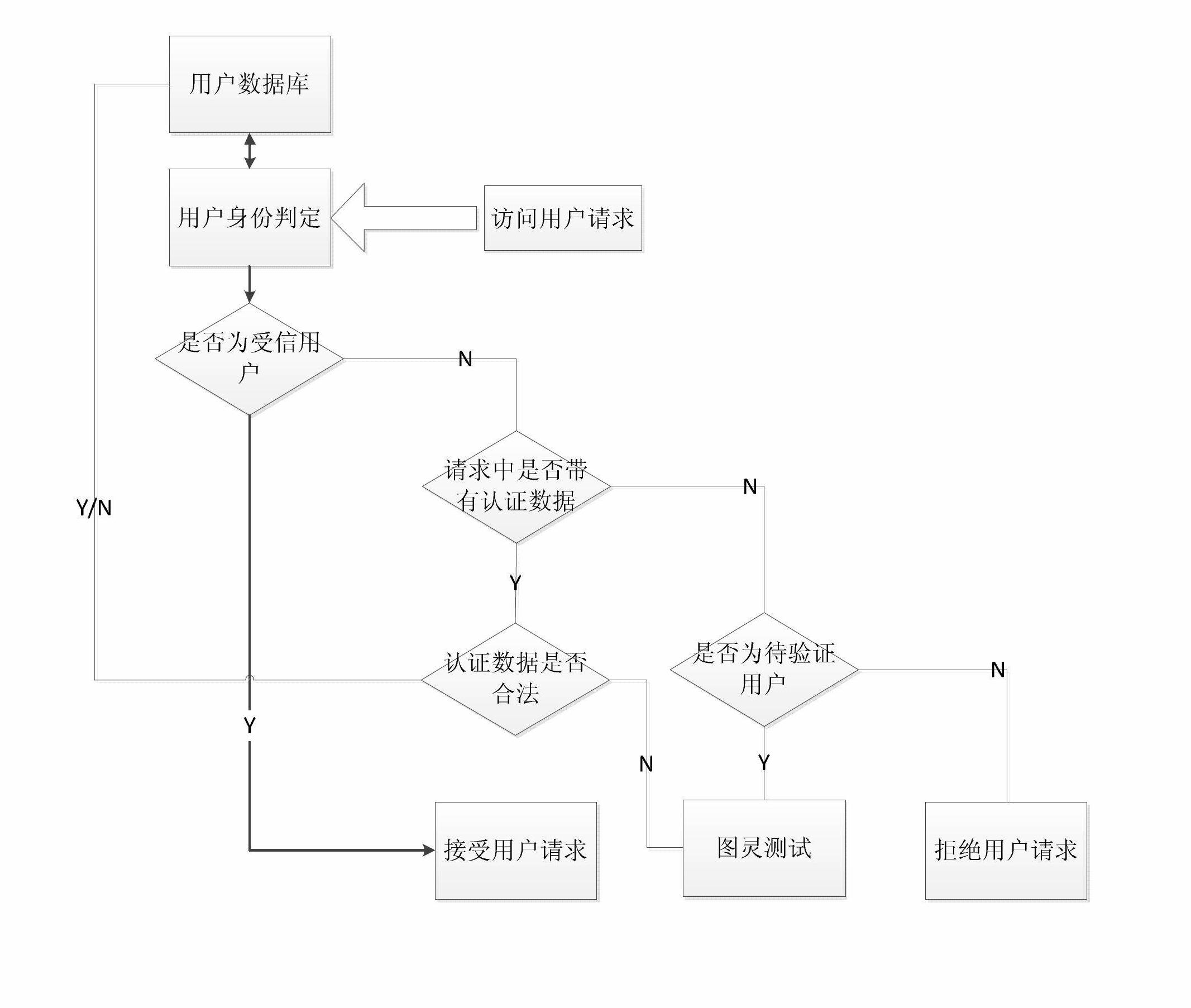
DDoS (distributed denial of service) defending method based on Turing test
The invention relates to a DDoS (distributed denial of service) defending method based on the Turing test. The method includes the steps: firstly, receiving user request data; and secondly, interacting with users on basis of simulated questions and answers or pattern recognition, wherein the interaction process includes steps: putting forwarding simulated questions and answers or pattern recognition problems to the users, receiving data returned by the users; determining whether the users are normal human users or not according to the data returned by the users, if yes, allowing the users to access; and if not, refuse the users to access. The DDoS defending method adopts the Turing test to determine whether target senders are normal human users or requests sent to a server by simulated normal users by machines or software, so that sources of illegal requests can be cut off to enable attackers to be in the dock, DDoS defence grasps the situation initiative, and continuous updating along with updating variation of attack modes is not needed.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
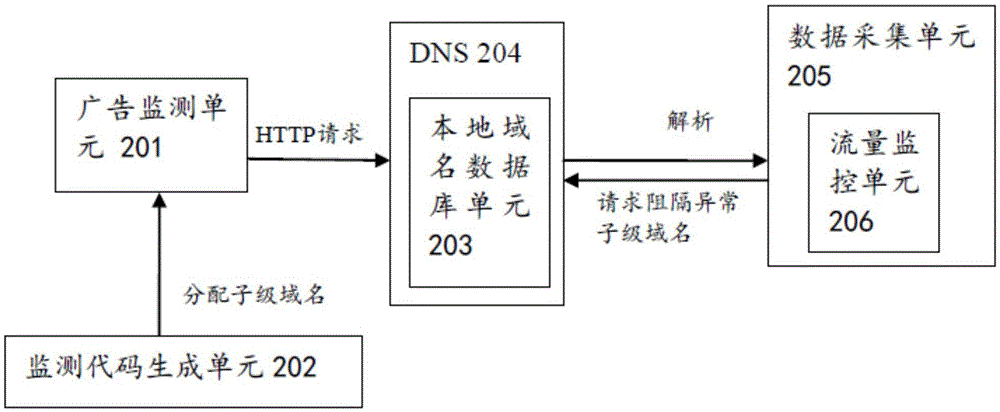
Data collection method and system capable of achieving DDoS defense
The invention relates to a data collection method capable of achieving DDoS defense, and the method comprises the steps: randomly distributing a sub-domain name for an HTTP request code; receiving an HTTP request sent by the HTTP request code to a data collection server; monitoring the network access flow of the distributed sub-domain name from the HTTP request code, modifying the resolving rule of the sub-domain name in a DNS when the network access flow of the distributed sub-domain name exceeds an early-warning value, and enabling the sub-domain name not to point to the IP address of the data collection server. The invention also relates to a data collection system capable of achieving DDoS defense.
Owner:BEIJING XUEZHITU NETWORK TECH
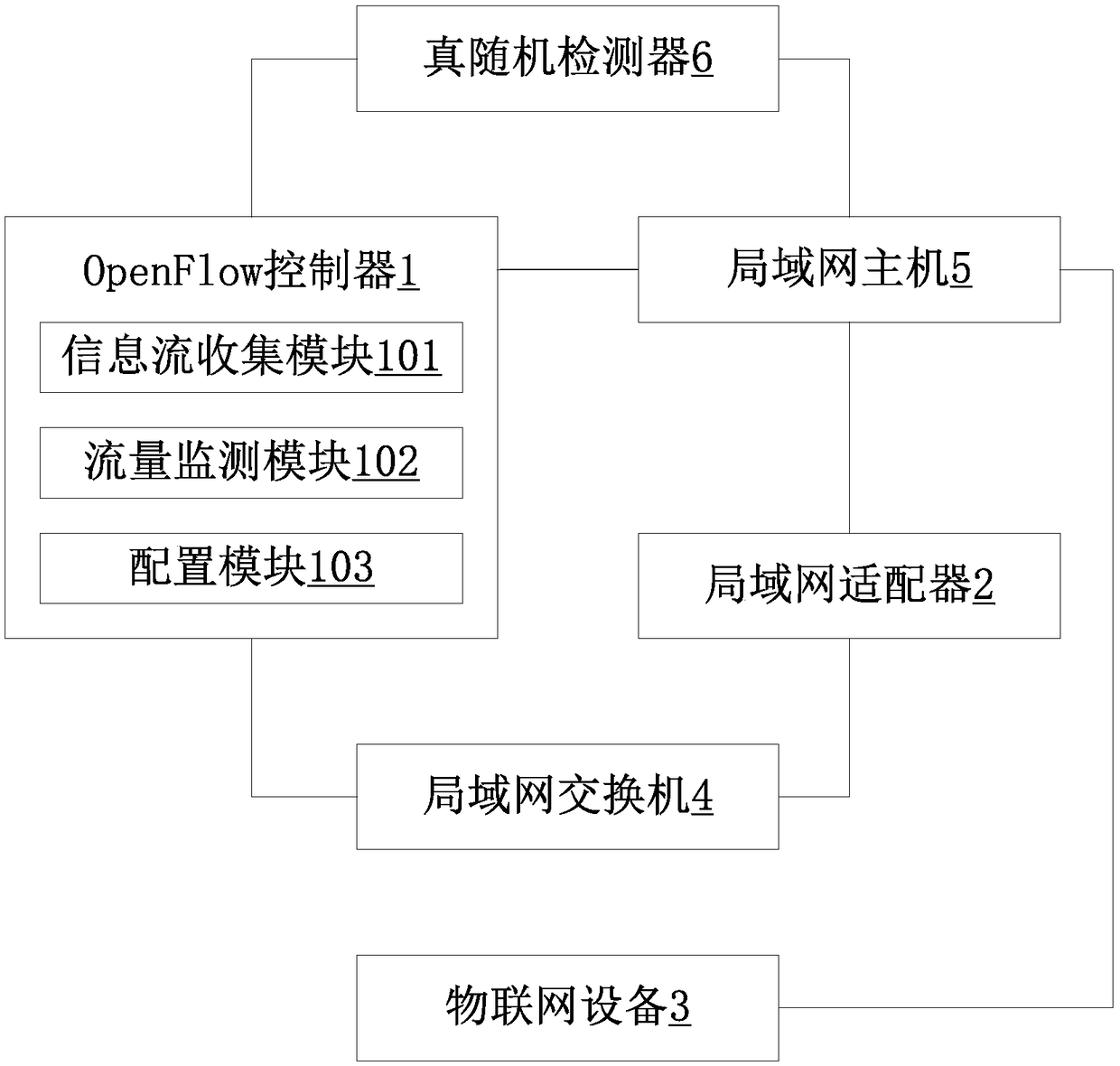
A working method of an Internet DDoS defense system based on the Internet of Things
The invention relates to a working method of an Internet DDoS defense system based on the Internet of Things, comprising the following steps: an OpenFlow controller obtains topology information; the information flow collection module collects the information flow propagated in the local area network. The OpenFlow controller calculates the packet update rate when the information flow is exchanged in the LAN switch and transmitted in the LAN. The flow monitoring module calibrates the information flow which exceeds or is lower than the message update speed limit value; the LAN adapter calculatesitself and the real-time processing rate of the LAN switch to the information flow; the configuration module adapts the packet update rate to the real-time processing rate. The OpenFlow controller transmits the adapted information stream to the corresponding LAN network. A LAN host compute selects that information flow retention with the correspond information flow message update rate according tothe real-time processing rate of the LAN host computer; the LAN host transmits the information flow which exceeds or is lower than the speed limit value of its own processing speed to the IOT equipment. A LAN switch diffuses the current flow of information that an IoT device currently has.
Owner:SHENZHEN POWER SUPPLY BUREAU
Defense method, system, node and storage medium of ddos attack
ActiveCN111786967BImprove accuracySolve technical problems that are difficult to deal with DDoS attacksSecuring communicationData packPacket loss
The embodiment of the invention relates to the technical field of network security, and discloses a DDoS attack defense method, system, node and storage medium. The embodiment of the present invention first obtains the first data packet whose destination IP field is the first destination IP; obtains the packet loss action probability corresponding to the first destination IP; determines the data packet processing operation corresponding to the first data packet through the packet loss action probability ; sending the data packet processing operation to the forwarding node connected to the control node, so that the forwarding node uses the data packet processing operation to process the first data packet to defend against DDoS attacks. Obviously, the embodiment of the present invention realizes the traffic restriction behavior based on the destination IP by limiting the number of data packets sent to a specific destination IP, and can perform dynamic real-time traffic restriction on suspicious traffic, thereby improving the DDoS defense behavior The accuracy solves the technical problem that the SDN control entity is difficult to deal with DDoS attacks.
Owner:TSINGHUA UNIV
A ddos defense method and system based on self-adaptive start of trust value in sdn
ActiveCN106657107BReduce resource usageGuaranteed detection accuracyTransmissionInformation controlData pack
The invention discloses a self-adaptively started ddos defense method based on a trust value in an SDN. The self-adaptively started ddos defense method comprises the following steps: a switch receives an unmatched packet, and sends a packet_in data packet to a controller; a counter is deployed in an SDN controller; the counter pre-sets a packet_in number value; when an arrival packet_in number is equal to a set value every time, the packet_in arrival rate in the time period is calculated; then, whether the packet_in arrival rate is abnormal or not is judged; the flow on the switch corresponding to packet_in is precisely detected by utilization of a reverse neural network classifier; a neural network, an intermediate layer of which is 50*50, is established; six characteristic values are calculated; training is carried out by taking the six characteristic values as input of the classifier; and, if the output value of the neural network is between 0.5 and 1, the fact that the flow is a ddos attack is determined. By means of the self-adaptively started ddos defense method and system based on the trust value in the SDN disclosed by the invention, the characteristics of the SDN, such as flow table information of a data layer and control of the controller in a control layer to the whole network, are sufficiently utilized; and thus, the ddos attack in the SDN can be effectively defensed.
Owner:NANJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com