A New Secure Anonymous Communication Method Based on Public-Private Key Cryptography Mechanism
An anonymous communication, public and private key technology, applied in the field of information security, can solve the problem of inability to resist data tampering attacks of relay routing nodes, and achieve the effects of improving message forwarding efficiency and anonymous communication efficiency, reducing computational complexity, and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] 1. The link establishment process is described as follows:
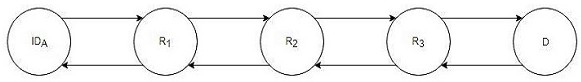
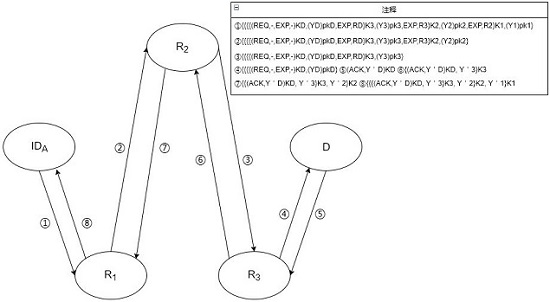
[0030] The first step: when the user ID A When wanting to establish an anonymous communication link with the destination node D, first randomly select L=3 onion routing nodes in the public list managed by KGC, and obtain the long-term public key QUOTE pk of the onion routing node at the same time i (i=1,2,3)pk i (i=1,2,3) and the long-term public key pk of destination node D D .
[0031] Step 2: User ID A First generate the destination node D and three onion routing nodes R respectively i (i=1,2,3) Temporary public-private key pair (X D ,Y D ) and (X i ,Y i ) (i=1,2,3). Based on these ephemeral private keys and the long-term public key of the onion routing node, the user ID A Run the DH key exchange algorithm to generate and destination node D and three routing nodes R i (i=1,2,3) shared temporary session key K D and K i (i=1,2,3).
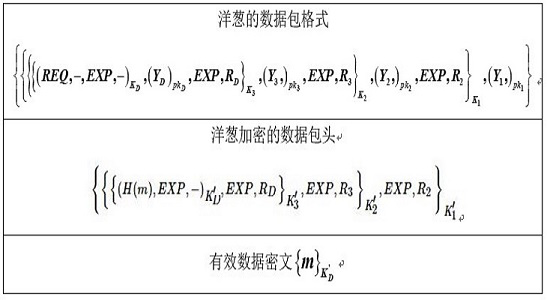
[0032] Step 3: User ID A Locally generate a link establishment...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com