Device and method for obtaining consistent encryption and decryption results in a synchronous redundant system
A redundant system and encryption and decryption technology, which is applied in the field of devices for obtaining consistent encryption and decryption results, can solve the problems that the results cannot be compared and judged, the secret key is different, and the encryption results are different, so as to reduce the number of repeated encryption and decryption operations, reduce the System power consumption and the effect of saving computing resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
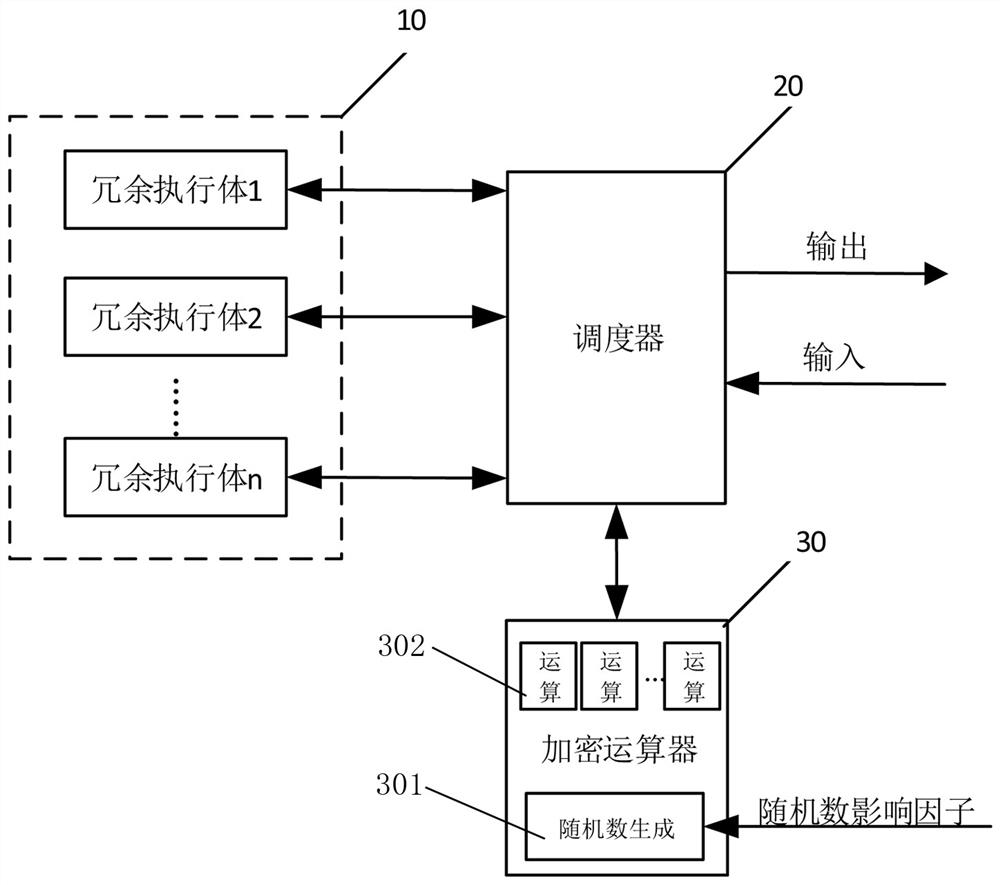
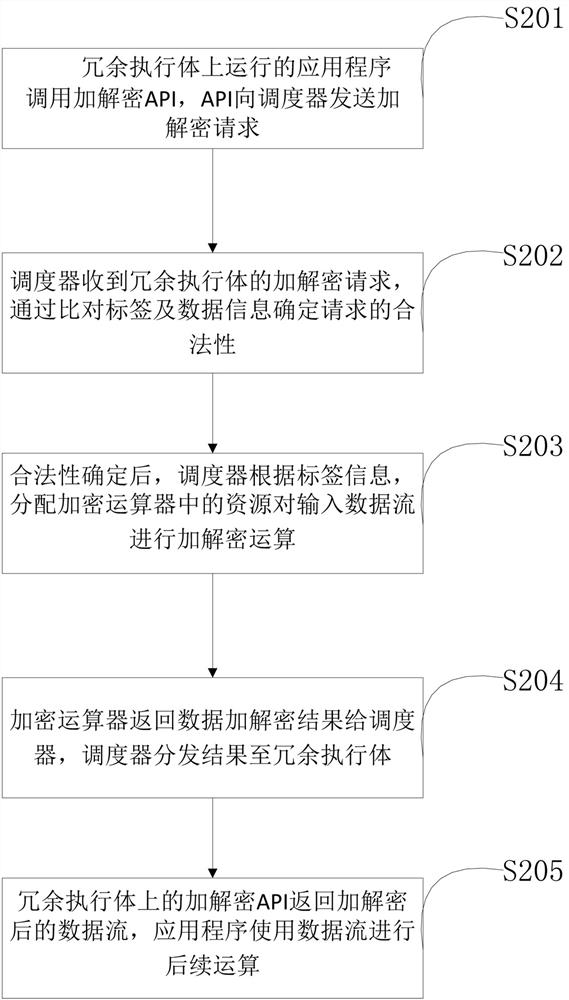
[0033] Embodiment one, such as figure 1 As shown, a device for obtaining consistent encryption and decryption results in a synchronous redundant system is used in an information control system with high security requirements, including several synchronously running homogeneous or heterogeneous redundant executive bodies 10 , scheduler 20 and encryption operator 30;
[0034] The redundant execution body 10 is connected with the scheduler and is used to execute the application program. Each redundant execution body is equivalent in function and can be homogeneous or heterogeneous in structure, and runs a series of application programs on it , according to the input of the scheduler, perform task processing.
[0035] The scheduler 20 is used for various management of redundant execution bodies, input and output agents, and other related operations, such as receiving external input and distributing input data to each redundant execution body; and judging the addition of redundant...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com