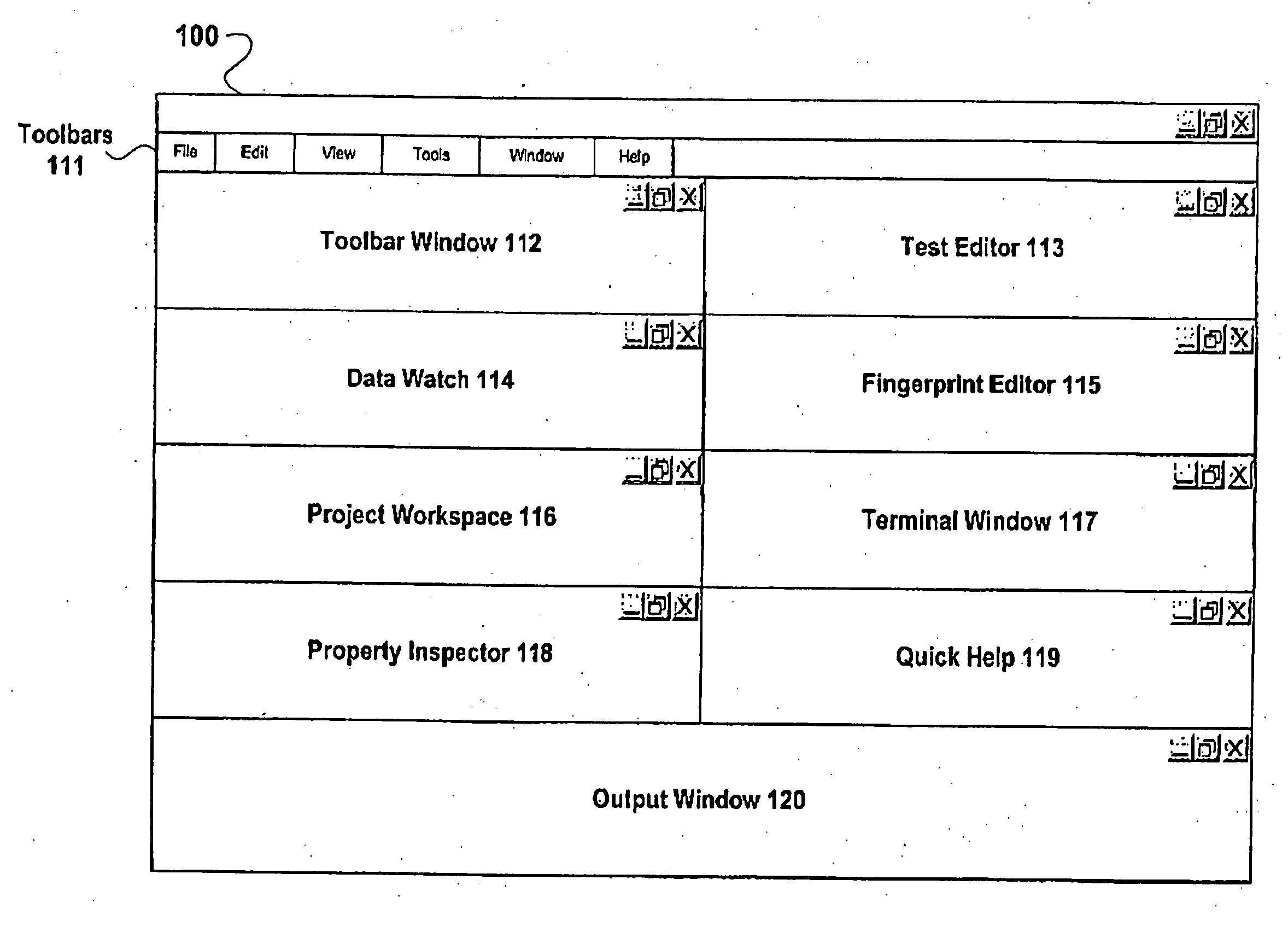
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1476 results about "Information access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information access is the freedom or ability to identify, obtain and make use of database or information effectively. There are various research efforts in information access for which the objective is to simplify and make it more effective for human users to access and further process large and unwieldy amounts of data and information.
Secure data interchange
InactiveUS20090254971A1Improve privacyLimited accessDigital data processing detailsAnalogue secracy/subscription systemsInformation accessData interchange
A secure data interchange system enables information about bilateral and multilateral interactions between multiple persistent parties to be exchanged and leveraged within an environment that uses a combination of techniques to control access to information, release of information, and matching of information back to parties. Access to data records can be controlled using an associated price rule. A data owner can specify a price for different types and amounts of information access.
Owner:STRIPE INC
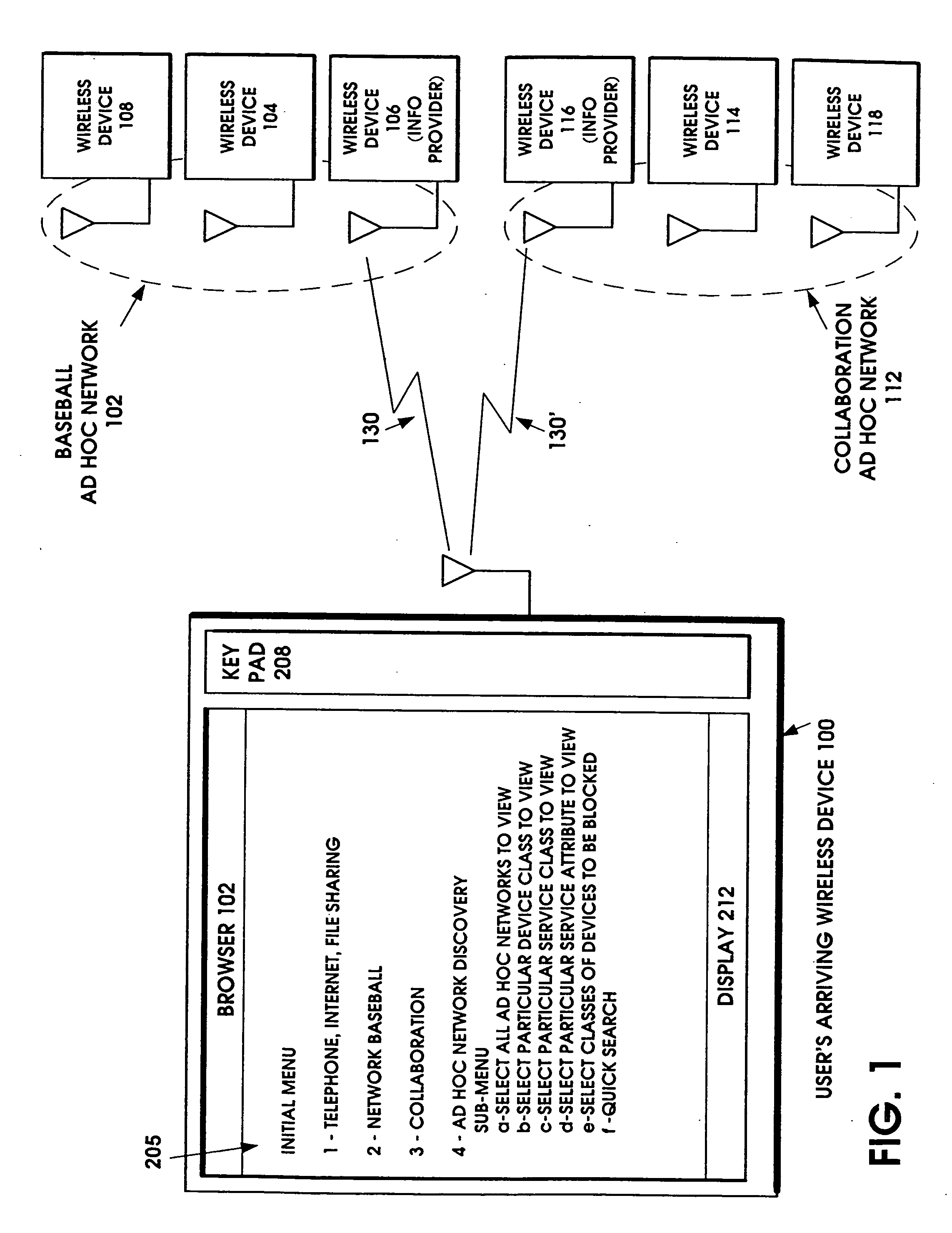
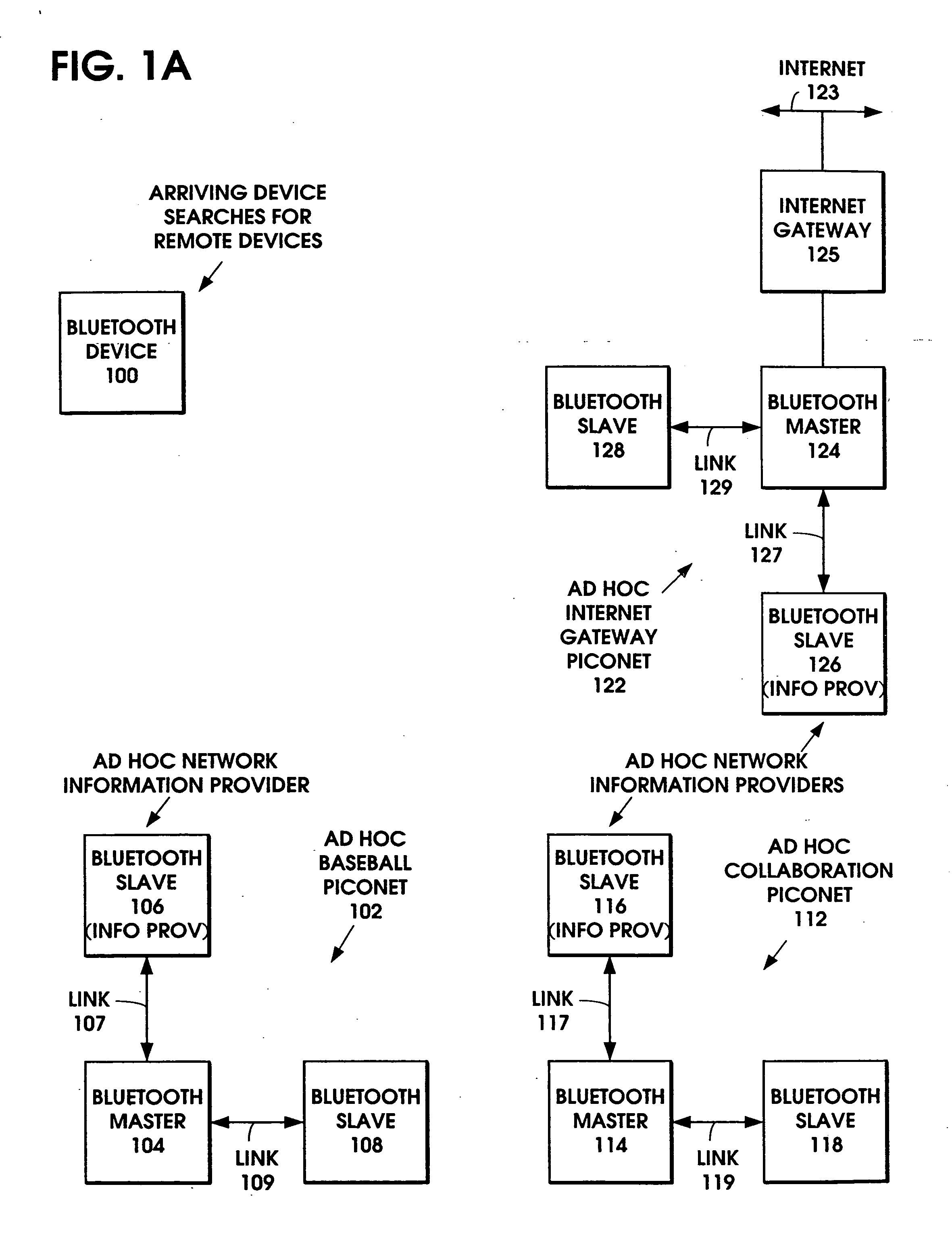
Ad hoc network discovery menu
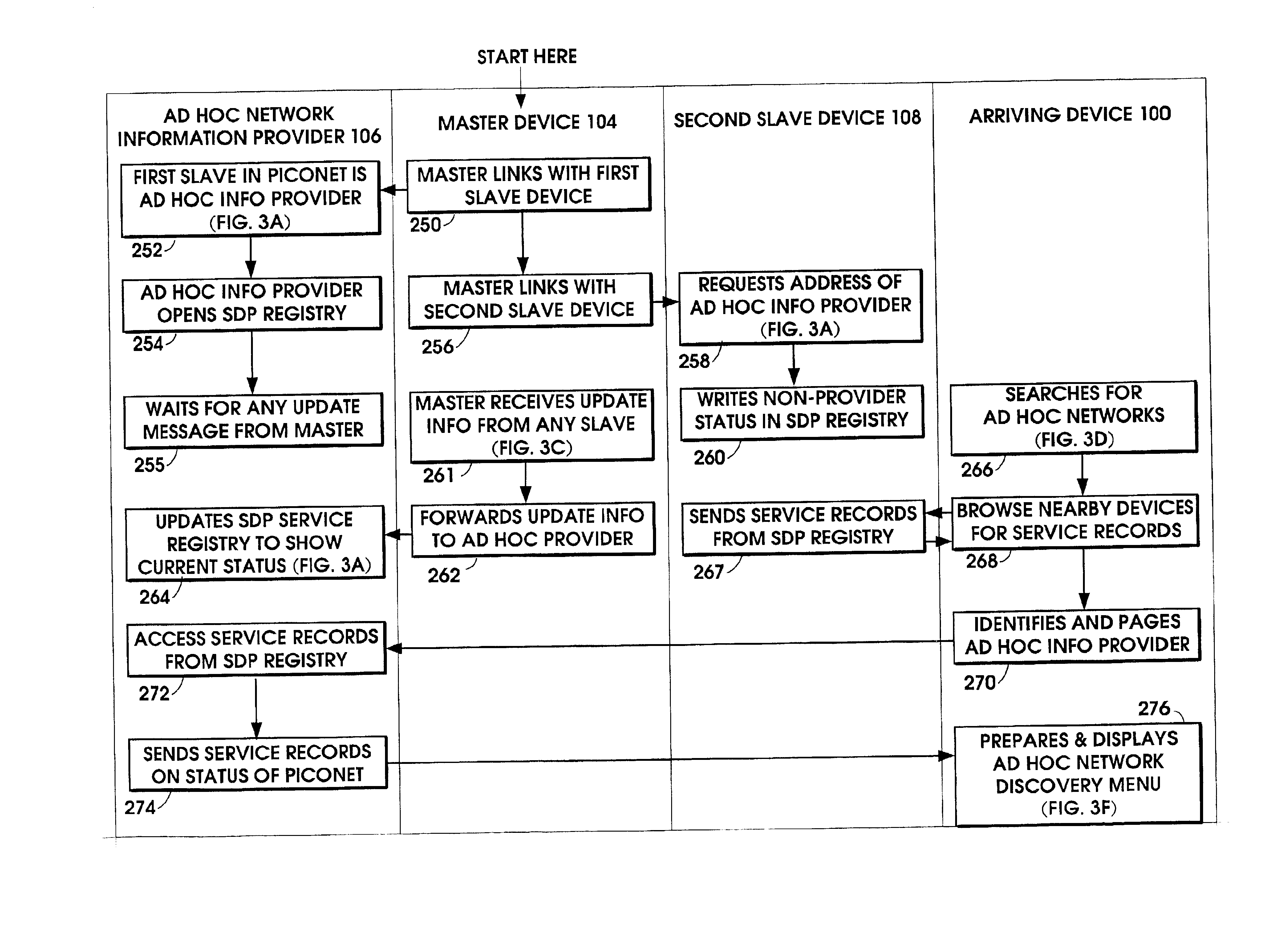
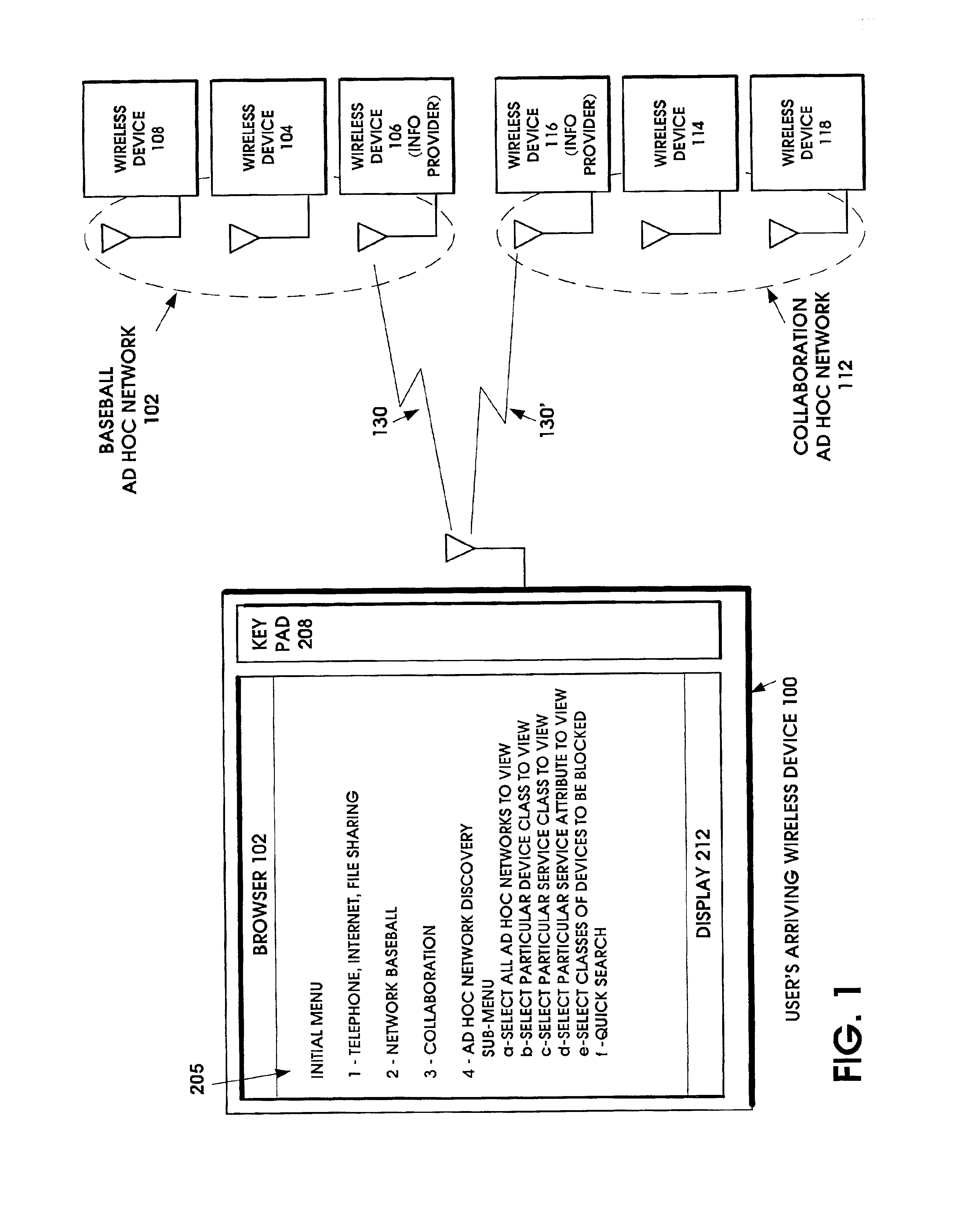
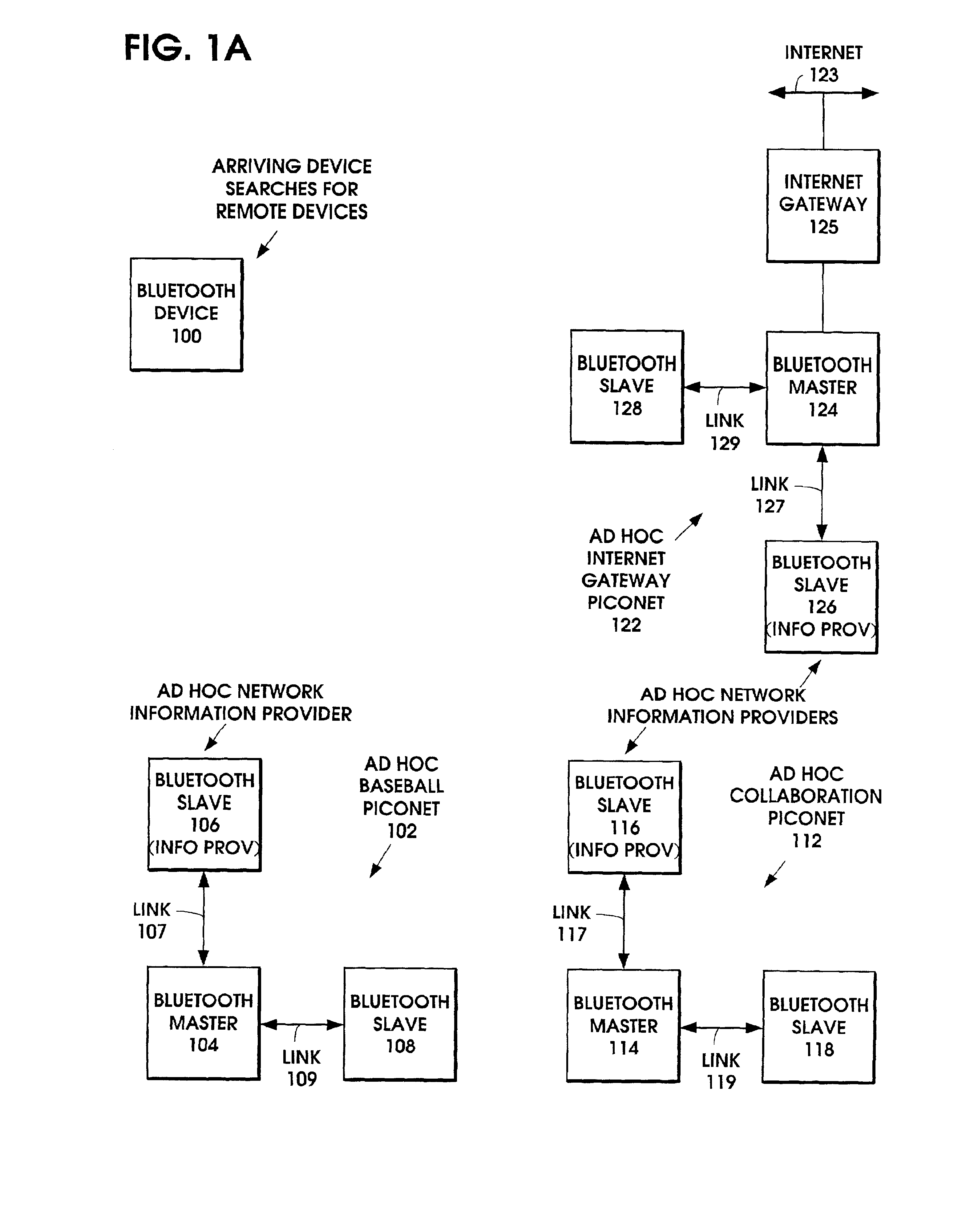
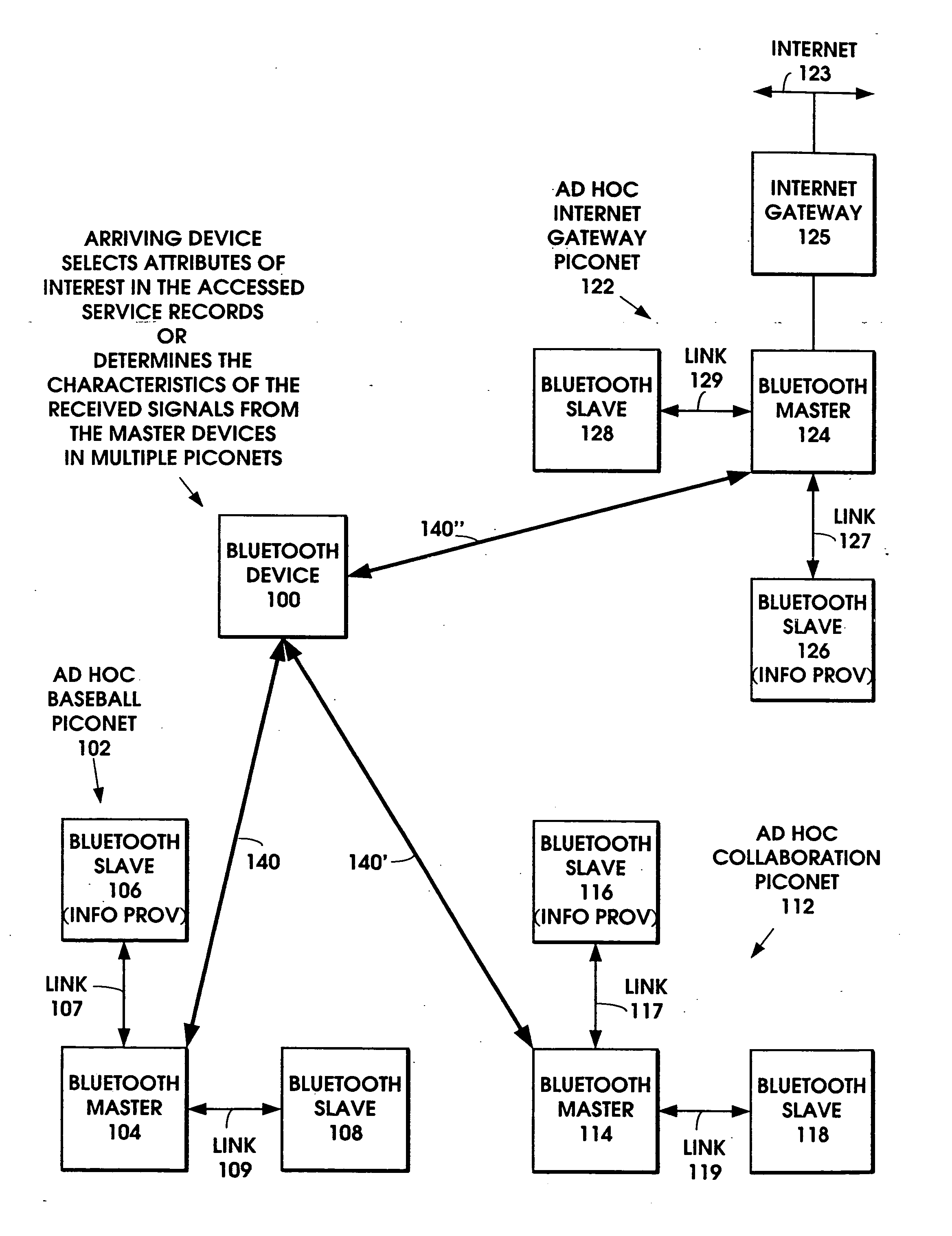
When an ad hoc network is formed between short range wireless devices, at least one device assumes the role of an ad hoc network information provider for the new piconet. In this role, the device allocates a browsing hierarchy of service classes in its service registry. The service classes will provide a record to characterize the ad hoc network. When a new wireless device arrives within the communication range of any member of the ad hoc network, its inquiry signals are answered by the first member detecting the inquiry. If that first member is an ad hoc network information provider, it responds with information accessed from its service registry characterizing the ad hoc network. If, instead, an ordinary device in the ad hoc network is the first to respond to the inquiry signals of the arriving device, the device responds with the address of the ad hoc network information provider. The arriving device then pages the ad hoc network information provider to obtain information characterizing the ad hoc network.
Owner:NOKIA TECHNOLOGLES OY
Systems and Methods for Providing Levels of Access and Action Control Via an SSL VPN Appliance
ActiveUS20070245409A1Digital data processing detailsUser identity/authority verificationOrganizational controlInformation access
The present invention relates to systems and methods to identify a level of access for a resource being accessed via a secure socket layer virtual private network (SSL VPN) connection to a network, and to control the action on the resource based on the identified level of access. The appliance described herein provides intelligent secure access and action control to resources based on a sense and respond mechanism. When a user requests access to a resource via the SSL VPN connection of the appliance, the appliance obtains information about the client to determine the user access scenario—the location, device, connection and identify of the user or client. Based on the collected information, the appliance responds to the detected user scenario by identifying a level of access to the resource for the user / client, such as rights to view, print, edit or save a document, Based on the identified level of access, the appliance controls the actions performs on the resource by various techniques described herein so that the user can only perform the allowed action n accordance with the level of access. As such, the present invention allows organization to control and provide the appropriate level of access to valuable, confidential or business critical information accessed remotely or via a pubic network while protecting such information by controlling the types of actions performed or allowed to be performed remotely on the information.
Owner:CITRIX SYST INC
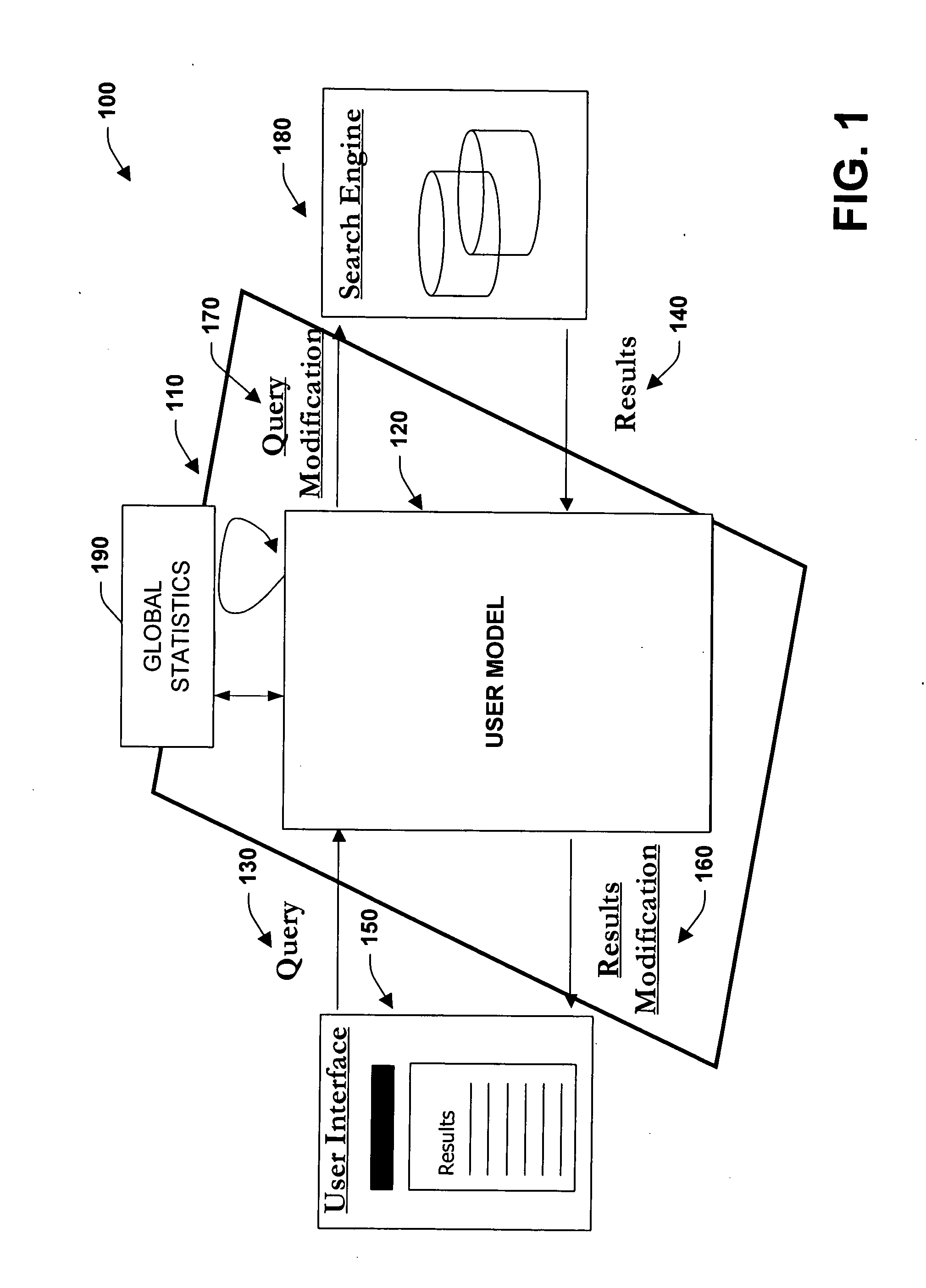
Systems, methods, and interfaces for providing personalized search and information access
InactiveUS20060074883A1Improve personalizationImprove the search experienceDigital data information retrievalSpecial data processing applicationsPersonalized searchInformation access
The present invention relates to systems and methods that employ user models to personalize generalized queries and / or search results according to information that is relevant to respective user characteristics. A system is provided that facilitates generating personalized searches of information. The system includes a user model to determine characteristics of a user. The user model may be assembled automatically via an analysis of a user's content, activities, and overall context. A personalization component automatically modifies queries and / or search results in view of the user model in order to personalize information searches for the user. A user interface receives the queries and displays the search results from one or more local and / or remote search engines, wherein the interface can be adjusted in a range from more personalized searches to more generalized searches.
Owner:MICROSOFT TECH LICENSING LLC
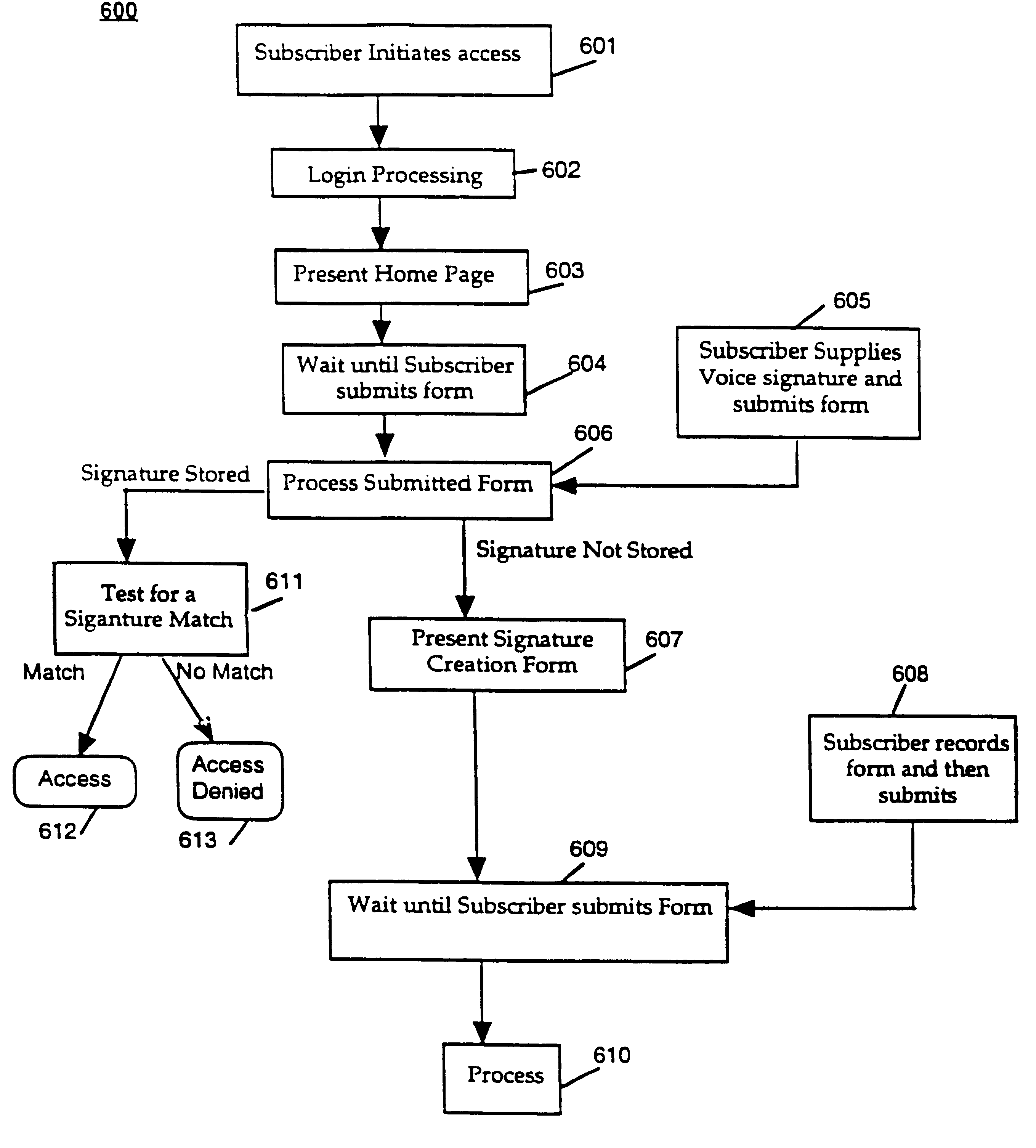
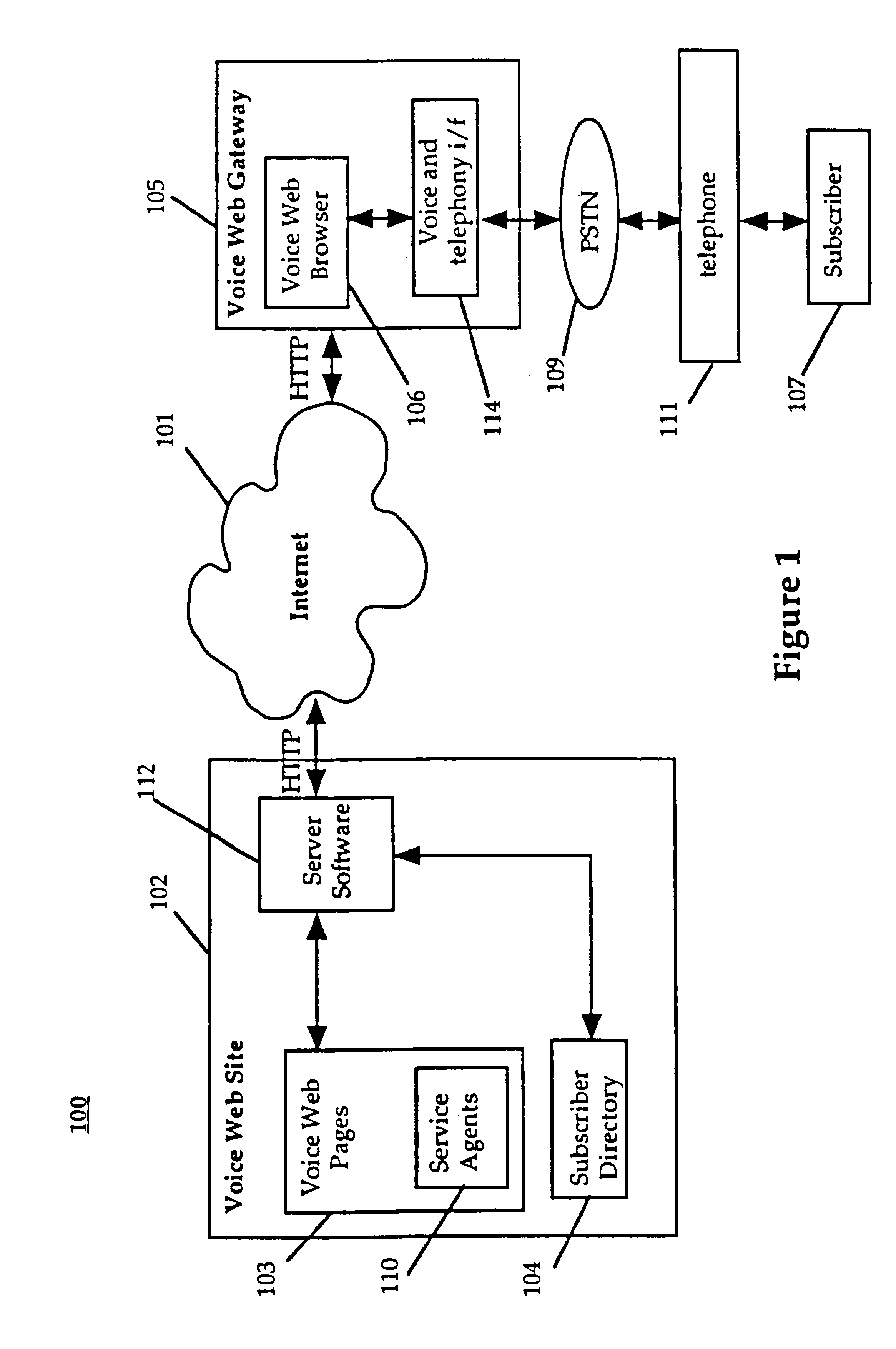
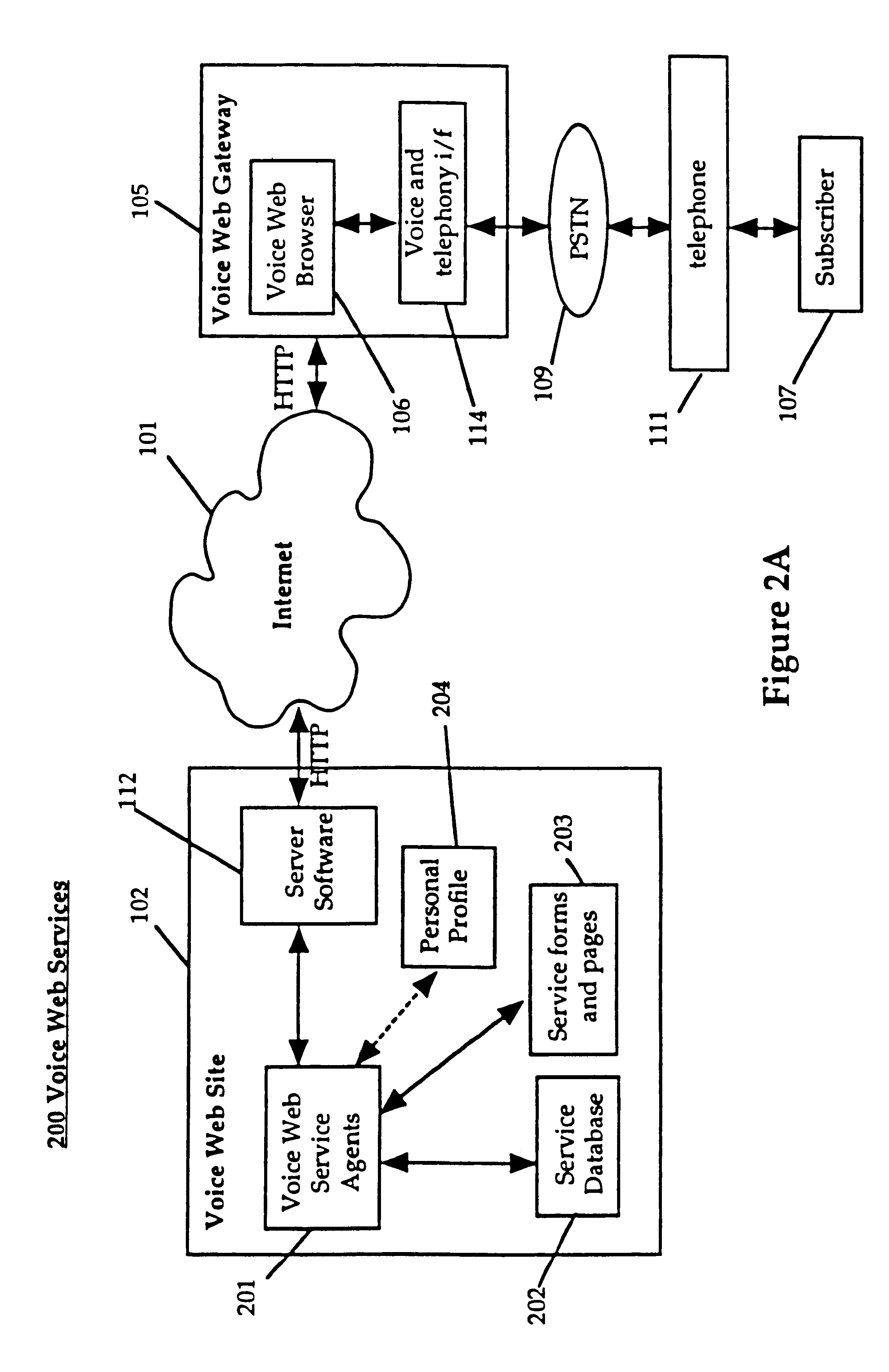
System and method for providing and using universally accessible voice and speech data files
InactiveUS6400806B1Automatic call-answering/message-recording/conversation-recordingAutomatic exchangesSpeech trainingHyperlink
A system and method provides universal access to voice-based documents containing information formatted using MIME and HTML standards using customized extensions for voice information access and navigation. These voice documents are linked using HTML hyper-links that are accessible to subscribers using voice commands, touch-tone inputs and other selection means. These voice documents and components in them are addressable using HTML anchors embedding HTML universal resource locators (URLs) rendering them universally accessible over the Internet. This collection of connected documents forms a voice web. The voice web includes subscriber-specific documents including speech training files for speaker dependent speech recognition, voice print files for authenticating the identity of a user and personal preference and attribute files for customizing other aspects of the system in accordance with a specific subscriber.
Owner:NUANCE COMM INC
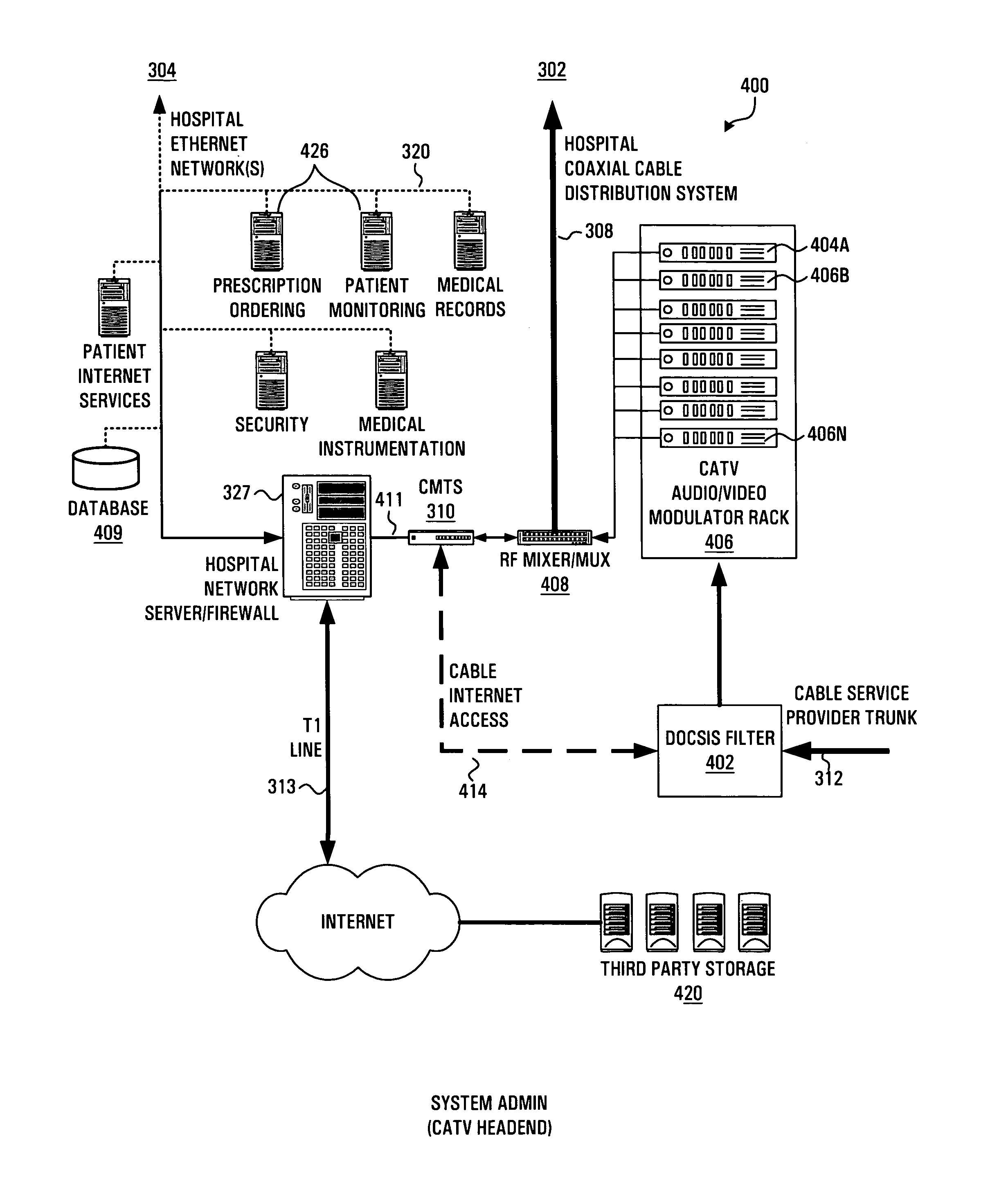
Non-intrusive data transmission network for use in an enterprise facility and method for implementing
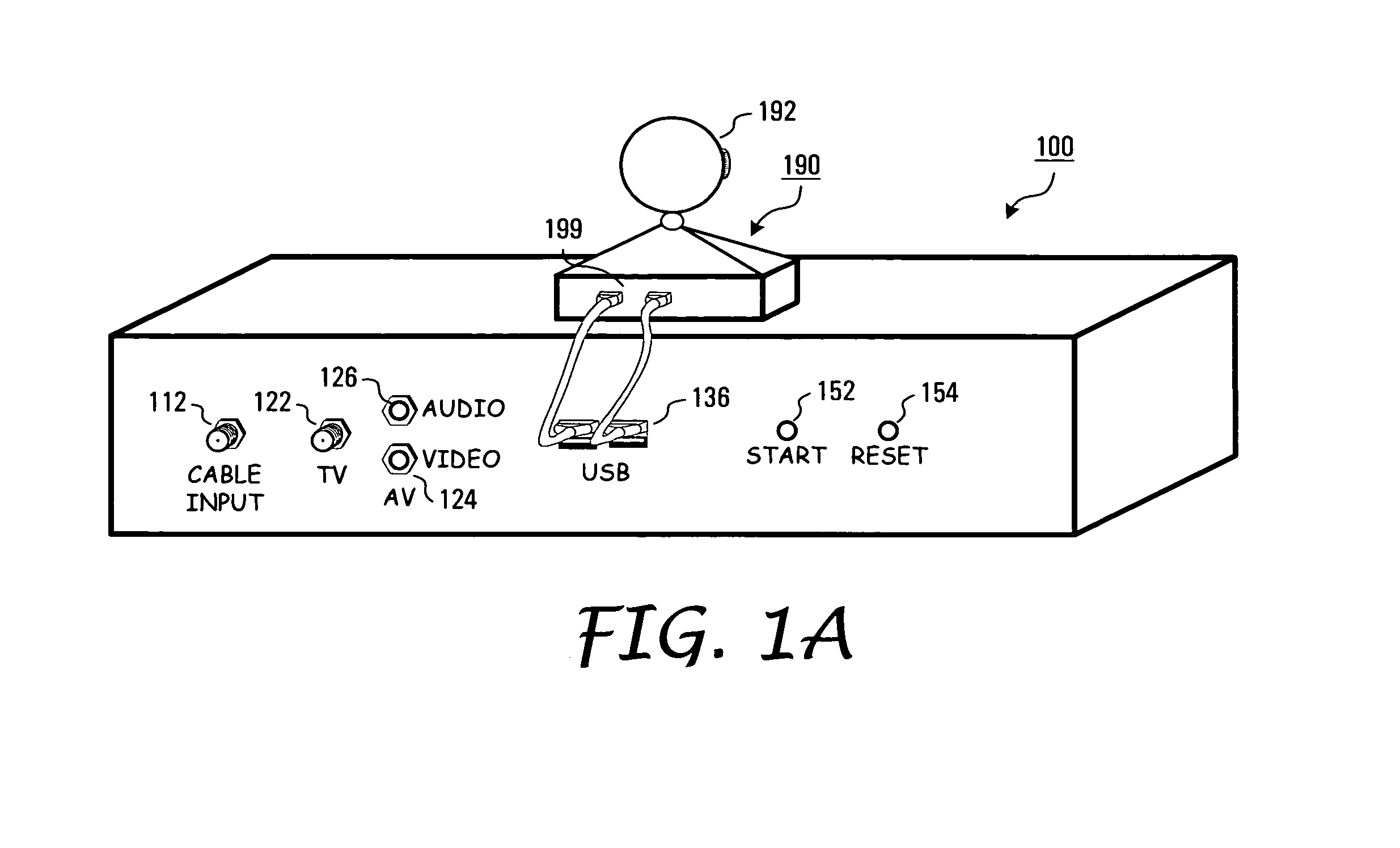
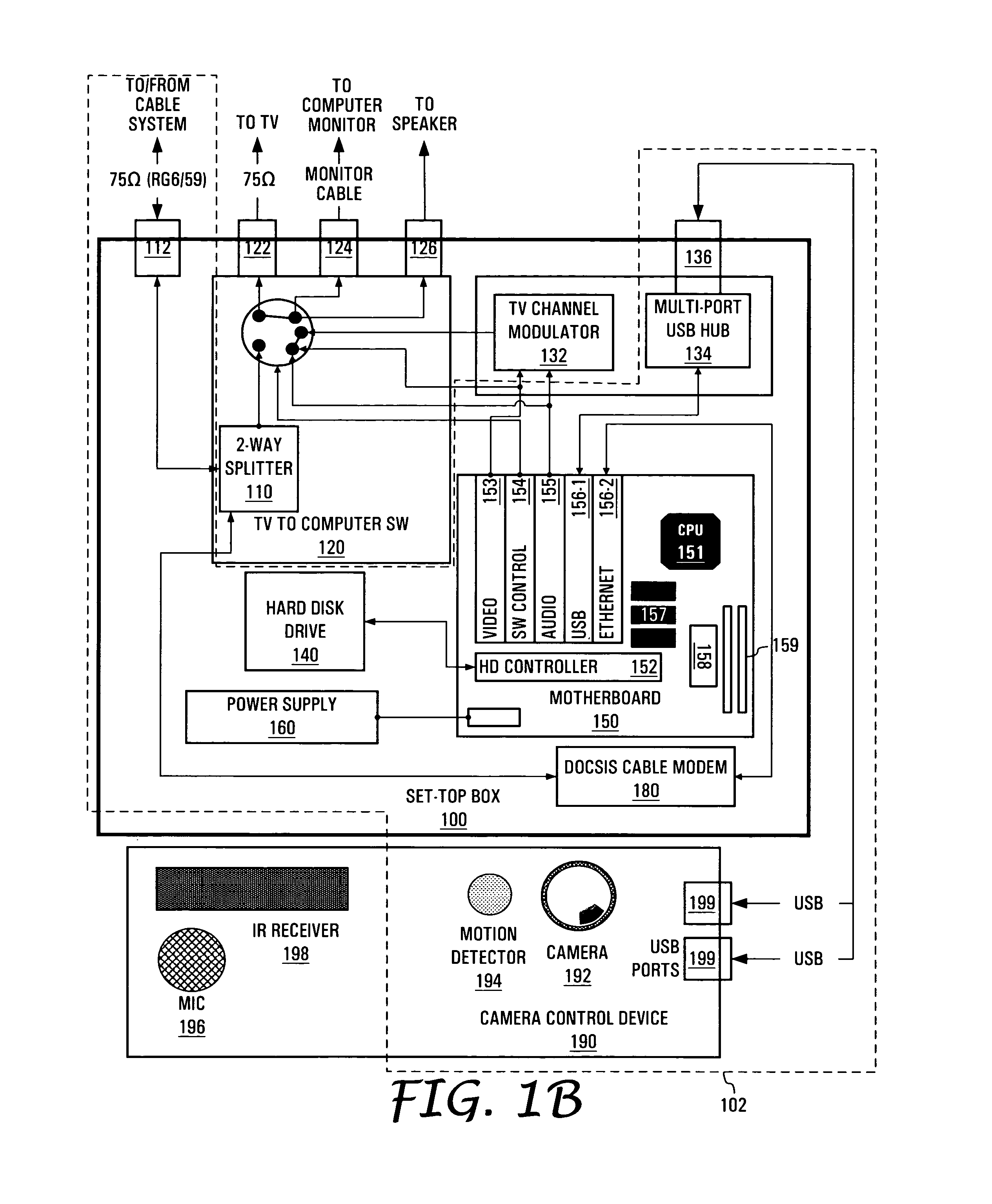
ActiveUS7477285B1Improve security levelTelevision system detailsColor television detailsCamera controlInformation access
The present invention is directed to a non-intrusive data transmission network for use in a healthcare facility and method for implementing such network. Each individual patient's room is equipped with a set-top control device, a separate camera, microphone, control module camera control device. The SCD allows for a non-intrusive installation within a minimum amount of time. By utilizing the existing cable television infrastructure, the device creates a high-speed data network throughout the facility. The interface between the SCD and the CCD is accomplished through a standard interface for universally connecting auxiliary devices, such as USB, for enabling expandable, hot-pluggable Plug and Play serial device interfaces. These ports allow external devices such as the camera, microphone, infrared keyboard and privacy control unit to communicate with the SCD. Additional USB ports on the SCD allow for other devices to be connected to the network at a future time. Such devices include those for instrument monitoring, doctor information access or pharmaceutical prescription ordering. Visual information such as e-mail, web browsing, video and audio communications via web camera applications from family members, friends or other parties may be viewed by the patient from the in-room TV set by way of the internal RF modulator (and connecting to the Internet via the patient Internet server). The SCD switches from the standard cable TV channels to the SCD by way of an internal switch controlled by the patient from an infrared control. This control also enables or disables the camera to allow for privacy at times when such privacy is required from external Internet access. The system is configurable to offer this privacy to be layered from specific Internet or external users to the nurses, doctors or security department as the hospital desires.
Owner:CAREVIEW COMM INC
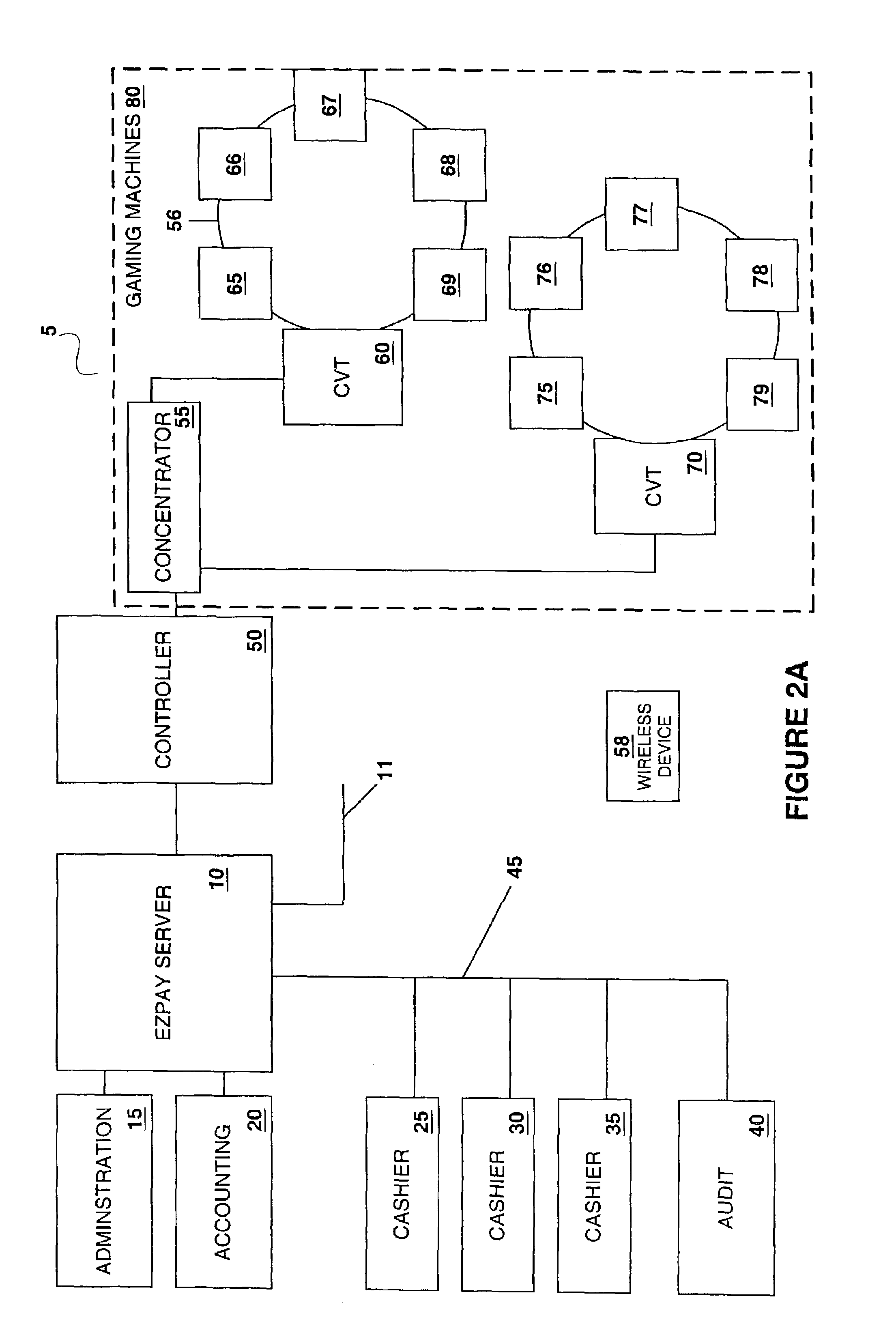
Cashless transaction clearinghouse
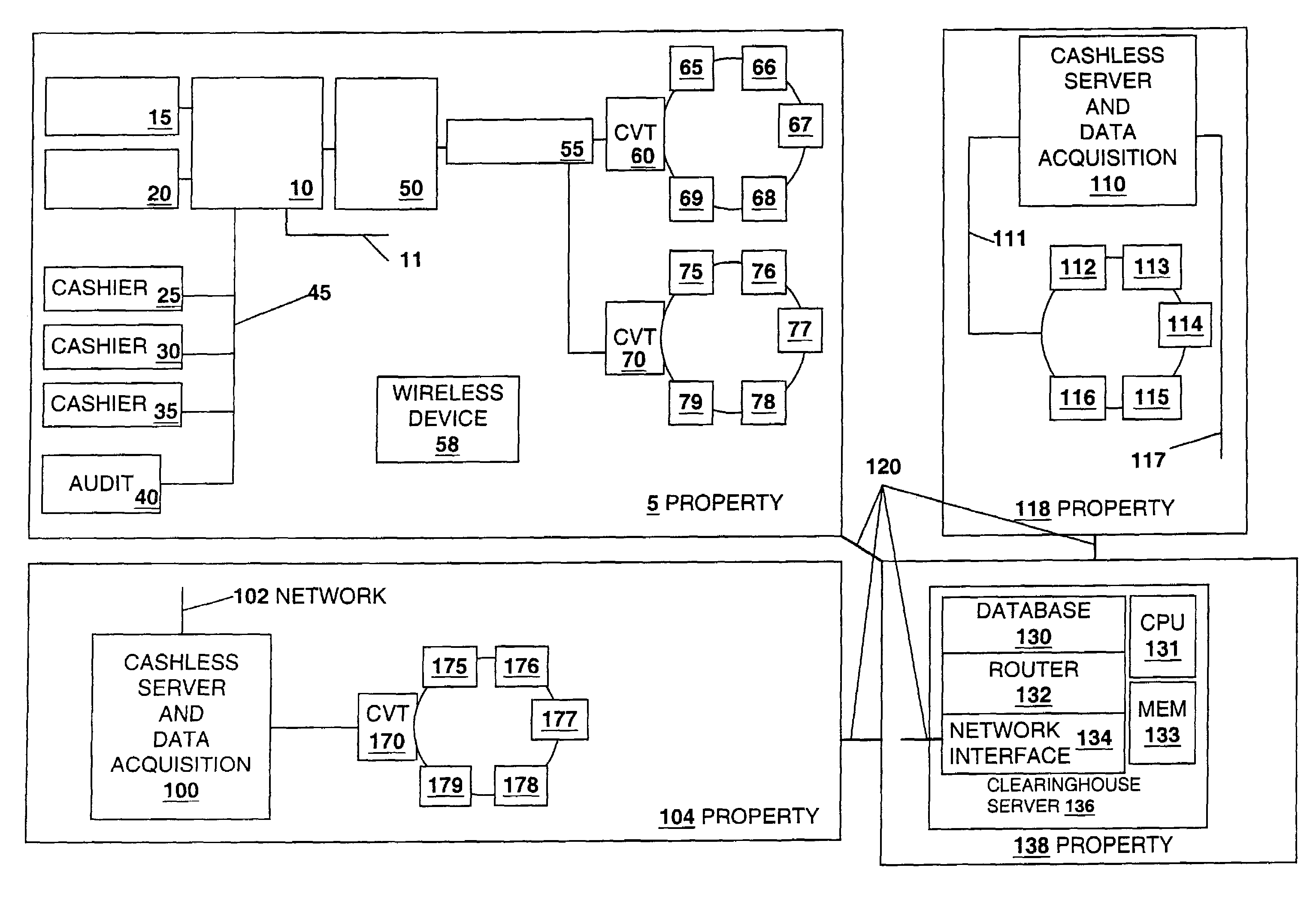
InactiveUS7419428B2Credit registering devices actuationApparatus for meter-controlled dispensingMulti siteInformation access
A disclosed cashless instrument transaction clearinghouse includes a network interface allowing the cashless instrument transaction clearinghouse to communicate with a number of gaming properties and a processor configured to enable the validation of cashless instruments at a gaming property different from where the cashless instrument was generated. Methods are provided at the cashless instrument transaction clearinghouse and at the gaming properties that enable cashless instrument transactions across multiple gaming properties including multi-site promotions. In addition, methods are provided at the cashless instrument transaction clearinghouse that allow 1) a transfer of resources from an account at a first gaming property to an account or device at a second gaming property, 2) account information access, 3) generation of cashless transaction threads comprising a plurality of related cashless transaction, 4) awards and services based upon properties of a cashless transaction thread and 5) local resource accounts maintained at the clearinghouse.
Owner:IGT
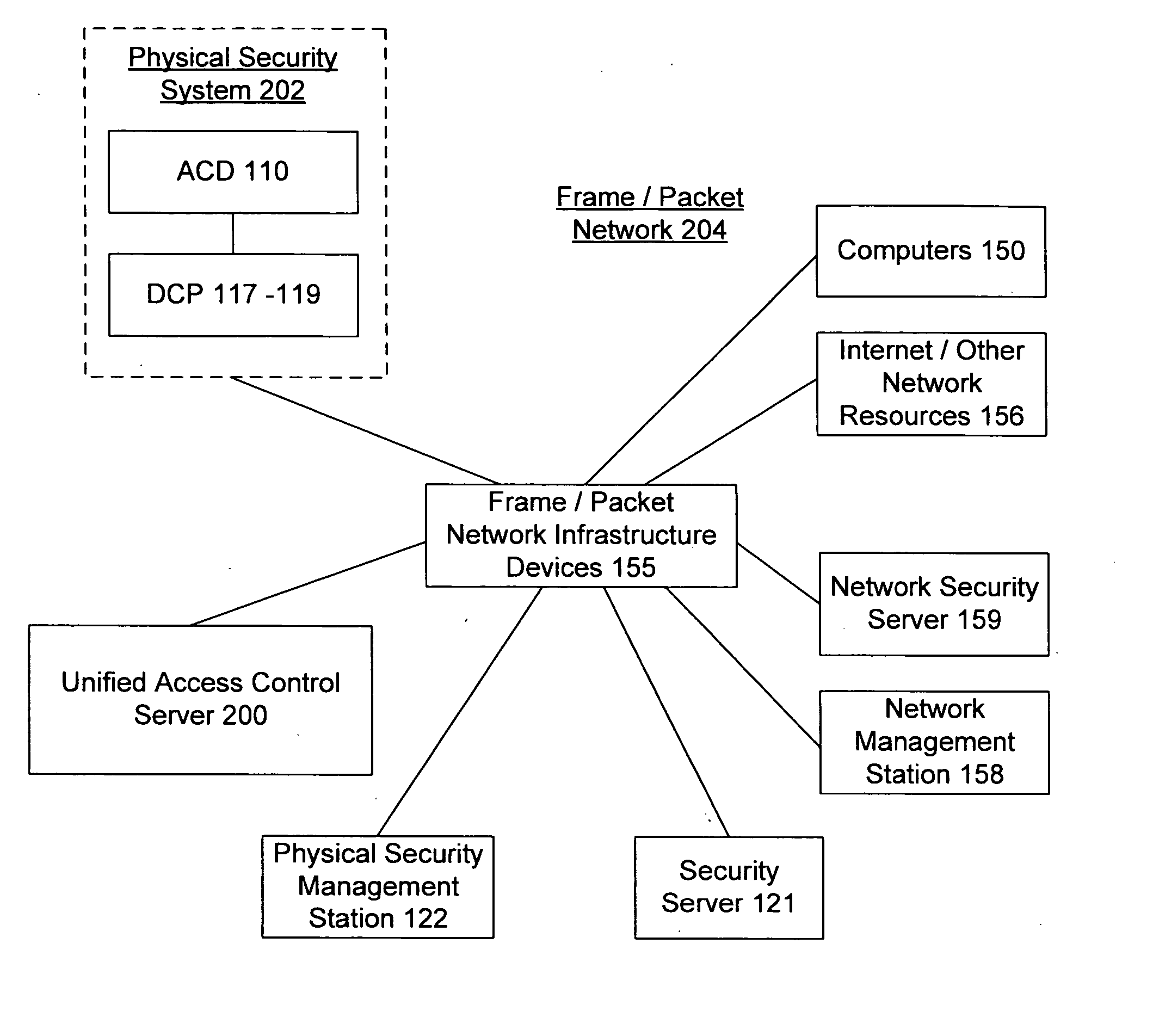
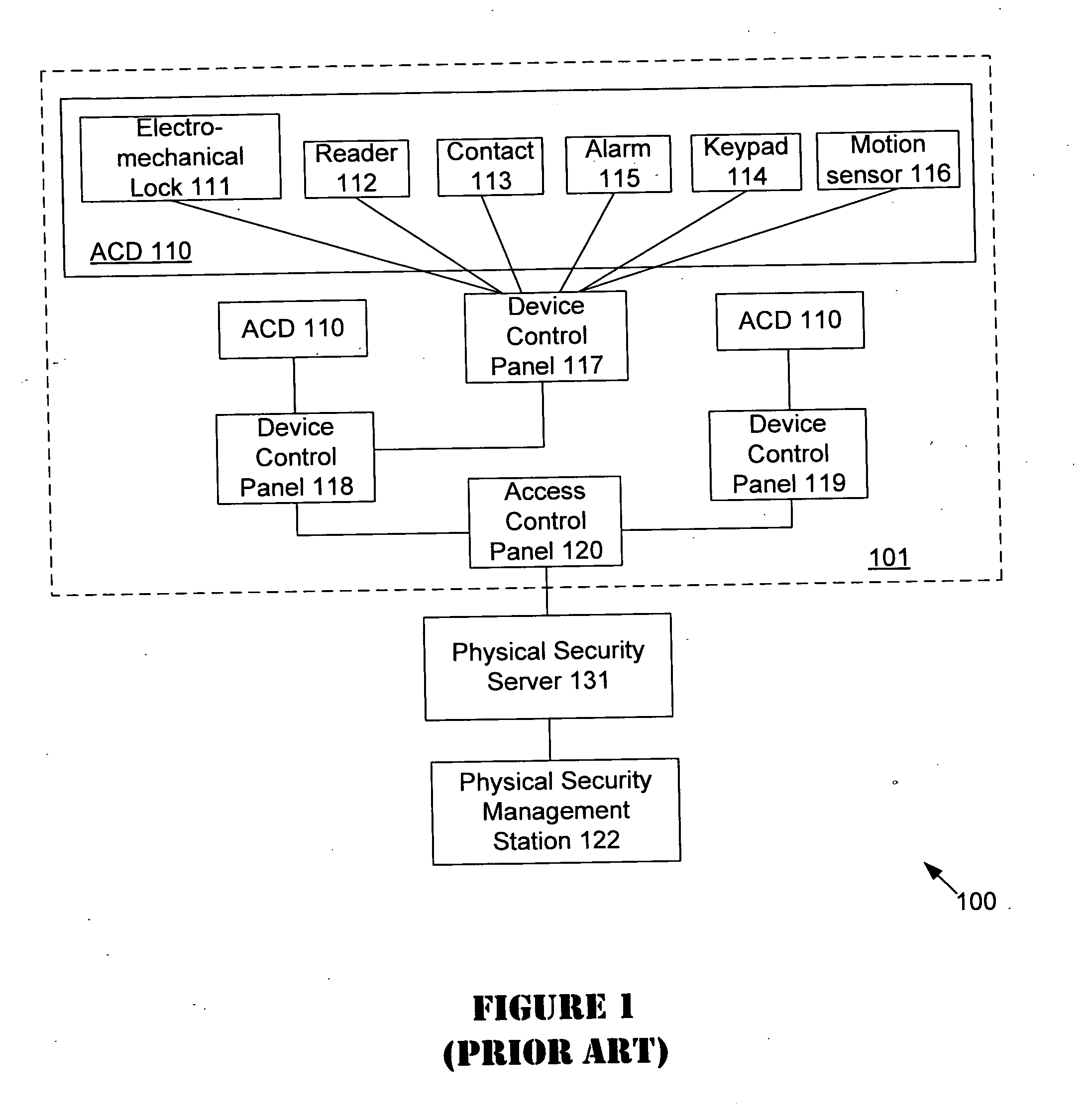
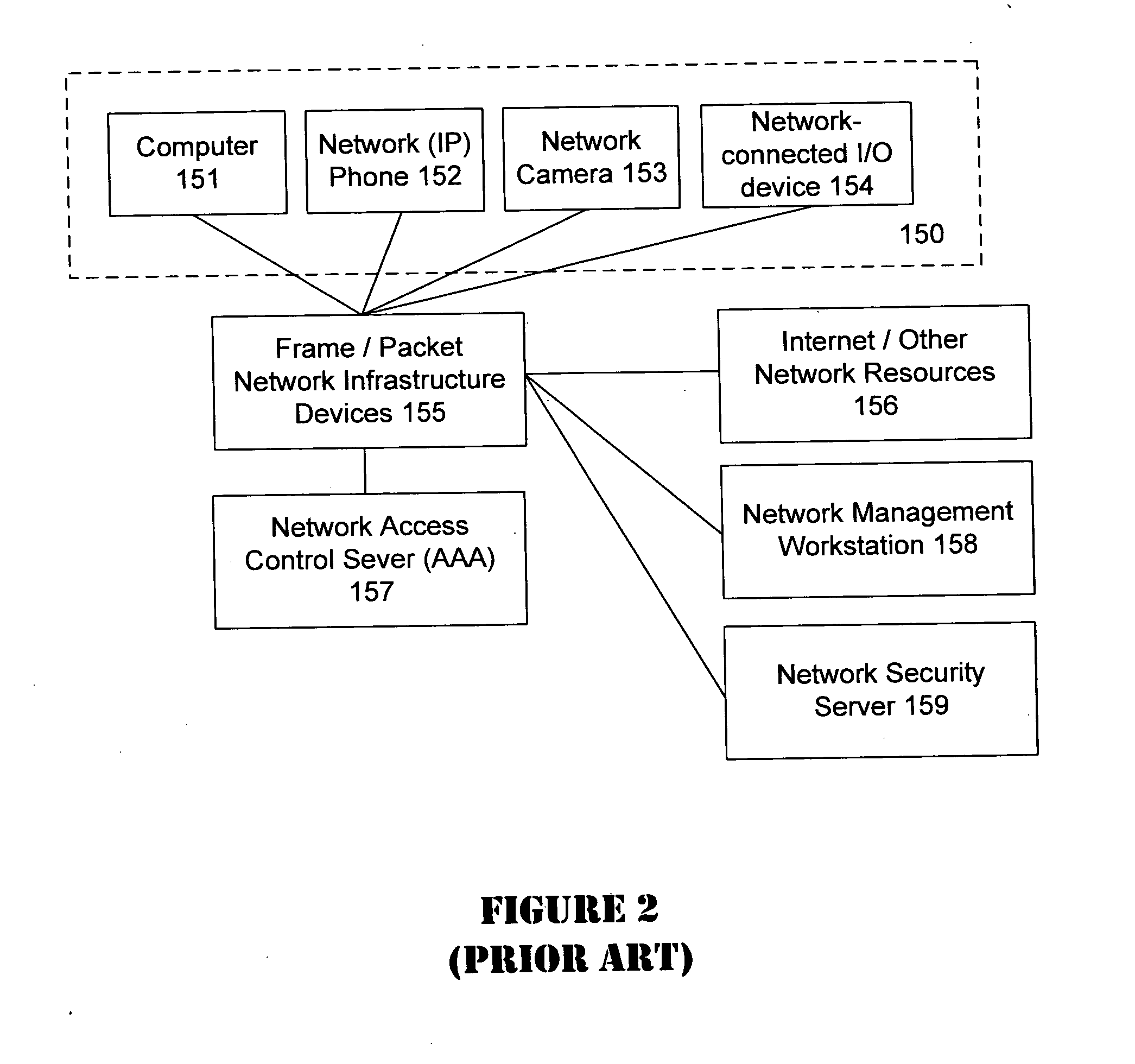
Unified network and physical premises access control server
ActiveUS20070094716A1Digital data processing detailsUser identity/authority verificationInformation accessTime of day
The present invention provides an access control server that holds information pertaining to both network access and facility access. The access control server enforces policies based on location, type of resource, time of day, duration, or other events, and logs all successful and unsuccessful attempts to access a given resource whether it be on the network or at the facility. The access control server operates off a common list or table of attributes and policies, or separate lists or tables of attributes and policies that are arbitrated by a credential verification and policy engine. This unified access control server implements protocols that work with network and / or physical premises-based devices. The unified access control server allows events in the facility to be associated with events on the network and vice versa and direct policies that may be executed in the physical or network realm.
Owner:CISCO TECH INC
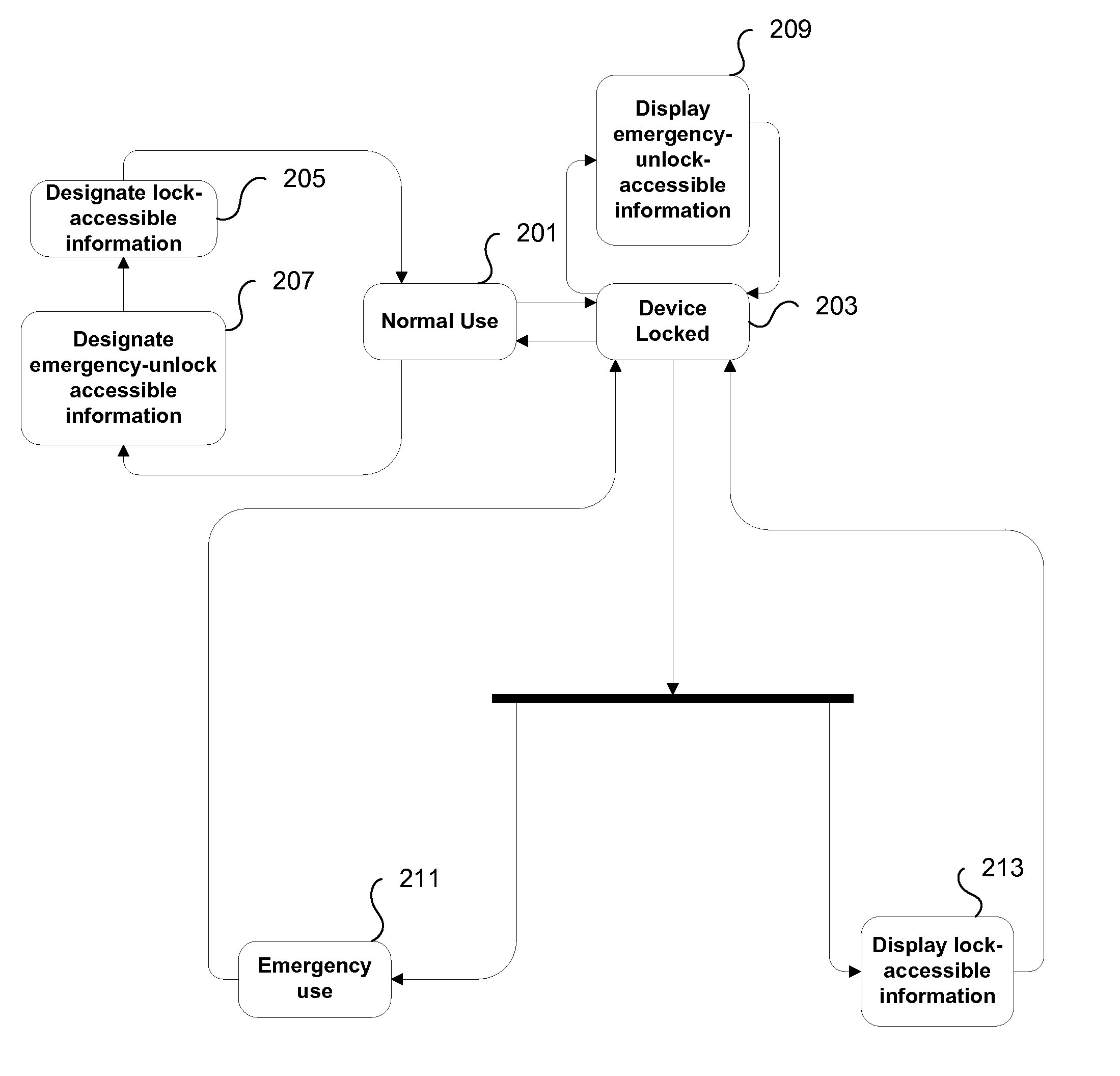
Emergency Information Access on Portable Electronic Devices
ActiveUS20090205041A1Prevent unauthorized accessEmergency connection handlingDigital data processing detailsPasswordInformation access
Improved techniques for facilitating emergency access to one or more contacts stored on a portable electronic device are disclosed. One or more contacts on the portable electronic device are designated as emergency contacts. While the portable electronic device is password-locked, a request to display the one or more emergency contacts on the password-locked portable electronic device is received. Without requiring a password, the one or more emergency contacts are displayed on the portable electronic device.
Owner:APPLE INC
Ad hoc network discovery menu
InactiveUS20050088980A1Assess restrictionNetwork topologiesInformation accessSelf-organizing network
When an ad hoc network is formed between short range wireless devices, at least one device assumes the role of an ad hoc network information provider for the new piconet. In this role, the device allocates a browsing hierarchy of service classes in its service registry. The service classes will provide a record to characterize the ad hoc network. When a new wireless device arrives within the communication range of any member of the ad hoc network, its inquiry signals are answered by the first member detecting the inquiry. If that first member is an ad hoc network information provider, it responds with information accessed from its service registry characterizing the ad hoc network. If, instead, an ordinary device in the ad hoc network is the first to respond to the inquiry signals of the arriving device, the device responds with the address of the ad hoc network information provider. The arriving device then pages the ad hoc network information provider to obtain information characterizing the ad hoc network.
Owner:NOKIA CORP
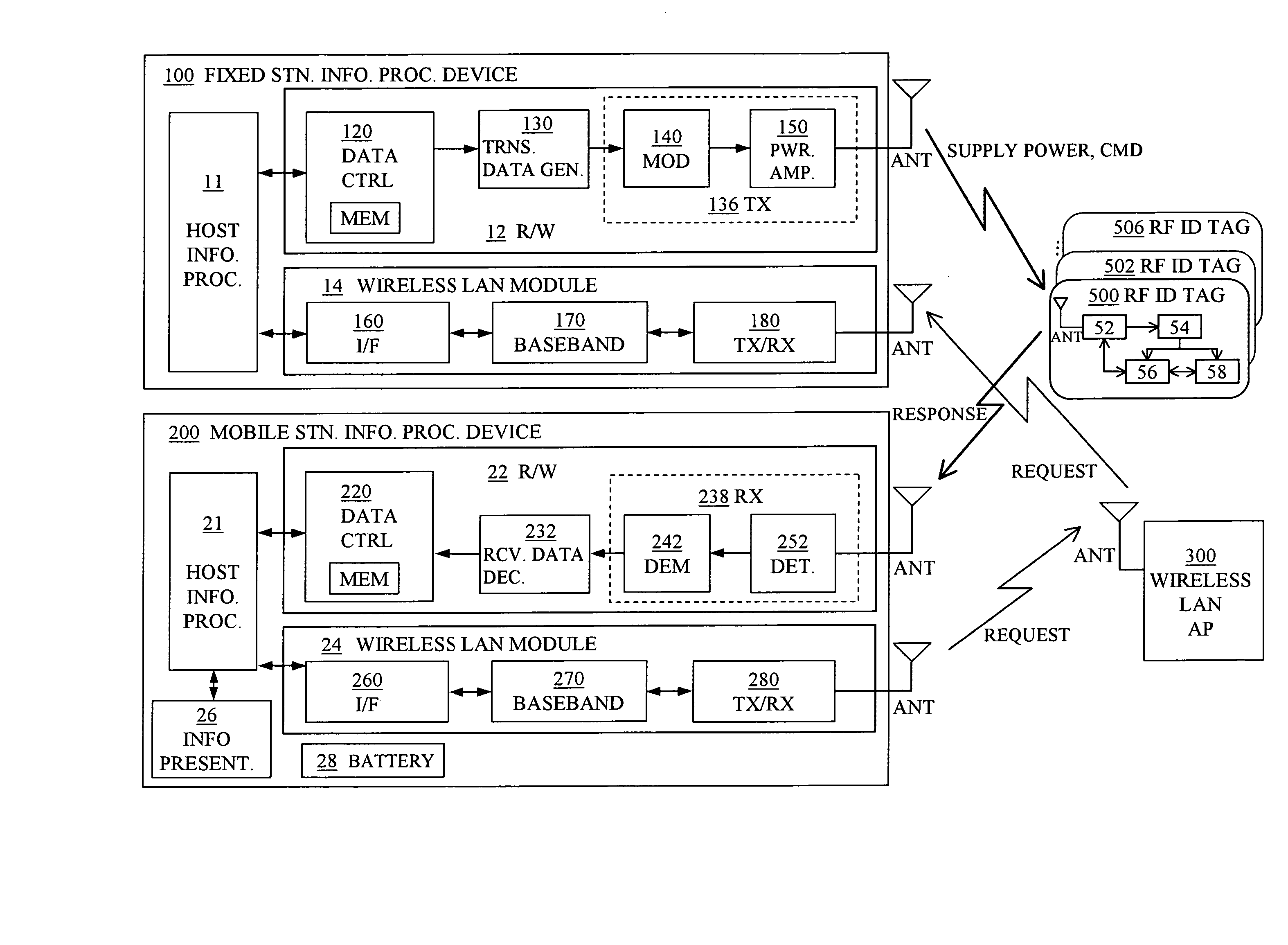
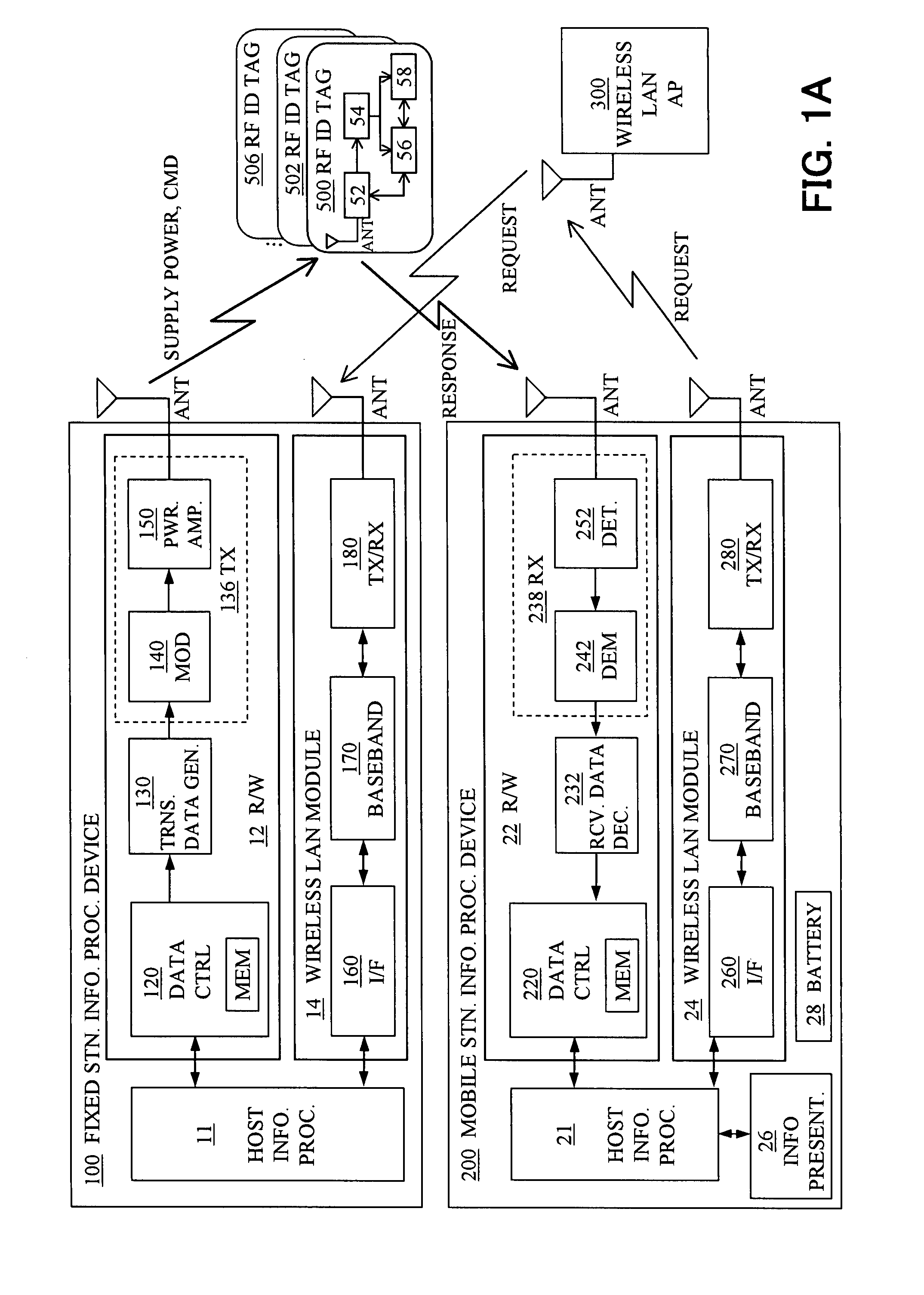
Information access system for accessing information in contactless information storage device, and method therefor
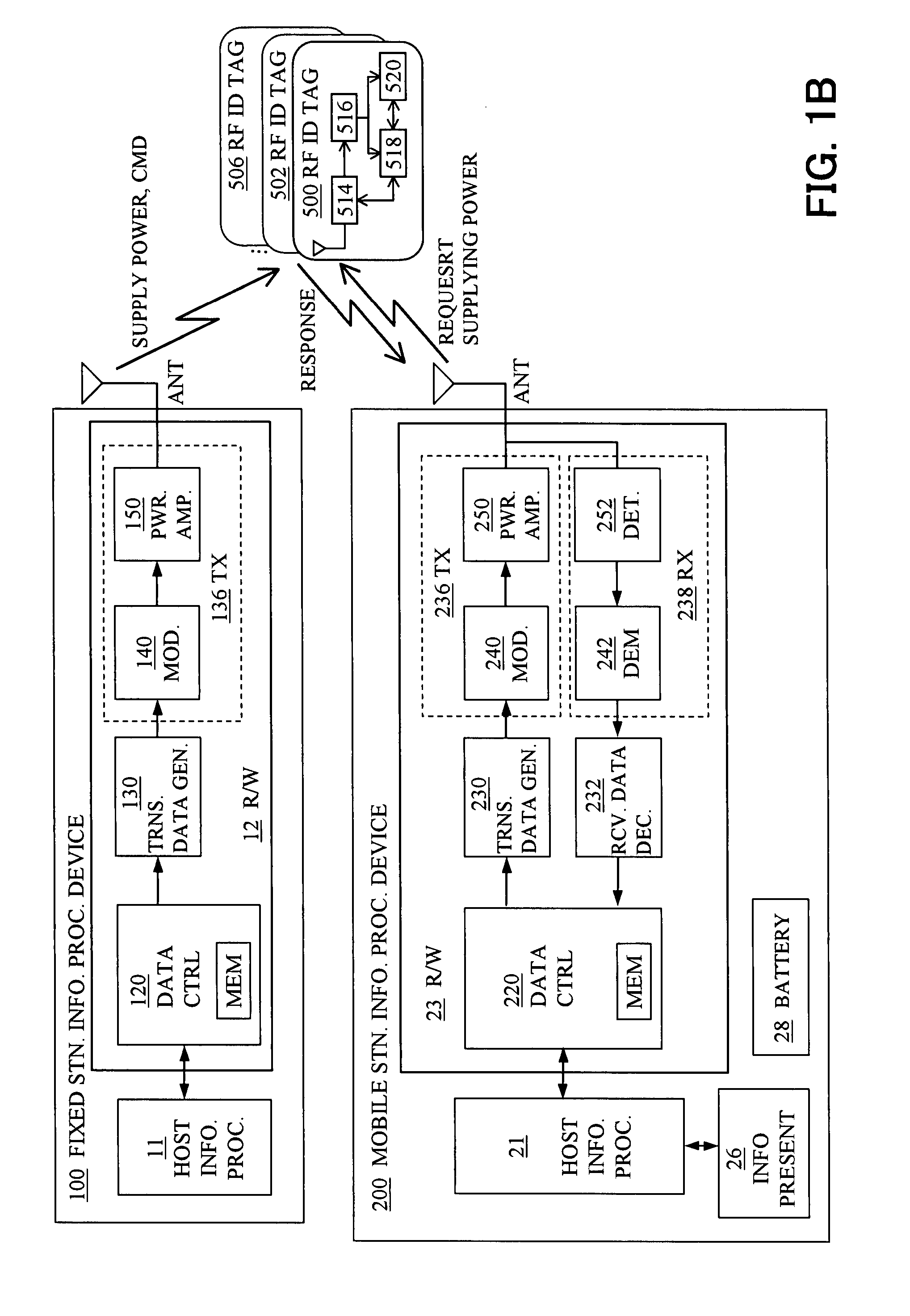
InactiveUS20070273486A1Reduce power consumptionAvoid collisionElectric signal transmission systemsDigital data processing detailsInformation processingComputer hardware
An information access system includes: a passive contactless information storage device (500) capable of transmitting and receiving signals; a fixed-station information processing device (100) having an information processing unit, and a wireless transmitter for transmitting, in a contactless manner, a command signal for requesting transmission of information stored in the information storage device and supplying power in a contactless manner to the information storage device; and a mobile-station information processing device (200) having an information processing unit, an information presenting unit, a battery, and a wireless receiver for receiving a response signal for response to the command signal, from the information storage device in a contactless manner. While the fixed-station device is supplying power to the information storage device in the contactless manner, the information storage device transmits, in response to the command signal, the response signal to the mobile-station device in the contactless manner.
Owner:FUJITSU LTD
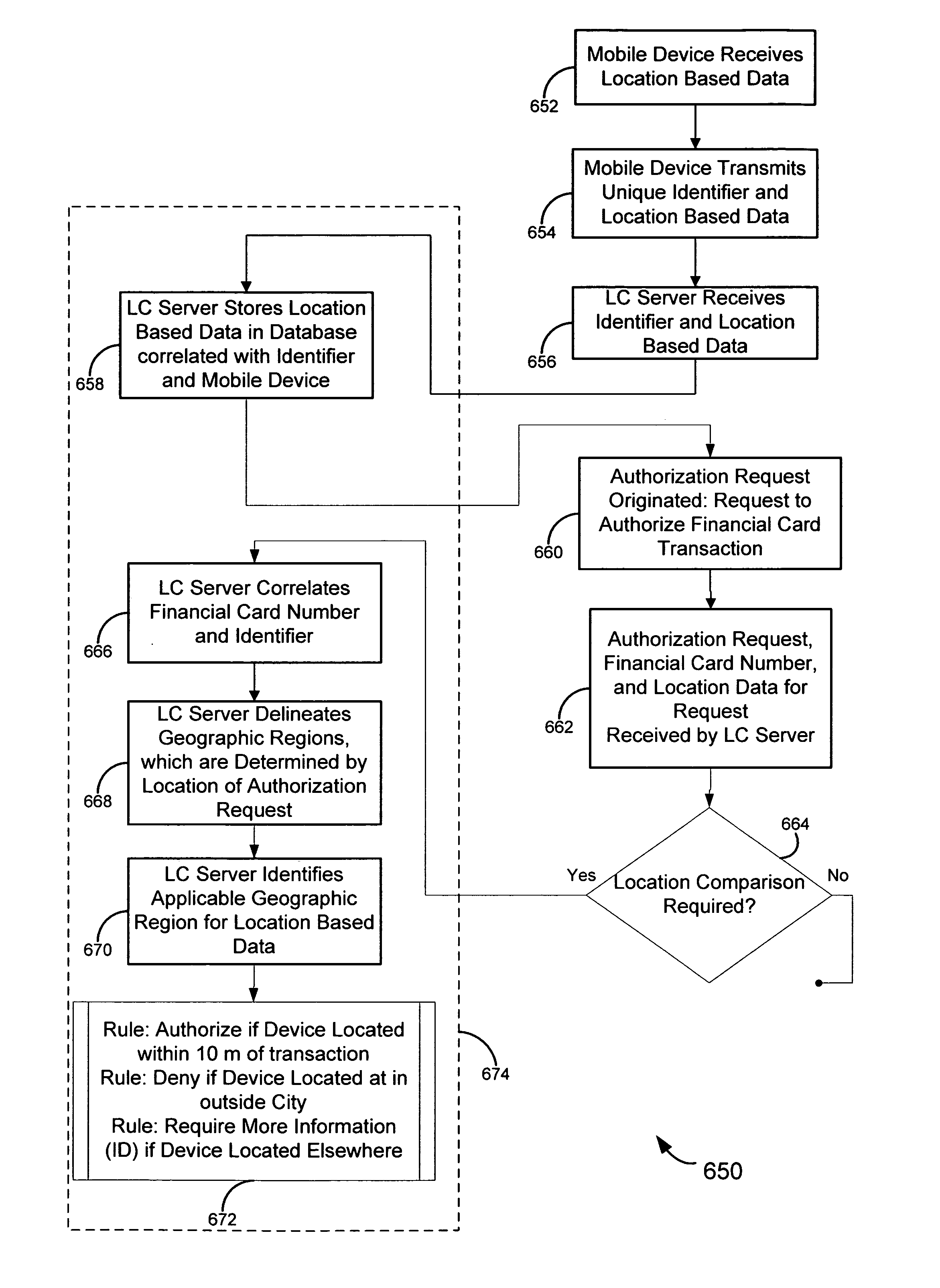
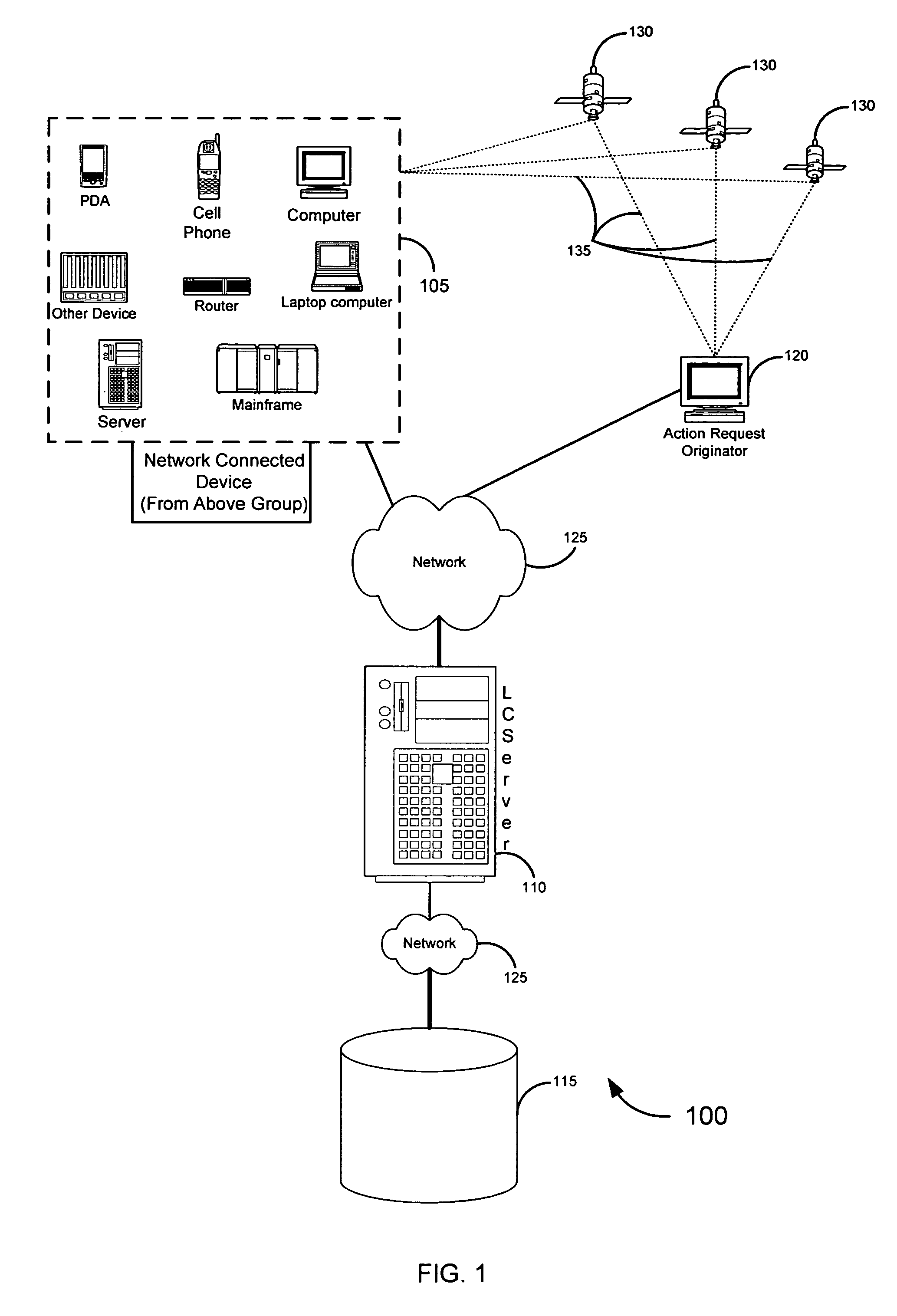
Location information for avoiding unwanted communications systems and methods
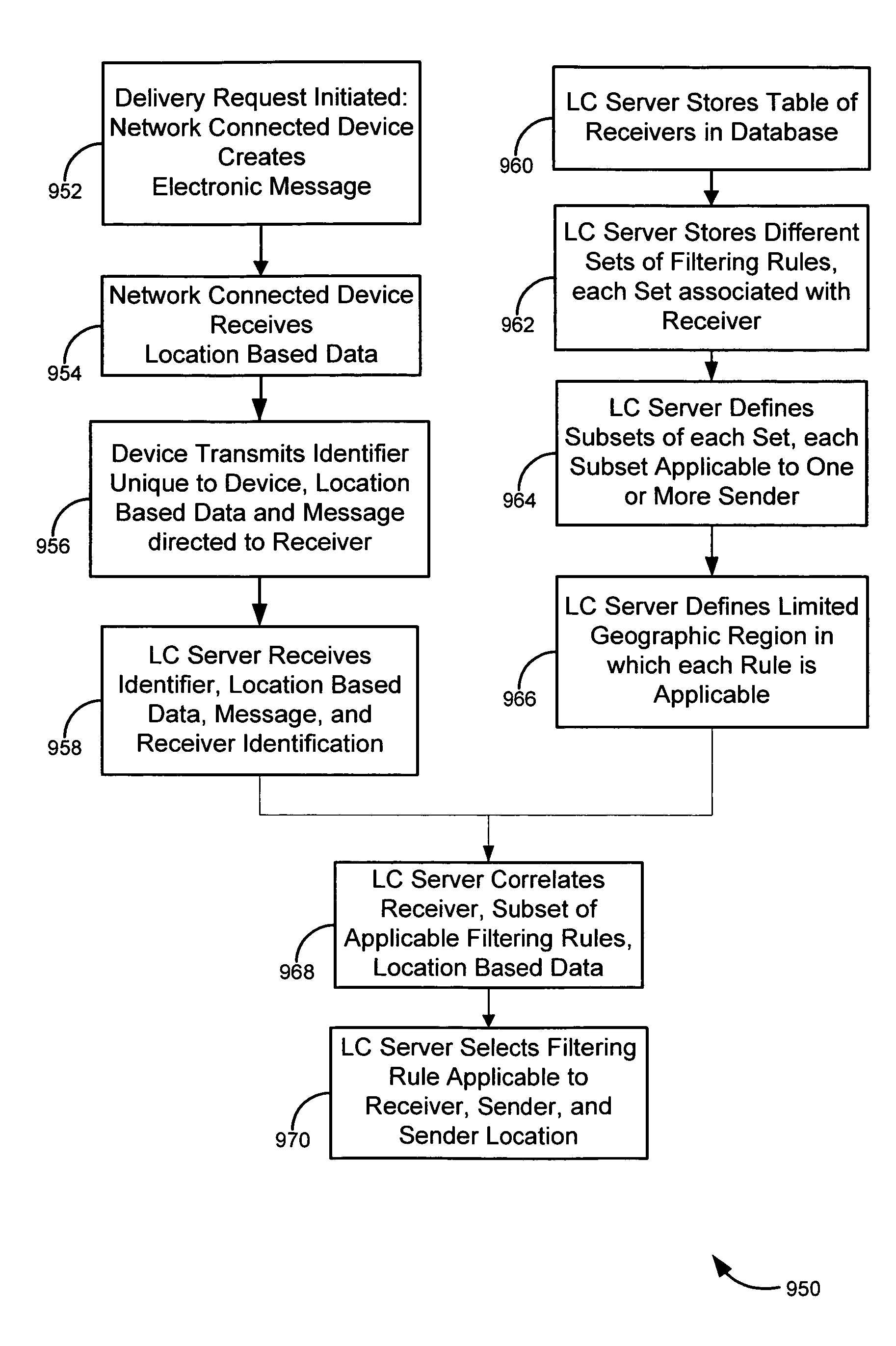
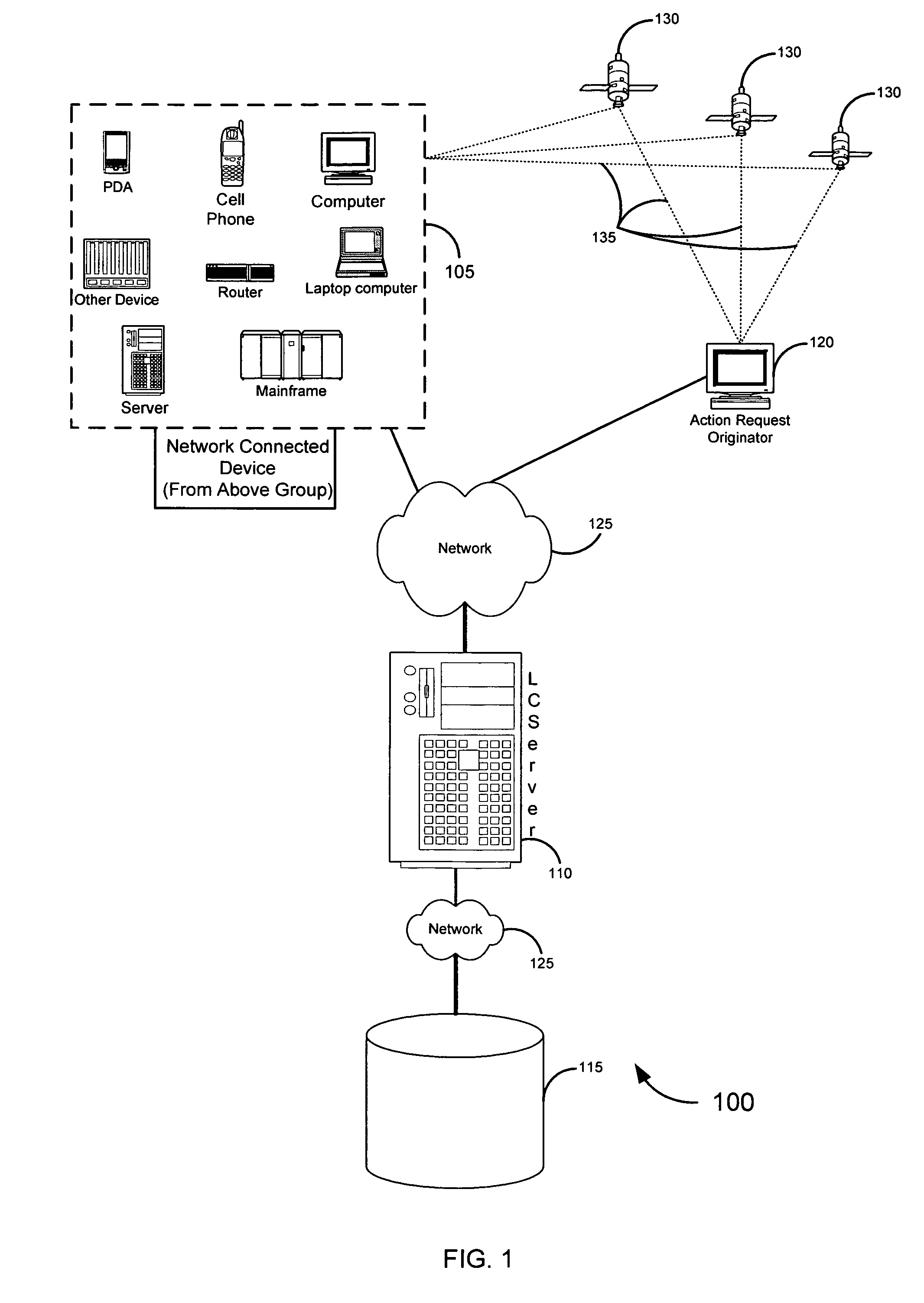
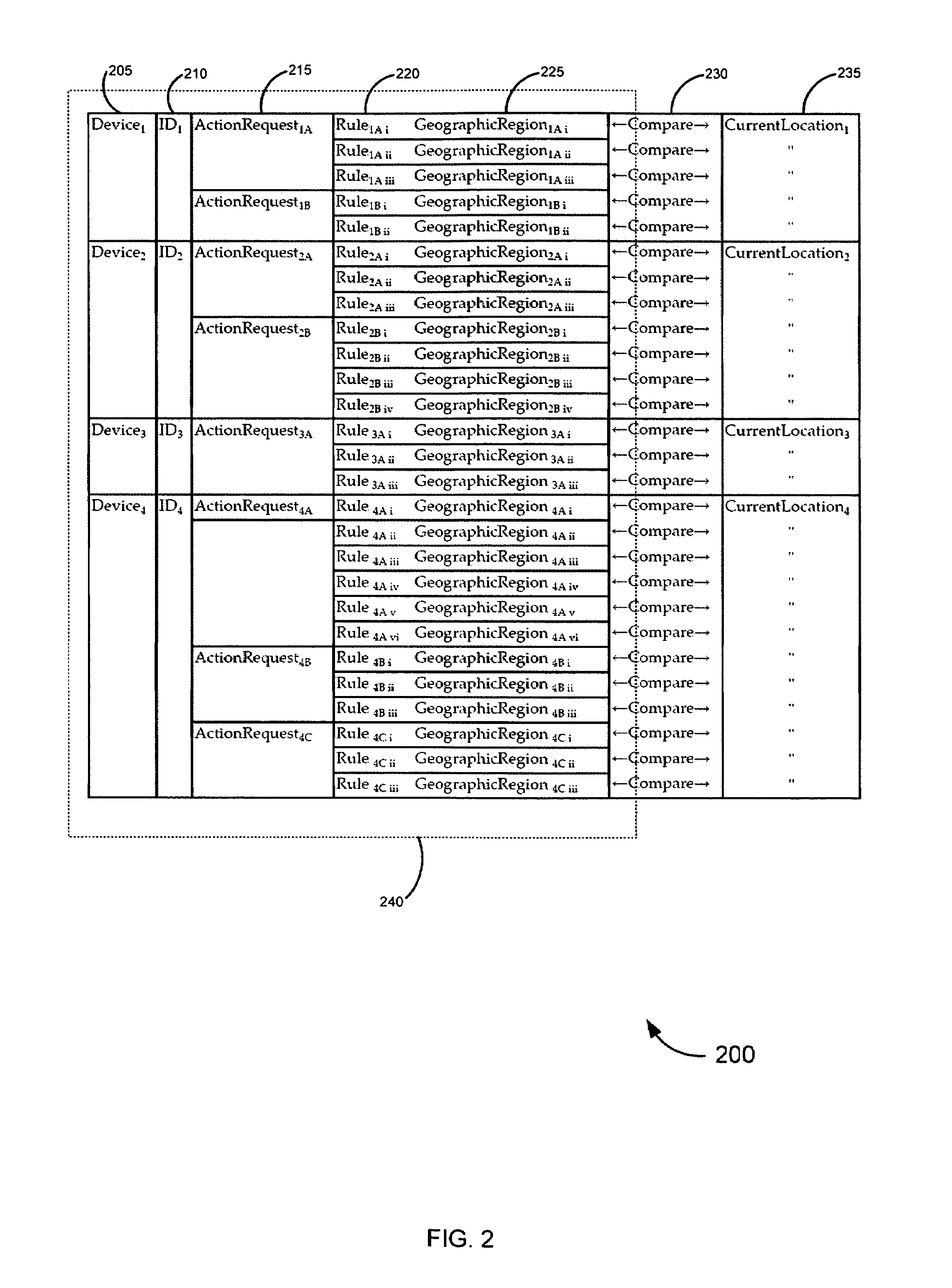
ActiveUS7487170B2Data processing applicationsData switching networksCommunications systemInformation access
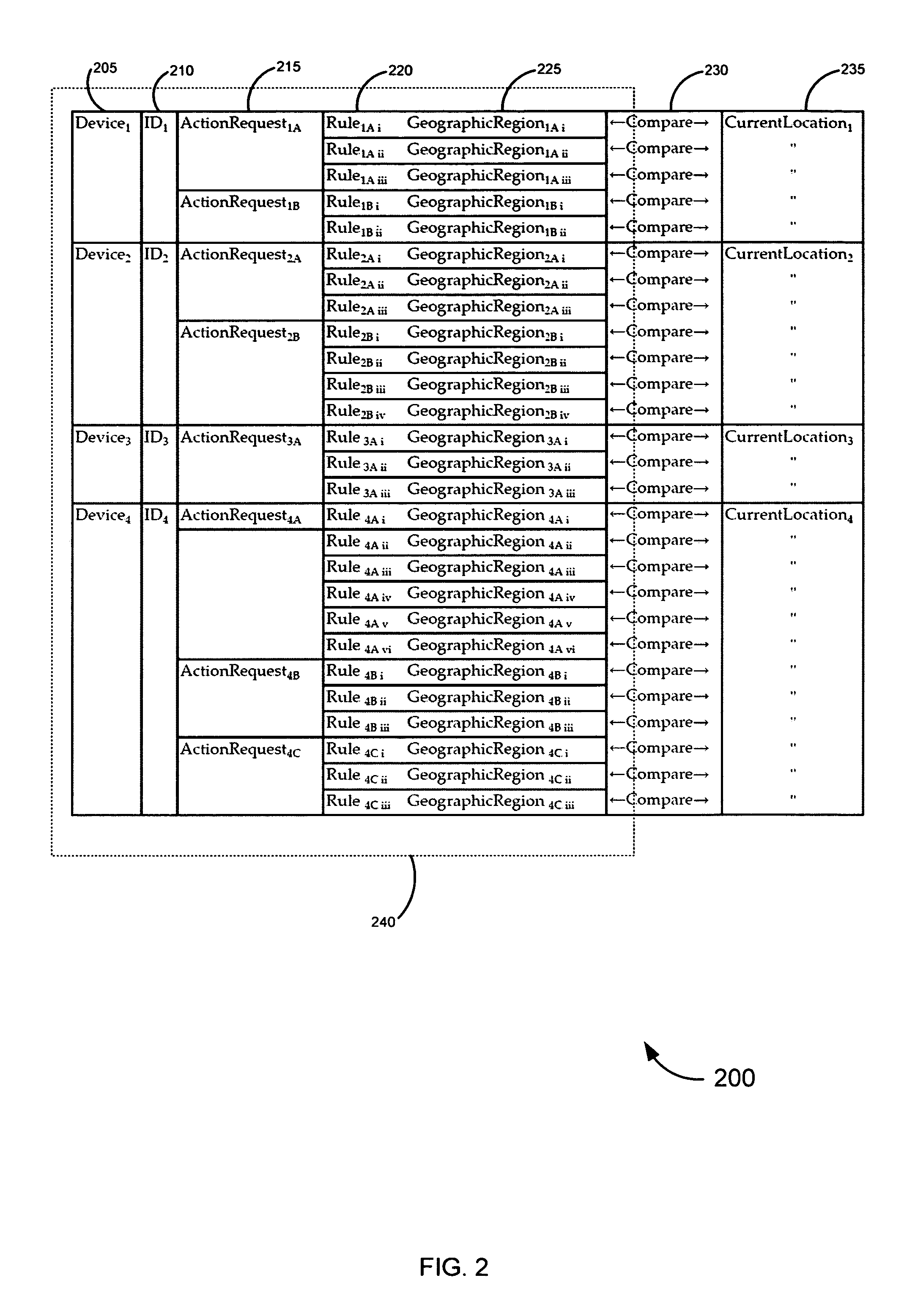
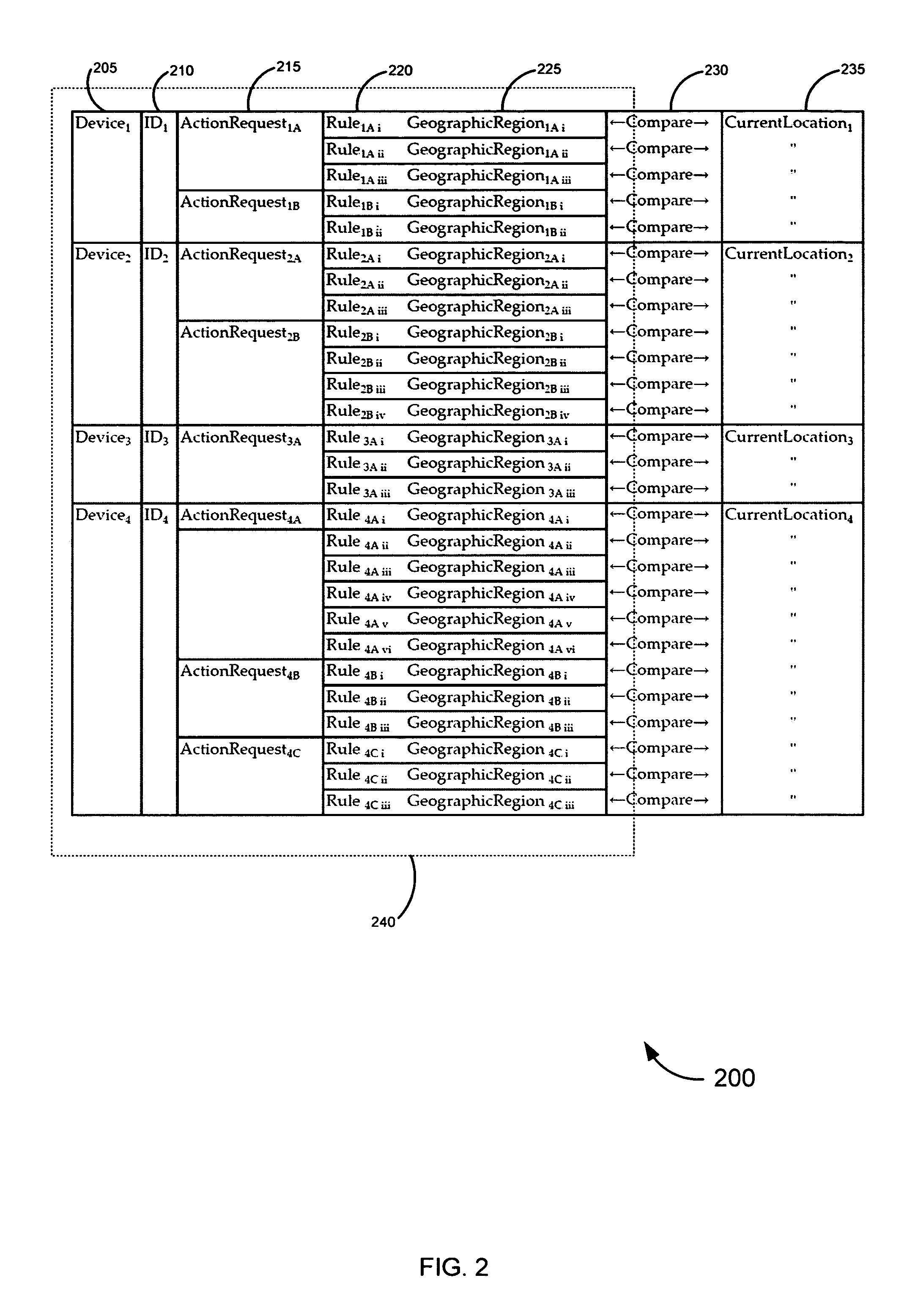
Systems, methods, and software for identifying location based rules related to a network connected device are described. A network connected device may transmit a set of data identifying the location of the device and an identifier unique to the device to a server. The server may also receive an action request, wherein the action request is associated with the identifier. The server may select a rule in a database to address the action request, the rule applicable to the identifier and location of the device. Various embodiments related to financial card transactions, access to financial information, emergency services contact, and electronic message filtering are also addressed.
Owner:QWEST
Method and apparatus for efficient handling of product return transactions
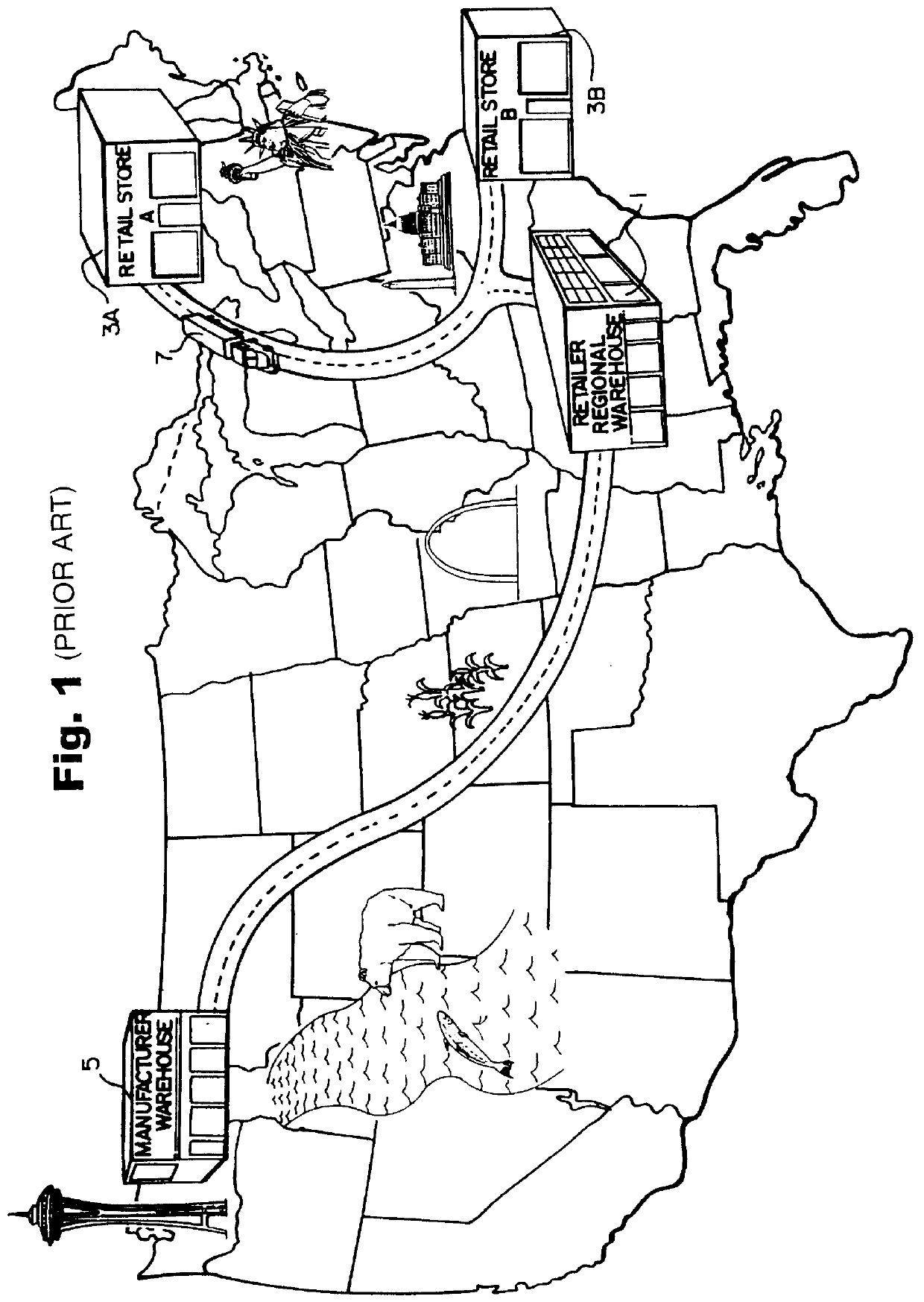
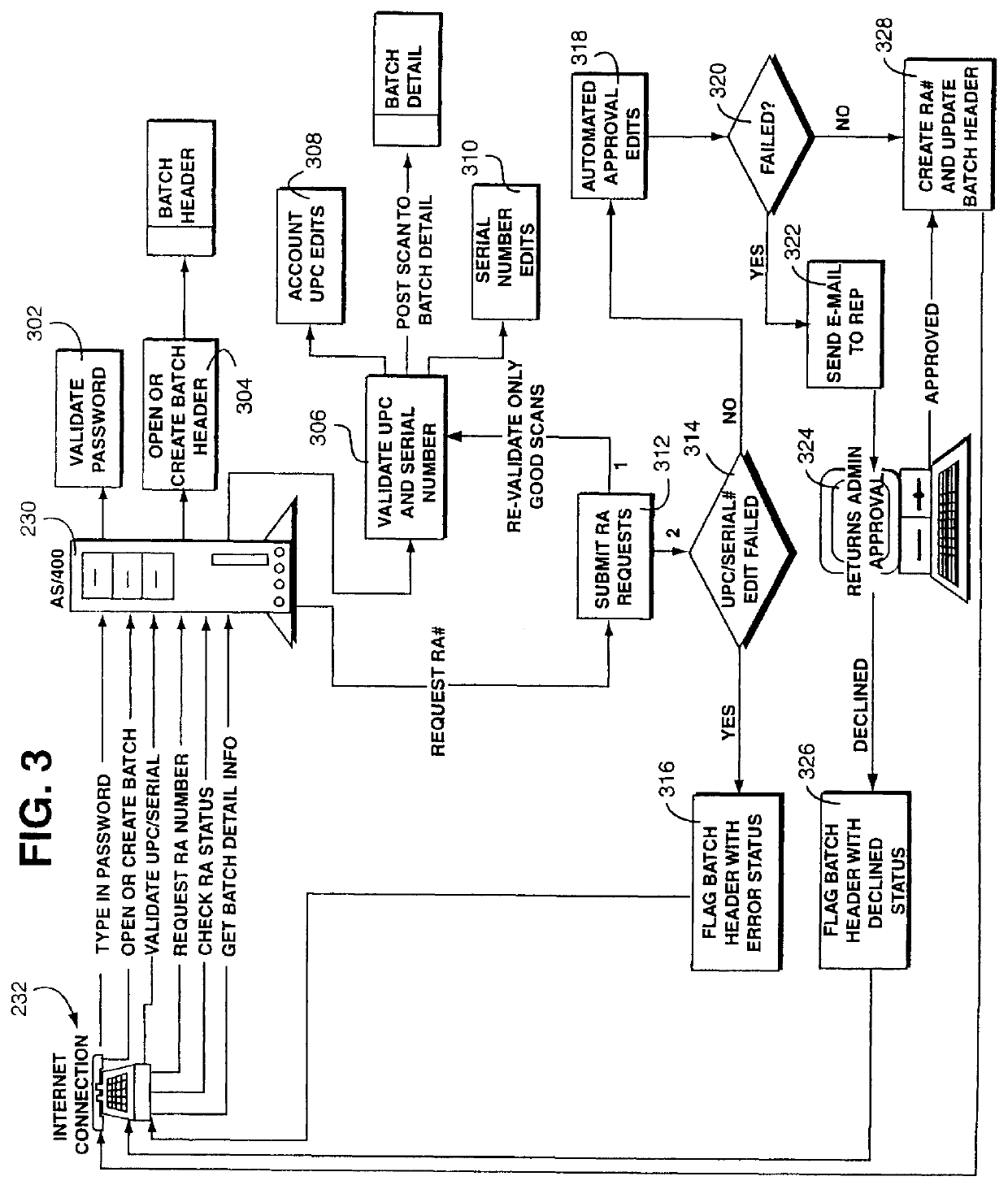
InactiveUS6085172ALow costReduce shipping costsFinanceBuying/selling/leasing transactionsSingle sessionInformation access
A method and apparatus for efficient handling of product returns to reduce associated costs. A computer system at a regional product return center scans a returned product for identifying information, accesses a manufacturer return approval computer system through the internet or the like, and then submits the identifying information to the manufacturer for return approval. The manufacturer computer system utilizes the identifying information to access an electronic registration database to determine whether the returned product satisfies applicable return criteria. If so, the product is approved for return to the manufacturer. The regional product return center preferably scans a plurality of returned products in a single session. In response to the product identifying information submitted by the regional product return center, the manufacturer provides a list of approved returns and unapproved returns, along with a return authorization number for the batch of approved returns. The regional product return center then assembles the approved product returns into a box, shipping pallet, or the like, applies a label indicating the return authorization label, and ships the batch to the manufacturer. Shipping costs can be saved by omitting rejected product returns from the shipment. The manufacturer can handle the approved product returns from the regional return center as a batch, thereby reducing costs.
Owner:E2INTERACTIVE INC D B A E2INTERACTIVE
Category-based selections in an information access environment
InactiveUS20030018659A1Digital data information retrievalDigital data processing detailsInformation accessDocumentation
Owner:LINGOMOTORS
Location based authorization of financial card transactions systems and methods
ActiveUS20070055785A1Digital data processing detailsMultiple digital computer combinationsNetwork connectionInformation access
Systems, methods, and software for identifying location based rules related to a network connected device are described. A network connected device may transmit a set of data identifying the location of the device and an identifier unique to the device to a server. The server may also receive an action request, wherein the action request is associated with the identifier. The server may select a rule in a database to address the action request, the rule applicable to the identifier and location of the device. Various embodiments related to financial card transactions, access to financial information, emergency services contact, and electronic message filtering are also addressed.
Owner:QWEST
Apparatus and method for the automatic positioning of information access points
ActiveUS6898434B2Optimize locationAccurate locationDirection finders using radio wavesNavigation by speed/acceleration measurementsAlgorithmInformation access
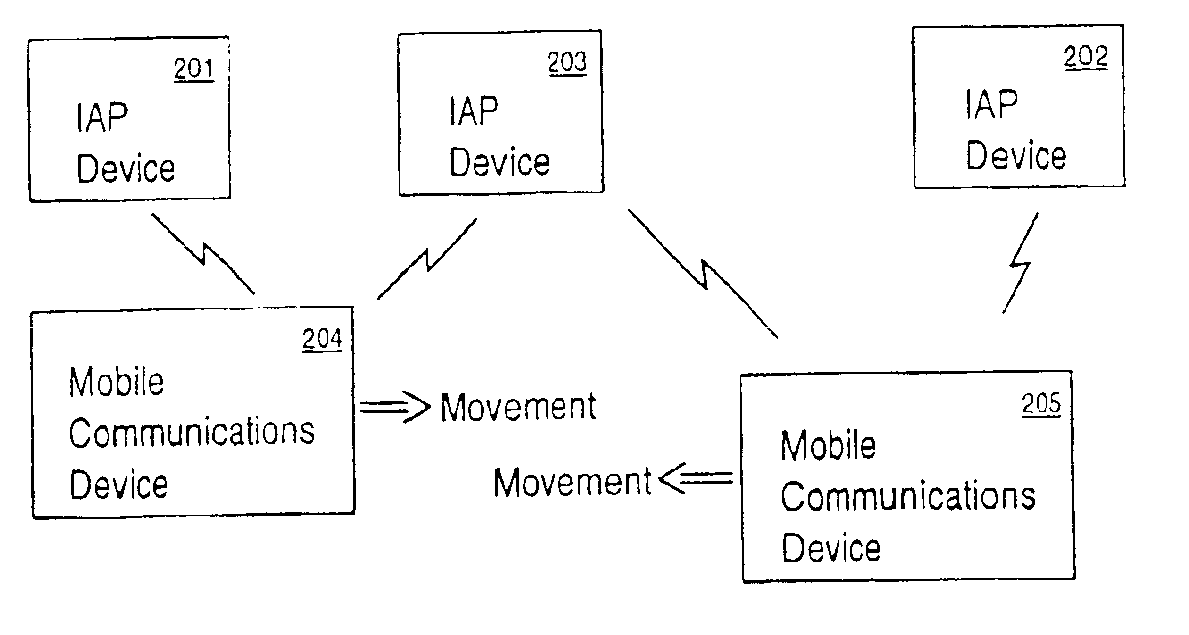
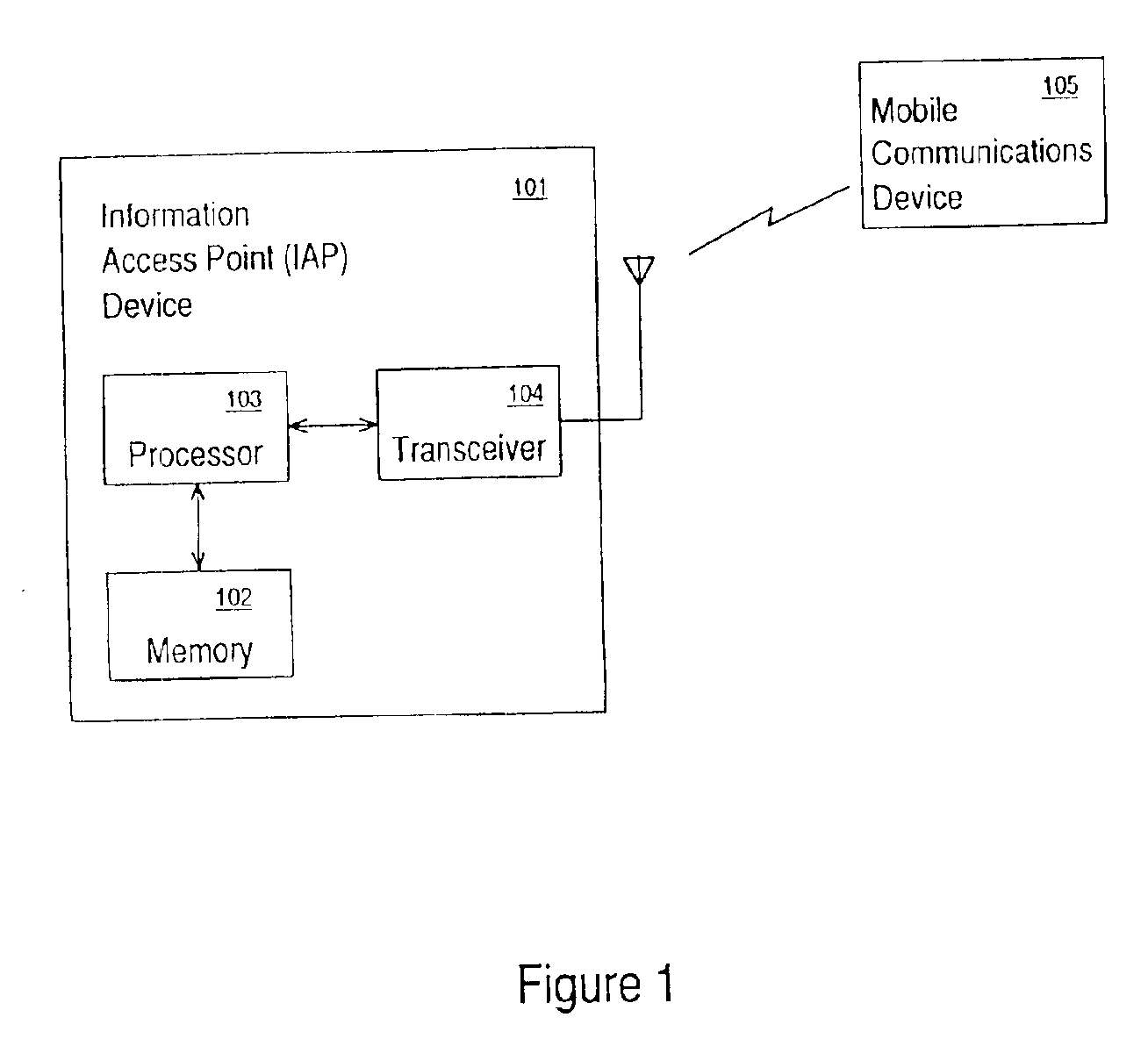
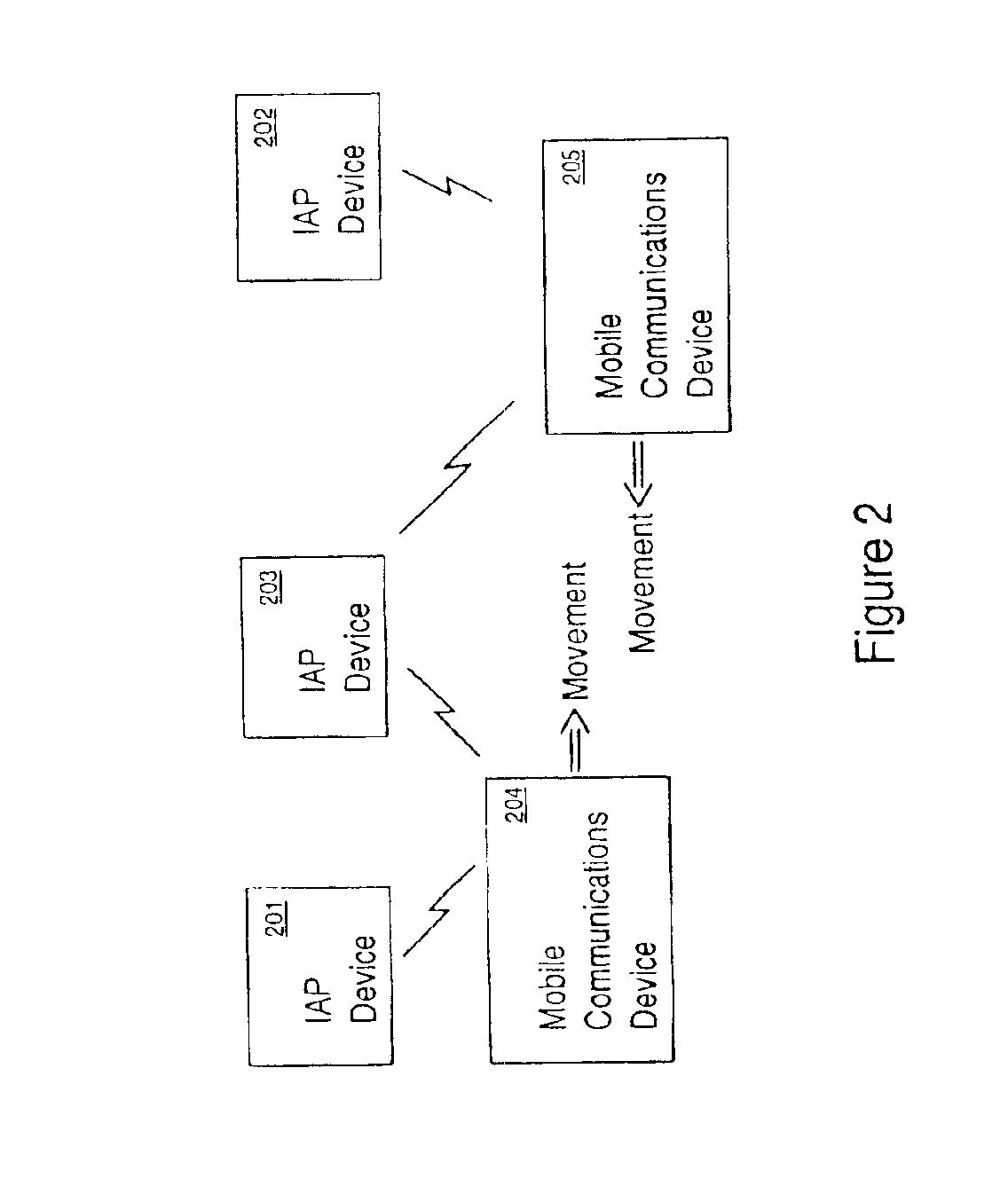
An apparatus and method for the automatic positioning of information access points. An electronically connected individual (ECI) passes within range of a first information access point (IAP) and obtains location information. Subsequently, the ECI passes within range of a second IAP which hitherto does not have any location information. The location for this second IAP can be estimated based on the location obtained from the first IAP, elapsed time, and the individual's estimated velocity vector. As the ECI passes by a third IAP, the location, elapsed time, and estimated velocity vector data corresponding to the third IAP can be used to refine the location of the second IAP. Over time, the location of the second IAP can be successively refined as ECI's move between IAP's.
Owner:HEWLETT PACKARD DEV CO LP
System and methods for constructing personalized context-sensitive portal pages or views by analyzing patterns of users' information access activities
InactiveUS20050267869A1Facilitates site selectionOptimize layoutDigital data processing detailsCommercePersonalizationWeb site
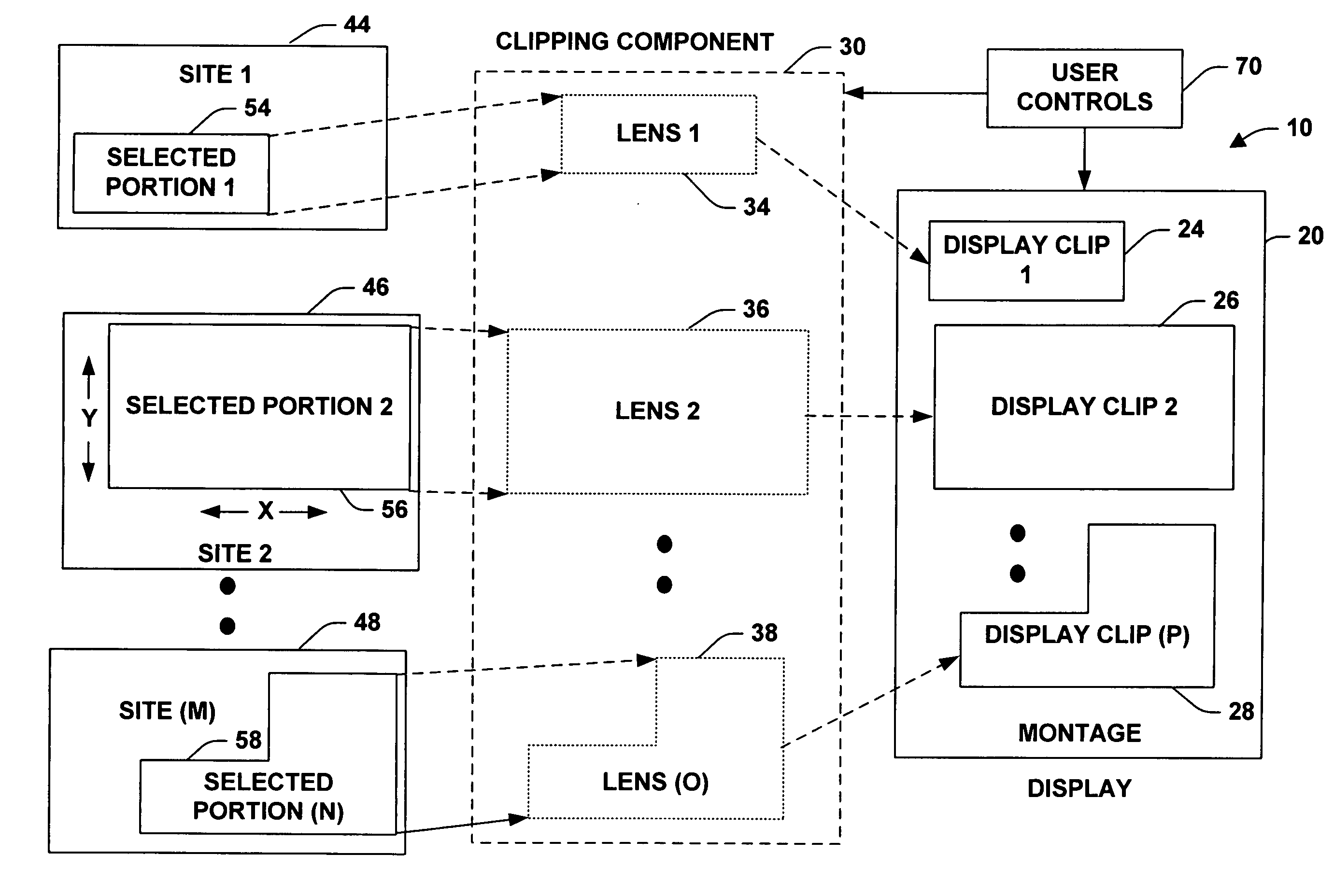
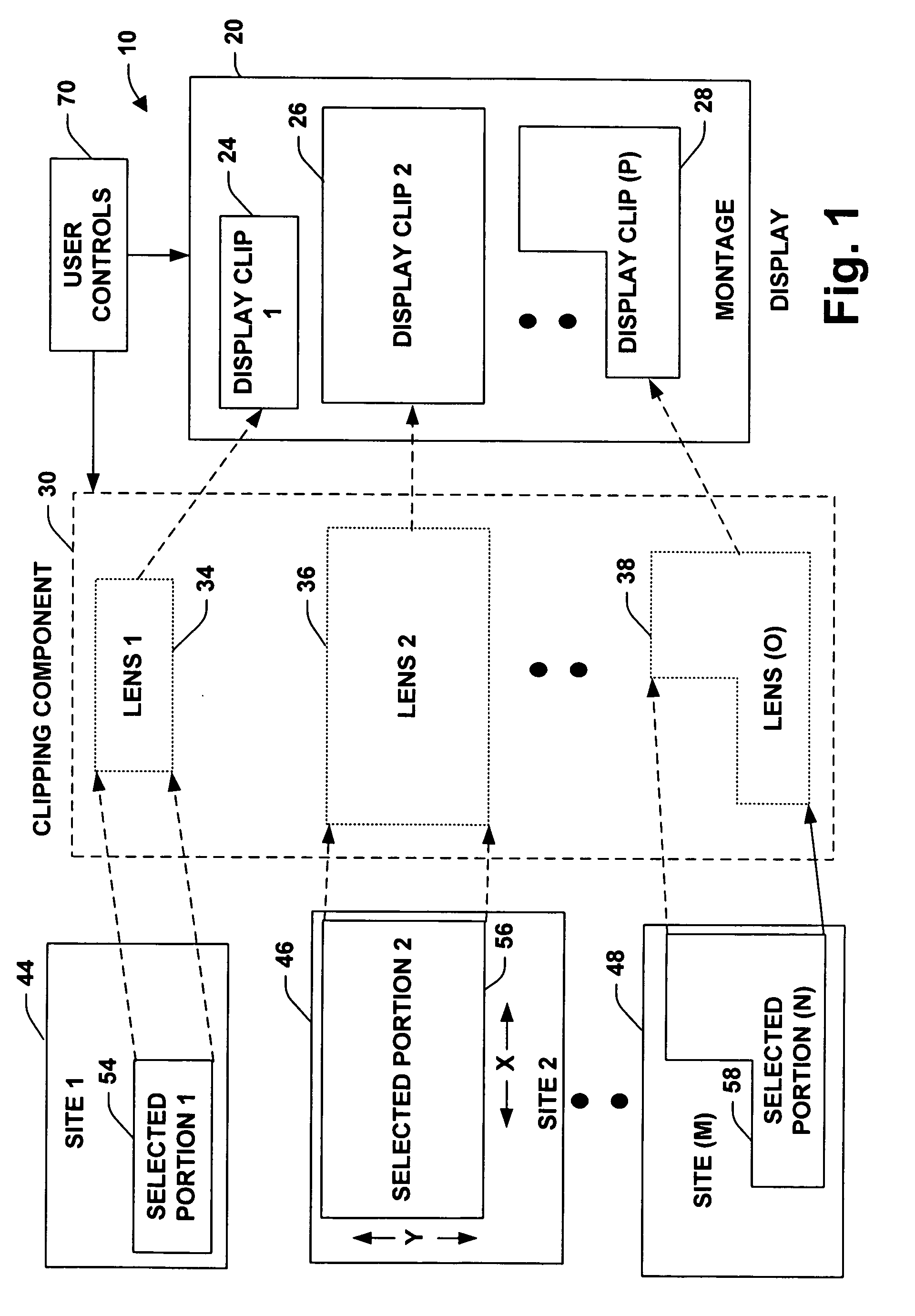
The present invention relates to a system and methodology to assist users with data access activities and that includes such activities as routine web browsing and / or data access applications. A coalesced display or montage of aggregated information is provided that is focused from a plurality of sources to achieve substantially one-button access to user's desired web or data source information / destinations in order to mitigate efforts in retrieving and viewing such information. Past web or other type data access patterns can be mined to predict future browsing sites or desired access locations. A system is provided that builds personalized web portals for associated users based on models mined from past data access patterns. The portals can provide links to web resources as well as embed content from distal (remote) pages or sites producing a montage of web or other type data content. Automated topic classification is employed to create multiple topic-centric views that can be invoked by a user.
Owner:MICROSOFT TECH LICENSING LLC
Enabling online and offline operation
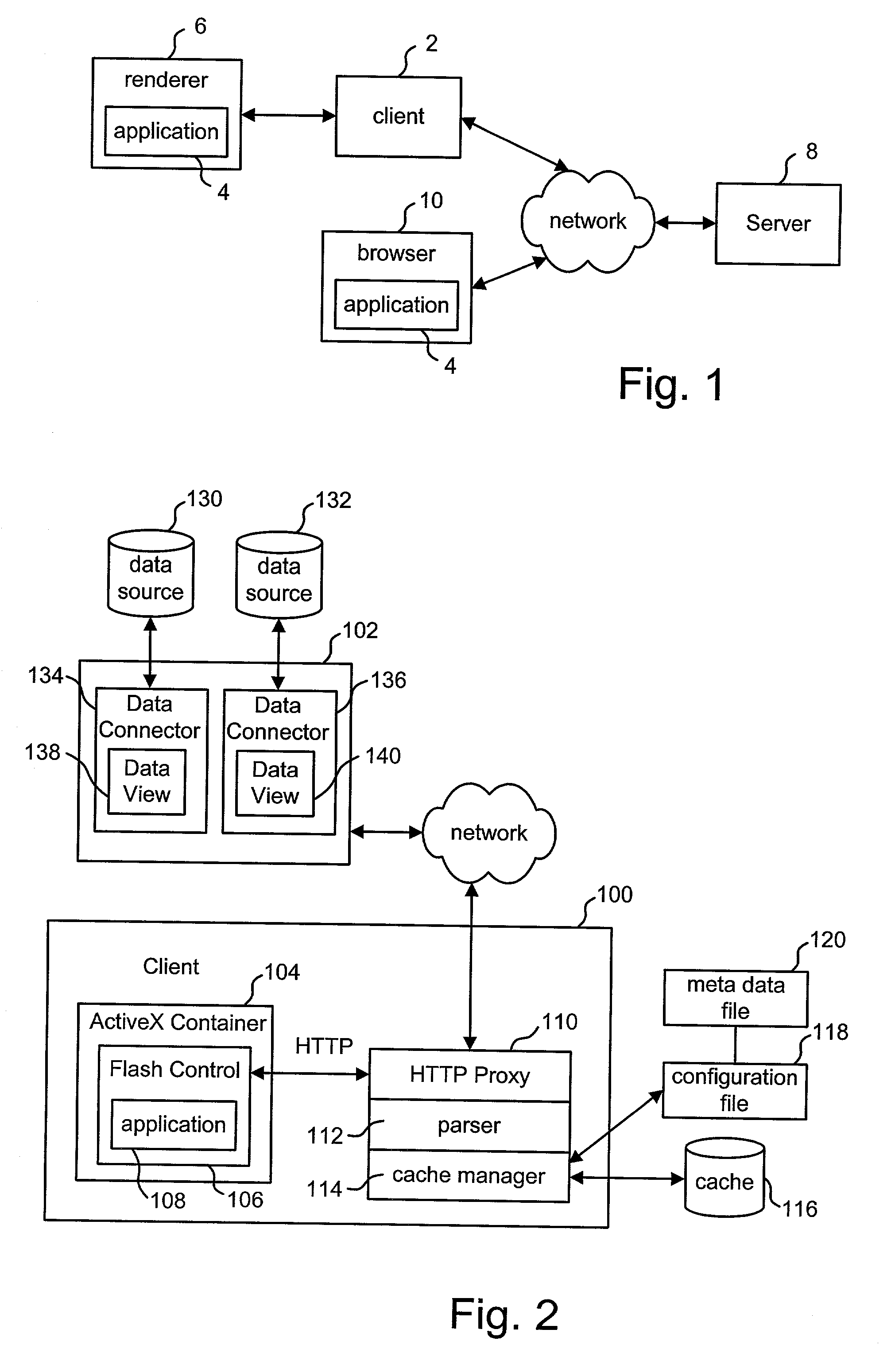
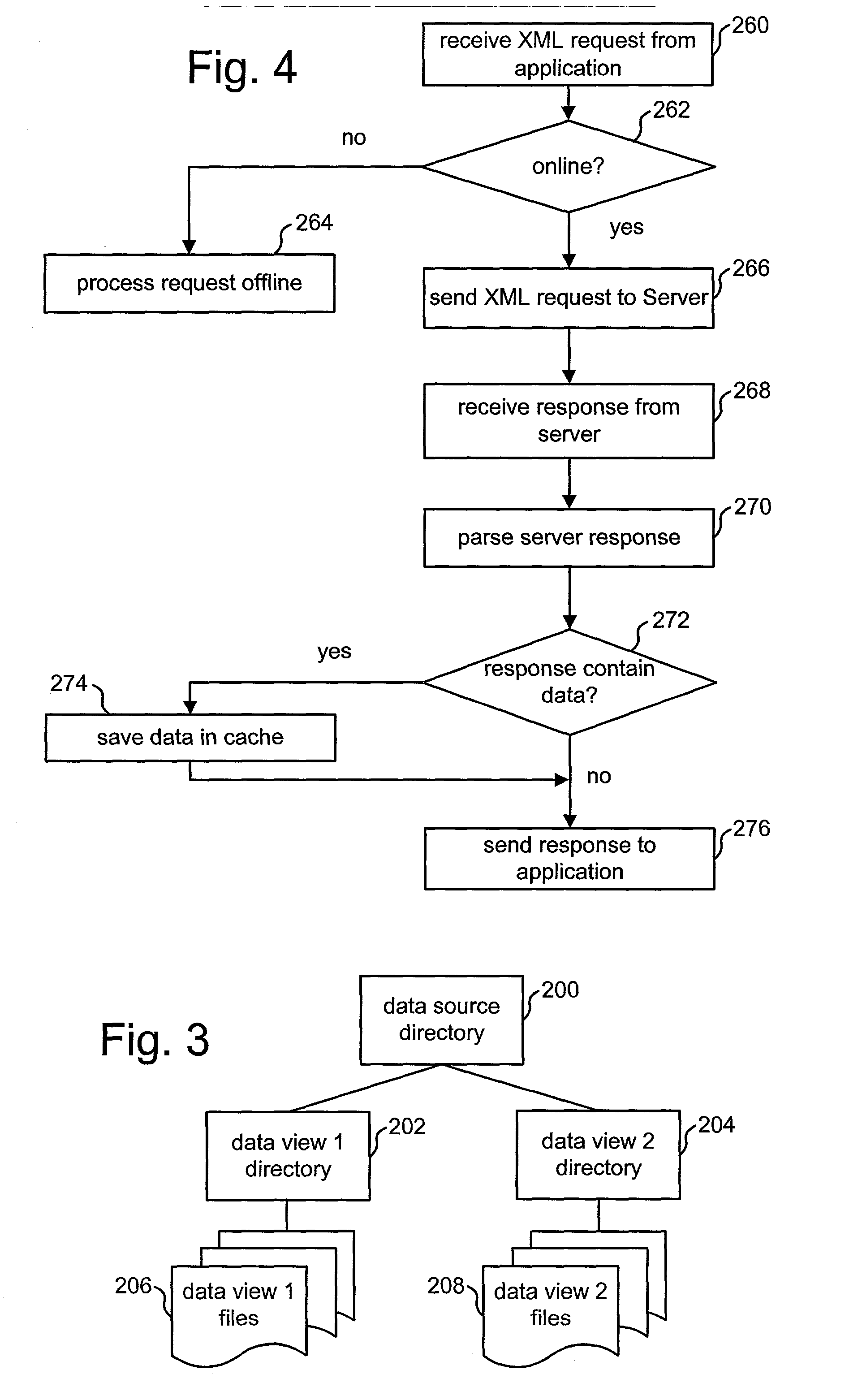
ActiveUS20030158947A1Digital data information retrievalMultiple digital computer combinationsInformation accessData source
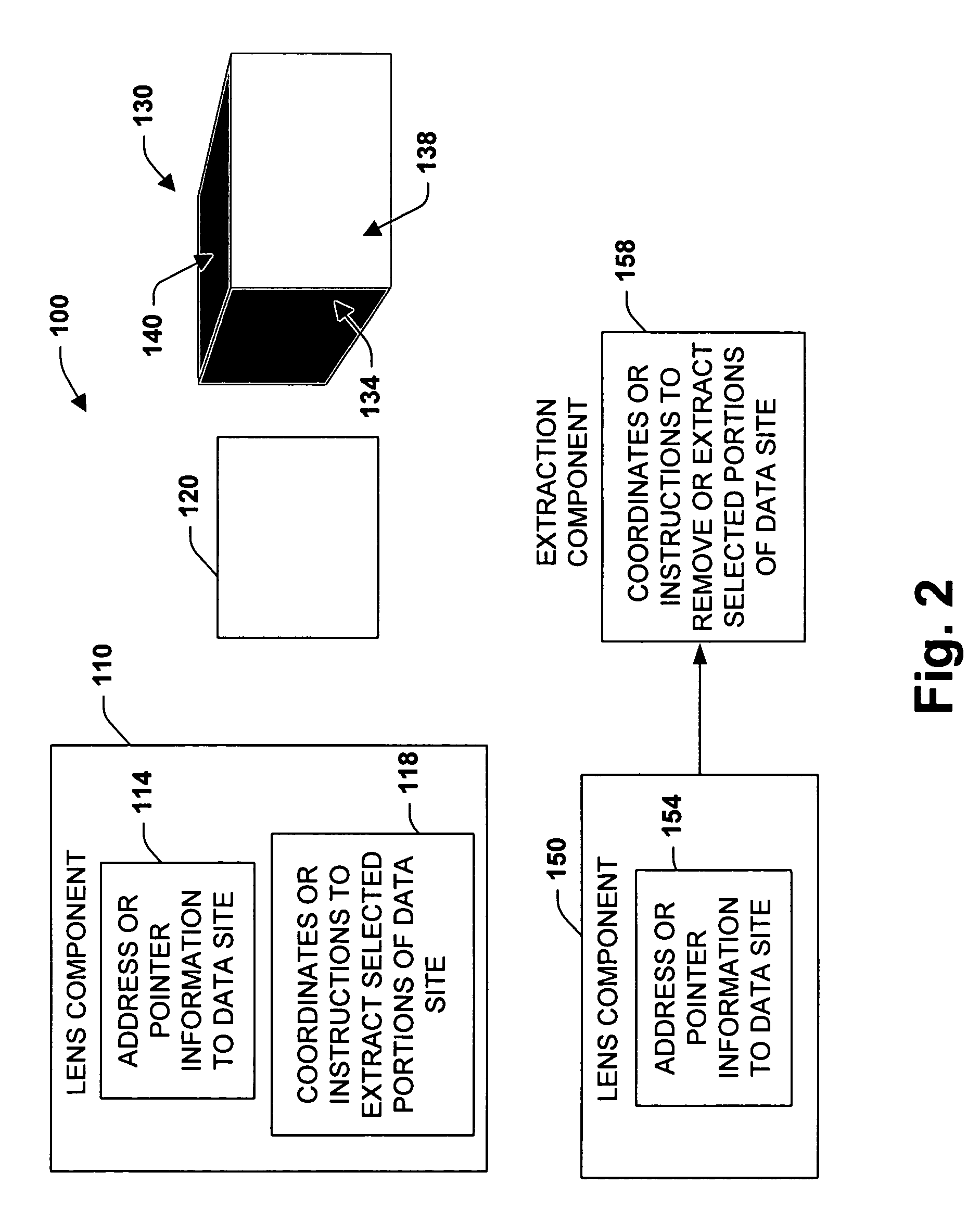
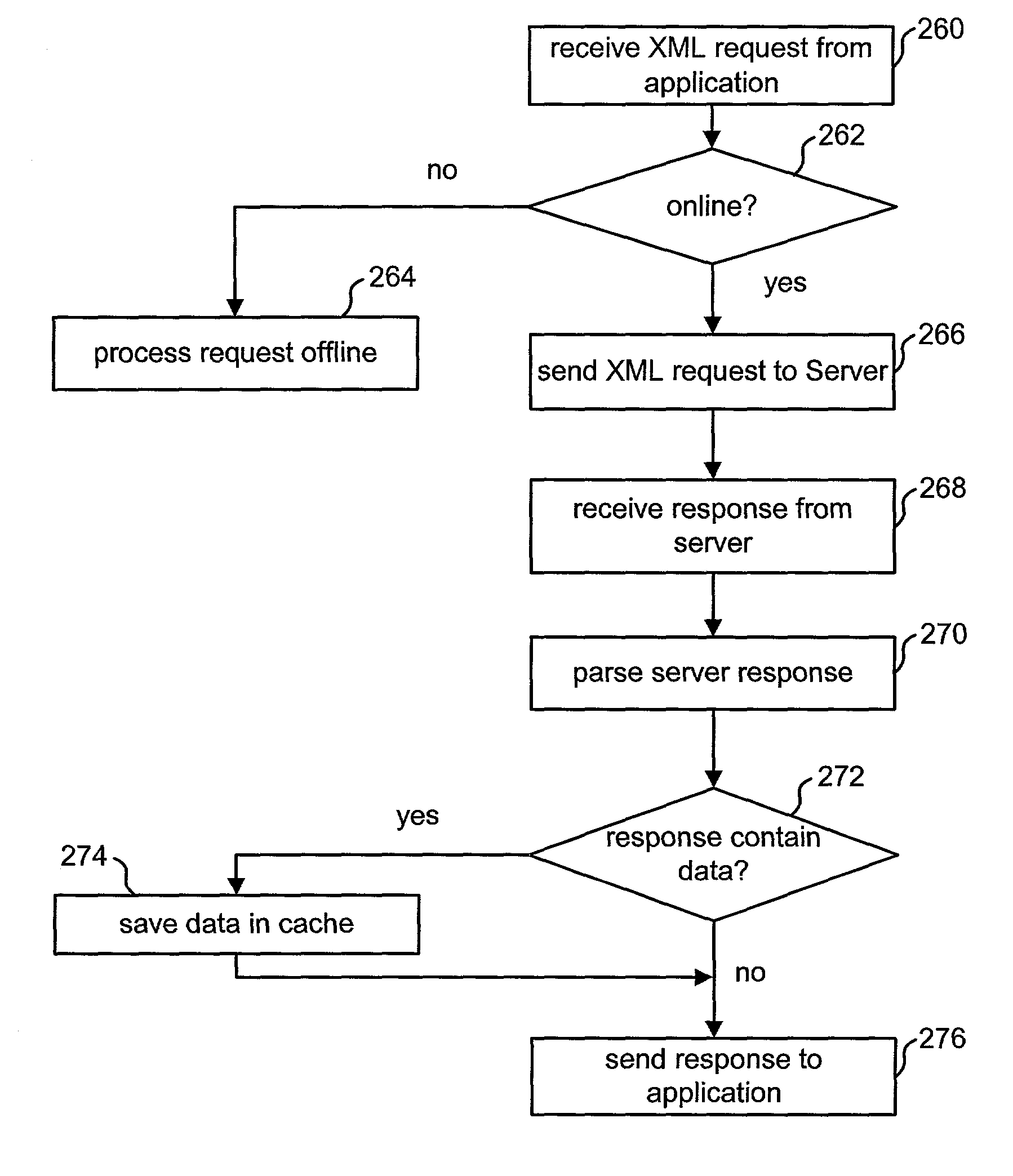
The present invention provides software developers with the capability to create applications that can access information online and offline without having to program such capabilities into their applications. An application can gather information from various remote data sources via a network or other communication means, and still have access to all or a portion of that information when the computing device running the application is no longer connected to the network. In one embodiment, a client manages information access, caching and synchronization for the application. When connected, information accessed is stored in a local data store on (or near) the computing device. When disconnected, requests are run against the local data store instead of the remote data source. When reconnected, information is synchronized between the local data store and the remote data source.
Owner:TAHOE RES LTD
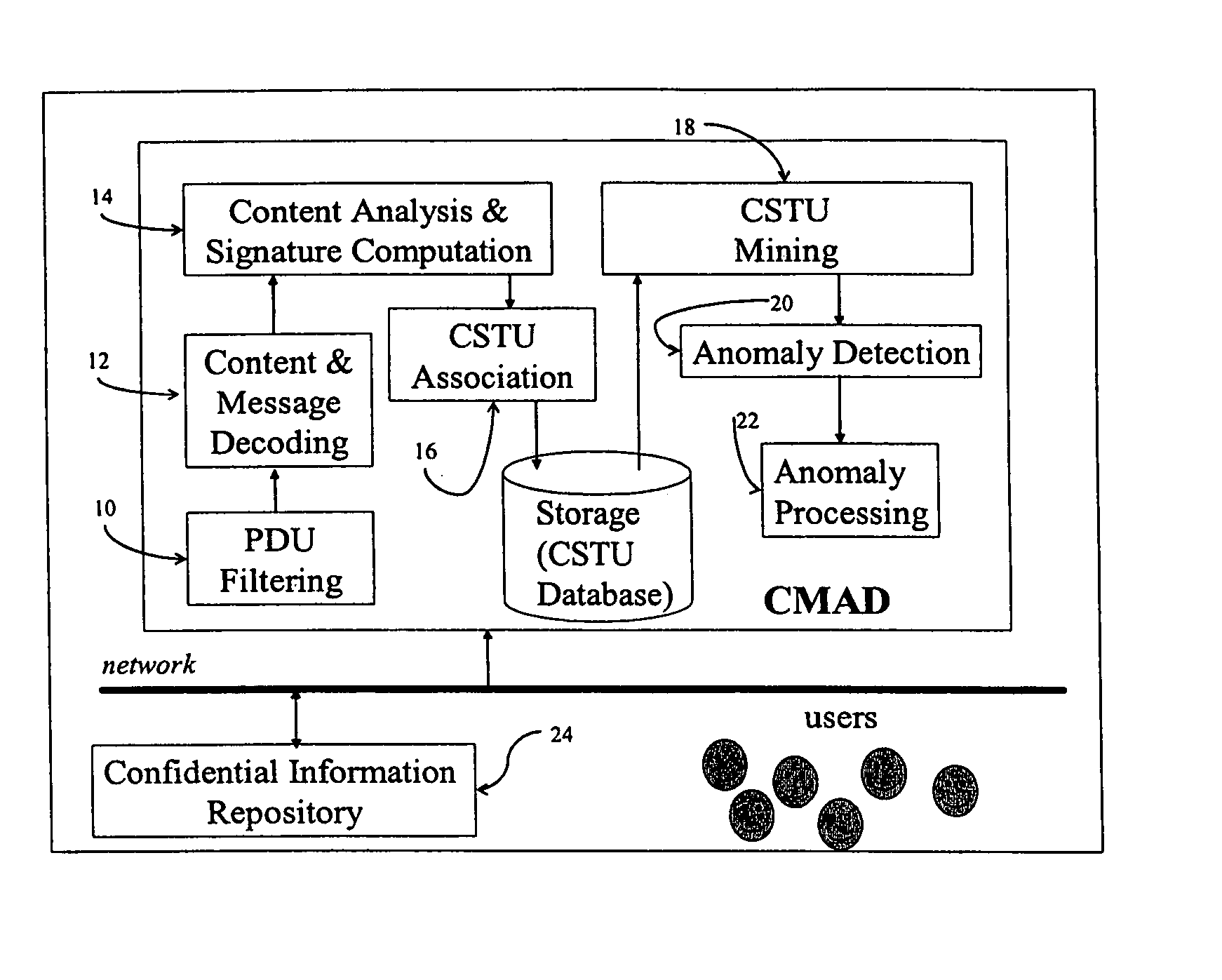
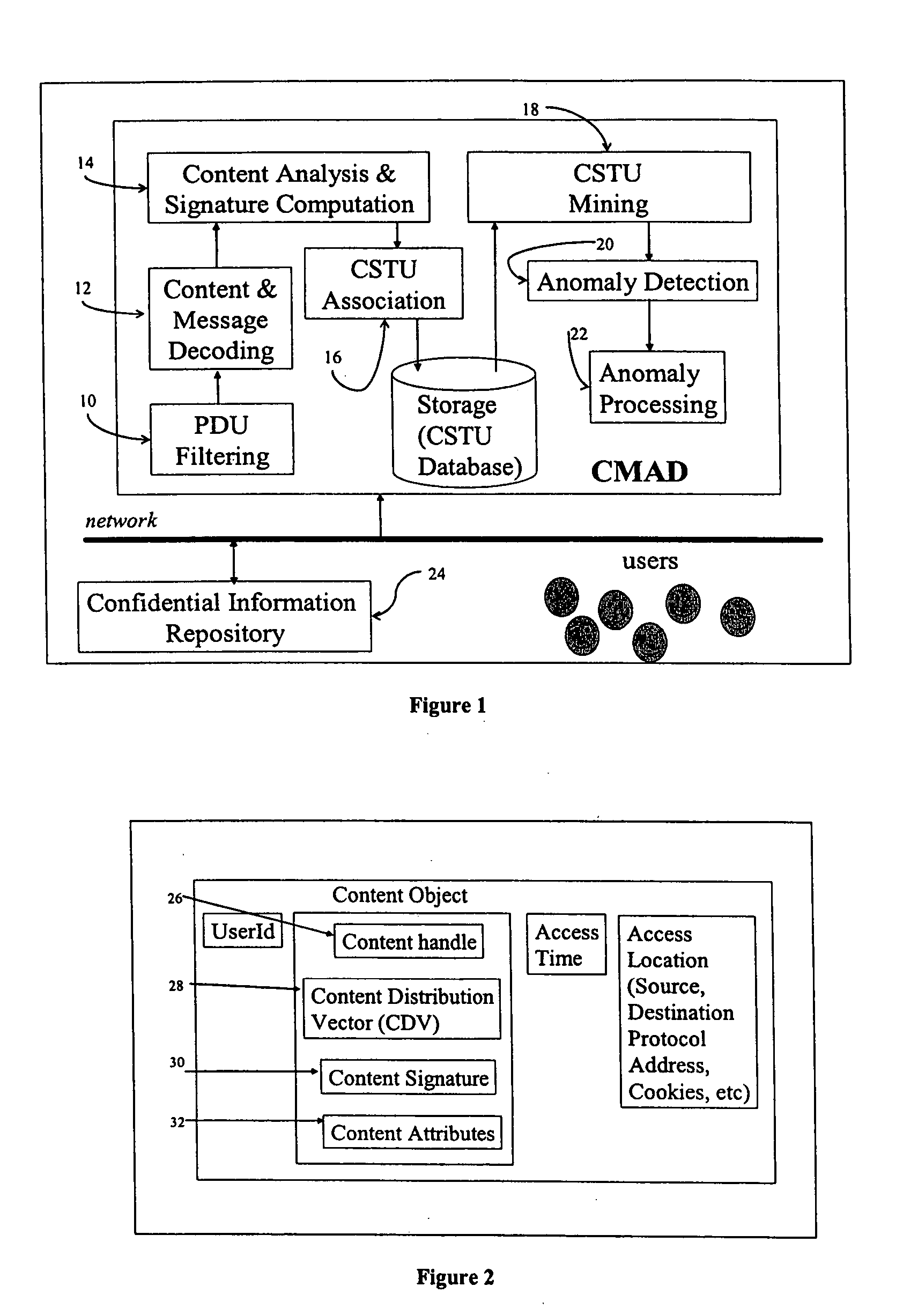
Method and apparatus to detect unauthorized information disclosure via content anomaly detection
ActiveUS20050091532A1Memory loss protectionError detection/correctionInternet privacyAnomaly detection
Method and apparatus to monitor and detect anomalies of information content flows, the method comprising the steps of capturing information access packets, filtering packets to extract information, decoding packets to determine information content, deriving content signatures, trending prototypical behavior, and detecting anomalies of information access, and said apparatus comprising a computing device comprising a network based device that captures the information and produces anomaly information.
Owner:IBM CORP
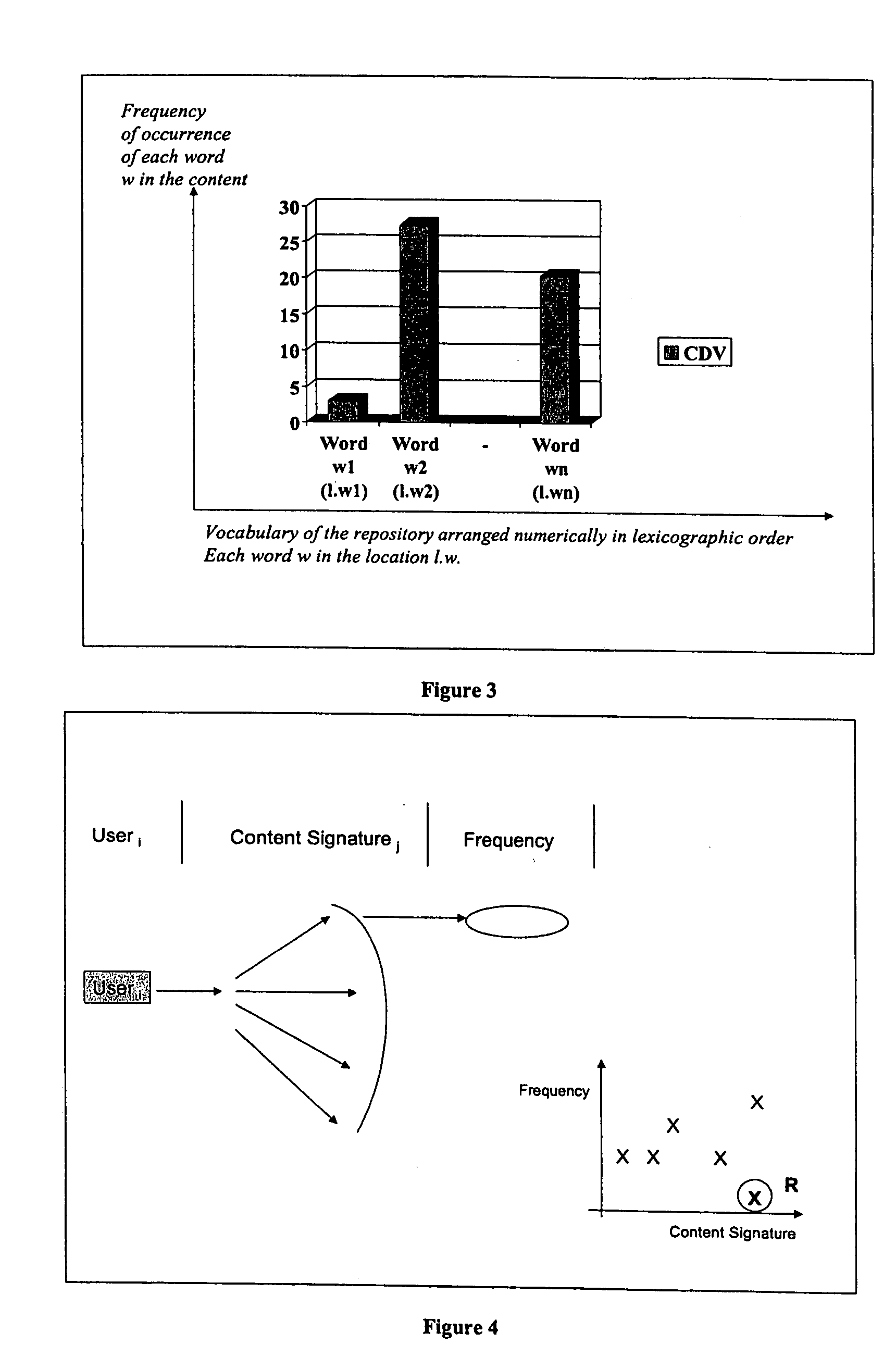
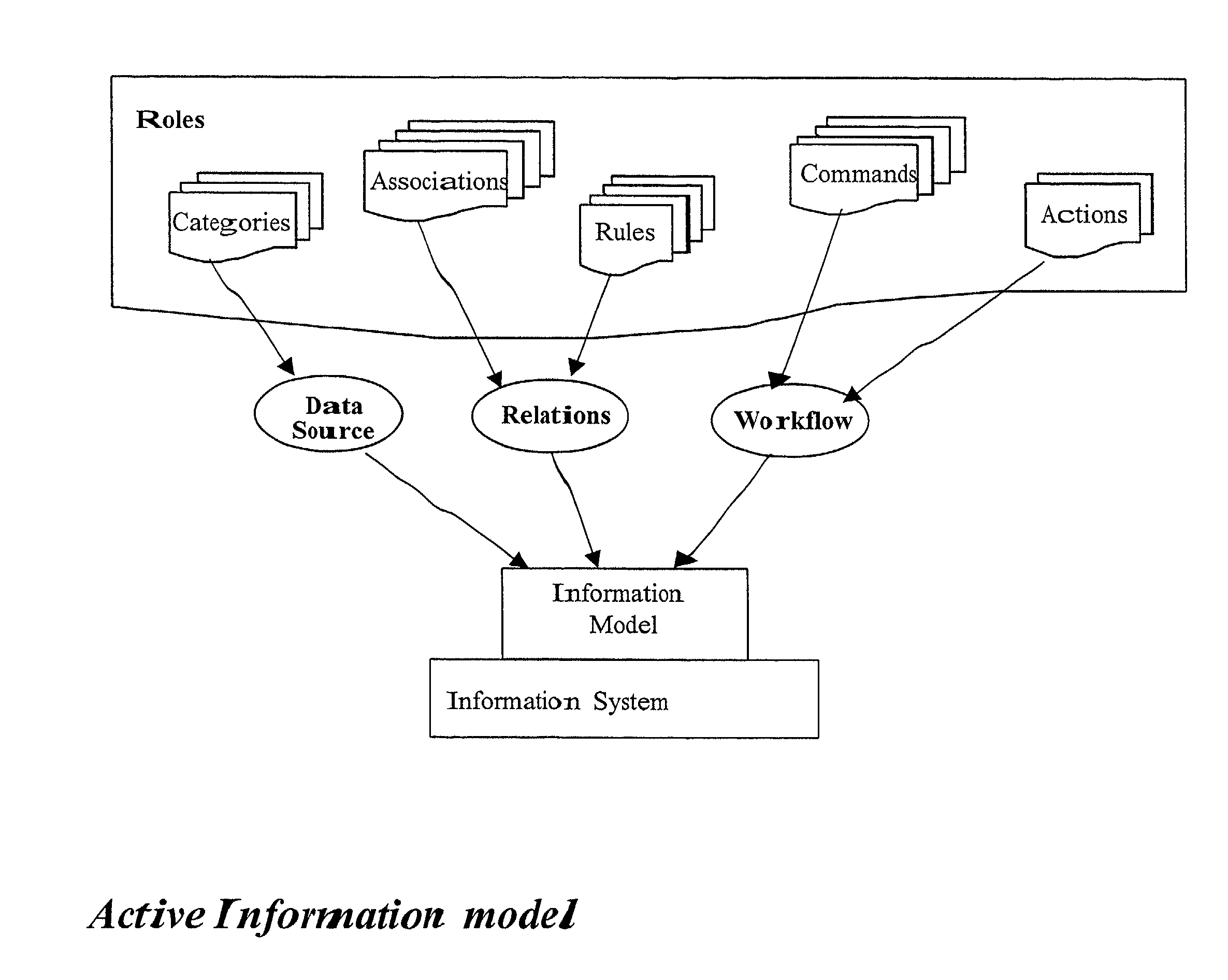
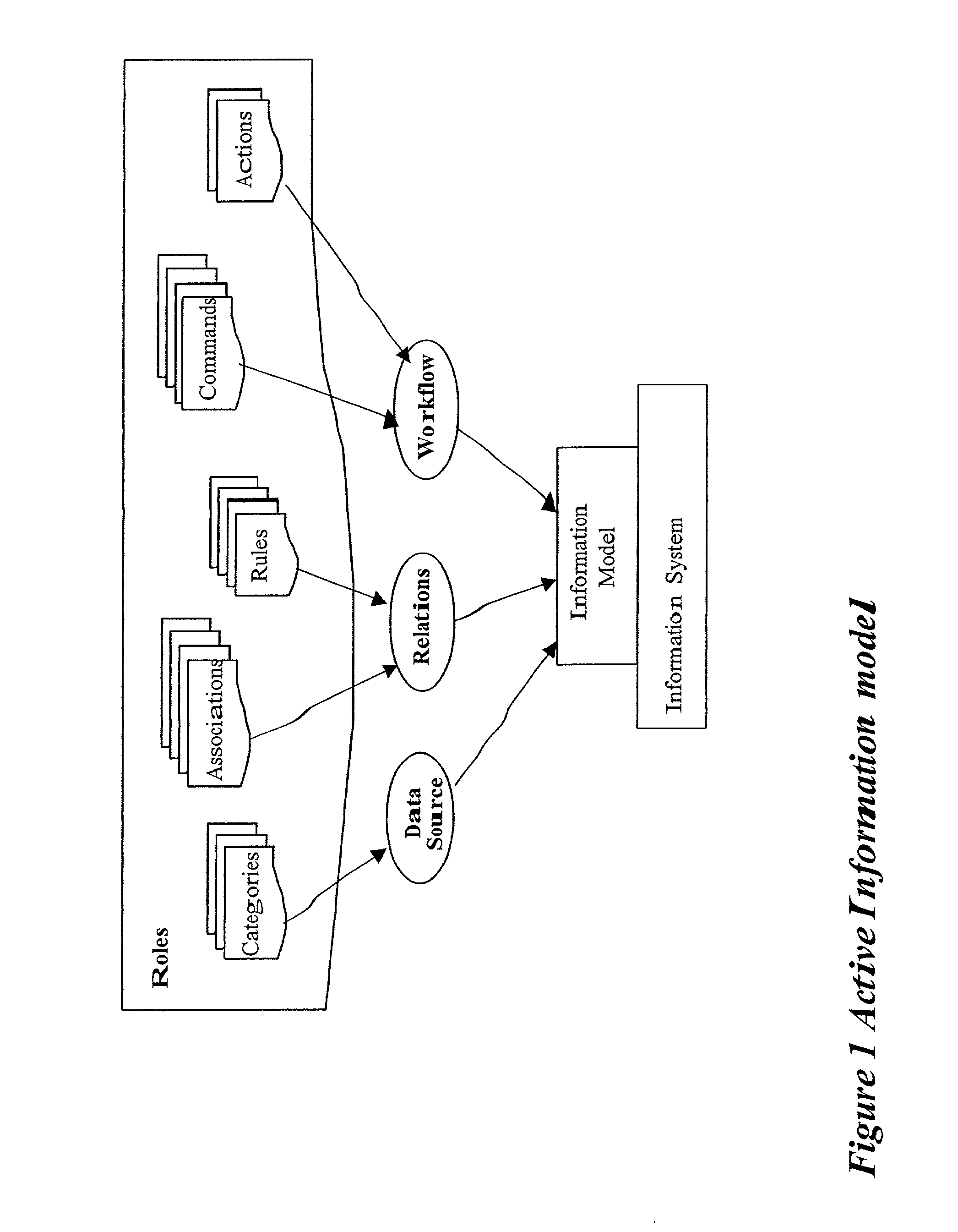
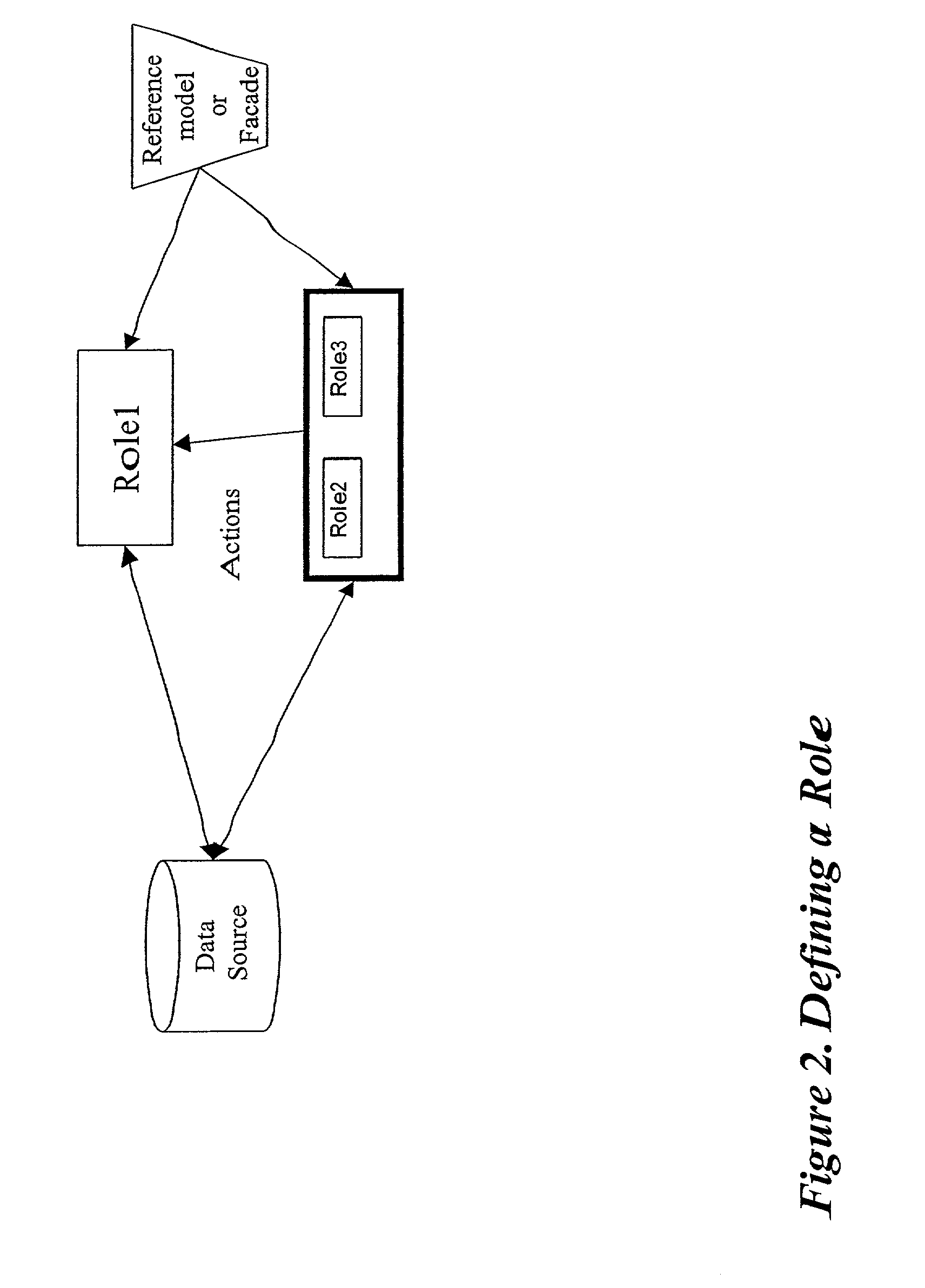
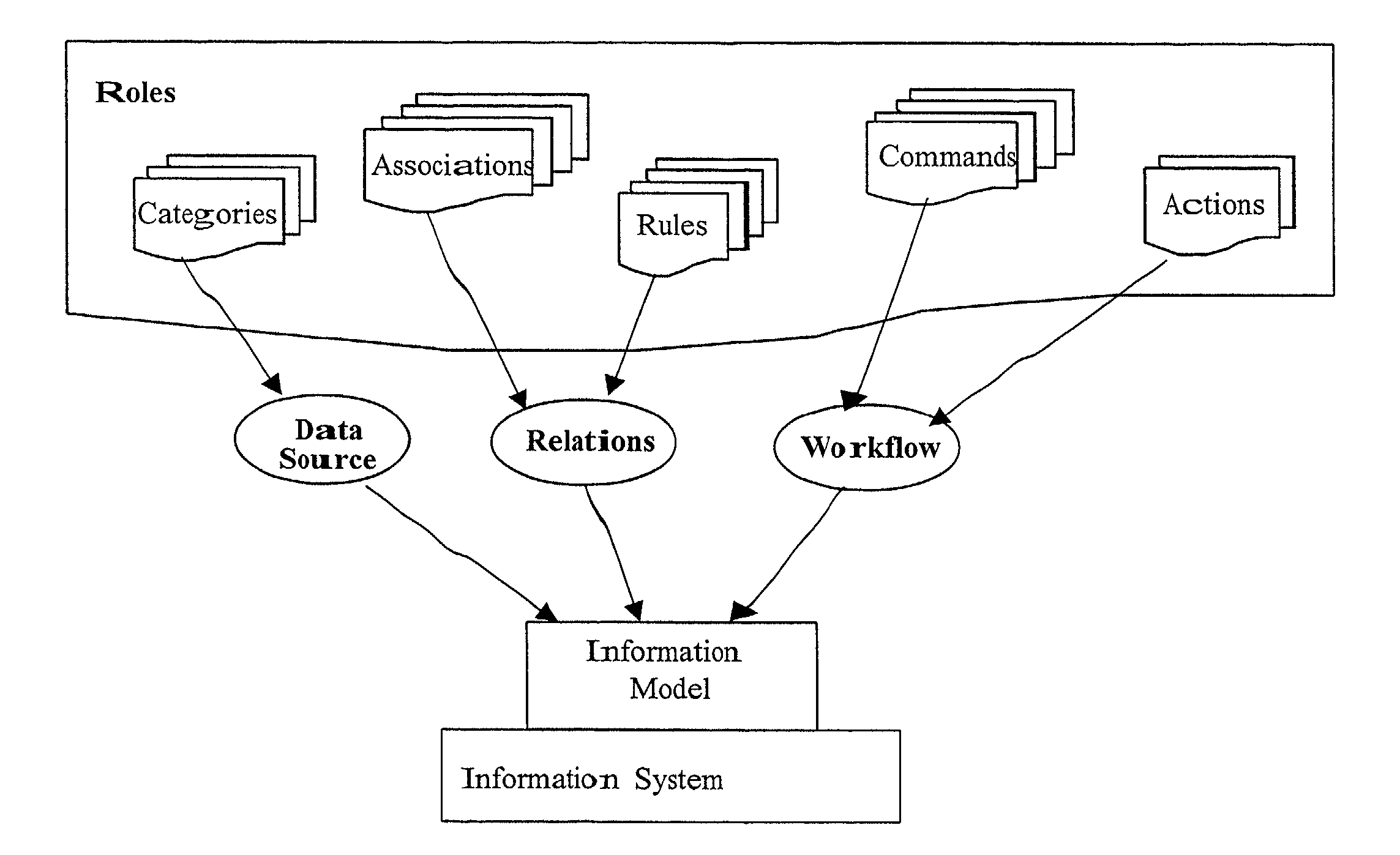
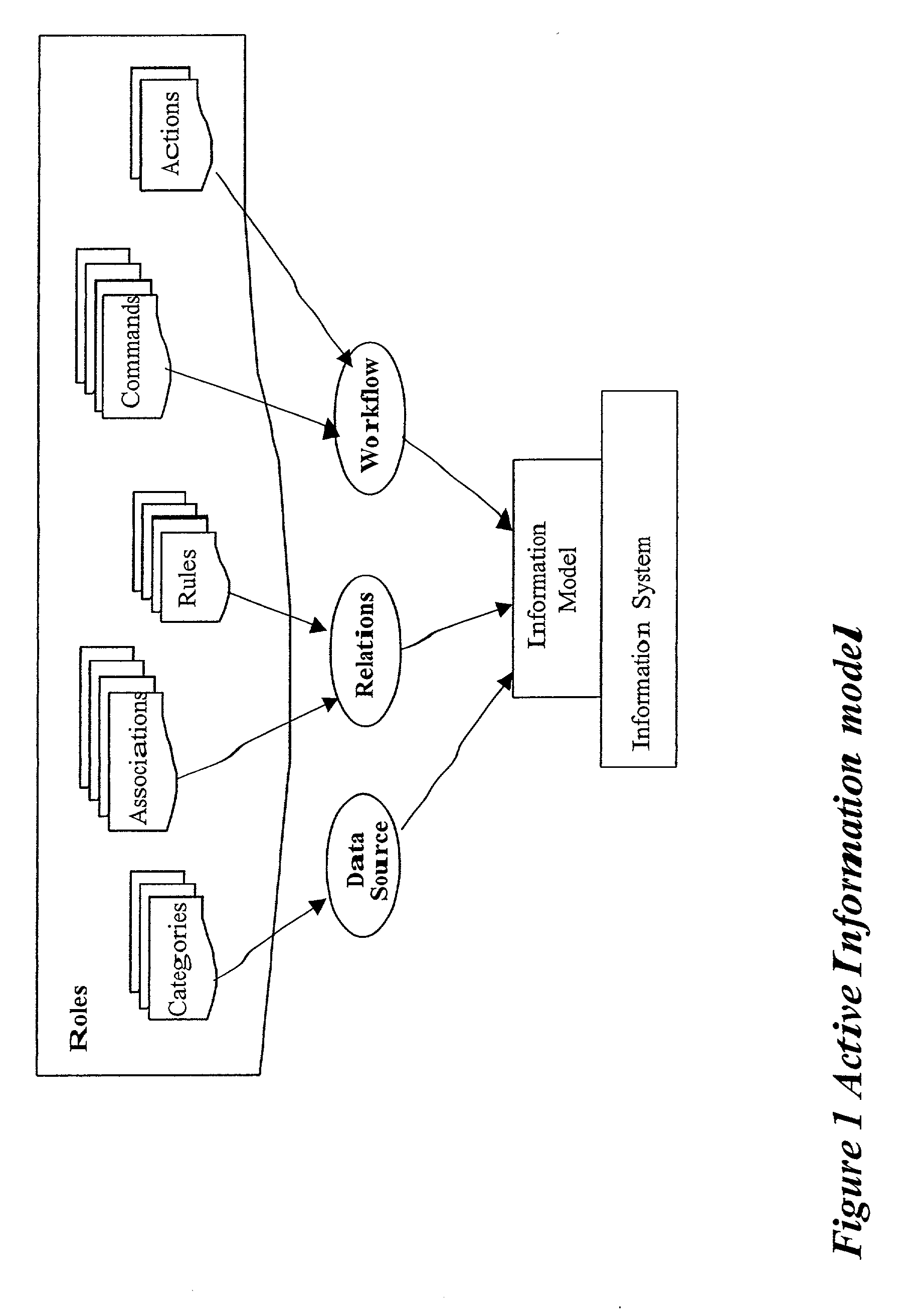
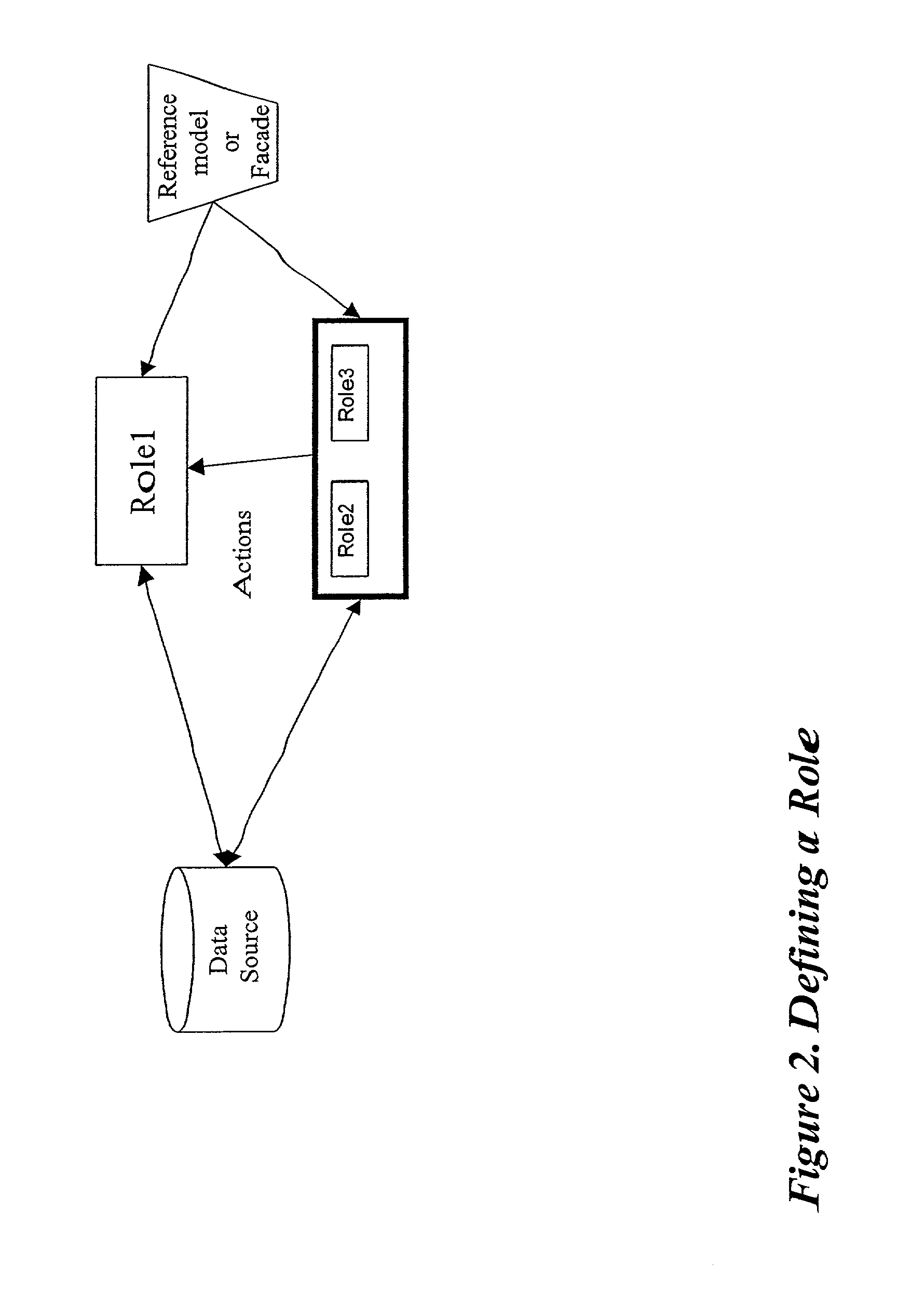
Method and apparatus for implementing an active information model
InactiveUS7328233B2Guaranteed to workMultiple digital computer combinationsOffice automationService provisionActive agent
An active information model constructed from an aggregation of personal information portals containing an active agent. In a preferred embodiment, the system of this invention can be offered as a network service providing for information access and exchange according to the individual users' preferences.
Owner:CORYBANT
Application integration system and method using intelligent agents for integrating information access over extended networks
InactiveUS20050027495A1Easy to readDigital computer detailsCathode-ray tube indicatorsInformation accessProblem statement
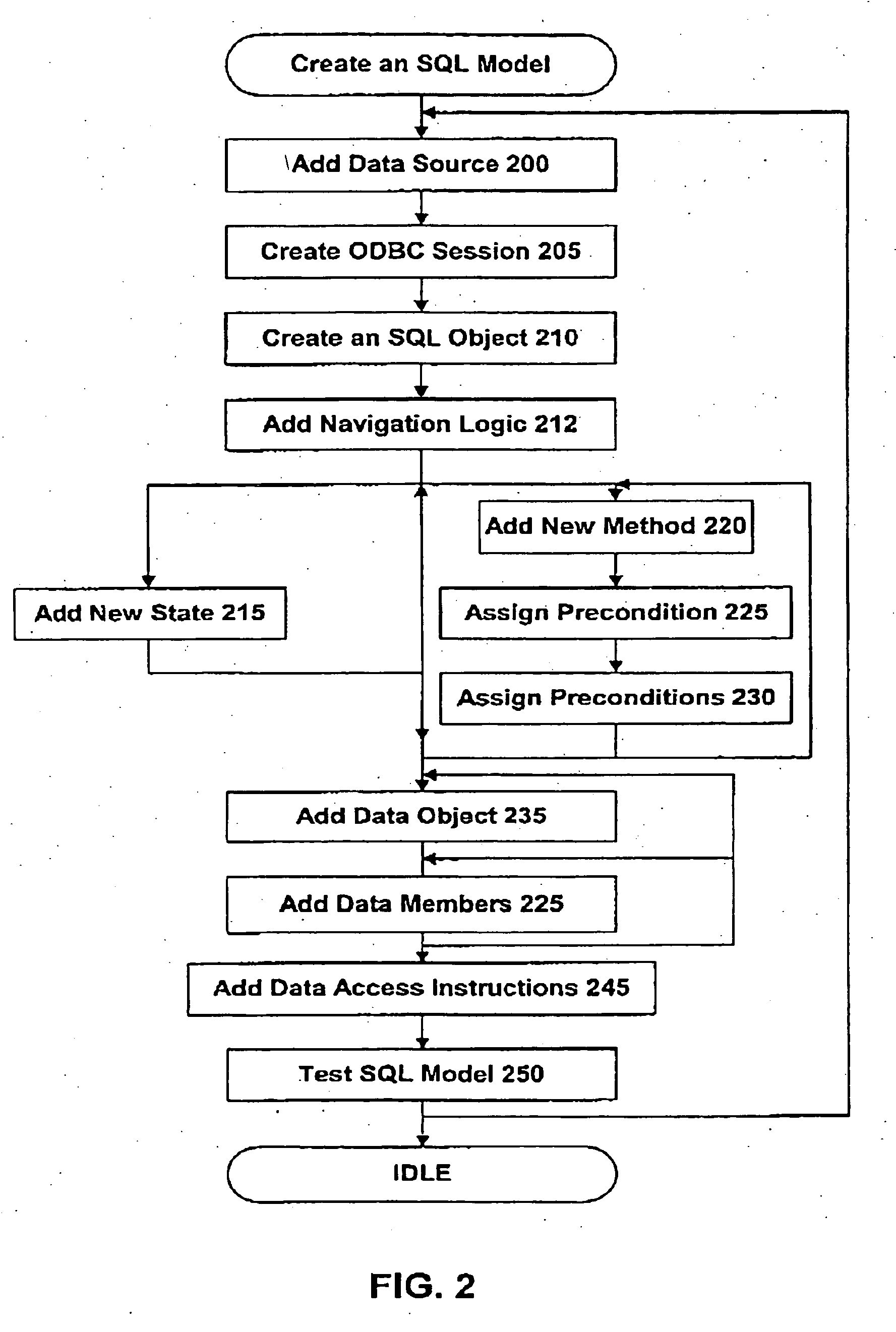
Models that encapsulate information on how remote applications are controlled and data is accessed are created to be used by a runtime agent that intelligently reasons out goal-oriented plans and execute tasks to solve problem statements generated by a user interface or other software agents. The models may be used to assemble workflows using a reasoning process. In particular, the models of the present invention include a state that includes a planning state and a navigational value. In embodiments of the invention, the models may include intelligent agents, a loop state, submodel invocation that allows the models to invoke agents over a network, and the ability to integrate the three application layers in a computer.
Owner:CELCORP
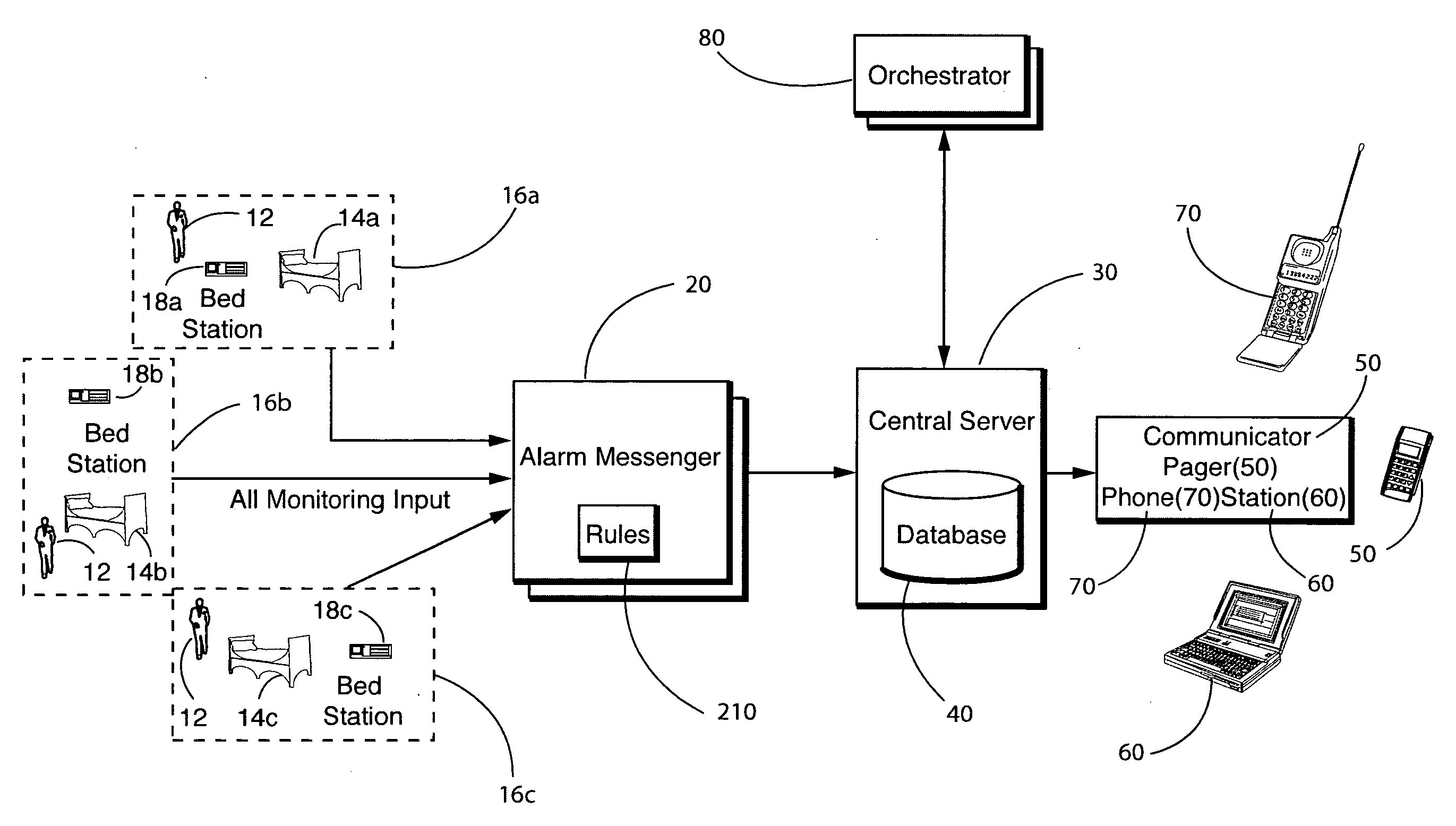
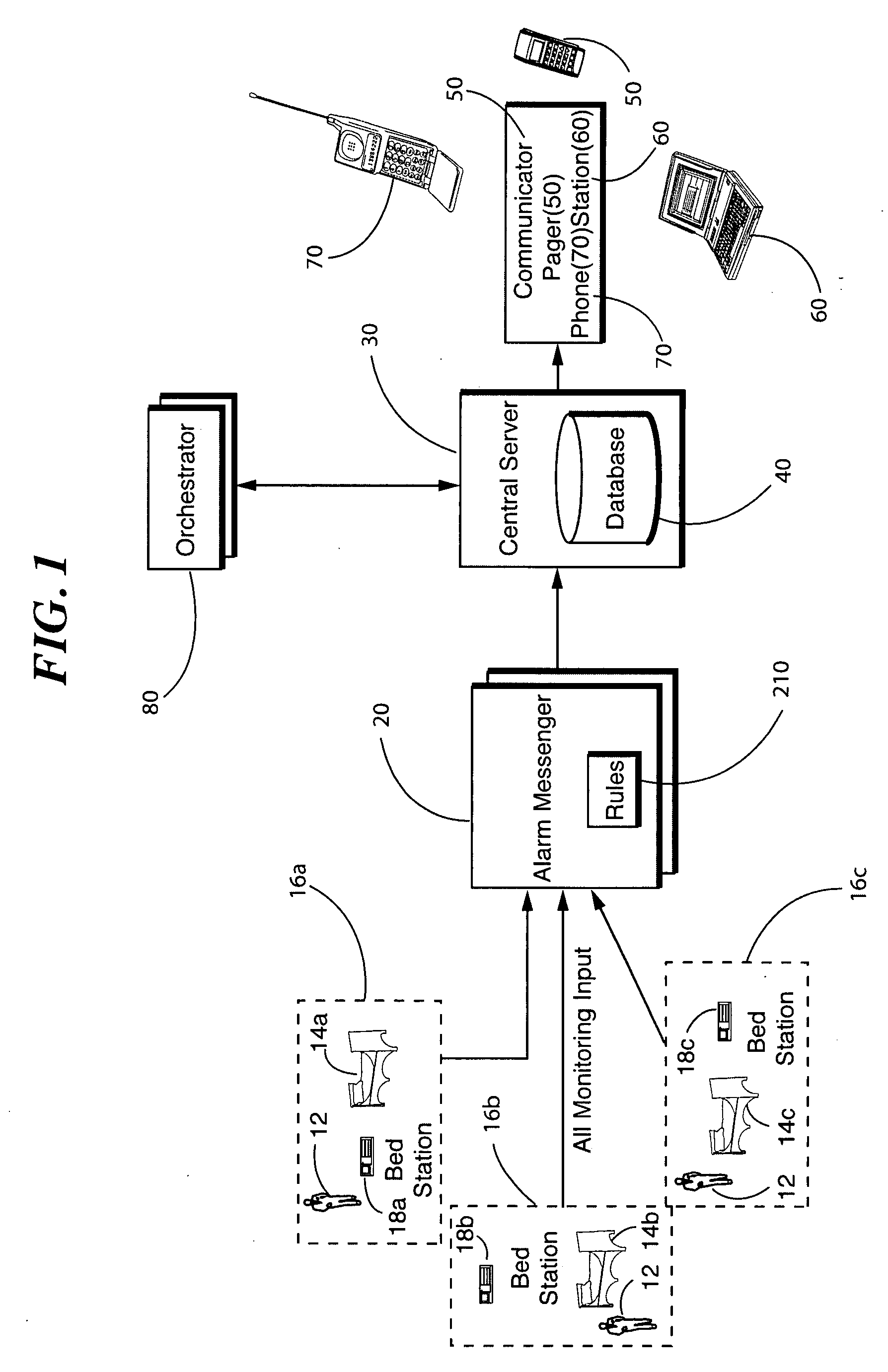
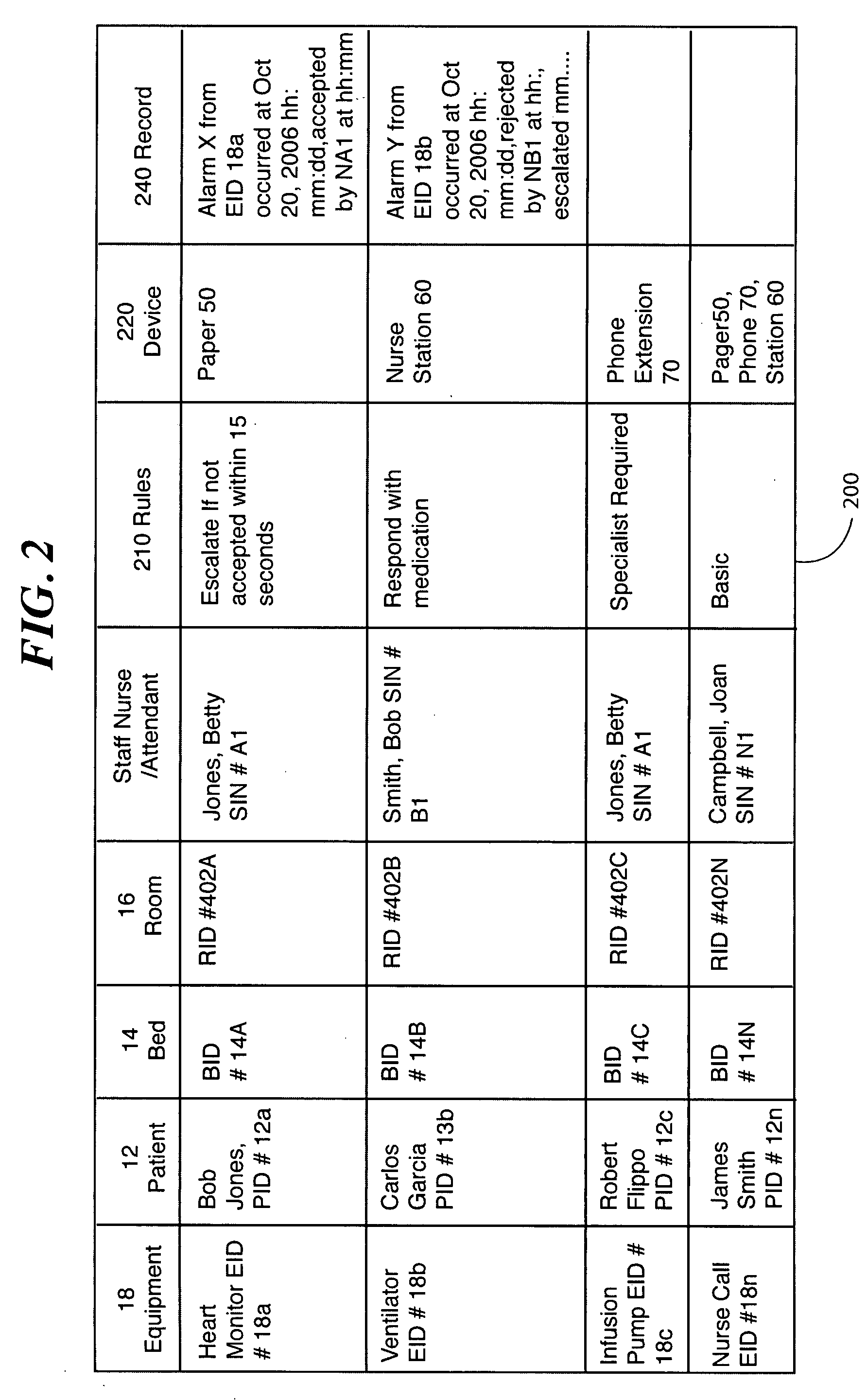
Method and system for medical alarm monitoring, reporting and normalization
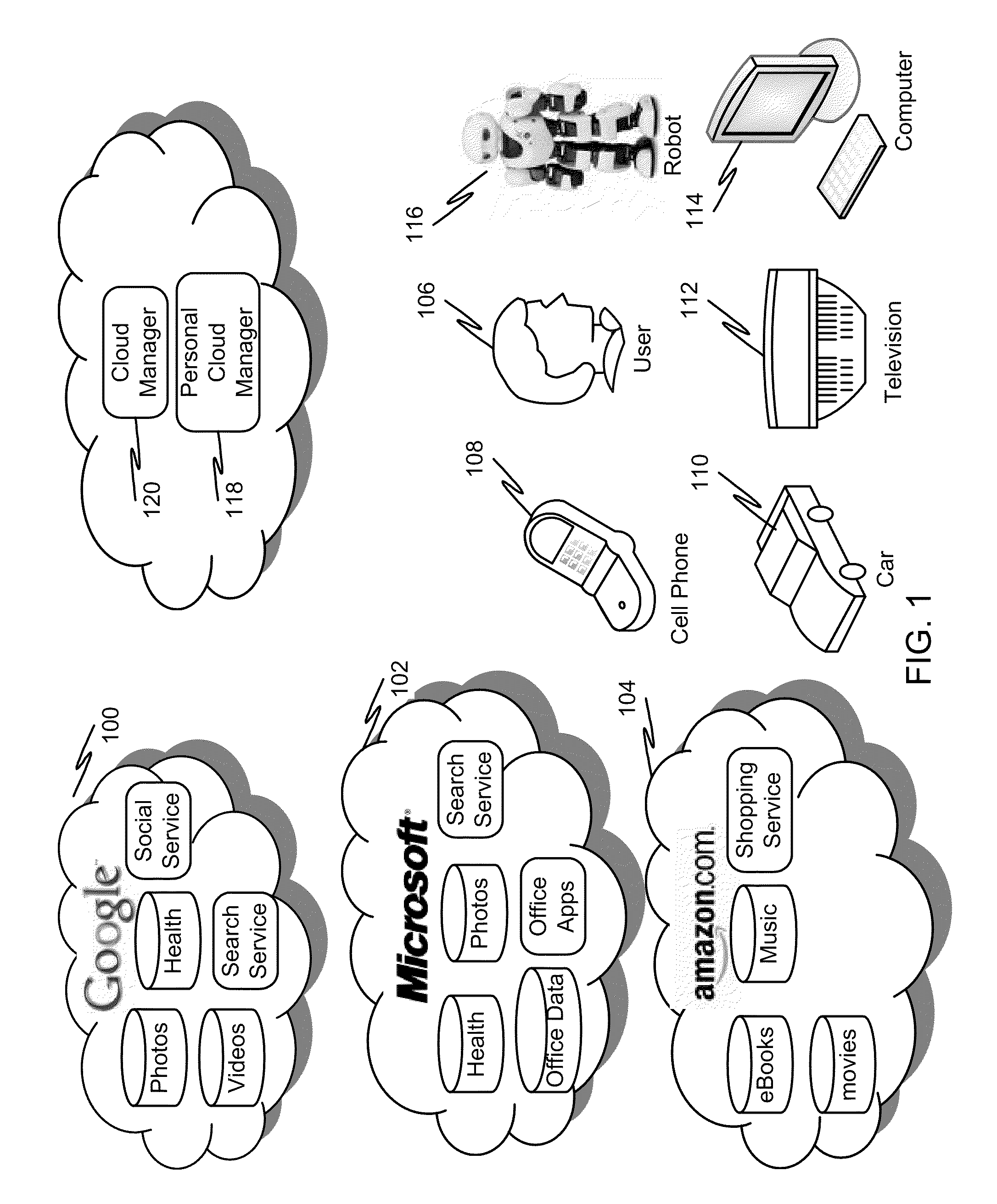
ActiveUS20070229249A1Healthcare resources and facilitiesSubscribers indirect connectionInformation accessComputer science
A system for monitoring and reporting medical alarms includes an alarm messenger for receiving an alarm signal from monitored equipment. The alarm signal includes information to enable determination of the location of the monitored equipment. The alarm messenger outputs an alarm messenger signal including the information. A database includes a master association table stored in the database. A central server receives the alarm signal, utilizes the information from the alarm signal to access the master association table to determine alarm information and, in response to the alarm information, notifies the appropriate staff of an alarm condition.
Owner:EMERGIN
Location based authorization of financial card transactions systems and methods
ActiveUS8166068B2Digital data processing detailsMultiple digital computer combinationsInformation accessNetwork connection
Owner:QWEST
Method of universal file access for a heterogeneous computing environment
ActiveUS7774391B1Simple methodReduce the numberData processing applicationsFile access structuresOperational systemAuto-configuration
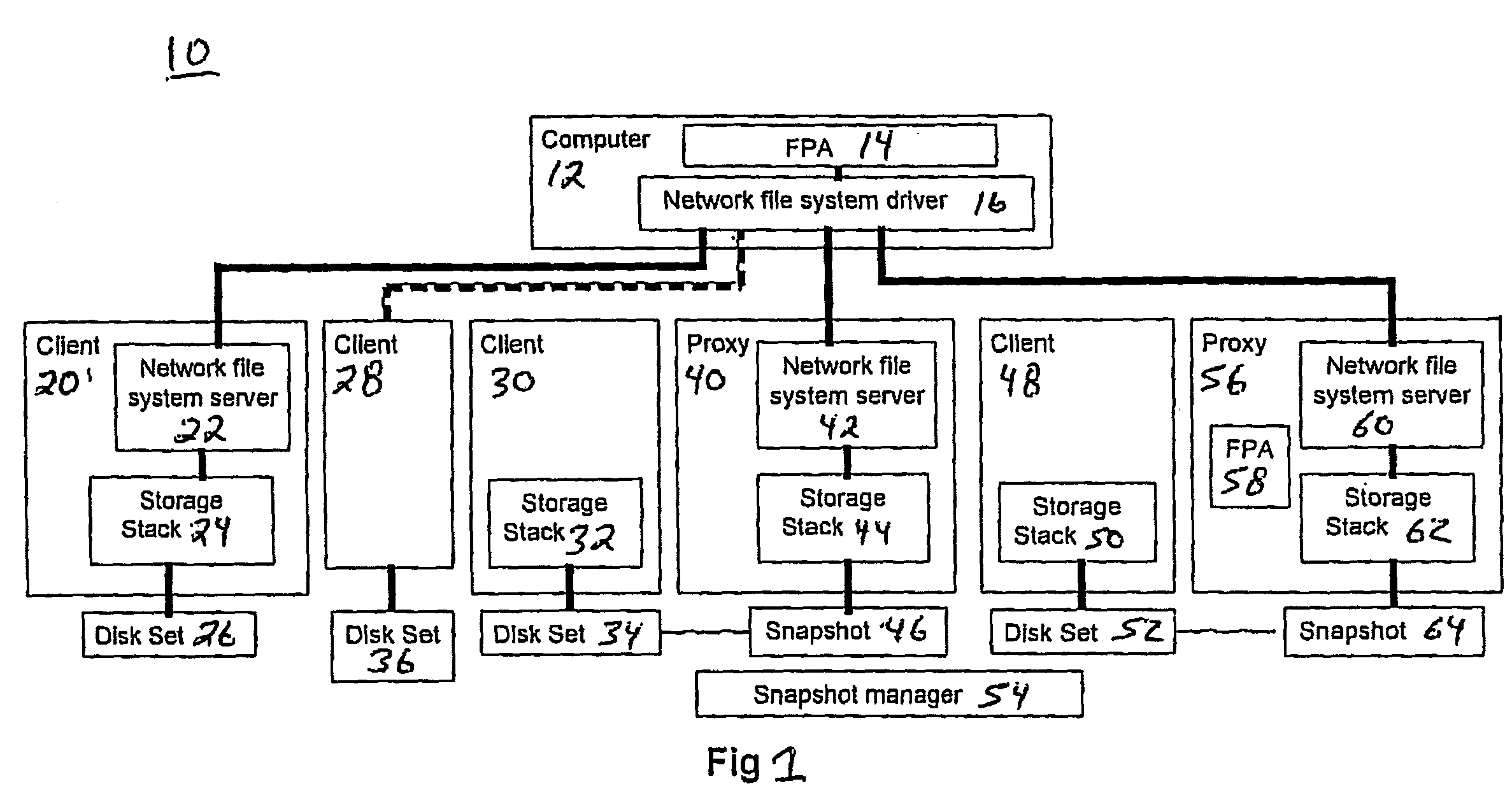
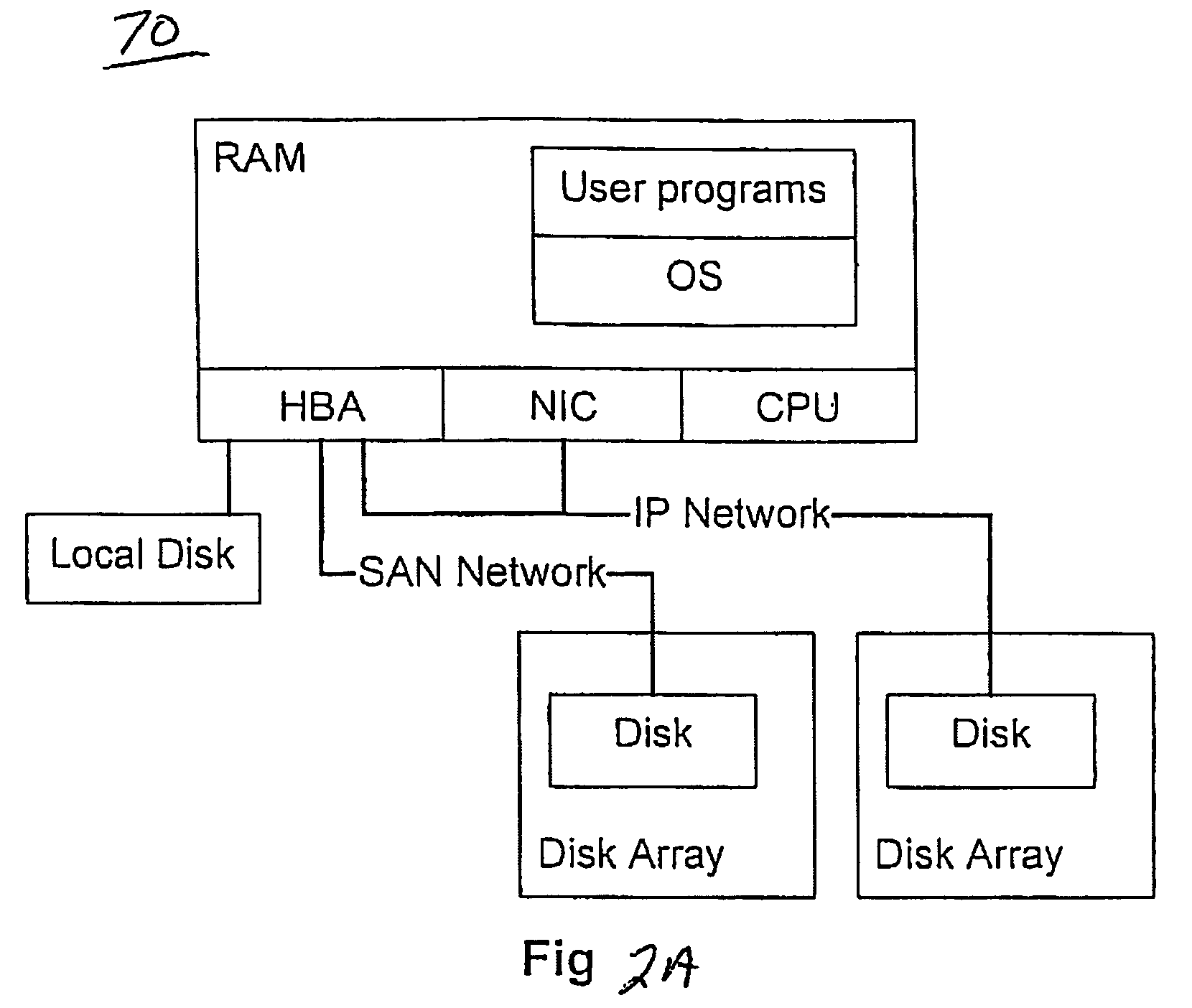
An architecture and system are described that provide a unified file access service within in a managed computing environment composed of diverse networks, computing devices, and storage devices. The service provides mechanisms for remotely accessing the file systems of any managed computer or disk snapshot, independently of the computer's current state (powered on, suspended or powered off), its location within the environment, its hardware type (virtual vs. physical), its operating system type, and its file system formats. The system isolates centralized FPAs from the details of clients, proxies and storage elements by providing a service that decomposes offloaded file system access into two steps. A FPA or a requester acting on behalf of the FPA first expresses the disk set or the computer containing the file systems it wishes to access, along with requirements and preferences about the access method. The service figures out an efficient data path satisfying the FPA's needs; and then automatically configures a set of storage and computing resources to provide the data path. The service then replies with information about the resources and instructions for using them. The FPA then accesses the requested file systems using the returned information.
Owner:VMWARE INC
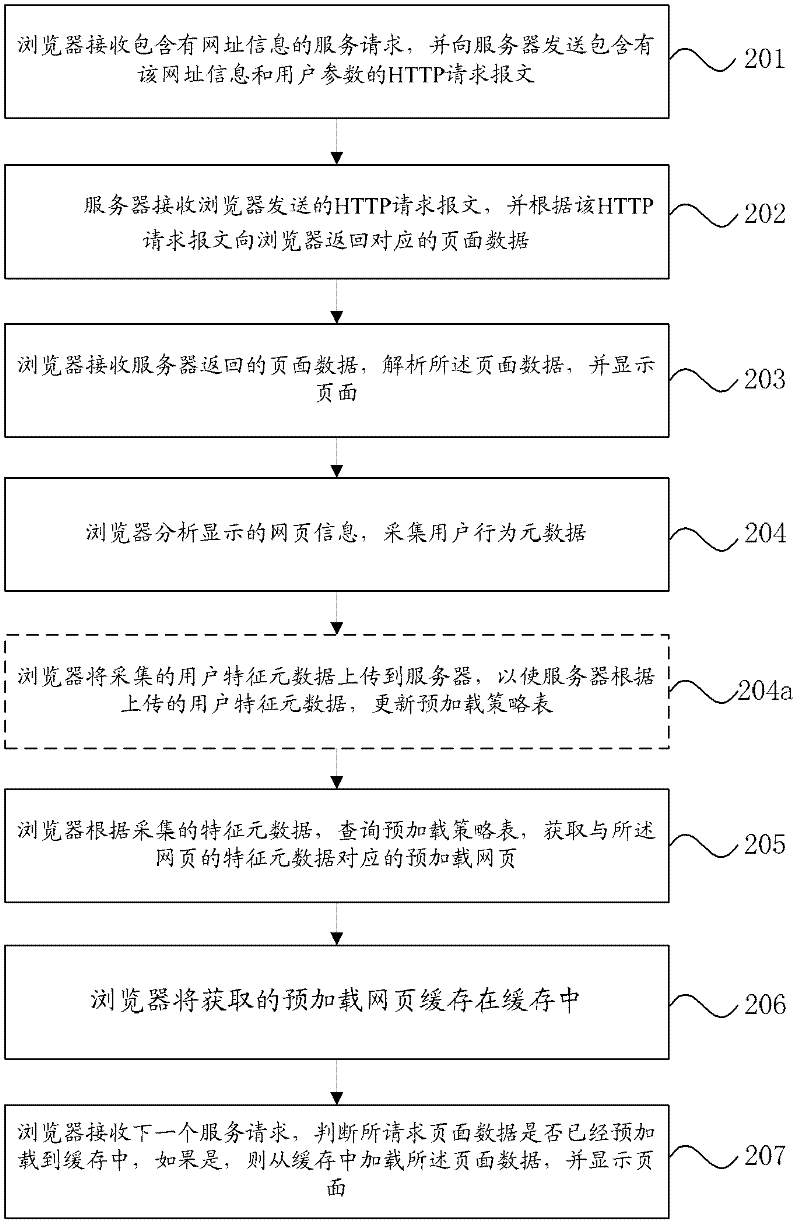
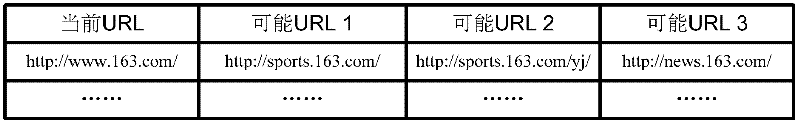
Method, device and system of webpage content preloading
InactiveCN102446222AOvercome long waiting timesImprove experienceDigital data information retrievalSpecial data processing applicationsCommunications systemInformation access
The embodiment of the invention discloses a webpage content preloading method, which includes collecting webpage feature metadata according to webpage information accessed by users at present, inquiring a preloading strategy table to obtain preloading data according to the collected feature metadata, and enabling the obtained preloading data to be loaded in a cache. Correspondingly, a webpage content preloading device, a preloading strategy table establishing method and a communication system are further disclosed. By means of the technical scheme, under the condition of guaranteeing of normal browsing service of users, a caching module caches the next webpage data which the users may access in advance, thereby reading data from the cache directly when users requests a next webpage, solving the problem of long waiting time for the users caused by the fact that a browser needs to read a large amount of data from a server after the users operate at the front end in a network management system, and improving experience of the users.
Owner:HUAWEI TECH CO LTD
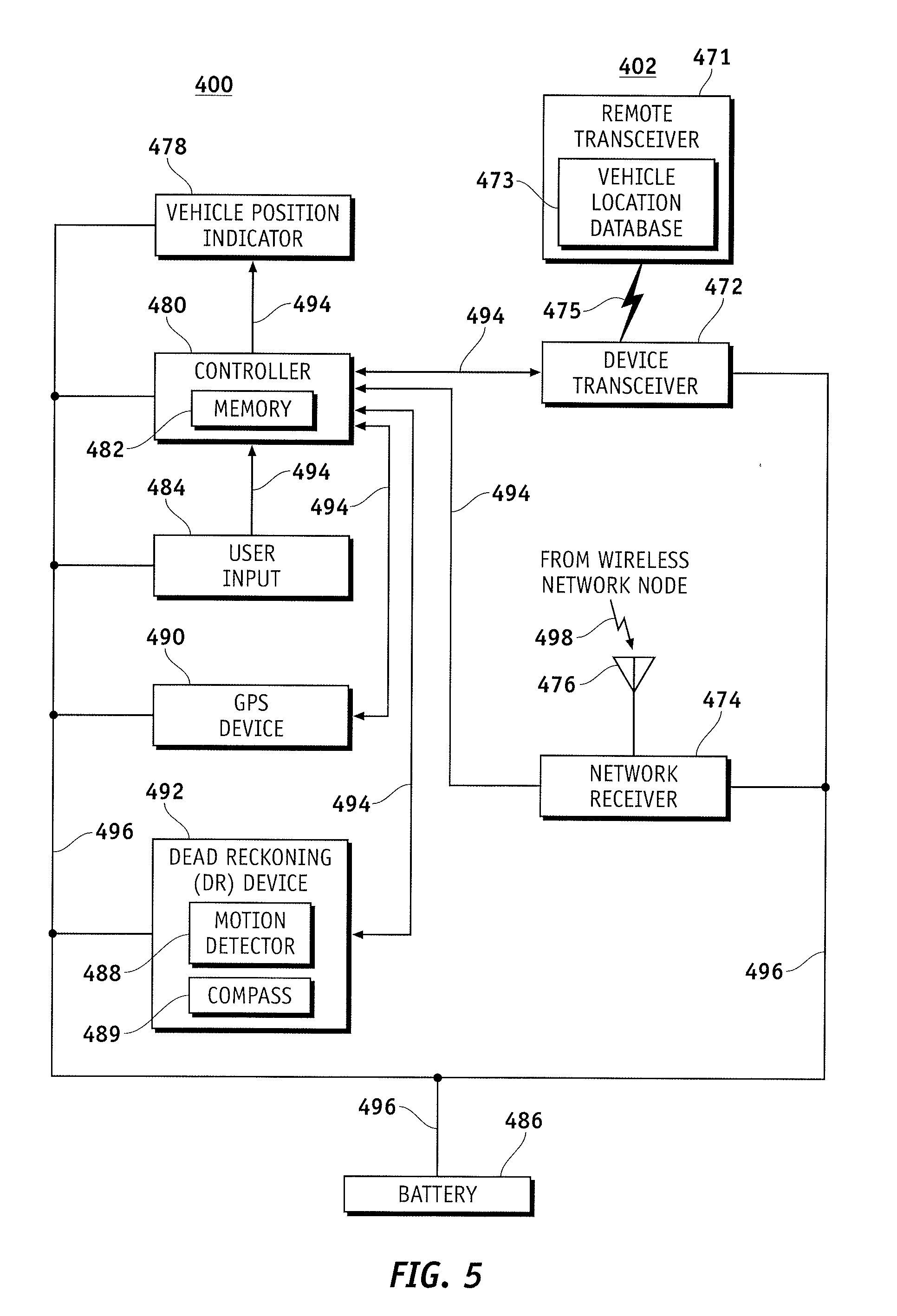
Parked Vehicle Location Information Access via a Portable Cellular Communication Device
InactiveUS20090098907A1Navigational calculation instrumentsRoad vehicles traffic controlInformation accessOn demand
A portable cellular communication device and system is provided for finding the current location of a vehicle on demand by a user. The portable cellular communication device can direct the user to a parked vehicle utilizing location data of the portable cellular communication device provided by a GPS transmitter or a wireless node, and current vehicle location information provided by accessing a vehicle location database.
Owner:GM GLOBAL TECH OPERATIONS LLC
Method and apparatus for efficient handling of product return transactions
InactiveUS6269344B1Reduce shipping costsLow costFinanceBuying/selling/leasing transactionsSingle sessionInformation access
A method and apparatus for efficient handling of product returns to reduce associated costs. A computer system at a regional product return center scans a returned product for identifying information, accesses a manufacturer return approval computer system through the internet or the like, and then submits the identifying information to the manufacturer for return approval. The manufacturer computer system utilizes the identifying information to access an electronic registration database to determine whether the returned product satisfies applicable return criteria. If so, the product is approved for return to the manufacturer. The regional product return center preferably scans a plurality of returned products in a single session. In response to the product identifying information submitted by the regional product return center, the manufacturer provides a list of approved returns and unapproved returns, along with a return authorization number for the batch of approved returns. The regional product return center then assembles the approved product returns into a box, shipping pallet, or the like, applies a label indicating the return authorization label, and ships the batch to the manufacturer. Shipping costs can be saved by omitting rejected product returns from the shipment. The manufacturer can handle the approved product returns from the regional return center as a batch, thereby reducing costs.
Owner:E2INTERACTIVE INC D B A E2INTERACTIVE
Method and apparatus for implementing an active information model
InactiveUS20020035593A1Satisfies requirementGuaranteed to workMultiple digital computer combinationsOffice automationService provisionActive agent
An active information model constructed from an aggregation of personal information portals containing an active agent. In a preferred embodiment, the system of this invention can be offered as a network service providing for information access and exchange according to the individual users' preferences.
Owner:CORYBANT
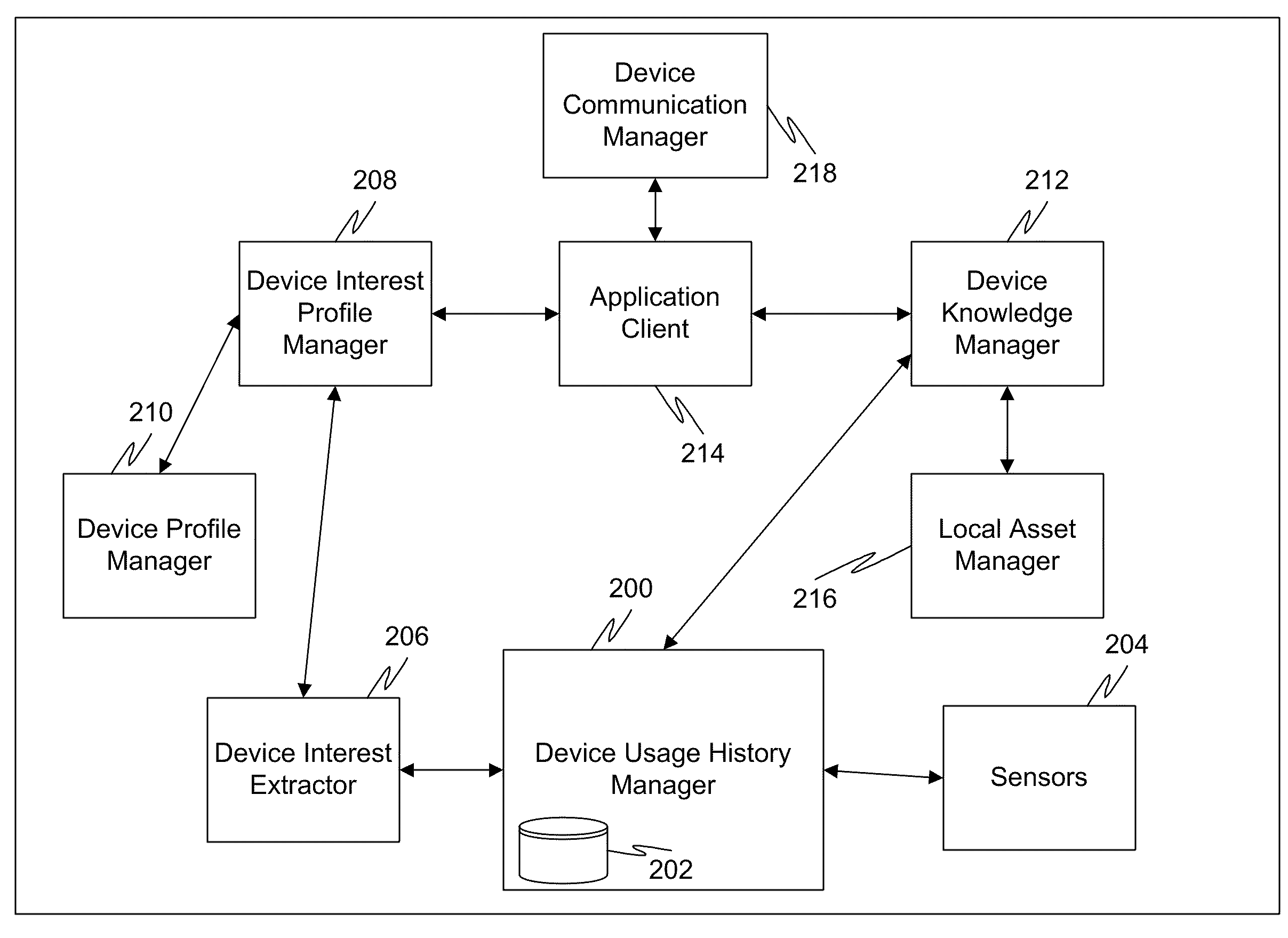
Managing personal digital assets over multiple devices
InactiveUS20100010944A1Metadata multimedia retrievalData switching by path configurationInformation accessDevice tracking
In a first embodiment of the present invention, a method for managing digital assets of a user over multiple home network-enabled devices, the method comprising: receiving information, from a plurality of home network-enabled personal devices, regarding digital assets accessed by the personal devices, wherein the plurality of personal devices are owned or operated by the user and the information is automatically gathered by each personal device tracking its own usage; storing the information; and providing, to one of the plurality of personal devices, identifications of digital assets accessed by the personal devices by accessing the stored information.
Owner:SAMSUNG ELECTRONICS CO LTD
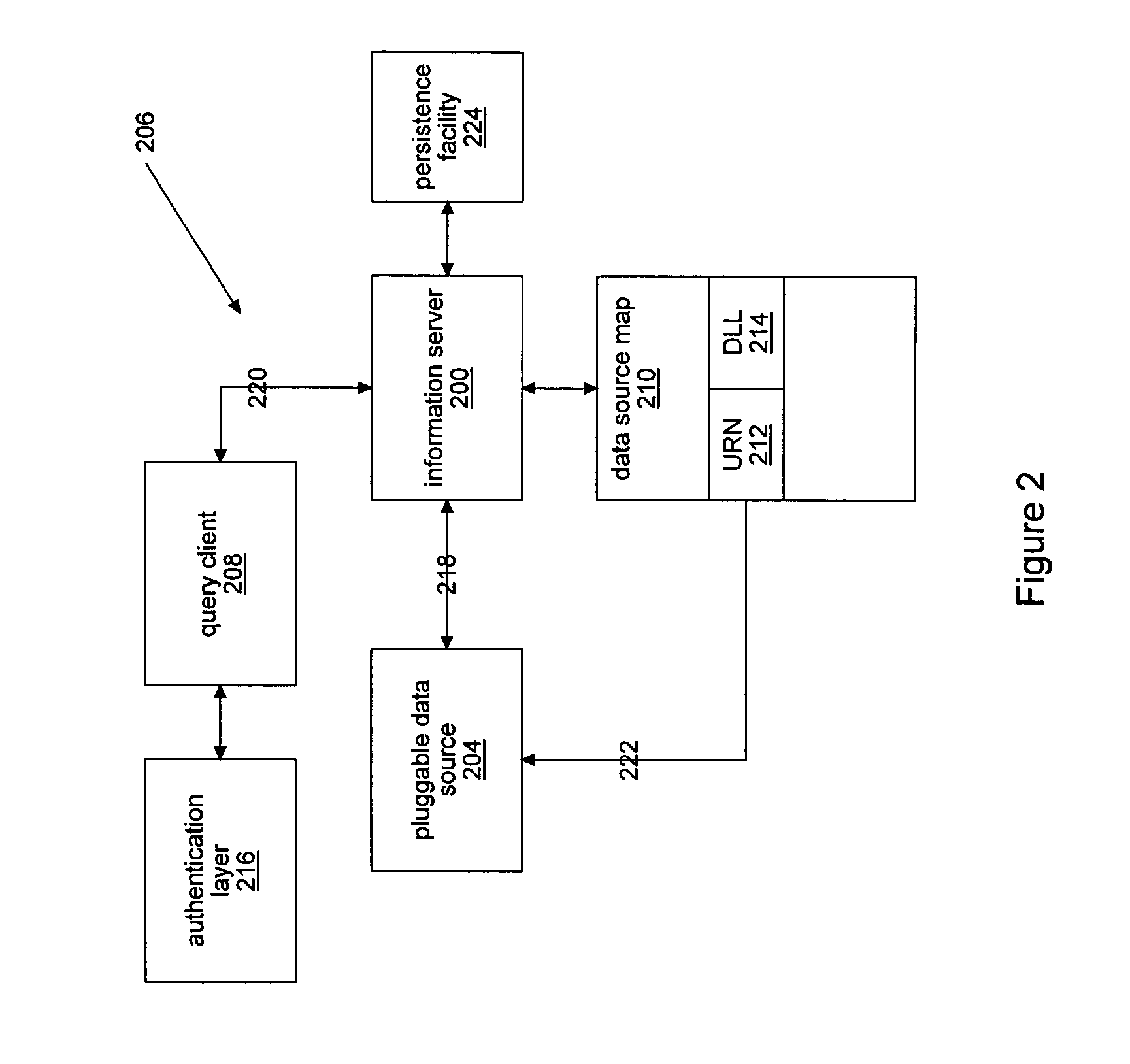
Information server and pluggable data sources
InactiveUS7493311B1Digital data information retrievalDigital data processing detailsInformation accessData source
An information server may function as a centralized query broker that accepts queries from query clients, dispatches queries to potentially disparate data sources, and returns query results to query clients. An information server may centralize information access and security / control operations and may provide a set of uniform interfaces for accessing various types of data sources. A pluggable data source interface may be used for extending the data and actions that are available to an information server. The queries that arrive at the data sources are typically simple queries, which contain no sub-query addressing to a different data source. To make a data source pluggable, a data source may expose a standard interface and may store information about the data source's existence so that an information server will be able to determine, from the stored information, which data sources are available for responding to queries in the information server system.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com