Cloud computing security system and method
A security system, cloud computing technology, applied in the field of cloud computing to achieve the effect of enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The present invention will be further described in detail below with reference to the accompanying drawings and specific embodiments, taking cloud computing data transmission as an example.
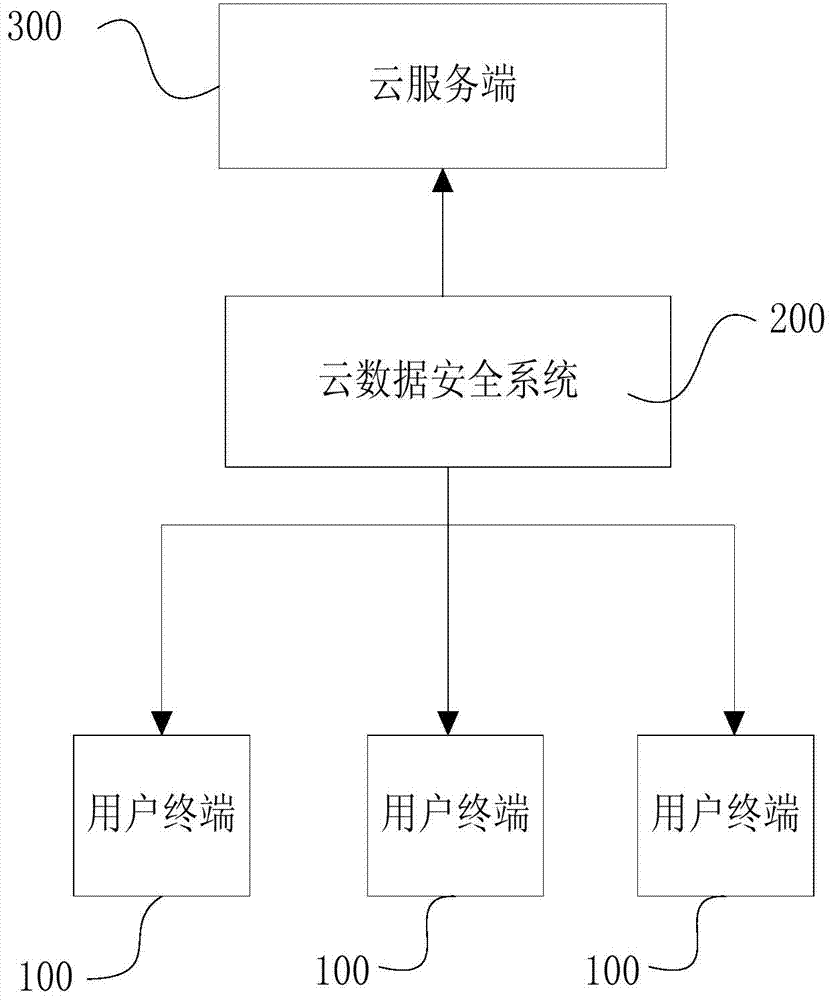
[0020] One aspect of the present invention provides a cloud computing security system, such as figure 1 As shown, it includes a plurality of user terminals 100, a cloud data security system 200, and a cloud server 300. In this embodiment, data interaction between the user terminal 100 and the cloud server 300 is taken as an example for illustration. Such as image 3 As shown, the user terminal 100 includes a service system 102 , a user terminal network interface 101 communicatively connected to the Internet and / or mobile Internet, and a software development kit 103 . Such as figure 2 As shown, the cloud server 300 includes an access system 301, a login system 302, a business connection system 303, a business processing and caching system 304, a database 305, and a cloud server n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com