Method and system for enhancing network attack prevention capability of multiple network ports
A network attack and network port technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as poor real-time performance and no consideration of attack information, and achieve enhanced attack defense capabilities, based on FPGA network port defense. The effect of powerful network attack capability and complete network attack capability based on FPGA network port
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
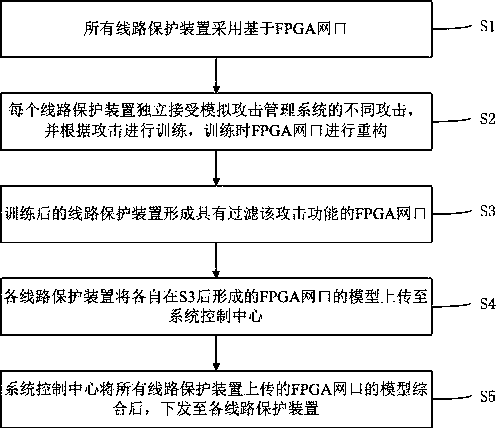
[0041] This embodiment provides a method for enhancing the ability of multi-network ports to prevent network attacks, such as figure 1 , including the following steps:
[0042] S1: All line protection devices are based on FPGA network ports;
[0043] S2: Each line protection device independently accepts different attacks from the simulated attack management system, and conducts training according to the attack, and the FPGA network port is reconfigured during training;
[0044] S3: The trained line protection device forms an FPGA network port with the function of filtering the attack;
[0045] S4: Each line protection device uploads the model of the FPGA network port formed after S3 to the system control center;
[0046] S5: The system control center synthesizes the models of FPGA network ports uploaded by all line protection devices, and sends them to each line protection device.
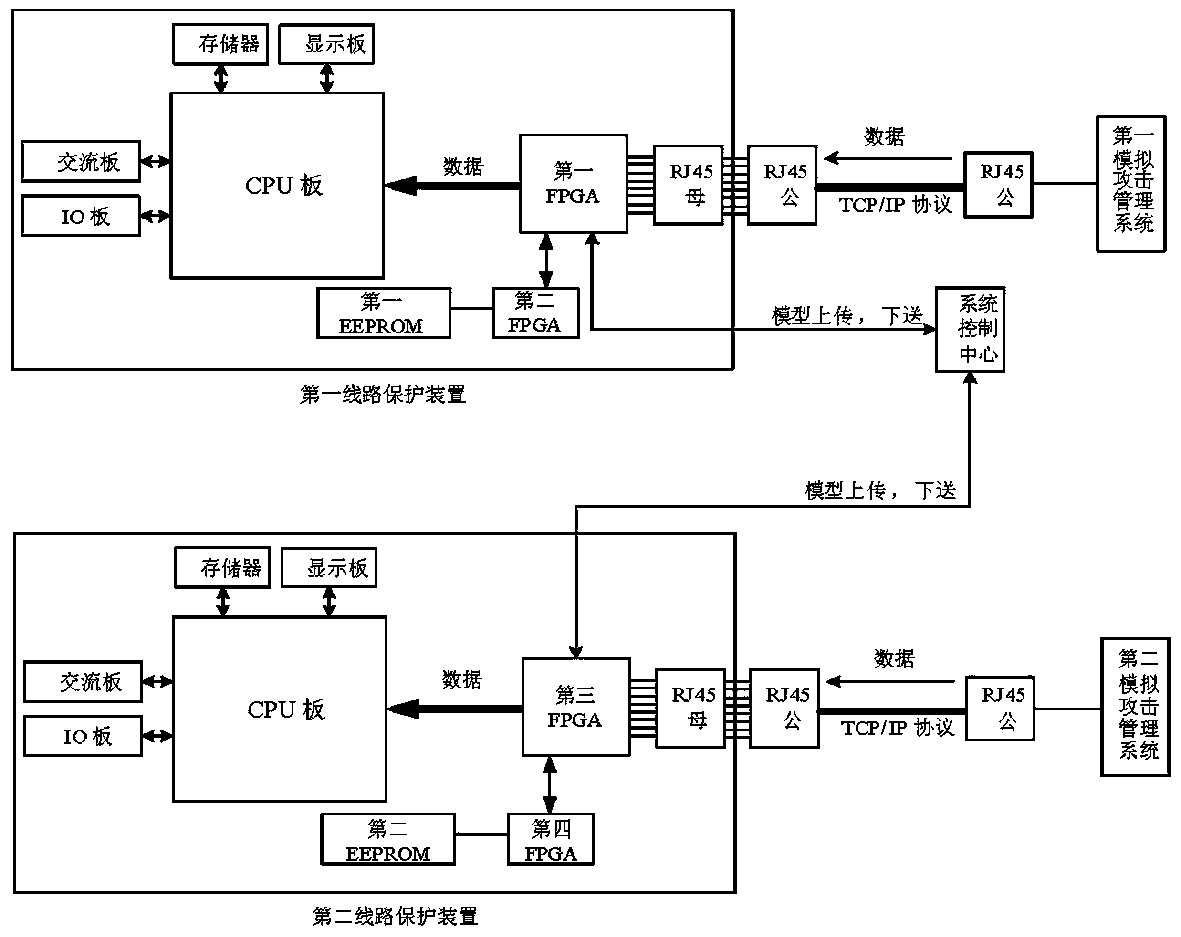
[0047] The network port is an FPGA Ethernet interface, which is used to transmit data and fi...
Embodiment 2
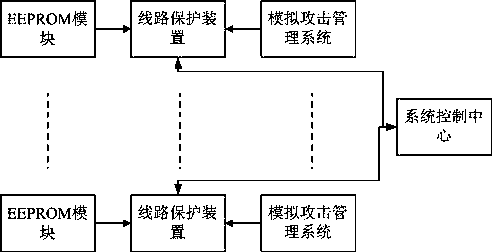
[0058] This embodiment provides a system for enhancing the ability of multi-network ports to prevent network attacks, and the system applies the method for enhancing the ability of multi-network ports to prevent network attacks described in Embodiment 1, such as figure 2 ,include:
[0059] Several line protection devices, the line protection devices use FPGA network ports;
[0060] Several simulated attack management systems, the simulated attack management systems carry out different attacks on the line protection device respectively;
[0061] A system control center, the system control center receives the models uploaded by all line protection devices, and sends them to all line protection devices after synthesis.
[0062] Preferably, several EEPROM modules are also included, each of the line protection devices has a built-in EEPROM module, and each of the EEPROM modules pre-stores attack types corresponding to power consumption characteristics of the line protection devic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com