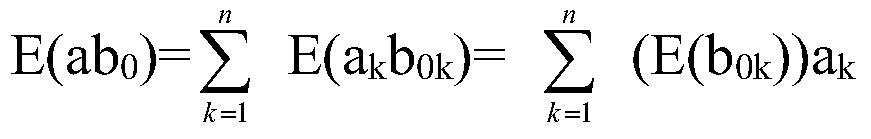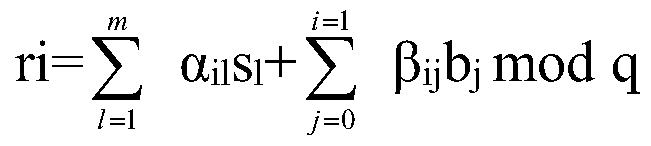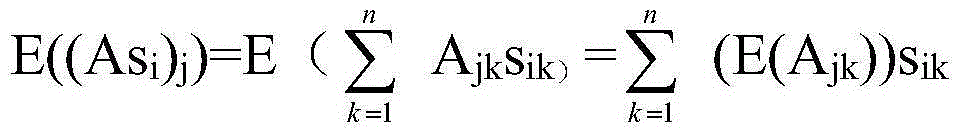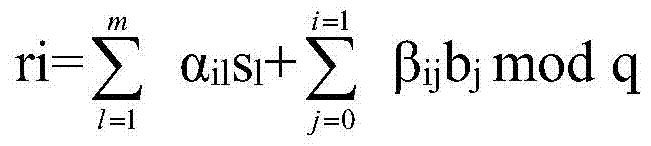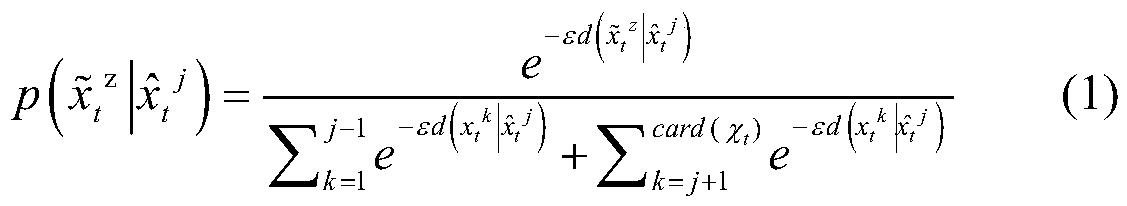Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30results about How to "Solve the problem of attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
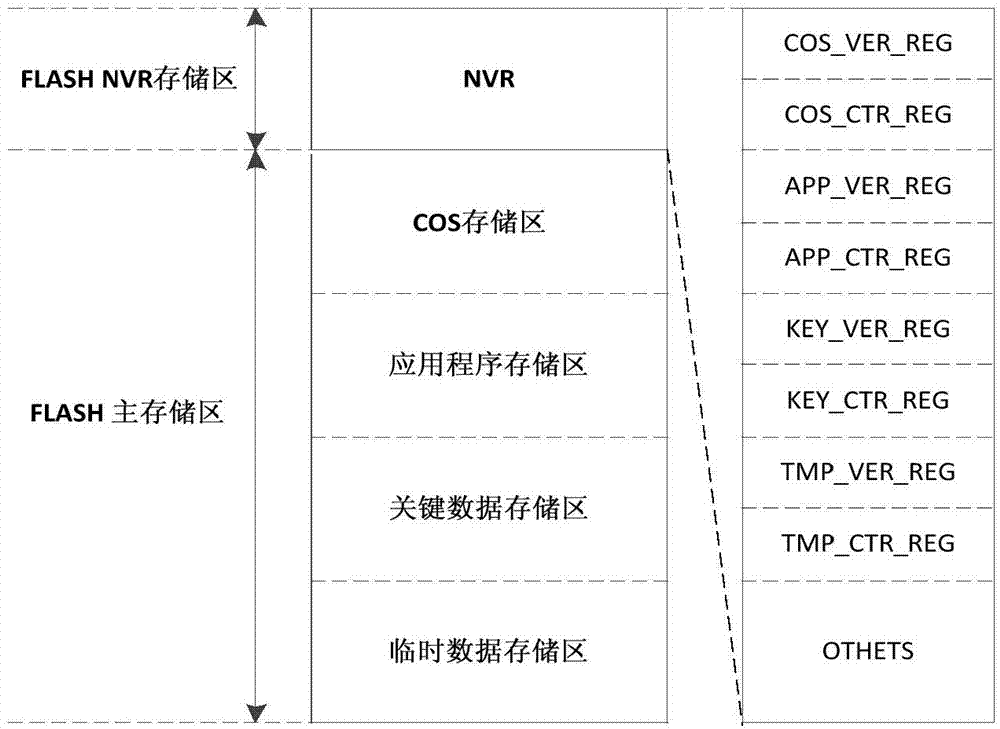
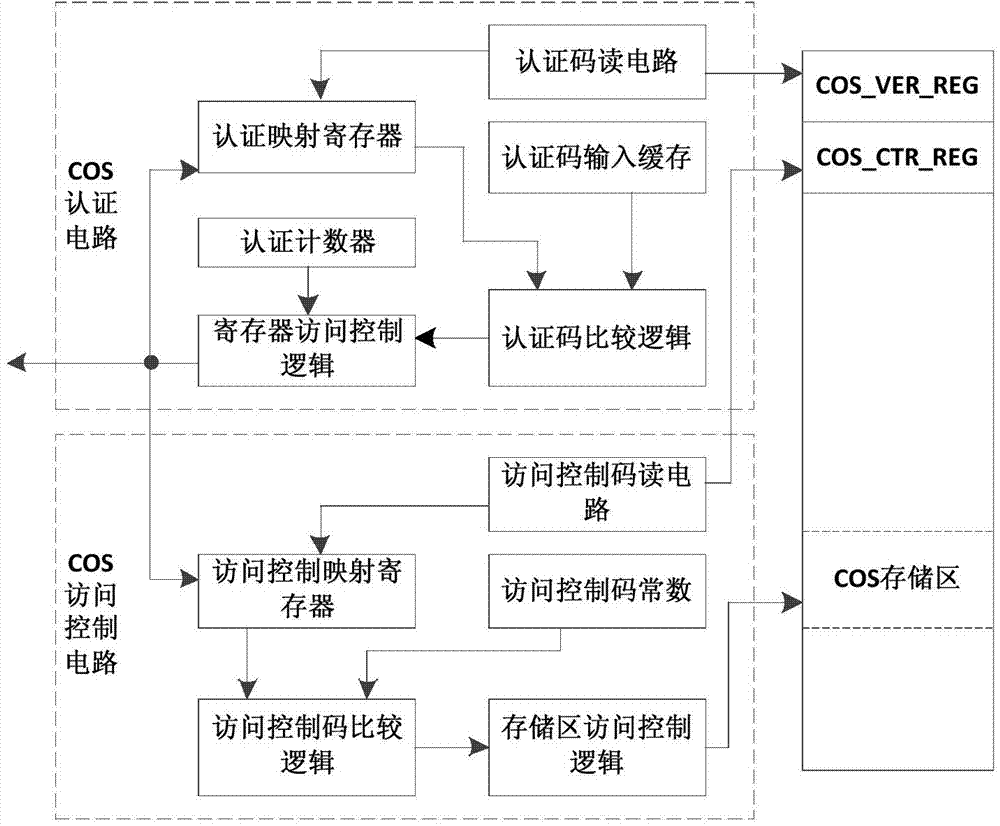
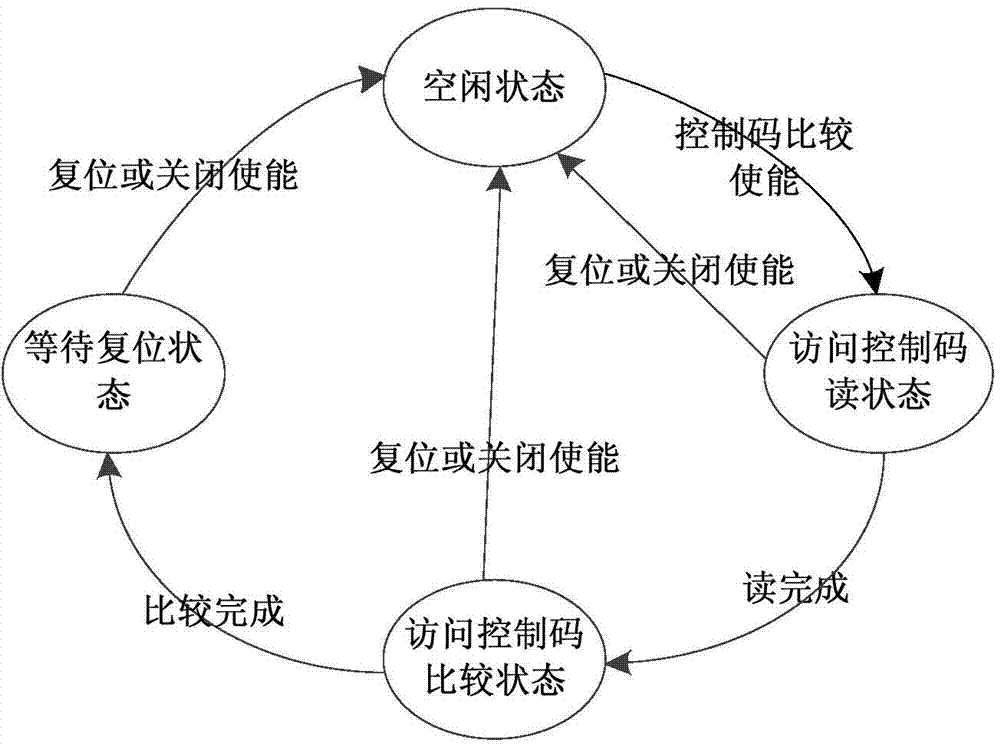
Security access control method for chip storage circuit
ActiveCN103714018ASolve the problem of attackIncrease flexibilityUnauthorized memory use protectionDigital data authenticationControl signalMedia access control
The invention discloses a security access control method for a chip storage circuit. Based on a nonvolatile storage circuit, subarea access control is conducted, an authentication and access control circuit is designed for each subarea, the authentication and access control circuits all skip in a mode of a state machine, authentication and access control signals under different states are output, and authorized access of the storage circuit is achieved. Two levels of authentication of identity authentication and access control authentication are adopted and finished by pure hardware circuits, and higher safety is achieved. The method is applicable to application specification integrated circuit (ASIC) chips and SoC chips of an integrated nonvolatile storage, even other circuit systems with the nonvolatile storage.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
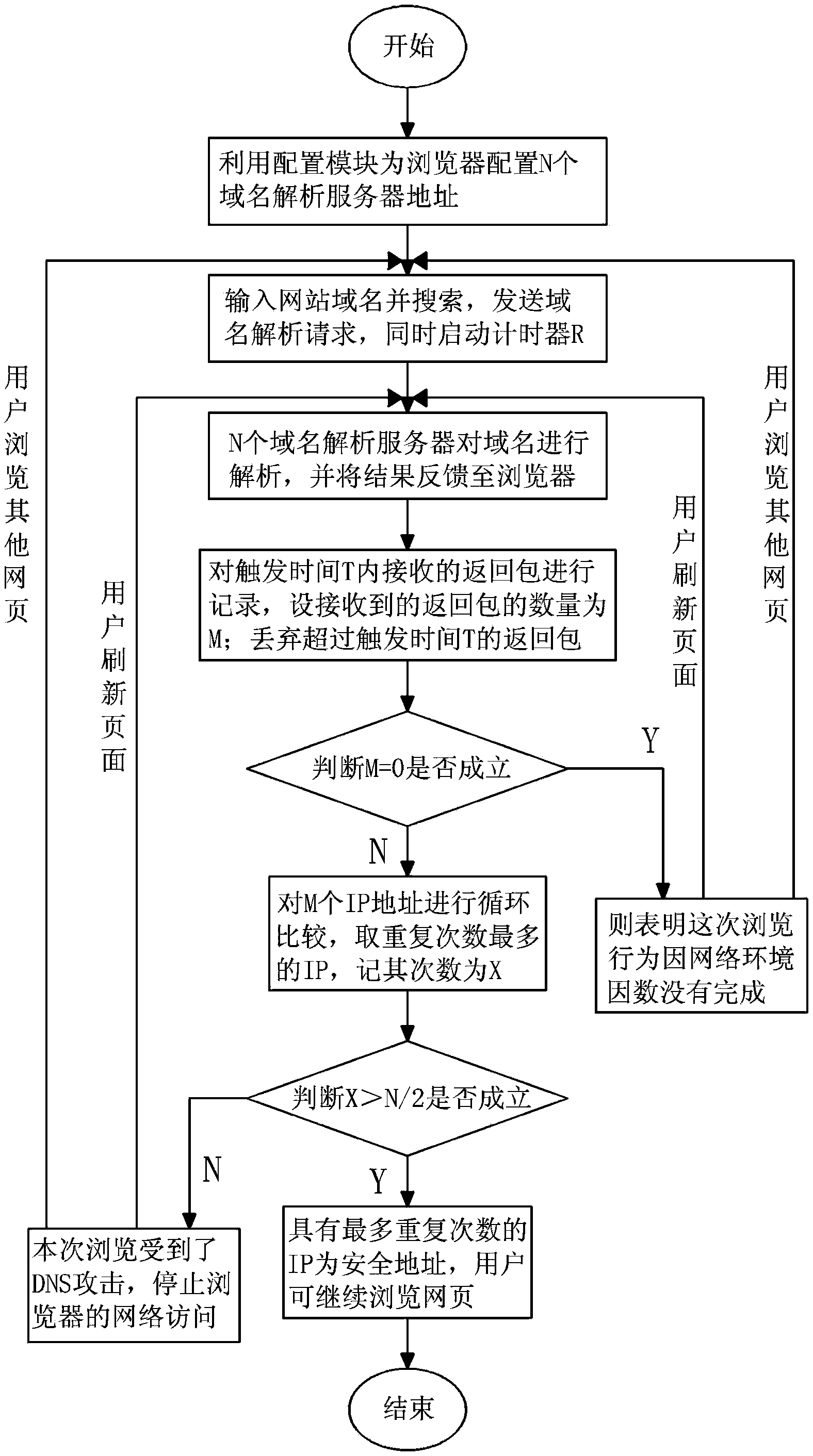
Safe DNS (Domain Name Resolution) method in internet browser
The invention discloses a safe DNS (Domain Name Resolution) method in an internet browser. The method comprises the steps: 1) preparing N DNS servers; b) transmitting a resolution request; c) performing domain name resolution; d) recording a received return packet, and recording the quantity to be M; e) judging whether the formula M=0 is established, indicating that a browsing behavior is not completed if the formula is established; indicating that there is the return packet if the formula is not established; f) when a user is used for refreshing, executing the step c); if other web pages are changed to browse, executing the step b); g) taking an IP (Internet Protocol) with most repeating times, and taking the times as X at the same time; and h) judging whether the formula that X is more than N / 2 is established, if the formula is established, indicating the IP to be a safe address; if the formula is not established, indicating this browsing to be attacked by the DNS. According to the DNS method in the internet browser provided by the invention, the domain name input by the user can be guaranteed to point to a corresponding web site or a service, therefore, the attacking problem in the DNS process can be solved; furthermore, the forged IP address can be filtrated to retain a correct IP address.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
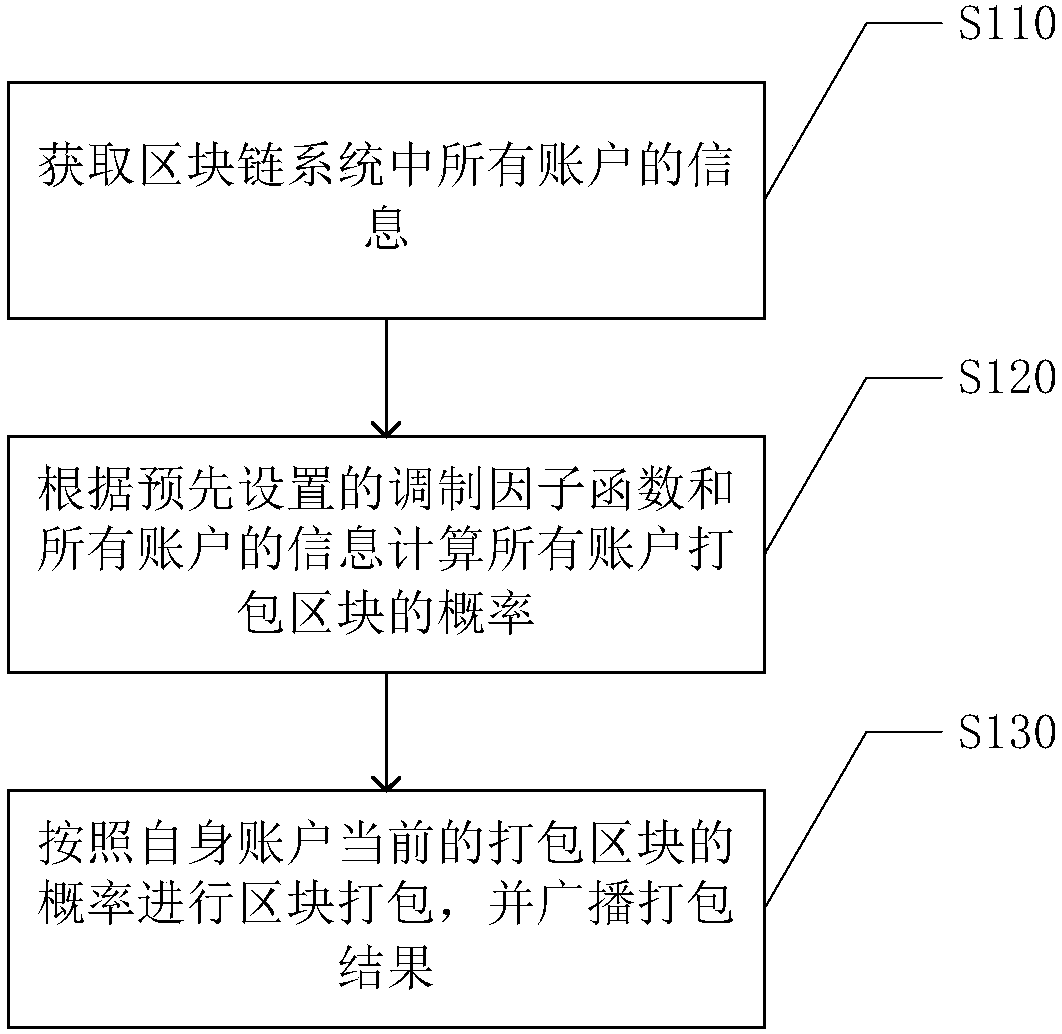
Method for preventing 51% attack, block chain system and computer readable storage medium
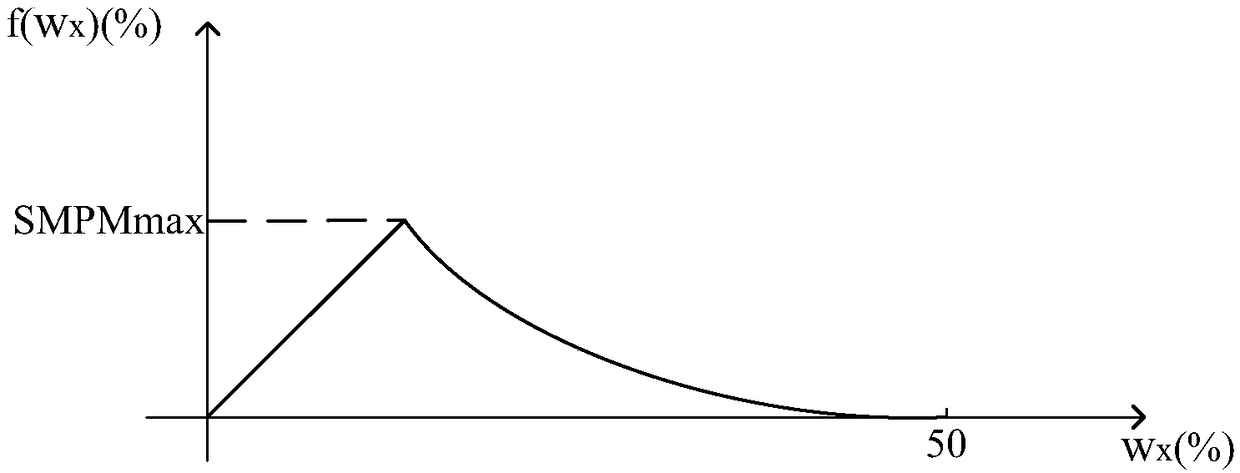
ActiveCN108537550AImprove efficiencySolve the problem of attackPayment protocolsModulation factorChain system
The invention discloses a method for effectively preventing 51% attack in a real-name block chain PoS mechanism, a block chain system and a computer readable storage medium. According to the method, the packaging difficulty of accounts is adjusted through a preset modulation factor function and the cash weight of the accounts, wherein the modulation factor function is used for describing the relationship between the cash weight of the accounts and the modulation factors of the probability of an account packaging block, and the modulation factor function is configured to enable the modulation factor of the probability when the cash weight of the accounts is Default to be maximum, and Default is greater than 0 and smaller than 50%. The block chain system solves the problem of 51% attack, andthe efficiency of the block chain system is improved.
Owner:丁江
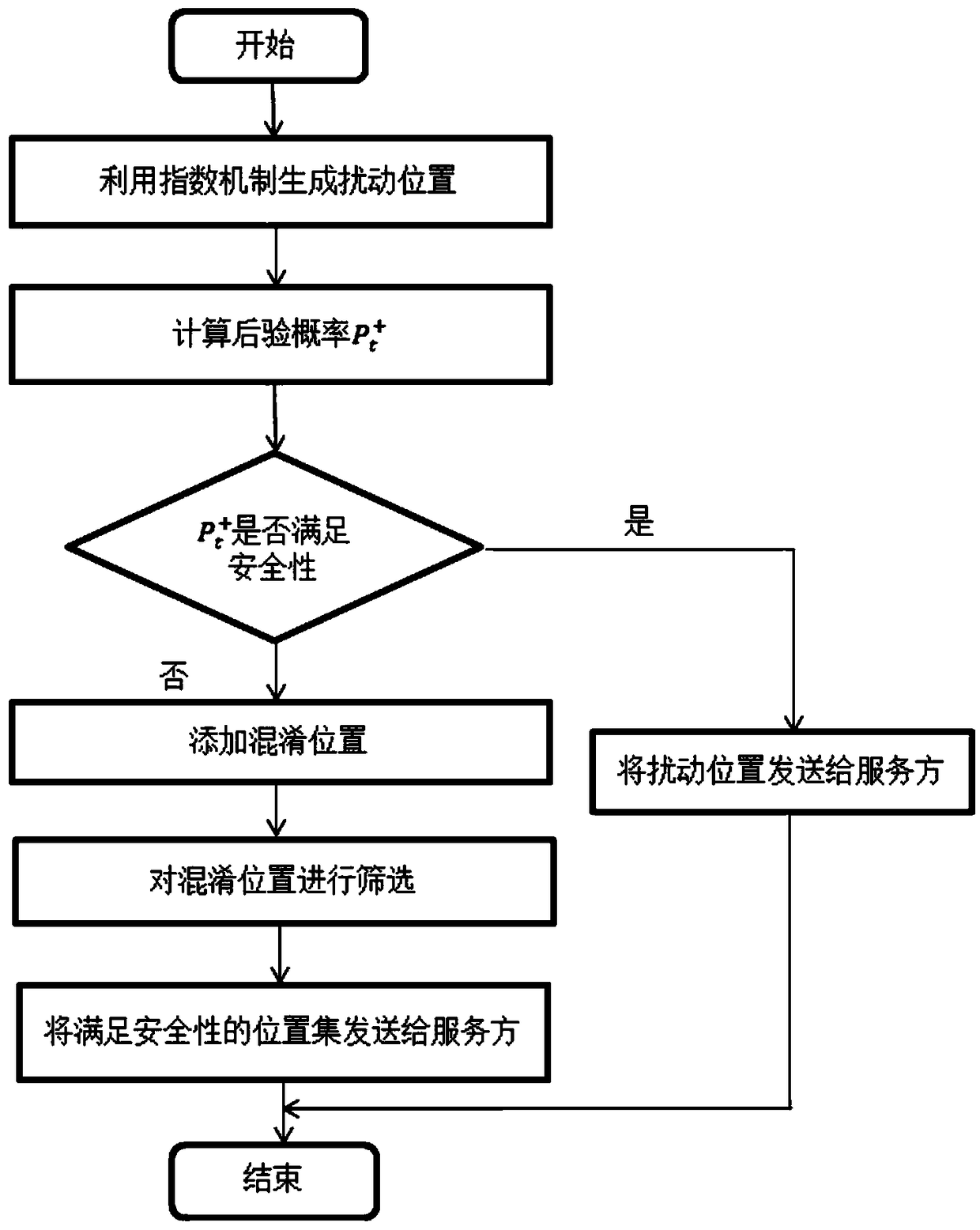
User location personalized differential privacy protection method for location-based service
ActiveCN109362032AReduce the risk of privacy breachesSolve the problem of attackLocation information based serviceSecurity arrangementPersonalizationDifferential privacy
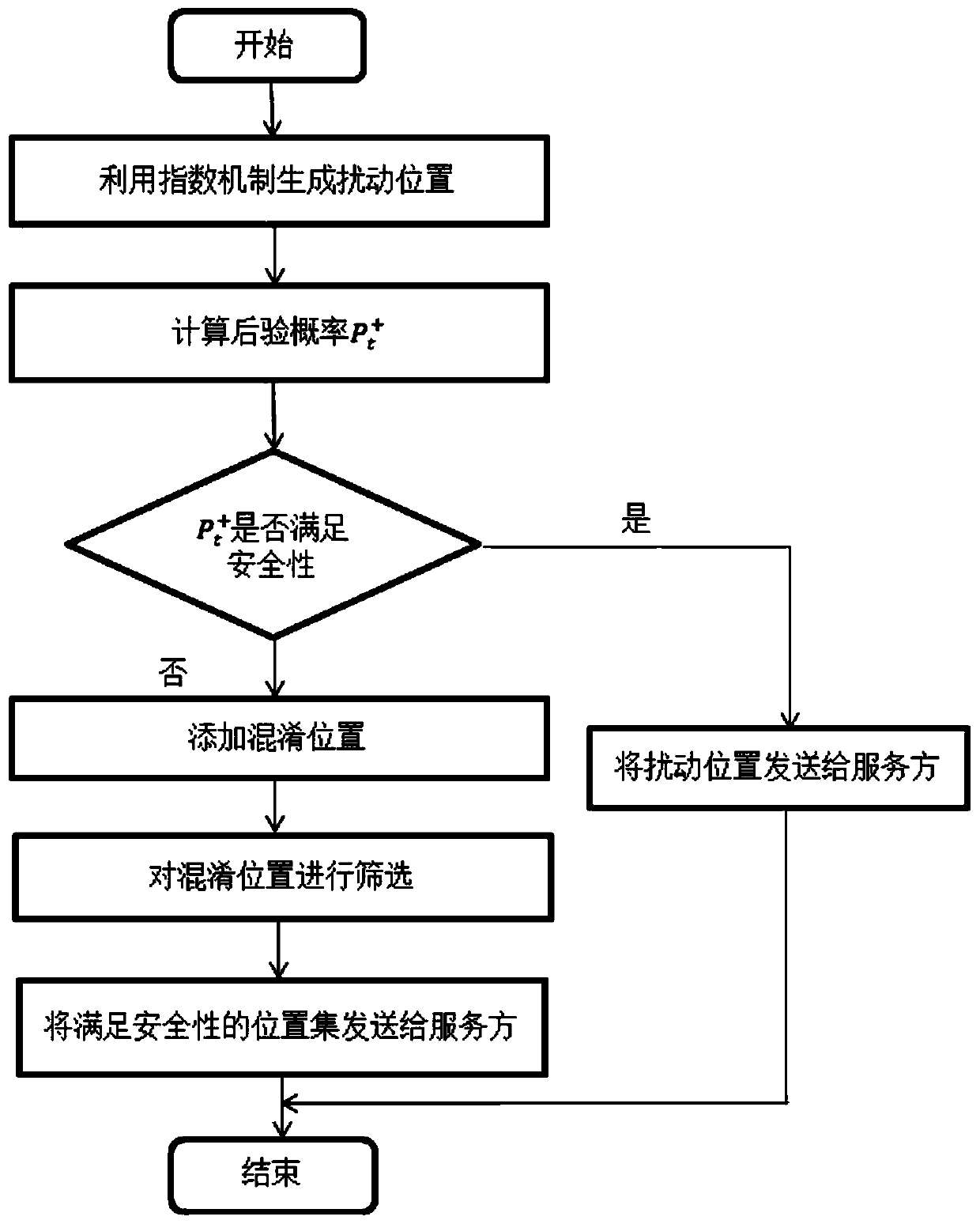
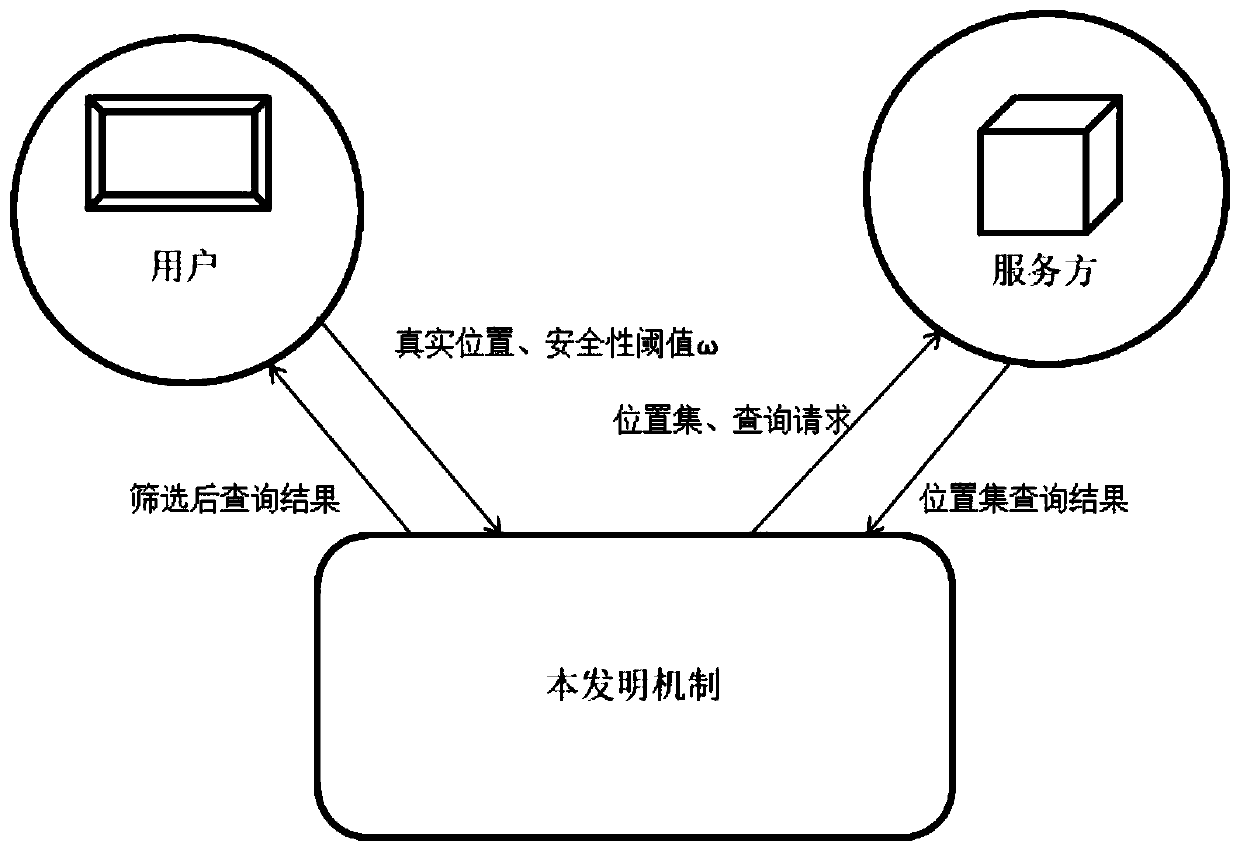
The invention discloses a user location personalized differential privacy protection method for location-based service. The method comprises the steps of 1, generating a disturbance location through utilization of an index mechanism; 2, obtaining a posterior probability of an opponent for a location of a user at time t according to a prior probability of the opponent for the location of the user at time t, index mechanism probability distribution and the generated disturbance location; 3, judging whether the posterior probability of the opponent for the location of the user at time t satisfiesa security requirement or not, sending the disturbance location and a query request to a service provider if the posterior probability of the opponent for the location of the user at time t satisfiesthe security requirement, and adding a confusion location if the posterior probability of the opponent for the location of the user at time t does not satisfy the security requirement; 4, adding theconfusion location, and sending a location set composed of the confusion location and the disturbance location to the service provider after the security requirement is satisfied; and 5, screening query results returned by the service provider. According to the method, the problem that user location privacy is leaked due to unreliability of the service provider can be solved, and moreover, a Bayesian attack can be effectively coped with, so security of the user location privacy in the location-based service can be improved.
Owner:ANHUI UNIVERSITY
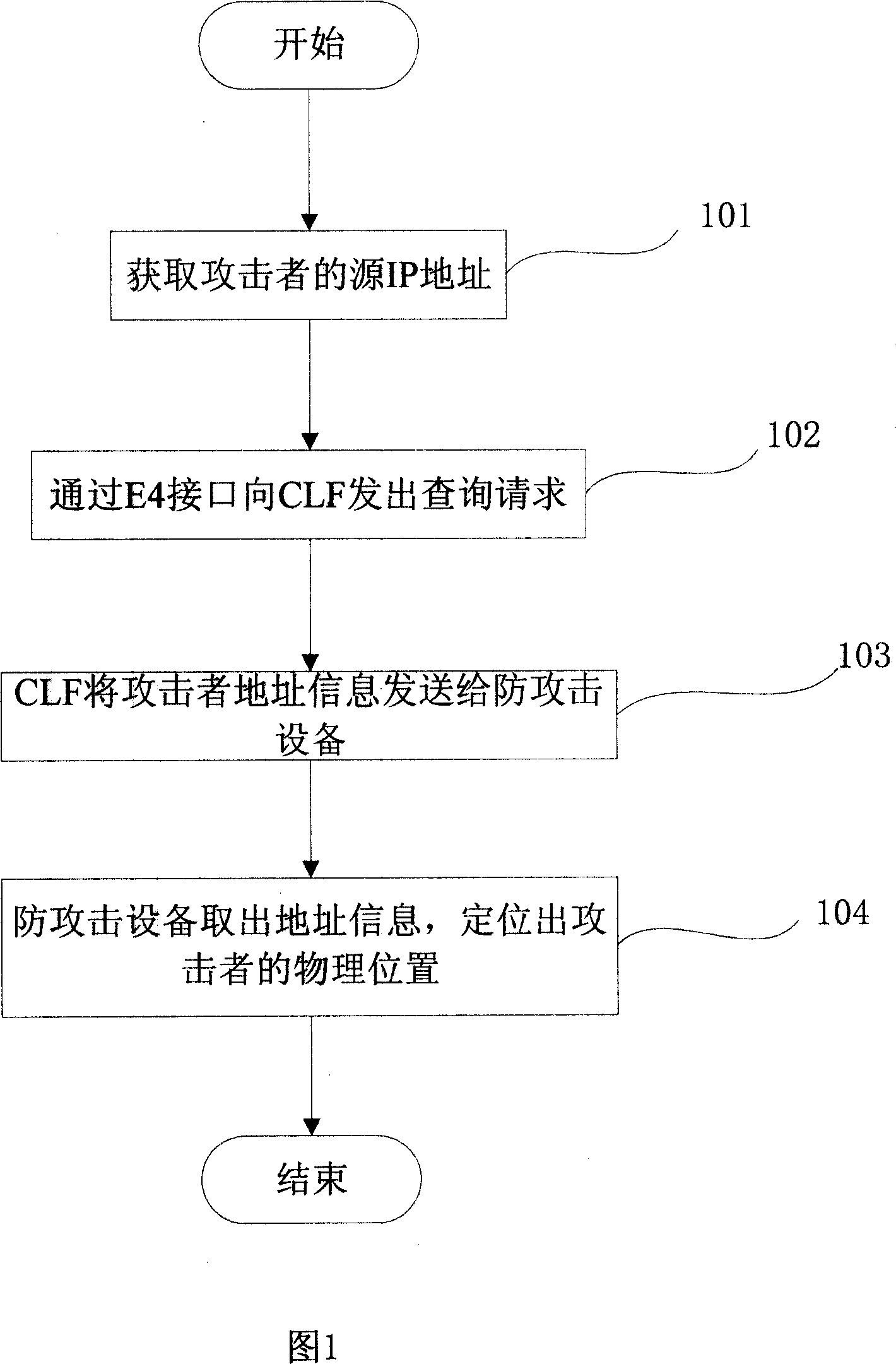
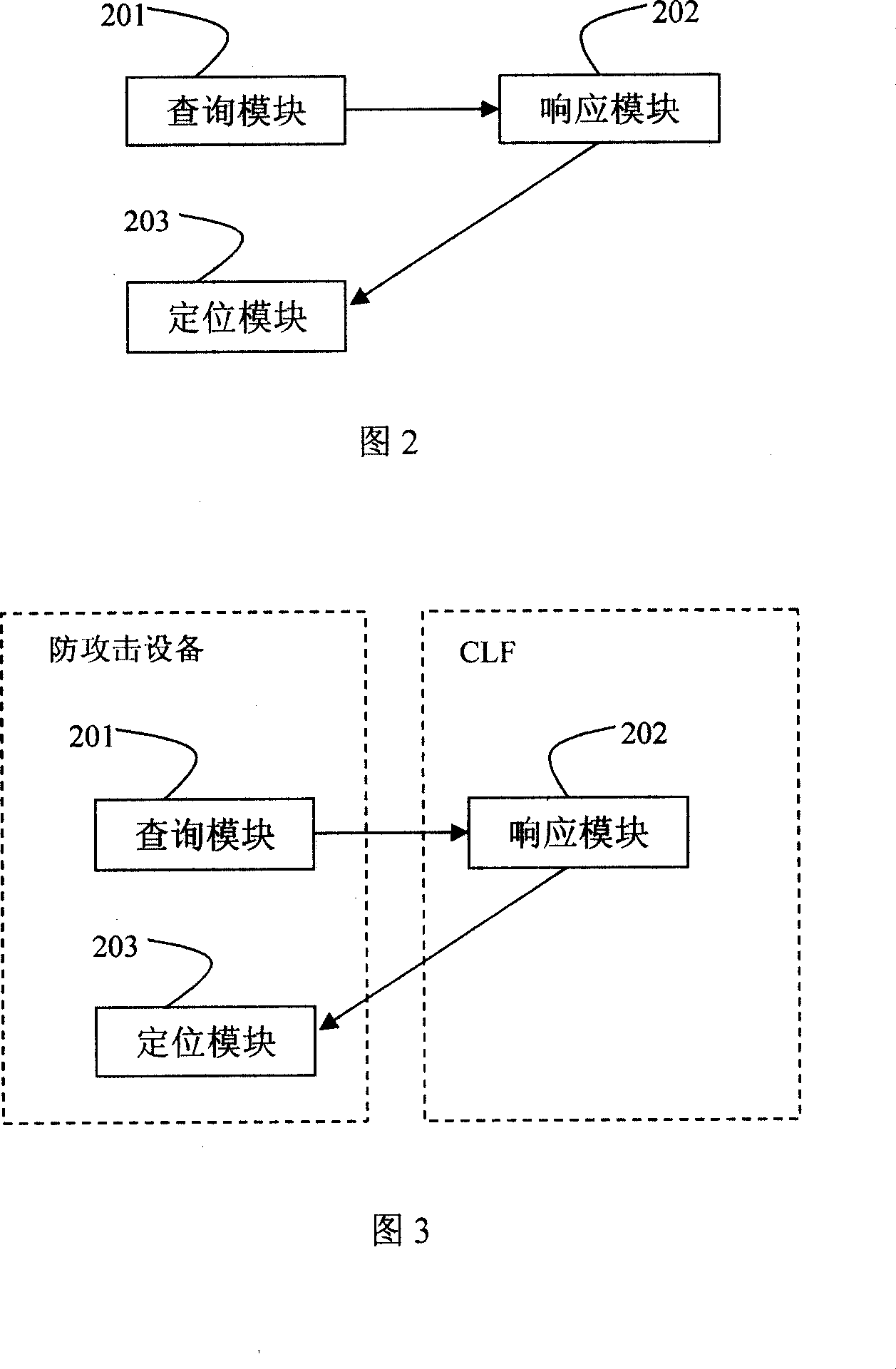
Method for locating the attack source of multimedia subsystem network, system and anti-attack system
InactiveCN101014047ASolve the problem of attackAchieve positioningRadio/inductive link selection arrangementsSecuring communicationIp addressNetwork attack
The invention provides one method, device and anti-attack system of one position IMS network attack source, which comprises the following steps: the anti-attack device tests attacks and sends require to CLF with require content composed of attacker source IP address information, CLF attacker source IP address information and sends the response information to the attack device; anti-attack device gets address information and positions attacker physical position.
Owner:HUAWEI TECH CO LTD
Unified identity authentication platform based on zero trust and confidential calculation
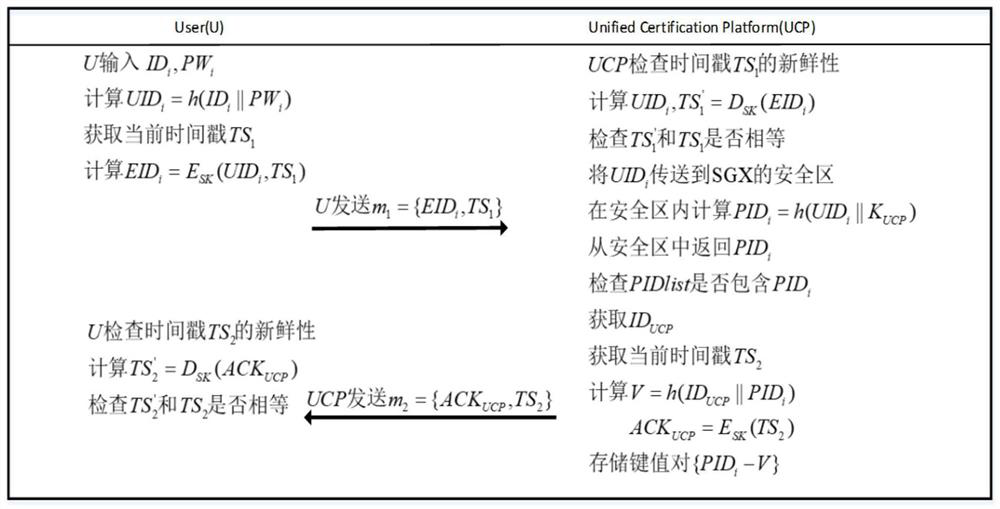
ActiveCN113849815ASolve the problem of attackGuaranteed legalityDigital data authenticationPlatform integrity maintainanceInternet privacyConfidentiality
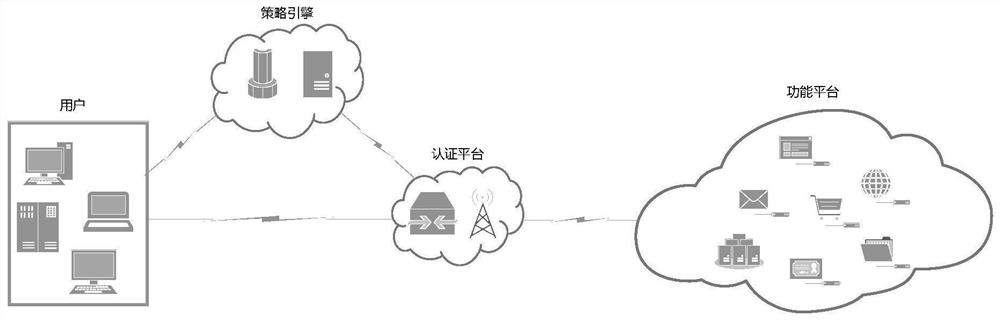
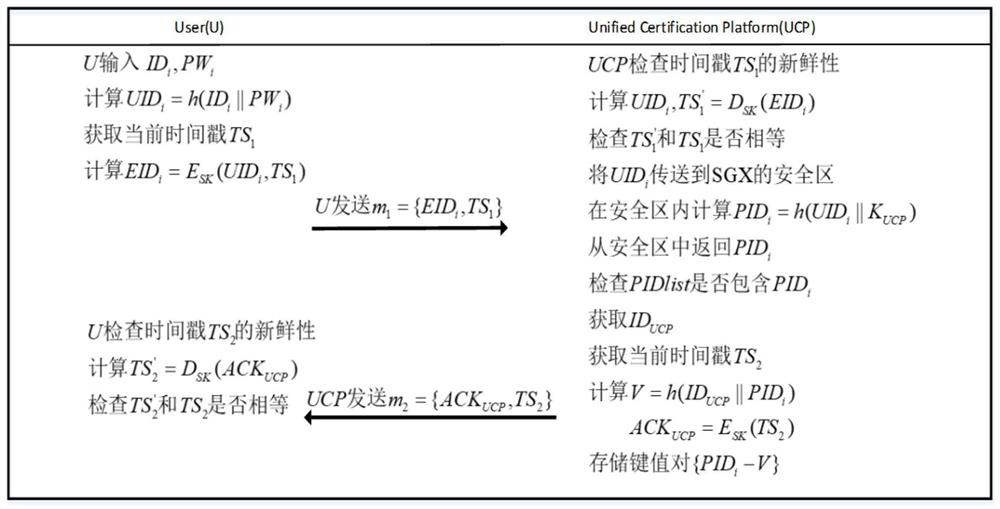
The invention relates to a unified identity authentication platform based on zero trust and confidential calculation, which comprises four stages, namely a communication establishment stage, a user registration stage, a function platform registration stage and a login and key negotiation stage, wherein the communication establishment stage is used for negotiating a symmetric key SK and establishing reliable communication between a user and a unified identity authentication platform; in the user registration stage and the function platform registration stage, a registration function verified by a unified identity authentication platform and a confidential calculation safety area and a function of constructing an anonymous authentication relation table are realized, and a legal user and a legal function platform are obtained; in the login and key negotiation stage, a function of negotiating a symmetric session key between a legal user and a legal function platform is realized, and the symmetric session key is used for encrypting subsequently transmitted privacy data. The method has the beneficial effects that the integrity and confidentiality of data in a running state are ensured; the low overhead and low time delay of the authentication process are ensured, and quick authentication is realized.
Owner:LANZHOU UNIVERSITY
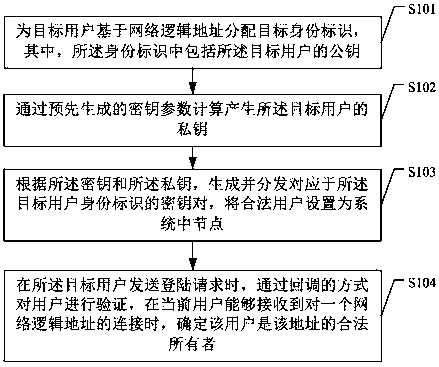
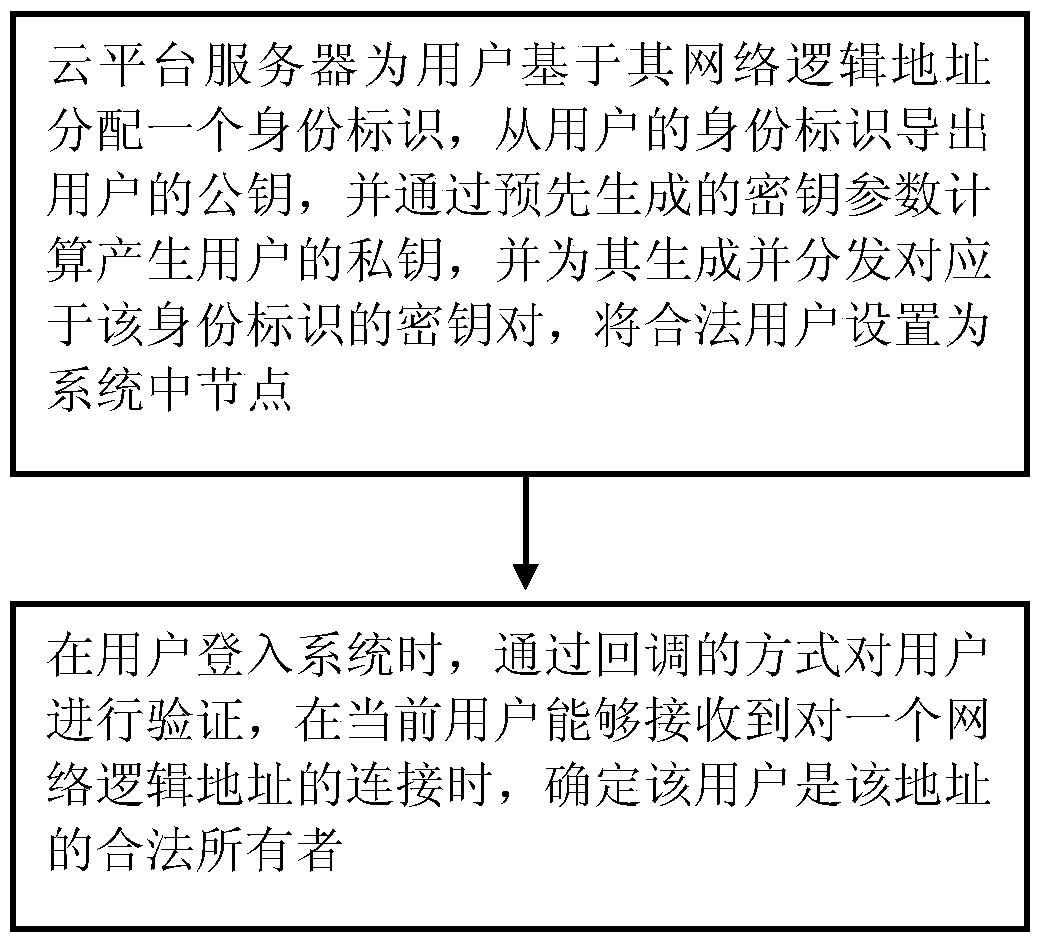
Big data storage method
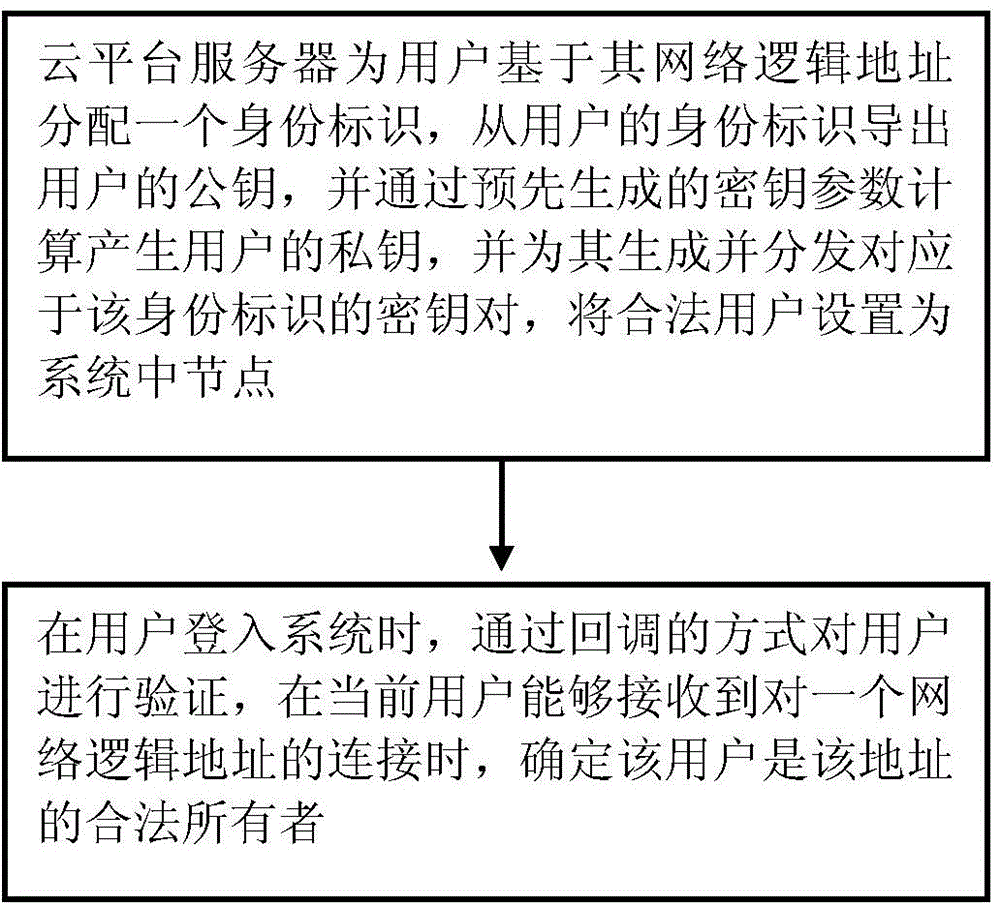
ActiveCN104935582ASecuritySolve the problem of attackPublic key for secure communicationComputer securitySpeaker verification
The invention provides a big data storage method. The method includes: a cloud server distributes an identification for a user based on a network logic address of the user, exports a public key of the user from the identification of the user, calculates and generates a private key of the user via a pre-generated secret key parameter, generates and distributes a key pair corresponding to the identification for the private key, and sets the legal user as the system middle node; during the login of the user, user verification is realized via the manner of callback, and when the current user can receive a connection of the network logic address, the user is determined to be the legal owner of the address. According to the method, the problem that illegal users carry out attacks via the network logic addresses can be effectively solved, the system security is guaranteed, and the method is applicable to cloud storage systems.
Owner:成都华西公用医疗信息服务有限公司
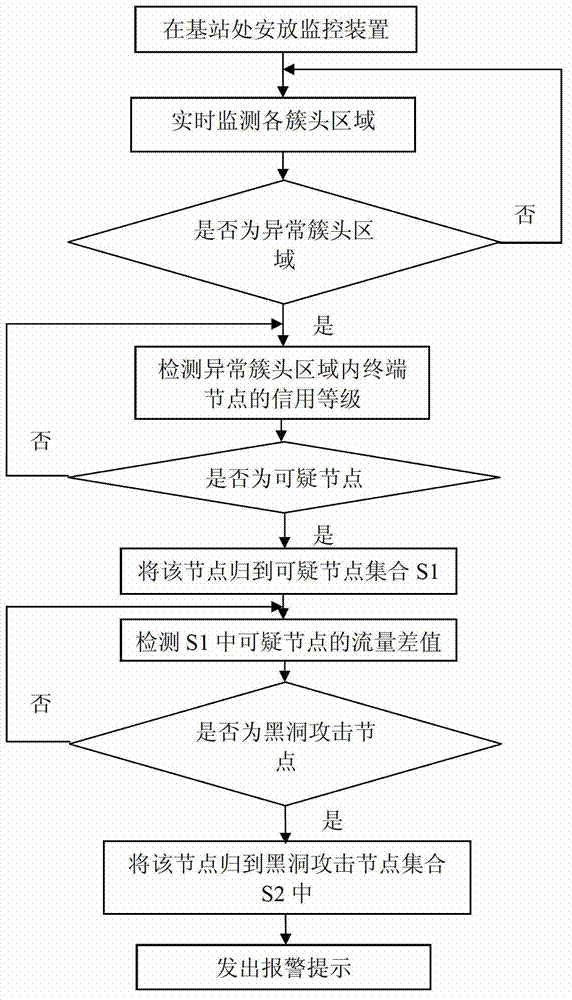
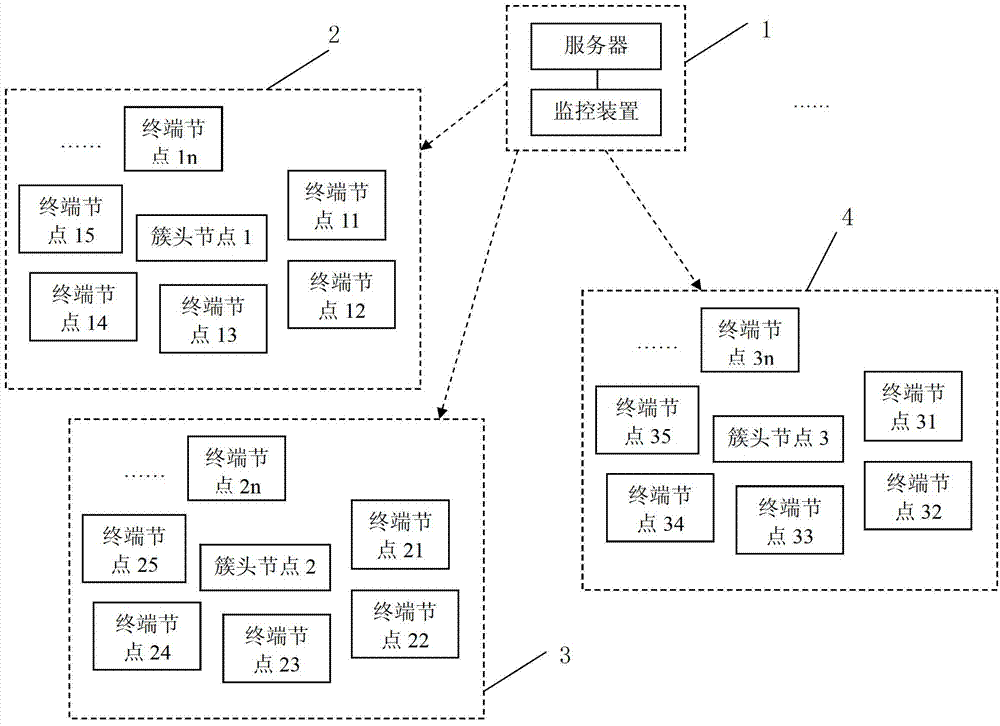
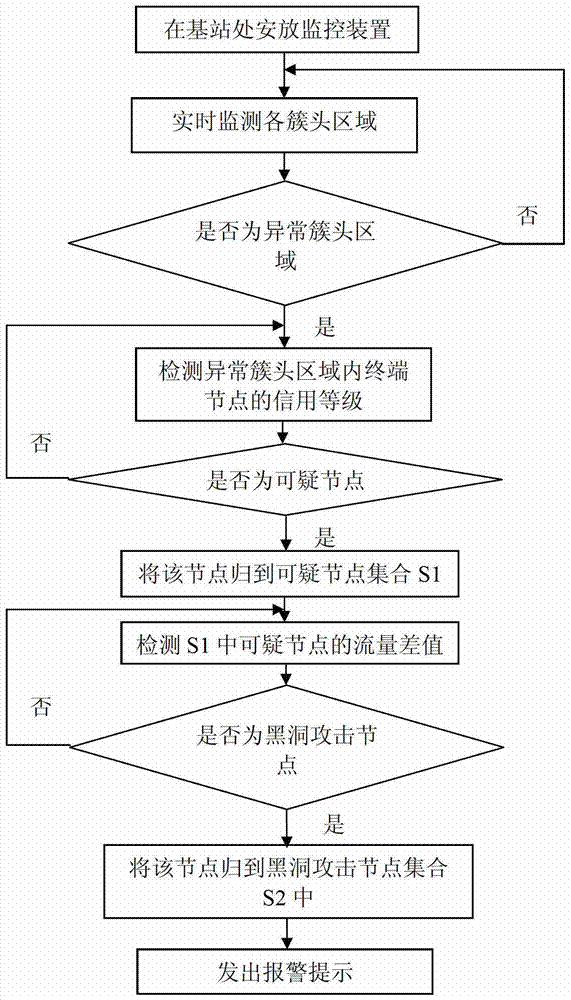
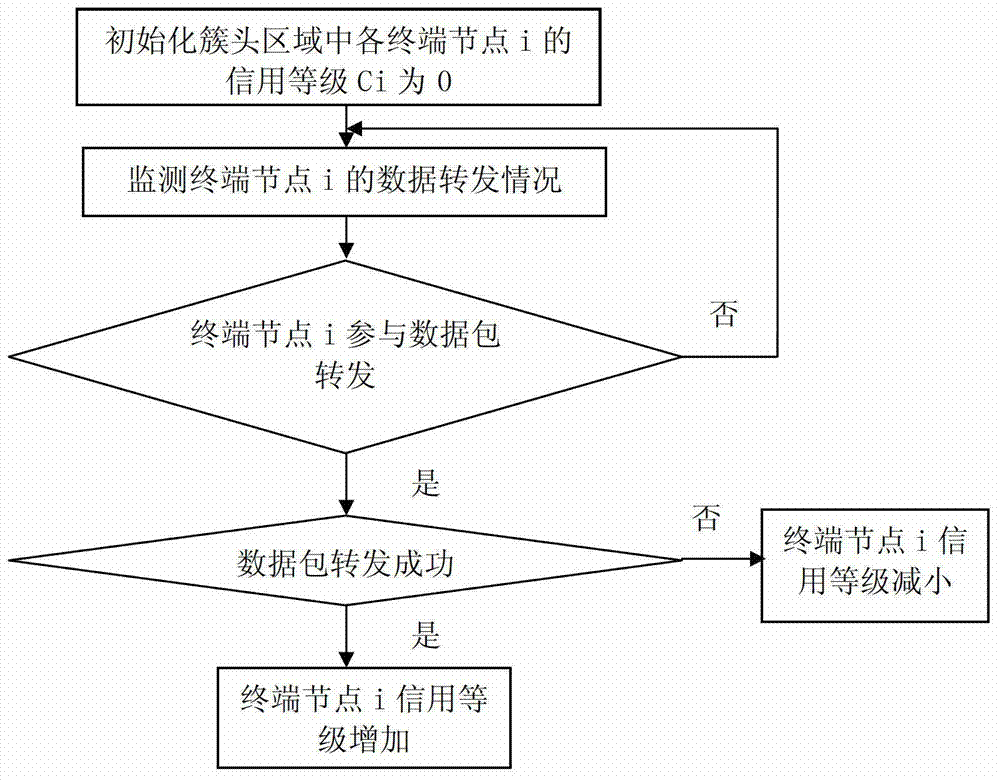
Method for detecting black hole attacks in clustering self-organized networks
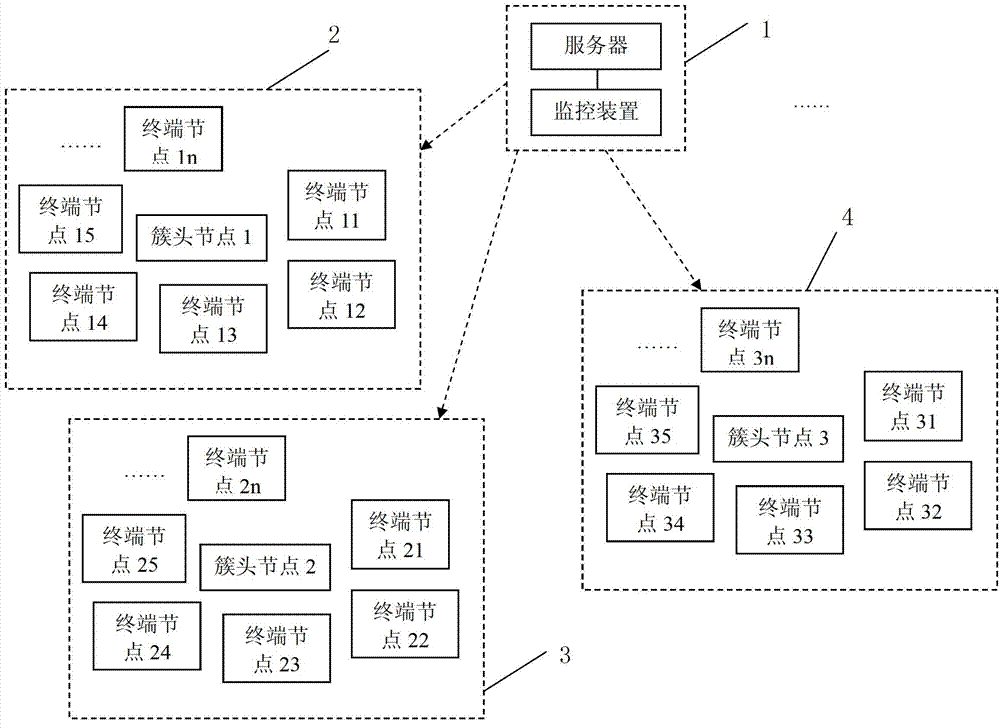
InactiveCN102932794AAvoid attackSolve the problem of attackNetwork topologiesSecurity arrangementSelf-organizing networkBlack hole
The invention relates to a method for detecting black hole attacks in clustering self-organized networks. The method includes that step one, a monitoring device is arranged at a base station; step two, cluster head areas in self-organized networks in an area covered by the base station are monitored in real time; step three, whether abnormal cluster head areas exist in the monitored area is judged, if the abnormal cluster head areas exist, step four is performed, and if not, the step two is repeated; step four, credit rates of terminal nodes in the abnormal cluster head areas are detected, and suspicious nodes are found to form a suspicious node set S1; step five, flow differences of nodes in the S1 are detected, and black hole attack nodes are found to form a black hole attack node set S2; and step six, the monitoring device sends early warning prompts. According to the method, not only a single malicious node attack is solved, the problem that a plurality of single malicious nodes are cooperated to attack can be effectively solved, alarms can be sent, and timely defense and treatment to the black hole attacks are facilitated.
Owner:INST OF INFORMATION ENG CAS
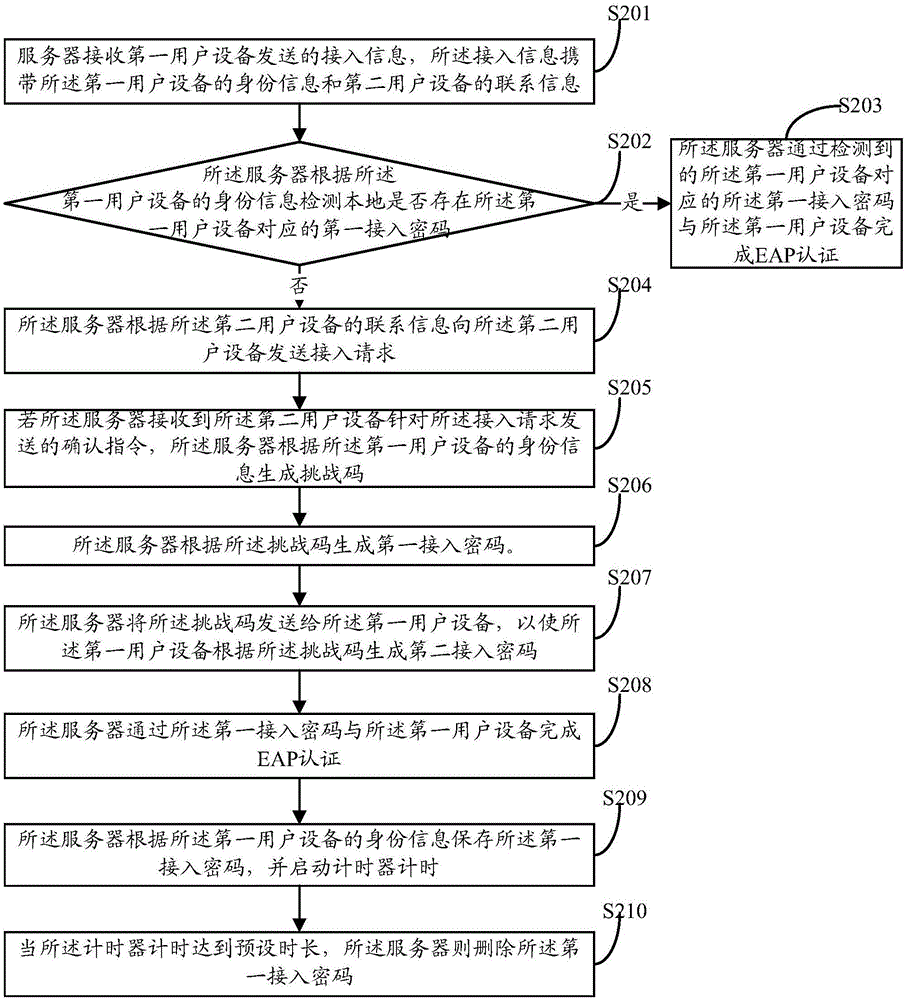
Access authentication method of wireless local area network, server and authentication system
ActiveCN106713222ASolve the problem of attackTransmissionSecurity arrangementAuthentication systemUser equipment
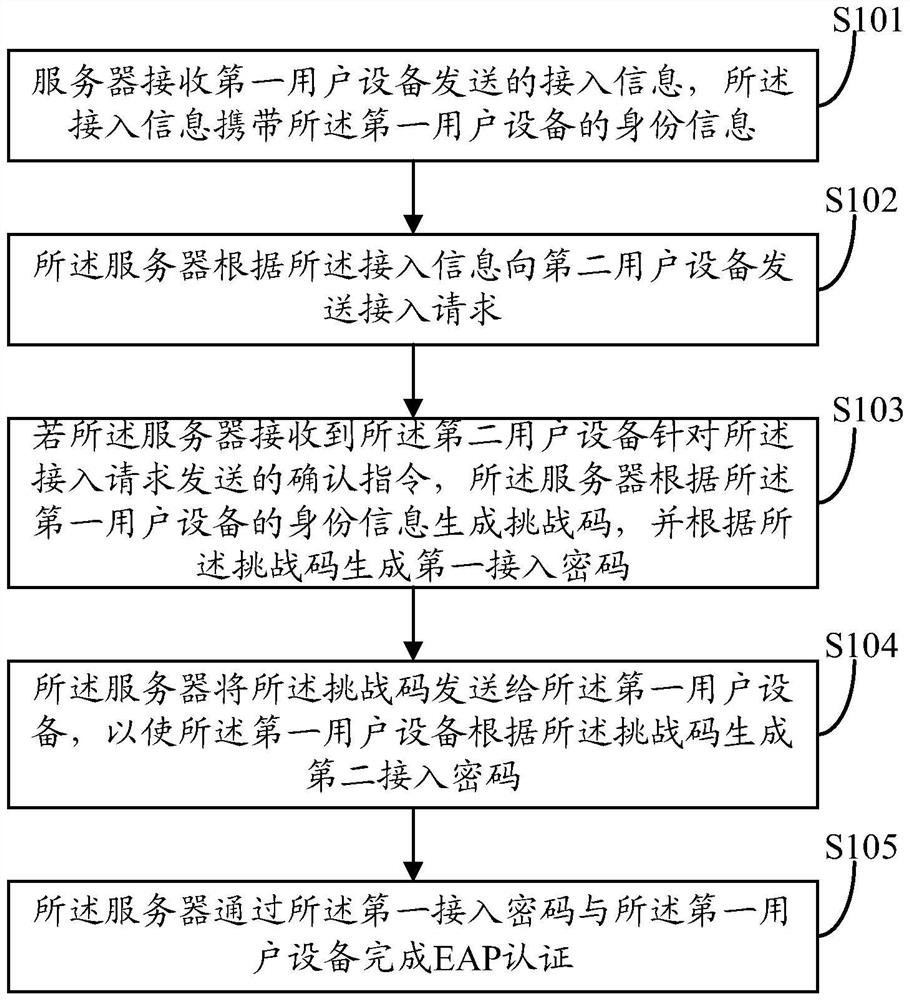
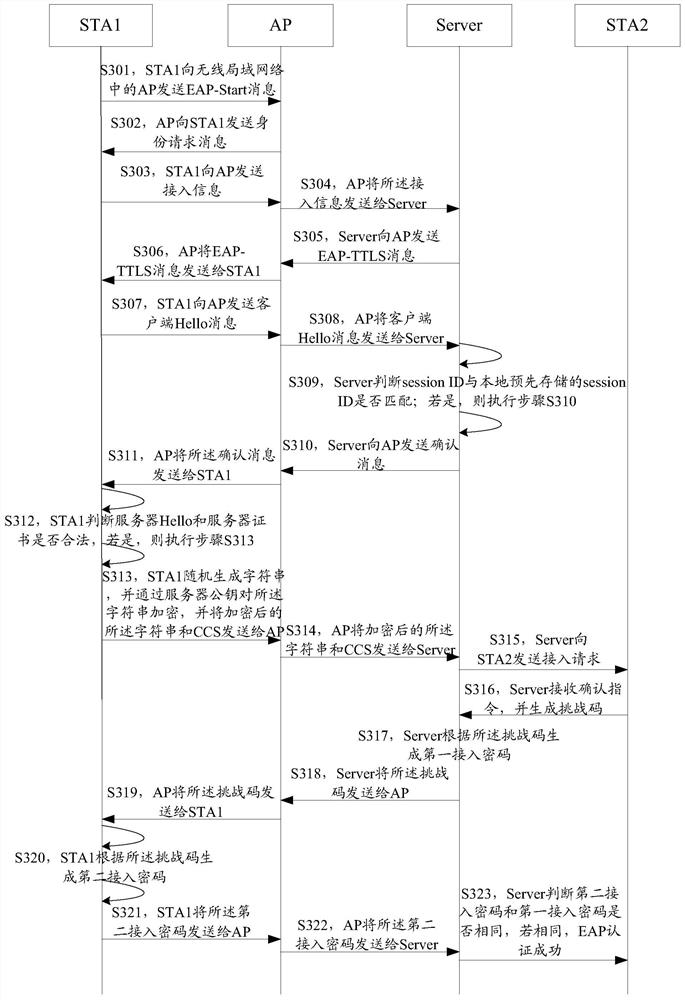
The invention discloses an access authentication method of a wireless local area network. The method comprises the steps that: a server receives access information sent by first user equipment, and the access information carries the identity information of the first user equipment; the server sends an access request to the second user equipment according to the access information; if the server receives a confirmation instruction sent by the second user equipment for the access request, the server generates a challenge code and generates a first access password according to the challenge code; the server sends the challenge code to the first user equipment such that the first user equipment generates a second access password according to the challenge code; and the server completes EAP certification through the first access password and the first user equipment. Correspondingly, the invention discloses the server and an authentication system. By using the access authentication method, the server and the authentication system, a problem of dictionary attack can be solved.
Owner:HONOR DEVICE CO LTD
Communication verification method, electronic equipment and storage medium
ActiveCN112087427AReal-time managementOvercome the disadvantages of only after-the-fact managementTransmissionAttackEngineering
The invention provides a communication verification method, electronic equipment and a storage medium, and aims to solve the problems that a network security scheme needs a large amount of boundary equipment and DDOS attacks and APT attacks are difficult to thoroughly prevent. The communication verification method comprises the steps that: a node server receives a service application instruction sent by user equipment; the node server inquires a service type from target equipment according to a target equipment address in the service application instruction; the node server inquires the user equipment whether to receive the service type provided by the target equipment or not according to the inquired service type; after the user equipment selects receiving, the node server generates a pass, wherein the pass is obtained through negotiation between the user equipment and the node server; the user equipment and the target equipment establish indirect connection according to the pass; andthe node server examines communication between the user equipment and the target equipment according to the pass. According to the communication verification method, the security of communication between the user equipment and the target equipment is improved.
Owner:NOVNET COMPUTING SYST TECH CO LTD
Cloud Platform Big Data Access Method
ActiveCN105007259BSolve the problem of attackEnsure safetyKey distribution for secure communicationKey exchangeAccess method
Owner:成都华西公用医疗信息服务有限公司
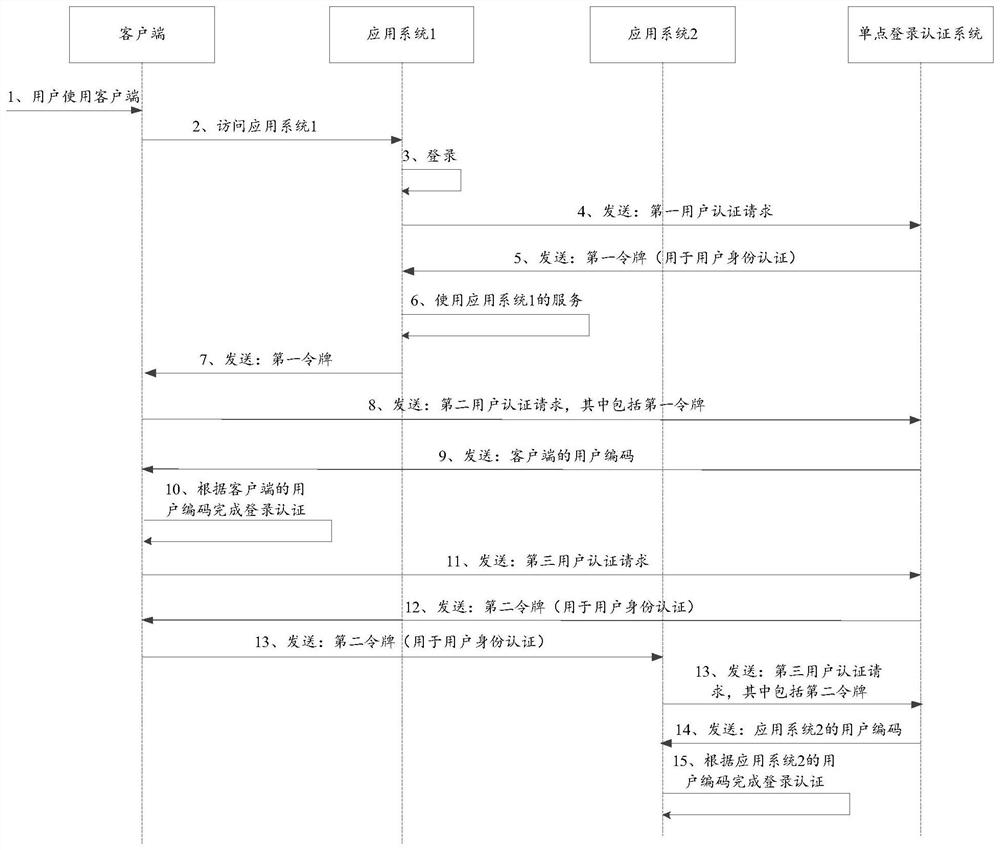
Single sign-on method and device, electronic equipment and storage medium
PendingCN114218550ASolve writing cookies (data stored on the user's local terminal)Work around the limitation of having to share the same client systemDigital data protectionDigital data authenticationTheoretical computer scienceEngineering
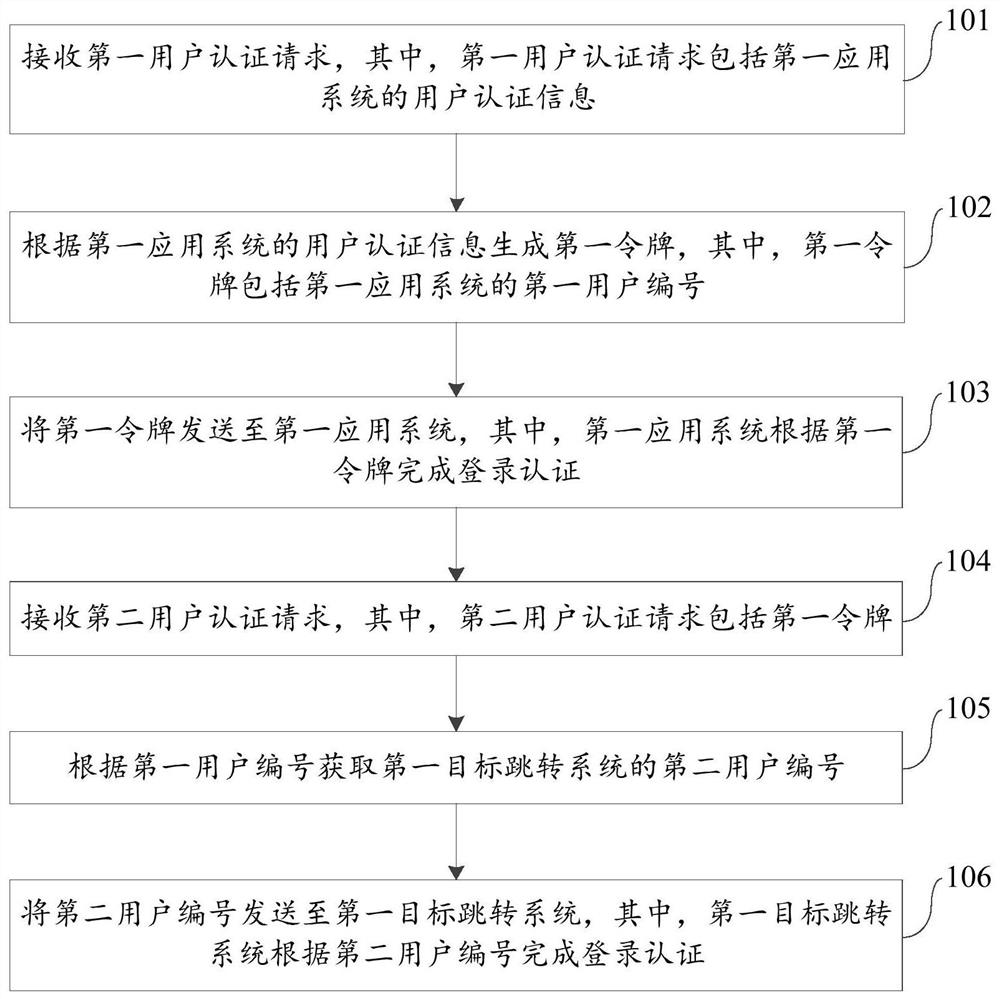
The invention provides a single sign-on method and device, electronic equipment and a storage medium, and belongs to the technical field of artificial intelligence recognition and classification. The method comprises the steps that a first user authentication request is received, and the first user authentication request comprises user authentication information of a first application system; a first token is generated according to the user authentication information of the first application system, and the first token comprises a first user number of the first application system; sending the first token to the first application system; receiving a second user authentication request, wherein the second user authentication request comprises the first token; acquiring a second user number of the first target jump system according to the first user number; the second user number is sent to the first target jump system, and the first target jump system completes login authentication according to the second user number. Therefore, the cross-domain single sign-on function can be realized, all application systems do not need to use the same user system, and meanwhile, the security and credibility of identity authentication can be effectively ensured.
Owner:CHINA CONSTRUCTION BANK
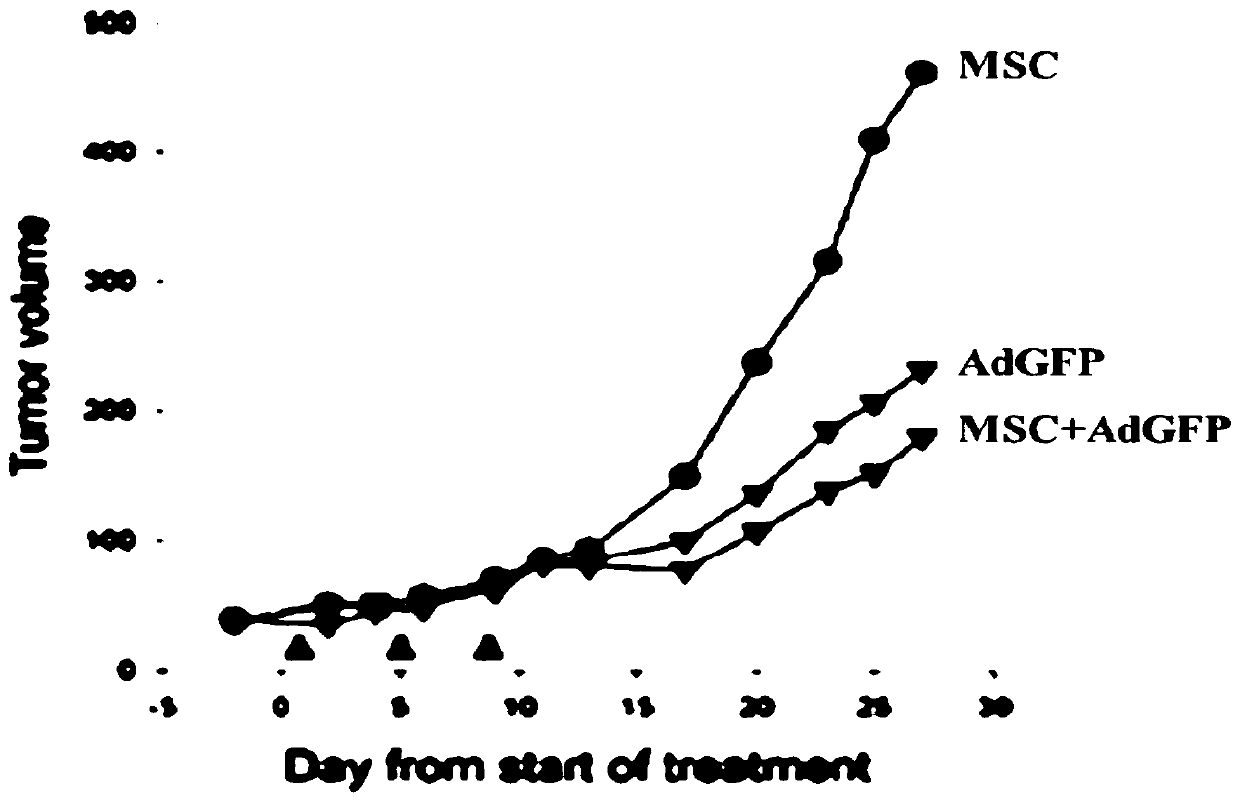
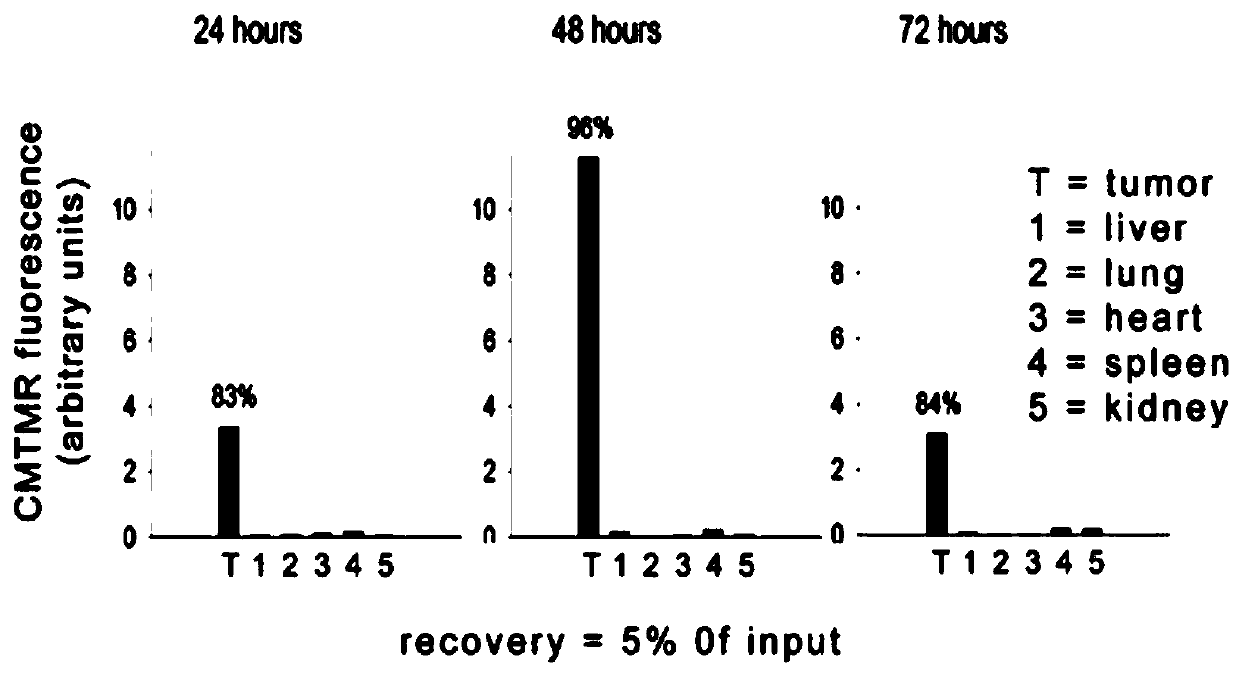
Establishing method and application of system for packing adenoviruses with mesenchymal stem cells
InactiveCN110499298ASolve the problem of attackImprove securityGenetically modified cellsSkeletal/connective tissue cellsBioremediationTumor tissue
The invention relates to an establishing method and application of a system for packing adenoviruses with mesenchymal stem cells, and belongs to the field of gene therapy. The method comprises the steps of reforming MSC cells as a carrier to obtain an MSC-E1 cell line for stable expression of E1 genes, enabling replication-defective adenoviruses having the effect of killing and damaging tumor cells to be infected with the cell line, and through intra-cellular assembling, preparing a cell system which can be packed and reproduce adenoviruses, wherein the cell system is used for performing caudal vein injection on a tumor model mouse, and the purpose of well killing and damaging tumor masses of the mouse is achieved. The established system can solve the three bottlenecks in tumor gene therapy, so that a bioremediation preparation is not attacked by a host defense mechanism, the bioremediation preparation can specially achieve the tumor parts, and therapeutic genes are in high-efficient expression in tumor tissues.
Owner:黄映辉
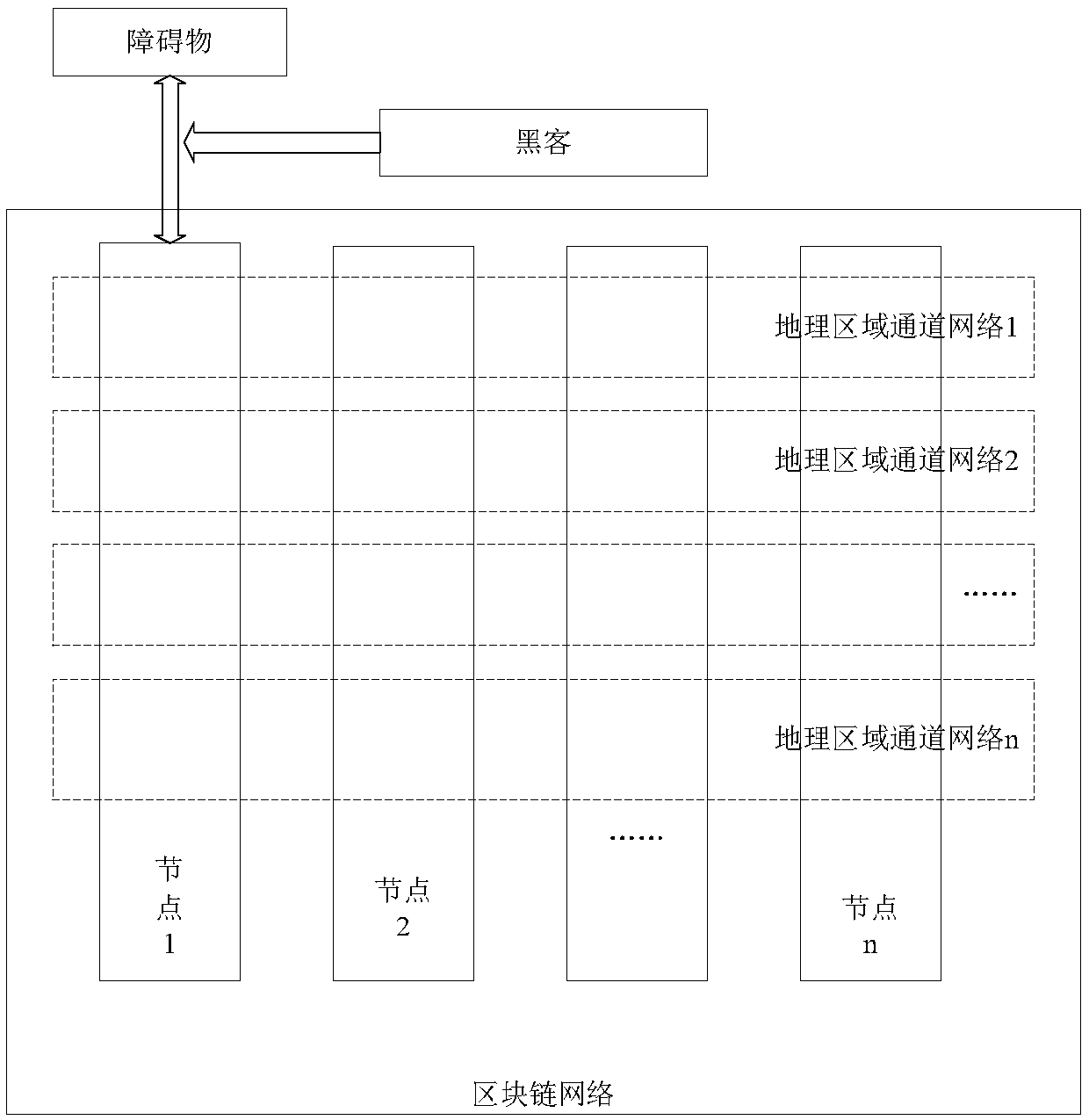
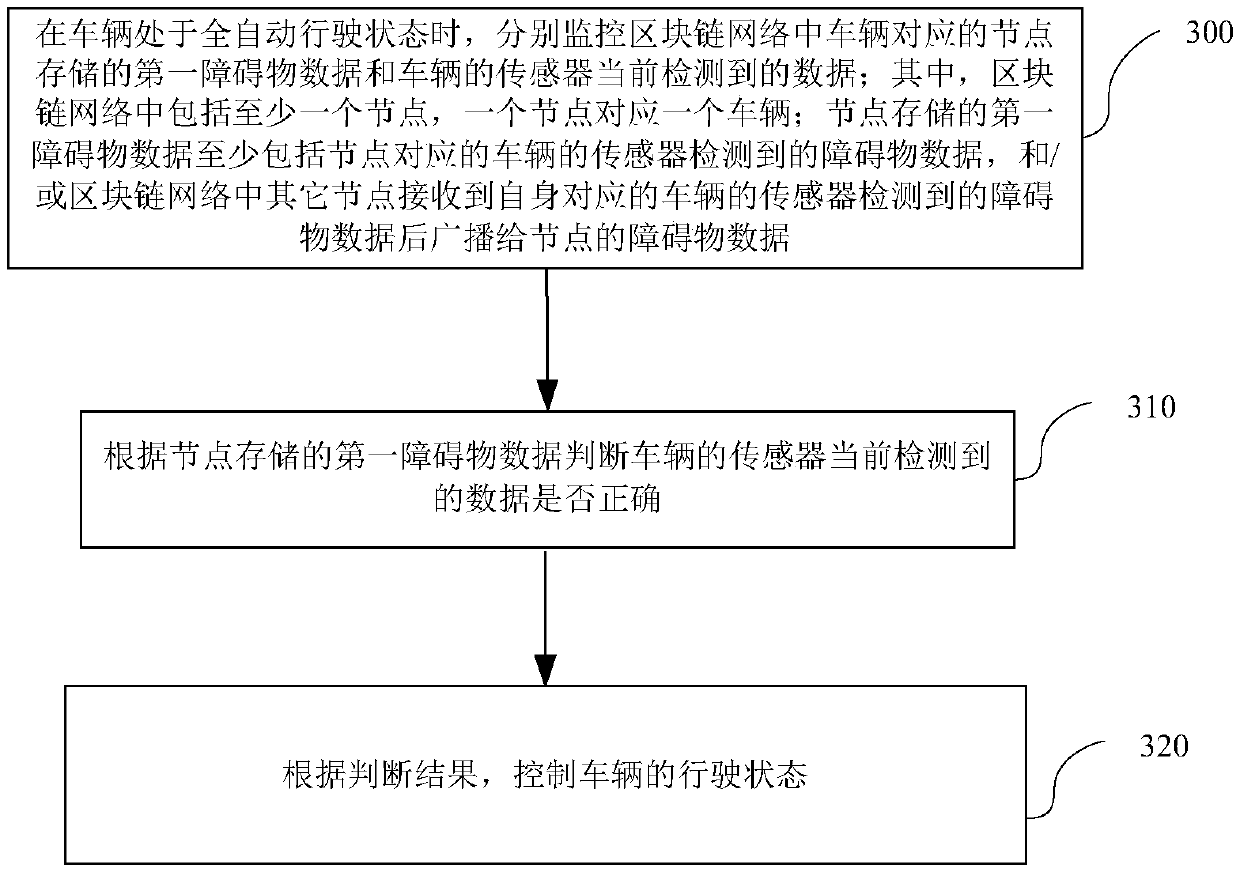
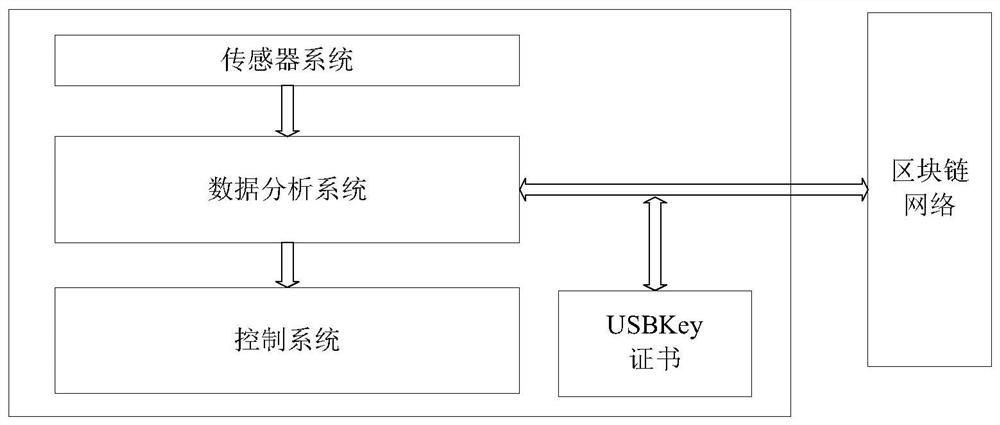
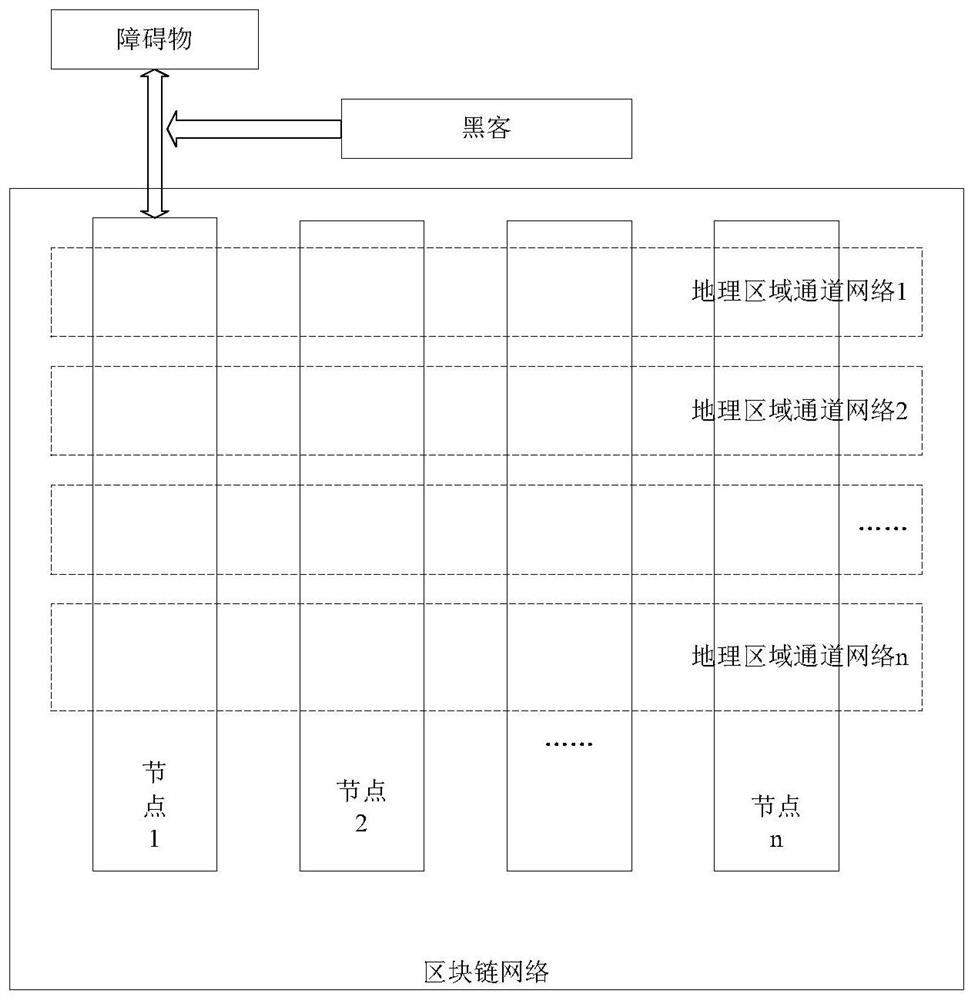
Vehicle driving control method and device
ActiveCN110808941AEnsure safetyImprove accuracyTransmissionElectric/fluid circuitData controlEngineering
The invention relates to the technical field of communication, in particular to a vehicle driving control method and device. The method comprises the following steps: respectively monitoring first obstacle data stored in a node corresponding to a vehicle in a blockchain network and data currently detected by a sensor of the vehicle when the vehicle is in a full-automatic driving state; judging whether the data currently detected by the sensor of the vehicle is correct or not according to the first obstacle data stored in the node; and controlling the driving state of the vehicle according to the judgment result, so that the data currently detected by the blockchain network and the sensor of the vehicle are monitored in real time by using the blockchain technology, the driving state of thevehicle is controlled, the problem that the sensor of the vehicle may be attacked is solved, the data of the sensor is prevented from being tampered, and the data accuracy is improved.
Owner:AEROSPACE INFORMATION
Method and apparatus for processing packets
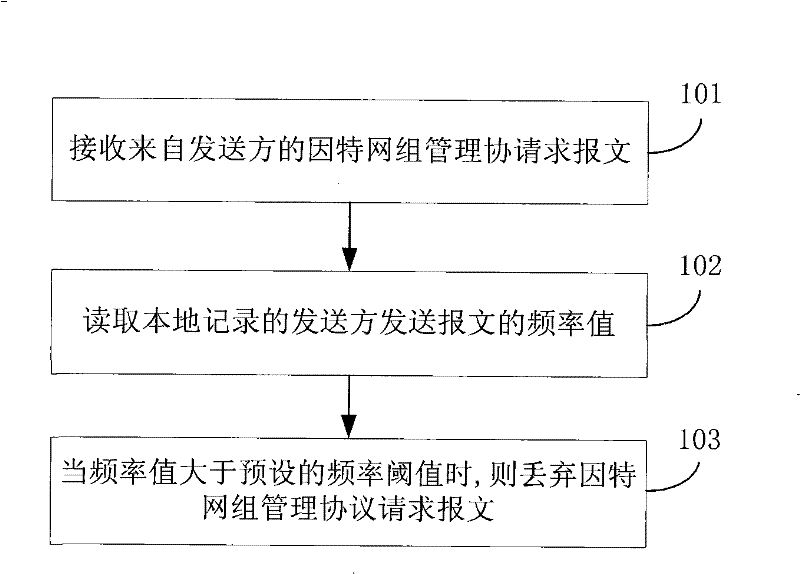
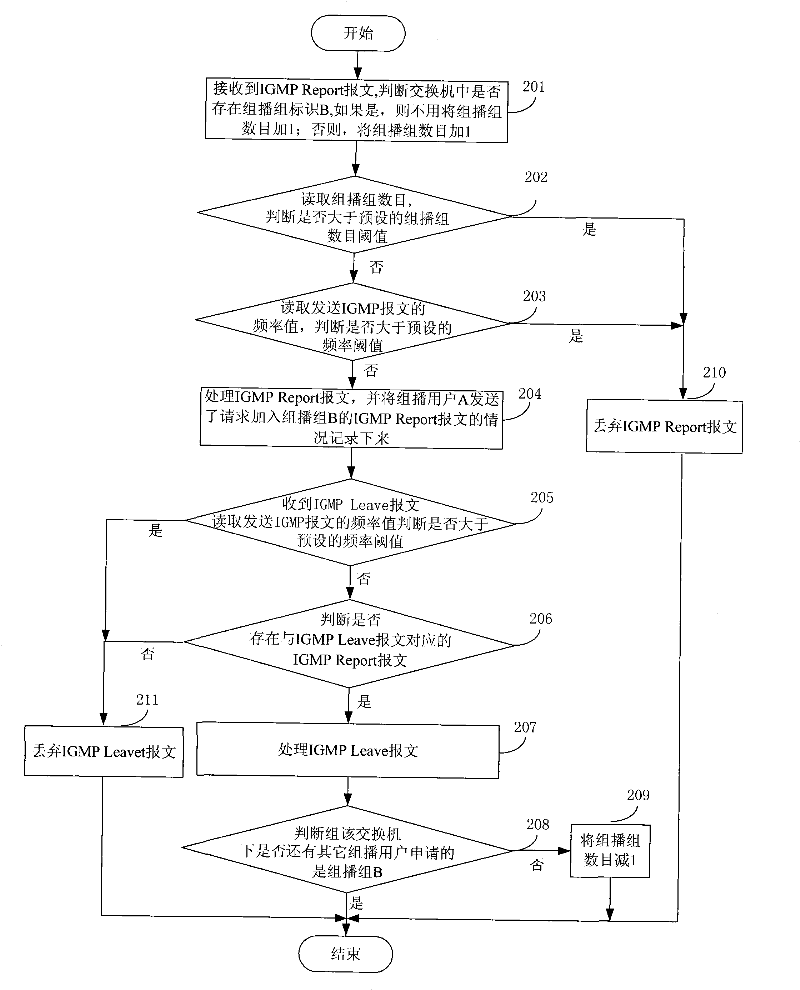
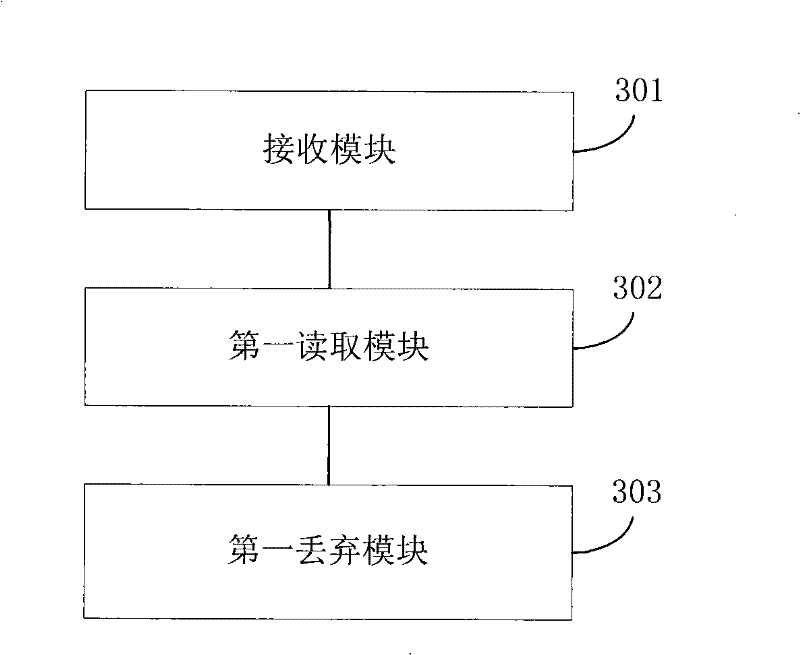
InactiveCN101478542BImprove attack defense capabilityImprove reliabilitySpecial service provision for substationComputer hardwareThe Internet
The invention discloses a method and an apparatus for processing messages belonging to the communication field. The method comprises: receiving an internet group management protocol (IGMP) request message from a sender; reading a local recording frequency value of sending message from the sender; discarding the internet group management protocol request message when the frequency value is larger than a presetting frequency threshold. The apparatus comprises: a receiving module, a first reading module and a first discarding module. The invention enables an exchange not to have a plurality of IGMP messages by discarding IGMP messages larger than the frequency threshold, improves the anti-attack ability of the exchange, avoids the IGMP messages attack to the exchange, and protects the exchange. Moreover the invention also solves the problem that a multicast client attacks by frequently adding the IGMP messages between different cast groups or sending the IGMP messages when leaving through discarding the IGMP messages larger than the frequency threshold.
Owner:HUAWEI TECH CO LTD
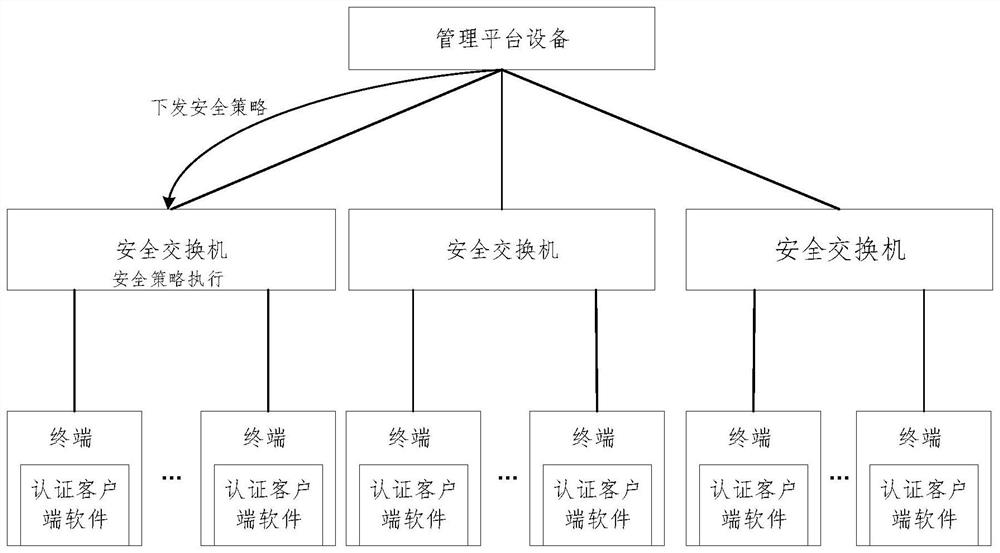
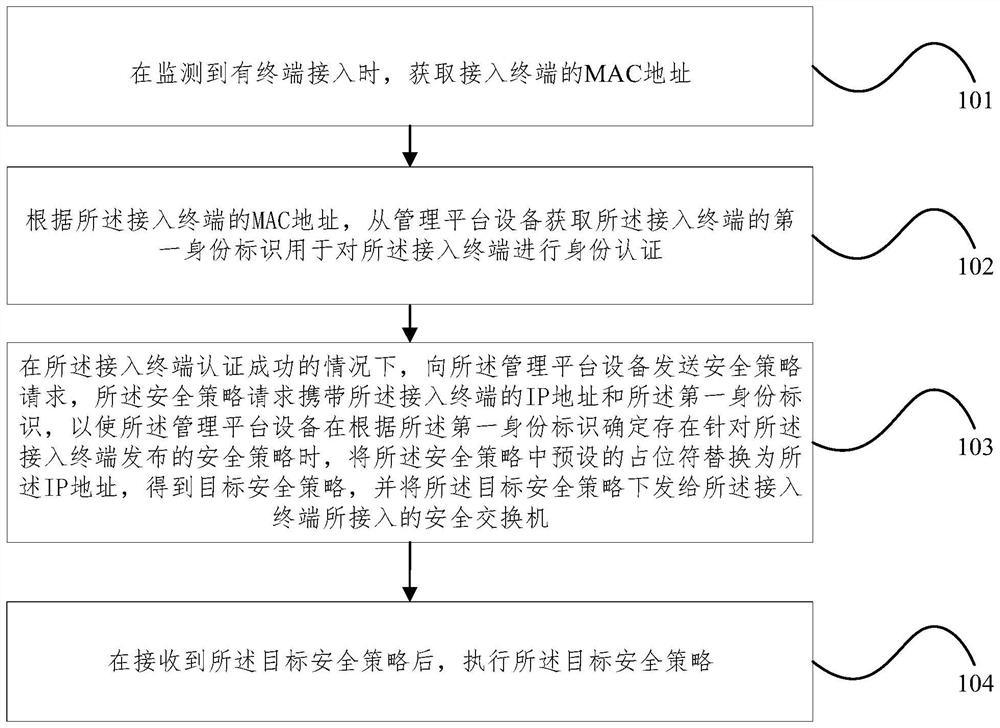
Network security protection method, system and device, security switch and storage medium
PendingCN114374543AThe solution cannot be formulated uniformlyFix security issuesSecuring communicationInternet privacyIp address
The invention relates to a network security protection method, system and device, a security switch and a storage medium, and the method comprises the steps: obtaining a first identity label of an access terminal from management platform equipment according to the MAC address of the access terminal when the access of the terminal is monitored, and carrying out the identity authentication of the access terminal, and under the condition that authentication of the access terminal succeeds, a security policy request is sent to the management platform equipment, and the security policy request carries the IP address and the first identity identifier of the access terminal, so that the management platform equipment sends the security policy to the access terminal when determining that a security policy issued for the access terminal exists according to the first identity identifier. And replacing a preset placeholder in the security policy with the IP address to obtain a target security policy, and issuing the target security policy to the security switch accessed by the access terminal, so that the security switch executes the target security policy after receiving the target security policy. According to the invention, unified formulation of security policies can be realized, and the efficiency and effect of security protection are improved.
Owner:BEIJING VRV SOFTWARE CO LTD
Method for accessing big data of cloud platform
ActiveCN105007259ASecuritySolve the problem of attackKey distribution for secure communicationLogical addressComputer security
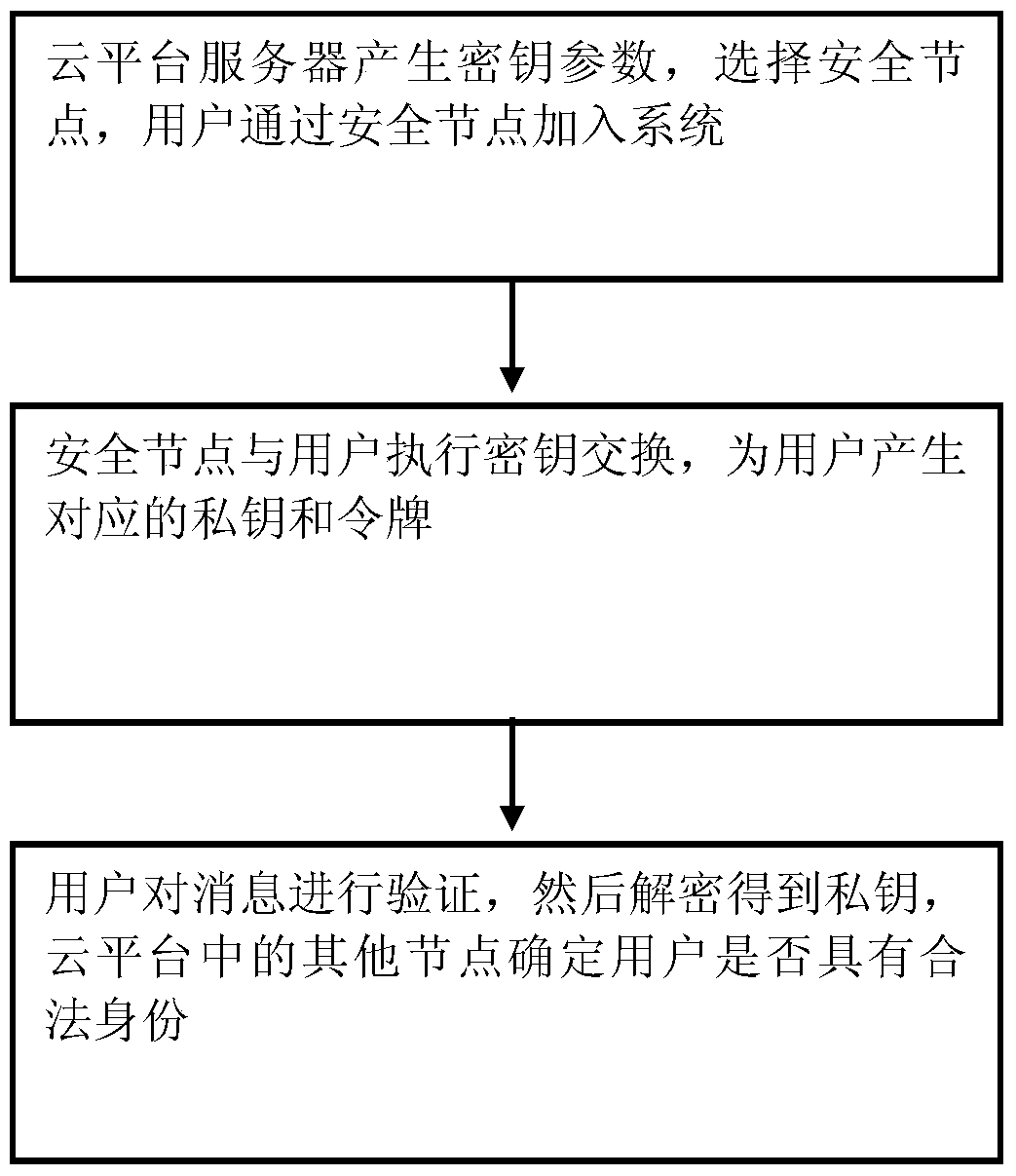
The present invention provides a method for accessing big data of a cloud platform. The method comprises the steps as follows: a cloud platform server generates a secret key parameter and selects a security node, a user joins a system through the security node; the security node executes secret key exchange with the user, the security node generates a corresponding private key and a token for the user; the user verifies a message, decryption is performed to obtain the private key, and other nodes in the cloud platform determine whether the user has a legal identity. The method of the present invention can effectively solve the problem that an illegal user makes an attack through a network logical address, can ensure security of the system, and is suitable for a cloud storage system.
Owner:成都华西公用医疗信息服务有限公司
Big data storage method
InactiveCN107623680ASolve the problem of attackEnsure safetyKey distribution for secure communicationCloud storage systemData store
The invention provides a big data storage method. The method is applied to a cloud server and comprises the steps of allocating a target identity to a target user based on a network logic address, wherein the identity comprises a public key of the target user; carrying out calculation to generate a private key of the target user through a pre-generated key parameter; generating and distributing akey pair corresponding to the identity of the target user according to the key and the private key, and setting a legal user as a system node; and verifying the user in a callback mode when the targetuser sends a login request, and determining that the user is a legal owner of the address when the current user can receive connection for the network logic address. According to the method, the problem that an illegal user carries out an attack through the network logic address can be effectively solved, the system security is ensured, and the method is applied to a cloud storage system.
Owner:佛山市高研信息技术有限公司
Method and device for driving a vehicle
ActiveCN110808941BEnsure safetyImprove accuracyElectric/fluid circuitSecuring communicationData controlVehicle driving
Owner:AEROSPACE INFORMATION
A black hole attack detection method in clustered self-organizing network
InactiveCN102932794BAvoid attackSolve the problem of attackNetwork topologiesSecurity arrangementSelf-organizing networkPacket drop attack
The invention relates to a method for detecting black hole attacks in a clustered self-organizing network. The method includes the following steps: Step 1: Install a monitoring device at a base station; Step 2: All clusters in the self-organizing network within the coverage of the base station The head area is monitored in real time; step 3: judge whether there is an abnormal cluster head area in the monitored area, if there is, enter step 4, otherwise return to step 2; step 4: detect the credit level of the terminal node in the abnormal cluster head area, Find suspicious nodes to form a set of suspicious nodes S1; step 5: detect the flow difference of nodes in S1, and find out black hole attack nodes to form a set S2 of black hole attack nodes; step 6: the monitoring device issues an early warning prompt. This method can not only solve the attack of a single malicious node, but also effectively solve the problem that multiple malicious nodes cooperate with each other to attack, and can issue an alarm, which is conducive to timely defense and processing of black hole attacks.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
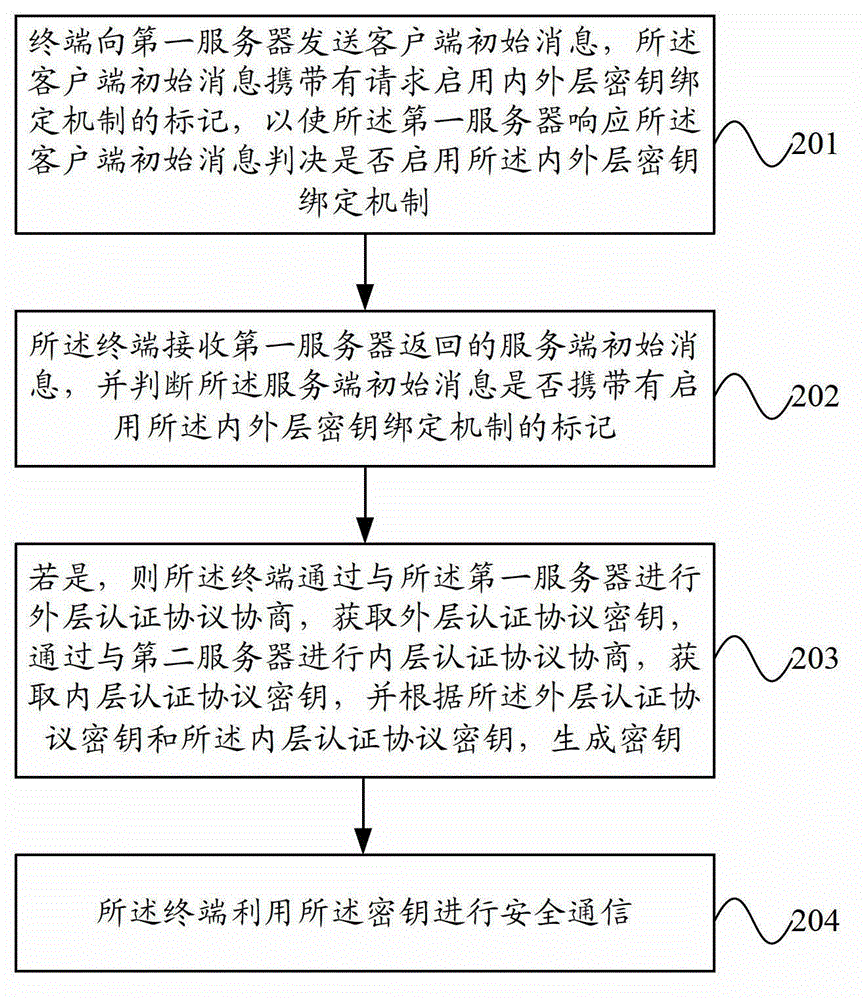
Secure communication method, terminal, server and system
ActiveCN102752298BSolve the problem of attackEasy to implementUser identity/authority verificationSecure communicationComputer terminal
The invention provides a secure communication method, a terminal, a server and a system. The method comprises the following steps that: the terminal sends a client-side initial message to a first server, wherein the client-side initial message carriers a mark requesting to start the inner-layer / outer-layer key binding mechanism so that the first server responds to the client-side initial message and judges whether to start the inner-layer / outer-layer key binding mechanism; the terminal receives the server-side initial message returned by the first server, and judges whether the server-side initial message carriers the mark requesting to start the inner-layer / outer-layer key binding mechanism; if the server-side initial message carriers the mark, the terminal performs outer-layer authentication protocol negotiation with the first server to obtain an outer-layer authentication protocol key, performs inner-layer authentication protocol negotiation with the second server to obtain an inner-layer authentication protocol key, and generates a master key according to the outer-layer authentication protocol key and the inner-layer authentication protocol key; and the terminal performs secure communication by use of the master key.
Owner:XFUSION DIGITAL TECH CO LTD
big data storage method
ActiveCN104935582BSolve the problem of attackEnsure safetyPublic key for secure communicationUser verificationCloud storage system
The invention provides a big data storage method. The method includes: a cloud server distributes an identification for a user based on a network logic address of the user, exports a public key of the user from the identification of the user, calculates and generates a private key of the user via a pre-generated secret key parameter, generates and distributes a key pair corresponding to the identification for the private key, and sets the legal user as the system middle node; during the login of the user, user verification is realized via the manner of callback, and when the current user can receive a connection of the network logic address, the user is determined to be the legal owner of the address. According to the method, the problem that illegal users carry out attacks via the network logic addresses can be effectively solved, the system security is guaranteed, and the method is applicable to cloud storage systems.
Owner:成都华西公用医疗信息服务有限公司
File processing method based on big data
ActiveCN104852924BSolve the problem of attackEnsure safetyKey distribution for secure communicationKey exchangePassword
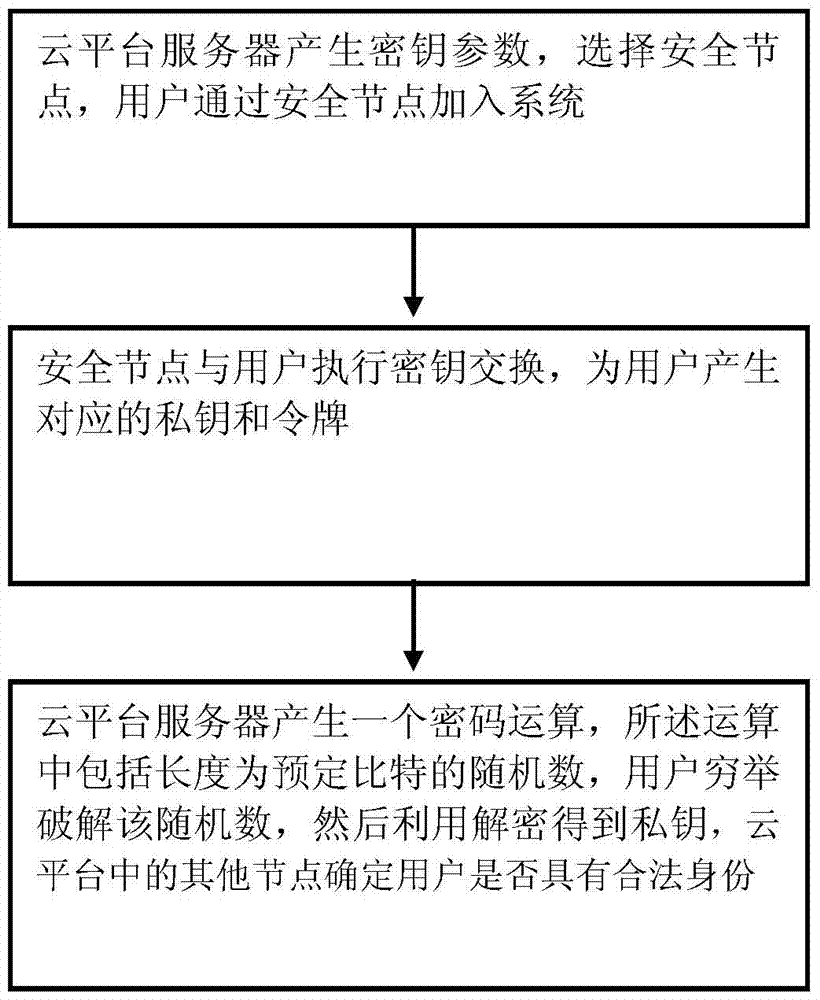
The present invention provides a method for processing a file based on large data, including: cloud platform server generates a secret key parameter, and selects a secured node; a user enters a system through the secured node; the secured node exchanges the secret key with the user; the secured node generates a corresponding private key and token for the user; the cloud platform server generates a password calculation; the calculation includes random numbers with the length of a preset bit; the user cracks the random number through exhaustion, and then obtains the private key by using decoding; and other nodes in the cloud platform determine whether the user has a legal identity. The method of the present invention can effectively solve the problem of attacking by an illegal user through a network logic address, guarantee the security of the system and is adapted to a cloud storage system.
Owner:成都华西公用医疗信息服务有限公司
A Unified Identity Authentication Platform Based on Zero Trust and Confidential Computing
ActiveCN113849815BSolve the problem of attackGuaranteed legalityDigital data authenticationPlatform integrity maintainanceInternet privacyConfidentiality
The invention relates to a unified identity authentication platform based on zero trust and confidential computing, which includes four stages, namely: communication establishment stage, user registration stage, function platform registration stage and login and key negotiation stage; wherein, the communication establishment stage It is used for the negotiation of the symmetric key SK to establish reliable communication between the user and the unified identity authentication platform; the user registration stage and the function platform registration stage realize the registration function verified by the unified identity authentication platform and the confidential computing security area, and build an anonymous authentication relationship table The function of obtaining the legal user and the legal function platform; the login and key negotiation stage realizes the function of negotiating the symmetric session key between the legal user and the legal function platform, and the symmetric session key will be used for the encryption of the subsequent transmission of private data . The invention has the beneficial effects of: ensuring the integrity and confidentiality of data in the "running state"; ensuring low overhead and low time delay in the authentication process, and realizing fast authentication.
Owner:LANZHOU UNIVERSITY
A wireless local area network access authentication method, server and authentication system
ActiveCN106713222BSolve the problem of attackTransmissionSecurity arrangementEngineeringAuthentication system
The present invention discloses an access authentication method for a wireless local area network, comprising: a server receiving access information sent by a first user equipment, the access information carrying the identity information of the first user equipment; the server according to the The access information sends an access request to the second user equipment; if the server receives the confirmation instruction sent by the second user equipment for the access request, the server generates a challenge code, and according to the challenge code Generate a first access password; the server sends the challenge code to the first user equipment, so that the first user equipment generates a second access password according to the challenge code; The first access password completes EAP authentication with the first user equipment. Correspondingly, the invention also discloses a server and an authentication system. The invention can solve the problem of dictionary attack.
Owner:HONOR DEVICE CO LTD
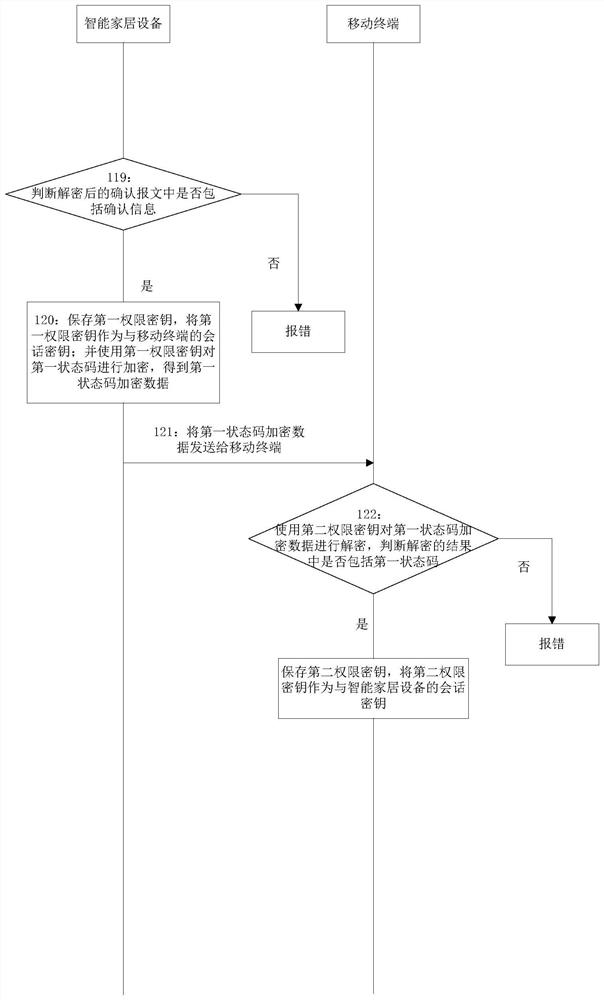
Method, system, mobile terminal and smart home device for negotiating session key
ActiveCN109068321BSolve the problem of attackEnsure communication securityKey distribution for secure communicationPublic key for secure communicationCommunications securityInternet privacy
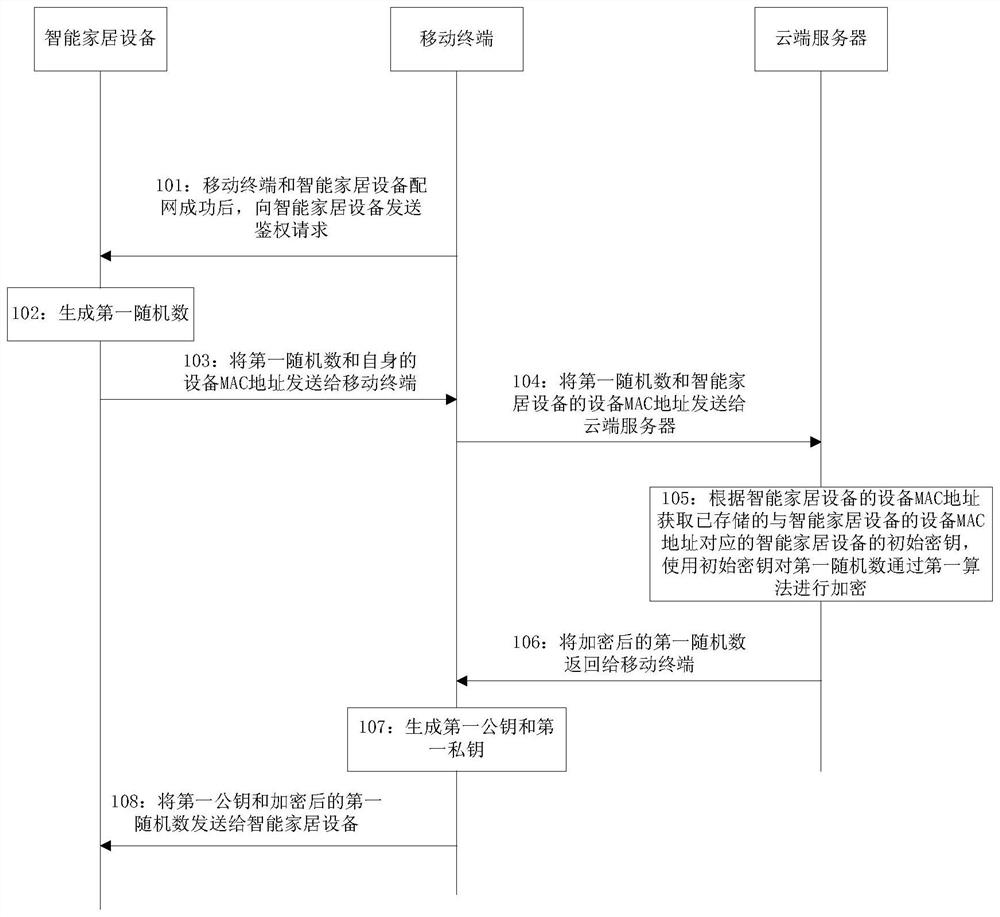
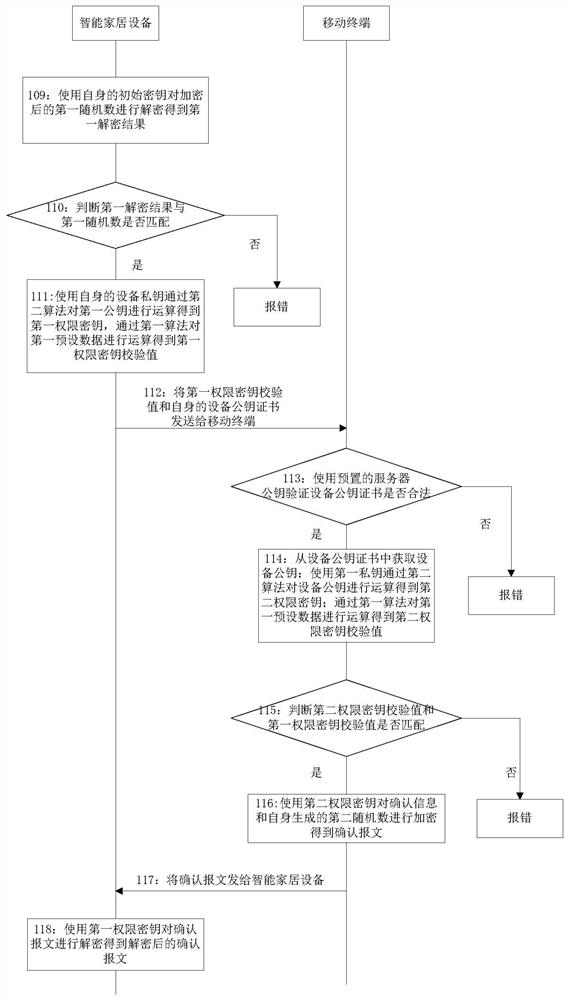
The invention discloses a method, a system, a mobile terminal and a smart home device for negotiating a session key; the system includes: a mobile terminal, a smart home device and a cloud server; The device public key of the home device is operated to obtain the second authority key, and the second authority key is used as the session key with the smart home device; the smart home device uses its own device private key to exchange the first The public key is operated to obtain the first authority key, and the first authority key is used as the session key with the mobile terminal; after the session key is negotiated between the mobile terminal and the smart home device, the session key can be used for encrypted communication, which can Solve the problem of smart home devices being attacked by the network, ensure the communication security between mobile terminals and smart home devices, and enhance user experience.
Owner:FEITIAN TECHNOLOGIES
Dynamic password authentication method for resisting man-in-the-middle attack
ActiveCN112235105AReduce the number of encryption and decryption operationsImprove authentication efficiencyKey distribution for secure communicationUser identity/authority verificationMan-in-the-middle attackAttack
The invention discloses a dynamic password authentication method for resisting man-in-the-middle attack. The method mainly comprises a registration stage and a login stage, is designed on the basis ofRSA difficulty, and can effectively resist man-in-the-middle attack and offline password guessing attack, and compared with a conventional password authentication scheme, the method has the advantages that in the authentication process, the times of executing encryption and decryption operations by a user and a server are reduced, and the authentication efficiency is improved; the remote login problem of a user can be conveniently solved, login information does not need to be stored in a public computer, and the login process is safer; violent cracking attack and man-in-the-middle attack on apassword can be effectively resisted, and meanwhile, bidirectional authentication is added, so that the problem of pseudo server attack is solved.
Owner:NANJING UNIV OF POSTS & TELECOMM
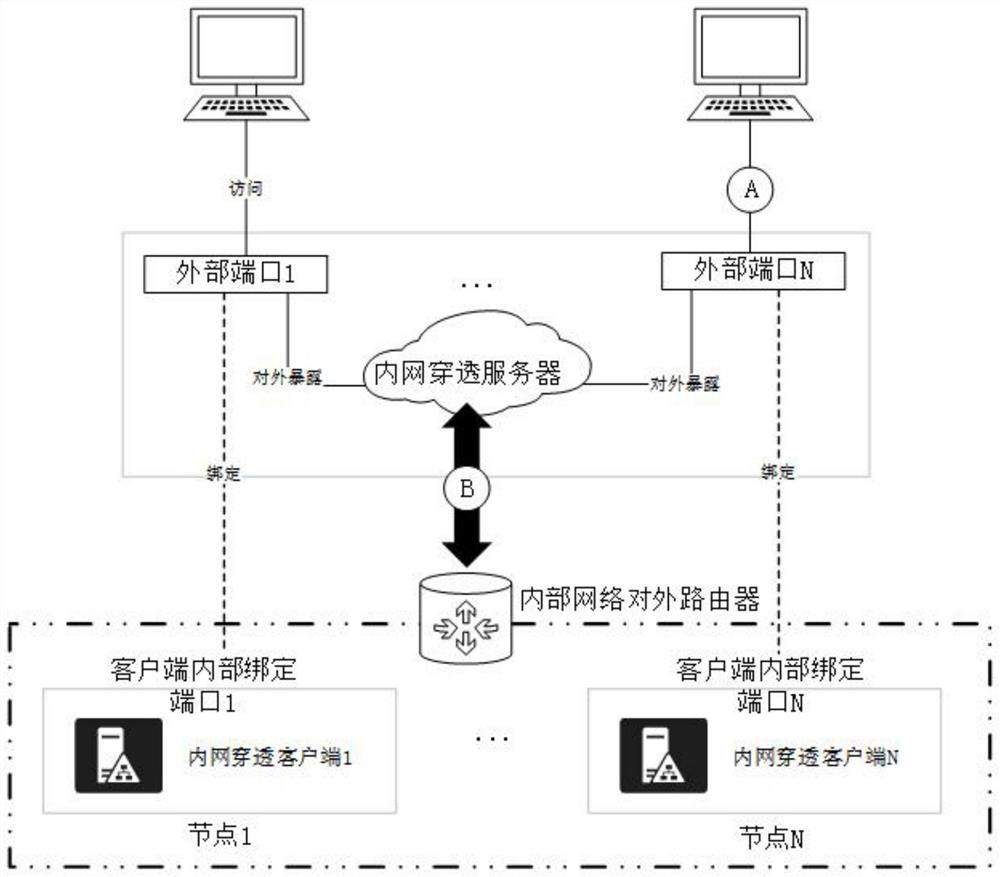
Intranet penetration security management and control method, management and control system and intranet penetration system
PendingCN114039757ASolving the vulnerability to sniffingSolve the disadvantages of brute force loginSecuring communicationControl systemEngineering
The invention discloses an intranet penetration security control method, a control system and an intranet penetration system, and the control method comprises the following steps: S1, identifying an external service port number of a to-be-connected internal node, and determining an external port bound with a to-be-connected intranet penetration client; S2, logging in an intranet penetration server; s3, opening an external port; s4, establishing communication with an intranet penetrating client through an external port; s5, after the preset time of successfully establishing the communication, closing the external port and keeping the current communication connection. The control system comprises a port number identification module, a login access module, an action module and a communication module. The intranet penetration system comprises an intranet, an external network and a security policy implementation system. The external port is opened and other ports are closed in a targeted manner by setting a firewall, and the defects that the intranet is exposed to the external network for a long time, and consequently the intranet is likely to be sniffed and cracked violently to log in are overcome.
Owner:上海承蓝数据科技有限公司
A location-based personalized differential privacy protection method for users
ActiveCN109362032BReduce the risk of privacy breachesSolve the problem of attackLocation information based serviceSecurity arrangementPersonalizationAttack
The invention discloses a user location personalized differential privacy protection method for location-based service. The method comprises the steps of 1, generating a disturbance location through utilization of an index mechanism; 2, obtaining a posterior probability of an opponent for a location of a user at time t according to a prior probability of the opponent for the location of the user at time t, index mechanism probability distribution and the generated disturbance location; 3, judging whether the posterior probability of the opponent for the location of the user at time t satisfiesa security requirement or not, sending the disturbance location and a query request to a service provider if the posterior probability of the opponent for the location of the user at time t satisfiesthe security requirement, and adding a confusion location if the posterior probability of the opponent for the location of the user at time t does not satisfy the security requirement; 4, adding theconfusion location, and sending a location set composed of the confusion location and the disturbance location to the service provider after the security requirement is satisfied; and 5, screening query results returned by the service provider. According to the method, the problem that user location privacy is leaked due to unreliability of the service provider can be solved, and moreover, a Bayesian attack can be effectively coped with, so security of the user location privacy in the location-based service can be improved.
Owner:ANHUI UNIVERSITY
A dynamic password authentication method against man-in-the-middle attacks
ActiveCN112235105BReduce the number of encryption and decryption operationsImprove authentication efficiencyKey distribution for secure communicationUser identity/authority verificationMan-in-the-middle attackBrute force
The invention discloses a dynamic password authentication method against man-in-the-middle attack, which mainly includes a registration phase and a login phase. The design of the invention is based on the difficult problem of RSA, and can effectively resist man-in-the-middle attacks and offline password guessing attacks. Compared with the existing password The authentication scheme of the present invention: in the authentication process, the number of times of encryption and decryption operations performed by the user and the server is reduced, and the authentication efficiency is improved; The process is more secure; it can effectively resist brute force attacks and man-in-the-middle attacks on passwords, and at the same time, two-way authentication is added to solve the problem of fake server attacks.
Owner:NANJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com