Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
38results about How to "Improve attack defense capability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
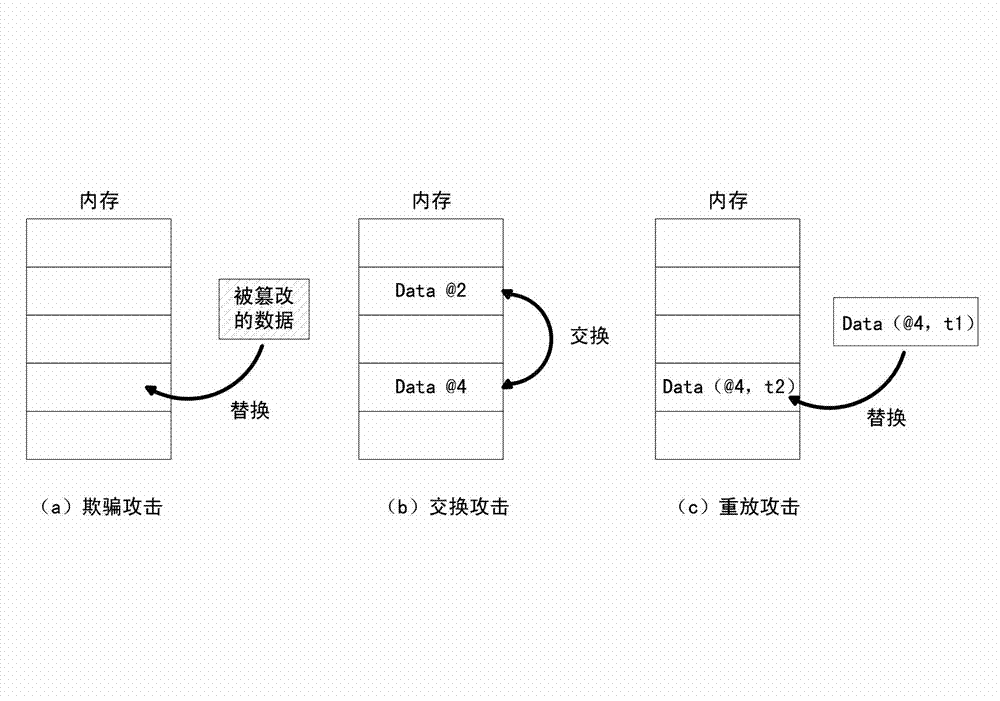
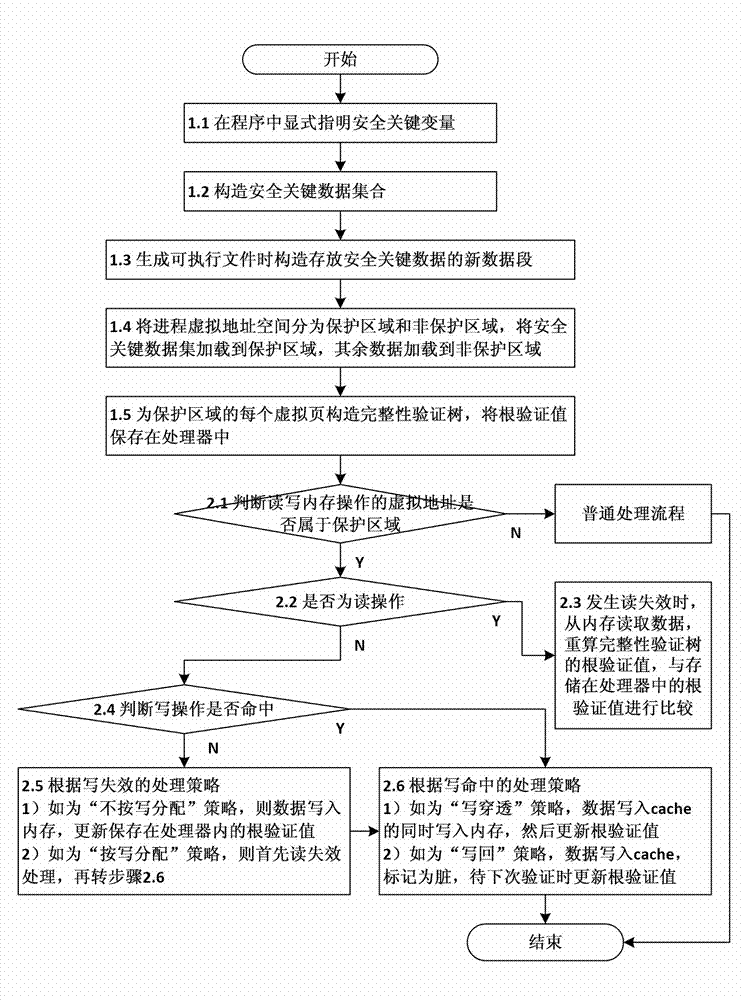
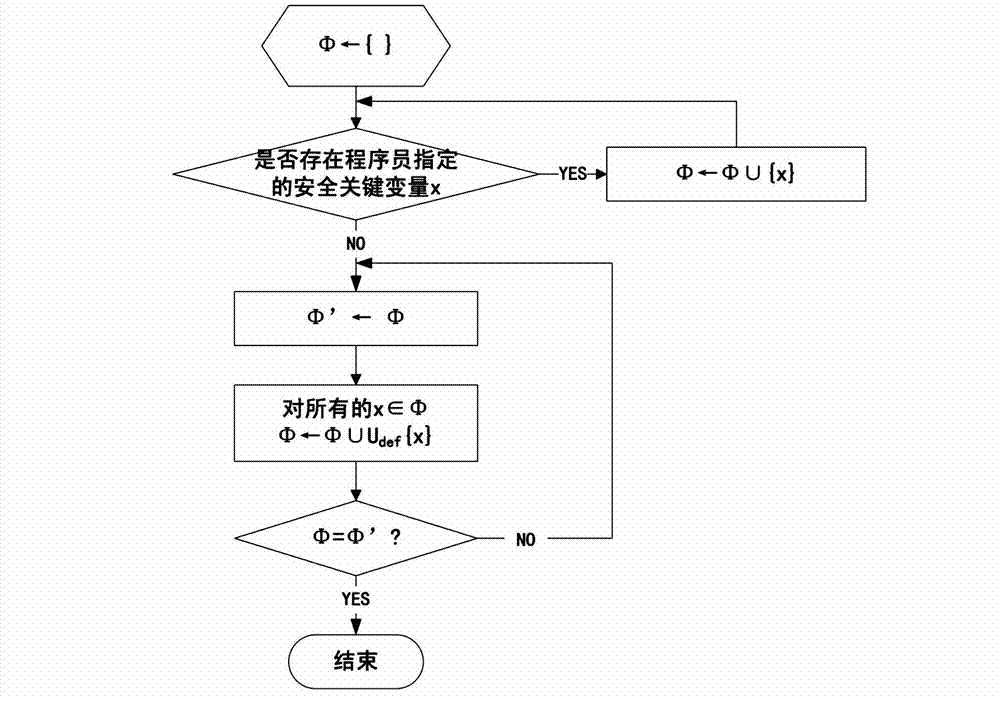
Method and device for verifying integrity of security critical data of program in process of running
ActiveCN102930185AAvoid attackIntegrity verification implementationProgram/content distribution protectionData setData integrity
The invention discloses a method and a device for verifying the integrity of security critical data of a program in the process of running. The method comprises the following steps: 1) indicating a security critical variable in the program, generating a security critical data set in the process of compiling, dividing a virtual address space of the program into a protected area and a non-protected area in the process of loading the program, loading the security critical data set to the protected area, and constructing an integrity verification tree for a virtual page of the protected area of the program; and 2) in the process of writing program data into a memory, updating a root verification value; and in the process of reading program data from the memory, generating a new root verification value, comparing the new root verification value with the original root verification value, if the two are equal, determining that the security critical data set is not tampered, otherwise, determining that the security critical data set is tampered. The device comprises a data integrity verification circuit, a root verification value storage module and a comparator. The method and the device disclosed by the invention have the advantages of high safety performance, strong attack prevention performance, small calculated amount, and less occupied storage space.
Owner:NAT UNIV OF DEFENSE TECH
DNS (Domain Name Resolution) acceleration method, system and device
ActiveCN105681491AAvoid incompatibility problemsAnalysis records are stable and effectiveTransmissionDomain nameComputer network
The invention provides a DNS acceleration method, system and device. The DNS acceleration device is connected with a DNS resolver and one or multiple authorized DNS servers. The DNS acceleration method comprises that a first request, from the DNS resolver, to resolve a domain name is received, and the first request includes a record type of a resolution result of the domain name to be resolved; the one or multiple authorized DNS servers associated with the domain name to be resolved is / are used to carry out recursive resolution on the domain name to be resolved to obtain resolution results of the one or multiple authorized DNS servers in the whole recursive resolution process; and all the resolution results are collected, all alias records which occur in the recursive resolution process are hidden in the resolution results, and a resolution result of in the same record type of the resolution result in the first request is selected, and response to the DNS resolver is made. According to the invention, it is ensured that the resolution records of the domain name are stable and effective, and scheduling is more accurate.
Owner:CHINANETCENT TECH
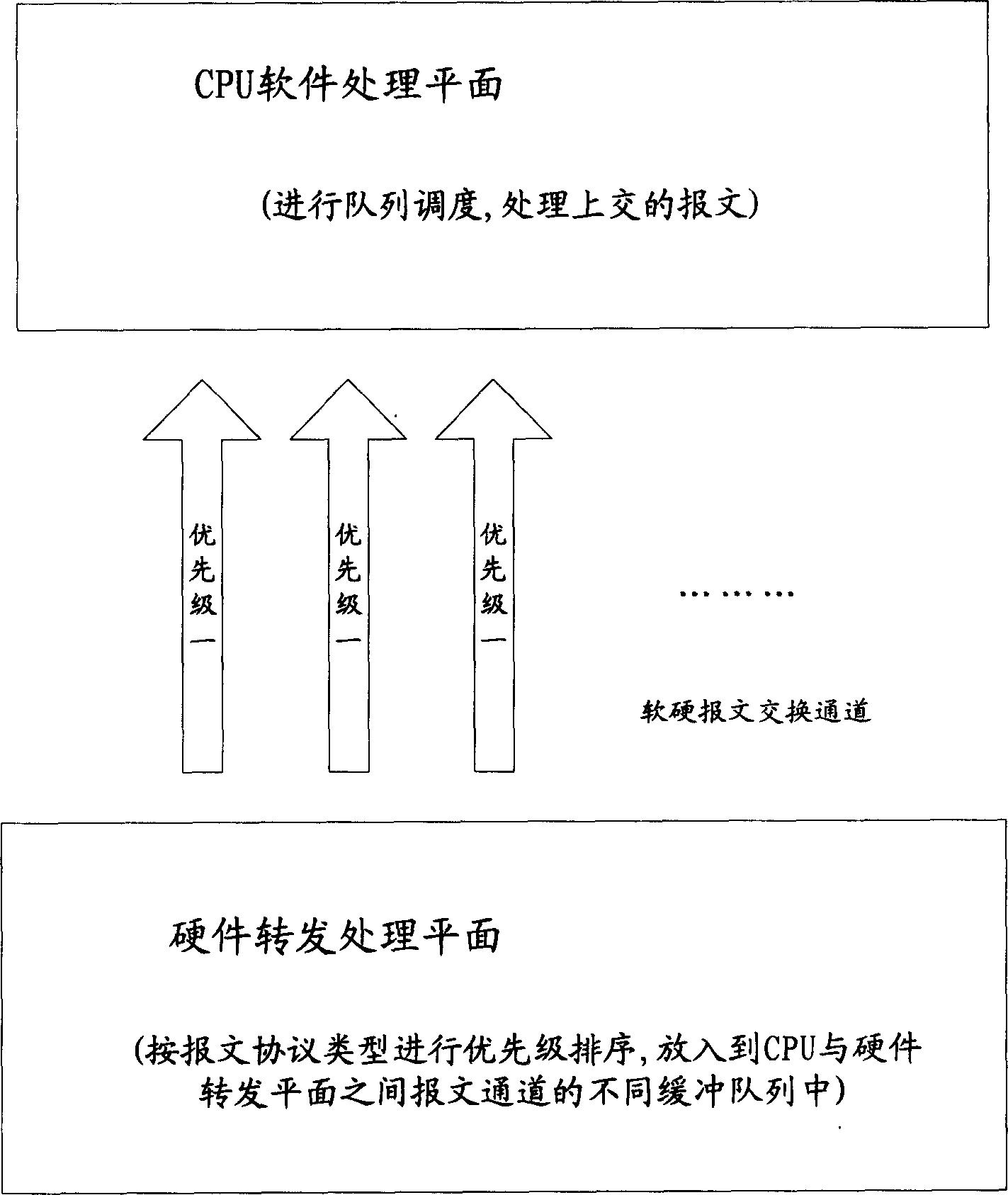
Method for raising network security via message processing
ActiveCN1889510AGuaranteed uptimeImprove reliabilityData switching networksElectric digital data processingMessage processingMessage passing
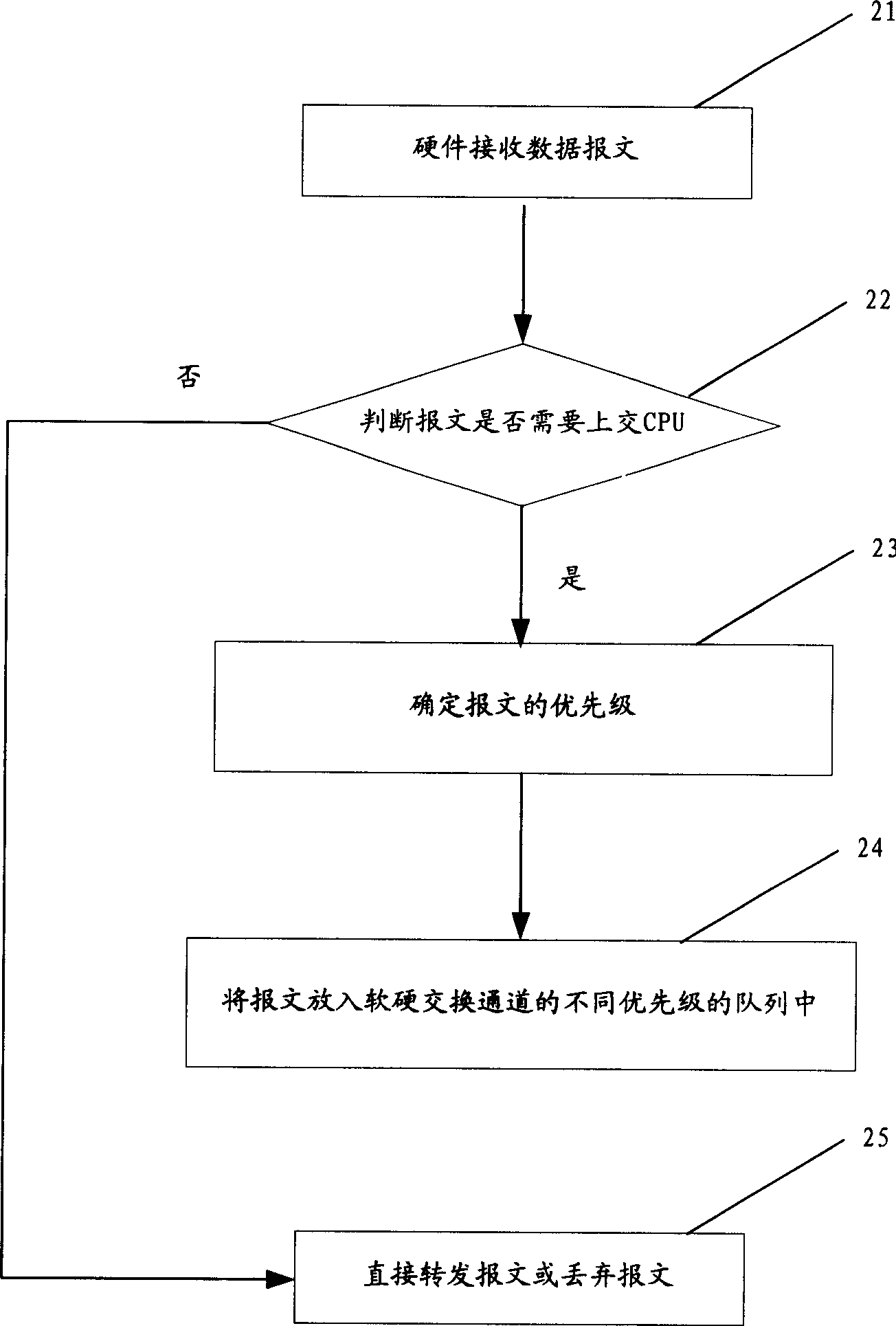
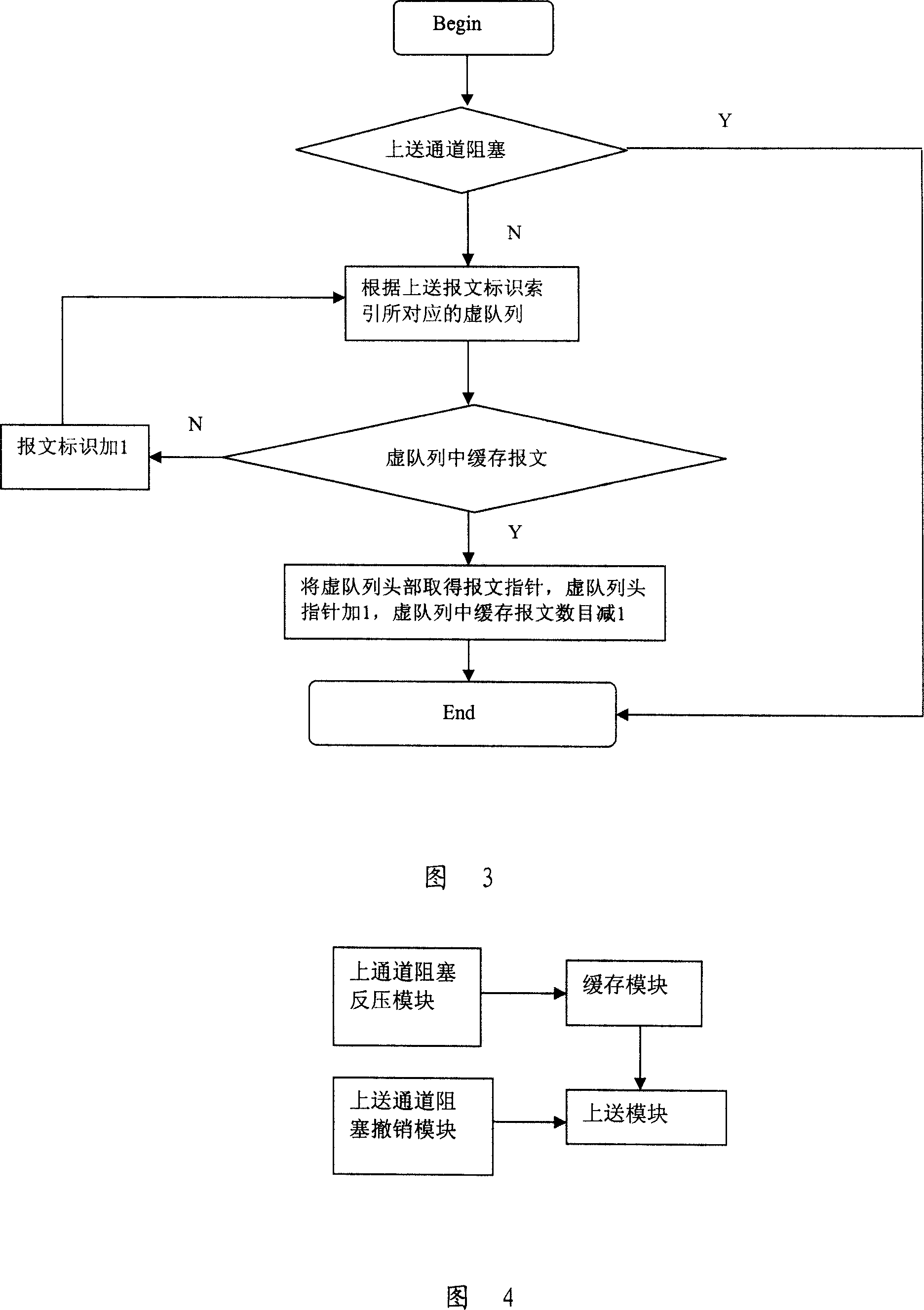
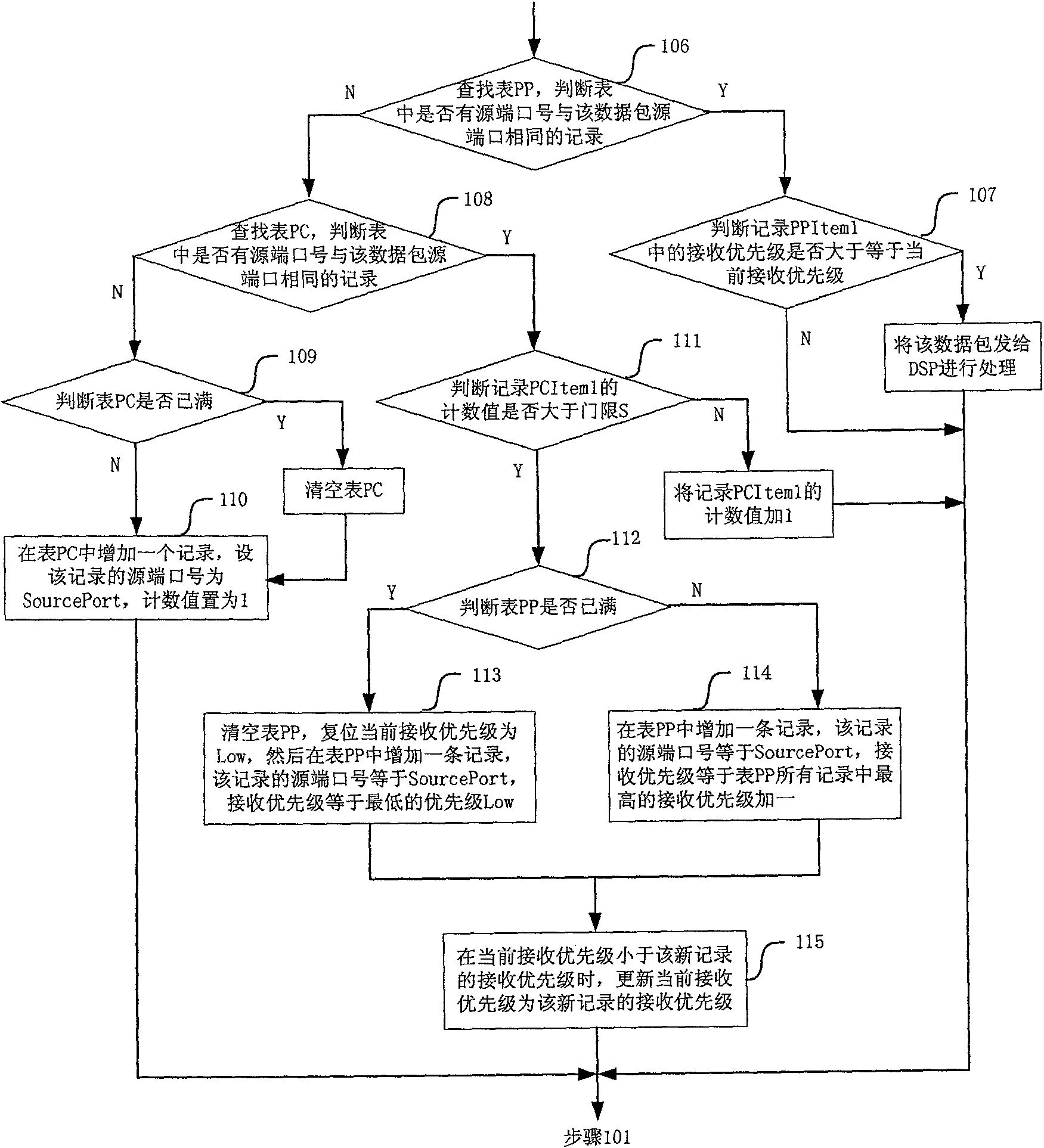
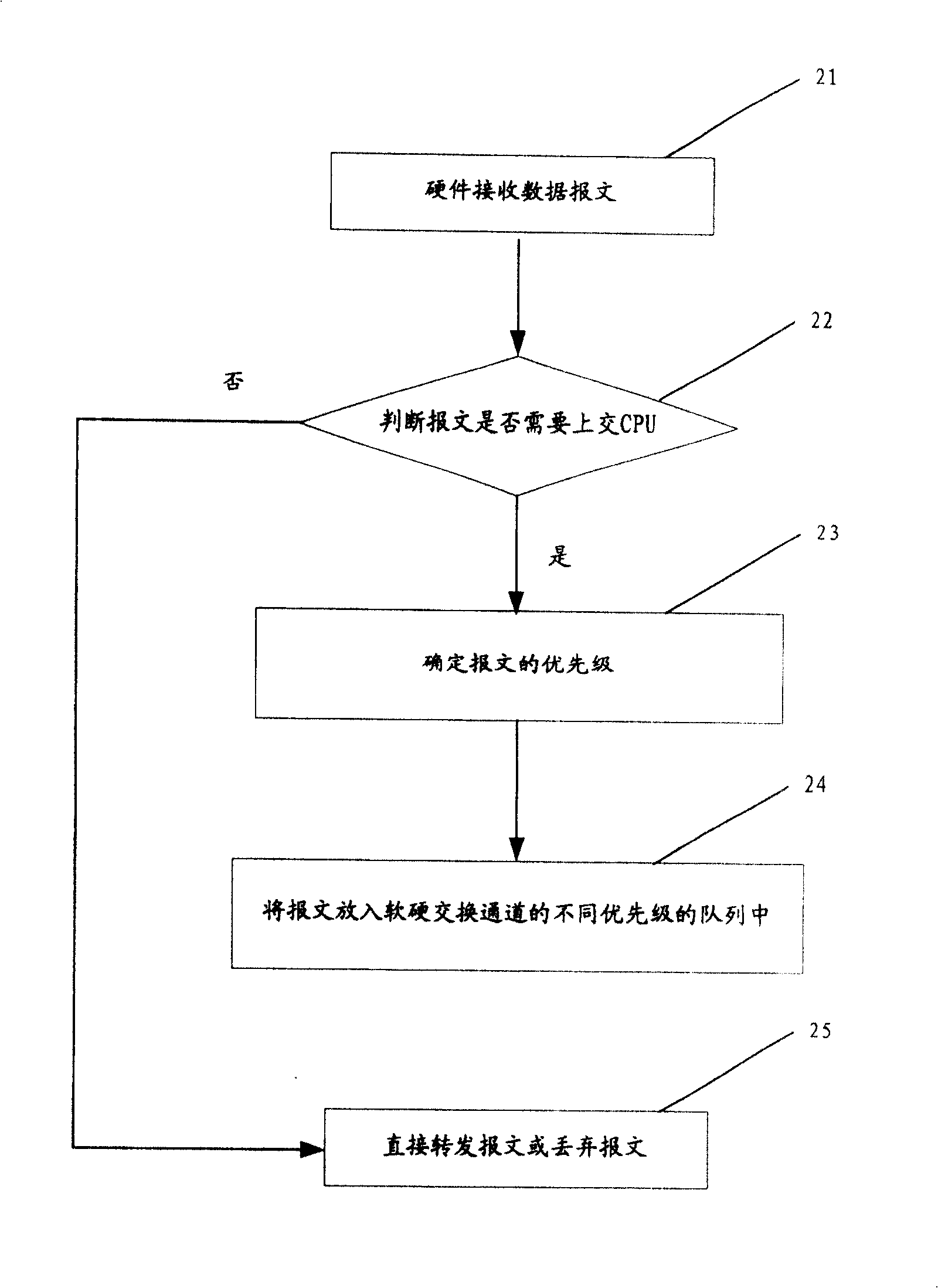
A method for raising network safety by utilizing message treatment includes placing message in buffer queue with relevant priority level and at channel between central processing unit and hardware retransmission plane separately according to priority level of message, carrying out treatment on message in buffer queue by central processing unit according to dispatch rule, carrying out treatment on message not required to be processed by control processing unit according to property of message and identifying those message according to specific rule for raising antiattack ability of network device.
Owner:北京知方知识产权管理有限公司
Hierarchical bus encryption system
ActiveCN105790927AImprove securityImprove speed performanceAcutation objectsSynchronising transmission/receiving encryption devicesBus encryptionComputer module
The invention relates to the technical field of system security, and especially relates to a hierarchical bus encryption system. The system is used for solving the problems that data transmission of a security module and an ordinary module is not physically isolated and buses are not utilized reasonably and fully according to the security of each module. The system comprises at least two buses of a first bus and a second bus, an encryption and decryption system corresponding to each bus, at least one signal processing module corresponding to each bus, and a bus converter coupled between the first bus and the second bus. Through adoption of the system provided by the embodiment of the invention, the data transmitted on the buses is encrypted data, even through an attacker obtains the bus data through a probe attack, a secret key is difficult to break, and the anti-attack capability of the system can be improved.
Owner:HUAWEI TECH CO LTD
Message retransmitting method and apparatus
ActiveCN101022414AImprove attack defense capabilityData switching networksComputer hardwareChannel use
Owner:HUAWEI TECH CO LTD
Method, apparatus, device and system for recognizing attack source information
InactiveCN108040039AImprove the ability to defend against attacksImprove attack defense capabilityTransmissionBlacklisting
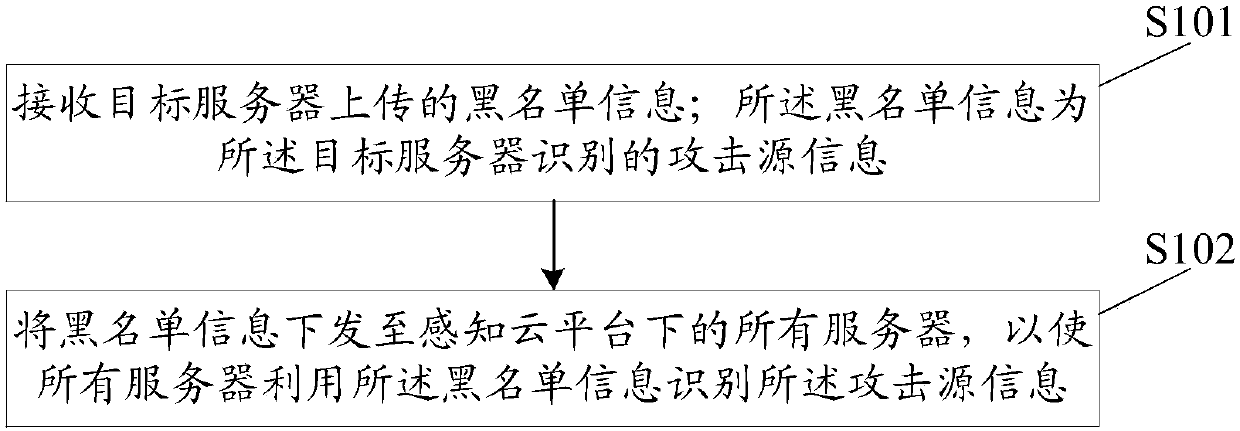
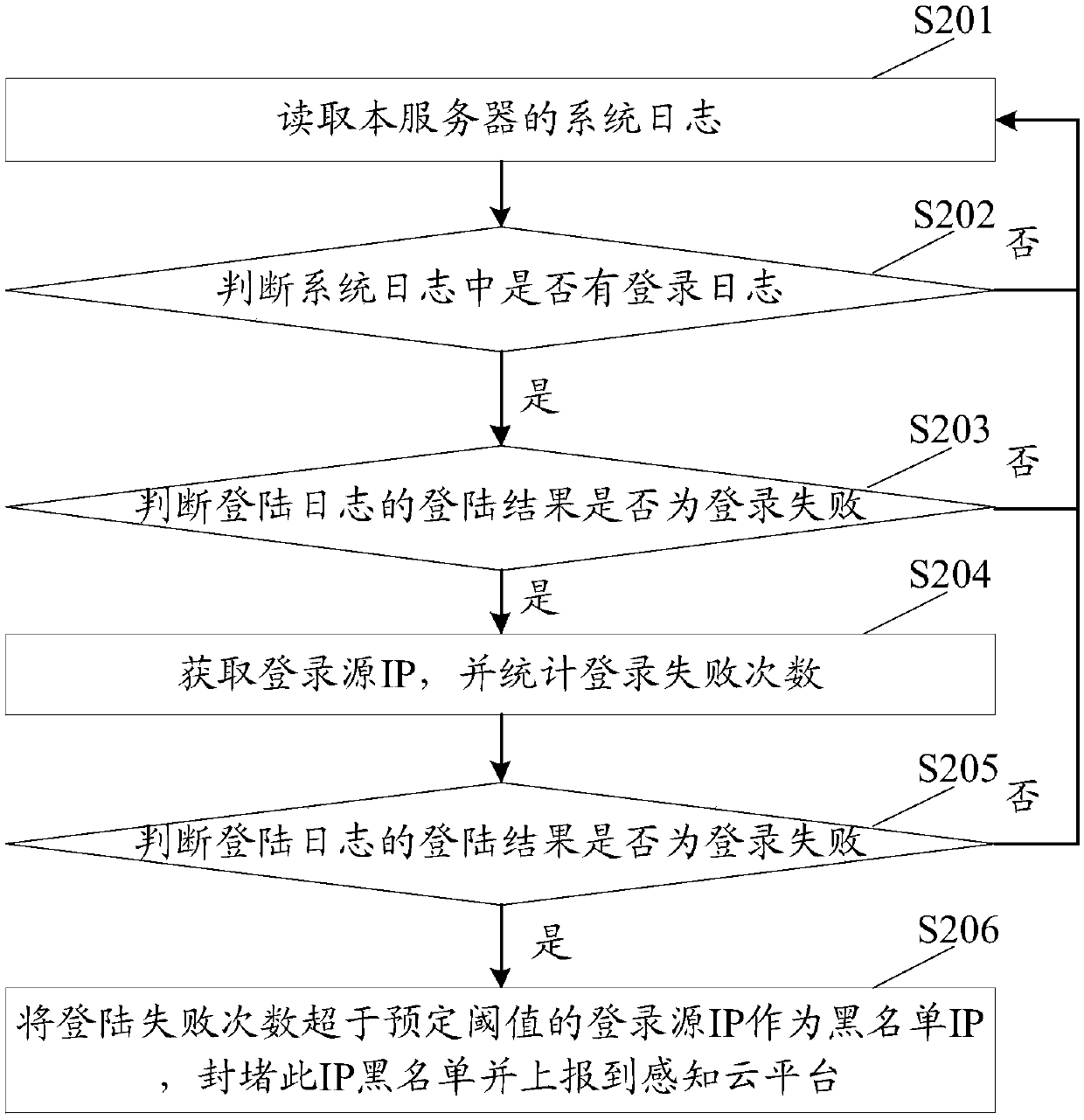
The invention discloses a method for recognizing attack source information, and the method comprises the following steps: receiving blacklist information uploaded by a target server, wherein the blacklist information is attack source information recognized by the target server; issuing the blacklist information to all the servers under a sensing cloud platform, and thereby enabling all the serversto recognize the attack source information through the blacklist information. Obviously, in the scheme, after the target server recognizes the attack source information and generates the blacklist information, the blacklist information is uploaded to the sensing cloud platform, the sensing cloud platform issues the blacklist information to all the servers under the platform, thus, the other servers are enabled to improve capability of defensing attacks, and a complete ecological chain is formed; and the invention also discloses an apparatus, a device and a system for recognizing attack sourceinformation and a computer readable storage medium, which also can realize the effects above.
Owner:SANGFOR TECH INC
Satellite mobile communication terminal user identification and authentication method
InactiveCN103686705ALess chance of human attackImprove securityNetwork topologiesSecurity arrangementTelecommunicationsSatellite mobile communication
The invention discloses a satellite mobile communication terminal user identification and authentication method. The mobile communication terminal is based on a Beidou satellite system. The test method comprises the authentication mechanism and the encryption mechanism, wherein the authentication mechanism comprises the following steps: a public key is sent by a sender to a receiver, and a private key is saved by the sender; encryption is performed on data by the sender with the private key, and signed data is added; and verification and authentication are performed on the data by the receiver with the public key of the sender, and decryption is performed after the authentication is successful to obtain the data; and the encryption mechanism comprises the following steps: the public key is sent by the sender to the receiver, and the private key is saved by the sender; encryption is performed on data by the sender with the private key, and complete content is added; and decryption is performed on the data by the receiver with the public key, and after the authentication is successful, the data integrity is verified. The method of the invention can be used to effectively prevent various phenomenons, such as stealing calling, embezzlement, secret divulging, etc., in which mobile communication resources and services are used illegally in satellite mobile communication, and ensure satellite mobile communication network safety and ensure the legitimate rights and interests of satellite mobile communication operators and users.
Owner:CHENGDU LINHAI ELECTRONICS
Communication method, device and system, readable storage medium and computer device
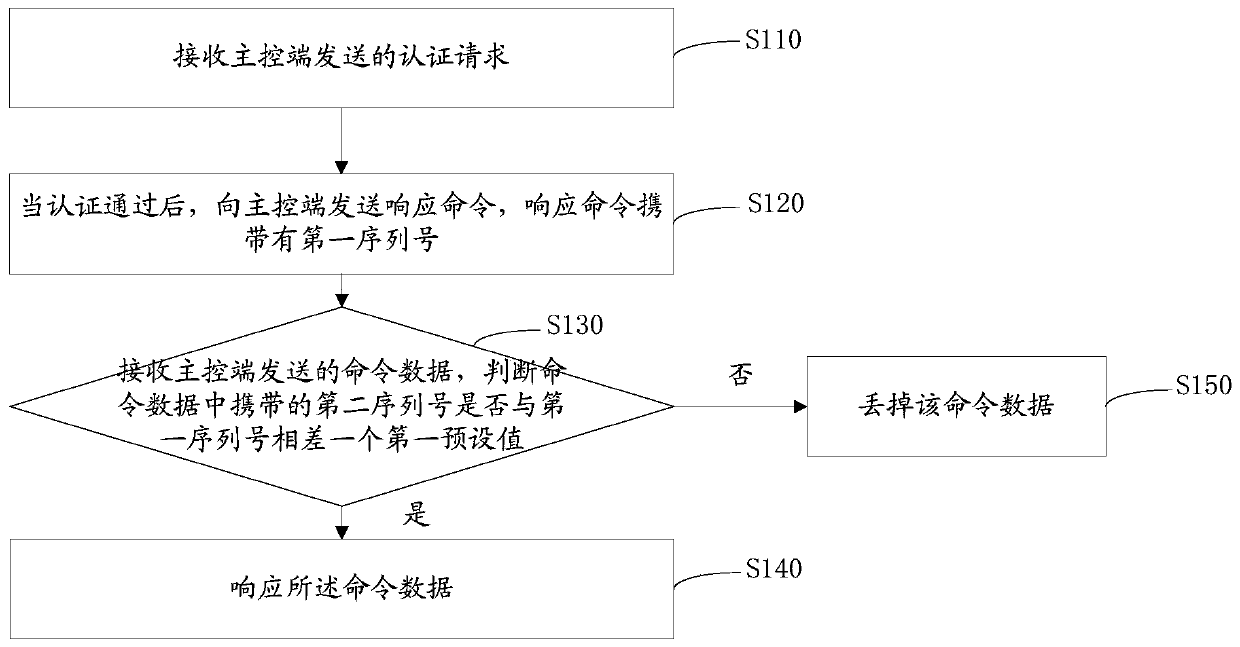
InactiveCN110572391AImprove attack defense capabilityImprove experienceTransmissionNetwork packetIntelligent equipment
The invention is applicable to the field of smart home, and provides a communication method, device and system, a readable storage medium and a computer device. The method comprises the following steps: receiving an authentication request sent by a main control end; after the authentication is passed, sending a response command to the main control end, wheein the response command carries a first serial number; receiving command data sent by the main control end, judging whether a second serial number carried in the command data is different from the first serial number by a first preset valueor not, and obtaining the second serial number through the first serial number and the first preset value; and if the judgment result is yes, responding to the command data. By dynamically changing the unique sequence value, the anti-attack capability of the intelligent equipment is provided, illegal data packets can be filtered out, and the security and the user experience are improved.
Owner:BULL GRP CO LTD
Satellite mobile communication terminal user identification and authentication function test method
InactiveCN103686803APrevent copyingPrevent tamperingSecurity arrangementInformation transmissionPassword
The invention discloses a satellite mobile communication terminal user identification and authentication function test method. The method comprises the following steps: a pulse digital signal is sent to an UIM card by a DSP in a timing manner; the received pulse digital signal is detected by the UIM card, if a pulse digital signal sequence code error occurs, then reset is performed directly, and connection is reestablished at the interval of a set time; the public key of an authorized user is saved by the UIM card, and the private key of the authorized user is saved by the DSP; after the password of the authorized user is received by the DSP, decryption is performed on the private key, and then signing is performed on an opening instruction with the private key and the signed data is sent to the UIM card; and after the data is received by the UIM card, authentication is performed on the opening instruction with the public key, and only after the authentication is successful, the information data can be read and a corresponding operation is entered. The method of the invention can be used to reliably verify and ensure the satellite mobile communication terminal user identification and authentication function and effectively prevent the stealing and damage of illegal users on wireless channels and information thereof so as to ensure the safety of information transmission.
Owner:CHENGDU LINHAI ELECTRONICS
Image processing method and device, image classification method and device, medium and electronic equipment
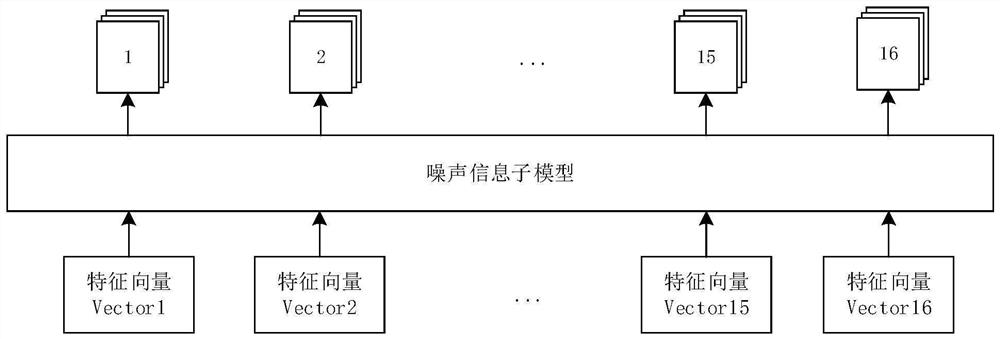
PendingCN114120364AImprove accuracyImprove robustnessBiometric pattern recognitionNeural architecturesFeature vectorImaging processing
The invention relates to an image processing method and device, an image classification method and device, a medium and electronic equipment. The image processing method comprises the steps of receiving a to-be-processed image; according to the to-be-processed image and an image processing model, a noise image corresponding to the to-be-processed image is determined, the image processing model comprises an image feature extraction sub-model and a noise information sub-model, and the image feature extraction sub-model is used for obtaining feature vectors of the to-be-processed image; the noise information sub-model is used for determining a noise image of the to-be-processed image according to a feature vector of the to-be-processed image, the image processing model in the training process further comprises a classification sub-model, and the loss of the image processing model is determined based on the noise vector added by the noise information sub-model and classification probability distribution output by the classification sub-model; according to the to-be-processed image and the noise image, a target image corresponding to the to-be-processed image is generated, and the to-be-processed image and the target image are the same in corresponding classification.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Method and system for secure application of machine learning model
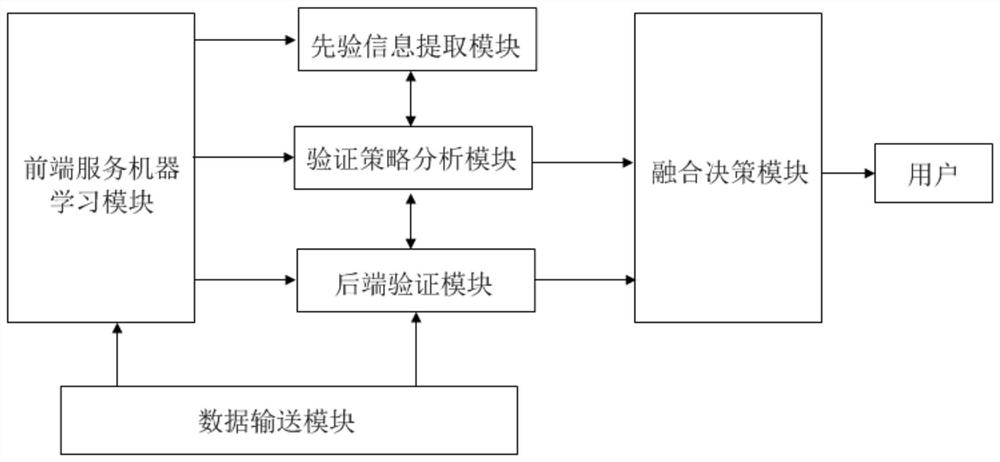
ActiveCN110837527BImprove verification conditionsImprove application securityDigital data information retrievalMachine learningPrior informationAlgorithm
The invention discloses a safe application method and system of a machine learning model. The method includes steps such as front-end service model processing, prior information extraction, verification strategy analysis, back-end verification module processing, and fusion decision-making. The back-end verification and the front-end service machine learning service model of the present invention are relatively independent, and the anti-attack ability can be enhanced through the separation of module functions, and the application security of the machine learning model can be improved; the back-end verification supports the multi-dimensional back-end of inherent attributes and external information Verification, the verification method is more comprehensive and stricter, and is suitable for the definition of verification strategies for various types of machine learning tasks. For the processing results of the front-end service machine learning model, the influence coefficient of the main feature can be defined, and the verification strategy can be flexibly formulated according to the influence coefficient. It is suitable for application scenarios of various machine learning models, and has good flexibility and versatility.
Owner:深圳市乾数科技有限公司
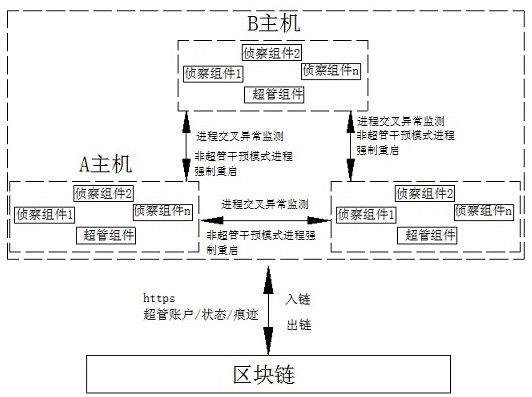
Method for realizing decentralized distributed process guarding based on ad hoc network technology
ActiveCN111835872AEnsure credibleImprove attack defense capabilityEncryption apparatus with shift registers/memoriesDigital data protectionFailoverEngineering
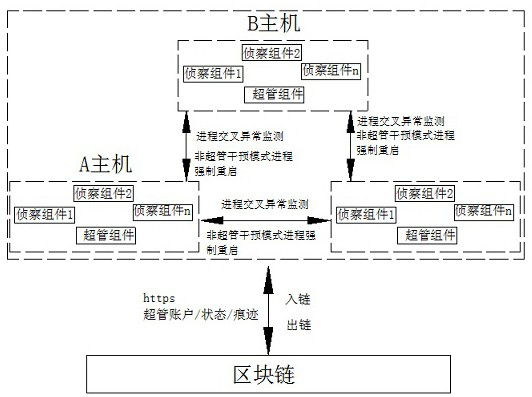
The invention relates to a method for realizing decentralized distributed process guarding based on an ad hoc network technology, which comprises the following steps of: generating a super-tube identity, authority and guarding strategy file through a creation module, and safely storing the file in each guarding node and system process: 1, perpetual motion guarding without external force intervention, and 2, iteratively updating / newly adding nodes in the process; the super administrator performs external force intervention and redeployment, and perpetual motion guards are started after deployment is completed and the super administrator intervention mode exits; and basic services of mutual monitoring, failover and takeover, message broadcasting and communication are started. The credible decentralized distributed process guarding system is constructed by utilizing an original ad hoc network technology and is used for avoiding the problem of failure of system process guarding capabilitycaused by a single-point fault of a guarder; meanwhile, the protection range can be expanded from a single machine to all hosts in the whole domain, the anti-attack capability of the whole protectionsystem is improved, and the credibility of the protection system is ensured.
Owner:江苏开博科技有限公司 +1
Method and apparatus for processing packets
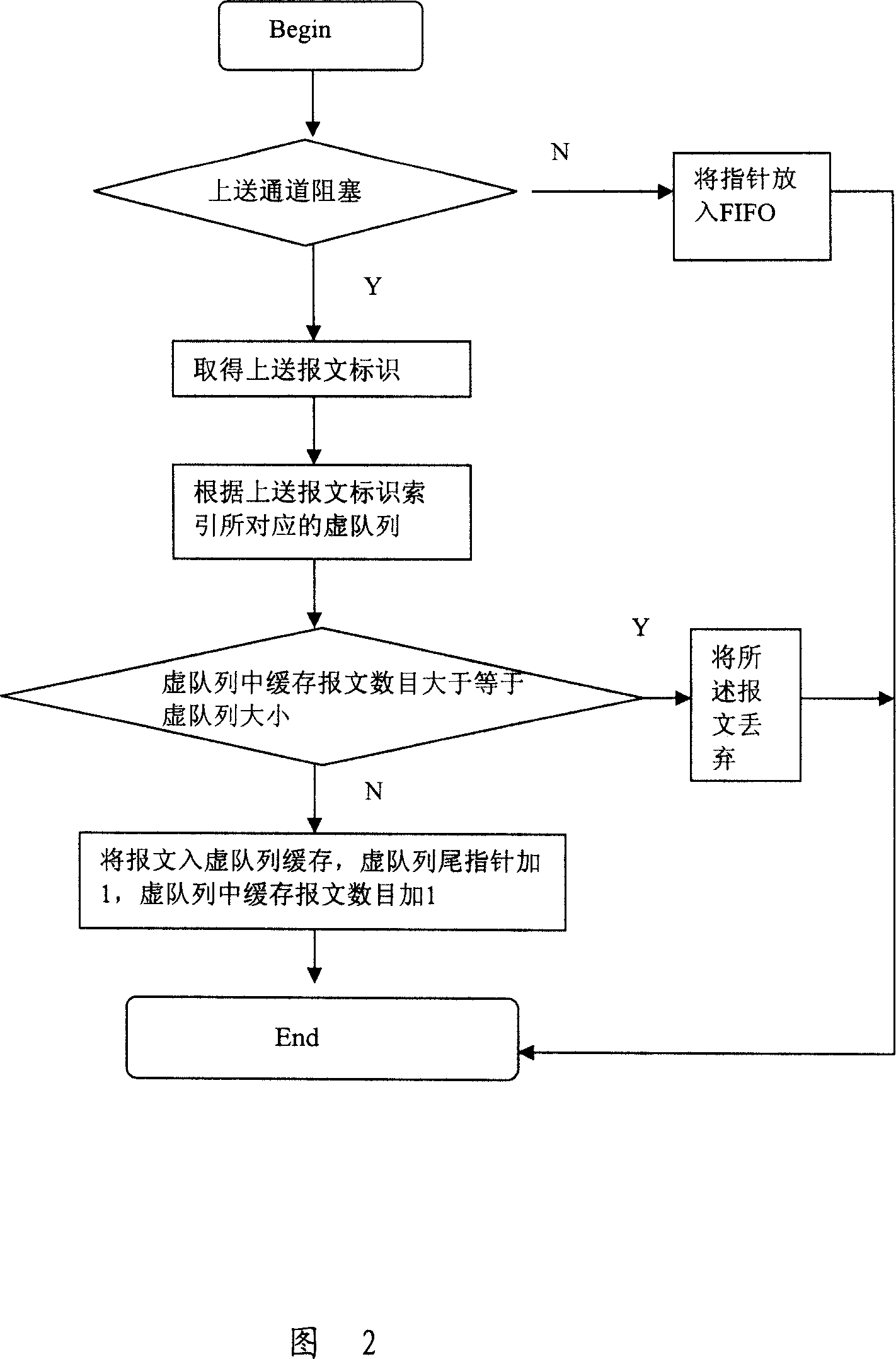
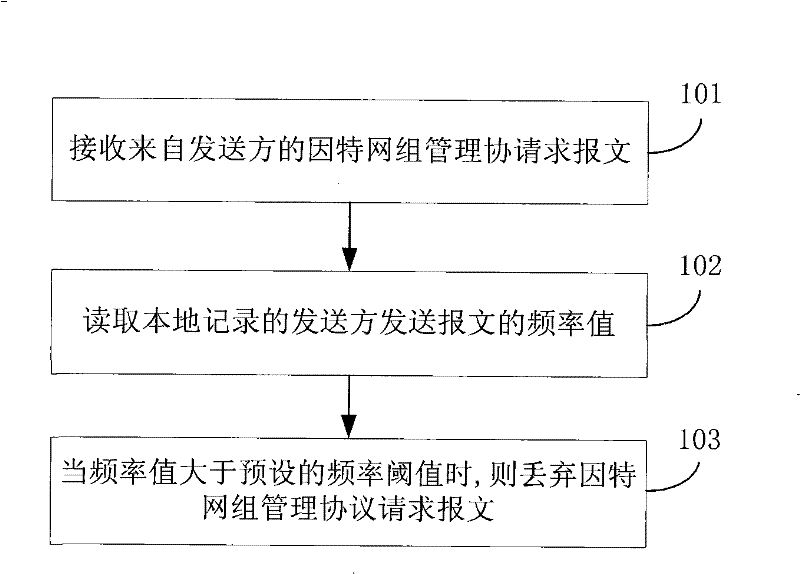
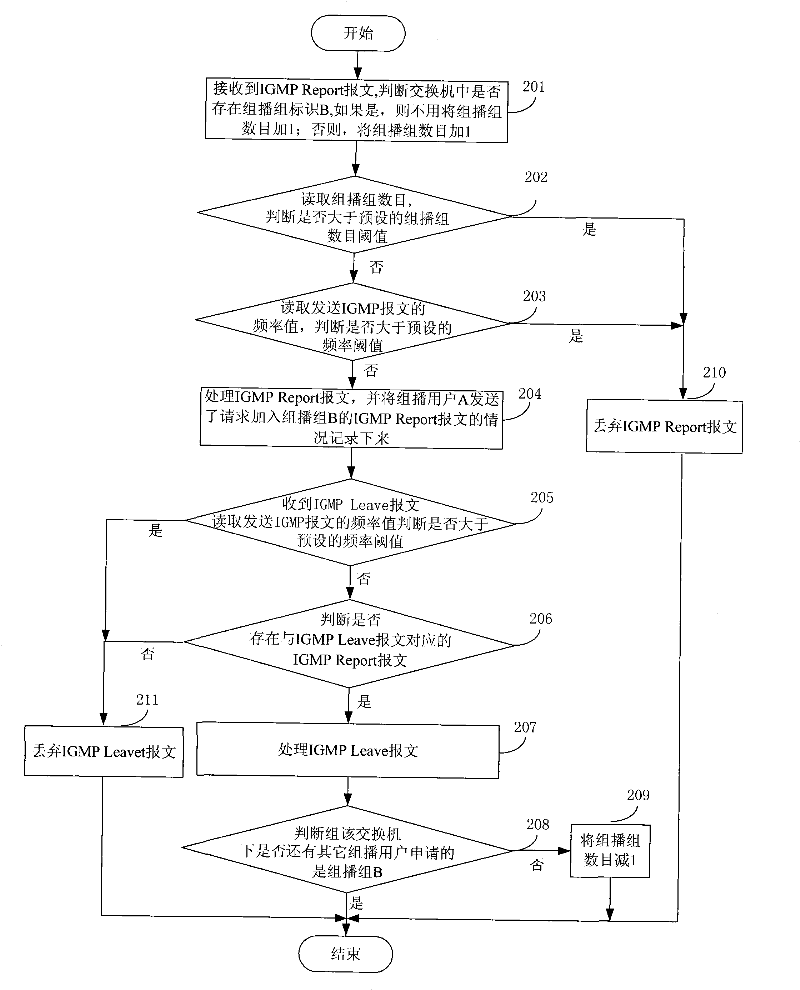
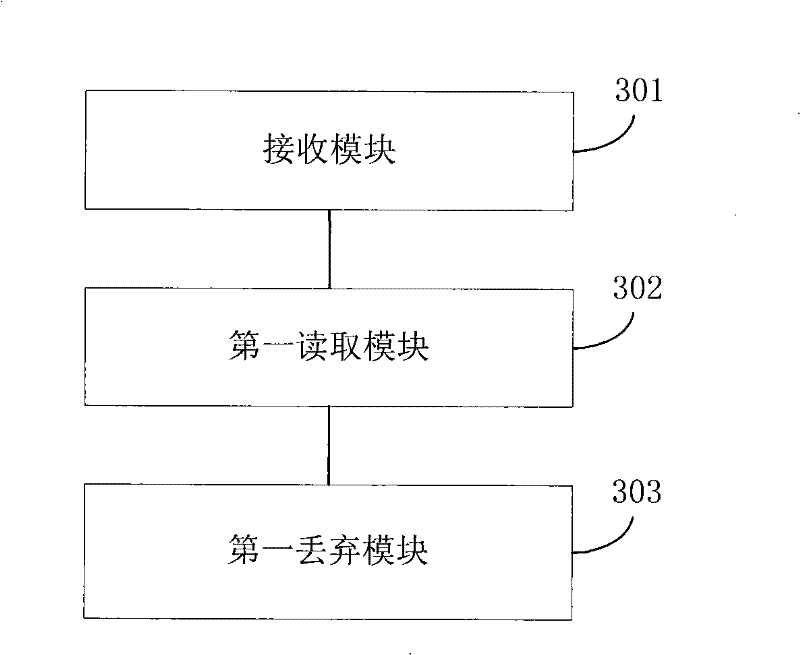
InactiveCN101478542BImprove attack defense capabilityImprove reliabilitySpecial service provision for substationComputer hardwareThe Internet
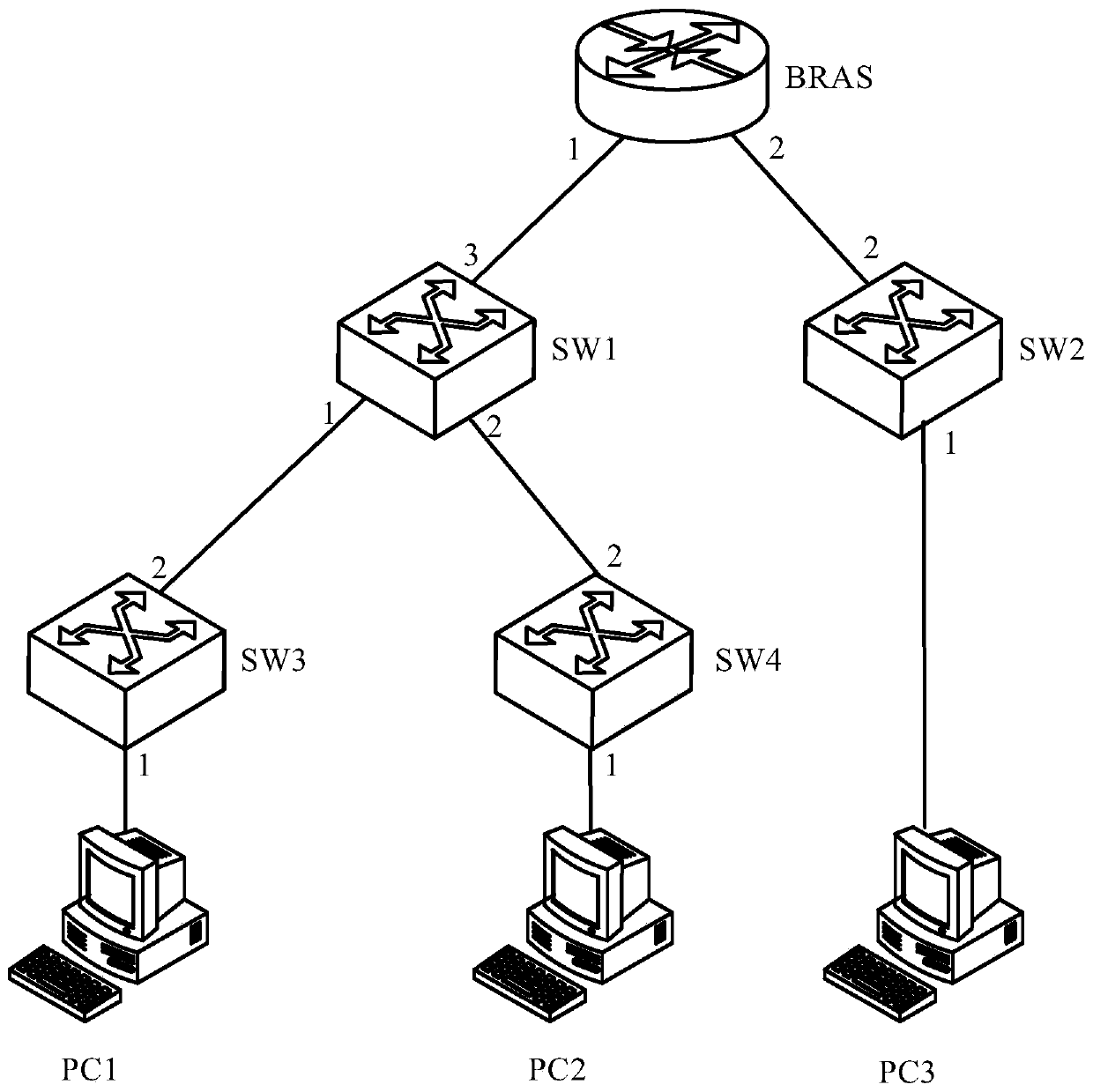
The invention discloses a method and an apparatus for processing messages belonging to the communication field. The method comprises: receiving an internet group management protocol (IGMP) request message from a sender; reading a local recording frequency value of sending message from the sender; discarding the internet group management protocol request message when the frequency value is larger than a presetting frequency threshold. The apparatus comprises: a receiving module, a first reading module and a first discarding module. The invention enables an exchange not to have a plurality of IGMP messages by discarding IGMP messages larger than the frequency threshold, improves the anti-attack ability of the exchange, avoids the IGMP messages attack to the exchange, and protects the exchange. Moreover the invention also solves the problem that a multicast client attacks by frequently adding the IGMP messages between different cast groups or sending the IGMP messages when leaving through discarding the IGMP messages larger than the frequency threshold.
Owner:HUAWEI TECH CO LTD
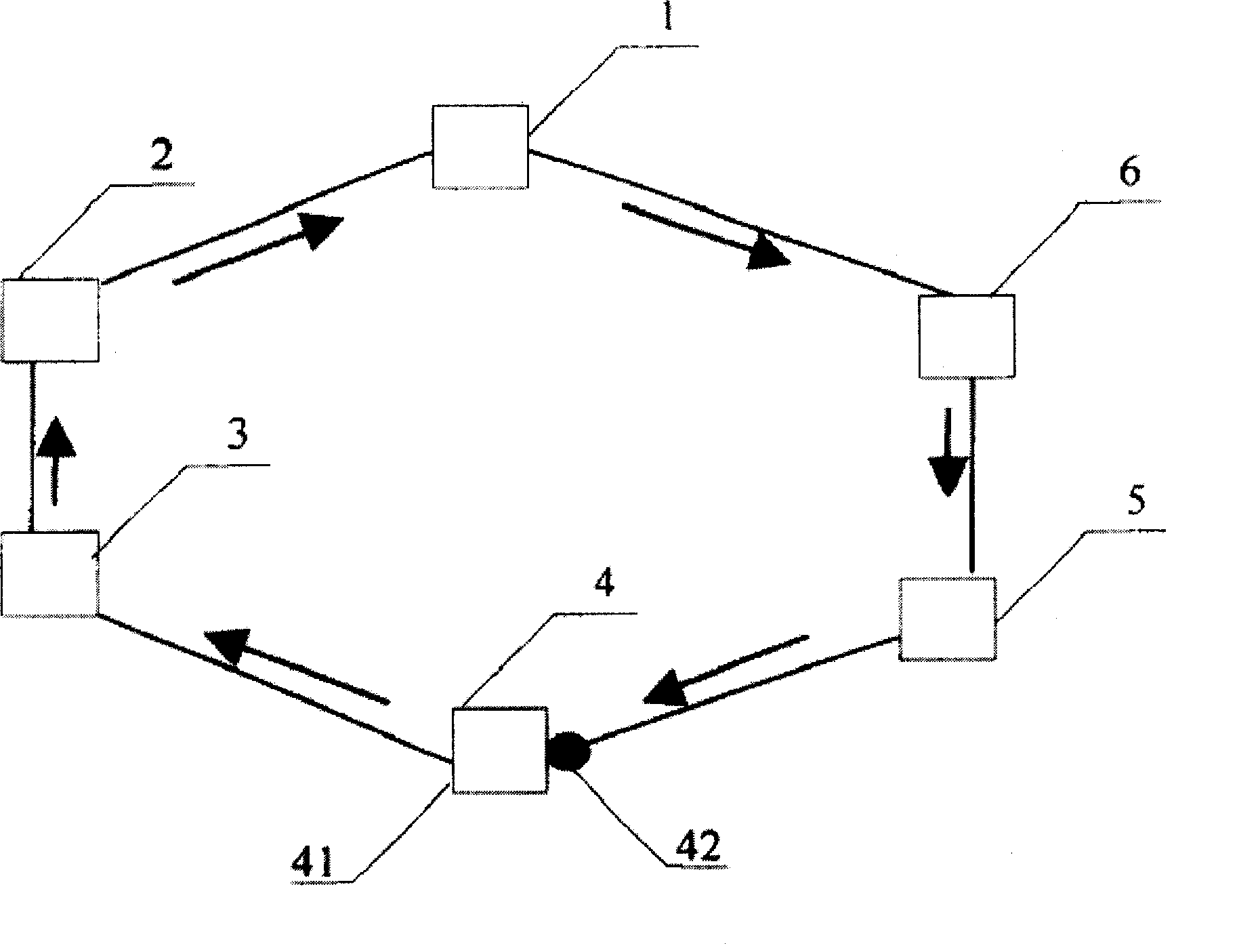
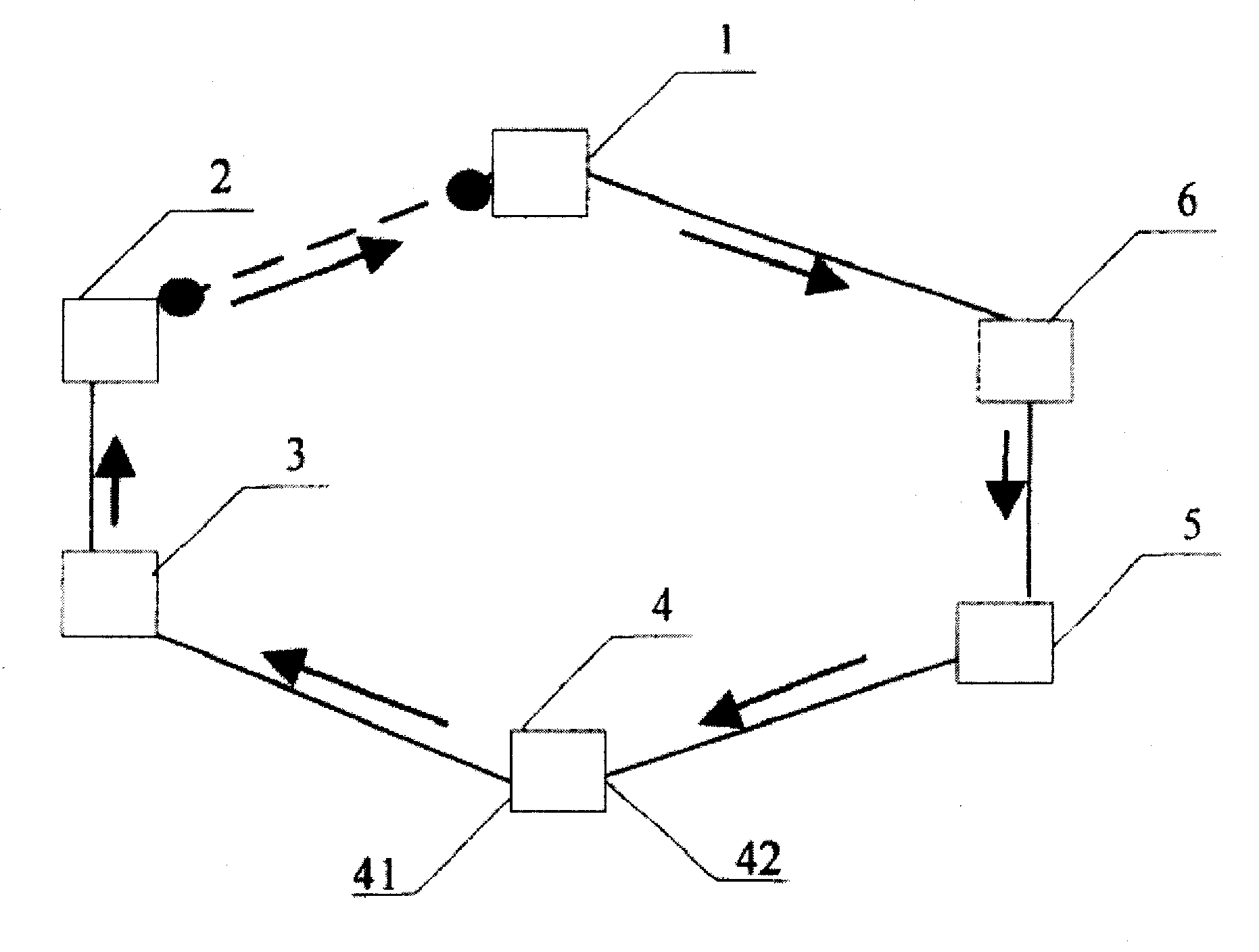
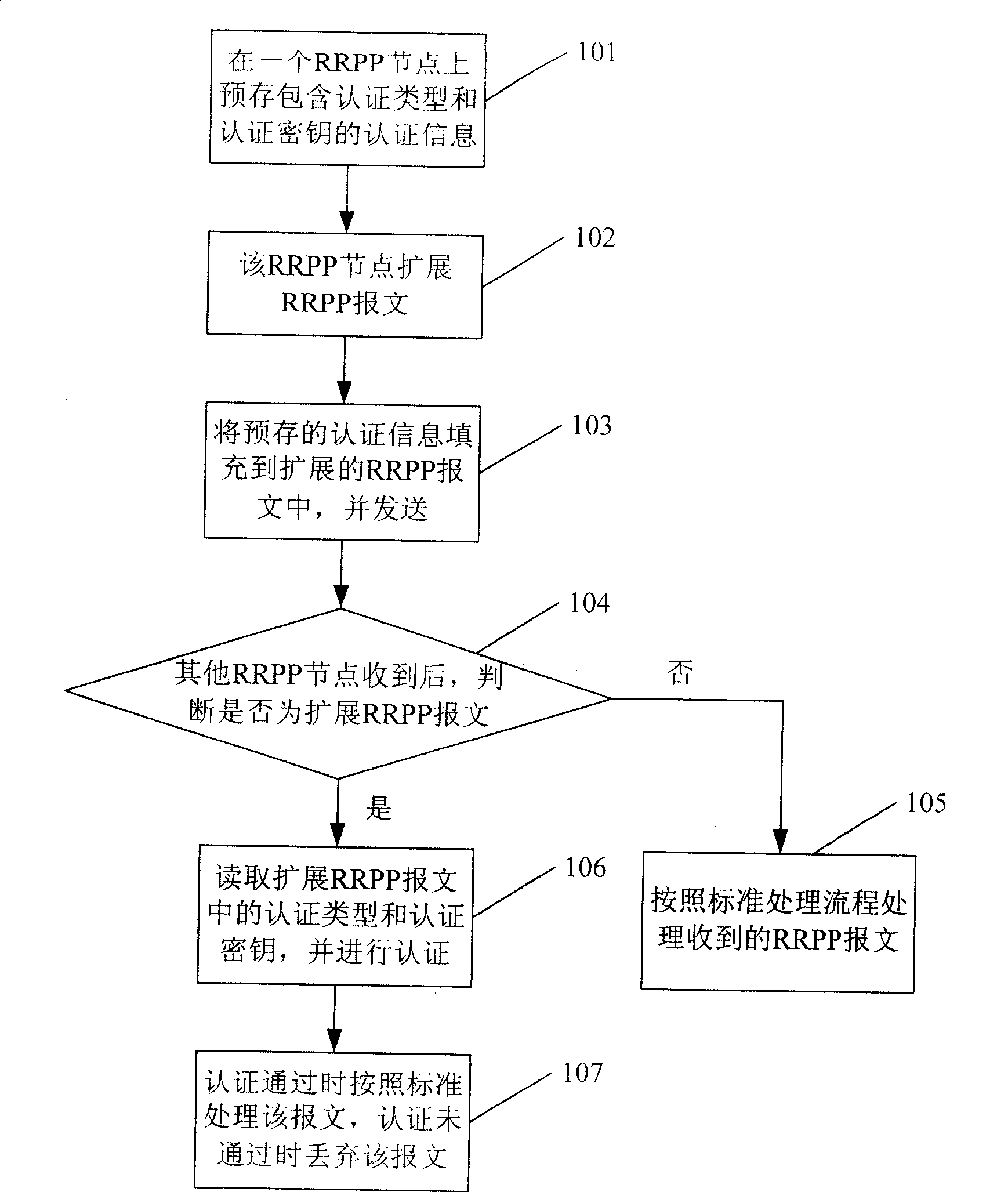
Fast ring network method against attack based on RRPP, apparatus and system
InactiveCN100466583CImprove attack defense capabilityAvoid attackTelevision system scanning detailsModulated-carrier systemsComputer moduleRing network
The method comprises: receiving the PRPPP message carrying authentication; reading out the authentication message in PRPPP message; comparing it with the local authentication information; if they are identical, then processing the PRPPP message; otherwise, abandoning the PRPPP message. The device thereof comprises: a PRPPP message receiving module carrying the authentication information; a PRPPP message processing module for reading and processing the PRPPP message. The system thereof comprises: a first node for sending the PRPPP message carrying the authentication message and a second node for receiving, reading and processing the PRPPP message.
Owner:苏师大半导体材料与设备研究院(邳州)有限公司
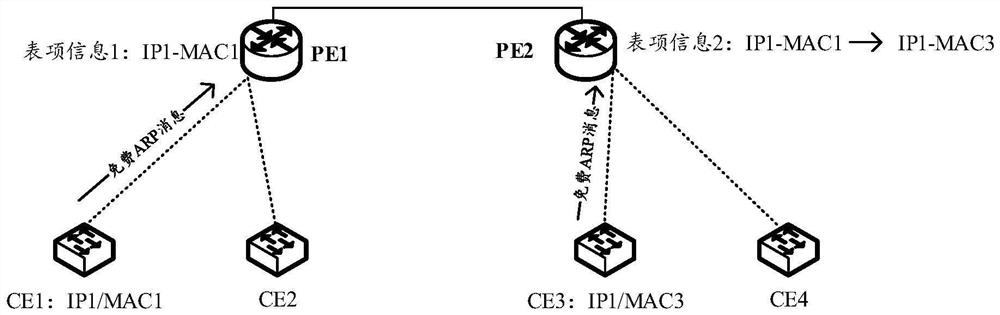
Address conflict processing method and device and storage medium
The invention discloses an address conflict processing method and device and a storage medium, and belongs to the technical field of communication. The method is applied to an EVPN and comprises: a first PE device receiving a second MAC / IP Advertent route sent by a second PE device, and the second MAC / IP Advertent route comprising second table item information; when the first PE equipment determines that the second IP address is the same as the first IP address, determining that the second table entry information conflicts with first table entry information stored in the first PE equipment; and when the first PE device determines that the number of conflicts between the second table entry information and the first table entry information is greater than or equal to a conflict number threshold in the first period, not sending the first MAC / IP Advertisement route to the second PE device. According to the method and the device, occupation of network resources can be reduced in a table entry information conflict scene, and the network anti-attack capability can be improved.
Owner:HUAWEI TECH CO LTD
Vehicle data message secure communication method
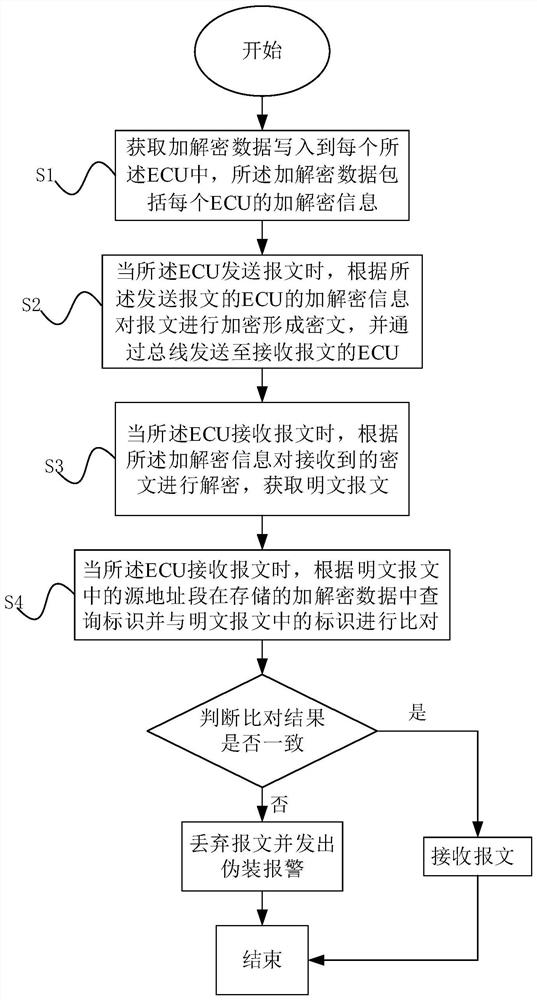
PendingCN114422181AImprove securityAvoid the risk of eavesdroppingKey distribution for secure communicationBus networksData packSecure communication
The invention relates to a vehicle data message safety communication method which is used for communication of ECUs of a vehicle, the ECUs of the vehicle are communicated through a communication bus, the method comprises the following steps that encryption and decryption data are obtained and written into each ECU, and the encryption and decryption data comprise encryption and decryption information of each ECU; when the ECU sends a message, encrypting the message according to the encryption and decryption information of the ECU sending the message to form a ciphertext, and sending the ciphertext to the ECU receiving the message through a bus; and when the ECU receives the message, decrypting the received ciphertext according to the encryption and decryption information to obtain a plaintext message. Compared with the prior art, the method has the advantage of effectively preventing vehicle message eavesdropping, playback attacks and camouflage attacks.
Owner:ZHEJIANG GEELY HLDG GRP CO LTD +1
A mobile communication method and system for the internet of things
ActiveCN109150899BAdd transit centerImprove securityTransmissionSecurity arrangementCommunications securityCiphertext
The invention relates to the technical field of internet of things communication safety, in particular to an internet of things mobile communication method and system, wherein the internet of things mobile communication method comprises the steps that a transfer center receives first encryption information; the transfer center decrypts the first encrypted information and integrity check accordingto a pre-stored first encryption key and a first integrity key to obtain plaintext information; the transfer center encrypts the obtained plaintext information according to a pre-stored second encryption key and a second integrity key to generate second encryption information; the transfer center sends the second encrypted information to a second mobile terminal. According to the embodiment of theinvention, a data transfer center is added without changing the original network structure, so that the transmission of the data and the voice over the wireless network and the backbone network is protected by ciphertext, the integrity checking is improved, the safety of data and voice is greatly improved, and the anti-attack capability is improved.
Owner:HENGBAO
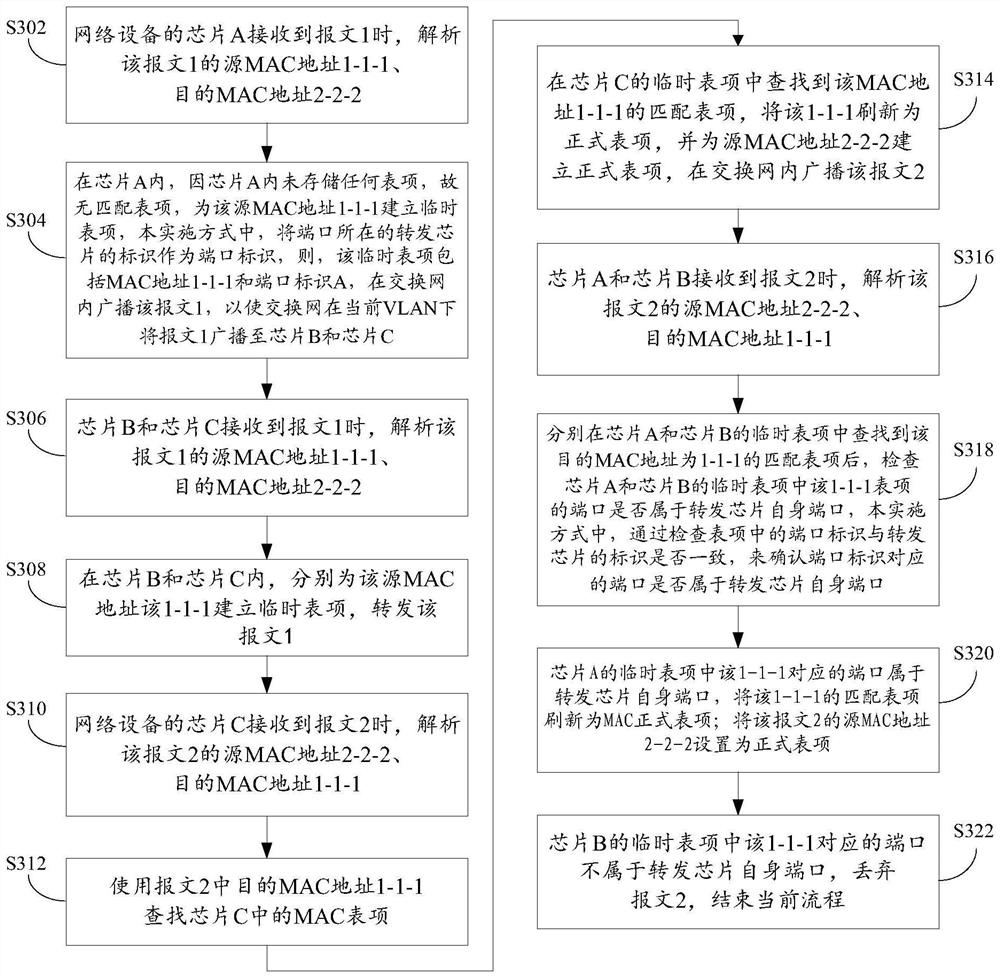
Anti-attack mac address learning method, device and network equipment
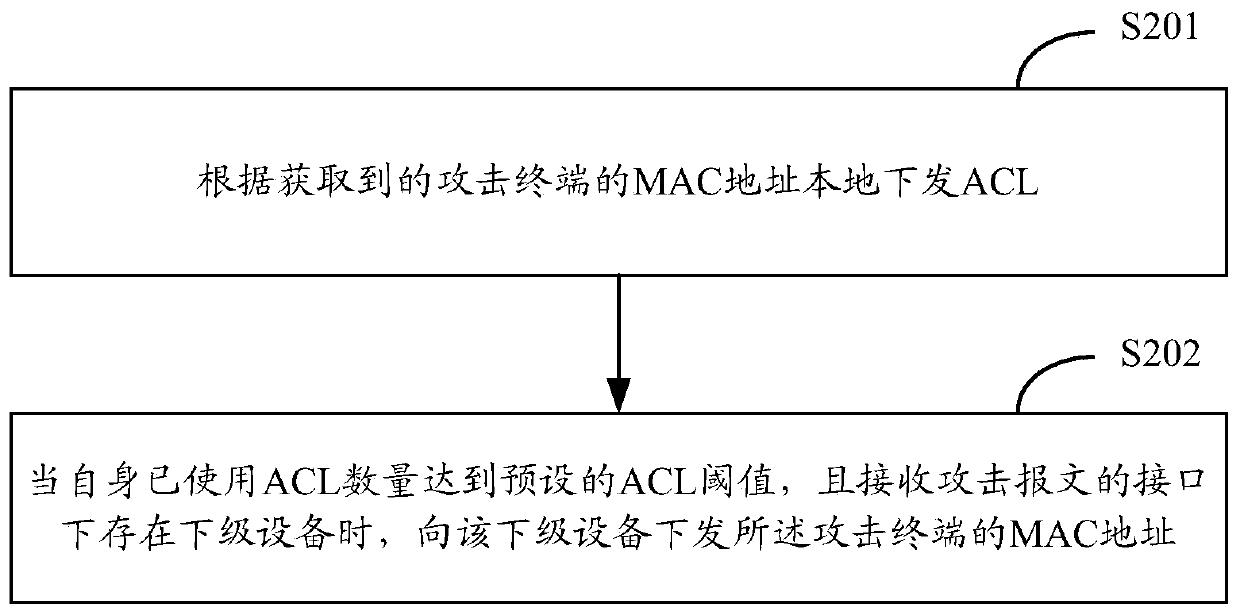
ActiveCN107547535BQuick deleteImprove attack defense capabilityTransmissionTheoretical computer scienceEngineering
Owner:XINHUASAN INFORMATION TECH CO LTD
Method for realizing decentralized distributed process guarding based on ad hoc network technology
ActiveCN111835872BEnsure credibleImprove attack defense capabilityEncryption apparatus with shift registers/memoriesDigital data protectionFailoverEngineering
Owner:江苏开博科技有限公司 +1
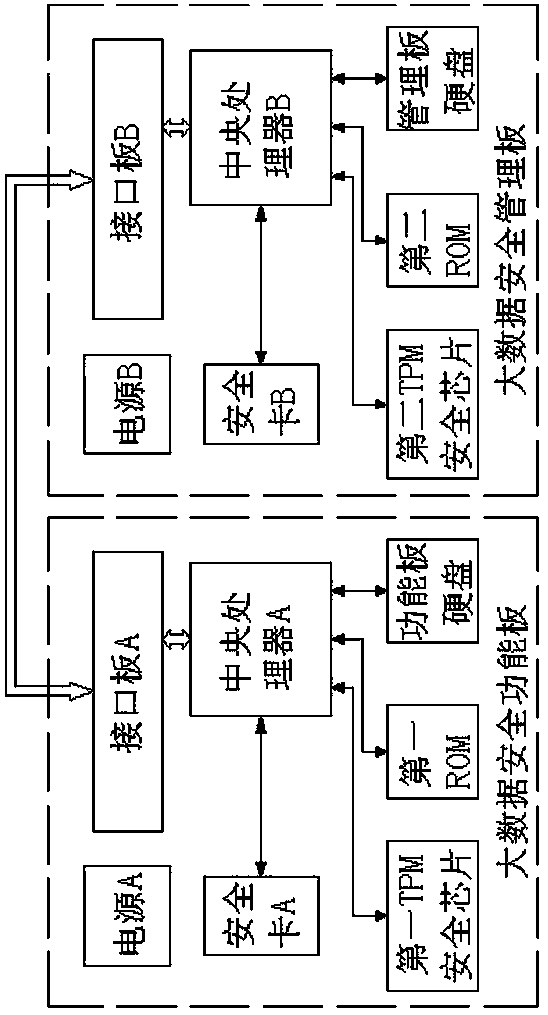
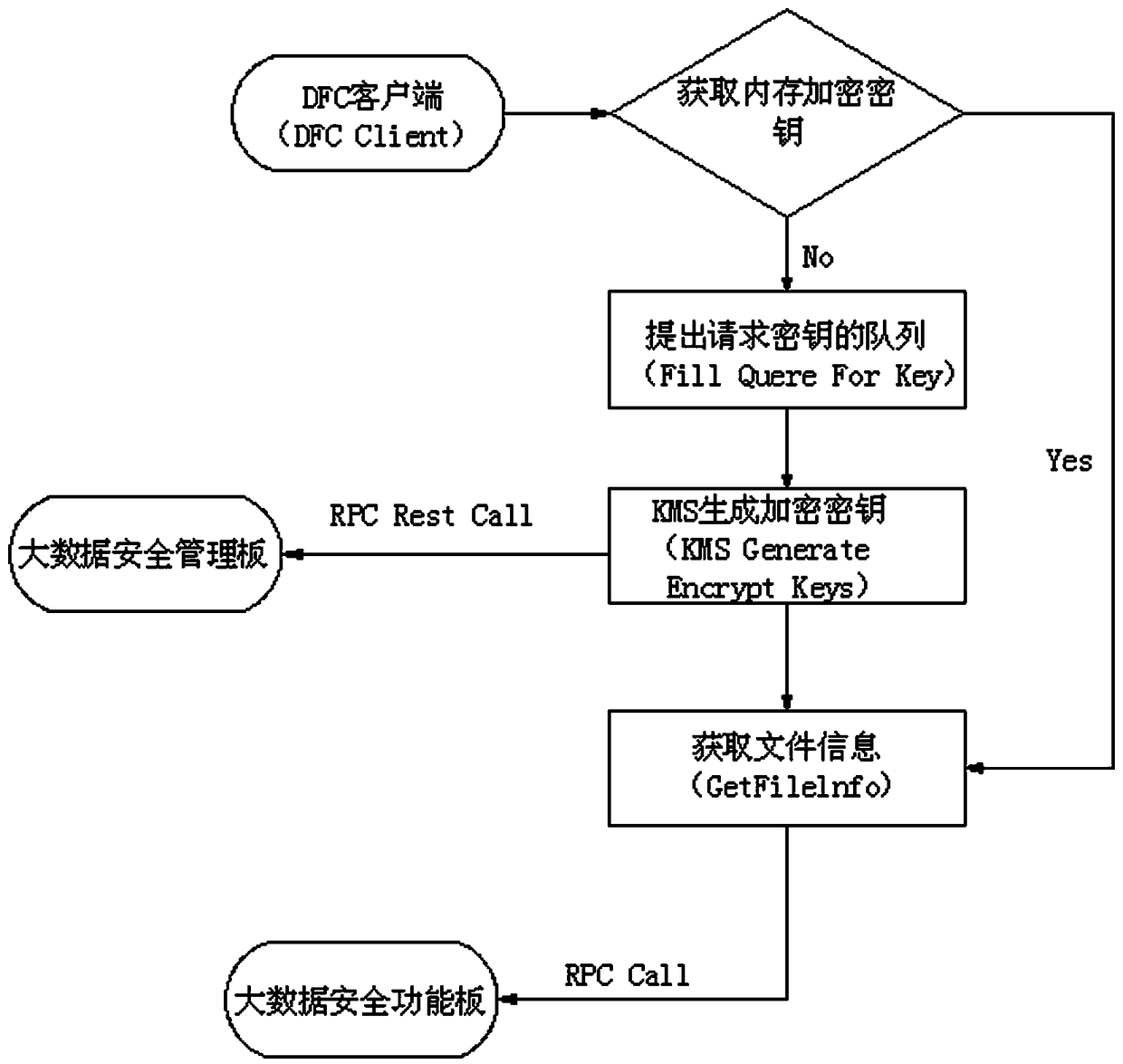
A way to achieve big data security
ActiveCN105426771BImprove securityImprove attack defense capabilityDigital data protectionData platformBig data security
The present invention discloses a method for realizing security of big data. The method comprises: a local cache will be accessed by a DFS for determining whether a data encryption key exists in data after the DFS client receives the data; if yes, acquiring a security file corresponding to the data with the data encryption key and transmitting a content into a safety function board of the bid data to perform security protection; if not, firstly requesting to generate the data encryption key; acquiring the security file corresponding to the data with the data encryption key by using a GetFileinfo; and transmitting the content of the security file into the safety function board of the big data to perform the security protection. According to the method for realizing security of the big data, a mode of performing security protection of the big data by using software and a network topology architecture is upgraded to directly use hardware protection; and a protection level is lifted to a hardware protection level from an original software protection level. Therefore, the capacity of a big data platform against an attack is greatly lifted and the security of the big data is effectively improved.
Owner:苏州比特信安科技有限公司
Watchdog feeding method for embedded Linux equipment with anti-attack capability and driving module
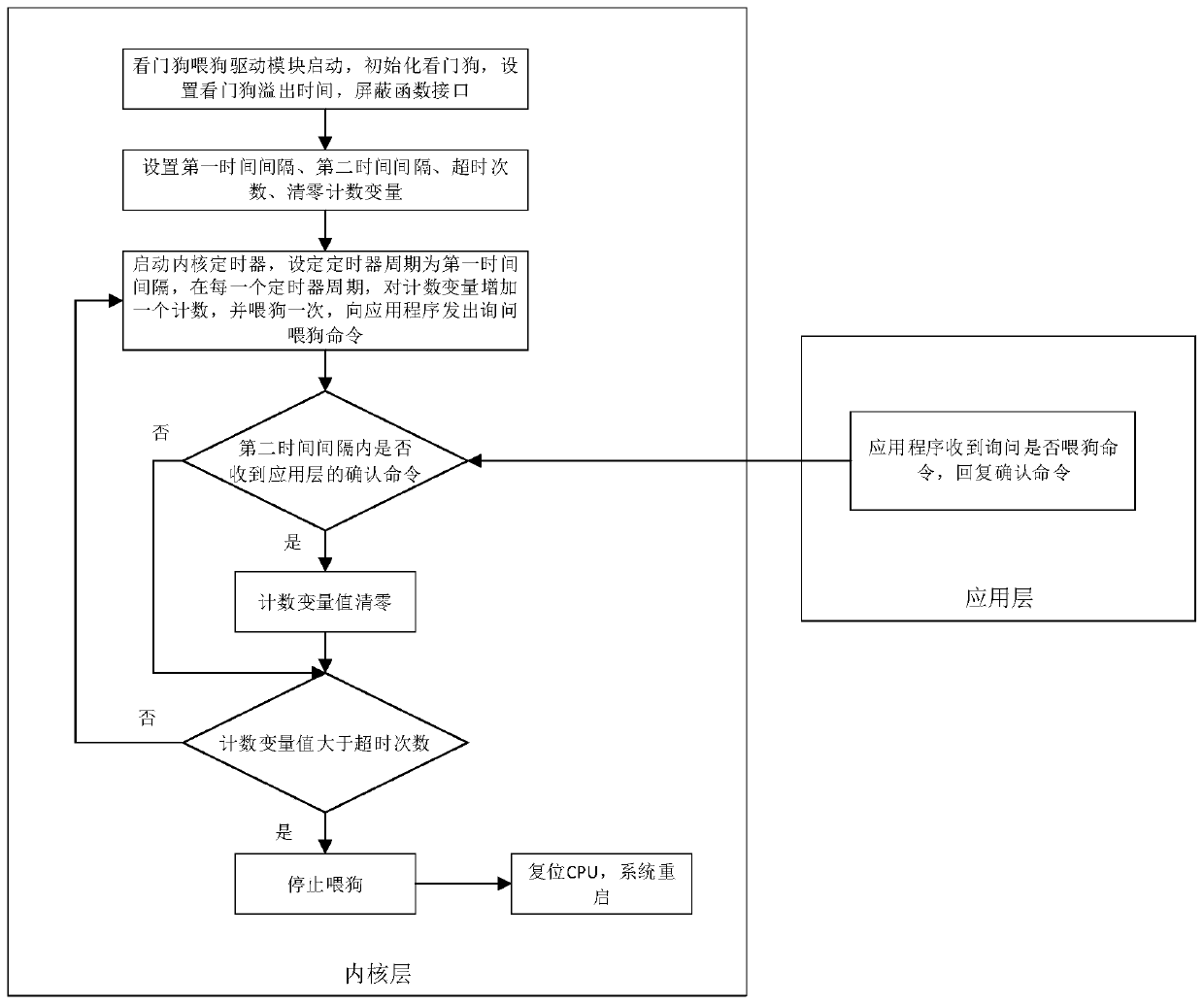
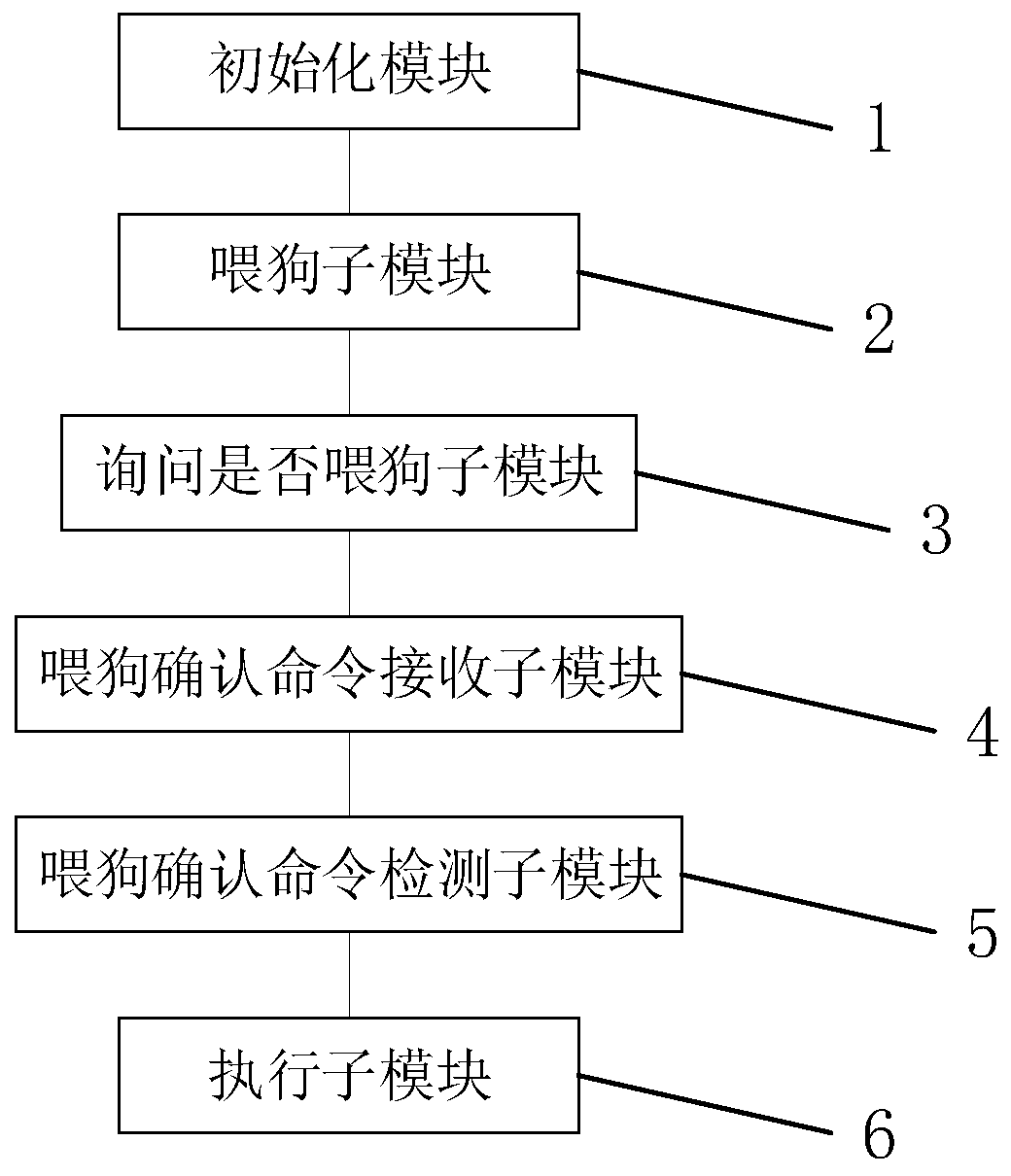
InactiveCN111241598AImprove attack defense capabilityFault responseInternal/peripheral component protectionThe InternetInit
The invention discloses a watchdog feeding method for embedded Linux equipment with an anti-attack capability and a driving module. A watchdog comprises an initialization module, a dog feeding sub-module, a sub-module for inquiring whether a dog is fed or not, a dog feeding confirmation command receiving sub-module, a dog feeding confirmation command detection sub-module and an execution sub-module. The method comprises the steps: initializing watchdog hardware circuit, obtaining watchdog overflow time, shielding a function interface in the drive code; obtaining a counting variable and a firsttime interval, carrying out periodic dog feeding operation according to the first time interval, and sending a dog feeding command to an application program or not; and judging whether a dog feedingconfirmation command replied by the application program is received within a set second time interval, judging whether the value of the counting variable exceeds a set overtime number, and resetting and restarting the system by the watchdog when the watchdog overflow time is exceeded, so the anti-attack capability of the embedded Linux equipment in the Internet of Things is improved.
Owner:ZHEJIANG WELLSUN INTELLIGENT TECH CO LTD
Integrity verification method and device for runtime program safety-critical data
ActiveCN102930185BAvoid attackIntegrity verification implementationProgram/content distribution protectionData setData integrity
The invention discloses a method and a device for verifying the integrity of security critical data of a program in the process of running. The method comprises the following steps: 1) indicating a security critical variable in the program, generating a security critical data set in the process of compiling, dividing a virtual address space of the program into a protected area and a non-protected area in the process of loading the program, loading the security critical data set to the protected area, and constructing an integrity verification tree for a virtual page of the protected area of the program; and 2) in the process of writing program data into a memory, updating a root verification value; and in the process of reading program data from the memory, generating a new root verification value, comparing the new root verification value with the original root verification value, if the two are equal, determining that the security critical data set is not tampered, otherwise, determining that the security critical data set is tampered. The device comprises a data integrity verification circuit, a root verification value storage module and a comparator. The method and the device disclosed by the invention have the advantages of high safety performance, strong attack prevention performance, small calculated amount, and less occupied storage space.
Owner:NAT UNIV OF DEFENSE TECH
A method for protecting Internet protocol voice technology gateway media channel
ActiveCN100550765CImprove securityImprove attack defense capabilityData switching networksNetwork packetDynamic management
Owner:ZTE CORP
Anti-attack processing method and device
ActiveCN106131046BReduce resource consumptionImprove attack defense capabilityTransmissionResource consumptionBroadband
Owner:NEW H3C TECH CO LTD
Method for raising network security via message processing
ActiveCN100454895CGuaranteed uptimeImprove reliabilityData switching networksElectric digital data processingMessage processingMessage passing
A method for raising network safety by utilizing message treatment includes placing message in buffer queue with relevant priority level and at channel between central processing unit and hardware retransmission plane separately according to priority level of message, carrying out treatment on message in buffer queue by central processing unit according to dispatch rule, carrying out treatment on message not required to be processed by control processing unit according to property of message and identifying those message according to specific rule for raising antiattack ability of network device.
Owner:北京知方知识产权管理有限公司
Message retransmitting method and apparatus
ActiveCN101022414BImprove attack defense capabilityData switching networksComputer hardwareChannel use
Owner:HUAWEI TECH CO LTD
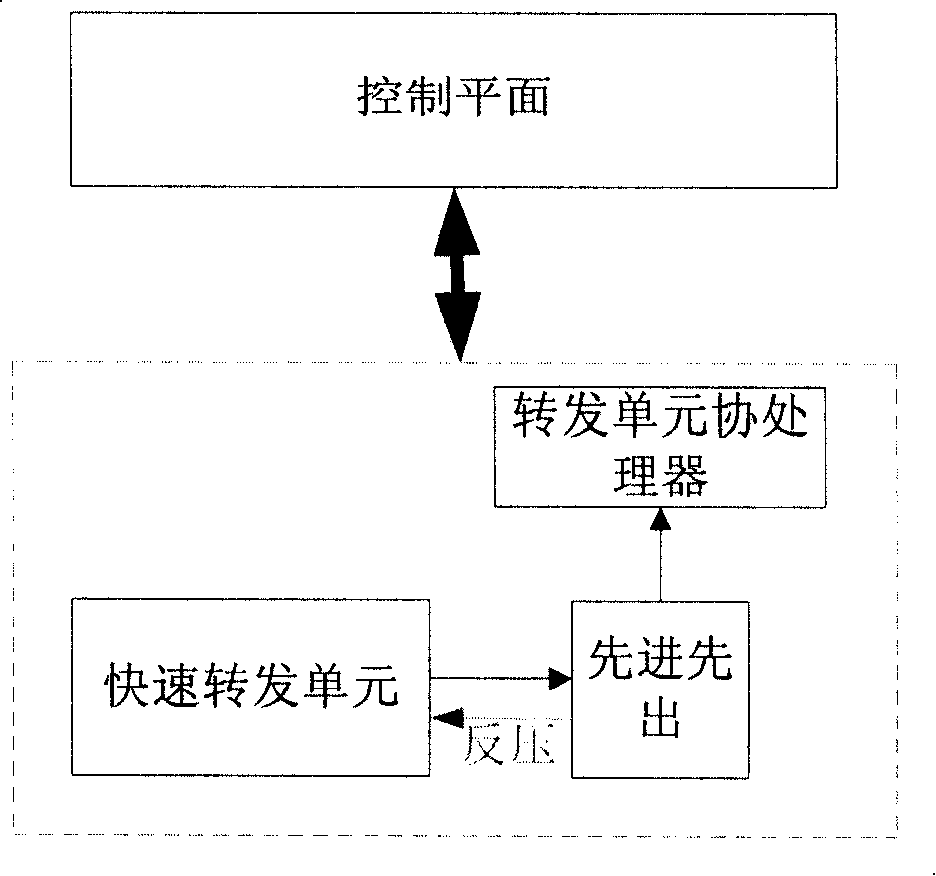
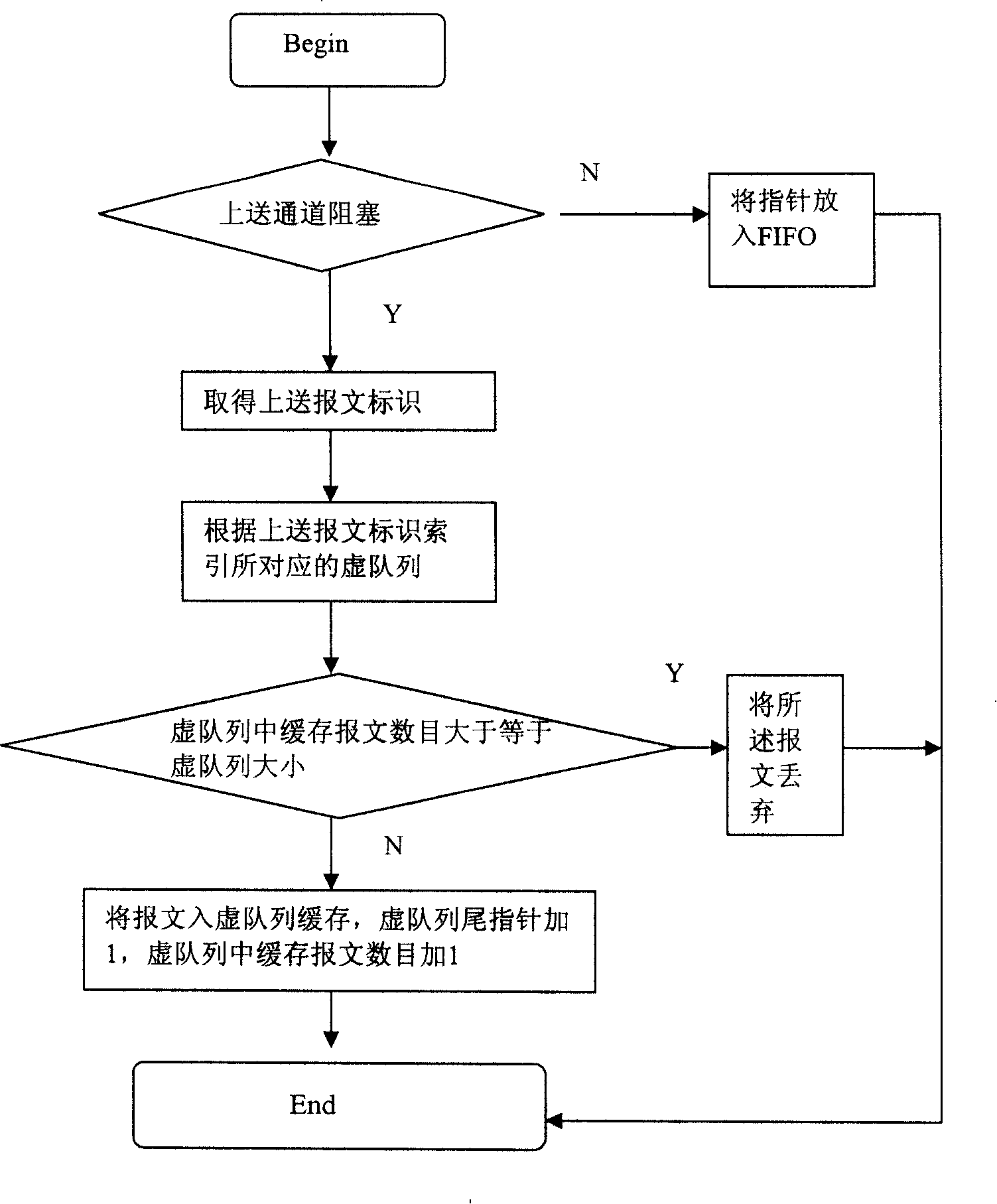
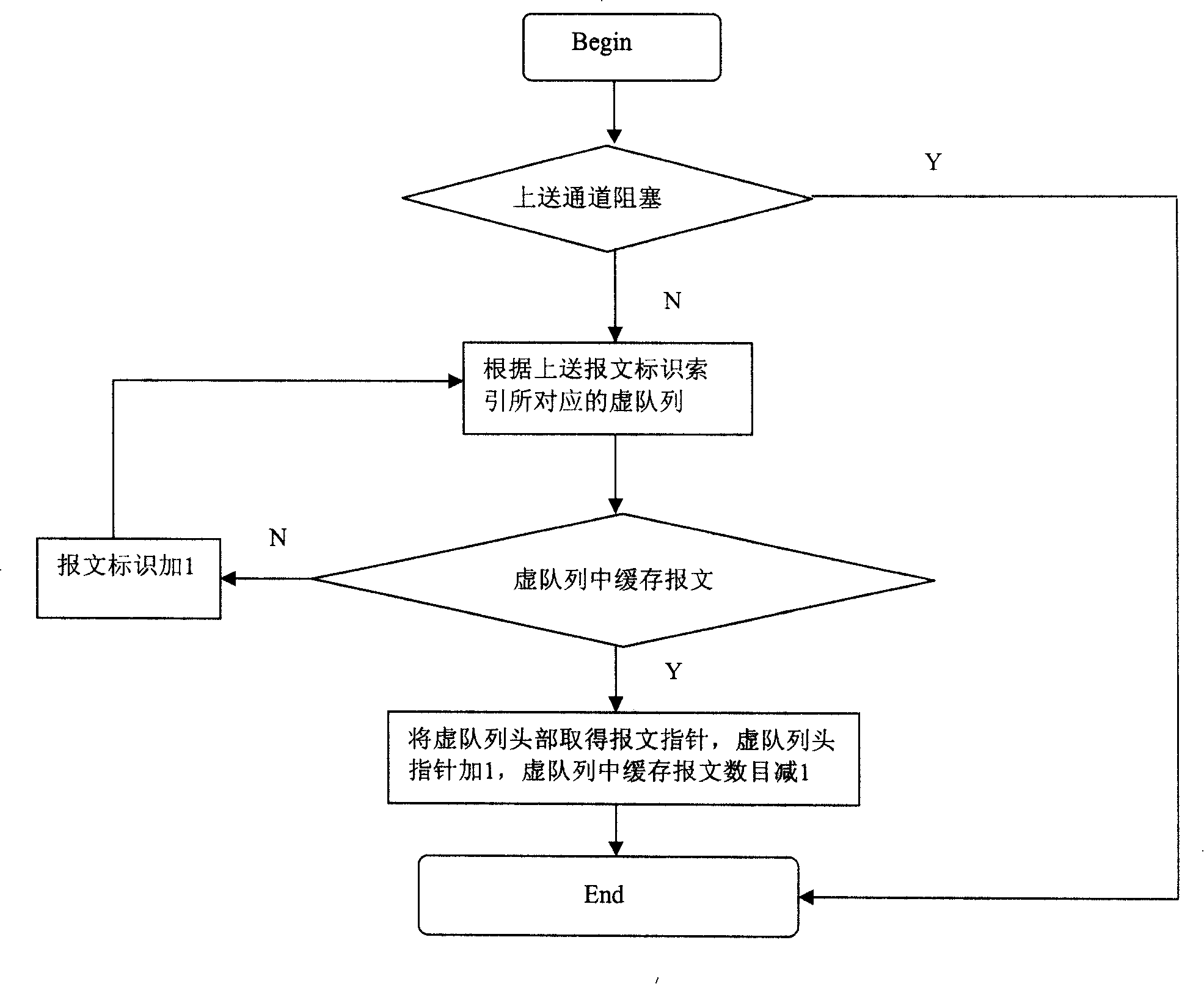
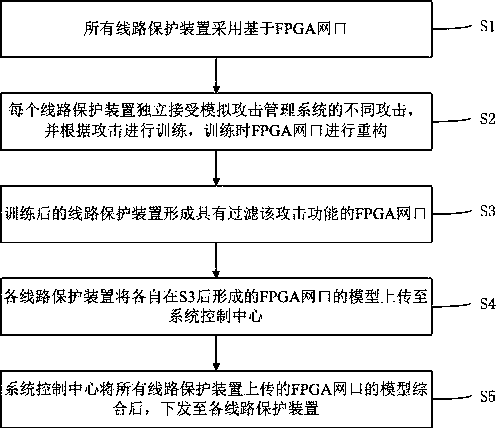
Method and system for enhancing network attack prevention capability of multiple network ports
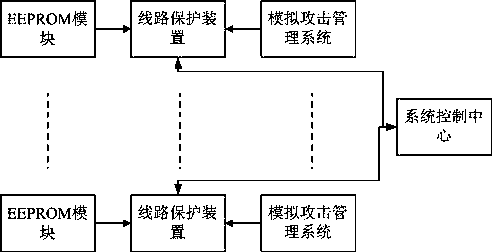
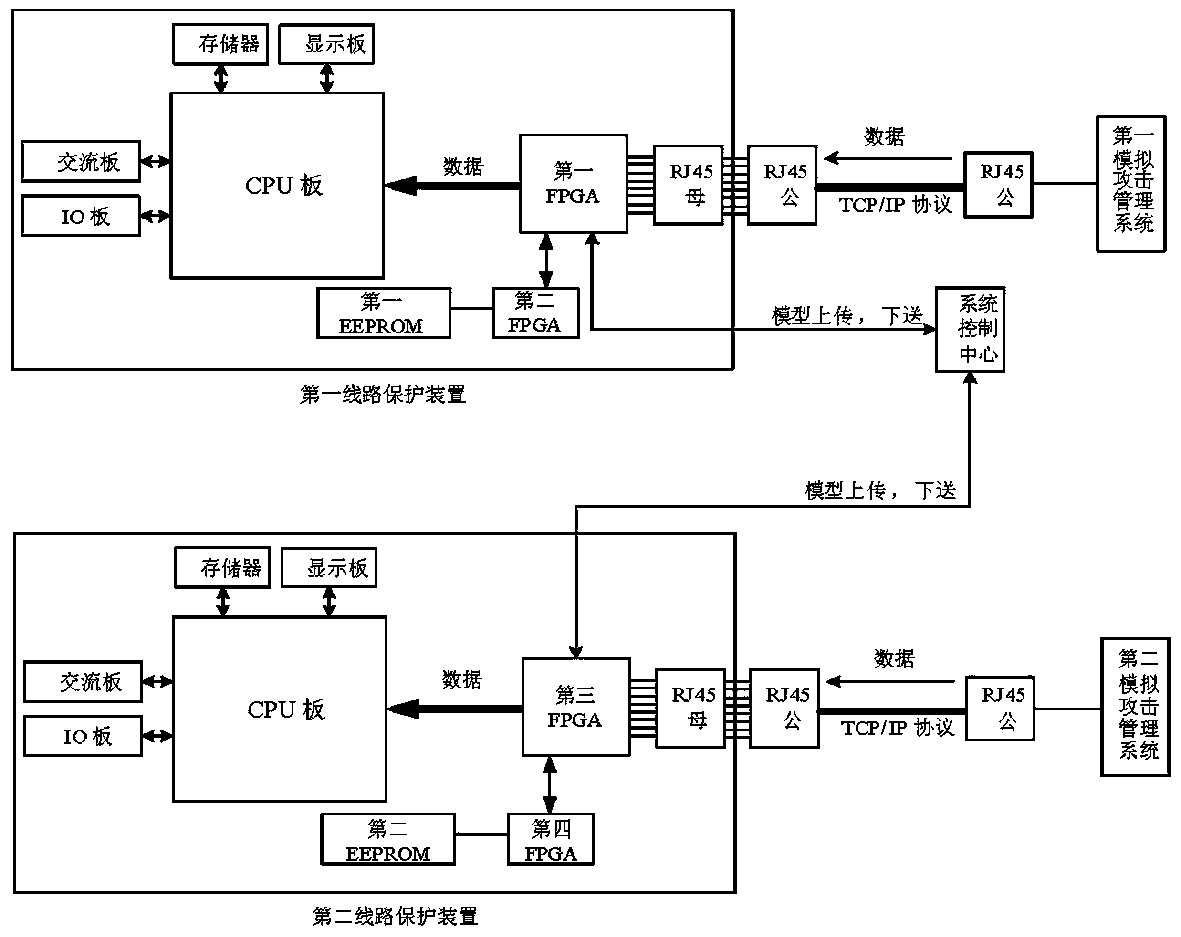
ActiveCN111464568AImprove attack defense capabilityFacilitate real-time online reconstructionData switching networksComputer networkAttack
The invention discloses a method and a system for enhancing the network attack prevention capability of multiple network ports. The method comprises the following steps that: S1, all line protection devices adopt FPGA-based network ports; S2, each line protection device independently receives different attacks of the simulation attack management system, training is carried out according to the attacks, and an FPGA network port is reconstructed during training; S3, the trained line protection device forms an FPGA network port with the function of filtering the attack; S4, each line protection device uploads the FPGA network port model formed after S3 to a system control center; and S5, the system control center synthesizes the models of the FPGA network ports uploaded by all the line protection devices and then issues the synthesized models to all the line protection devices. According to the reconfigurable multi-network-port anti-network-attack and enhancement mechanism based on the FPGA, each single network port can share attack information with other network ports to enhance the self anti-attack capability, and the FPGA-based network port anti-network-attack capability of each device becomes more and more powerful and complete as time goes on.
Owner:FOSHAN POWER SUPPLY BUREAU GUANGDONG POWER GRID
A security interaction control method between an intelligent terminal and a server
ActiveCN113141362BHigh degree of anti-crackingImprove securitySecuring communicationInteraction controlTerminal server
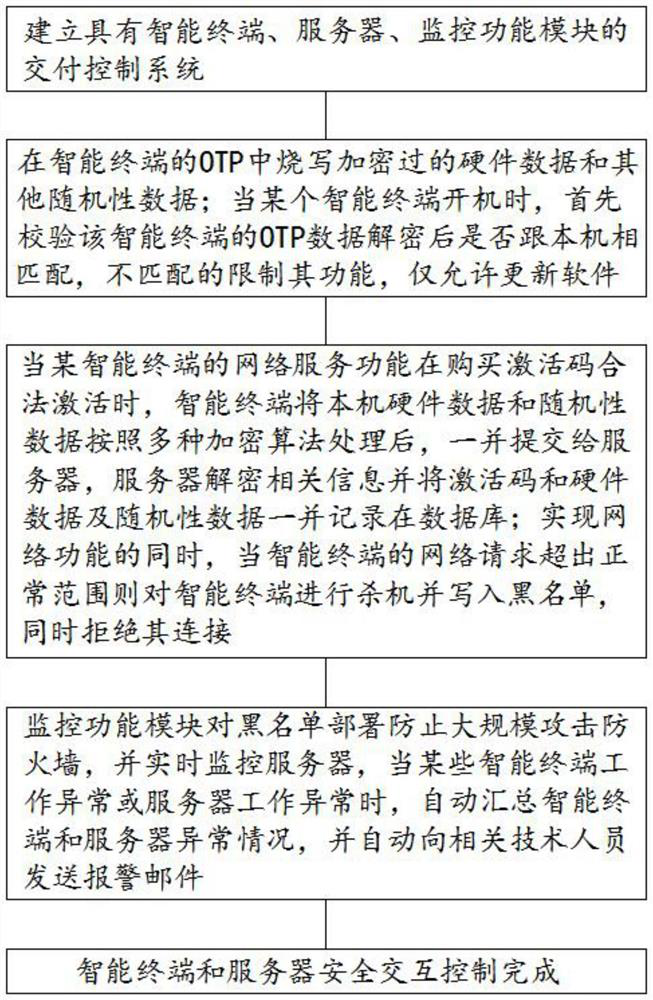
The present invention provides a safe interactive control method between an intelligent terminal and a server, comprising the following steps: S1: establishing a delivery control system with an intelligent terminal, a server, and a monitoring function module; S2: programming encrypted hardware data in the OTP of the intelligent terminal and other random data; when a smart terminal is turned on, first check whether the decrypted OTP data of the smart terminal matches the machine, and if it does not match, its functions are limited and only software updates are allowed; S3: when a smart terminal When the network service function of the network service function is legally activated by purchasing an activation code, the smart terminal processes the local hardware data and random data according to various encryption algorithms, and then submits them to the server together, and realizes safe interaction through monitoring the server and smart terminal. Experience selection, high degree of anti-cracking, high security and anti-attack capabilities, and automatic operation and maintenance capabilities and intelligent capabilities.
Owner:中山亿联智能科技有限公司
Chip anti-power consumption attack circuit and method for preventing power consumption attack
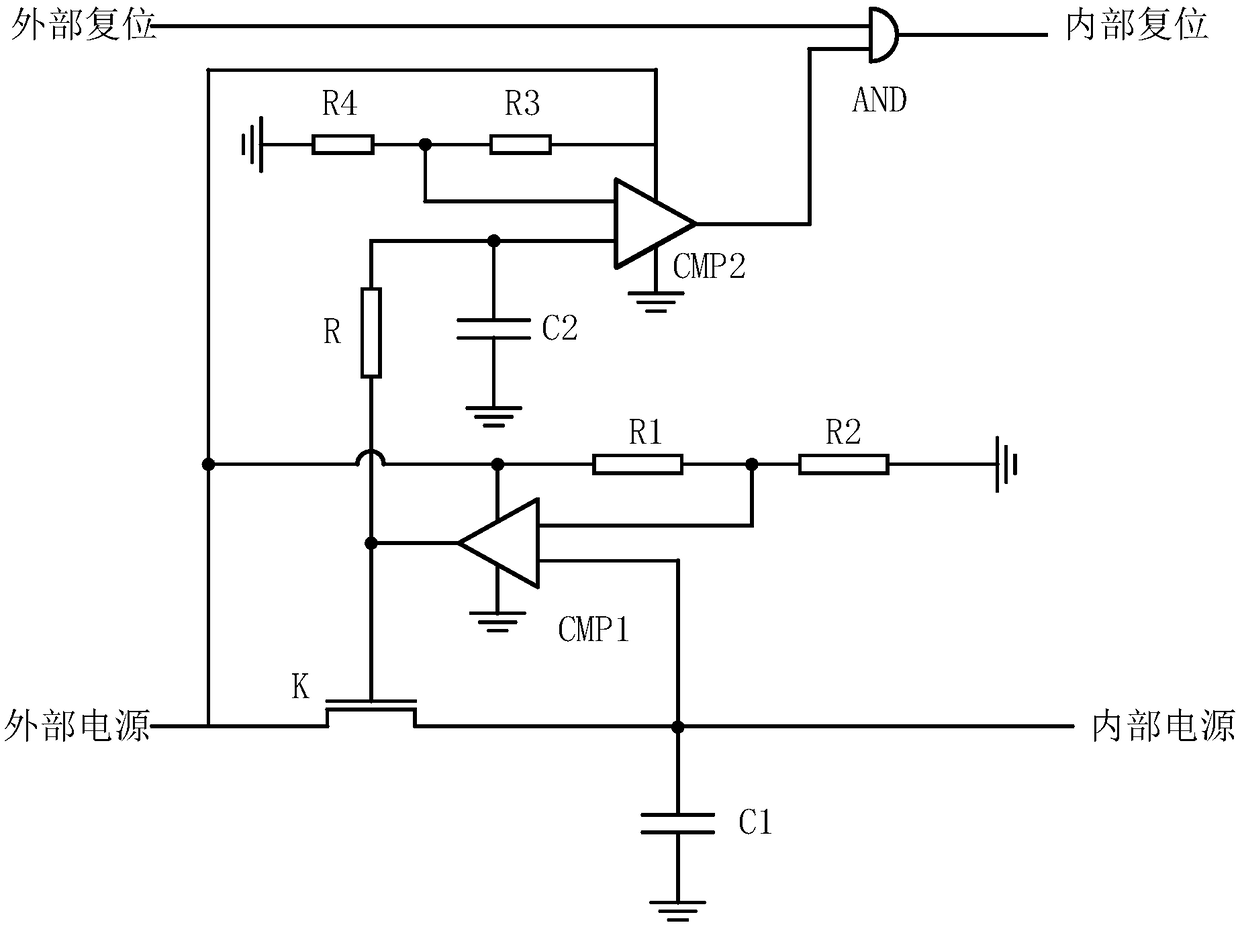
ActiveCN106503590BImprove attack defense capabilityImprove securityInternal/peripheral component protectionElectric capacityHemt circuits
The invention relates to a circuit and method for preventing power consumption attack against a chip. The problem of power consumption attack is not solved fundamentally according to an existing method. The circuit comprises an NMOS switch, a charging capacitor, a filter resistor, a filter capacitor, a charging voltage comparator, a switching voltage comparator, a two-input AND gate and four divider resistors. When the chip is electrified, the switch is switched off, and an external power supply charges the capacitors. When the chip starts encryption and decryption operation, the switch is switched on, the inside of the chip is disconnected with the external power supply, and the circuit in the chip relies on the charging capacitor to be powered. After the electric quantity of the capacitor is reduced to a threshold, the chip stops operating temporarily, the switch is switched off, and the external power supply charges the capacitors. When the capacitors are fully charged, the switch is switched on, the inside of the chip is disconnected with the external power supply, and the circuit in the chip relies on the charging capacitor to go on working. According to the circuit and method for preventing power consumption attack against the chip, useful information contained in power consumption information is damaged, the chip protection capability is improved, and the circuit has a self active protection capability.
Owner:HANGZHOU NATCHIP SCI & TECH
Vehicle network access method and device, readable storage medium and gateway
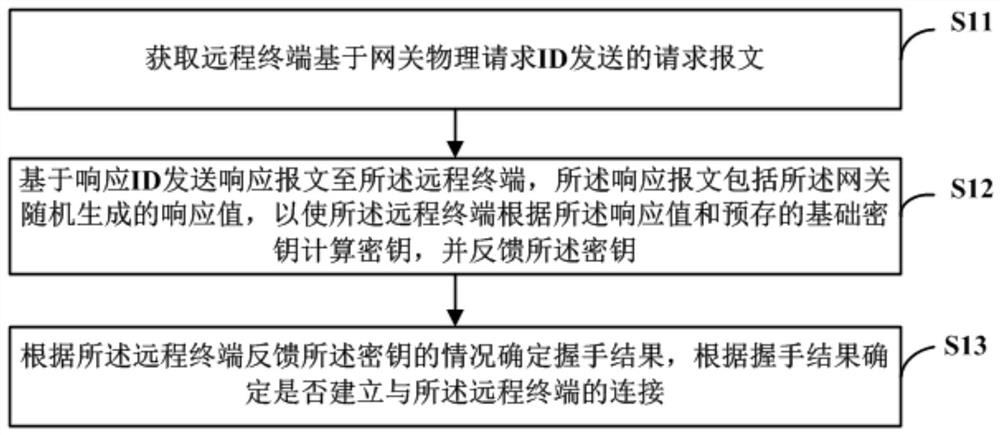
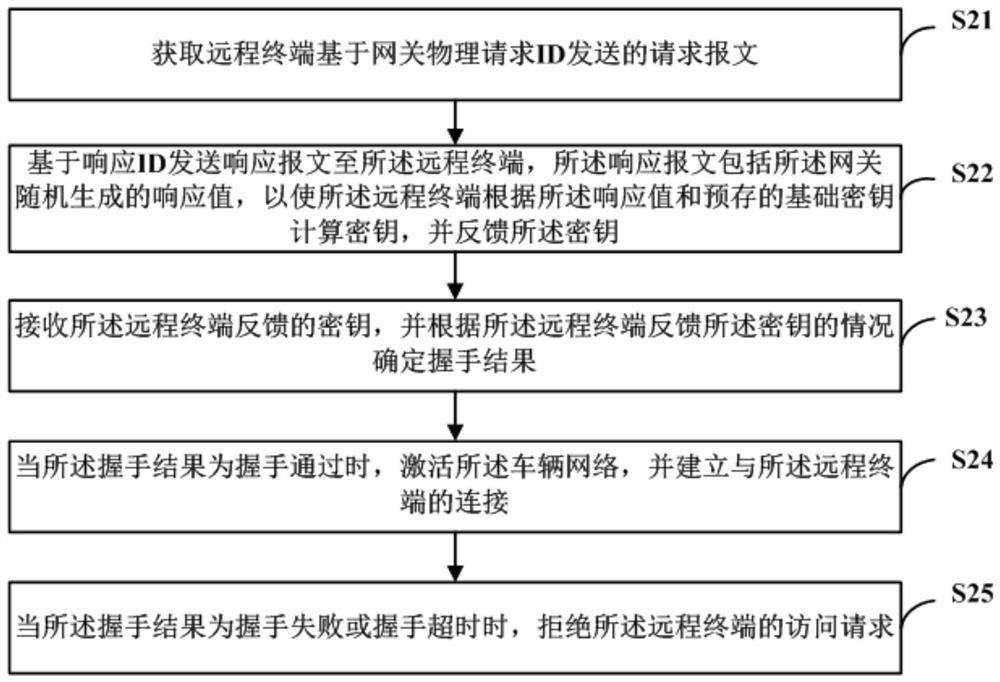
ActiveCN113037720AImprove attack defense capabilityImprove securityKey distribution for secure communicationEngineeringAuthentication
The invention discloses a vehicle network access method and device, a readable storage medium and a gateway. The vehicle network access method comprises the following steps: acquiring a request message sent by a remote terminal based on a gateway physical request ID; sending a response message to the remote terminal based on the response ID, the response message comprising a response value randomly generated by the gateway, so that the remote terminal calculates a key according to the response value and a pre-stored basic key, and feeds back the key; determining a handshake result according to the condition that the remote terminal feeds back the key, and determining whether to establish connection with the remote terminal according to the handshake result. According to the invention, identity authentication is carried out by using the handshake process between the gateway and the remote terminal, and the whole vehicle communication is carried out based on the authentication result, so that the anti-attack ability of the whole vehicle is greatly improved, and the driving safety is improved.
Owner:JIANGLING MOTORS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com