Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
212 results about "Blacklisting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Blacklisting is the action of a group or authority, compiling a blacklist (or black list) of people, countries or other entities to be avoided or distrusted as not being acceptable to those making the list. A blacklist can list people to be discriminated against, refused employment, or censored. As a verb, blacklist can mean to put an individual or entity on such a list.
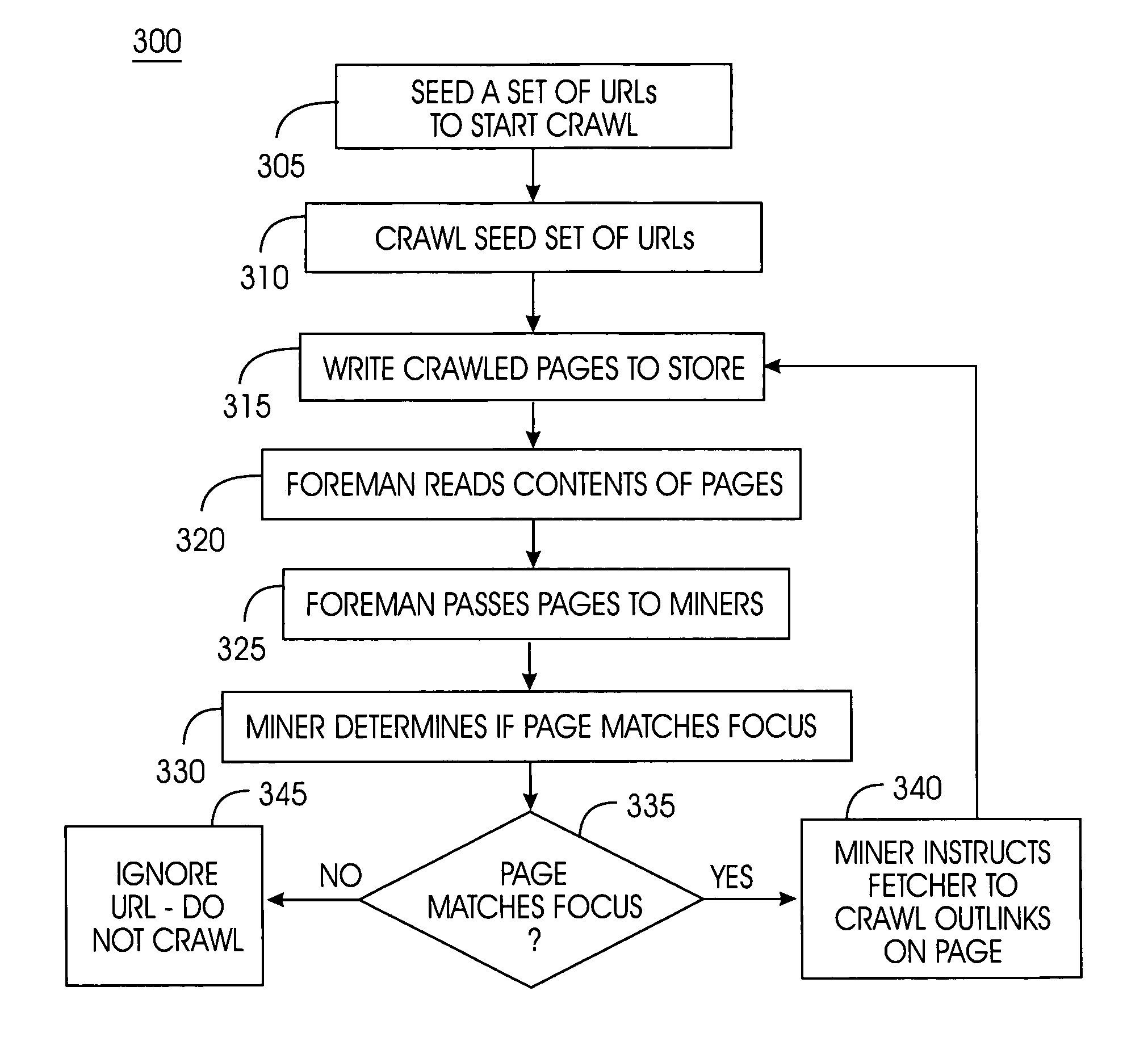
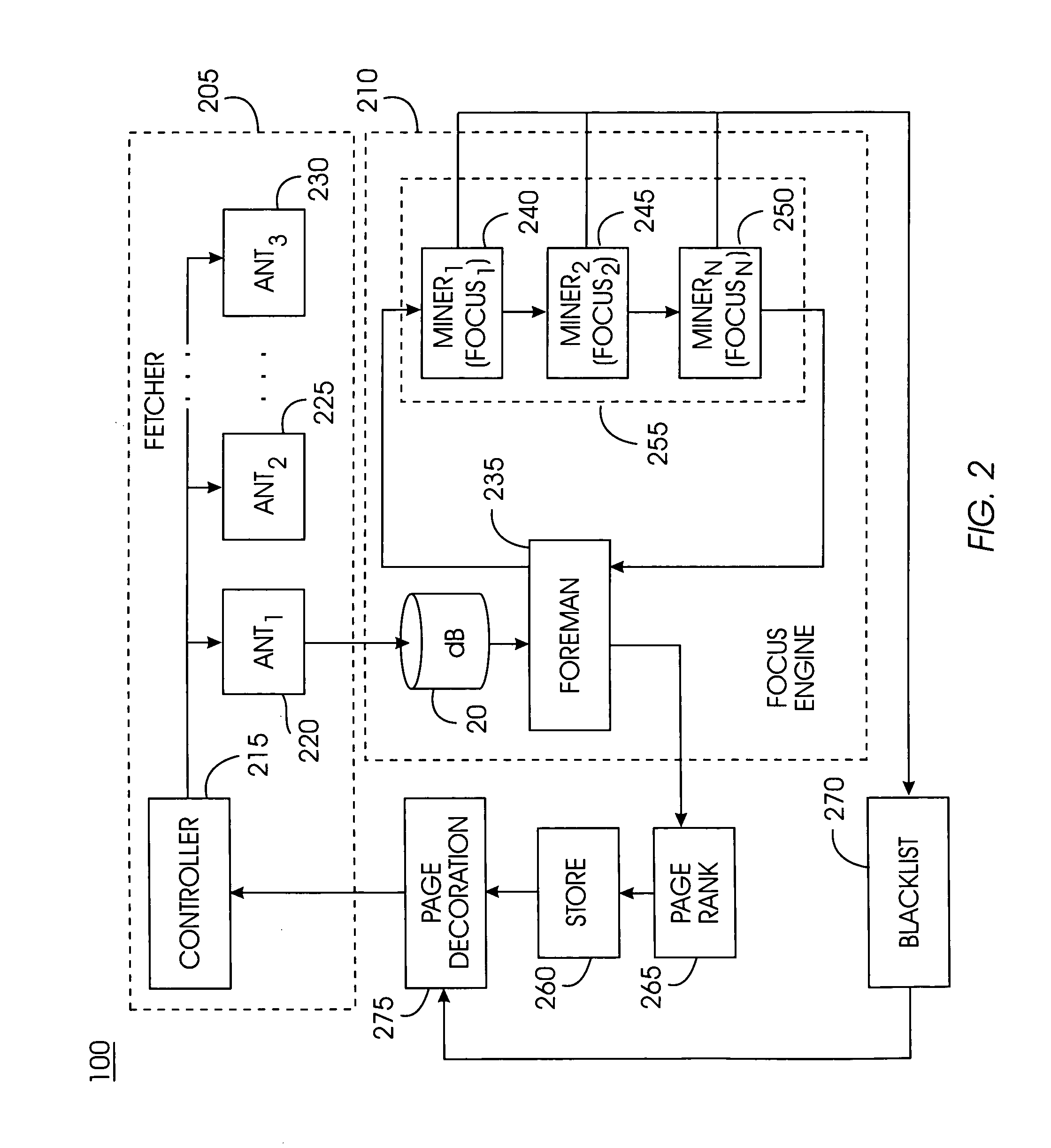
System, Method, and service for collaborative focused crawling of documents on a network
InactiveUS20050086206A1Save resourcesData processing applicationsWeb data indexingWeb spaceIp address
A collaborative focused crawler crawls documents on a network locating documents that match multiple focus topics. The collaborative crawler comprises a fetcher and a focus engine. The fetcher prioritizes which documents to crawl based on a set of rules, obtains documents from the network, and outputs crawled documents to the focus engine. The focus engine determines whether a fetched document is relevant to any of the multiple focus topics. The focus engine determines whether fetched documents are disallowed. If a fetched document is disallowed, the present system may place the URL for that web document in a blacklist, a list of URLs that may not be crawled. URLs may be disallowed if they match a disallowed topic or if they fail a set of rules designed for a web space focus, for example, domain rules, IP address rules, and prefix rules.
Owner:IBM CORP
Disambiguating conflicting content filter rules
A content filtering mechanism is enhanced to resolve conflicts in filtering rules (e.g., those created by a whitelist, on the one hand, and a blacklist, on the other hand). Preferably, a conflict between or among content filtering rules is resolved by selecting among conflicting rules based on a notion of “risk” associated with the rules. According to this risk-based approach, when two or more rules conflict with one another, the particular rule whose risk value has a predetermined relationship (e.g., aligns most closely) with a risk level associated with the application (applying the rules) then takes precedence. By selecting among conflicting rules based on risk, the potential or actual conflicts are disambiguated, with the result being that the content is filtered appropriately.
Owner:IBM CORP
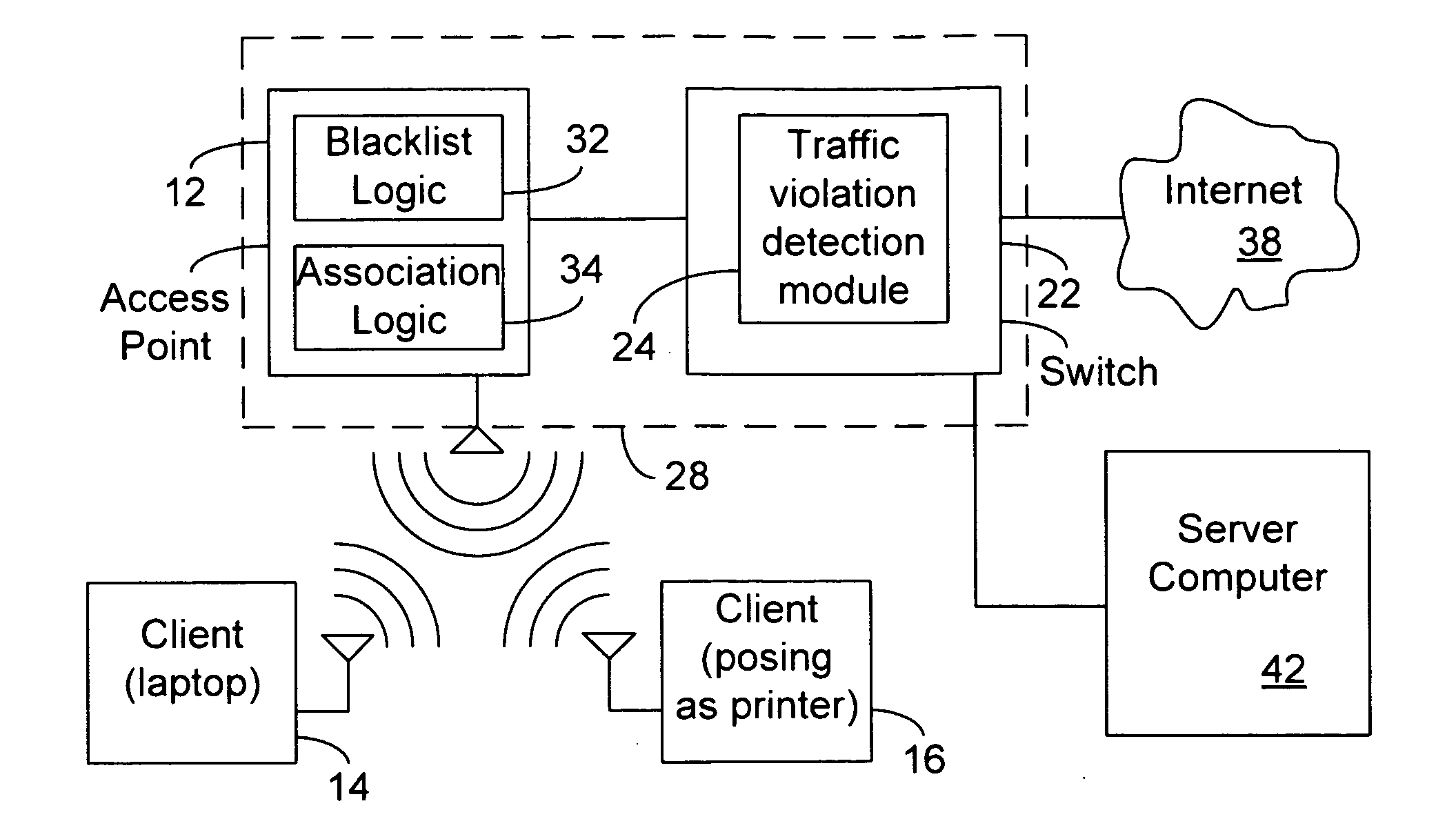
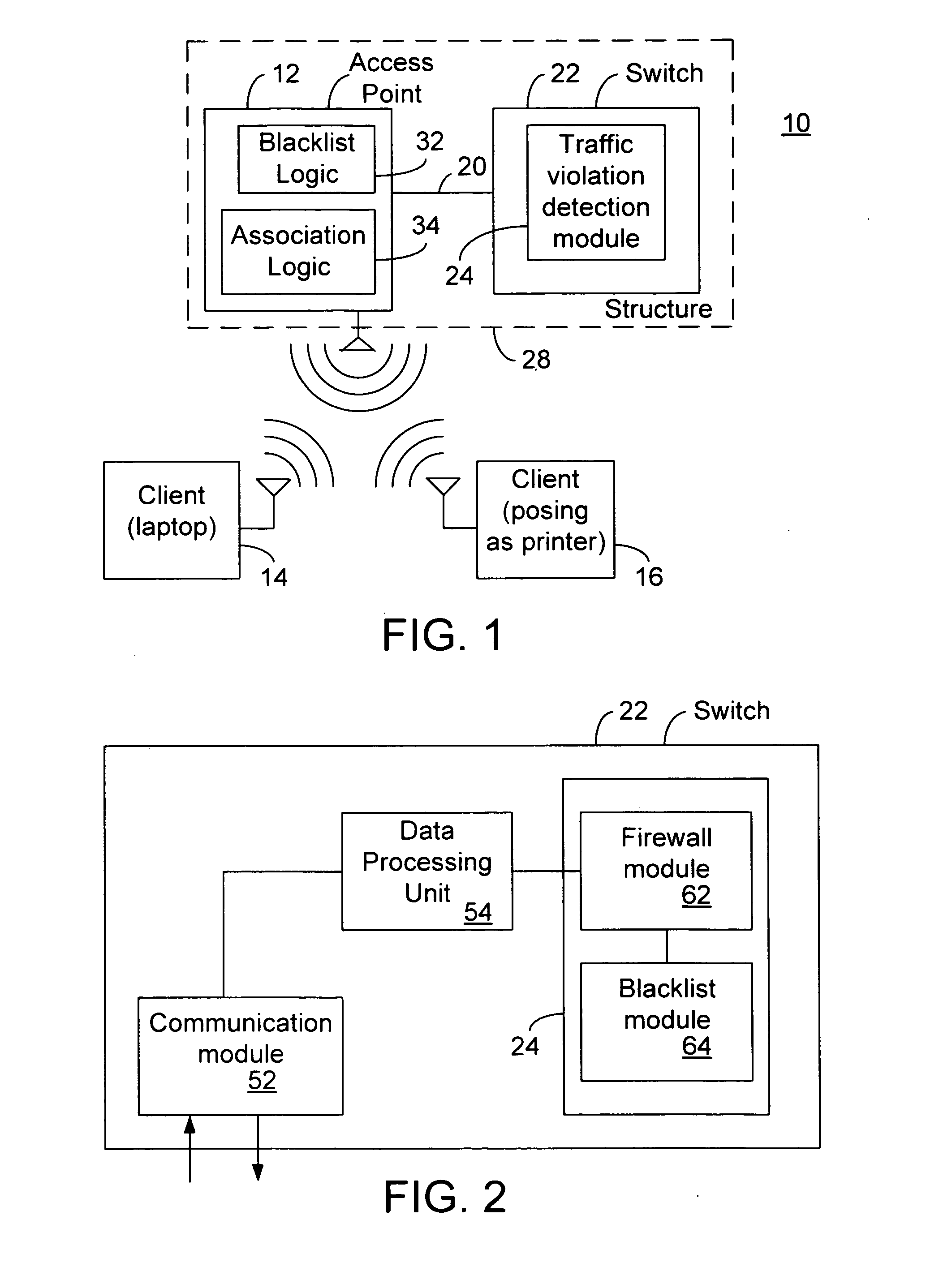
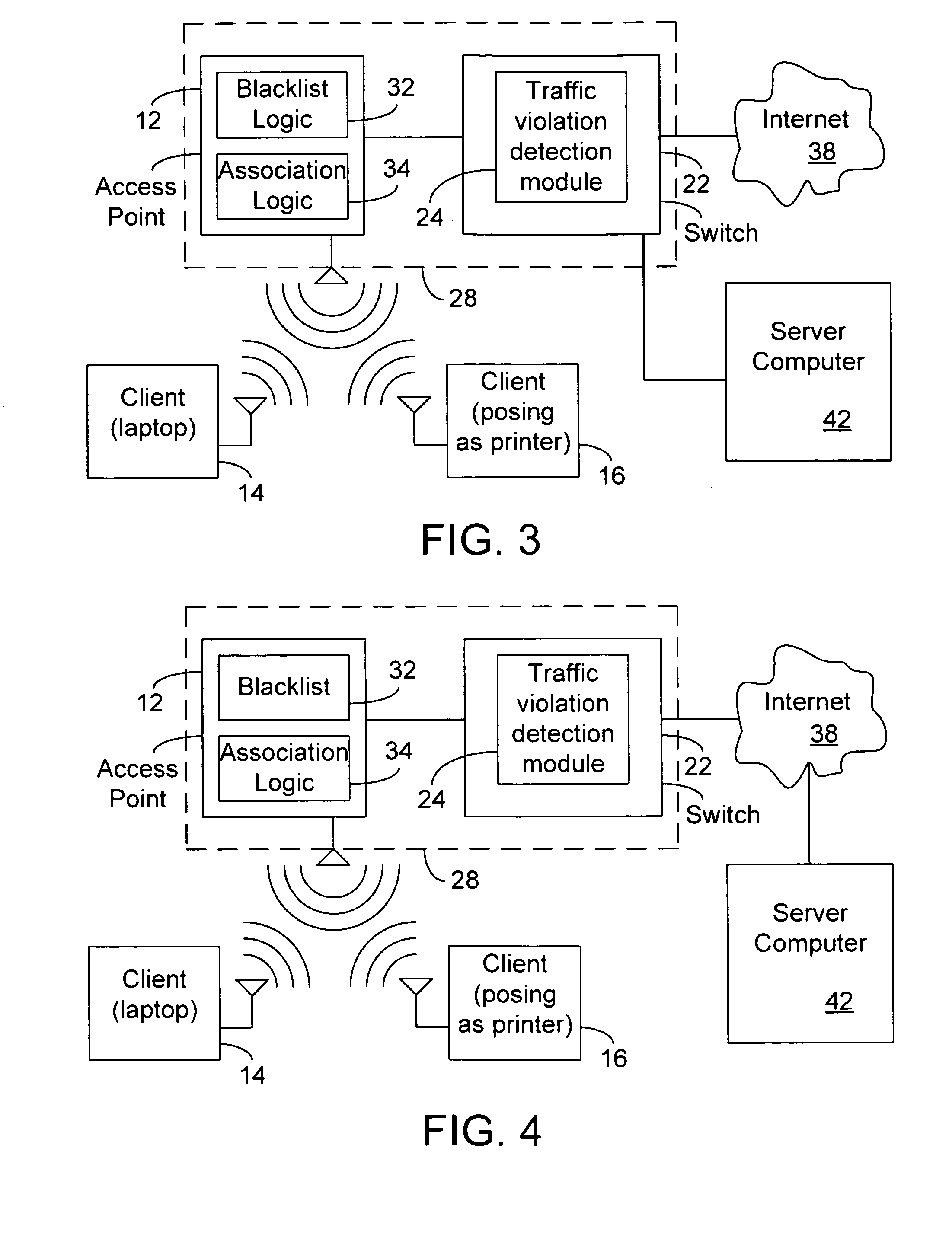
Blacklisting based on a traffic rule violation
In some embodiments, a network system includes an access point to wirelessly associate with a client that provides signals with traffic specification attributes to the access point. The system also includes circuitry detect if at least one of the signals violates a traffic rule through considering at least one of the traffic specification attributes and to instruct the access point to disassociate the client in response to a particular number of violations. Other embodiments are described.
Owner:ARUBA WIRELESS NETWORKS +1
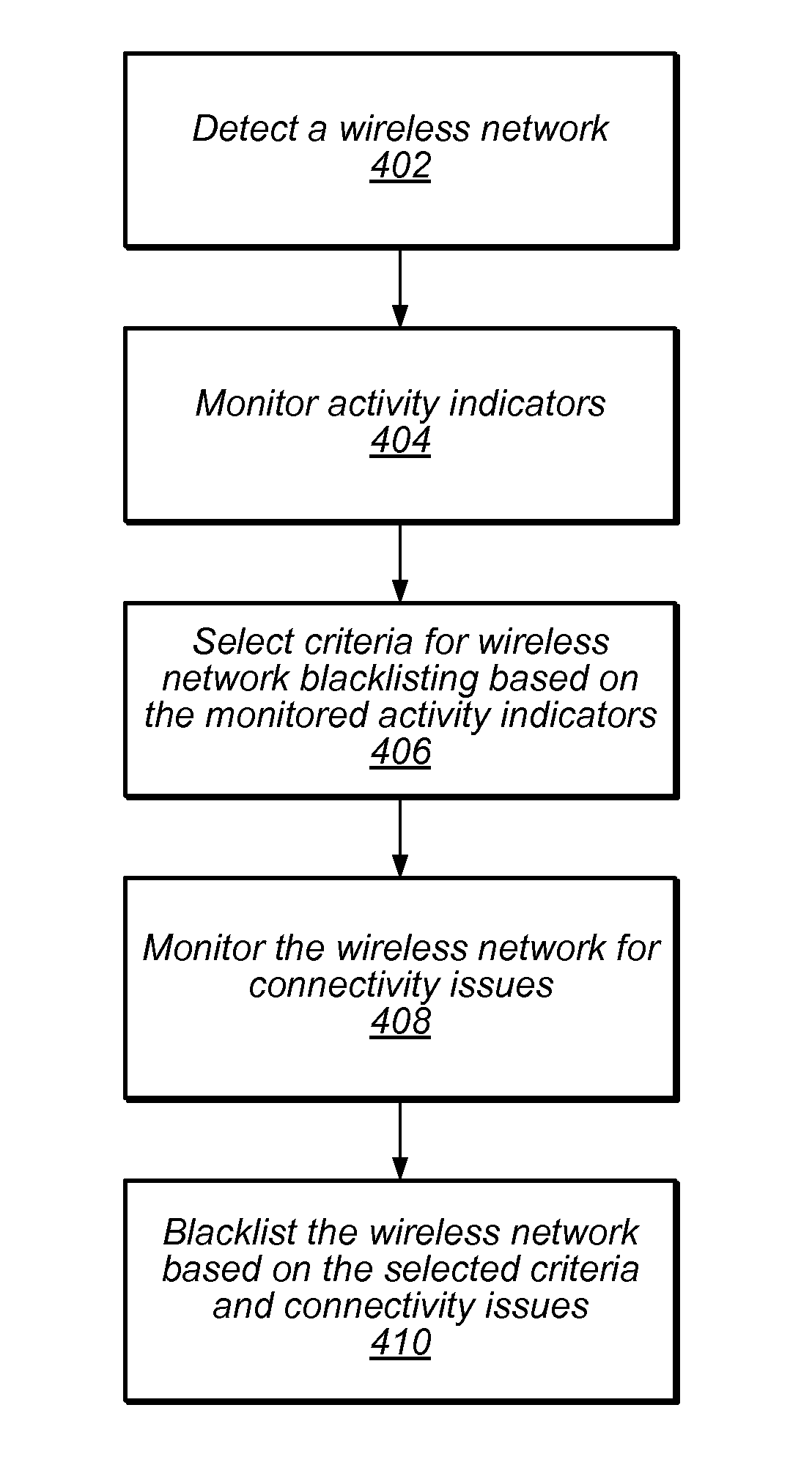
Automatically modifying wireless network connection policies based on user activity levels
ActiveUS8718644B2Avoid excessively draining the battery of the wireless deviceAvoid negatively impacting user experienceAssess restrictionRadio transmissionWireless mesh networkNetwork connection
Modifying network connection policies of a wireless device based on user activity levels. One or more activity indicators of the wireless device may be monitored. One or more criteria for wireless network blacklisting may be selected based on the one or more activity indicators. The criteria may include different types of connectivity problems. A wireless network may be detected. The wireless network may be monitored for connectivity problems. The wireless network may be blacklisted if connectivity problems meeting the selected criteria for wireless network blacklisting are determined to have occurred.
Owner:APPLE INC
Method for quickly confirming real name identity in important place and human image and identity comparison safety inspection system
InactiveCN104240349AEasy to controlEliminate or reduce potential safety hazardsCharacter and pattern recognitionIndividual entry/exit registersBusiness requirementsControl equipment
The invention belongs to a method for quickly confirming a real name identity in an important place and a human image and identity comparison safety inspection system. The method comprises the steps that (1) human image acquisition equipment acquires a human face image or a video steam of passing people or a migrant in real time, and analyzes feature information from the human image and personal information, such as the height and the age; (2) certificate reading assorted equipment reads information, such as an identity card picture and the height, of passing people or the migrant according to a service specification in real time; (3) a management host unit performs on-site or real-time on-line comparison on the face picture or the video stream acquired by the human image acquisition equipment and the certificate information read by the certificate reading assorted equipment, and supports a manual blacklist introduction or on-line blacklist downloading and updating function; and (4) traveling control equipment is controlled according to a comparison result. According to the method and the human image and identity comparison safety inspection system, first-line policemen or workers in important fields can quickly identify and confirm the real identity of passing people or the migrant on site according to a police human image identification comparison service requirement on the basis of an advanced face identification core technology in the industry at present, and an unthinkable massive picture library comparison requirement in the past is met on site.
Owner:BAOJI TRAFFIC INFORMATION ENG INST
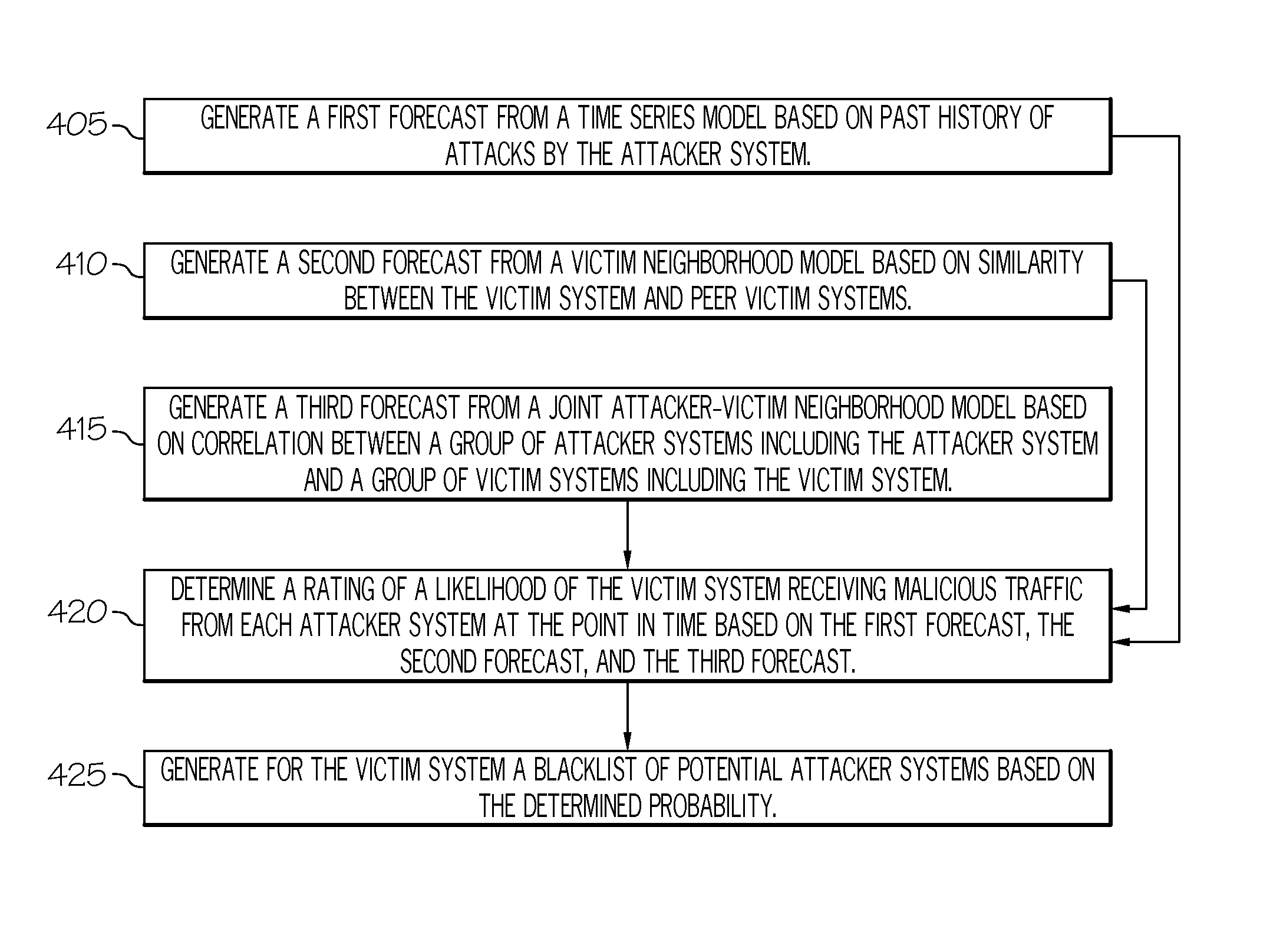
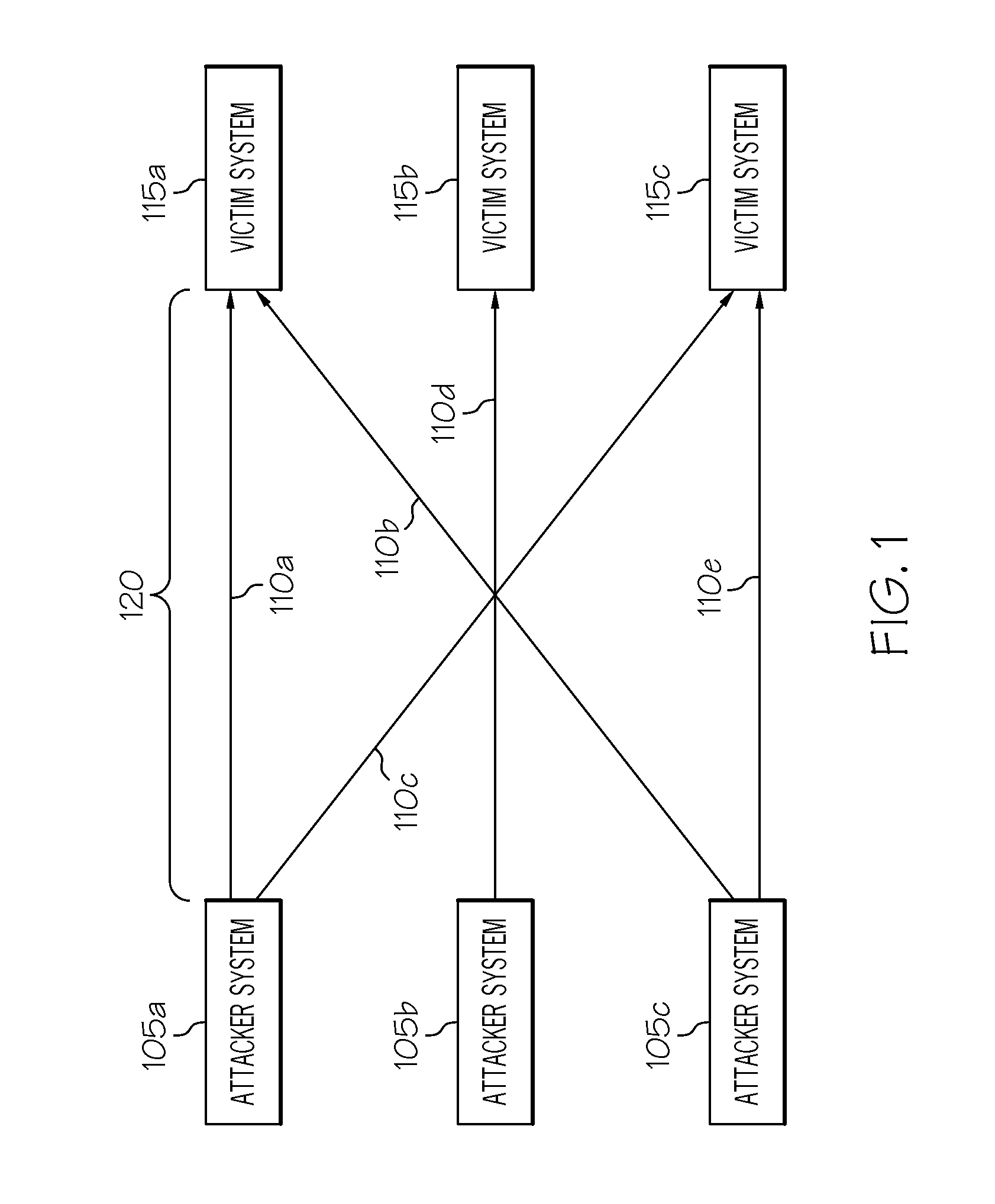
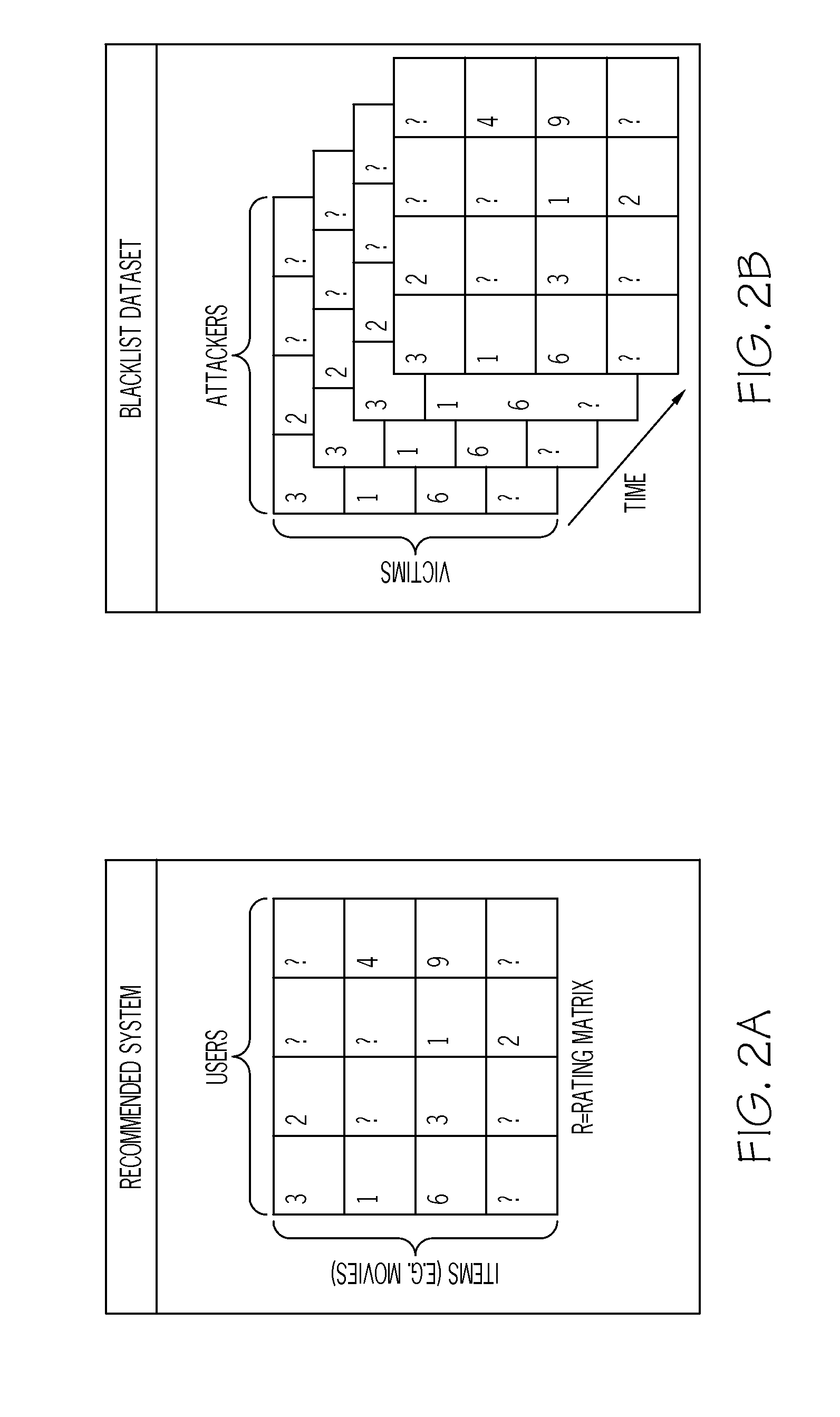
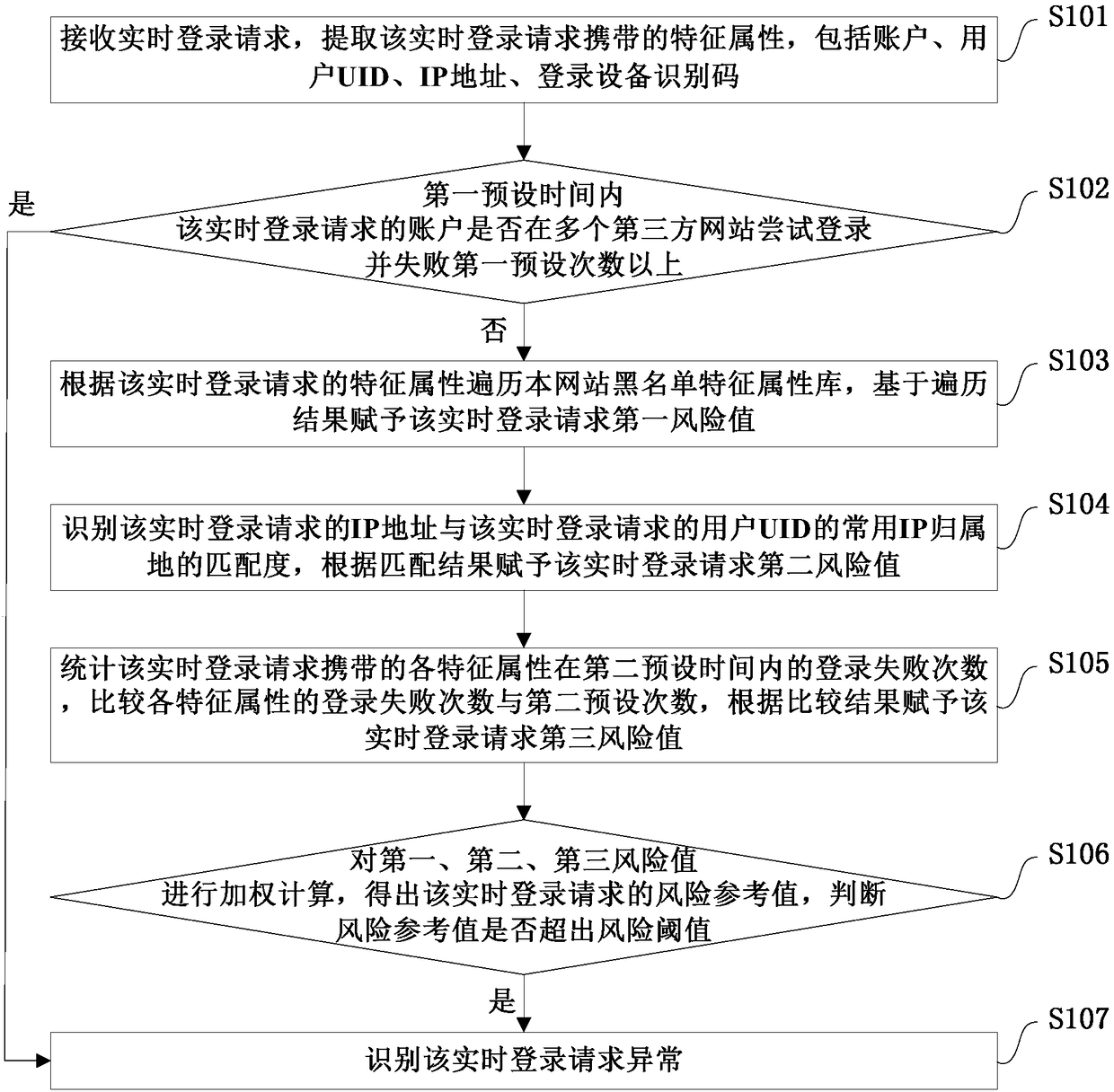
Predictive blacklisting using implicit recommendation
A method is provided for determining a rating of a likelihood of a victim system receiving malicious traffic from an attacker system at a point in time. The method comprises: generating a first forecast from a time series model based on past history of attacks by the attacker system; generating a second forecast from a victim neighborhood model based on similarity between the victim system and peer victim systems; generating a third forecast from a joint attacker-victim neighborhood model based on correlation between a group of attacker systems including the attacker system and a group of victim systems including the victim system; and determining the rating of the likelihood of the victim system receiving malicious traffic from the attacker system at the point in time based on the first forecast, the second forecast, and the third forecast.
Owner:RGT UNIV OF CALIFORNIA
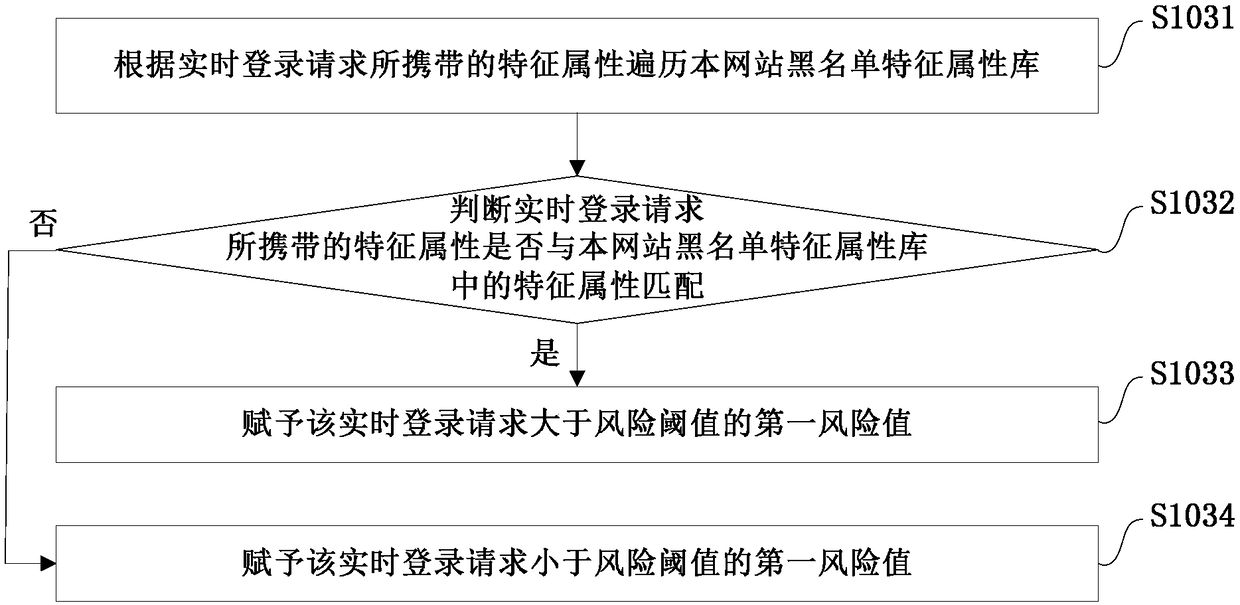
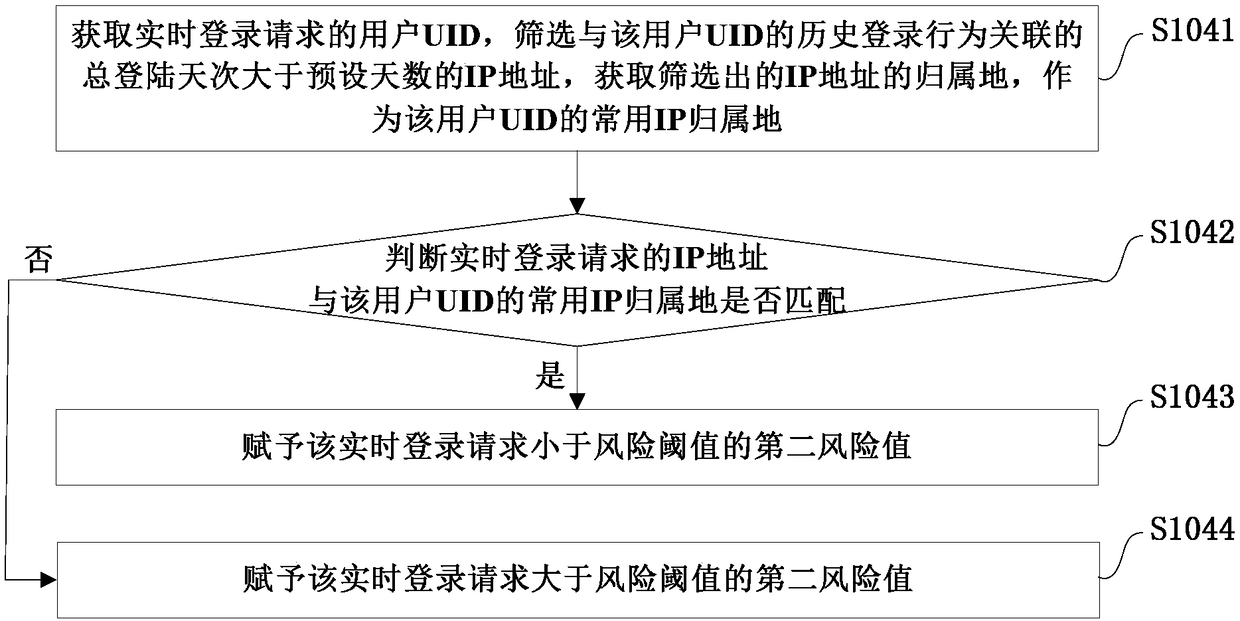
Abnormal login identification method and system, storage medium and electronic equipment
ActiveCN108092975AEnsure safetyAccurate and effective identification and defenseTransmissionThird partyIp address
The invention provides an abnormal login identification method and system, a storage medium and electronic equipment. The method includes the following steps: receiving and extracting characteristic attributes carried in a real-time login request; judging whether an account of the real-time login request tries to log in to multiple third-party websites within a preset time and fails more than a preset number of times, and if yes, identifying the login as an abnormal login; traversing a blacklist library according to the extracted characteristic attributes, and assigning a first risk value based on a traversal result; assigning a second risk value according to the matching degree between an IP address of the real-time login request and a common IP attribution of a UID of the real-time loginrequest; comparing the number of login failures and the number of preset times of each characteristic attribute within the preset time, and assigning a third risk value according to a comparison result; and performing weighted calculation on the first, second and third risk values to obtain a risk reference value of the real-time login request, and identifying the login as the abnormal login whenthe risk reference value exceeds a risk threshold. According to the scheme of the invention, by combining the external anti-scanning identification and the internal multidimensional identification, abnormal login behaviors can be intercepted to a maximum extent.
Owner:SHANGHAI CTRIP COMMERCE CO LTD
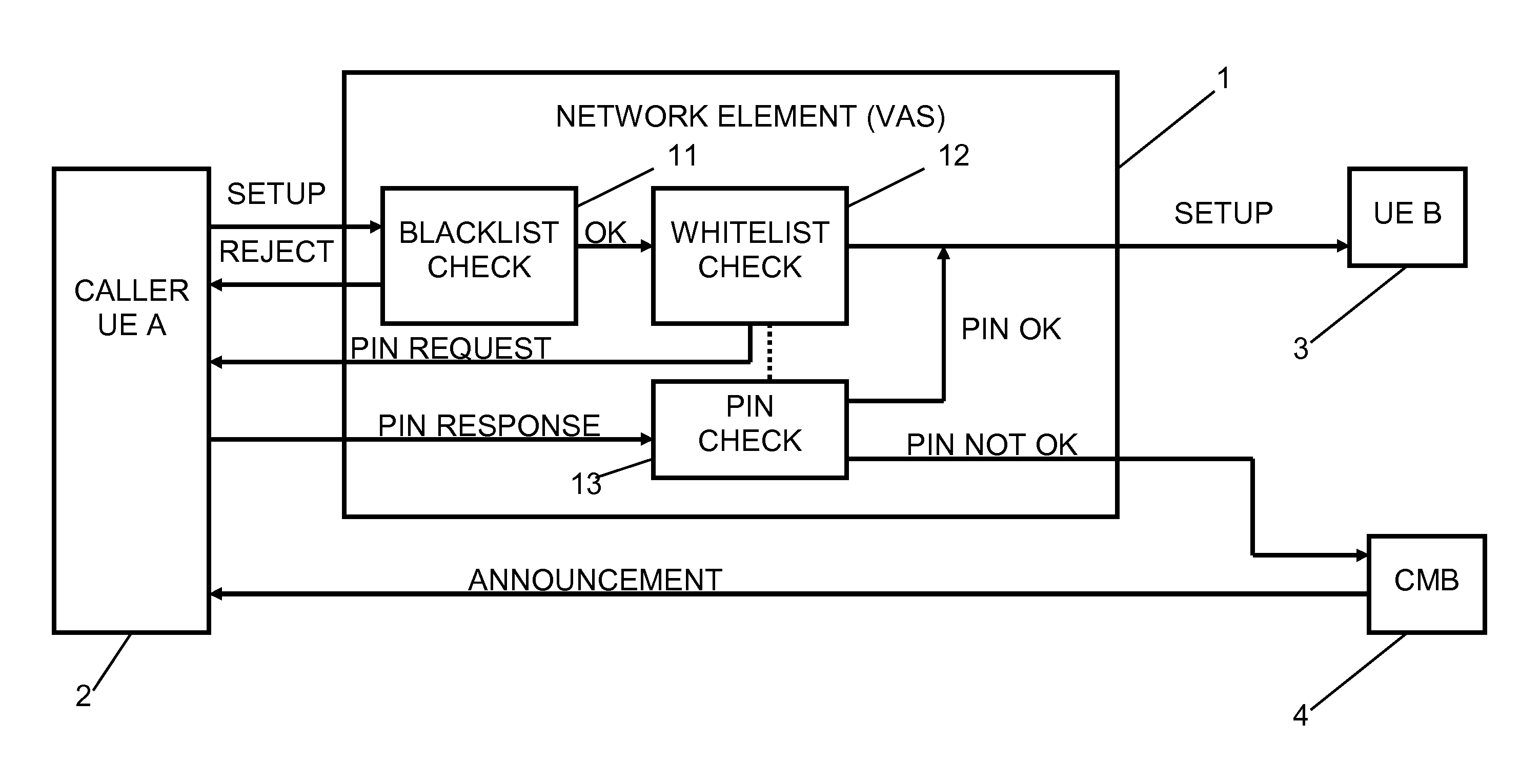
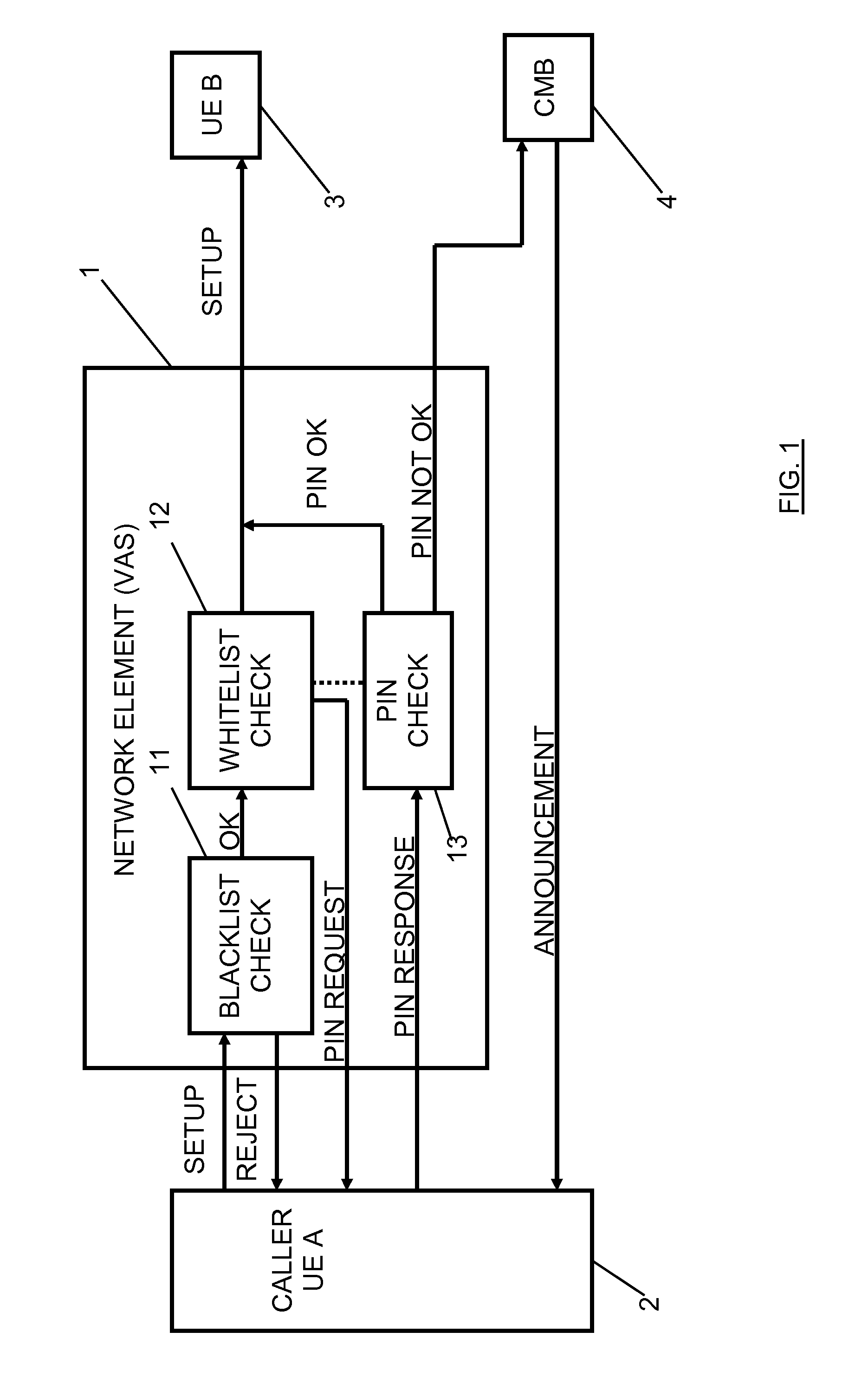
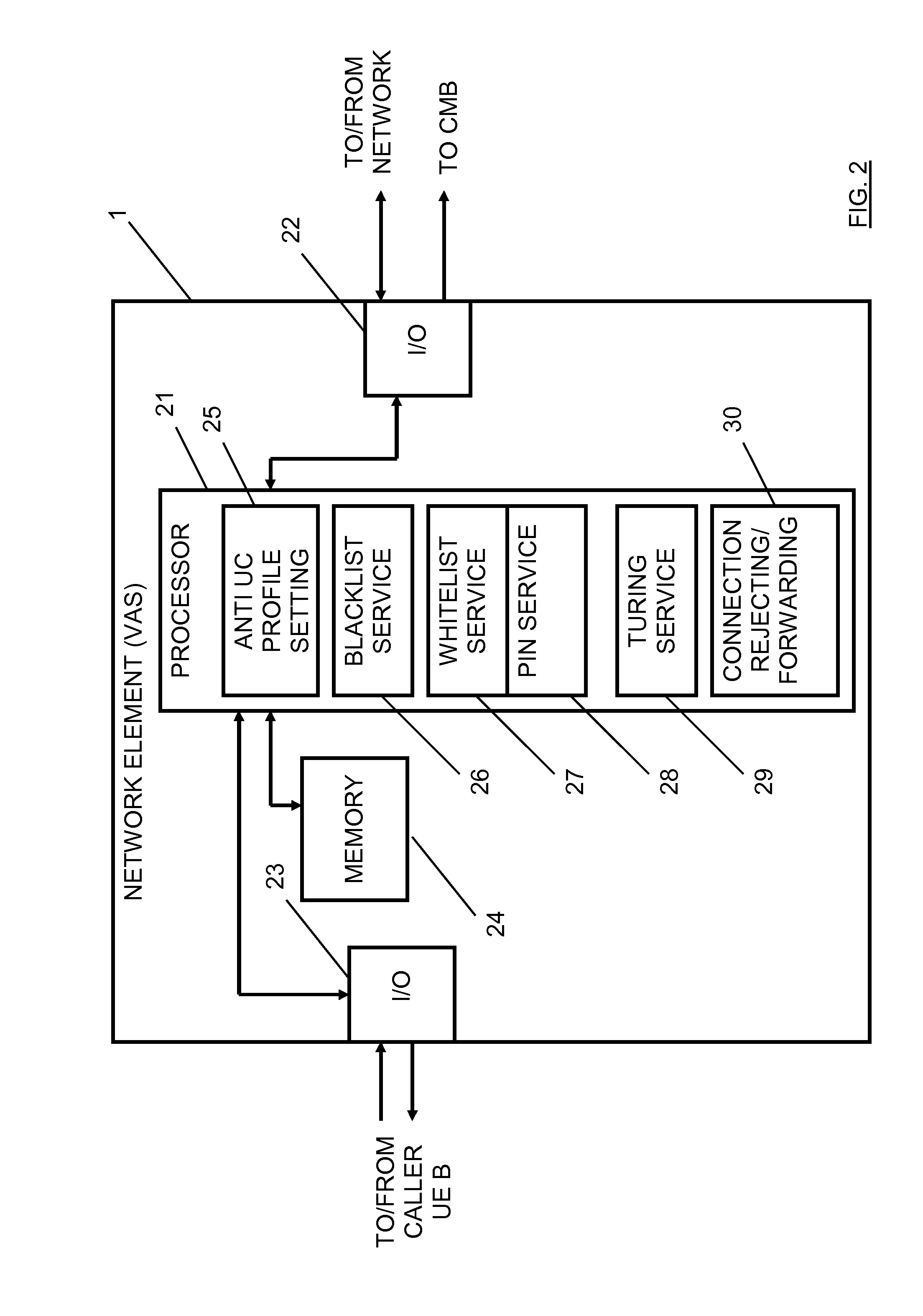
Communication Connection Establishment Control for Preventing Unsolicited Communication
InactiveUS20120039452A1Easy to moveNegatively affect user experienceSpecial service for subscribersTransmissionPersonalizationTelecommunications
There is proposed a mechanism for controlling a communication connection establishment to a subscriber using service including blacklisting, whitelisting, authentication request and / or Turing test for unsolicited communications prevention. Furthermore, there is proposed a management system used to configure a corresponding communication connection establishment control on the basis of an interface for the subscriber for defining a personalized communication connection establishment control profile.
Owner:NOKIA SOLUTIONS & NETWORKS OY
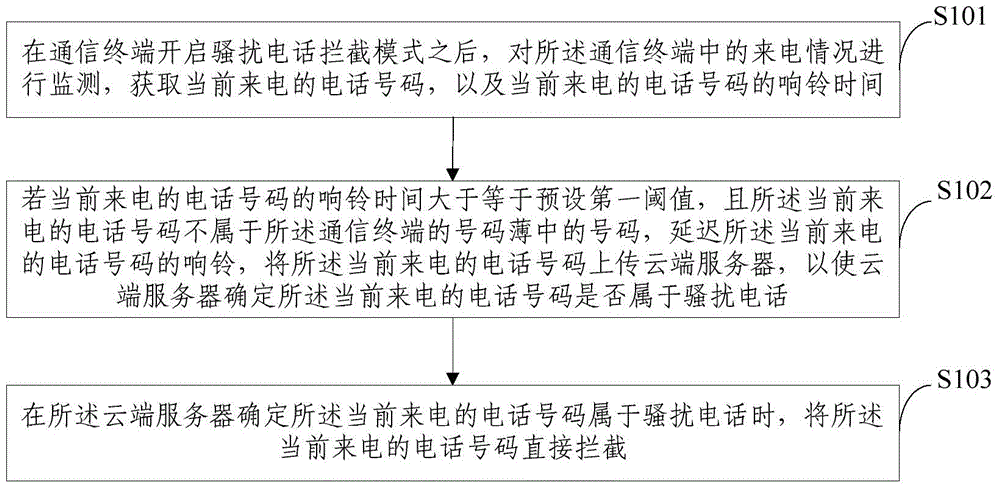
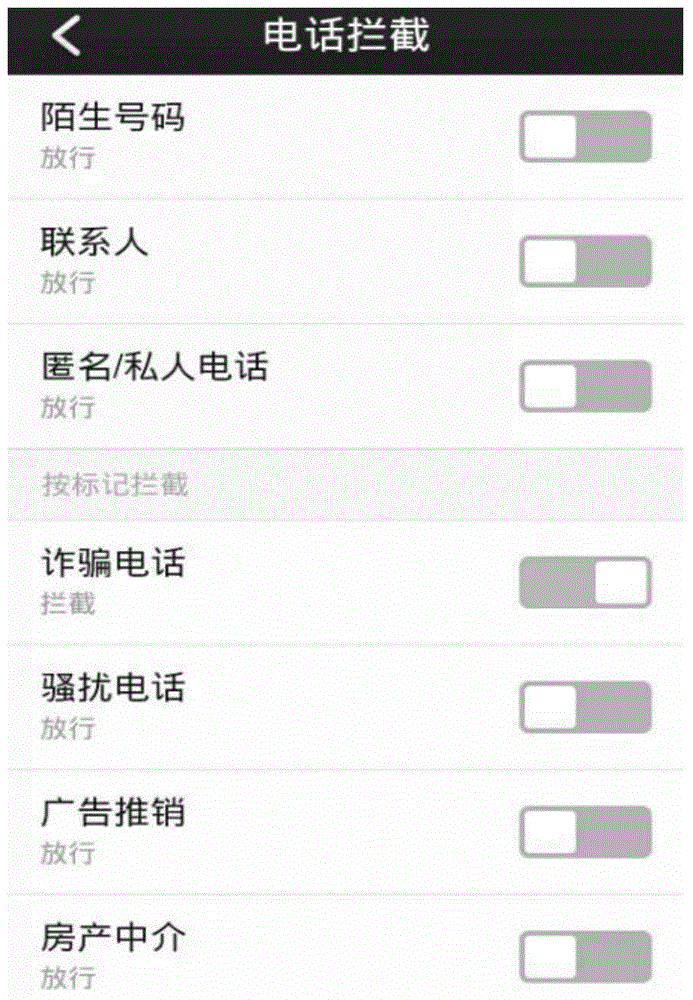
Crank call interception method and device
InactiveCN104486476AAvoid harassmentSubstation equipmentSecurity arrangementCloud serverBlacklisting
The invention provides a crank call interception method and device. The crank call interception method comprises the following steps: acquiring a calling number which is calling at present and the ringing time of the calling number after the crank call interception mode of a communication terminal is started; if the ringing time of the calling number is smaller than a first preset threshold and the calling number is not a number of the number directory of the communication terminal, directly intercepting the calling number; if the ringing time of the calling number is larger than or equal to the first preset threshold and the calling number is not a number of the number directory of the communication terminal, prolonging the ringing time of the calling number, uploading the calling number to a cloud server, and directly intercepting the calling number when the cloud server confirms that the calling number is a crank call. Compared with a method that crank call numbers are manually added into call firewalls or blacklists, the crank call interception method is relatively accurate in identifying crank calls, and a user is effectively prevented from harassment of malicious crank calls.
Owner:BEIJING QIHOO TECH CO LTD +1
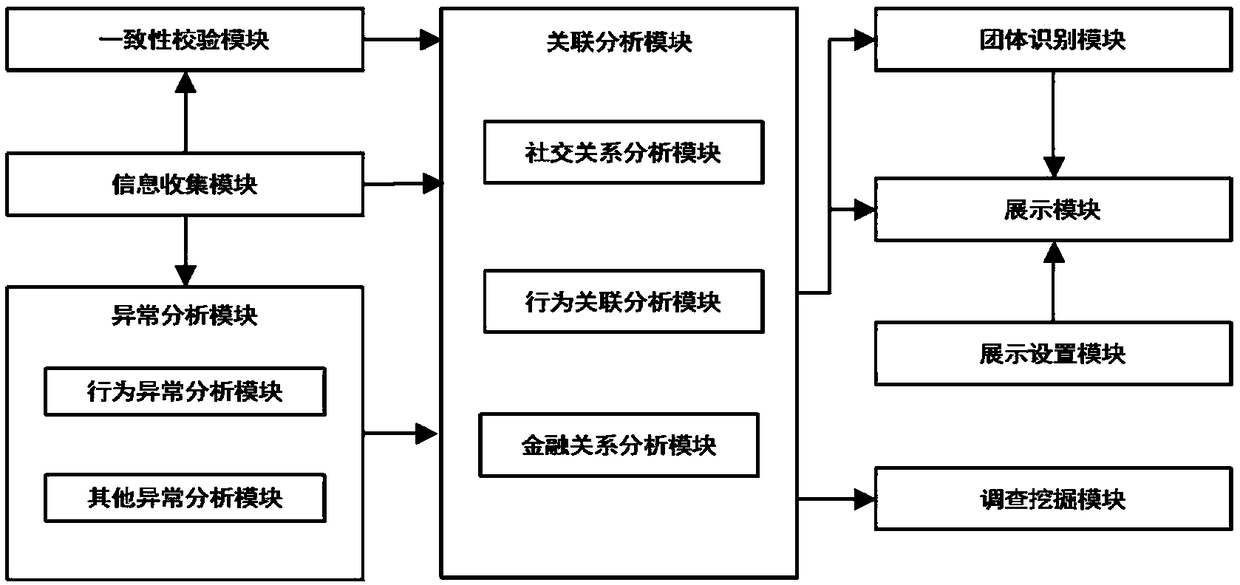
A group fraud identification system based on knowledge map
InactiveCN109191281AAvoid damageAchieving identifiabilityFinanceSemantic tool creationRisk preventionThird party
The invention relates to the technical field of loan risk prevention and control system, in particular to a group fraud identification system based on a knowledge map, which includes an information collection module, an abnormality analysis module, an association analysis module, a group identification module, a display module, a display setting module and a survey and digging module. The information collection module is used for collecting personal information of the borrower. The abnormality analysis module is used for detecting and analyzing abnormal behavior or abnormal data of the borrower, and the association analysis module is used for analyzing the association relationship between the suspected fraudulent user and other borrowers or third-party blacklisted persons. The group identification module is used for finding other suspected fraudulent users related to the suspected fraudulent users according to the association relationship and forming a suspected fraudulent group for the case investigator to judge. The invention provides a group fraud identification system based on a knowledge map, which can identify and evaluate the groups among borrowers, find out the groups thatmay have fraud risk, and reduce unnecessary losses of banks.
Owner:重庆富民银行股份有限公司
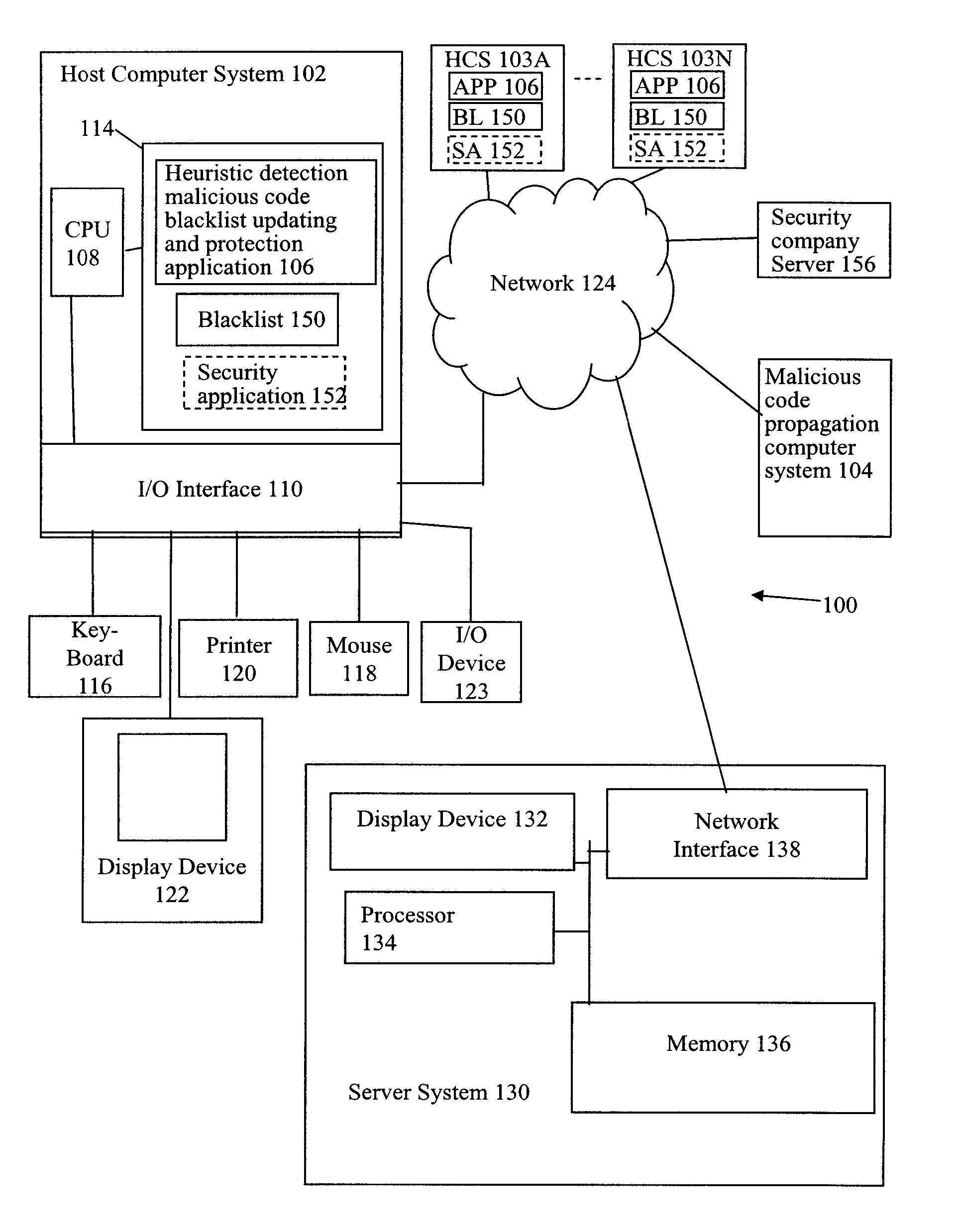
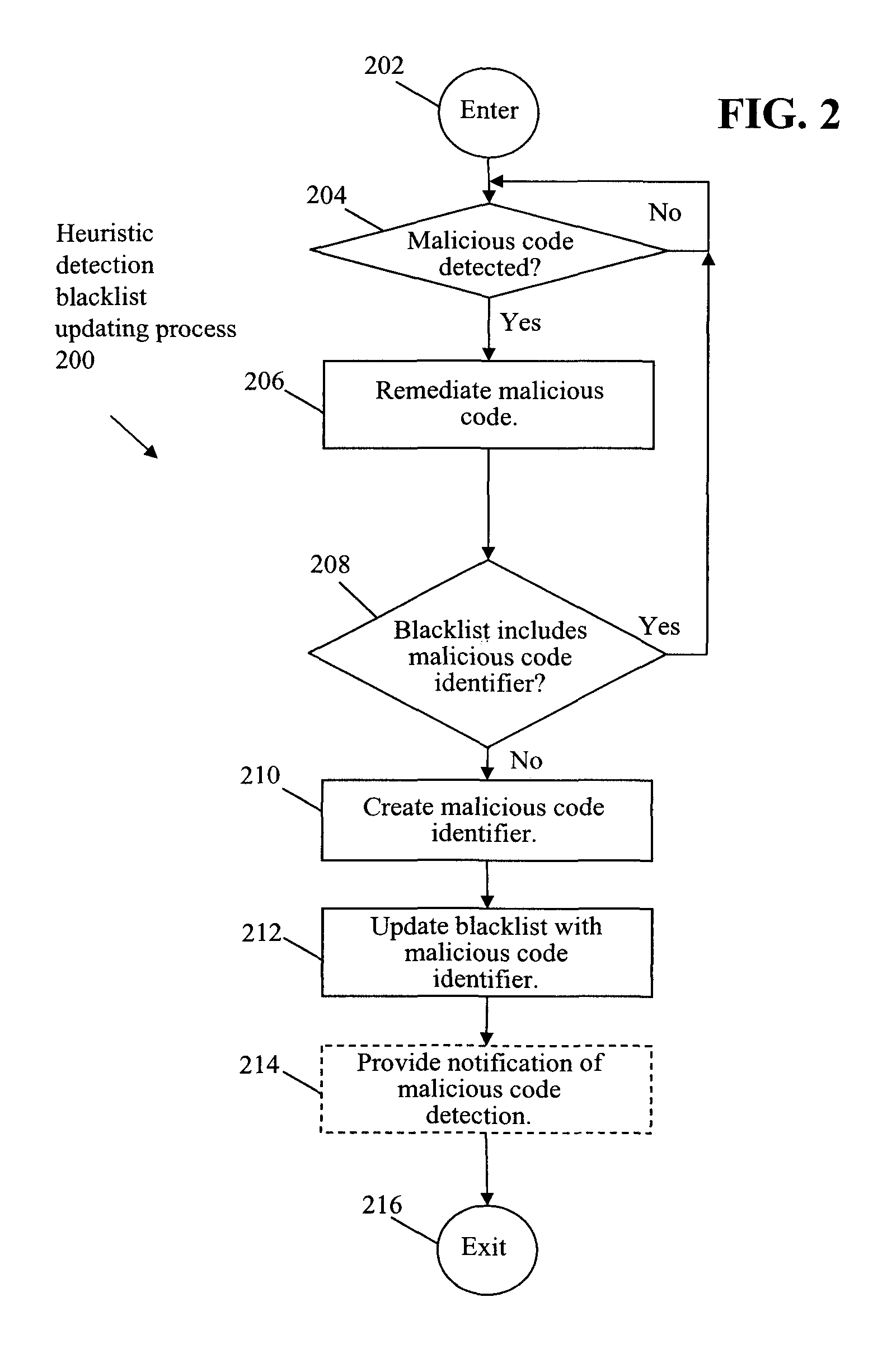
Heuristic detection malicious code blacklist updating and protection system and method
ActiveUS8225405B1Memory loss protectionUnauthorized memory use protectionComputerized systemProtection system
Unknown malicious code is heuristically detected on a host computer system. A virus signature for the malicious code is created locally on the host computer system. A blacklist on the host computer system is updated with the virus signature for the heuristically detected malicious code. Accordingly, the blacklist is updated with the virus signature of the heuristically detected malicious code without distribution of the virus signature to the general public. Further, the host computer system is scanned for other instances of the heuristically detected malicious code using the created virus signature. Accordingly, file based detection and remediation of the malicious code is achieved without requiring execution of the malicious code for detection and the associated risks.
Owner:CA TECH INC
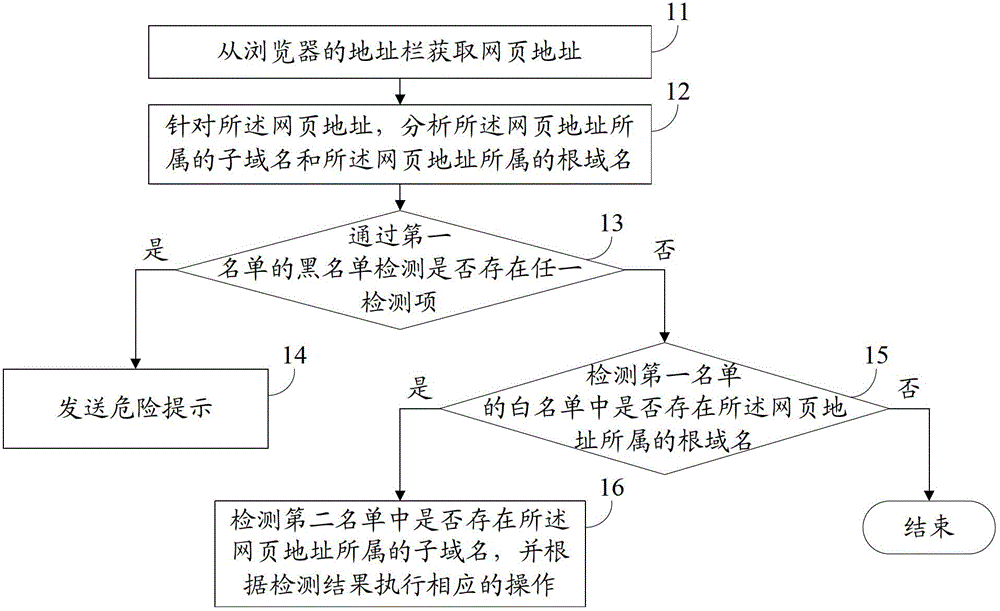
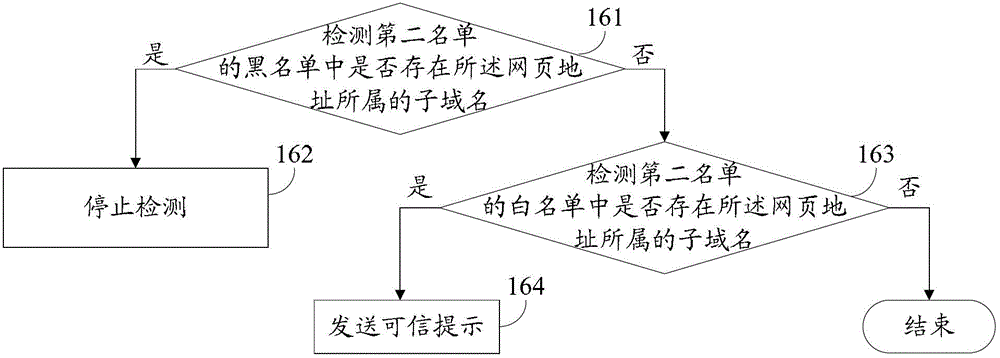
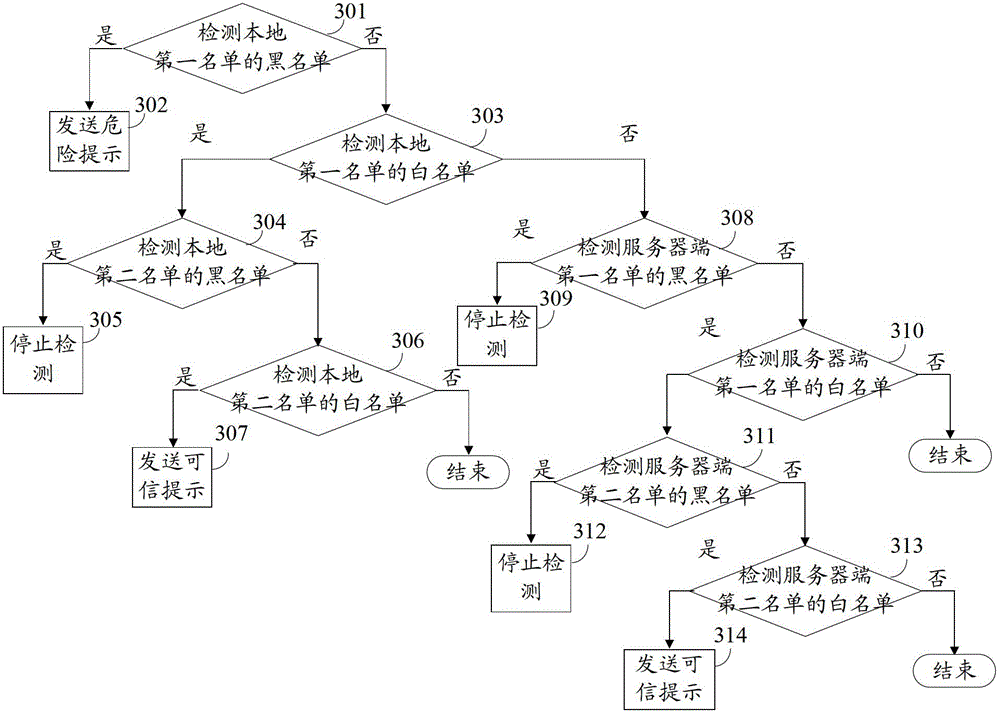
Method and device for safety detection of universal resource locators
The invention provides a method and a device for safety detection of universal resource locators. The method and the device solve the safety problem still remaining in user internet access caused by existing detection methods. After obtained, a universal resource locator is analyzed, and malicious websites can be detected according to a backlist of a first list, and a dangerous prompt is transmitted. As for credible websites in a white list of the first list, subdomain names such as forums and blogs editable to a user under domain names of the credible websites can have safety problems such as phishing by means of some special processing technologies so as to be incredible. Therefore, suspicious subdomain names and credible subdomain names in the credible websites can be detected by the aid of a second list, and the suspicious subdomain names refer to incredible subdomain names, so that the malicious websites and suspicious subdomain names can be guaranteed to be detected by the method and the device, and internet access safety is improved for the user.
Owner:BEIJING QIANXIN TECH
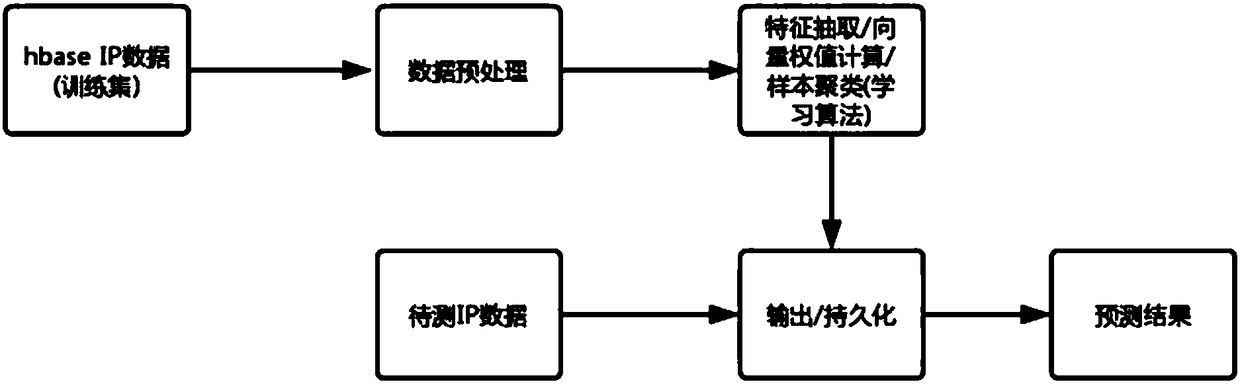
Method for intelligently intercepting threat IP based on cloud protection
The invention relates to the field of Internet security, and aims to provide a method for intelligently intercepting a threat IP based on cloud protection. The method for intelligently intercepting athreat IP based on cloud protection comprises the steps that: after receiving a cloud protection log, a big data log analysis server performs analysis according to a preset analysis rule, and stores the analyzed field information to an hbase cluster; a machine learning cluster establishes an analytic statistics model, the analytic statistics model can identify the behavior characteristics of an IPafter training, the machine learning cluster pushes the threat IP and corresponding domain name information to a cloud protection platform engine in real time, and the cloud protection platform engine dynamically adds the threat IP and the corresponding domain name information to a blacklist after receiving and implements corresponding interruption based on the attack threat level. The IP blacklist has high real-time property, and the configuration can be dynamically added and changed according to the log analysis result to effectively reduce the problem that the rule is bypassed and falselyreported.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
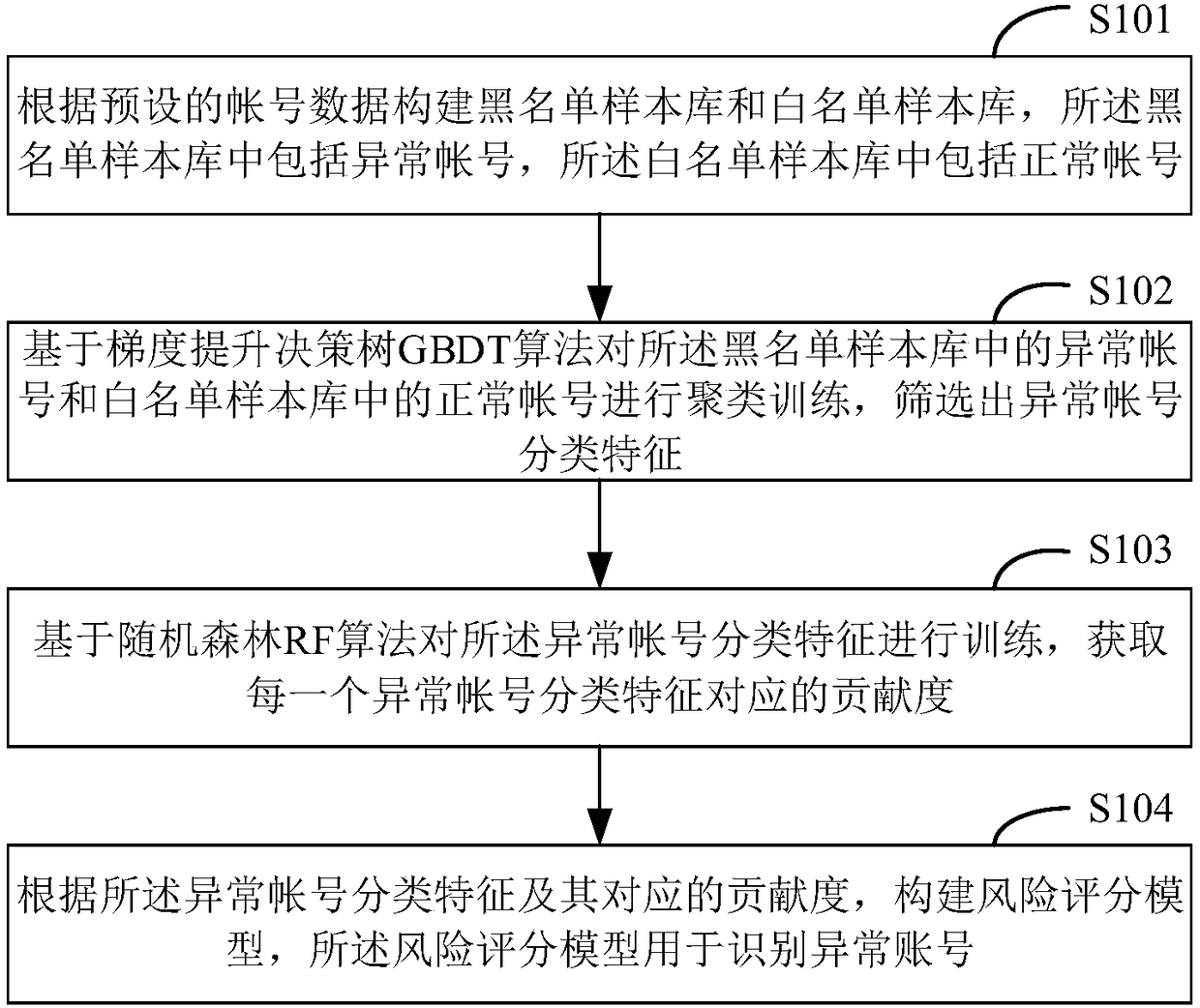
Risk scoring model construction method, device, storage medium and terminal
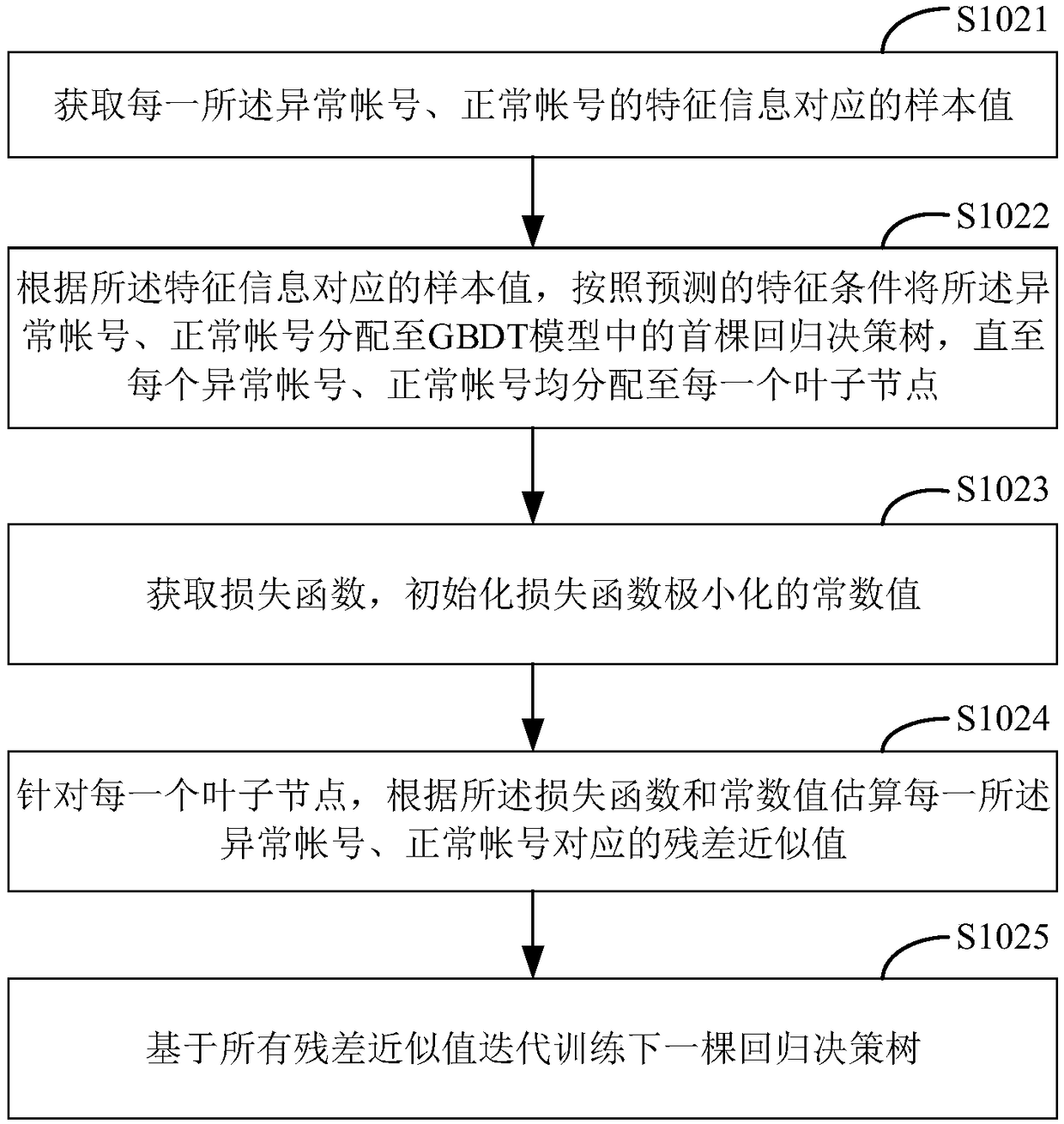
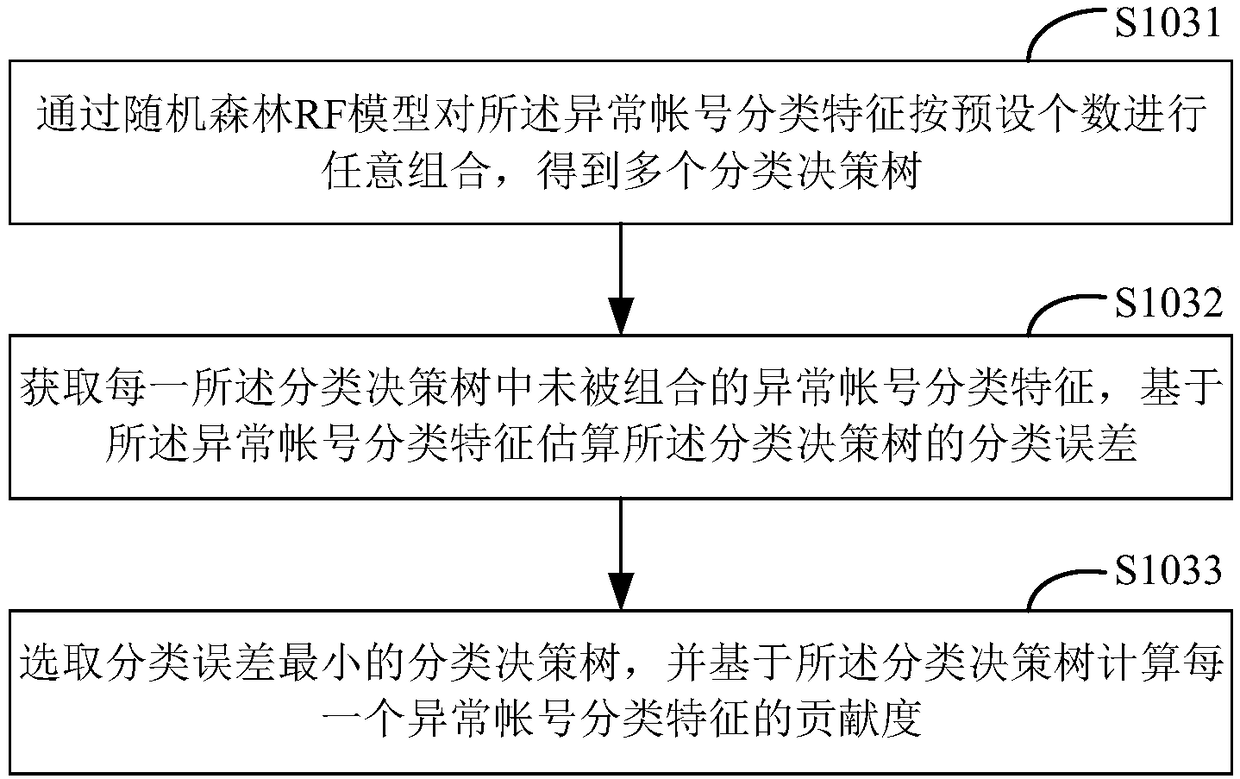
InactiveCN108269012AQuality improvementImprove calculation accuracyFinanceCharacter and pattern recognitionAlgorithmComputer terminal
The present invention provides a risk scoring model construction method. The construction method includes the following steps that: a blacklist sample library and a whitelist sample library are constructed according to preset account data, wherein the blacklist sample library includes abnormal accounts, and the whitelist sample library includes normal accounts; cluster training is performed on theabnormal accounts in the blacklist sample library and the normal accounts in the whitelist sample library on the basis of a gradient boosting decision tree (GBDT) algorithm, and abnormal account classification features are screened out; the abnormal account classification features are trained on the basis of a random forest (RF) algorithm, and a contribution degree corresponding to each abnormalaccount classification feature is obtained; and a risk scoring model is constructed according to the abnormal account classification features and the contribution degrees corresponding to the abnormalaccount classification features, and the risk scoring model is used for identifying the abnormal accounts. The risk scoring model constructed by the method of the invention improves the timeliness ofclearing the abnormal accounts, reduces noise interferences caused by the abnormal accounts, and improves the calculation precision of many indicators of APPs.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
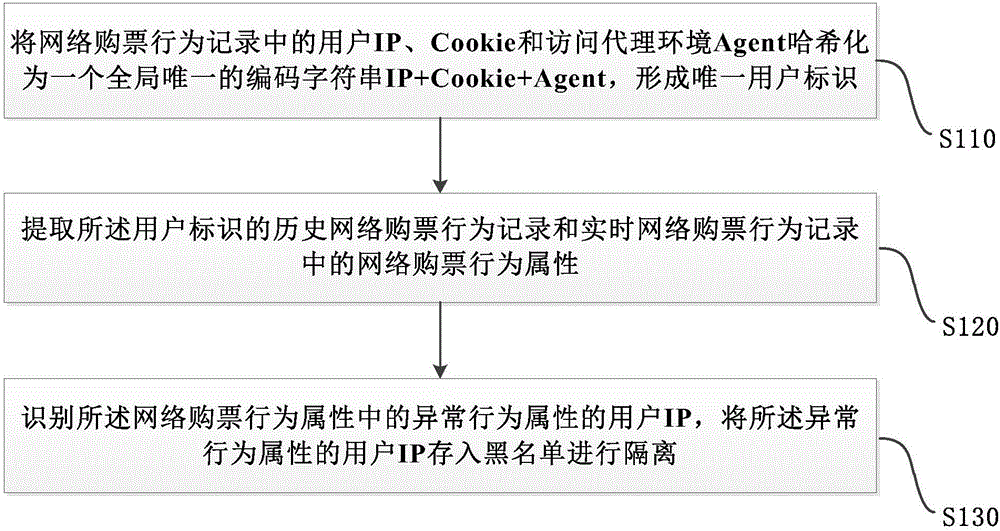
Network ticket buying abnormal behavior recognition method and system and equipment
The invention provides a network ticket buying abnormal behavior recognition method and system and equipment. The method comprises the steps that user IP, Cookie and access proxy environment Agent hashing in network ticket buying behavior records are adopted as global unique encoding character string IP+Cookie+Agent, and a unique user identifier is formed; network ticket buying behavior attributes in historic network ticket buying behavior records and real-time network ticket buying behavior records of the user identifier are extracted; the user IP with the abnormal behavior attribute in the network ticket buying behavior attribute is recognized, and the user IP with the abnormal behavior attribute is stored into a blacklist to be isolated. According to the network ticket buying abnormal behavior recognition method and system and equipment, various thresholds of ticket resale can be determined and recognized, and the data judgment basis is provided for determination of ticket resale. Behavior characteristics of users are recorded in real time, and the real-time basis can be provided for real-time interception of ticket resale; the blacklist can be built, the ticket resale can be intercepted in advance on the basis of the blacklist, and resource distribution is more reasonable and fairer.
Owner:BEIJING HONGMA MEDIA CULTURE DEV
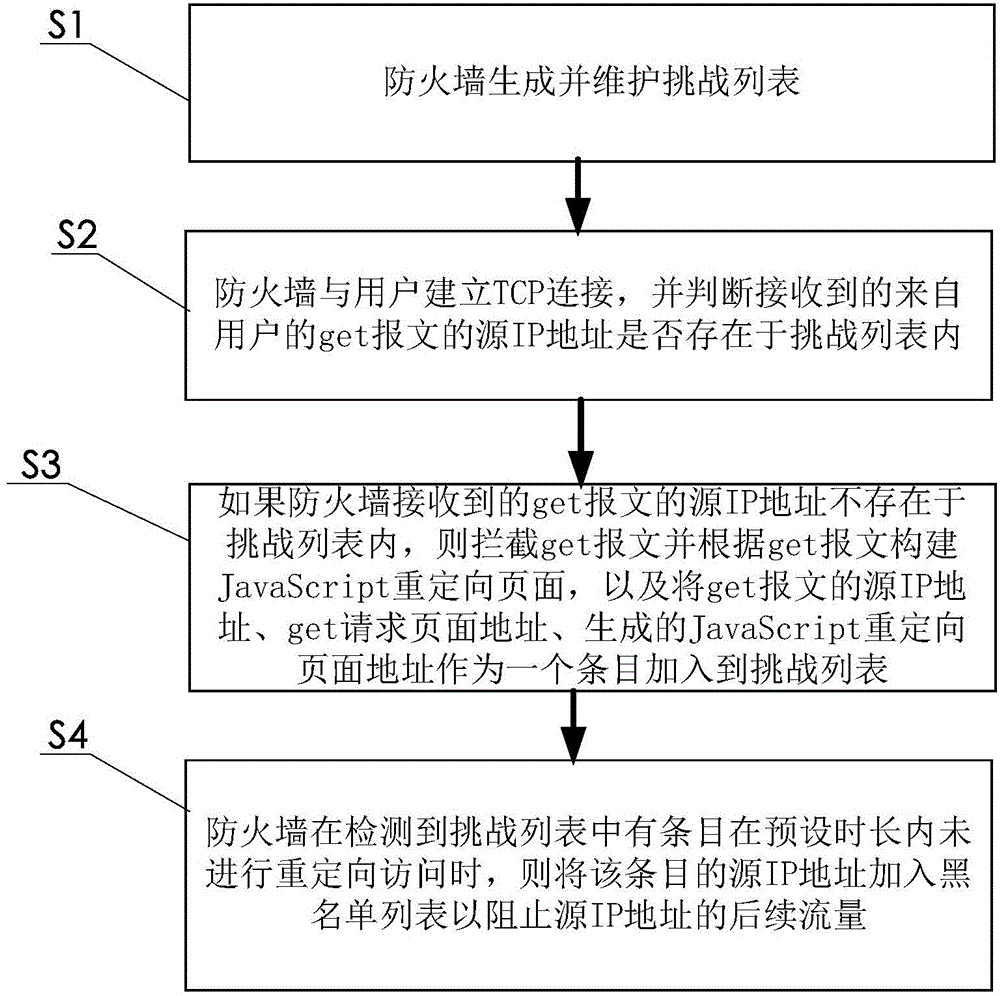
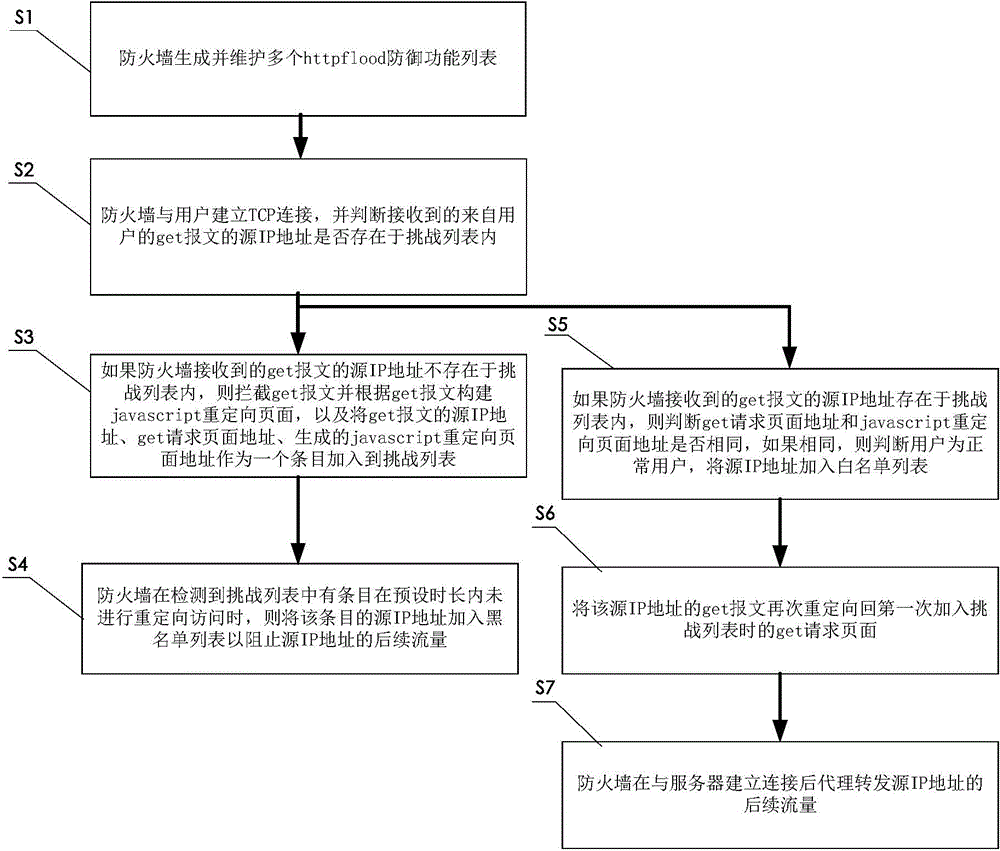
Method for preventing HttpFlood attack and firewall
The invention provides a method for preventing an HttpFlood attack. The method includes the steps that a firewall generates and maintains a challenge list; the firewall establishes TCP connection with a user and judges whether a source IP address of a get message received from the user exist in the challenge list; if the source IP address of the get message received by the firewall does not exist in the challenge list, the firewall intercepts the get message and establishes a JavaScript redirection page according to the get message and adds the source IP address of the get message, the address of a get request page and the generated address of the generated JavaScript redirection page into the challenge list; when the firewall detects that an entry in the challenge list does not have a redirection access in a preset duration, the firewall adds the source IP address of the entry into a blacklist so as to prevent the subsequent traffic of the source IP address. The invention further provides the firewall for preventing the HttpFlood attack. Through the method, the firewall will not make a misjudgment, so the judgment accuracy rate is high.
Owner:OPZOON TECH
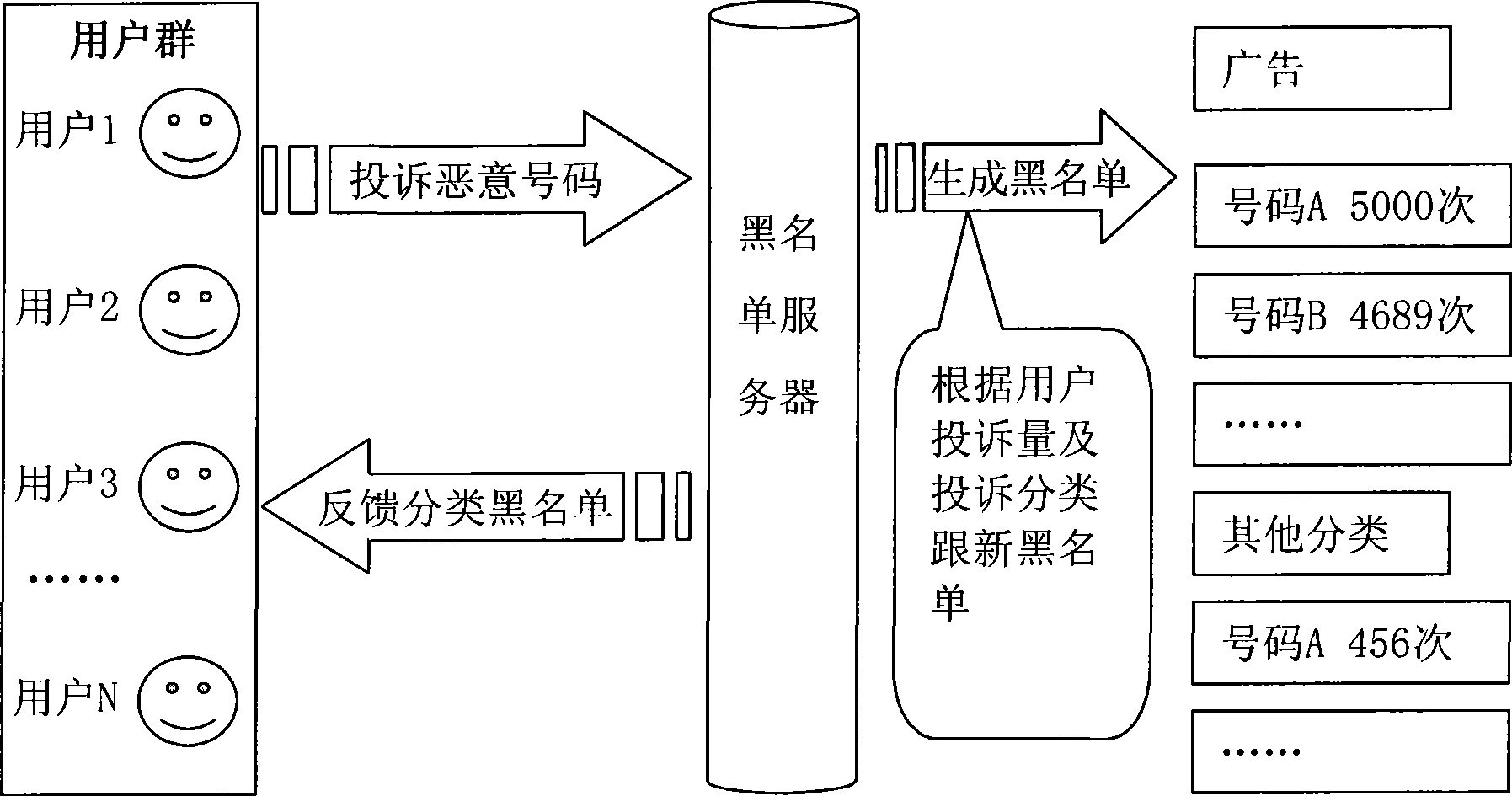
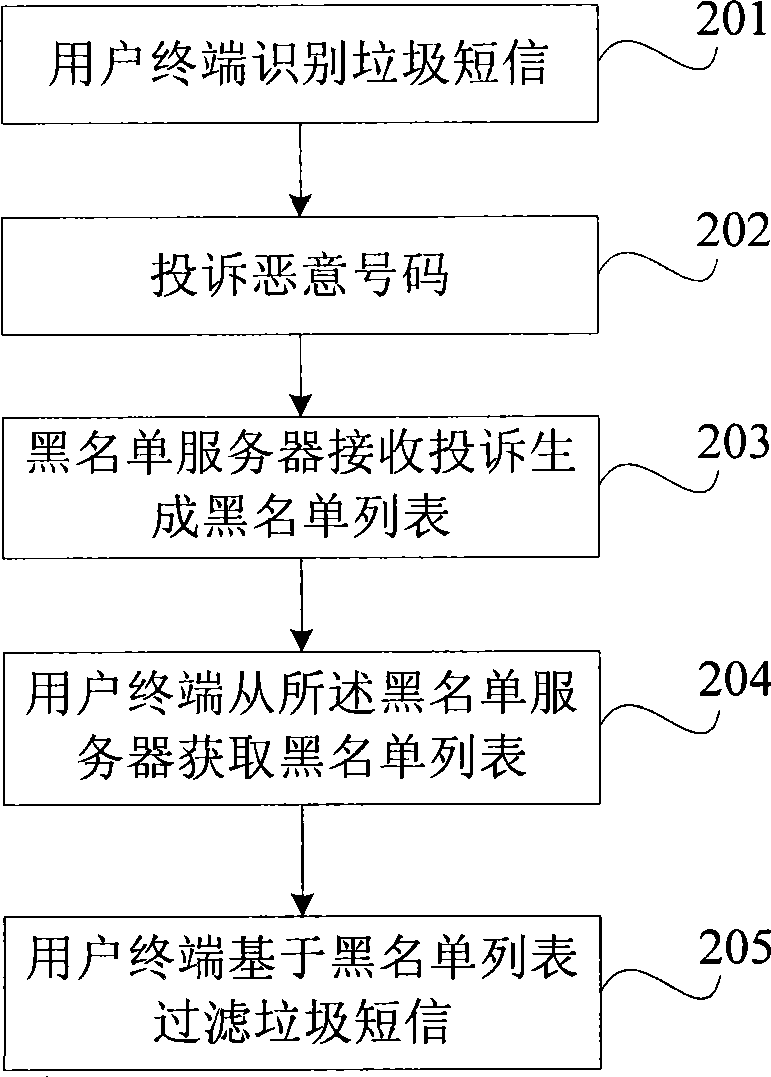
Method and apparatus for filtrating rubbish short message
InactiveCN101415161AIncrease success rateSubstation equipmentMessaging/mailboxes/announcementsLitterFiltration
The invention provides a method for filtering litter messages and a device thereof. The method comprises: a litter message sending party number blacklist is acquired from a server; the blacklist comprises the telephone number complained by a user terminal in the server user group; the litter message is filtered based on the telephone number of the acquired blacklist. By adopting the embodiment of the invention, the blacklist is generated based on the complaint of the user terminal in the user group, thus improving the success ration of litter message filtration.
Owner:HUAWEI DEVICE (SHENZHEN) CO LTD
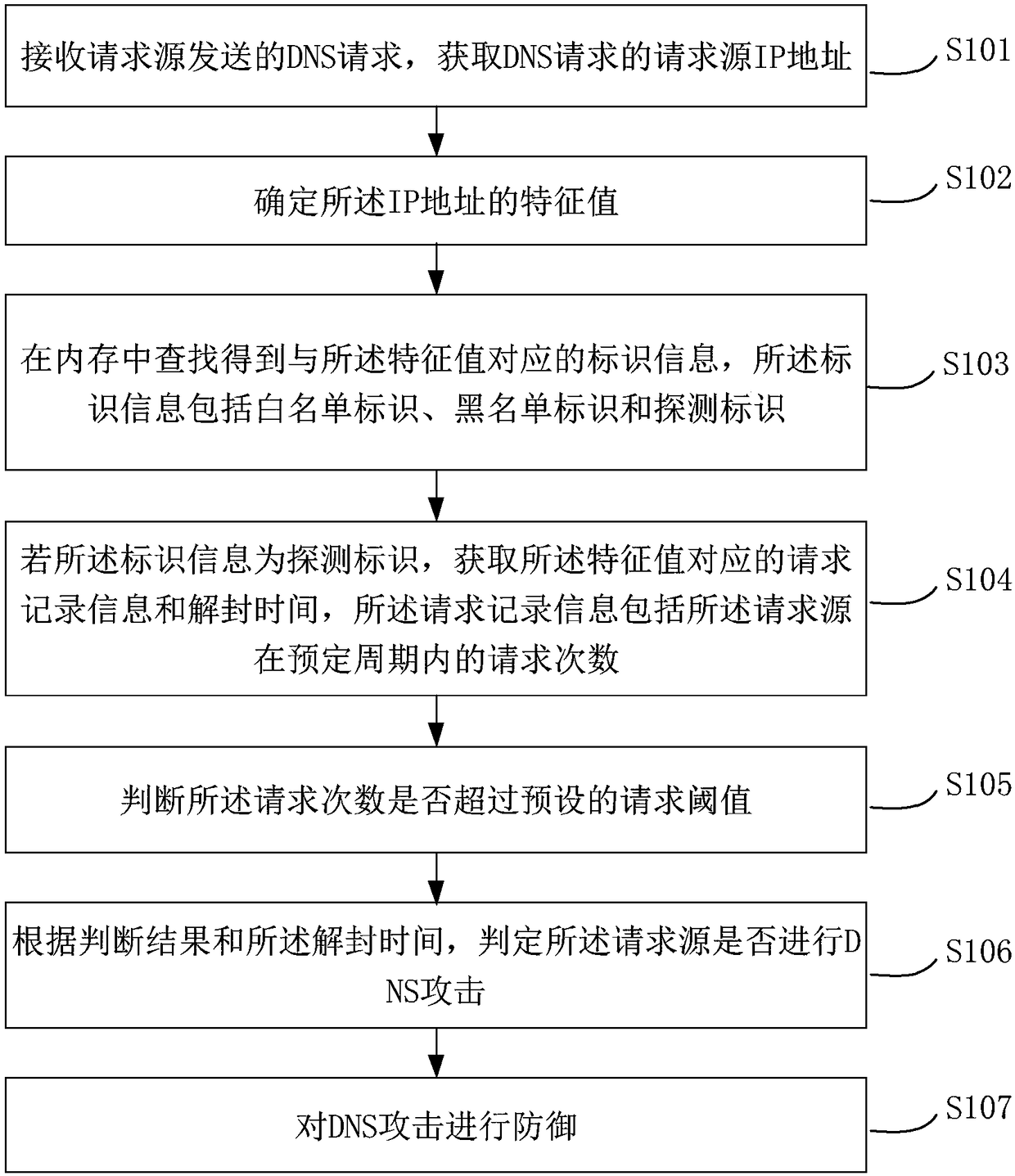
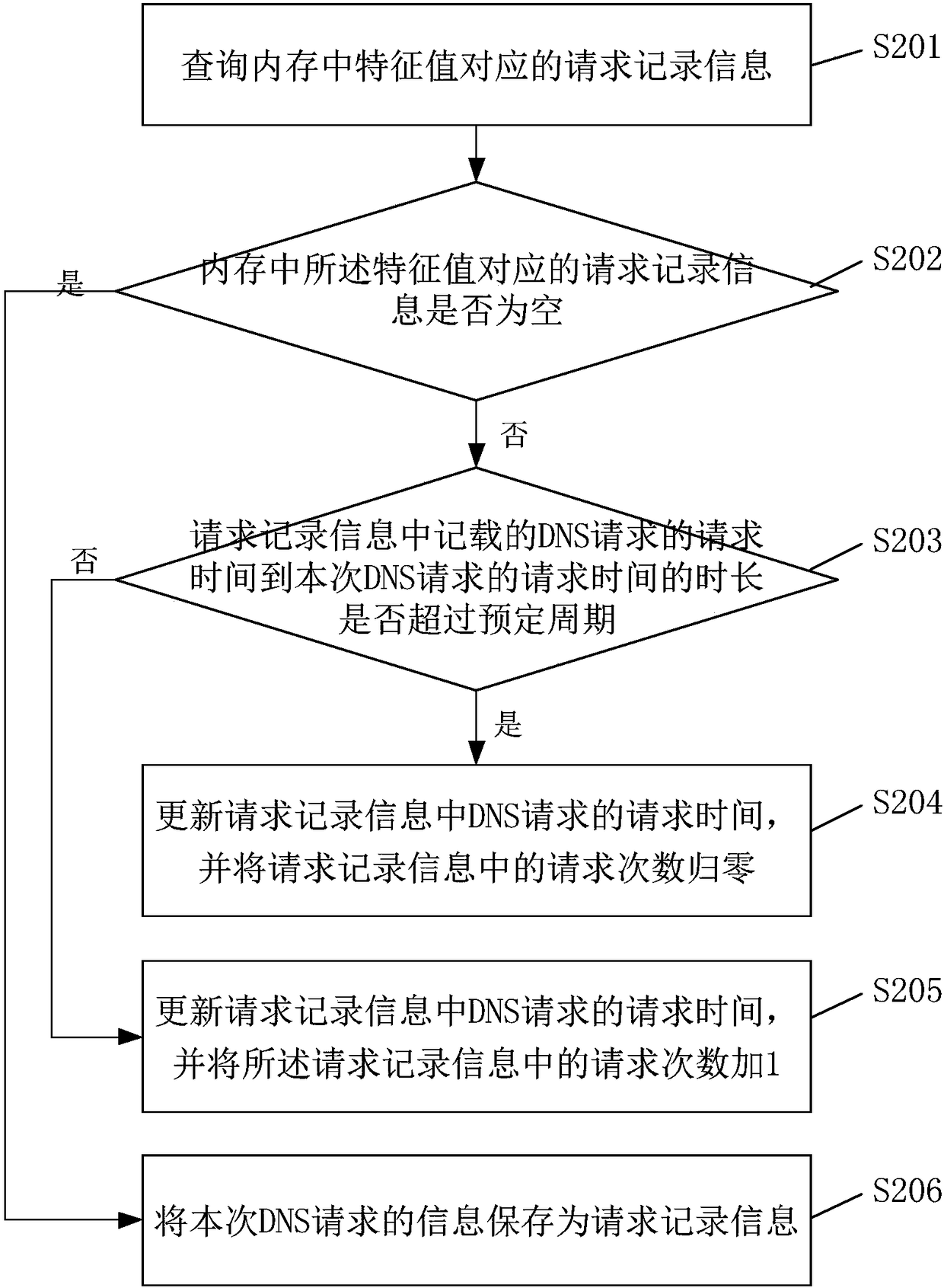
DNS attack defense method, device and system
ActiveCN108206814AThe judgment process is simpleImprove the efficiency of judging DNS attacksUser identity/authority verificationDomain nameWhitelist
The invention relates to the computer safety technology field and particularly relates to a DNS attack defense method, device and system. The method comprises steps that after DNS requests are received, the corresponding identifier information is searched in a memory according to association data of the DNS requests, the whitelisted or unpacked identifier DNS requests are responded to, the blacklisted or banned identifier DNS requests are defended, for the DNS requests with detection identifiers, the request frequency within the predetermined period is determined, the DNS requests surpassing the request threshold are defended, for the DNS requests not surpassing the request threshold, unpacking time determination is carried out, the DNS requests reaching the unpacking time are responded to, and the DNS requests not reaching the unpacking time are defended. The method is advantaged in that the identifier information is preset, determined request sources or domain names a re directly responded or defended, for the undetermined request sources or domain names, further determination and detection are carried out, the DNS attack determination flow is simplified, and DNS attack determination efficiency is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
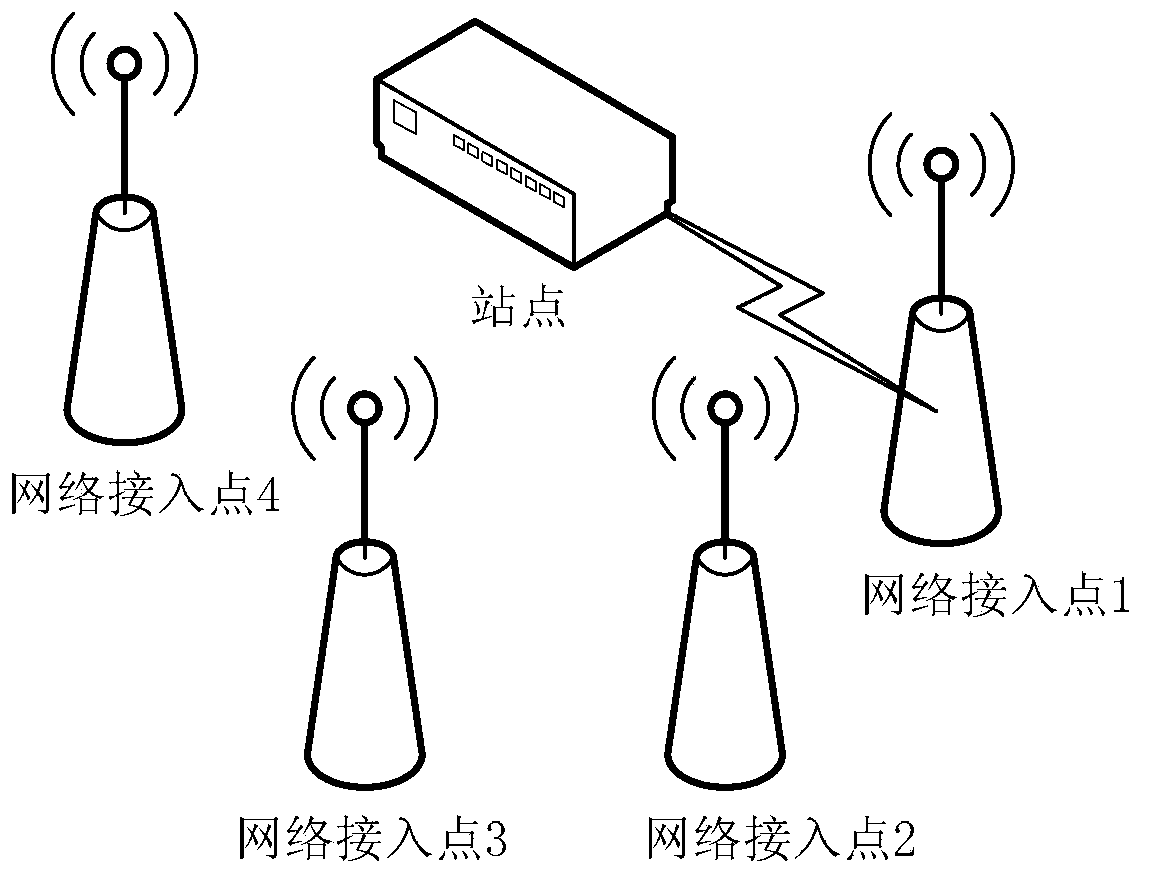
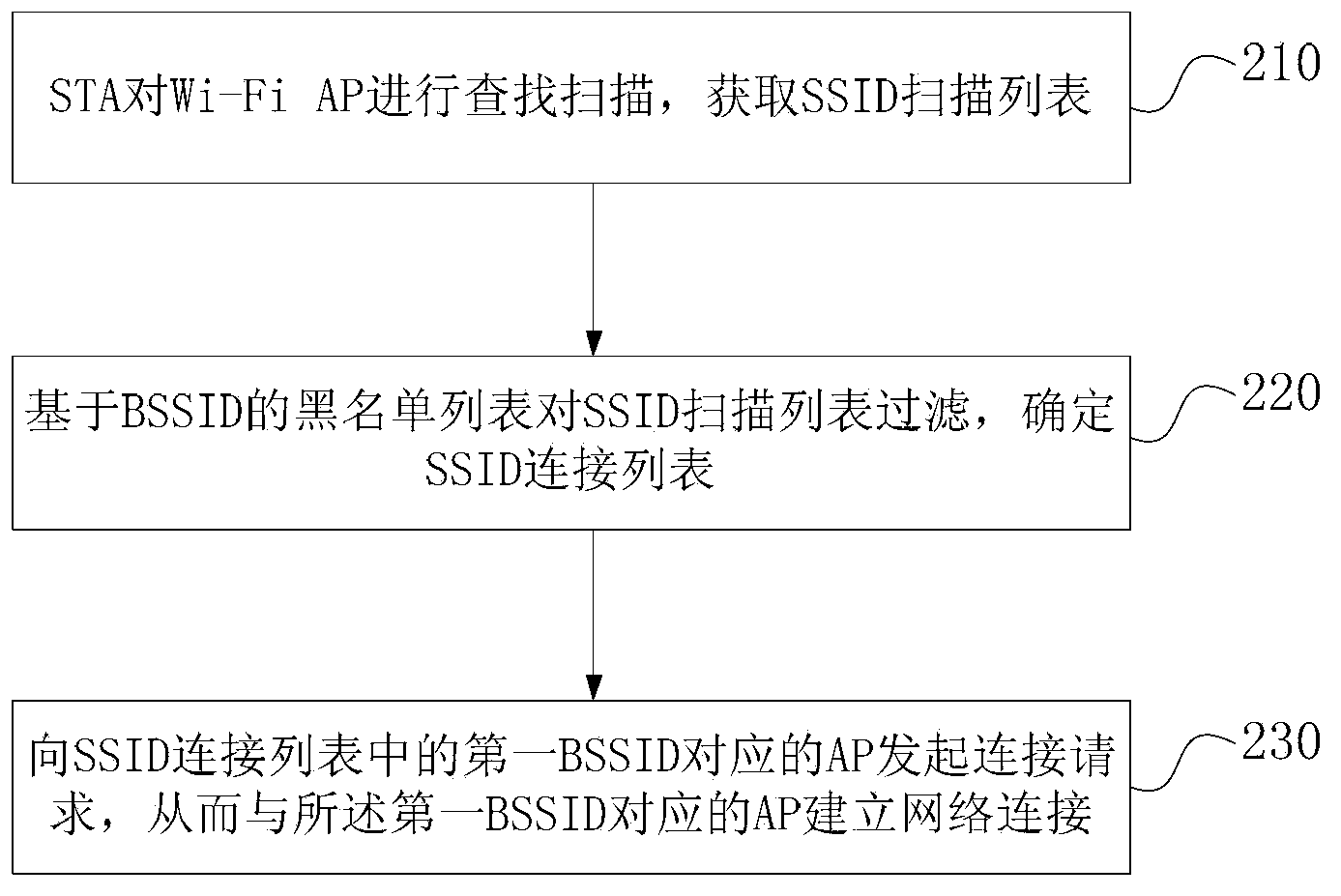
Method and device for achieving rapid network connection
InactiveCN104080148AImprove access network efficiencyImprove efficiencyAssess restrictionConnection managementWi-FiNetwork connection
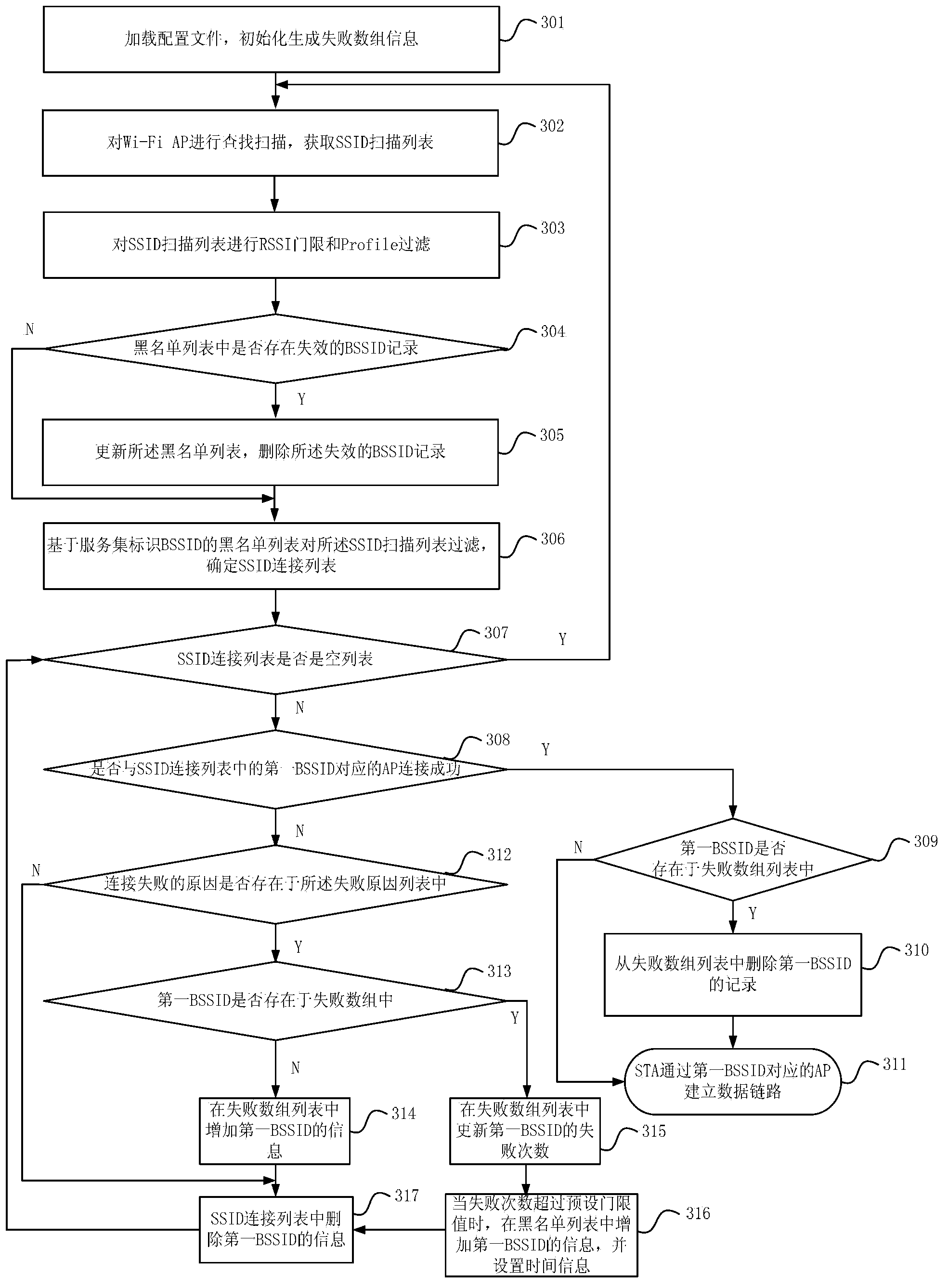
The embodiment of the invention discloses a method and device for achieving rapid network connection. The method includes the steps that a Wi-Fi STA searches for and scans Wi-Fi APs, so that an SSID scanning list is obtained; based on a blacklist of BSSIDs, the SSID scanning list is filtered, and an SSID connecting list is determined; the AP corresponding to the first BSSID in the SSID connecting list is accessed, so that network connection is established. Through addition of dynamic blacklist management, the BSSIDs with access failure are recorded, so that when the STA has access to the SSIDs, the condition that the STA tries to have access to the SSIDs which are not available is avoided, and the network access efficiency of the STA is improved.
Owner:HUAWEI DEVICE CO LTD
Method and system for preventing telecommunication fraud by using No.7 signaling message of switch
ActiveCN102572124ACall autoRaise awareness of preventionMetering/charging/biilling arrangementsAccounting/billing servicesSignal onRisk awareness
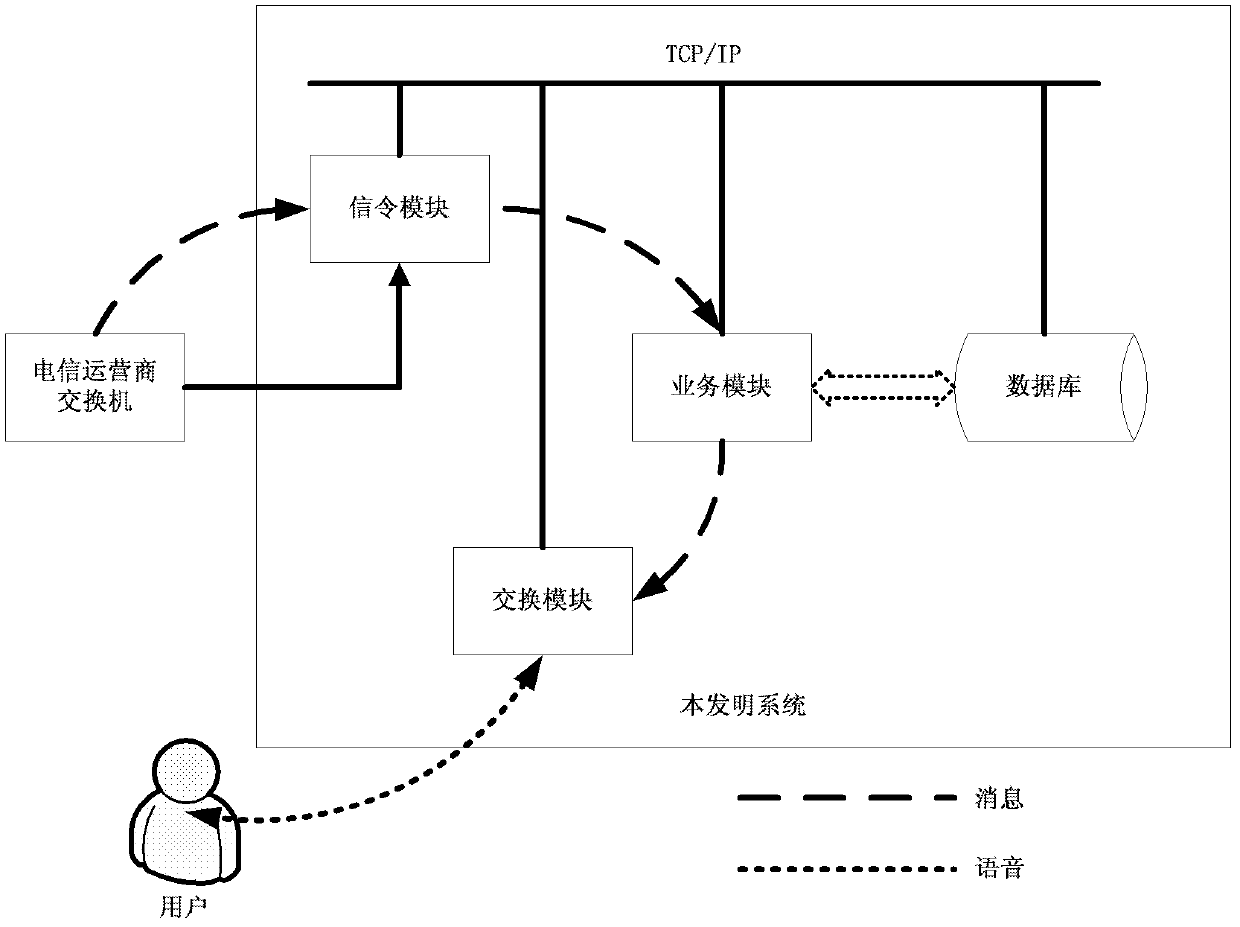
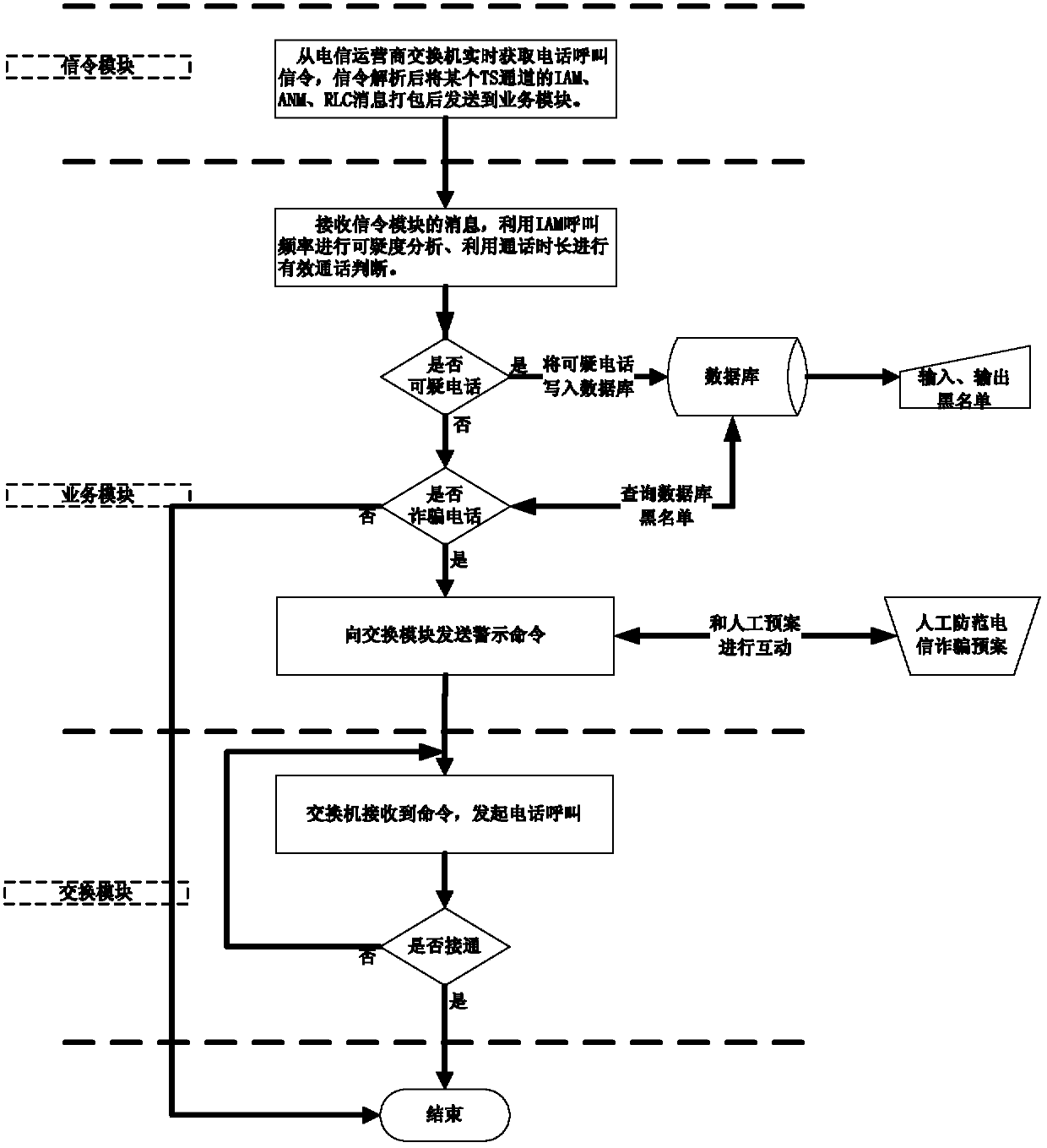
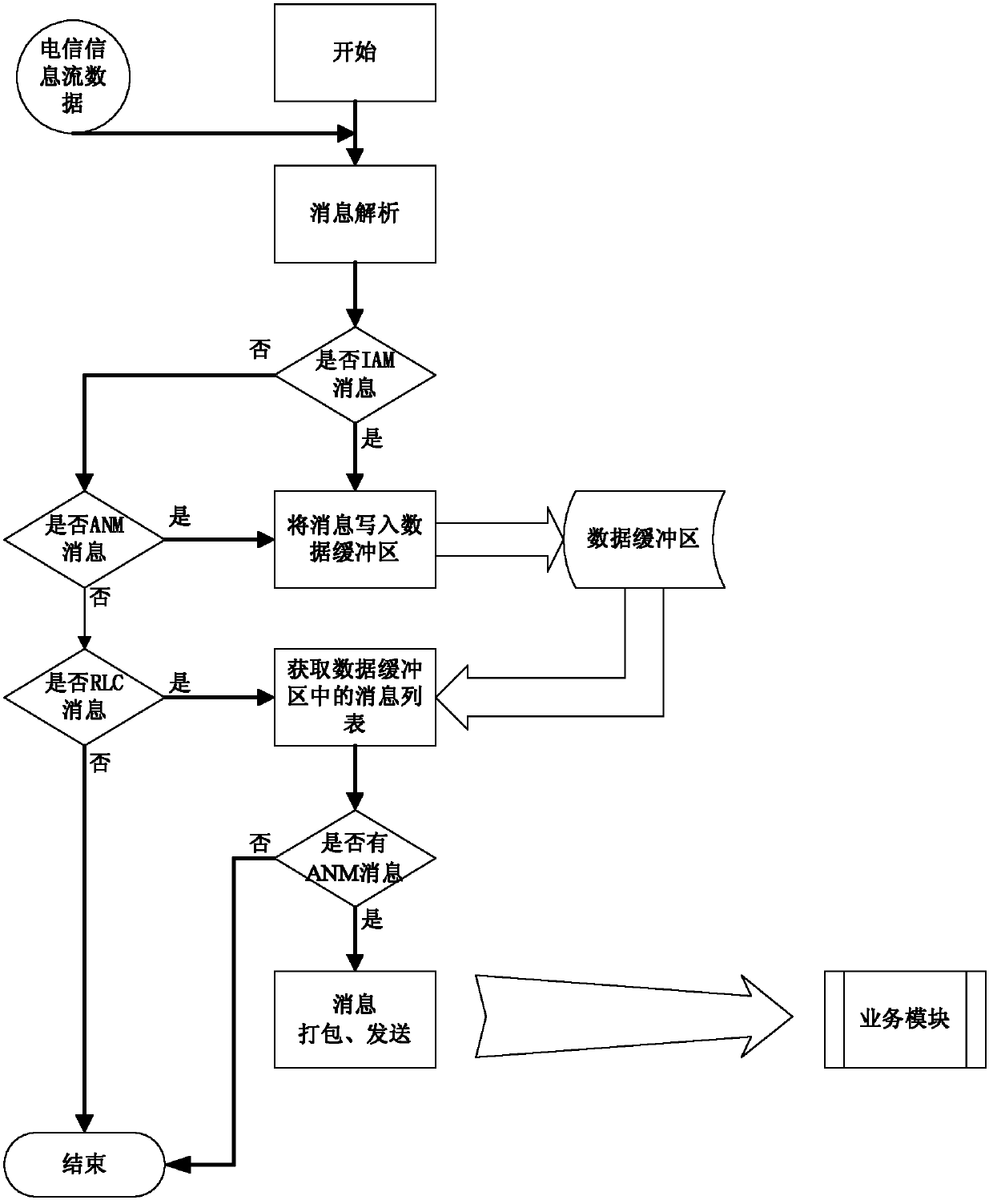
The invention discloses a method and a system for preventing telecommunication fraud by using signaling messages of a switch No.7. In the invention, the NO.7 message in the telephone call is used, so as to design the method and the device for preventing telecommunication fraud. According to the invention, through monitoring telephone call signaling on line in real time and carrying out activities such as suspiciousness analysis to the calling number in a signaling message, blacklist matching and the like, whether the calling telephone is suspicious or fraud can be determined, after users of both sides end up the call, a telephone for originating call can call an aggrieved party in time, and after the user receives the call, warning speeches can be played automatically so as to remind the user to enhance a risk awareness and put an end to further development of a fraud case. After the adoption of the invention, through concurrent precaution to cases in an on-line dynamic way, the cases are ended up, and an excellent precaution effect can be achieved.
Owner:XIAN DATANG TELECOM
Dynamic denial of service detection and automated safe mitigation
Methods, systems, and computer programs are presented for automated detection and mitigation of Denial of Service (DoS) attacks. One method includes an operation for collecting traffic data from service network routers that provide users access to a service. The traffic data is applied to security rules to identify a blacklist of illegitimate users to be blocked. Further, the method receives from the one or more servers a whitelist with information regarding legitimate users and their geographical location. A safe blacklist is determined for each router based on the blacklist and the whitelist, and the respective safe blacklist is sent to each router. Legitimate users are not blocked from accessing the service, but an illegitimate user spoofing a legitimate user is blocked by the routers when trying to access the service from a geographic location that is not the geographic location of the legitimate user.
Owner:SONY INTERACTIVE ENTRTAINMENT LLC
Method and system for preventing crank calls
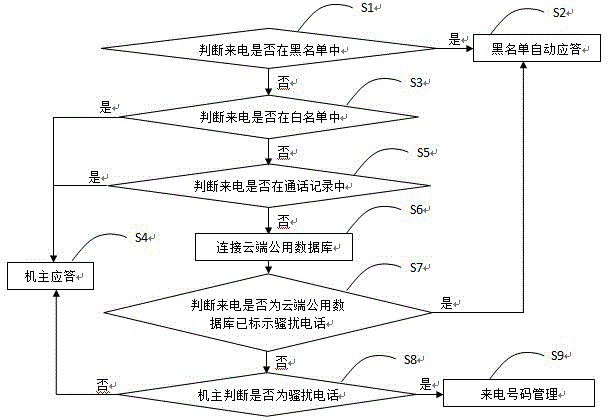
InactiveCN104601782ASolve repeated rejectionsTime consumingCalling susbscriber number recording/indicationBlacklistingTelephony
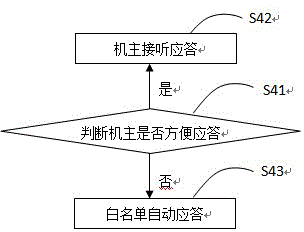
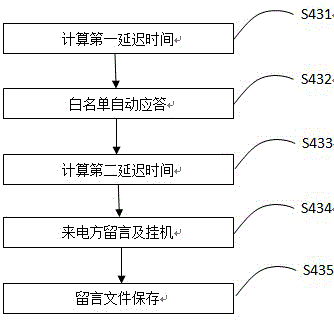
The invention discloses a method for preventing crank calls, including the following steps of: judging a calling number is within a blacklist, if yes, judging to be a crank call, and starting blacklist automatic response; if no, further judging whether the calling number is within a white list or owner call records, if yes, starting owner response; if no, connecting a cloud public database, judging whether the calling number is a crank call which is labeled in the cloud public database, if yes, judging to be the crank call, and starting blacklist automatic response; if no, allowing the owner to judge whether the calling number is the crank call, if yes, directly hanging up, and entering calling number management; if no, starting owner response. Compared with the mode in the prior art that the crank calls are rejected, the method is opposite and adopts an automatic answer mode, which not only consumes the time and expense of callers, and also spiritually combats the enthusiasm of the callers, so that the calling targets of the callers cannot be achieved, and the crank calls can be effectively prevented.
Owner:POWER IDEA TECH (SHENZHEN) CO LTD
Method for implementing black sheet
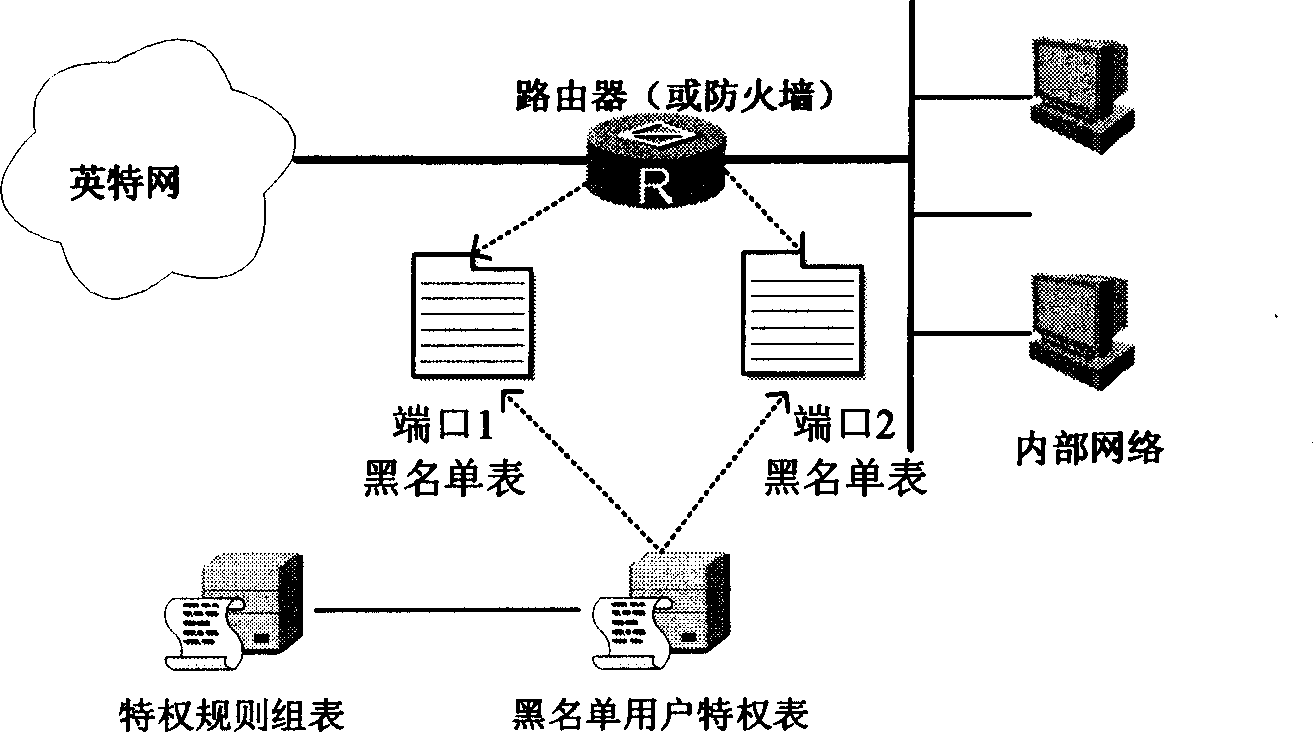
ActiveCN1874303AIncrease flexibilityImprove effectivenessData switching networksIp addressBlacklisting
The method comprises: a) receiving message from one port of system, and analyzing the received message to get its source IP address; b) checking said source IP address to decide if it is in the blacklist of said port; if yes, discarding said message. Taking port as the scope of influence of blacklist can avoid an expanding of blacklist scope caused by the address cheating or other attack, which can influence normal operation of users; the user in blacklist is not limited to visit a trusted site in which the access privilege has been set; the visit to a dedicated network from a privilege user can be implemented by setting a privilege rule.
Owner:HUAWEI TECH CO LTD
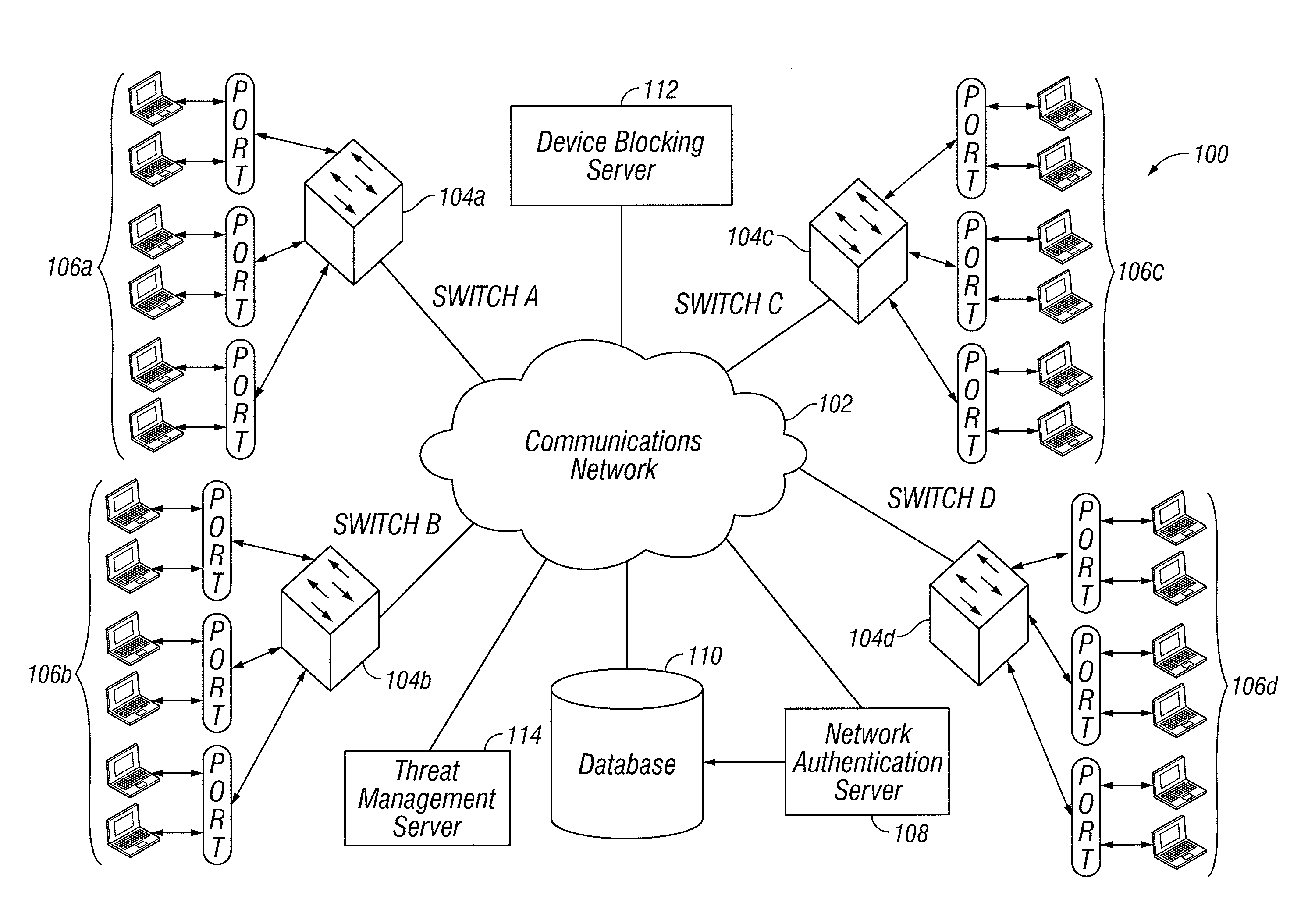
Device blocking tool
ActiveUS20170034161A1Eliminates and reduces disadvantageEliminates and reduces and problemComputer security arrangementsTransmissionComputer hardwareNetwork strategy
Automated locating and disconnection of undesired devices may include receiving a unique address of a candidate device, determining the address of the switch coupled to the candidate device based on the address of the candidate device, accessing the switch using the switch address, receiving switch information from the switch, receiving credentials from the user and commands to transform the candidate device into a disconnected state, and determining whether the user is permitted to execute the commands based on the credentials from the user. If it is determined that the user is permitted to execute the commands, the candidate device may be transformed into a disconnected state on the network and its address may be added to a blacklist. A device may be deemed to be undesired on the network due to intrusion events, violation of network policies, or other appropriate criteria.
Owner:BANK OF AMERICA CORP
Automatically Modifying Wireless Network Connection Policies Based on User Activity Levels
ActiveUS20130331101A1Reduce in quantityAmount of timeAssess restrictionWireless commuication servicesWireless mesh networkNetwork connection
Modifying network connection policies of a wireless device based on user activity levels. One or more activity indicators of the wireless device may be monitored. One or more criteria for wireless network blacklisting may be selected based on the one or more activity indicators. The criteria may include different types of connectivity problems. A wireless network may be detected. The wireless network may be monitored for connectivity problems. The wireless network may be blacklisted if connectivity problems meeting the selected criteria for wireless network blacklisting are determined to have occurred.
Owner:APPLE INC
Industrial control information safety monitoring system adopting black and white lists for analysis
InactiveCN110868425AEnhancing fine-grained analysisImprove accuracyTransmissionMonitoring systemWhitelist
The invention relates to the field of industrial control system information safety, in particular to an industrial control information safety monitoring system adopting a black list and a white list for analysis, which comprises the following steps of: (1) collecting an initial sample library; (2) blacklist rule formation and alarm generation; (3) white list rule formation and alarm generation; (4) intelligently generating a communication white list; (5) protocol rule formation and alarm generation; and (6) performing visual alarm and report display. The beneficial effects of the invention arethat the system carries out the credible monitoring of assets in the industrial control network, carries out the credible monitoring of communication in the industrial control network, carries out the deep analysis of a plurality of industrial protocols, carries out the visual display of a topological structure of the industrial control network, and carries out the report statistics of a threat form in the industrial control network; the method is beneficial to realization of abnormal monitoring in the network, is beneficial to realization of quick positioning and troubleshooting of problem assets and problem communication behaviors, is beneficial to avoiding human operation errors, improves the accuracy of a white list, reduces missing reports and false reports, and constructs a monitoring system easy to operate and capable of quickly positioning problems.
Owner:上海三零卫士信息安全有限公司
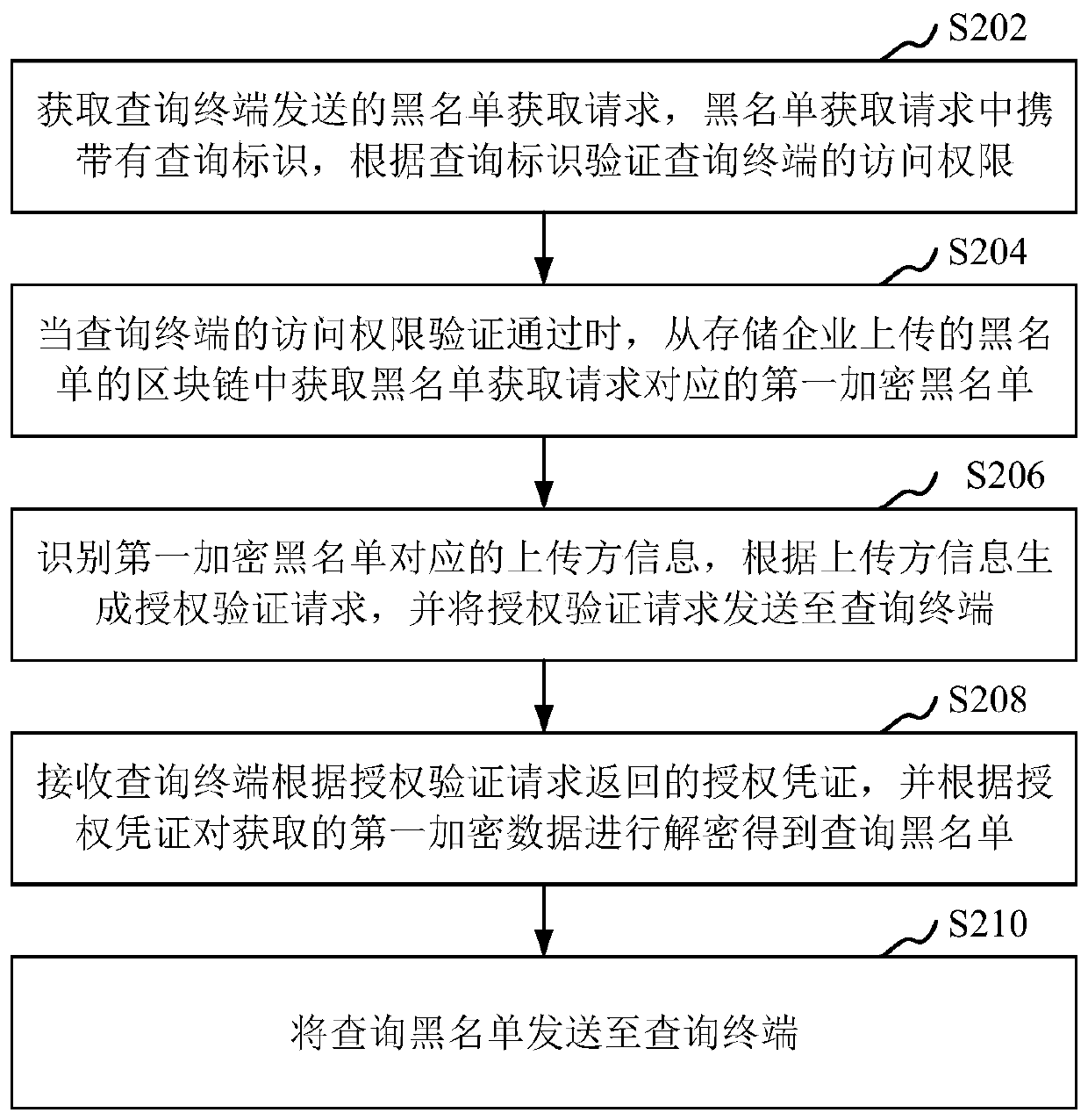
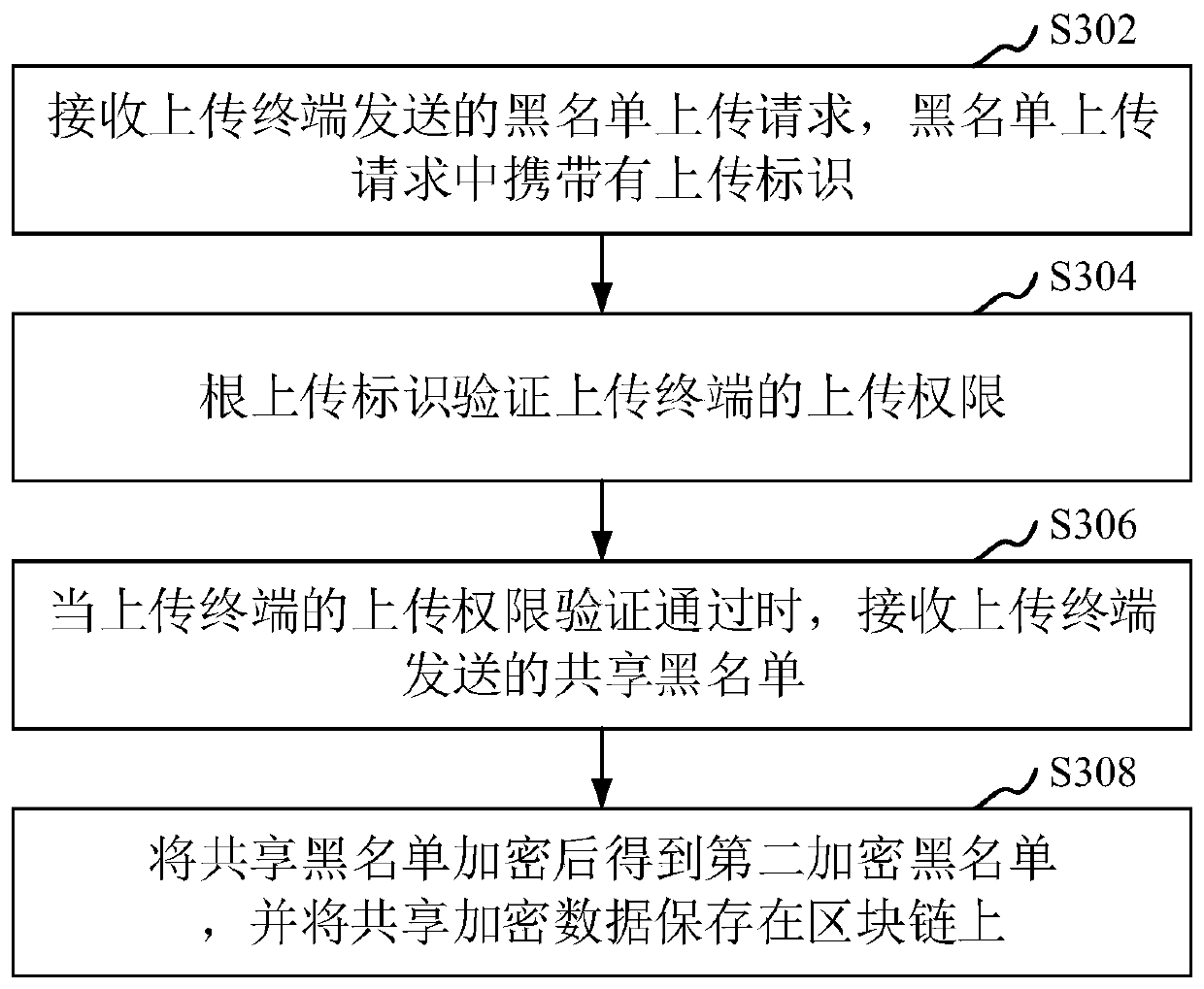
Blacklist sharing method and device, computer device and storage medium
ActiveCN110365670APrevent tamperingRealize safe circulationDatabase updatingUser identity/authority verificationAuthorization certificateComputer terminal
The invention relates to the field of block storage areas, in particular to a blacklist sharing method and device, a computer device and a storage medium. The method comprises: obtaining a blacklist obtaining request sent by a query terminal, the blacklist obtaining request carrying a query identifier, and verifying the access permission of the query terminal according to the query identifier; obtaining a first encrypted blacklist corresponding to the blacklist obtaining request from a block chain storing the blacklist when the access permission of the query terminal passes verification; identifying uploading party information corresponding to the first encryption blacklist, generating an authorization verification request according to the uploading party information, and sending the authorization verification request to a query terminal; receiving an authorization certificate returned by the query terminal according to the authorization verification request, and decrypting the obtained first encryption blacklist according to the authorization certificate to obtain a query blacklist; and sending the query blacklist to a query terminal. By adopting the method, safe circulation of blacklist data among multiple enterprises can be effectively realized.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
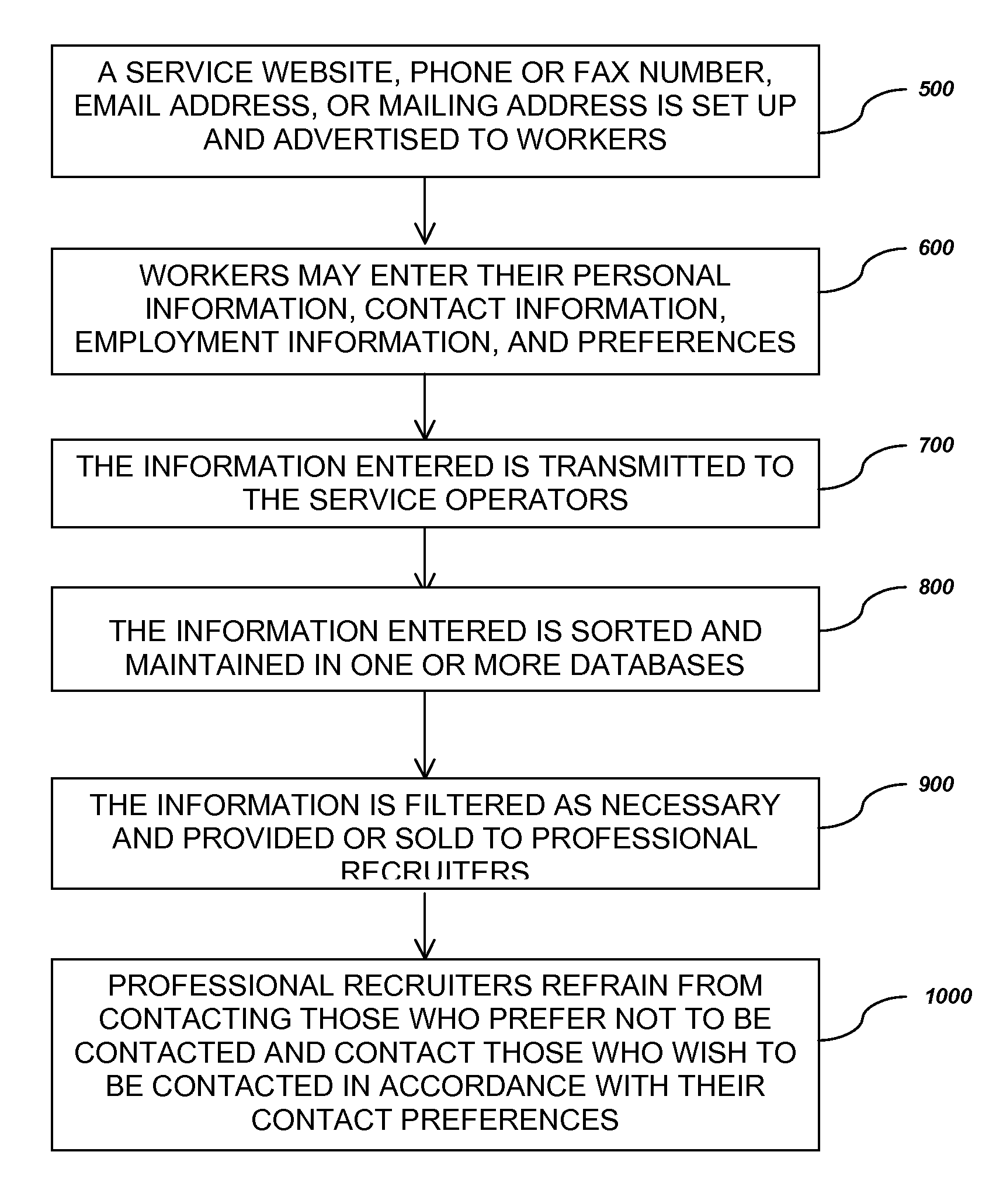
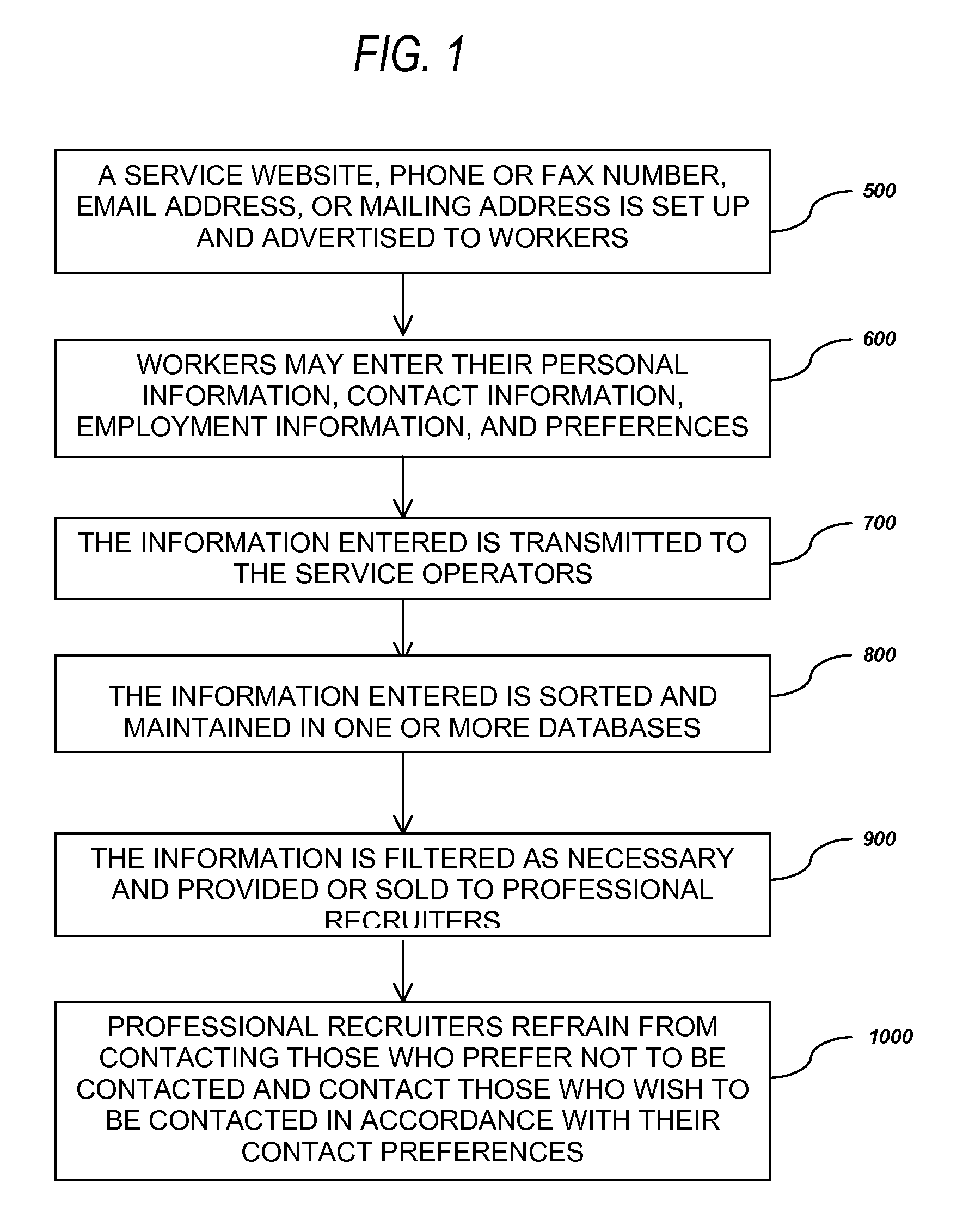
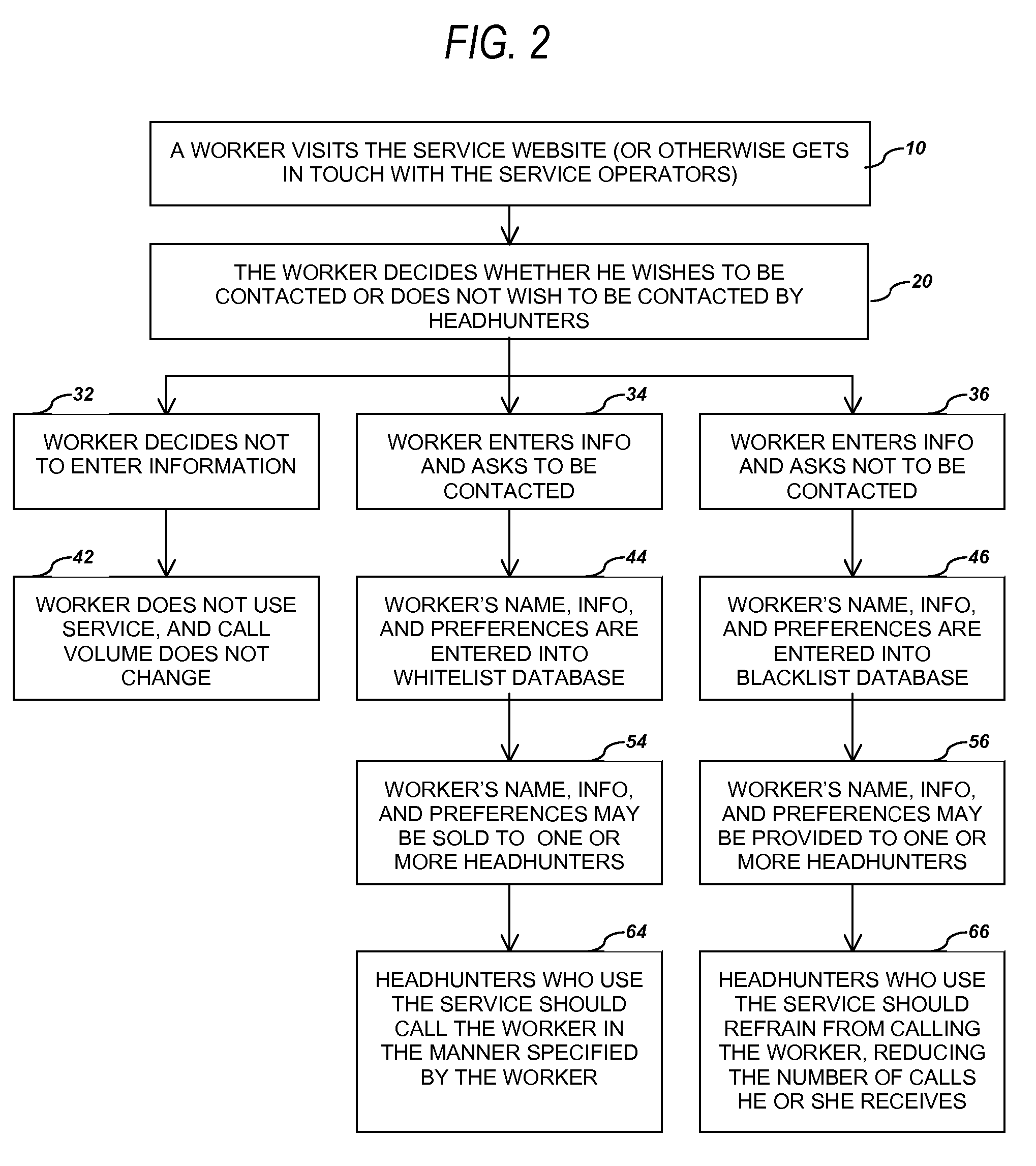
Procedure to collect, maintain, and distribute workers' preferences for professional recruiter contact
A system for collecting, maintaining, and distributing information and preferences of workers regarding whether and how they wish to be contacted by professional recruiters (or “headhunters”). Such a system involves the workers entering identifying information (e.g., name, profession, phone number, address, etc.) and their preferences though an Internet website, email, telephone, mail, or by other method. The information is then collected into a database or pair of databases—a “whitelist” of people who wish to be contacted by professional recruiters, and a “blacklist” of people who do not wish to be contacted by recruiters. The blacklist could either be sold or distributed for free to headhunters who operate in the worker's geographic area, with instruction to the headhunter not to contact the individuals on the list. The whitelist could be sold to those same headhunters as a listing of individuals who may be interested in using the headhunters' services.
Owner:DERRICO DAVID GERALD
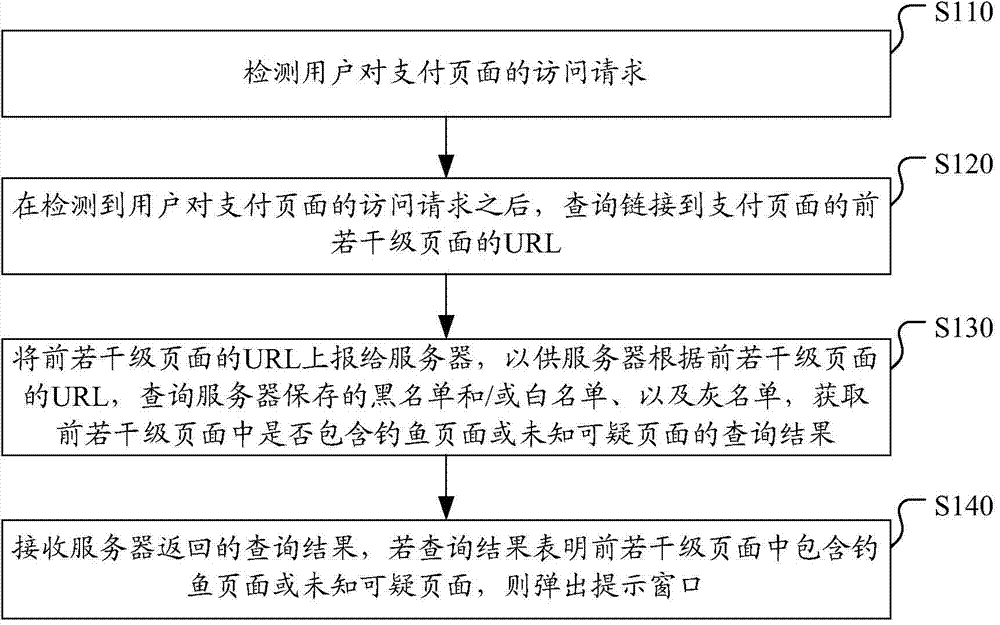
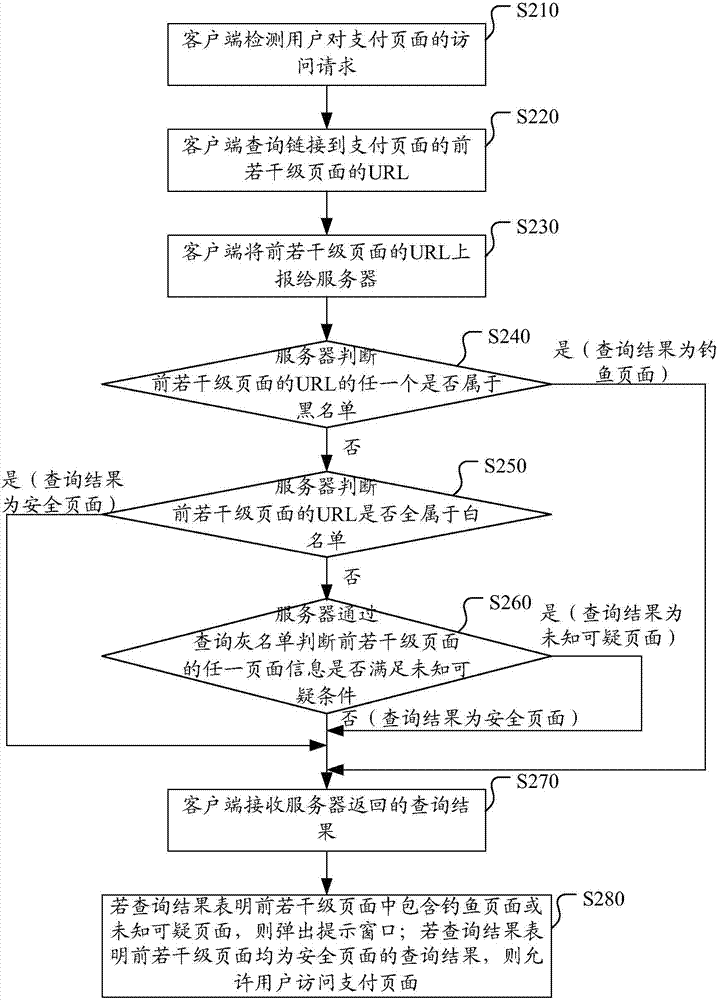
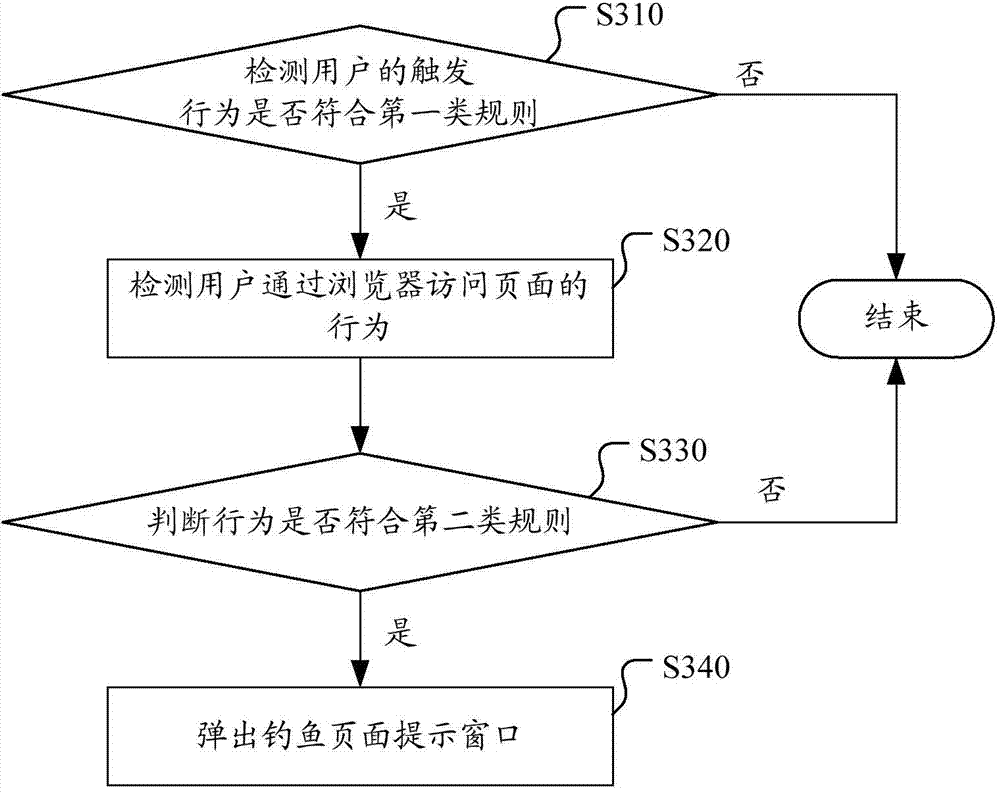
Method and system for detecting phishing pages, client side and server
InactiveCN103685312AImplement real-time interceptionProtection securityTransmissionSpecial data processing applicationsPaymentNetwork behavior
The invention discloses a method and system for detecting phishing pages, a client side and a server. The method comprises the following steps: detecting an access request of a user on a payment page; after the access request of the user on the payment page is detected, inquiring the URL (Uniform Resource Locator) of first several levels of pages linked to the payment page; reporting the URL of the first several levels of pages to the server to cause the server to inquire a blacklist and / or a white list and a gray list stored by the server according to the URL of the first several levels of pages to obtain a query result; if the query result shows that the first several levels of pages contain the phishing pages or unknown suspicious pages, popping up a hint window. Under the condition that a phishing website is not determined, the scheme can also judge the phishing behaviors aiming at the network behavior characteristics. The scheme effectively makes prompts in real time when the user accesses the payment page, realizes the real-time interception for the phishing website, and protects the web browsing safety of the user.
Owner:BEIJING QIHOO TECH CO LTD +1
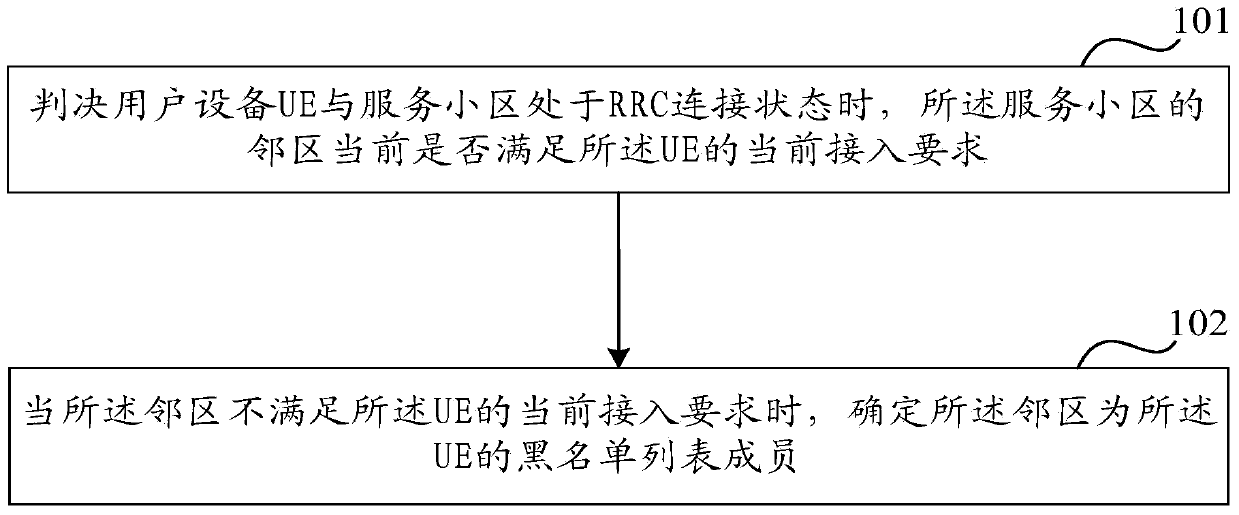
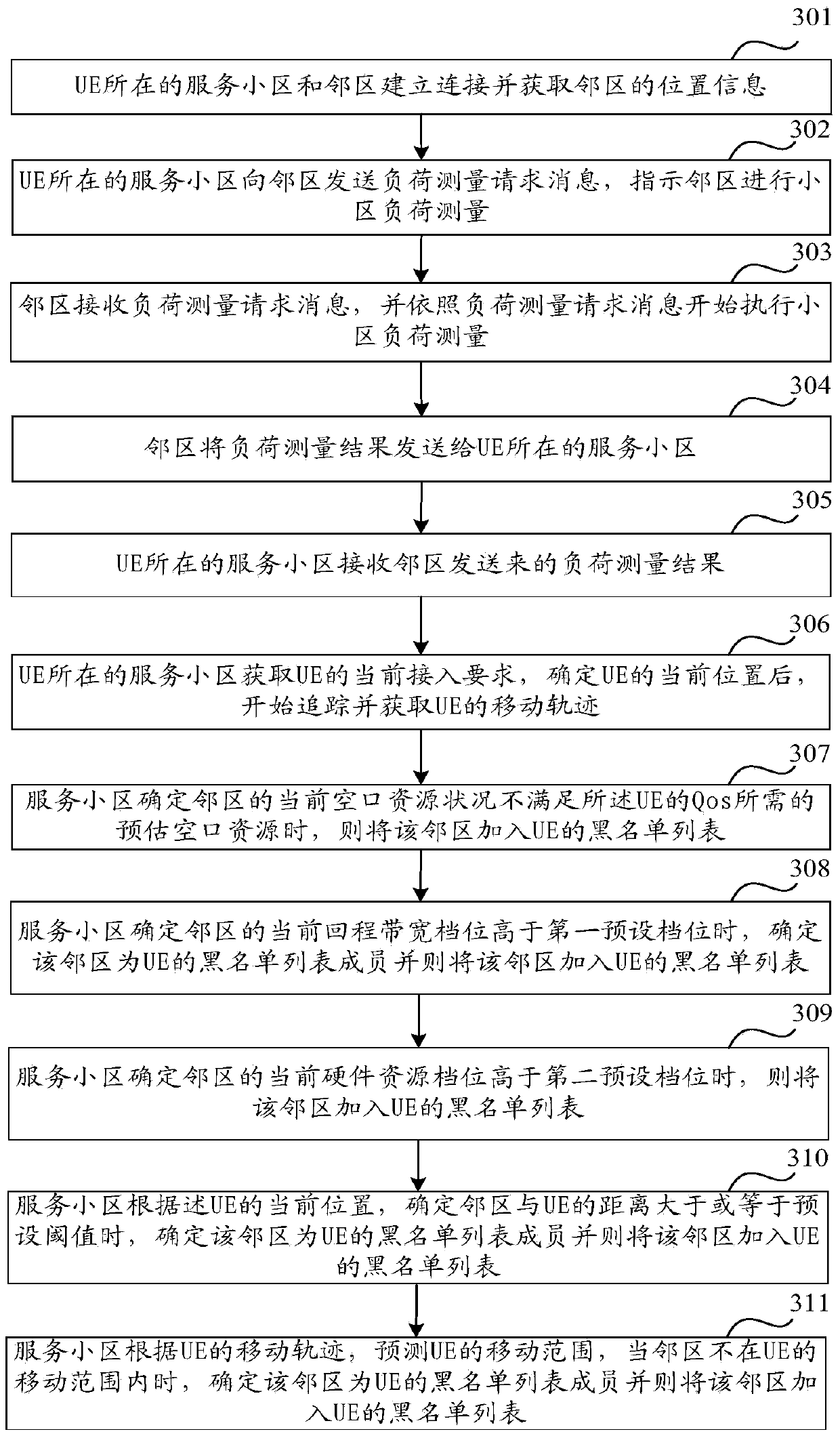
Method and device for determining members of blacklist
ActiveCN104053195AOptimizationEasy to optimizeWireless communicationComputer networkTelecommunications
The invention relates to the field of wireless communication and discloses a method and device for determining members of a blacklist. The method comprises the steps that when UE and a servicing cell are in an RRC connection state, whether adjacent cells of the servicing cell meet the current access requirements of the UE is judged; when the adjacent cells do not meet the current access requirements of the UE, the adjacent cells are determined to be the members of the blacklist of the UE. Through the method, the members of the blacklist can be determined so that configuration on the blacklist can be achieved; when the UE measures the adjacent cells to complete switching of the adjacent cells, the number of the measured adjacent cells is reduced, and the measurement accuracy of the adjacent cells which are possibly switched and used is improved; when measurement results are reported, the number of measurement reports of the adjacent cells in the blacklist is decreased, so that the load of bandwidth on the network side is reduced; the UE can better enable service to be conducted normally in the pilot frequency measurement process.
Owner:COMBA TELECOM SYST CHINA LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com