IP spoofing DDoS attack defense method based on active IP record
A record table, inactive technology, applied in the field of network information security, can solve problems such as increased network load, long backtracking time, and damage path backtracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
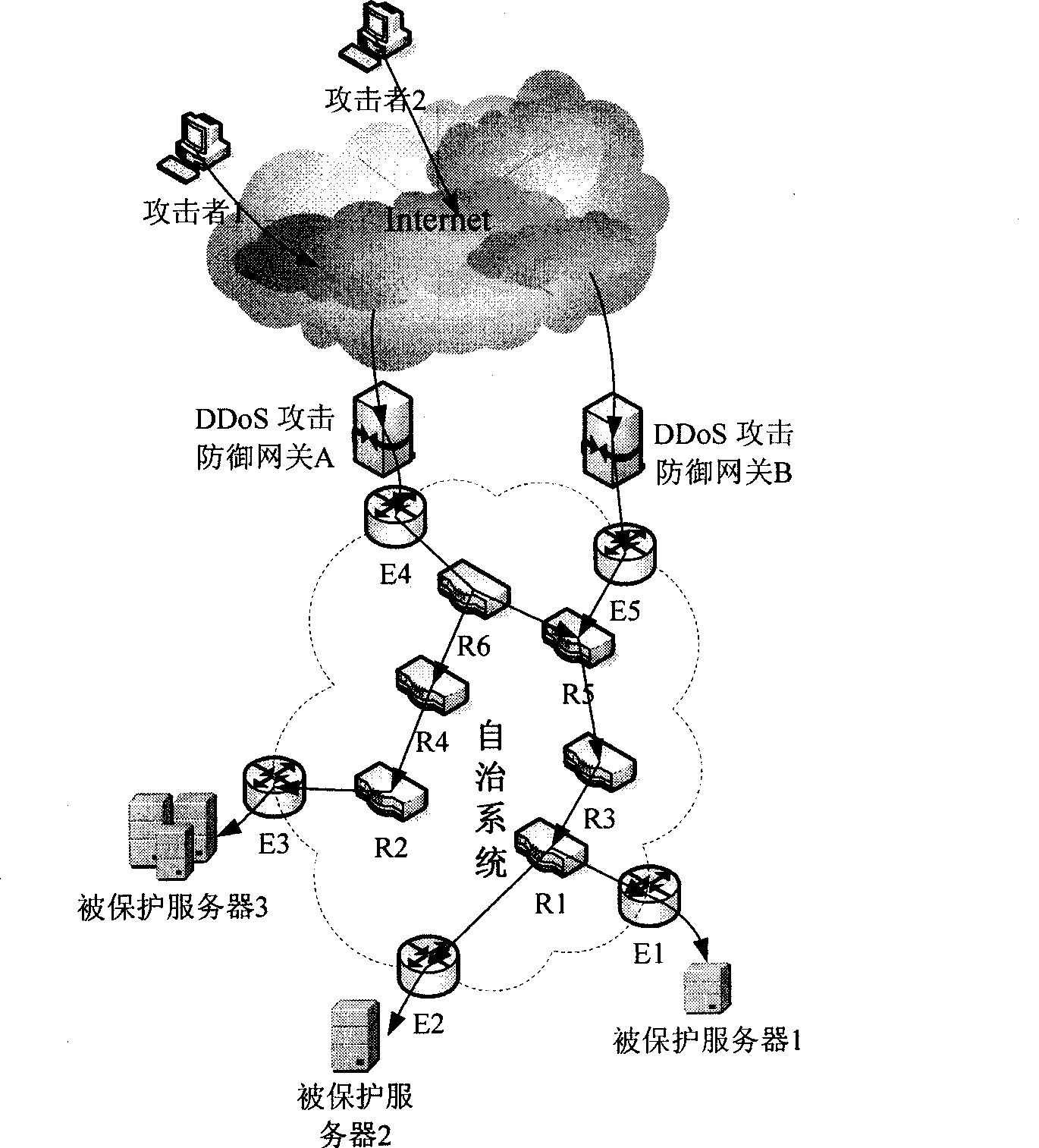
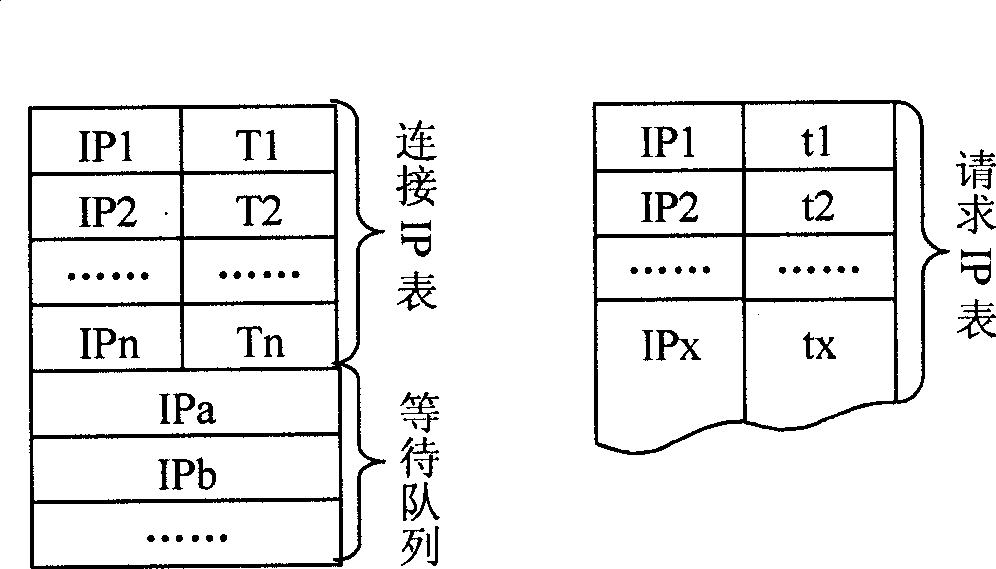
[0032] The IP spoofing DDoS defense method based on active IP records maintains an active IP table on the DDoS attack defense gateway to save active IP records. The active IP table uses the frequency of IP appearing in the source address of the data packet as the criterion for whether the IP is active. The IP that establishes a connection with the autonomous system or requests to establish a connection will be judged as an active IP and added to the active IP table, and IP spoofing is usually random IP is generated, and the frequency of occurrence is low, so it is judged as an inactive IP.
[0033] The size of the active IP table is used to set the maximum network traffic that the defense gateway can withstand, which can be manually set by the network administrator, or can be obtained by the program through self-learning based on the passing network traffic curve when there is no attack.
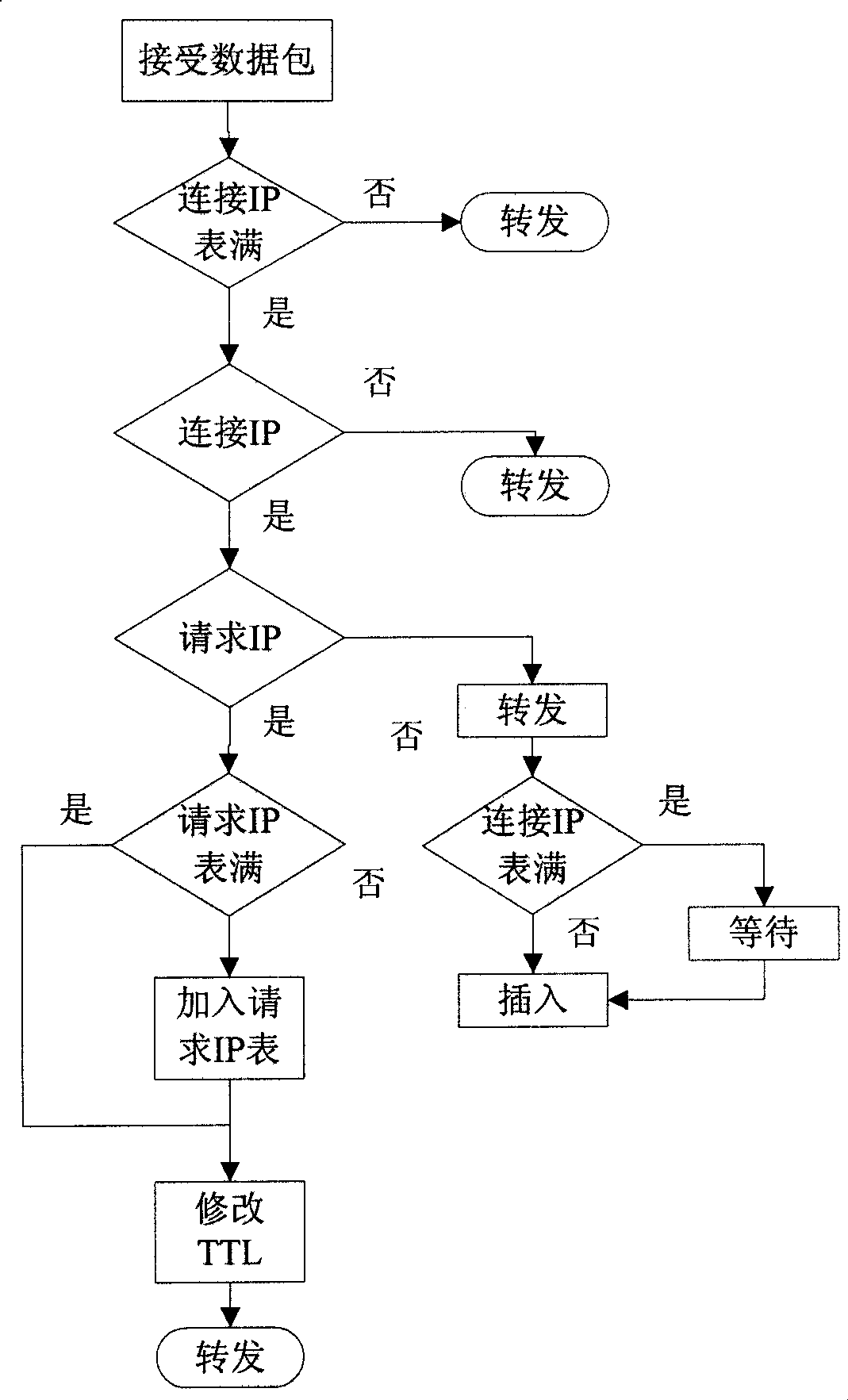
[0034] After receiving the data packet, the DDoS defense gateway uses the source IP of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com