Chip anti-power consumption attack circuit and method for preventing power consumption attack
A power consumption attack, chip technology, applied in the direction of internal/peripheral computer component protection, etc., can solve the problems of increasing clock disturbance, reducing the signal-to-noise ratio of useful information, increasing the redundancy of power consumption information, etc., to improve security and prevent Being attacked and improving the effect of attack defense ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
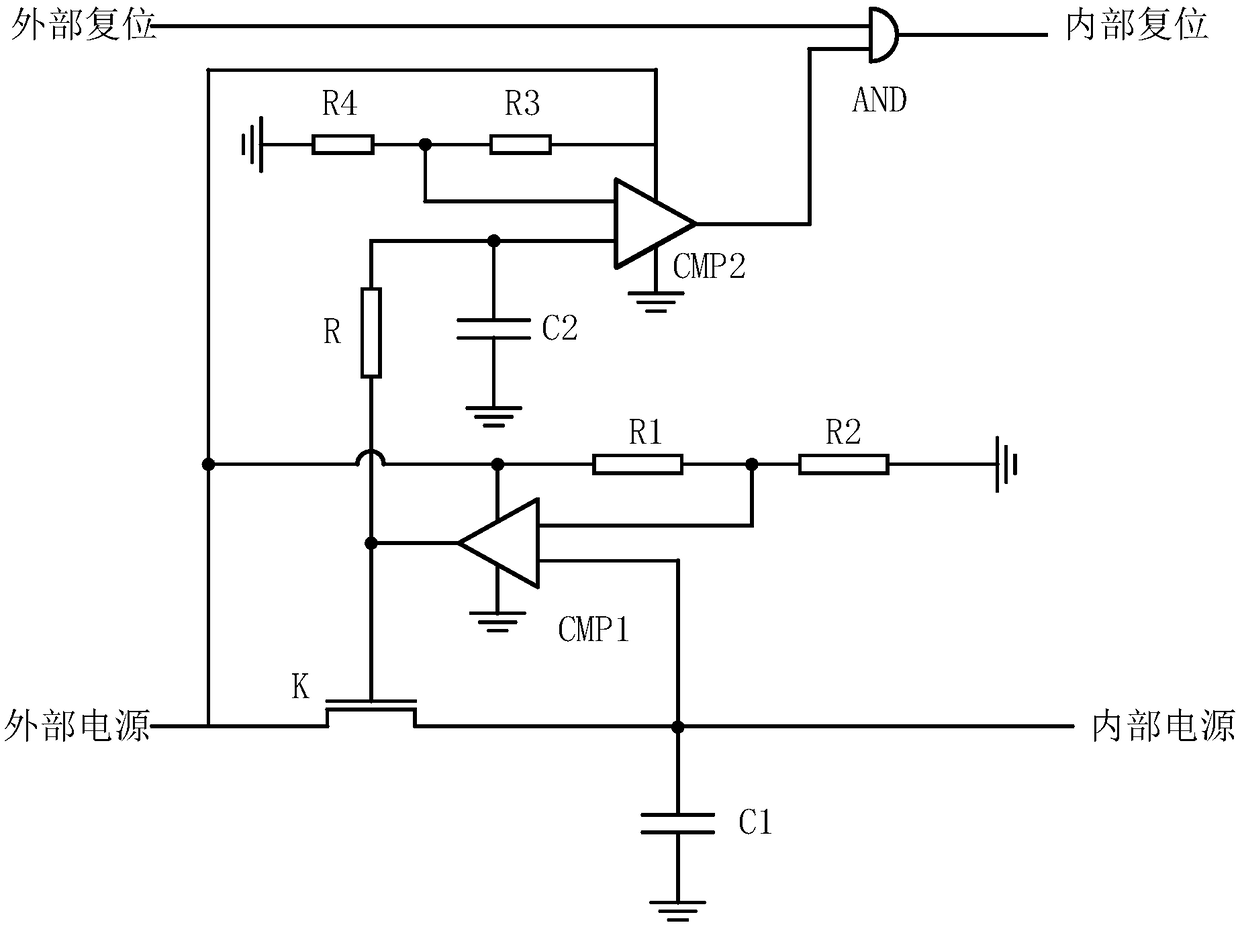
[0022] Such as figure 1 As shown, a chip anti-power attack circuit includes an NMOS switch K, a charging capacitor C1, a filter resistor R, four voltage divider resistors, a filter capacitor C2, a charging voltage comparator CMP1, a switch voltage comparator Device CMP2, a two-input AND gate AND.
[0023] The source end of the NMOS switch K, the power end of the charging voltage comparator CMP1, the power end of the switching voltage comparator CMP2 are connected to the external power supply of the chip, the gate end of the NMOS switch K, the output end of the charging voltage comparator CMP1 and the filter resistor R One end is connected, the drain end of the NMOS switch K, the positive pole of the charging capacitor C1 and the comparison input terminal of the charging voltage comparator CMP1 are connected to the internal power supply of the chip, and the negative pole of the charging capacitor C1 is grounded; one end of the first voltage dividing resistor R1 and the second d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com