Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
145 results about "Cloud computing security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Cloud computing security or, more simply, cloud security refers to a broad set of policies, technologies, applications, and controls utilized to protect virtualized IP, data, applications, services, and the associated infrastructure of cloud computing. It is a sub-domain of computer security, network security, and, more broadly, information security.
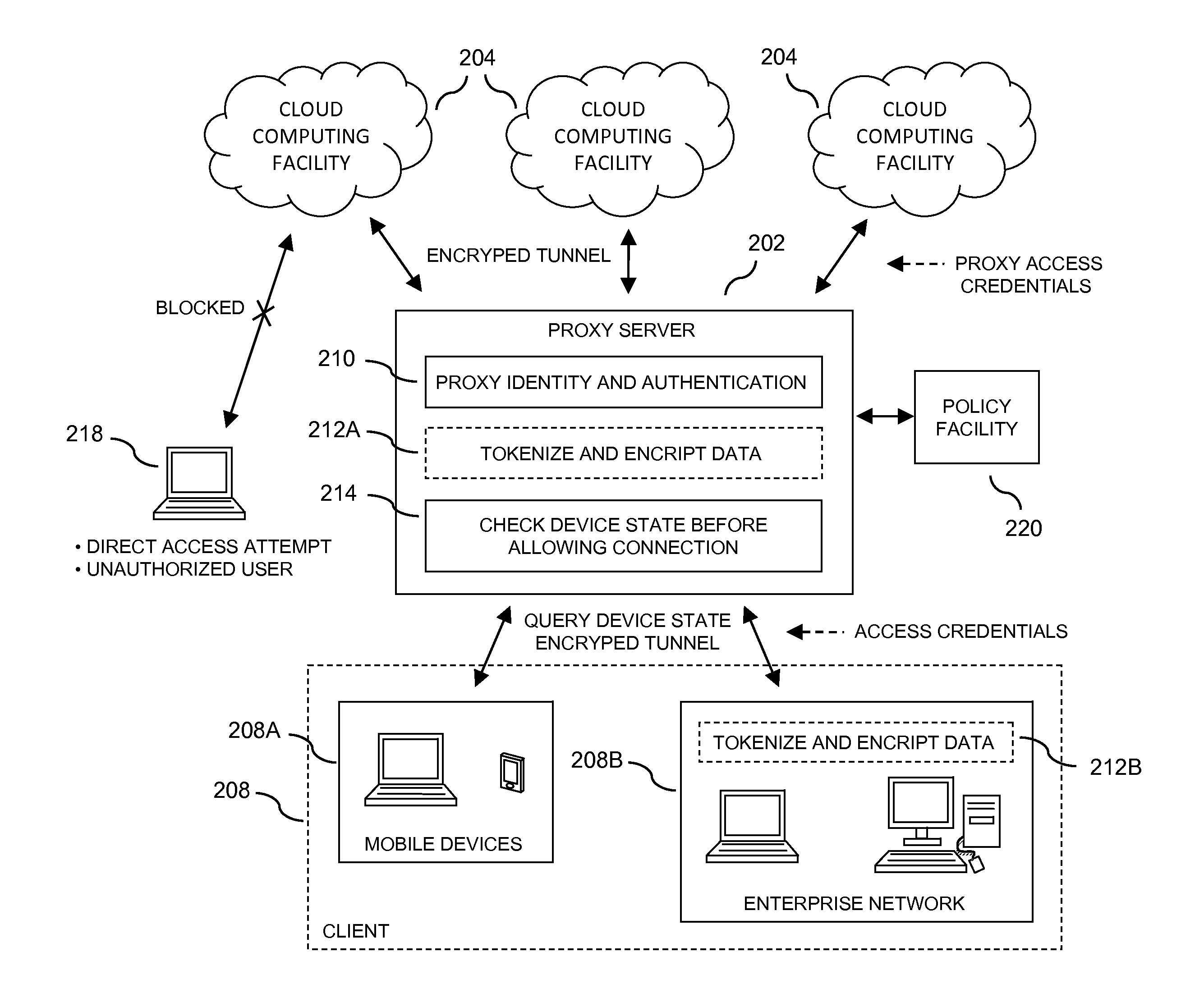
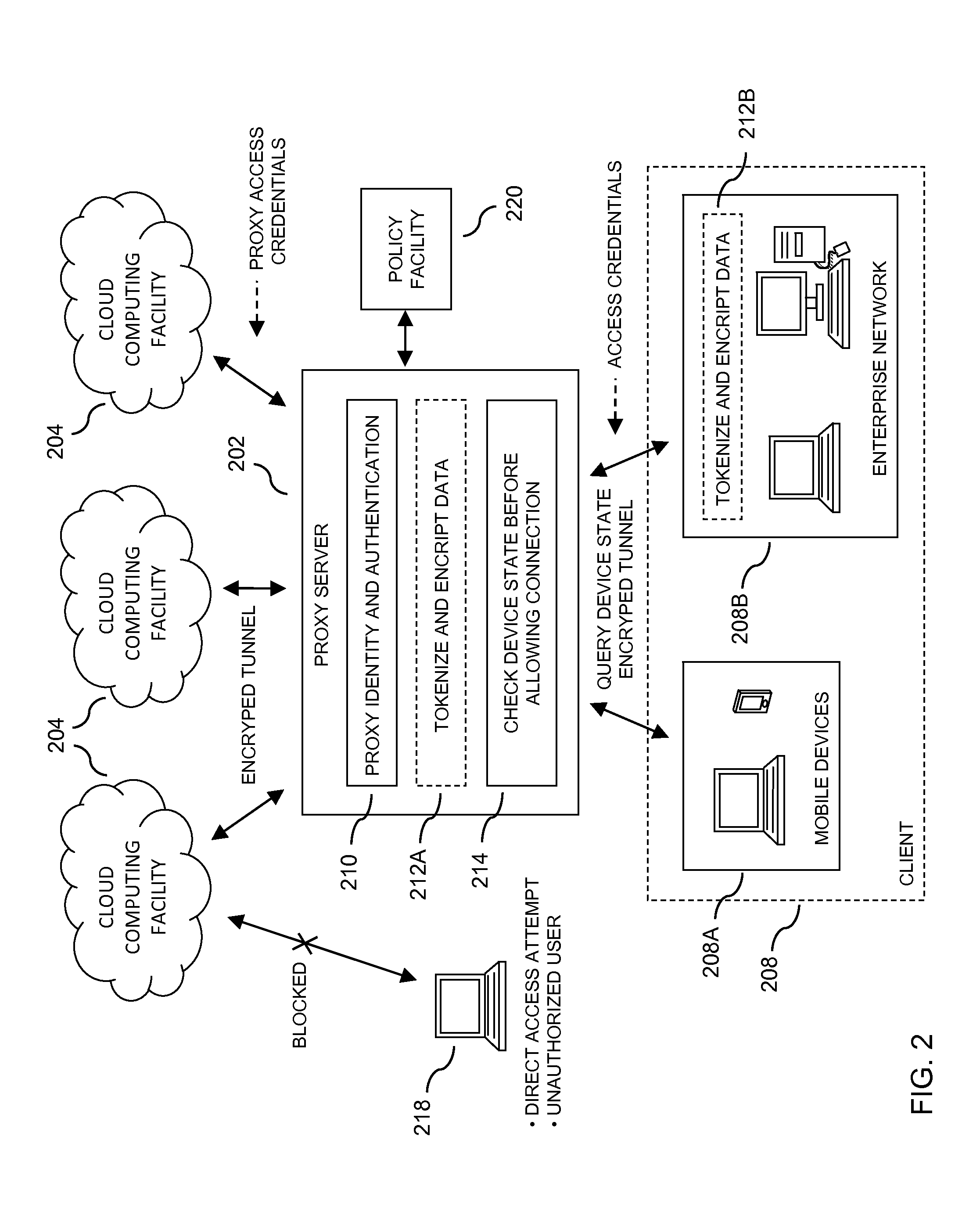
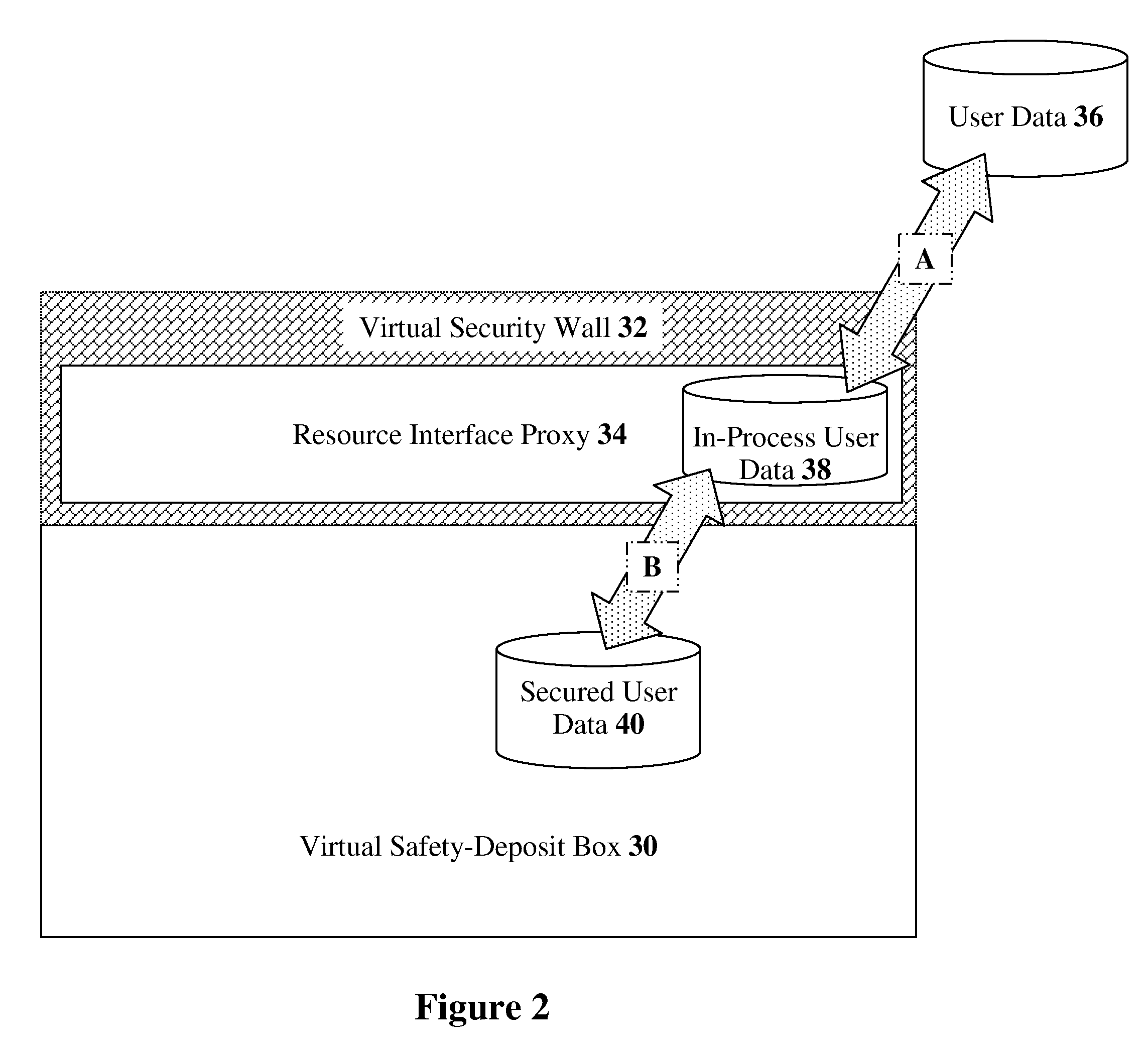
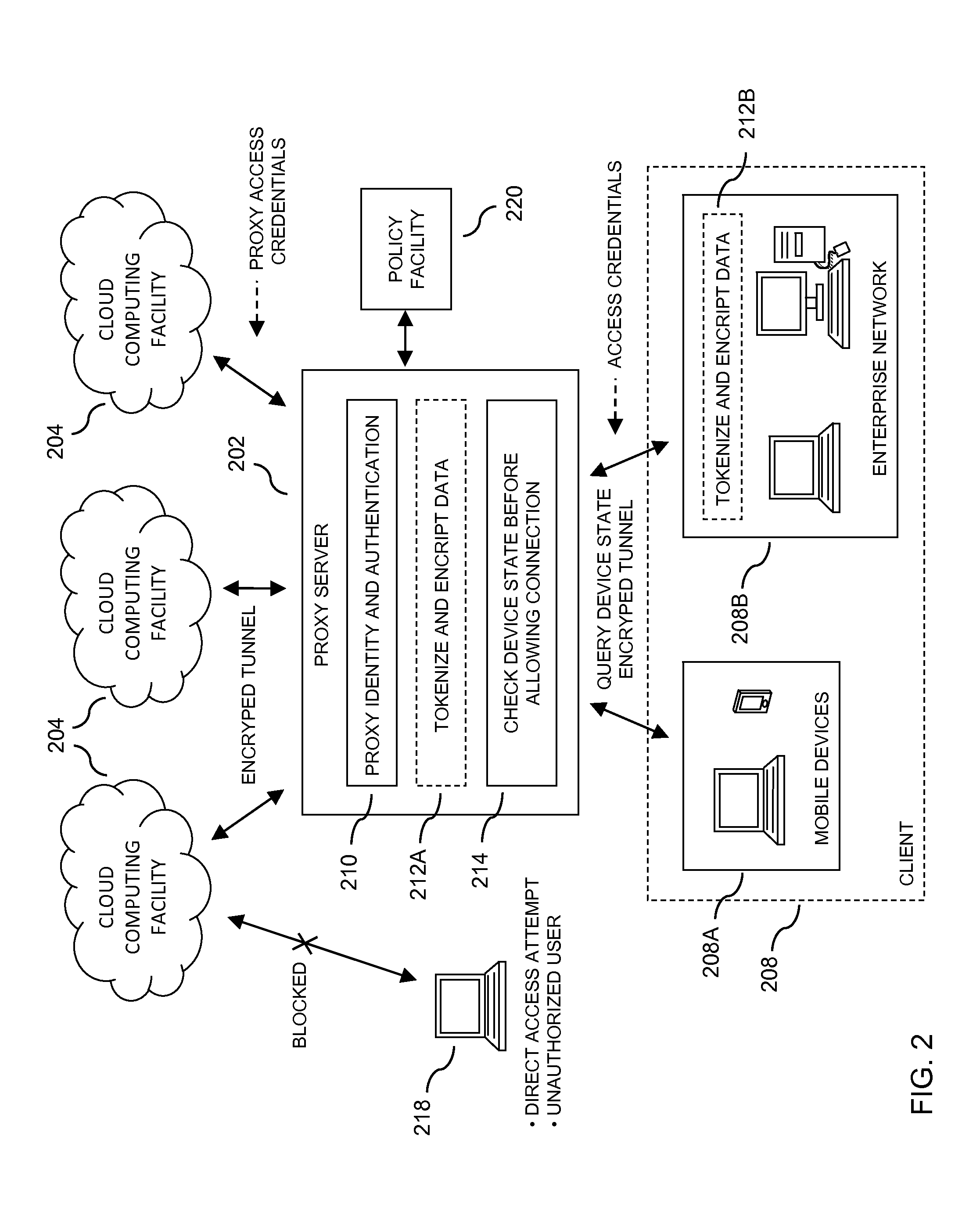
Security access protection for user data stored in a cloud computing facility
ActiveUS20140020072A1Digital data processing detailsUser identity/authority verificationTelecommunications linkSecure state
In embodiments of the present invention improved capabilities are described for a method and system including storing a plurality of proxy access credentials for a user to securely access each of a plurality of cloud computing facilities; receiving a request from a client device for access to one of the plurality of cloud computing facilities; securing a communication link to the client device, thereby providing a secure link; receiving access credentials from the user through the secure link; verifying an identity of the user with the access credentials; assessing a security state of the client device to determine if the client is in compliance with a security policy; and if the client is in compliance with the security policy, coupling the client to one of the plurality of cloud computing facilities through a second secure link using a corresponding one of the plurality of proxy access credentials for the user.
Owner:SOPHOS
Methods, devices, and media for securely utilizing a non-secured, distributed, virtualized network resource with applications to cloud-computing security and management
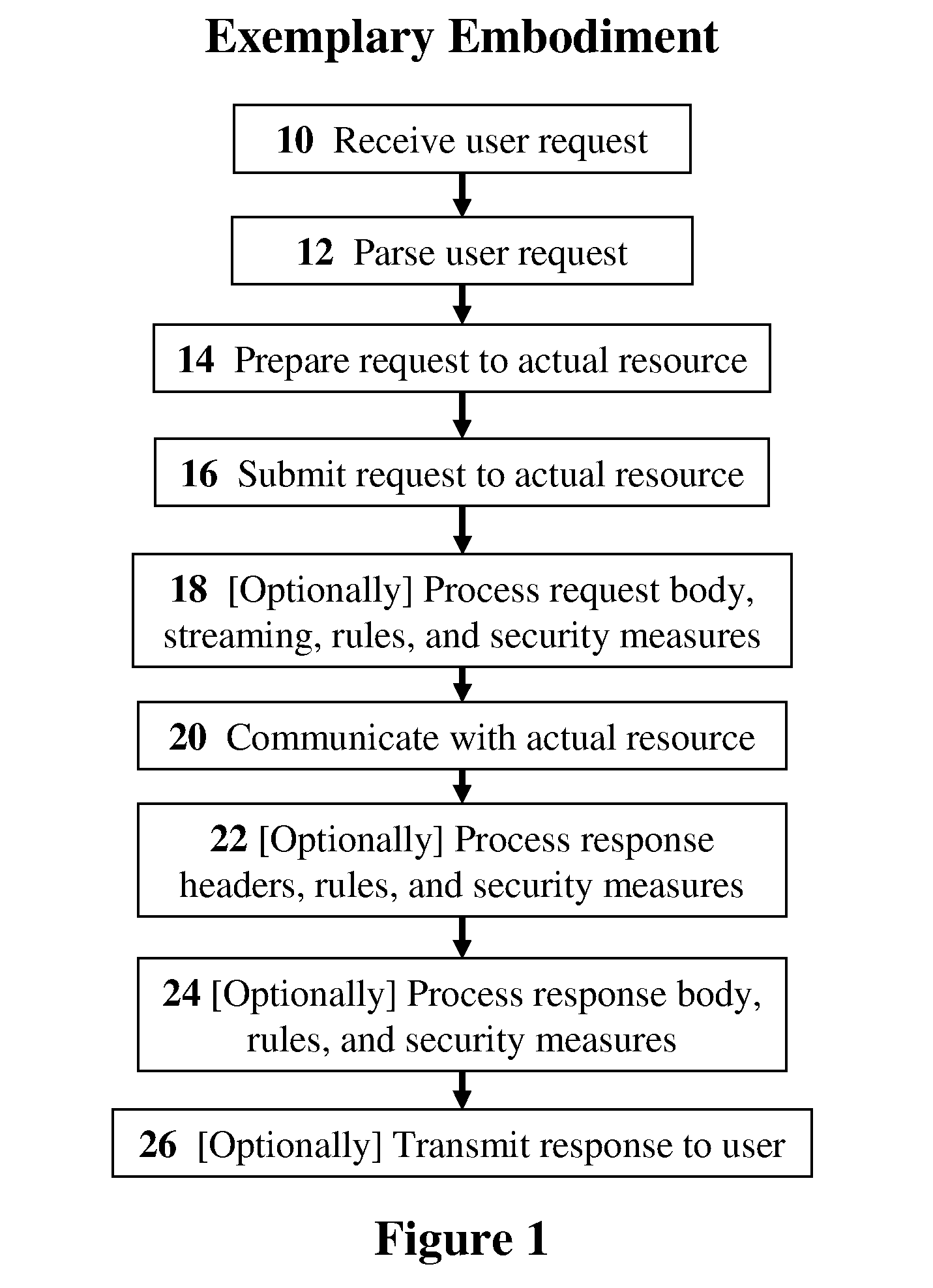
InactiveUS20110072489A1Full securityFull controlDigital data protectionMultiple digital computer combinationsVirtualizationData stream
The present invention discloses methods, devices, and media for securely utilizing a non-secured, distributed, virtualized network resource with applications to cloud-computing security and management. Methods including the steps of: receiving, by a deployed security mechanism, a user request over a network; parsing the user request by the deployed security mechanism; preparing, including applying security measures, the user request to transmit to a computing-service resource; and submitting, by the deployed security mechanism, the user request to the computing-service resource. Methods further including the steps of: dividing an original data stream into a set of split data streams; applying a first invertible transformation function to the split data streams, which produces an intermediate set of data streams; and extracting a final set of data streams from the intermediate set by applying a selection rule which produces the final set, thereby transforming the original data stream into individually-unintelligible parts.
Owner:PORTICOR
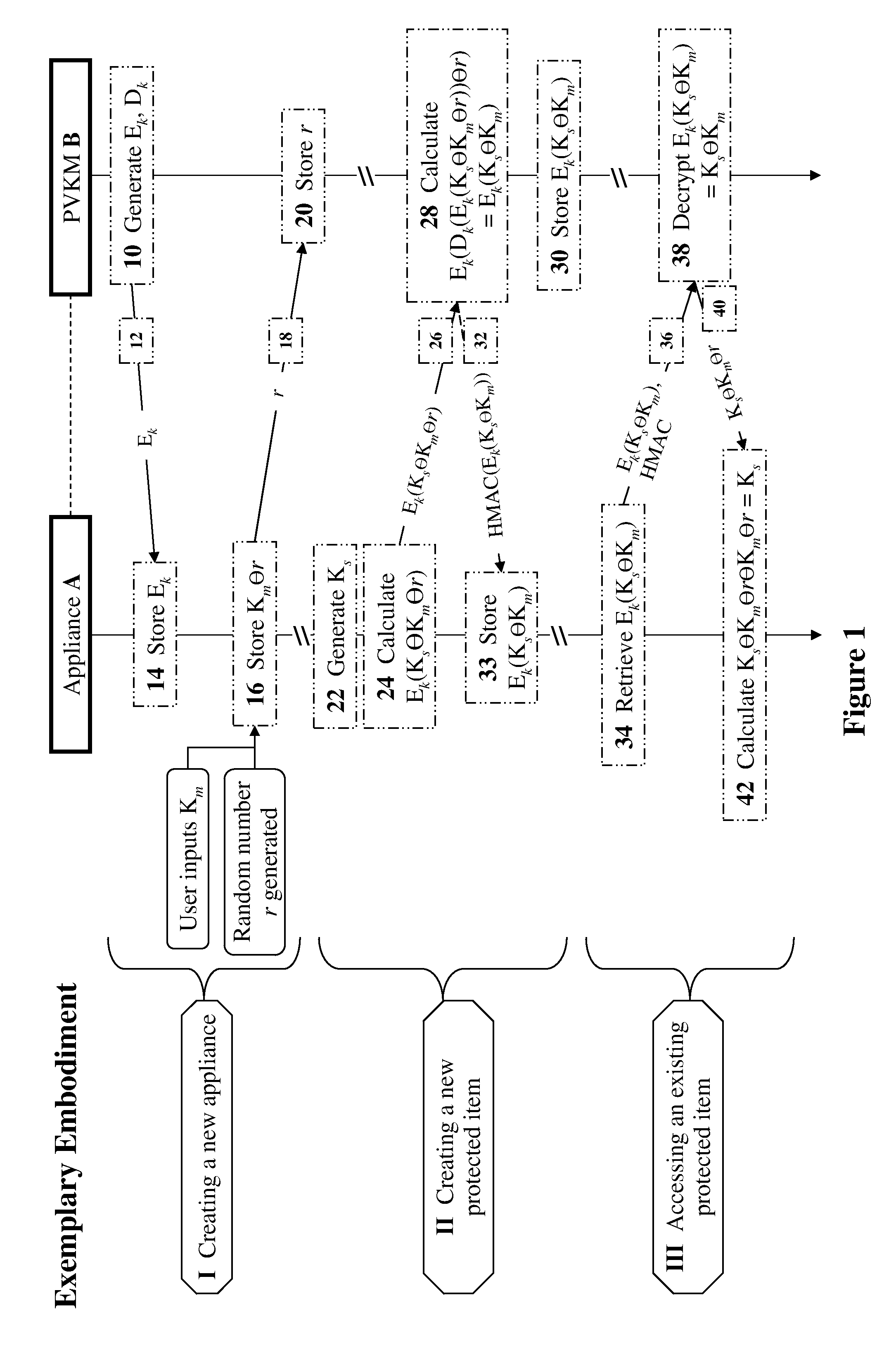
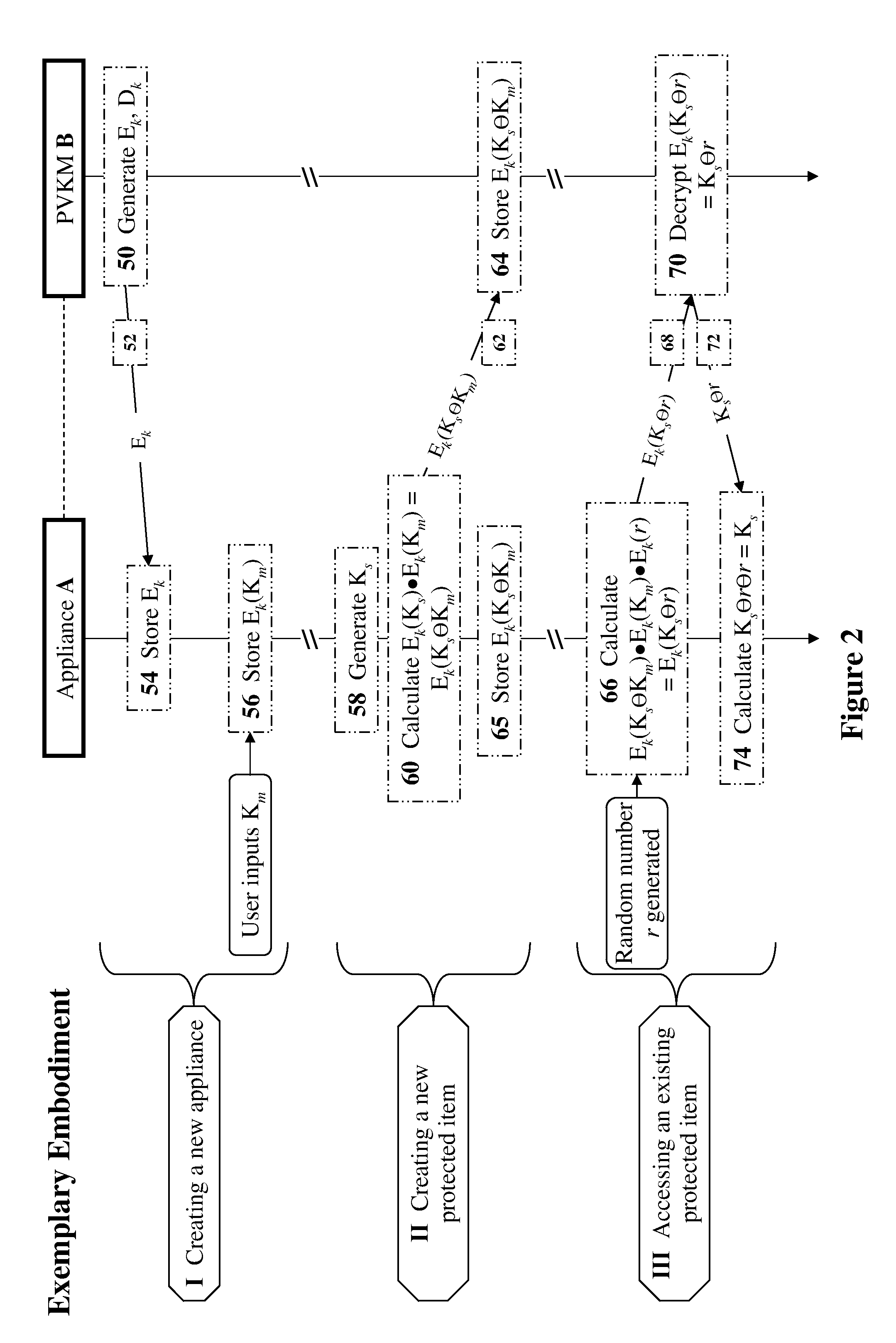
Methods, devices, and media for secure key management in a non-secured, distributed, virtualized environment with applications to cloud-computing security and management
ActiveUS20110311055A1Easy to optimizeKey distribution for secure communicationMultiple keys/algorithms usageVirtualizationCloud computing security
The present invention discloses methods, devices, and media for secure key management in a non-secured, distributed, virtualized environment with applications to cloud-computing security and management. Methods include the steps of: receiving an encryption request for protecting an original key at a first encryption location in a network computing-environment; initially encrypting the original key with a first location-specific secure-key, located at a second encryption location, to create a location-specific initially-encrypted key; and finally encrypting the location-specific initially-encrypted key with a second location-specific secure-key, located at a third encryption location, to create a finally-encrypted key which may then be used in any way in a cipher-location; wherein the locations are regions of memory located in computing devices operationally connected to the network computing-environment; and wherein each of the location-specific secure-keys is protected from compromise by any owner of other location-specific secure keys using an appropriate technique in the respective locations.
Owner:PORTICOR
Virtualized infrastructure platform for cloud data centers
ActiveCN103281306AEnsure safetyFunction extension of scheduling controlTransmissionSoftware simulation/interpretation/emulationInteraction systemsPython language
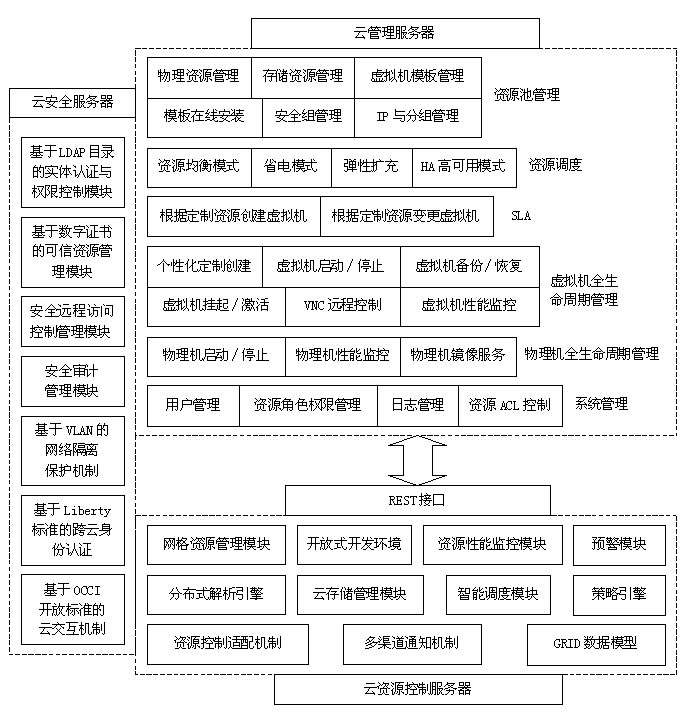
The invention discloses a virtualized infrastructure platform for cloud data centers, which comprises a cloud management server, a cloud resource control server and a cloud security server, the whole life cycles of various computational resources of a cloud platform are monitored and managed by the cloud management server, the various resources of the physical layer of the cloud platform are scheduled, controlled and managed by the cloud resource control server, and the cloud security server is used for establishing a cloud computation security control system in a private cloud and a secure interaction system for the private cloud and a public cloud; the cloud management server is integrated with the cloud resource control server through REST interfaces, and the cloud security server is respectively connected with the cloud management server and the cloud resource control server. The virtualized infrastructure platform for cloud data centers can realize security gateway-based unified remote virtual machine control and management, providing administrators with a unified access entrance for the management of virtual resources, and moreover, by means of directory service, the virtualized infrastructure platform for cloud data centers checks the validity of user identities; and a user can use the Python language to extend the resource scheduling control function.
Owner:INFORMATION & TELECOMM COMPANY SICHUAN ELECTRIC POWER
Security access protection for user data stored in a cloud computing facility
ActiveUS8713633B2Digital data processing detailsUser identity/authority verificationTelecommunications linkSecure state
In embodiments of the present invention improved capabilities are described for a method and system including storing a plurality of proxy access credentials for a user to securely access each of a plurality of cloud computing facilities; receiving a request from a client device for access to one of the plurality of cloud computing facilities; securing a communication link to the client device, thereby providing a secure link; receiving access credentials from the user through the secure link; verifying an identity of the user with the access credentials; assessing a security state of the client device to determine if the client is in compliance with a security policy; and if the client is in compliance with the security policy, coupling the client to one of the plurality of cloud computing facilities through a second secure link using a corresponding one of the plurality of proxy access credentials for the user.
Owner:SOPHOS
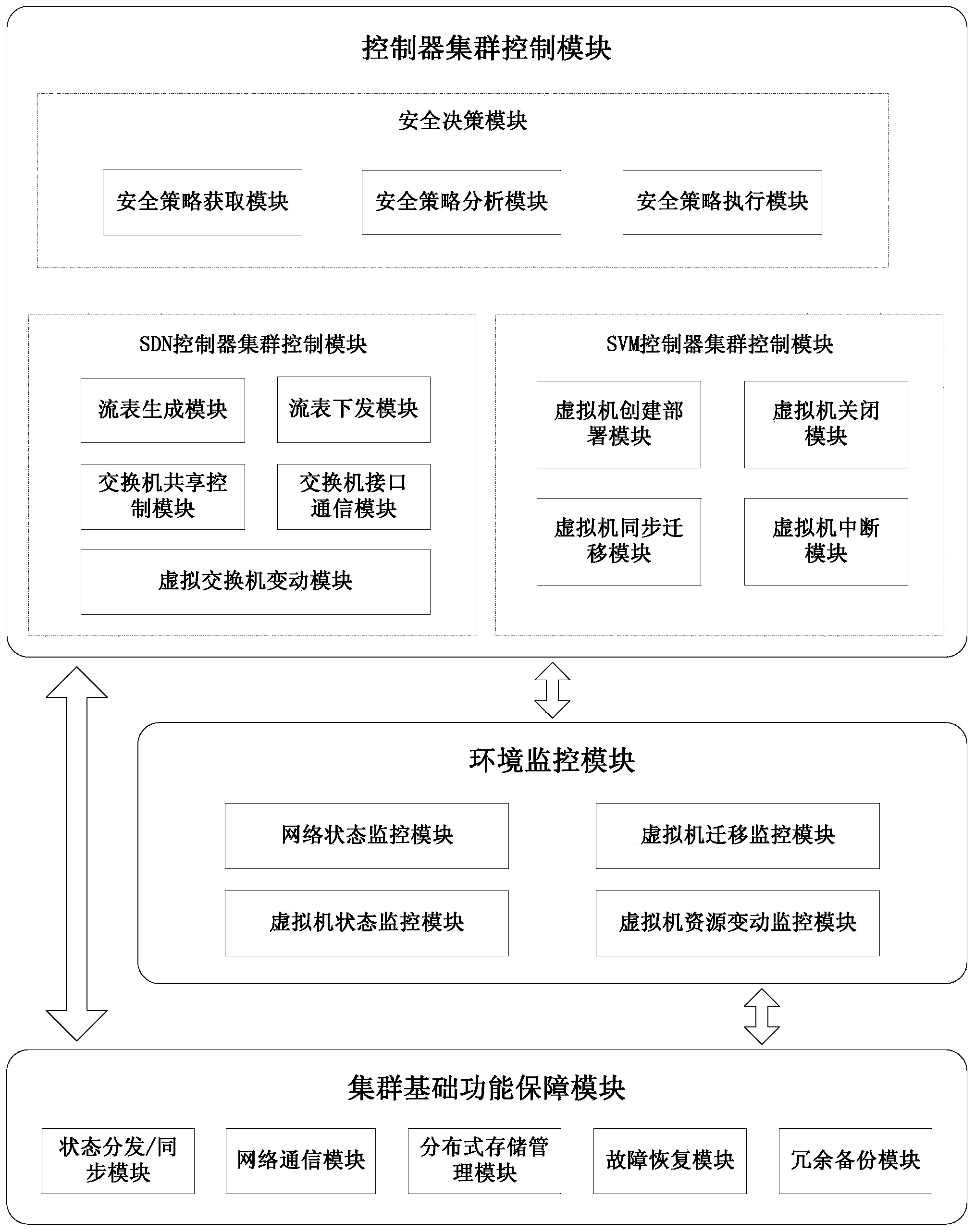
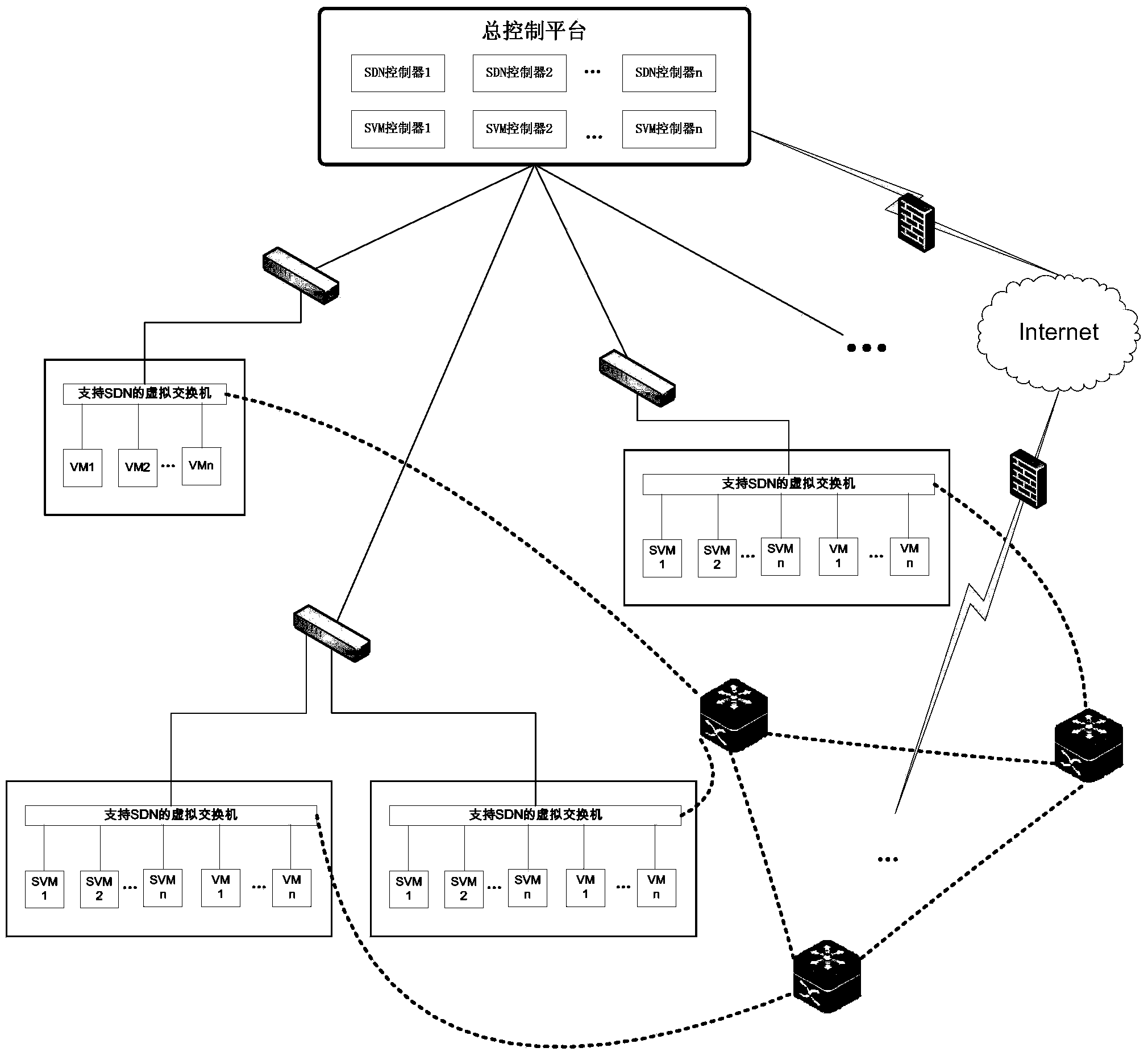
Cloud computing safety protection system and method based on SDN
The invention discloses a cloud computing safety protection system based on an SDN. The system is composed of a controller cluster control module, an environment monitoring module and a cluster basic function guarantee module. The controller cluster control module is the core of the whole system and acquires the change situations such as addition and deletion of switches, and addition and deletion of terminals of a current network and the change situations such as addition, deletion and migration of virtual machines in a cloud computing environment according to information fed back by the environment monitoring module, virtual switches supporting the SDN and virtual platform management interfaces supporting the SDN are adopted in the environment monitoring module, and changes, caused by migration, addition and deletion of the virtual machines and other service flow changes, of safety requirements are automatically recognized under the condition that normal service operation is not affected. The cluster basic function guarantee module conducts coordinated management on multiple controllers in the cloud environment. The invention further discloses a cloud computing safety protection method based on the SDN. According to the system and the method, customizable safety protection services can be flexibly and quickly provided according to requirements in the cloud environment.
Owner:蓝盾信息安全技术有限公司
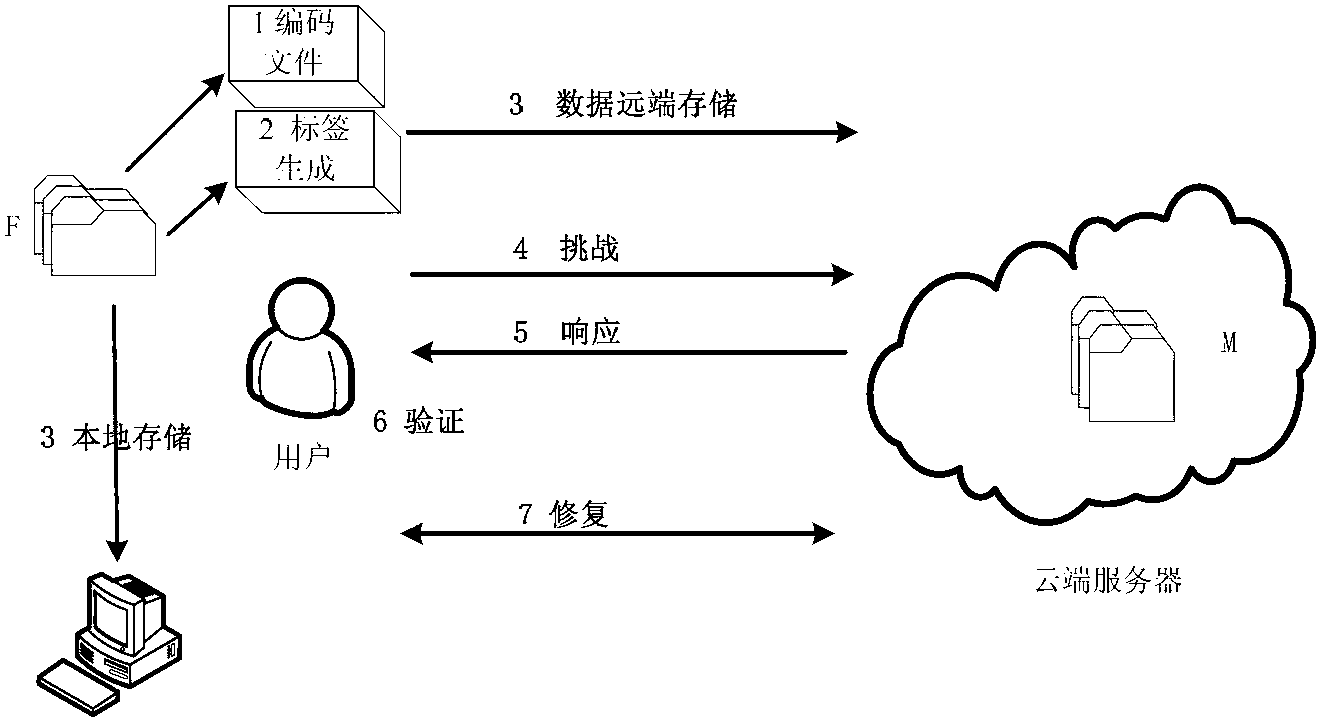
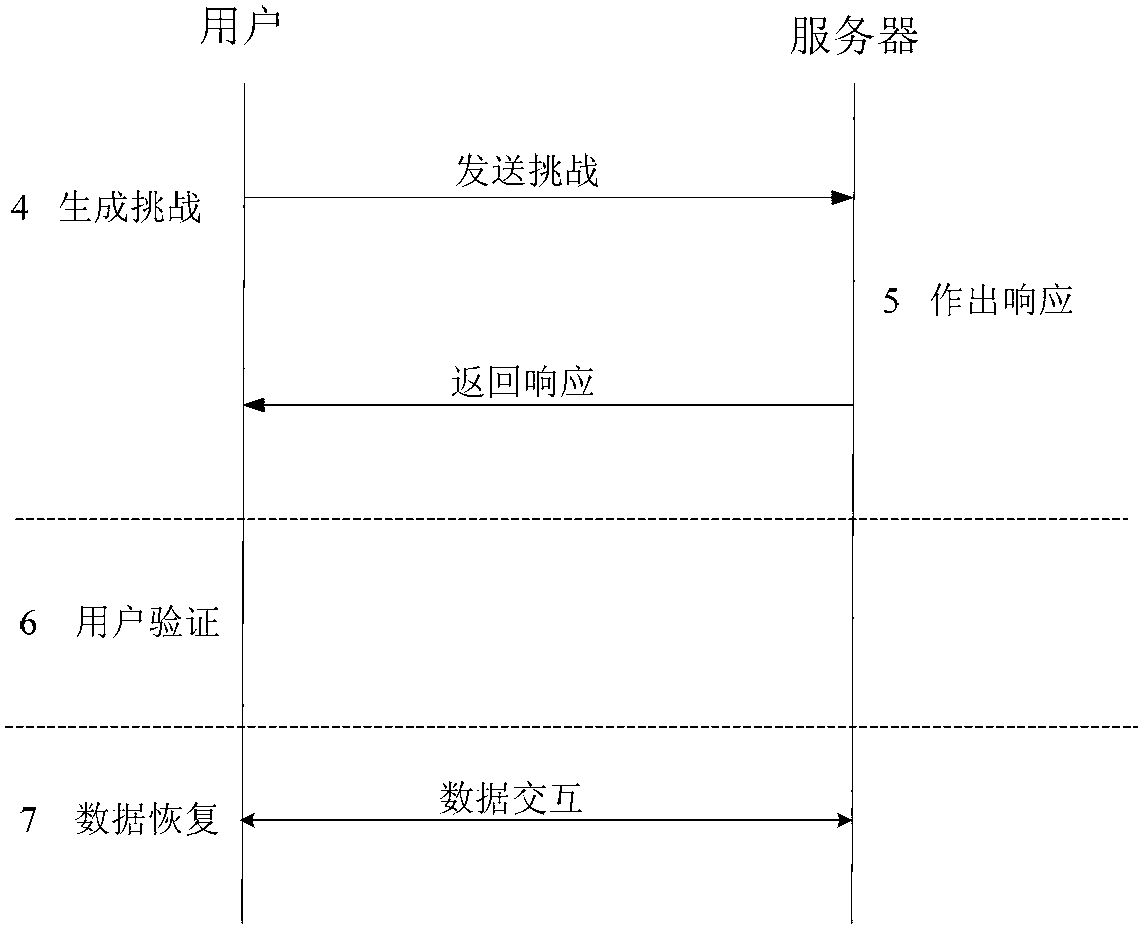
Distributed cloud storage data integrity protection method
InactiveCN102710757AAchieve positioningSmall amount of local storageTransmissionData integrityLinear coding
The invention relates to a distributed cloud storage data integrity protection method. The method comprises: (1) data division and coding {F--M}; (2) generation of homomorphic verifiable tags (HVTs) {(sk,F)--HVTs}; (3) remote data storage {(M(j),HVT--Sj)}; (4) a user launching a challenge {chal}; (5) a server making a response {R}; (6) verification{(R,sk)--('success', 'failure')}; and (7) data recovery {(M*,P)--F}. According to the method provided by the invention, the communication cost is reduced by adopting random data block sampling; data error location and error recovery can be realized by using linear coding; and the method has no limits to the number of times for data possession verification, is high in the verification confidence, safe and reliable. Accordingly, the method provided by the invention has good practical value and wide application prospect in the technical field of cloud security.
Owner:BEIHANG UNIV
Methods and devices for trusted protocols for a non-secured, distributed environment with applications to virtualization and cloud-computing security and management
ActiveUS20130247230A1Without impairing functionalityControl process safetyDigital data processing detailsAnalogue secracy/subscription systemsVirtualizationTrusted Computing
The present invention discloses methods for trusted protocols for a non-secure computing-environment. Methods include the steps of: upon request for determining that an untrusted computing resource is trustworthy, vouching for the untrusted resource as trustworthy by a trusted computing resource upon satisfying at least one criterion of: the trusted resource was directly involved in setting up and / or activating the untrusted resource; and / or has access to a database of identifying credentials and / or information which allow the trusted resource to verify that the untrusted resource is trustworthy; and concealing at least one secret that needs to be present on any computing resource, wherein at least one secret is concealed differently on each computing resource; and transmitting at least one secret from any computing resource to any other computing resource in a way that changes the step of concealing at least one secret without any computing resource knowing at least one secret.
Owner:PORTICOR
Methods, devices, and media for secure key management in a non-secured, distributed, virtualized environment with applications to cloud-computing security and management
ActiveUS8625802B2Key distribution for secure communicationError detection/correctionVirtualizationCloud computing security
The present invention discloses methods, devices, and media for secure key management in a non-secured, distributed, virtualized environment with applications to cloud-computing security and management. Methods include the steps of: receiving an encryption request for protecting an original key at a first encryption location in a network computing-environment; initially encrypting the original key with a first location-specific secure-key, located at a second encryption location, to create a location-specific initially-encrypted key; and finally encrypting the location-specific initially-encrypted key with a second location-specific secure-key, located at a third encryption location, to create a finally-encrypted key which may then be used in any way in a cipher-location; wherein the locations are regions of memory located in computing devices operationally connected to the network computing-environment; and wherein each of the location-specific secure-keys is protected from compromise by any owner of other location-specific secure keys using an appropriate technique in the respective locations.
Owner:PORTICOR
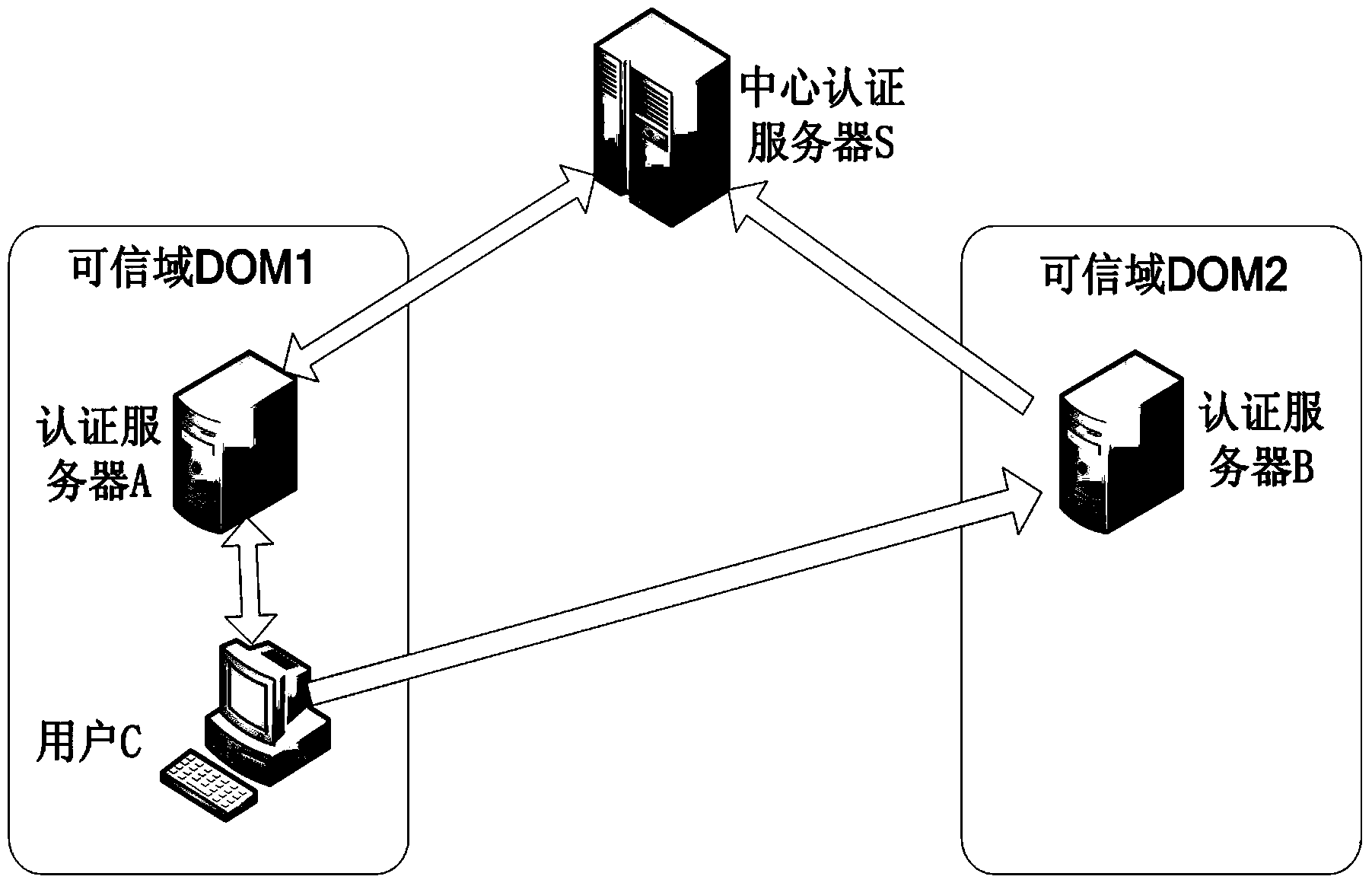
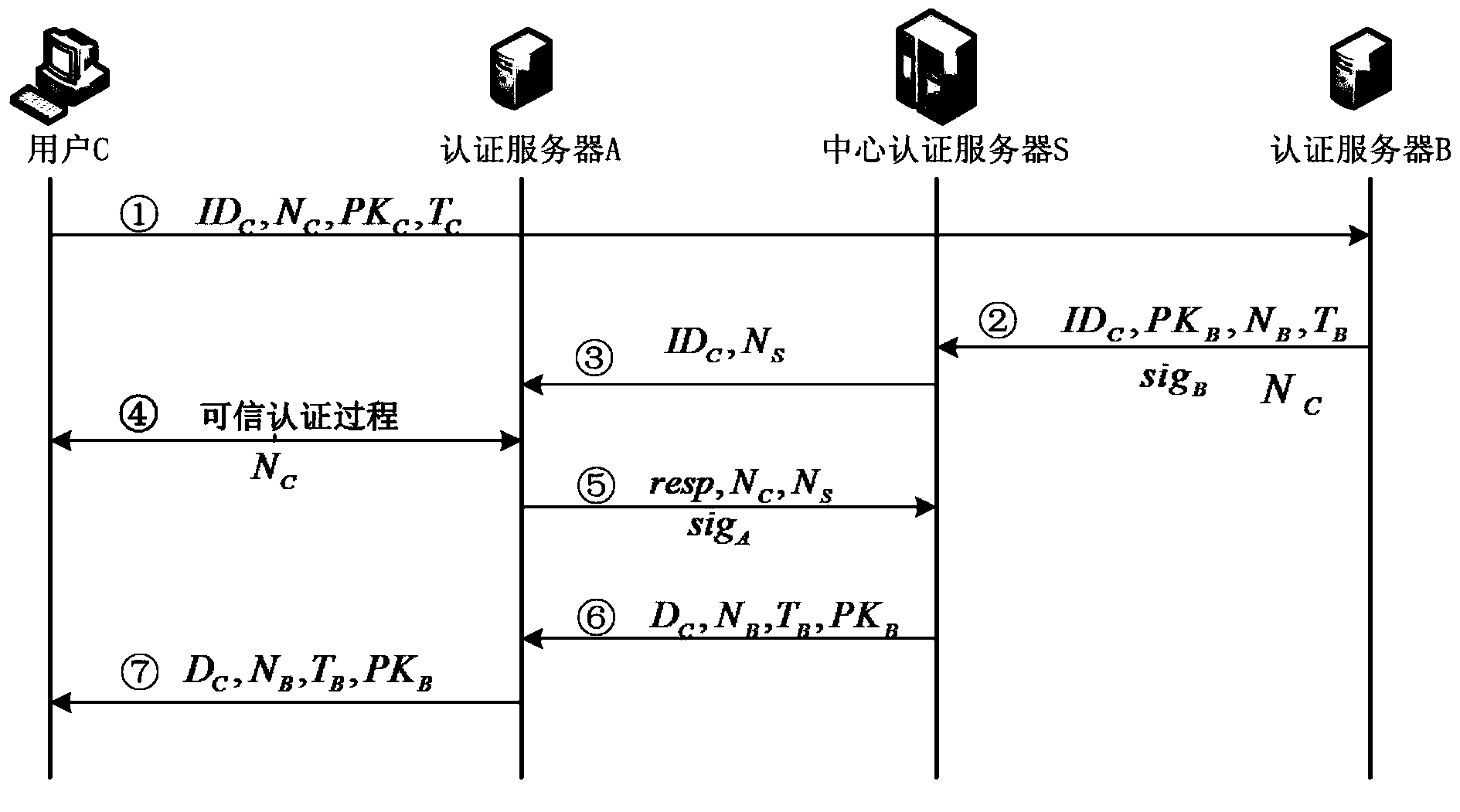
Method for certificateless cross-domain authentication in credible could computing environment
ActiveCN103546567AAddress certificate maintenance overheadReduce overheadKey distribution for secure communicationHypothesisAuthentication server
The invention relates to a method for certificateless cross-domain authentication in a credible cloud computing environment and belongs to the technical field of cloud computing safety. According to the method for certificateless cross-domain authentication in the credible cloud computing environment, the certificateless public key cryptography technology is introduced into cross-domain authentication, credible cross-domain authentication is achieved in the process of credible cloud computing, a certificateless public key cryptosystem is applied, the problem of the certificate maintenance expense of a traditional digital certificate authentication system and the problem of private key trusteeship of a public key cryptography system based on the identity are solved. According to the method for certificateless cross-domain authentication in the credible cloud computing environment, a user public key is generated based on the identity, a part of a private key of a user is generated by the user, and the other part of the private key of the user is generated by a center authentication server. According to the method for certificateless cross-domain authentication in the credible cloud computing environment, a certificate system is abandoned, the expense of the authentication system is reduced, the private key of the user is protected at the same time, bilinear pairing computation is applied to the certificateless public key cryptosystem, it is proved that a safety hypothesis based on bilinear pairing computation is high in safety, the certificateless public key cryptosystem is used for identity authentication and session key negotiation, and therefore it is ensured that the system is high in safety.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND +1
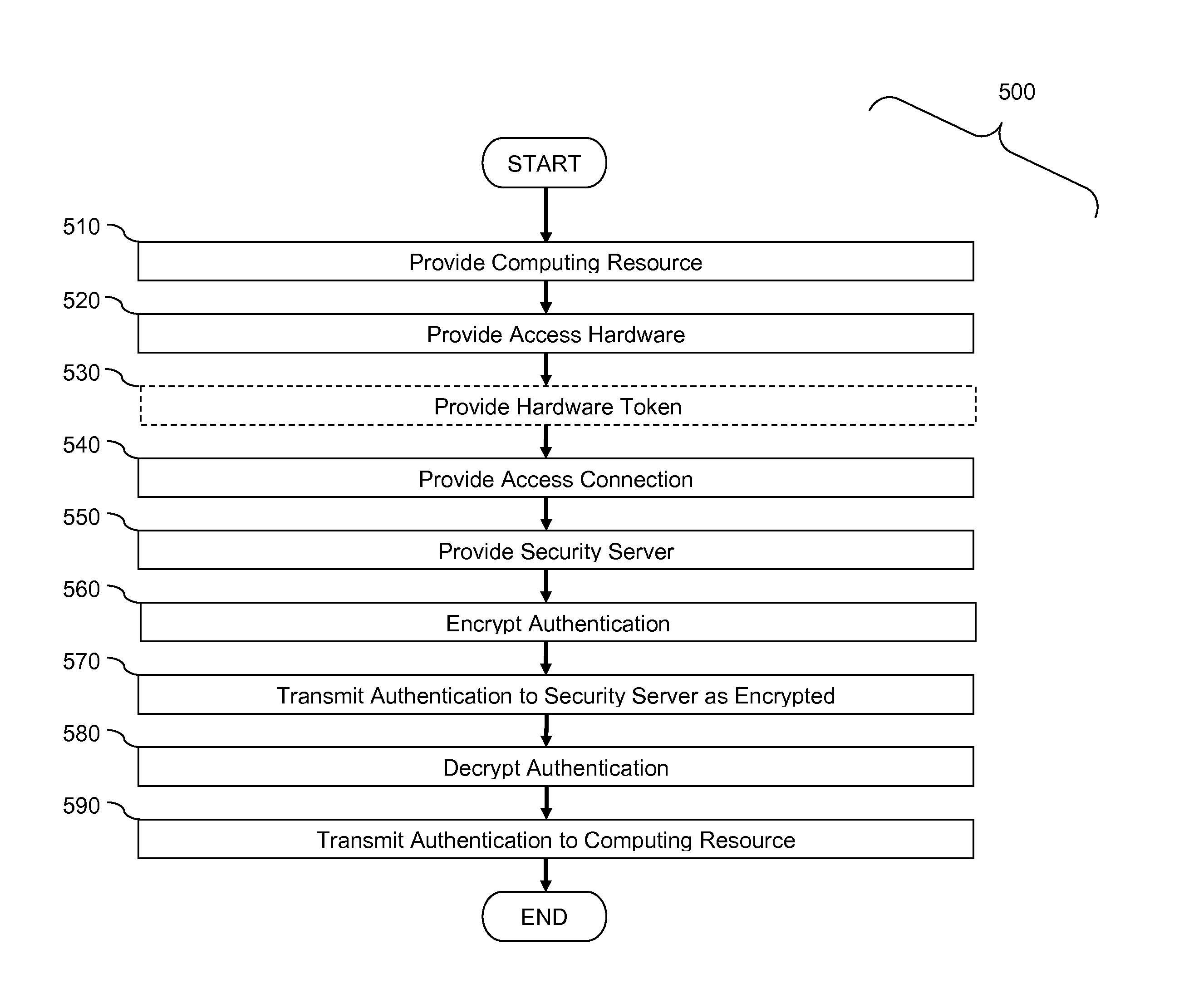
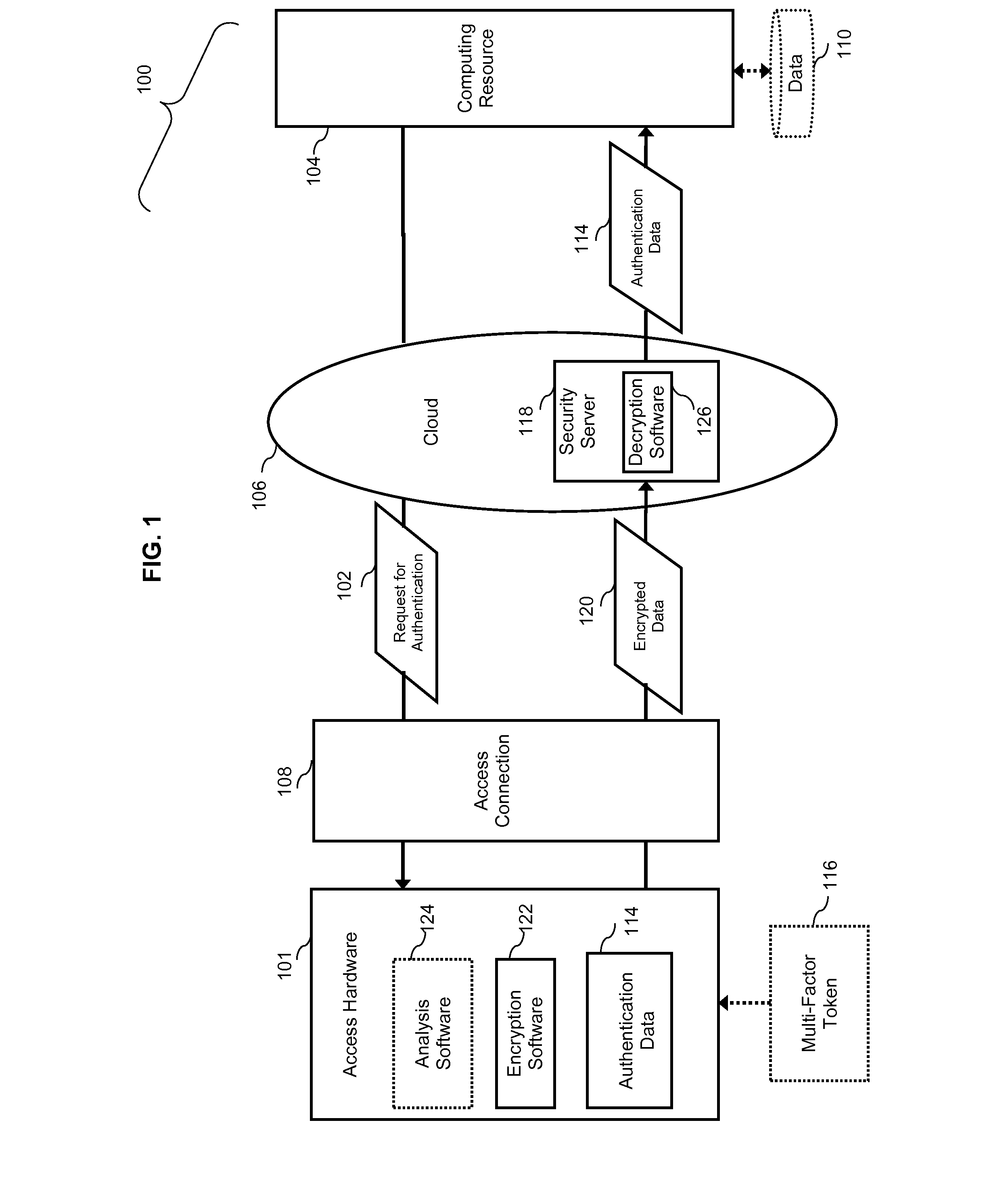
Security server for cloud computing
InactiveUS20130061310A1Improve securityDigital data processing detailsMultiple digital computer combinationsComputer resourcesPhysical security
A system, method, and server improving the security of accessing Internetworked computer resources, especially over public access connections, without requiring additional servers from either the resource provider or the authenticating user. User authentications are transmitted over data access connections over which users do not have administrative rights and / or physical security control. A resource request which includes user authentications can be encrypted on a user computer and transmitted over the internet or other data network over which the user has no administrative access or physical control. A security server receives the encrypted resource request, decrypts it, and forwards the resource request to a cloud computing resource.
Owner:WHITMYER JR WESLEY W
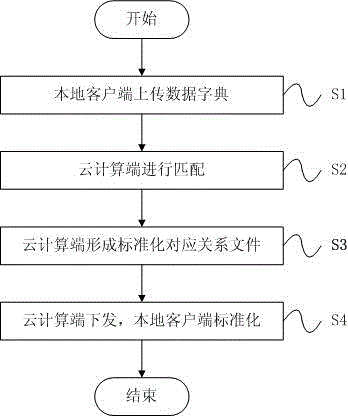
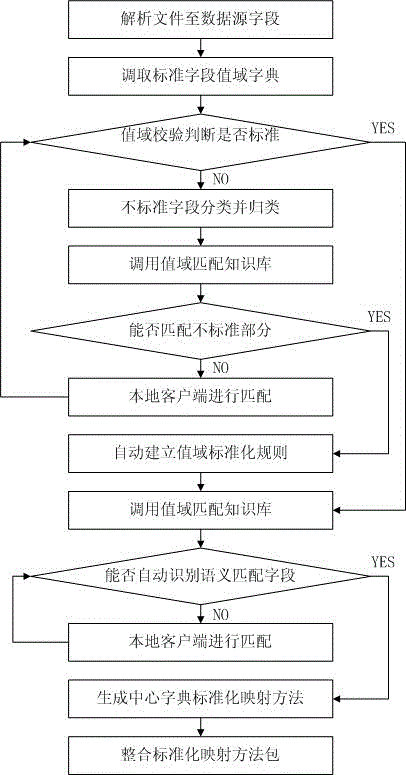
Automatic standardization method and system for medical data dictionaries
ActiveCN105787282AImprove reliabilityEasy to useNatural language data processingSpecial data processing applicationsClient-sideCloud computing security
The invention discloses an automatic standardization method and system for medical data dictionaries. The method comprises steps as follows: S1: a local client side uploads a data dictionary with unknown standard conformance to a cloud computing side; S2: the cloud computing side matches the uploaded data dictionary with unknown standard conformance with a center standard dictionary, and the corresponding relation between the two dictionaries is automatically established; S3: a standardized corresponding relation file is formed on the cloud computing side; S4: the cloud computing side sends the standardized corresponding relation file to the local client side, and the local client side standardizes local data according to the standardized corresponding relation file. Based on cloud service, non-standard data dictionaries of manufacturers or hospitals are standardized, local client sides of the manufacturers or the hospitals upload the non-standard data dictionaries to the cloud computing side, the cloud computing side performs automatic matching, the standardized corresponding relation files are sent to the local client sides, the local client sides can standardize the non-standard data dictionaries locally, and the method and system are convenient and quick.
Owner:国家卫生计生委统计信息中心 +1
Cloud computing safety control platform based on safety classification
InactiveCN102843387AEasy to install and deploySimple configurationTransmissionVirtual memorySafety control
The invention discloses a cloud computing safety control platform based on safety classification. The cloud computing safety control platform comprises a cloud computing system, at least one domain included in the cloud computing system and at least one virtual platform included in the domain, wherein at least one cloud controller is arranged in the cloud computing system; at least one domain controller is arranged in the domain; at least one security manager is arranged in the virtual platform; the overall cloud is monitored and all domains are controlled by the cloud controller; an instruction from the cloud controller is received and all virtual platforms in the domain are controlled by the domain controller; and the instruction of the domain controller is received by the security manager in the virtual platform and corresponding safety level of VM (virtual memory) is operated. According to the cloud computing safety control platform based on safety classification, a cloud environment is divided into different safety level domains, so that the cloud computing system has the characteristics of simplicity, isolation, flexibility and expandability.
Owner:北京太能沃可网络科技股份有限公司
Cloud computing scheduling method and system based on big data and deep learning neural networks
ActiveCN108037993AImprove scheduling efficiencyResource allocationNeural learning methodsCloud resourcesDistributed computing
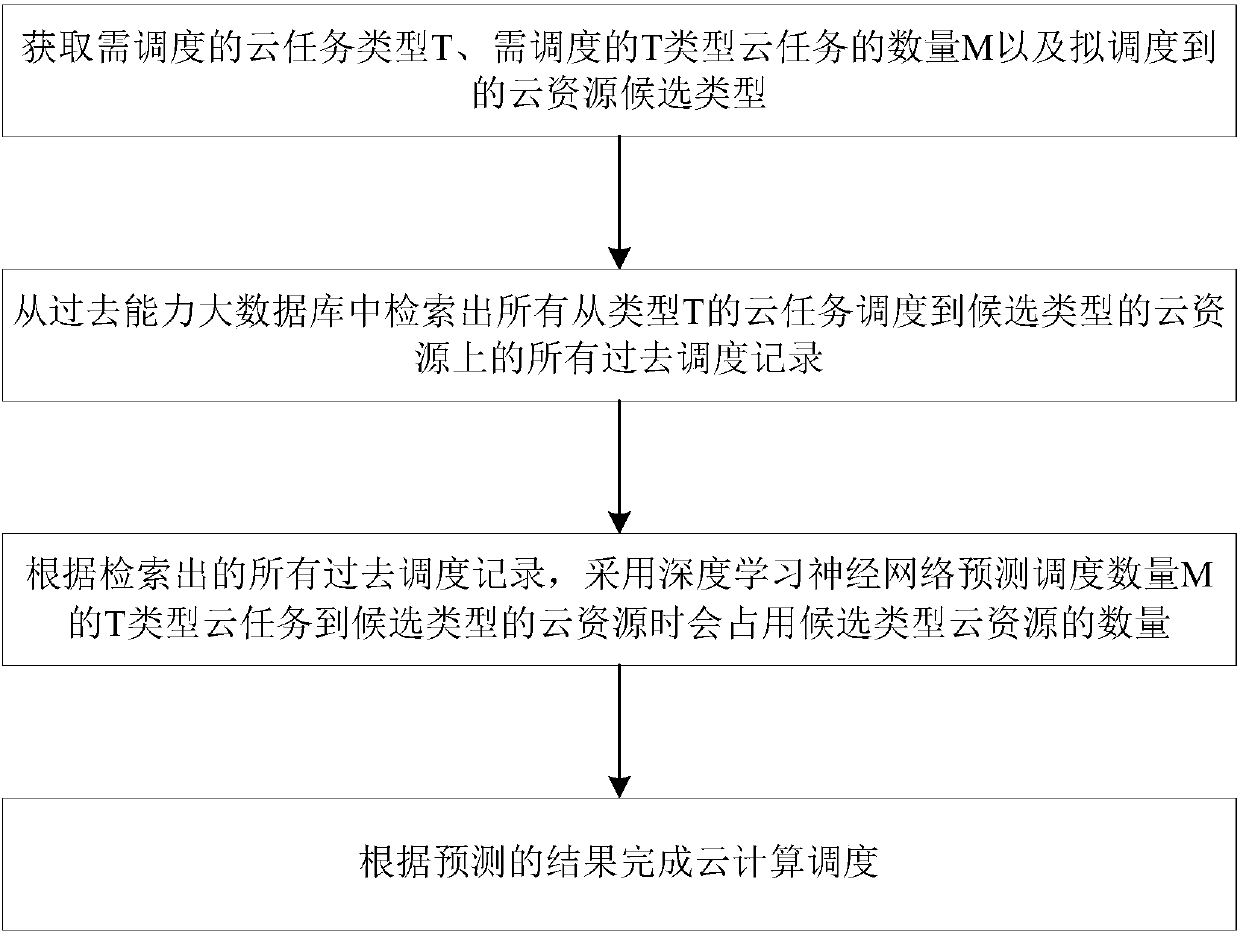
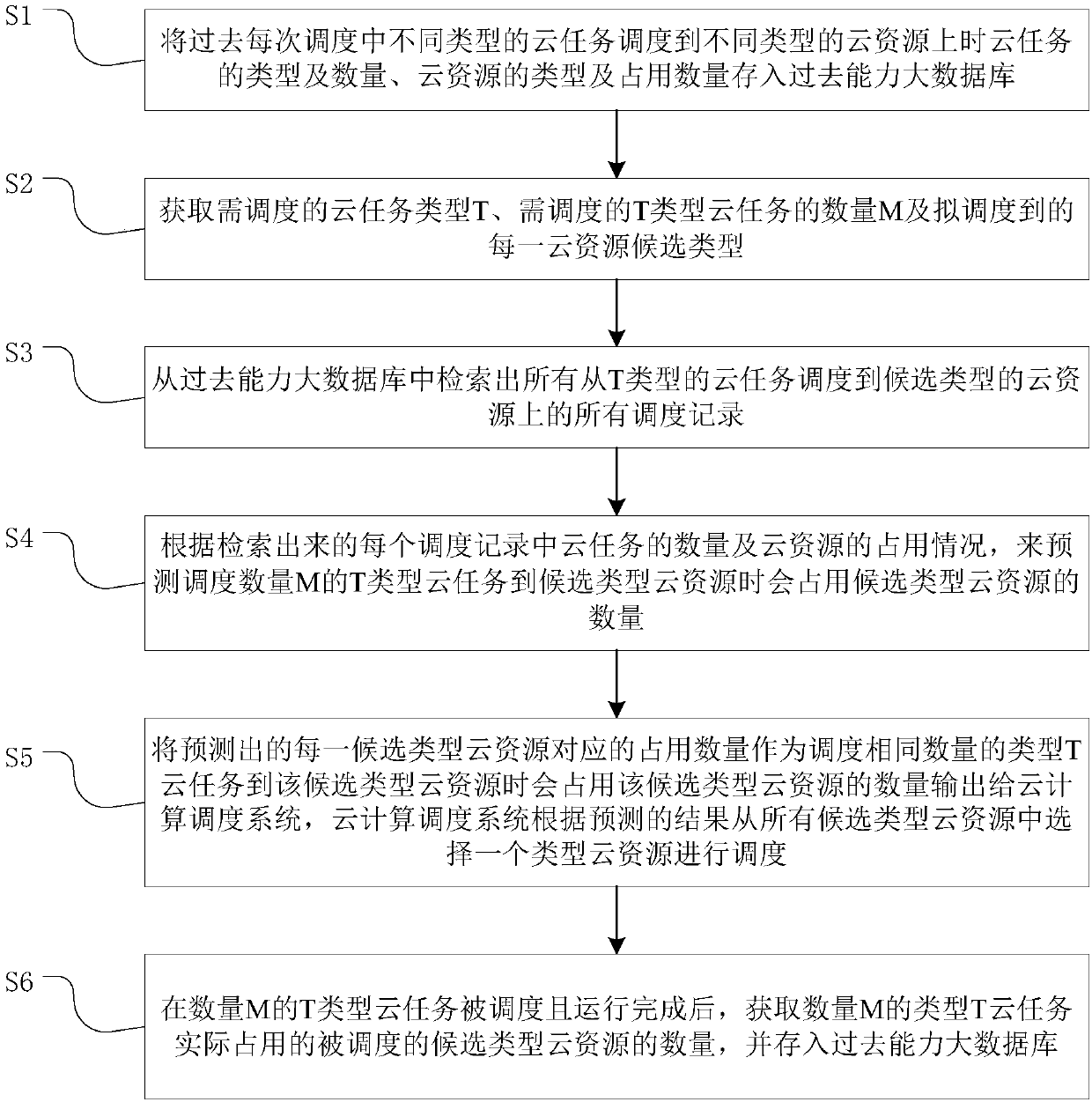
The invention discloses a cloud computing scheduling method and a system based on big data and deep learning neural networks. The method includes the steps that a cloud task type T to be scheduled, amount M of type T cloud tasks to be scheduled and a scheduled cloud resource candidate type are acquired; all past scheduling records scheduled from all the cloud tasks of the type T to the cloud resources of the candidate type are searched out from past ability big database; according to all the past scheduling records searched out, when T type cloud tasks of the amount M is scheduled to the cloudresources of the candidate type, the deep learning neural network is used to predict the amount of the can-be-occupied cloud resources of the candidate type; and according to the predicted results, the cloud computing scheduling is accomplished. The cloud computing scheduling method and the system based on the past ability big data and the deep learning neural networks, by a objective fact of occupation situation of the cloud resources when the cloud tasks of different types in the past are scheduled to different cloud resources, the predicting is carried out, the predicted results are more accurate, and the scheduling efficiency is higher. The cloud computing scheduling method and the system based on big data and deep learning neural networks are widely applicable to the field of cloud computing.
Owner:SUPERPOWER INNOVATION INTELLIGENT TECH DONGGUAN CO LTD
Virtualization technology-based cloud computing security terminal
InactiveCN104125251AHigh strengthRealize two-way data backupTransmissionHuman–machine interfaceOperational system
The invention discloses a virtualization technology-based cloud computing security terminal, which comprises a virtualization technology-based cloud computing terminal key, which is characterized in that the hardware part of the cloud computing terminal key comprises a cloud computing security terminal; and a software part is also included and comprises an operation system arranged on a virtualization operation platform. A clean, sealed, comprehensive and dedicated operation system which can realize two-way data backup is provided for the cloud computing terminal. Virtualization is carried out on all tools and applications of the cloud computing operation on the dedicated human-computer interface provided by the dedicated operation system. Self explosion and self destruction are carried out on the cloud computing terminal in the cases of illegal access, reading, copying and interception of data and the system. the invention provides a cloud computing security terminal which is high in strength and applicable to the government, the financial department, the military department and the political science and law department. The terminal can serve as an intelligent Key to be connected onto other intelligent online electronic device for use, can also be equipped with a display device, an input device and an internet device to serve as a special cloud computer and has wide market application prospects.
Owner:华茂云天科技(北京)有限公司
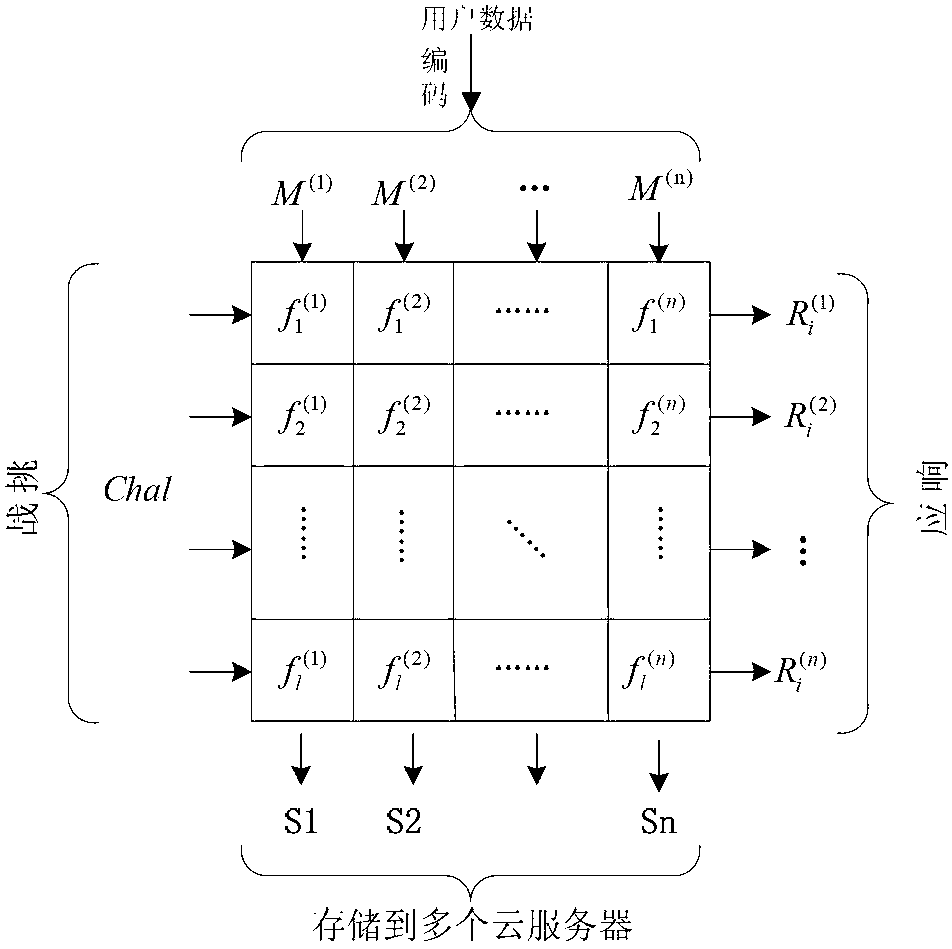
Efficient cloud storage data possession verification method
InactiveCN102647433AReduce computational overheadConfidenceUser identity/authority verificationValidation methodsCloud data
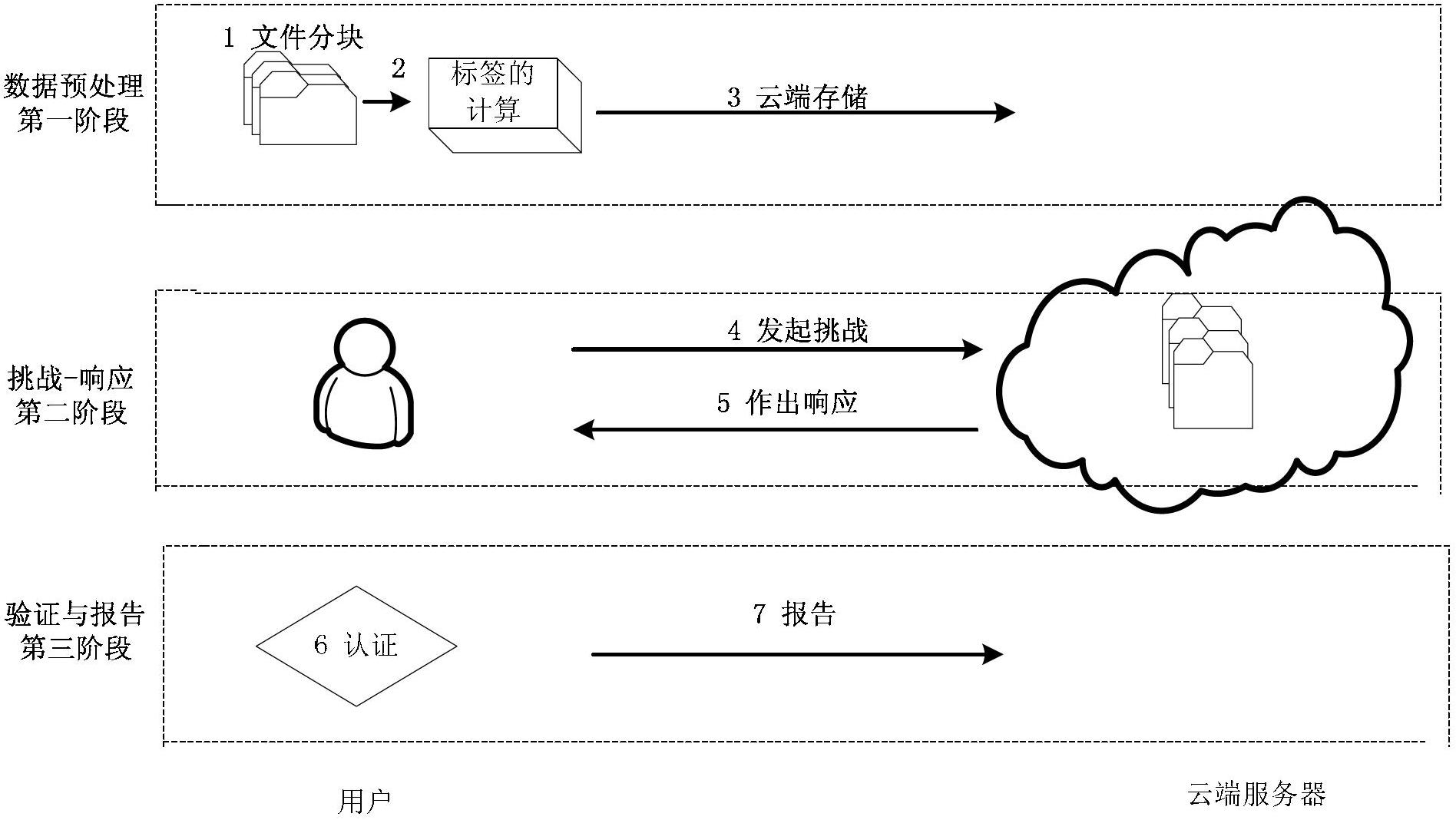
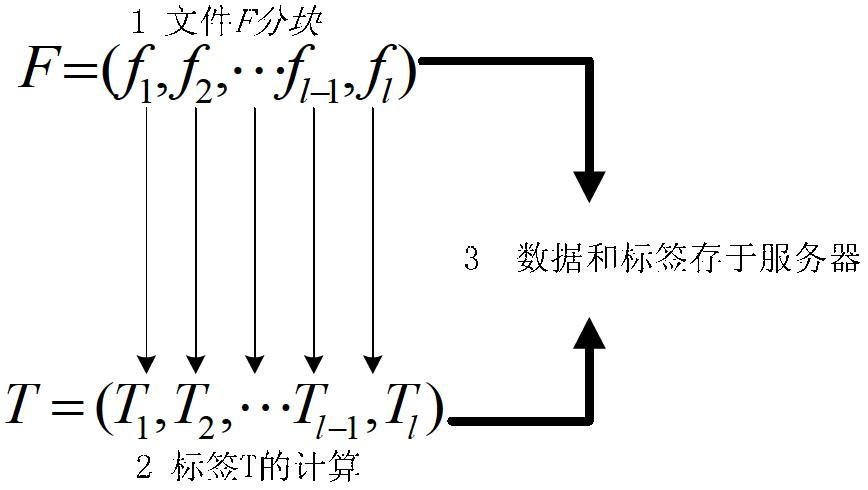
The invention discloses an efficient cloud storage data possession verification method. The method comprises the following steps of: step 1, file partitioning {F->(f1, f2...fl)}; step 2: label computation {(sk, F) ->Ti}; step 3: cloud storage of data {(F, Ti->S}; step 4: initiating challenge by a user (chal); step 5: making a response by a server; step 6: verification {(R, sk) ->('success', 'failure')}; and step 7: reporting {Report}: if verification output is 'failure', sending a warning notice to the server by the user. According to the method, a double-line pair technology is used for realizing the possession verification for the cloud data, in the challenge-response interactive process, data blocks are sampled randomly, the communication traffic is low and fixed, and is independent from the size of the file, and moreover, the verification times is not limited. The method has better practical value and wide application foreground in the technical field of cloud computing security.
Owner:BEIHANG UNIV
Security service device and method, service processing device and method, and system
InactiveCN106161378AReflect individual needsMeet individual needsMetering/charging/biilling arrangementsPersonalizationClient-side
The invention provides a security service device and method, a service processing device and method, and a system. The method comprises the steps of obtaining a current application scene and a security level setting parameter of a client as a strategy identifier in real time according to a security request sent by the client after the client is authenticated successfully; matching in a preset strategy library according to the strategy identifier, determining a security strategy corresponding to the strategy identifier, and issuing the security strategy to the client and a service processing module of the service processing device of a cloud computing security service system; providing a corresponding security service capability to the client and / or the service processing device according to the determined security strategy; and monitoring the resource use amount when the security service capability is called by the service processing device of the cloud computing security service system, and charging the resource use amount according to resource charging standards. According to the scheme, different security strategies are made through the strategy identifiers, therefore, the corresponding security service is provided, and the individual security demands of a user and service are satisfied.
Owner:CHINA MOBILE COMM GRP CO LTD
Data processing delay optimization method and system based on edge computing
ActiveCN108418718AImprove processing efficiencyReduce processing latencyData switching networksSpecial data processing applicationsEdge computingNetwork architecture
The invention discloses a data processing delay optimization method and system based on edge computing. The method comprises the following steps: building a network architecture model; determining thecomputation delay of an edge computing layer by using a Lagrangian multiplier method; determining the communication delay of the edge computing layer by adopting a Kruskal method; determining the computation delay of a cloud computing layer; determining the communication delay of the cloud computing layer by adopting a balanced transmission method; determining a data processing delay optimizationmodel according to the computation delay and the communication delay of the edge computing layer, and the computation delay and the communication delay of the cloud computing layer; and determining an optimal data processing delay value according to the data processing delay optimization model. The data processing delay optimization method based on the edge computing provided by the invention firstly determines the data processing delay of the edge computing layer, then determines the data processing delay of the cloud computing layer, and finally, determines the optimal data processing delayvalue according to the data processing delay of the edge computing layer and the data processing delay of the cloud computing layer, therefore the system data processing delay is reduced, and the data processing efficiency is improved.
Owner:QUFU NORMAL UNIV
Cloud computing secure access method, device and system
The invention discloses a cloud computing secure access method, a device and a system. The method includes obtaining authentication information input by a client, determining a client identification of the client, which can not be changed voluntarily, when a common password corresponding to a user name is determined to be correct, determining whether a corresponding relationship between the client identification and the address of a cloud machine exists in a data base of a distribution authentication server or not through the distribution authentication server, determining whether a dynamic password is correct or not as well, if the corresponding relationship exists and the dynamic password is correct, informing the client of a successful logging, otherwise, informing the client of a failed logging, and when the password information corresponding to the user name is determined to be incorrect, informing the client of a failed logging. By means of the scheme, even though an illegal user steals the user name and the common password, the illegal user is incapable of establishing the corresponding relationship between the client identification and the address of the cloud machine, and the illegal user can not obtain a permission of logging in the cloud machine through stealing the common password, and thereby the safety of logging in the cloud machine is improved.
Owner:GUANGZHOU BINGO SOFTWARE
Method and system for multi-tenant application isolation in cloud computing platform
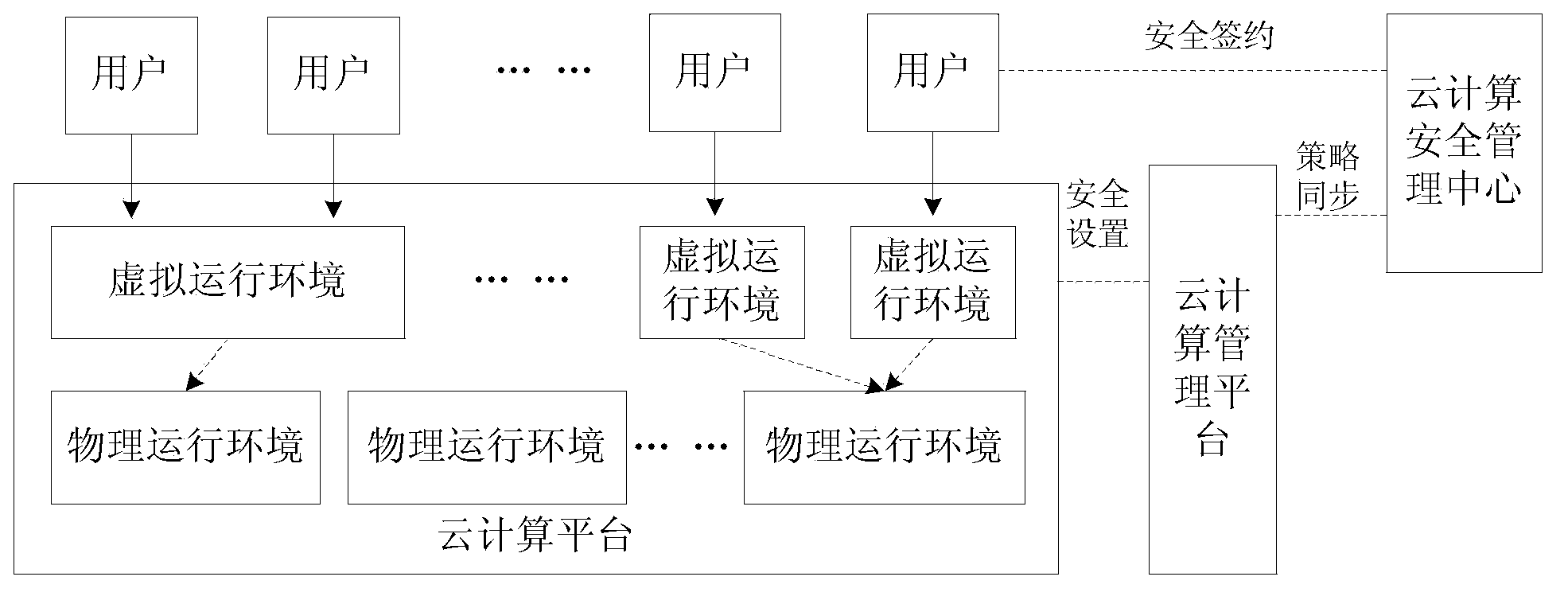
ActiveCN103810444AAchieve safe operationInternal/peripheral component protectionTransmissionSecurity policySafe operation
The invention discloses a method for multi-tenant application isolation in a cloud computing platform. The method comprises the steps that before deploying a user application, a cloud computing security management center and a user sign a security contract, and after signing, the cloud computing security management center builds an authority record for the user application; after the cloud computing security management center receives the environment deployment information of the user application sent by a cloud computing management platform, if the authority record of the user application is inquired, a security policy of the user application is generated according to the authority record and the environment deployment information, and is sent to the cloud computing management platform; after the cloud computing management platform receives the security policy, the cloud computing operating environment of the user application is deployed according to the security policy. According to the method, the safe operation of applications of different tenants under a multi-tenant framework in the isolated cloud platform environment is realized. The invention also discloses a system for multi-tenant application isolation in the cloud computing platform.
Owner:ZTE CORP
SDN-based SDP security group implementation method and security system
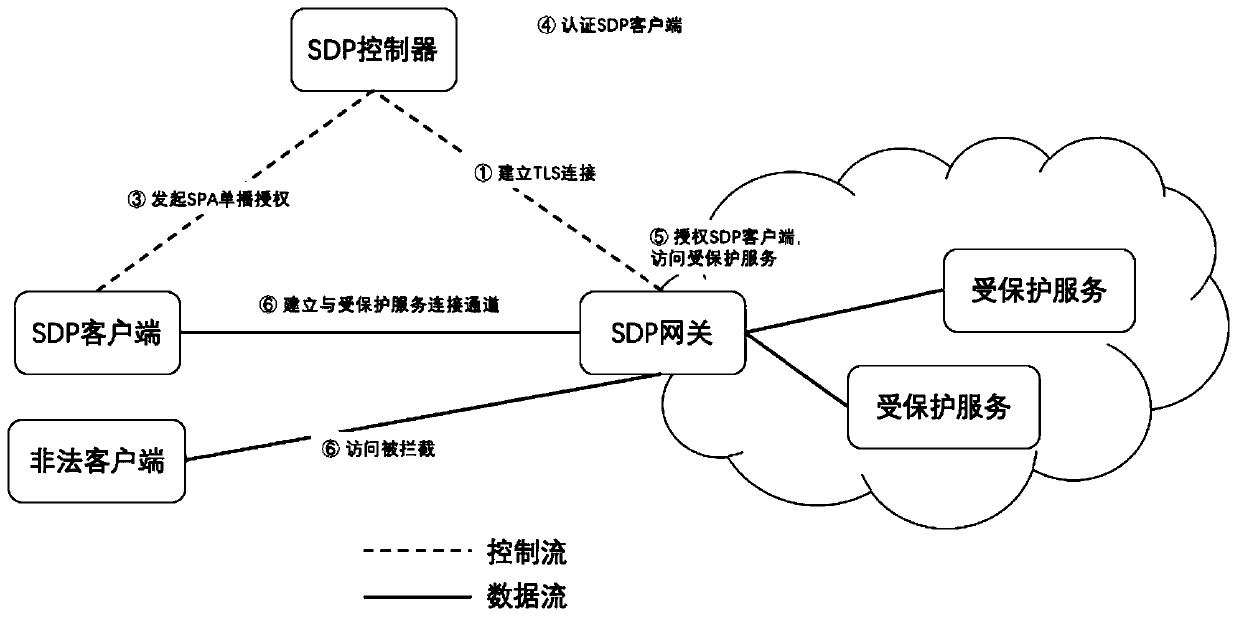
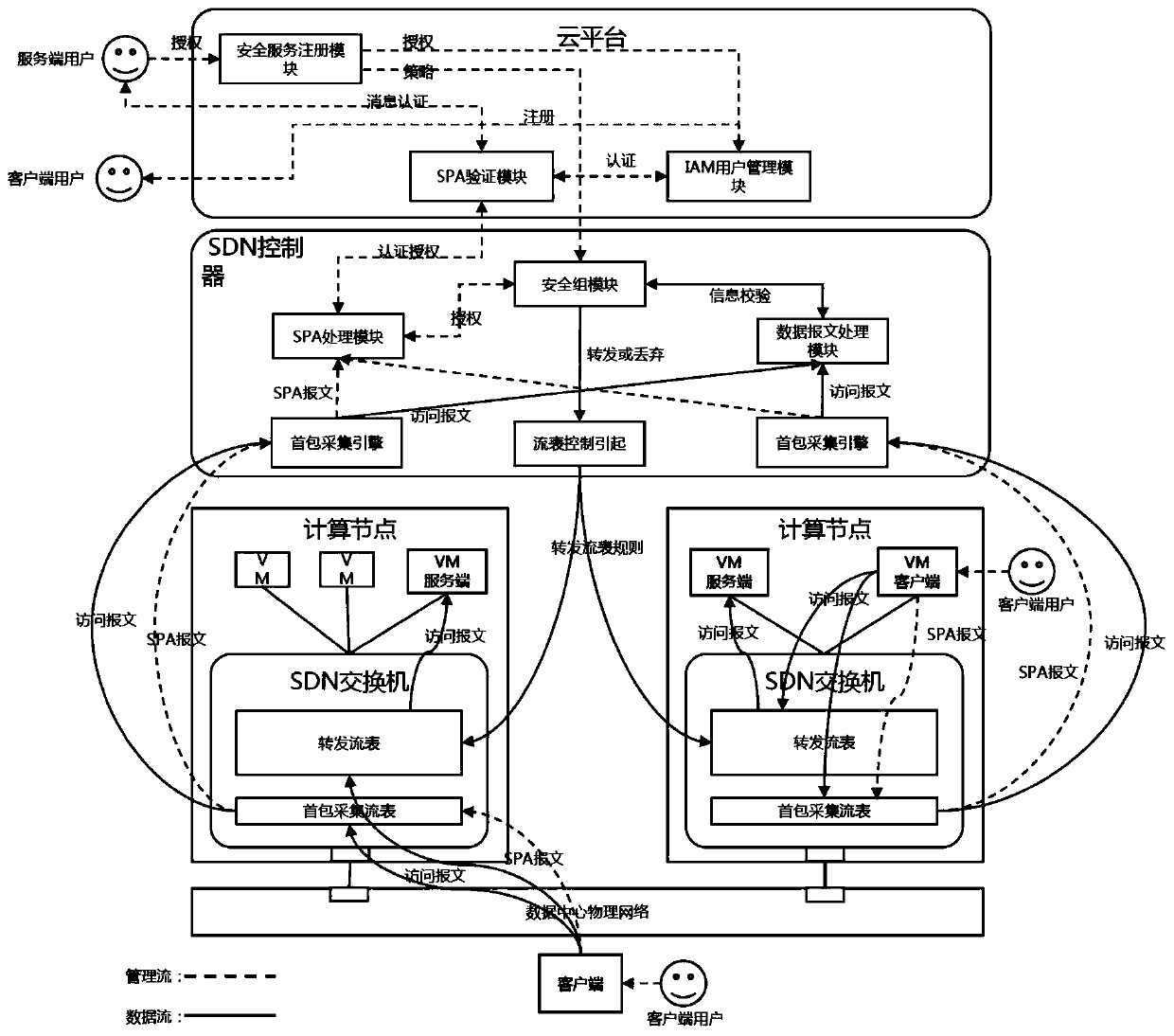
The invention discloses an SDN-based SDP security group implementation method and a security system, and the method achieves SPA single-packet authorization service logic through adoption of a flow table method of an SDN network, and carries out the planning and identity authentication of access authorities of different users through combining with the IAM user management of a cloud platform. According to the invention, the security of the cloud platform security group function is enhanced; accurate control of the security group on external authorization is realized; in combination with the identity authentication technology of the cloud platform and the SDN cloud network, the additional cost of the SDP gateway and the SDP controller is reduced, the SDP technology and the cloud computing security technology are fused, meanwhile, attacks from an internal network can be effectively defended, and comprehensive defense of flow in all directions of the cloud platform can be achieved.
Owner:GUANGZHOU BINGO SOFTWARE
Access control and range query method of ciphertext spatial data in cloud environment
ActiveCN108985094AEnsure safetyNarrow down the search rangeDigital data protectionSpecial data processing applicationsCiphertextData access control
The invention discloses an access control and range query method of ciphertext spatial data in a cloud environment, belonging to the cloud computing security technical field. In the invention, a dataowner firstly generates a ciphertext data index by using the order-preserving encryption and the safe inner product operation, and all the indexes are indexed by R-tree is organized and sent to the cloud server; the user generates ciphertext search instructions according to the geometric range of the query and submits them to the cloud server; the cloud server returns the corresponding ciphertextmatching result according to the user's request and the user's current access authority; finally, after receiving the ciphertext result, the user decrypts the ciphertext by using the key sent by the data owner in advance, and realizes the range query and data access control under the ciphertext environment. The method guarantees the high efficiency and security in the search process, and the specific user can only access the authorized ciphertext spatial data.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Scheduling method, management nodes and cloud computing cluster
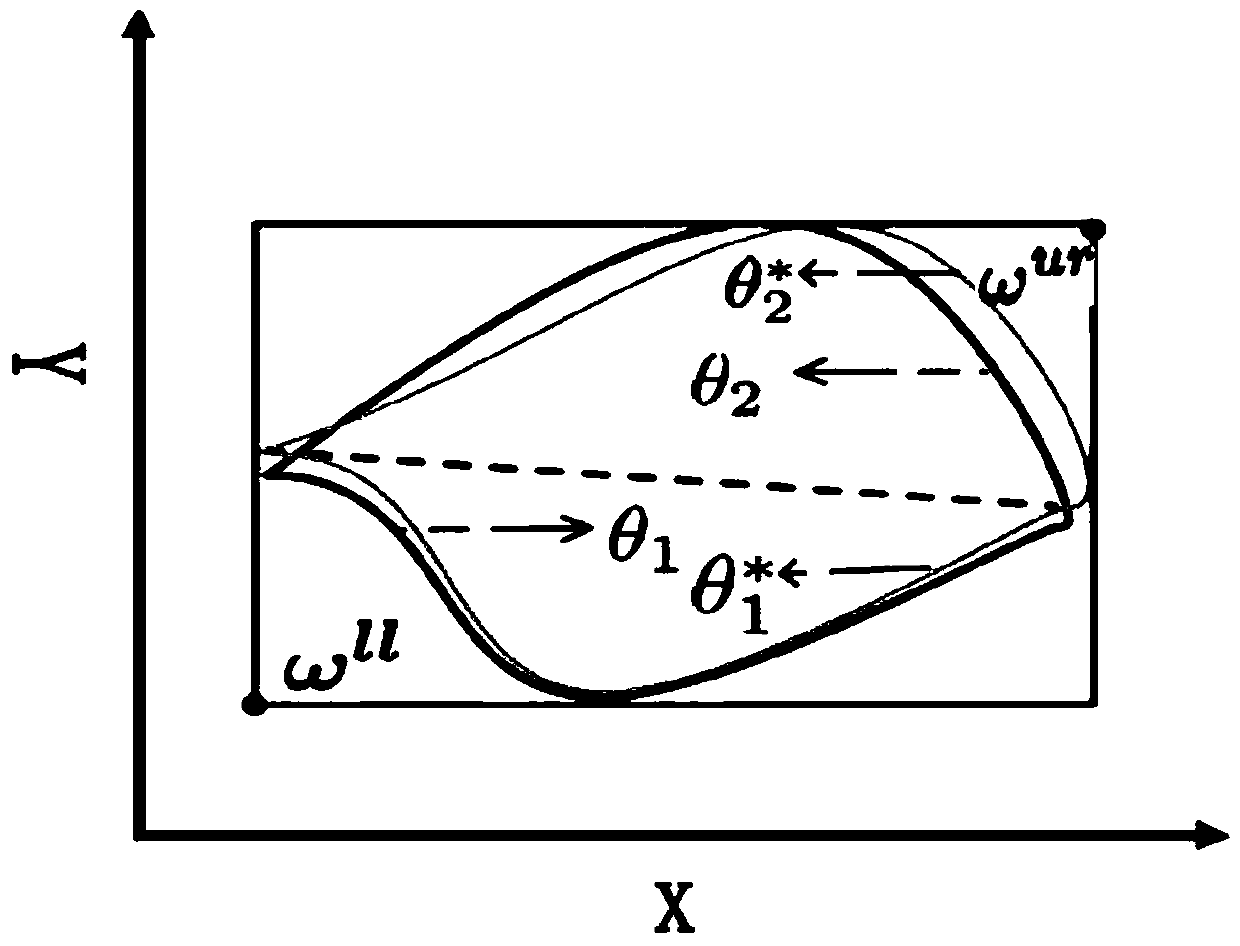
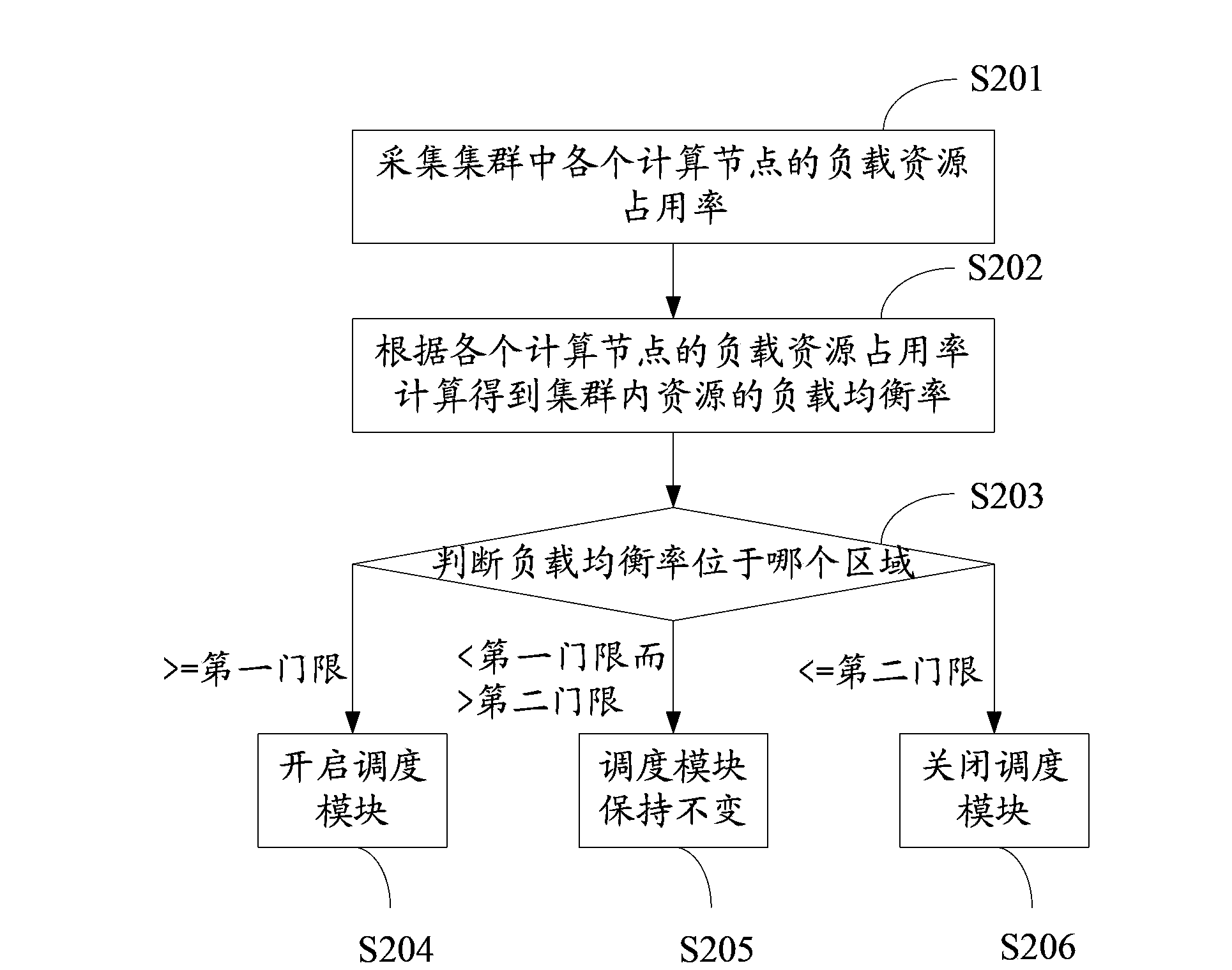
InactiveCN103812895AAvoid overloadImprove performanceTransmissionOccupancy rateCloud computing security
The invention discloses a scheduling method, management nodes and a cloud computing cluster. The scheduling method comprises the steps of collecting the load resource occupation rate of every computing node in the cluster; performing calculation according to the load resource occupation rate of every computing node to obtain the load balancing rate of resources in the cluster; if the load balancing rate is larger than or equal to a first threshold, starting a scheduling module so as to dispatch the load to the computing nodes light in load from the computing nodes heavy in load; if the load balancing rate is smaller than or equal to a second threshold, shutting down the scheduling module so as to forbid scheduling; and if the load balancing rate is smaller than the first threshold and larger than the second threshold, keeping an original state of the scheduling module unchanged. By arranging the two thresholds, an area between the two thresholds is a buffer area, the state of the scheduling module is kept as the original state when in the buffer area, the problem that the shock effect is caused due to the fact that the scheduling module is frequently in an open and closed state can be solved, and accordingly plenty of resources of the management nodes are released.
Owner:HUAWEI TECH CO LTD
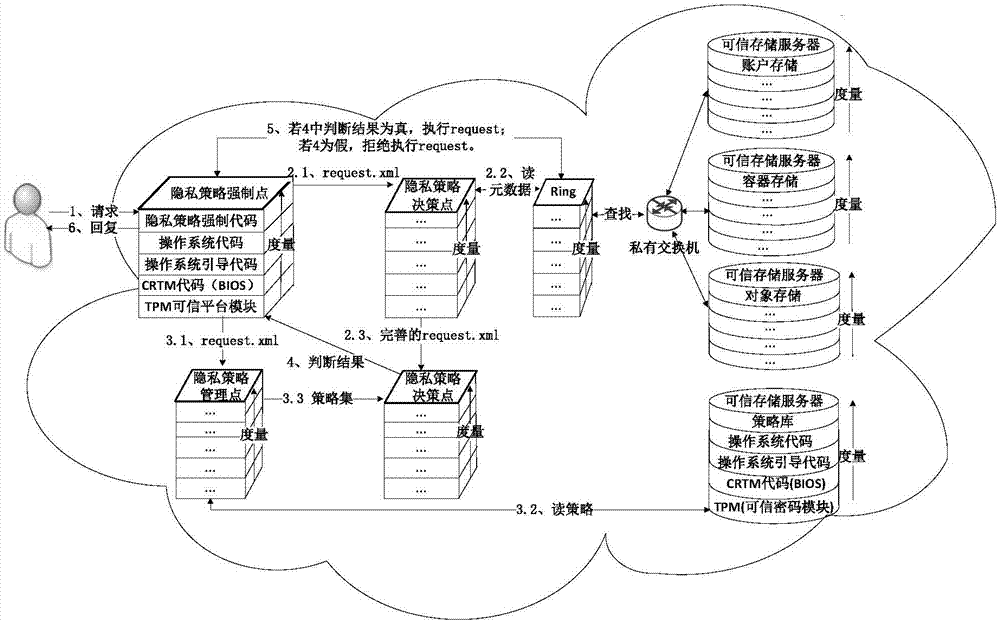
Credible execution method for privacy policy in cloud environment
ActiveCN104506487AIncrease flexibilityAvoid Malicious ModificationsTransmissionData privacy protectionCloud data
Owner:BEIJING UNIV OF TECH
Cloud computing safty architecture
The invention relates to a mobile Internet data transmission and storage method. A client transmits data which needs to be uploaded to a storage cloud system. The storage cloud system carries out identification and encryption to each information. When needing the information, the other client sends a request to the storage cloud system and sends a verification code. After receiving the relevant information and performing the verification, the storage cloud system sends the relevant information to a user. The cloud computing safety architecture has the following advantages: for a video file, a recipient can perform playback without storing the whole file; the storage cloud system is used to receive the file, receive a demand of the playback and then receive the file; many times, the recipient does not play the whole video; for an image and a photo, if the recipient does not have an enough space, other parts of the file can be eliminated; after the file is stored in cloud, if the same file is sent to other friends, uploading bandwidth is not consumed any more; a file name needs to be transmit so that a server can push the file to the recipient.
Owner:江苏真云计算科技有限公司
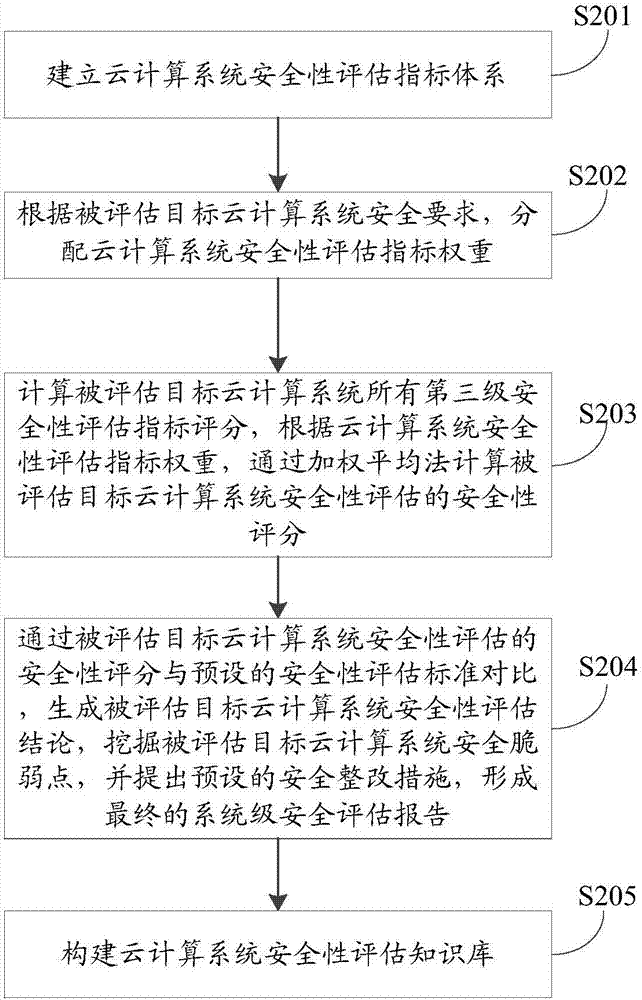
Cloud computing system security assessment method and device
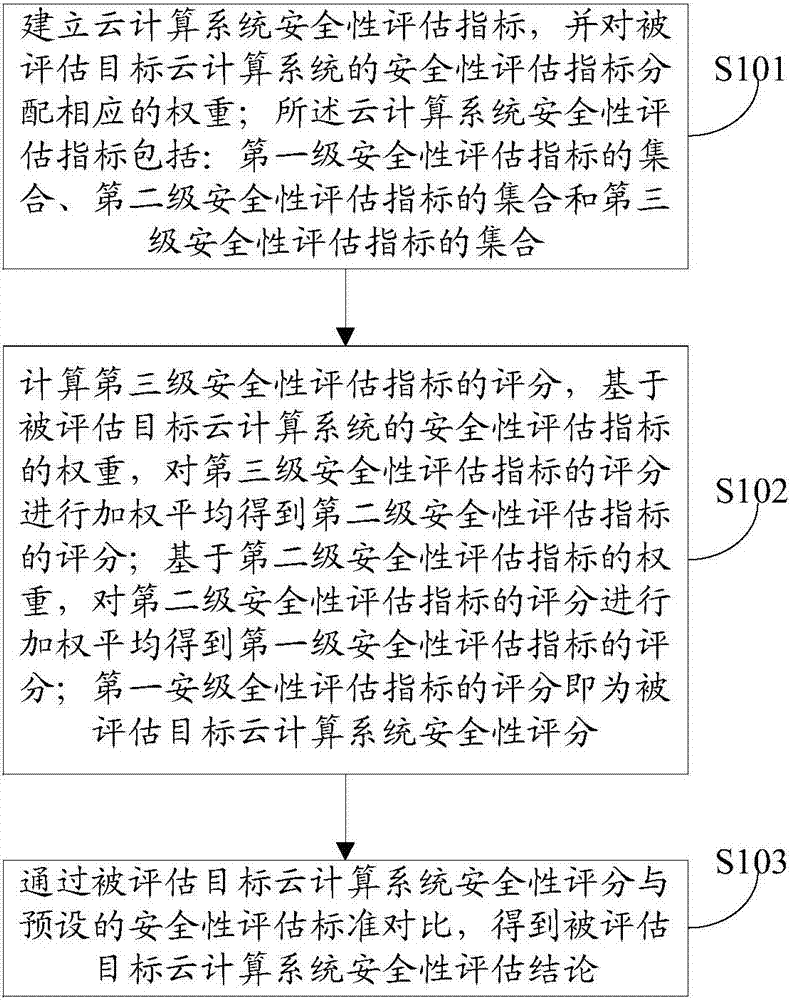
InactiveCN107292174AAdvance the construction processPerfect and scientific cloud computing security evaluation indicatorsPlatform integrity maintainanceUser needsComputing systems
The invention provides a cloud computing system security assessment method and device. According to the method, cloud computing system security assessment indicators are established, and corresponding weights are allocated to the security assessment indicators of an assessed target cloud computing system; a security score of the assessed target cloud computing system is calculated; and a security assessment conclusion of the assessed target cloud computing system is obtained through comparison of the security score of the assessed target cloud computing system and a preset security assessment standard. Through the cloud computing system security assessment method and device, the complete and scientific cloud computing security assessment indicators are established, and the demands of different service providers, developers and users in different cloud computing platforms are met. A clear and feasible cloud computing platform system-level security assessment technical implementation scheme is proposed, and the construction progress of a high-security cloud computing platform is powerfully promoted.
Owner:CHINA ACADEMY OF ELECTRONICS & INFORMATION TECH OF CETC
Cloud data privacy protection public auditing method based on symmetric keys
ActiveCN103916393ASave computationSave on storage overheadKey distribution for secure communicationUser identity/authority verificationThird partyData integrity
The invention discloses a cloud data privacy protection public auditing method based on symmetric keys and belongs to the technical field of cloud computing safety. The method comprises the steps of (1) key generation, (2) signature computing and (3) proving. In the key generation step, a data owner generates four private keys randomly, two private key pairs are formed, one private key pair is shared by the data owner and a cloud server, and the other private key pair is shared by the data owner and a third-party auditor; in the signature computing step, the data owner inputs the private keys and data blocks, signature computing is conducted on each data block and indexes of the data block, and signatures are sent to the cloud server; in the proving step, after the cloud server receives the indexes of the data blocks and challenges generated by the third-party auditor randomly from the third-party auditor, data integrity evidence is obtained through computing and sent to the third-party auditor, and the third-party auditor conducts verification. By means of the cloud data privacy protection public auditing method based on the symmetric keys, computing and storing expenses are reduced, and public auditing and privacy protection can be provided.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
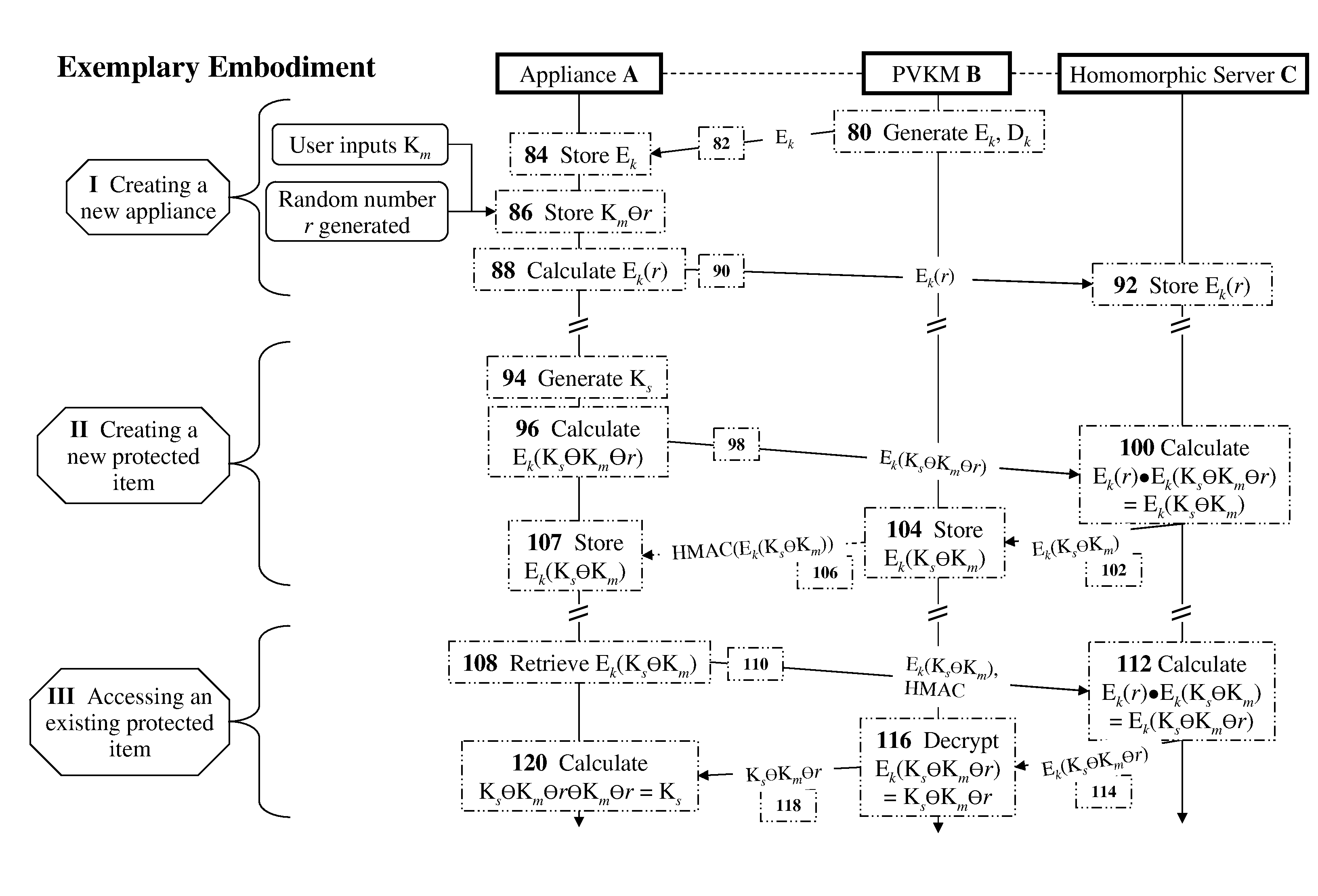
Methods and devices for securing keys for a nonsecured, distributed environment with applications to virtualization and cloud-computing security and management
ActiveUS9380036B2Without impairing functionalityControl process safetyKey distribution for secure communicationDigital data protectionVirtualizationCloud computing security
The present invention discloses methods and devices for securing keys for a non-secure computing-environment. Methods include the steps of: providing a security-key framework which is adapted, upon receiving an encryption request for protecting a secret item, for repetitively encrypting the secret item with each of a set of N location-specific secure-keys, wherein each location-specific secure-key corresponds to a respective encryption location, to create an encrypted item; wherein the locations are regions of memory located in computing resources operationally connected to the computing-environment; and concealing through encryption at least one location-specific secure-key such that the concealing is configured: to prevent at least one location-specific secure-key from ever being known in an unconcealed form on any computing resource in any computing-environment during the encrypting; and to allow mathematical operations, performed as part of the encrypting and concealing, to be performed while at least one location-specific secure-key is in its concealed form.
Owner:PORTICOR
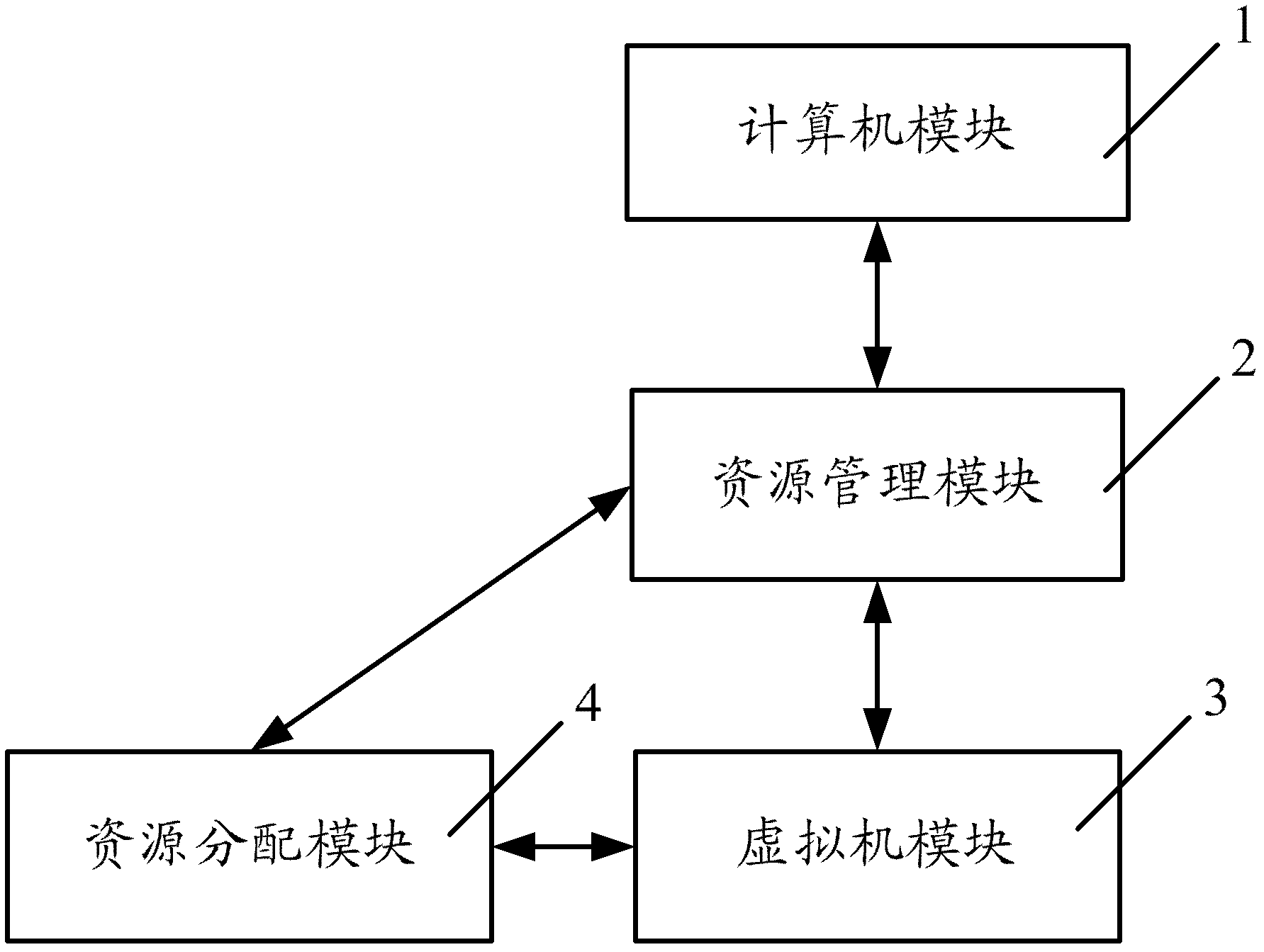
Cloud computing equipment
InactiveCN102567119AReduce complexityImprove compatibilityResource allocationTransmissionApplication lifecycle managementVirtualization
The invention discloses cloud computing equipment. The equipment comprises a plurality of computer modules, a resource management module, a virtual machine module and a resource allocation module, wherein the resource management module is used for managing resources provided by the plurality of computer modules in a virtualization way, and the virtual machine module is used for loading an application required to operate into a moldboard according to requests of a user and allocating and operating the loaded application; and the resource allocation module is used for allocating hardware resources of the computer modules, corresponding to virtual resources, to an application which is in operating according to the requests. The cloud computing equipment disclosed by the invention has the advantages of realizing uniformization hardware and software management, improving compatibility of the equipment, reducing complexity of hardware and software allocation, being beneficial to improving operational performance, being capable of being convenient for subsequent management and maintenance, and reducing cost brought by development, and management and maintenance through uniform resource management, application management (comprises allocation and operation) and resource allocation.
Owner:SUGON INFORMATION IND
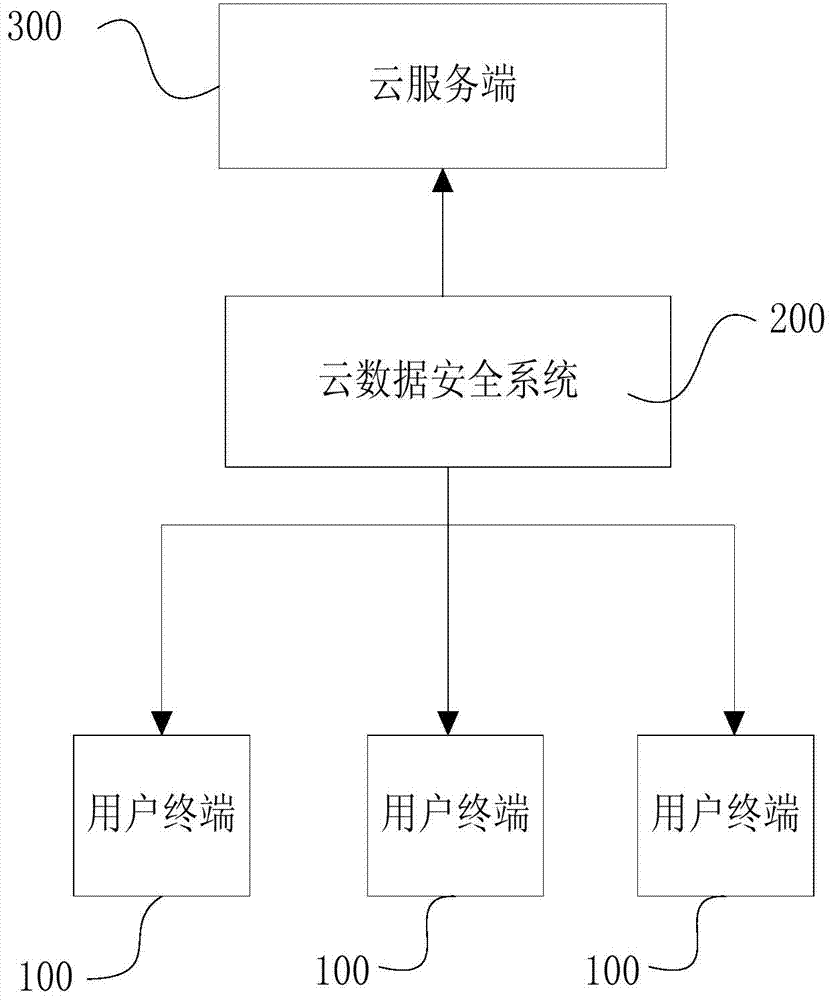
Cloud computing security system and method
The invention provides a cloud computing security system, comprising a plurality of user terminals, a cloud data security system and a cloud server side, wherein each user terminal comprises a business system, a user terminal network interface and a software development kit, wherein the business system is connected with a login system of the cloud server side through an internet and / or mobile internet, a heartbeat packet is transmitted to the login system by the business system, the user terminal network interface is in communication connection with the internet and / or mobile internet, and used for realizing data interaction between the user terminal and the cloud server side, and the software development kit is arranged inside a memory of the user terminal, and used for being implanted into developed application software by a developer. The cloud data security system comprises a monitoring system for monitoring reading and writing-in operations of a user, a filtering system for filtering file data which does not need to be encrypted, and an encryption and decryption system for data encryption and data decryption.
Owner:GUANGDONG XUANYUAN NETWORK & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com