Patents
Literature
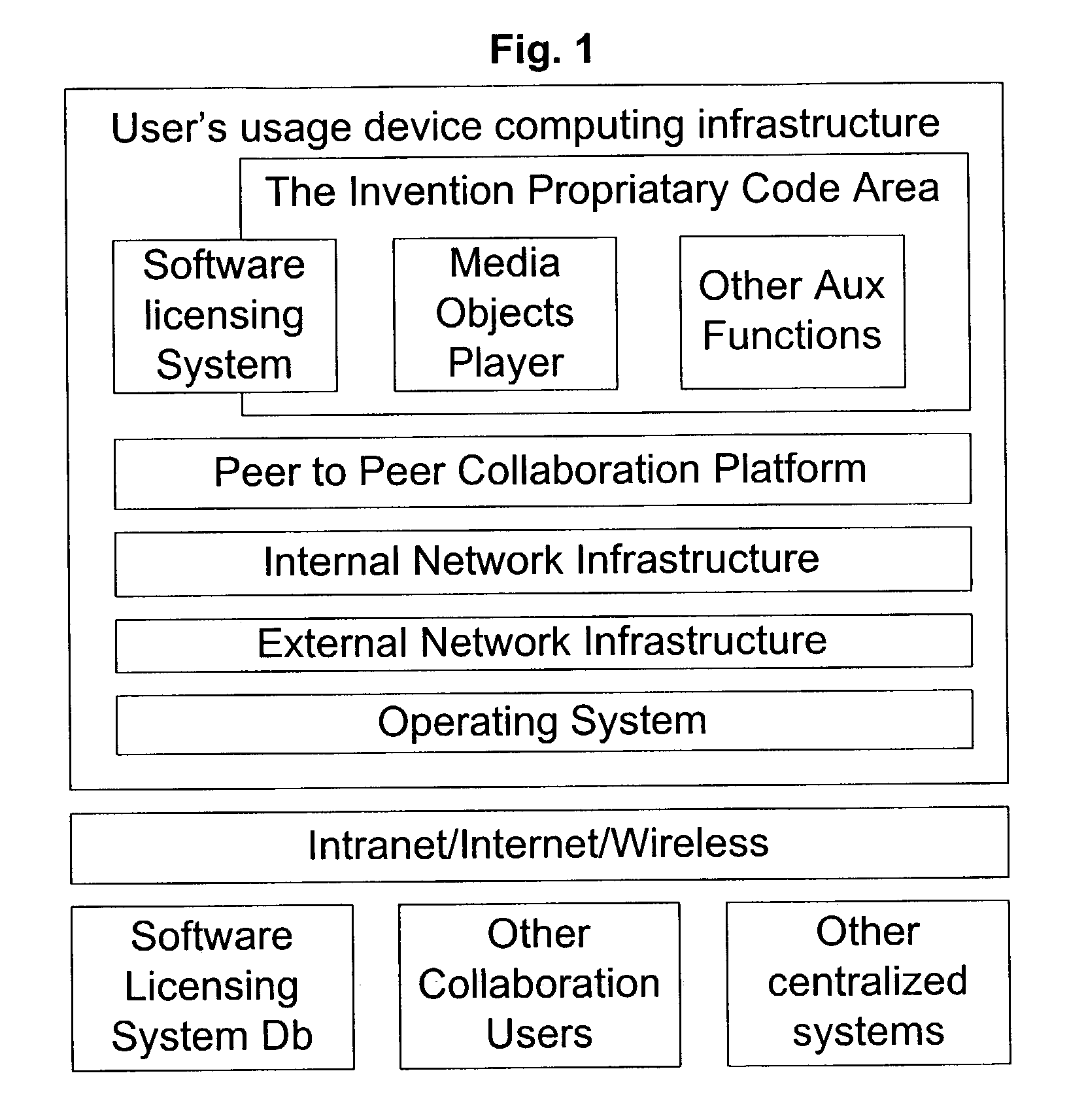
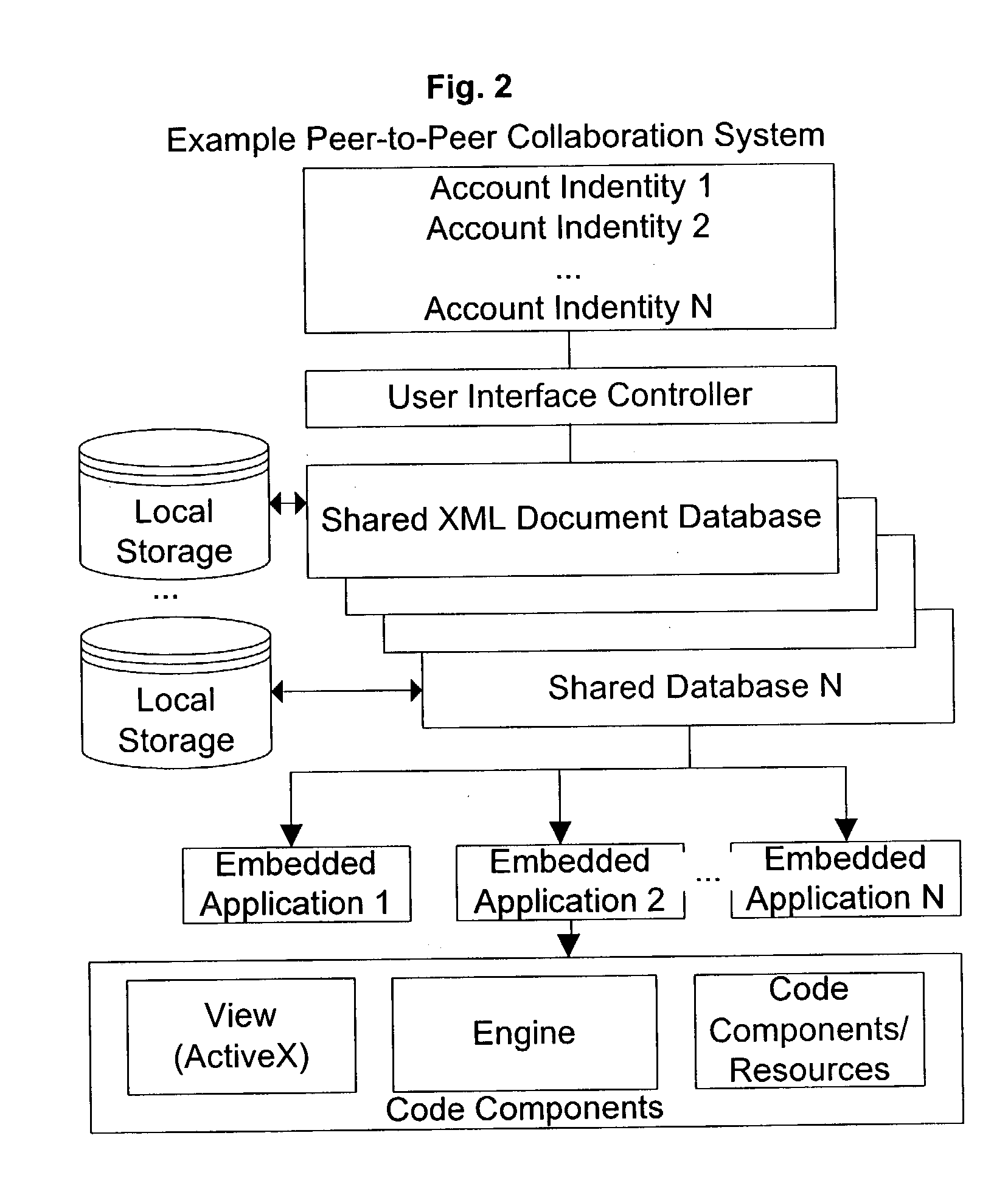
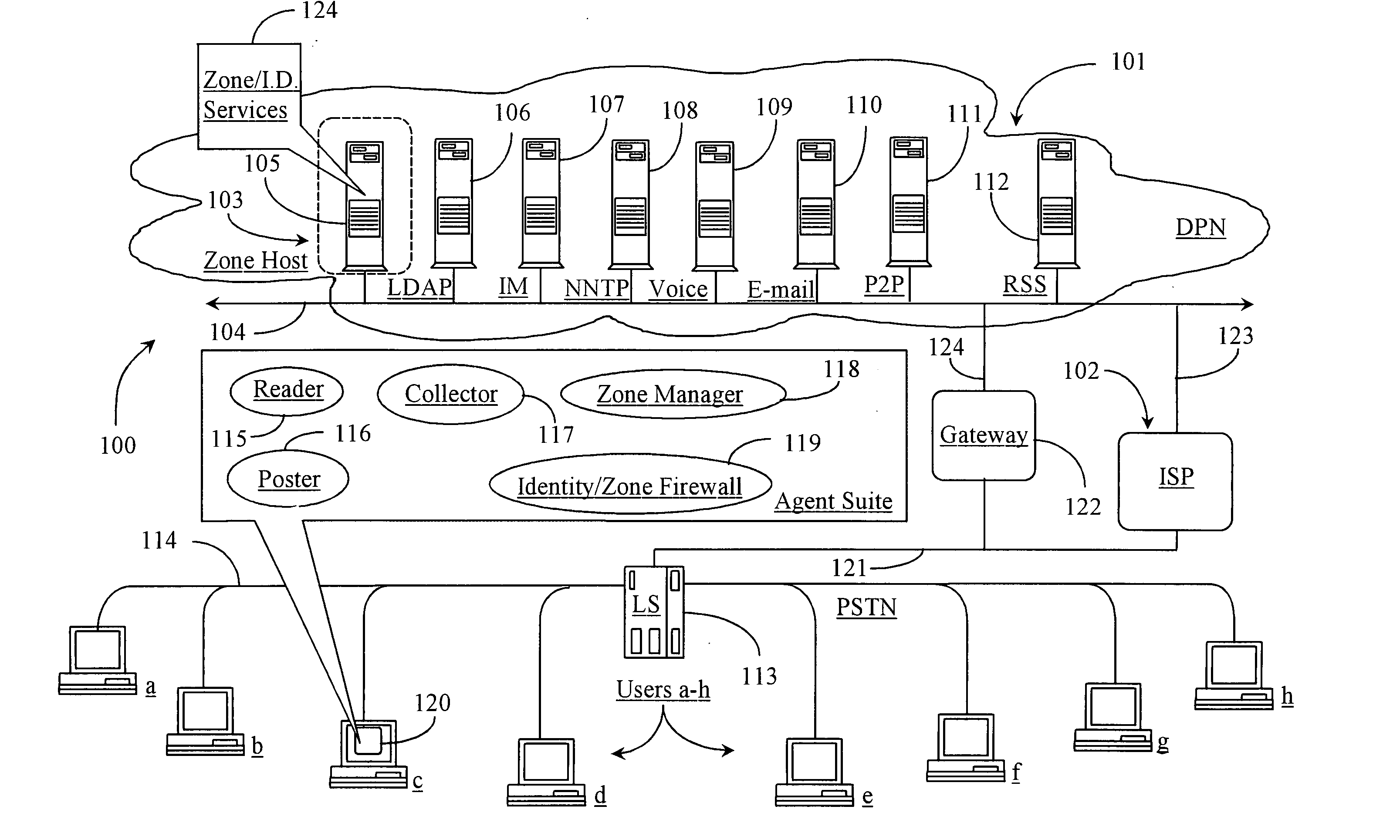
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
582 results about "Unique user" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
According to IFABC Global Web Standards, a unique user (UU) is "An IP address plus a further identifier. The term "unique visitor" may be used instead of "unique user" but both terms have essentially the same meaning (see below). Sites may use User Agent, Cookie and/or Registration ID." Note that where users are allocated IP addresses dynamically (for example by dial-up Internet service providers), this definition may overstate or understate the real number of individual users concerned.
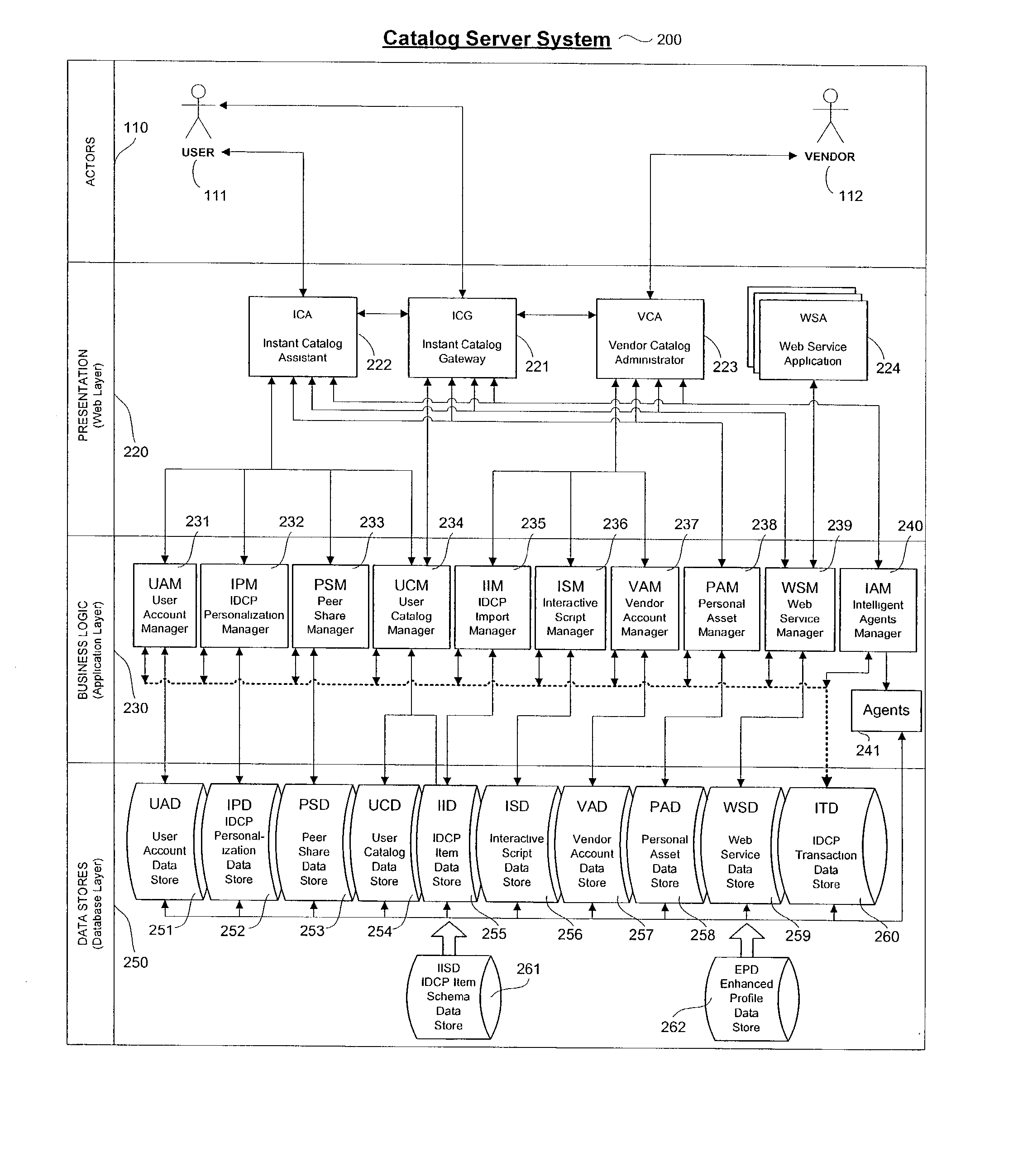
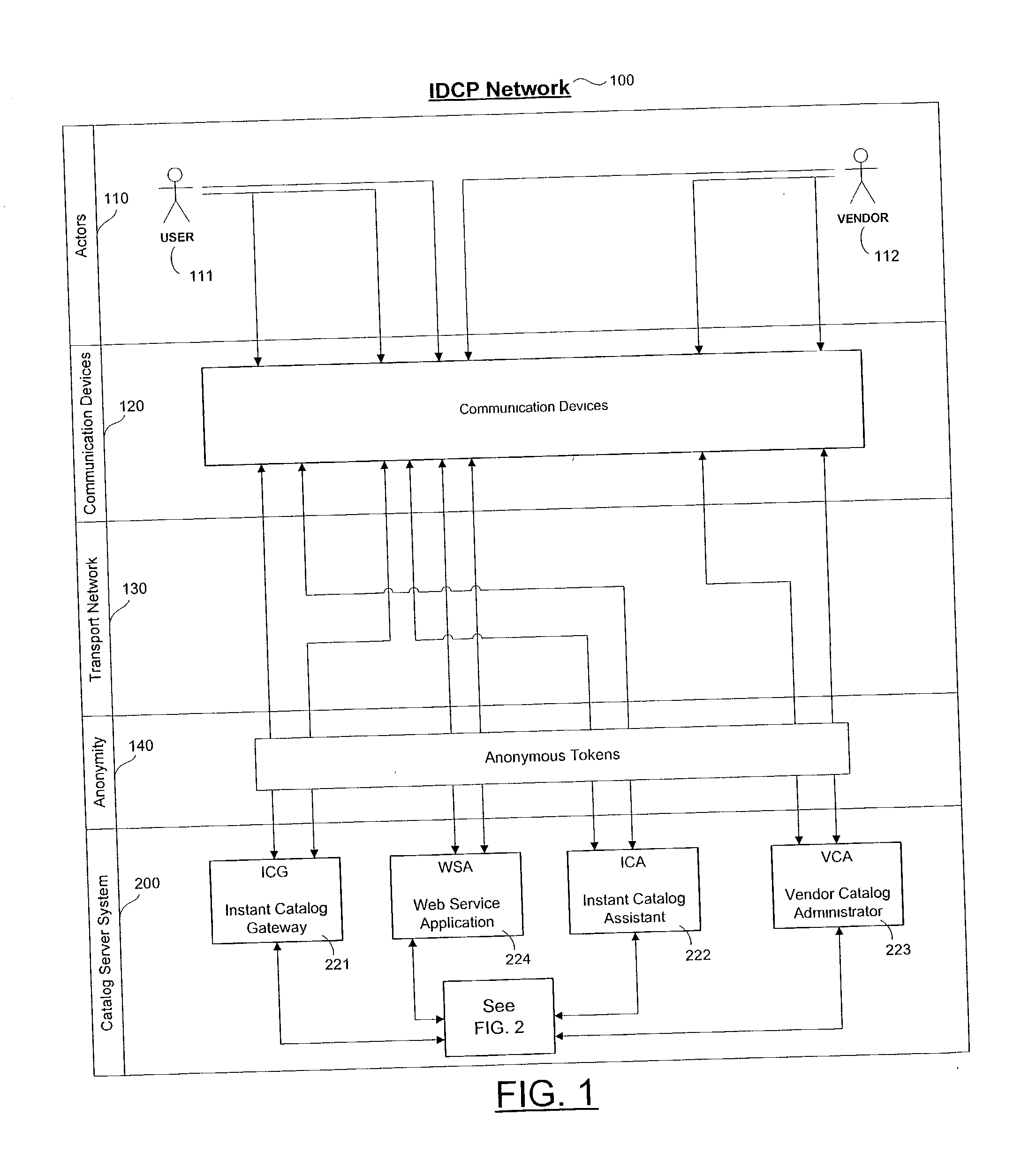
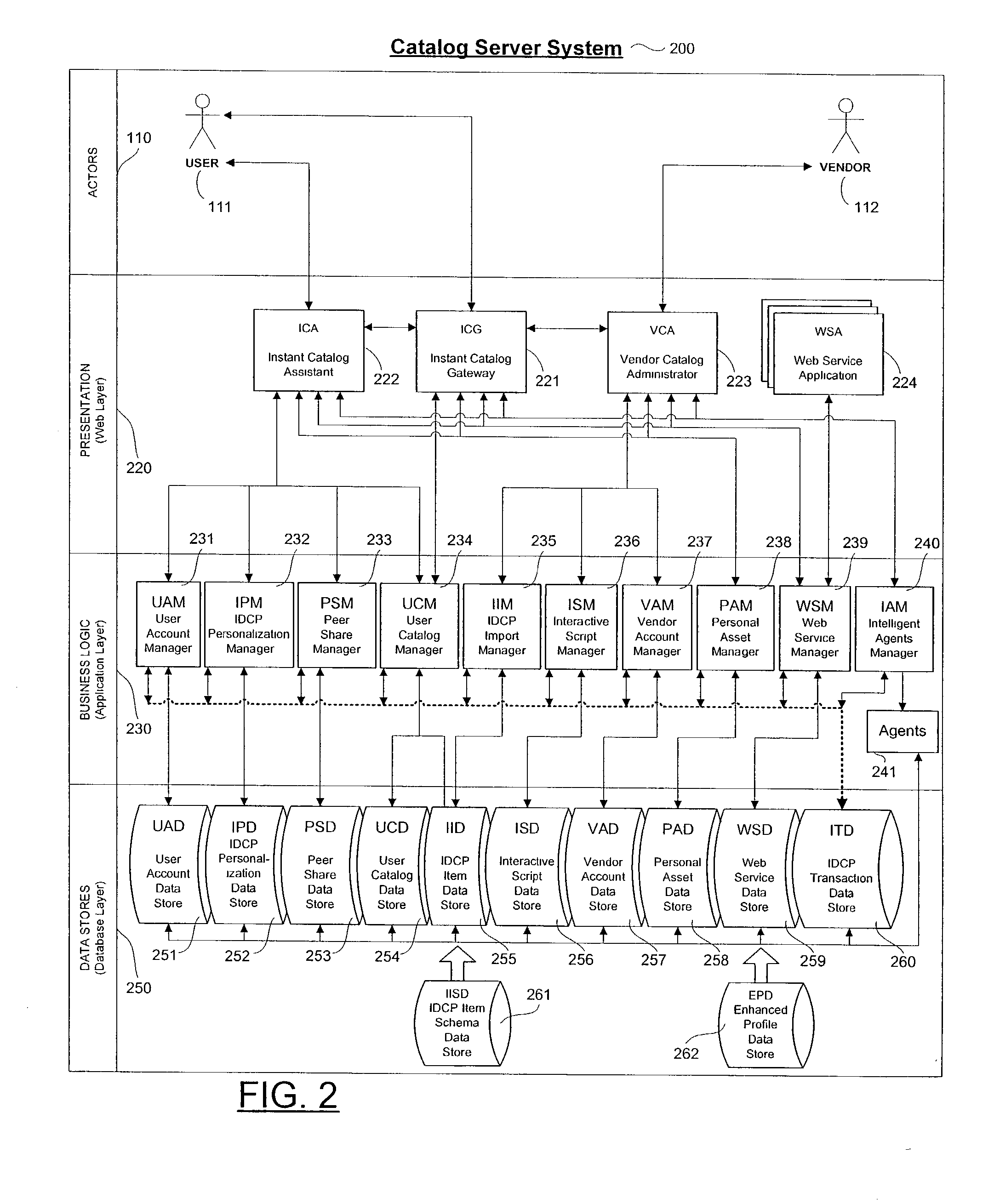
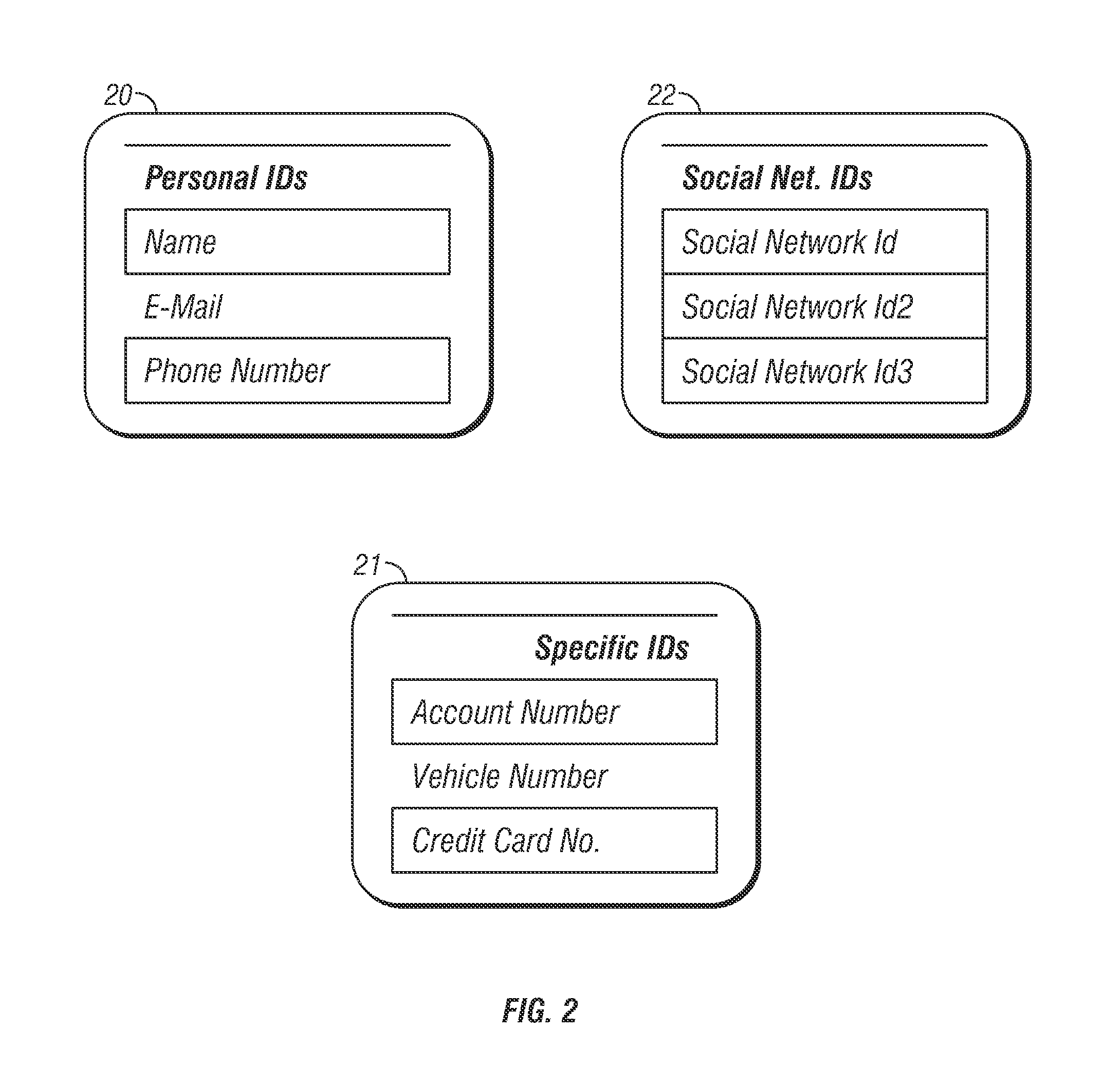
Personalized interactive digital catalog profiling
InactiveUS20030028451A1Facilitate transactionsReduce deliveryDigital data information retrievalComputer security arrangementsPersonalizationWeb browser
An interactive and enhanced digital Instant Catalog of products, services, and information that is personalized or personally profiled, to each unique user of the catalog. The catalog instantly and intelligently captures, stores, manages, and processes self-selected, reusable and "re-distributable" catalog groupings anonymously, for personalizing, enhancing, monitoring, tracking, and peer sharing through multiple mediums and platforms by intelligent agents for a variety of user and vendor specified purposes. The personally profiled cataloged information can be viewed instantaneously and simultaneously by each effected component or member of a supply chain, at the time the product or service has been cataloged, without identifying the cataloger. The user, who preferably employs a Web browser over the Internet, personalizes the interactively produced intelligent catalog content. Products, services, and information groupings are digitally captured and stored by an intelligent catalog agent for enhanced personalized interaction and networking through a peer sharing network, or through an open catalog exchange. The user has the ability to create their own individualized world of products, services, and information that is contextually tailored to each user's unique environment in real-time. Web services hosted within a personal Extranet can anonymously assist and facilitate a context specific task or service insightfully and spontaneously. Through the selective cataloging of multi-vendor products, services, and information, a user is able to fully control, personalize, enhance and share, any lifestyle interest captured from ITV, print, the World Wide Web, businesses, and peers.
Owner:INTENTIONIZE LLC
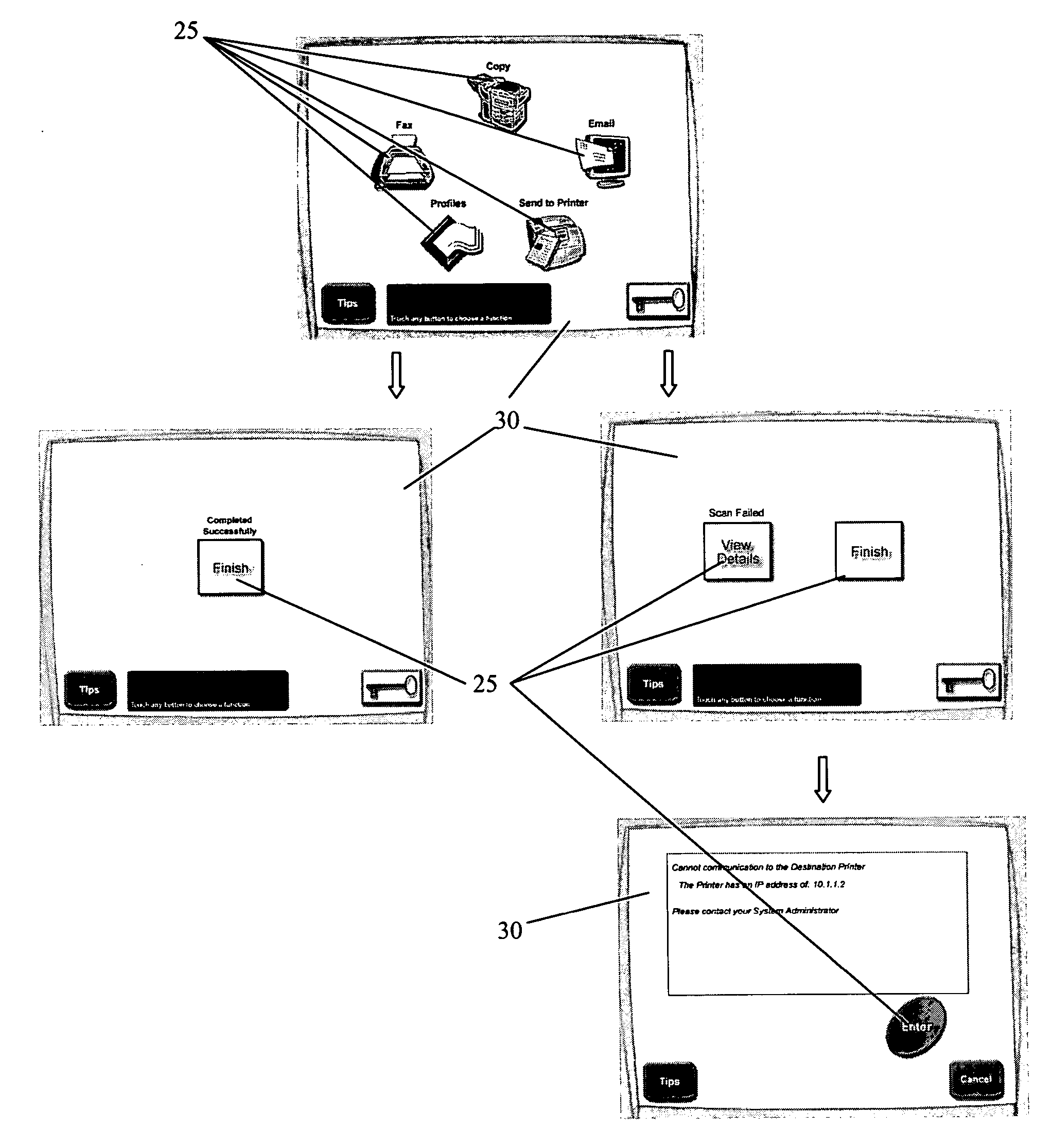
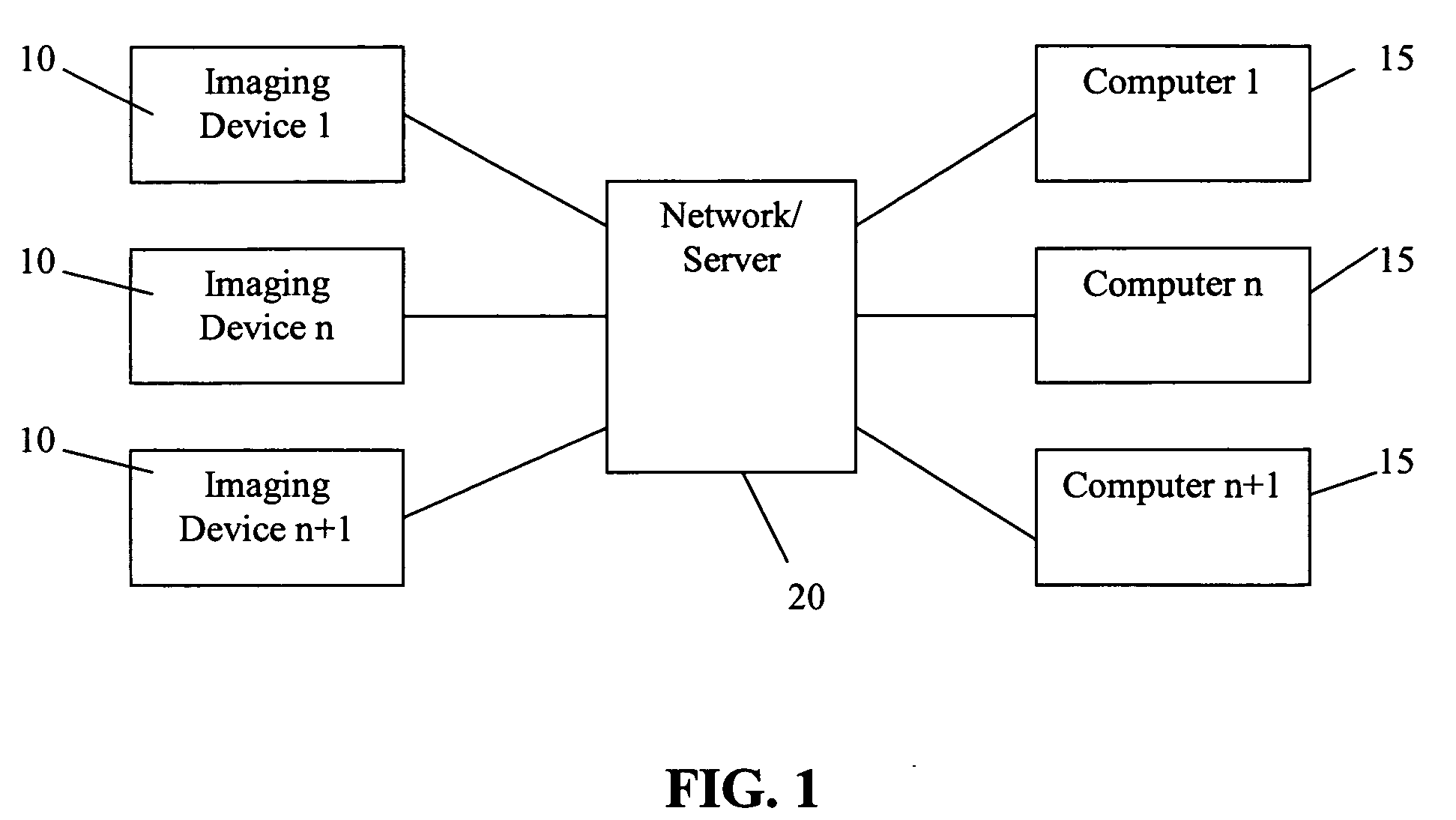
Apparatus and method regarding dynamic icons on a graphical user interface
InactiveUS20050193340A1Improve usabilityMinimize end user training requirementInput/output processes for data processingPictoral communicationGraphicsGraphical user interface
A multifunctional device, such as a multifunction printer, enabling dynamic configurations of the icons on a graphical user interface. In some embodiments, the dynamic configurations create context specific icon layouts. Additionally, in some embodiments, a single icon button can be dynamically configured to represent a particular workflow operation conventionally requiring several inputs by a user at the graphical user interface. Specifically, the display of some embodiments can dynamically change to reflect the “next step” context within a workflow operation. Also, the display of some embodiments can dynamically change to reflect a unique user-context on the graphical user interface.
Owner:LEXMARK INT INC
Method and system for relationship management and intelligent agent
InactiveUS20120150888A1Improve identityDigital data processing detailsRelational databasesThird partyWeb site
The present invention provides computer-based systems and methods directed to maintaining a database of user profiles based, respectively, on user interaction with third-party systems. The invention includes the processes of: accessing a unique user profile associated with a unique user; automatically collecting, by an agent module executing on a processor associated with a first system, data associated with the unique user based at least in part on the unique user's interaction with a system unassociated with the first system; evaluating by the processor the collected data and searching available databases to identify potential items of interest to the unique user based at least in part on the unique user profile and the collected data; determining a set of predicted items of interest to the unique user from the identified potential items of interest; and presenting at a display associated with the unique user data representing the set of predicted items of interest. In one implementation, the invention provides an intelligent agent possessing a level of “awareness” concerning individual users associated with user profiles or accounts and is adapted to access private and public databases, websites, resources, and other systems to efficiently collect, filter and deliver / present content and resources of interest to the individual user in a predictive fashion.
Owner:THOMSON REUTERS GLOBAL RESOURCES UNLIMITED CO
Self-replicating and self-installing software apparatus
InactiveUS20030217171A1Special service provision for substationElectronic editing digitised analogue information signalsContent creationRemote control
Self-replicating and self-installing software apparatus for content-creation, manipulation, and static or dynamic exhibition with a self-regulating license management component with methods for remote controlled and synchronized functionality and license binding to a Peer-to-Peer computing paradigm derived communication and collaboration platform's unique User ID.
Owner:VON STUERMER WOLFGANG R +1
Methods and system for creating and managing identity oriented networked communication
ActiveUS20050198125A1Multiple digital computer combinationsData switching networksWorkspaceApplication software
A software application for managing routing of communiqués across one or more communication channels supported by a data-packet-network includes one or more workspaces for segregating communication activity; one or more unique user identities assigned per workspace; and one or more contact identities assigned to and approved to communicate with a workspace administrator of the one or more workspaces using the assigned user identities. In a preferred embodiment the application enforces a policy implicitly defined by the existing architecture of the workspaces and associated user and contact identities.
Owner:FORTE INTERNET SOFTWARE
Telemetry system with tracking receiver devices
ActiveUS20140247152A1Improved wireless power transmissionElectric signal transmission systemsTelemetry/telecontrol selection arrangementsElectric power transmissionCommunication interface
A wireless power transmission system includes, a transmit antenna which in operation produces a wireless field, an amplifier coupled to the transmit antenna, a load sensing circuit coupled to the amplifier and a controller coupled to the load sensing circuit. A monitoring device has one or more sensors and a unique user ID. The one or more sensors acquire user information selected from of at least one of, a user's activities, behaviors and habit information. The monitoring device includes an ID circuitry. A communication interface receives information about the unique user ID when the load sensing circuit indicates the monitoring device is within the wireless field. The indication is created using at least a change in power consumption.
Owner:FITBIT INC
Multi-media wireless watch
InactiveUS20150098309A1Acoustic time signalsMechanical clocksDisplay deviceHuman–computer interaction
A method for controlling a smart watch with a touch-sensitive display comprises detecting contact with the touch-sensitive display while the smart watch is displaying a first application interface associated with a first application. The detected contact can originate in a first area of the touch-sensitive display and move in a first direction. The method can further comprise displaying a first menu of first application interfaces available within the first application. The first application interfaces can comprise a set of unique user interfaces that are accessible within the first application. Additionally, the method can comprise detecting contact on an indication of a particular first application interface from within the first menu. The method can also comprise displaying, on the touch sensitive display, the particular first application interface.
Owner:I AM PLUS
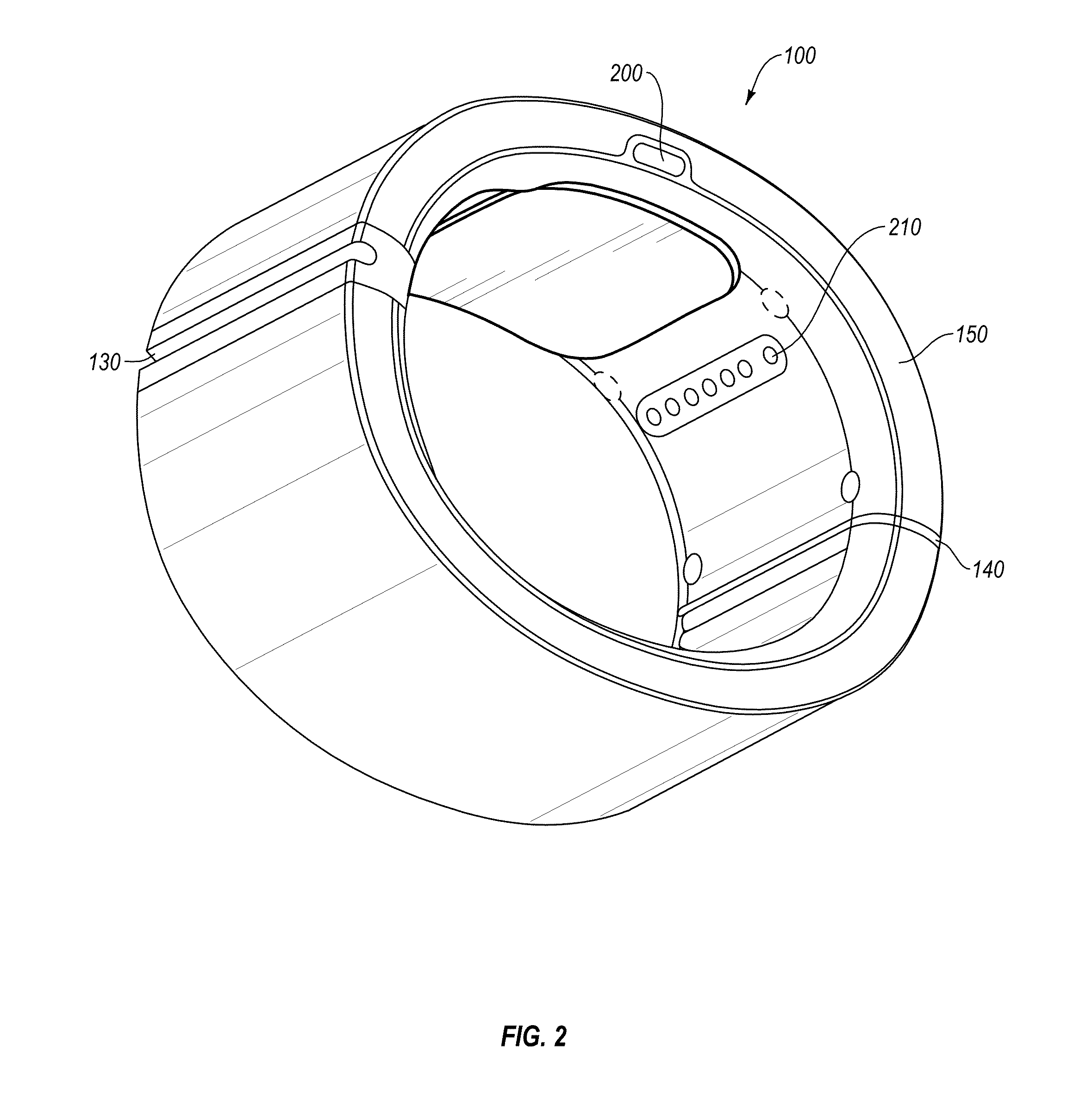
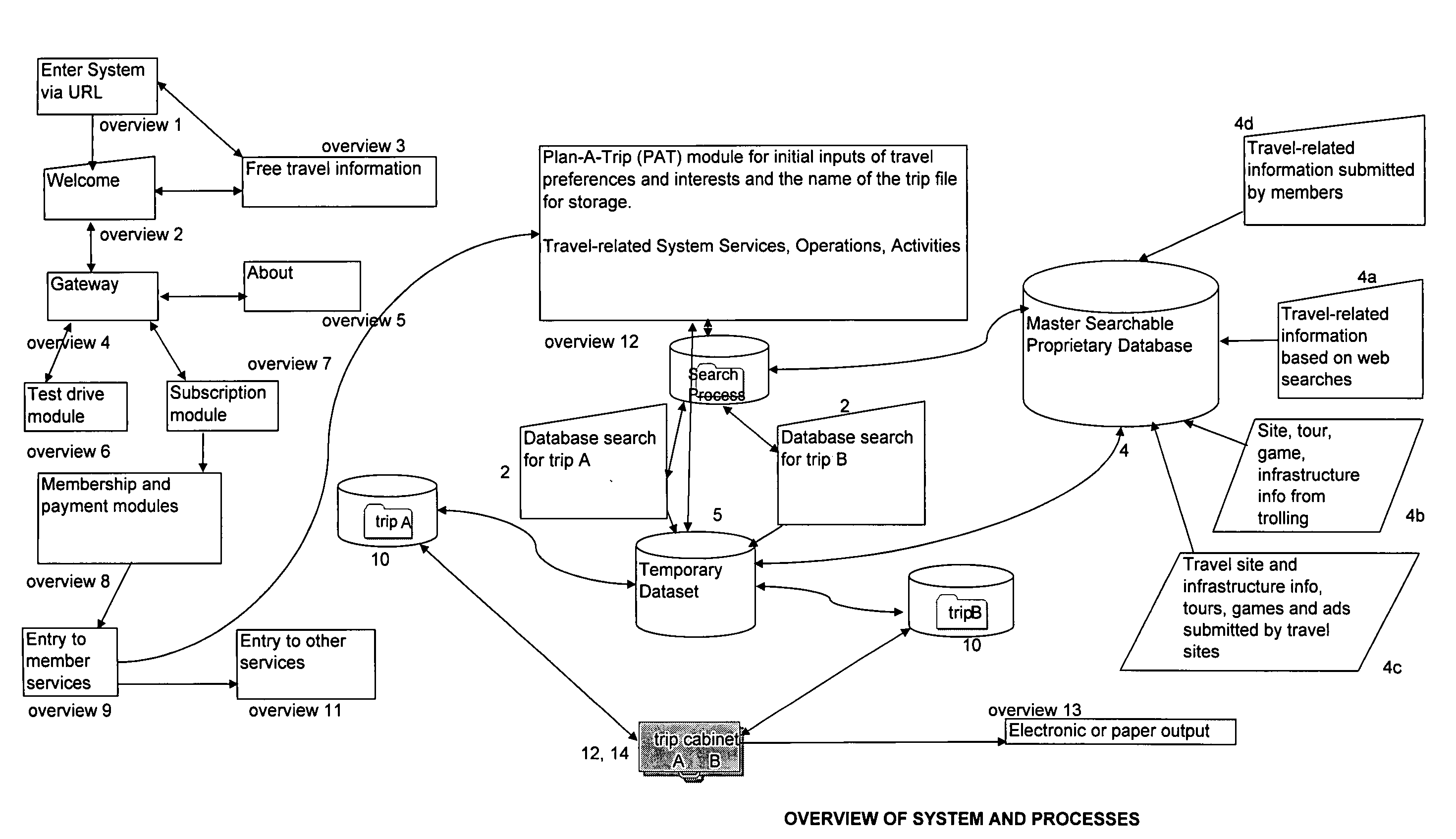
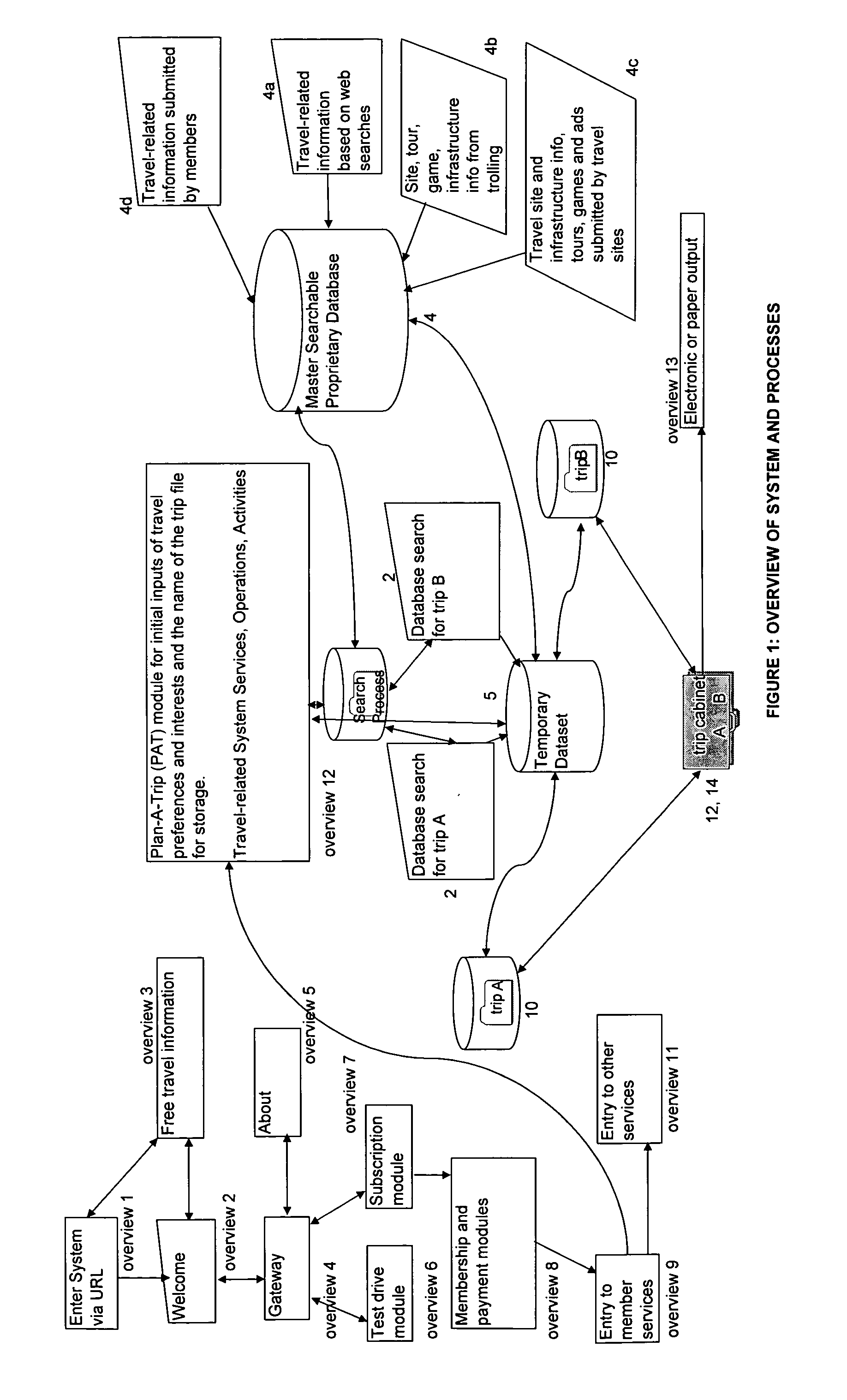
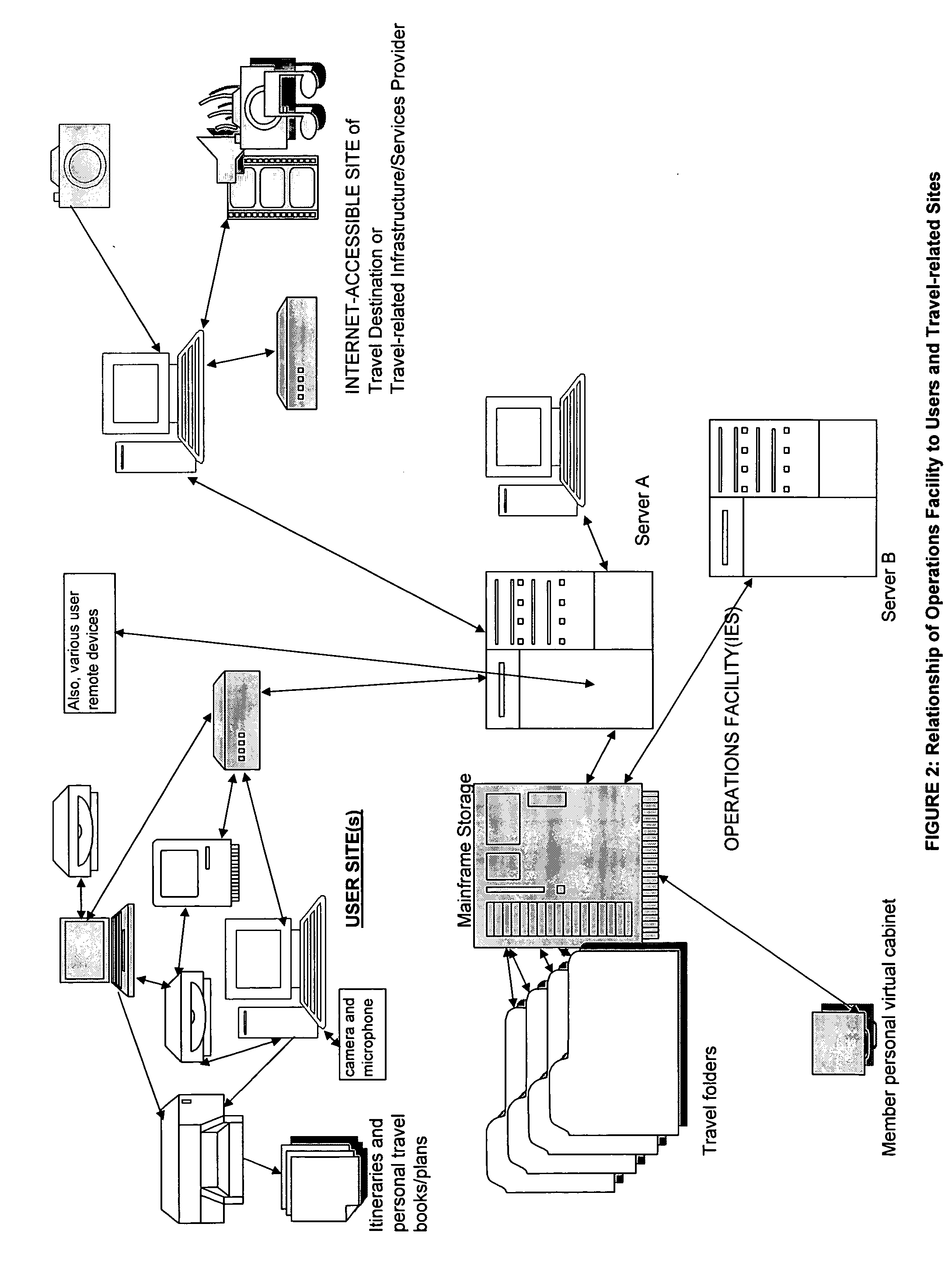
Interactive, Internet-based, trip planning, travel resource, travel community, virtual travel, travel-based education, travel-related gaming and virtual/live tour system, methods, and processes, emphasizing a user's ability to tailor complete travel, trip, route, game and touring choices to unique user-specified personal interests, preferences, and special requirements for self and companions
Interactive, Internet-based, Trip Planning, Travel Resource, Travel Community, Virtual Travel, Travel-based Education, Travel-related Gaming and Virtual / Live Tour System, Methods, and Processes, emphasizing a user's ability to tailor complete travel, trip, route, and touring choices to unique, user-specified personal interests, preferences, and special requirements for self and companions throughout a particular trip or for gaming or virtual (including live, passive, interactive, individual, group, and scheduled, reserved or on-demand) tours, and including methods and processes related to scheduling games, tours, site visits and other travel-events, making related reservations and obtaining confirmations and e-tickets, and on-line banking services to process ticket, membership and merchandise payments and advertising, reservation and ticket and merchandise transactions for vendors.
Owner:BAKEWELL LUCIA URBAN +1
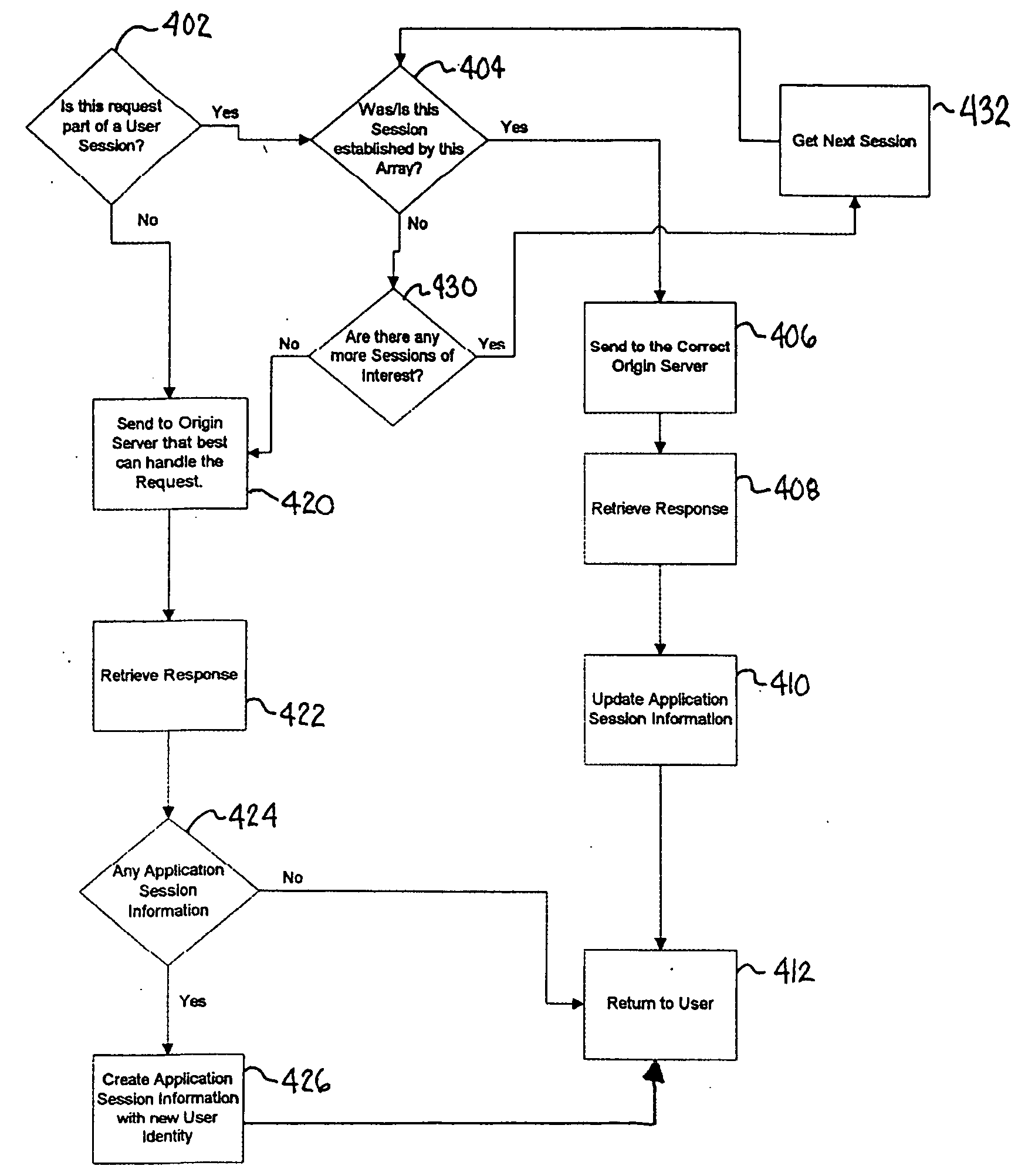
Deterministic session state management within a global cache array
InactiveUS20060155857A1Digital data information retrievalMultiple digital computer combinationsState managementSession state
The present invention is directed to binding a user session in an application to a particular coordination point. The method includes recognizing a defined application session in response to an application generated by a cache. A user session and an origin server that generated the response are bound in a session cookie. Subsequent requests are routed to the same origin server that served the application content for each unique user session based on the session cookie.
Owner:ORACLE INT CORP
Methods and apparatus for monitoring end-user experience in a distributed network
InactiveUS6970924B1Accurate assessmentAccurately determineMultiple digital computer combinationsProgram loading/initiatingMonitoring systemSystem usage
A network performance monitoring system uses a plurality of user modules, each user operating on a unique user machine coupled to one or more provider servers and an experience test server for collecting data from the plurality of user modules. The collected data includes at least one performance datum relating to user experience with a link from the user machine to the provider server. The system also cleanses the collected data to account for variable user configurations, user errors and the like.
Owner:INVERSE NETWORK TECH INC +1
Method and apparatus to provide secure purchase transactions over a computer network
Owner:BENEDORTSE
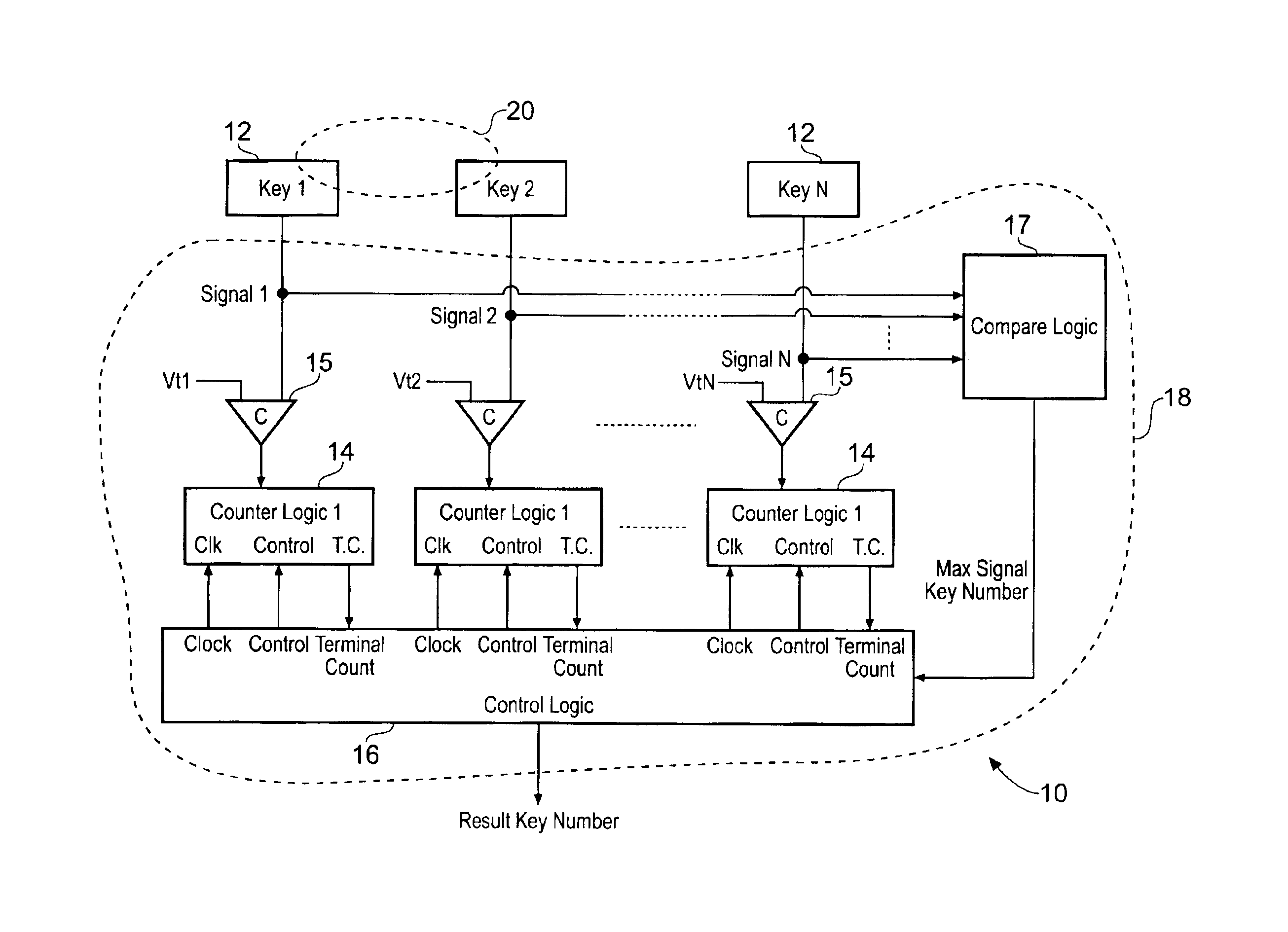
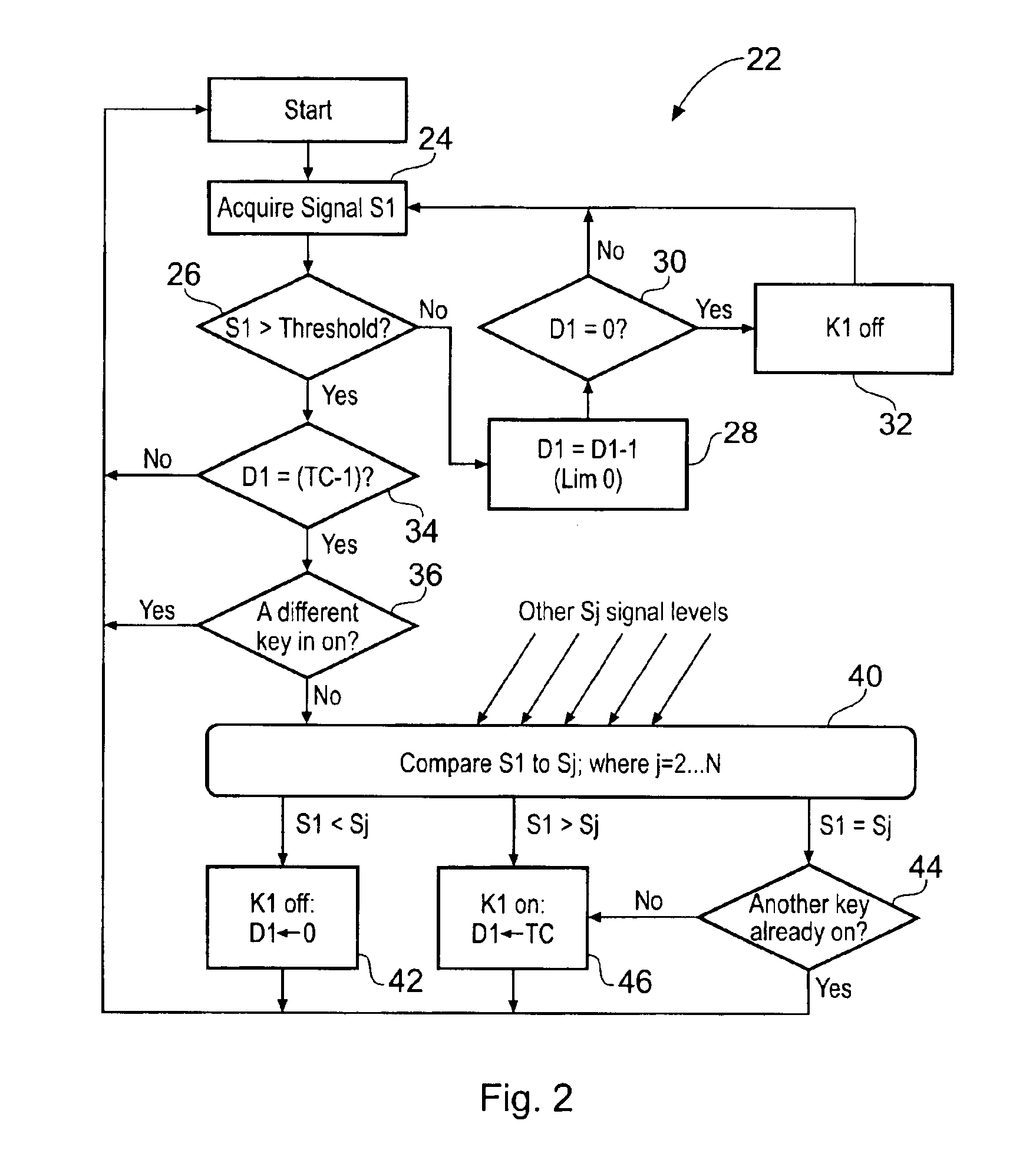
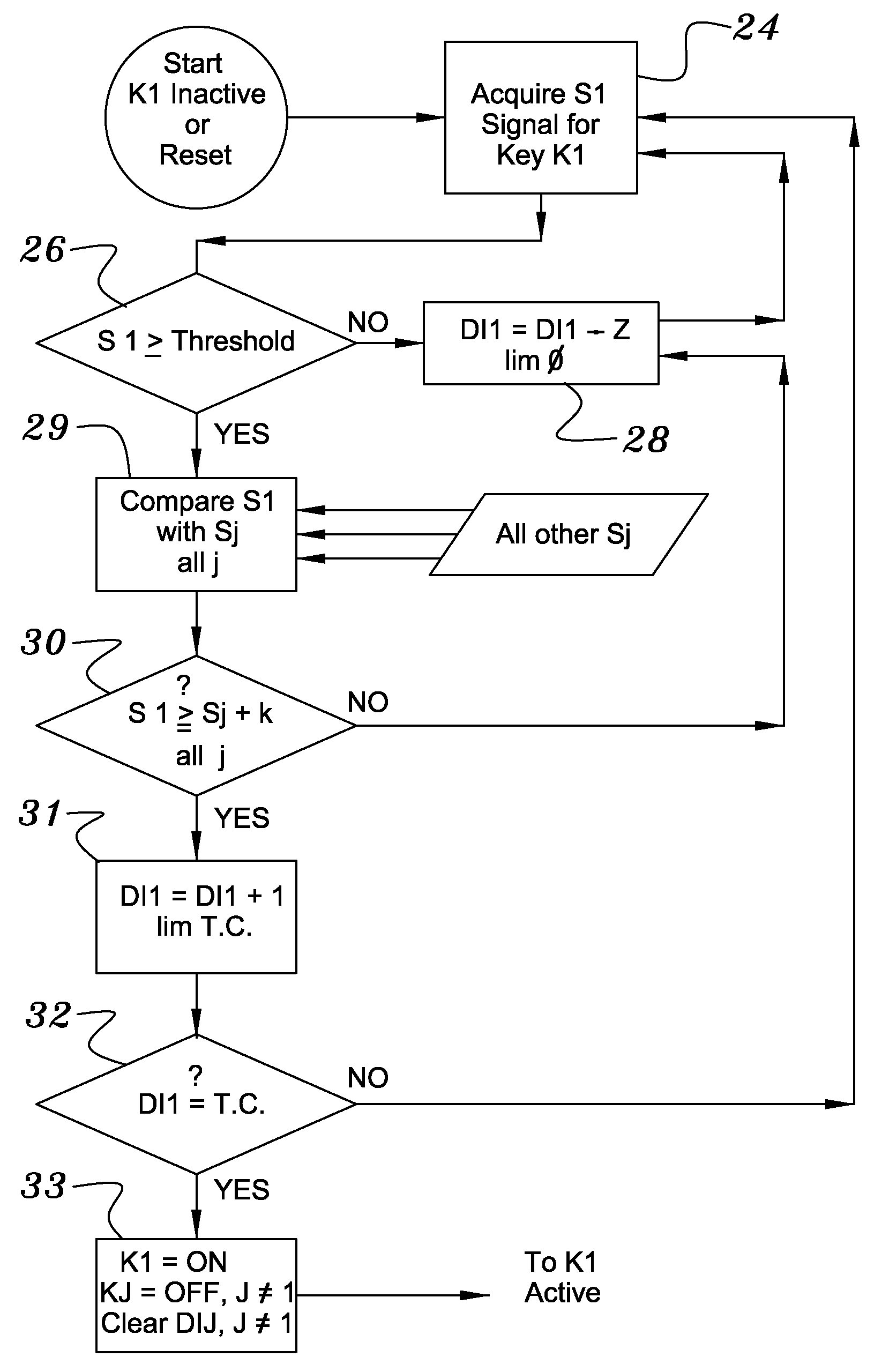
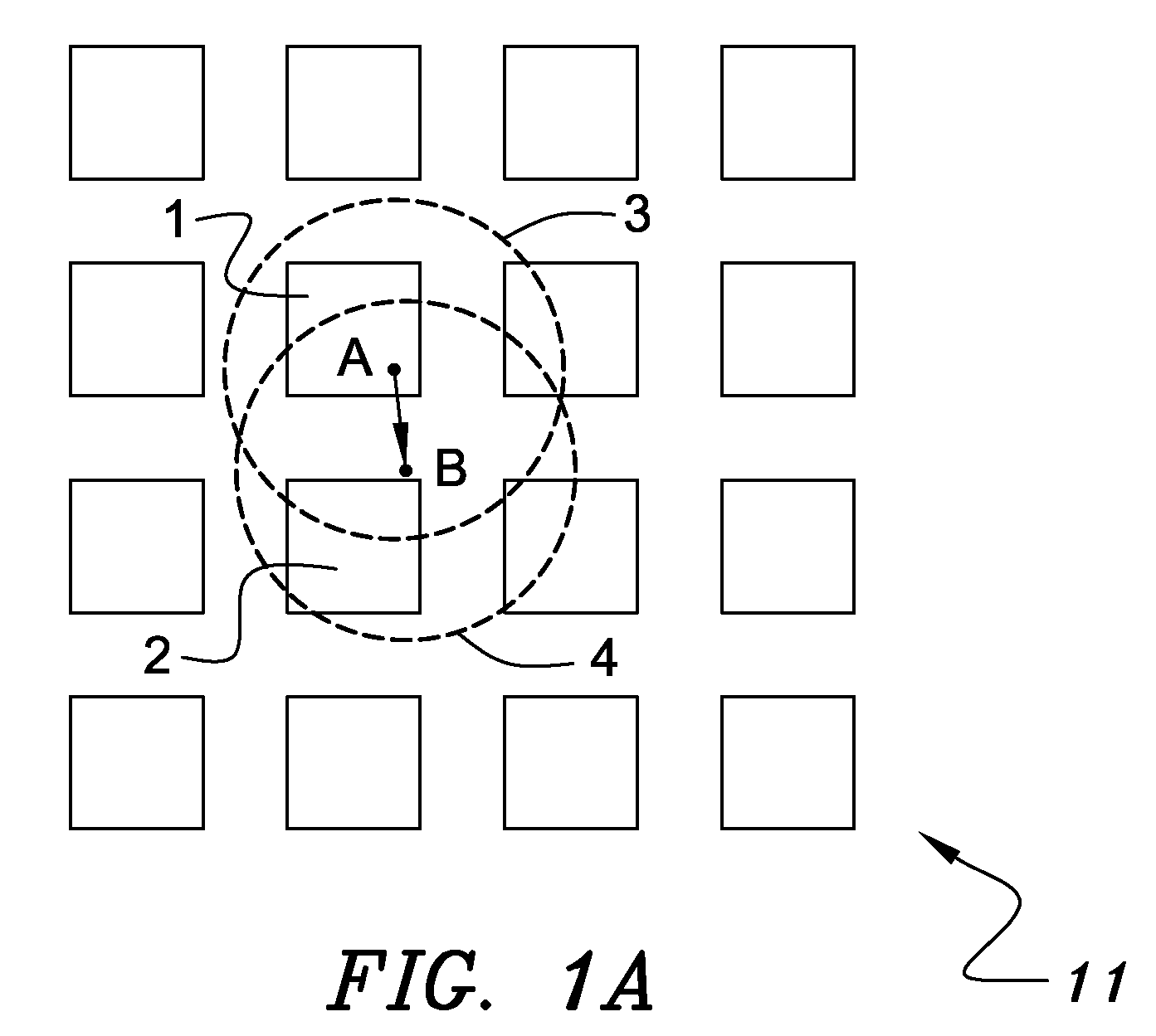
Keyboard with reduced keying ambiguity
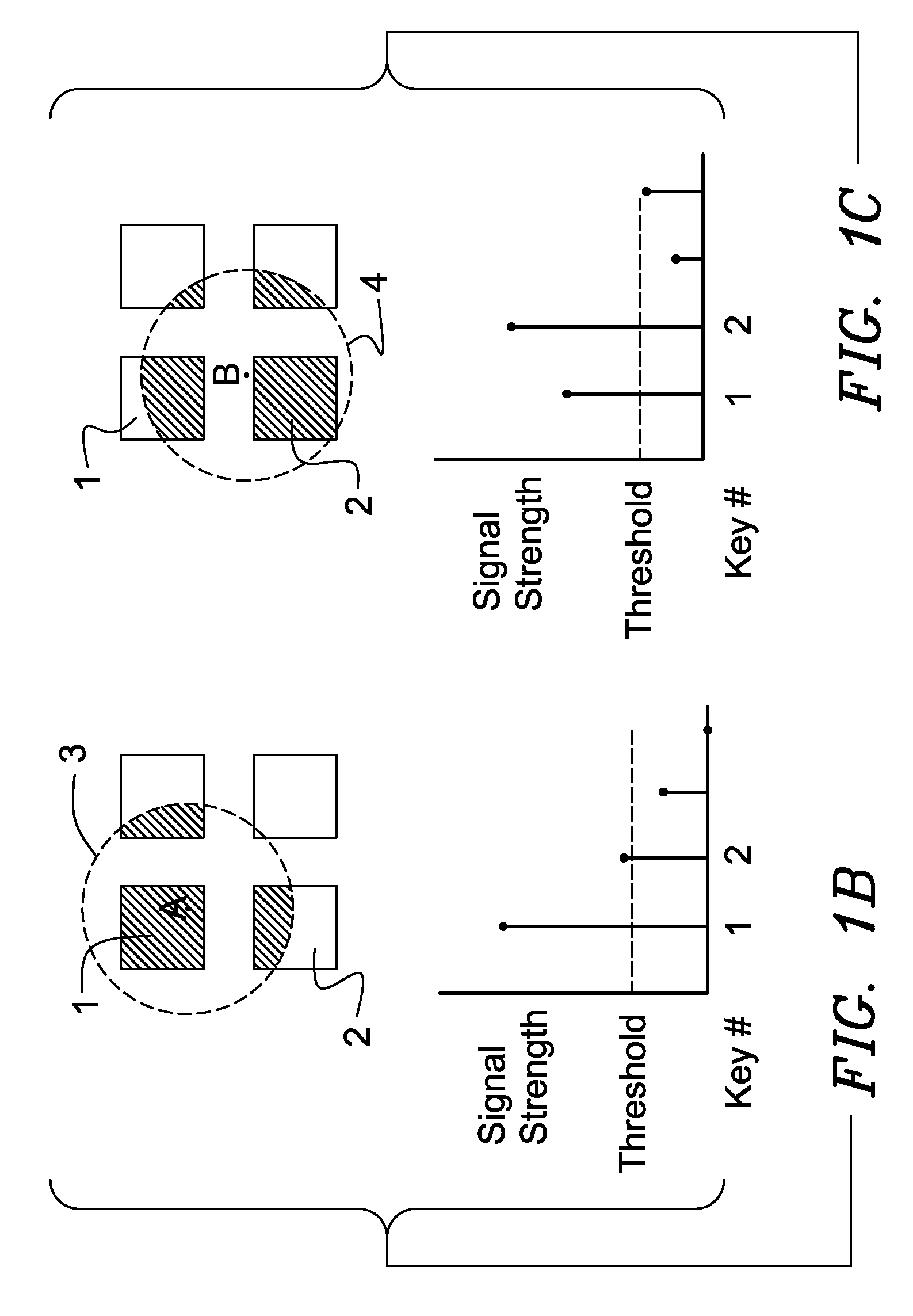
When an array of proximity sensors is used as a keyboard, it can provide an ambiguous output if a user's finger overlaps several keys or if liquid is spilled on the keyboard. This ambiguity is reduced by an iterative method that repeatedly measures a detected signal strength associated with each key, compares all the measured signal strengths to find a maximum, determines that the key having the maximum signal strength is the unique user-selected key and then suppresses or ignores signals from all other keys as long as the signal from the selected key remains above some nominal threshold value.
Owner:NEODRON LTD
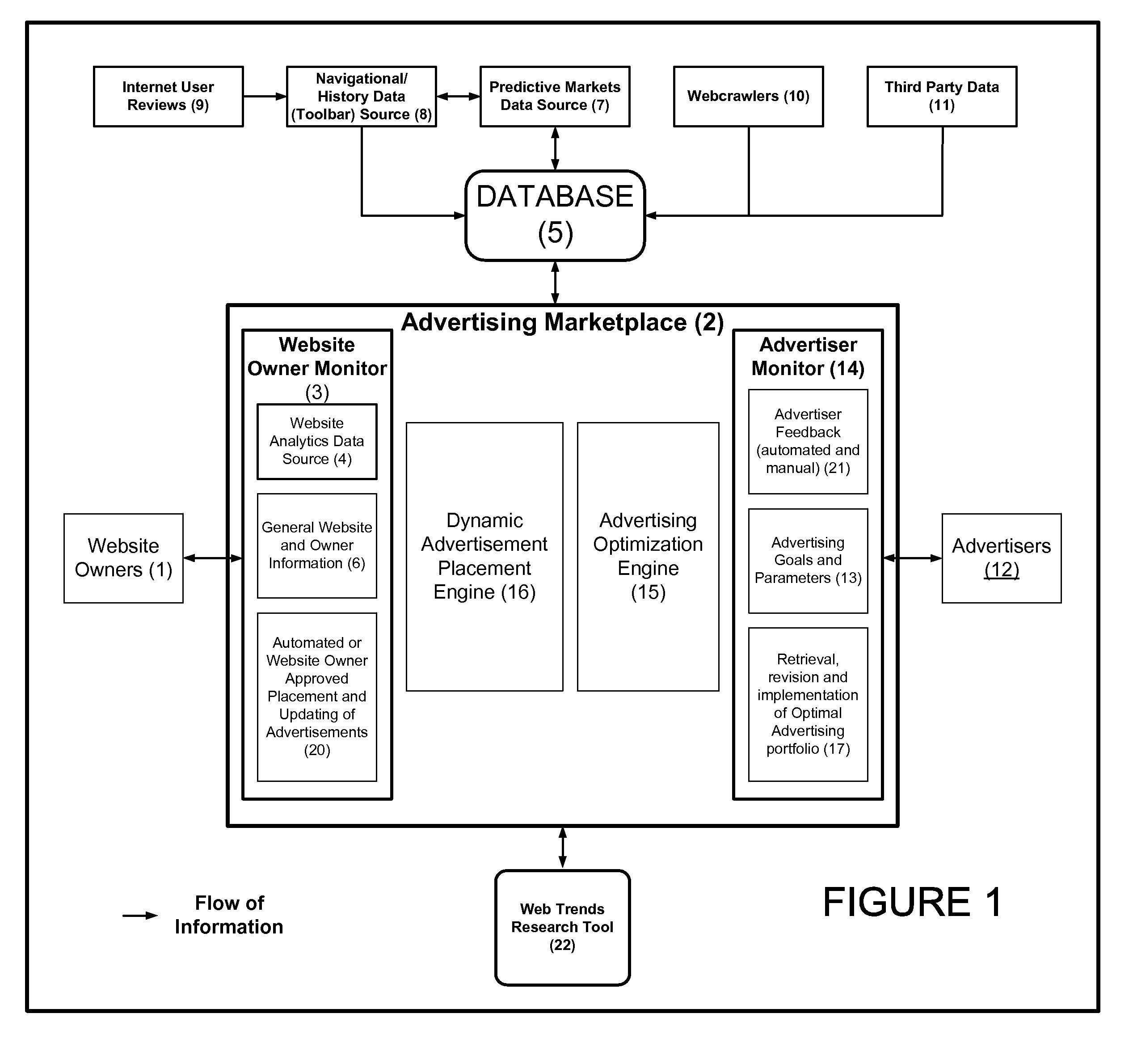
Method And System For Collecting And Correlating Data From Information Sources To Deliver More Relevant And Effective Advertising
A method and system for collecting and using in combination data from information sources in a correlated manner to deliver more relevant and effective advertising is provided. Website owners register with a service provider, submit relevant information about their website and download website analytics software enabling relevant data to be tracked by and transmitted to the service provider's online database. Service provider also collects data from other information sources including an online website exchange, webcrawlers and other software (e.g. toolbars, cookies, javascript) that track the navigation history of individual Internet users and their demographic information. Service provider correlates and analyzes submitted data from some or all of the information sources to determine scores, meaningful ranking and other useful information regarding the efficacy of websites for potential advertisers. Potential advertisers perform search requests on the service provider's database using advertiser-specific parameters to retrieve a portfolio of advertising opportunities that are optimally matched with the advertiser's specifications. The advertisers may edit the results and submit a request via service provider to the one or multiple website owners to implement the portfolio of resulting and / or revised advertising opportunities.
Owner:SWOOGE
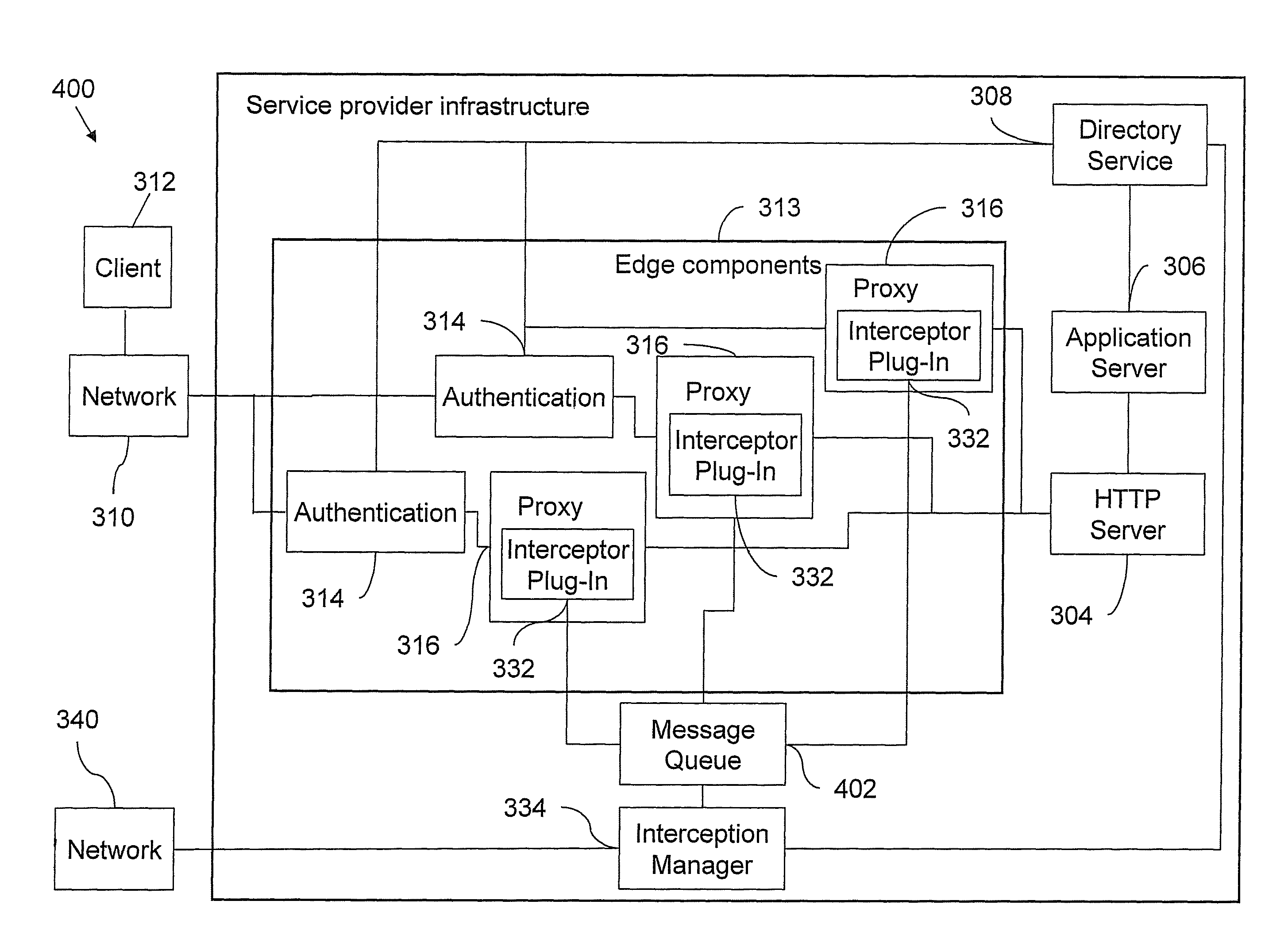
Method and data processing system for intercepting communication between a client and a service
InactiveUS8024785B2Memory loss protectionError detection/correctionData processing systemClient-side
A method and data processing system for intercepting communication between a user and a service. An authentication component receives, from the user, a user request directed to the service. The authentication component adds a user-specific token to the user request to generate a tokenized request. The tokenized request includes the user request and the token. The token includes a unique user identifier that identifies the user. The authentication component sends the tokenized request to a proxy. The proxy sends the tokenized request to the service. The proxy invokes an interceptor plug-in that is plugged into the proxy. The interceptor plug-in ascertains that the unique user identifier in the tokenized request is present in an interception control list of unique user identifiers. The interception control list is accessible to the interceptor plug-in. The interceptor plug-in sends the tokenized request to an interceptor manager who stores the tokenized request.
Owner:IBM CORP
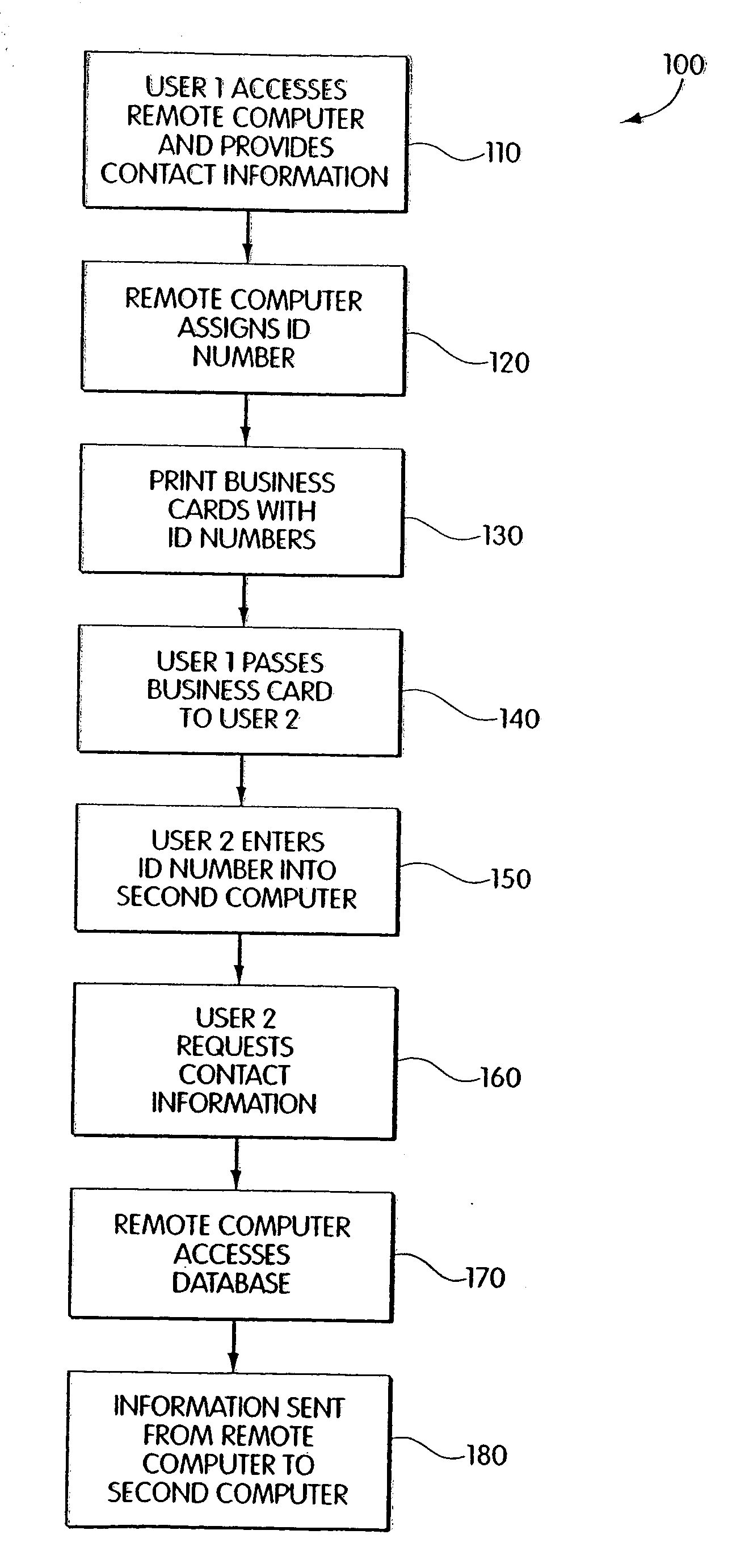
Method and apparatus for storing and retrieving business contact information in a computer system
InactiveUS20050149487A1Digital data processing detailsSubstation equipmentDatabase interfaceData transmission
The present invention provides an information management system comprising a remote device, a remote database operatively coupled to the remote device, the remote database containing contact information for each of a plurality of users of the information management system, wherein each of the users is assigned a unique user identifier, and the information for each user is stored along with the unique user identifier of the user in the remote database, wherein the remote device includes a wireless network interface module that interfaces with a wireless network to allow users of the information management system to access the remote device, a database interface module that coordinates transfer of data between the remote database and the remote device, and an application module to enable a wireless network user to access the remote database over the wireless network using a second network device to retrieve information in the remote database related to a first user having an assigned unique user identifier.
Owner:XENOGENIC DEV LLC
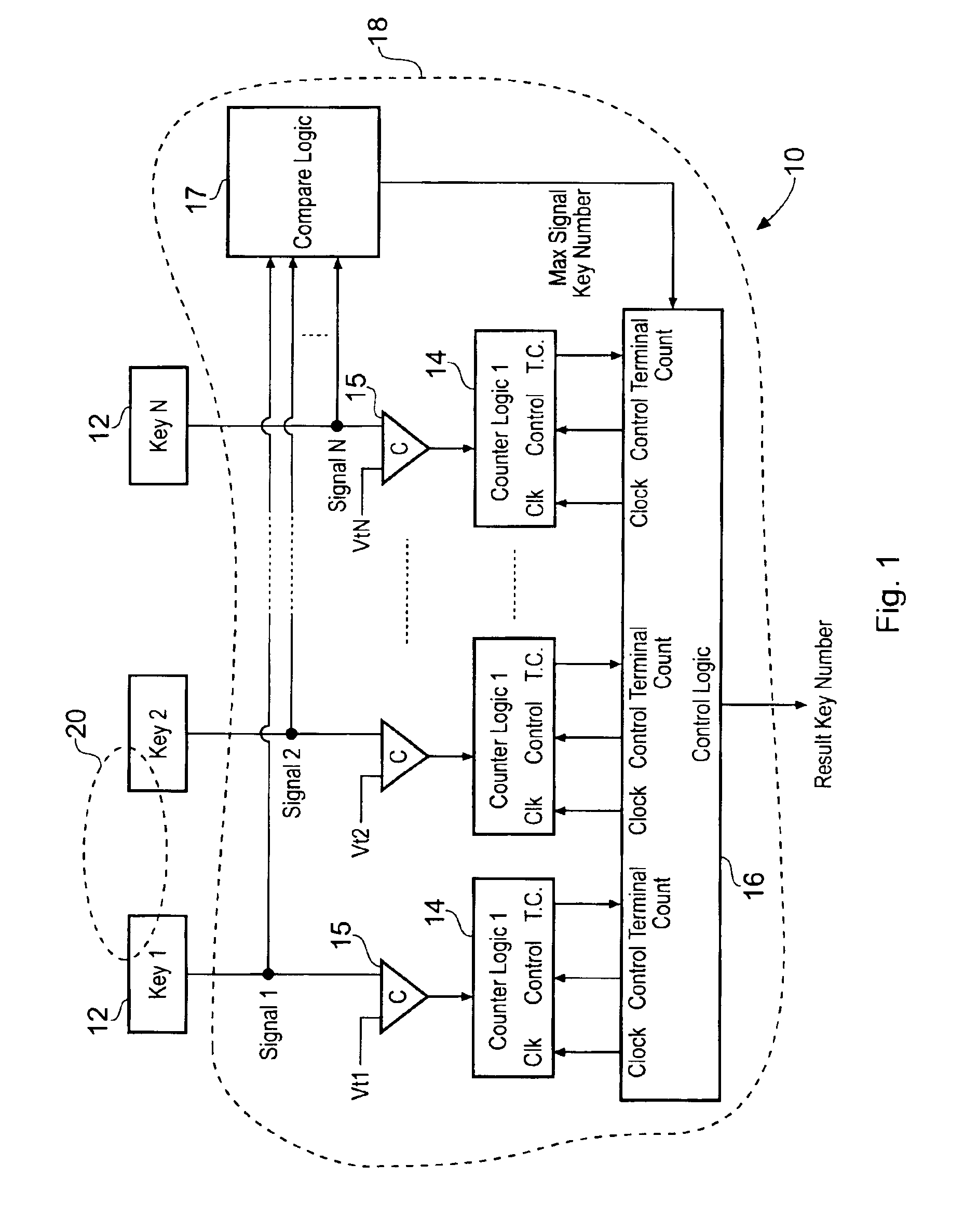
Capacitive Keyboard with Non-Locking Reduced Keying Ambiguity
ActiveUS20060192690A1Reduce ambiguitySignal strength valueElectronic switchingDevice coding detailsEngineeringIterative method
Keyboards, keypads and other data entry devices can suffer from a keying ambiguity problem. In a small keyboard, for example, a user's finger is likely to overlap from a desired key to onto adjacent ones. An iterative method of removing keying ambiguity from a keyboard comprising an array of capacitive keys involves measuring a signal strength associated with each key in the array, comparing the measured signal strengths to find a maximum, determining that the key having the maximum signal strength is the unique user-selected key, and maintaining that selection until either the initially selected key's signal strength drops below some threshold level or a second key's signal strength exceeds the first key's signal strength.
Owner:NEODRON LTD
Telemetry system with remote firmware updates or repair for remote monitoring devices when the monitoring device is not in use by the user
A system sends firmware updates from a telemetry system to a monitoring device. One or more sensors are coupled to a monitoring device that has a unique user ID. The sensors acquire user information selected from of at least one of, a user's activities, behaviors and habit information. ID circuitry at the monitoring device includes ID storage, a communication system that reads and transmits the unique ID from an ID storage, a power source and a pathway system to route signals through the circuitry and elements to enable installation of firmware updates. A telemetry system is in communication with the one or more sensors and includes a database of user ID's. The telemetry system analyzes telemetry data from the monitoring device based on at least one of, user's activities, behaviors and habit information and creating personalized information about the user.
Owner:FITBIT INC
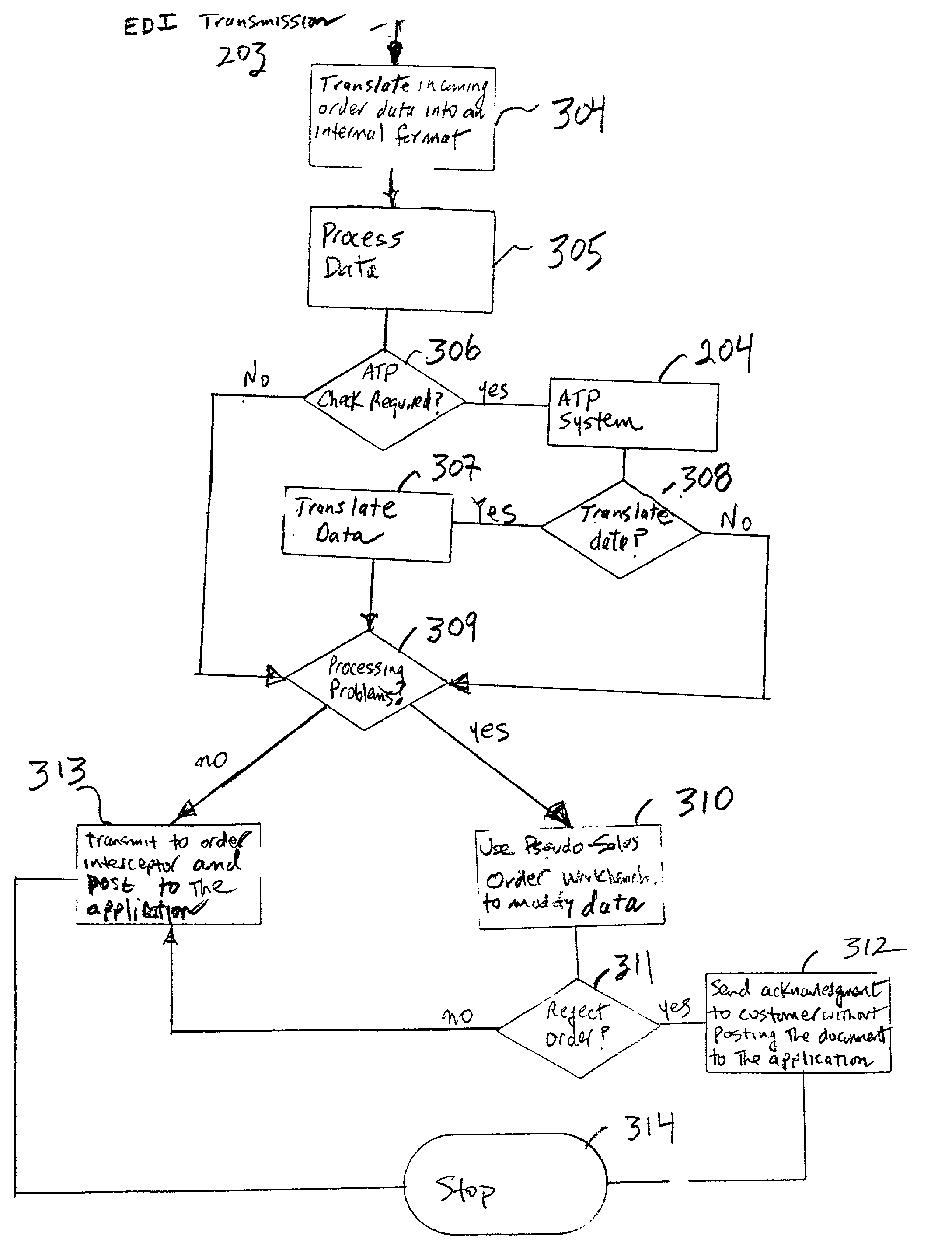
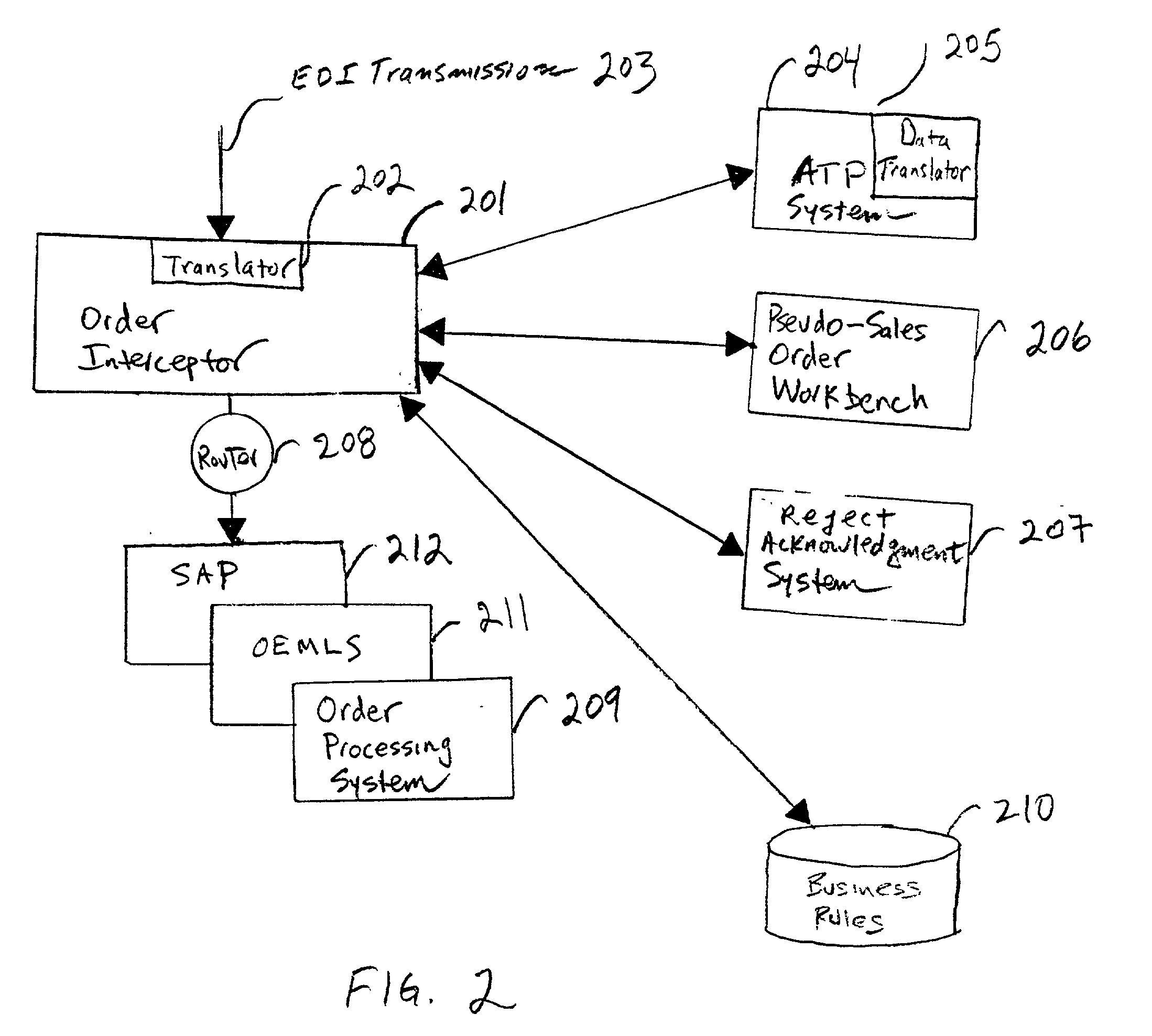
Pre-processor for inbound sales order requests with link to a third party available to promise (ATP) system
InactiveUS20020013731A1Hand manipulated computer devicesAnimal feeding devicesOrder fulfillmentDocumentation procedure
A method and apparatus for pre-processing electronic data requests within the EDI subsystem layer and within the order fulfillment application system. An order interceptor, third-party Available To Promise (ATP) interface, pseudo-sales order workbench, and the reject acknowledgment system processes are provided within the order fulfillment application system to accomplish the pre-processing. The order interceptor performs an asynchronous availability check before a sales order is posted. The result of the ATP check is stored in an ESO, and is applied during the posting process with unique user exits. The result of the ATP check is also used to determine key information about the sales order, such as the sales organization, and division and distribution channels. The pre-processor uses business rules to determine if the ESO should be split into multiple documents for requests satisfied across multiple sales areas. The Workbench provides a customer purchase order view of the ESO that looks, feels and behaves like actual order entry screens. The Workbench also displays messages generated from the pre-processor describing why the ESO was held for review. After the condition is corrected the Workbench re-executes the ESO pre-processor. This continues until all messages are corrected or marked reviewed. The supplier can decide to either accept the request, reject the request or accept individual line items.
Owner:IBM CORP
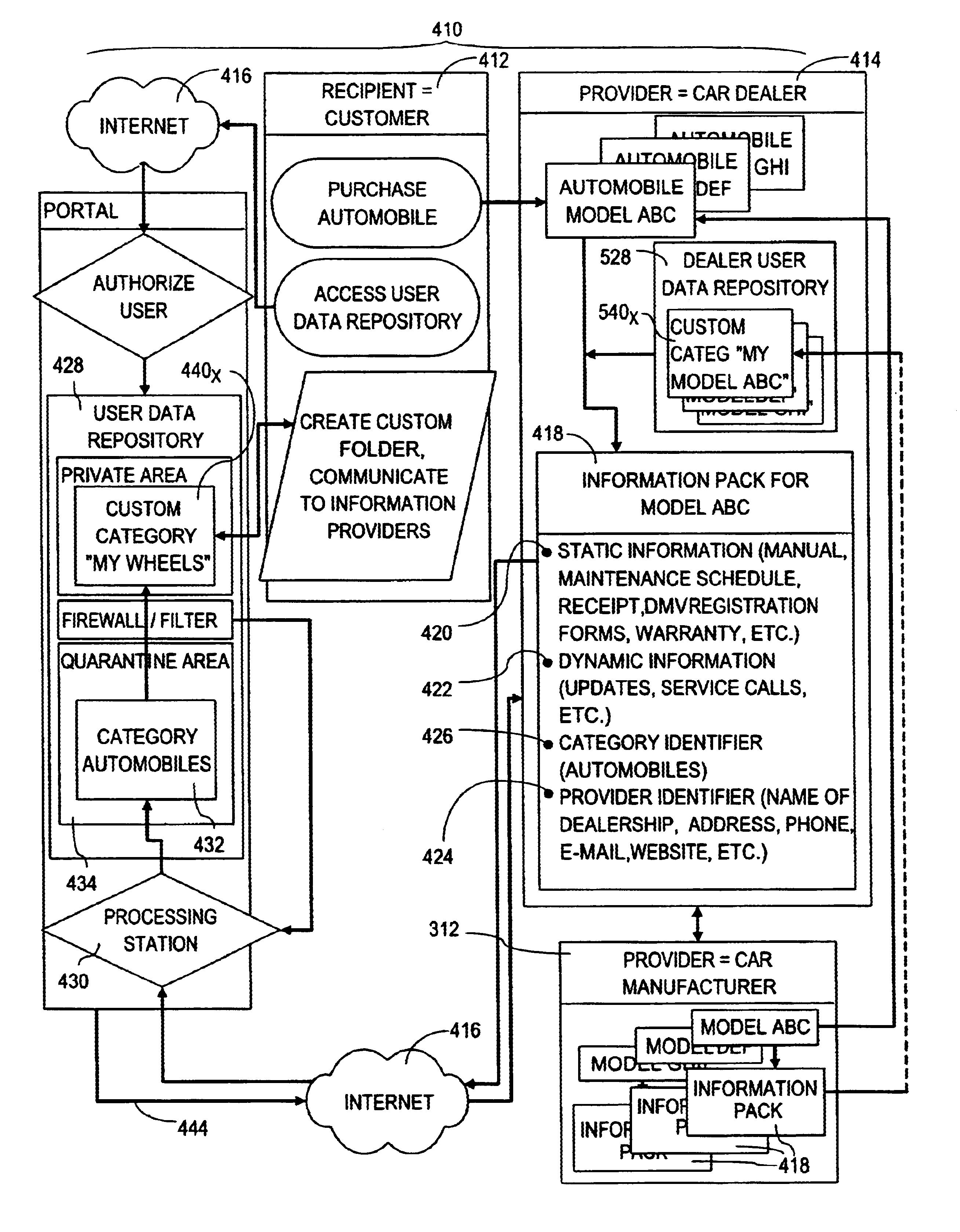
Data organization and management system and method
InactiveUS6651063B1Easy to operateSimple processDigital data information retrievalData processing applicationsData storeProcess information
An information storage and management system pre-categorizes information in generic categories to which the information generally pertains, to facilitate organization of information with little or no effort on the part of the recipient. Providers send information to user data repositories associated with unique user destination addresses within the system. Identifiers associated with the information allow the recipient to easily assess the nature of the information and conduct further processing of the information if desired. At least one of the identifiers associated with the information is a category identifier, used to place the information in a location within the user data repository reserved for information in that given identified category. One of the ways in which the recipient can further process the information is to place the information in a custom location according to a custom category location within the user data repository. Such custom categorization can further be communicated to the provider or to a data processing station so that subsequent information from the same provider to the same recipient is automatically placed in the custom category location within the user data repository.
Owner:DATACLOUD TECH LLC
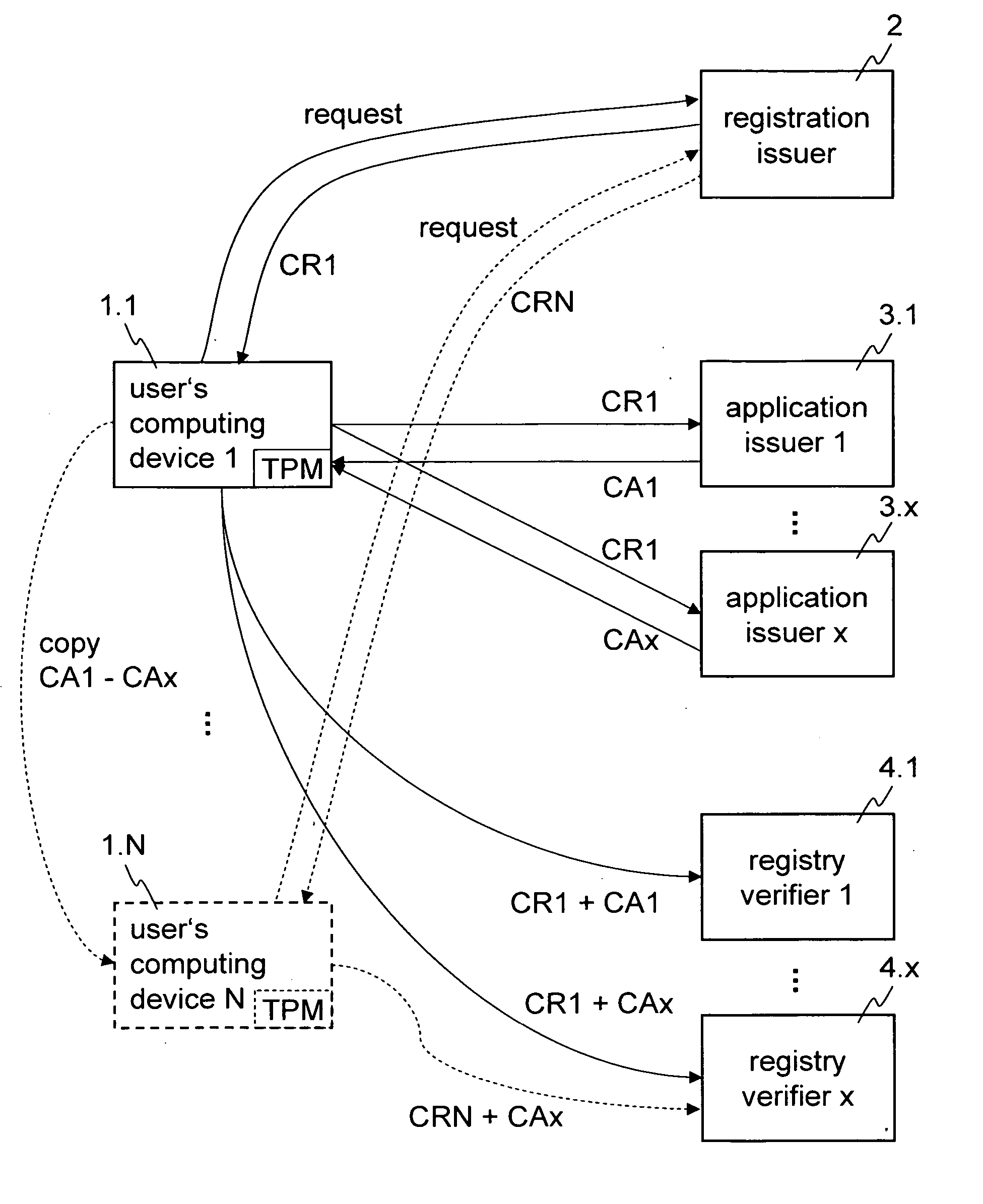
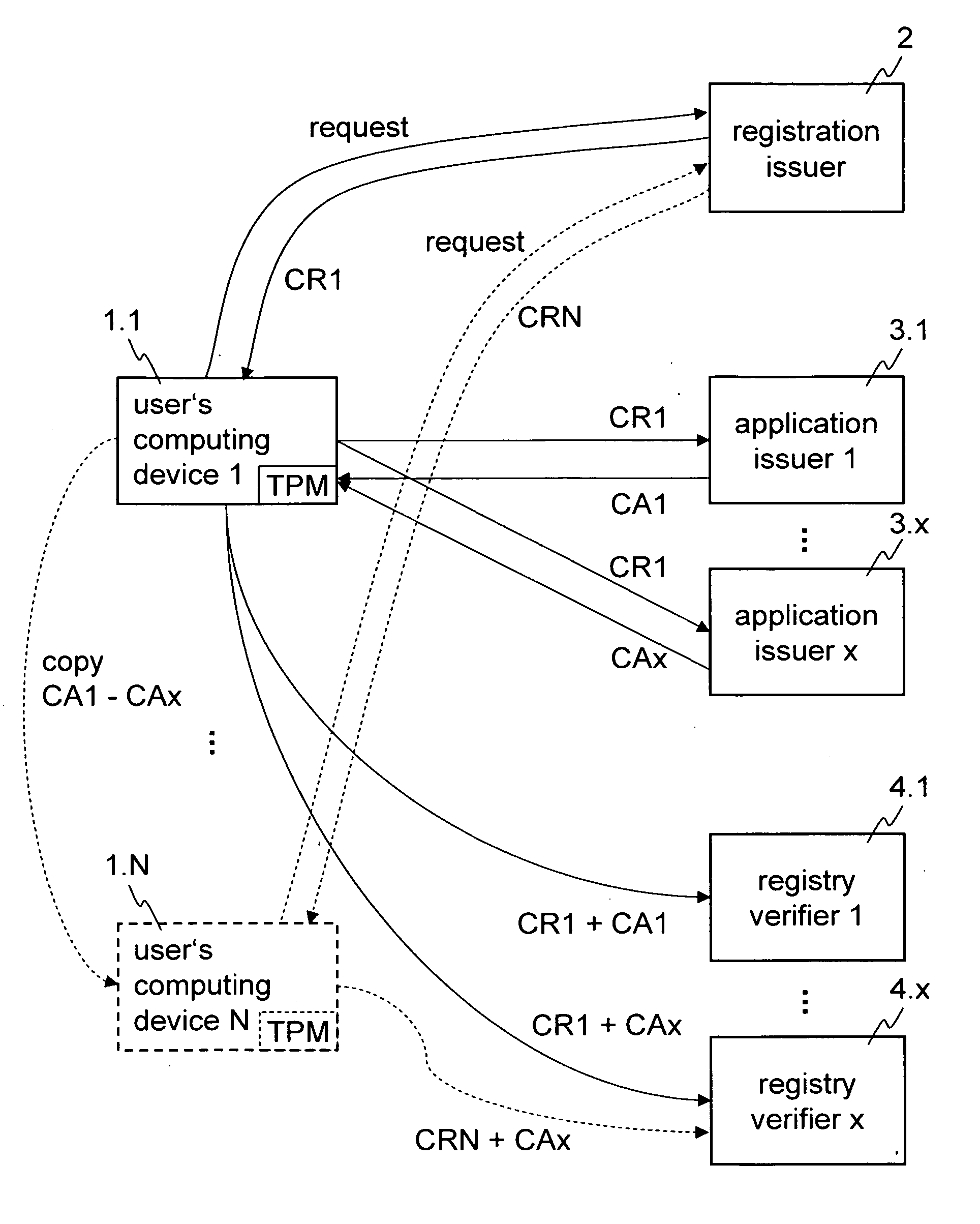
Method and apparatus for obtaining and verifying credentials for accessing a computer application program
InactiveUS20060101507A1Discourage unwanted and unauthorized circulationRandom number generatorsUser identity/authority verificationUnique identifierRegistered user
Methods for obtaining credentials and for verifying credentials are disclosed. In some embodiments, a request may be generated to register a computing device of a user to a registration issuer, and in response a device related credential for the computing device may be obtained, the device related credential being for exclusive use of that computing device and being related to a unique identifier of the user. A request for a credential for an application program may be generated, and in response an application credential for the application program may be obtained, the application credential being related to the unique identifier of the user. A request for access to the application program may be generated, the request comprising the application credential and the device related credential. In response to the request for access, access to the application may be granted if the device related credential and the application credential relate to the same unique user identifier.
Owner:IBM CORP
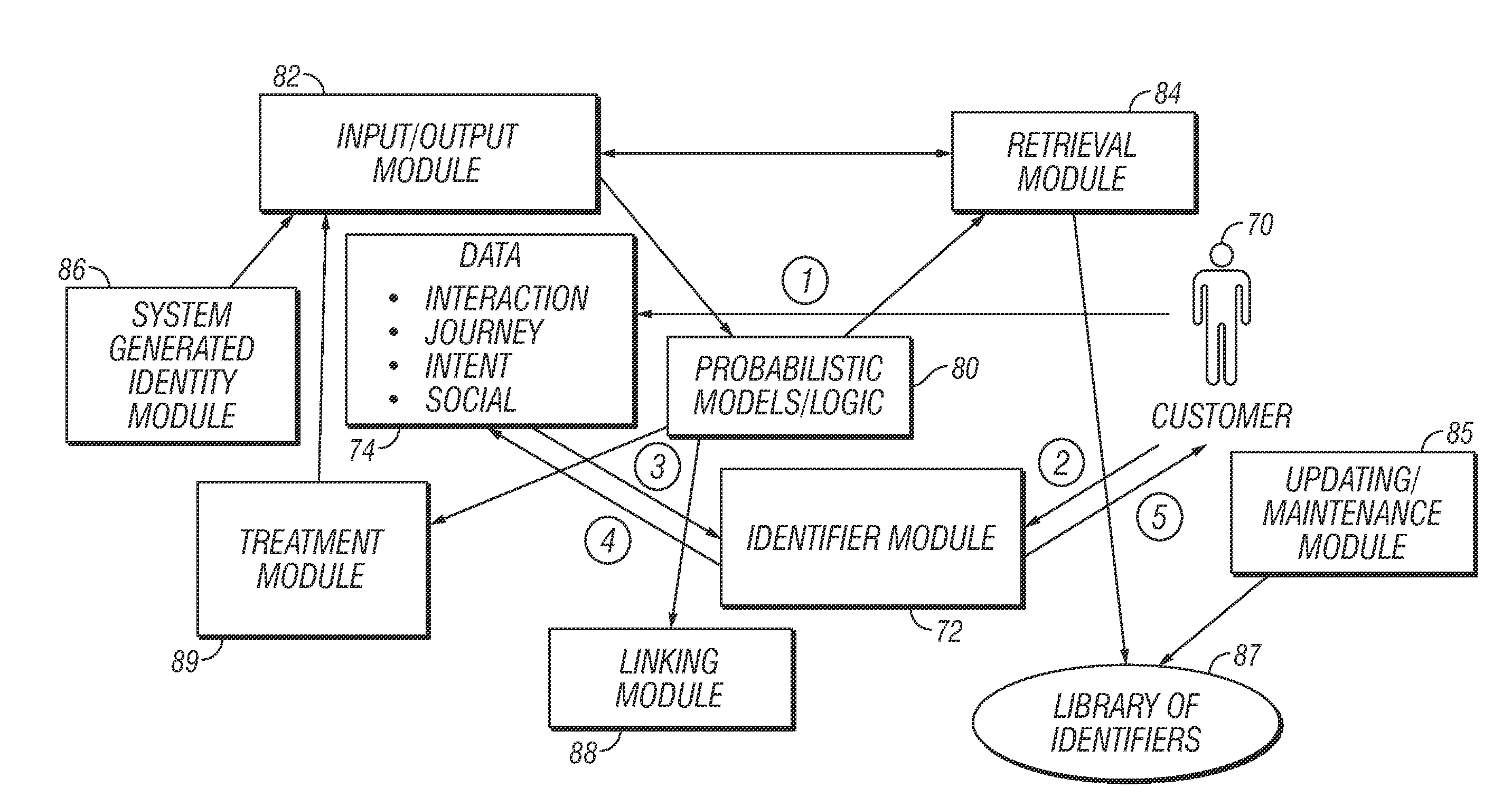
Method and Apparatus for Building a User Profile, for Personalization Using Interaction Data, and for Generating, Identifying, and Capturing User Data Across Interactions Using Unique User Identification
ActiveUS20140207518A1Upgrade user experienceWebsite content managementTransmissionPersonalizationHuman–computer interaction
A user profile is creates, and personalization is provided, by compiling interaction data. The interaction data is compiled to generate a value index or score from a user model. Parameterized data is used to build tools which help decide an engagement strategy and modes of engagement with a user. Several facets relating to the user, such as user behavior, user interests, products bought, intent, chat language, and so on, are compiled to create a user profile based personalization technique. In another embodiment, a unique ID is provided that can be mapped across multiple channels for use by the user to contact various organizations across multiple channels, and thus upgrade the user's experience.
Owner:24 7 AI INC
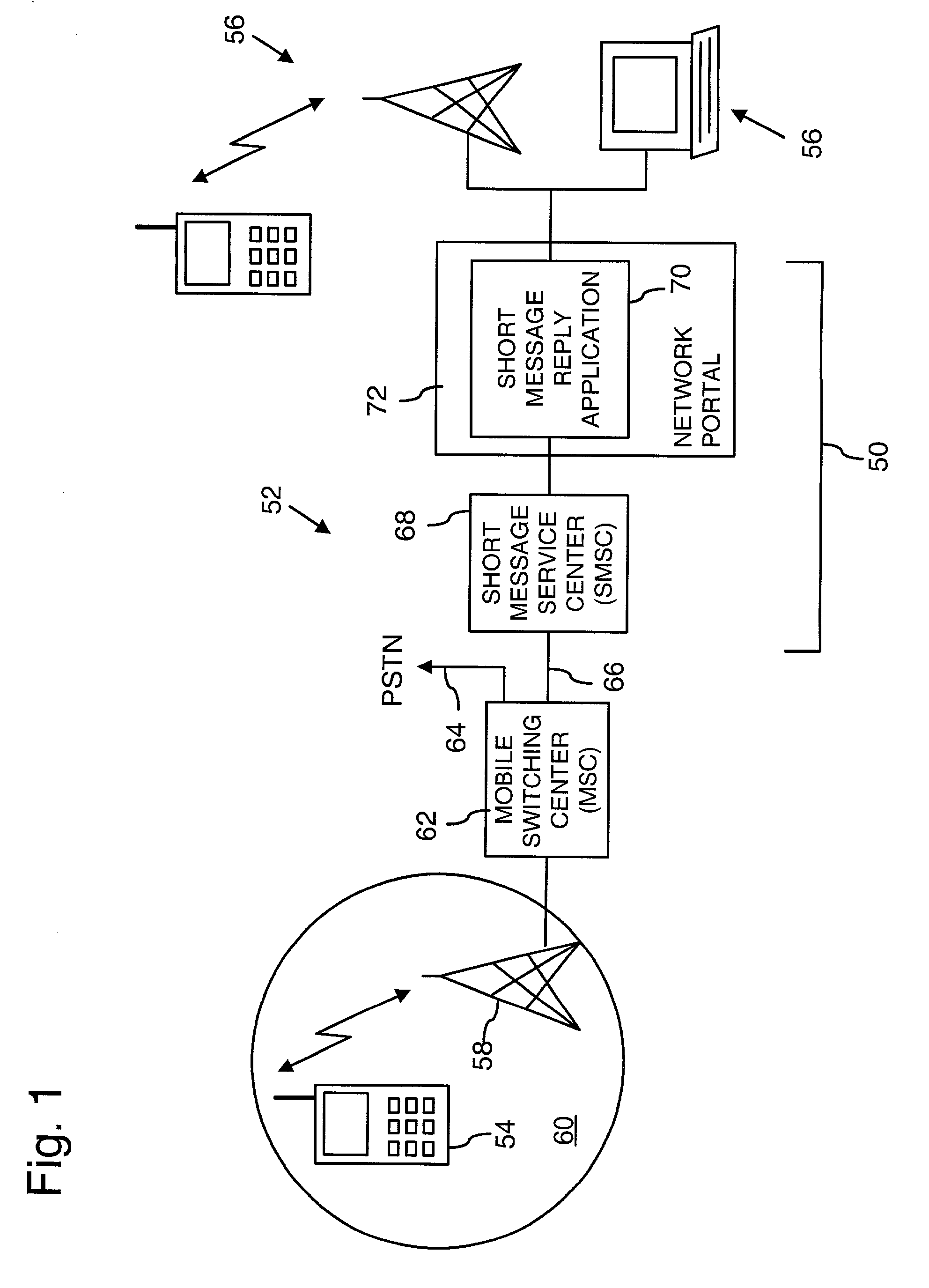
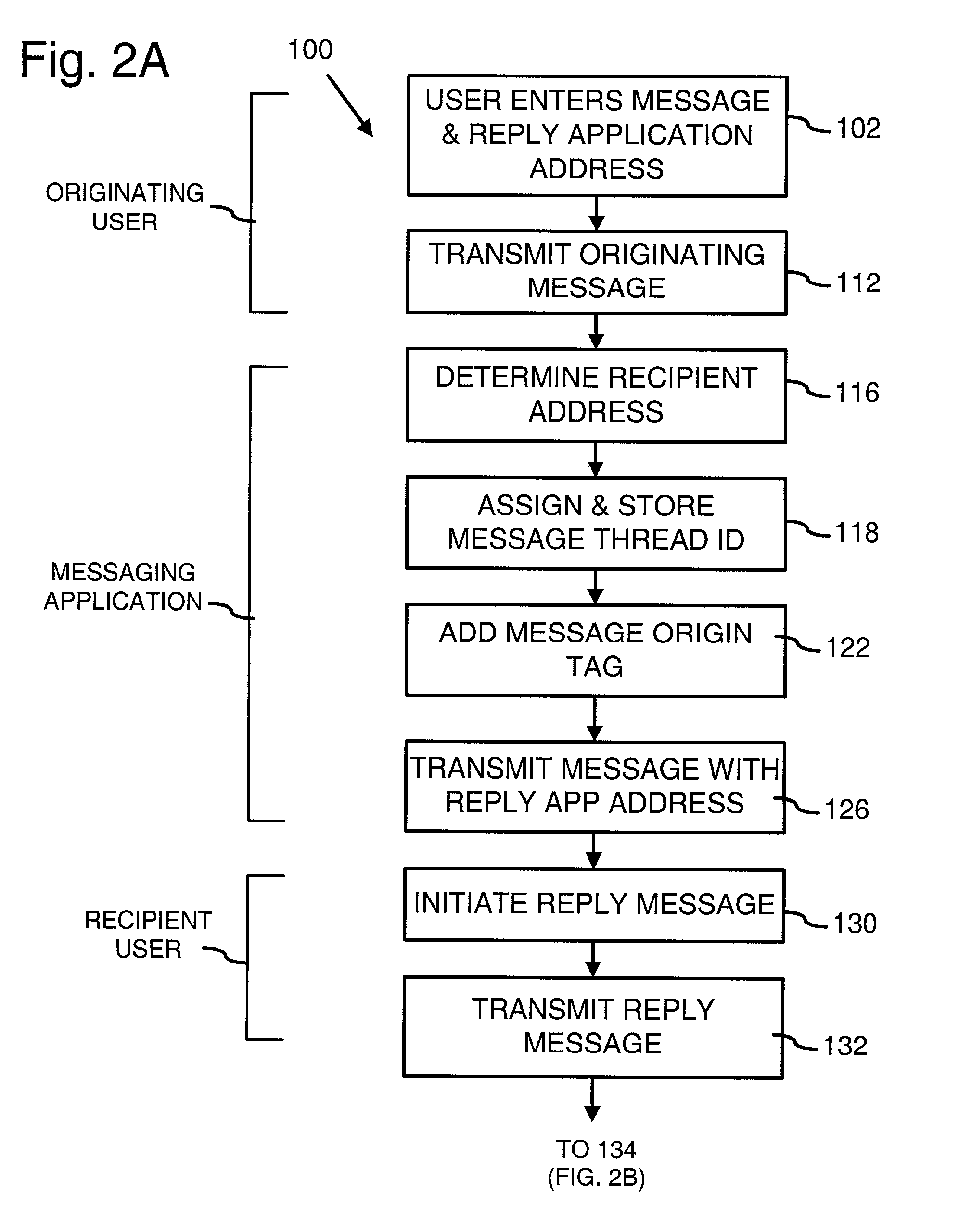
Mobile telephone short text messaging with message thread identification
InactiveUS20030114174A1Simplify reply messagingLess spaceRadio/inductive link selection arrangementsMessaging/mailboxes/announcementsNetwork addressingNetwork address
Electronic messaging in a one-to-one, one-to-many, or many-to-many messaging session is directed through a short text messaging application. The short text messaging application incorporates a message thread identifier with a message that is sent to a recipient or group of recipients. The message thread identifier may be embedded in the header information of the message, for example, and is associated with the unique user identification code or network address of each recipient. Any reply to such a message is directed to the originating user and any other recipients based upon the message thread identifier.
Owner:AT&T WIRELESS SERVICES
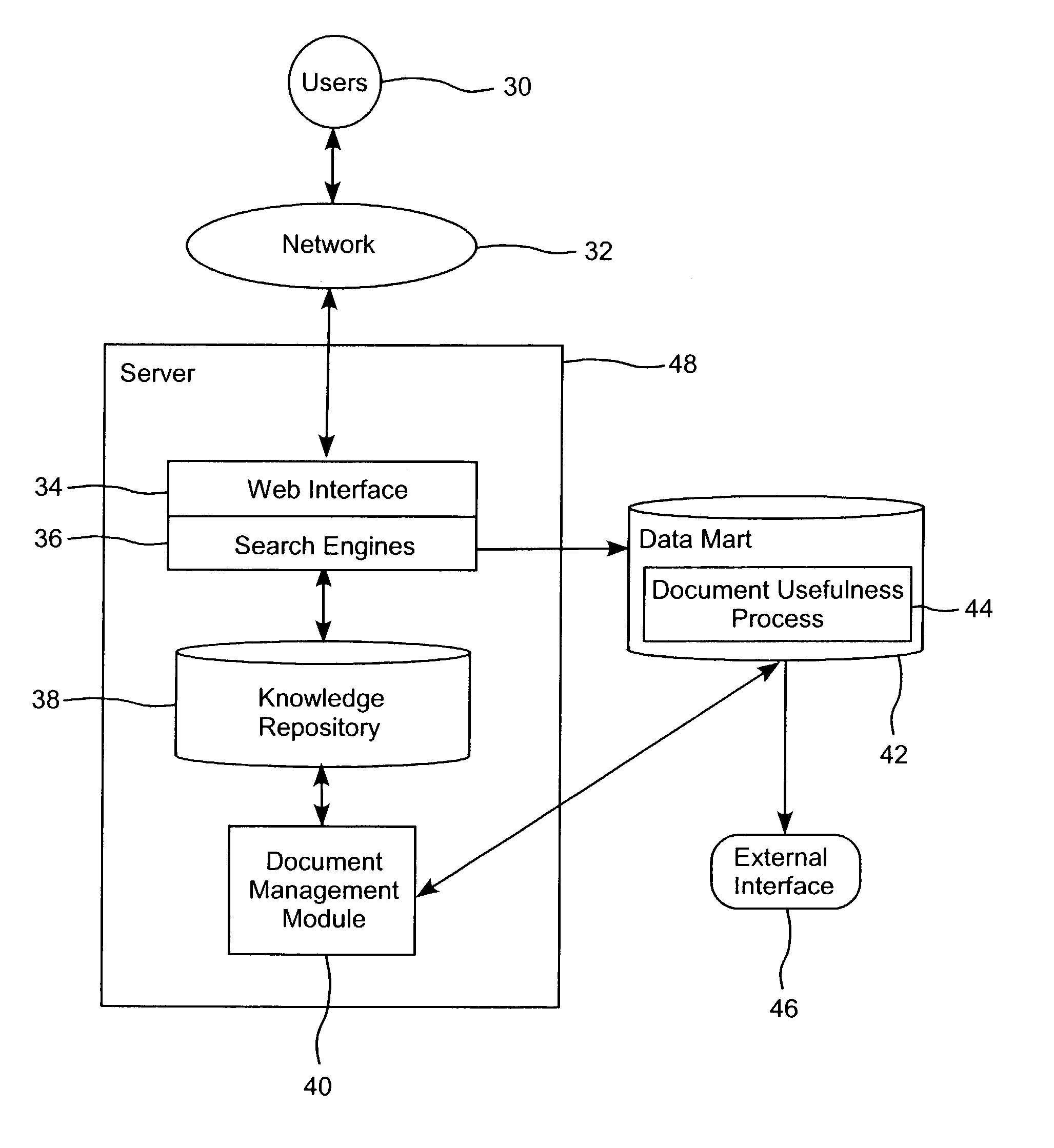
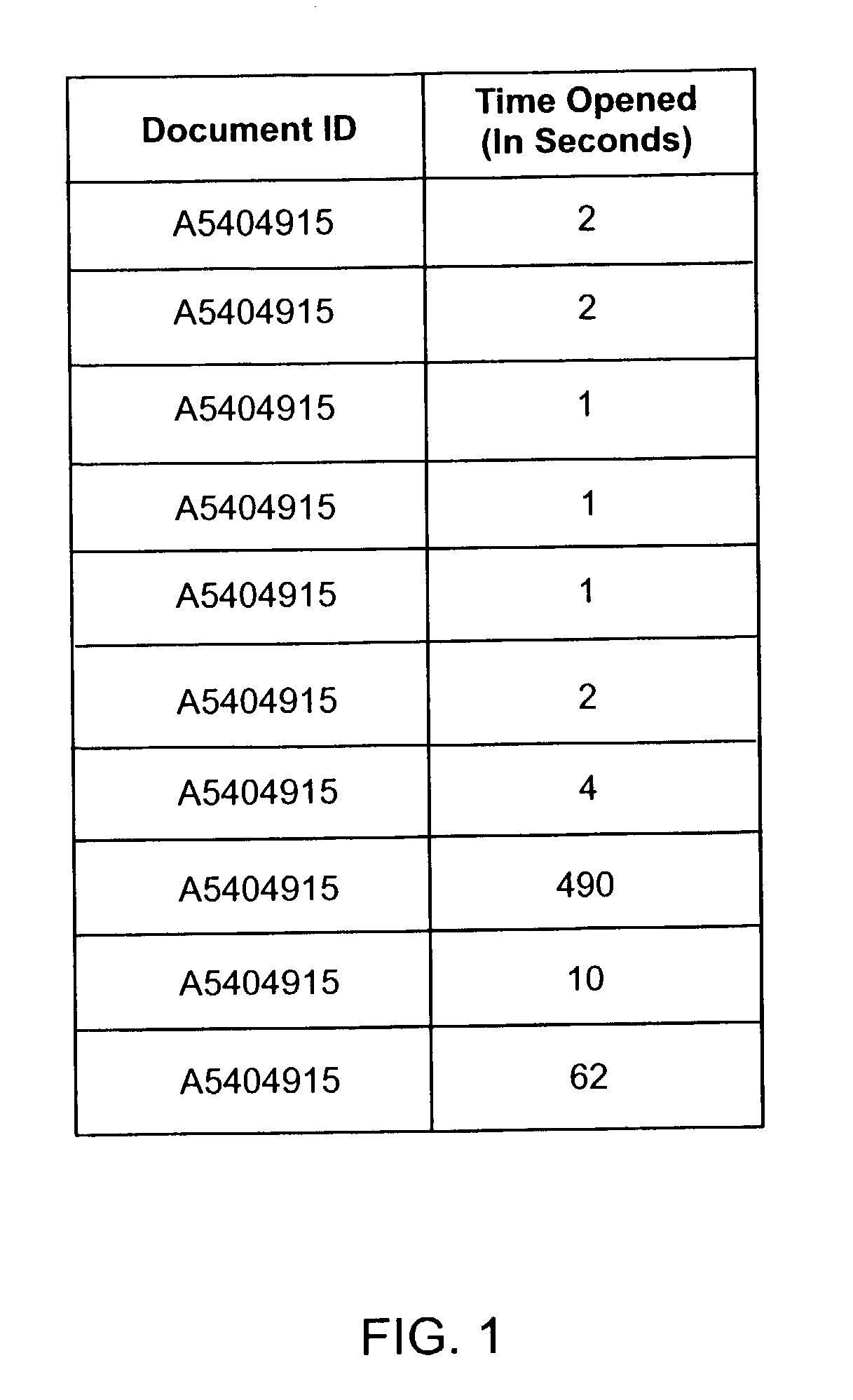
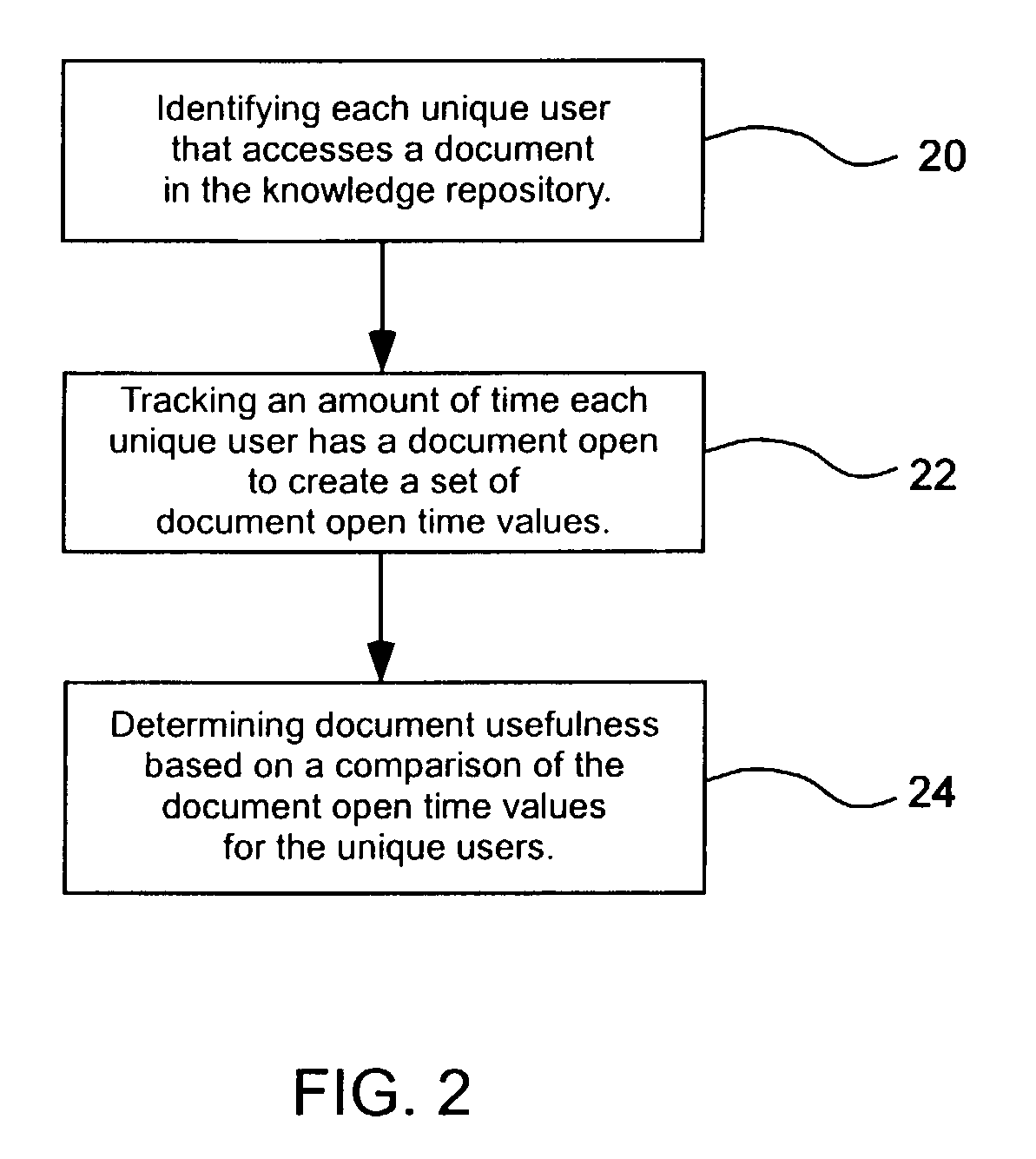
System and method for identifying useful content in a knowledge repository
ActiveUS7016889B2Knowledge representationSpecial data processing applicationsDocumentationKnowledge base
A system and method is provided for identifying useful content in a knowledge repository accessed by a plurality of users. The system and method includes the operation of identifying each unique user that accesses a document in the knowledge repository. Another operation is tracking an amount of time each unique user has a document open to create a set of document open time values. Document usefulness is then determined based on a comparison of the document open time values for the unique users.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
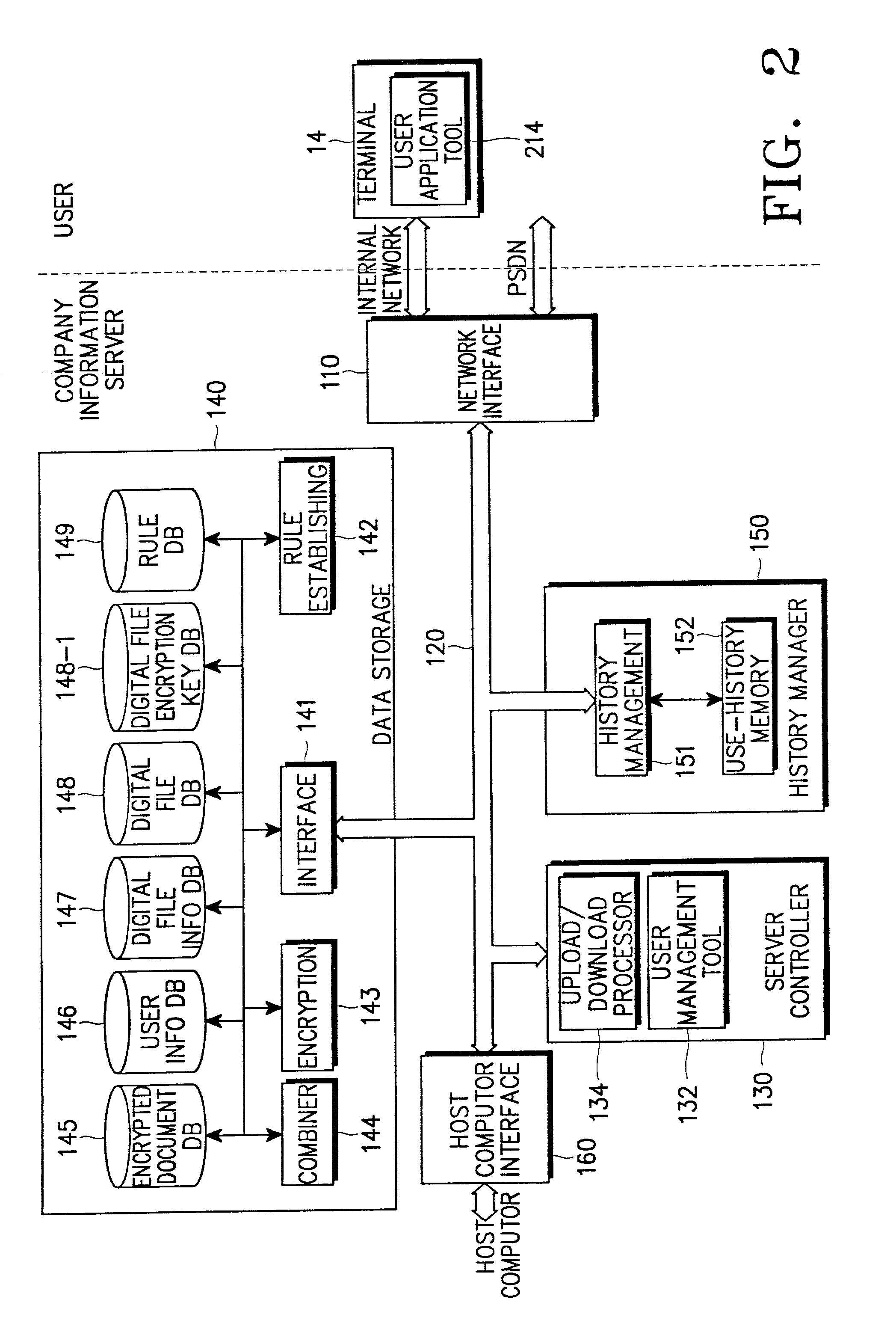
Method for securing digital information and system therefor
InactiveUS20030023559A1Key distribution for secure communicationData taking preventionUser authenticationInformation security
A digital information security system is disclosed. A user application tool installed in a user terminal, creates a unique user key using unique system information of the user terminal. A data storage unit stores user information and digital information. A user management tool installed in a server, receives the unique user key created by the user application tool, stores the received unique user key in the data storage unit as part of the user information, and compares, during user authentication, the stored unique user key with a unique user key provided from the user application tool of a user currently being subjected to authentication.
Owner:MARKANY
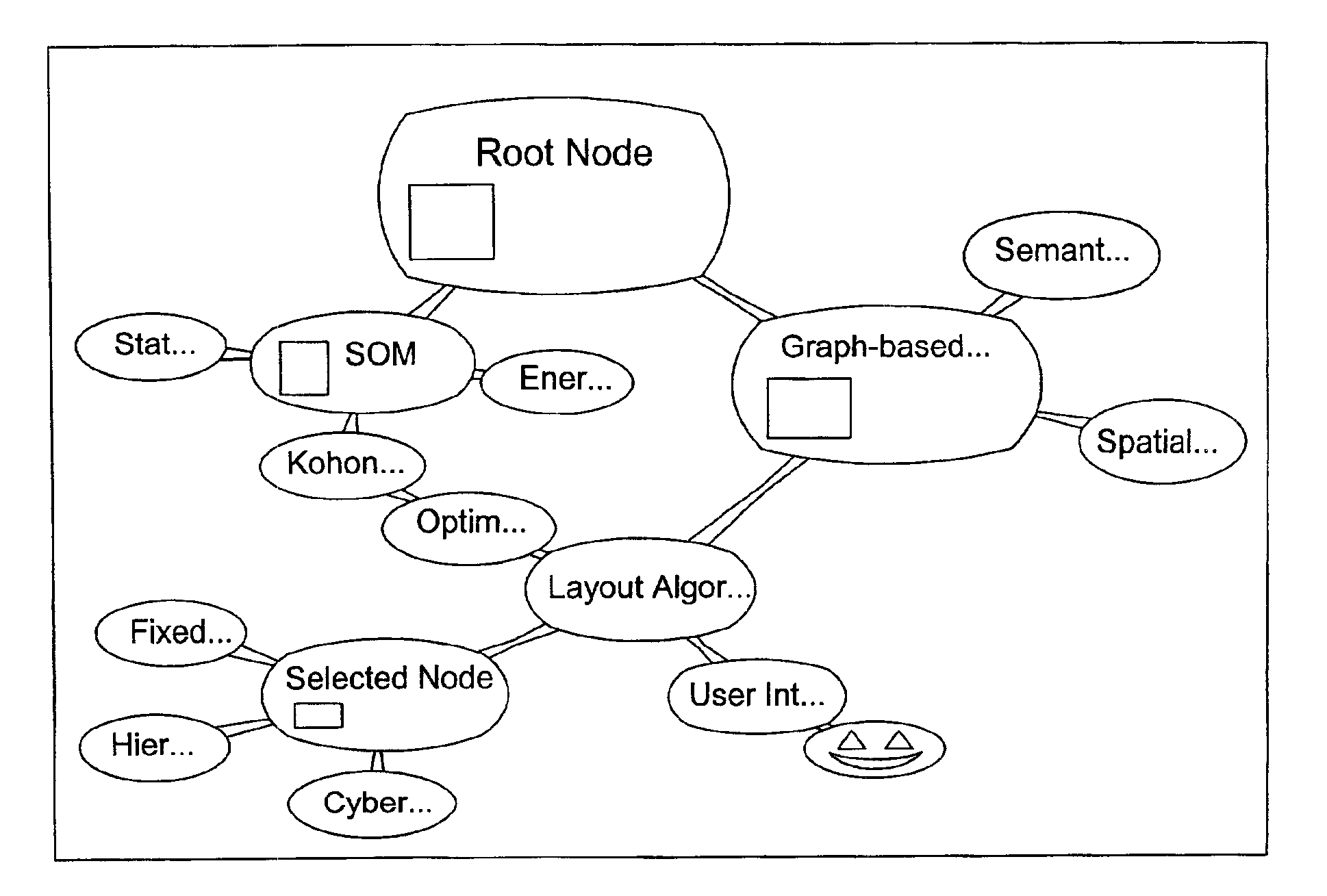
Method of navigating a collection of interconnected nodes
InactiveUS6931604B2Display moreAccurate descriptionDrawing from basic elementsDigital output to display deviceGraphicsTheoretical computer science
A method and apparatus for organizing and processing interconnected pieces of information (“nodes”) using a digital computer is disclosed. Each node has elements that may be text, images, audio, video, and other computer programs. A graph-based user interface presents the individual nodes in spatial arrangements that reflect the relationships among the nodes. User interaction indicating interest in a particular node results in an increase in the “activation” of that node. This leads to an increase in the size of the presentation of that node, as well as an increase in the size of the presentation of closely related nodes. The result is a unique user interaction paradigm that allows for intuitive traversal of complex collections of nodes.
Owner:LANE DEREK GRAHAM
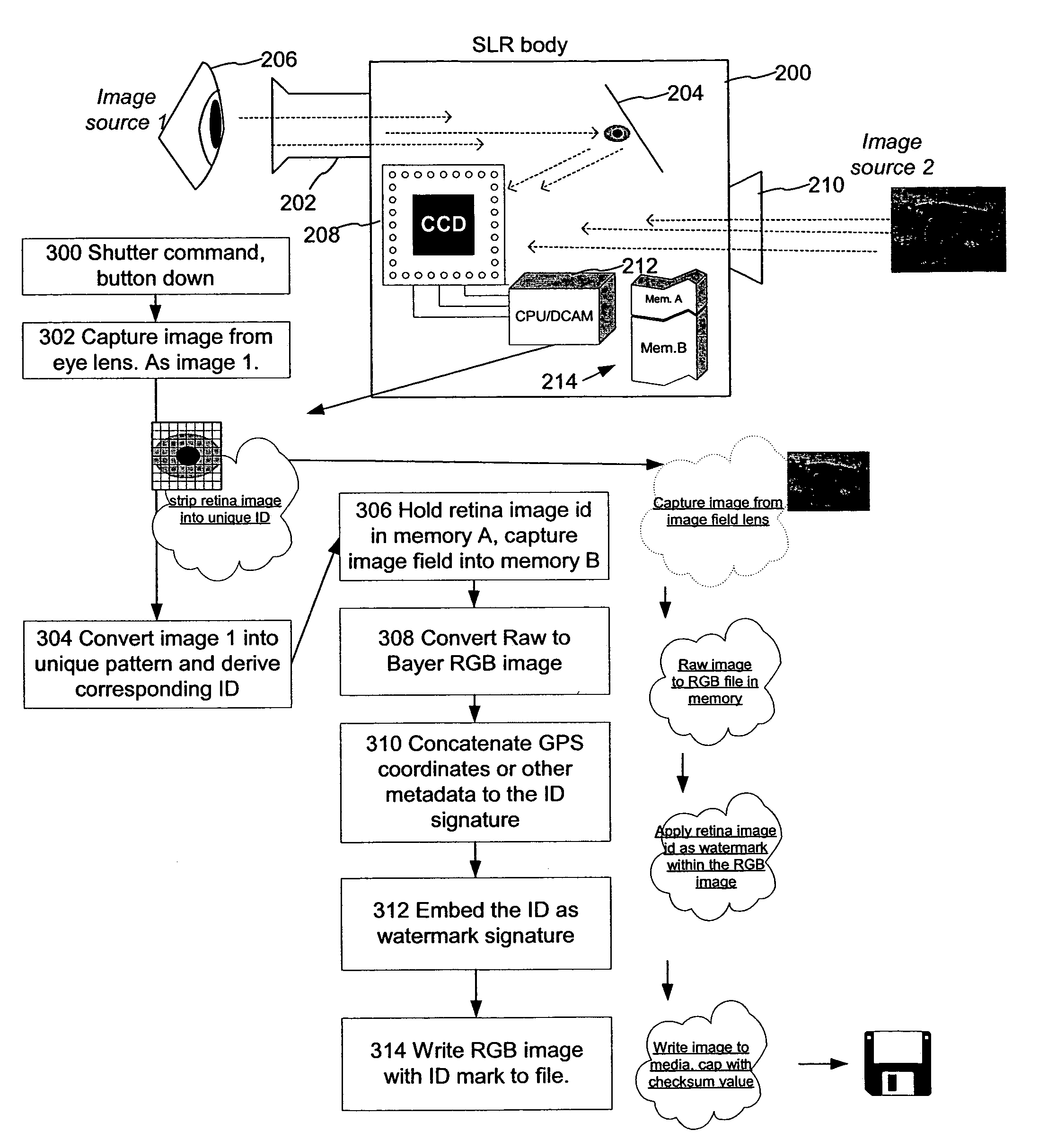
Capturing and encoding unique user attributes in media signals
InactiveUS7043048B1Character and pattern recognitionPictoral communicationComputer scienceRetinal scan
User attribute data, such as a retinal scan, is encoded into a media signal as it is captured in media capture device, such as a camera, video recorder, etc. The user attribute data uniquely associates the creator with the content he or she creates. By steganographically embedding the user attribute data into the content at or near the time of capture, the creator of the content can be authenticated at a subsequent time. In addition, alteration of the content can be detected.
Owner:DIGIMARC CORP
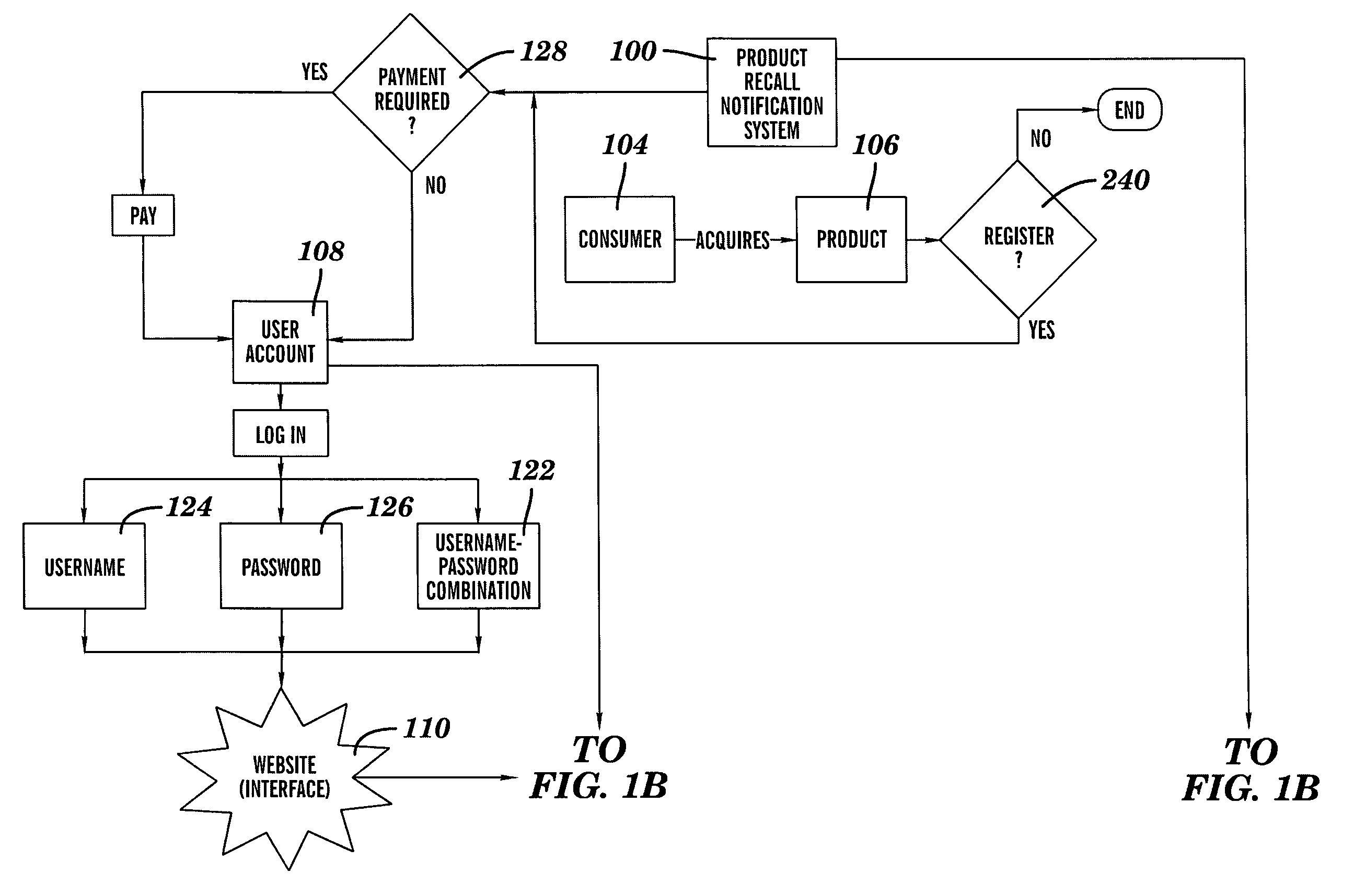
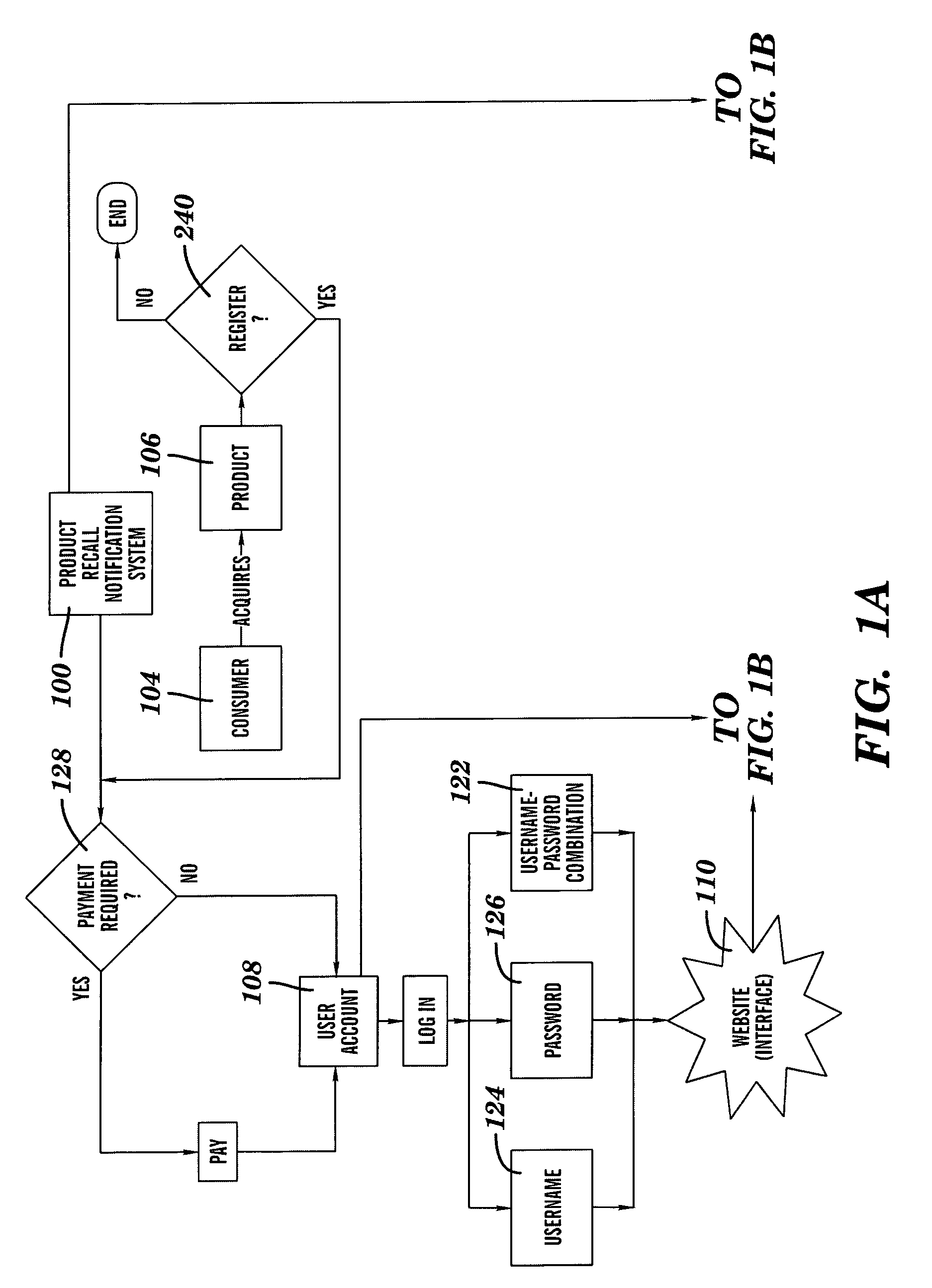
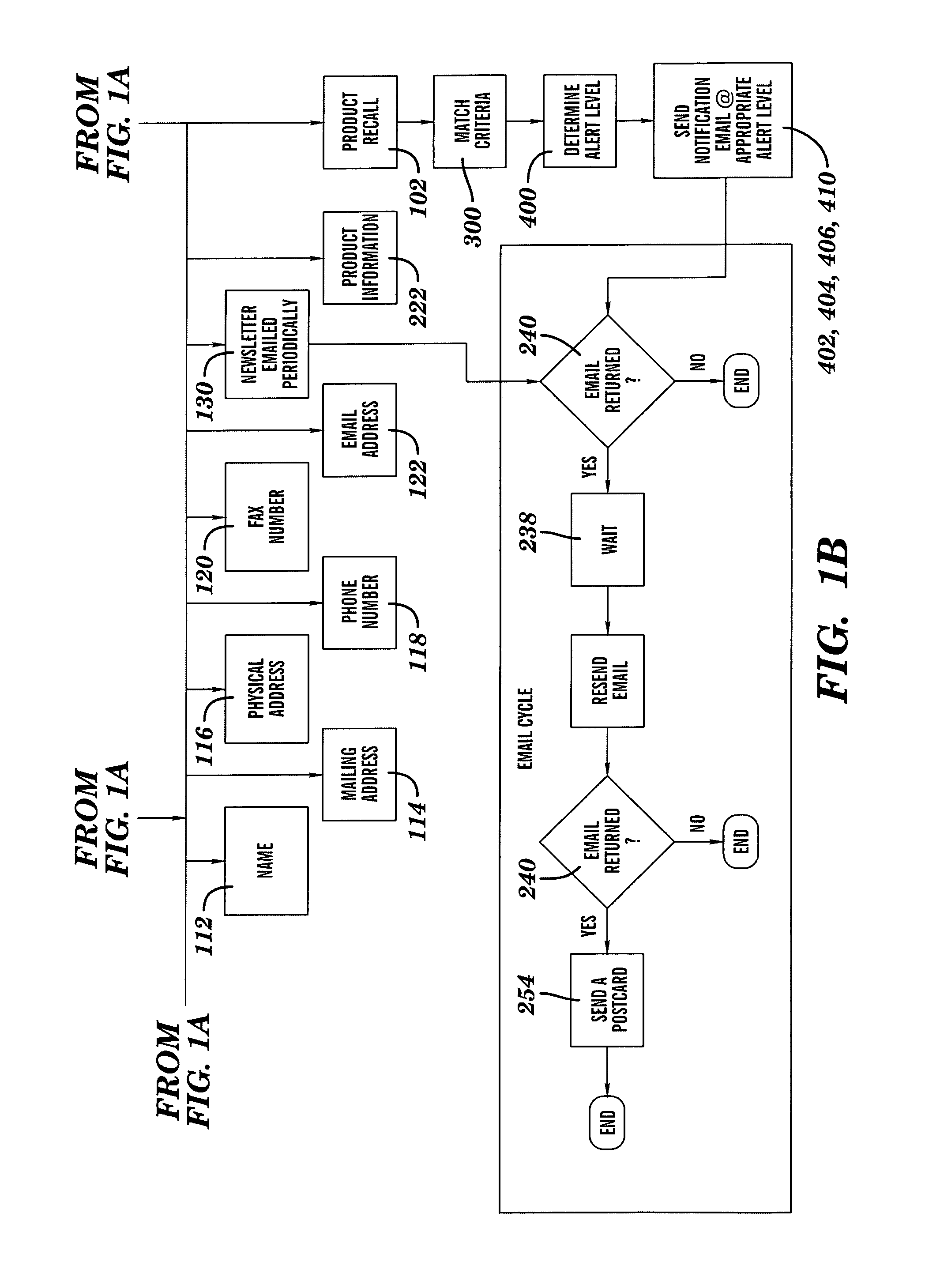
System and Method of Selectively Notifying Consumers of Product Recalls
Described herein is a system and method of using the system for notifying consumers regarding product recall comprising: assignment of a unique user account to a newly registered consumer by an internet-based product recall notification system, the user account comprising a database wherein all products registered by that consumer are listed and a web interface whereon the products the consumer has listed as owned are listed with product recall alert-level status shown, and the unique user account requiring a logon verification method that is selected from the group consisting of username-and-password match, username match, and password match; the product recall notification system collecting consumer contact information; the product recall notification system collecting product information from the consumer about one or more products that the consumer has acquired; the product recall notification system sending regular periodic email to the registered consumers; the product recall notification system responding to email returned undeliverable; the product recall notification system receiving information about a product recall; the product recall notification system comparing the information received about the product recall to the consumer's data; the product recall notification system generating an email alert at a level determined by the match between the consumer's registered product and a recalled product to the consumer notifying the consumer about the recall of the registered product; and the product recall notification system generating a flashing screen alert at a level determined by the match between the consumer's registered product and a previously recalled product when the consumer enters information about a product that has previously been recalled.
Owner:JOHNSON SCOTT KEVIN +1
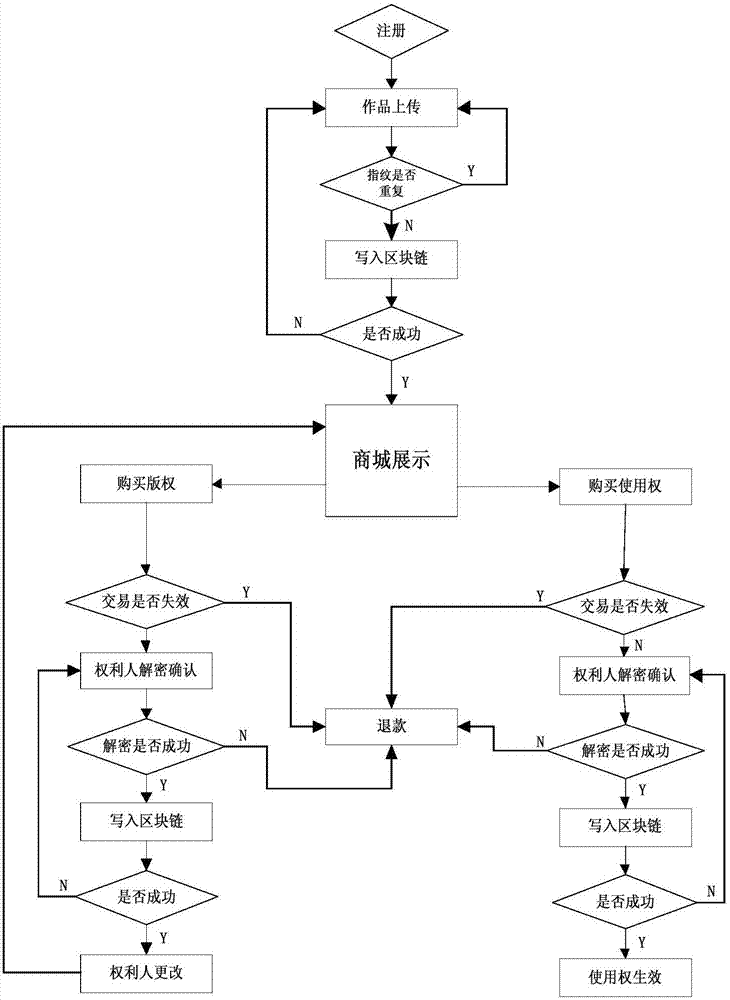
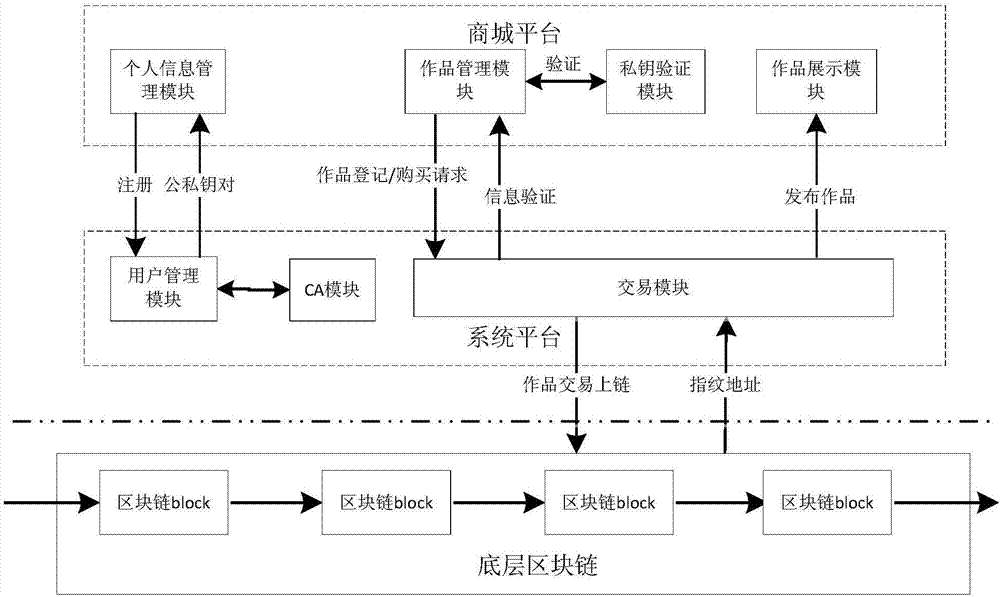
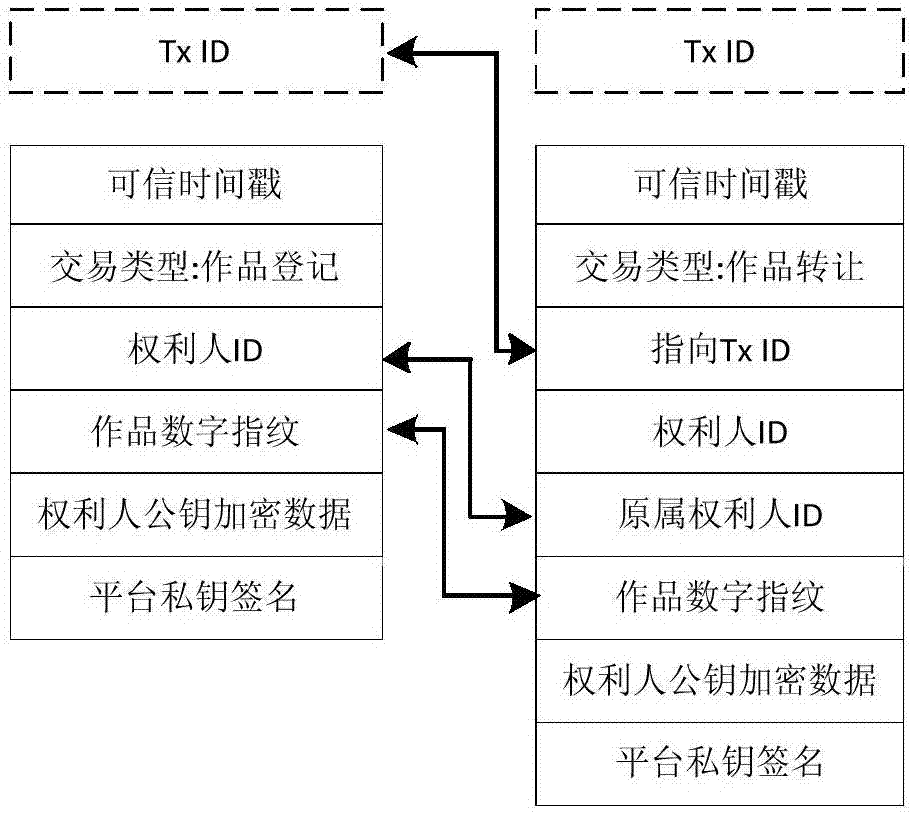
Blockchain-based copyright trading system and trading method
InactiveCN107330694AEliminate secondary transactionsCopyright transactions are open and transparentProtocol authorisationTimestampTransaction data
The invention discloses a blockchain-based copyright trading system and a trading method. The blockchain-based copyright trading method comprises creating the copyright trading system, and the trading system comprises a system platform, a shopping mall platform and bottom blockchains. The method is characterized in that a user is registered as a platform user through the system platform, and the system platform issues a unique public-private key pair and a unique user ID for the platform user; a copyright owner uploads a work to the shopping tall platform, and adds signatures of public and private keys to the work; the shopping mall platform verifies signature information of the copyright owner through the private key, and generates fingerprint information uniquely corresponding to the signature information for the work; and the system platform creates a blockchain transaction, and perform cochain on fingerprint information, copyright owner public key encrypted data, the copyright owner ID, a transaction type, a credible timestamp and the platform private key signature, which are taken as transaction data, at the same time. All transaction details are recorded by utilizing the blockchains, and then copyright trading is very secure.
Owner:重庆小犀智能科技有限公司
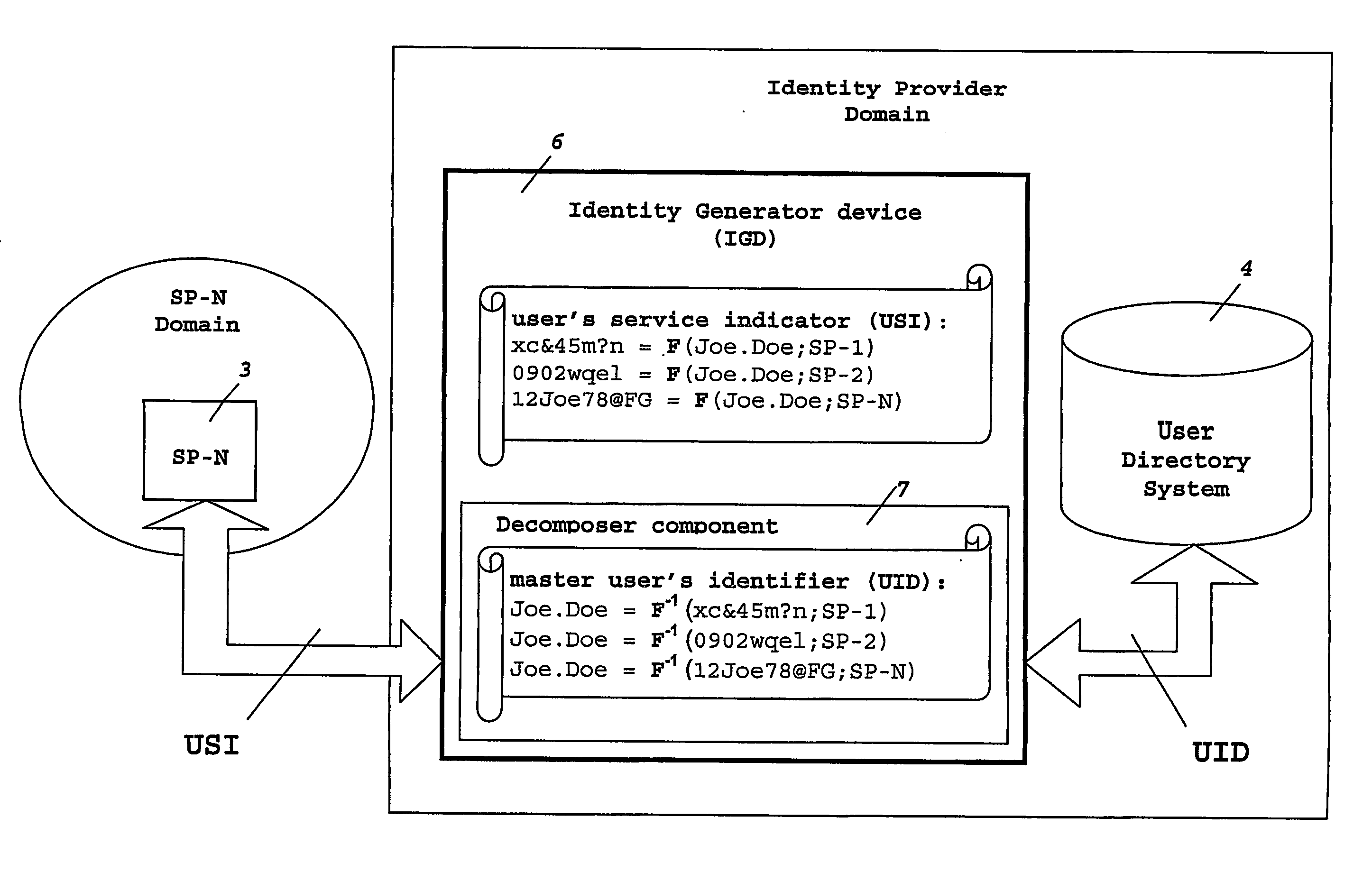
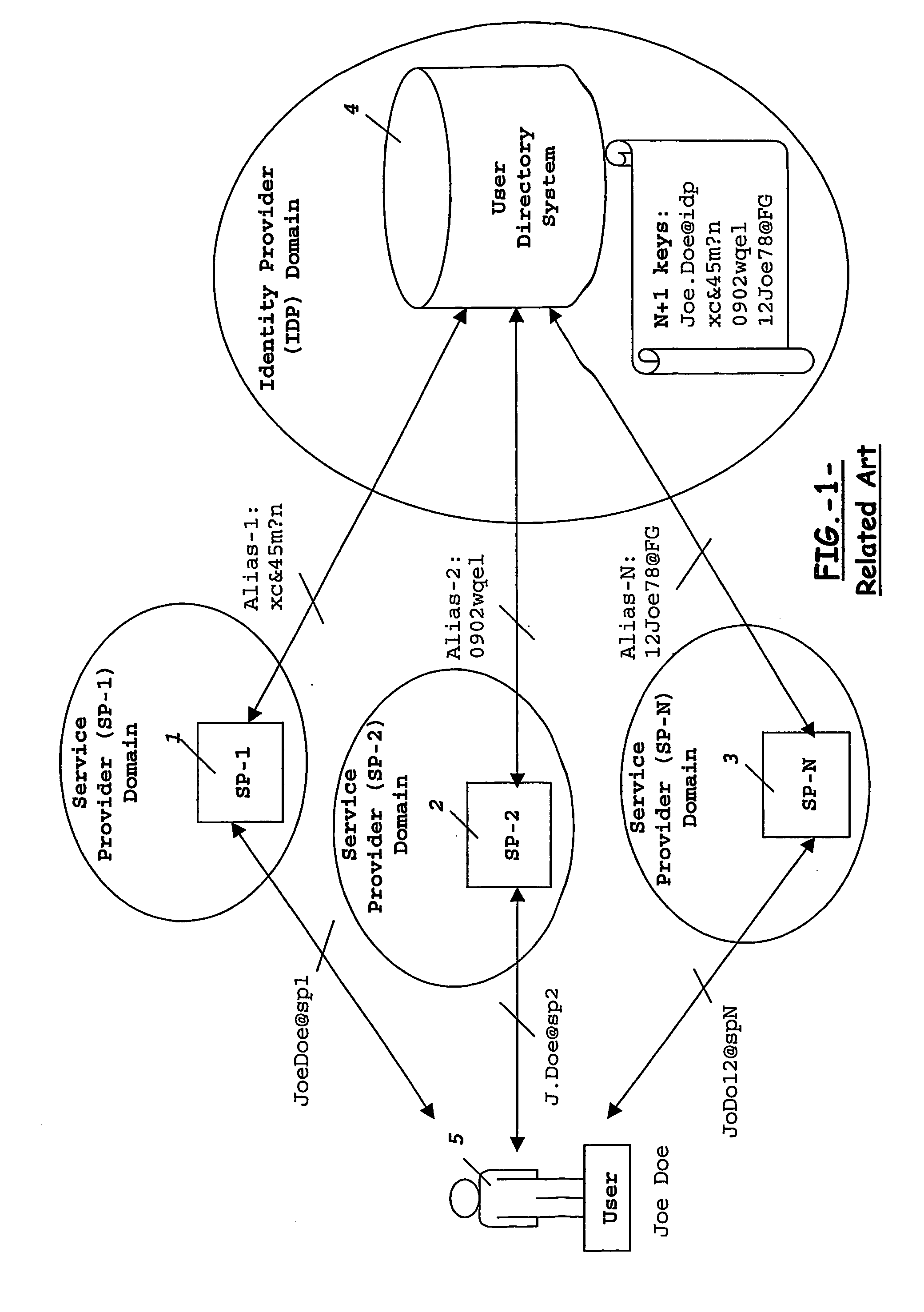
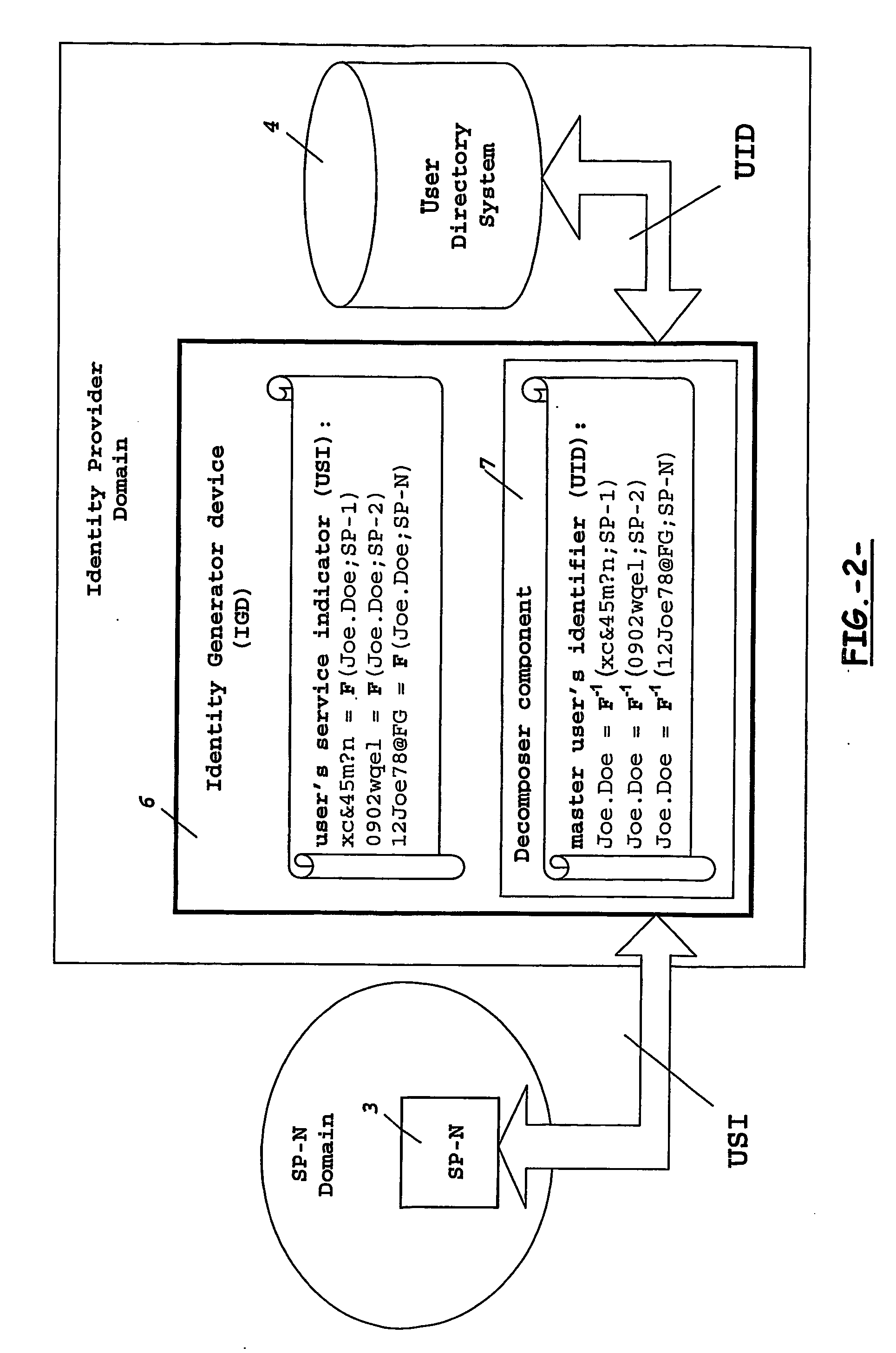
Means and method for generating a unique user's identity for use between different domains
InactiveUS20070130343A1Multiple digital computer combinationsTransmissionComputer networkIdentity provider
Mobile operators presently offer services on behalf of service providers where such services are really carried out for the users. Mobile operators act as identity providers in this scenario, wherein service provider and identity provider share a unique identity to identify each particular user accessing a number of services. As the number of users accessing these services, and the number of services offered from different service providers increase, the storage required at the operator's network for such amount of user's identities becomes a problem. To overcome this and other problems, the present invention provides an identity Generator device arranged to generate a user's service indicator to identify the user between the service provider and the identity provider, the user's service indicator comprising a master user's identifier for identification of the user at the identity provider, and a service identifier indicating the services to be accessed at a given service provider.
Owner:TELEFON AB LM ERICSSON (PUBL)
Parking management system and method based on Internet of things
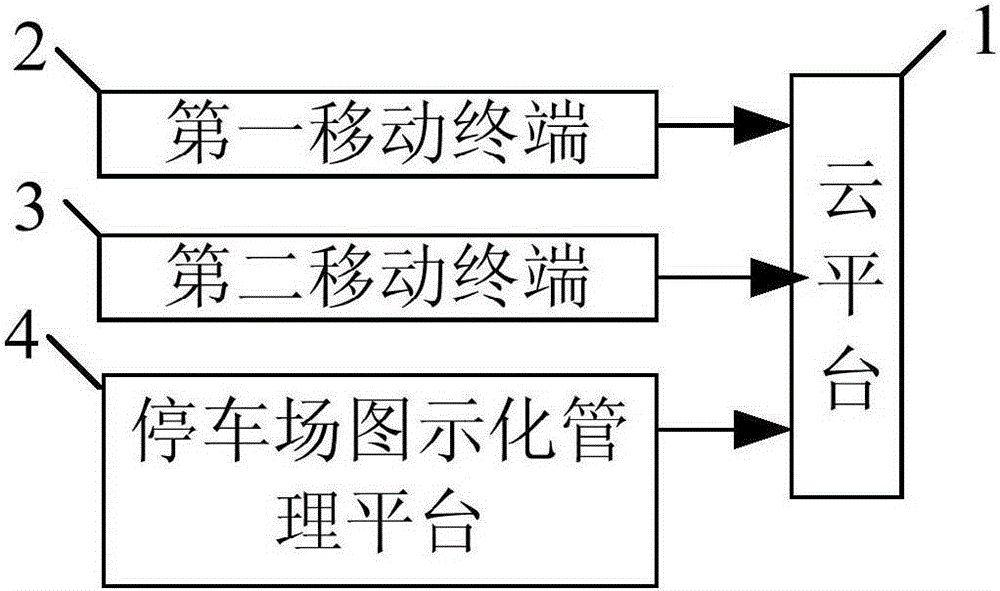
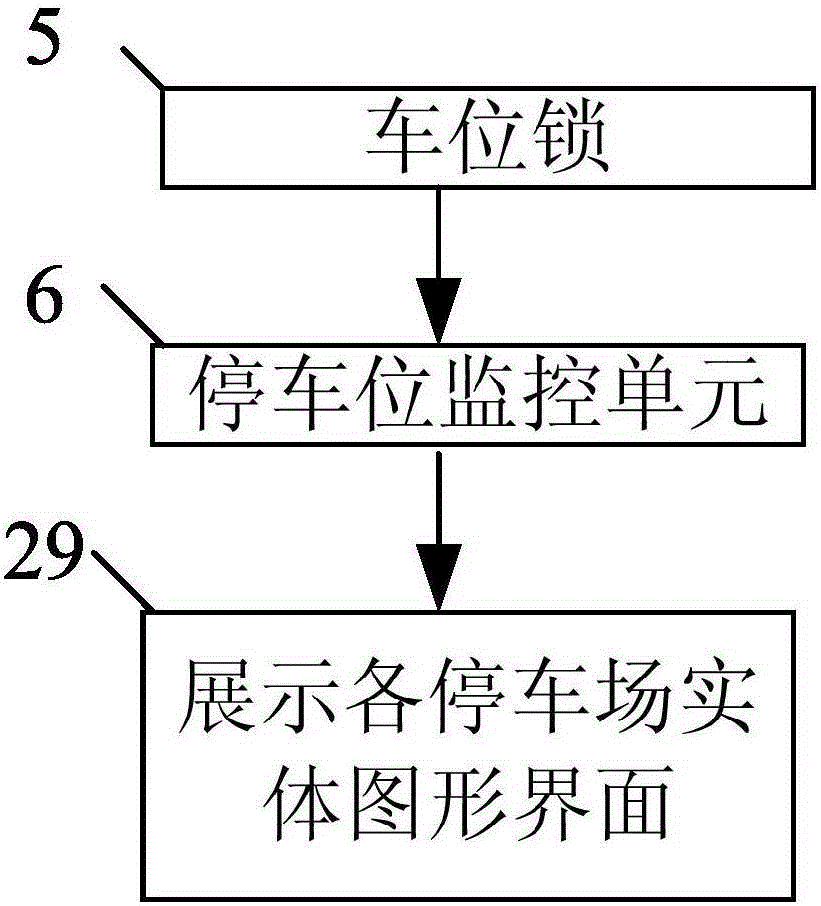
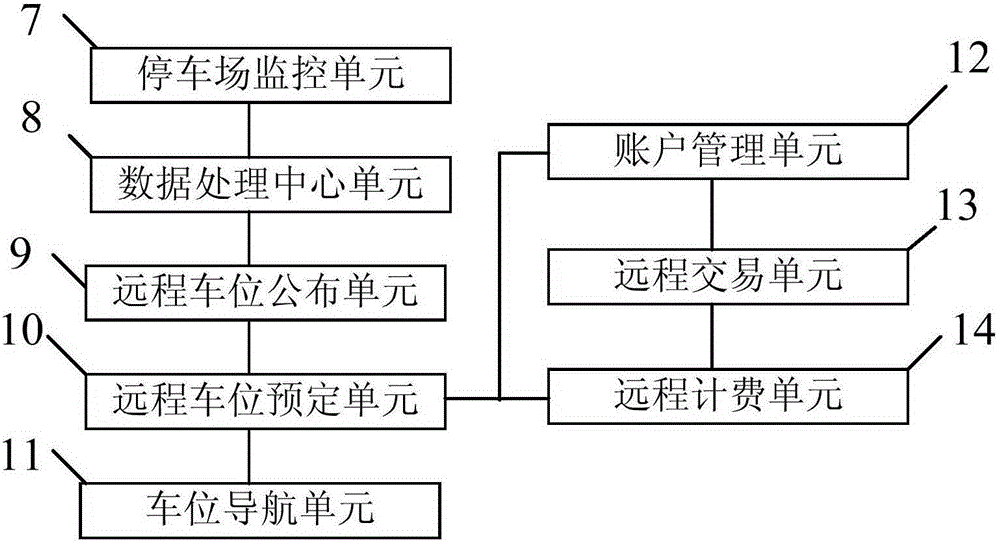
InactiveCN105225521AMeet just needsUniqueTicket-issuing apparatusIndication of parksing free spacesIdentity recognitionParking space
The invention discloses a parking management system and method based on the Internet of things. The system comprises a cloud platform, a graphical parking lot management platform, a first mobile terminal and a second mobile terminal; the graphical parking lot management platform comprises a parking lot entity graphical interface display module, parking stall locks and a parking stall monitoring assembly, the parking stall locks upload state information of parking stalls automatically, and the parking stall monitoring assembly issues parking stall information to the cloud platform; and the cloud platform manages parking stall information, transaction and users, and provides a navigation service. When an owner of a certain parking stall issues vacancy information of the parking stall via the first mobile terminal, a user reserves the parking stall via the second mobile terminal, the parking stall is locked by the unique user after reservation succeeds, when the user arrives at the parking lot and enters parking lot after identity recognition, the user is autonomously or automatically navigated to the preserved offline parking stall, and the system carries out electronic settlement automatically after use. Thus, the value of limit resources is maximized.
Owner:CHONGQING DINGCHECHE TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com