Dynamic password authentication method for resisting man-in-the-middle attack
A dynamic password and authentication method technology, applied in the field of information security, can solve problems such as inability to resist password guessing attacks or man-in-the-middle attacks, and inability to achieve two-way authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
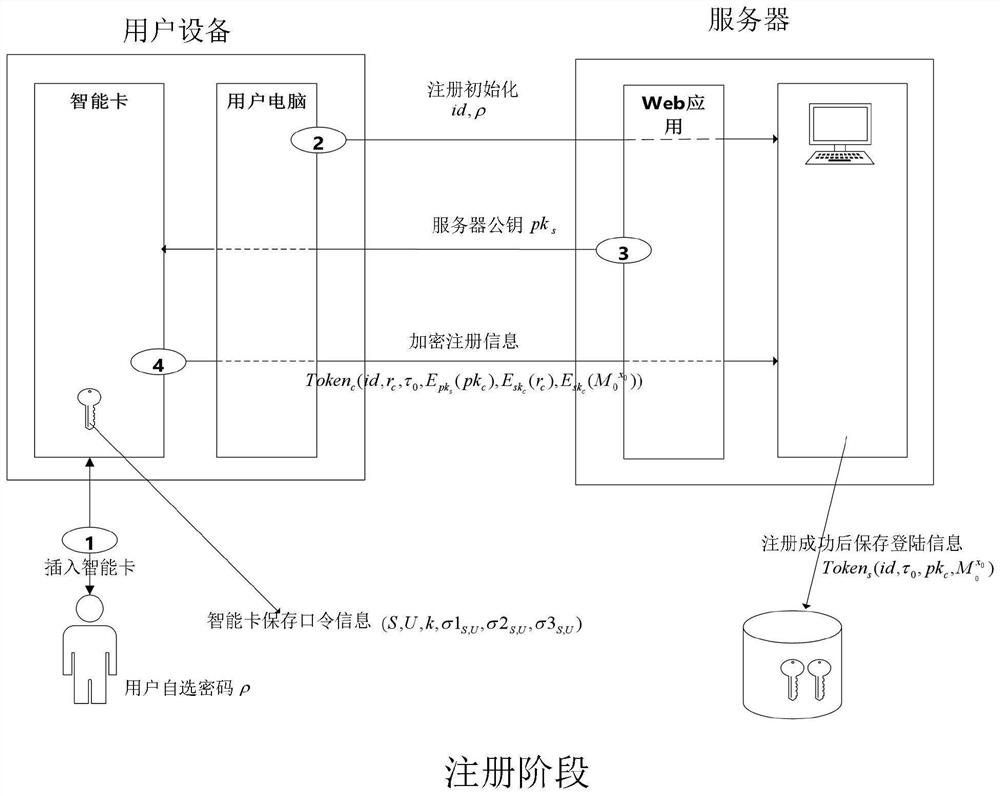
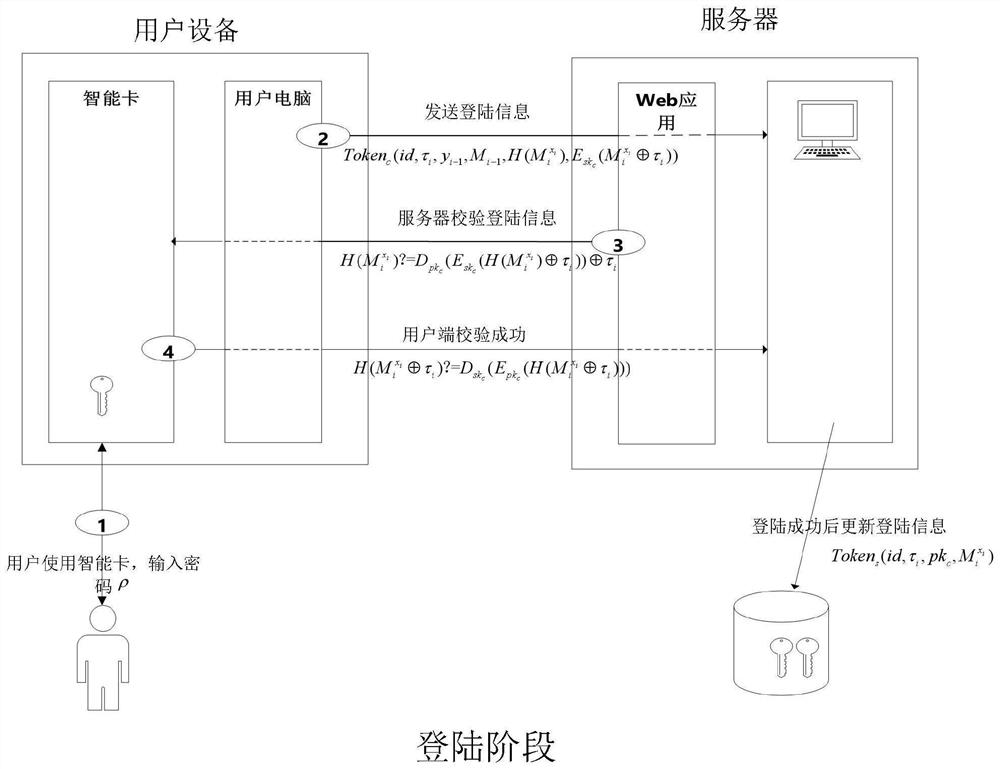
[0073] Example 1, see Figure 1 to Figure 4 , this embodiment proposes a new design of a smart card-based dynamic password authentication protocol in order to solve the security and convenience problems of password authentication technology. This embodiment utilizes the RSA difficult problem and smart card technology to improve authentication efficiency.
[0074] For a clearer and brief description, the concept of user Alice is introduced in this embodiment. User Alice means user Alice herself, and also means user Alice's mobile terminal or fixed terminal. The mobile terminal can be a smart phone, a tablet, or a handheld computer. , the fixed terminal may be a desktop computer, etc., and in this embodiment, the two are regarded as the same execution subject.
[0075] A dynamic password authentication method against man-in-the-middle attacks, including: a registration phase and a login phase;
[0076] see figure 1 and figure 2 , the registration phase includes the following...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com