Method, system, mobile terminal and smart home device for negotiating session key
A smart home device and mobile terminal technology, applied in the field of smart home devices and negotiating session keys, can solve problems such as insufficient intelligence, achieve the effects of ensuring communication security, enhancing user experience, and solving network attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0073] This embodiment provides a method for negotiating a session key, including:
[0074] Step s1: the mobile terminal sends an authentication request to the smart home device;
[0075] Step s2: the smart home device sends its own first data and its own device identification to the mobile terminal;
[0076] In this embodiment, the first data may specifically be a first random number.
[0077] Step s3: the mobile terminal sends the first data and the device identification to the cloud server;
[0078] Step s4: The cloud server acquires an initial key corresponding to the device identifier, encrypts the first data using the initial key to obtain first encrypted data, and sends the first encrypted data to the mobile terminal;
[0079] In this embodiment, the first encrypted data may specifically be an encrypted first random number.
[0080] Step s5: the mobile terminal sends the first encrypted data and its own first public key to the smart home device;
[0081] Step s6: Th...
Embodiment 2
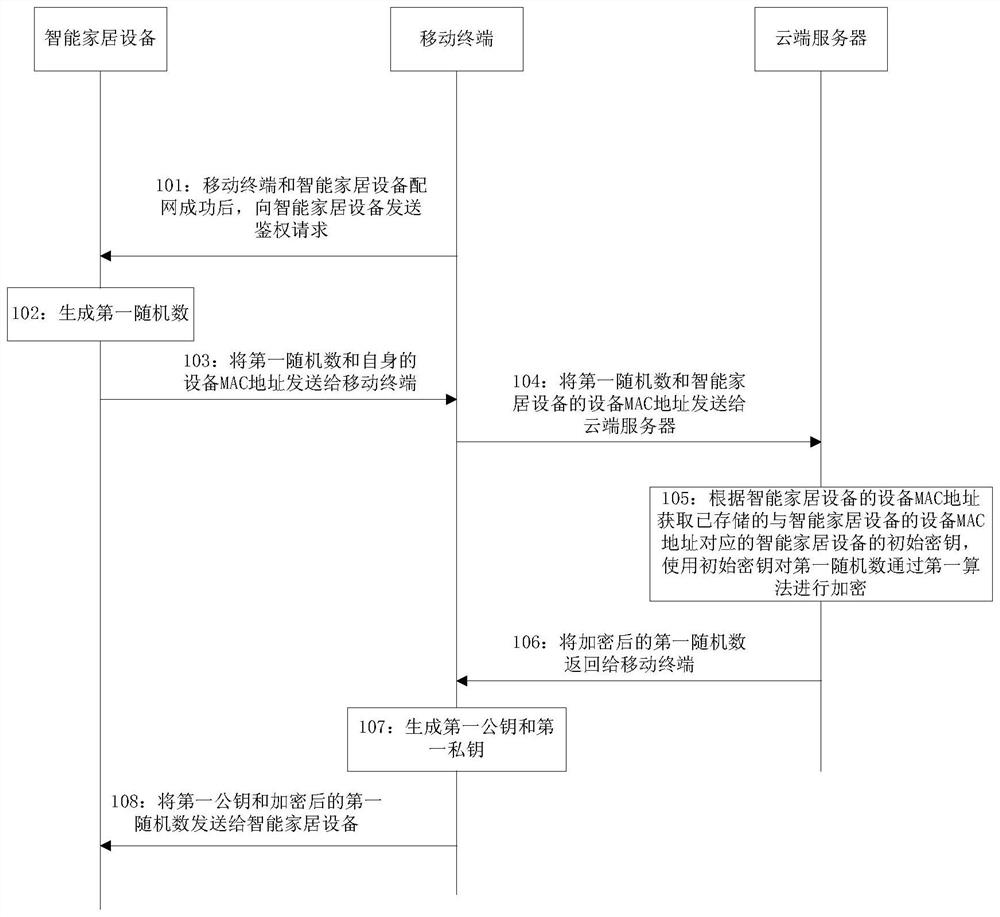
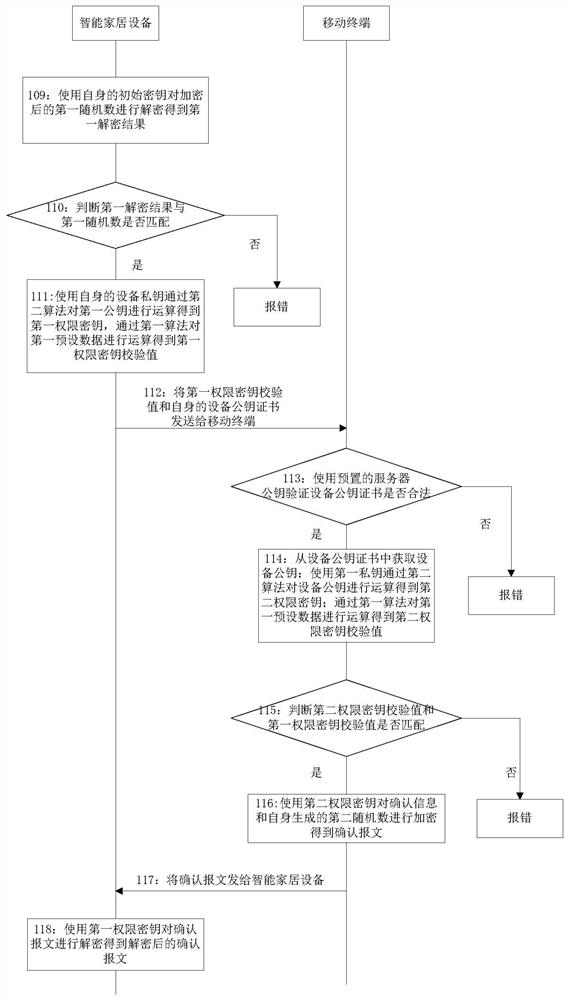
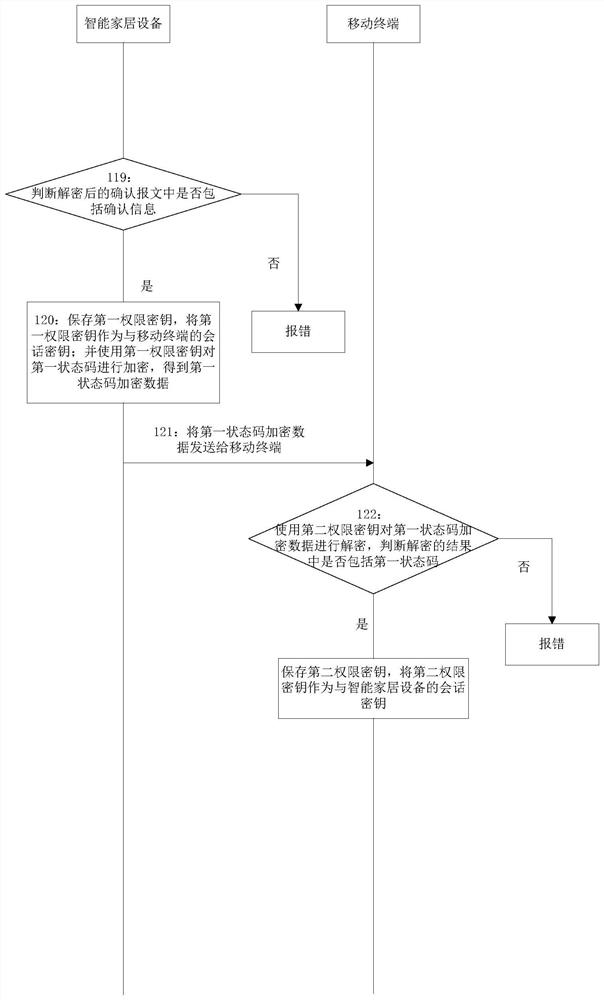
[0158] This embodiment provides a method for negotiating a session key, such as Picture 1-1 , Figure 1-2 , Figure 1-3 shown, including:
[0159] Step 101: After the mobile terminal and the smart home device are successfully connected to the network, the mobile terminal sends an authentication request to the smart home device;
[0160] In this embodiment, after the mobile terminal and the smart home device are successfully connected to a network, the mobile terminal and the smart home device communicate through a wireless network channel.
[0161] Step 102: the smart home device generates a first random number;
[0162] For example: smart home devices generate the first random number: 28 67 FA 12 A3 D8 C7 A5 55 66 28 7838 C7 A5 E7.
[0163] Step 103: the smart home device sends the first random number and its own device MAC address to the mobile terminal;
[0164] Specifically, the smart home device splices the first random number with its own device MAC address, and sen...
Embodiment 3
[0265] This embodiment provides a system for negotiating a session key, such as figure 2 As shown, the system includes: mobile terminals, smart home devices and cloud servers;
[0266] The mobile terminal includes: a first sending module 11, a first receiving module 12, a second sending module 13, a second receiving module 14, a third sending module 15, a third receiving module 16 and a first computing module 17;
[0267] The first sending module 11 is configured to send an authentication request to the smart home device;
[0268] The first receiving module 12 is configured to receive the first data and device identification from the smart home device;
[0269] The second sending module 13 is configured to send the first data and device identification received by the first receiving module 12 to the cloud server;
[0270] The second receiving module 14 is used to receive the first encrypted data from the cloud server;
[0271] The third sending module 15 is configured to s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com