Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
440 results about "Resource Provider" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An organization or person that typically provides financial or other resources for the conduct of research. EXAMPLE(S): National Cancer Institute, National Institutes of Health (Federal Agencies)Pharmaceutical companies (private industry)
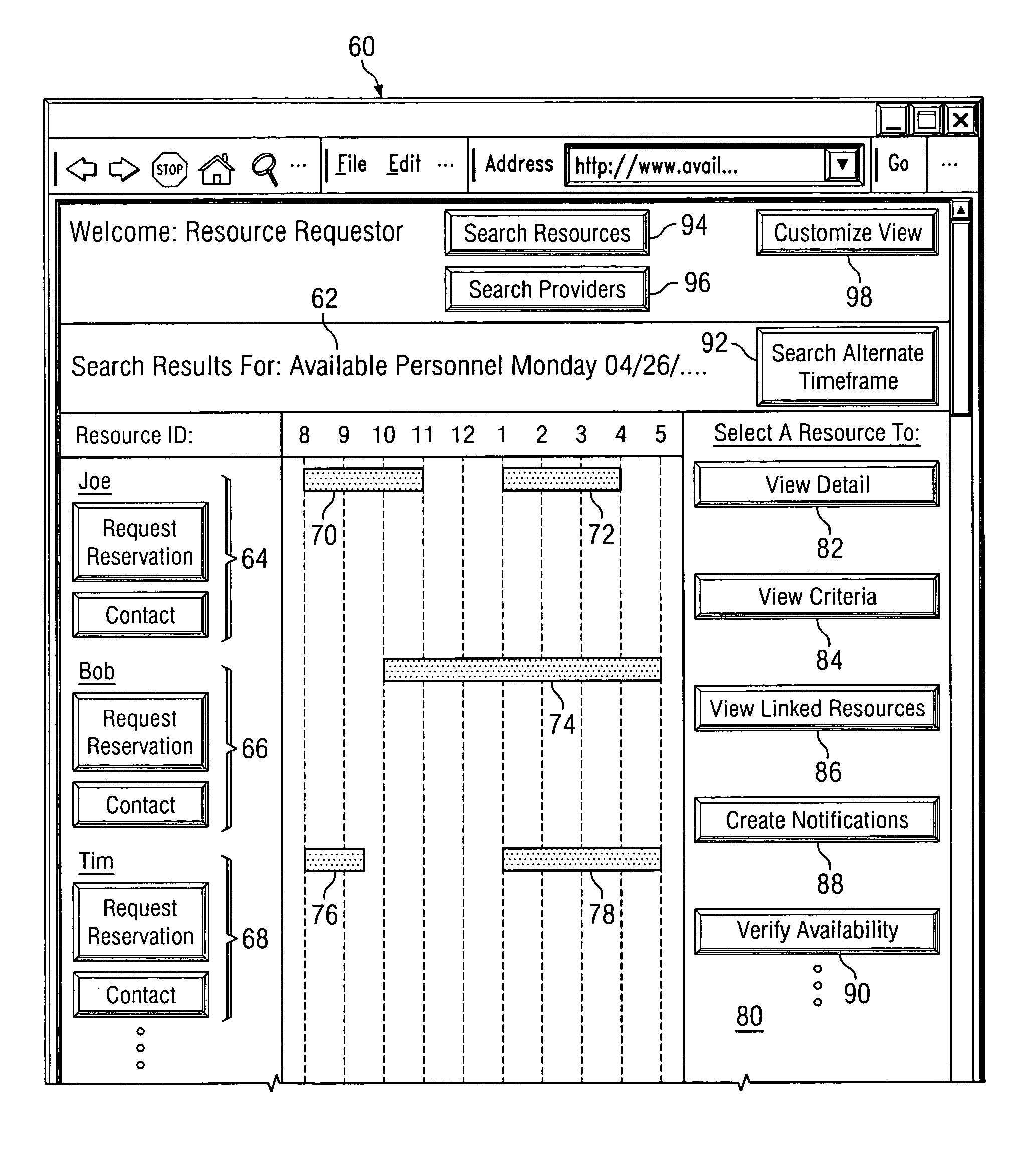
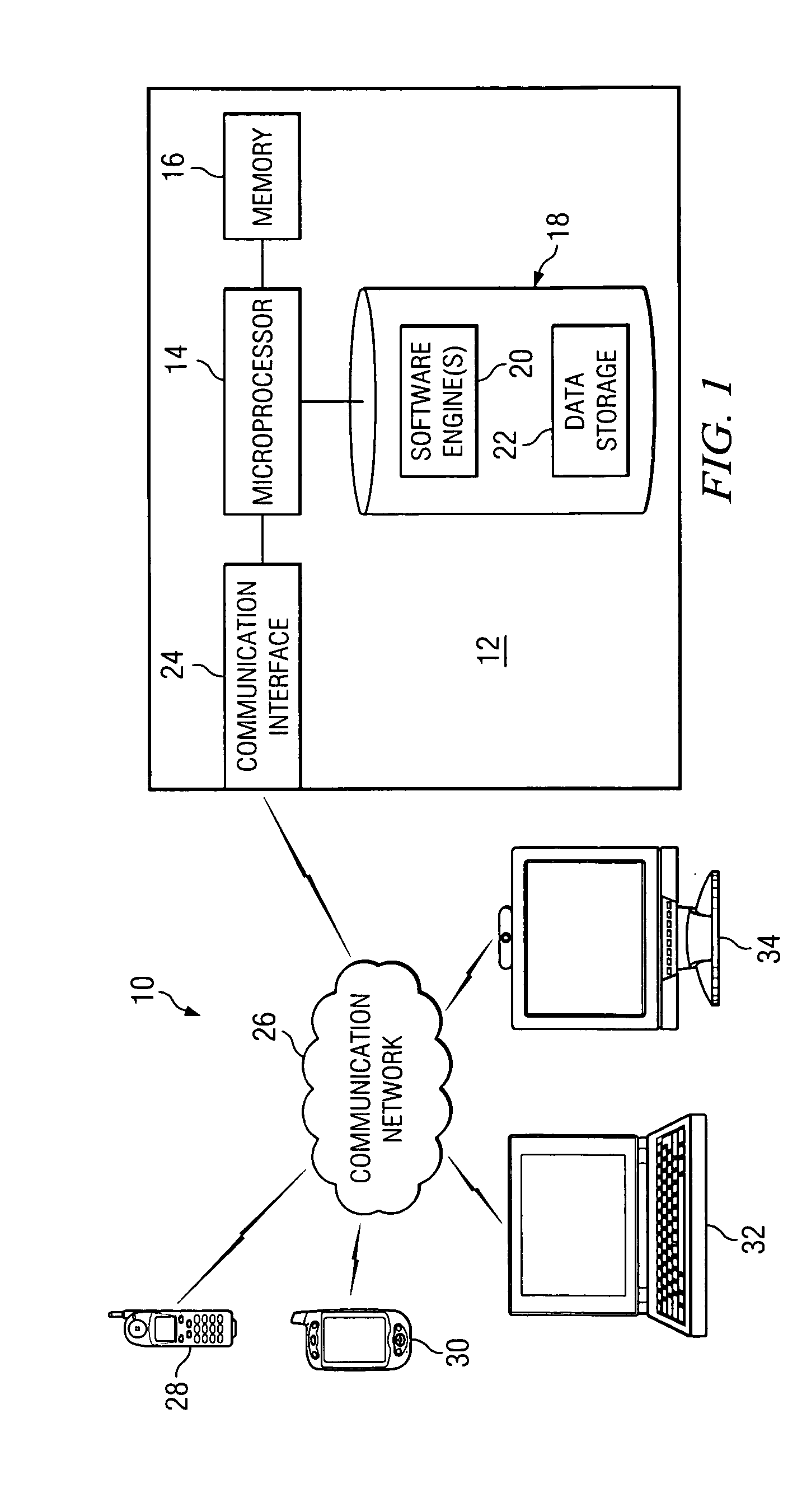
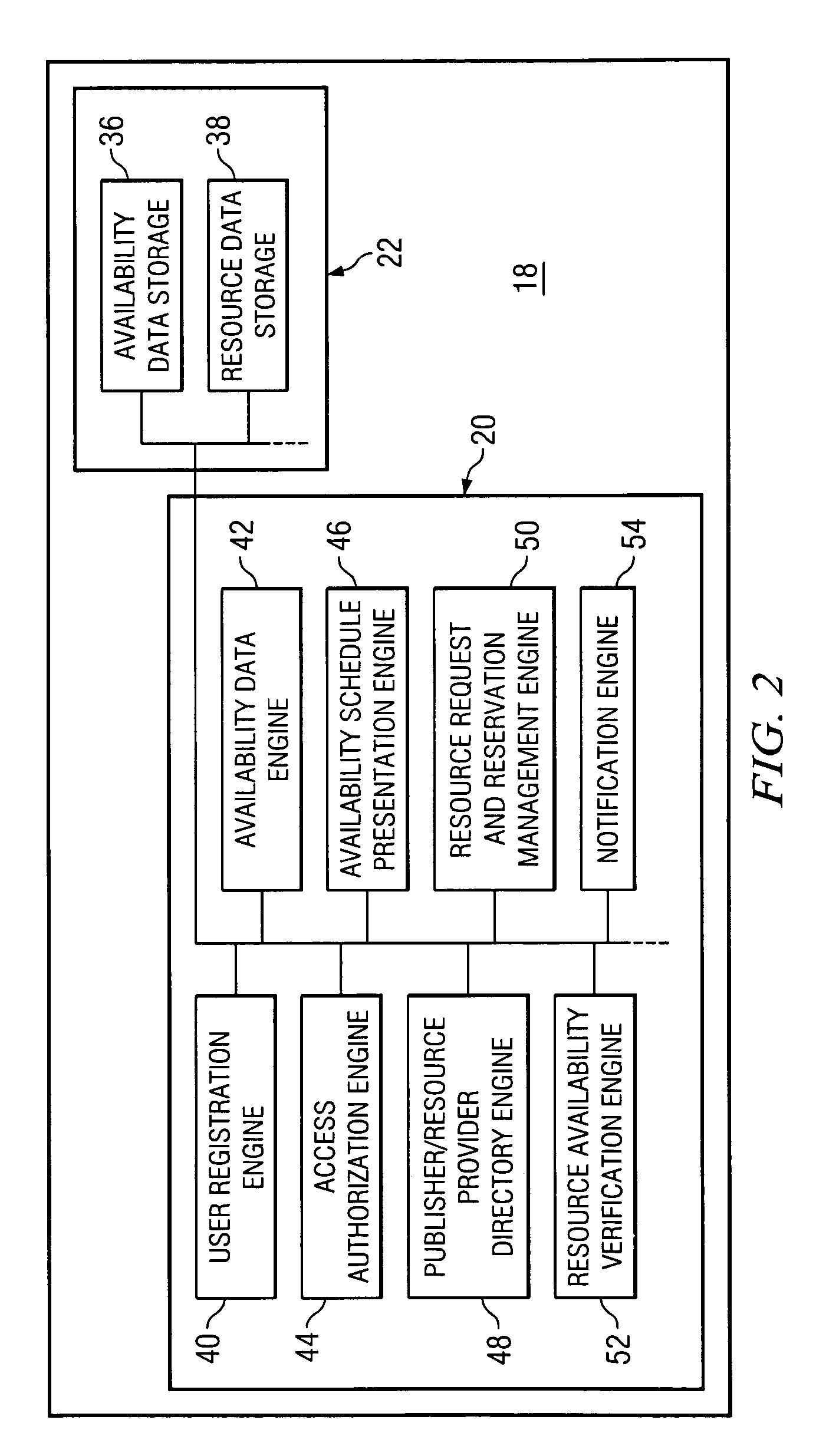
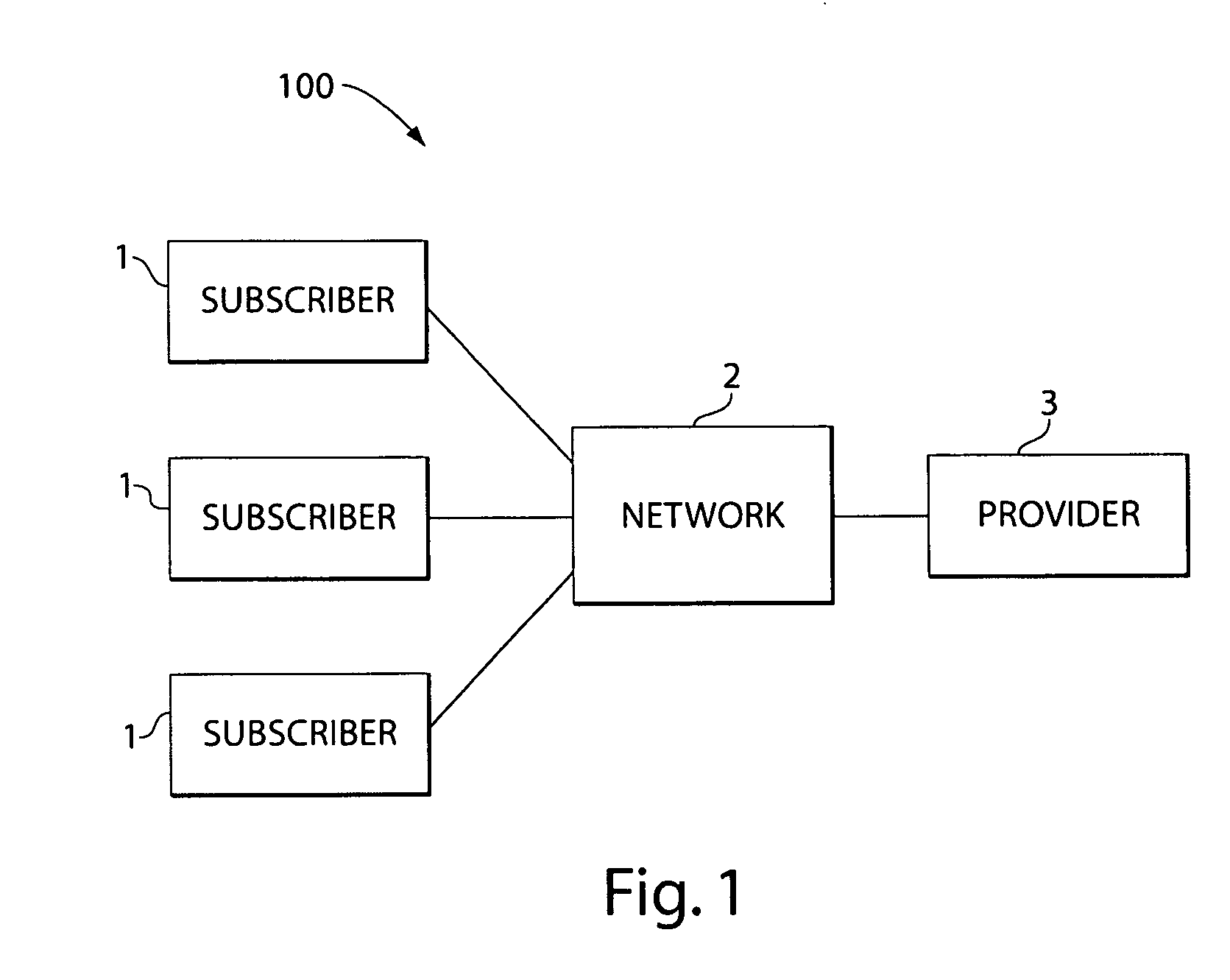
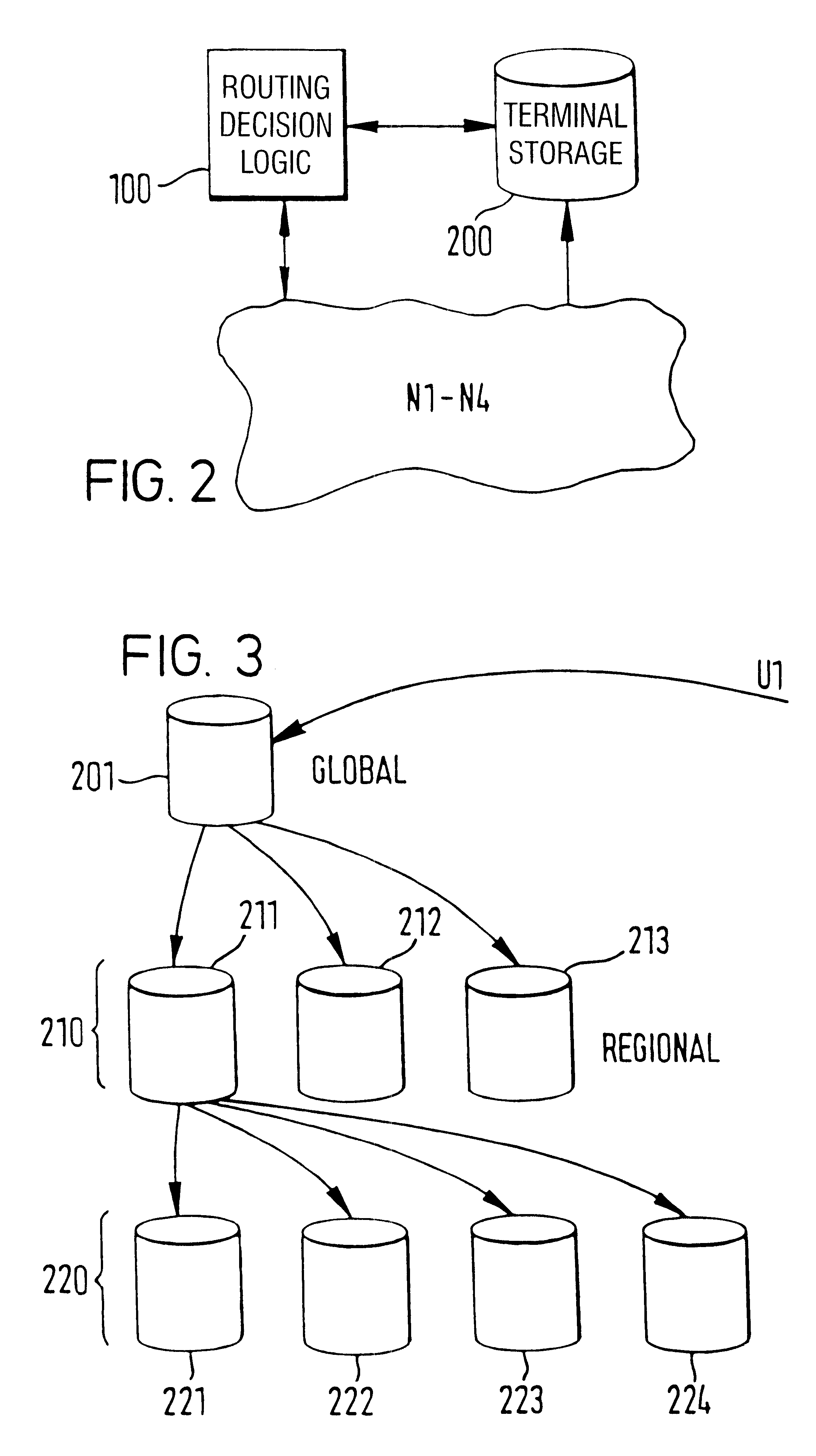
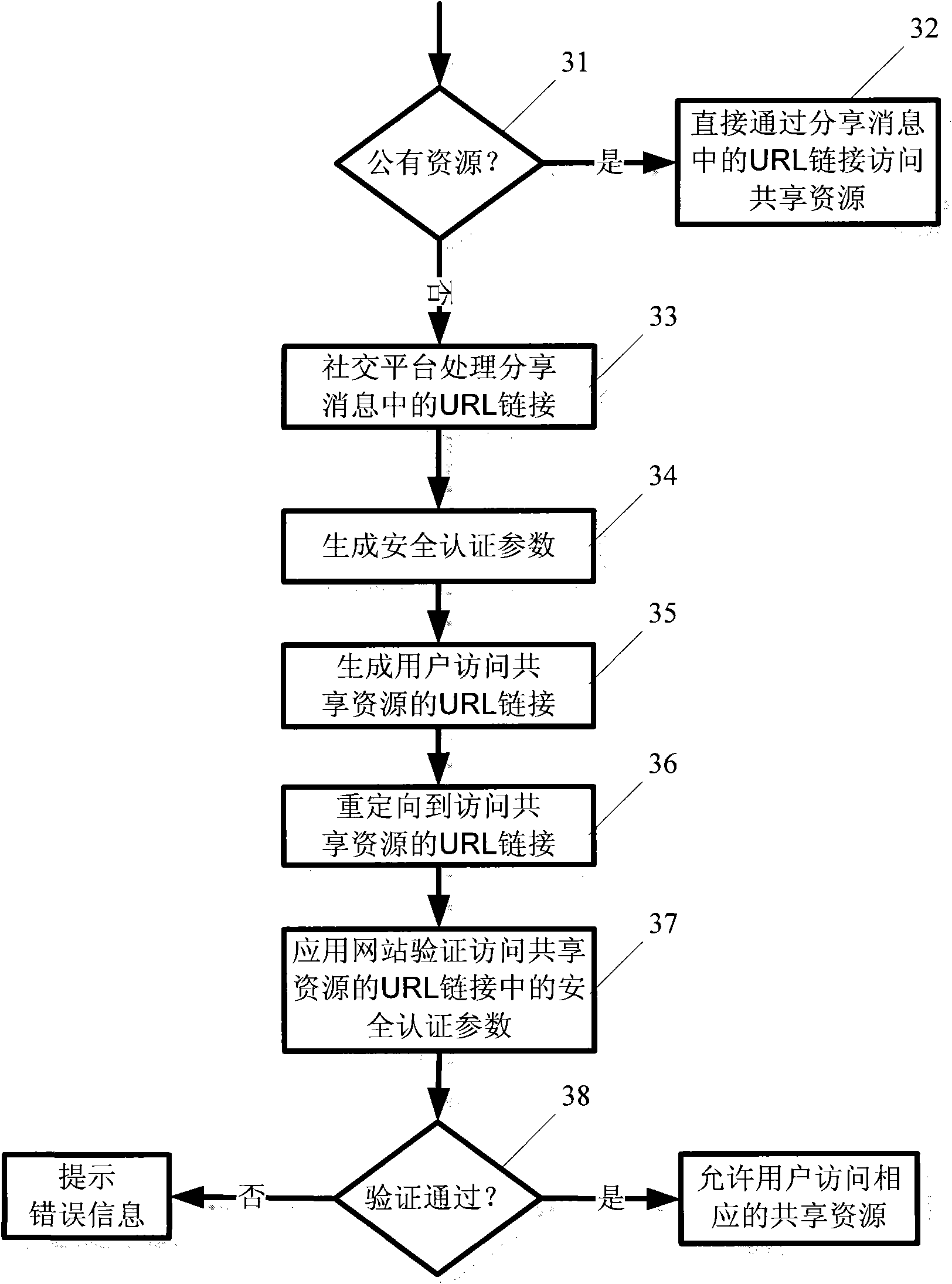
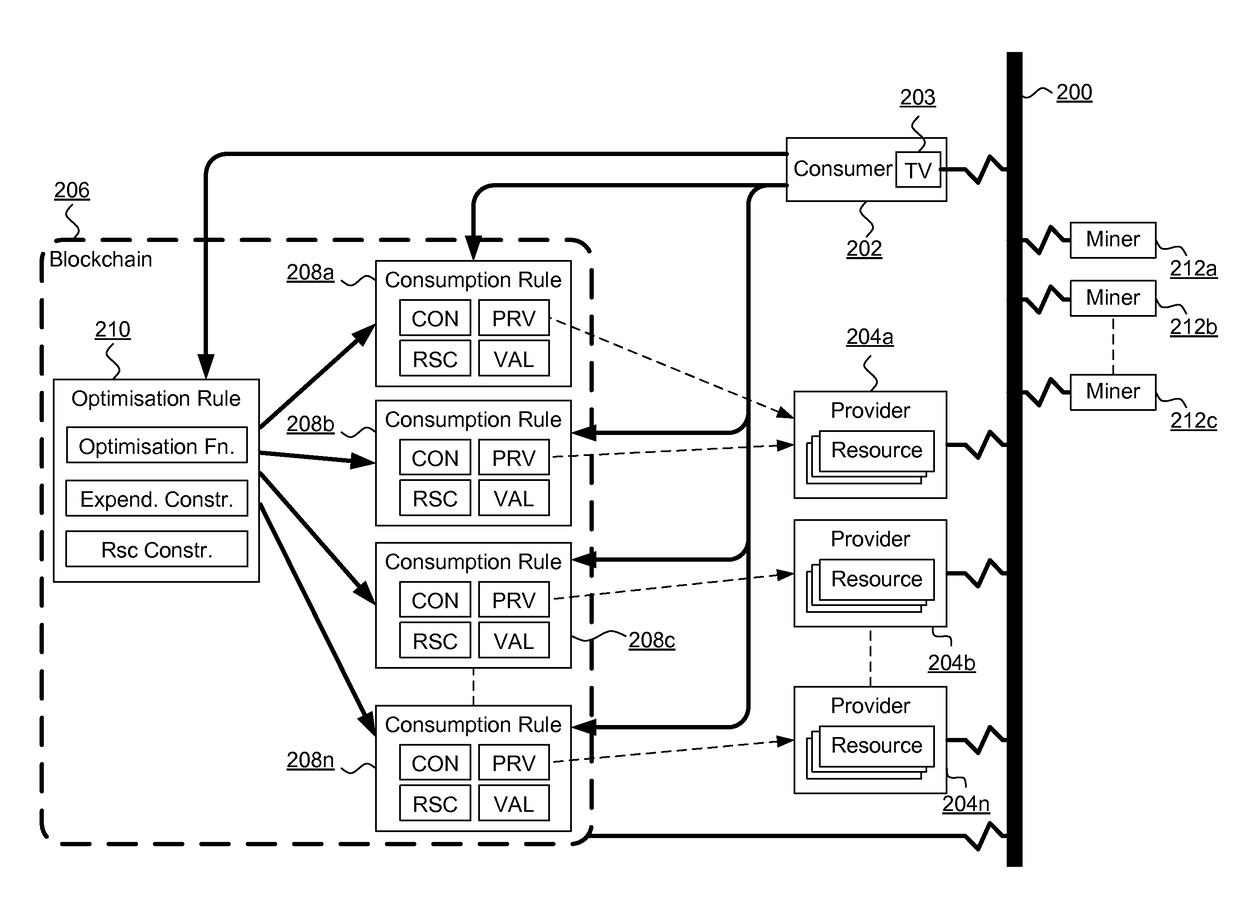
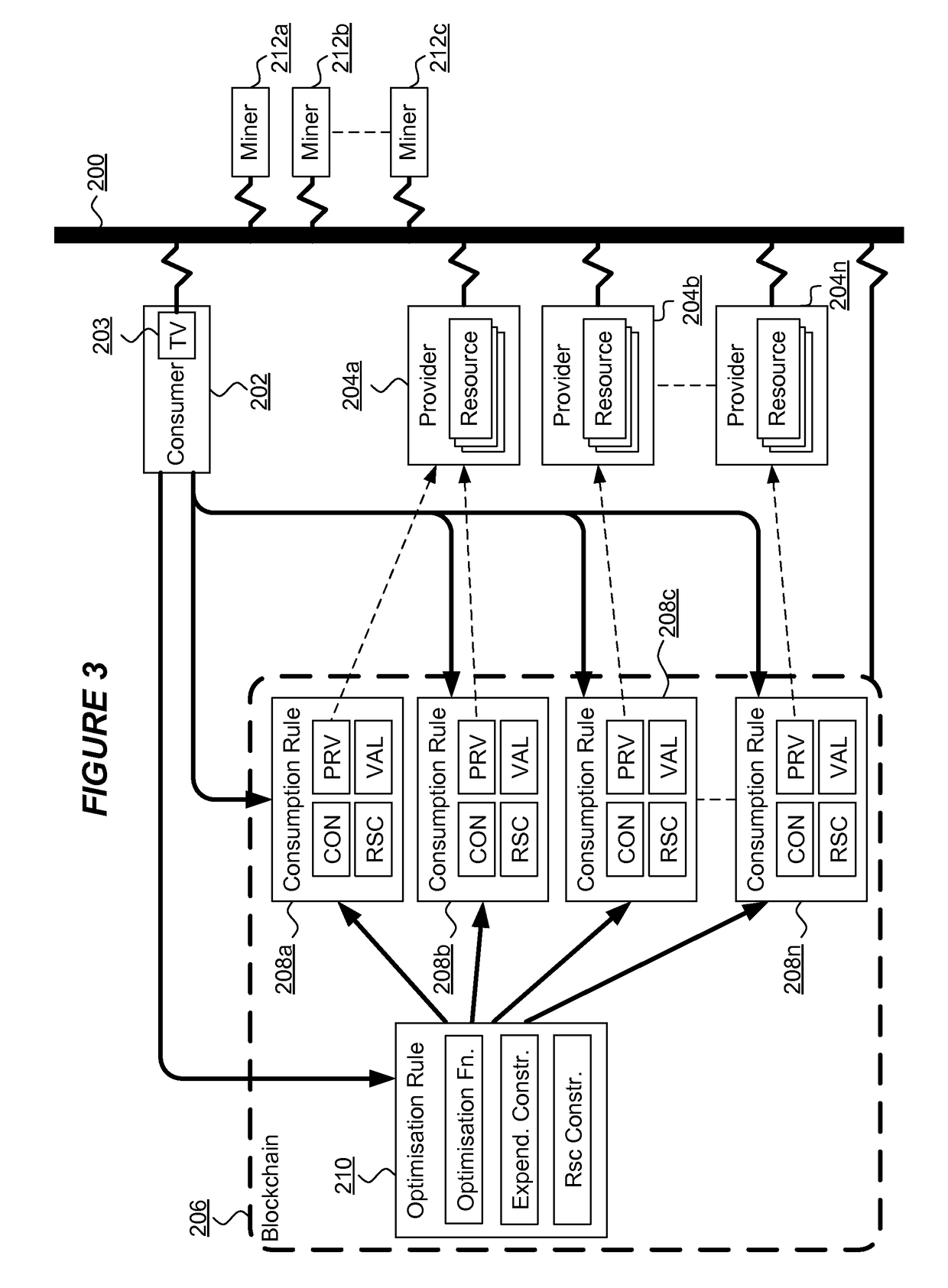
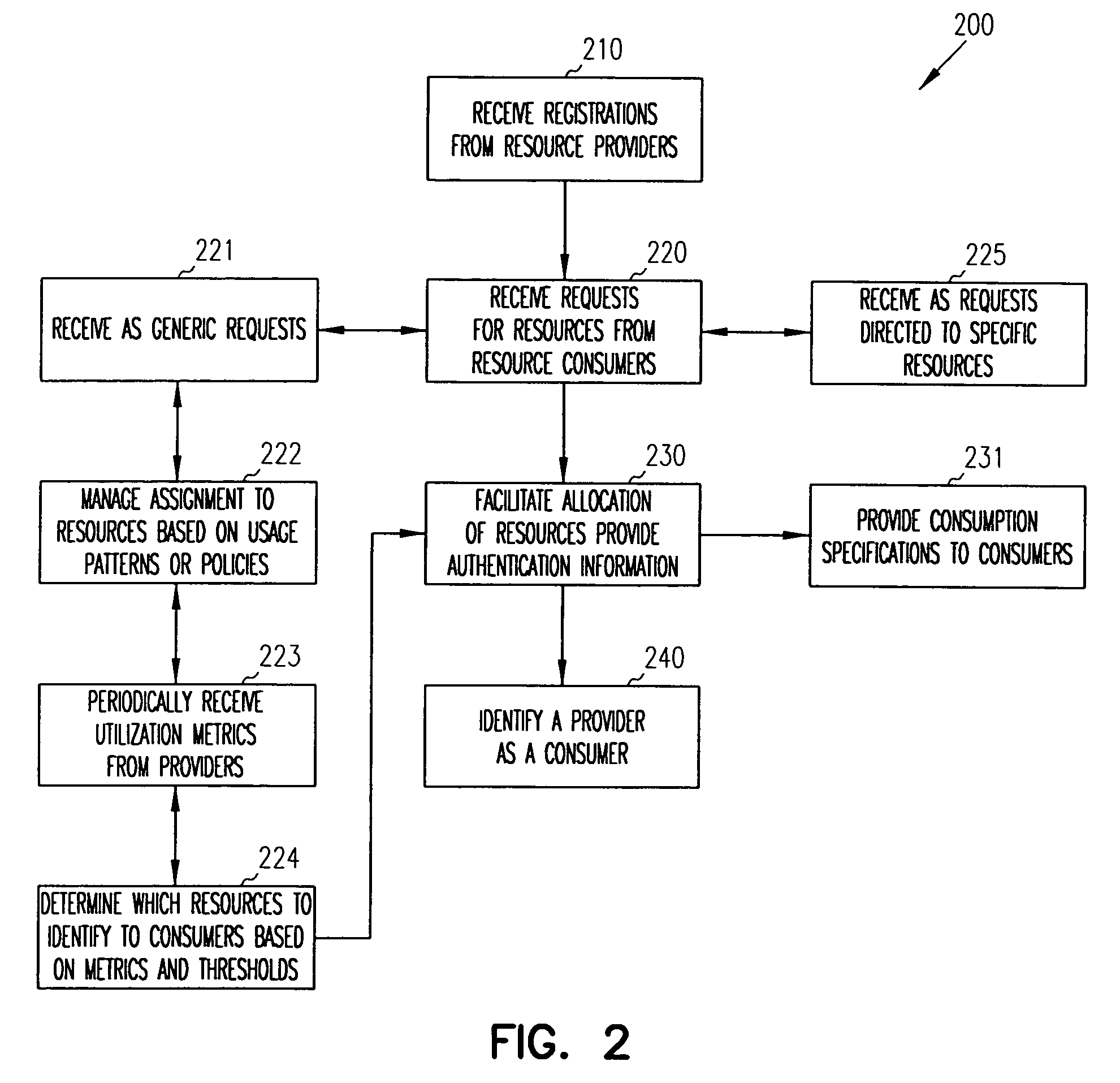
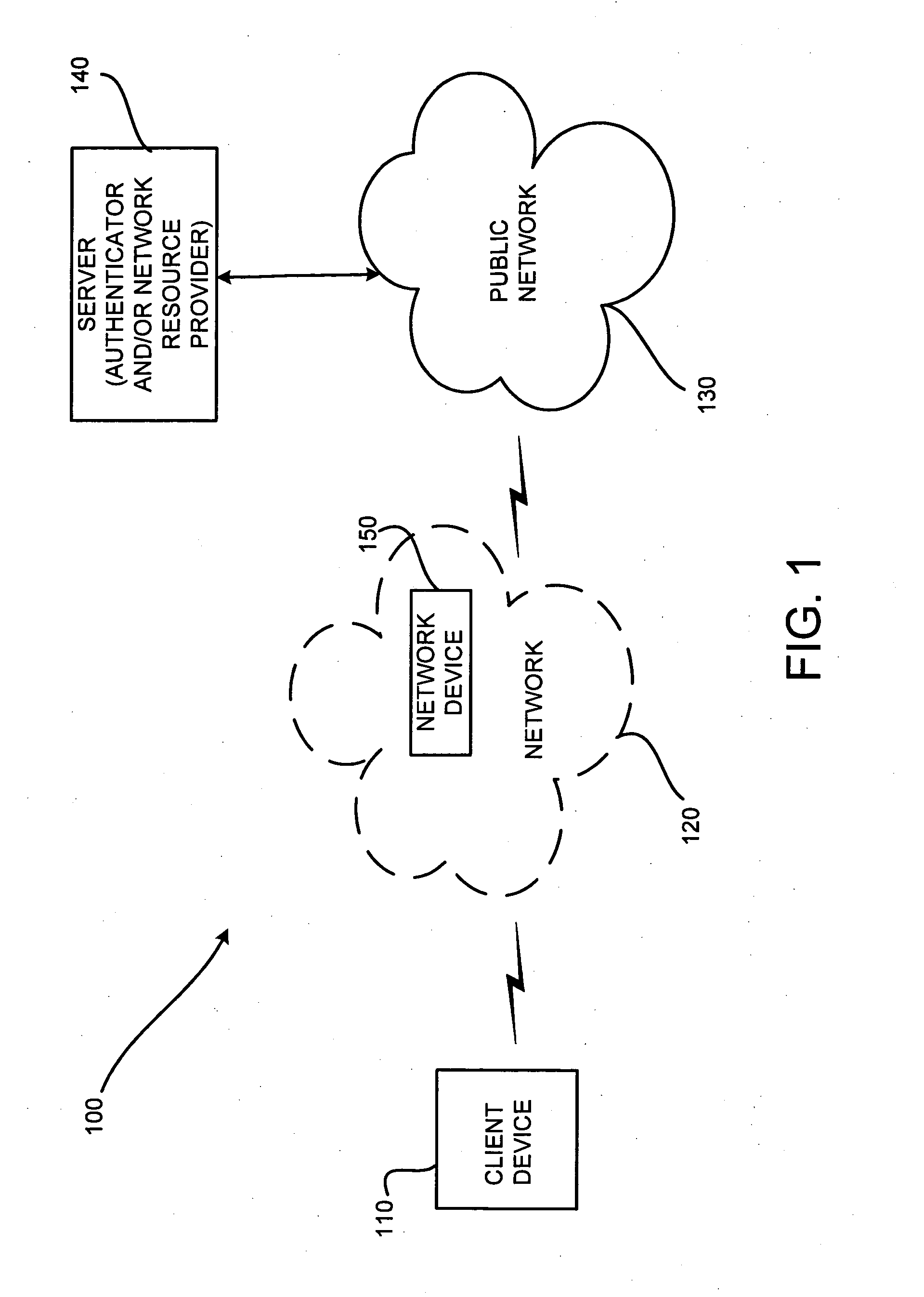
System, method and software for managing and publishing resource availability data
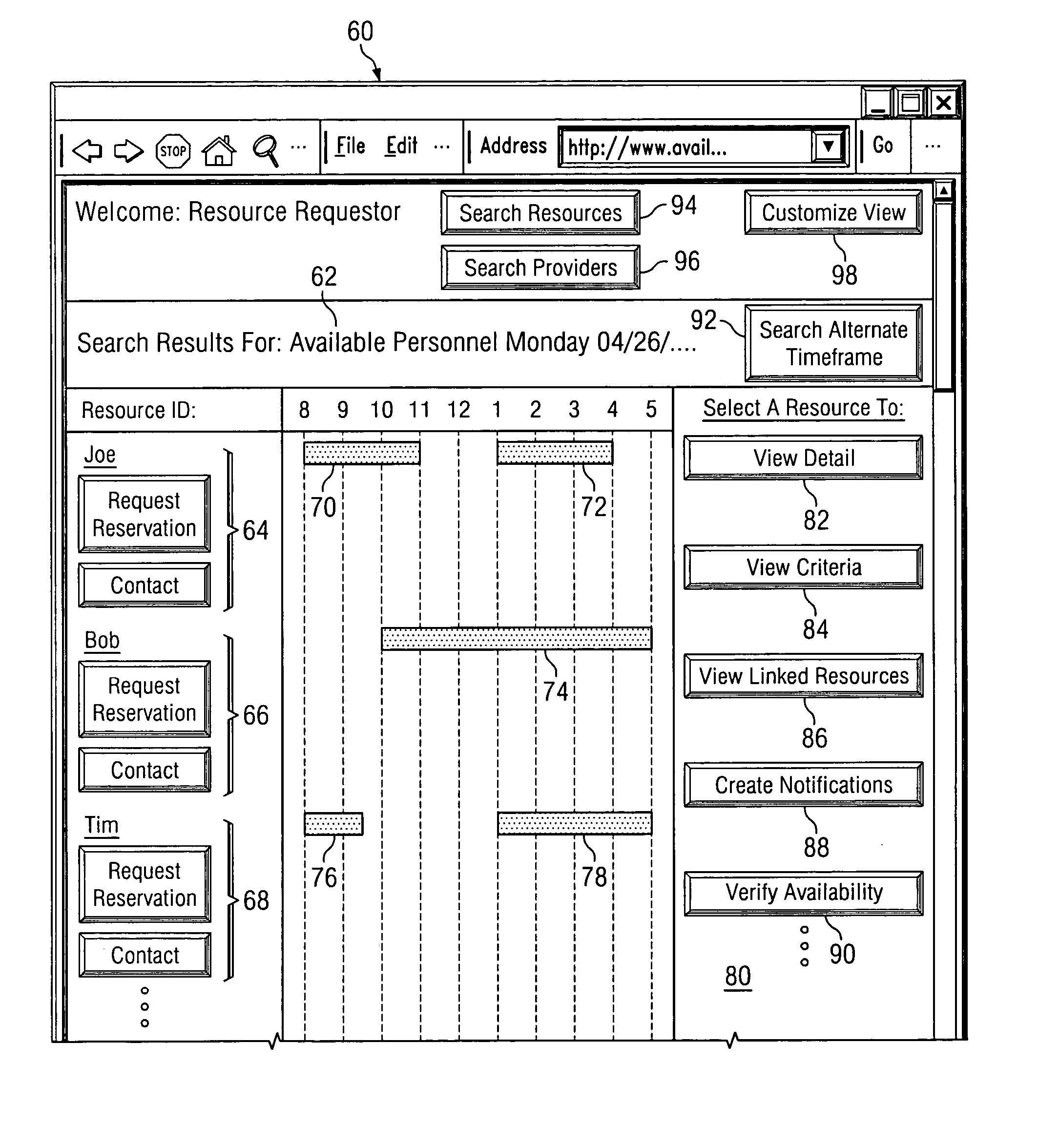
A system, method and software permitting the publication of resource availability information and the management of reservation requests therefor are provided. In an exemplary embodiment, a resource provider provides authorization, availability, descriptive, linking and criteria information for a resource available for reservation presented on a publicly accessible web site. Users permitted to access to the data can browse and search the published resource related data and request appointments with or reservations of the listed resources. Resource providers are permitted to actively or automatically manage reservations and appointments requesting their resources. Available on a publicly accessible web site, resource providers may also control and define access limitations for various groups of viewers.
Owner:CISCO TECH INC
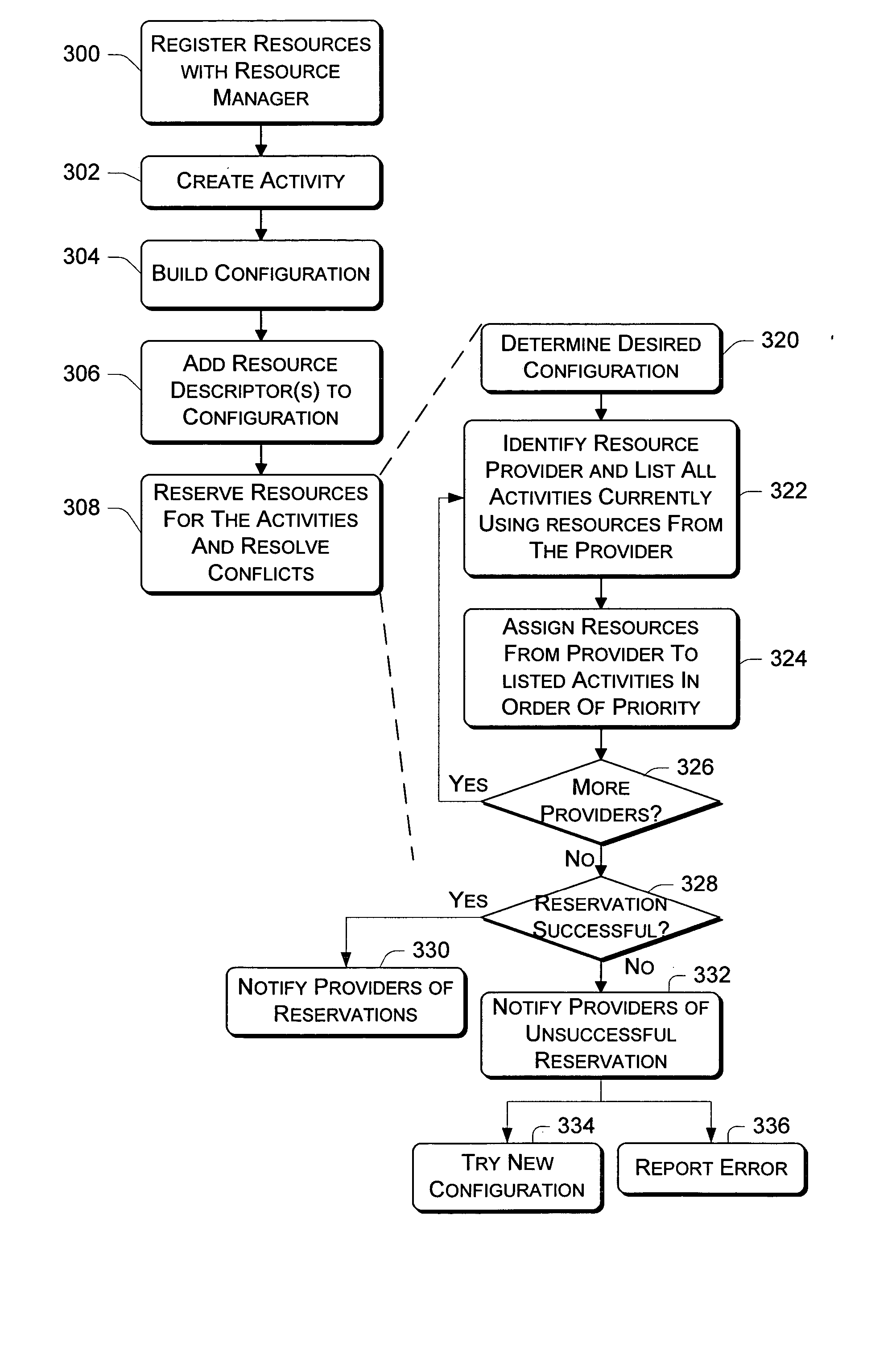
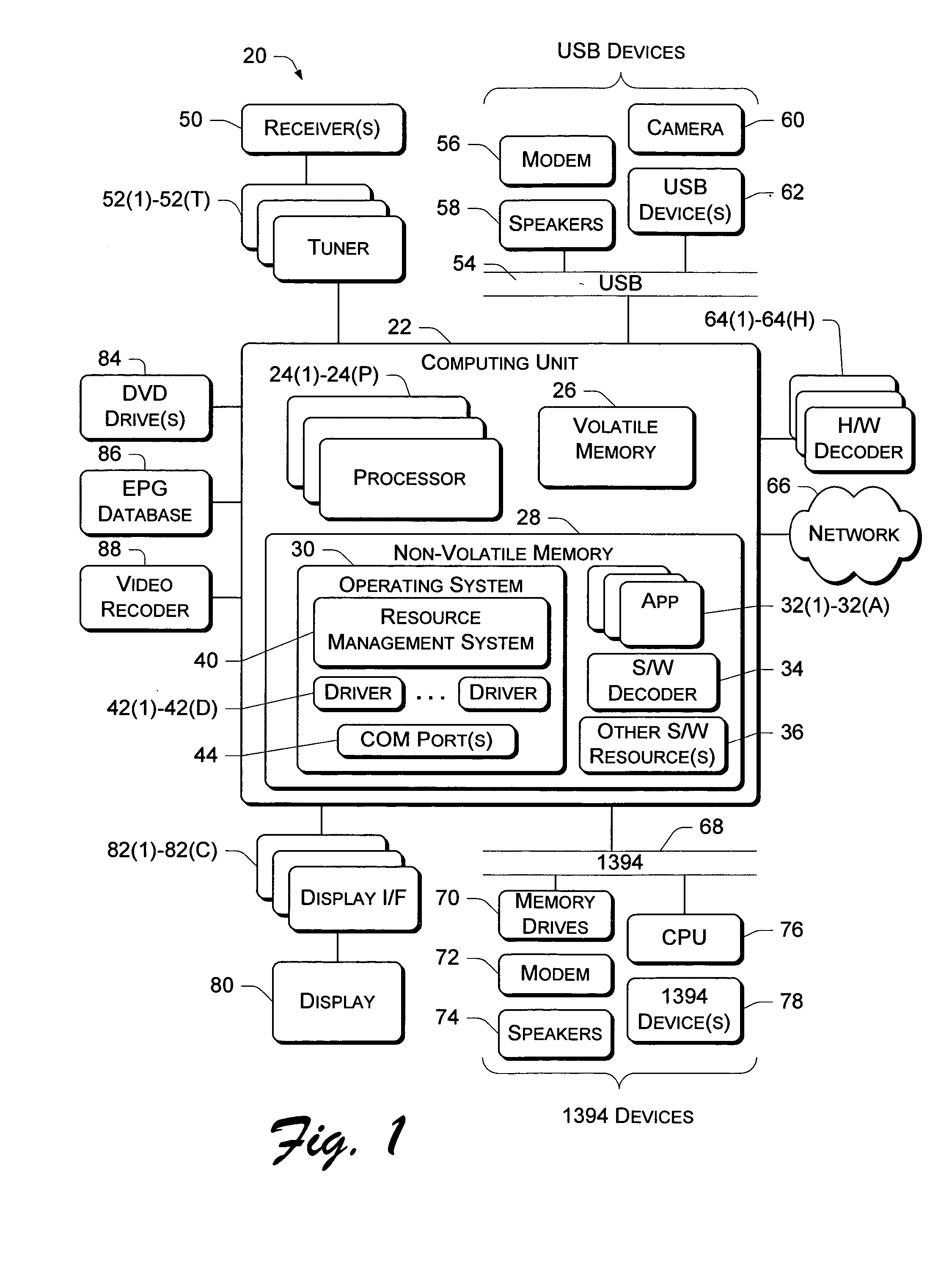
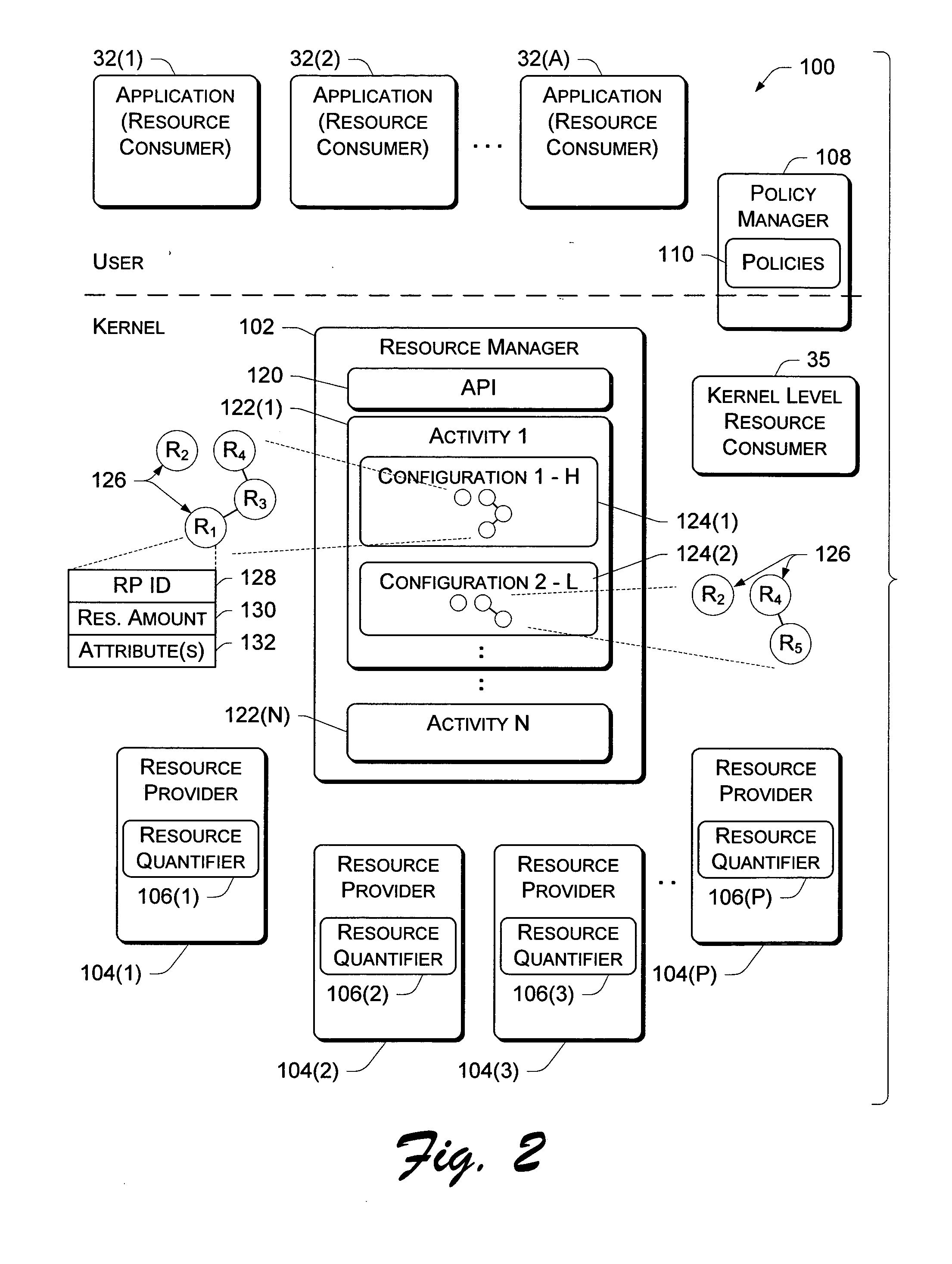
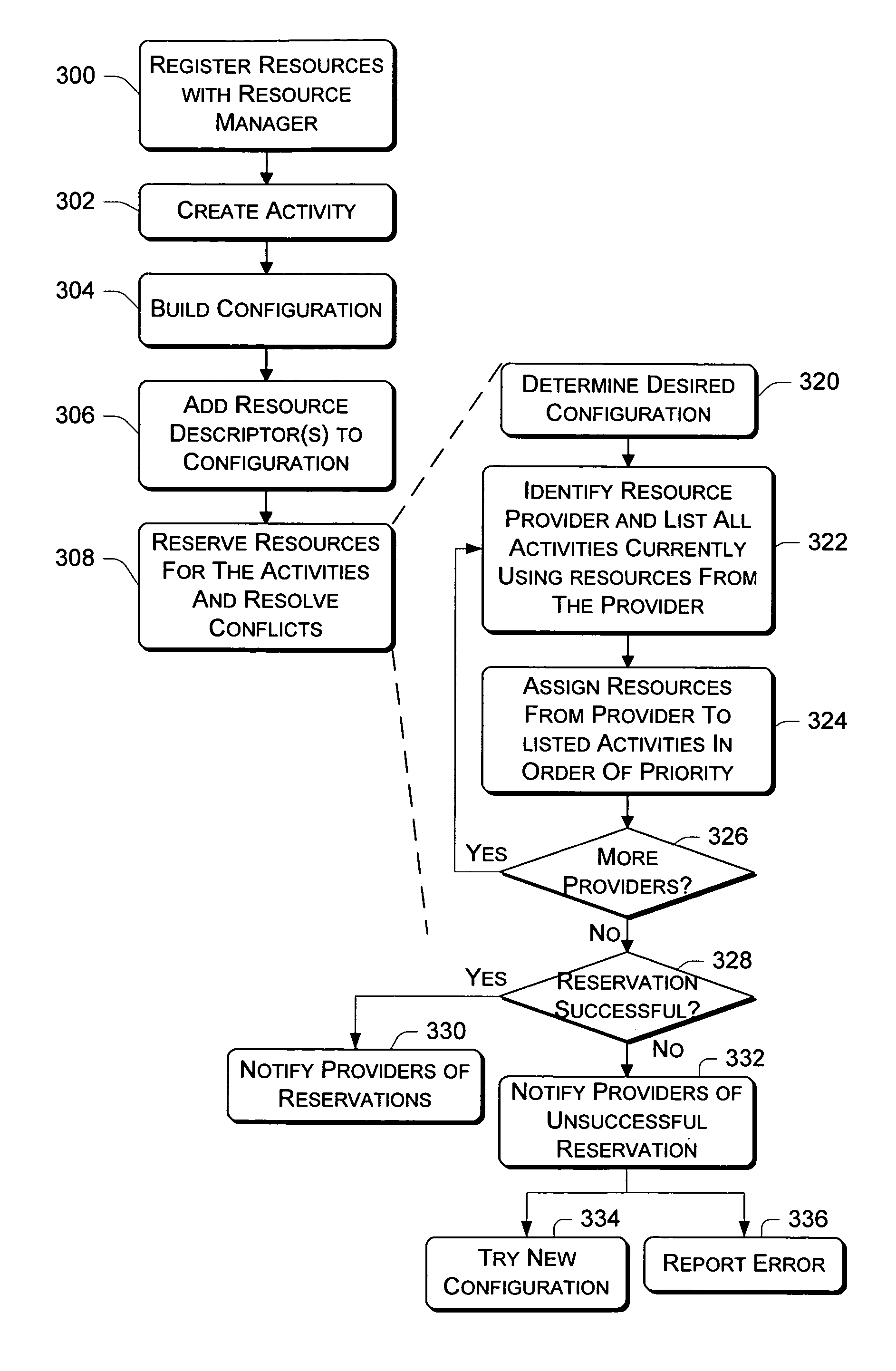
Resource manager architecture
InactiveUS20050044205A1Facilitates reservation and error reportingError efficientResource allocationProgram synchronisationResource managementResource Provider
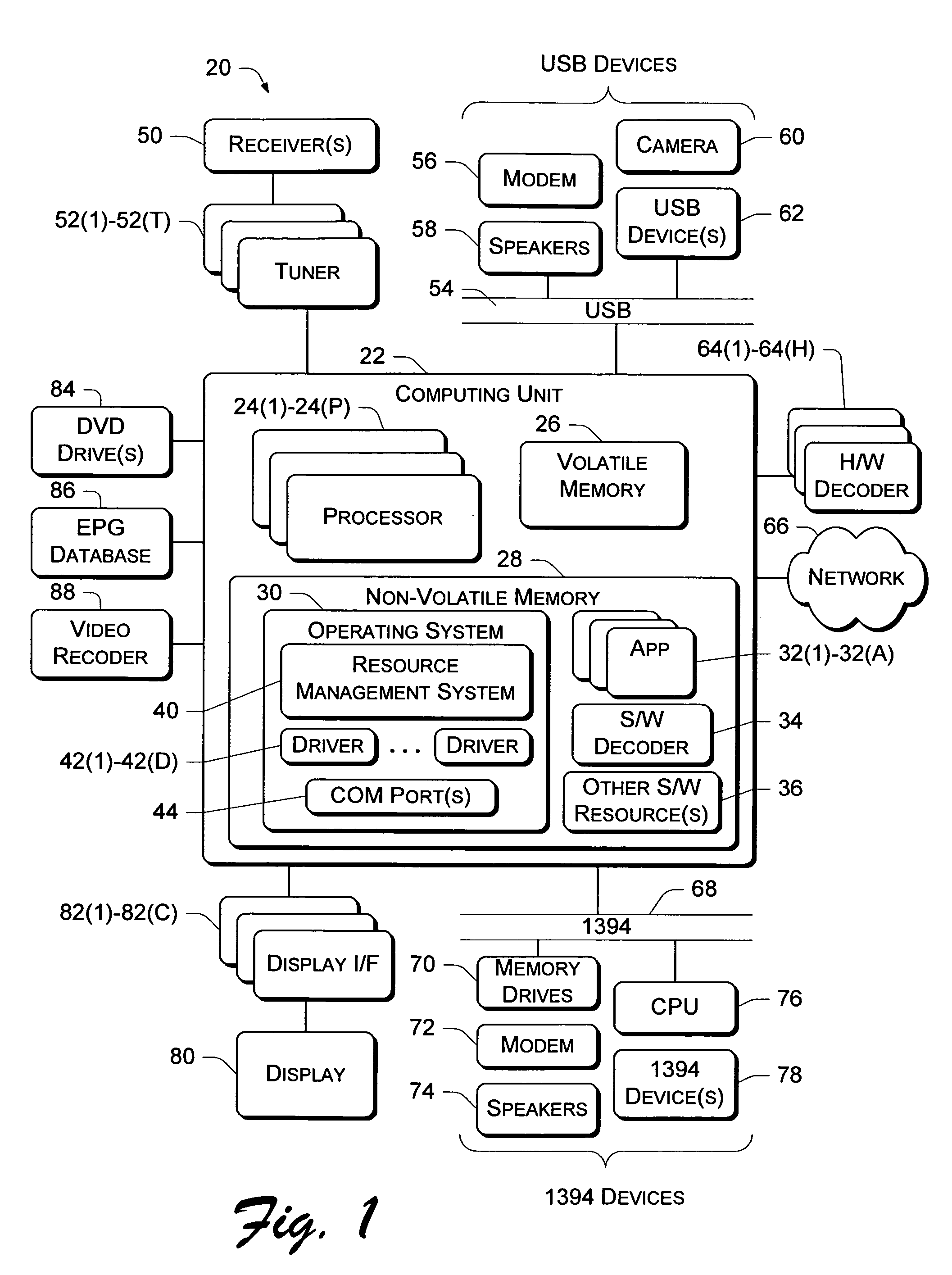
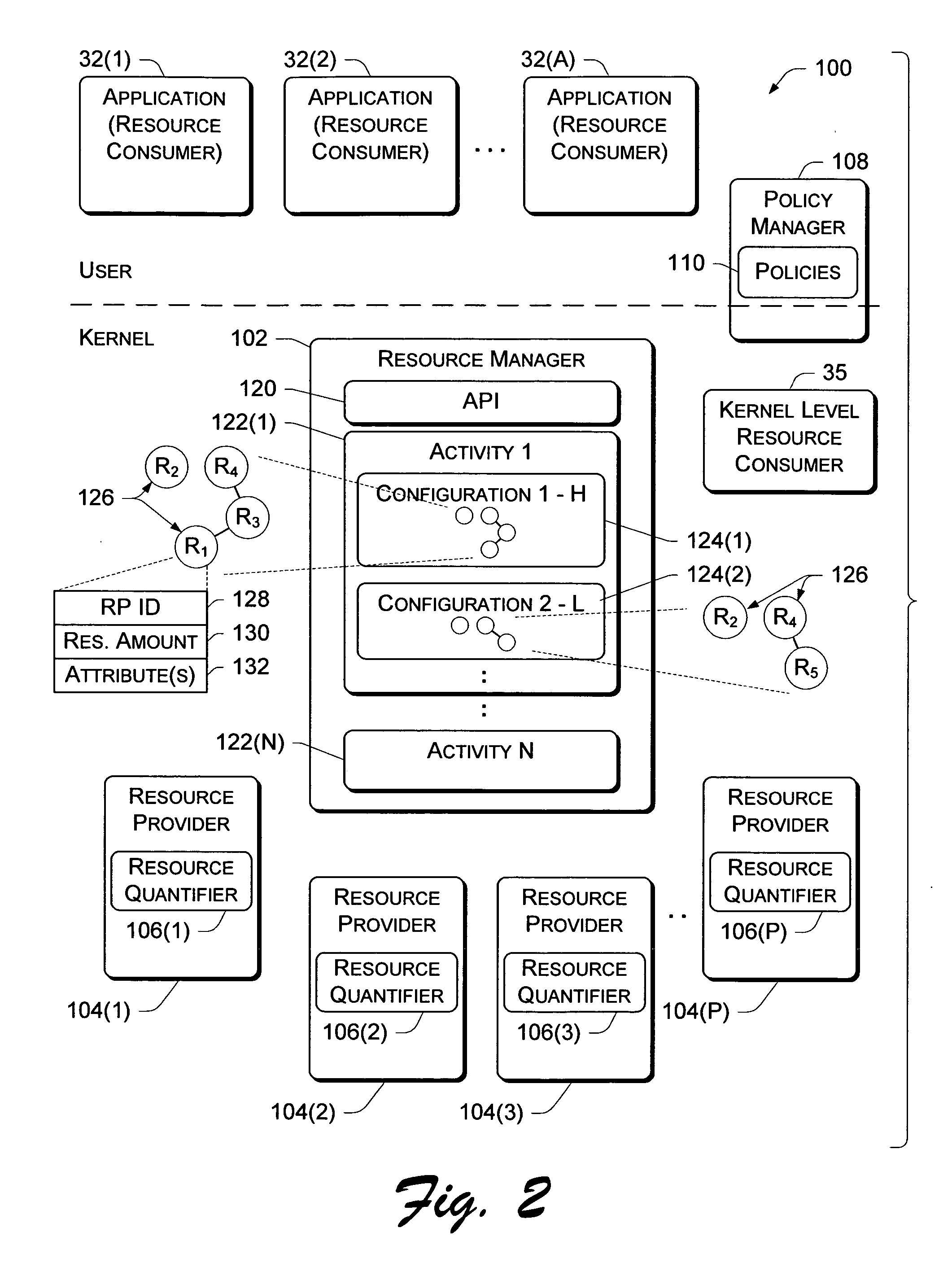
Resource management architectures implemented in computer systems to manage resources are described. In one embodiment, a general architecture includes a resource manager and multiple resource providers that support one or more resource consumers such as a system component or application. Each provider is associated with a resource and acts as the manager for the resource when interfacing with the resource manager. The resource manager arbitrates access to the resources provided by the resource providers on behalf of the consumers. A policy manager sets various policies that are used by the resource manager to allocate resources. One policy is a priority-based policy that distinguishes among which applications and / or users have priority over others to use the resources. A resource consumer creates an “activity” at the resource manager and builds one or more “configurations” that describe various sets of preferred resources required to perform the activity. Each resource consumer can specify one or more configurations for each activity. If multiple configurations are specified, the resource consumer can rank them according to preference. This allows the resource consumers to be dynamically changed from one configuration to another as operating conditions change.
Owner:ZHIGU HLDG
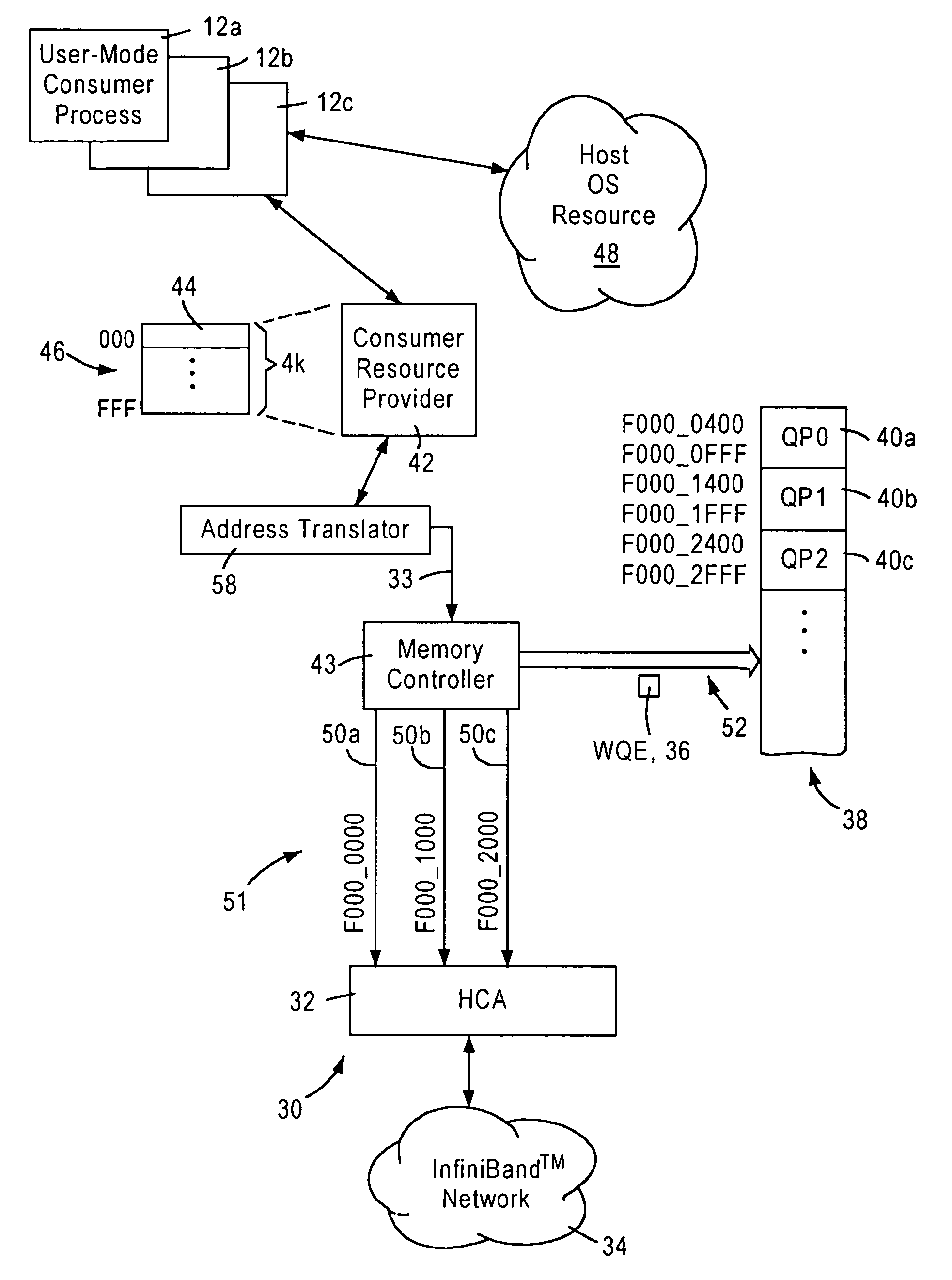
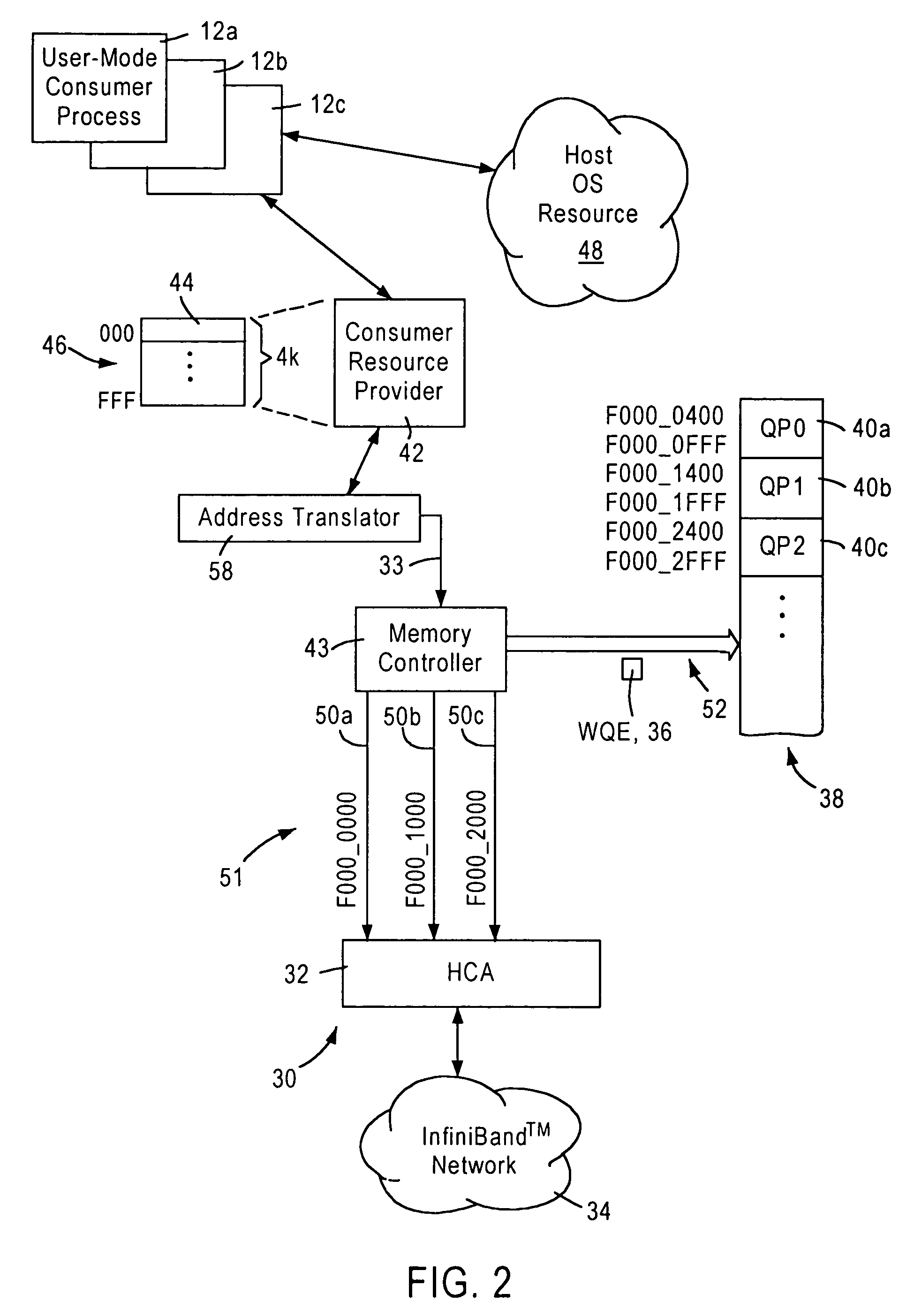
Arrangement for implementing kernel bypass for access by user mode consumer processes to a channel adapter based on virtual address mapping
InactiveUS7003586B1Memory adressing/allocation/relocationMultiple digital computer combinationsVirtual destinationOperational system
A consumer resource provider is configured for generating a work request to a prescribed virtual destination address on behalf of a user-mode consumer process requiring a memory access. An operating system resource, configured for establishing communications between the consumer resource provider and a host channel adapter configured for servicing the work notifications, assigns virtual address space for use by the consumer resource provider, and respective unique mapping values specified as user mode access for use by the consumer resource provider in executing the memory accesses on behalf of the respective user-mode consumer processes. An address translator includes a translation map for uniquely mapping the virtual address space used by the consumer resource provider to a prescribed physical address space accessible by the host channel adapter. The address translator, in response to receiving the work notification at a virtual address from the consumer resource provider on behalf of an identified user-mode consumer process, maps the work notification to a corresponding prescribed physical address based on the corresponding mapping value assigned for the identified user-mode consumer process, enabling the host channel adapter to detect the work notification at the mapped physical address.
Owner:ADVANCED MICRO DEVICES INC
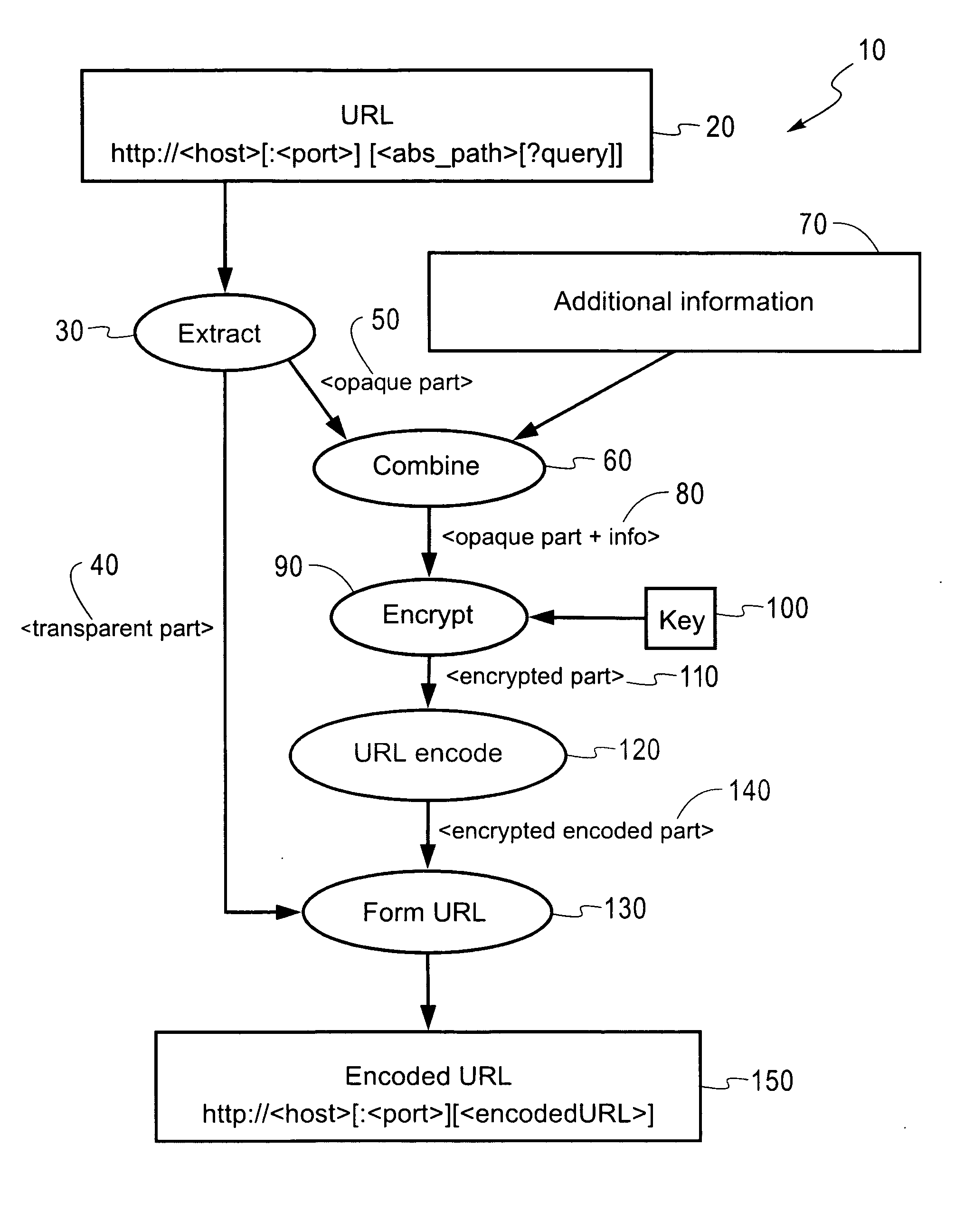
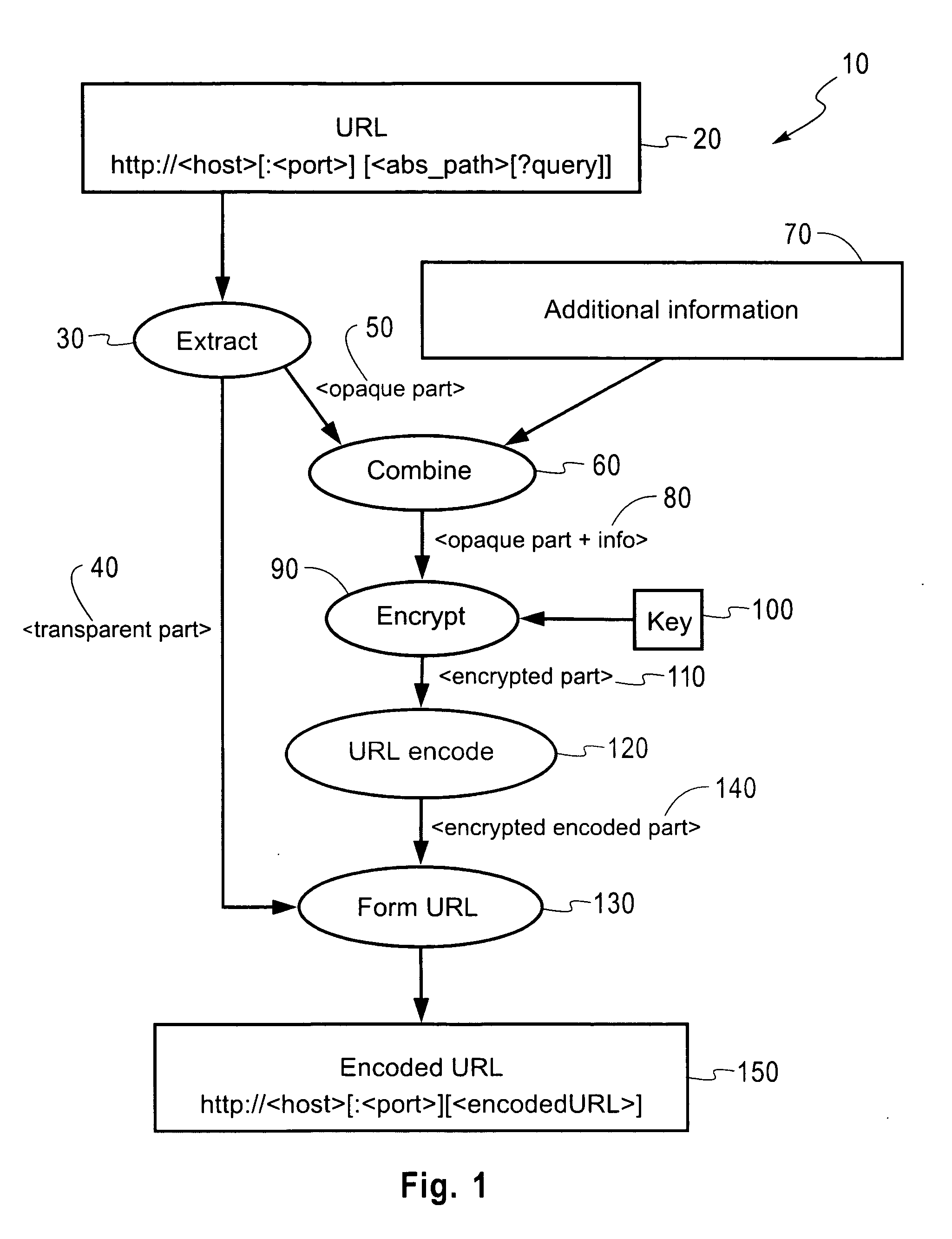
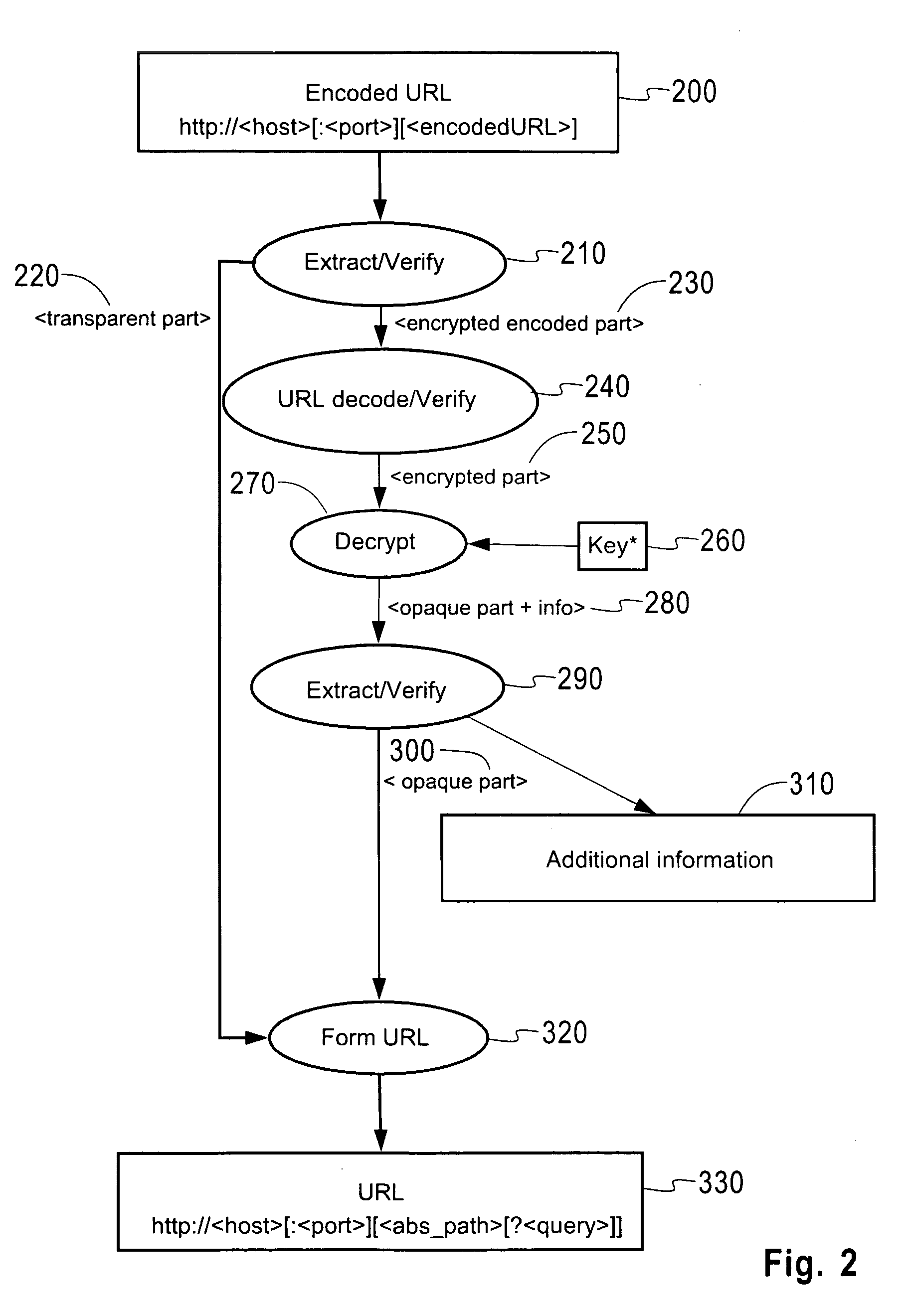
Stateless methods for resource hiding and access control support based on URI encryption
InactiveUS20060106802A1Eliminate the problemDigital data processing detailsComputer security arrangementsUniform resource identifierResource Provider
An apparatus and method are disclosed for enabling controlled access to resources at a resource provider server. The invention may encrypt or decrypt a portion of a uniform resource identifier (URI), according to a stateless method for hiding resources and / or providing access control support. Upon receipt of a URI having an encrypted portion, the invention decrypts the encrypted portion using a predetermined key to obtain a decrypted segment, extracts additional information from the decrypted segment and forms a decrypted URI, before the decrypted URI is forwarded to a resource producer server. The invention may also encrypt a URI from a resource provider server before it is sent to a client in response to a client request.
Owner:IBM CORP
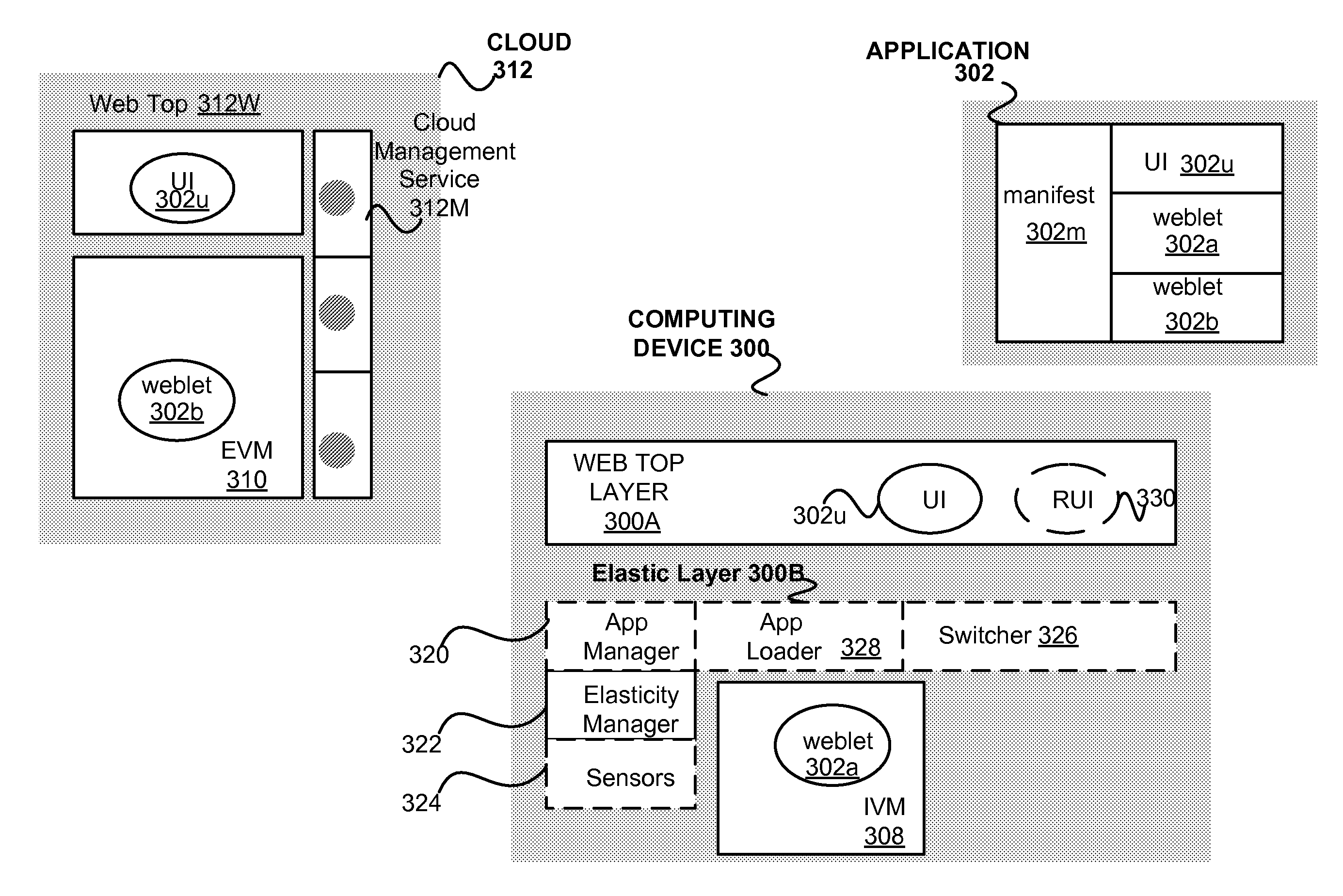
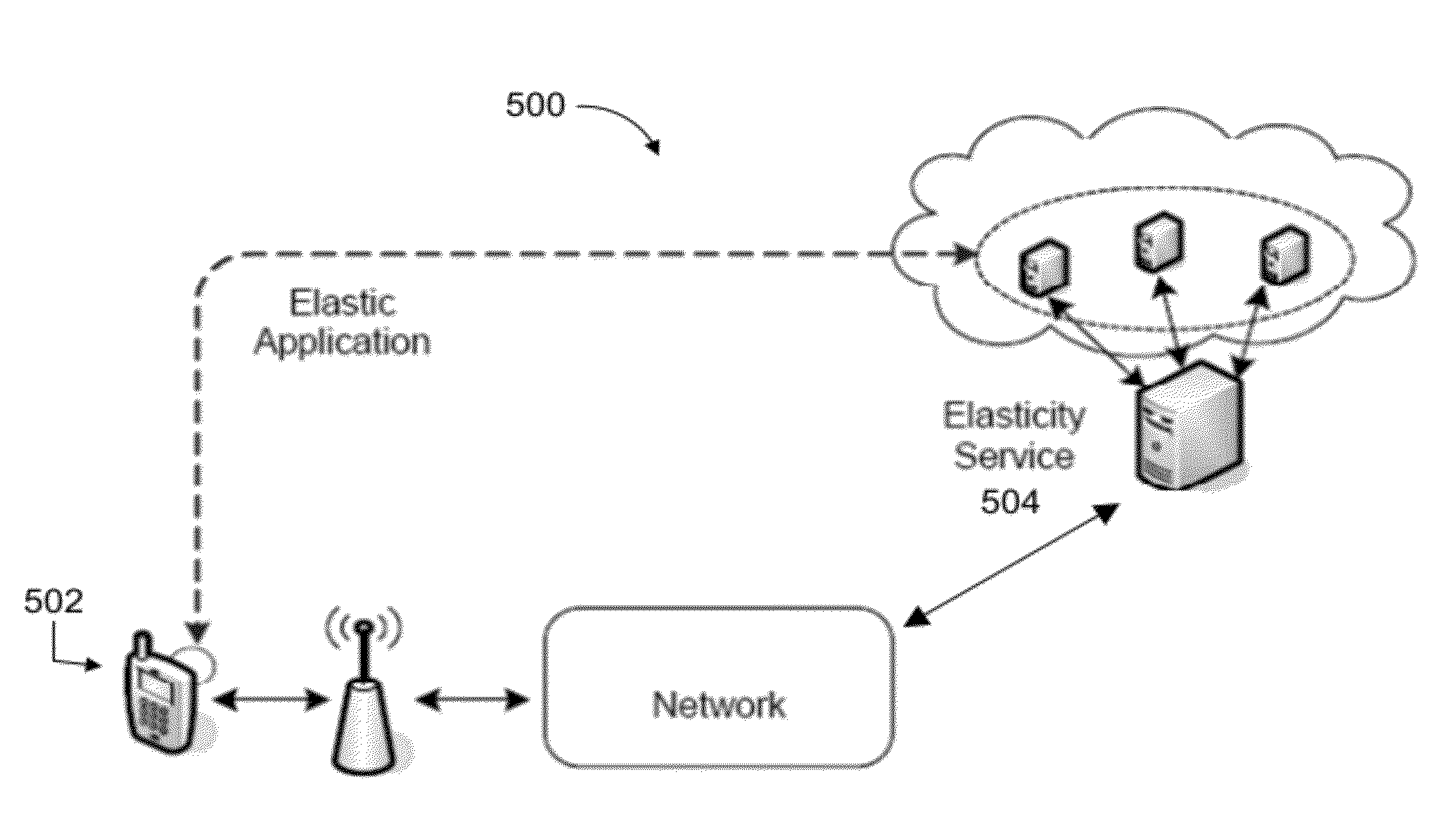
Securely using service providers in elastic computing systems and environments
InactiveUS20110004916A1Improve abilitiesEasy to useDigital data authenticationProgram controlScalable computingService provision
Access permission can be assigned to a particular individually executable portion of computer executable code (“component-specific access permission”) and enforced in connection with accessing the services of a service provider by the individually executable portion (or component). It should be noted that least one of the individually executable portions can request the services when executed by a dynamically scalable computing resource provider. In addition, general and component-specific access permissions respectively associated with executable computer code as a whole or one of it specific portions (or components) can be cancelled or rendered inoperable in response to an explicit request for cancellation.
Owner:SAMSUNG ELECTRONICS CO LTD
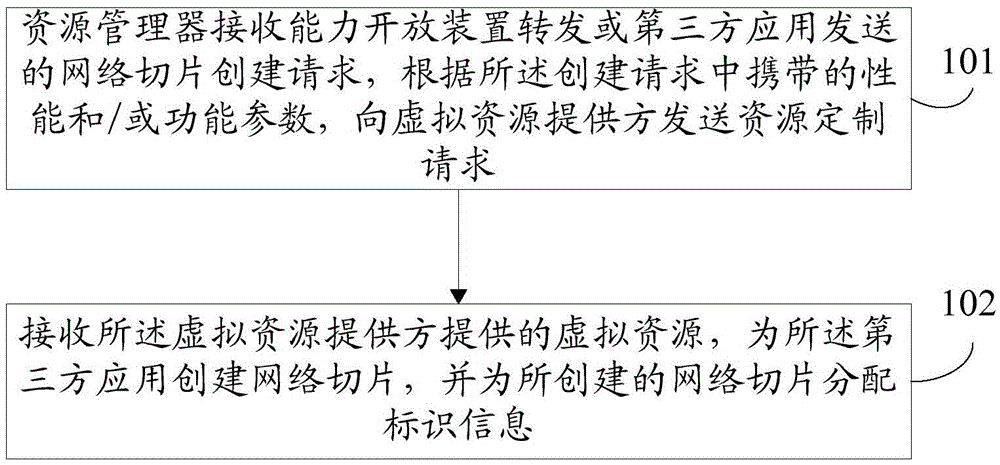
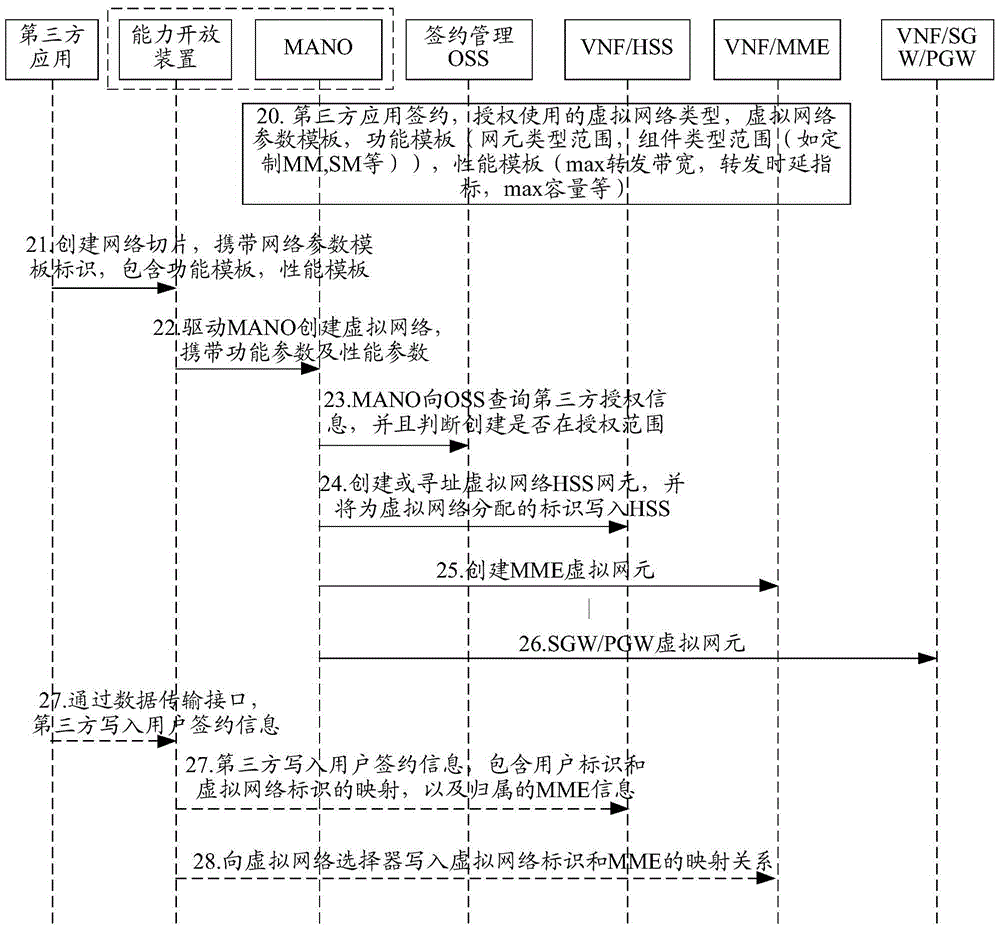
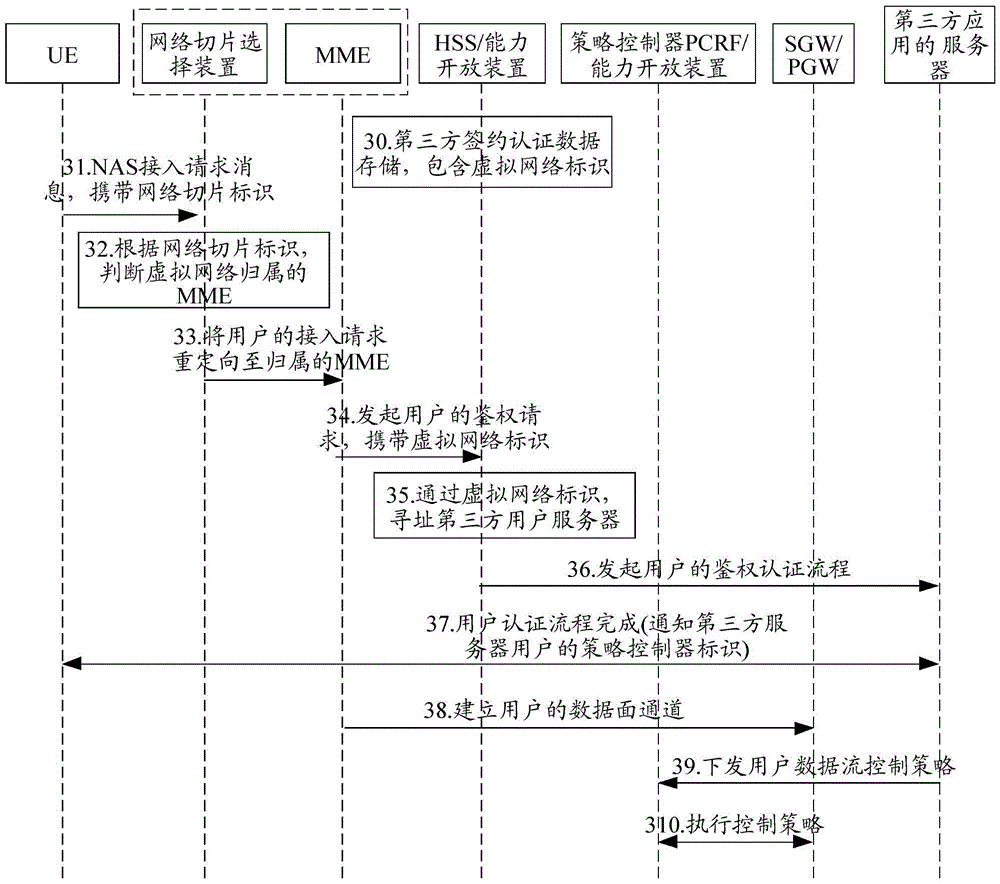
Method and system for accessing to slice network
ActiveCN106713406AAchieving Pipeline CapabilitiesOpen authentication capabilityTransmissionSoftware simulation/interpretation/emulationThird partyResource Provider
The invention discloses a method and system for accessing to a slice network. The method comprises the steps that a resource manager receives a network slice establishment request sent by a third-party application, and sends a resource customization request to a virtual resource provider according to performance and / or function parameters carried in the establishment request; and a virtual resource provided by the virtual resource provider is received, a network slice is established for the third-party application, and identification information is distributed to the established network slice.
Owner:CHINA MOBILE COMM GRP CO LTD
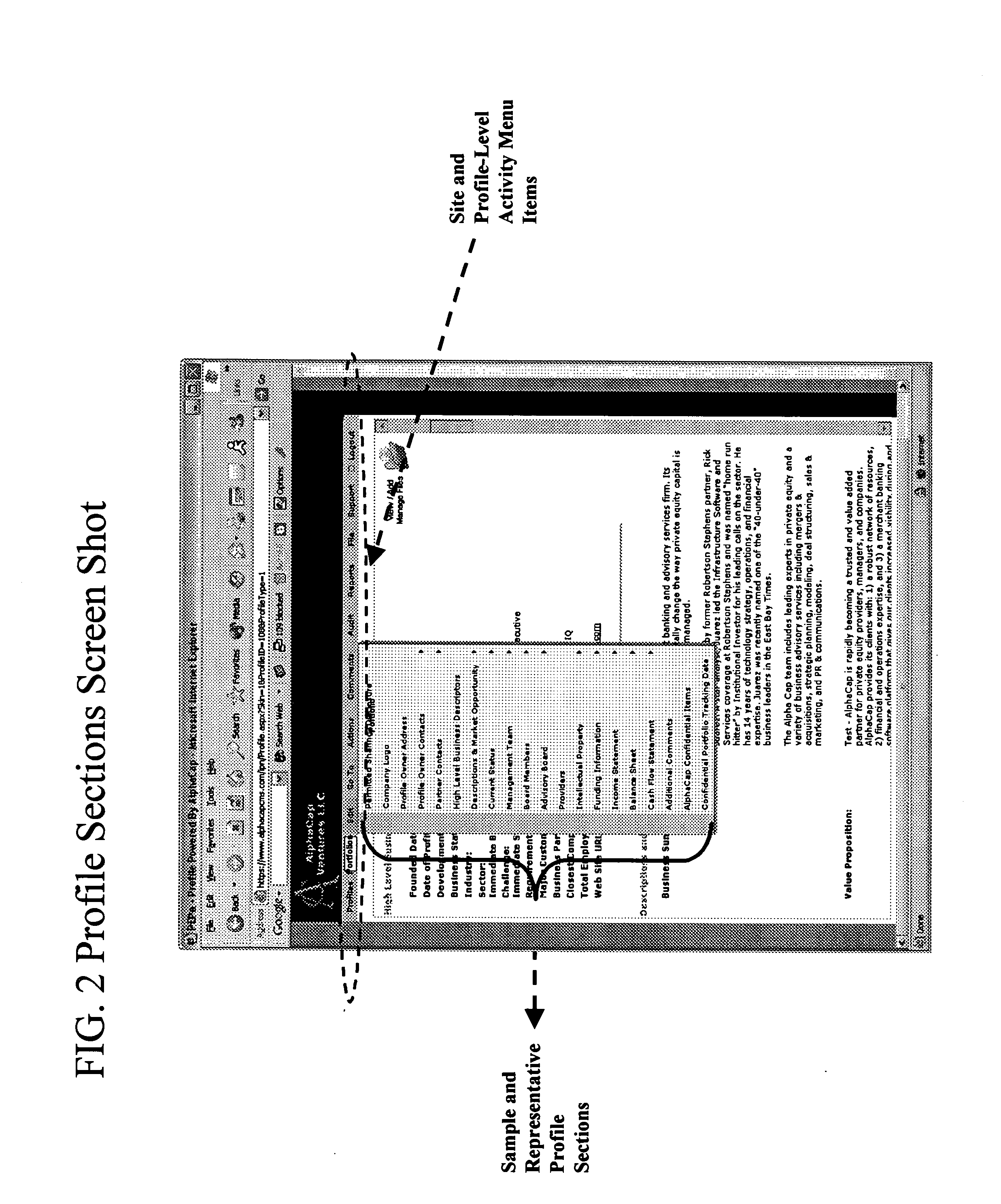
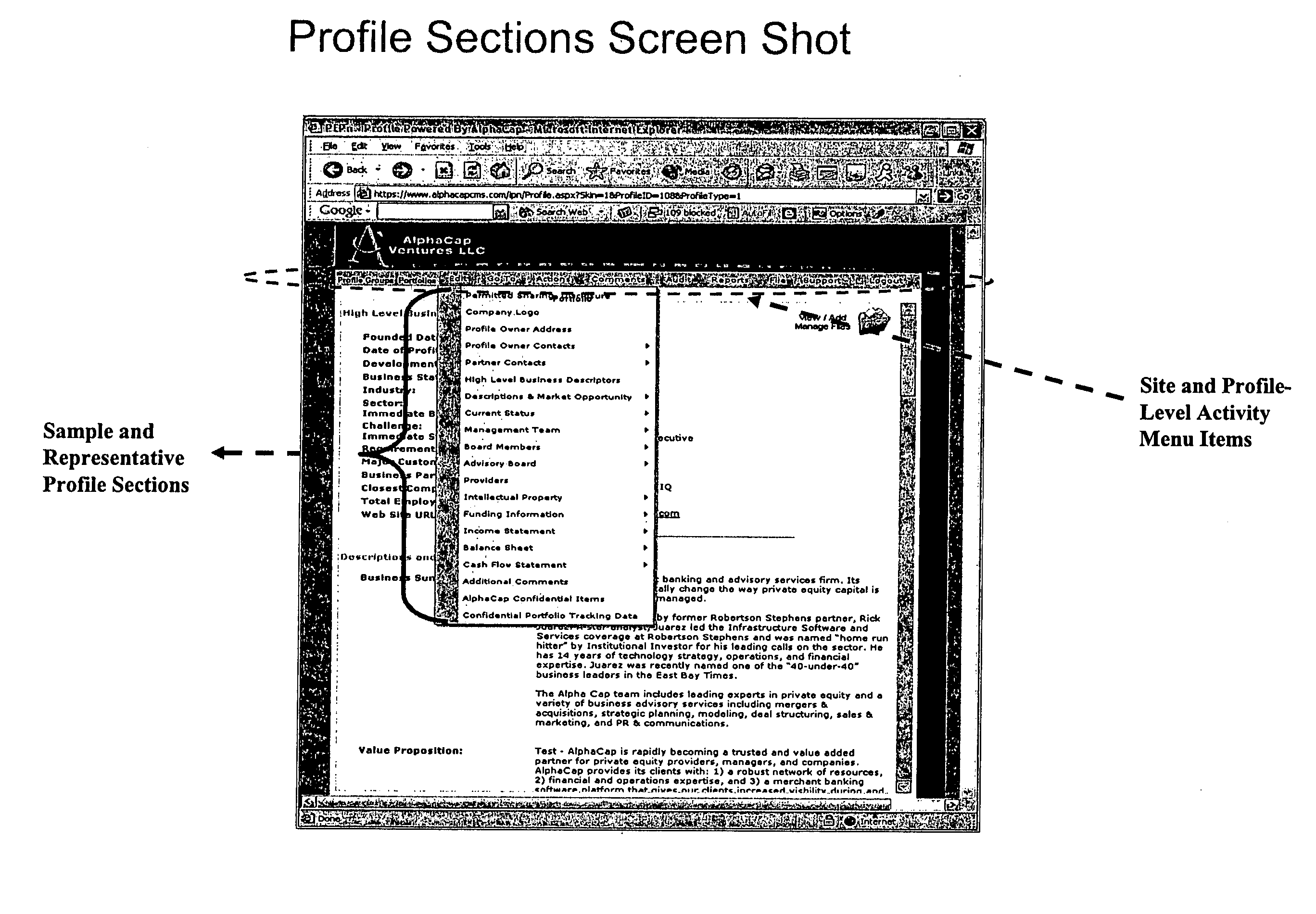
Private entity profile network
InactiveUS20050131830A1Shorten the timeReduce needFinanceComputer security arrangementsPersonalizationThird party
In private equity and debt funding operations, resource providers define electronic data collection templates to be filled in by prospective resource consumers to form semi-homogeneous profiles. Providers and / or consumers can assign themselves and / or selected third parties various individualized levels of permissions to access and to perform activities on the profiles. Providers can organize profiles into portfolios to further manage the data. All accesses and activities, such as changes to the data, are tracked and recorded in logs useful for audit purposes.
Owner:ALPHACAP VENTURES
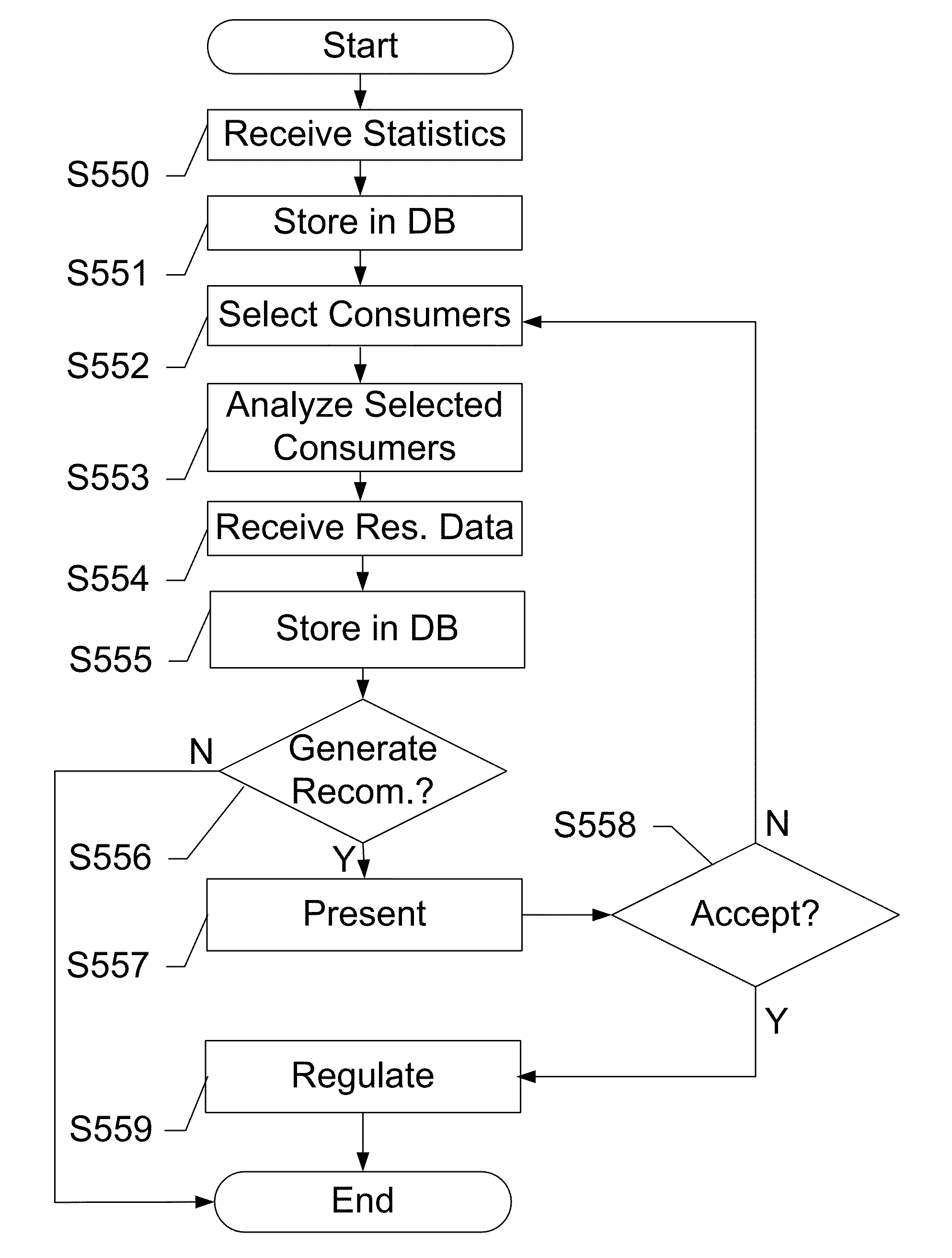
Providing Resource Consumption Recommendations
ActiveUS20140006329A1Reduce consumptionResource consumption is often greatData processing applicationsKnowledge representationResource consumptionTechnical standard
The subject disclosure provides systems and methods for recommending optimal consumption of a variety of resources that may be consumed by a consumer. A recommendation provided by the system may be based upon resource-consumption statistics gathered by a plurality of sensors, consumer's resource-consumption behavior, consumer-defined criteria, resource availability, and a cost of consumption. The recommendation may include a recommendation on how the consumer may lower resource consumption costs. The recommendation may further include optimal consumption considering consumption trends of a plurality of consumers living in a geographical proximity. The recommendation may include optimal usage of a consumer's vehicle such that the vehicle may consume the least amount of energy. The recommendation may further include offer(s) of credit / incentives by resource providers to consumers in exchange for less consumption of resource, alternative consumption of resources, and any combination thereof.
Owner:AT&T INTPROP I L P +1
Resource manager architecture
InactiveUS20050033846A1Facilitates reservation and error reportingError efficientResource allocationProgram synchronisationResource managementResource Provider
Resource management architectures implemented in computer systems to manage resources are described. In one embodiment, a general architecture includes a resource manager and multiple resource providers that support one or more resource consumers such as a system component or application. Each provider is associated with a resource and acts as the manager for the resource when interfacing with the resource manager. The resource manager arbitrates access to the resources provided by the resource providers on behalf of the consumers. A policy manager sets various policies that are used by the resource manager to allocate resources. One policy is a priority-based policy that distinguishes among which applications and / or users have priority over others to use the resources. A resource consumer creates an “activity” at the resource manager and builds one or more “configurations” that describe various sets of preferred resources required to perform the activity. Each resource consumer can specify one or more configurations for each activity. If multiple configurations are specified, the resource consumer can rank them according to preference. This allows the resource consumers to be dynamically changed from one configuration to another as operating conditions change.
Owner:ZHIGU HLDG
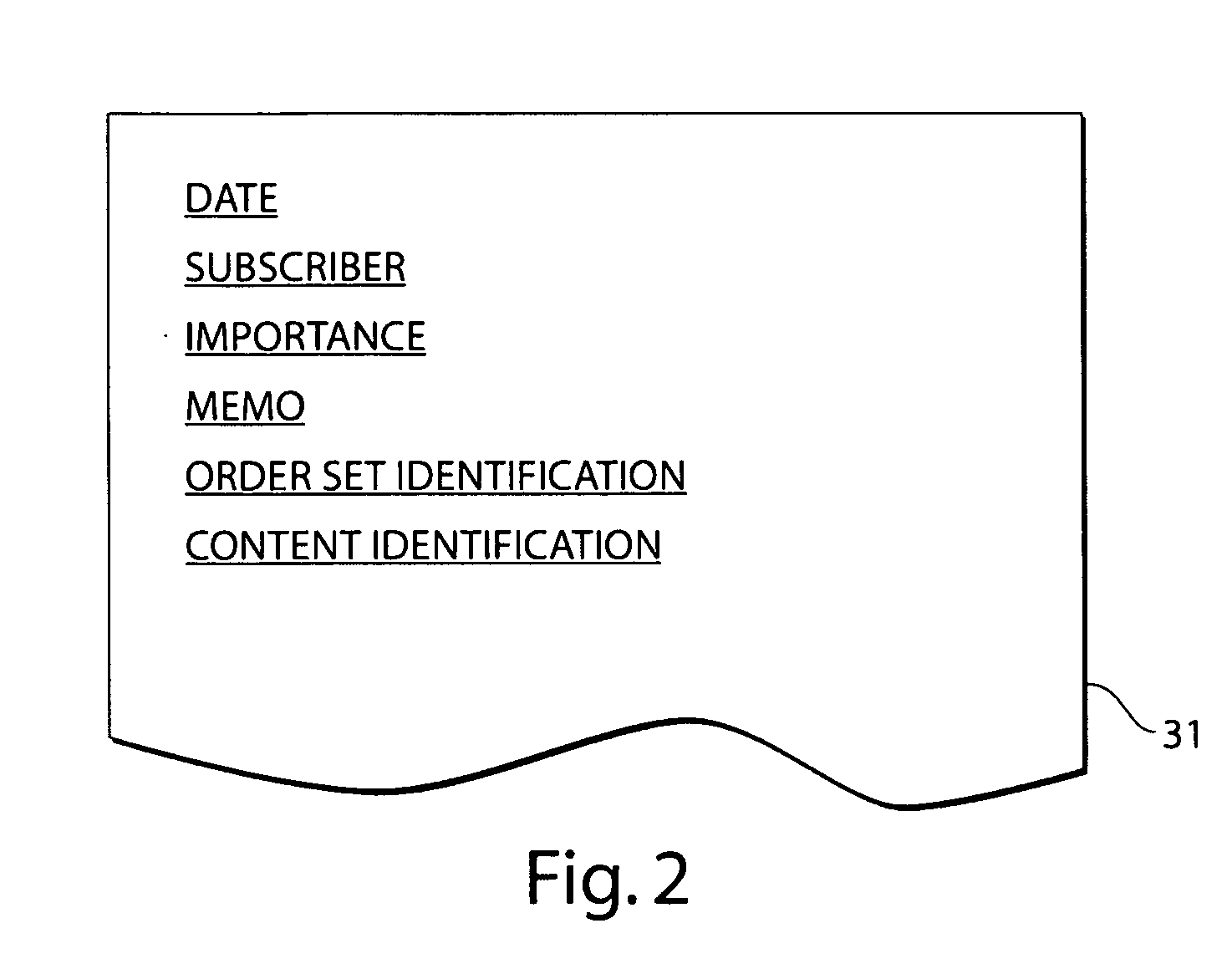
Method and apparatus for managing medical order sets
InactiveUS20070005394A1Reduce duplicationEasy accessMedical practises/guidelinesCommerceResource ProviderOrder set
A system and method for maintaining medical order sets allows for a medical information resource provider to generate and make available order sets for use in providing medical care. Subscribers to the order sets may modify the order sets, and may receive notification when changes to the order sets and / or changes to content in the medical information resource that are relevant to the order sets occur. Subscriber-created and / or provider-created associations between order sets and content in the medical information resource may be used to identify the need to provide a notification when changes to content occur.
Owner:UPTODATE
Telecommunications service delivery
InactiveUS6522883B2Increase in sizeIncrease volumeMultiplex system selection arrangementsAccounting/billing servicesService provisionEngineering
Routing apparatus for a telecommunication system includes a telecommunications user apparatus arranged to generate a request for a telecommunications delivery service, to receive a plurality of telecommunications delivery service offers and to select one of them. The system also intends a plurality of telecommunication service supply apparatuses each arranged to receive one of the request to generate an offer signal specifying a proposed delivery service and to receive an acceptance signal indicating acceptance thereof and, on receipt thereof, to generate a service provision invitation. The system further provides a plurality of resource supplier apparatuses each representing a communications resource arranged to communicate with each of said service supply apparatuses. The resource supplier apparatus is arranged to receive an invitation to determine whether the telecommunications resource they represent would contribute to the provision of the corresponding service; and, if so, to signal this to the service supply apparatus. The service supply apparatus is arranged, on the basis of signals from the resource supplier apparatus to select the route subsequent to the offer of the service.
Owner:BRITISH TELECOMM PLC
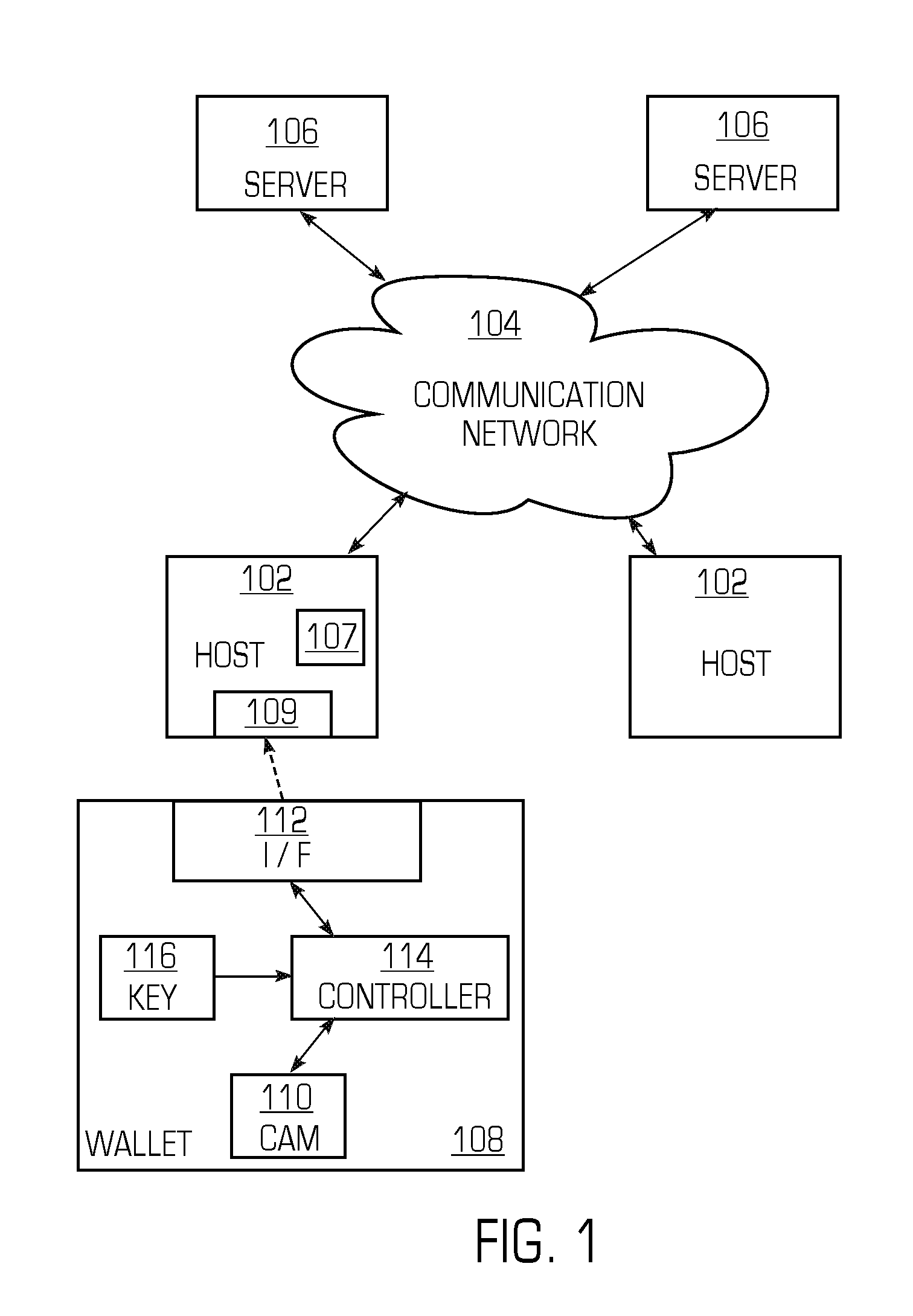
Smart memory card wallet
InactiveUS7533063B2Coded identity card or credit card actuationProtocol authorisationUser inputPassword
A system includes at least one server and at least one host computer coupled to a communication network. A memory card wallet includes a content addressable memory that stores server identifiers, such as URLs, and user information associated with the resource provider, such as user identification numbers and passwords. The user inserts the memory card wallet into the host computer, and instead of entering user identifiers and passwords, the memory card wallet can provide such information to the server. When the user enters a server identifier that matches a server identifier stored in the content addressable memory, the memory card wallet provides the user information associated with the matched sever identifier.
Owner:SILICON STORAGE TECHNOLOGY
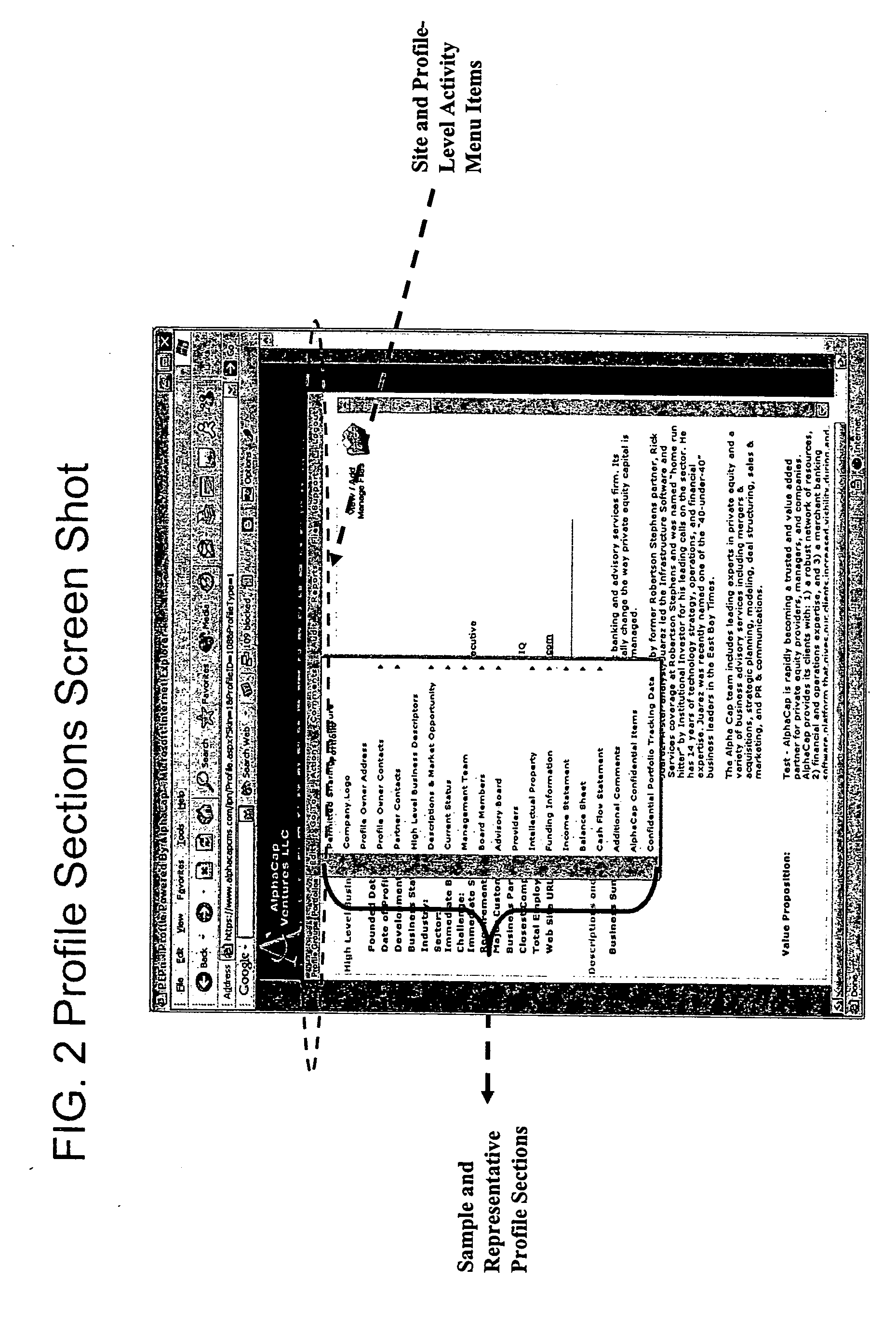
Private entity profile network
InactiveUS20050144135A1Reduce needLow costFinanceComputer security arrangementsPersonalizationThird party
In private equity and debt funding operations, resource providers define electronic data collection templates to be filled in by prospective resource consumers to form semi-homogeneous profiles. Providers and / or consumers can assign themselves and / or third parties various individualized levels of permissions to access and to perform activities on the profiles. Providers can organize profiles into portfolios to further manage the data. All accesses and activities, such as changes to the data, are tracked and recorded in logs useful for audit purposes.
Owner:ALPHACAP VENTURES
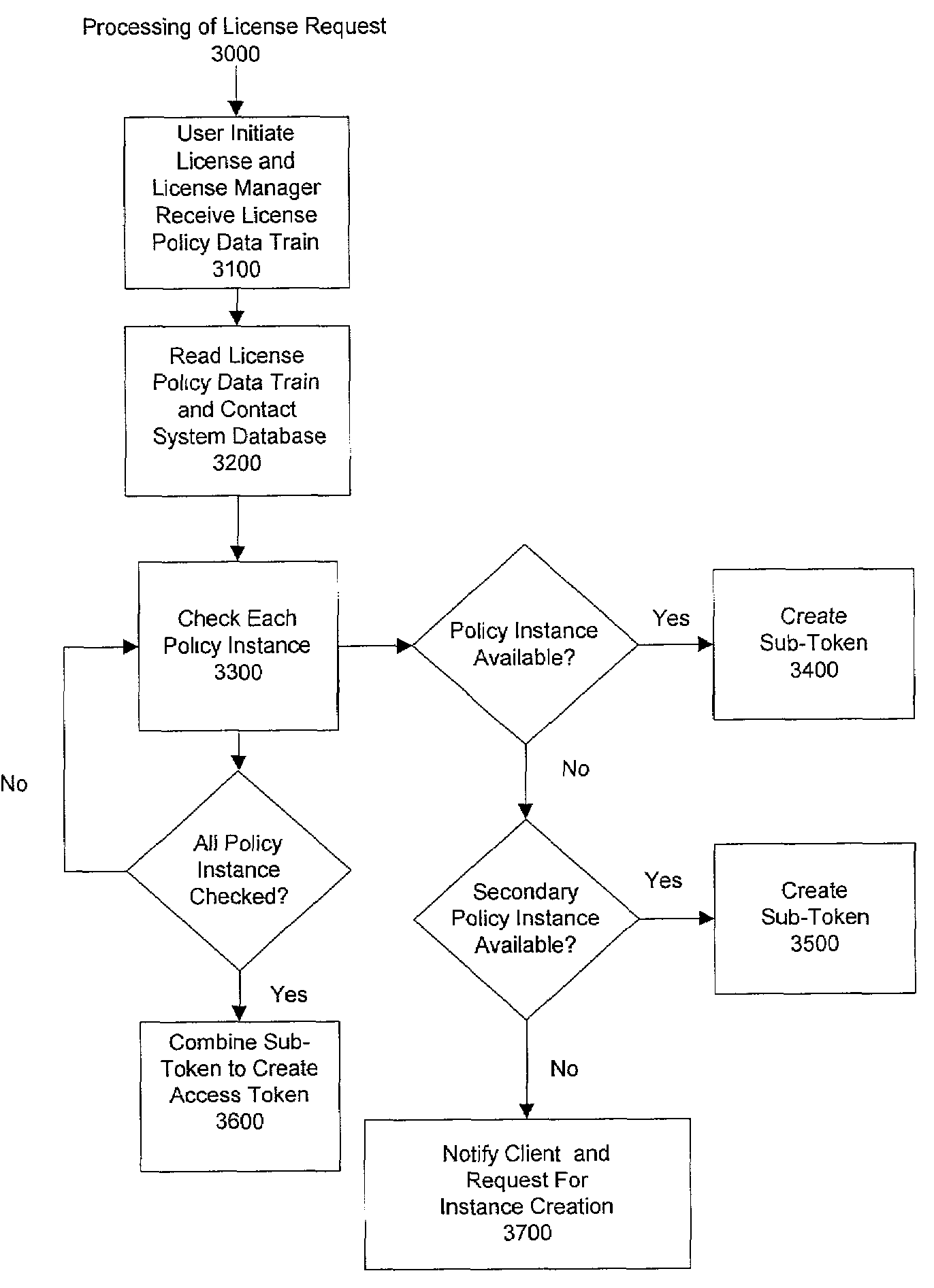
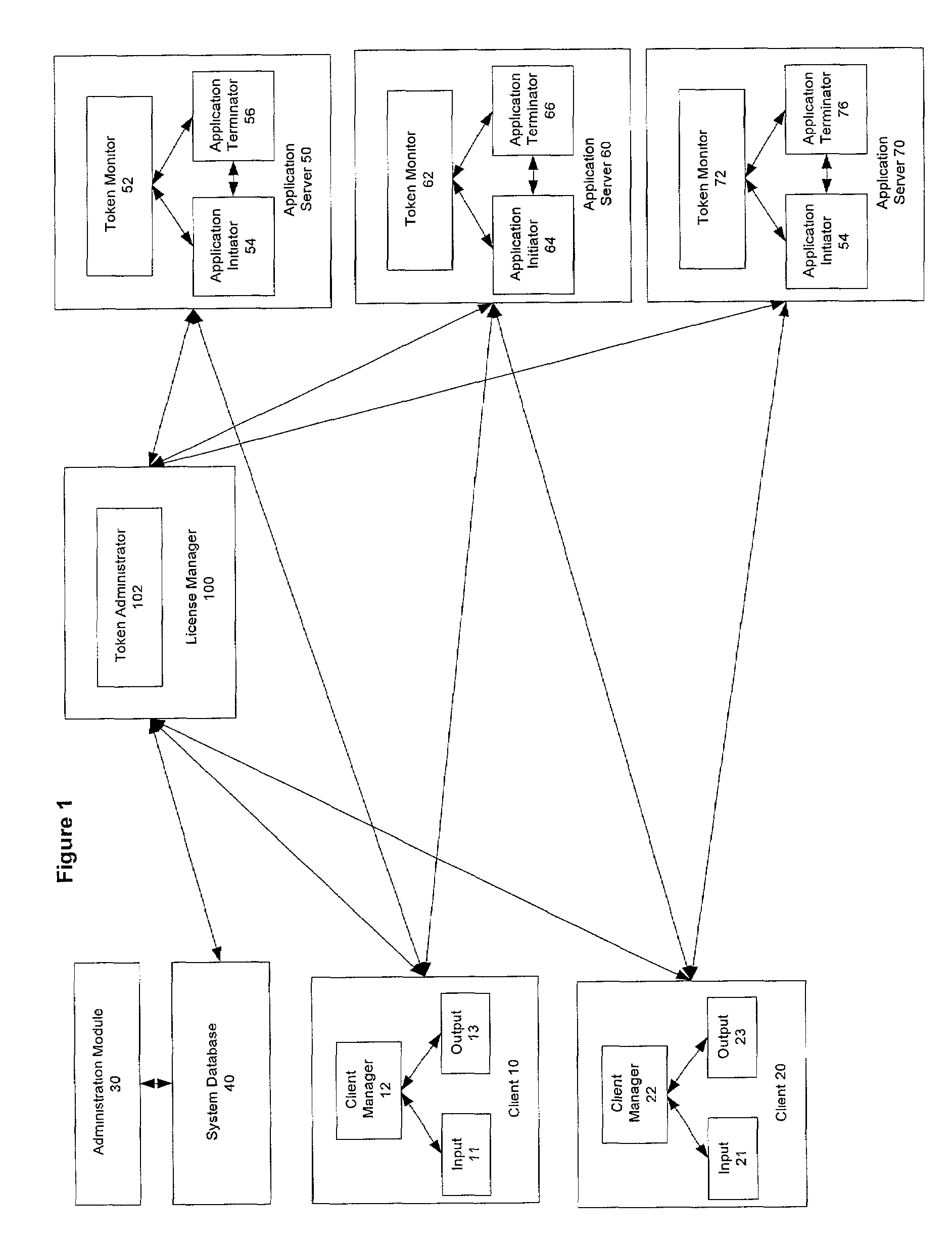
Managing user access of distributed resources on application servers
InactiveUS7249176B1Digital data processing detailsAnalogue secracy/subscription systemsApplication serverResource based
A method and system to manage user access to resources and computing tasks on servers located on a network. The preferred embodiments of this system would enable a resource provider to manager user access to resources based on user specific criteria and resource specific criteria. The invention creates user associated access session(s) and generates tokens corresponding to such access session(s) to allow user access. The system is able to manage any type or any combination of licensing criteria, to manage different licensing criteria associated with the same user, to manage different licensing criteria associated with the same resource, and to manage different licensing relationship among users and resources. The system is scalable as additional sets of license managers can be added to manage additional users and resources. Optionally, secondary access sessions are provided to users to allow for completion of a current task when initial access session(s) are depleted.
Owner:ORACLE INT CORP
Mode multiplexing isomerous database access and integration method under gridding environment
InactiveCN101187937AFlexible Virtual Database MechanismImprove practicalityTransmissionSpecial data processing applicationsMultiplexingResource Provider
Owner:BEIHANG UNIV
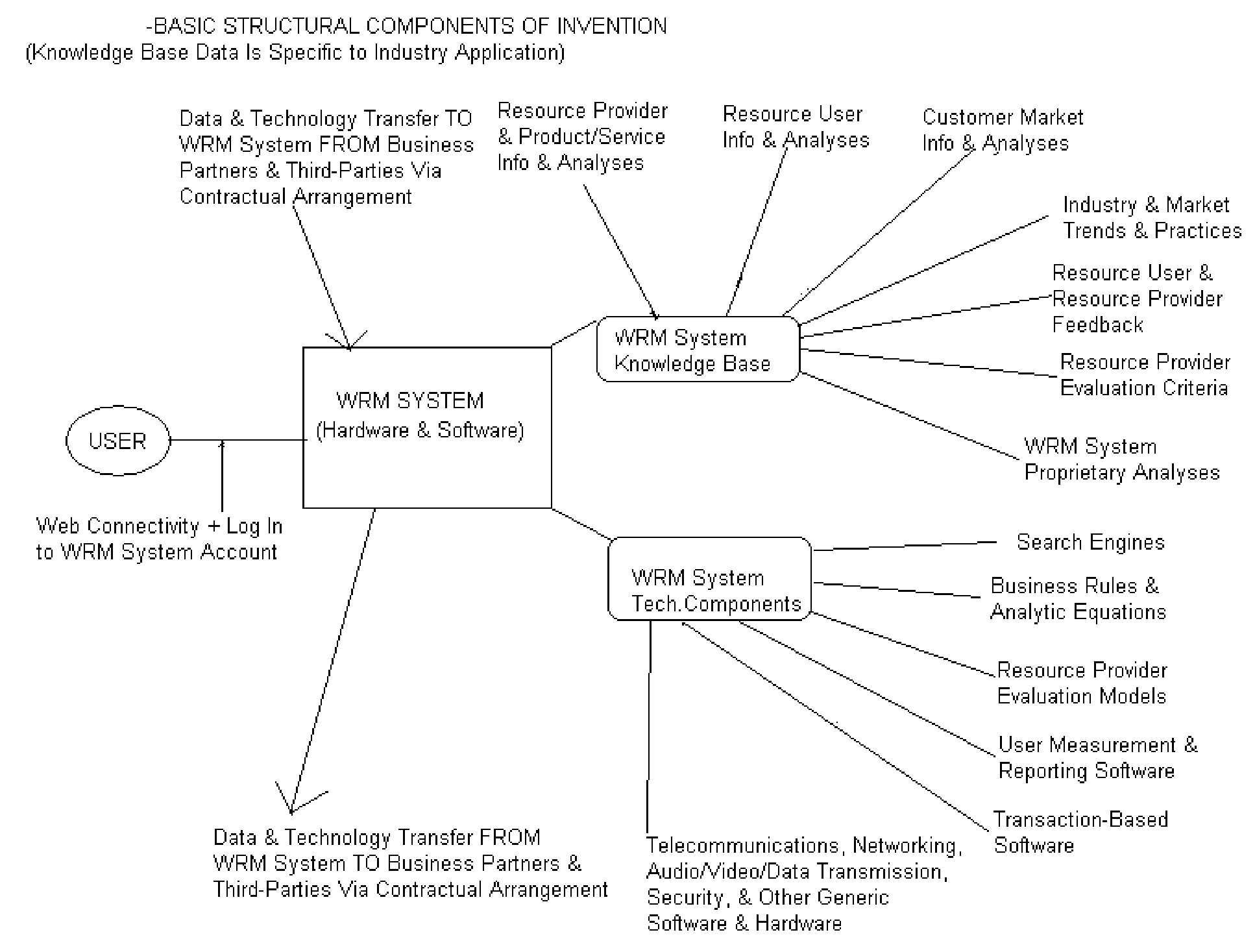
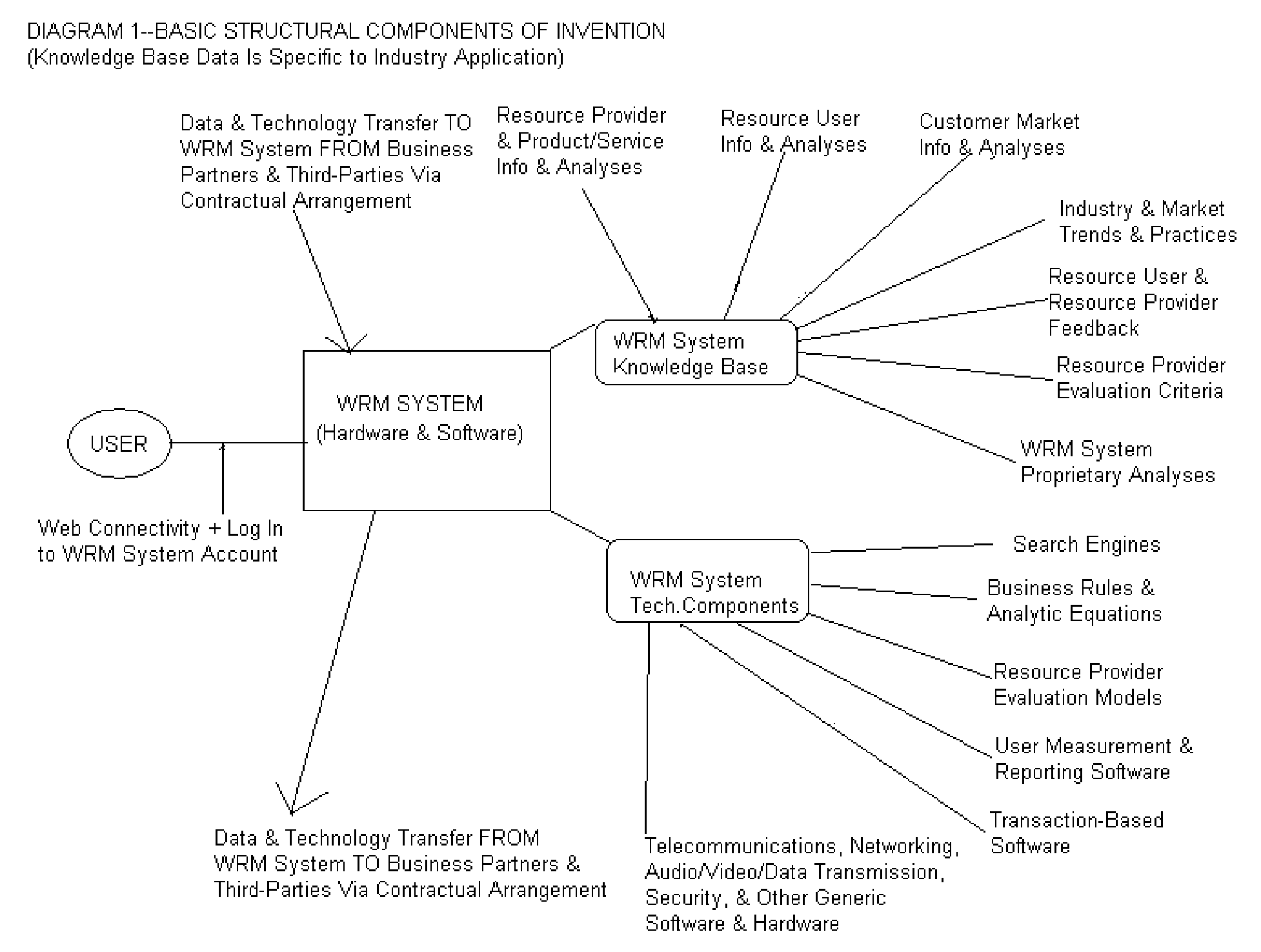
System and method for resource management
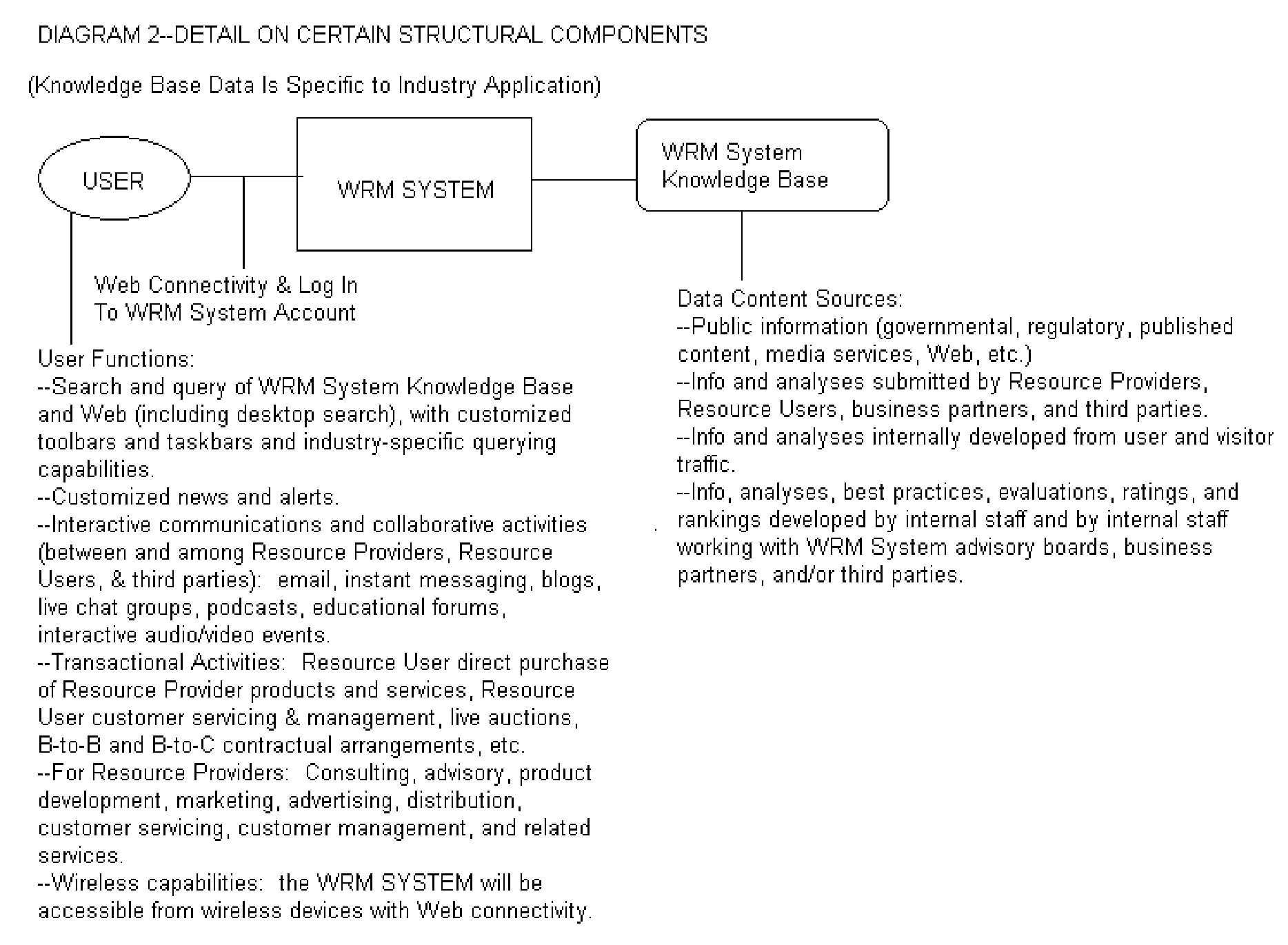
InactiveUS20060112130A1Shorten the timeSave moneyCommerceSpecial data processing applicationsGuidelineResource Management System
A system and method that standardizes, automates, and facilitates the process of identifying, evaluating, selecting, and managing product and service resources for both individual and business resource users within specific industries. In one embodiment, this resource management system includes a web-based or other computer server with at least one database containing data related to product and service resources within a specific industry that can be searched and queried by the user, and at least one resource management system application that contains business rules and industry-specific or user-based criteria, qualitative and / or quantitative resource evaluation standards, and / or other guidelines or reference points, that, when applied to the product and service resource data, generates a resource-related selection, recommendation, rating, ranking, descriptive result, or other action or result that helps the user understand the resource options and the relative merits of the resource options for the user's particular needs, based in large part upon resource criteria chosen by the user, so that the user can make intelligent, informed, efficient, and timely decisions in sourcing, selecting, and managing these product and service resources. In this embodiment, the combination of unbiased industry-specific database information, unbiased industry-specific criteria and / or evaluation standards, and industry-specific search and querying capabilities, accessible on demand by the user, provides the user with a more accurate, precise, higher quality result that is reliable, immediately actionable, and can save the user time, money, and undesirable product or service performance results and / or customer service experiences. In another embodiment, this resource management system may further include software components that provide interactive communication and / or transactional capabilities for users and / or providers of the product and service resources, thus further facilitating the resource management process for both resource users and resource providers in a specific industry.
Owner:LOWSON LINDA
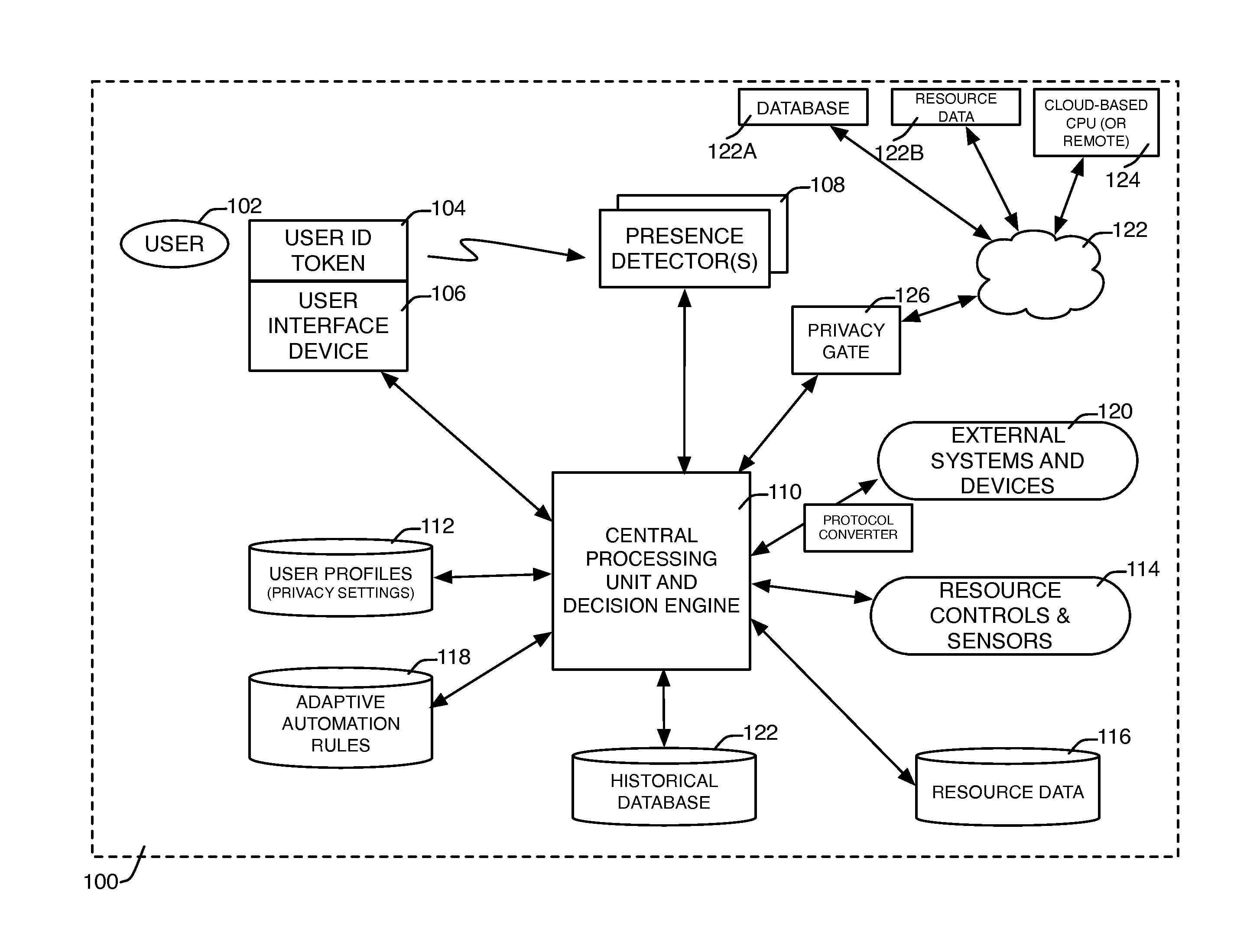
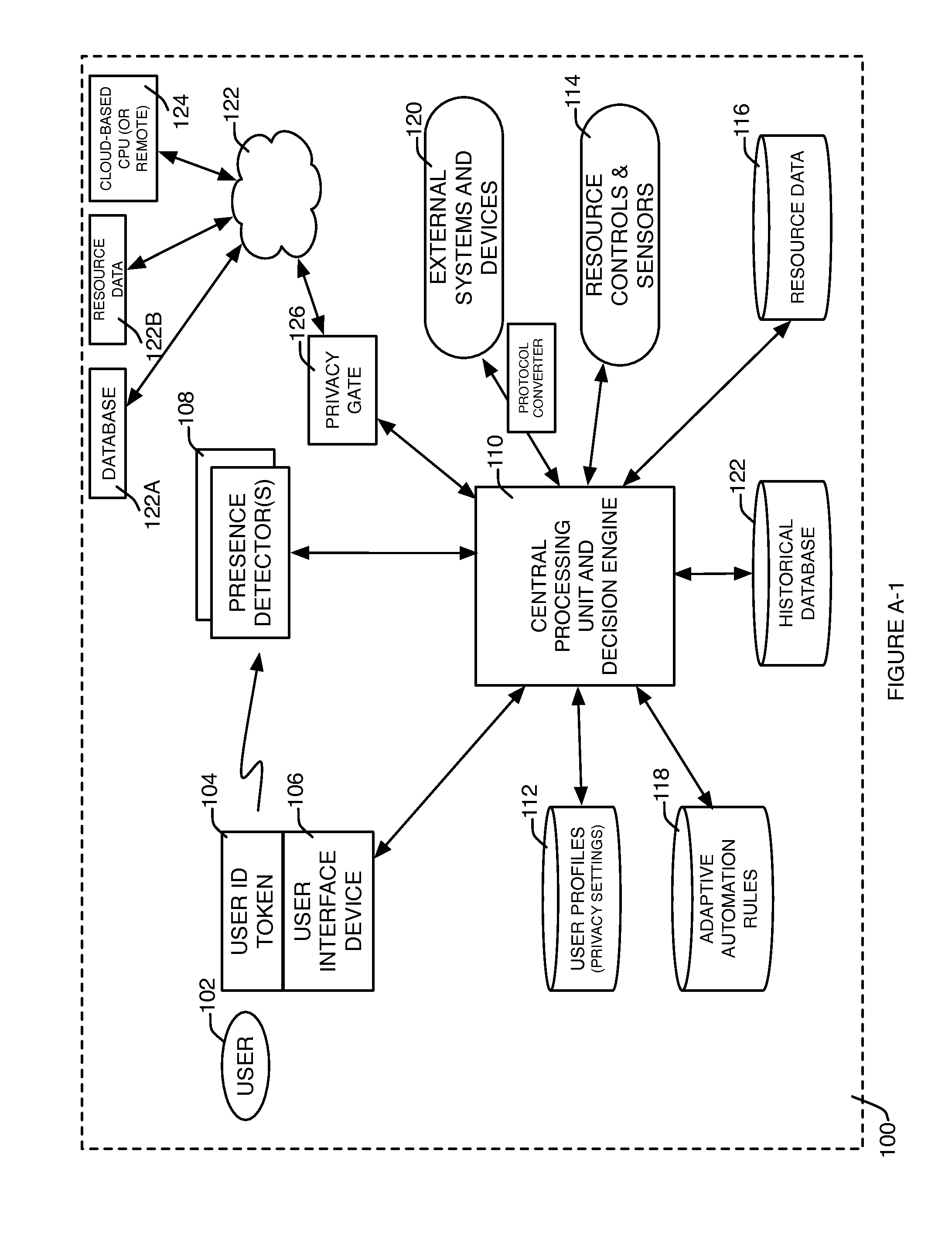
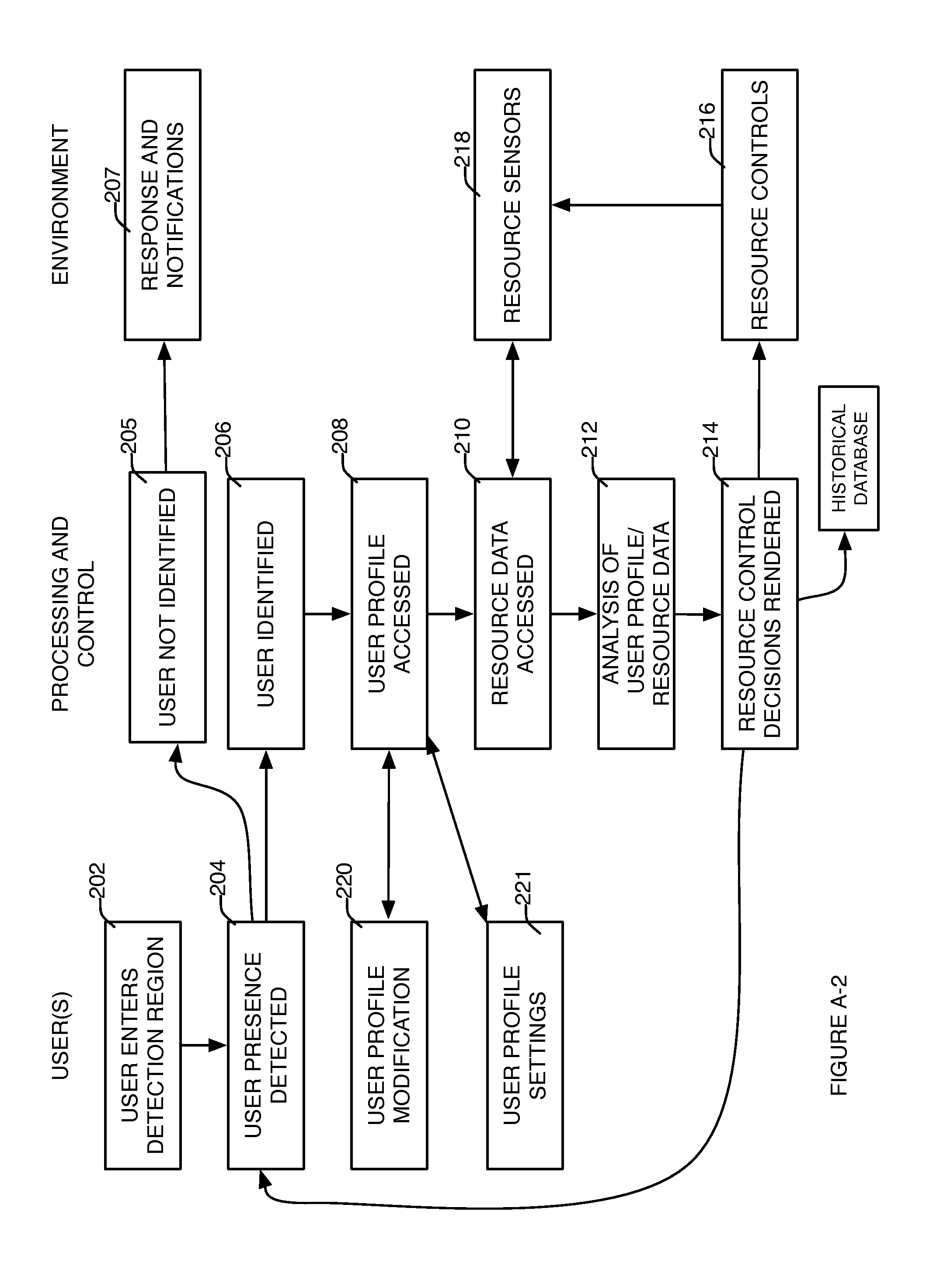
System and method for adaptive automated resource management and conservation
InactiveUS20140297001A1Accurately pattern of useEliminate needProgramme controlComputer controlElectricityResource Management System
Systems, methods, and devices to provide simple adaptive automated resource management of a resource system (such as but not limited to electricity, natural gas, water, data, bandwidth allocation, access to information, etc.) on a local basis, based on automatically detecting, measuring and combining time-varying resource provider preferences, resource market conditions, resource supply source conditions, environmental conditions and resource system impact on the environment, together with resource user locations, user priorities and preferences, and information about other conditions that may be relevant to the operation of the resource management system in order to optimize performance of the resource system to better meet or approach defined goals, and to measure and display the results achieved by the resource management system compared against those goals.
Owner:KASPAR LLC
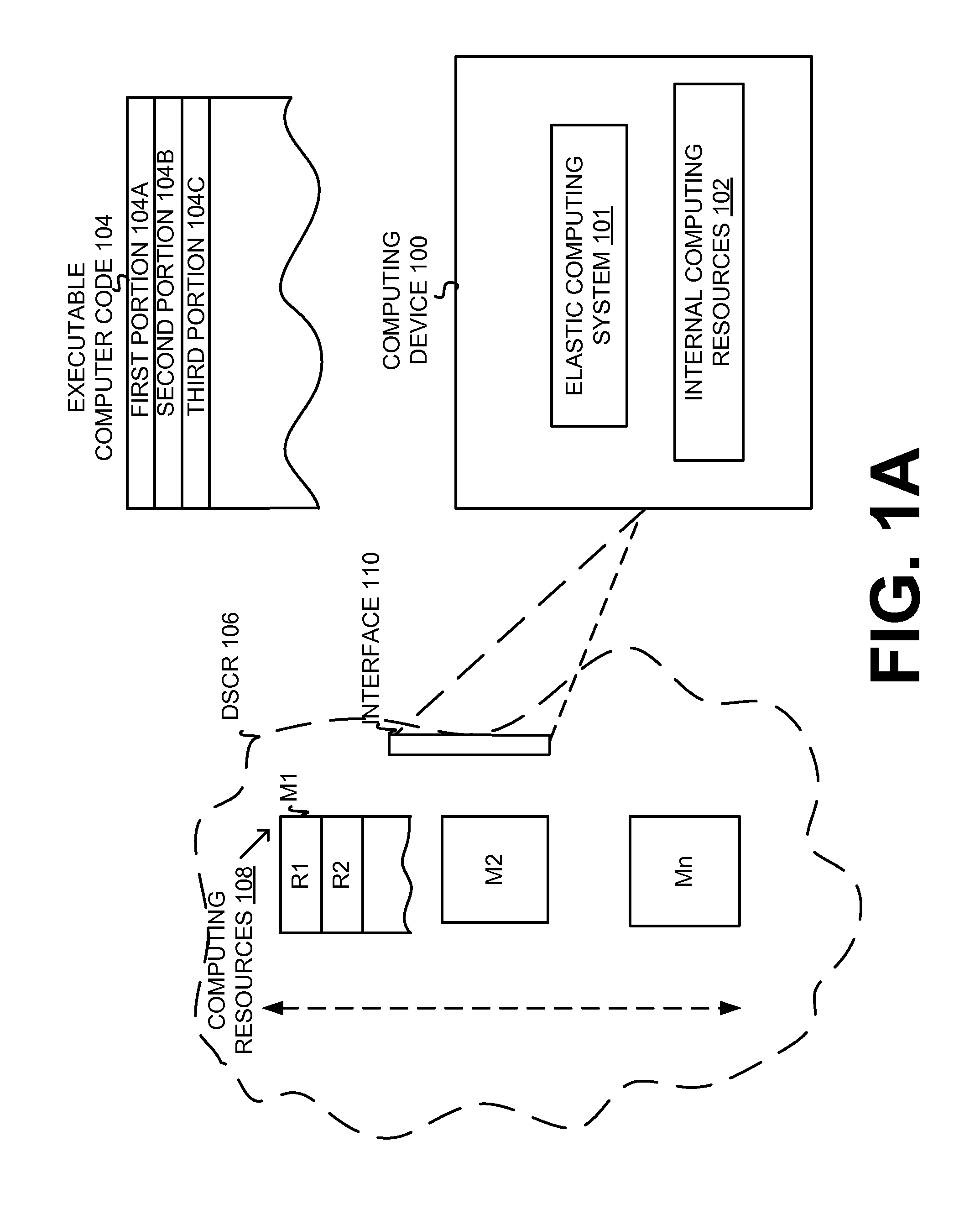
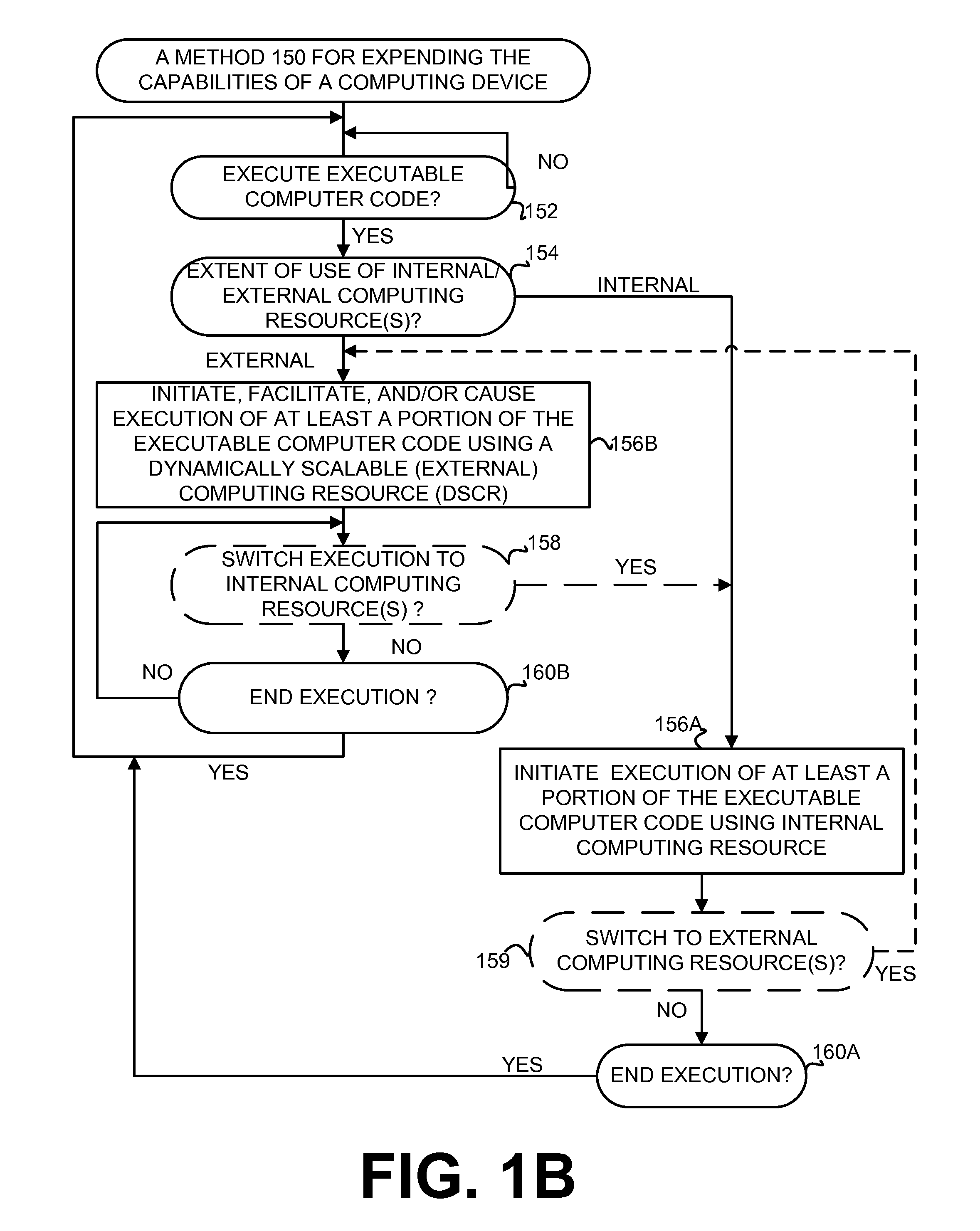
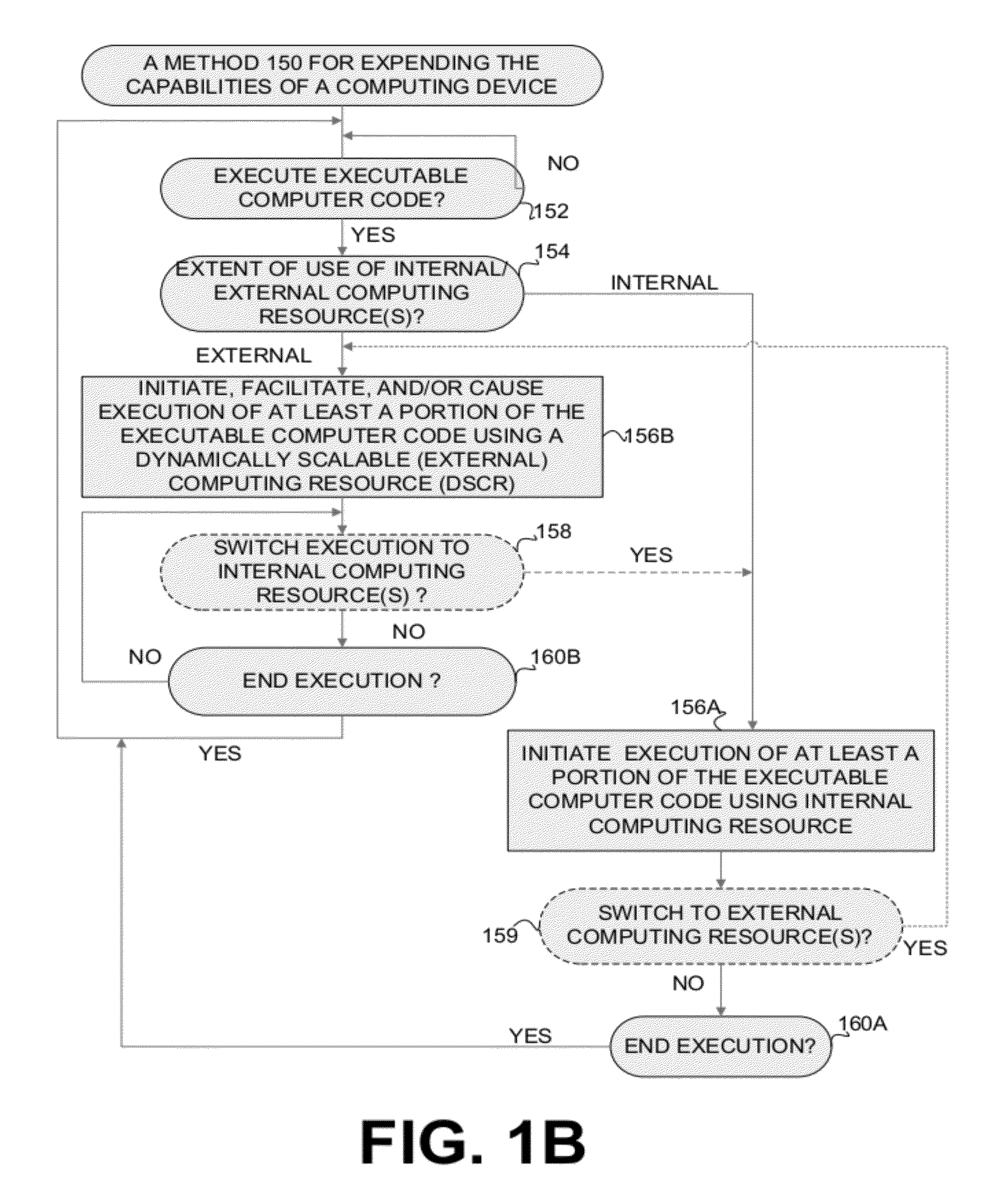
Execution allocation cost assessment for computing systems and environments including elastic computing systems and environments
InactiveUS8239538B2Limited and reduced computing resourceEfficiently provideEnergy efficient ICTDigital computer detailsService provisionResource Provider
Techniques for assessing the cost of allocation of execution and affecting the allocation of execution are disclosed. The cost of allocation of execution to or between a first computing device (e.g., a mobile device) and one or more computing resource providers (e.g., one or more Clouds) can be determined during runtime of the executable code. It will be appreciated that a computing system can operate independently of the first computing device and one or more computing resource providers and provide execution allocation cost assessment as a service to the first computing device and / or one or more computing resource providers. Execution allocation cost can be assessed (or determined) based on execution allocation data pertaining to the first computing device and / or one or more computing resource providers. By way of example, power consumption of a mobile device can be used as a factor in determining how to allocate individual components of an application program (e.g., weblets) between a mobile phone and a Cloud. The invention is especially suited for Elastic computing environment and systems. In an Elastic computing environment, scalable and dynamic external computing resources can be used in order to effectively extend the computing capabilities beyond that which can be provided by internal computing resources of a computing system or environment.
Owner:SAMSUNG ELECTRONICS CO LTD
Method, device and system for realizing resource sharing
ActiveCN101771532AAvoid visitingKey distribution for secure communicationData switching networksResource informationInformation access
Owner:HUAWEI TECH CO LTD
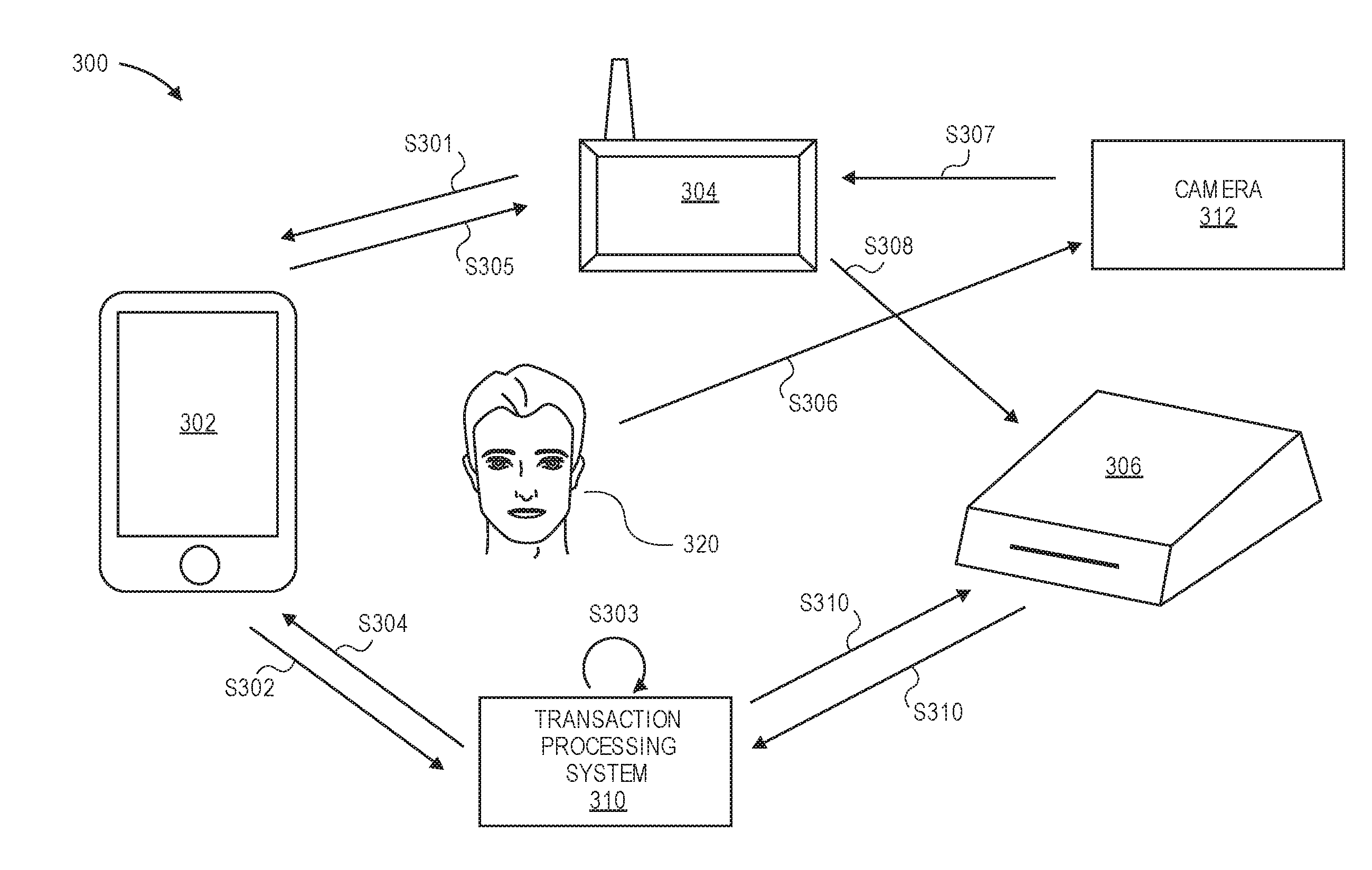
Multi-device transaction verification
ActiveUS20160277380A1Accurately determinedExtension of timeTransmissionSecurity arrangementFinancial transactionResource Provider
When a user enters a resource provider location with a portable communication device, the portable communication device provides an indication to a transaction processing system that the portable communication device is currently at the resource provider location. At a later time when the user conducts a transaction with a portable transaction device, the fact that the user's portable communication device had been detected at the resource provider a short time ago is taken into account as a positive indicator that the transaction is not fraudulent. By verifying that both the portable communication device and the portable transaction device are present at the resource provider, the risk of approving a fraudulent transaction from a stolen portable transaction device can be reduced.
Owner:VISA INT SERVICE ASSOC
Transferring Language of Communication Information
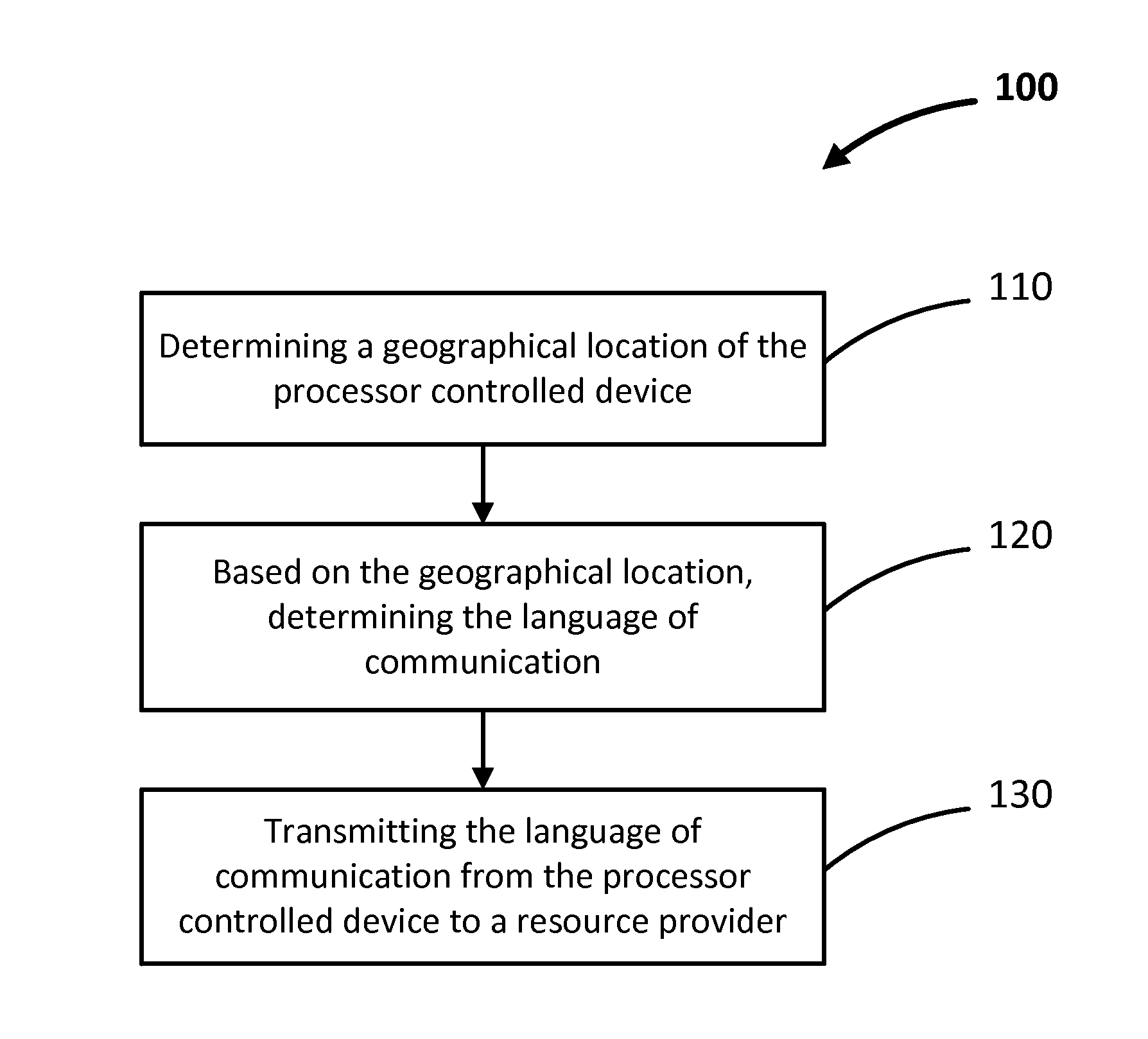
InactiveUS20140180671A1Natural language data processingSpeech recognitionTelecommunicationsGeolocation
The invention provides a method of determining a language of communication from a processor controlled device. In one case, the language of communication is derived from language of communication information retrieved from the processor controlled device, such as, for example, GPS information. In one implementation, the method includes: determining a geographical location of the processor controlled device; determining the language of communication based on the geographical location information; and transmitting the language of communication from the processor controlled device to a resource provider. Resources from the resource provider are received by the processor controlled device in the language of communication of the processor controlled device.
Owner:ABBYY PRODUCTION LLC
System, method and software for managing and publishing resource availability data
A system, method and software permitting the publication of resource availability information and the management of reservation requests therefor are provided. In an exemplary embodiment, a resource provider provides authorization, availability, descriptive, linking and criteria information for a resource available for reservation presented on a publicly accessible web site. Users permitted to access to the data can browse and search the published resource related data and request appointments with or reservations of the listed resources. Resource providers are permitted to actively or automatically manage reservations and appointments requesting their resources. Available on a publicly accessible web site, resource providers may also control and define access limitations for various groups of viewers.
Owner:CISCO TECH INC
Controlled resource provisioning in distributed computing environments
ActiveUS20180225611A1Alleviate challengeDatabase distribution/replicationComputer security arrangementsDistributed Computing EnvironmentResource consumption
A computer implemented method to provide allocation of one or more computing resources for a consumer computing component, each resource having a resource type and being provided by one or more resource providers, and the consumer having associated a quantity of tradeable value constraining an extent of resource consumption.
Owner:BRITISH TELECOMM PLC
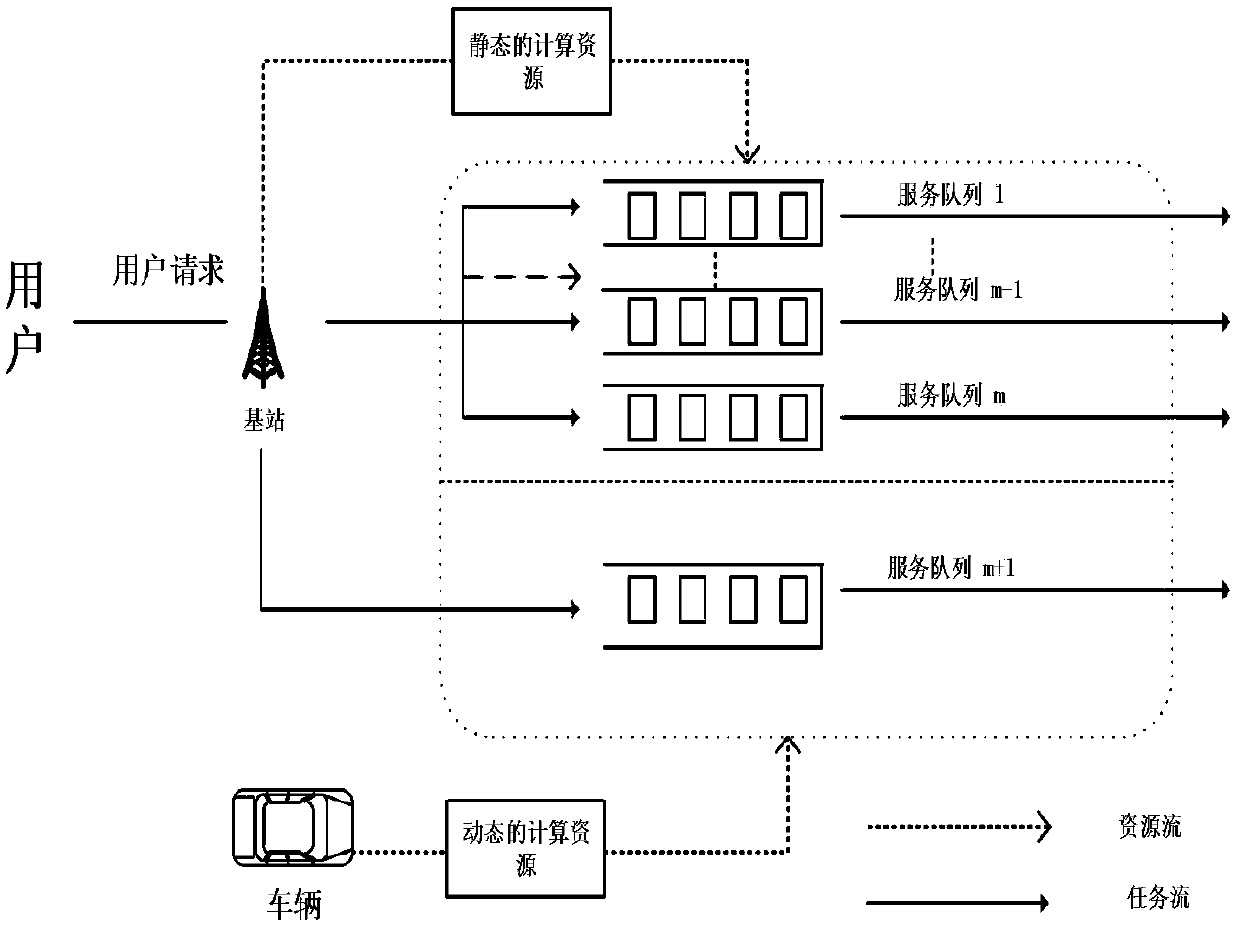
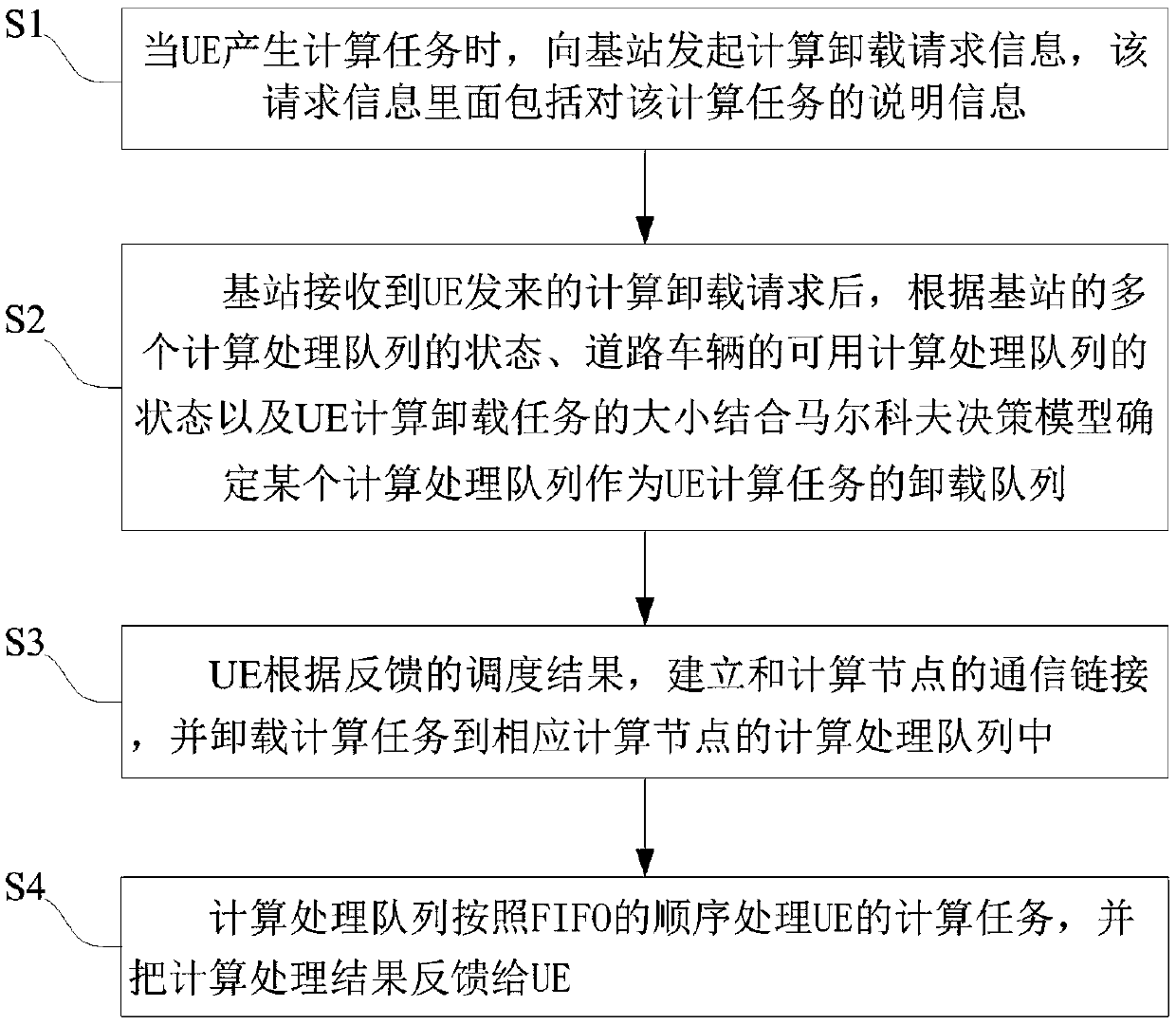
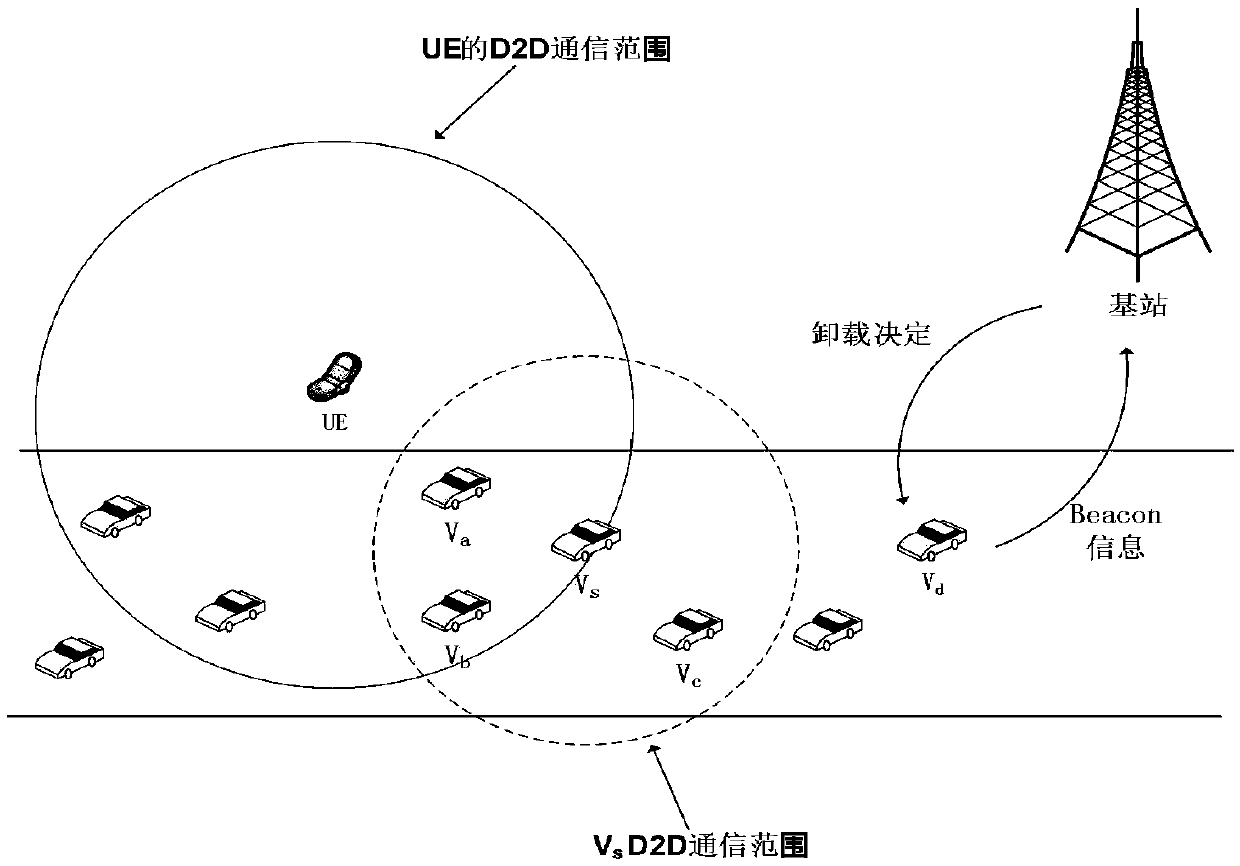
Vehicle networking oriented computing task unloading method
ActiveCN109067842AIncrease incomeGuaranteed Latency RequirementsProgram initiation/switchingParticular environment based servicesMathematical modelTime delays
The invention discloses a vehicle networking oriented computing task unloading method. In order to improve the benefit of computing resource providers during computing task unloading and to ensure thecompletion delay of computing tasks to a certain extent, the invention provides an unloading scheme for the computing tasks of the roadside UE by adopting the computing resources of the base stationside MEC server and the computing resources of the road traveling vehiclethe communication delay of the task, the computing time delay and the computing processing queue processing rate and queue length are taken into the decision-making reference factors, the mathematical model of Markov decision is used to analyze the change of the state, and the depth learning algorithm is used to obtain an optimal strategy space, that is, the corresponding state adopts the corresponding behavior, which maximizes the revenue of the resource provider and ensures the time delay requirement of the user's computing task to a certain extent.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
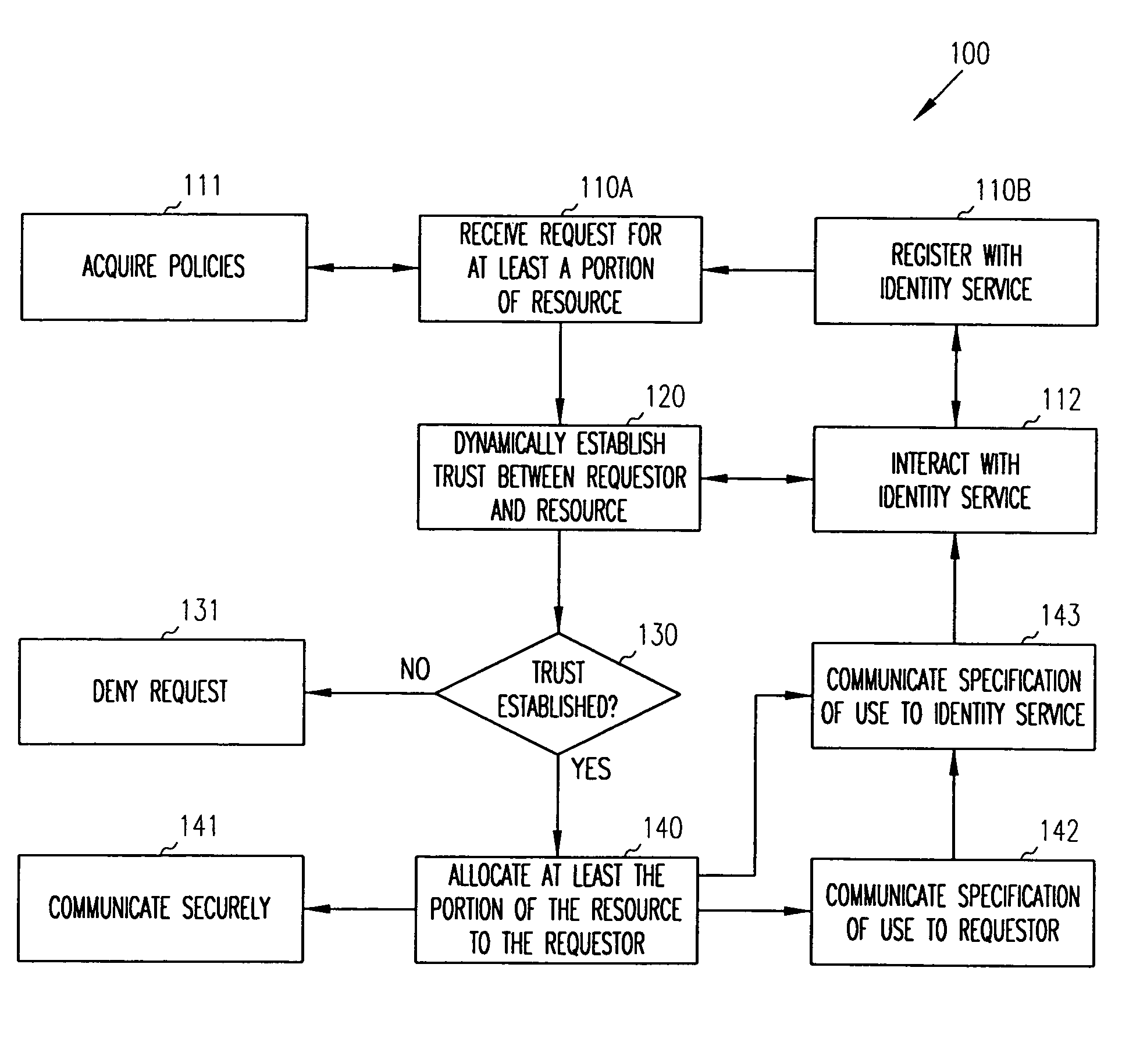
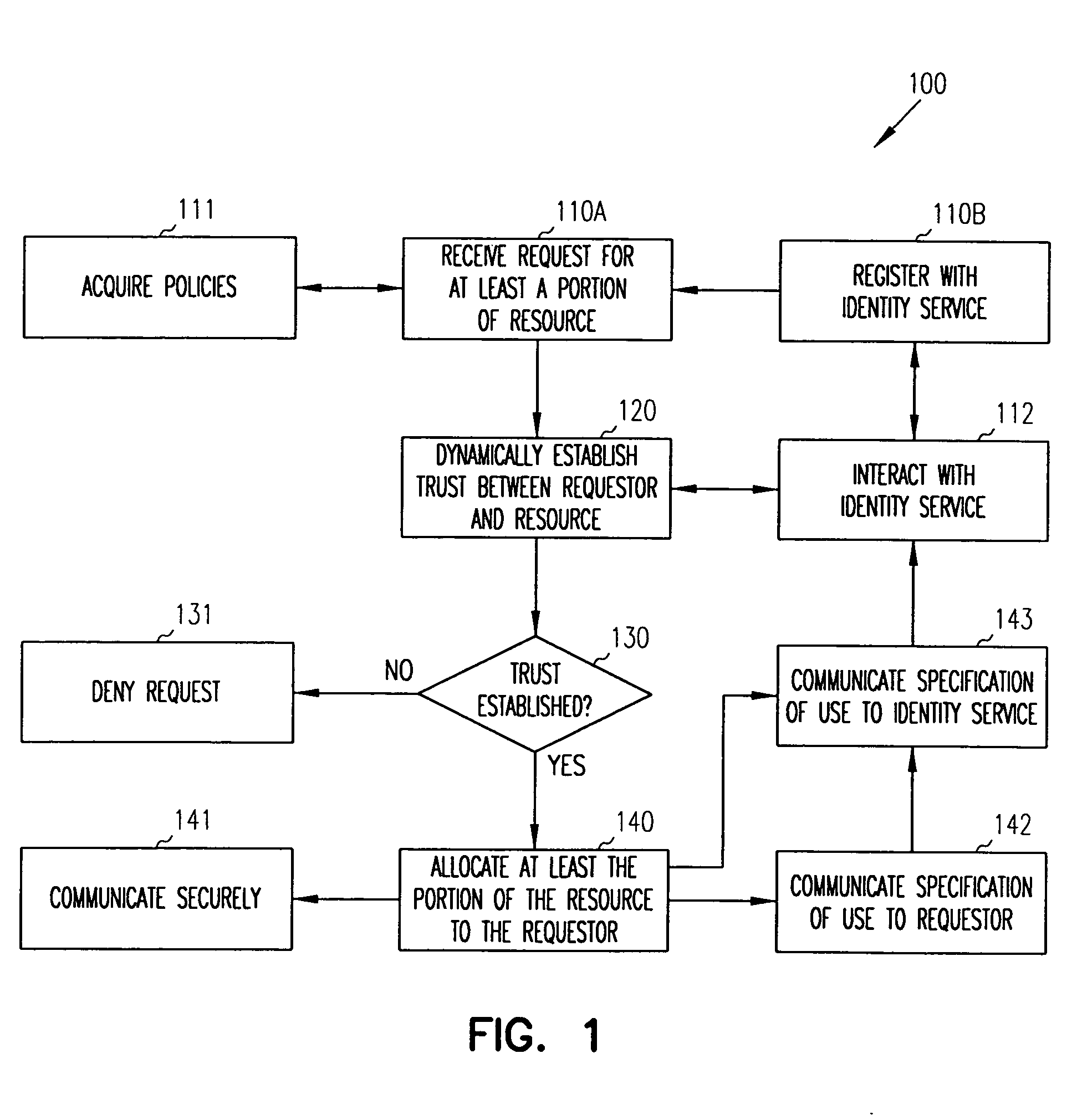
Allocation of network resources
ActiveUS20060059565A1Resource allocationDigital data processing detailsResource ProviderResource use
Techniques are provided for allocating resources over a network. A resource consumer requests access to a resource over a network. As part of that request, the resource consumer acquires information that permits it to securely communicate with a resource provider. The resource provider controls the resource and once satisfied with the security of a request from a resource consumer allocates the resource for access by the resource consumer.
Owner:ORACLE INT CORP
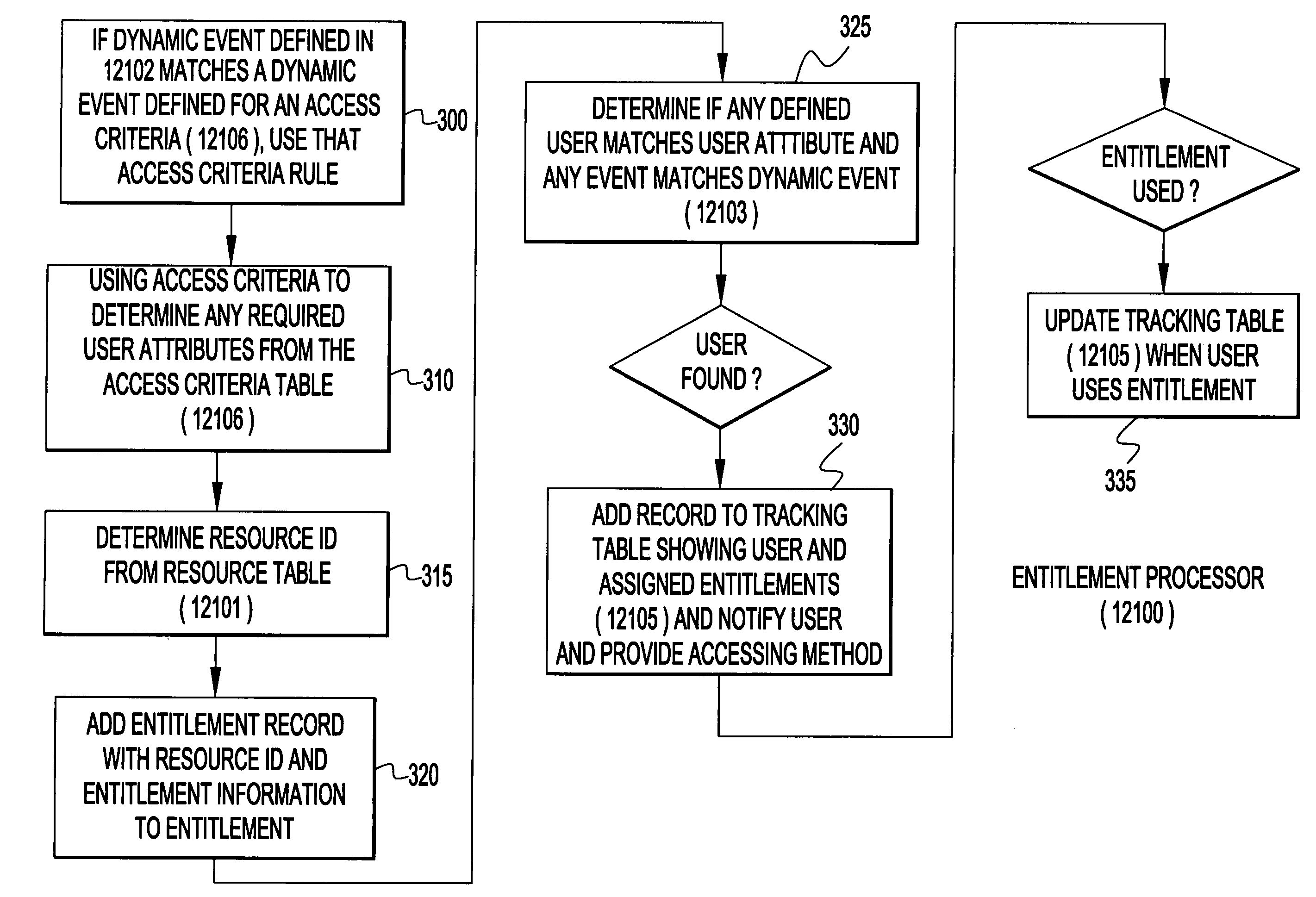
System, method, service method, and program product for managing entitlement with identity and privacy applications for electronic commerce
ActiveUS7549054B2Digital data processing detailsComputer security arrangementsE-commerceResource Provider
A system, method, service method, and program product for defining and / or managing entitlements and / or authentication entitlements to resources in a computer networking environment is disclosed. Upon receiving one or more dynamic events, the invention verifies one or more users (a selected user) has (entitlement) attributes that satisfy one or more access criteria to access one or more resources. The invention then permits and / or provides access to one or more resources for the selected user over one or more networks without revealing the identity of the selected user to the resource provider.
Owner:GOOGLE LLC
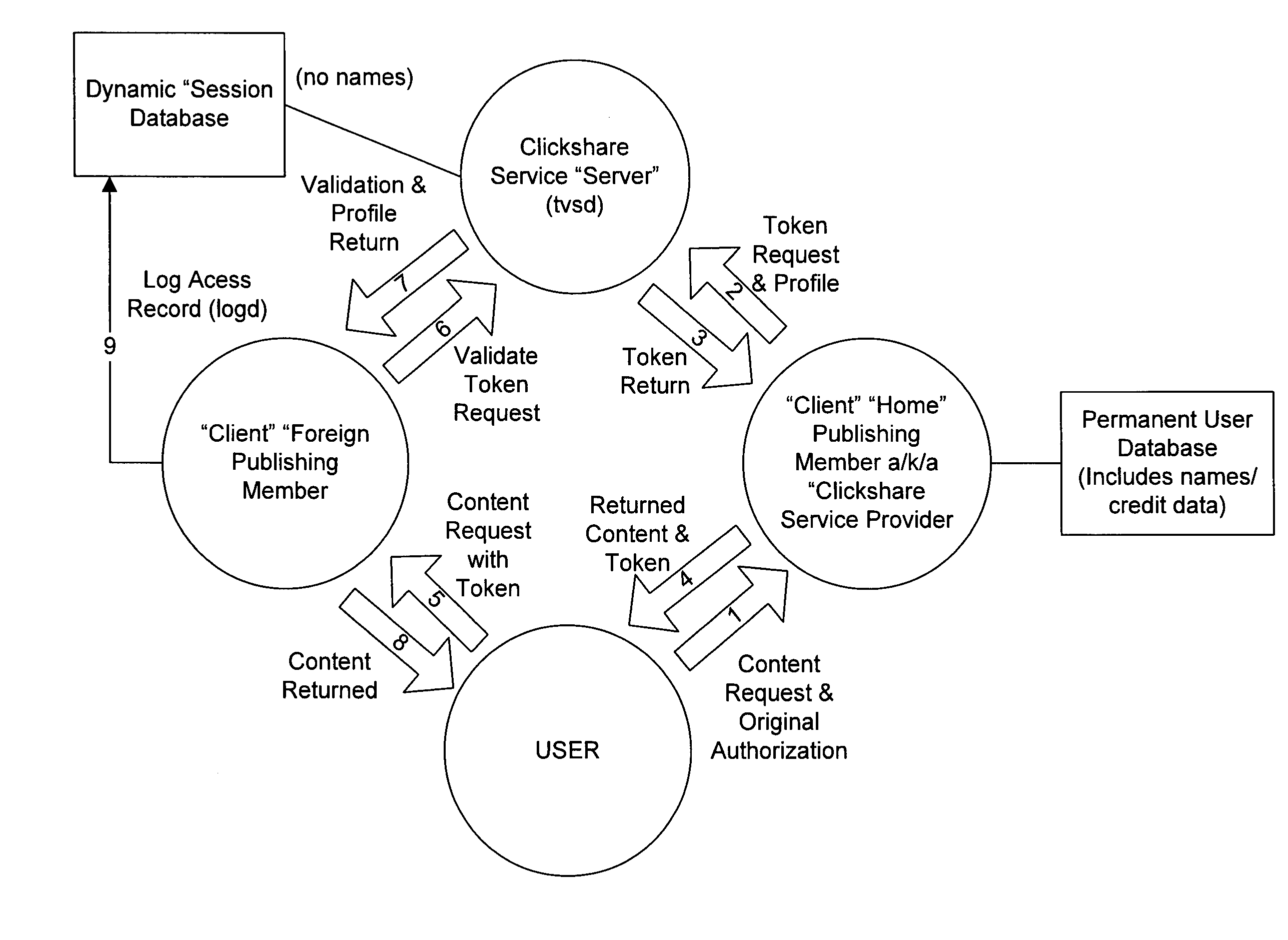
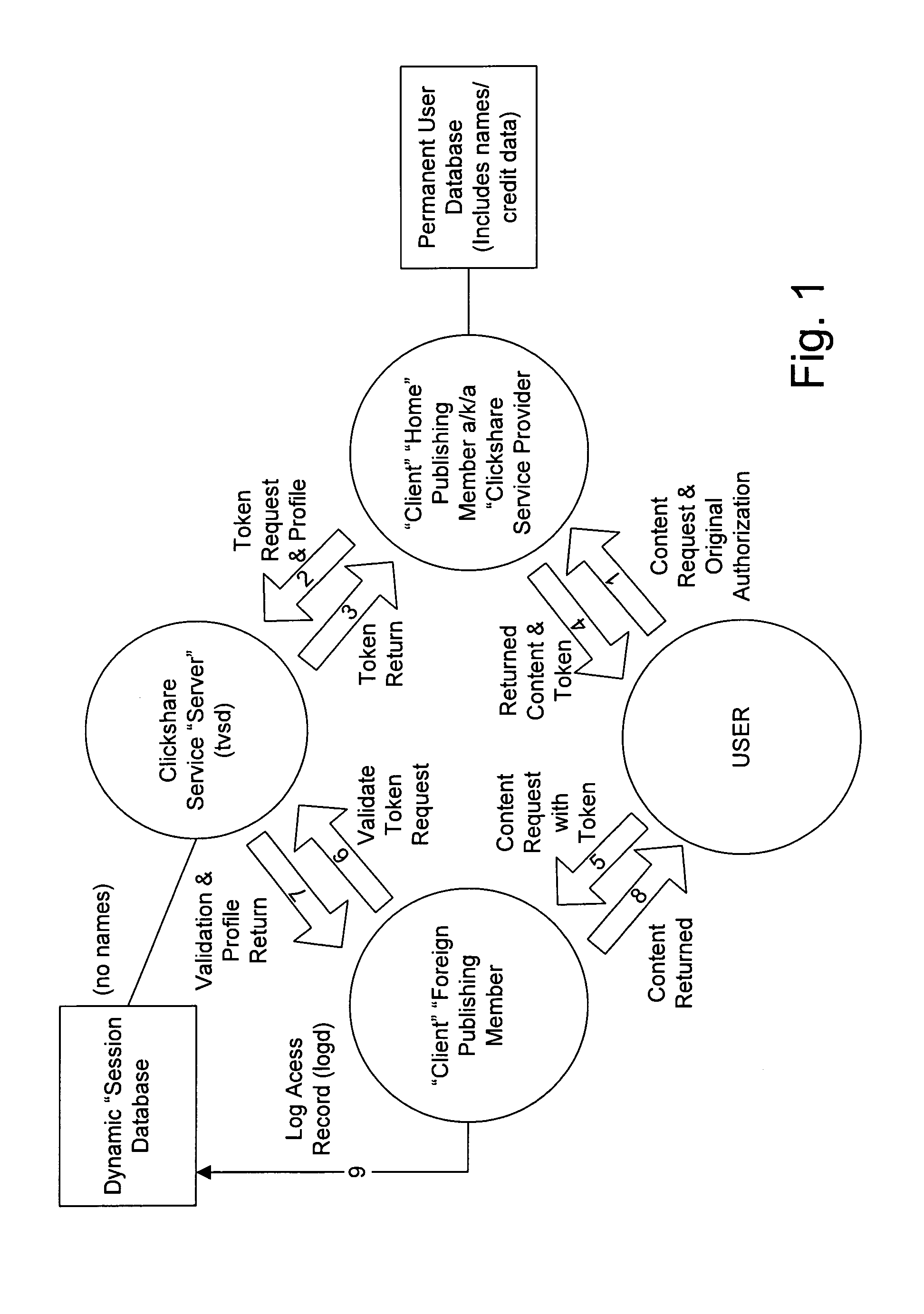
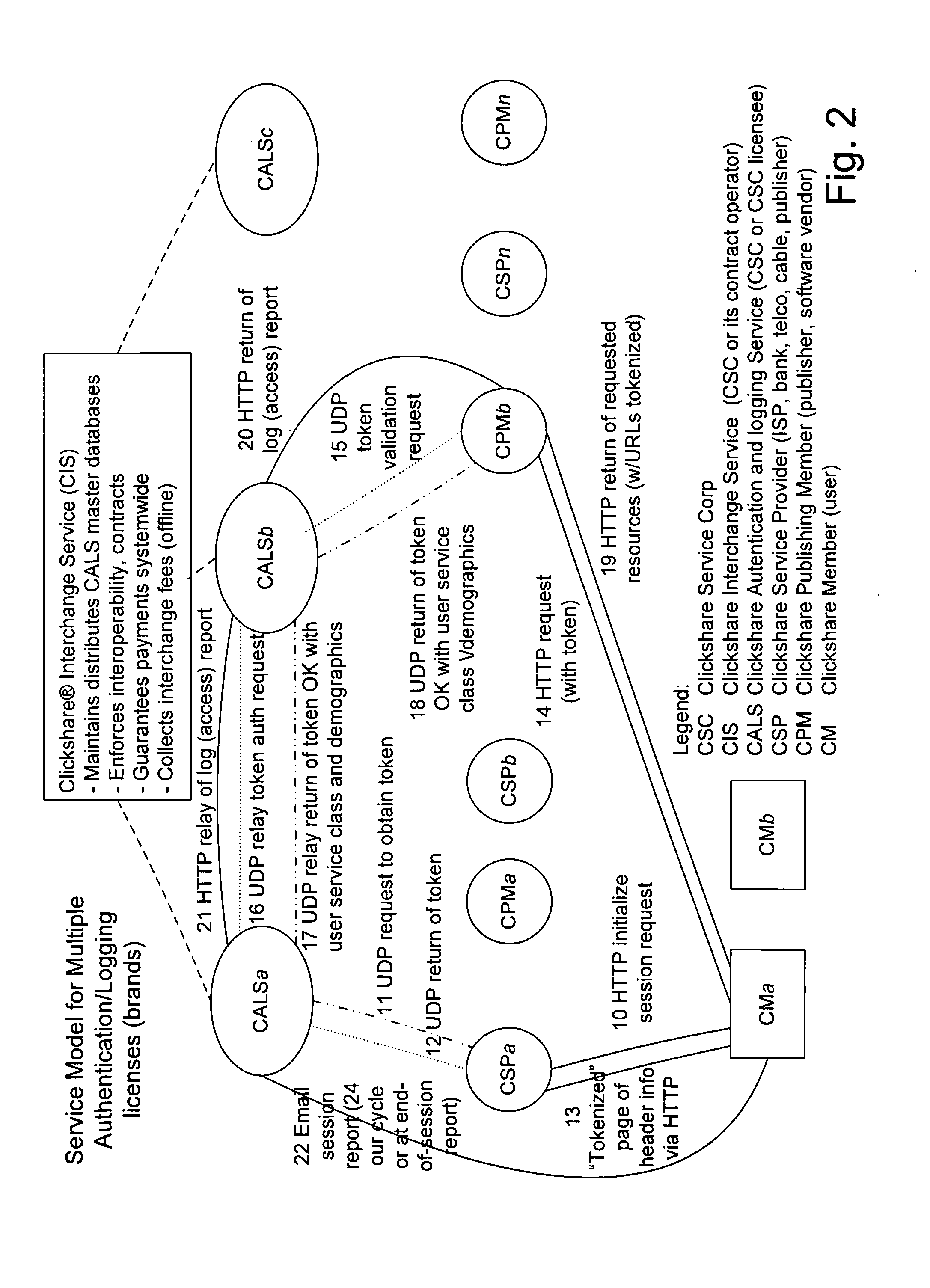
System for management of alternatively priced transactions on network
InactiveUS20080183628A1Improve scalabilityTransparent to userComplete banking machinesFinanceEngineeringFinancial transaction
Owner:CLICKSHARE SERVICE
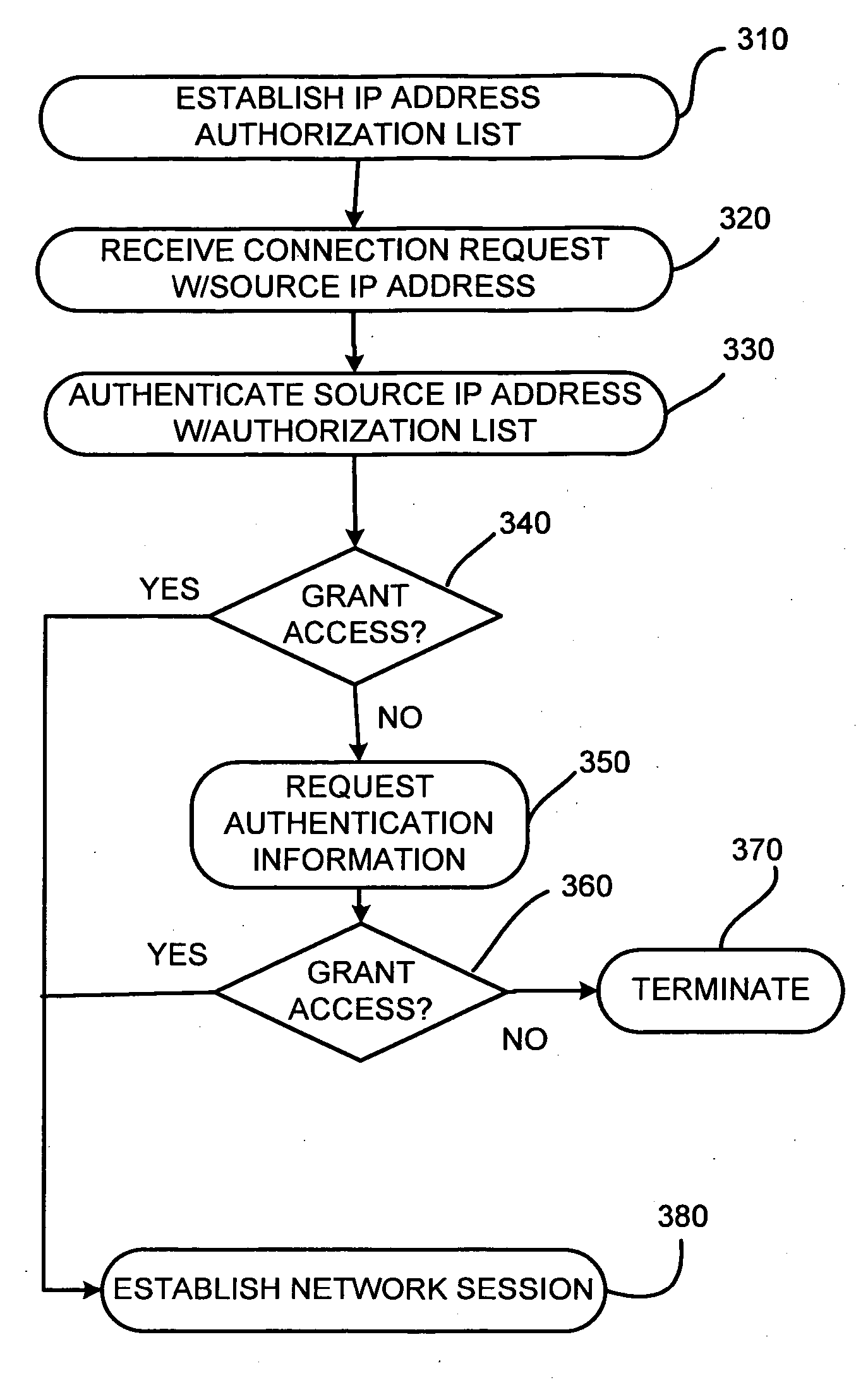
Preventing fraudulent internet account access
A method and system for authenticating requests for accessing network resources are described. Network address information may be associated with a network resource user. An authenticator may maintain the associated network address information. The authenticator may receive, from a requesting party, a request to authenticate the network resource user, where the request may include a network address identifier. The network resource user may be authenticated based on the network address information and the network address identifier. The authentication determination may be forwarded to the requesting party for purposes of controlling access to a network resource of a network resource provider in response to an access request made by the network resource user.
Owner:VERIZON PATENT & LICENSING INC
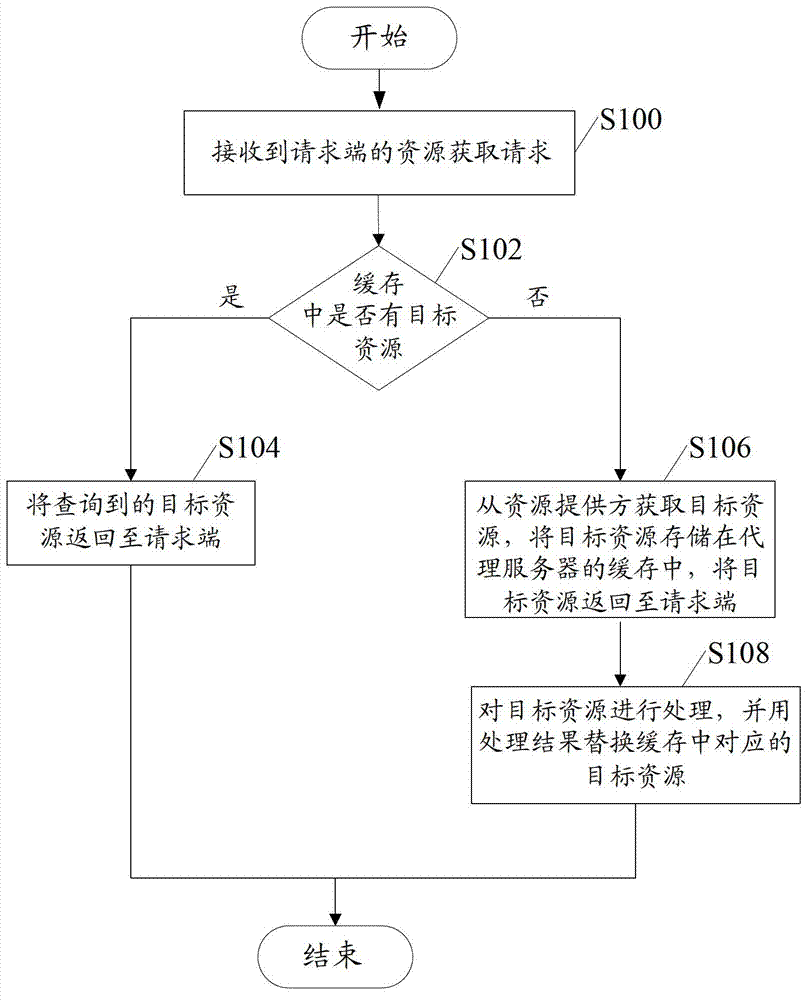
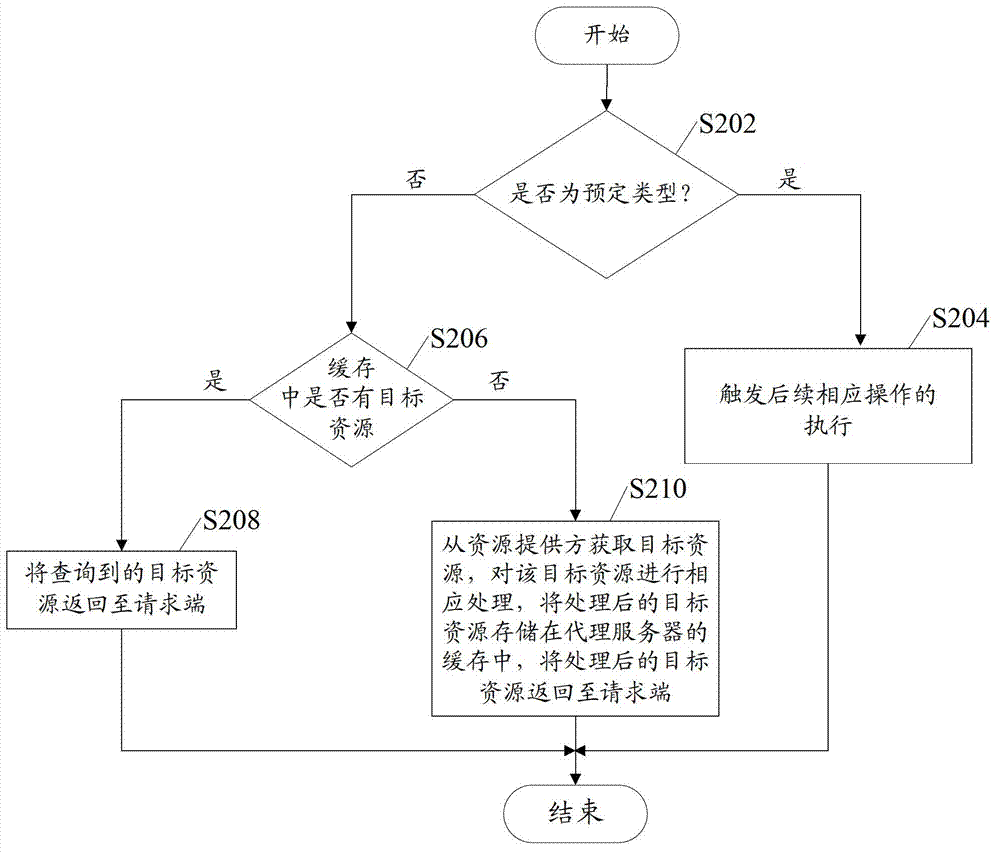
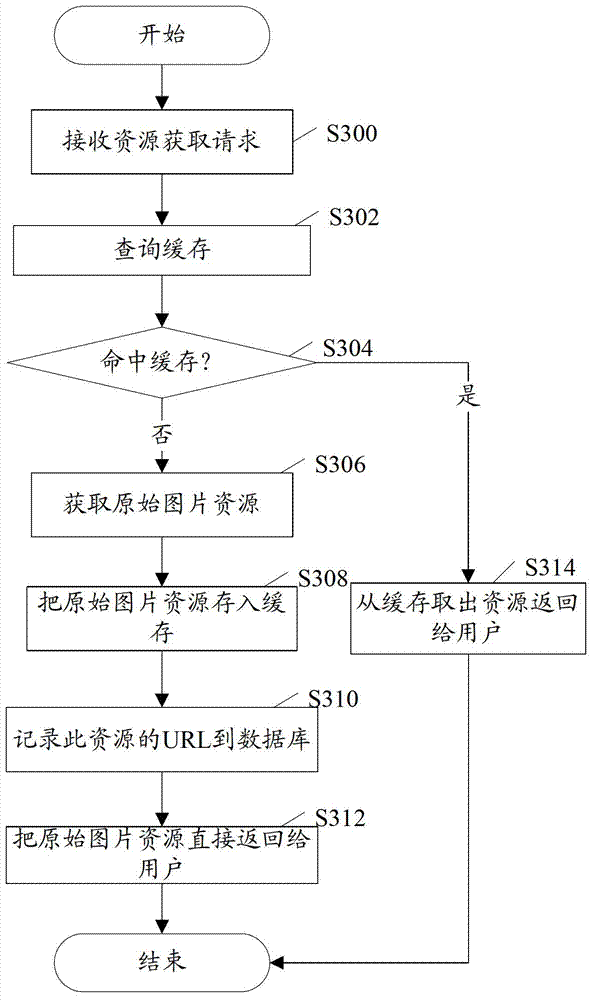
Resource acquiring method and device on Internet
The invention discloses a resource acquiring method and device on the Internet. The resource acquiring method on the Internet, provided by the embodiment of the invention, comprises the following steps: inquiring whether requested target resources exist in the cache of a proxy server according to a resource acquiring request when the resource acquiring request of a request end is received; returning the inquired target resources to the request end when the requested target resources exist in the cache, acquiring the target resources from a resource provider when the requested target resources do not exist in the cache, storing the target resources in the cache of the proxy server, and returning the acquired target resources to the request end; and processing the target resources acquired from the resource provider accordingly and replacing the corresponding target resources in the cache with the processing results.
Owner:BEIJING QIHOO TECH CO LTD
Seed enquiring method of P2P system and P2P server
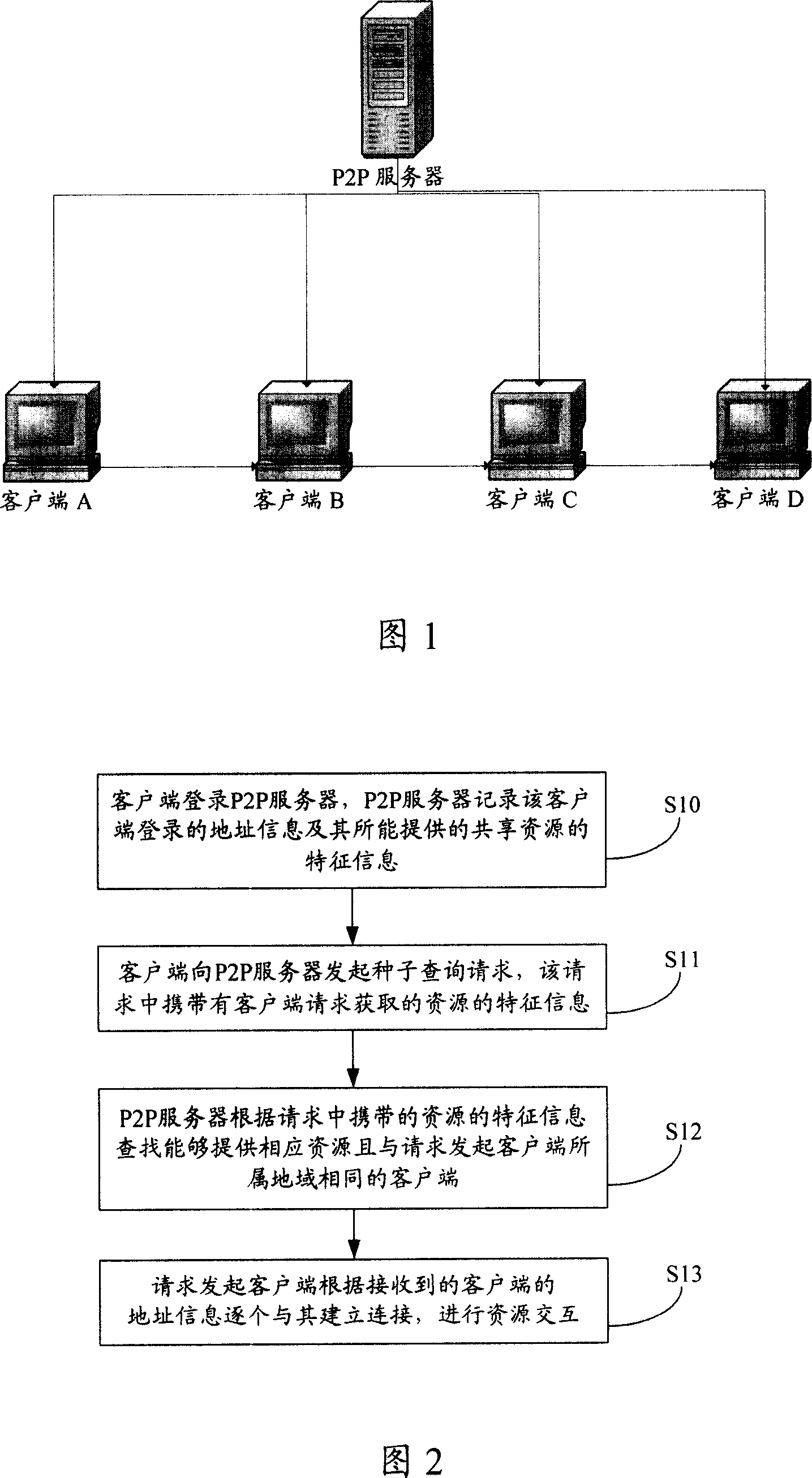
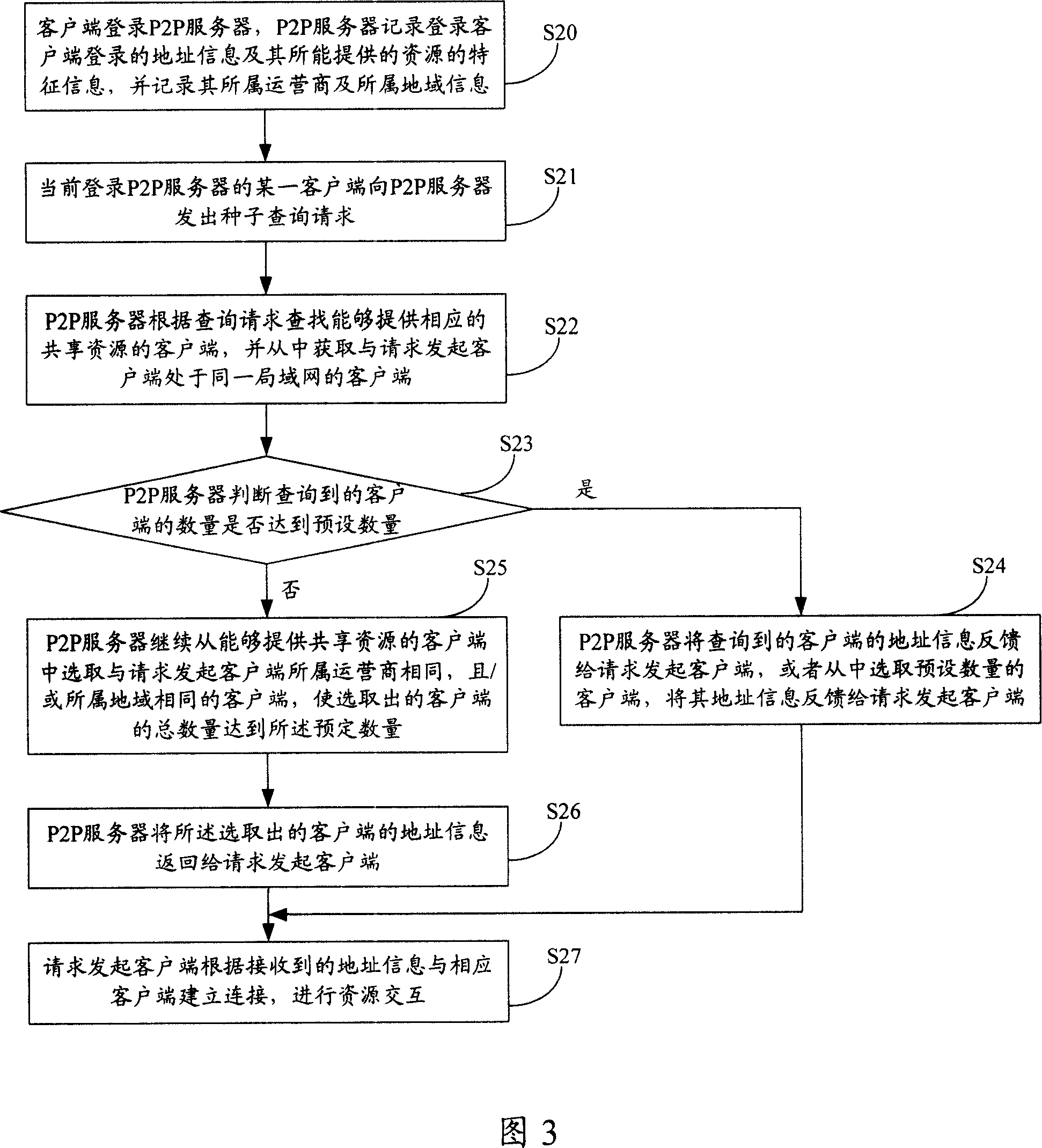
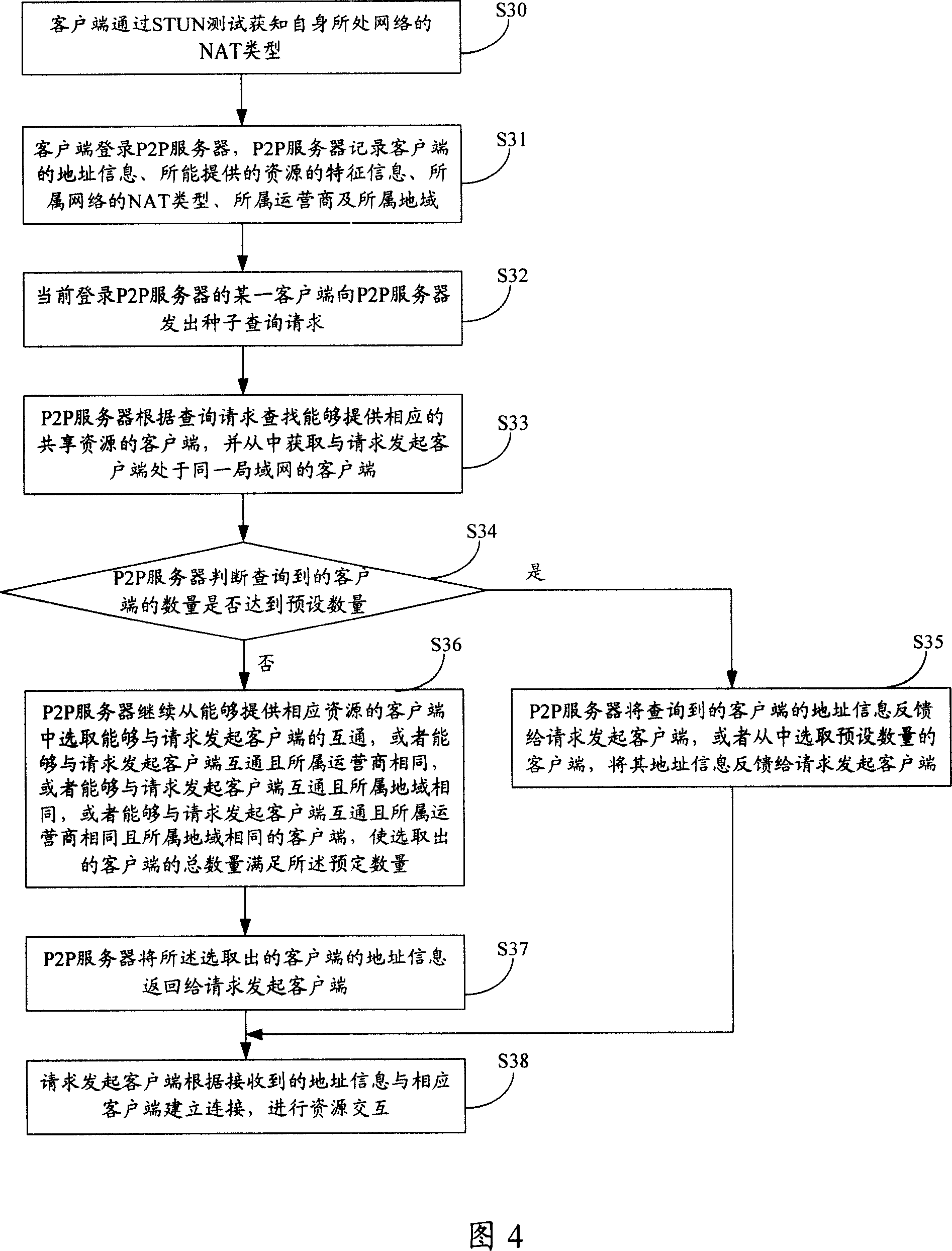
InactiveCN101098272AFast data transferResource interaction effect is goodNetworks interconnectionInformation findingResource Provider
The invention discloses a seed inquire method and a relative P2P server in P2P system, for resolving the problem of prior art which P2P server can only select, inquire and request the client with same domain of initial client from the resource provider when in seed inquire. The method comprises that client initializes seed inquire request to a P2P server, while the request carries the character information of the resource requested by the client, the P2P server according to the character information searches the address of the client which can provide relative share resource, in same local network of the initialize client, to be feedback to the initialize client, the initialize client according to received address builds connection with relative client, to intercommunicate resource. The P2P server comprise a memory unit, a seed inquire unit, and a seed information provider. The invention can improve resource intercommunication between clients in P2P system.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com