Deep learning based DDOS defensive device and method in SDN
A deep learning and DDOS technology, applied in the field of network communication, can solve problems such as difficulty in defense and ferocious attacks, and achieve the effects of improving accuracy, improving high cohesion characteristics, and reducing coupling correlation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
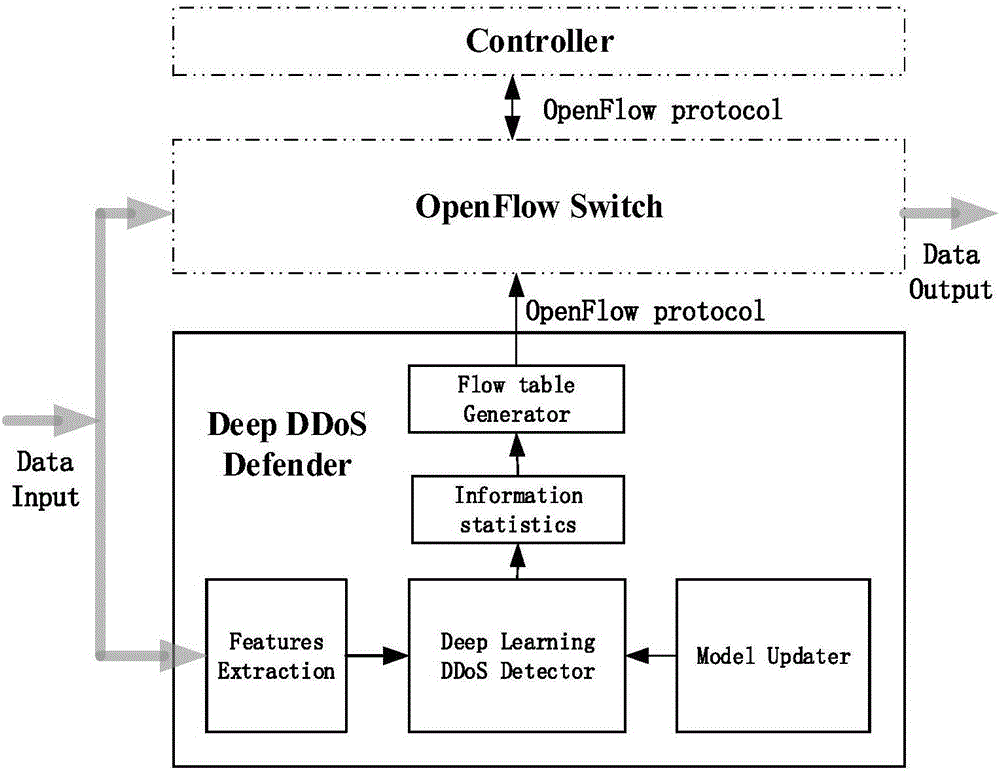
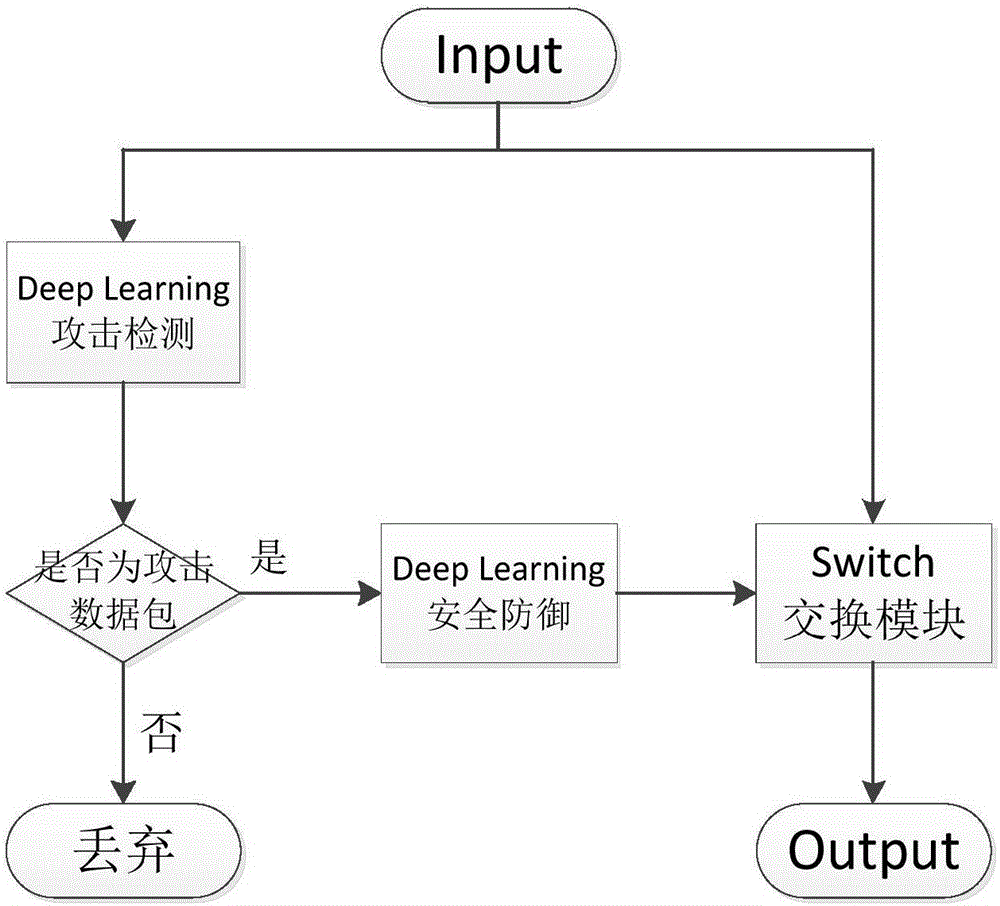
[0049] At present, most SDN architectures use the OpenFlow protocol as the communication interface between the control layer and the data exchange layer, which can change network resources and add new switch rules in real time. The OpenFlow protocol relies on the secure channel between the controller and the switch. Once a DDOS attack occurs on the secure channel and the connection is disconnected, the SDN architecture will collapse due to the loss of the controller. If a DDOS attack occurs between the switch and the controller, If the connection is lost, it means that the entire network architecture loses the control layer. In this case, the entire network may be paralyzed. To sum up, it is imminent to study an efficient and accurate DDoS security defense measure. The present invention provides a DDOS defense device and method based on deep learning in SDN, which is mainly used to solve the problem of how to effectively defend against DDOS attacks in an SDN network. The pres...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com