A way to achieve big data security
A technology of big data and big data platform, which is applied in data security transmission and big data field, can solve the problems of no big data system security system, inability to protect sensitive information and sensitive data of big data platform, and improve the security of big data , Improve the effect of the ability to defend against attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
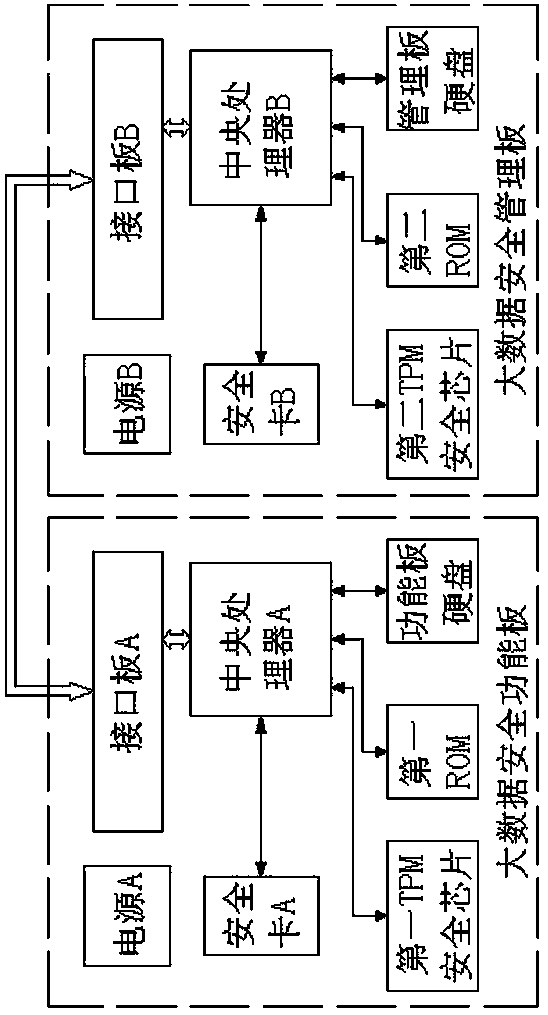
[0064] A method for realizing big data security in a system that realizes big data security, upgrades the original mode of using software and network topology architecture for big data security protection to directly adopts hardware protection, and upgrades the protection level from the original software protection level to hardware The level of protection greatly improves the anti-attack capability of the big data platform, which can effectively improve the security of big data, including the following steps:
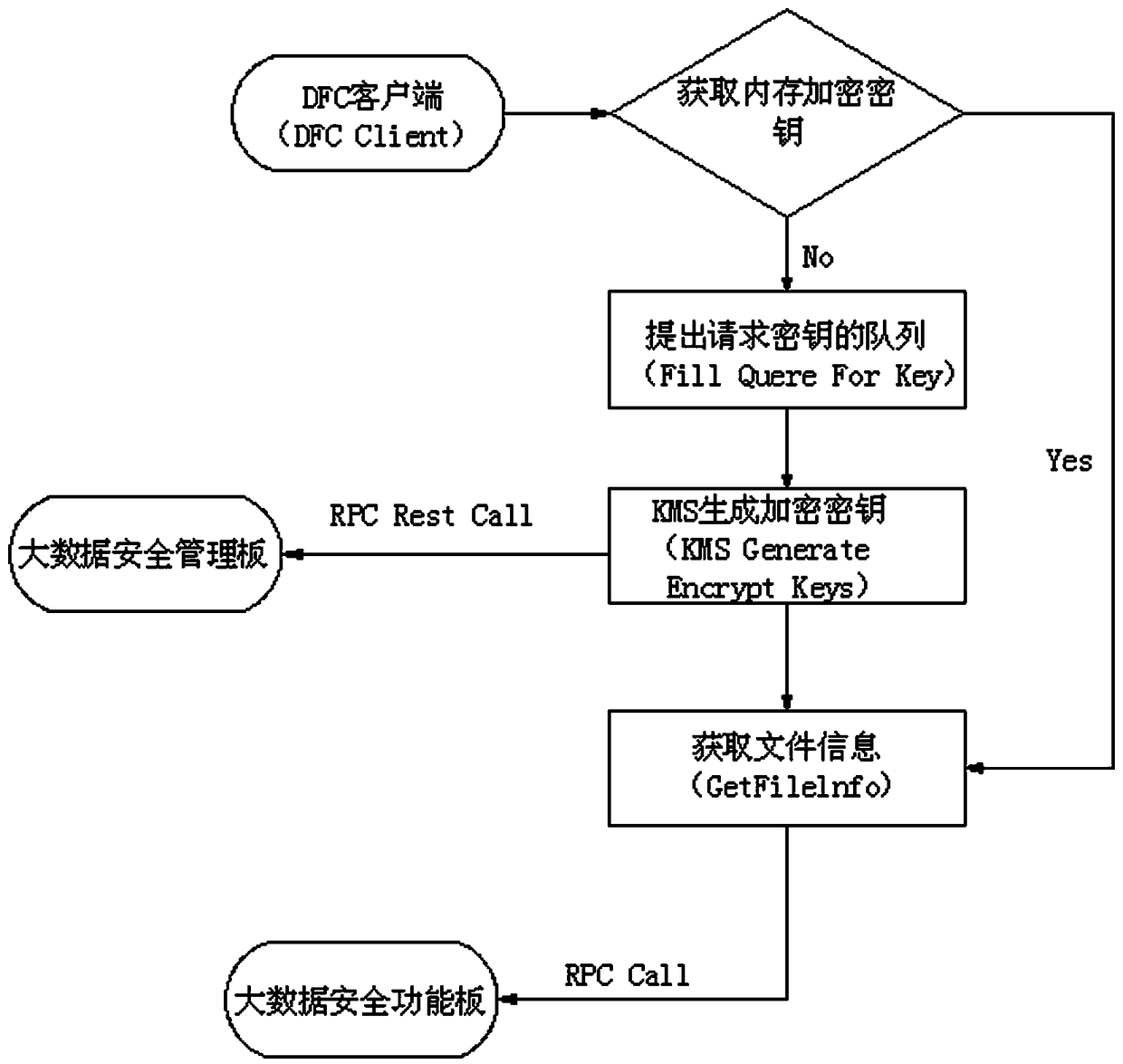
[0065] 1) After receiving a piece of data, the DFS client will access the local cache to see if there is a data encryption key for the data;
[0066] 2) After step 1), if the data has a data encryption key, then perform step 4); if the data does not have a data encryption key, then perform step 3);
[0067] 3) After step 1), if the data does not have a data encryption key, then perform the following steps:
[0068] 3-1) A key request will be formed and the key request...
Embodiment 2
[0074] This embodiment is further optimized on the basis of the above-mentioned embodiments, and further for better realizing the method of the present invention, the following setting mode is adopted in particular: the specific steps of the described step 3-2) are:
[0075] 3-2-1) The KMS server requests the production data encryption key from the big data security management board through the REST API interface of the interface board B;
[0076] 3-2-2) The REST API interface initiates a request for the production data encryption key to the second TPM security chip;
Embodiment 3
[0078] This embodiment is further optimized on the basis of any of the above-mentioned embodiments. Further, in order to better realize the method of the present invention, the specific steps of the step 3-3) are:
[0079] 3-3-1) The second TPM security chip generates a data encryption key and returns it to the DFS client;
[0080] 3-3-2) The DFS client caches the data encryption key obtained in step 3-3-1) in the local cache.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com