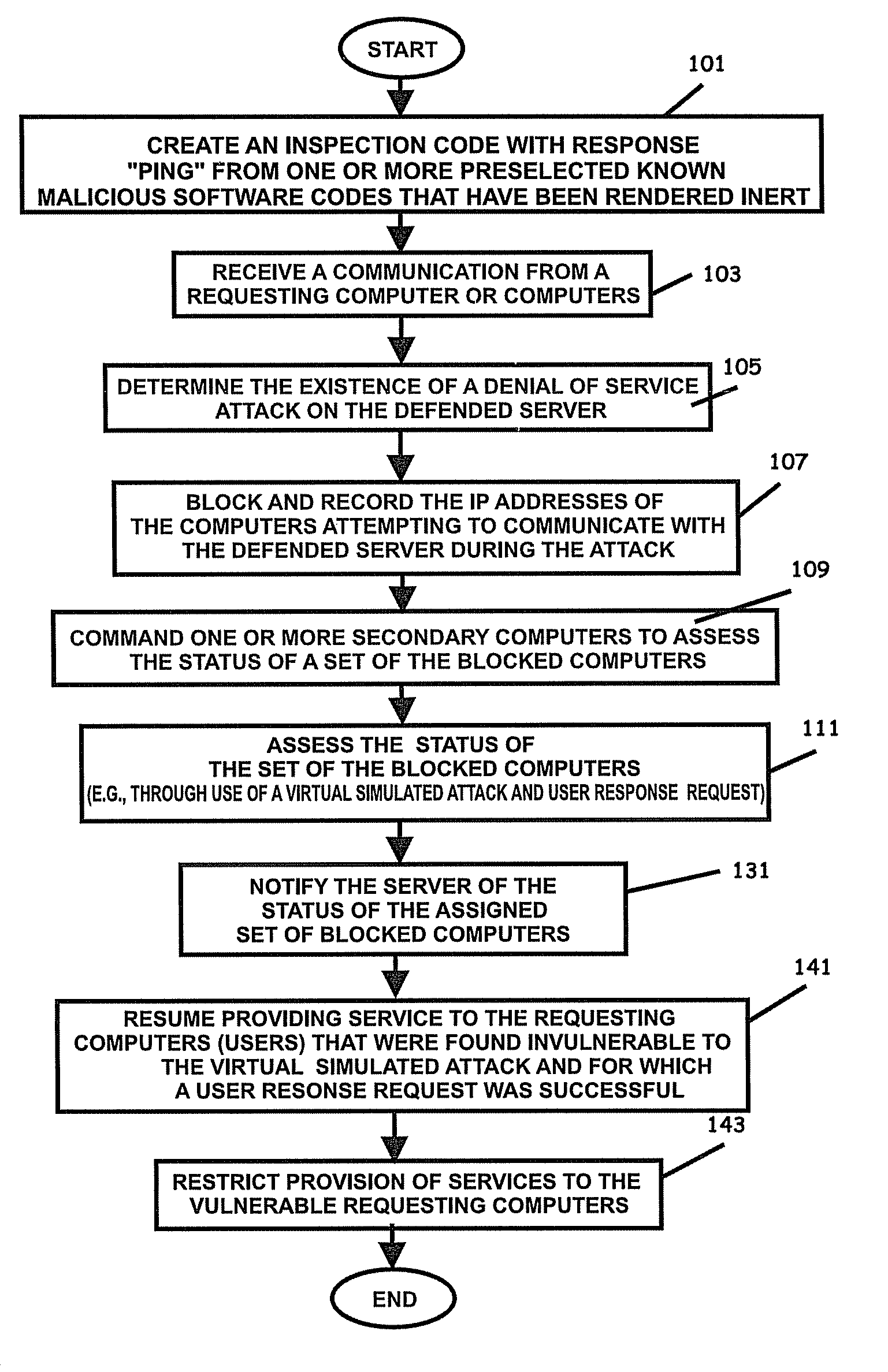
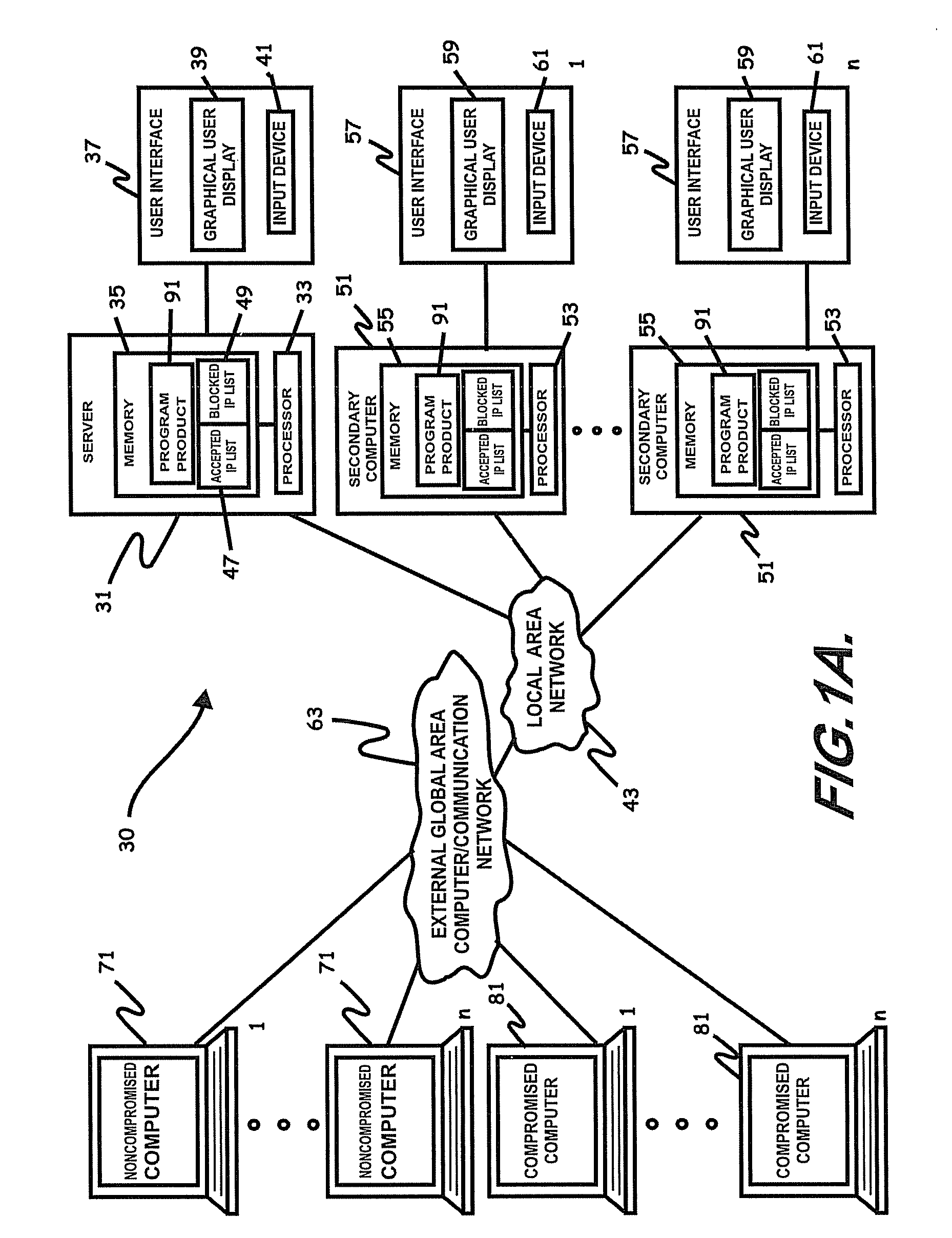
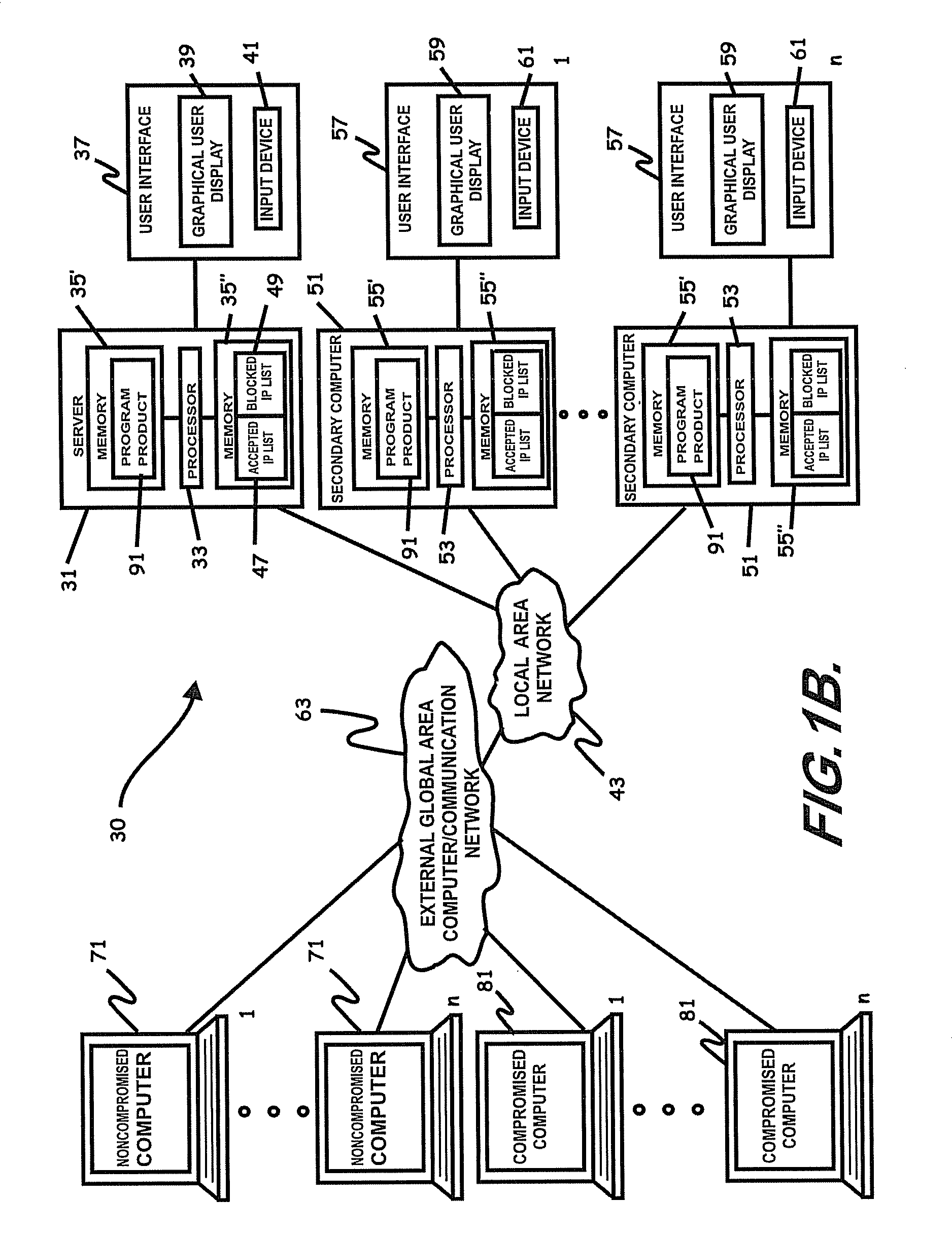
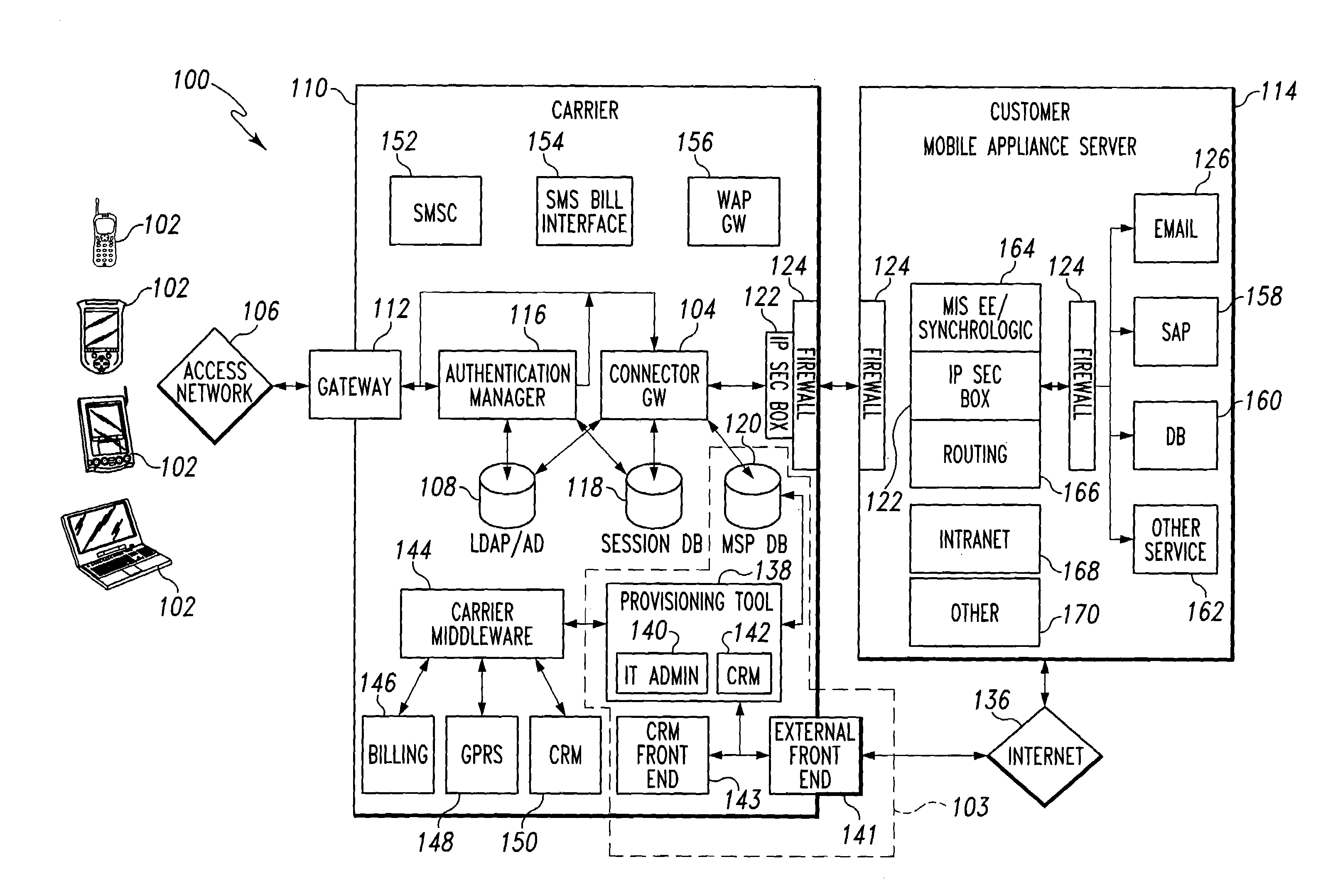
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
799results about How to "Limited access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
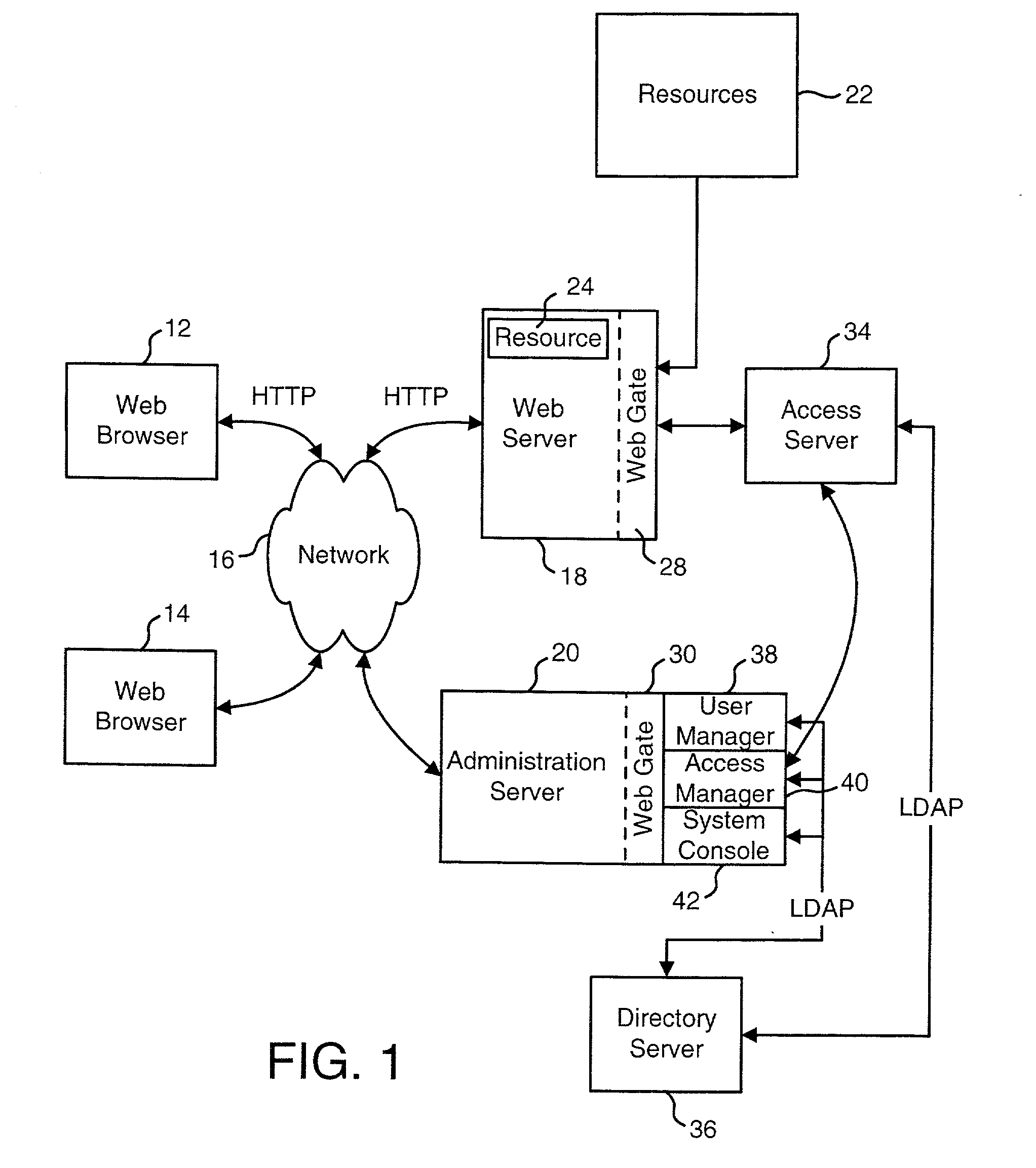
Patent Type
Patent Status
Application Year
Inventor
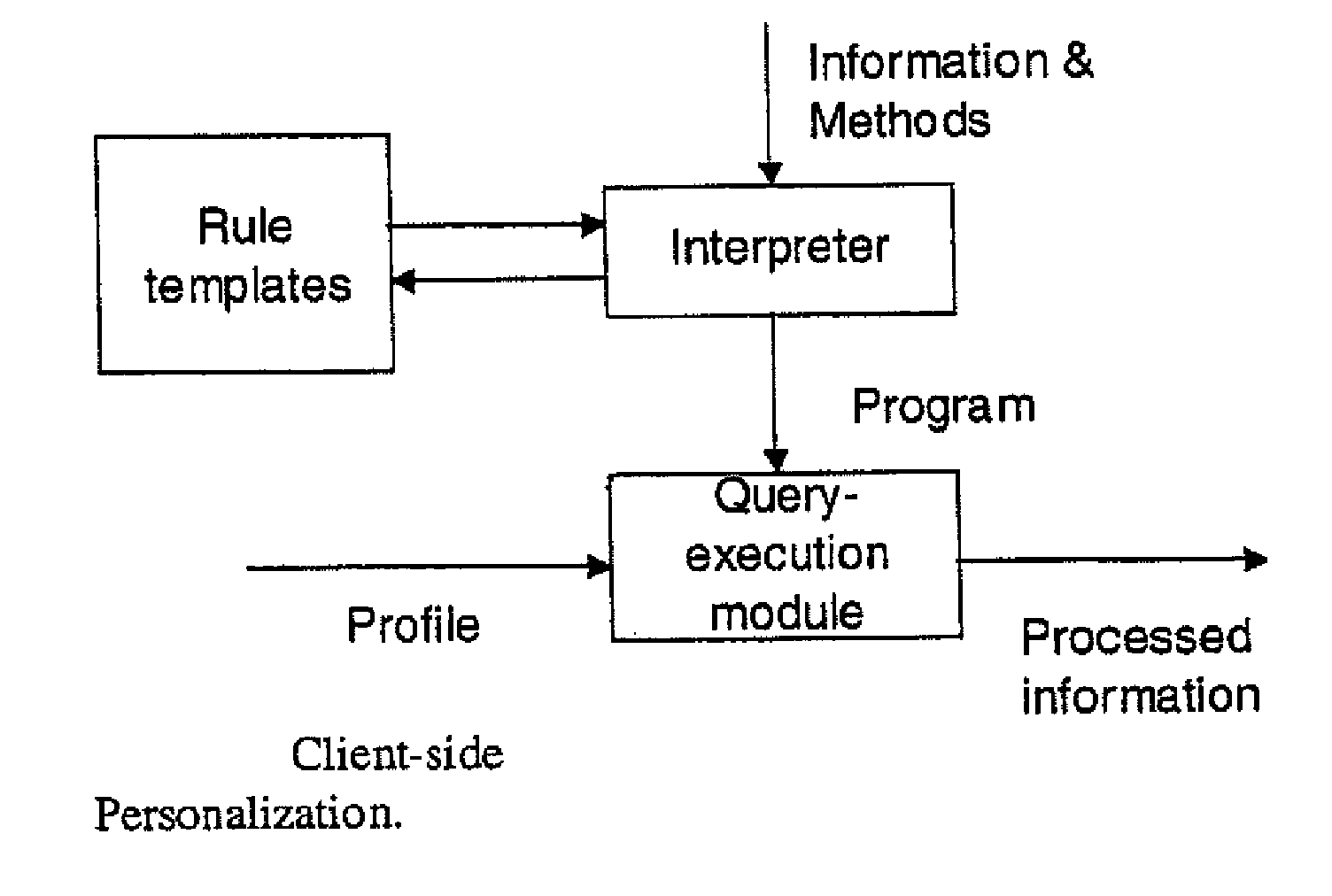
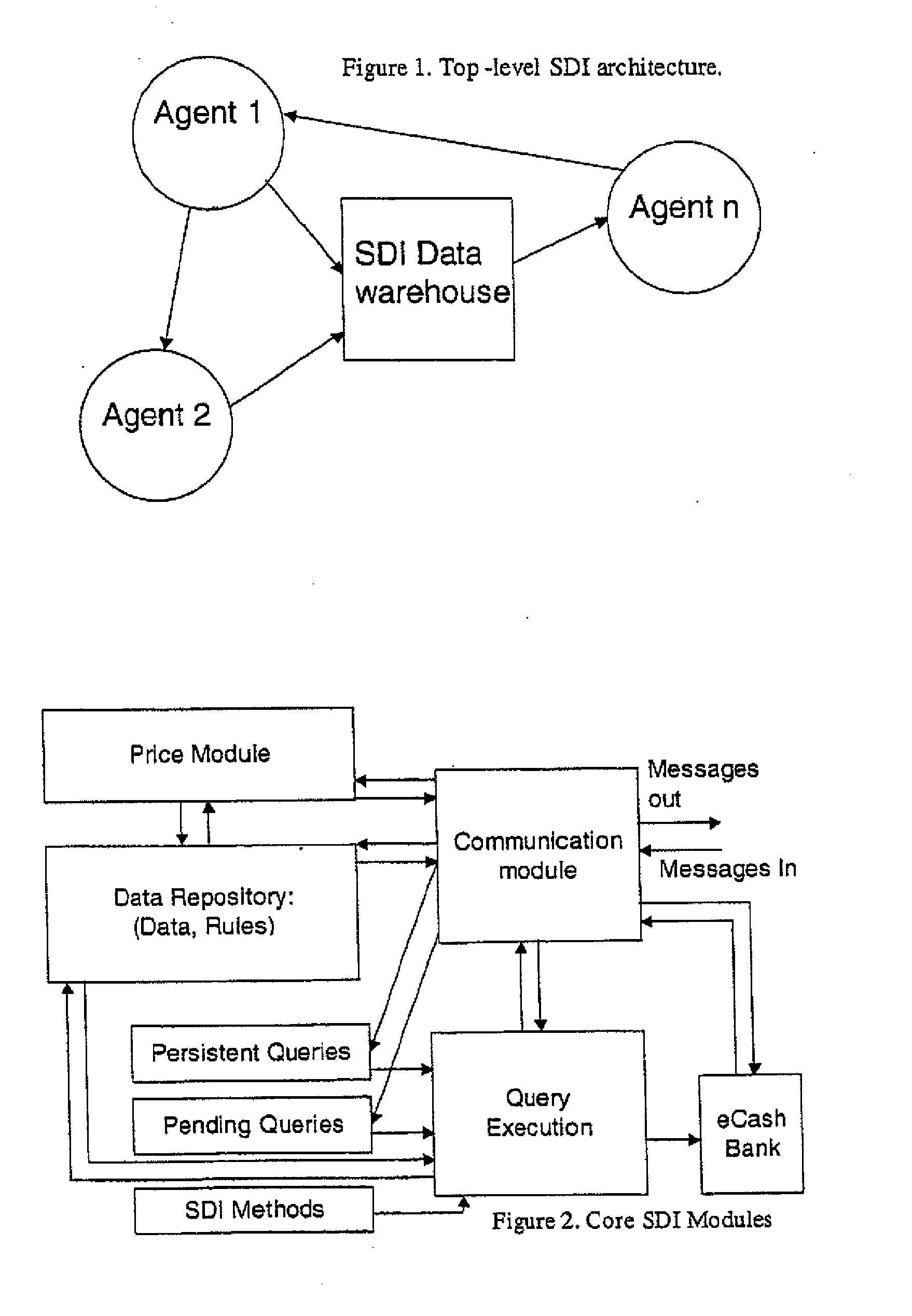
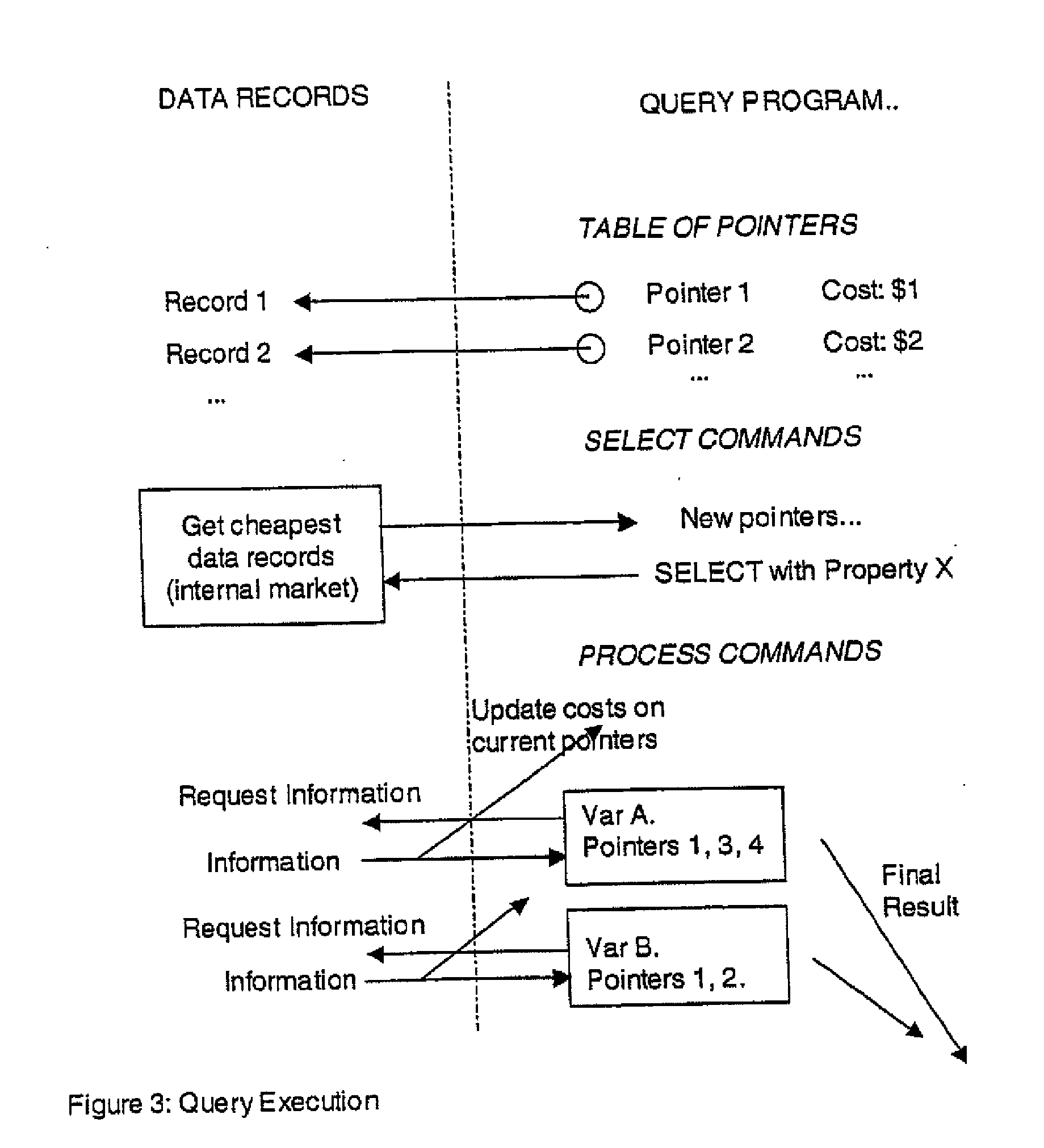
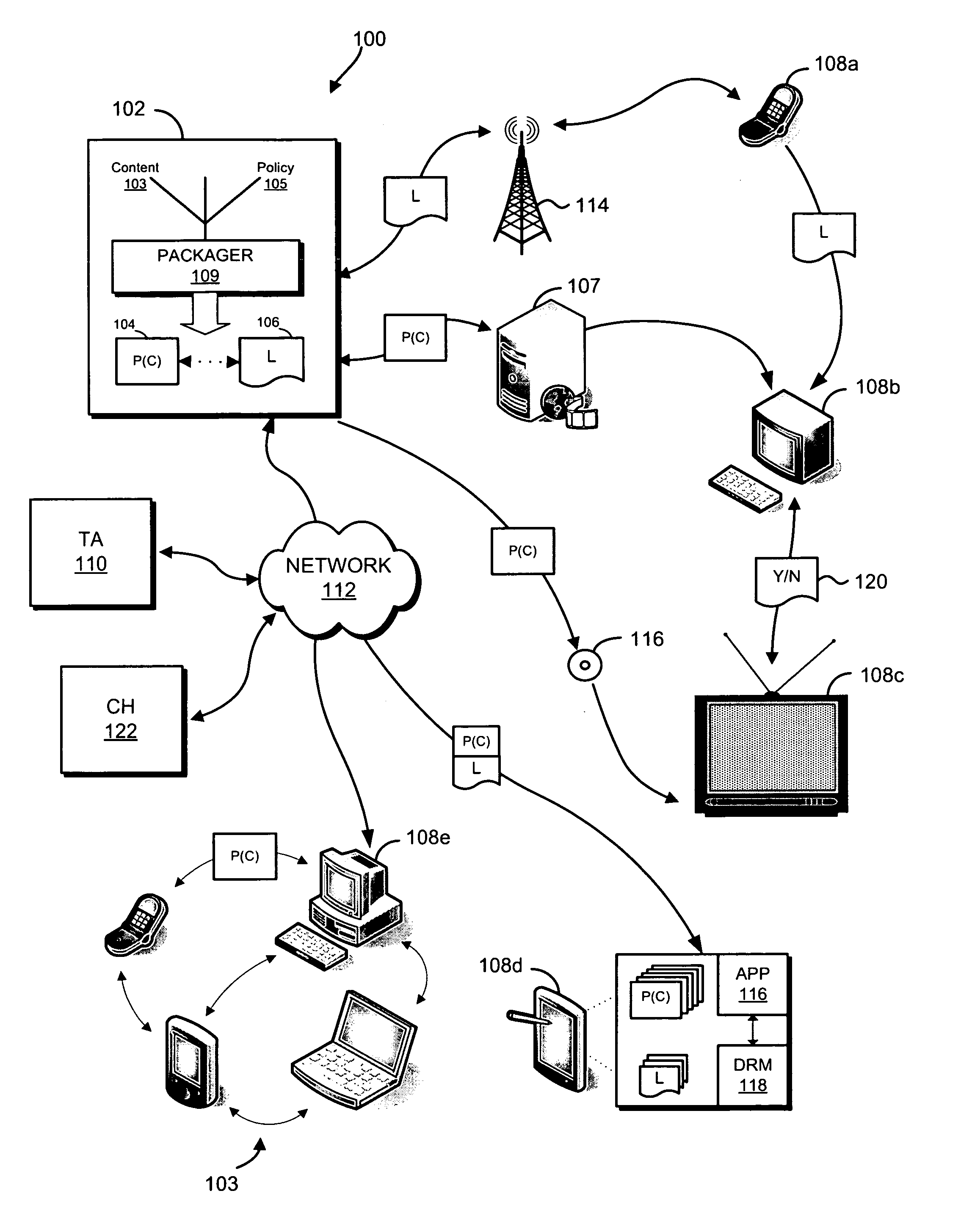
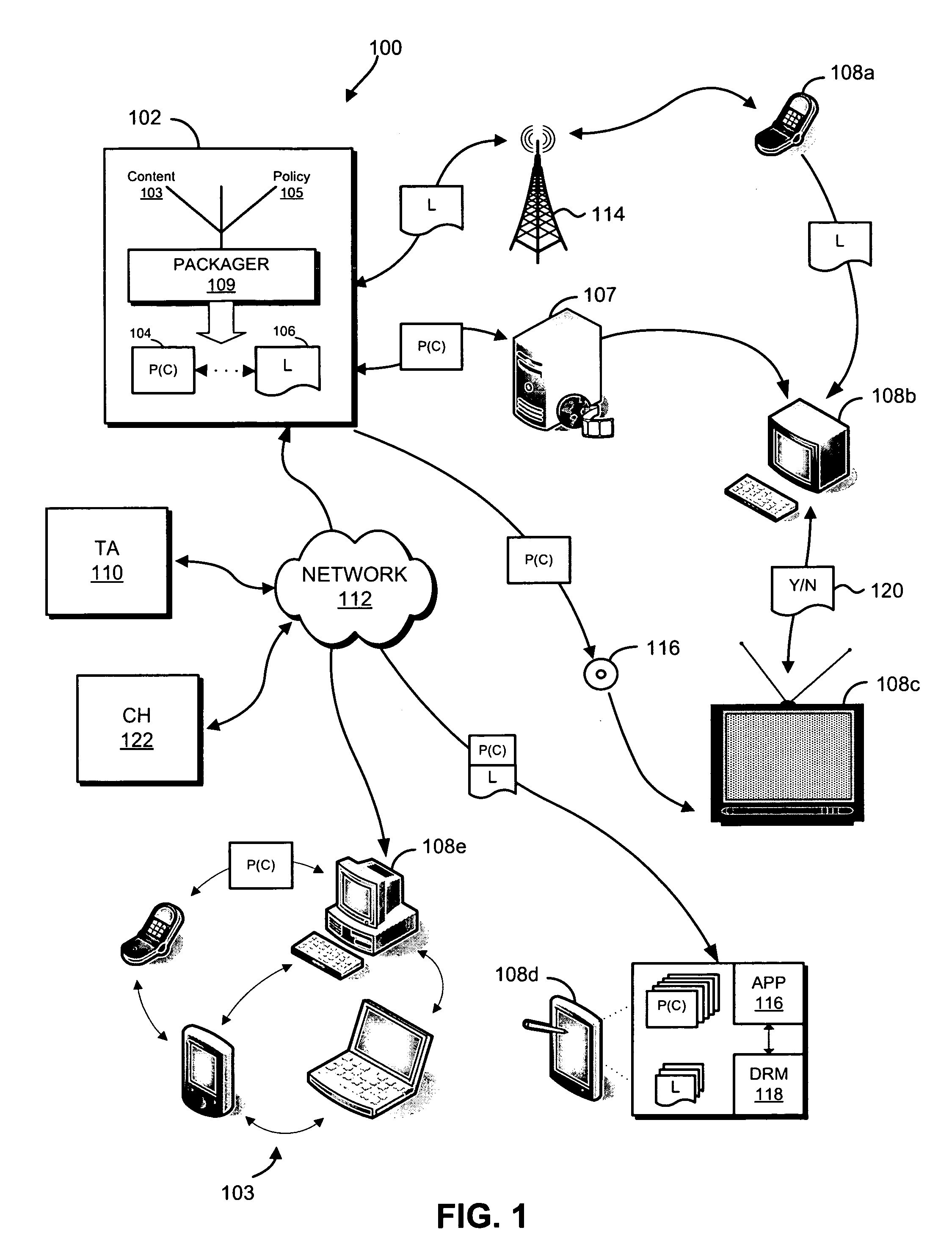
Secure data interchange
InactiveUS20090254971A1Improve privacyLimited accessDigital data processing detailsAnalogue secracy/subscription systemsInformation accessData interchange
A secure data interchange system enables information about bilateral and multilateral interactions between multiple persistent parties to be exchanged and leveraged within an environment that uses a combination of techniques to control access to information, release of information, and matching of information back to parties. Access to data records can be controlled using an associated price rule. A data owner can specify a price for different types and amounts of information access.
Owner:STRIPE INC
Electroactive polymer actuated medical devices
ActiveUS6969395B2High degreeLimited accessSuture equipmentsDilatorsBiomedical engineeringMedical procedure
The present invention is directed to novel apparatus for use in medical procedures relating to tubular body fluid conduits. According to a first aspect of the invention, a filter apparatus is provided for delivery over a guidewire within a tubular body conduit, such as a blood vessel. The filter apparatus comprises: (a) a filter element transformable between a collapsed state and a deployed state, wherein the filter element is adapted to filter particulate matter from fluid within the tubular body conduit while in the deployed state; and (b) a locking member comprising one or more electroactive polymer actuators which switch the locking member between (i) a locking state wherein the locking member securely engages the guidewire and (ii) a release state wherein the locking member is movable along the length of the guidewire. According to a second aspect of the invention, a connector apparatus is provided for use in making an anastomotic connection between first and second tubular fluid conduits in a patient. The connector apparatus comprises: (a) a locking member, which further comprises one or more electroactive polymer actuators that switch the locking member between a locking state and a release state; and (b) a connector body that is configured to permit flow of bodily fluid between the first and second tubular fluid conduits. The connector body has a first portion configured for insertion into an axial end of the first tubular fluid conduit and a second portion configured for insertion through a sidewall of the second tubular fluid conduit. The second portion of the connector body is further configured to securely engage the locking member when the locking member is in the locking state.
Owner:BOSTON SCI SCIMED INC
Secured data format for access control
ActiveUS7380120B1Facilitate access control managementGood synchronizationDigital data processing detailsUser identity/authority verificationMedia access controlDocumentation
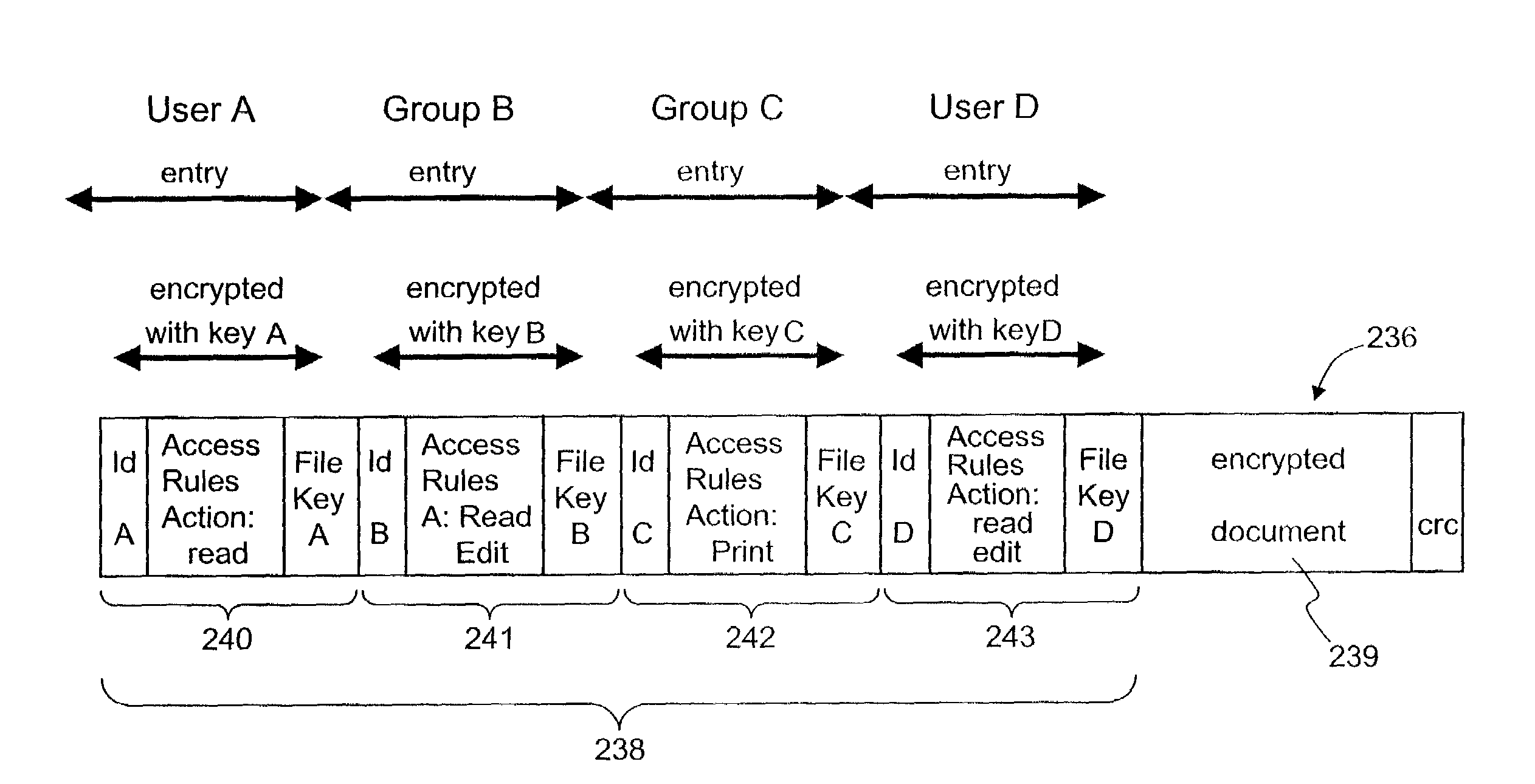
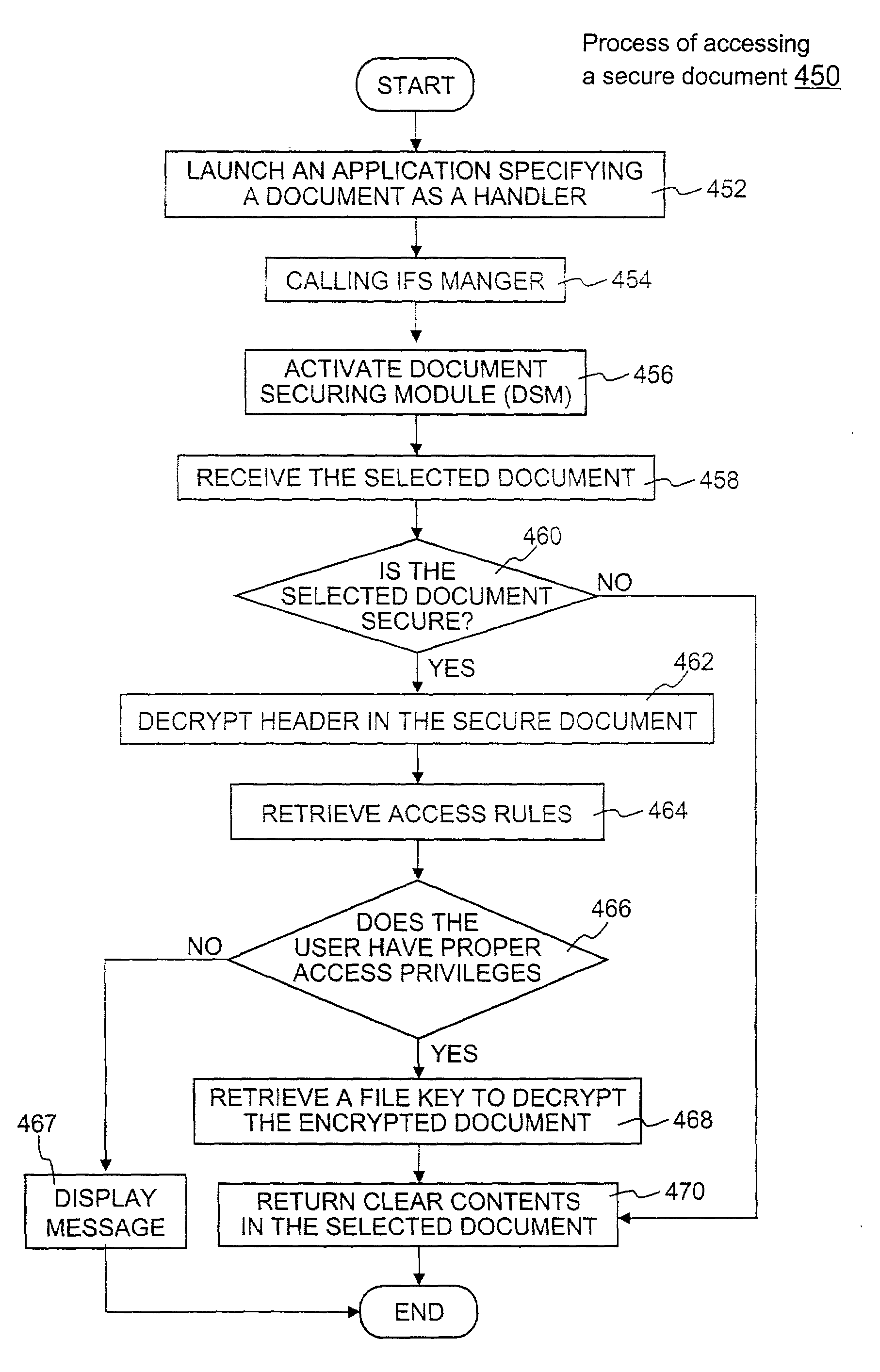
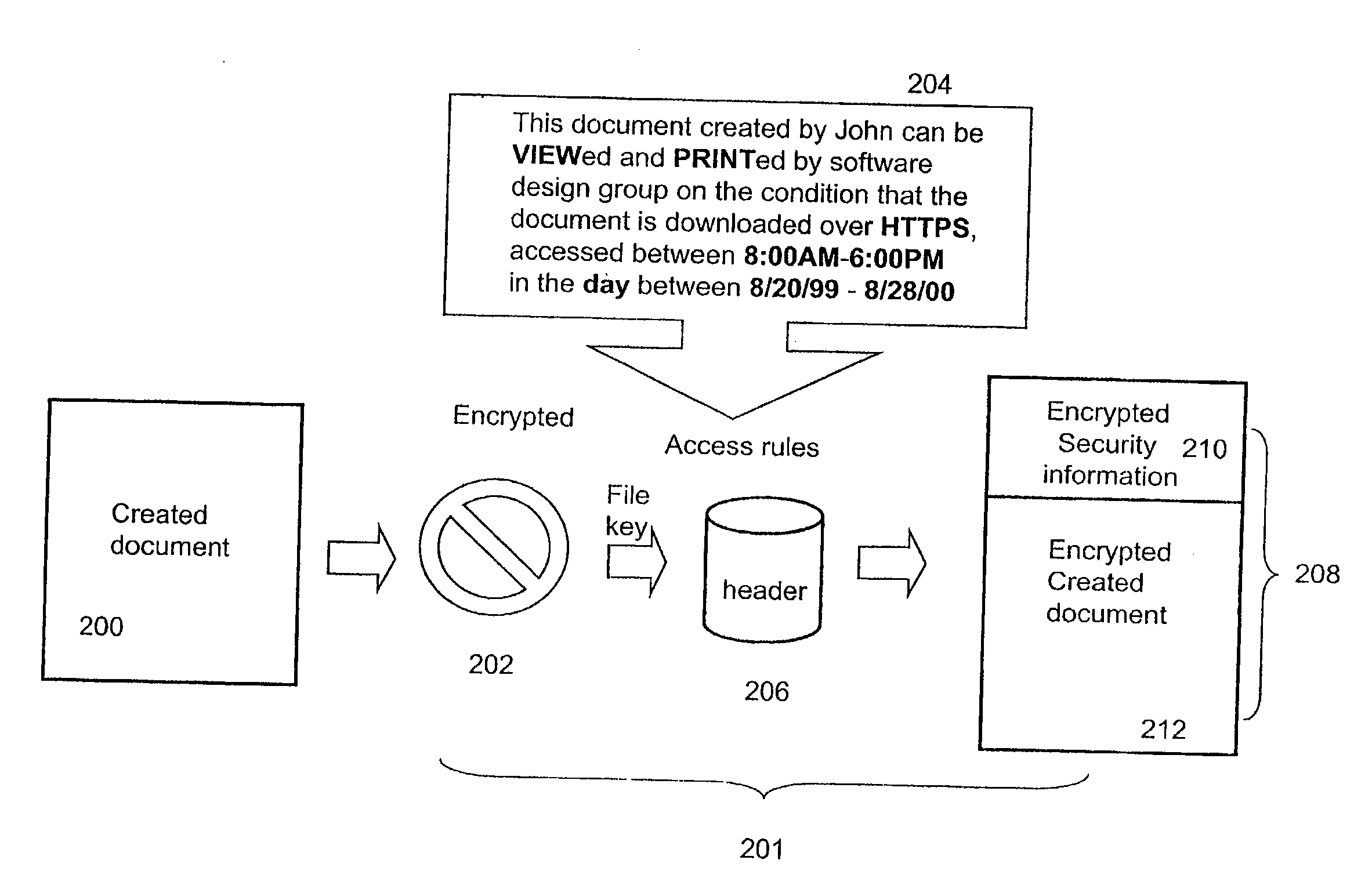
In a system for providing access control management to electronic data, techniques to secure the electronic data and keep the electronic data secured at all times are disclosed. According to one embodiment, a secured file or secured document includes two parts: an attachment, referred to as a header, and an encrypted document or data portion. The header includes security information that points to or includes the access rules and a file key. The access rules facilitate restrictive access to the secured document and essentially determine who / when / how / where the secured document can be accessed. The file key is used to encrypt / decrypt the encrypted data portion. Only those who have the proper access privileges are permitted to retrieve the file key to encrypt / decrypt the encrypted data portion.
Owner:INTELLECTUAL VENTURES I LLC
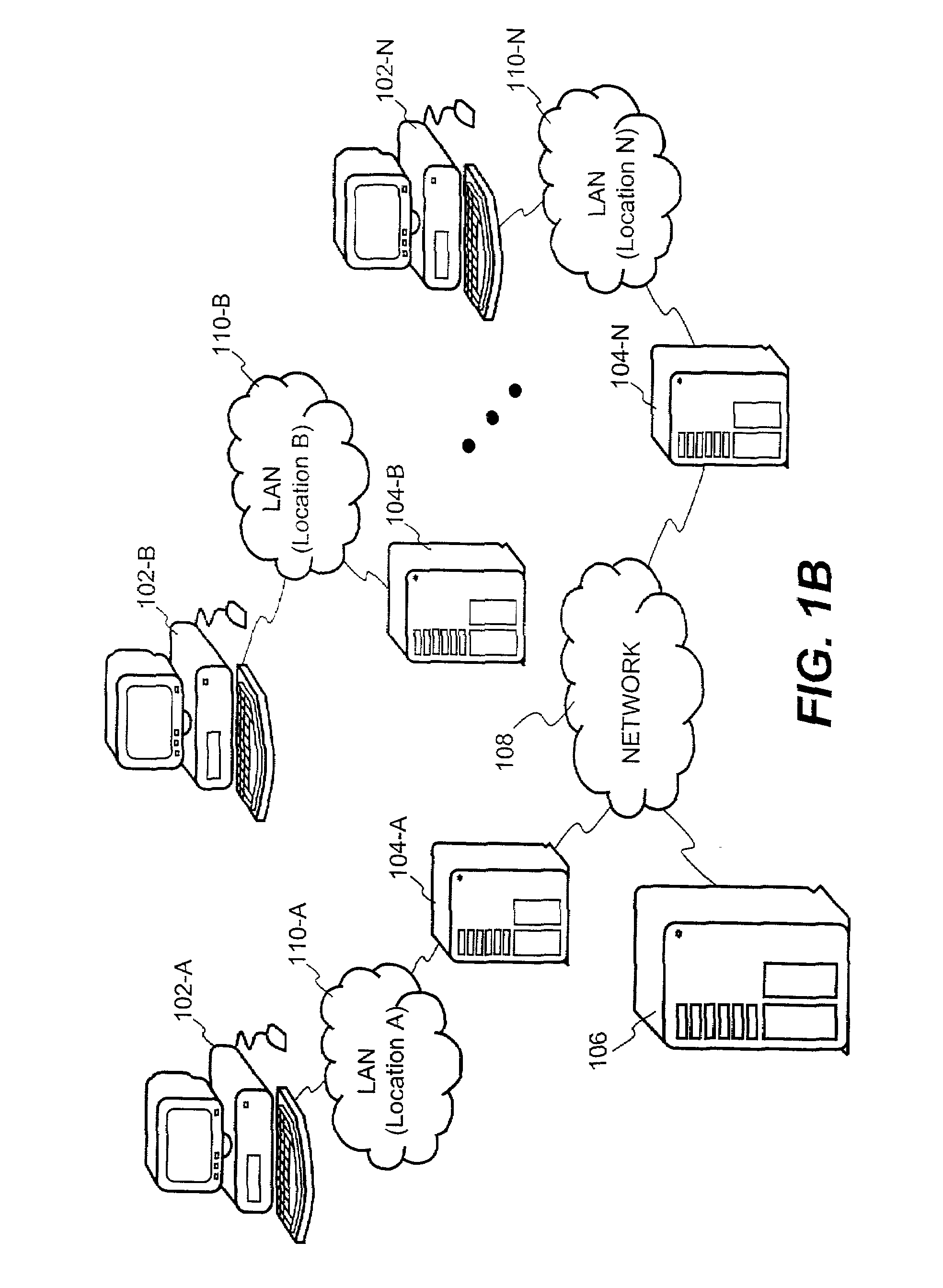
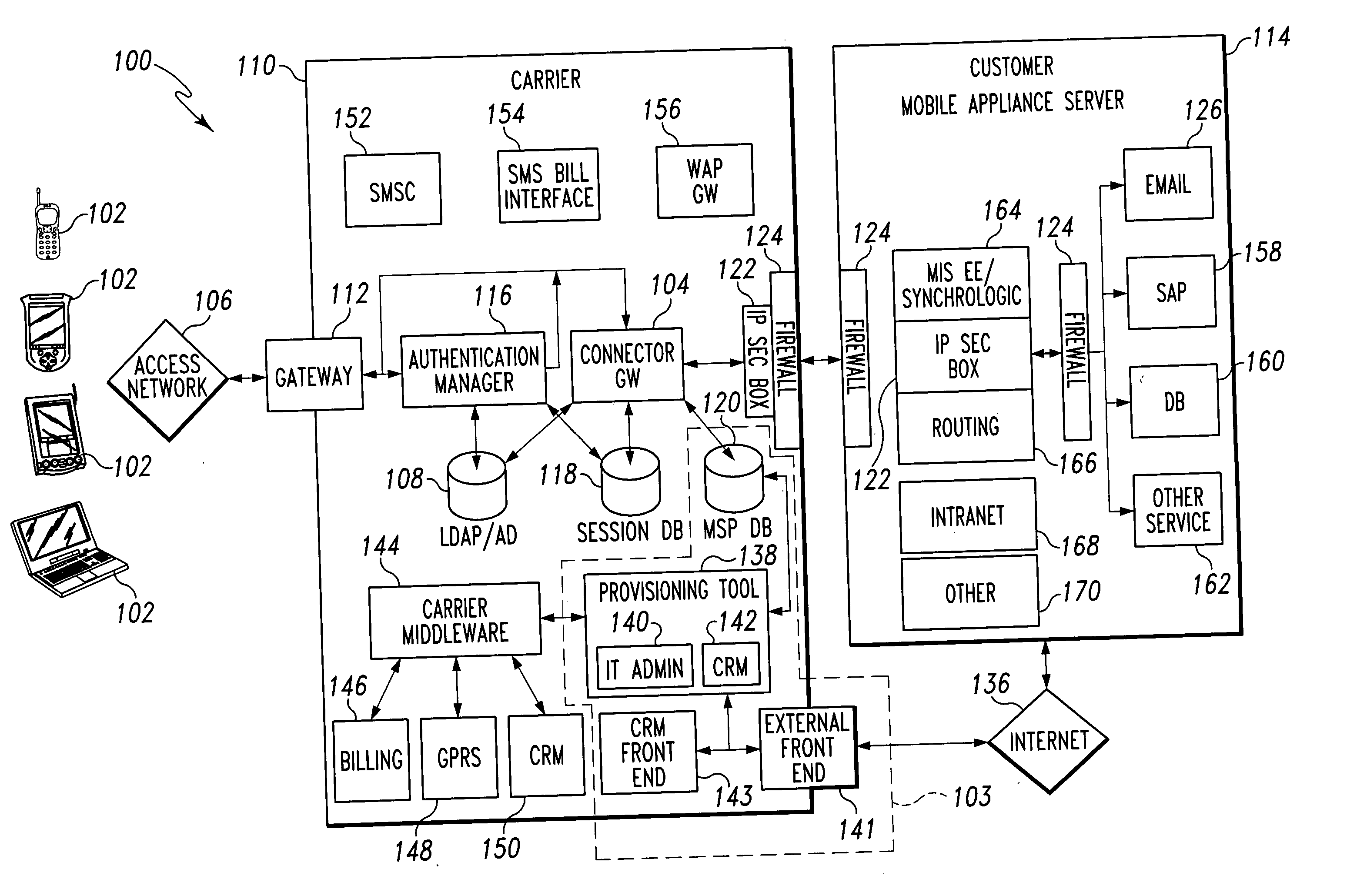
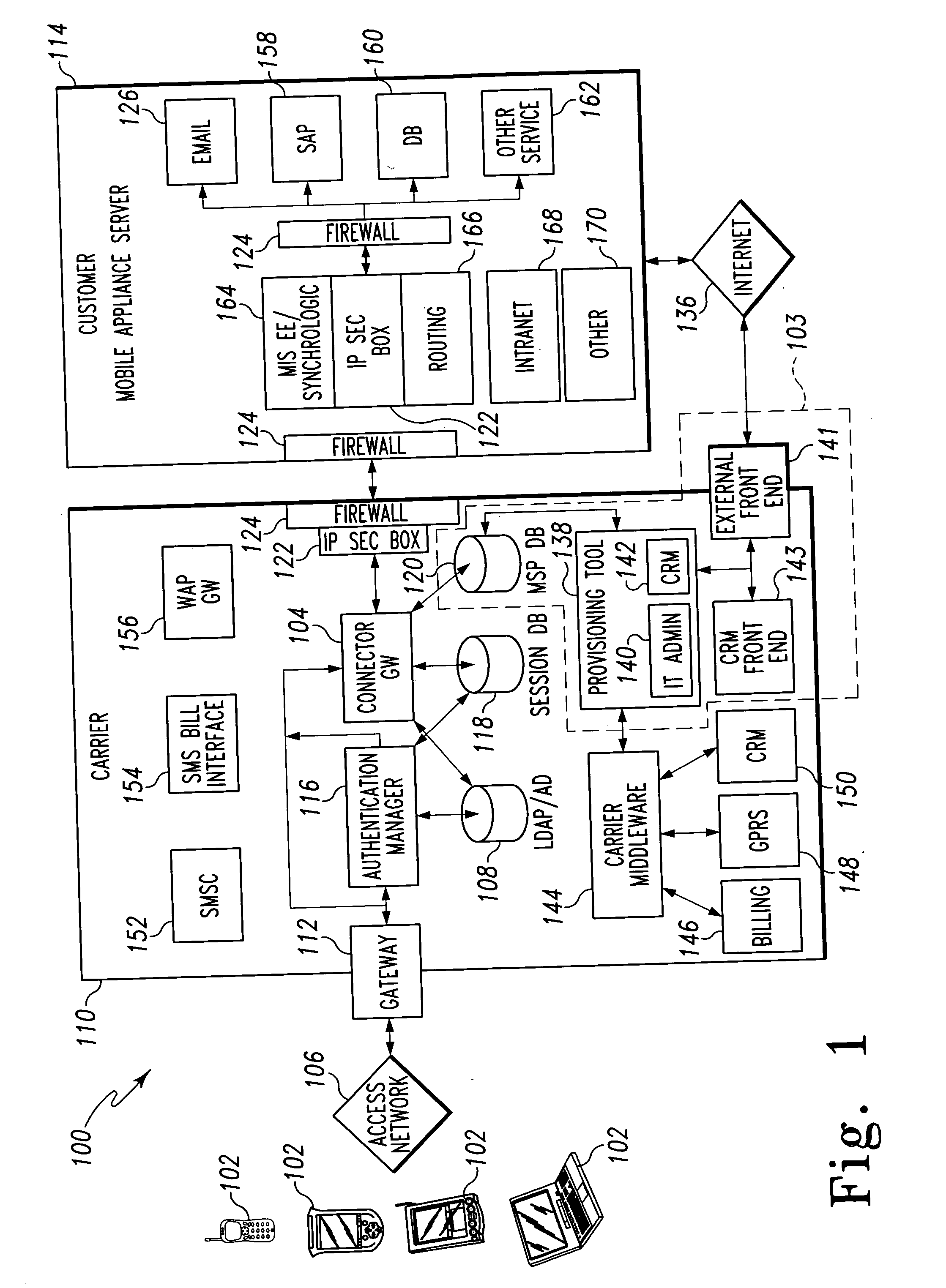
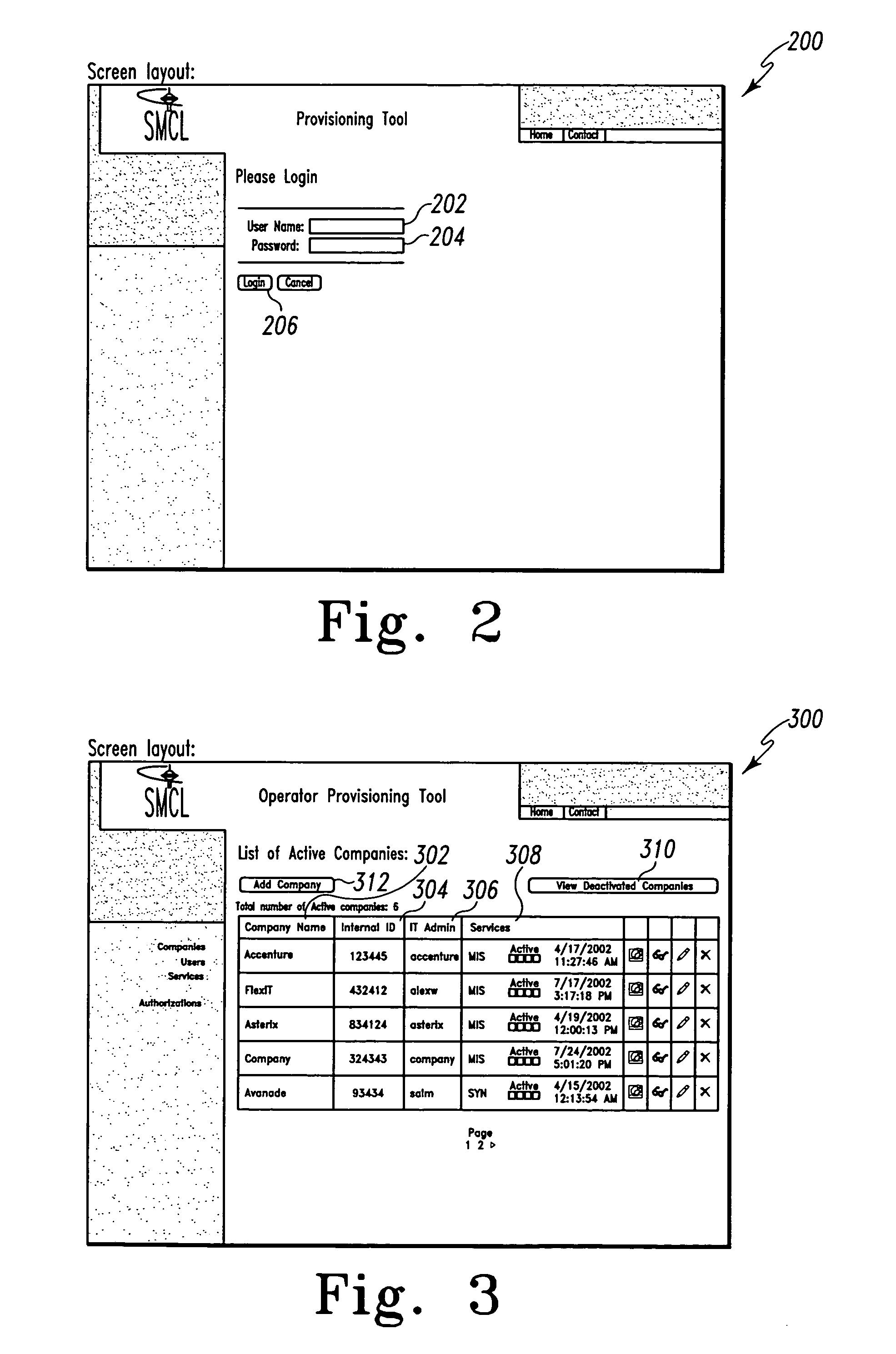
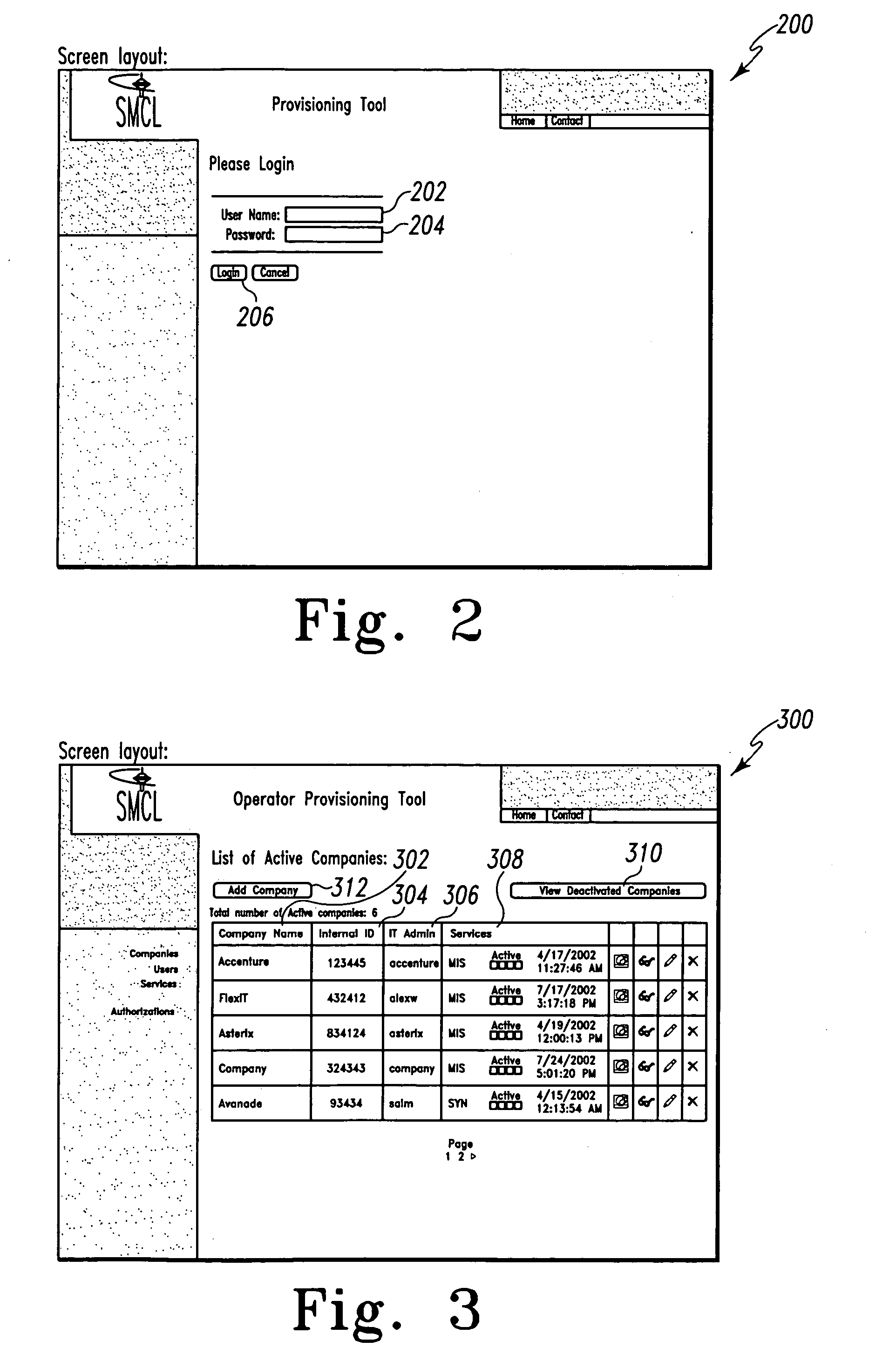
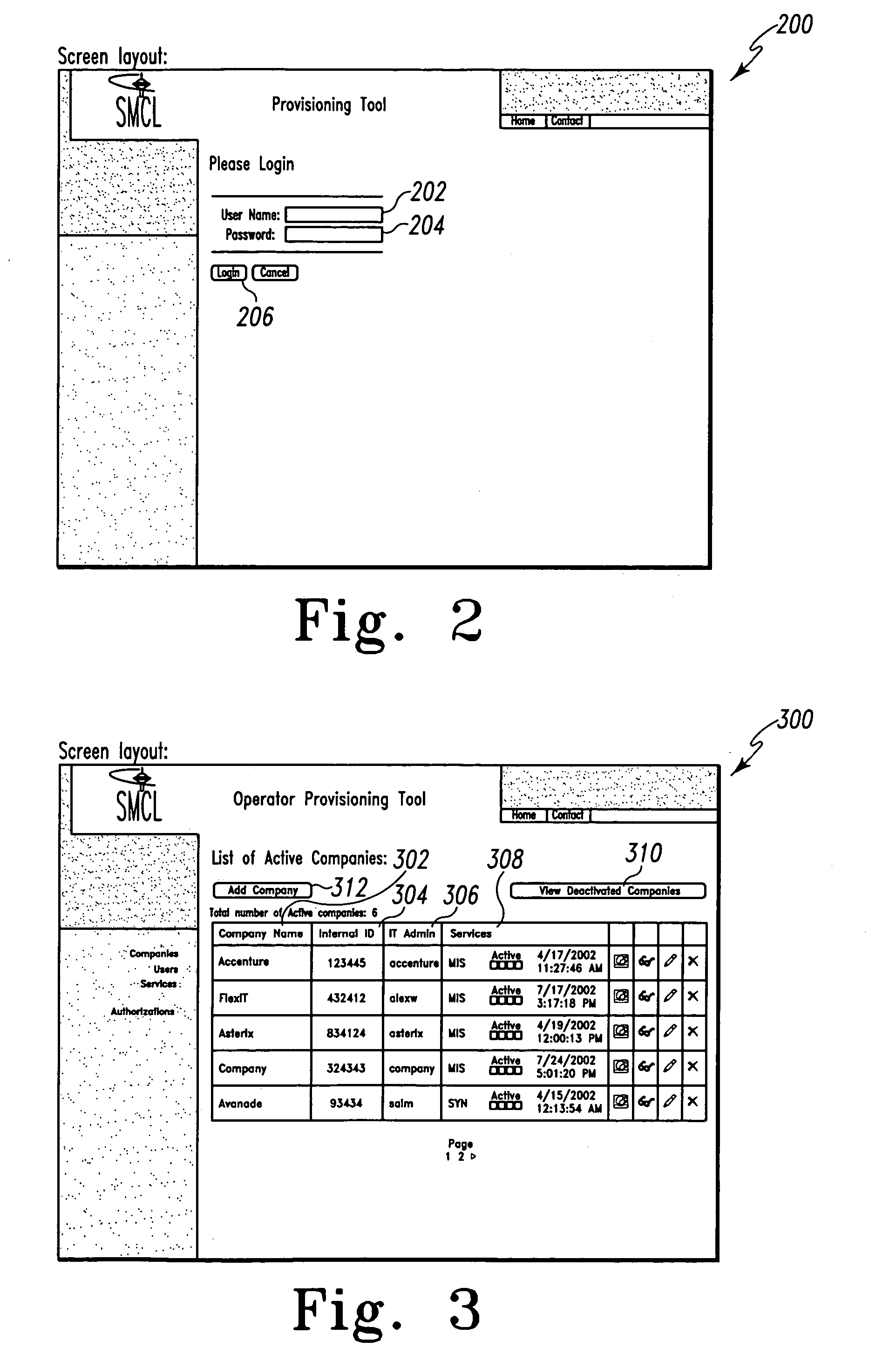
Mobile provisioning tool system
ActiveUS20050075115A1Simple processLimited accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile businessWorkstation
A mobile provisioning tool system including a software provisioning tool application. The mobile provisioning tool system includes mobile devices capable of conducting wireless communication with wireless access points. A carrier network is connected with the wireless access points and a customer network that includes at least one business application. A provisioning tool application is located on a provisioning server. The provisioning tool application includes a CRM Rep component and an IT Admin component. A software provisioning tool application allows the provisioning workstation to automatically install mobile business services and configure network configuration settings on the mobile device.
Owner:ACCENTURE GLOBAL SERVICES LTD
Secured transaction system and method
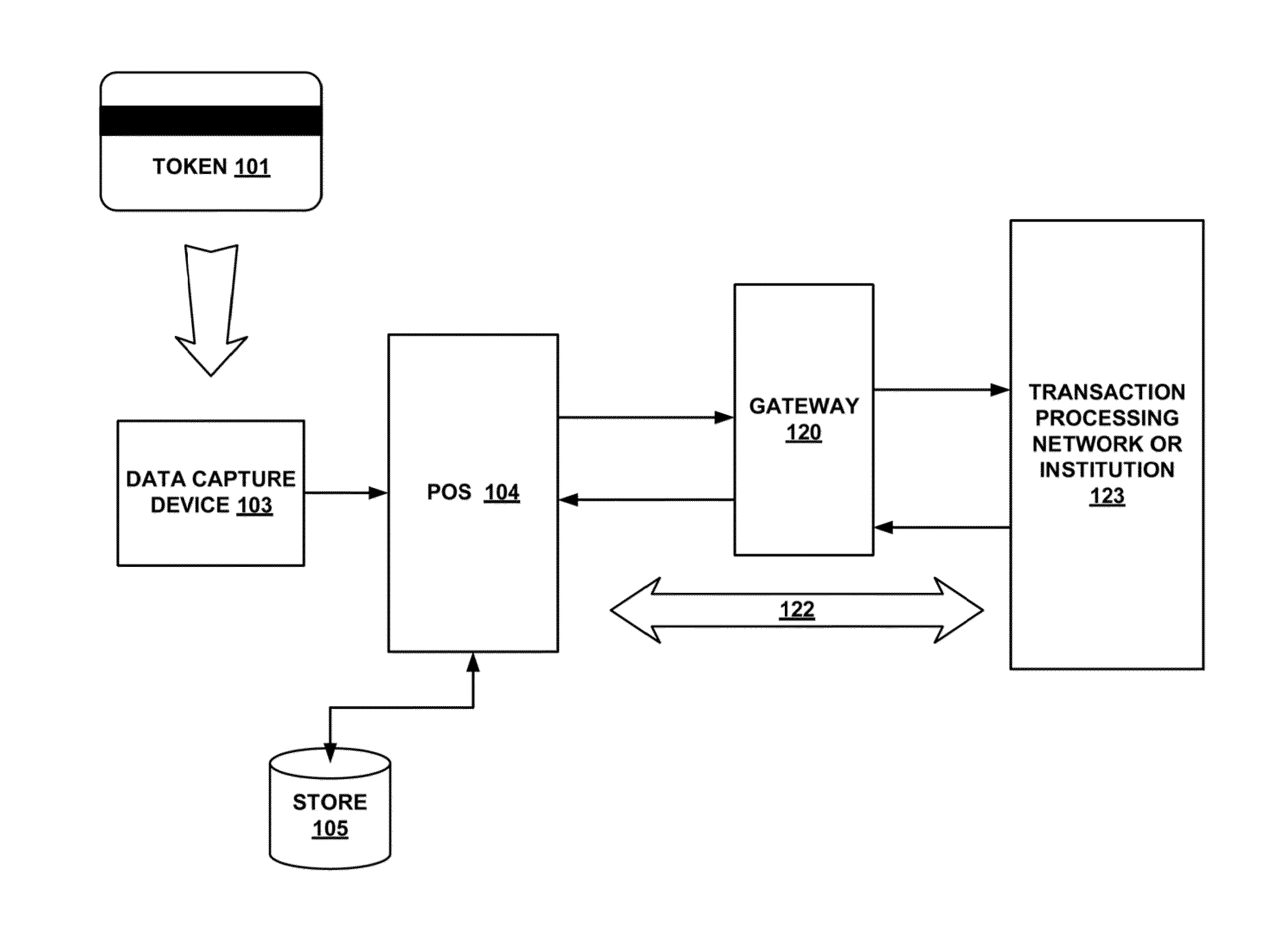
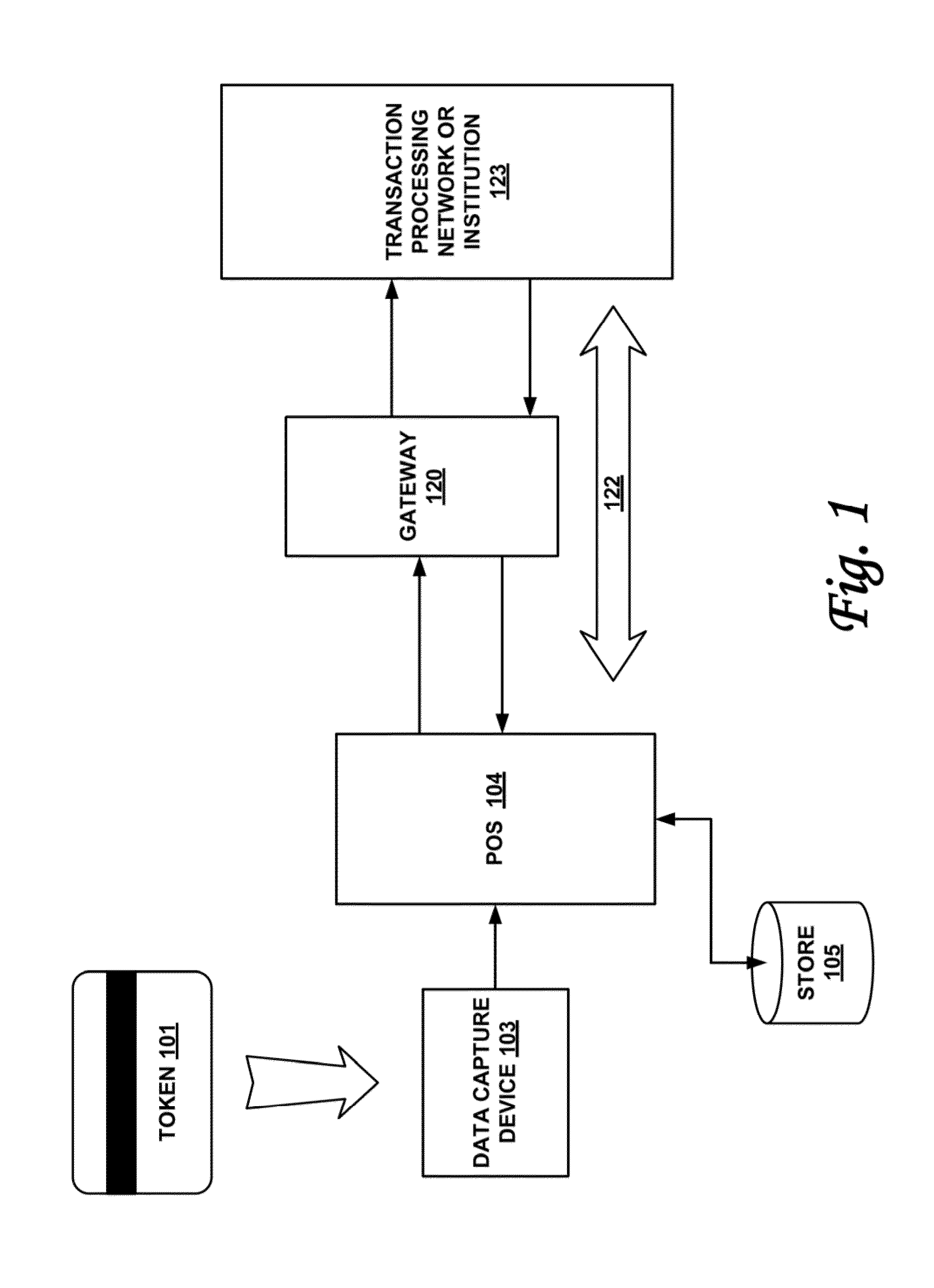
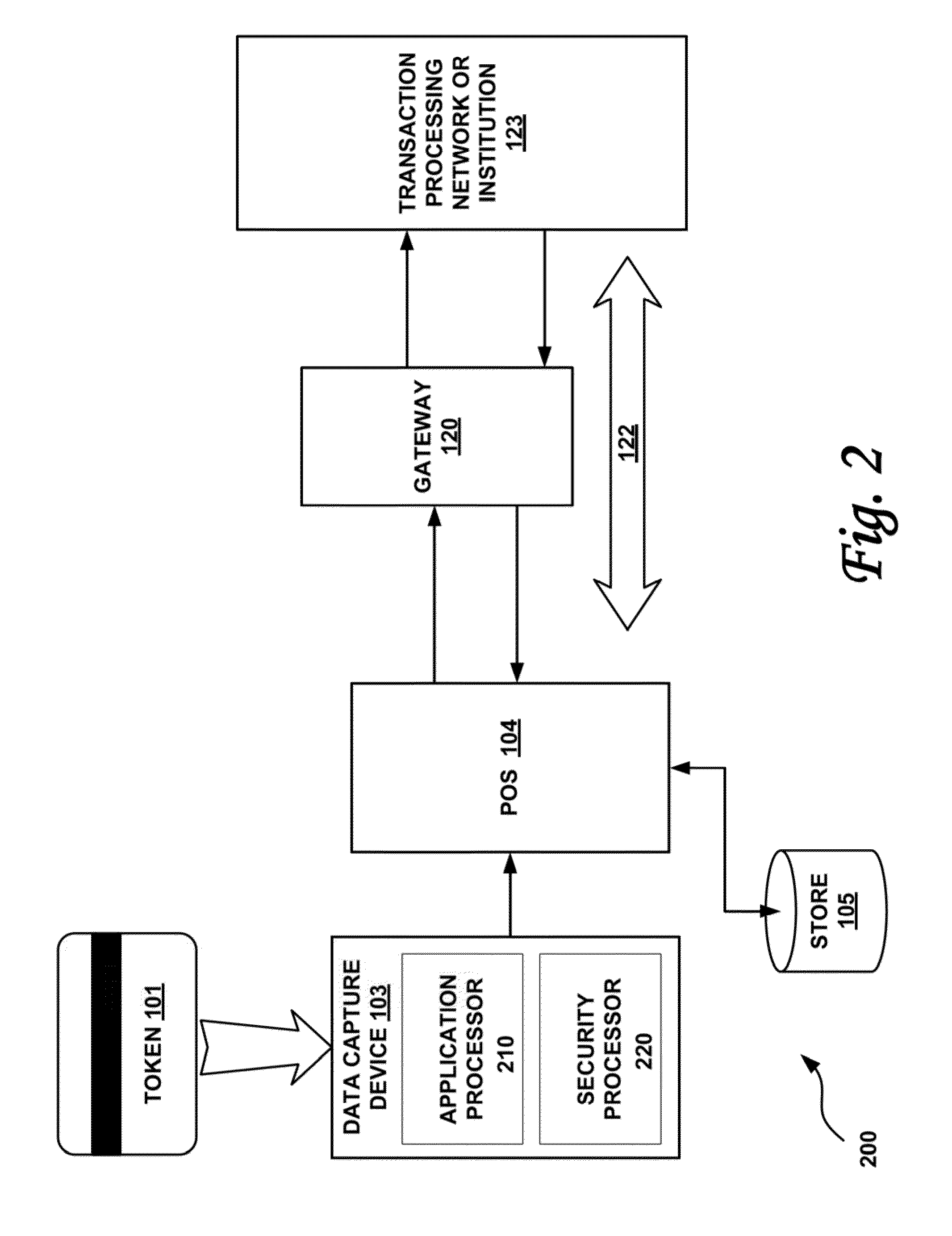
InactiveUS20130254117A1Reduce riskEasy to optimizePayment protocolsInternet privacyEncryption decryption
Systems and methods for performing financial transactions are provided. In one embodiment, the invention provides for method for bank card transactions, including: reading the token information at the point of swipe for traditional and non-traditional POS platforms; performing a low-security task on the token information using a first microprocessor, wherein the non-security task includes one or more tasks from the group of encryption determination, encryption-decryption request, key management, token information delivery, or transactional data delivery; and performing a security-related task on the token information using a second microprocessor based on a request from the first microprocessor, wherein the security-related task includes one or more tasks from the group of token information authentication, token information decryption, or token information encryption. Formatting the encrypted information such that it is compatible with the format of the current POS system.
Owner:VON MUELLER CLAY W +1
System and method to authenticate users to computer systems
InactiveUS20050091338A1Facilitates rapid secondary logLimited accessDigital data processing detailsDrug and medicationsTelecommunications linkTransceiver
A system utilizing a personal security device to provide access to a computer terminal where the personal security device includes circuitry and transceiver components for transmitting identification information and exchanging other digital information with a computer terminal and other compatible devices and the personal security device establishes a communication link with a computer terminal to allow a user to logon to the terminal so that when a user leaves the computer terminal, the communication link is terminated, causing the computer terminal to lock the keyboard, blank the monitor, and / or logoff the user if the communication link is not restored within a sufficient time period and also allowing the personal security device to facilitate subsequent computer access within a time range by providing time related access codes to the terminal that can be used to reestablish computer terminal access.
Owner:DLH TECH LLC
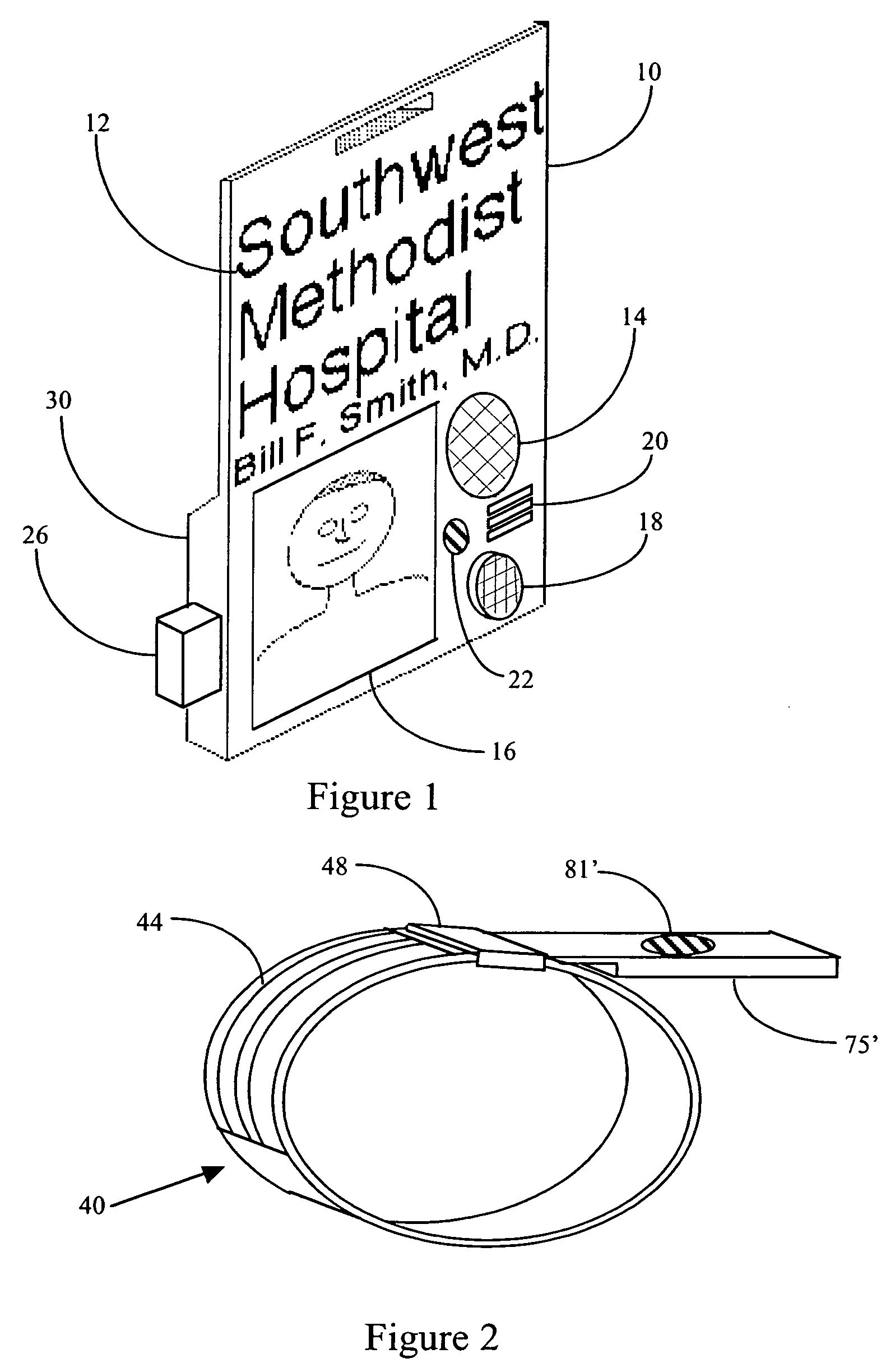
Document security system that permits external users to gain access to secured files
ActiveUS8176334B2Minimal amountLimited accessDigital data processing detailsUser identity/authority verificationUser PrivilegeInternal documentation
An improved system and approaches for exchanging secured files (e.g., documents) between internal users of an organization and external users are disclosed. A file security system of the organization operates to protect the files of the organization and thus prevents or limits external users from accessing internal documents. Although the external users are unaffiliated with the organization (i.e., not employees or contractors), the external users often have working relationships with internal users. These working relationships (also referred to herein as partner relationships) often present the need for file (document) exchange. According to one aspect, external users having working relationships with internal users are able to be given limited user privileges within the file security system, such that restricted file (document) exchange is permitted between such internal and external users.
Owner:INTELLECTUAL VENTURES I LLC
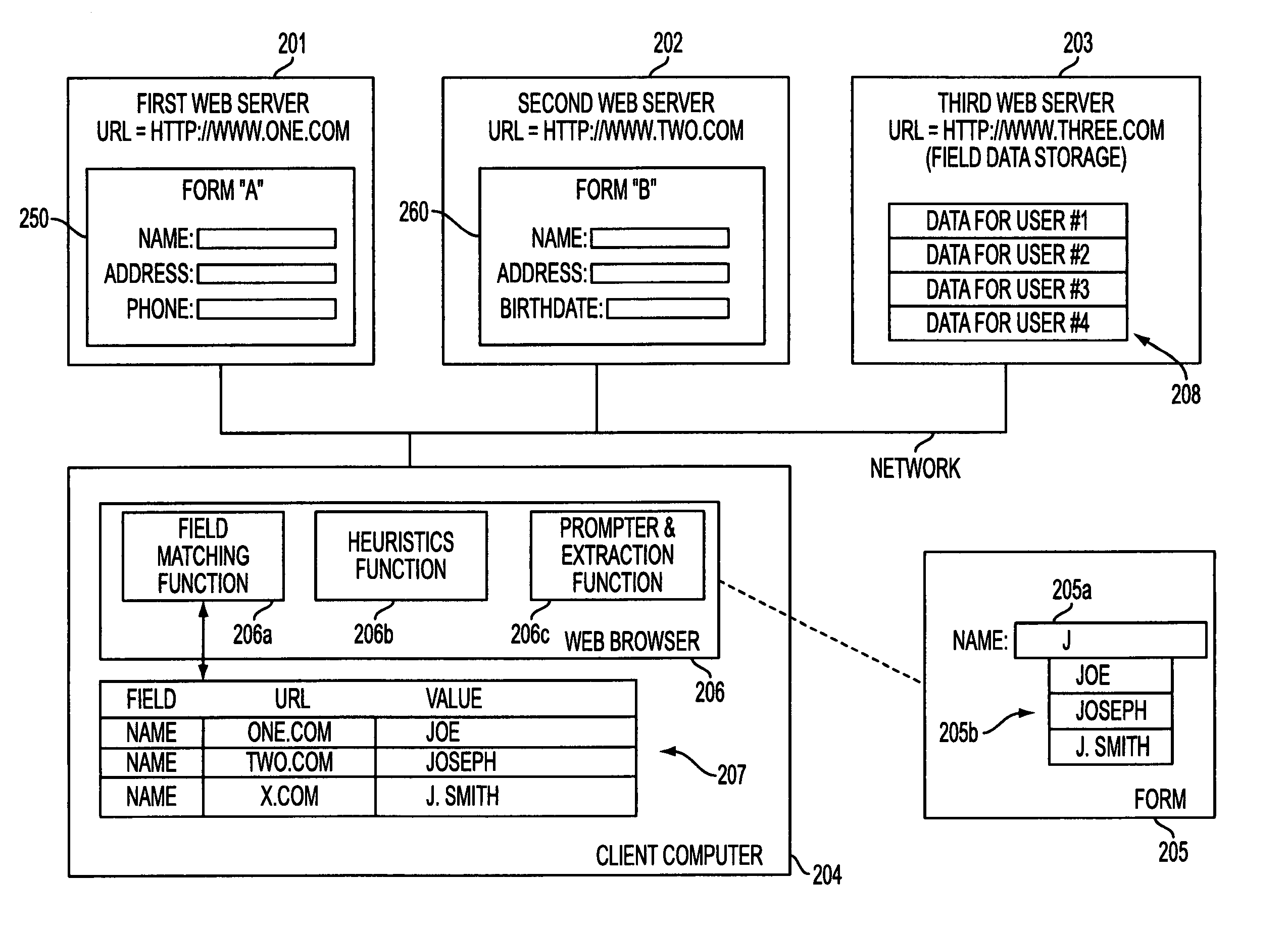
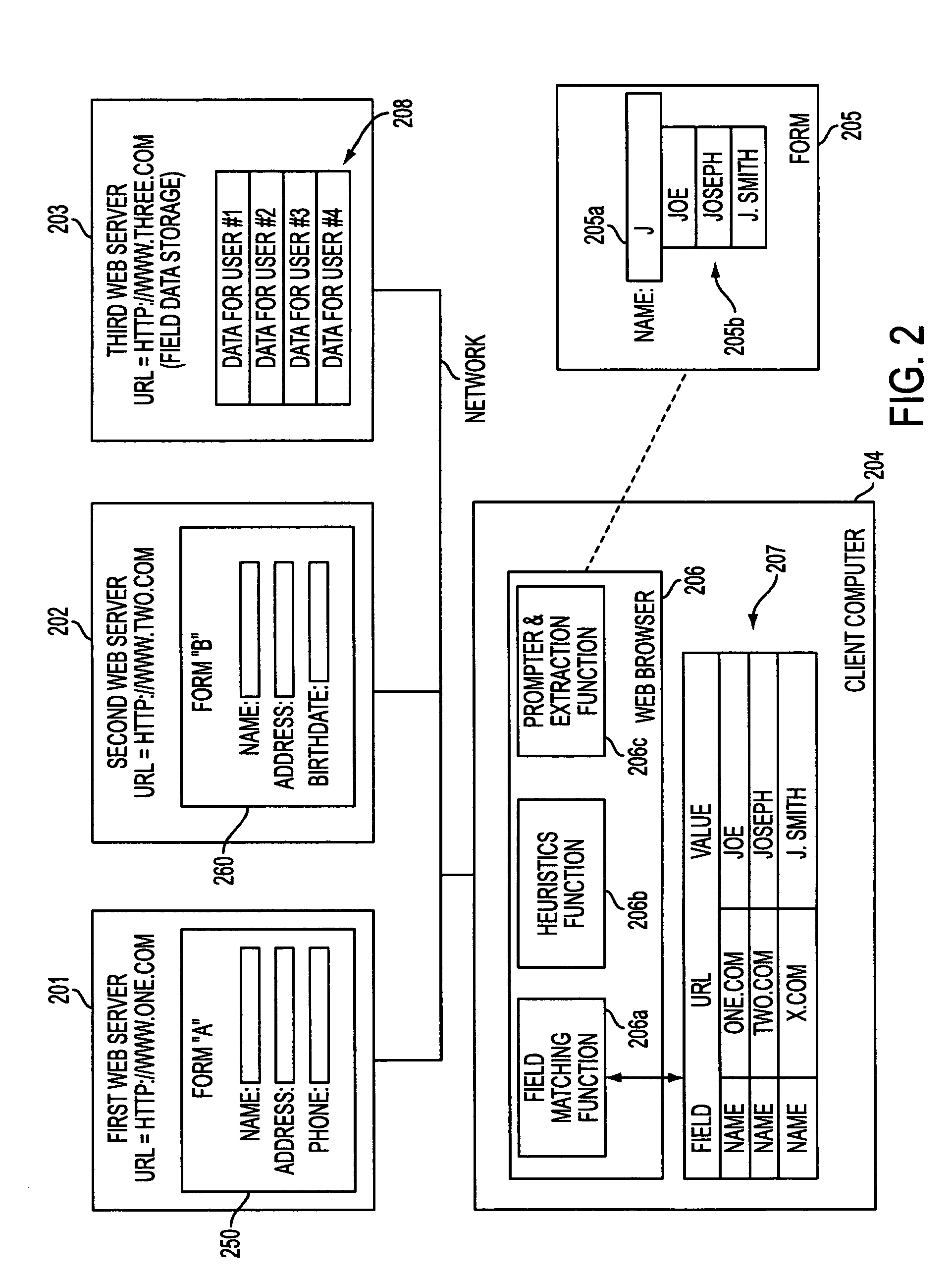
System and method for populating forms with previously used data values
InactiveUS7216292B1Compromising securityCompromising privacyDigital computer detailsNatural language data processingWeb siteWeb browser
A system and method is provided for learning data values over time as they are entered by a user on a form such as a web page form. An Internet web browser can be modified to suggest previously used data values for any form field that is the same as or similar to a previously used form field. Application programs that use the web browser can gain access to previously used form field values even if they have no knowledge of the field names. Software in a web browser associates field names across different Universal Resource Locators (URLs), so that when a user enters a value into a field (e.g., username) at a first web site, that same value can be automatically suggested when the user displays a different form on a different web site that uses the same field name.
Owner:MICROSOFT TECH LICENSING LLC
Methods and systems relating to personalized evolving avatars
InactiveUS20170080346A1Limited accessImprove security accessMedical simulationVideo gamesGraphical user interfaceLife style
Graphical user interfaces can exploit avatars to provide represent the user or their alter ego or character. It would be beneficial to provide users with an avatar not defined by the software provide but one that represents their quantified self so that their virtual world avatar evolved, adjusted, and behaved based upon the real world individual. It would also be beneficial that such a dynamically adaptive avatar provides the individual with an evolving and adjusting graphical interface to access personal information, establish adjustments in lifestyle, and monitor their health etc. within the real world but also define the characteristics, behaviour, skills, etc. that they possess within virtual worlds. Accordingly, such an avatar established in dependence upon the user's specific characteristics can then be exploited to provide data for a wide range of additional aspects of the user's life from filtering content through to controlling devices within their environment.
Owner:ABBAS MOHAMAD
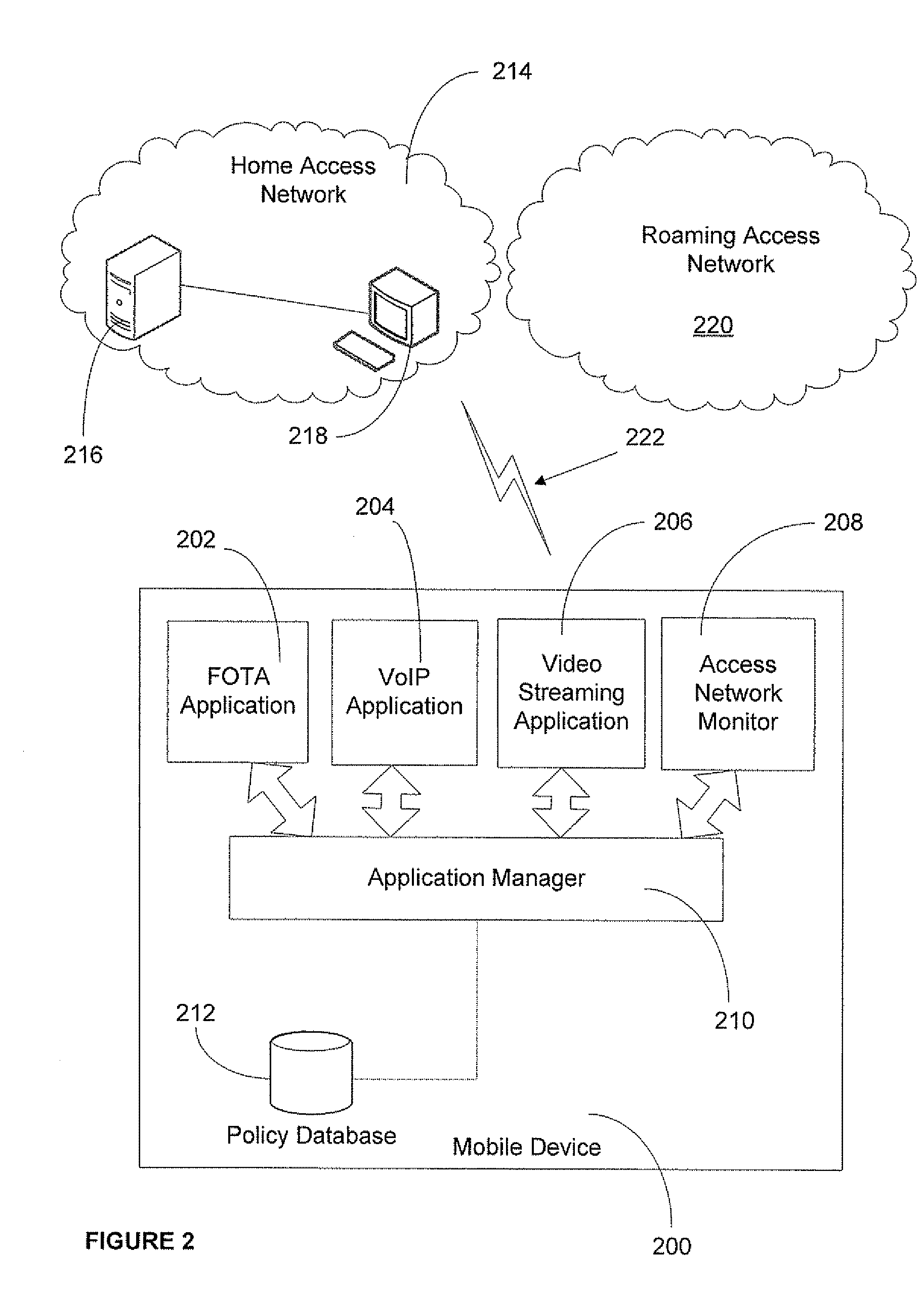
Application access control in a mobile environment
ActiveUS20080160958A1Avoid unwanted roaming chargeAvoid runningUnauthorised/fraudulent call preventionEavesdropping prevention circuitsData connectionAccess network
A system and method are described whereby a mobile device controls access to mobile applications based on access conditions associated with a current access network. To prevent mobile applications from running when the access conditions are not suitable, the mobile device includes a policy database used to store a list of access conditions that are inappropriate for launching the installed applications. The access conditions are based on the type of the current access network used by the mobile device for launching or maintaining the requested application session. The access conditions indicate whether the mobile device is currently accessing its home network or roaming on another provider's network. Similarly, the access conditions indicate the type of network access interface used by the current network to provide the data connection necessary to run the requested application. The policy database correlates predetermined actions with the access conditions associated with a given application session.
Owner:U S CELLULAR
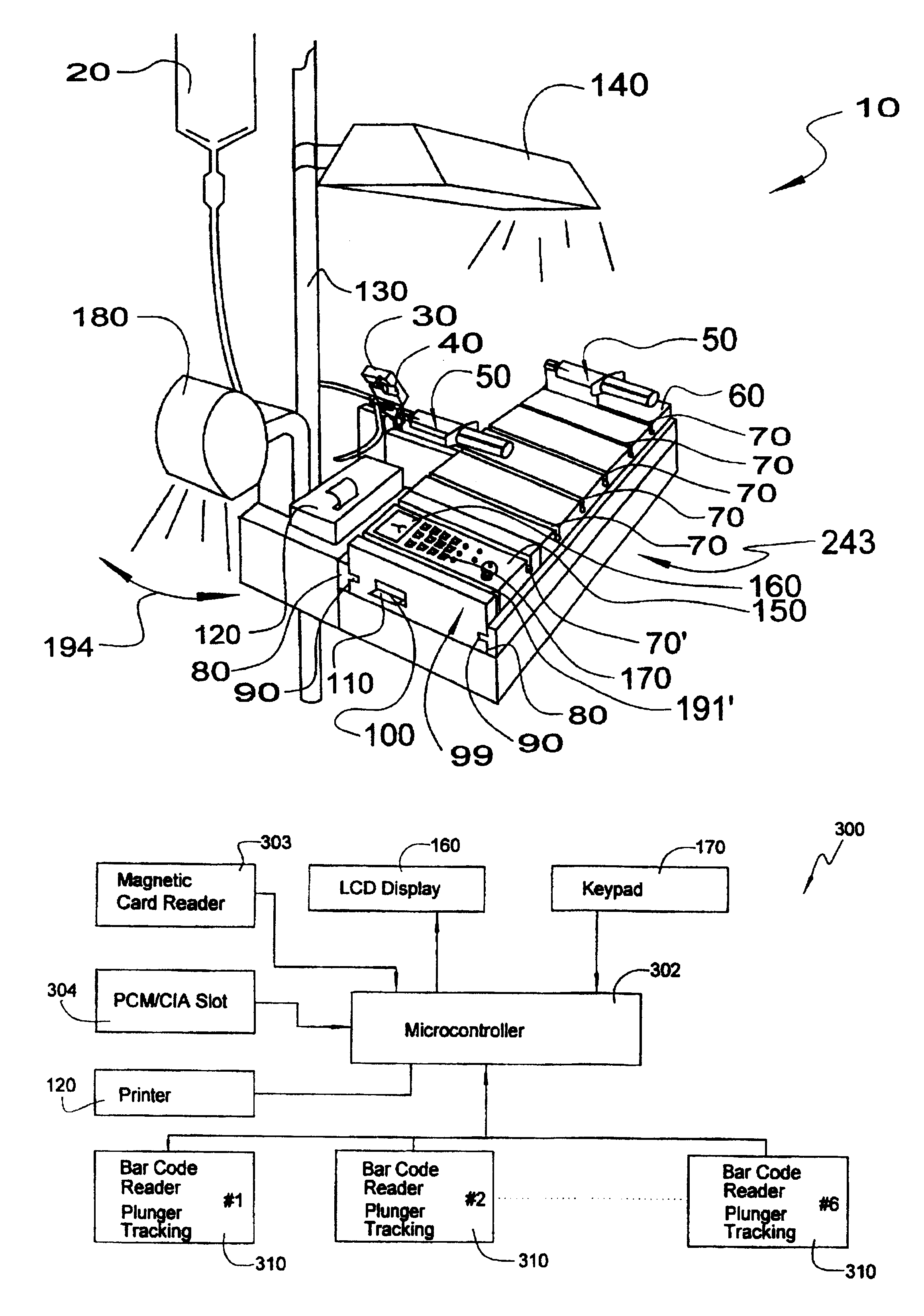
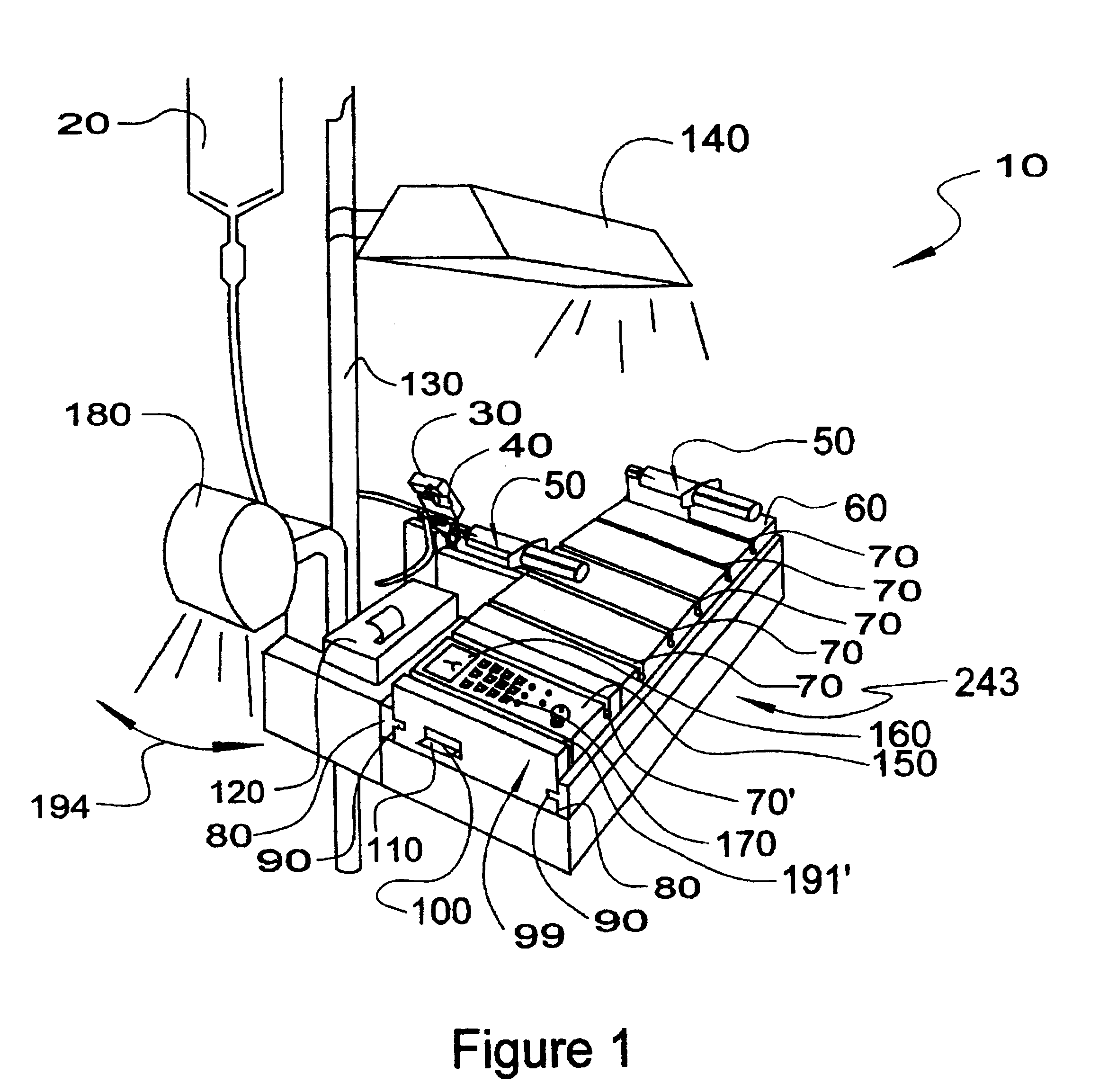
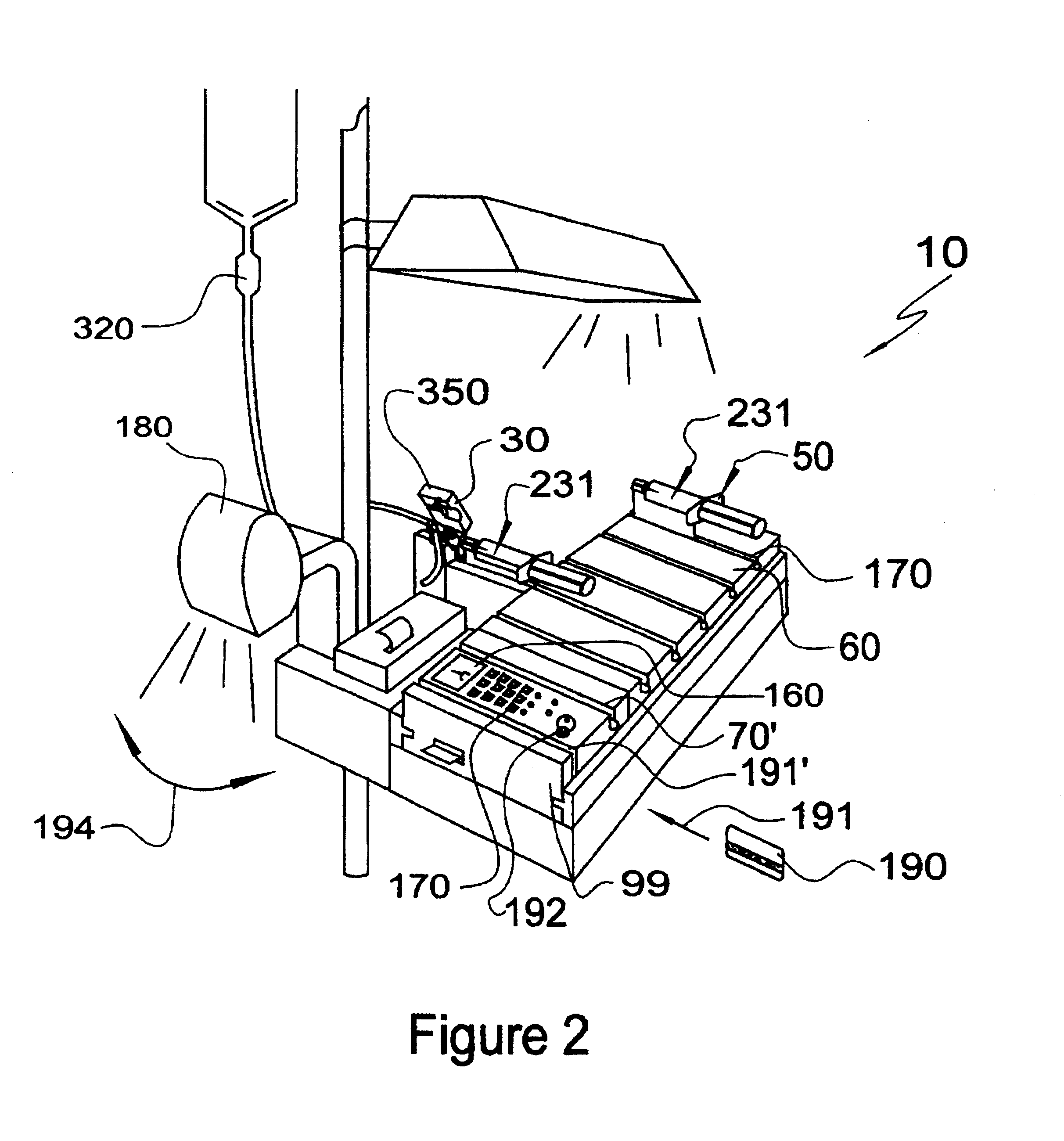
Medication delivery and monitoring system and methods
InactiveUSRE38189E1Low costLimited accessMedical devicesPressure infusionOperational systemDrugs preparations
A medication delivery and monitoring system and methods whereby drugs are safely delivered to a patient, monitored in real-time during delivery and crucial events are recorded during delivery to provide real-time, on-line information and detail for an audit trail. A novel safety label cradle unit is disclosed. Safety label cradles (SLC's) are provided in a plurality of sizes to match varying sizes of syringes which are disposed on a cradle of the SLC to provide a constant needle height on the SLC unit independent of syringe volume (barrel diameter). A selected SLC is securely affixed to a syringe by an adhesively backed label wrapping. The label is preprinted to provide drug identification indicia and drug preparation information. The information is automatically read into the system from the label. A novel delivery station of the system monitors drug delivery as a plunger of the syringe is pushed to deliver a drug to a patient. A smart tray in cooperation with a slider portion of the SLC is used to selectively deliver drugs to a port in the IV set. The smart tray comprises a first portion for carrying SLC units, an attachable second portion having a control panel for operating the system and a cover for lockably affixing the SLC units to the tray.
Owner:IBM CORP
Integrated computer security management system and method
InactiveUS7331061B1Centralized controlIncrease speedMemory loss protectionError detection/correctionSafety management systemsSecurity management
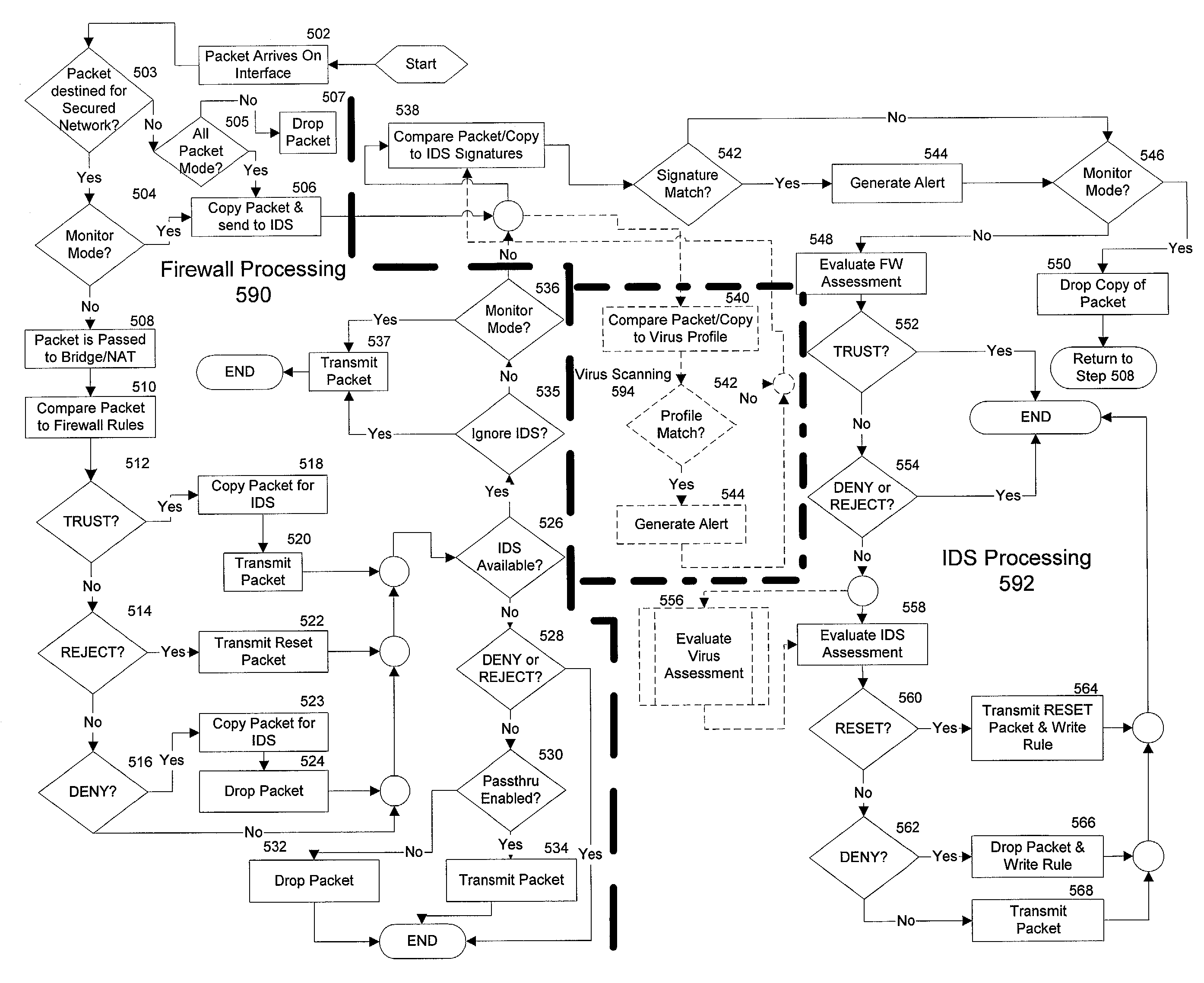
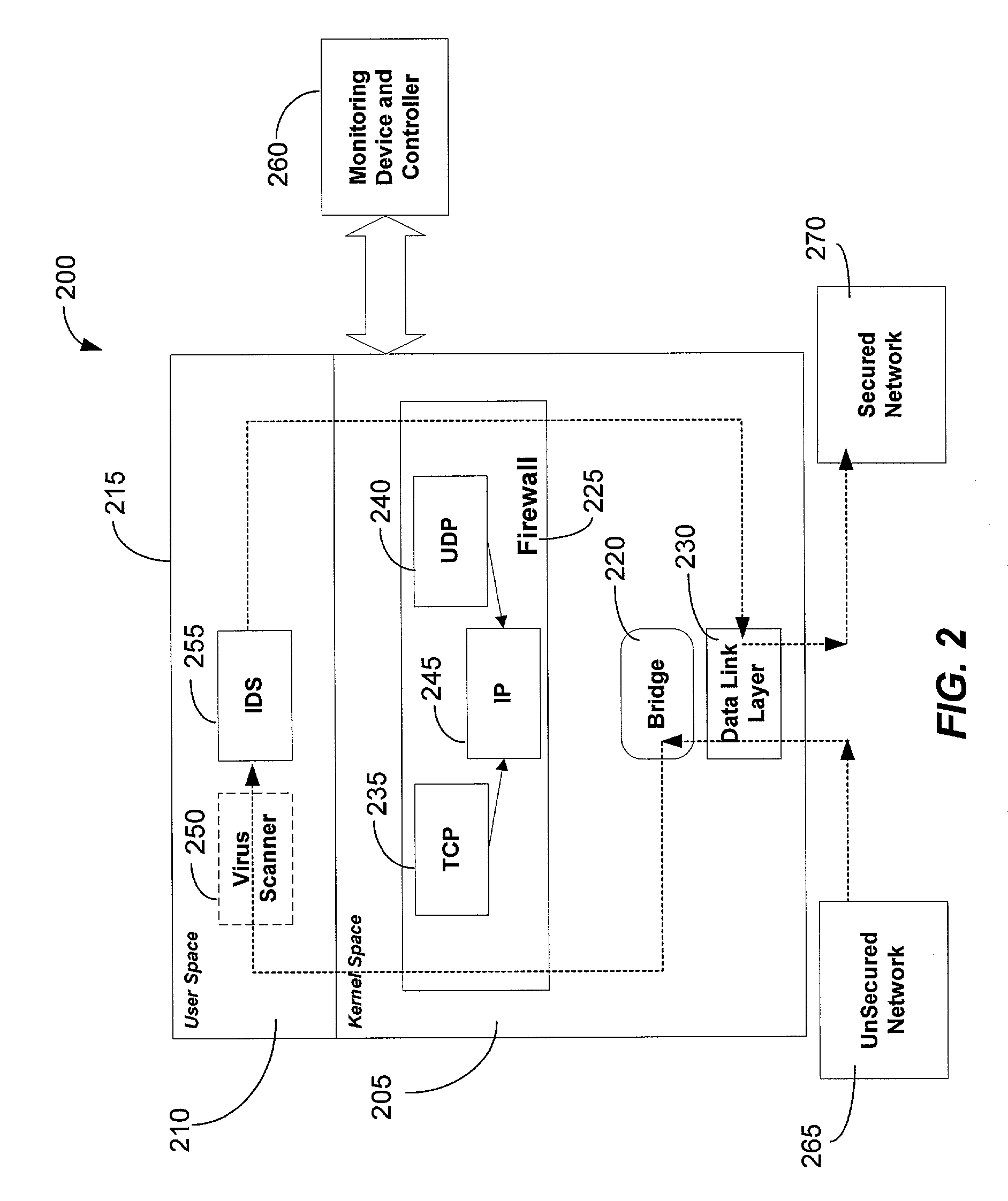
The present invention is generally directed to a computer security management system that integrates a firewall with an intrusion detection system (IDS). In other words, the firewall and IDS of the present invention can be designed to communicate process or status information and packets with one another. The present invention can facilitate centralized control of the firewall and the IDS and can increase the speed at which packets are passed between a secured computer network and an external network. Increased packet processing speed can be achieved in several ways. For example, the firewall and IDS can process packets in series, in parallel, and sometimes singularly when one of the components is not permitted to process a packet. Alternatively, singular processing can also be performed when one component is permitted to pass a packet to the secured computer network without checking with the other component.
Owner:SECUREWORKS
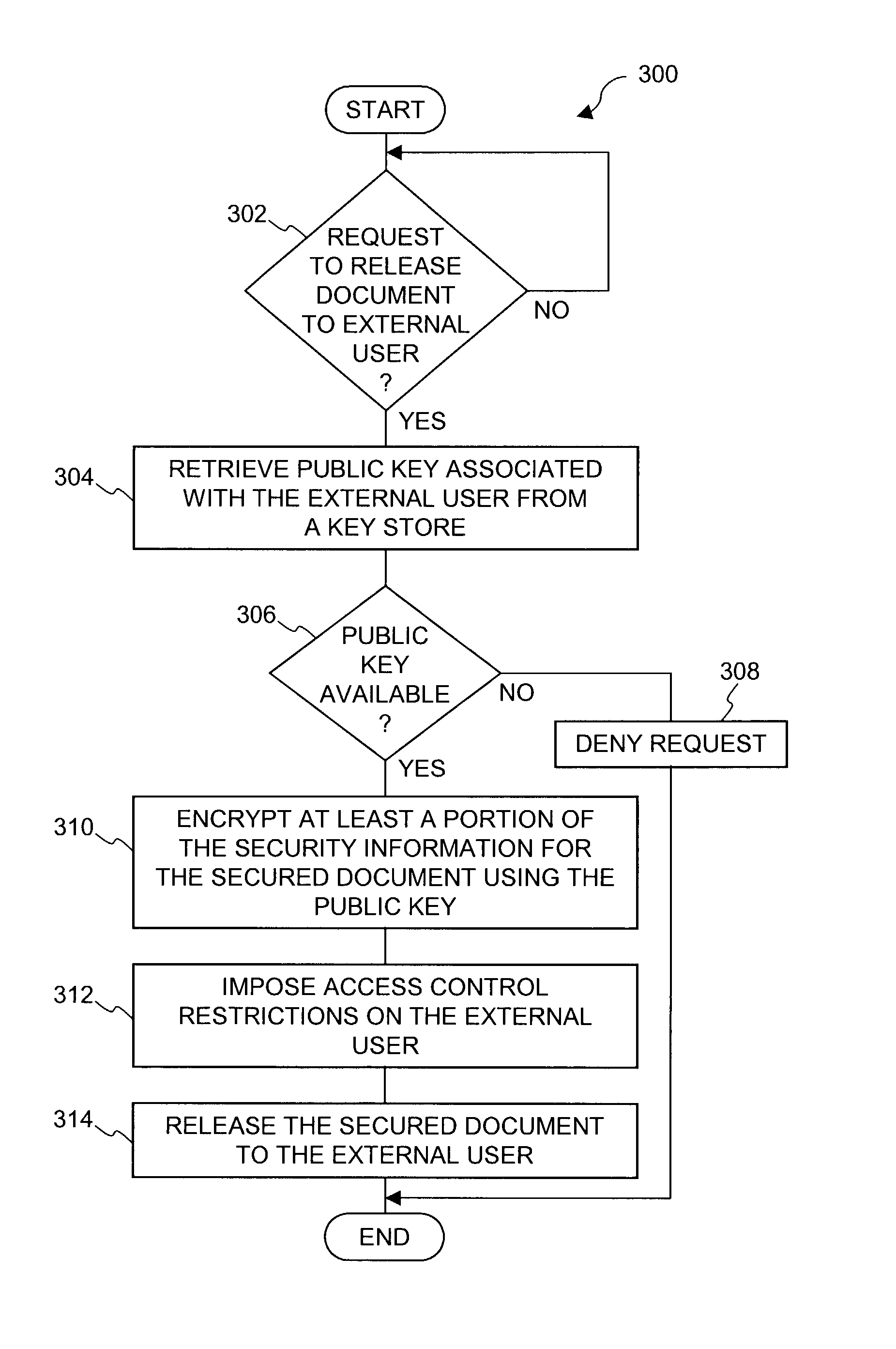
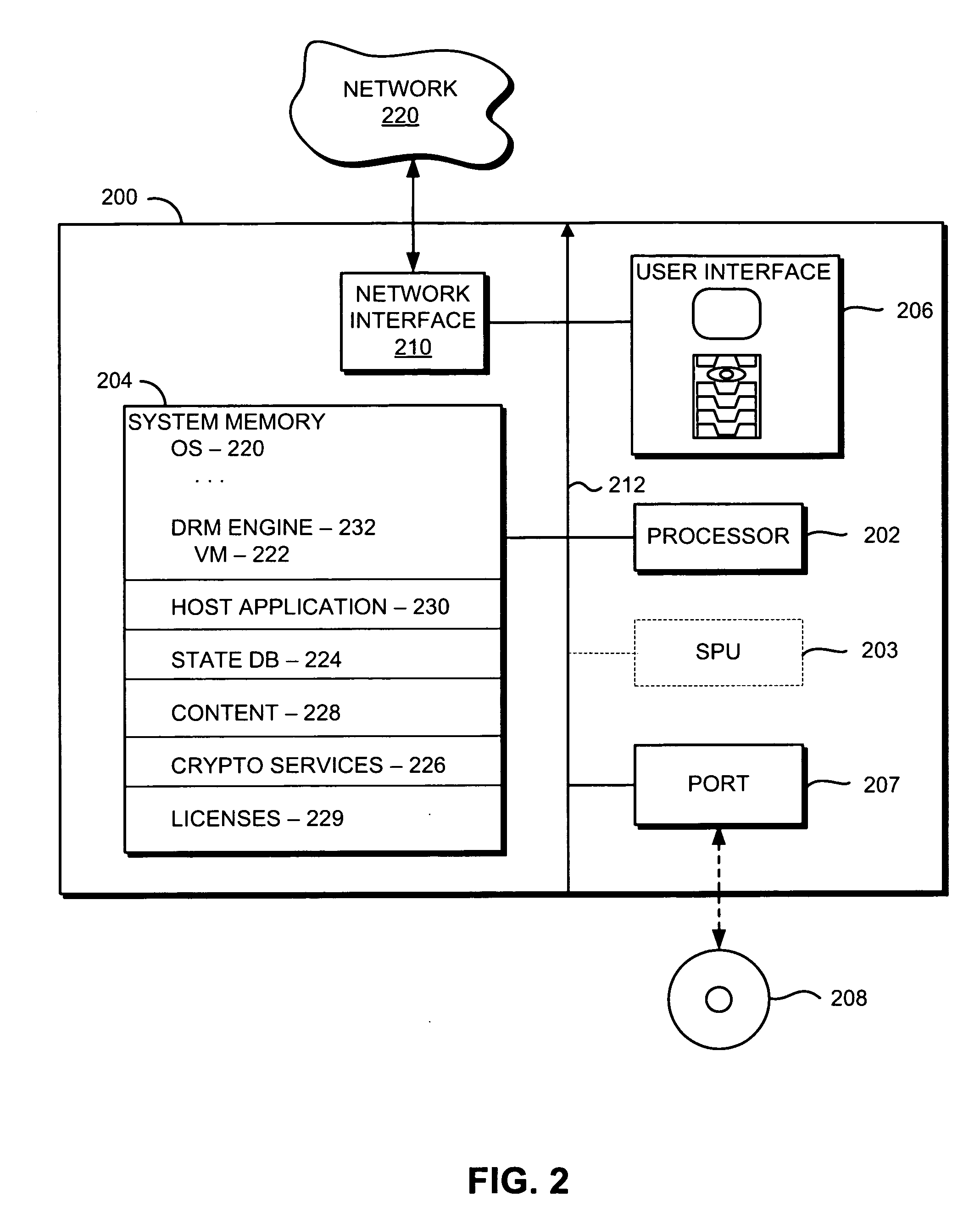
Method and apparatus for securing electronic data
ActiveUS7681034B1Facilitate access control managementGood synchronizationDigital data processing detailsUnauthorized memory use protectionPathPingEngineering
Techniques for securing electronic data and keeping the electronic data secured at all times are disclosed. According to one embodiment, a client module in a client machine is configured to provide access control to secured documents that may be located in a local store, another computer machine or somewhere over a data network. The client module includes a document-securing module configured to operate in a path through which a document being accessed is caused to pass so that the document can be examined or detected for the security nature. If the document is secured, the document-securing module obtains a user or group key to decrypt security information in the secured document for access rules therein. If a user accessing the document is determined to have the access privilege to the secured document, a file key is retrieved from the security information and a cipher module is activated to decrypt the encrypted data portion with the file key. Likewise, if a document is to be secured, the cipher module encrypts clear data from the document to create the encrypted data portion. The document-securing module integrates proper or desired security information with the encrypted data portion to produce the secured document.
Owner:INTELLECTUAL VENTURES I LLC
Movable audio/video communication interface system
InactiveUS7626569B2Easily integrated with other mode of workingReduce componentsCathode-ray tube indicatorsTwo-way working systemsHead movementsSensor array
A system that includes a desk top assembly of a display and sensors mounted on a robotic arm. The arm moves the assembly so that it remains within position and orientation tolerances relative to the user's head as the user looks around. Near-field speaker arrays supply audio and a microphone array senses a user's voice. Filters are applied to head motion to reduce latency for arm's tracking of the head. The system is full duplex with other systems allowing immersive collaboration. Lighting and sound generation take place close to the user's head. A haptic interface device allows the user to grab the display / sensor array and move it about. Motion acts as a planar selection device for 3D data. Planar force feedback allows a user to “feel” the data. Users see not only each other through display windows, but can also see the positions and orientations of each others' planar selections of shared 3D models or data.
Owner:MORGAN STANLEY +1
Digital rights management engine systems and methods
ActiveUS20070100701A1Limited accessHand manipulated computer devicesDigital data protectionRights managementDigital rights management
Systems and methods are described for performing digital rights management. In one embodiment, a digital rights management engine is provided that evaluates license associated with protected content to determine if a requested access or other use of the content is authorized. In some embodiments, the licenses contain control programs that are executable by the digital rights management engine.
Owner:INTERTRUST TECH CORP
Internet security dynamics assessment system, program product, and related methods
ActiveUS8069471B2Prevent malicious attacksLimited accessMemory loss protectionDigital data processing detailsIp addressThe Internet
Owner:LOCKHEED MARTIN CORP
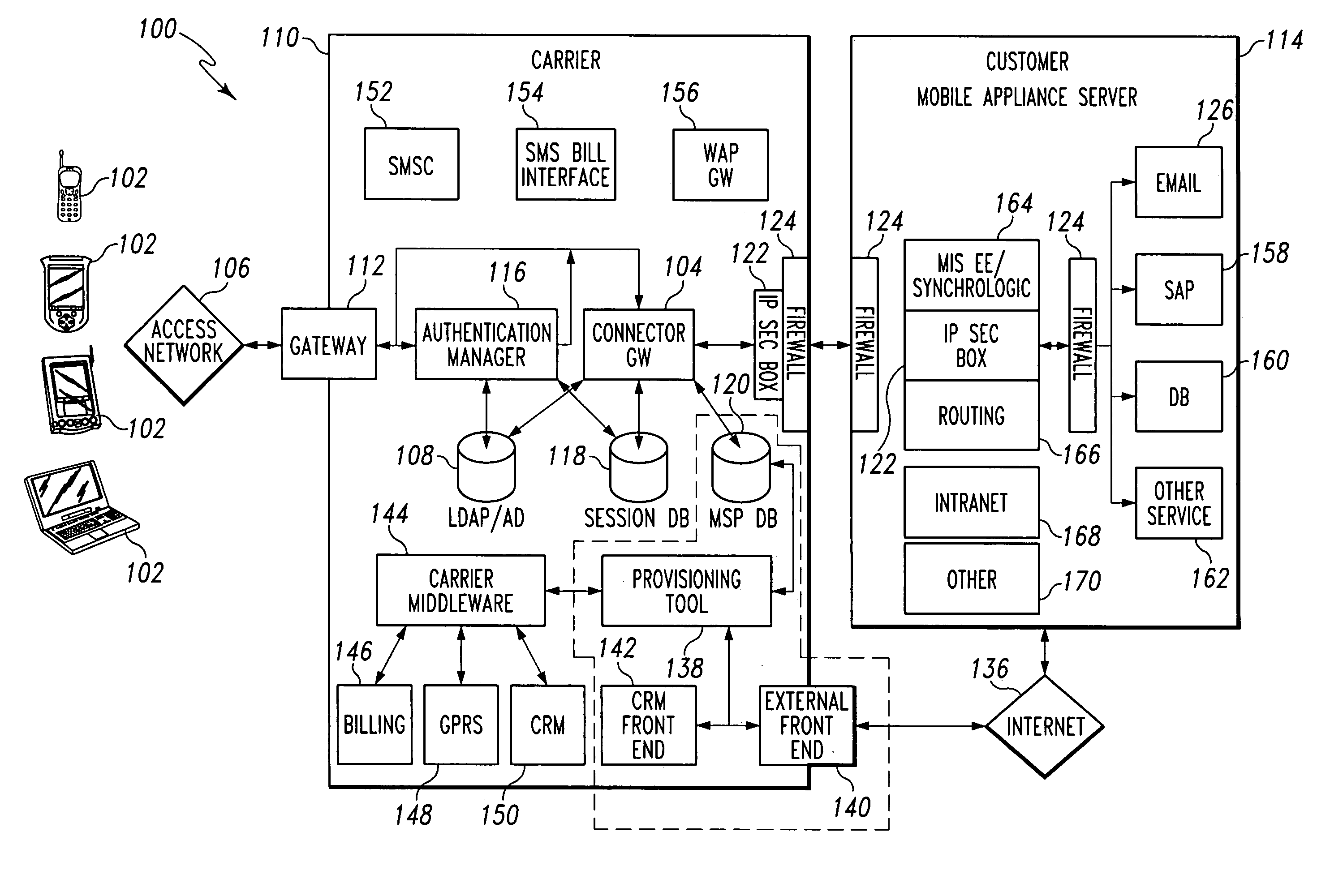
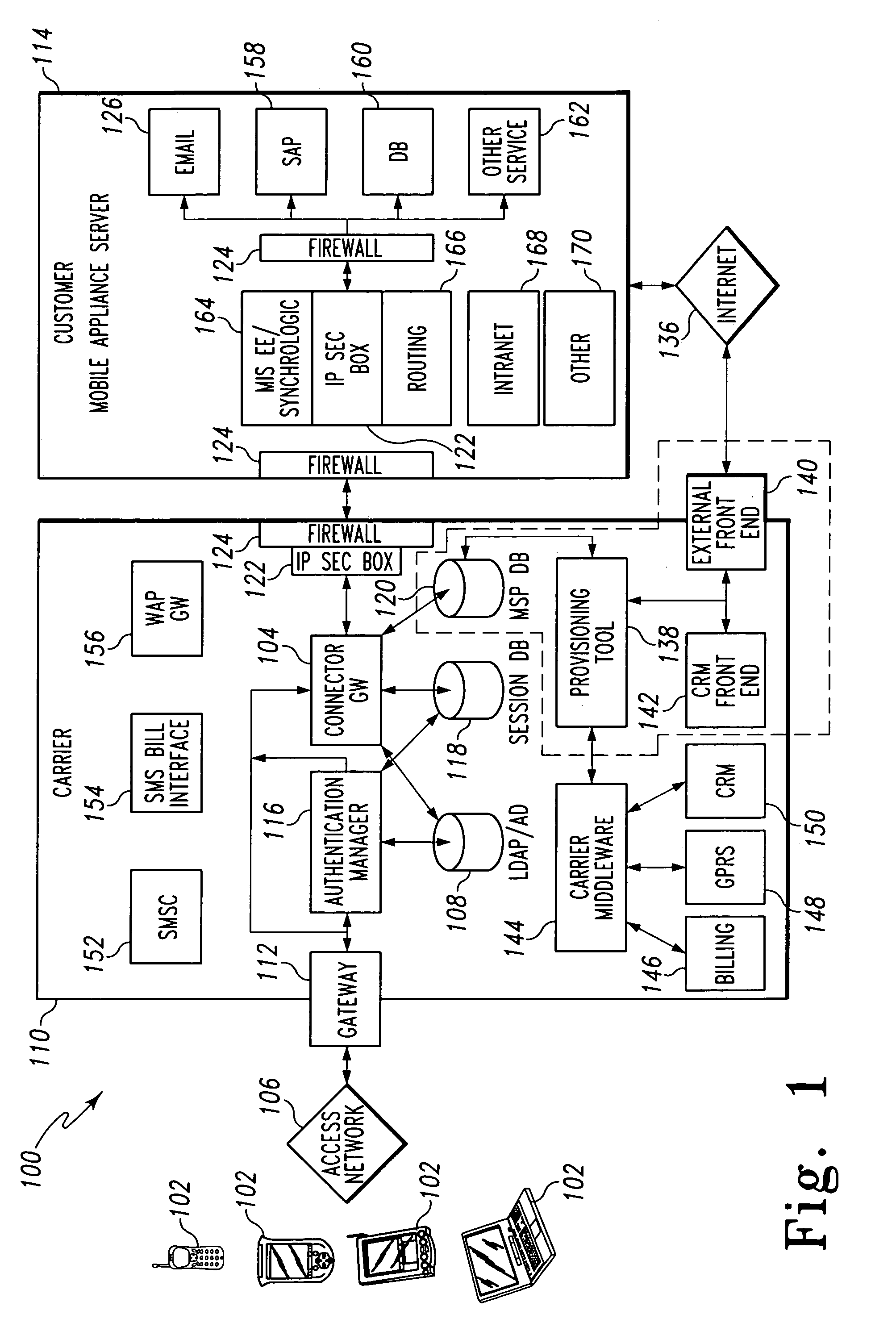
Mobile provisioning tool system
ActiveUS7239877B2Significant processingLimited accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile businessNetwork connection
Owner:ACCENTURE GLOBAL SERVICES LTD
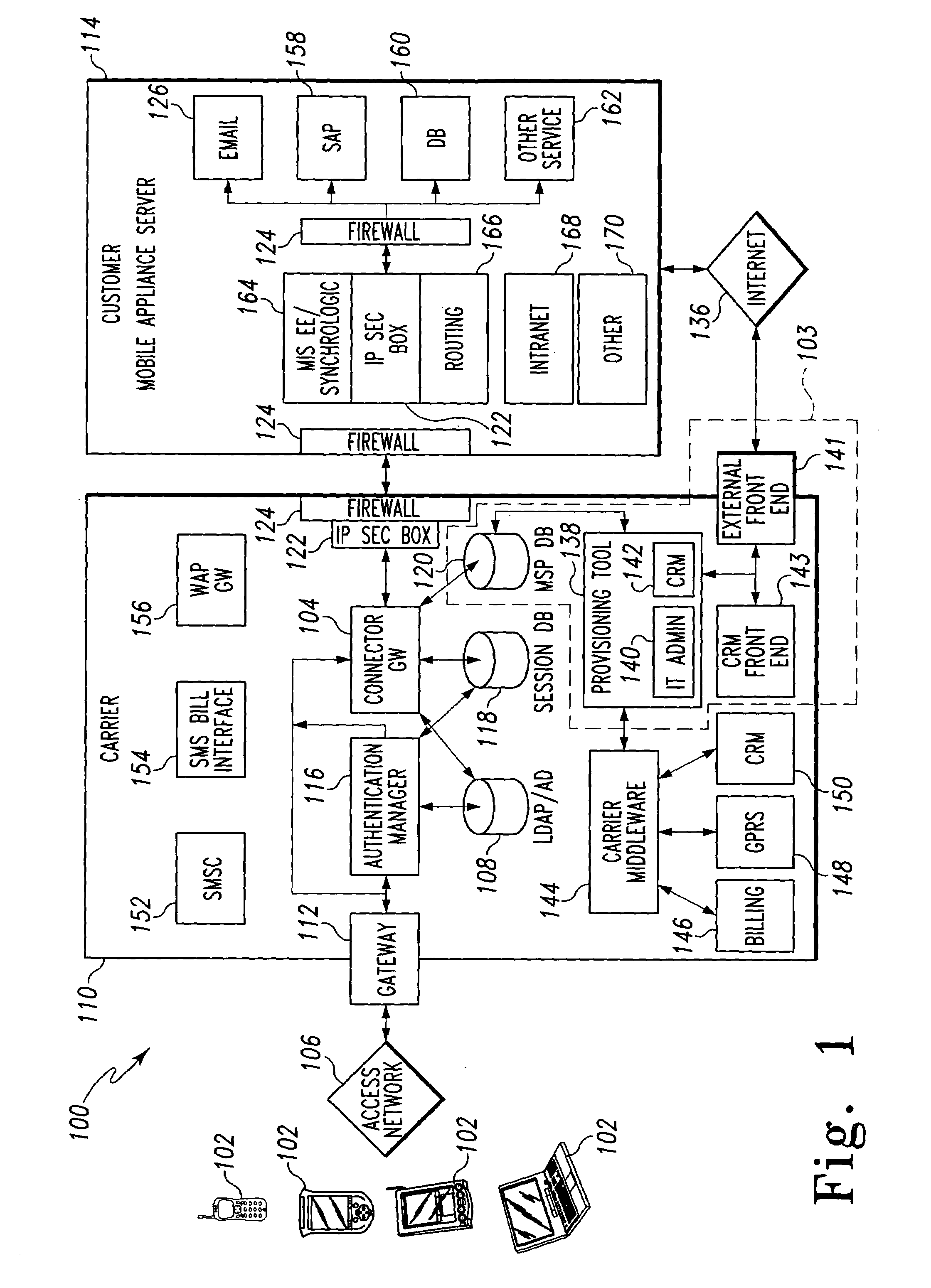
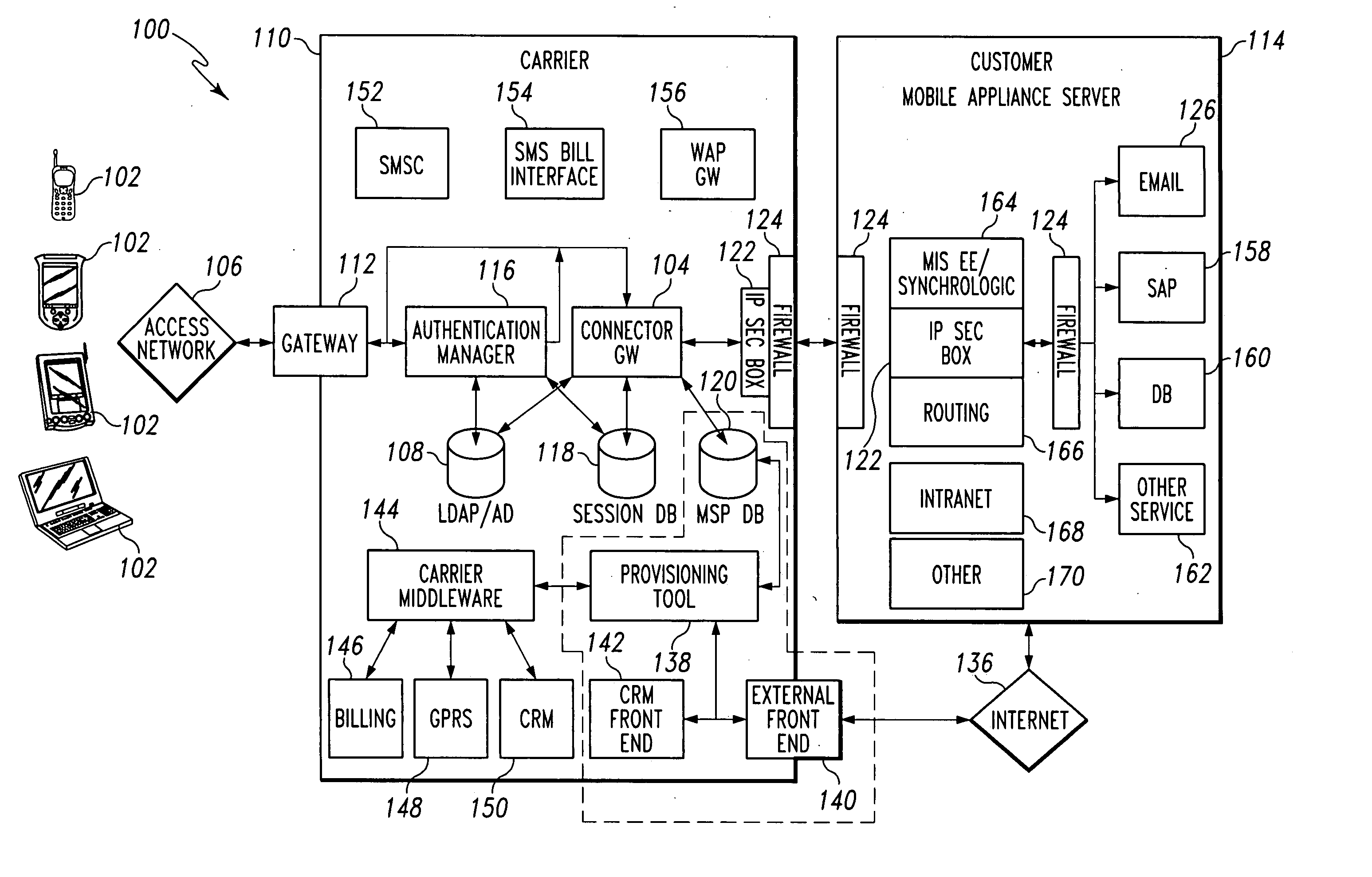
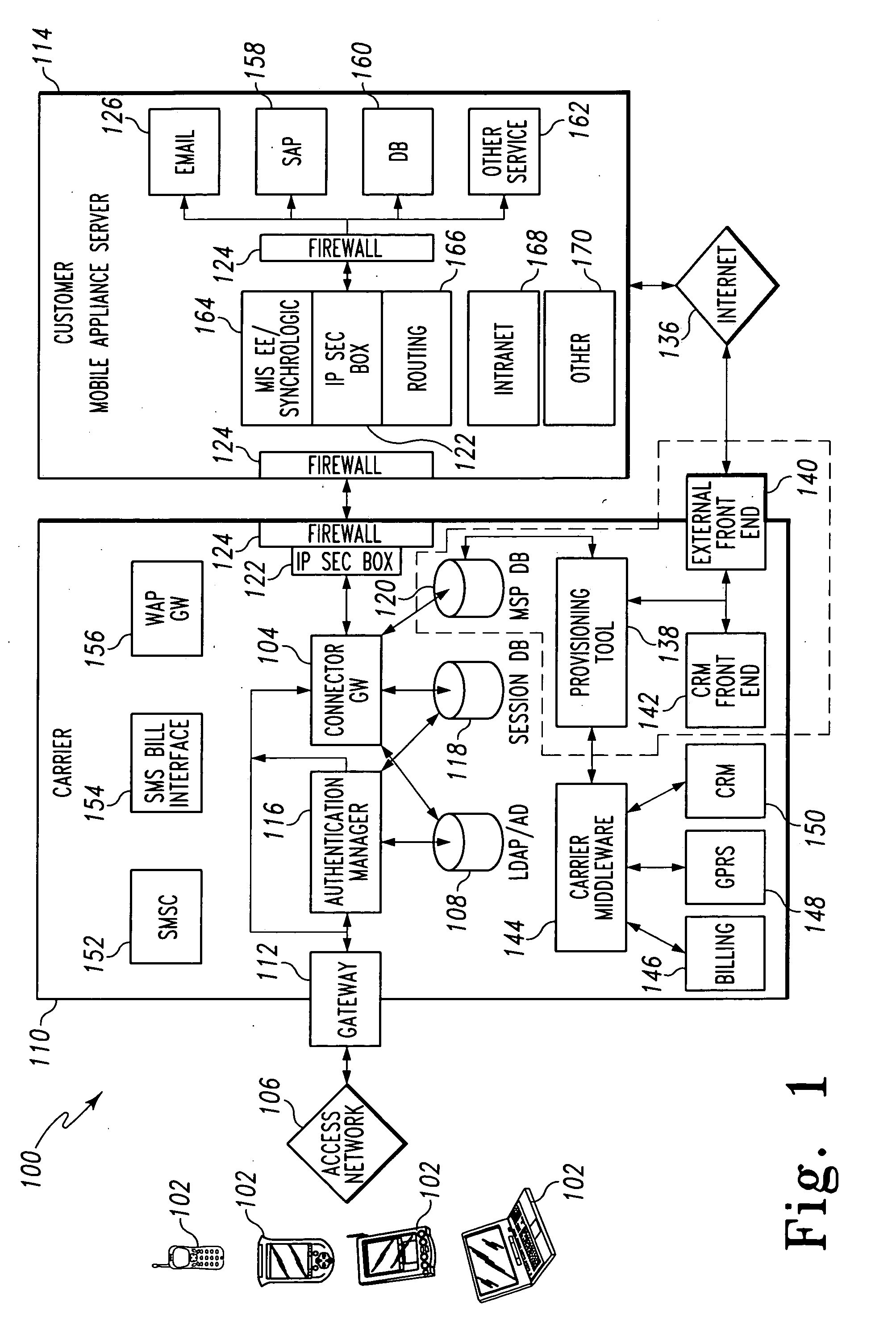
Connector gateway
ActiveUS20050073982A1Simple processLimited accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsGateway systemComputer network
A connector gateway system that provides mobile devices with access to business services is disclosed. The connector gateway system comprises a mobile device that includes an application that is capable of generating a service request. The service request may be generated from the application and may include a DNS name that translates to an address on the connector gateway server. The connector gateway server performs a lookup operation to determine the business server associated with the service request. The connector gateway server creates a data filter that drives an emulation between the mobile device and the business server to pump data between the mobile device and the business server.
Owner:ACCENTURE GLOBAL SERVICES LTD
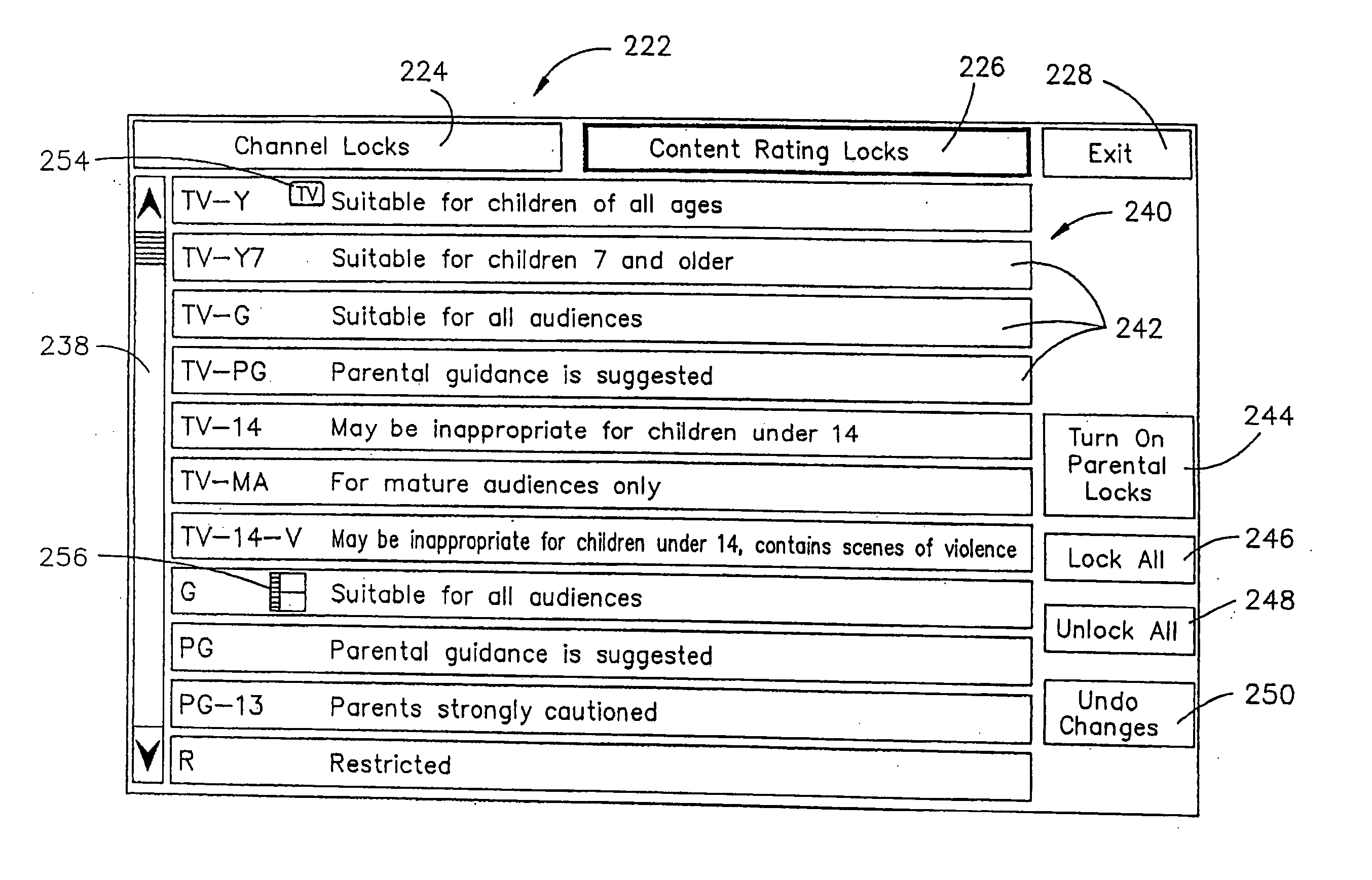
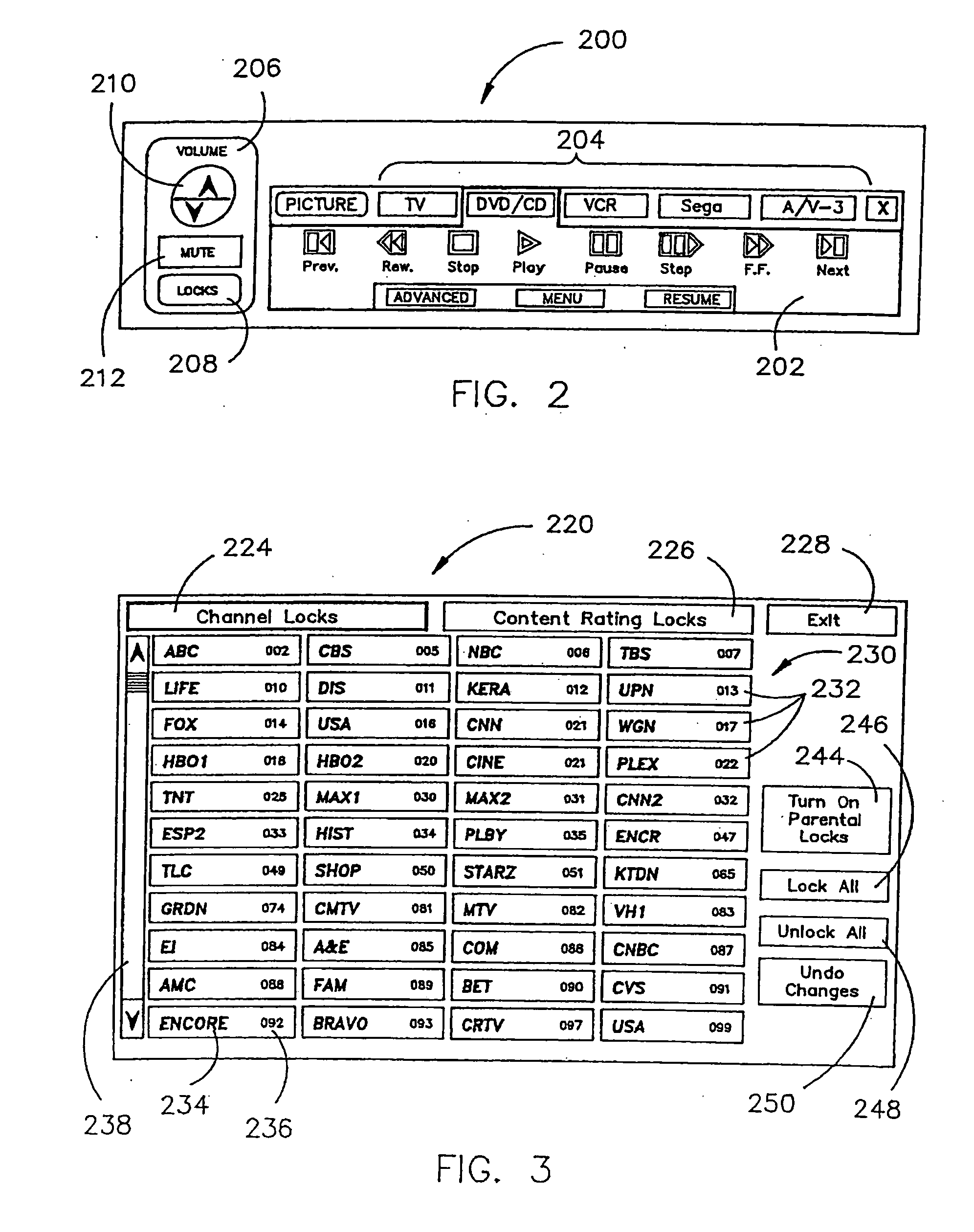
Content control system
InactiveUS20050028191A1Limited accessTelevision system detailsPicture reproducers using cathode ray tubesInformation processingComputer network
A content control system for limiting access by sensitive users, such as children, or the like, to certain types of content. The content control system provides a user interface for an information handling system, information appliance, content recorder, or the like that provides a single point of user control for parental locks for multiple audio and / or audiovisual devices. In embodiments of the invention, the content control system may employ a method of setting the content rating parameters of a content control system based on content rating of example content. The content control system may also employ a method for modifying the content rating of content received by a content recorder such as a personal video recorder, or the like.
Owner:SULLIVAN GARY E +4
Digital rights management engine systems and methods
InactiveUS20070204078A1Limited accessValidity is limitedDigital data protectionProgram/content distribution protectionDigital rights managementLicense
In one embodiment, a digital rights management engine is provided that evaluates license associated with protected content to determine if a requested access or other use of the content is authorized. In some embodiments, the licenses contain control programs that are executable by the digital rights management engine.
Owner:INTERTRUST TECH CORP
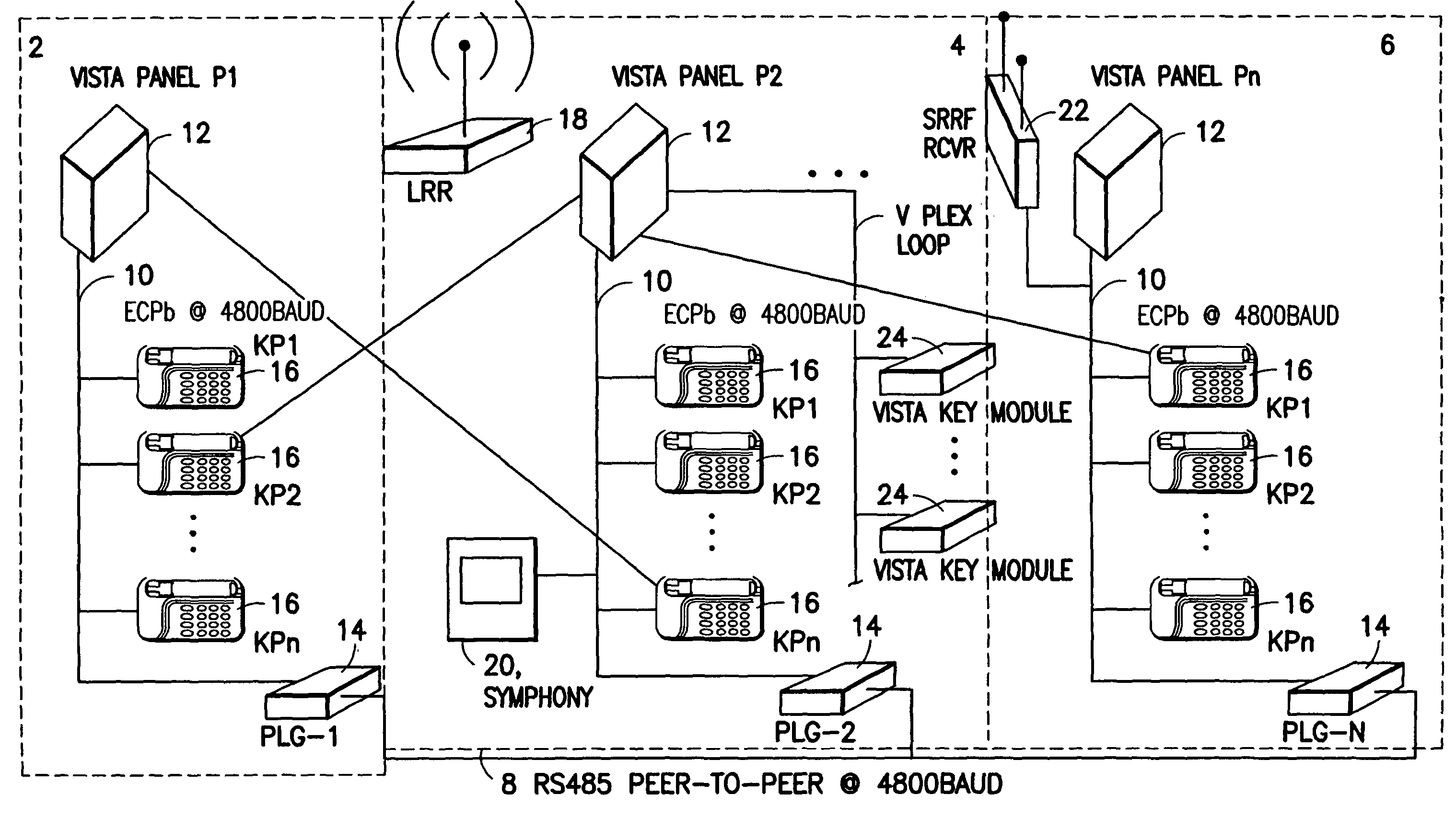
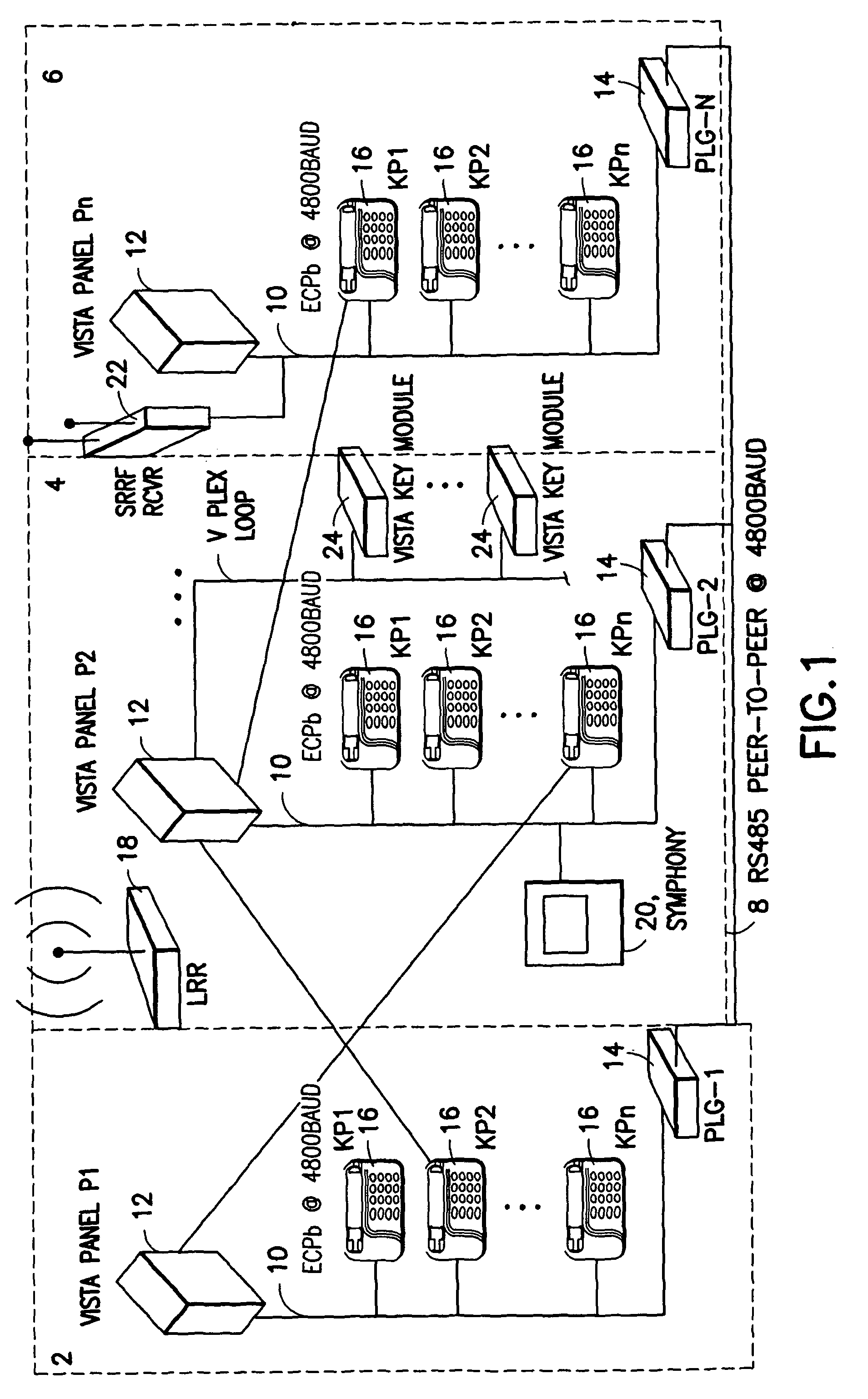
System and method for panel linking in a security system
InactiveUS7734906B2Low costLimited accessDigital data processing detailsTelephonic communicationEngineeringSecurity system
A security system comprising a plurality of security subsystems each of the security subsystems being discretely located, typically in separate buildings. The security subsystems are interconnected by a system communications bus to enable bi-directional communication between the security subsystems. Each of the security subsystems comprises a user interface, a control panel, a plurality of security devices, a local communications bus, and a panel linking gateway. The panel linking gateway allows data on the local communications bus of each security subsystem to be transmitted to and received from the system communications bus. The security system allows a keypad or other user interface from one security subsystem to access and control a second remote security subsystem.
Owner:ADEMCO INC
Connector gateway
ActiveUS7324473B2Significant processingLimited accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer networkApplication software
Owner:ACCENTURE GLOBAL SERVICES LTD
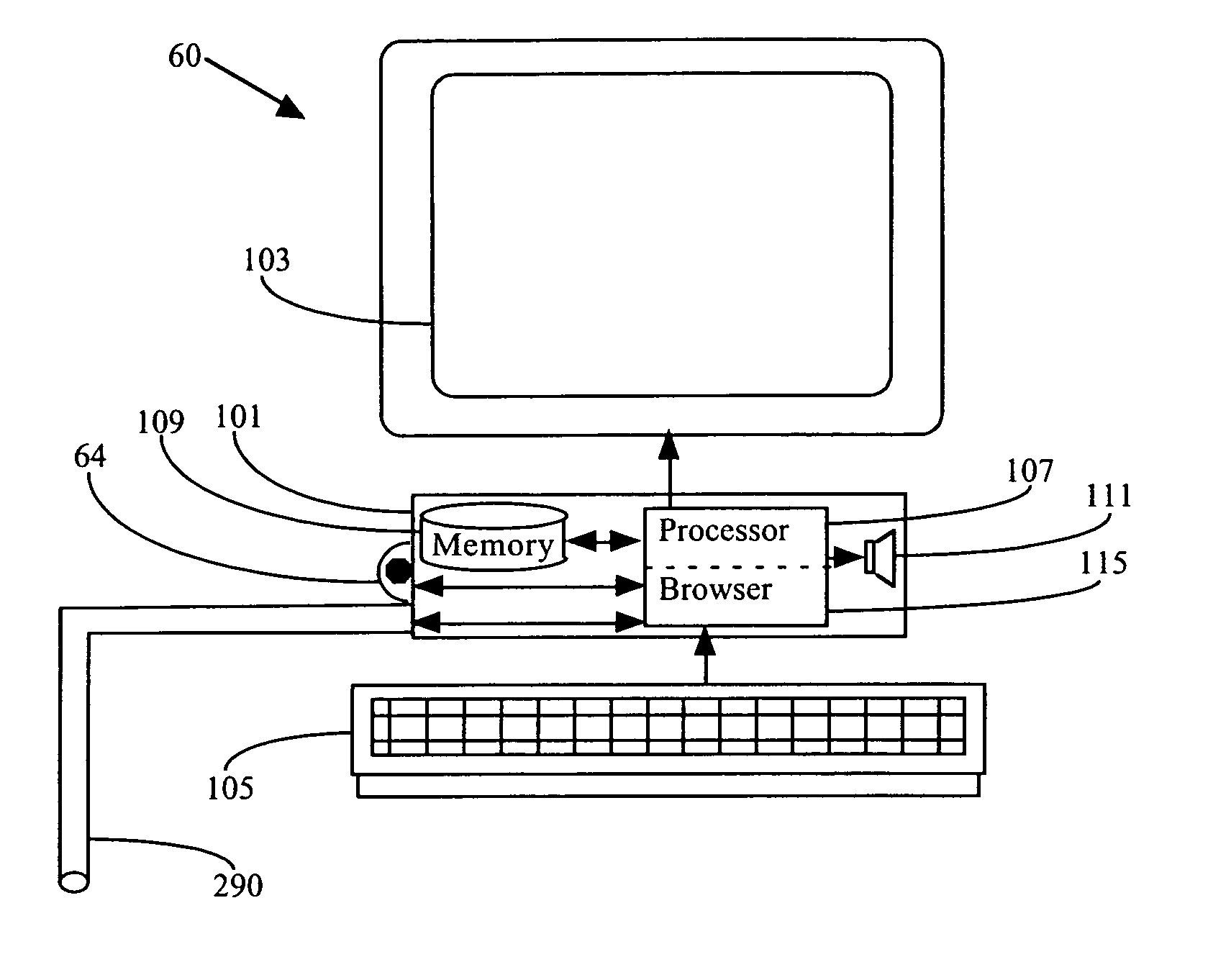
System and method to authenticate users to computer systems
InactiveUS7941534B2Facilitates rapid secondary logLimited accessDigital data processing detailsDrug and medicationsTransceiverTelecommunications link
Owner:DLH TECH LLC
Localized access
InactiveUS20020091745A1Limited accessData processing applicationsDigital data processing detailsIdentity management systemDatabase
An identity management system manages identity profiles that store information about various entities. A localized access feature for an identity management system allows for a set of identity profiles to be grouped together in order to define a locale. Users outside the locale can be restricted from accessing identity profiles inside the locale. Alternatively, users outside the locale can be restricted from accessing certain attributes of identity profiles inside the locale.
Owner:ORACLE INT CORP
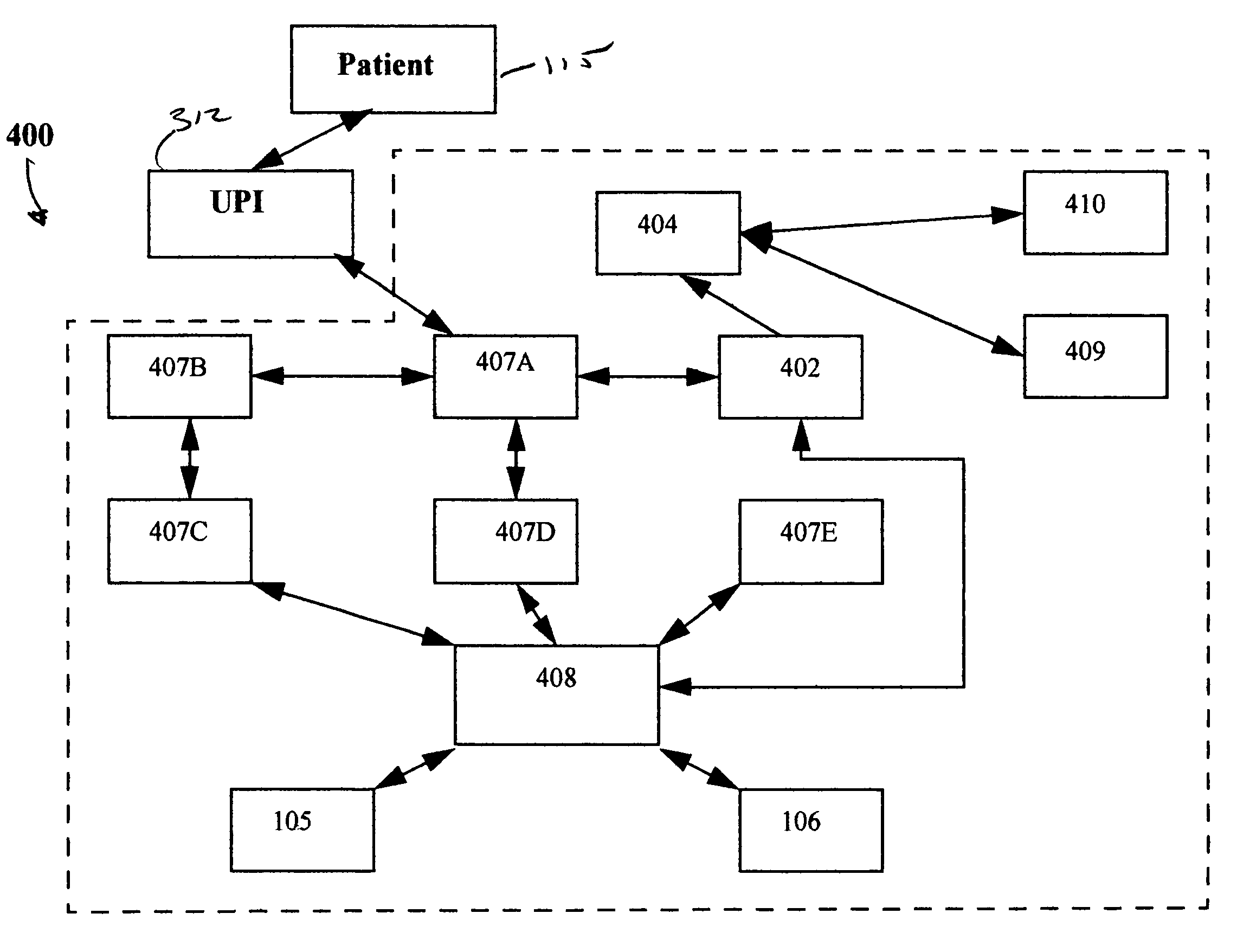
System and method for obtaining, processing and evaluating patient information for diagnosing disease and selecting treatment
InactiveUS7379885B1Increase efficiencyImprove overall quality of careDrug and medicationsDiagnostic recording/measuringComputer basedRisk factor
A computer-based system and method is disclosed which constructs medical histories by direct interactions between the patient and system that acquires pertinent and relevant medical information covering the complete life of a given patient. The system and method insure that a complete life long medical history is acquired from every patient interacting with the health care system. Once acquired, the facts of the patient's life long and family medical history are analyzed automatically by databases to generate a set of the most reasonable diagnostic possibilities (the differential diagnosis) for each medical problem identified and for each risk factor for disease that is uncovered in the historical database. Further, the automatically analyzed database of historical medical information is used as the search tool for bringing to bear, on the diagnosis and treatment of each medical problem identified in each patient, the entirety of medical knowledge that relates to and can be useful for the correct and efficient diagnosis and treatment of each of every patient's medical problems. This collection of information is analyzed to generate a final diagnosis and treatment regimen.
Owner:ZAKIM DAVID S
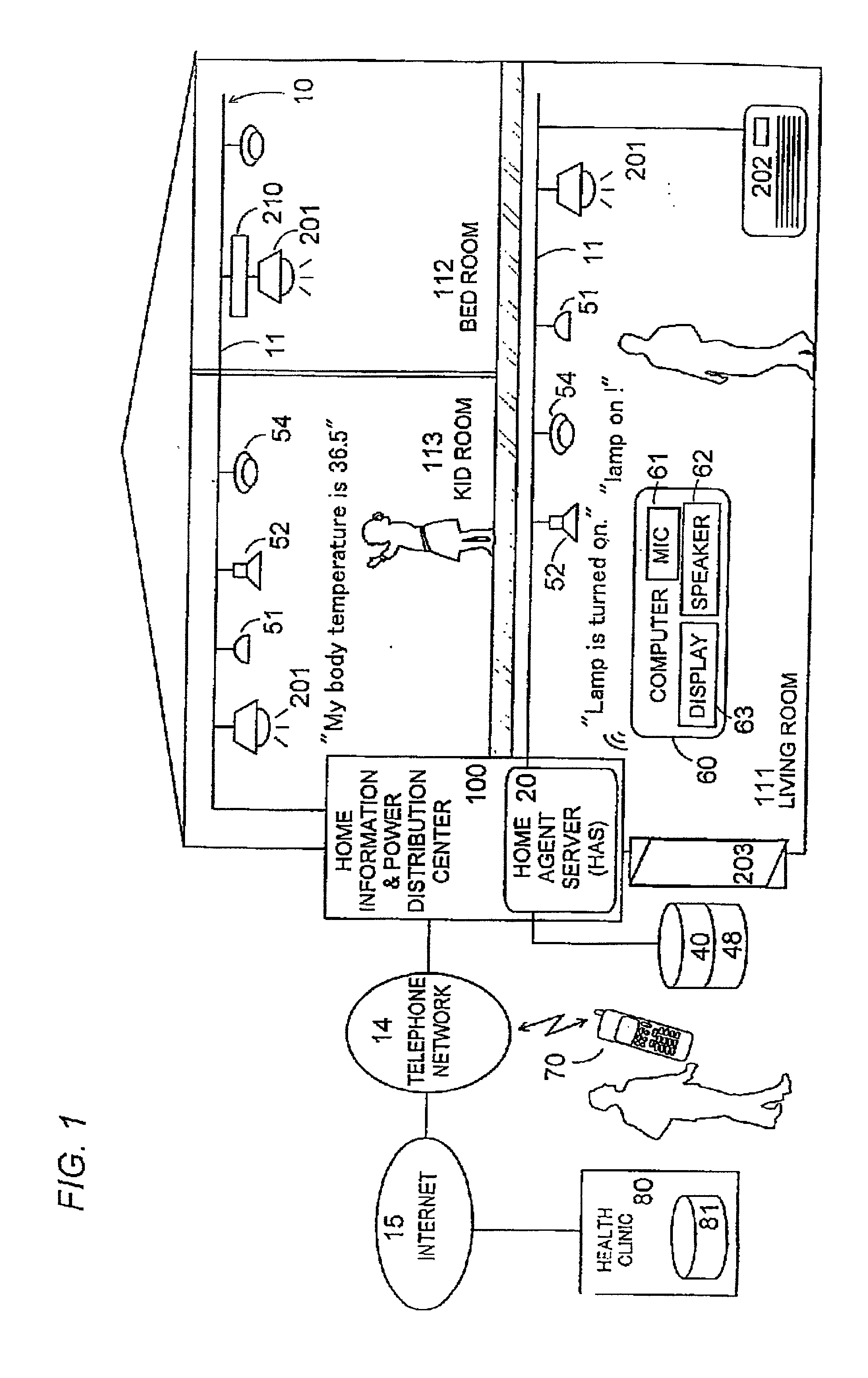
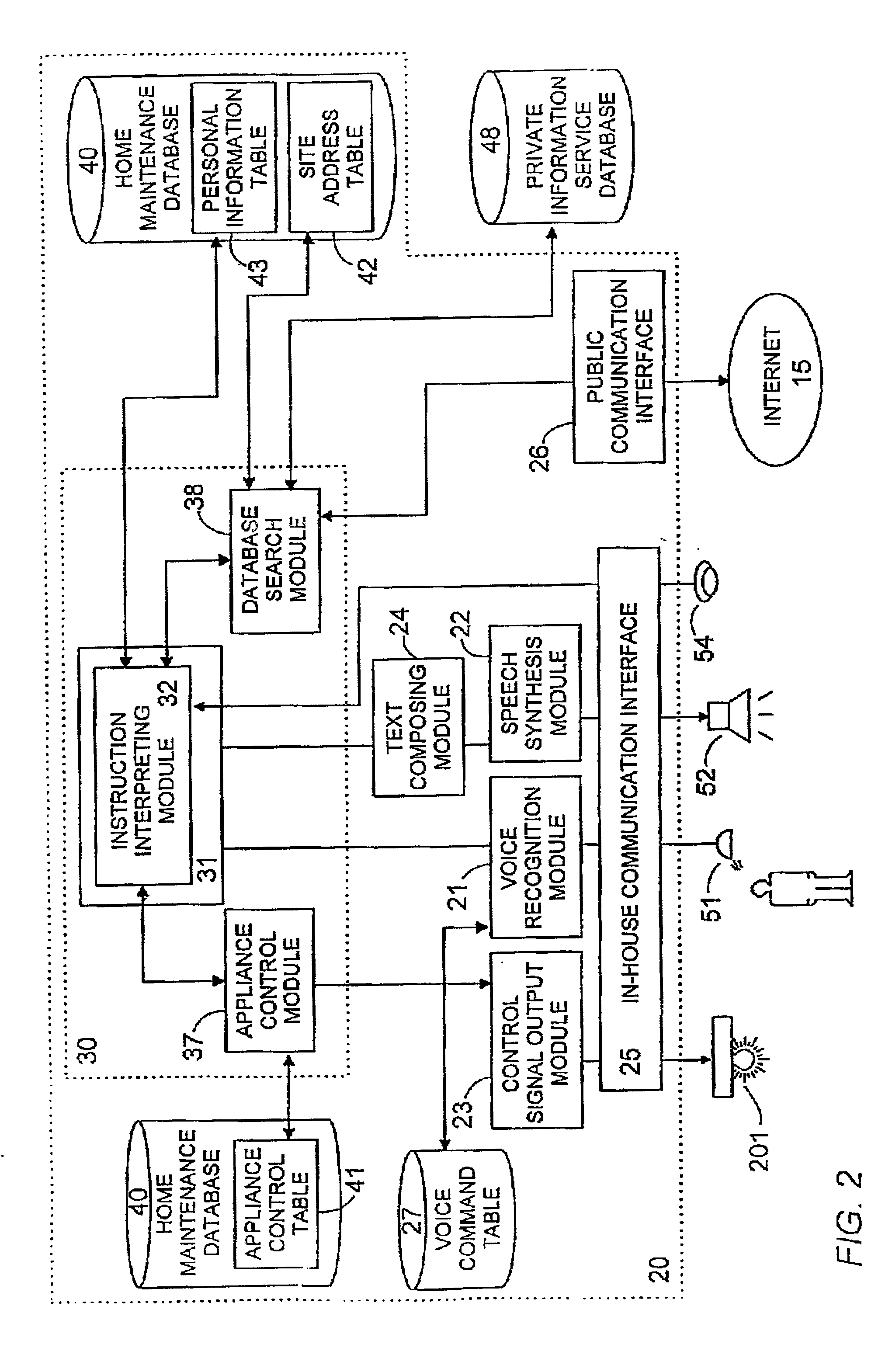
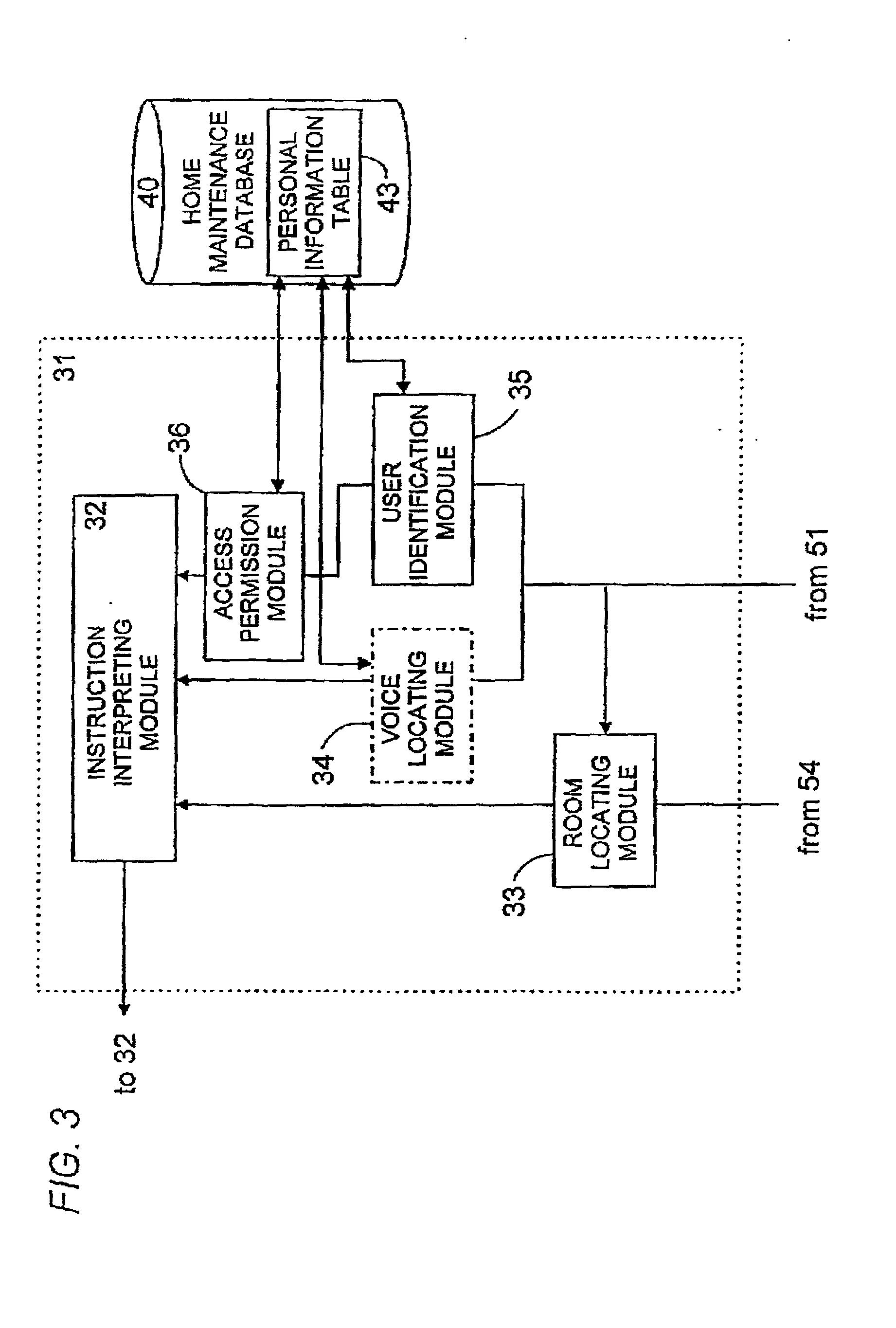
Voice control system for operating home electrical appliances
InactiveUS20010041982A1Avoid controlSafety managementData processing applicationsTelemetry/telecontrol selection arrangementsControl mannerControl system
A voice control system for managing home electrical appliances includes a home agent server (HAS) connected to the home electrical appliances, a microphone and a speaker linked to the agent server through an in-house network. An transaction processing (TP) program runs on HAS and interprets the user's voice request to find a destined appliance and a manner of control the same, and performs the requested control to the destined appliance. The result is notified to the user by means of a voice message.
Owner:MATSUSHITA ELECTRIC WORKS LTD
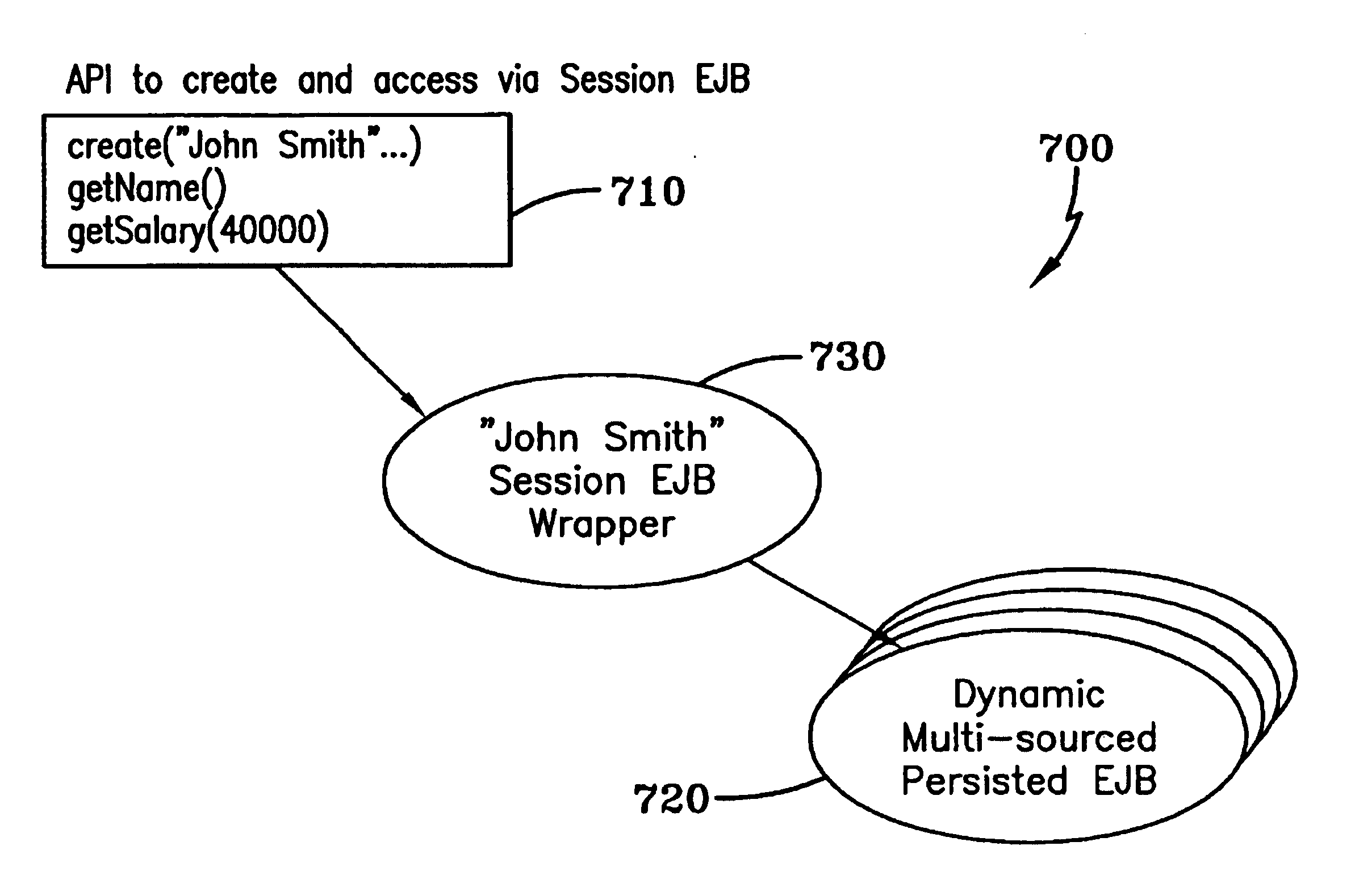
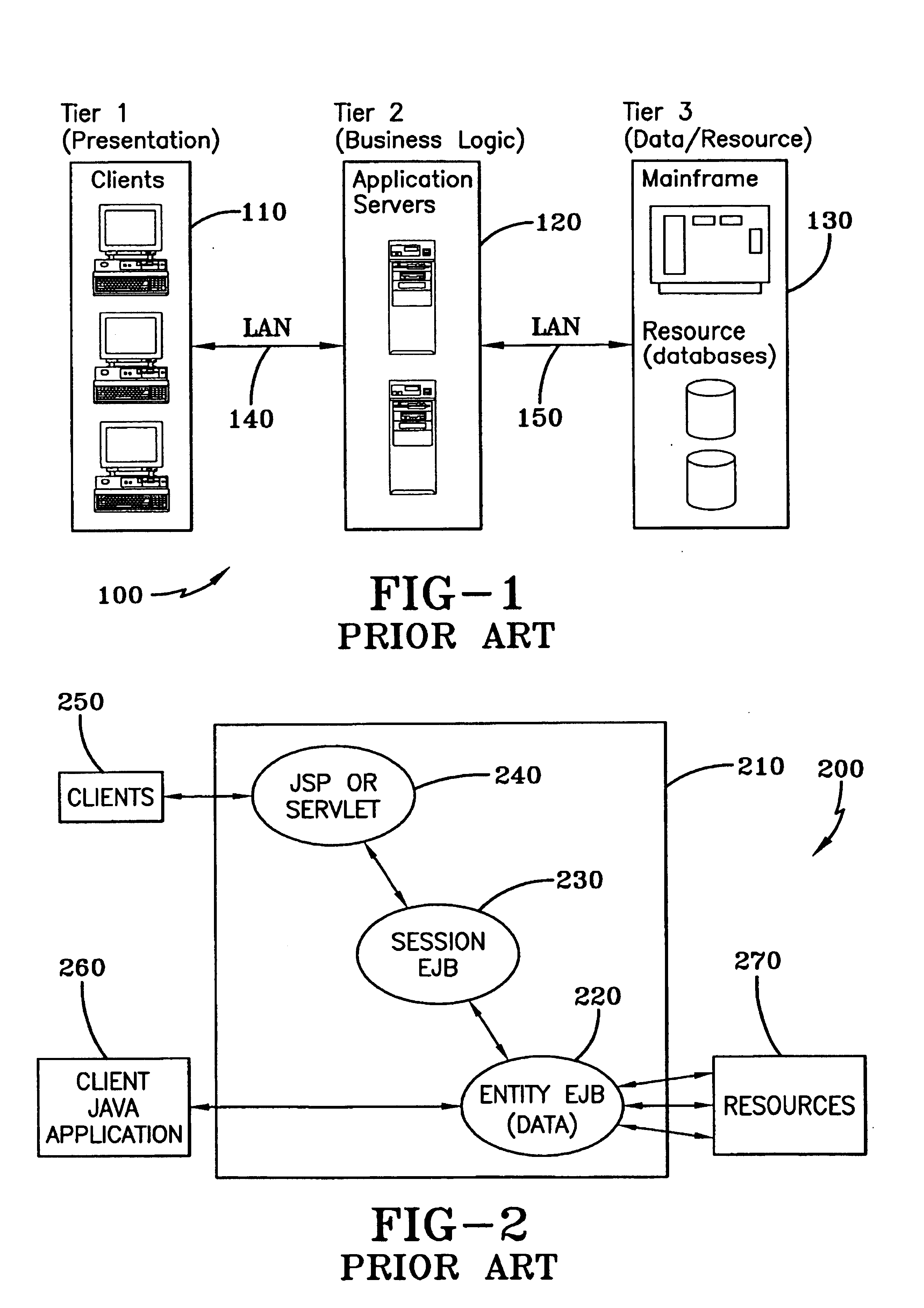
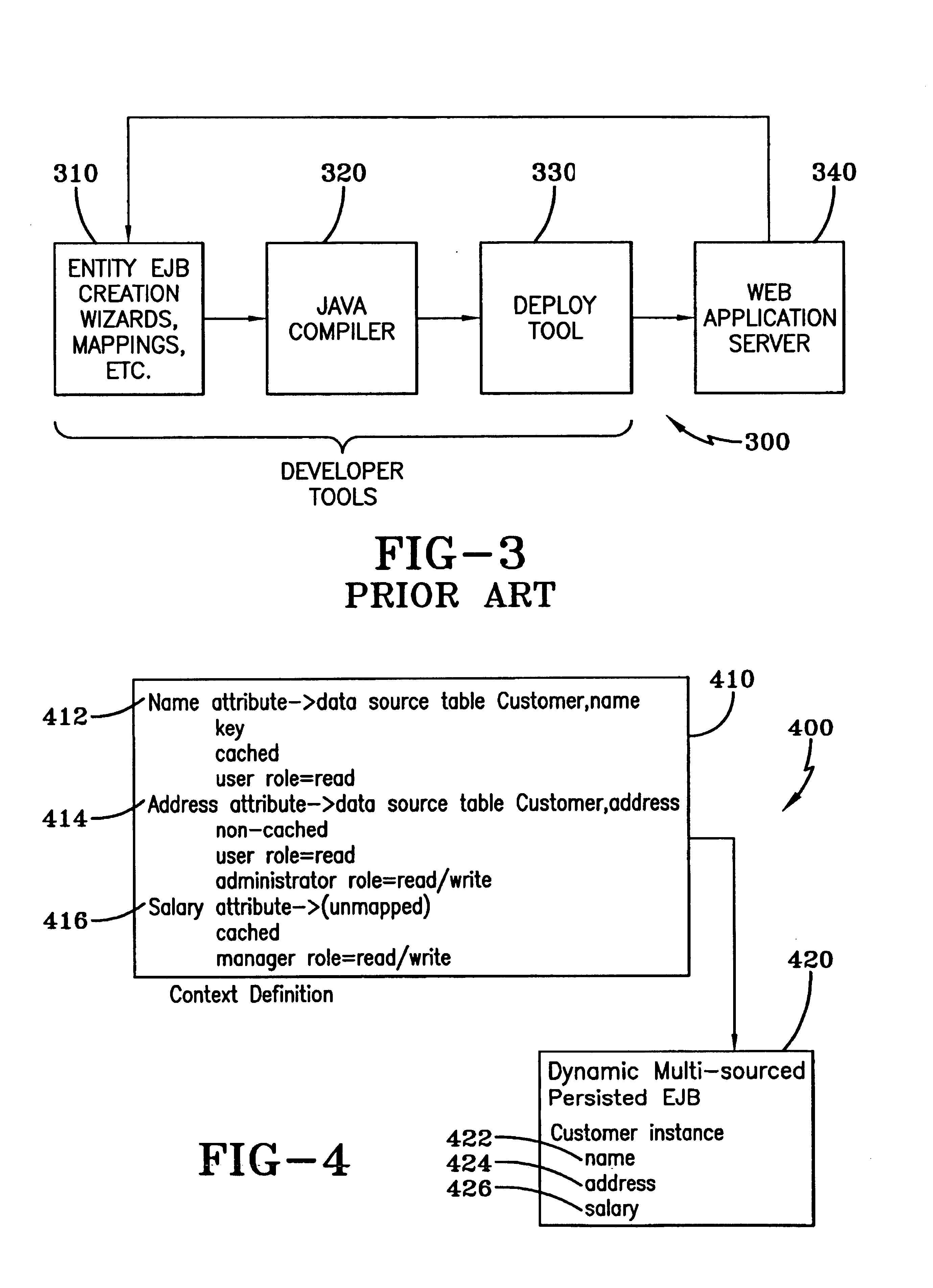
System and method for dynamically securing dynamic-multi-sourced persisted EJBS
InactiveUS6922695B2Improve securityEfficient use ofData processing applicationsDigital computer detailsApplication serverData source
Dynamic Multi-sourced Persisted Enterprise Java Bean (EJB) instances are dynamically created on a J2EE compliant Application Server to access data contained in multiple data source systems. This Dynamic Multi-sourced Persisted EJB is a general class responsible for dynamically aggregating source system information and securing it based on a Context definition. Individual EJB attributes that include mapping, caching and security definitions are mapped to individual pieces of data in source systems by the Context definition. A Context definition can be reloaded during execution as desired. Applications can access the Dynamic Multi-sourced Persisted EJB directly, or use a Session EJB to create a static interface to the dynamically mapped, cached and secured data. Using an attribute securing element, a security engine enforces access requirements on a system-wide basis.
Owner:IBM CORP
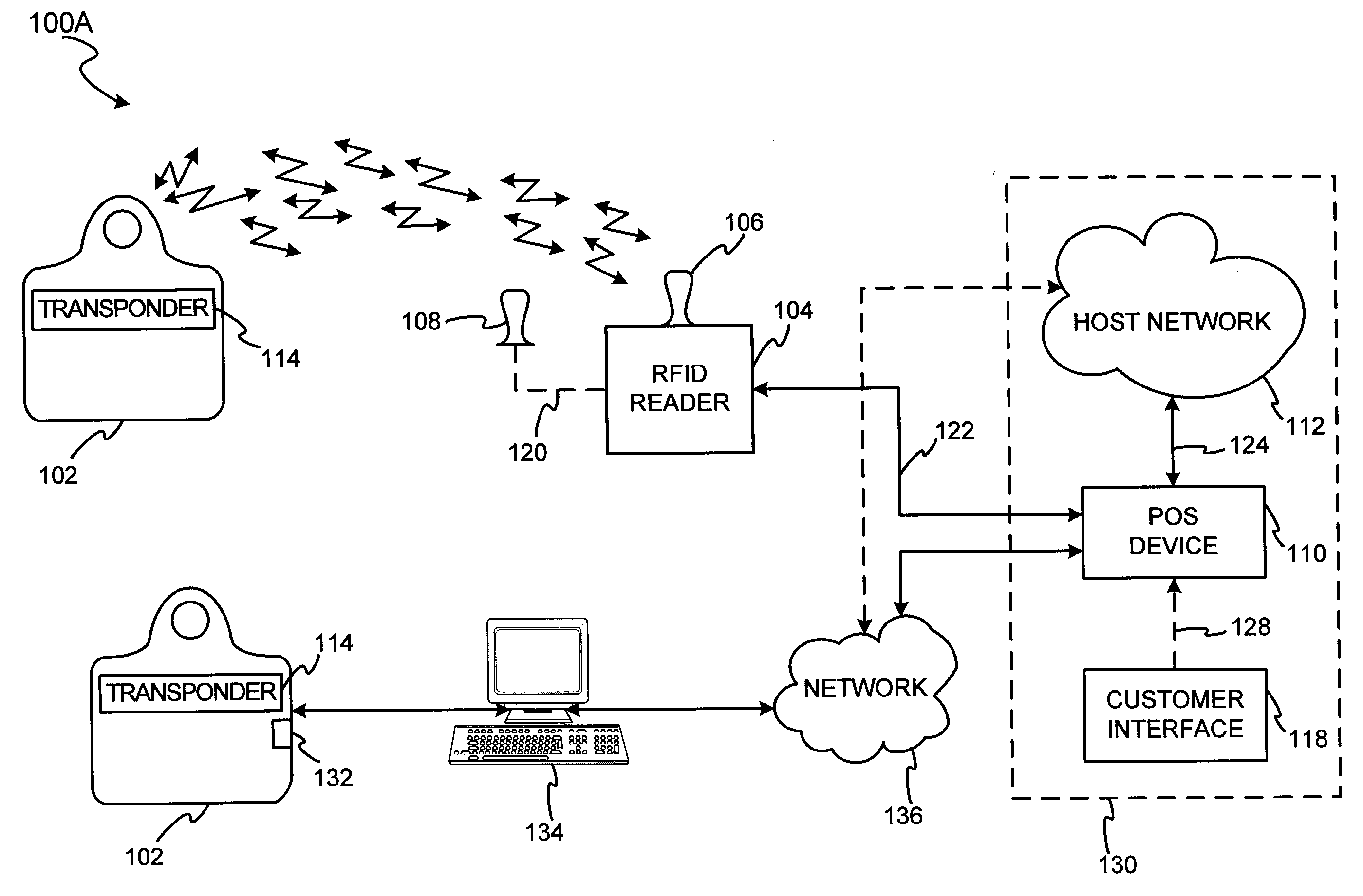
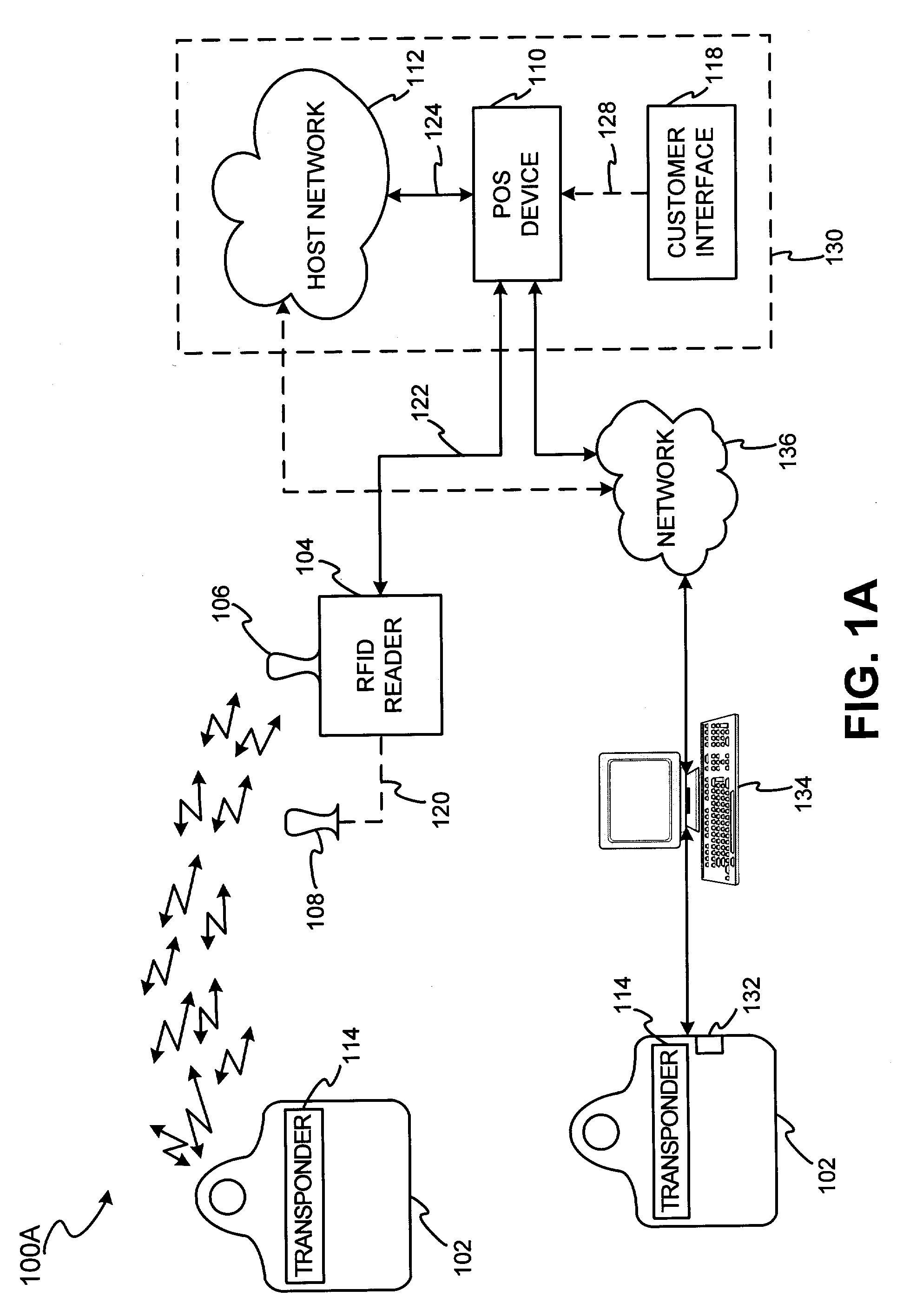
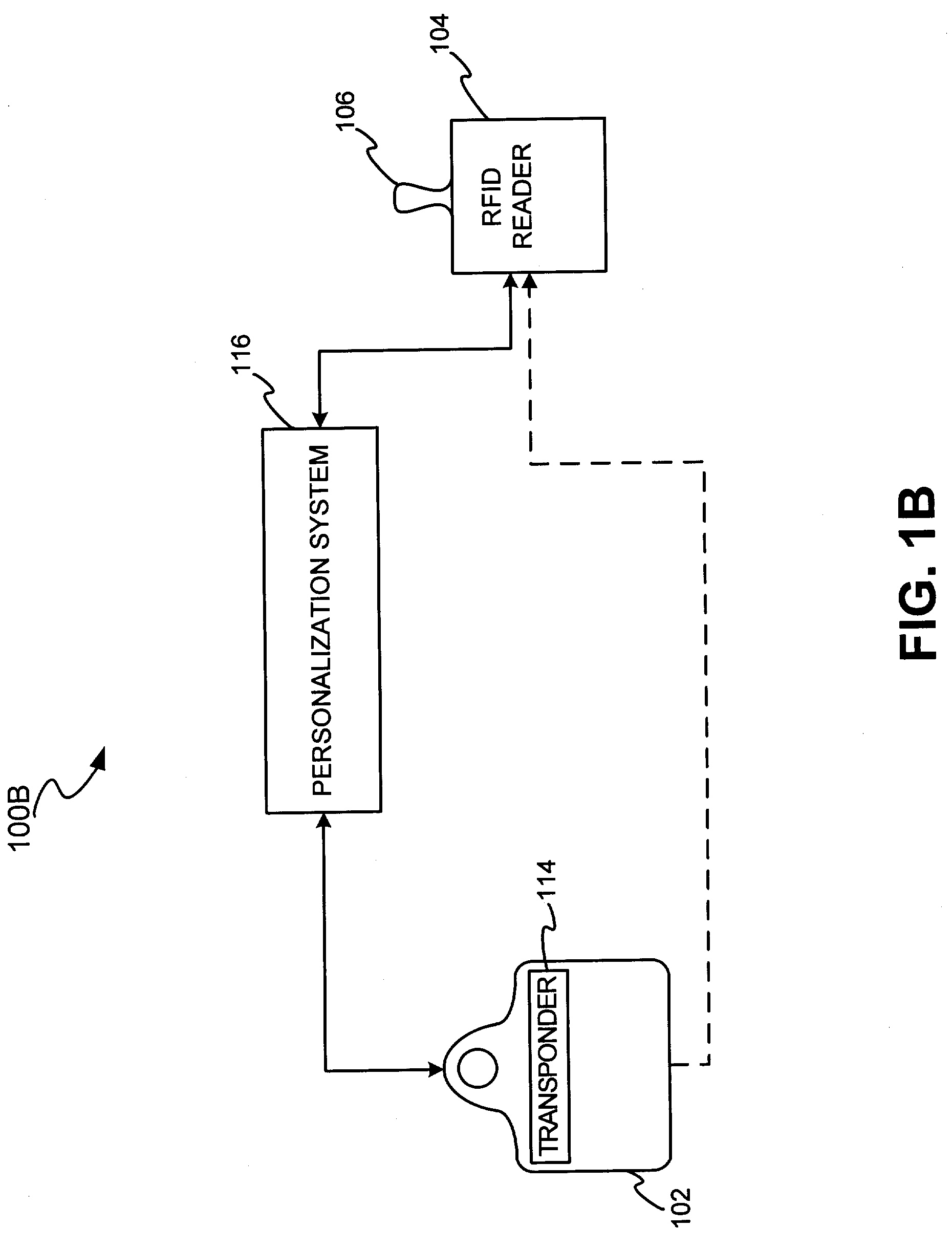
System for biometric security using a FOB
InactiveUS7303120B2Easy to completeLimited accessDigital data processing detailsComputer security arrangementsSecurity systemBiometric trait
The present invention discloses a system and methods for biometric security using biometrics in a transponder-reader system. The biometric security system also includes a biometric sensor that detects biometric samples and a device for verifying biometric samples. In one embodiment, the biometric security system includes a transponder configured with a biometric sensor. In another embodiment, the system includes a reader configured with a biometric sensor. The device for verifying samples compares the biometric samples with information stored on databases.
Owner:LIBERTY PEAK VENTURES LLC
Universal, Biometric, Self-Authenticating Identity Computer Having Multiple Communication Ports
InactiveUS20080148059A1Maintain securityLimited accessUser identity/authority verificationPayment architectureSmart cardCard reader
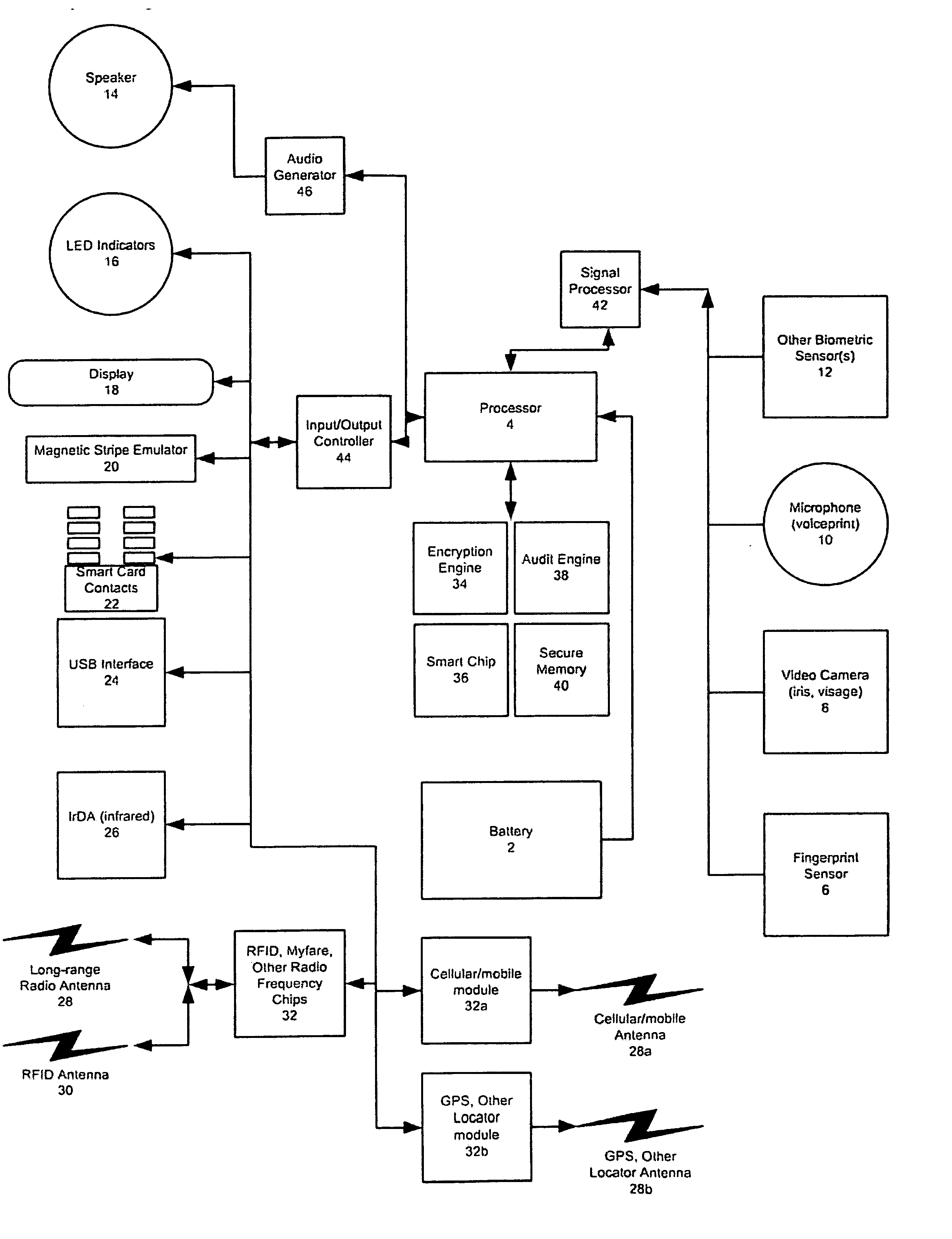
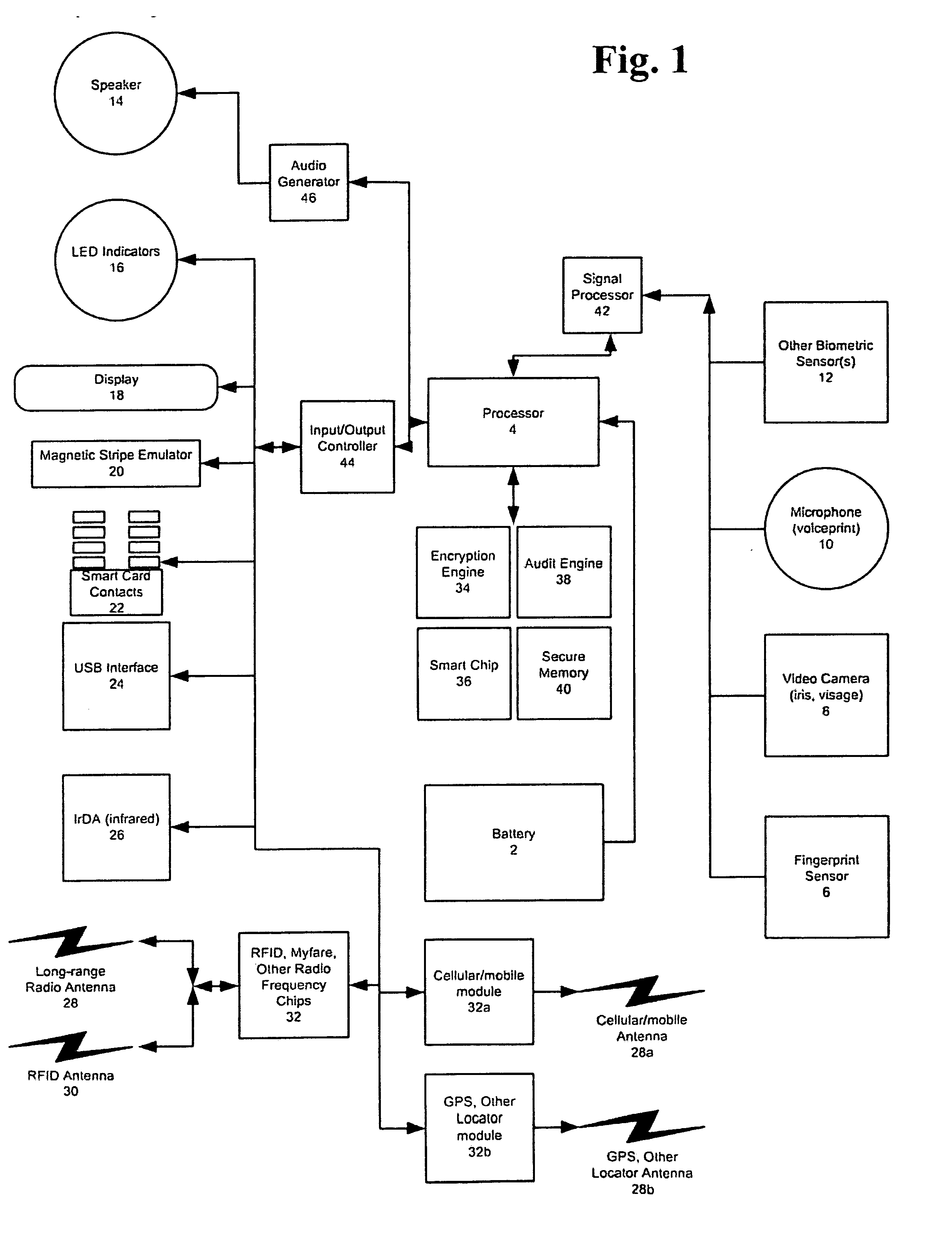
An improved device for use in authorizing transactions, supplying information and performing applications is provided by the present invention, effectively implementing a secured individual and portable Public Key Infrastructure (PKI) terminal. The device uses a local processor and secure data storage in conjunction with a variety of sensors to perform authentication processes that establish an individuals identity and provide authority to perform a desired transaction. The sensors allow the device to directly scan biometric identifying information from an individual. A card swipe interface and a proximity antenna are provided to facilitate communication between the device and remote interface devices such as magnetic swipe card readers, smart card readers, infrared communications ports and proximity and long range radio scanners. In addition, the local processor, memory, display and user inputs allow the device to run applications such as those performed by a traditional computer, gaming device, personal data assistant and smart phone.
Owner:SHAPIRO MICHAEL F
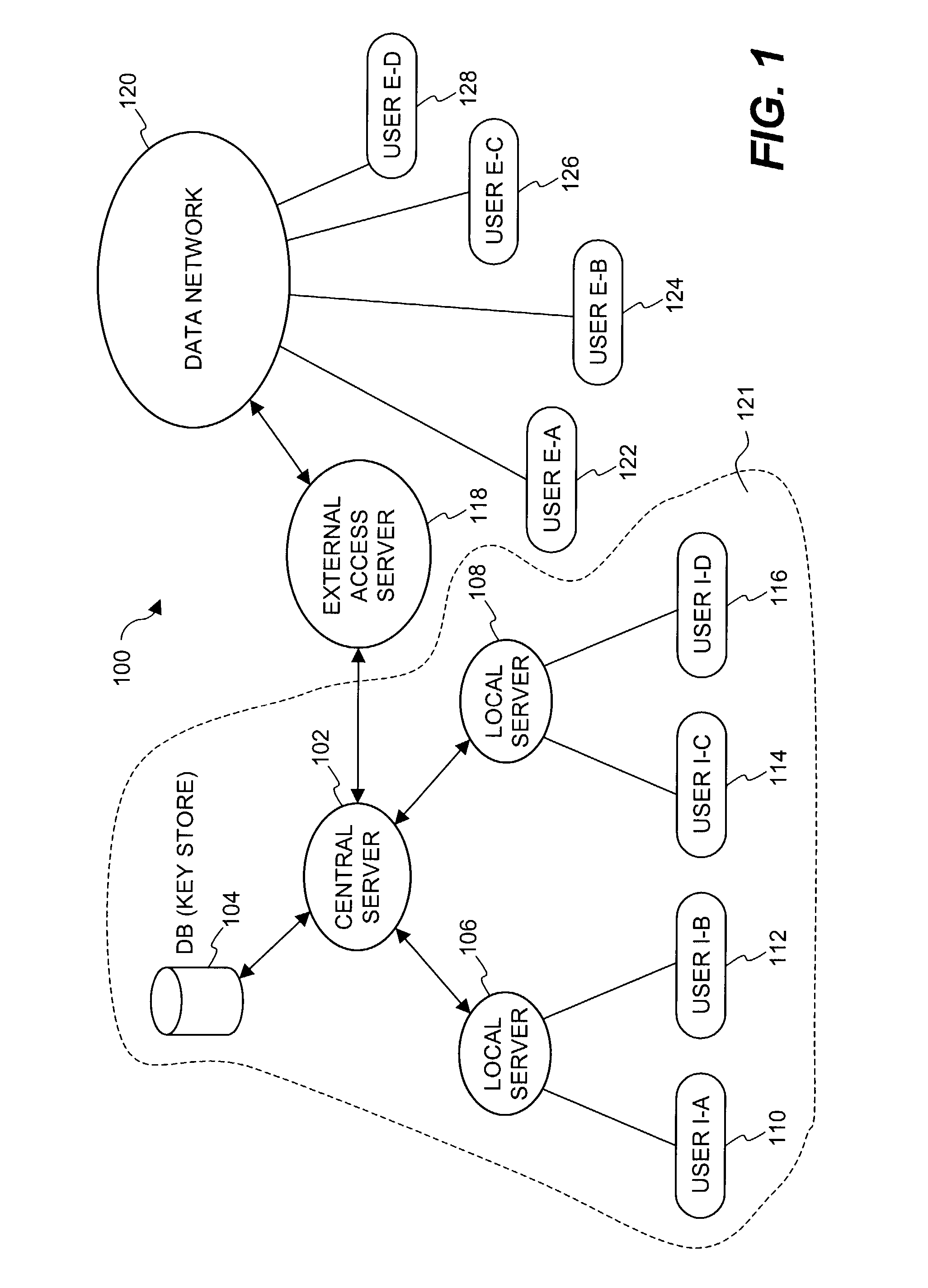
Methods and systems for providing access control to secured data
ActiveUS20090100268A1Ensures dependabilityEnsure reliabilityDigital data processing detailsUser identity/authority verificationEngineeringEncryption decryption
In a system for providing access control management to electronic data, techniques to secure the electronic data and keep the electronic data secured at all times are disclosed. According to one embodiment, a secured file or secured document includes two parts: an attachment, referred to as a header, and an encrypted document or data portion. The header includes security information that points to or includes the access rules and a file key. The access rules facilitate restrictive access to the secured document and essentially determine who / when / how / where the secured document can be accessed. The file key is used to encrypt / decrypt the encrypted data portion. Only those who have the proper access privileges are permitted to retrieve the file key to encrypt / decrypt the encrypted data portion.
Owner:INTELLECTUAL VENTURES I LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com