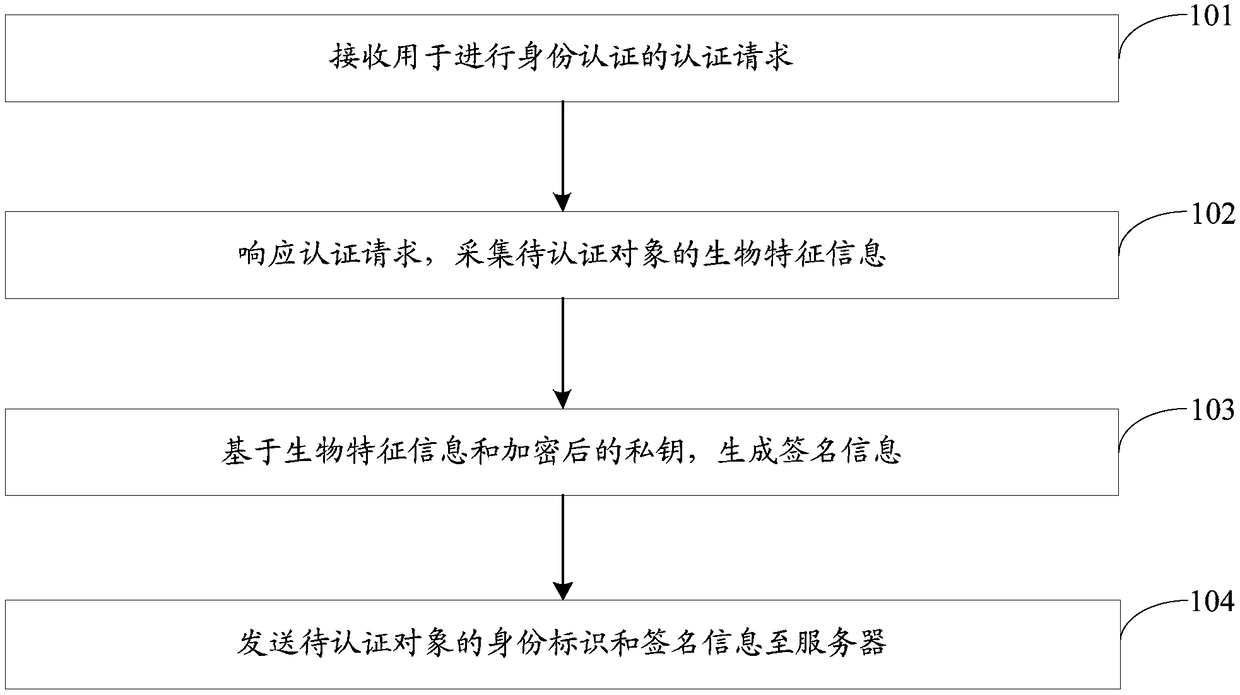
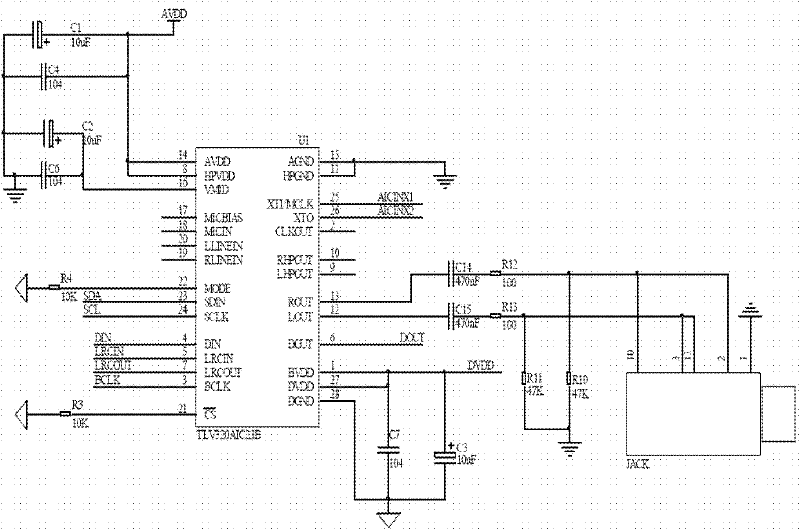
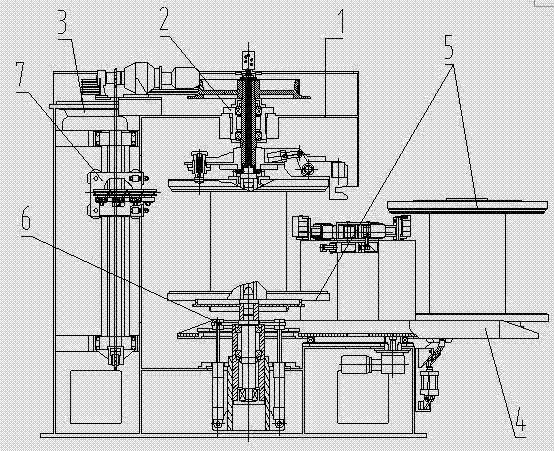
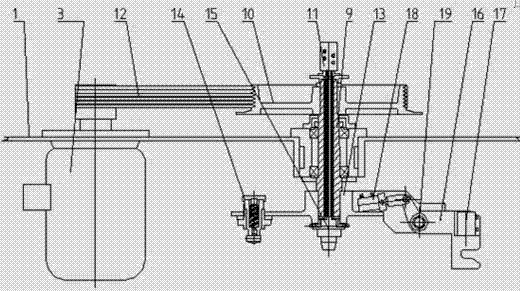
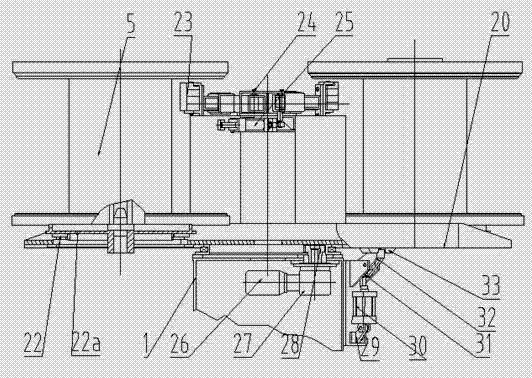
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
911results about How to "Security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
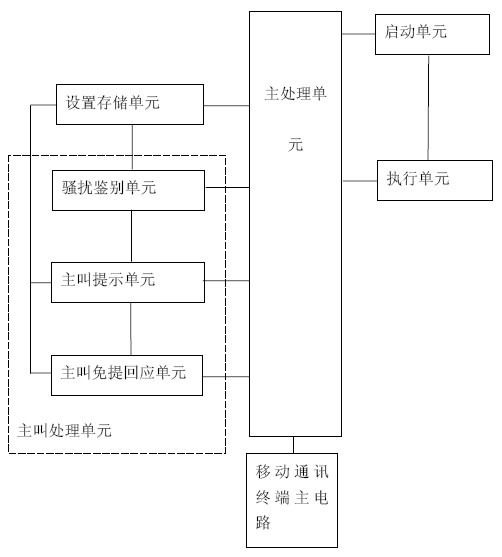
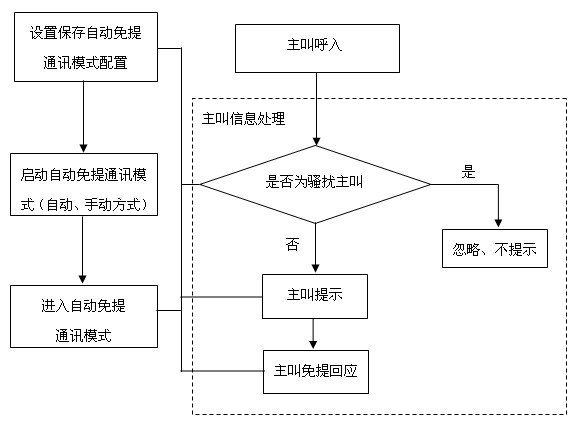
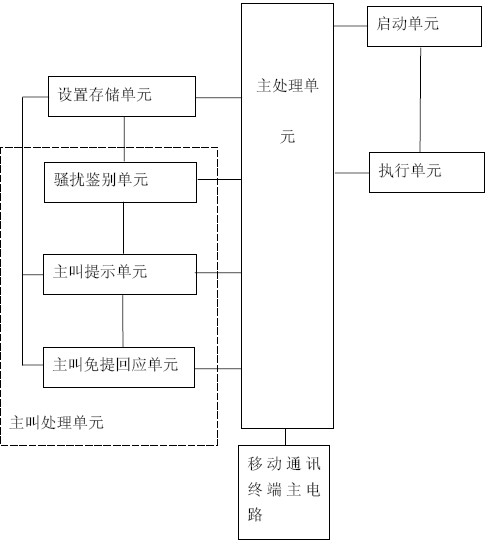
Mobile communication terminal and communication control method thereof
InactiveCN102137193ASecurityAvoid harassing caller interferenceSubstation speech amplifiersHands freeCommunication control
The invention discloses a mobile communication terminal and a communication control method thereof. The mobile communication terminal comprises a mobile communication terminal main circuit, a main processing unit, a start unit and an execution unit, wherein the main processing unit is connected with the mobile communication terminal main circuit; the start unit is used for starting and stopping an automatic hands-free communication mode; and the execution unit is connected with the start unit and is used for controlling the main processing unit to enter or exit the automatic hands-free communication mode according to a start and stop instruction of the start unit. The communication control method is the control method for the terminal. The terminal and the method have the advantage that: automatic hands-free communication can be convenient to realize without manual operation under the condition that some special circumstances are met (particularly in the driving of vehicles).
Owner:KAIHONG MOBILE COMM
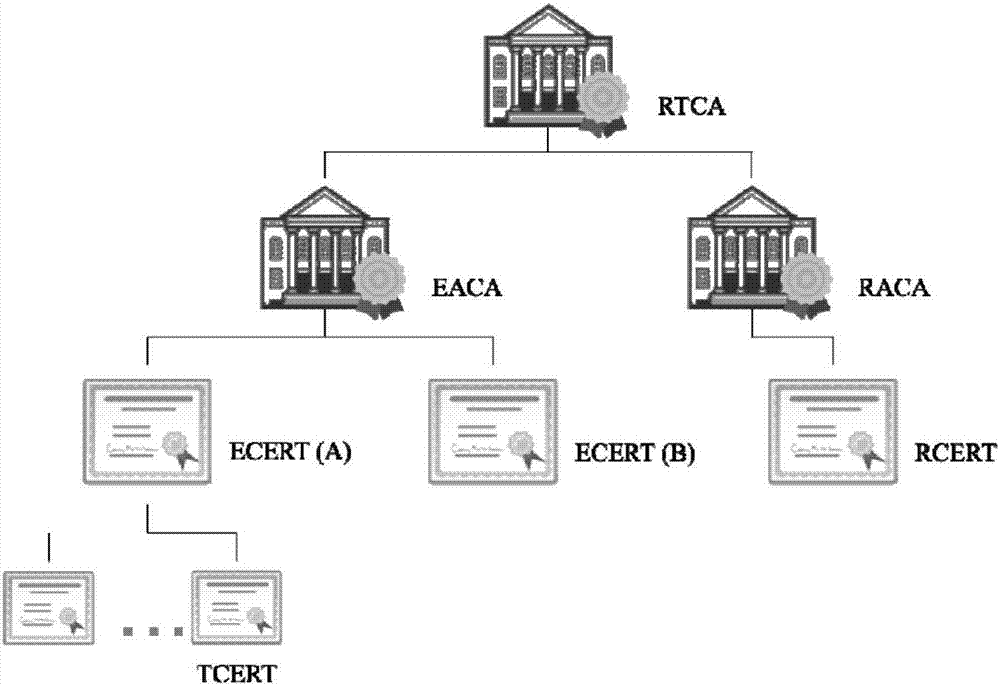
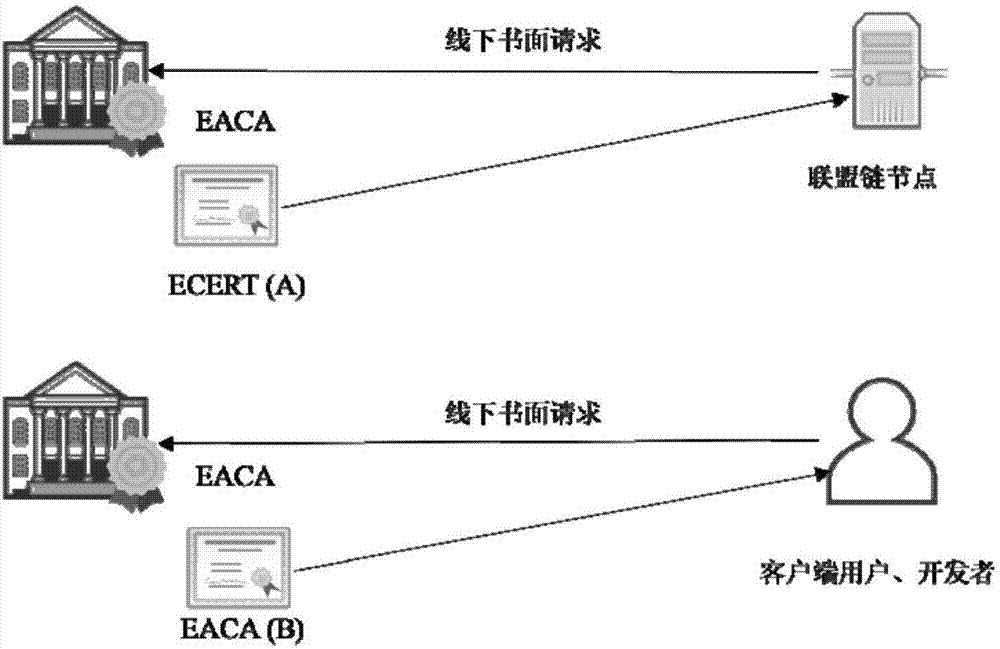
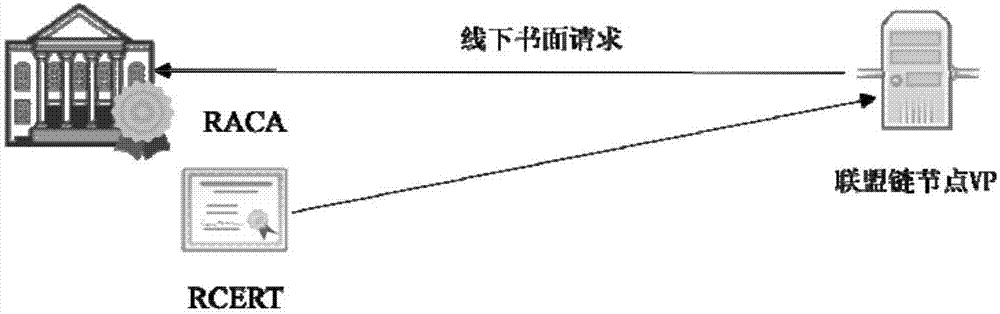
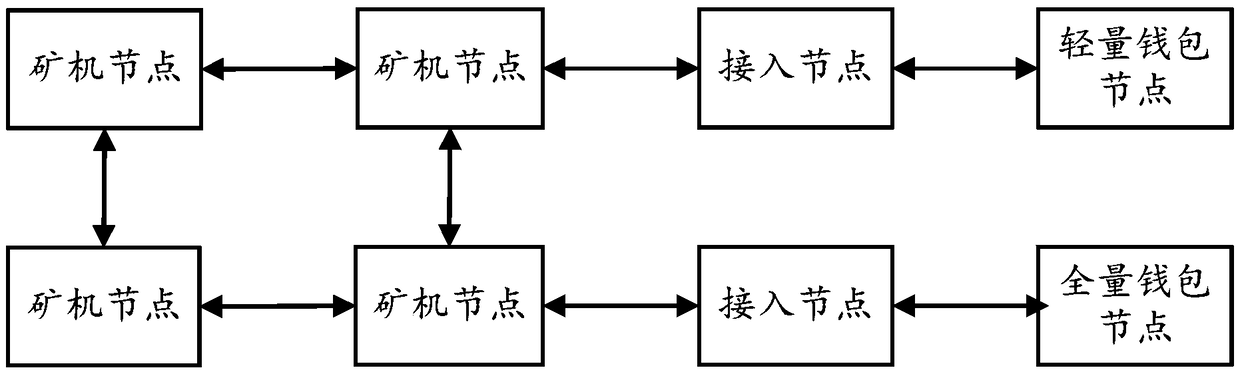
Consortium chain permission control method based on digital certificates and CA authentication system
ActiveCN107426157AProcess controlSecurityUser identity/authority verificationGranularityDigital Signature Algorithm
The invention discloses a consortium chain permission control method based on digital certificates and a CA authentication system. In a consortium chain, the enrollment control and automatic authorization of the consortium chain are realized through a layered digital certificate issuance system. The method of the invention pre-defines three kinds of permission mechanisms for respectively controlling enrollment permissions between consortium chain nodes, role permissions of the consortium chain nodes and access permissions of blockchain users. Three kinds of digital certificates including the enrollment certificate, role certificate and transaction certificate are used for respectively controlling the three permissions of node enrollment, role identification and client enrollment. An internationally accepted elliptic curve digital signature algorithm or a national crypto digital signature algorithm is used for achieving the generation of the digital certificates and secure message signature and validation, the defects of being large in permission granularity of a traditional blockchain or even having no enrollment functions and the like are overcome, the blockchain users are provided with anonymous transaction features, the security of blockchain transactions is improved, and the privacy needs of the users are met.
Owner:HANGZHOU QULIAN TECH CO LTD
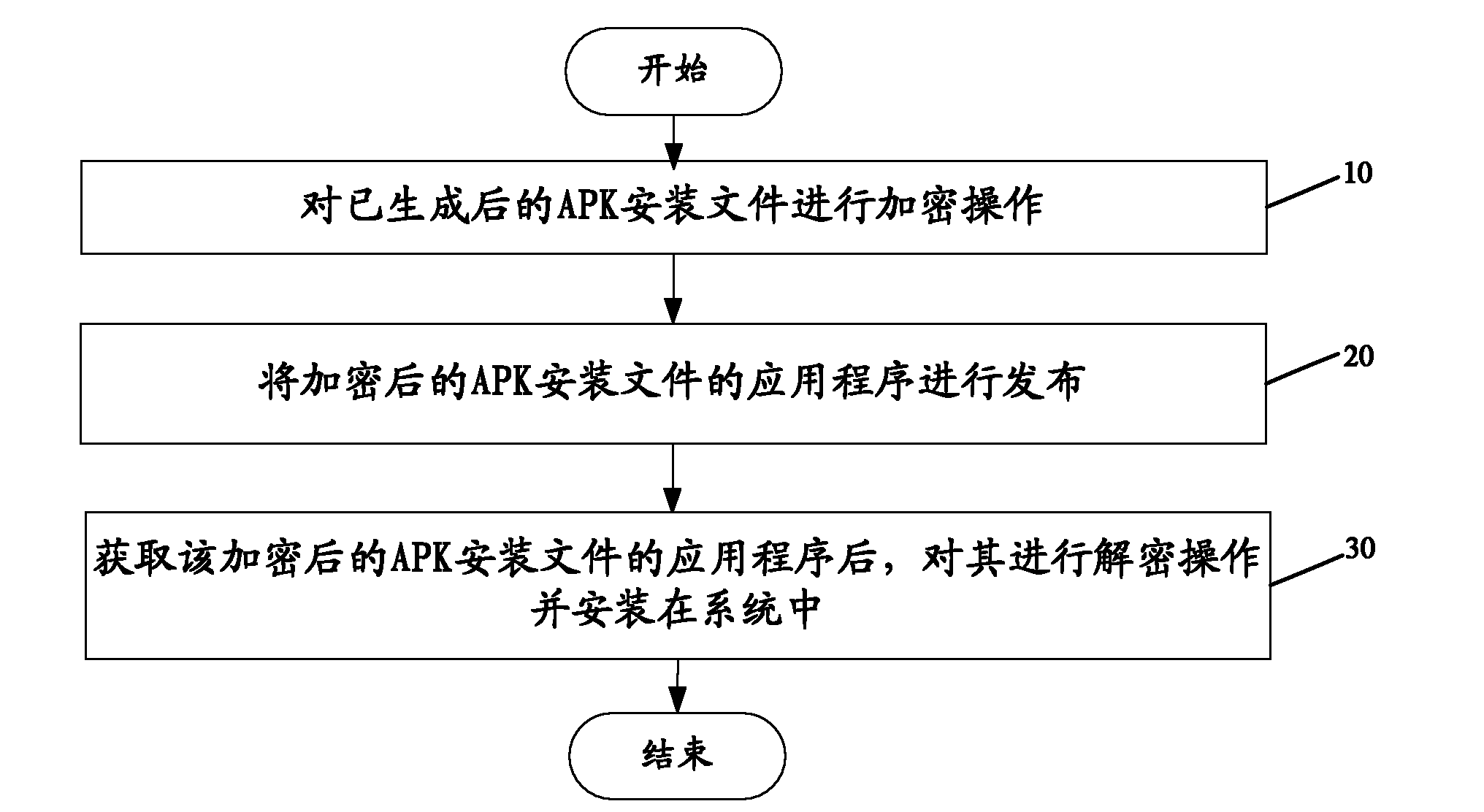
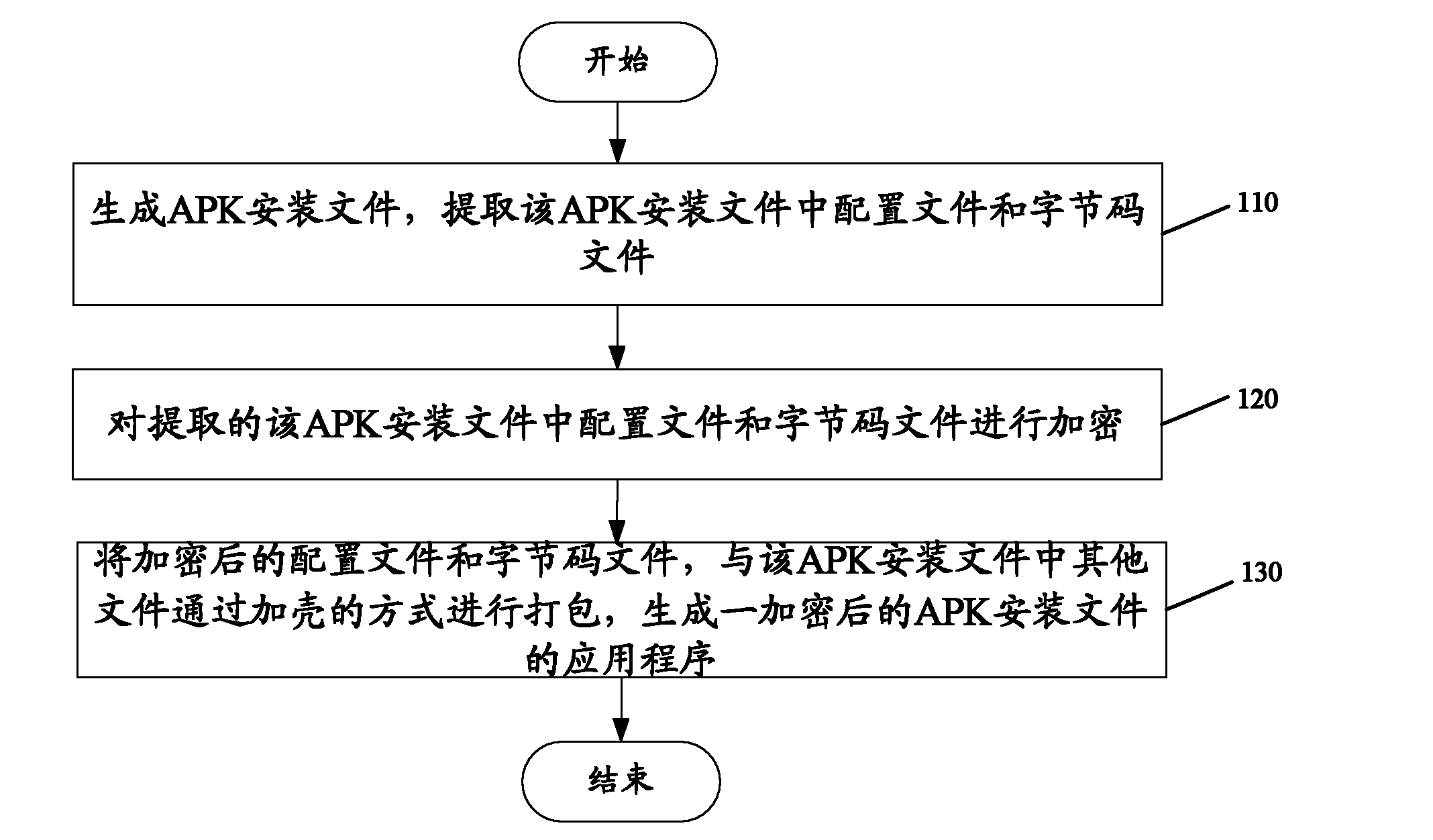
Android-based platform application installation control method and system
InactiveCN102087605APrevent tamperingSecurityComputer security arrangementsProgram loading/initiatingApplication softwareEncryption
The invention discloses an android-based platform application installation control method and an android-based platform application installation control system. The method comprises the following steps of: encrypting a generated android application package (APK) installation file; issuing the application program of the encrypted APK installation file; and decrypting the application program of the encrypted APK installation file, and installing the application program in the system. The APK installation file is encrypted by internal encryption and external encryption and simultaneously installed by using the corresponding decryption installation, so that a user cannot acquire a complete APK installation file packet, the falsification danger of the APK installation file is avoided, and the security of using a mobile terminal by the user is guaranteed.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Wireless fidelity (WiFi) authentication method and system, and terminal
InactiveCN102883315ASecurityEnsure safetyNetwork topologiesTransmissionAuthentication systemE communication
The invention discloses a wireless fidelity (WiFi) authentication method, a WiFi authentication system and a terminal. The method comprises the following steps of: storing wireless access point (AP) information in predetermined hotspot information storing equipment in advance; and reading the AP information in the hotspot information storing equipment through a near field communication (NFC) function by the terminal, and performing WiFi authentication according to the AP information. The system comprises the hotspot information storing equipment, the terminal, a wireless AP information processing module and an authentication module. According to the method, the system and the terminal, the AP information can be acquired by the terminal through the NFC function, and safety of a WiFi hotspot can be effectively ensured.
Owner:ZTE CORP
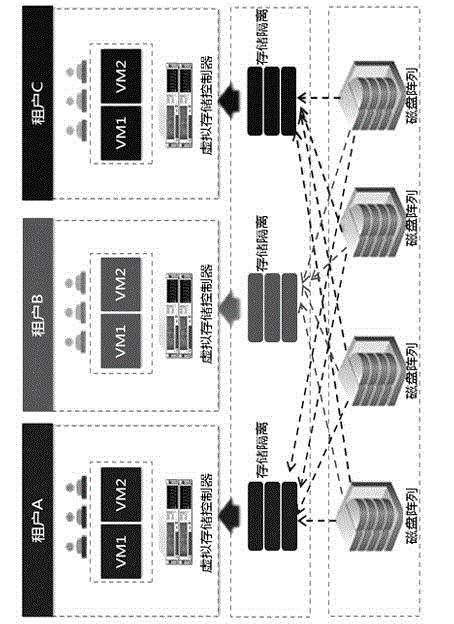
Safety isolation method for cloud side multi-tenant data storage
InactiveCN104104513ASecurityEnsure safetyUser identity/authority verificationCloud service providerCloud computing
The invention provides a safety isolation method for cloud side multi-tenant data storage. According to the safety isolation method for cloud side multi-tenant data storage, isolated distributed storage is applied to multi-tenant data storage, when a tenant applies for a data storage space, storage software API provided by an operator is called, a specific virtual storage area is provided for the tenant through division according to the ID of the tenant, the storage area of each tenant is relatively independent and isolated, and when a tenant uses private data, the distributive storage software collects tenant data from a private space in a disk array on the physical layer according to the ID of the user and provides a data service for the tenant in a concentrated mode; for each tenant, the data isolated distributed storage process is automatically completed by a system, transparent encryption and decryption is conducted on the volume levels, of cloud side multi-tenant data, in the storage disk array on the physical layer, safety isolation of the multi-tenant data in the cloud computing environment is achieved, and the problem that a cloud service provider administrator views, tampers and deletes sensitive data of the tenants without authorization is solved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
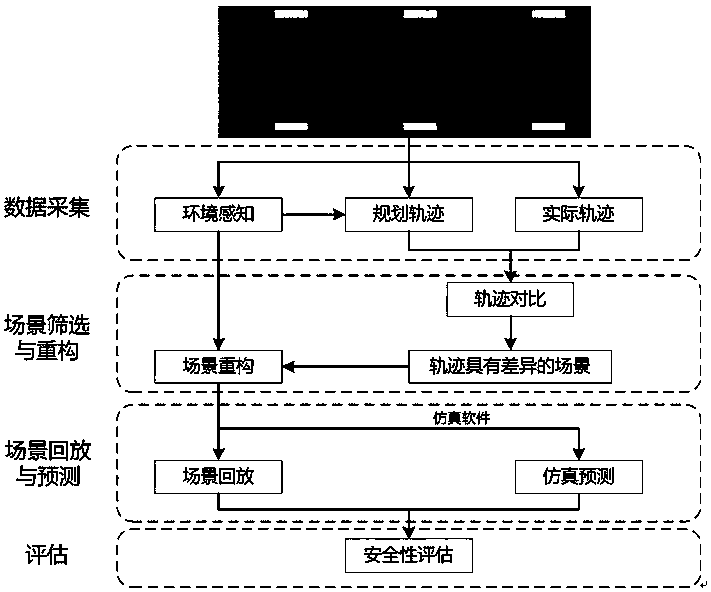
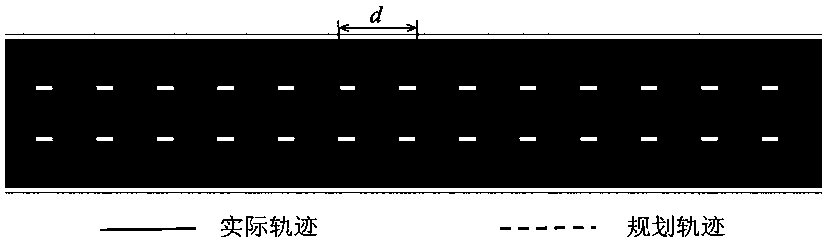
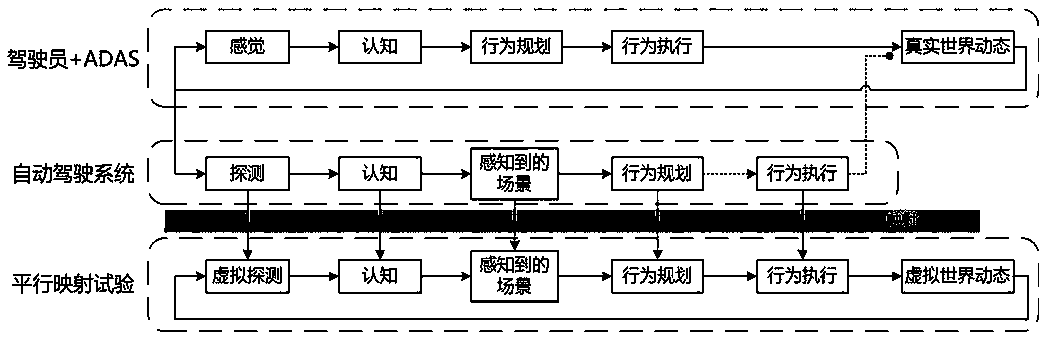
Road running and virtual test parallel mapping experiment method of intelligent automobiles
ActiveCN108549366AImprove test efficiencySecurityProgramme controlVehicle testingVirtual testTest efficiency
The invention relates to a road running and virtual test parallel mapping experiment method of intelligent automobiles. The objectives of the invention are to improve efficiency and safety of intelligent automobile test. The method comprises steps of firstly acquiring track data of an automobile driven by a driver, interception data of an automatic driving system and planed track data (wherein theintelligent automobile fails to execute the planed track at this moment); then comparing an actual track and the planned track, and searching whether there is a remarkably different scene between thetwo tracks; and then, through the interception information of the intelligent automobile, reconstructing the scene, carrying scene replaying and simulating prediction, calculating safety of the two tracks and evaluating the safety of the tracks. According to the invention, there is no need to use an automatic driving system to control the automobile; and as long as the intelligent automobile runson a road (i.e., a driver is operating the automobile), the test and the experiment can be carried out. Thus, test efficiency can be improved and safety of the test can be ensured.
Owner:TONGJI UNIV
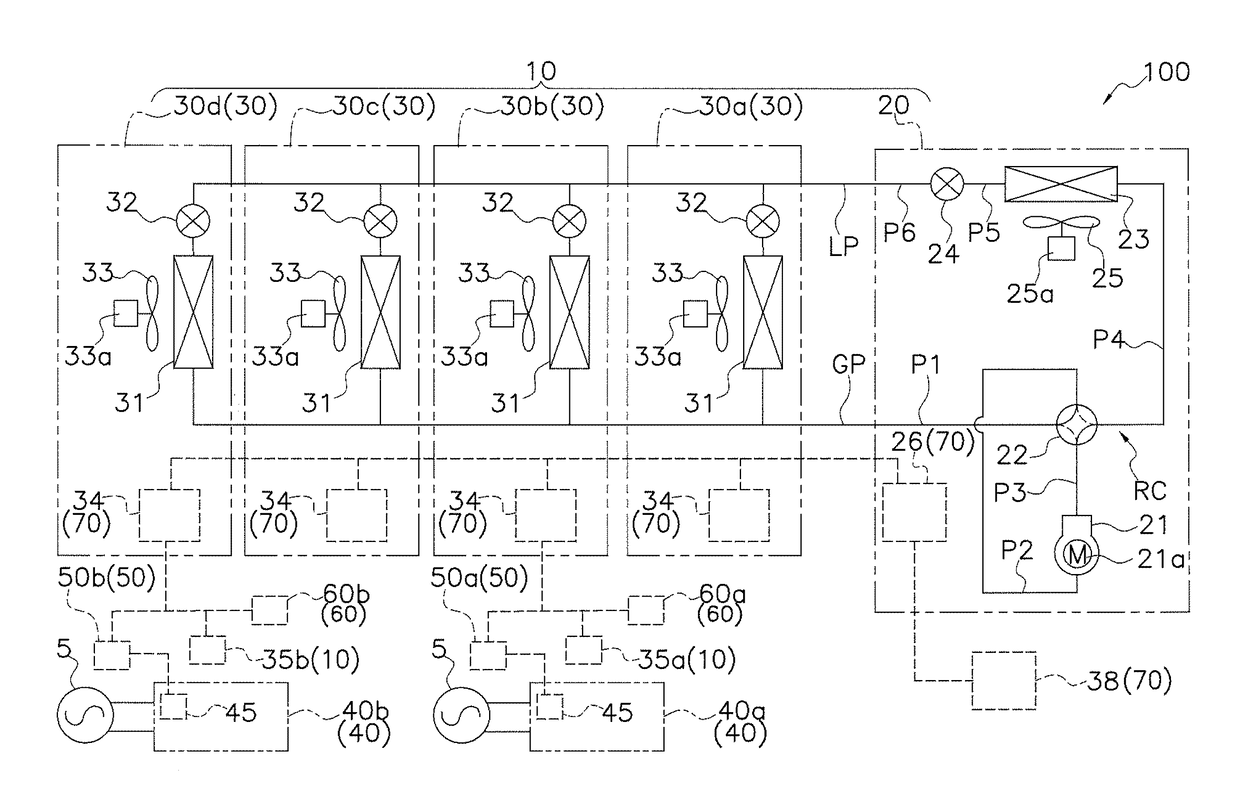
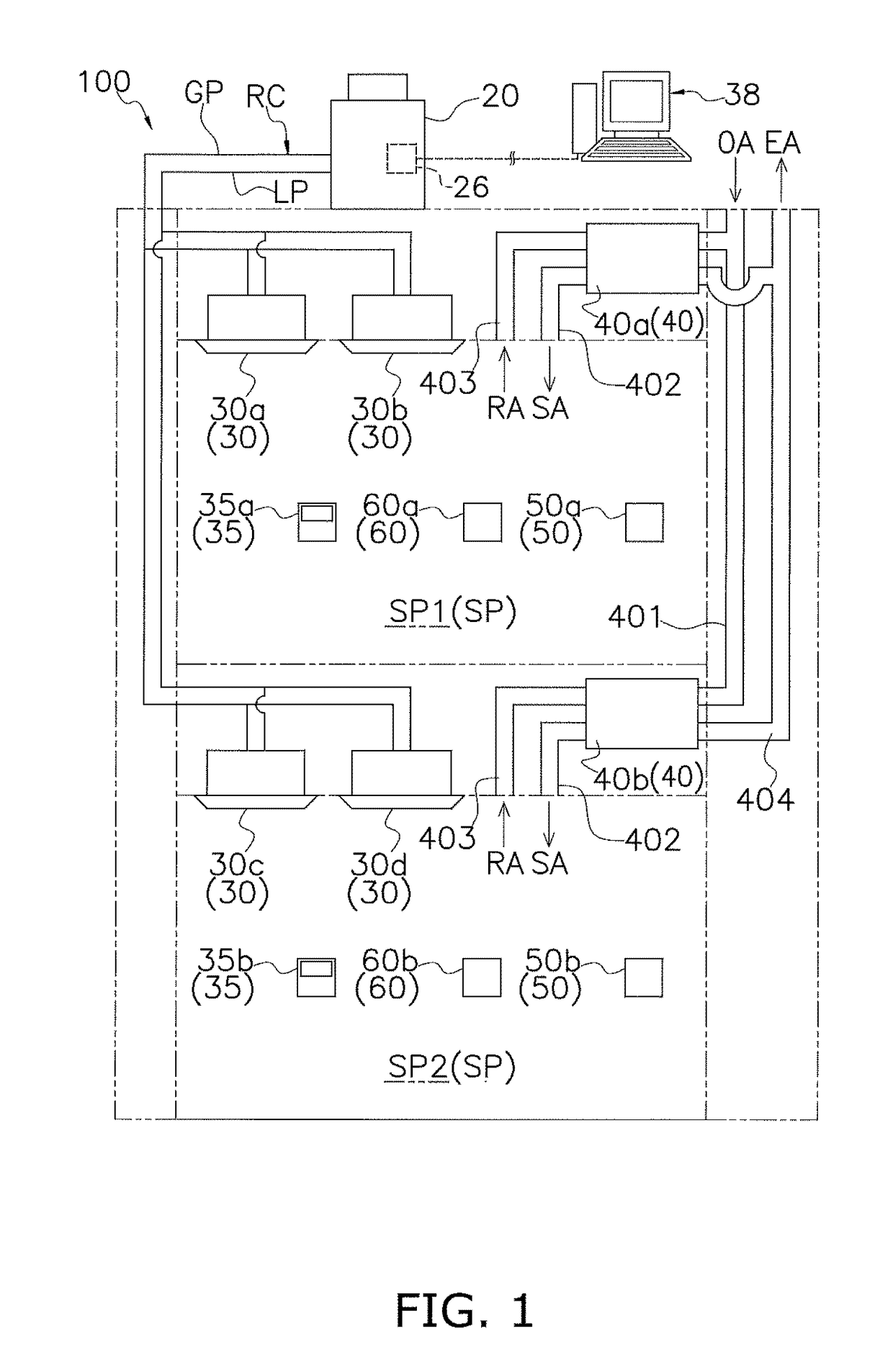
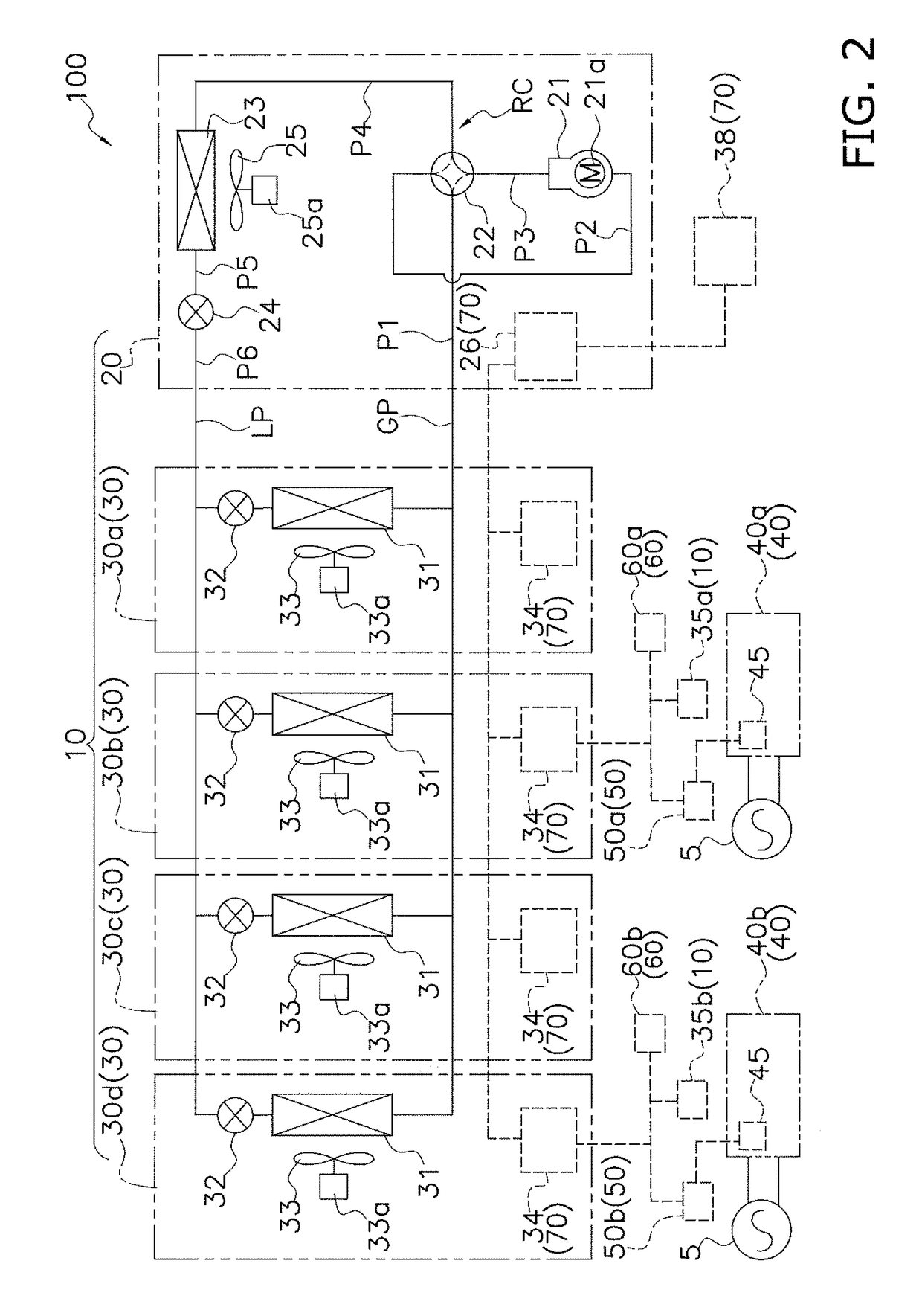
Air conditioning system
ActiveUS20180045424A1Cost containmentSecurityMechanical apparatusSpace heating and ventilation safety systemsCountermeasureEngineering
An air conditioning system has an air conditioner, which includes an outdoor unit and an indoor unit that configure a refrigerant circuit, and a controller, which controls the running of the air conditioner. The controller does not allow operation of the air conditioner to start in a case where a signal from a ventilation unit that includes a ventilation fan for ventilation and ventilates a target space or a refrigerant leak sensor that detects refrigerant leakage in the target space is not input to the controller. Because of this, even in a configuration where an air conditioner and a ventilation unit are installed independently of each other, operation of the air conditioner can be performed in a state in which there is reliably established a countermeasure such as the ventilation unit being operated when the refrigerant has leaked, and safety and security with respect to refrigerant leakage are reliably ensured.
Owner:DAIKIN IND LTD
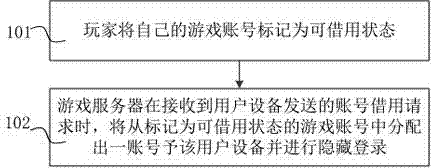
Method and system for temporarily sharing game account
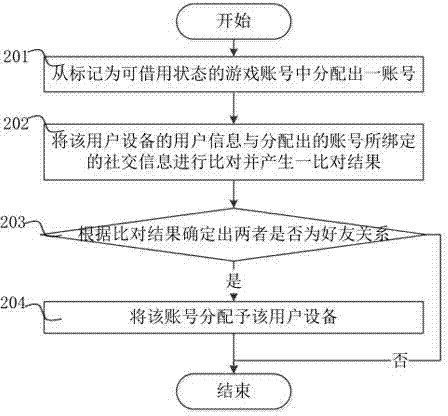
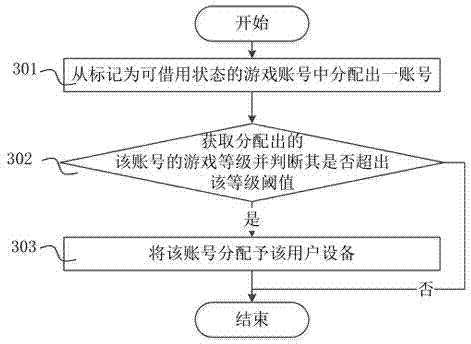
The invention relates to a method and system for temporarily sharing a game account. The method comprises that a player marks the game account of the player with a borrowable state; and a game server allocates an account from the game account marked with the borrowable state to the user equipment and performs concealed registration when receiving an account borrowing request transmitted from user equipment. The method and the system solve a complex problem due to a fact that a user is required to register an account when playing a game and enables an idle game account to be signed in so as to achieve an effect of playing the game in a substituting manner and guarantee the safety of the account.
Owner:重庆六花网络科技有限公司
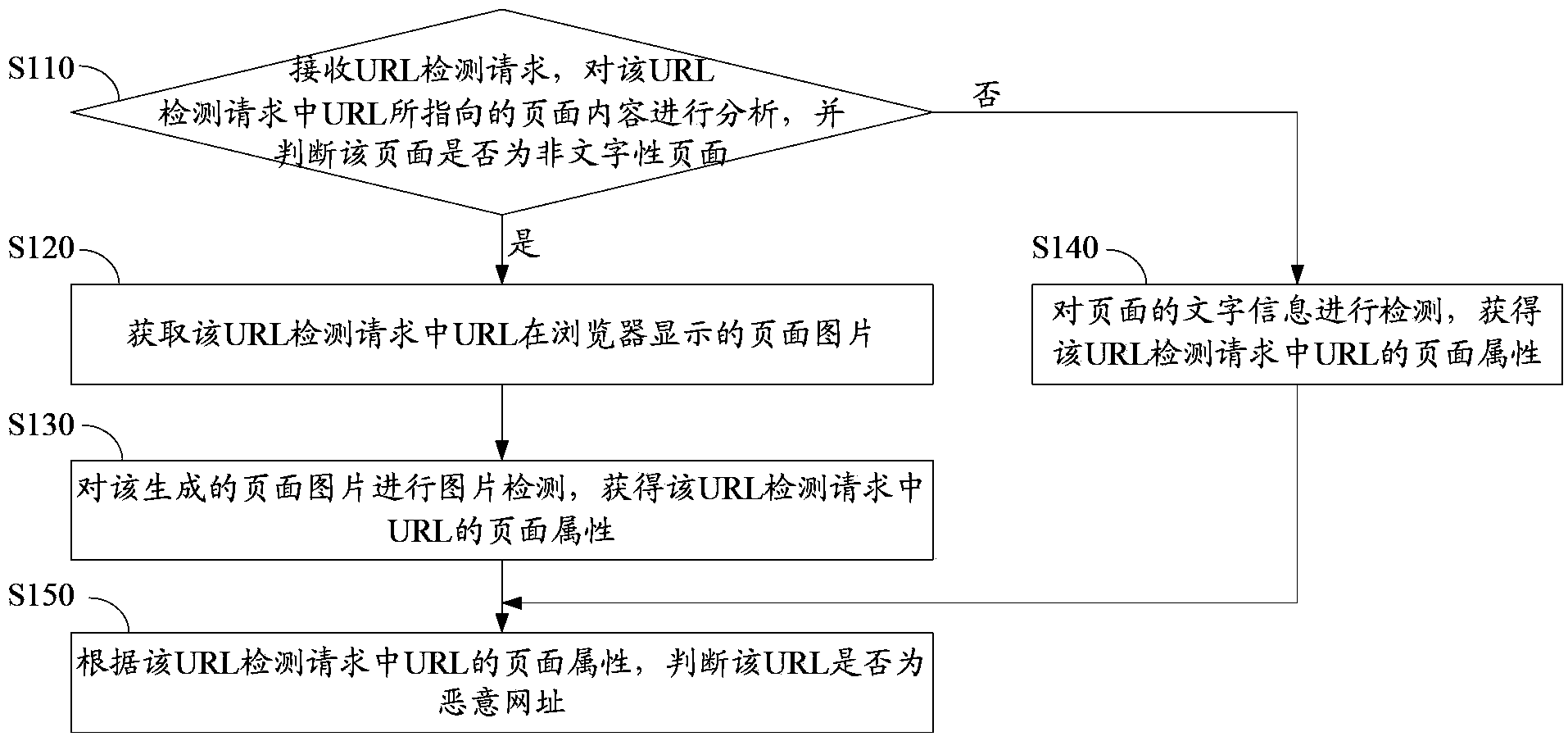
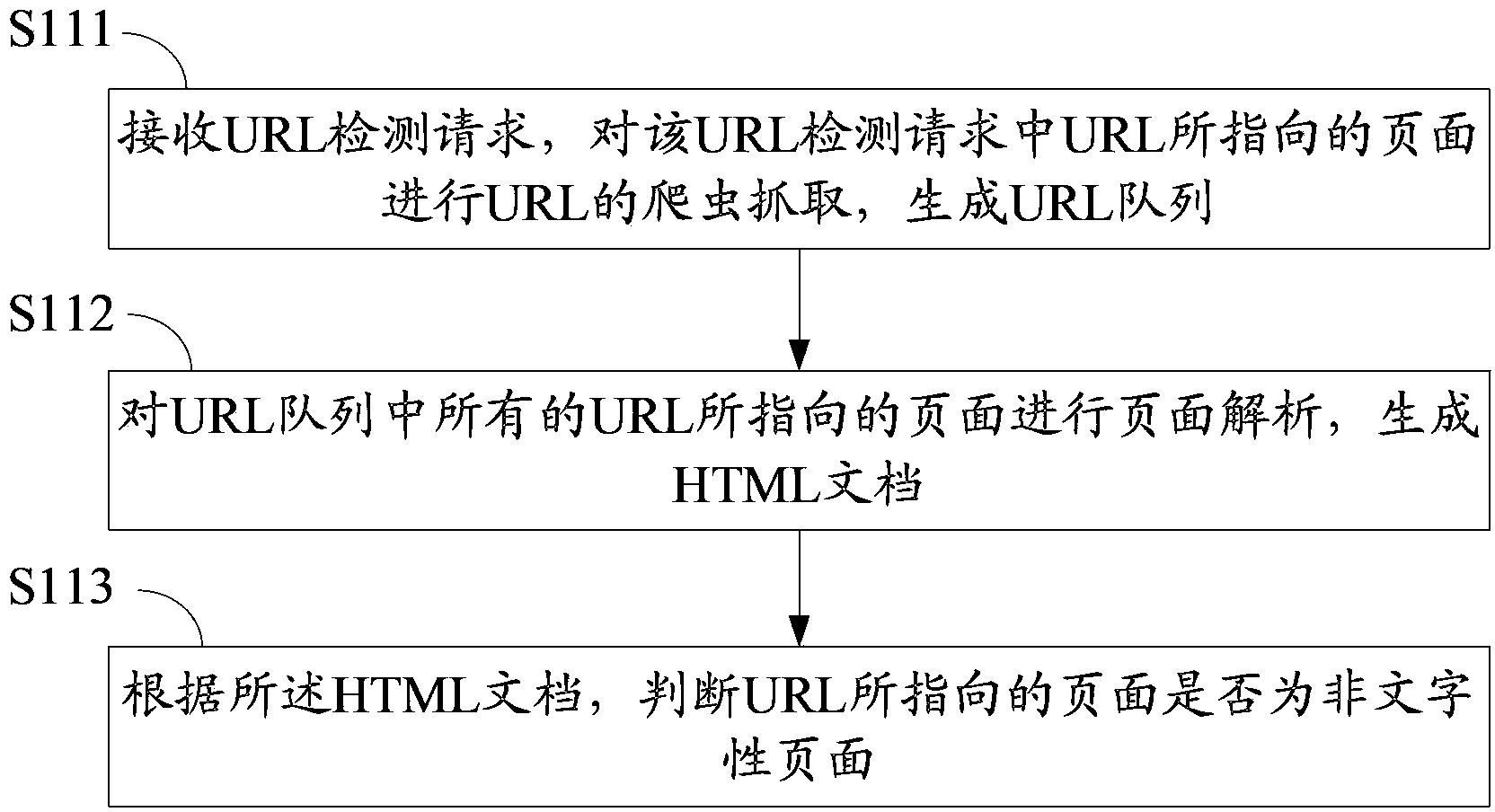
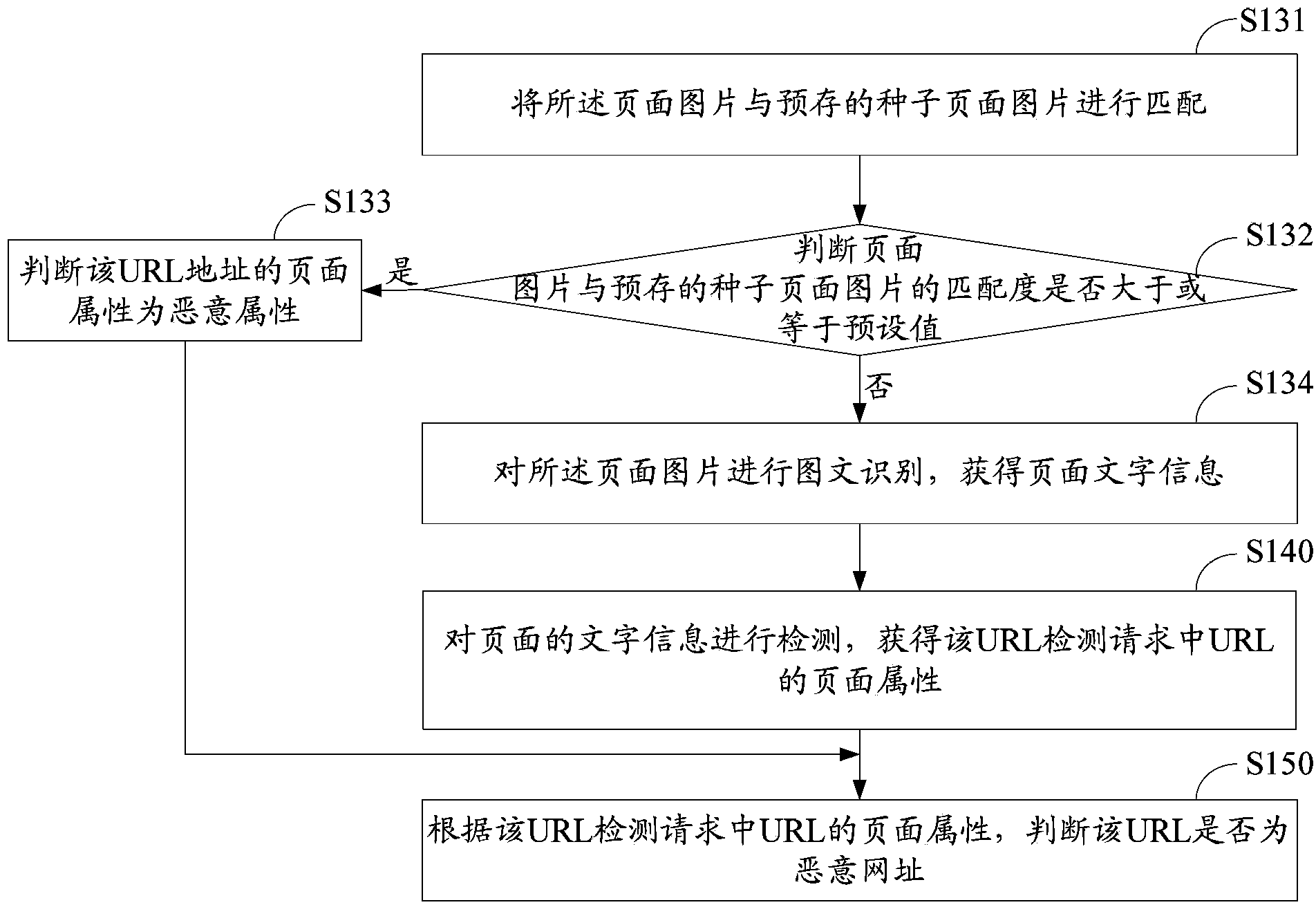
Method and device for detecting malicious website
ActiveCN103810425ASecurityGet page propertiesPlatform integrity maintainanceTransmissionInternet privacyWeb page
Owner:TENCENT TECH (SHENZHEN) CO LTD
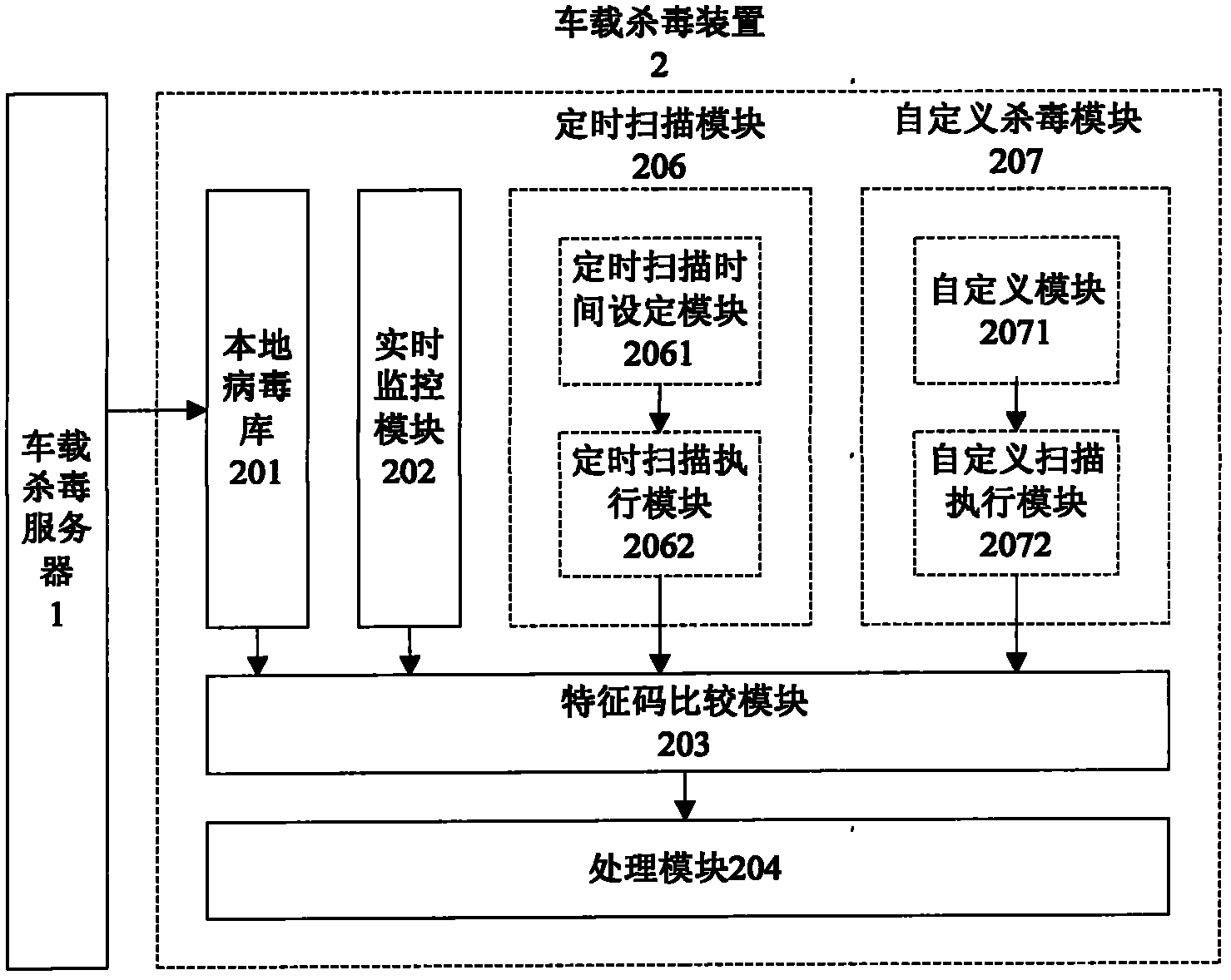
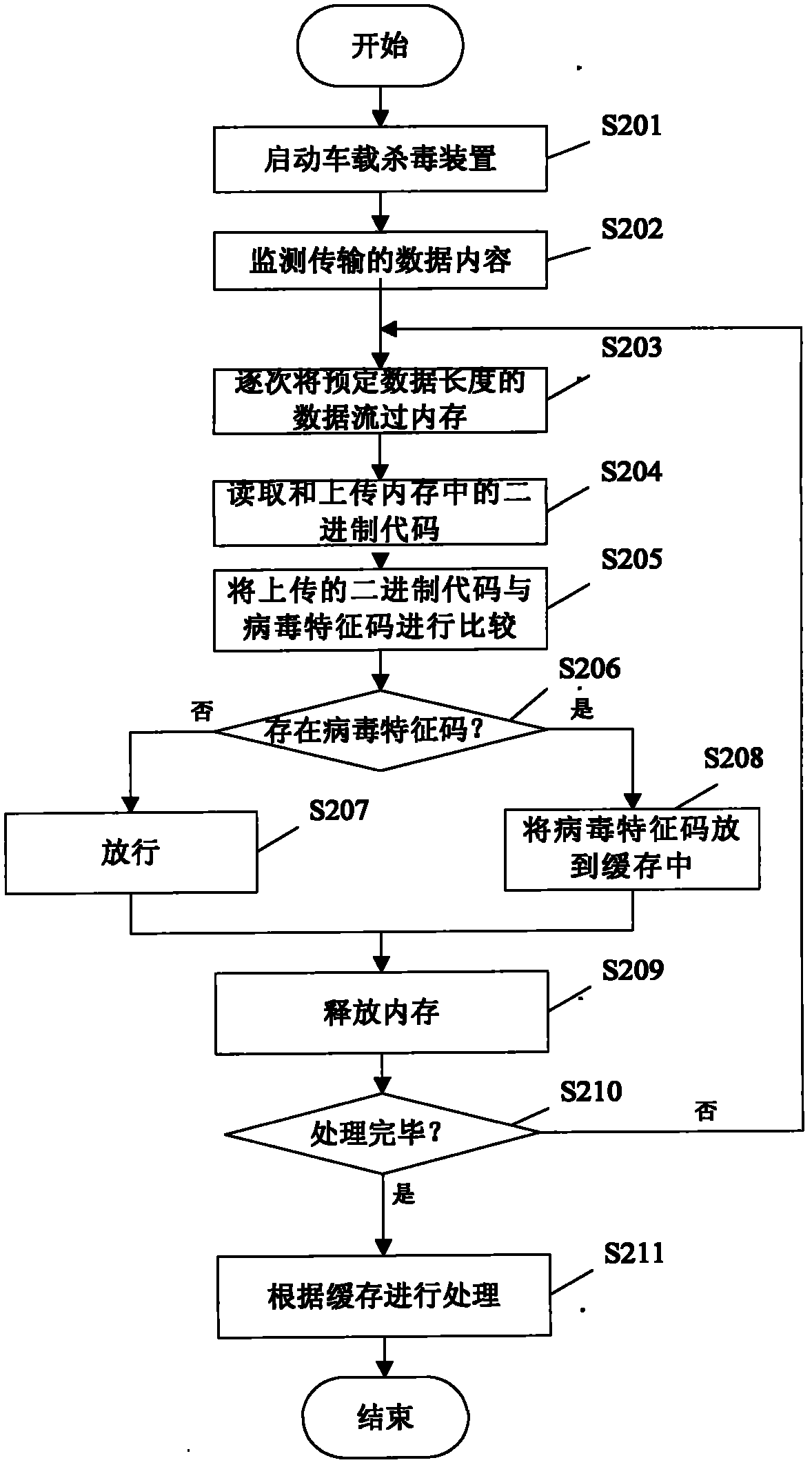
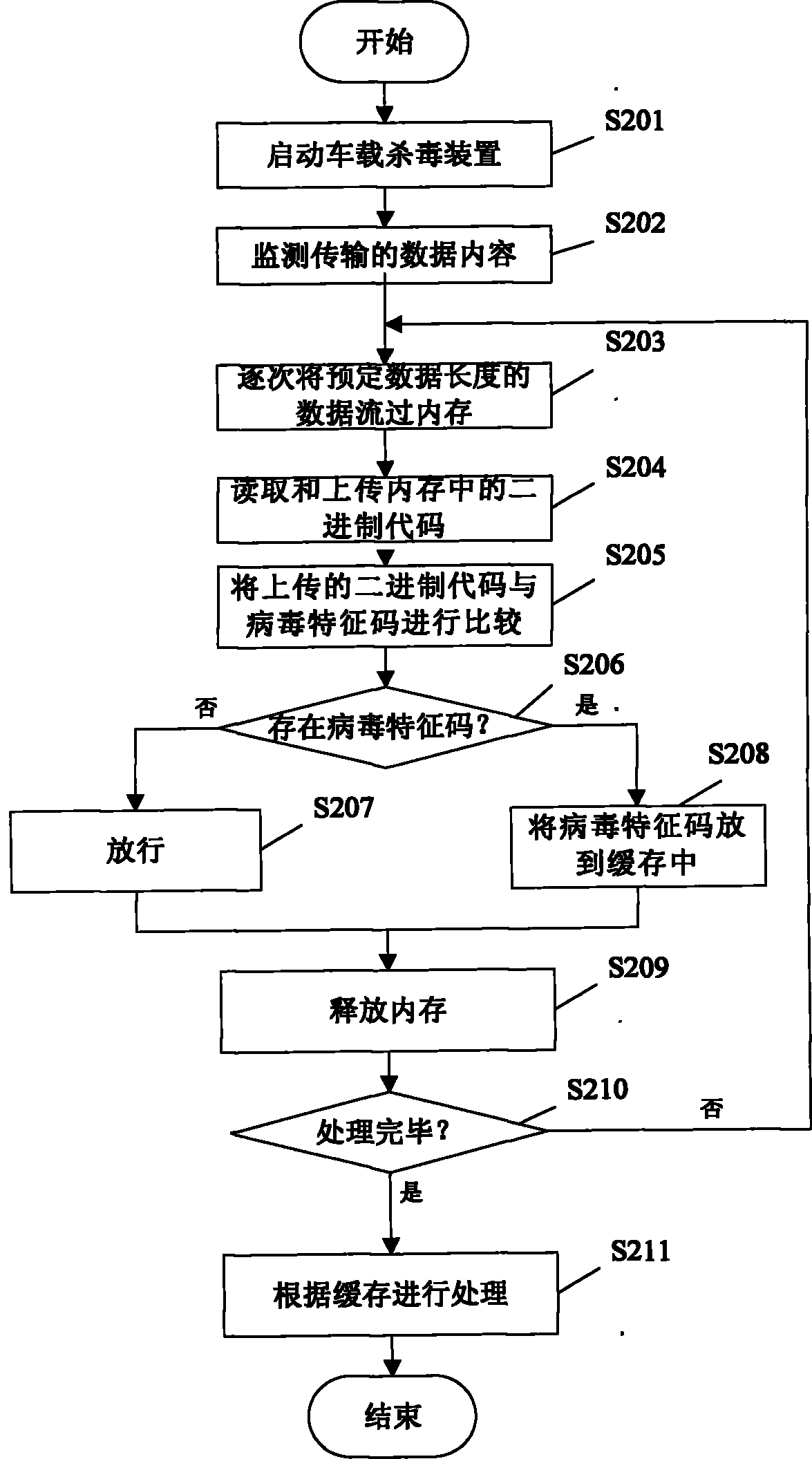
Vehicle-mounted antivirus system and antivirus method
The invention provides a vehicle-mounted antivirus system, which comprises a vehicle-mounted antivirus server for saving and updating a virus database and sending the updated virus database to a vehicle-mounted antivirus device, and the vehicle-mounted antivirus device for monitoring data contents transmitted through the interface of a vehicle-mounted information system in real time, comparing the monitored data contents with virus feature codes in the virus database so as to detect whether the data contents comprise the virus feature codes, clearing the data contents or prompting a user to process the data contents if the virus feature codes are detected from the data contents, and discharging the data contents if the virus feature codes are not detected from the data contents, or for virtually executing the data contents, and determining and processing according to executing action and an executing result. By using the system, the data contents transmitted through the interface of the vehicle-mounted information system can be monitored in real time, so that the aim of performing antivirus on the vehicle-mounted information system is fulfilled.
Owner:CHERY AUTOMOBILE CO LTD
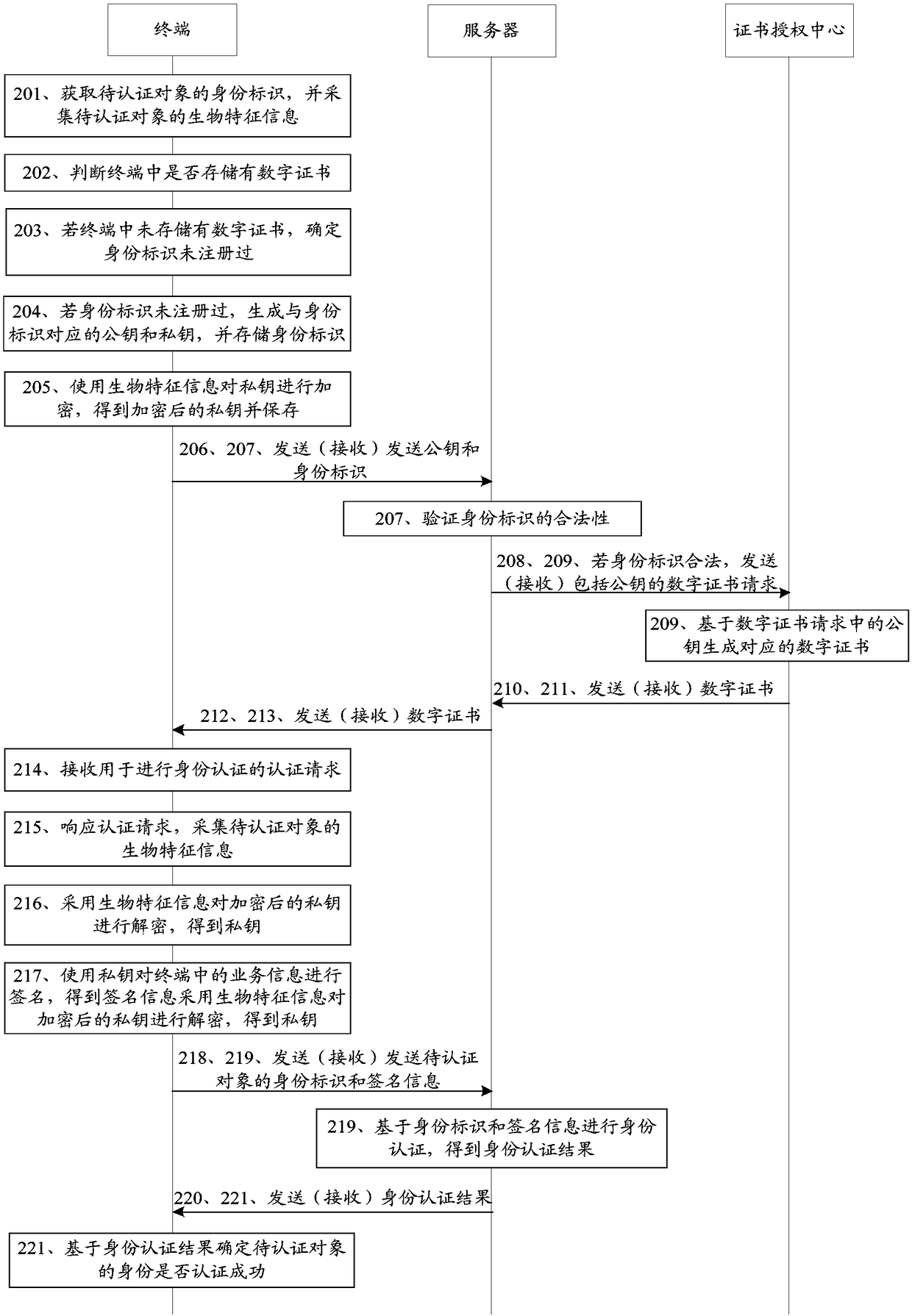
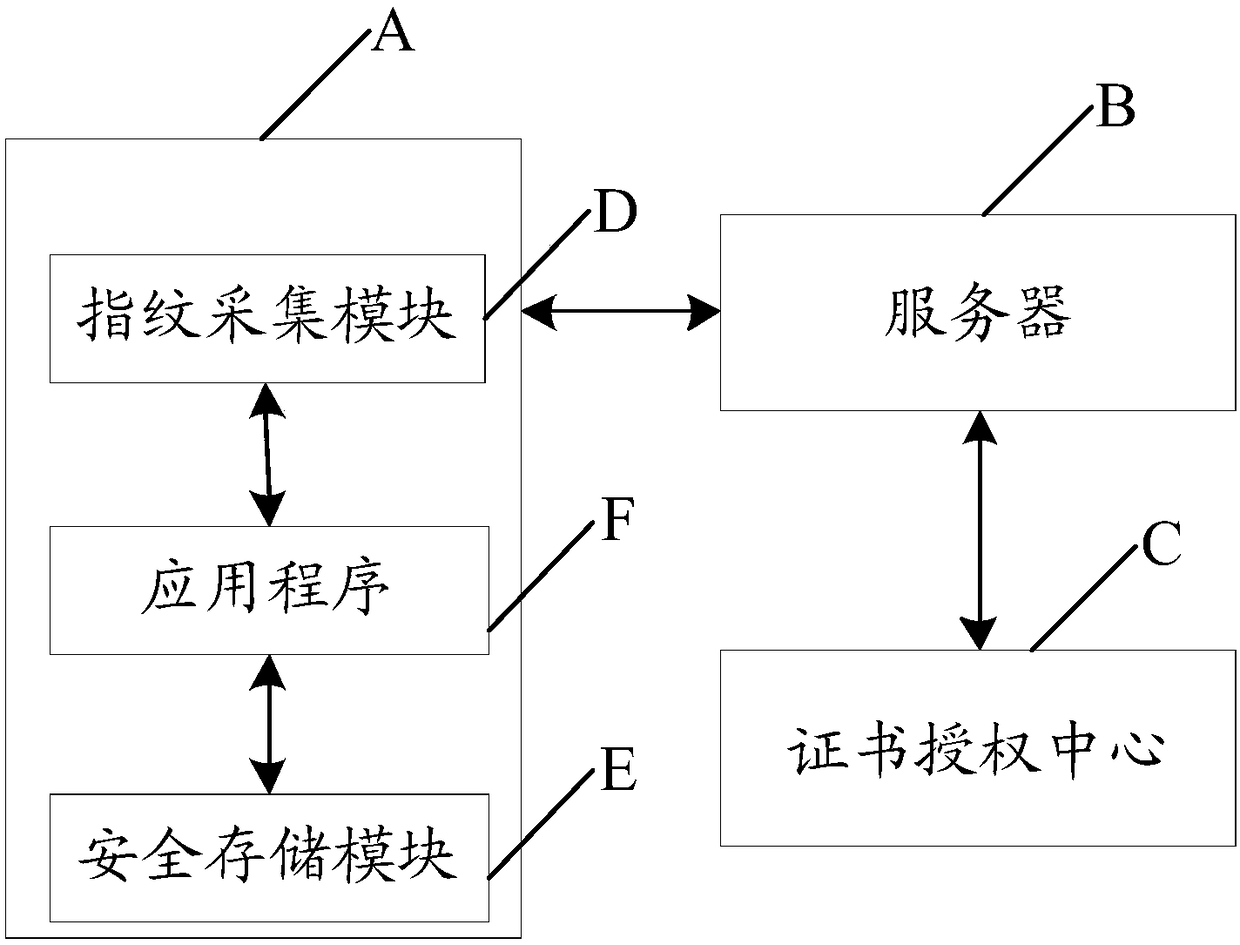
Identity authentication method, apparatus, computer readable storage medium and device
InactiveCN109150535AEnsure safetySecurityKey distribution for secure communicationUser identity/authority verificationAuthentication
Owner:CHINA MOBILE COMM GRP CO LTD
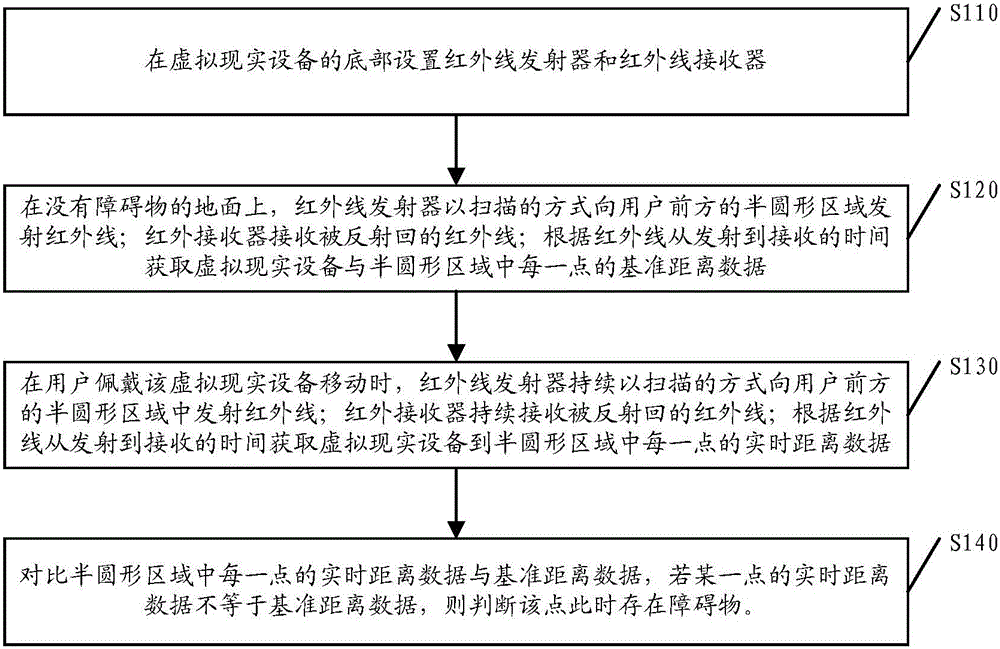
Virtual reality equipment as well as method and device for monitoring ground obstacles under using scene of virtual reality equipment
InactiveCN105807920AEnsure safetySecurityInput/output for user-computer interactionOptical detectionInfrared emitterReference distance
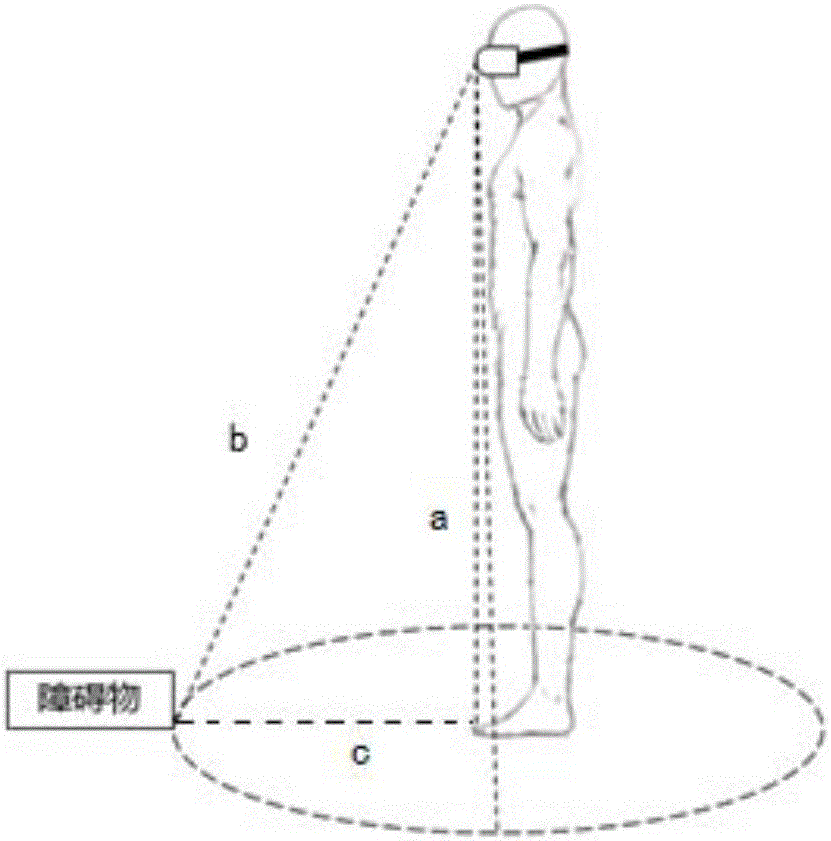
The invention discloses a virtual reality device and a ground obstacle monitoring method and device in a usage scene thereof. The method includes: setting an infrared transmitter and an infrared receiver at the bottom of the virtual reality device; Calibration, to obtain the reference distance data between the virtual reality device and each point in a semicircular area centered on the user in front of the user; when the user moves, the infrared emitter continuously emits infrared rays into the semicircular area in a scanning manner and It is received by the infrared receiver to obtain the real-time distance data from the virtual reality device to each point in the semicircular area; compare the real-time distance data and the reference distance data of each point, if they are not equal, it is judged that there is an obstacle at this point, A prompt is sent to the user to avoid danger and safety is ensured; and the power consumption is low, which less interferes with the user's sense of immersion in the virtual reality scene and improves the user experience.
Owner:BEIJING PICO TECH
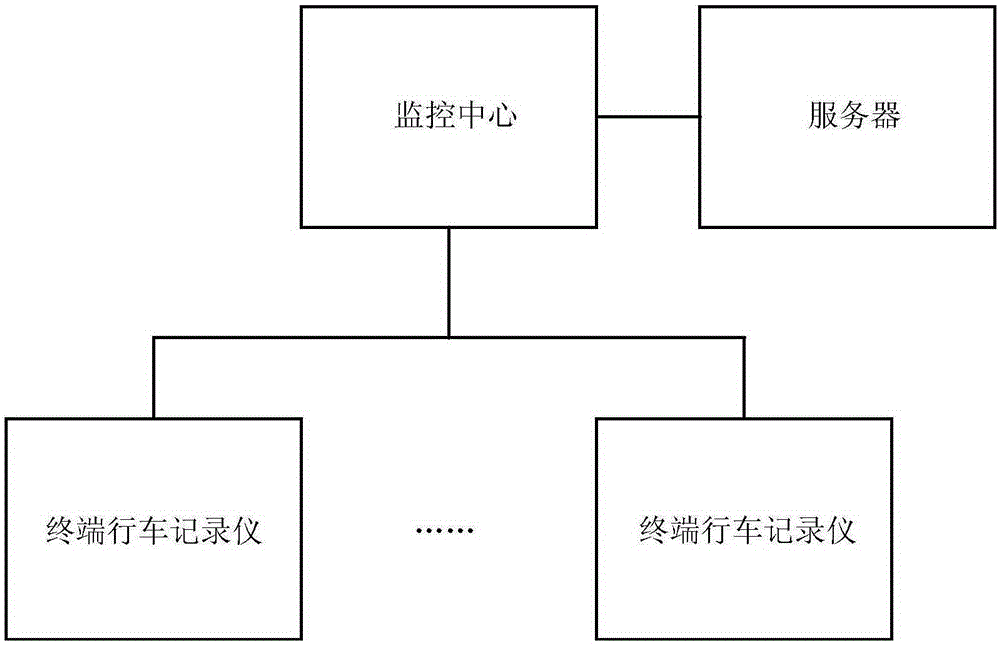
Automobile data recorder with automatic SOS functions, method, and system
InactiveCN105243700ASecurityEnsure safetyRegistering/indicating working of vehiclesAlarmsIn vehicleMemory module
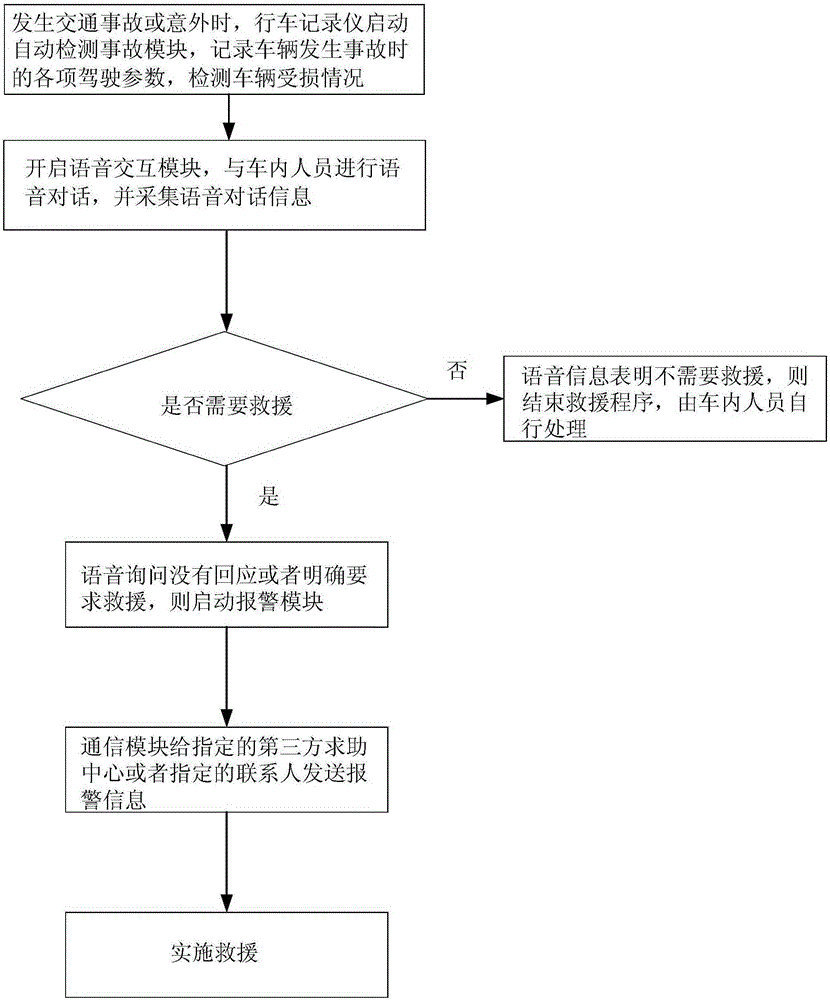
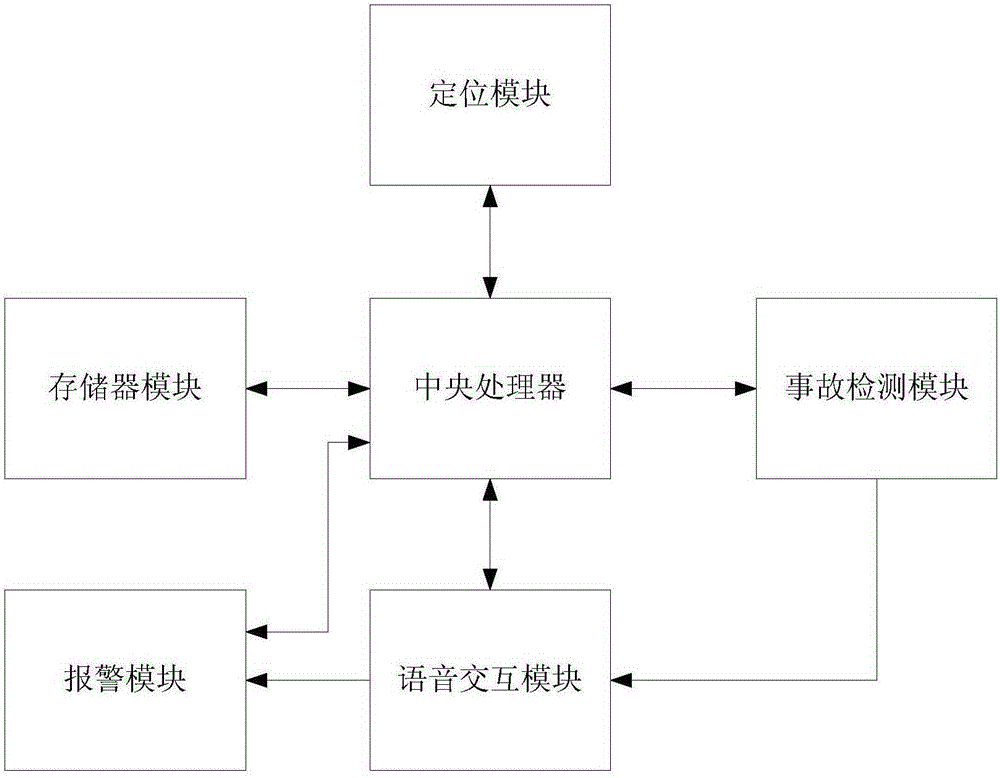
The invention provides an automobile data recorder. The automobile data recorder comprises a positioning module used for determining vehicle position; a communication module used for remote data transmission with a preset specified communication device; an automatic detection accident module used for recording driving parameters in accidents, and detecting vehicle damage situations; a voice interaction module used for realizing voice conversation with people in vehicles so as to determine personal casualty situations; a memory module used for storing information of the voice interaction module, a sensor module, and the positioning module; an alarm module used for sending alarm commands; a central processing unit which is connected with the voice interaction module, the communication module, the positioning module, the automatic detection accident module respectively, and is used for receiving data of the voice interaction module, the positioning module, and the automatic detection accident module, and sending the corresponding data to the memory module. The invention also discloses a vehicle accident automatic alarm SOS method based on the automobile data recorder, more time is saved for traffic accident rescue, and the safety of drivers and vehicles can be guaranteed more effectively.
Owner:SHENZHEN VCYBER TECH
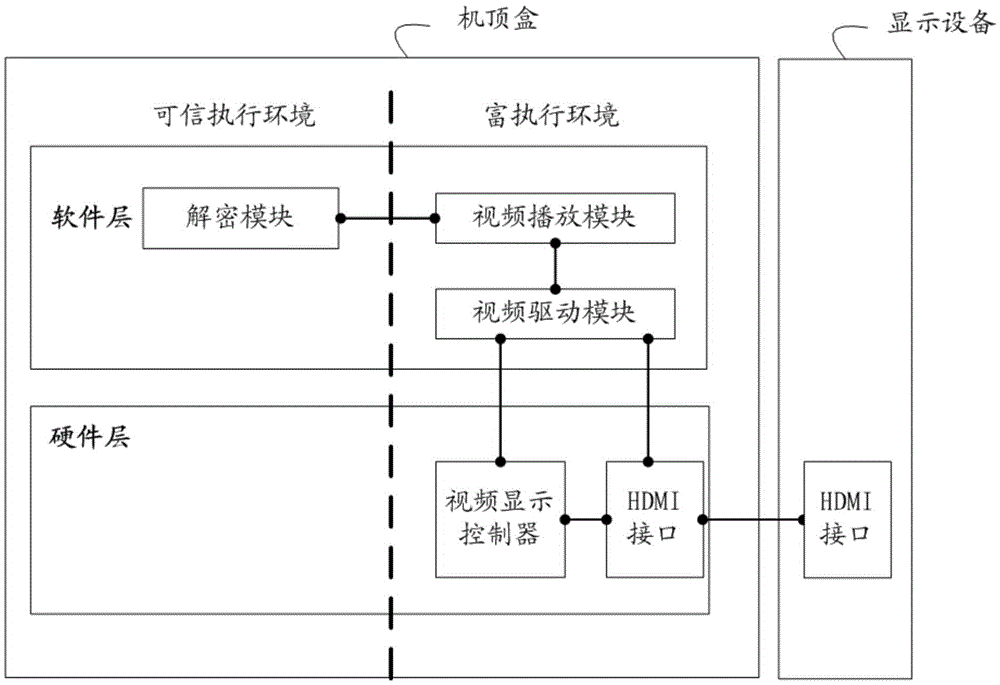
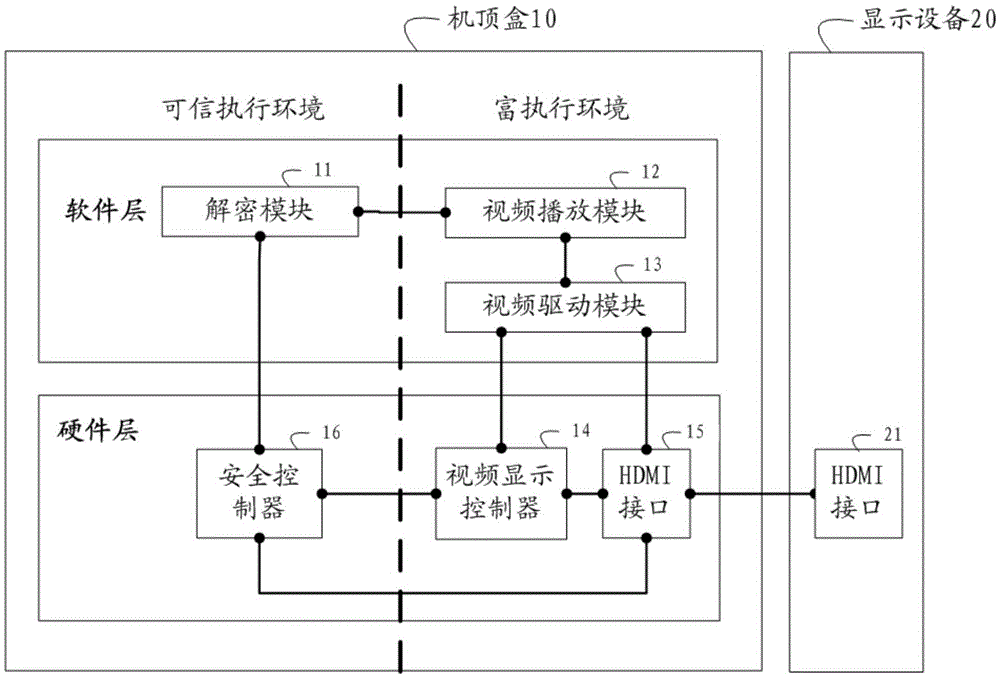
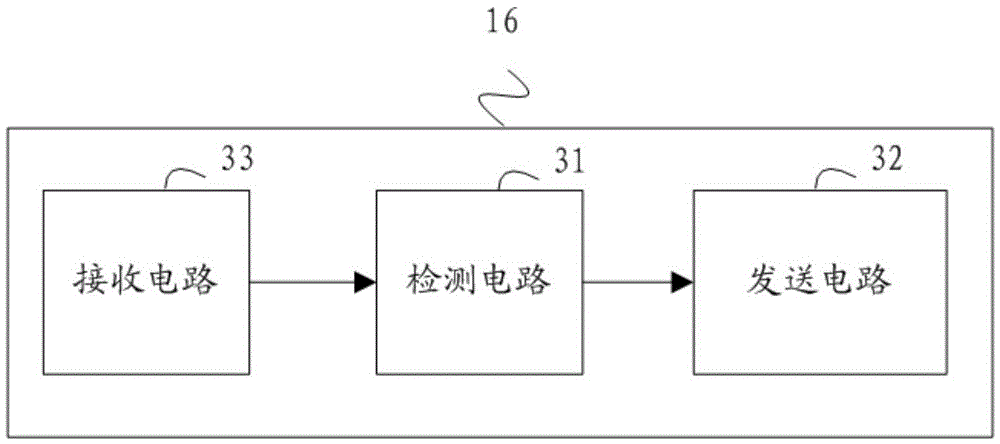
Video output control method, video output control device and control circuit
ActiveCN105681882ASecurityEnsure safetyInternal/peripheral component protectionSelective content distributionImage resolutionVideo output
The invention provides a video output control method and a video output control device. The video output control method comprises the following steps that: a safety controller detects whether the output resolution configured in a video display controller and the HDCP encryption state configured in a HDMI interface satisfy the HDCP protection requirement of a video or not in real time; and, if the output resolution configured in the video display controller and the HDCP encryption state configured in the HDMI interface do not satisfy the HDCP protection requirement of the video, the safety controller sends an instruction to the video display controller, such that the video display controller is indicated to close output of the video. From the foregoing, when the output resolution configured in the video display controller and the HDCP encryption state configured in the HDMI interface do not satisfy the HDCP protection requirement of the video, it shows that the output resolution of the video display controller or the HDCP encryption state of the HDMI interface is tampered due to the fact that a video driving module in a rich execution environment REE is attacked; the video output at this time is unsafe; the safety controller sends the instruction to the video display controller, such that the video display controller is indicated to close output of the video; and thus, the video output safety is ensured.
Owner:HUAWEI TECH CO LTD
URL filtering method and device
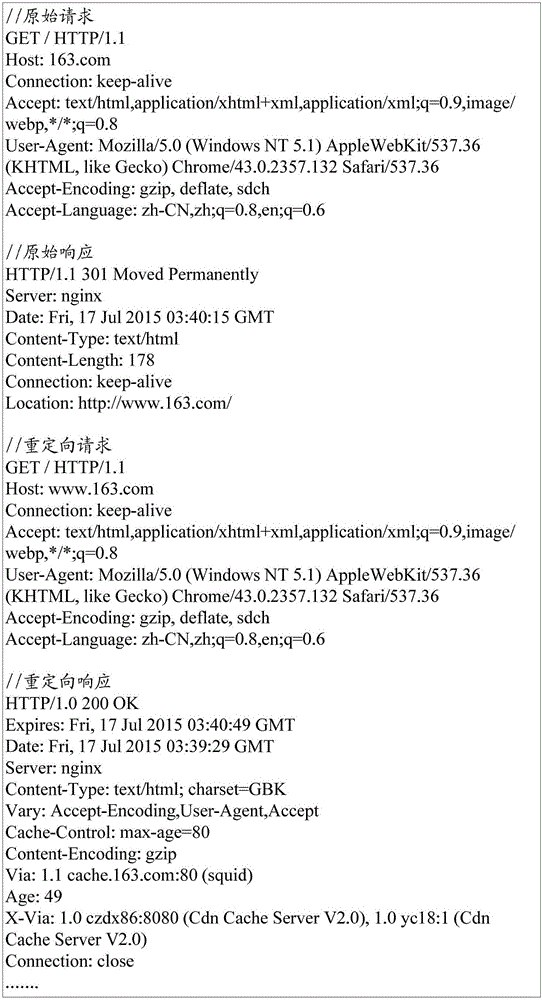
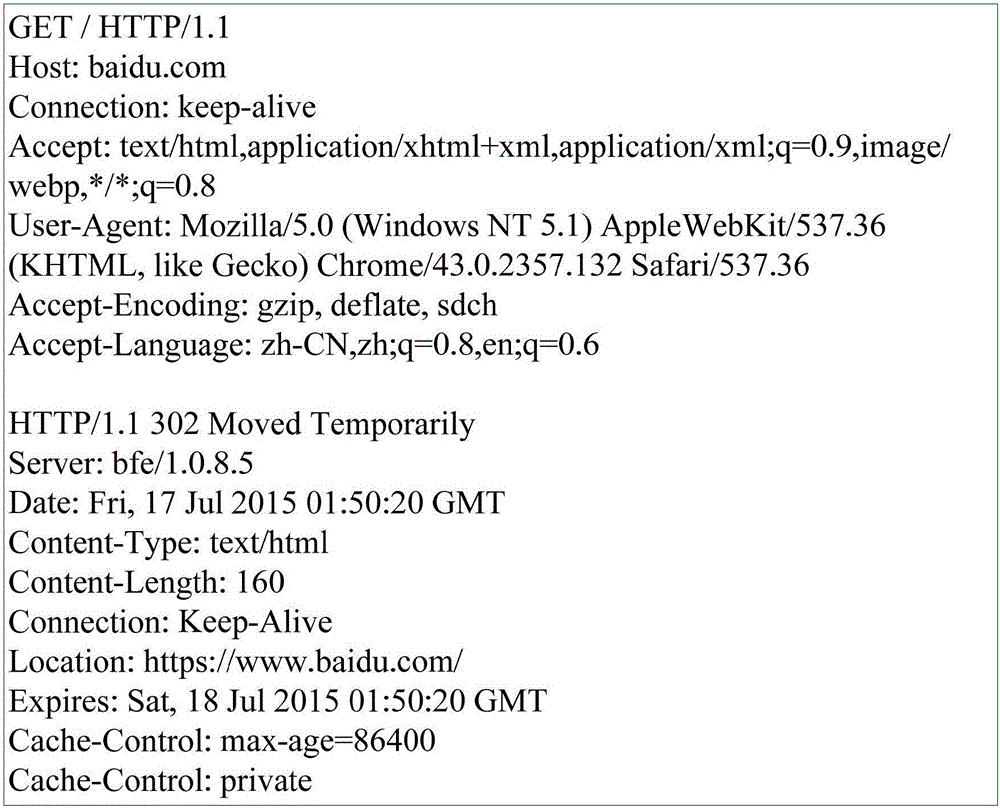
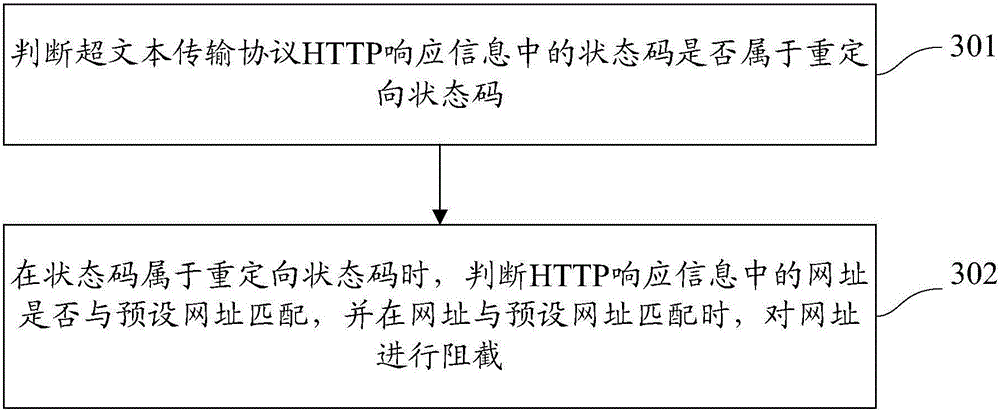
The invention discloses a uniform resource locator (URL) filtering method. The URL filtering method comprises the steps: judging whether a status code of hypertext transfer protocol (HTTP) response information belongs to a redirection status code; if the status code belongs to the redirection status code, judging whether a URL of the HTTP response information matches a preset URL; and if the URL matches the preset URL, blocking the URL. The invention further discloses a URL filtering device.
Owner:BEIJINGNETENTSEC
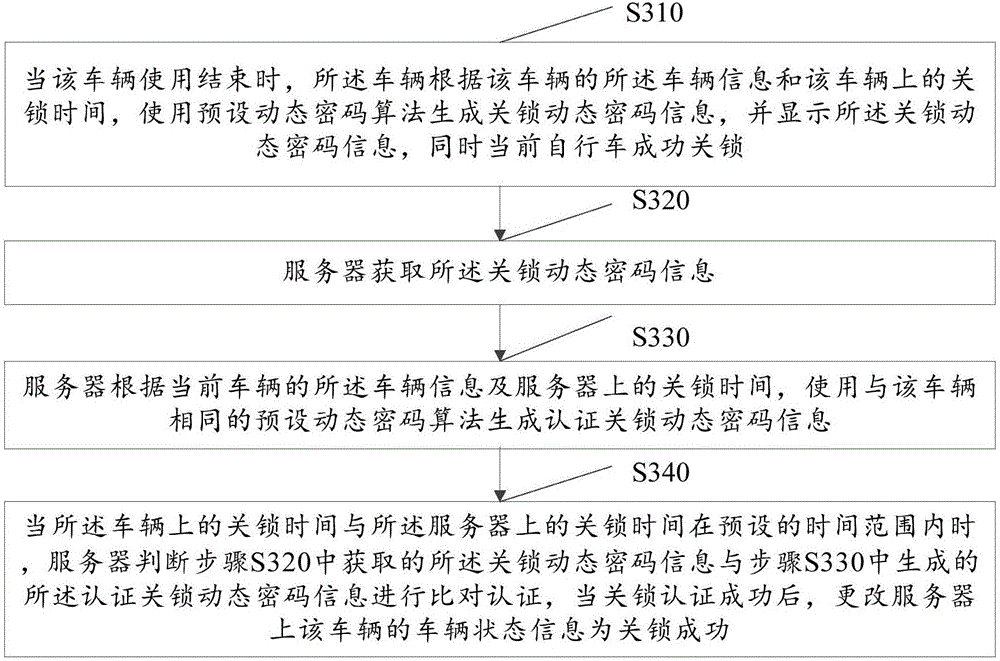
Method and system for controlling time type vehicle unlocking/locking
ActiveCN106780859ASecurityStrict verificationApparatus for meter-controlled dispensingIndividual entry/exit registersLock timeOn the fly
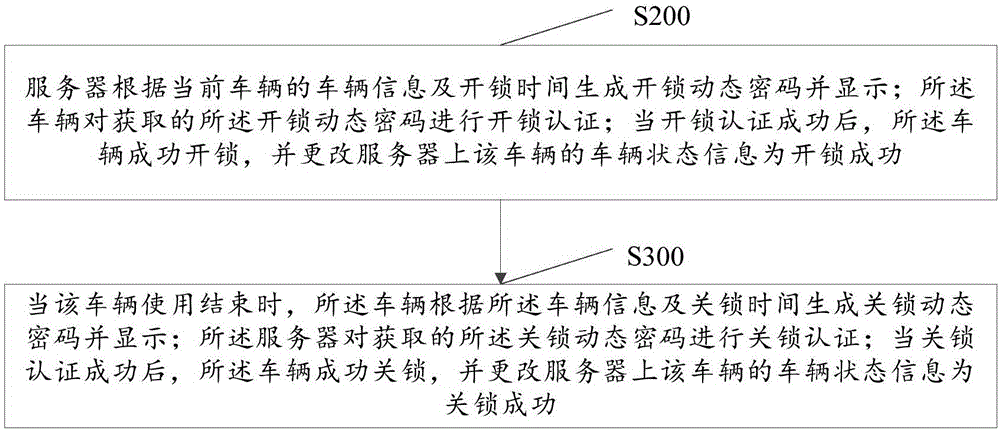
The invention discloses a method for controlling time type vehicle unlocking / locking. The method comprises the following steps of enabling a server to generate an unlocking dynamic password according to the vehicle information and unlocking time of the existing vehicle, and displaying; enabling the vehicle to perform unlocking verification on the obtained unlocking dynamic password; after the unlocking verification is successful, successfully unlocking the vehicle, and changing the vehicle state information of the vehicle into the successful unlocking state; after the vehicle is used, enabling the vehicle to generate a locking dynamic password according to the vehicle information and the locking time, and displaying; enabling the server to perform locking verification on the obtained locking dynamic password; after the locking verification is successful, successfully locking the vehicle, and changing the vehicle state information on the vehicle into the successful locking state. The method has the advantage that a dynamic password is generated through a transaction platform and a vehicle intelligent lock, and then a public vehicle is locked / unlocked, namely the use / return state, so as to solve the problem of password stealing, and also solve the problems of stealing and waste by illegal persons.
Owner:SHANGHAI PEOPLENET SECURITY TECH
Method for monitoring of drug temperature and humidity and trace management of quality
InactiveCN104346705ASecurityRealize traceabilityMeasurement devicesCo-operative working arrangementsDrugEngineering
Owner:NEWLAND DIGITAL TECH CO LTD
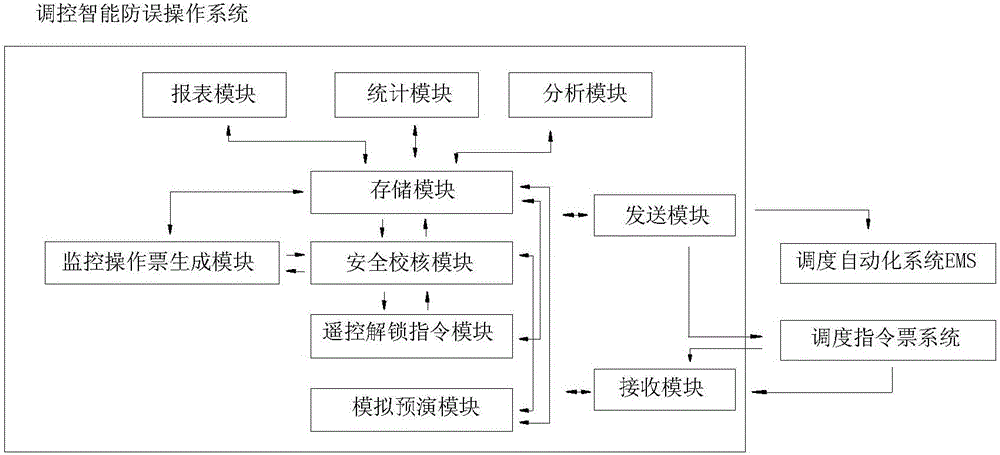
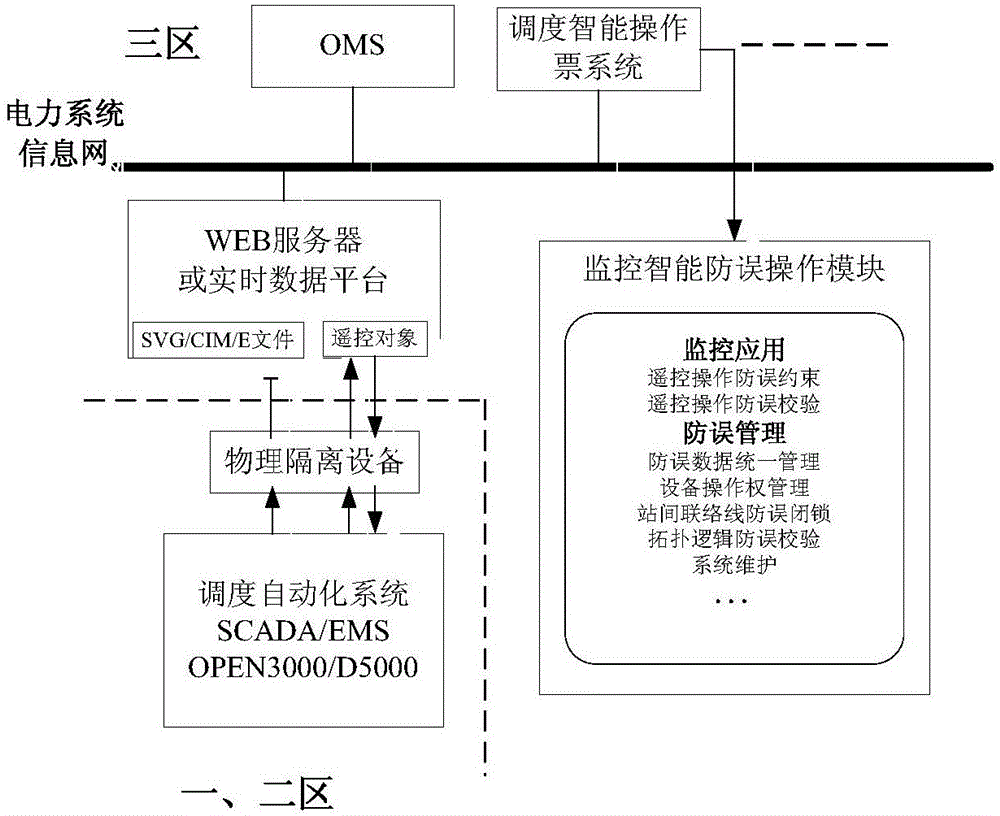
Regulation and control intelligent anti-error operation system based on operation order system
ActiveCN106483890ASecurityReduce stepsProgramme control in sequence/logic controllersPower gridError prevention
The invention discloses a regulation and control intelligent anti-error operation system based on an operation order system. The regulation and control intelligent anti-error operation system is added on the basis that the regulation and control intelligent anti-error operation system has already achieved an EMS (OPEN3000 or D5000) system power grid model and the real-time data sharing, achieves the organic integration of operation order, intelligent error prevention and anti-error constraint functions, and guarantees the safety of regulation and control remote operation. The system does not change a mode of a controller in remote control of an EMS system, reduces the operation steps to maximum degree, optimizes the operation flow, and improves the operation efficiency.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD QUZHOU POWER SUPPLY CO +2
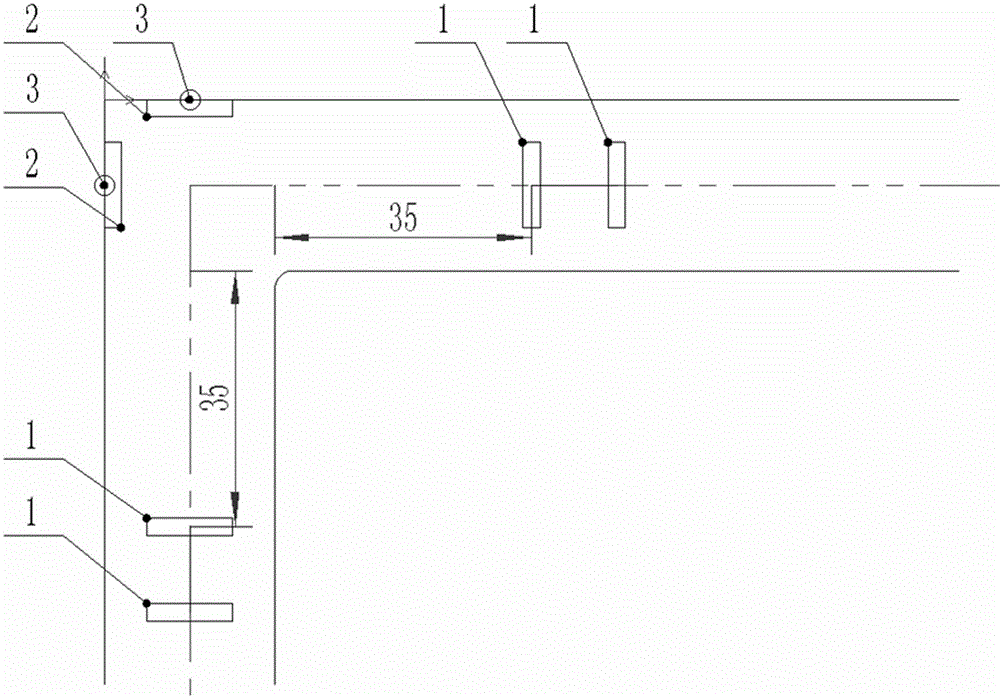
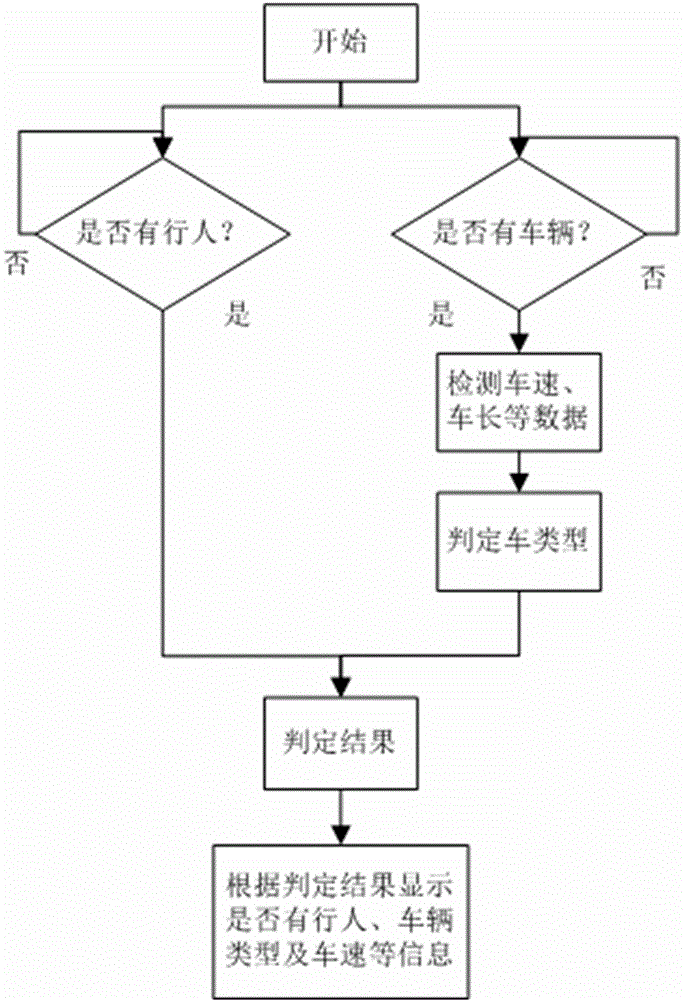
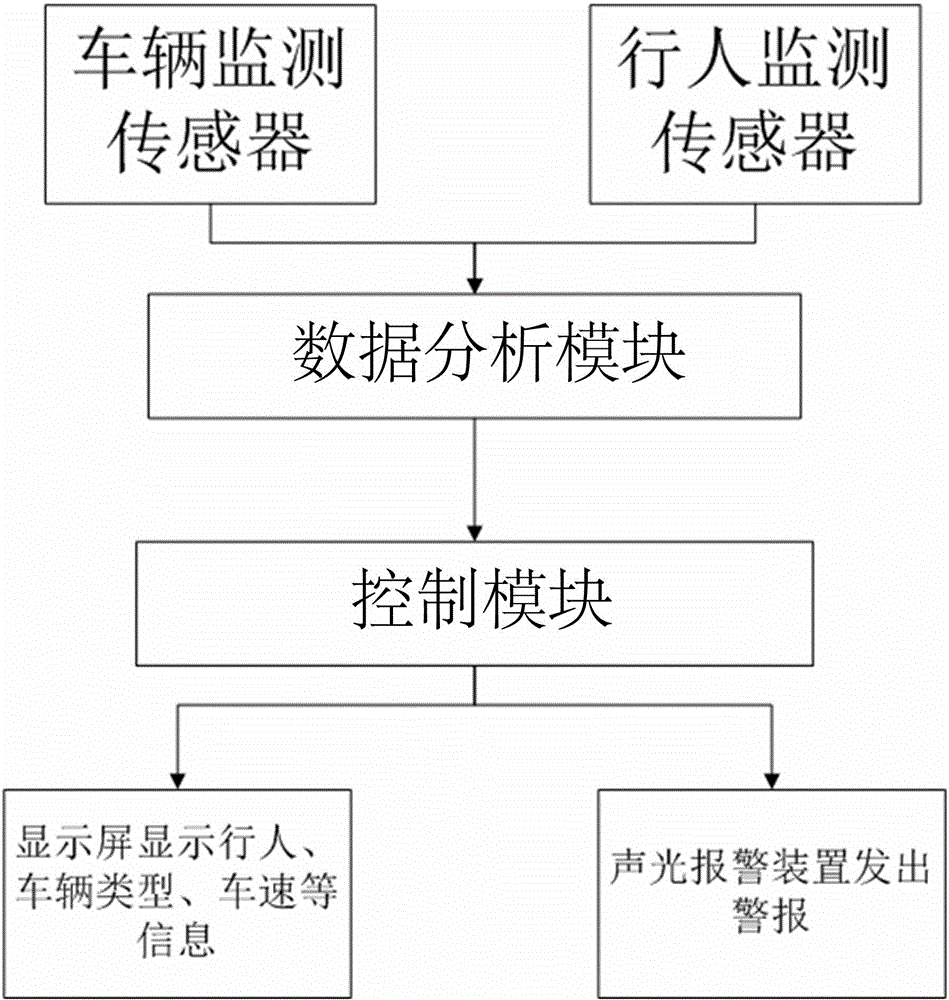
Pre-warning system used for curve vehicle crossing pre-warning
The invention discloses a pre-warning system used for curve vehicle crossing pre-warning. The pre-warning system is characterized by comprising a control module, and a detection module, a data analysis module and a pre-warning module which are sequentially connected with the control module. In the practical application, a crossroad is detected in real time by utilizing a ground sensor and a pedestrian detection sensor so that data of speed and the vehicle type of a vehicle entering the curve can be automatically detected, and the detected data are processed and then displayed on an alerter arranged at the crossroad to prompt passing vehicles of another crossroad. Visual observation of a driver is substituted by automatic detection, and safety of curve vehicle crossing is enhanced so that an objective of guaranteeing safety of pedestrians and vehicles can be achieved. Vehicle speed detection, vehicle length detection and pedestrian detection are combined by the system and can be displayed on pre-warning screens of other crossroads in real time, and a mode of purely relying on visual observation of the driver for the traffic condition of another crossroad is substituted by a sound-light alarm device so that safety of the pedestrians and the vehicles of the curve is guaranteed to the largest extent.
Owner:GUILIN UNIV OF ELECTRONIC TECH
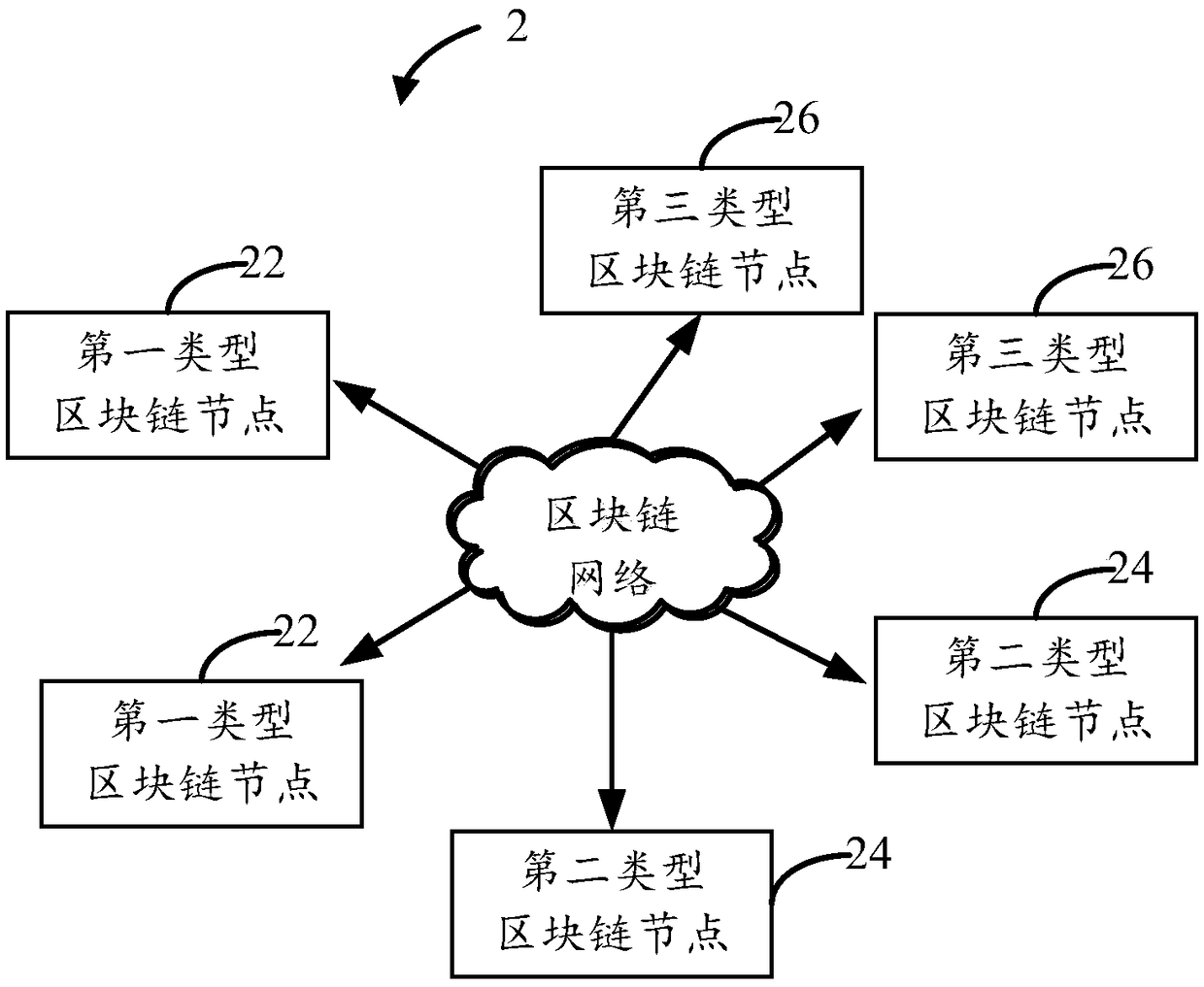
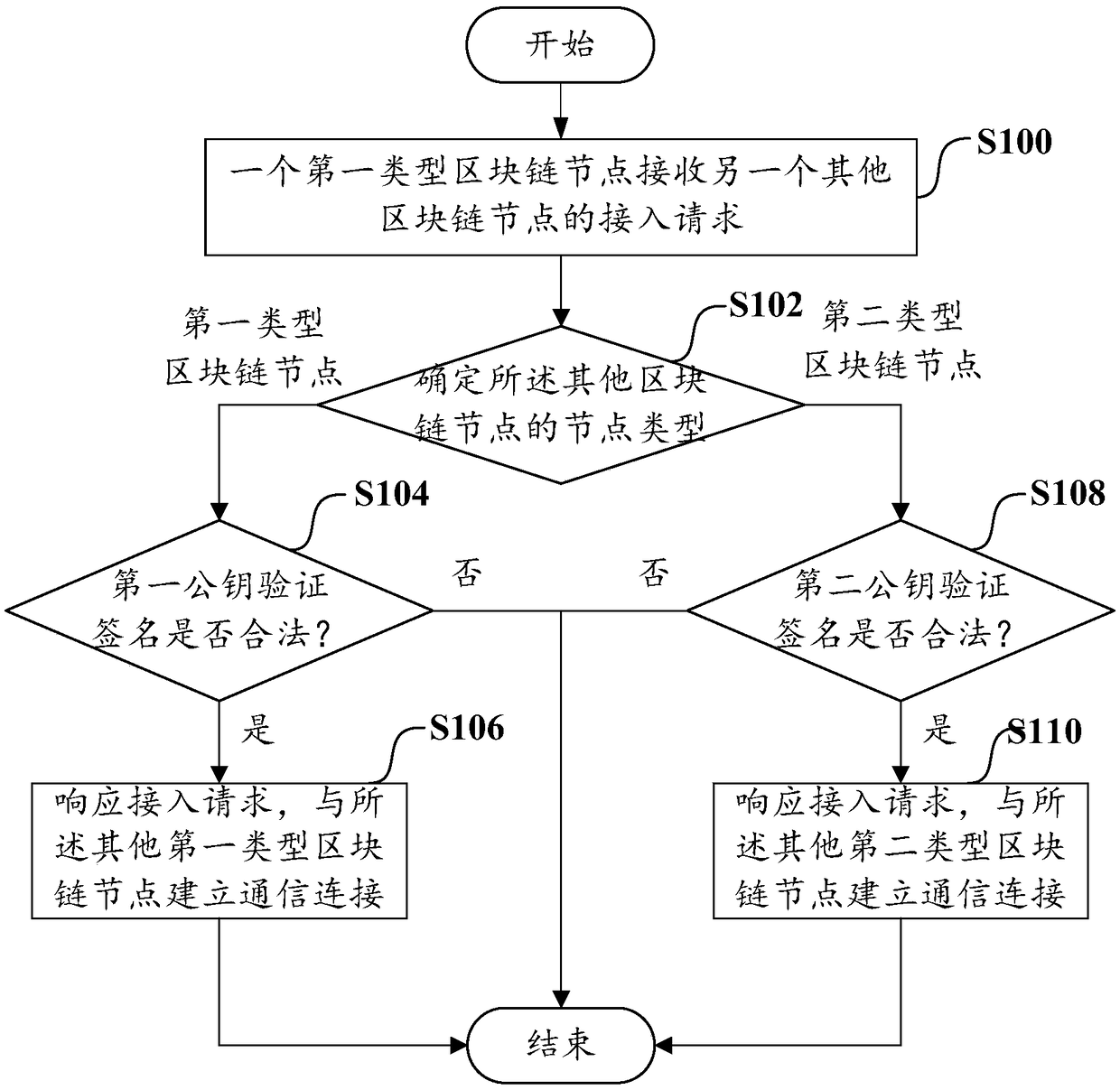
Blockchain node authority control method, blockchain system and storage medium
ActiveCN108696502AGuaranteed legalitySecurityUser identity/authority verificationBlockchainWhitelist
The invention discloses a blockchain node authority control method, which is applied to a blockchain system including first-type blockchain nodes, second-type blockchain nodes and third-type blockchain nodes. The method includes the following steps: after a first-type blockchain node receives an access request of another other blockchain node, determining a node type of the other blockchain node according to a first identifier in a first whitelist and a second identifier in a second whitelist; according to the node type, verifying whether the signature of the other blockchain node is legal byusing a first public key in the first whitelist or a second public key in the second whitelist respectively; and if the signature is legal, establishing a communication connection with the other blockchain node in response to the access request. The invention also provides a blockchain system and a storage medium. Thereby, the security of blockchain transaction data can be effectively guaranteed.
Owner:SHENZHEN THUNDER NETWORK TECH
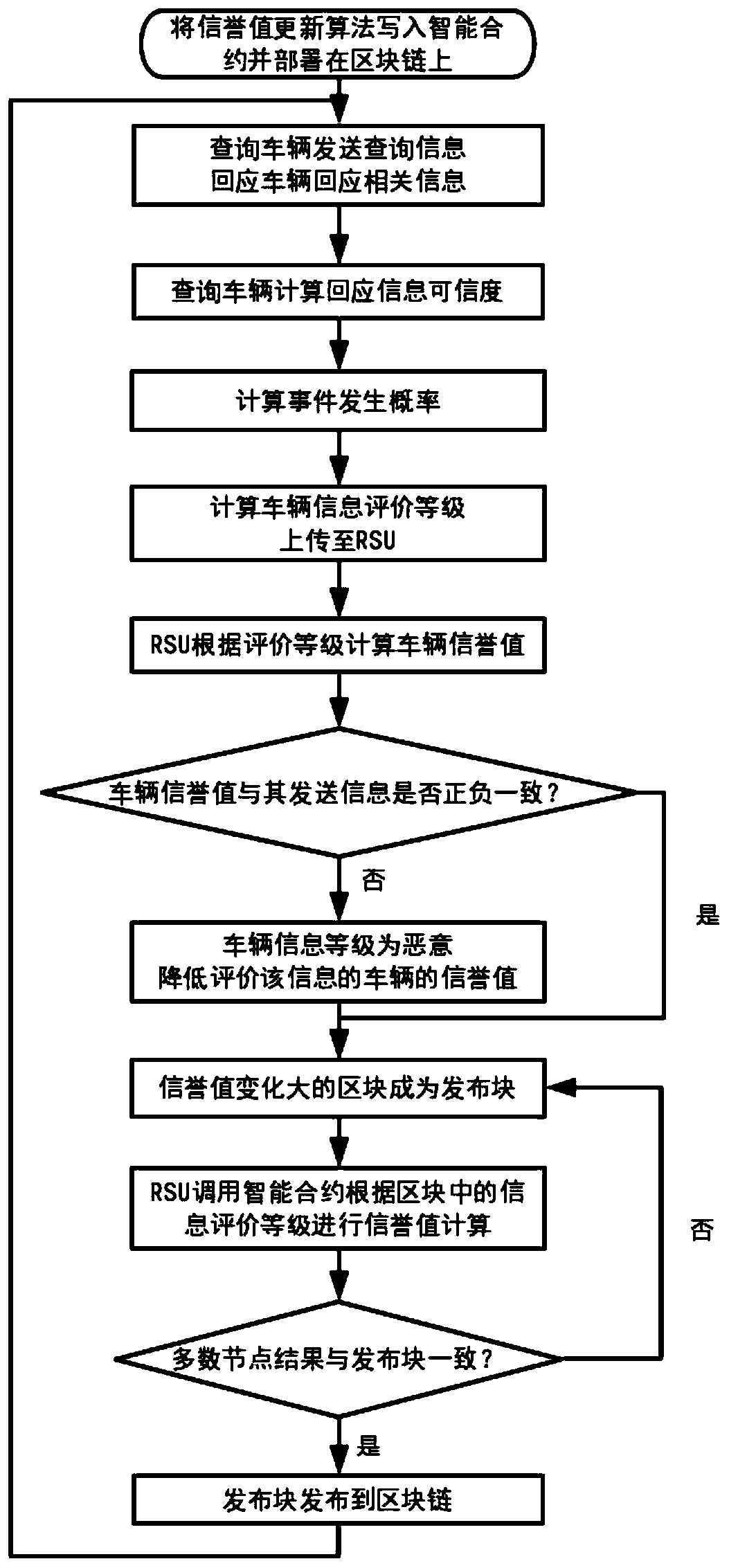
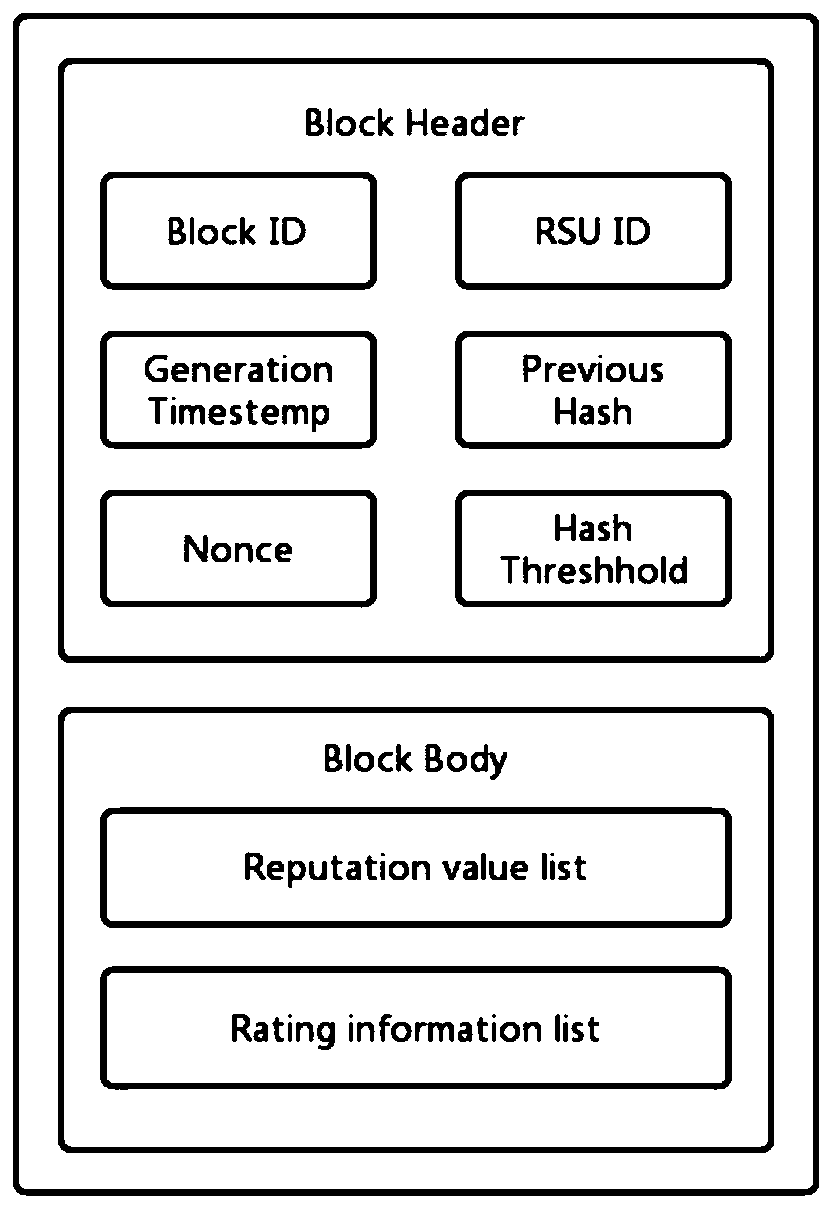
Internet-of-Vehicles trust management method based on block chain
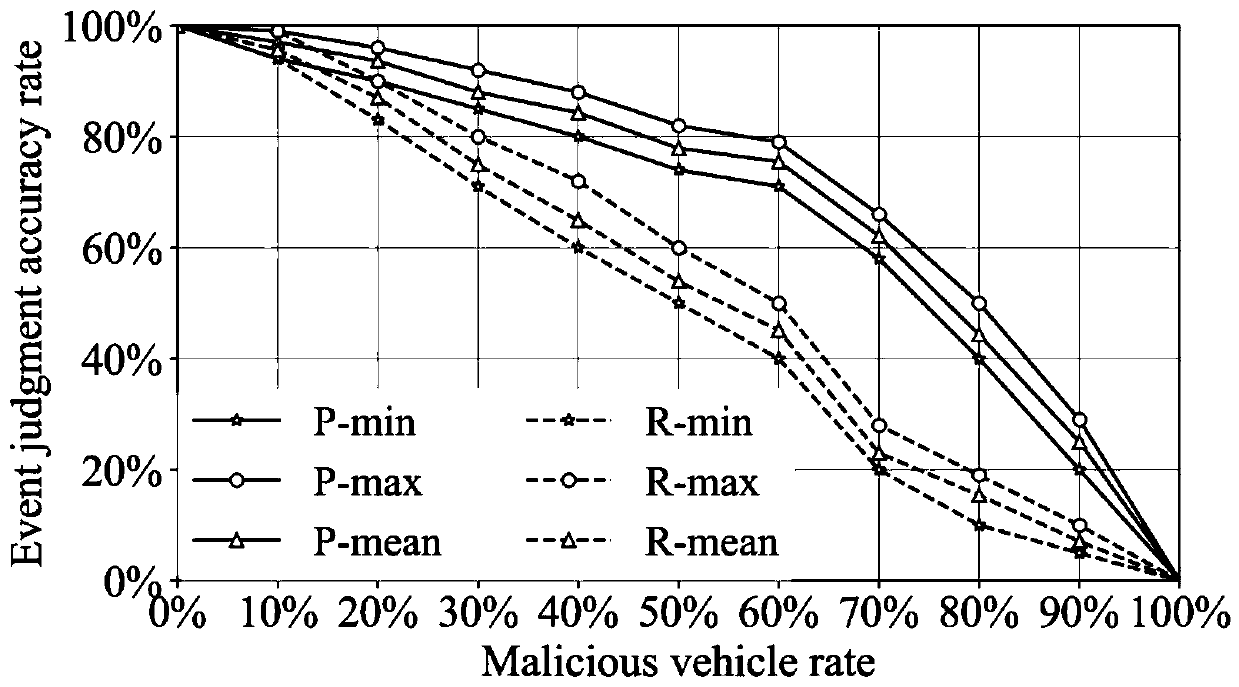
ActiveCN111447177ASecurityInformation judgment is accurateDatabase distribution/replicationDigital data protectionBlockchainData security
The invention discloses an Internet-of-Vehicles trust management method based on a block chain, and the method comprises the steps: firstly calculating the credibility of received vehicle informationrelated to an event, judging the occurrence probability of each event through the credibility of the vehicle information, generating a rating for transmitted information, and uploading the rating of the vehicle information to nearby RSUs; enabling the RSU to call a reputation value updating method in an intelligent contract deployed on a block chain to calculate a vehicle reputation value, whereinthe calculated vehicle reputation value and the collected rating information are all packaged into a block; through a consensus mechanism combining PoW and PoS, ensuring RSUs with larger change of vehicle reputation values to serve as miner nodes to publish blocks; and enabling other RSUs to re-use the reputation value updating method of the smart contract to re-calculate the rating in the release block, and if the calculation results of most nodes are consistent with the data in the release block, releasing the release block to the block chain to realize Internet-of-Vehicles trust management. According to the invention, the data security is ensured, and the accuracy of event judgment in the Internet of Vehicles is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Implementation method for grade-based passive registered real-name alumni service
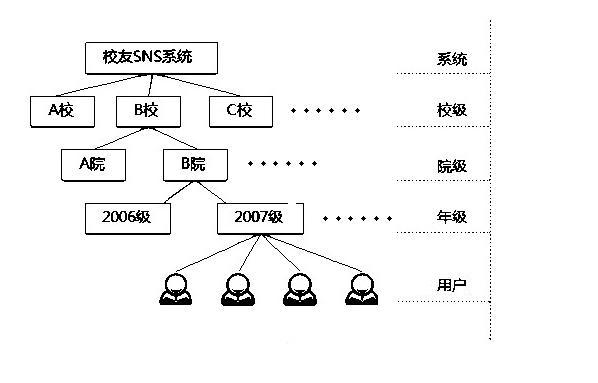
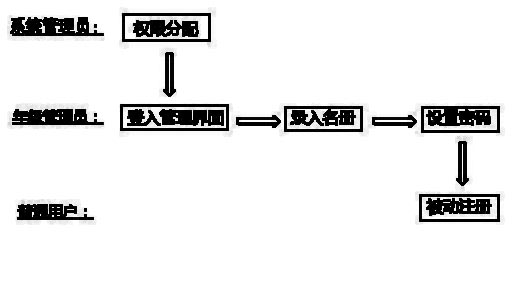
The invention relates to a network system registry method and provides an implementation method for a grade-based passive registered real-name alumni service. On a basis of a mathematical set theory, the method expands a real-name user group step by step so as to construct a real-name social network. The method divides an alumni SNS (social networking service) website into a few levels from top to bottom, namely a system level, a school level, a college level, a grade level and a user level. Basic registration information is input on a basis of the grade level, a grade administrator sets a uniformly initial password for member users in the grade level, and common users enter an activated page of the alumni SNS system to complete passive registration based on a real name and an initial password. The invention realizes a real-name alumni SNS website in a grade-based passive registration mode, provides a simple login mode for alumni, and realizes a real function of finding a person, thus real-time services can be well provided for alumni and a real-name social website can be truly created.
Owner:WUHAN TAOXING NETWORK TECH
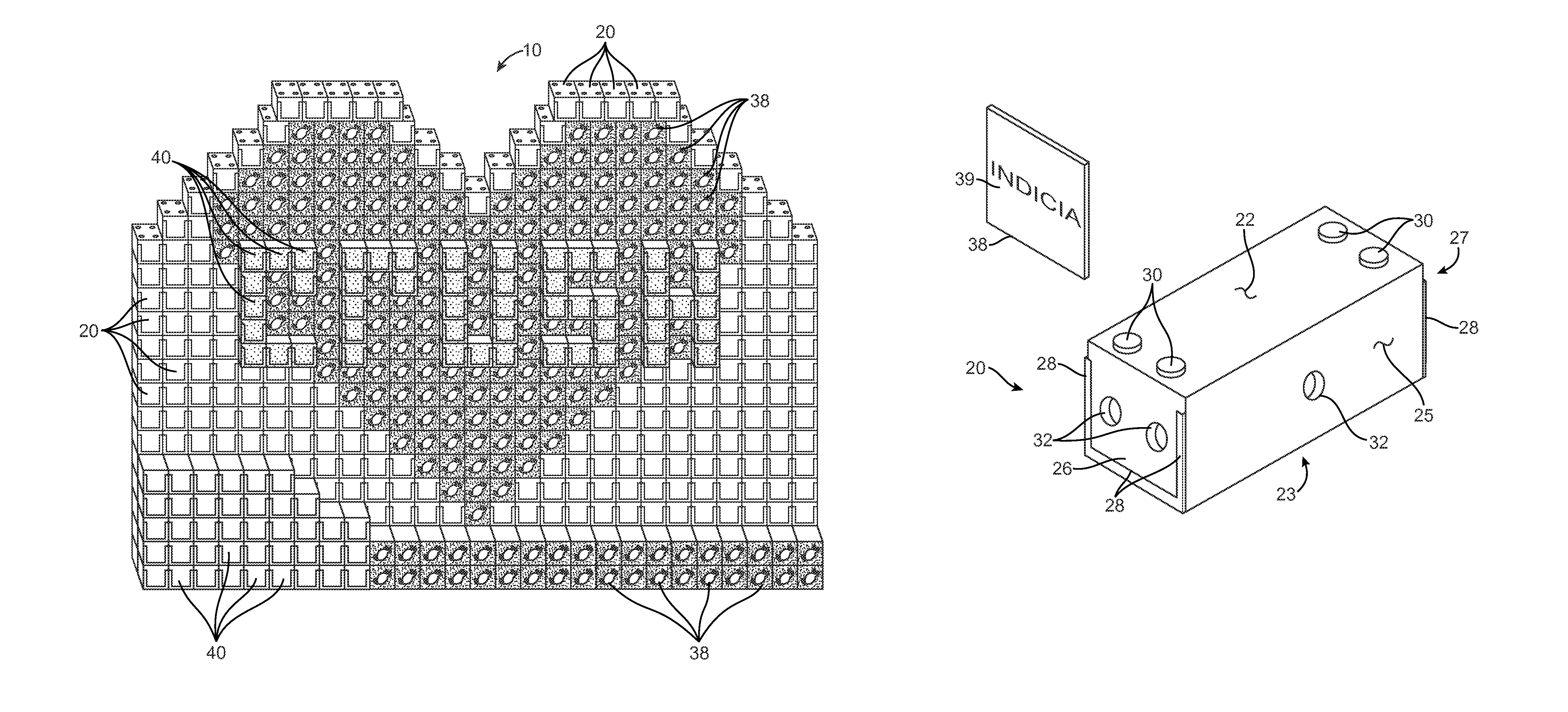
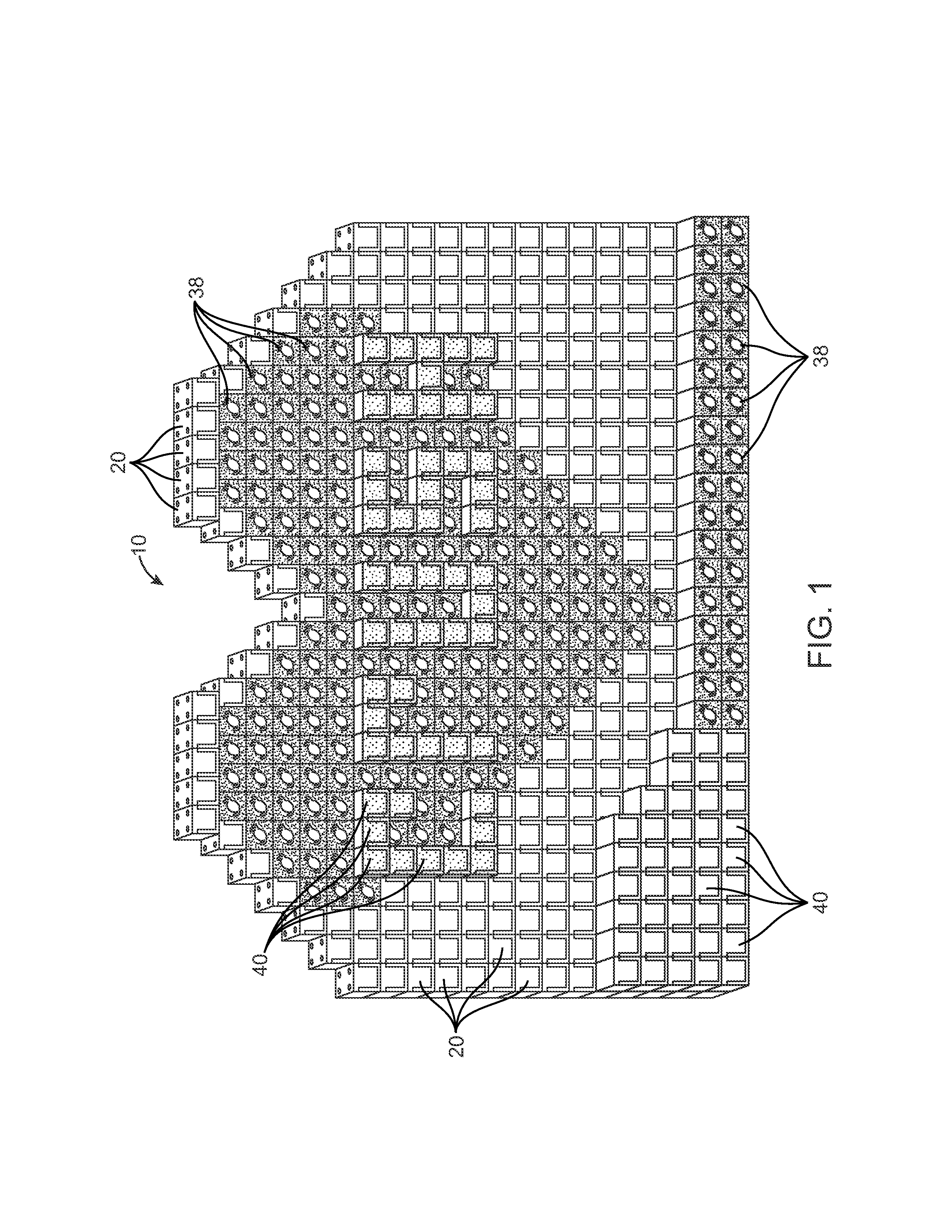
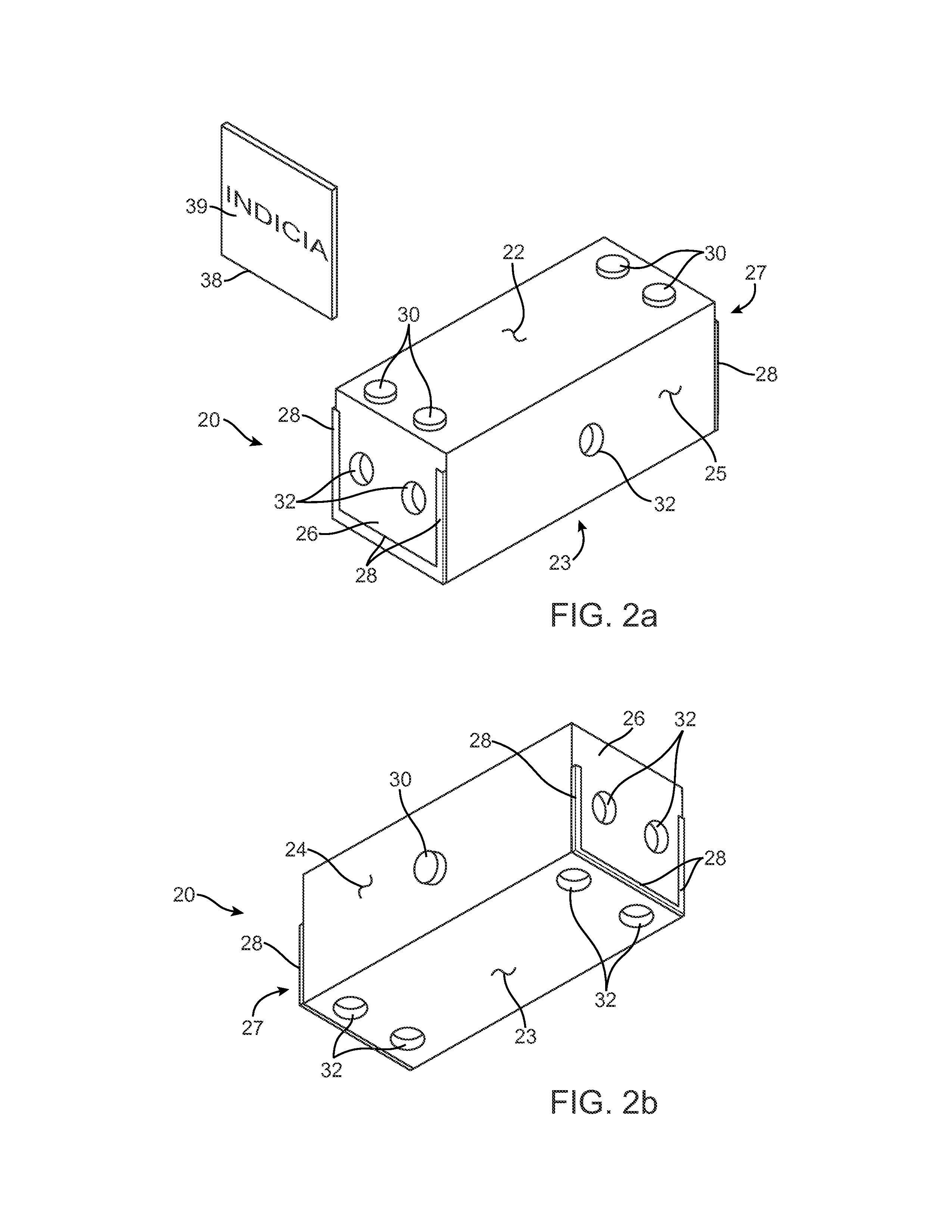
Modular display system
A novelty advertising system using a plurality of hollow plastic rectangular enclosures simulating stacking boxes of real products to construct an advertising display is herein disclosed. The hollow enclosures provide replaceable advertising inserts depicting the product being sold. Each enclosure is provided with a plurality of interlocking posts and sockets allowing creation of large stable displays without using large quantities of real product which cannot be sold. Such displays can be built with minimal expense while avoiding a danger of toppling displays built with the actual heavy product.
Owner:GARDINIER JERRY D +1
Intelligent method and system for monitoring graze
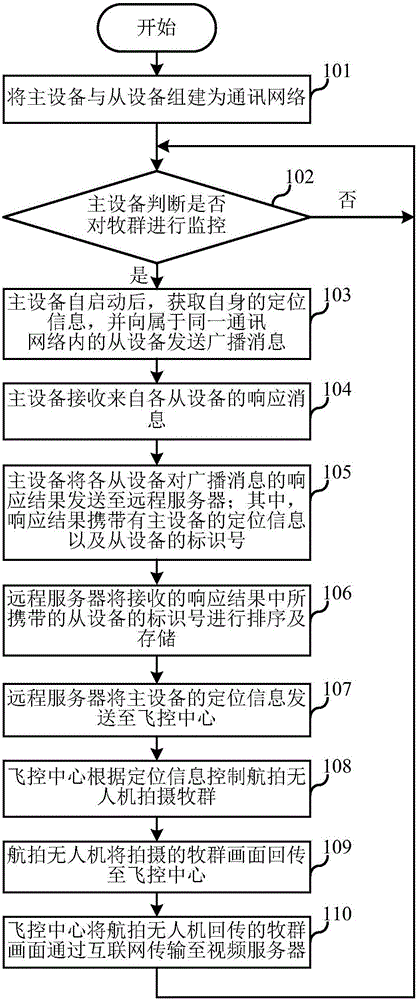
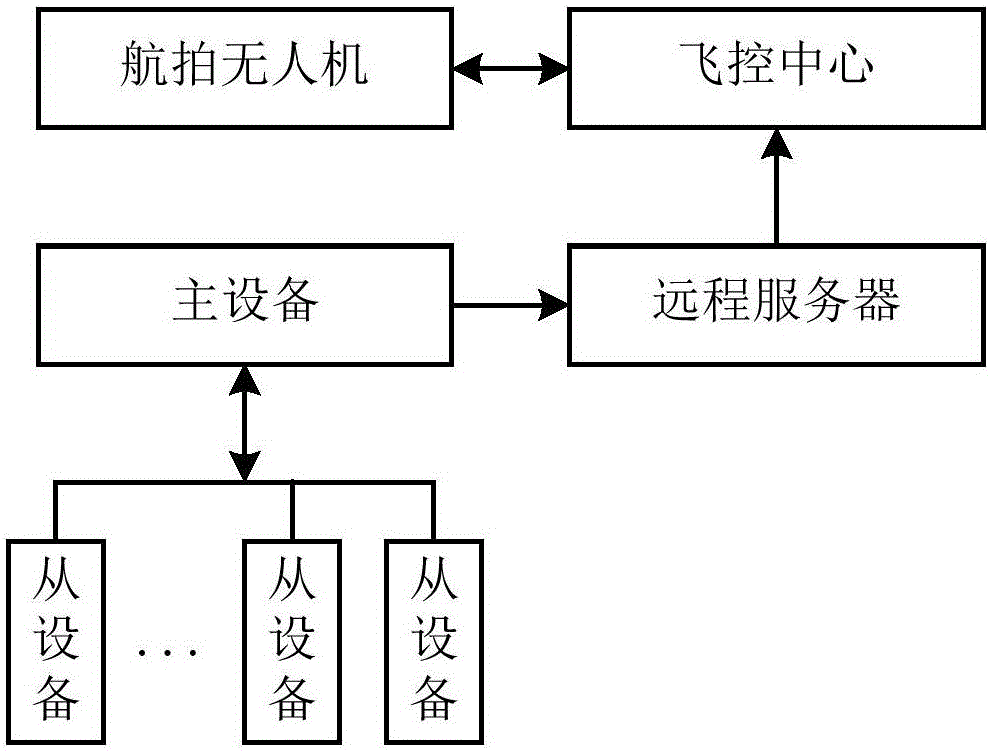
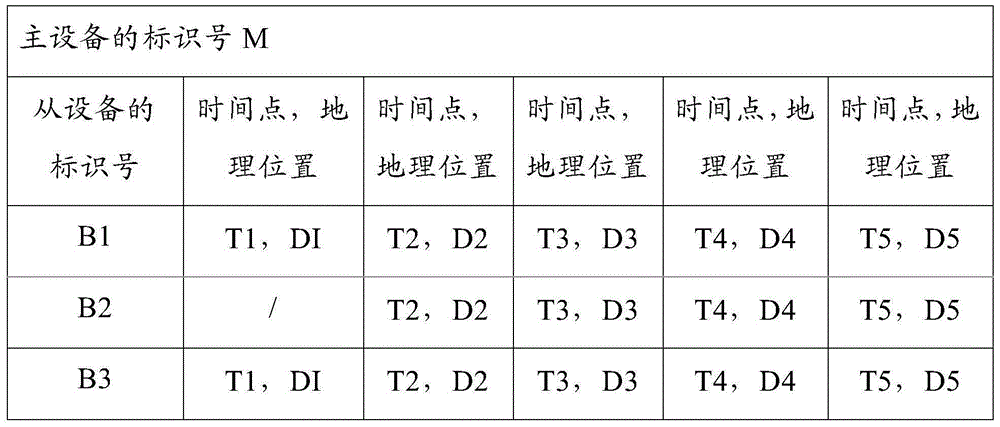
InactiveCN105072417AReduce workloadSecurityClosed circuit television systemsTransmissionAerial photoLivestock
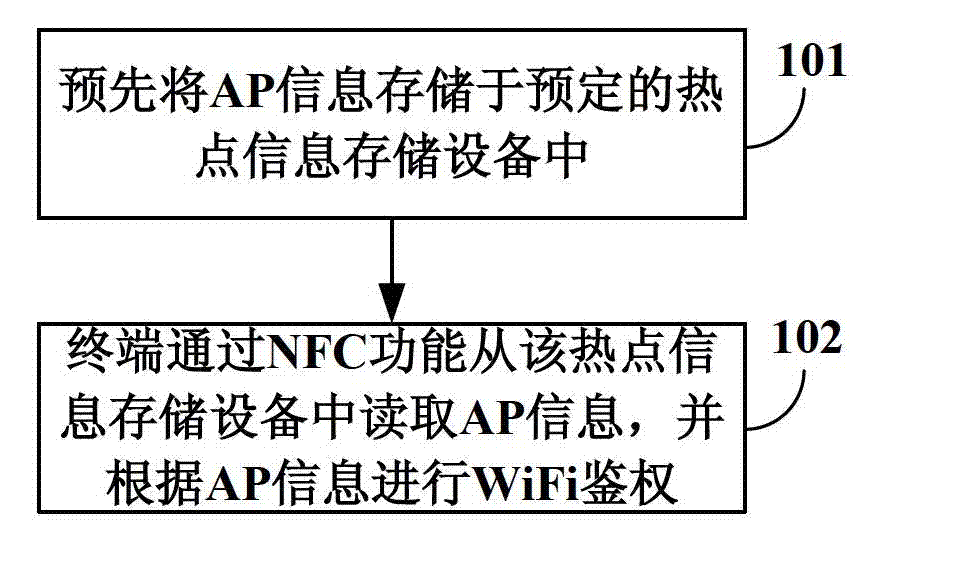
The invention discloses an intelligent method and an intelligent system for monitoring graze. The method in the invention comprises the steps as follows: wearing a primary device for head livestock in advance; the primary device of a herd transmitting self locating information to a remote server while needing to monitor the herd; the remote server transmitting the locating information to a flight control centre, the flight control centre controlling an aerial photo unmanned plane to shoot the herd according to the locating information, and the aerial photo unmanned plane transmitting the shot herd image back to the flight control centre. In the invention, a herdsman could obtain the graze condition of the herd in the field via remote video monitoring in real time even in the home to relieve the work load of the herdsman and ensure the safety of the herdsman. The method and the system of the invention solve the problem of desertification of meadow adjacent to the residence of the herdsman brought by excessively gnawing, avoid the property loss brought to the herdsman because of the loss of the livestock, and enable the potential consumers of the livestock to know the breeding condition of the livestock via the video in real time.
Owner:上海宇芯科技有限公司
Lane departure early warning method
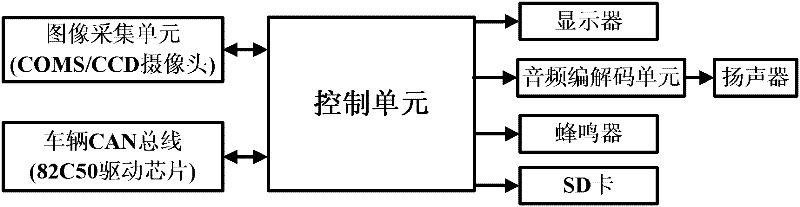
InactiveCN102514572ASecurityReduce the chance ofSignalling/lighting devicesLoudspeakerTraffic accident
The invention discloses a lane departure early warning method, which comprises a lane departure early warning system, wherein the lane departure early warning system comprises an image acquisition unit, a vehicle CAN bus, a control unit, a displayer, an audio coding and decoding unit, a buzzer, a security digital (SD) card and a loudspeaker, wherein the image acquisition unit, the vehicle CAN bus and the control unit are connected in two ways; the displayer, the audio coding and decoding unit, the buzzer and the SD card are connected with a control unit; and the audio coding and decoding unit is connected with a loudspeaker. The method disclosed by the invention can provide an in-time and effective early warning mechanism for the lane departure of an automobile, divide conditions of road ahead into far visual field road conditions and short visual field road conditions according to the calibration result of an image acquisition unit, provide near visual field lane departure early warning and far visual field inner curve lane vehicle speed early warning methods and effectively reduce traffic accidents.
Owner:HUNAN UNIV
High-speed vertical and continuous wire-rewinding machine
The invention discloses a high-speed vertical and continuous wire-rewinding machine, which mainly comprises a machine body, a main shaft mechanism, a rotary wire rewinding platform mechanism, spools, a supporting mechanism, a wiring mechanism and a clamping and cutting device. The main shaft mechanism fixed on the upper part of the machine body is a main transmission mechanism of the device, and the main shaft is driven by a variable frequency motor to rotate. The rotary wire rewinding platform mechanism is installed on the machine body by a rotary support and is driven by the variable frequency motor to rotate so as to change the positions of the spools. When at work, the supporting mechanism installed on the lower part of the machine body supports one spool to deviate from a rotary platform so as to be combined with the main shaft, and the spools and the supporting mechanism rotate with the main shaft. The wiring mechanism installed on the side face of the machine body is used for controlling the wiring uniformity. If the wires are fully distributed on the spools, the clamping and cutting device installed on the lower end of the main shaft clamps and cuts the wires to finish the wire rewinding work. The high-speed vertical and continuous wire-rewinding machine disclosed by the invention has the advantages that the vertical wire rewinding manner guarantees the high-speed and stable rotation of the spools so as to guarantee firm and regular wire rewinding, and that double spools are utilized to quickly change the spools so as to improve the production efficiency.
Owner:张谷旭
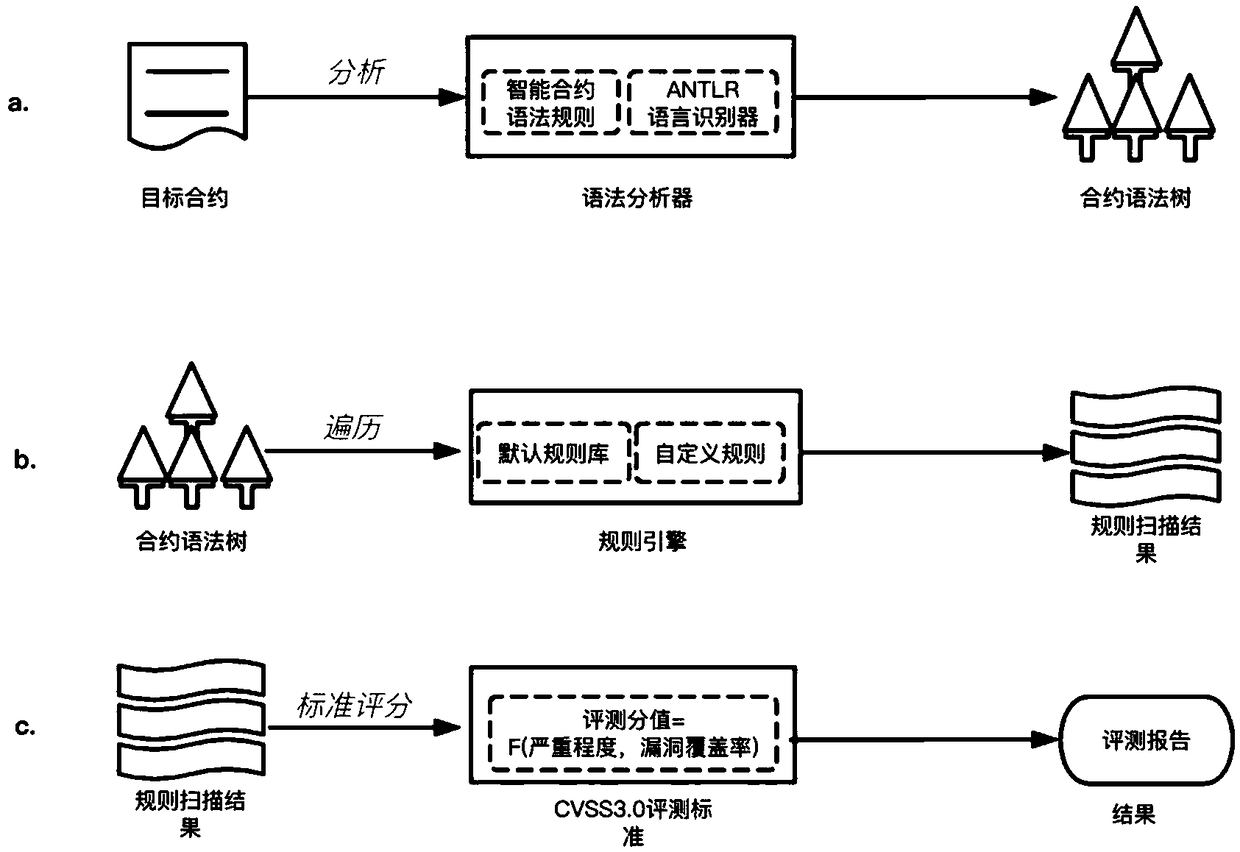
Intelligent contract safety evaluation method based on a rule engine
InactiveCN109492402ASecurityReduce lossesPlatform integrity maintainanceCode compilationAnalyserAmbiguity
The invention discloses an intelligent contract safety evaluation method based on a rule engine, and the method comprises the following steps: obtaining a target intelligent contract, generating a grammar analyzer according to the language rule of the target intelligent contract, and enabling the language rule of the target intelligent contract not to carry an ambiguity statement; analyzing the target intelligent contract by using the syntax analyzer generated in the step S1, and generating a contract syntax tree; customizing a rule base of the intelligent contract vulnerability rule engine; s2, using an intelligent contract vulnerability rule engine to continuously traverse and scan the contract syntax tree in the step S2 to obtain a scanning result of each rule in the rule base; and S3;performing standard evaluation on the rule scanning result obtained in the step S3 to obtain a final evaluation result. According to the invention, the problem that the security risk of the smart contract is difficult to perceive before the smart contract is deployed to the blockchain is solved, and the detection and protection of the vulnerability hidden danger of the smart contract development to the blockchain application are realized.
Owner:HANGZHOU QULIAN TECH CO LTD
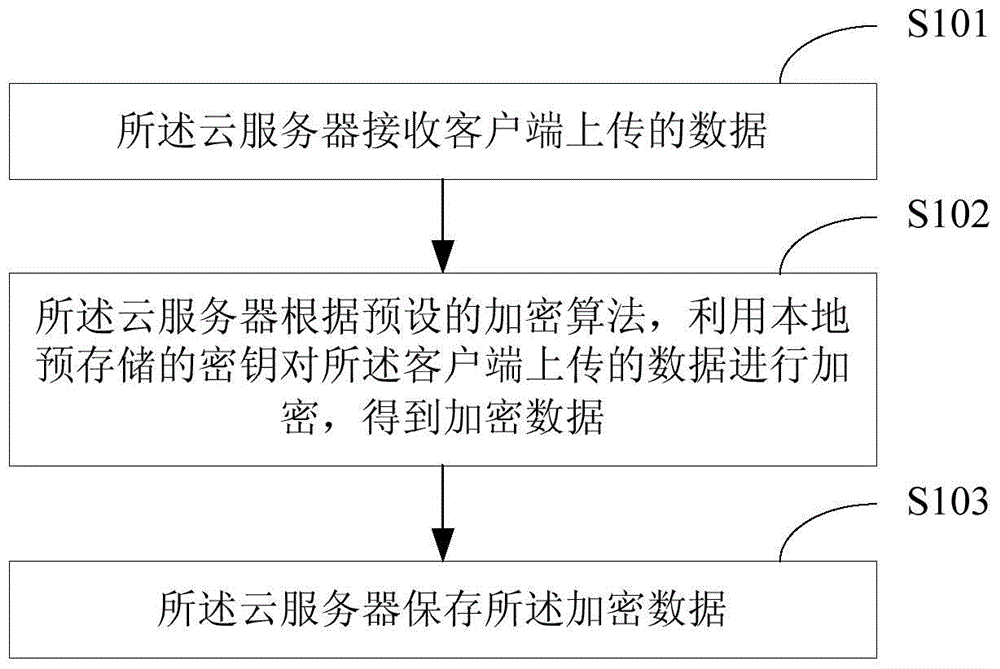
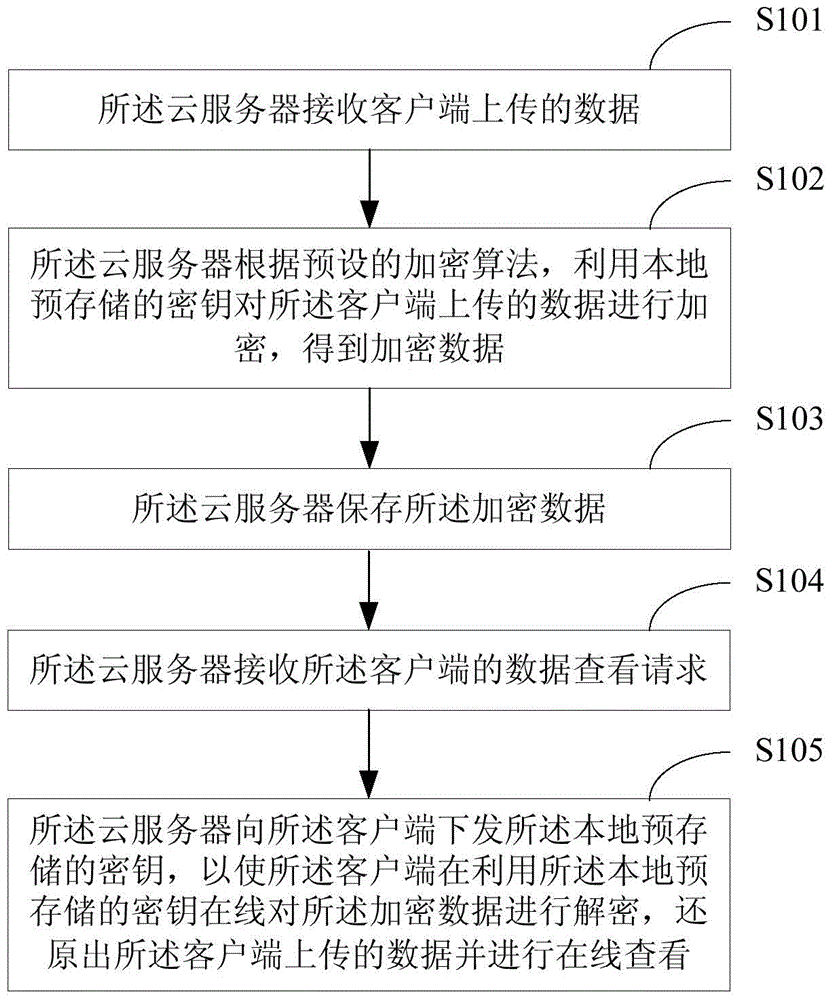
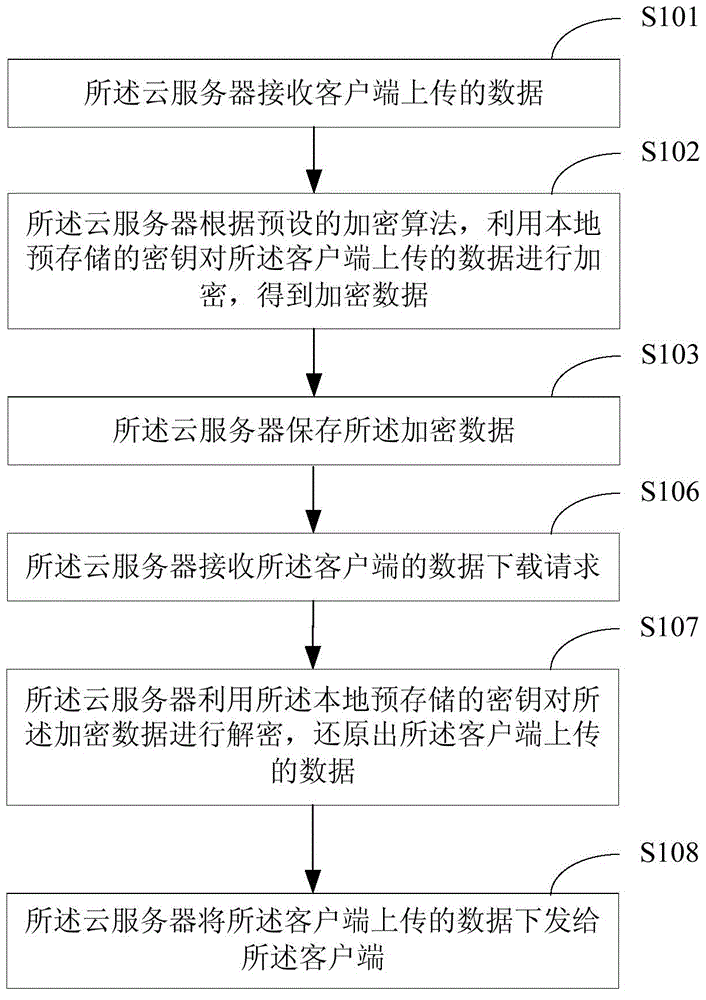
Method for protecting cloud storage data and cloud server
The invention relates to the technical field of information security and provides a method for protecting cloud storage data and a cloud server. The method comprises the steps that data uploaded by a client side are received by the cloud server; the data uploaded by the client side are encrypted by the cloud server through a locally-stored key according to a preset encryption algorithm, so that encrypted data are obtained; the encrypted data are stored by the cloud server. According to the method, in terms of the cloud storage data, the data are converted into a ciphertext from a plaintext by the cloud server and stored by the cloud server, so that even though the cloud storage data are leaked, the real data are difficult to obtain for a third party, the safety of the cloud storage data is guaranteed, and therefore the information safety of a cloud server user is guaranteed.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
Information hiding and protecting method based on image
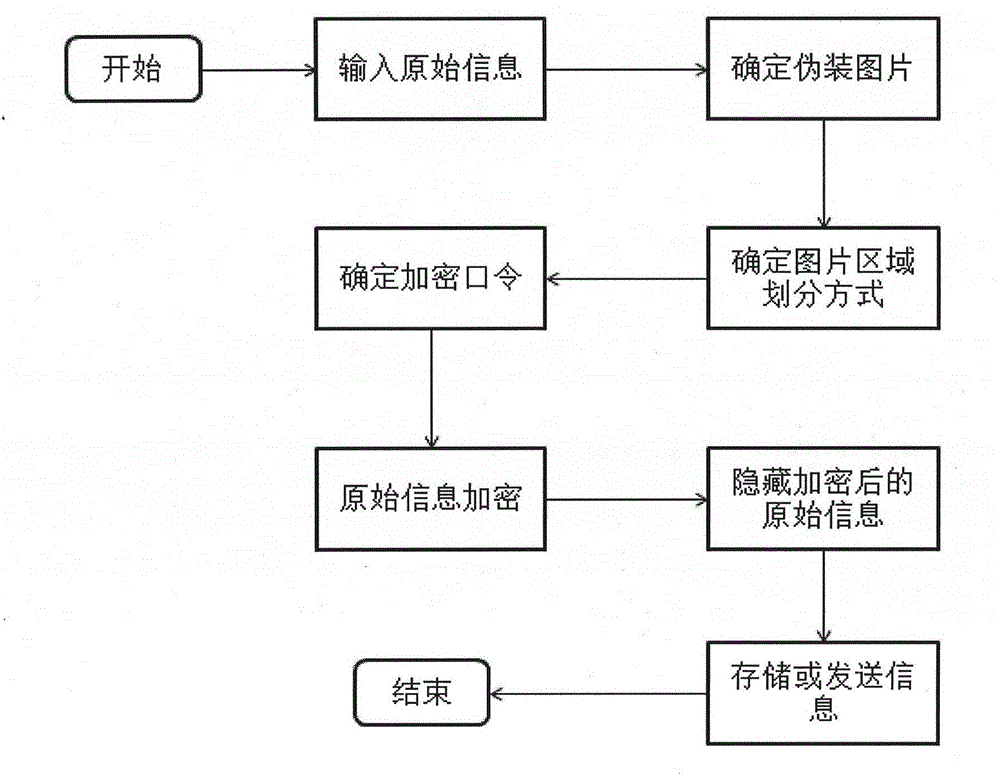
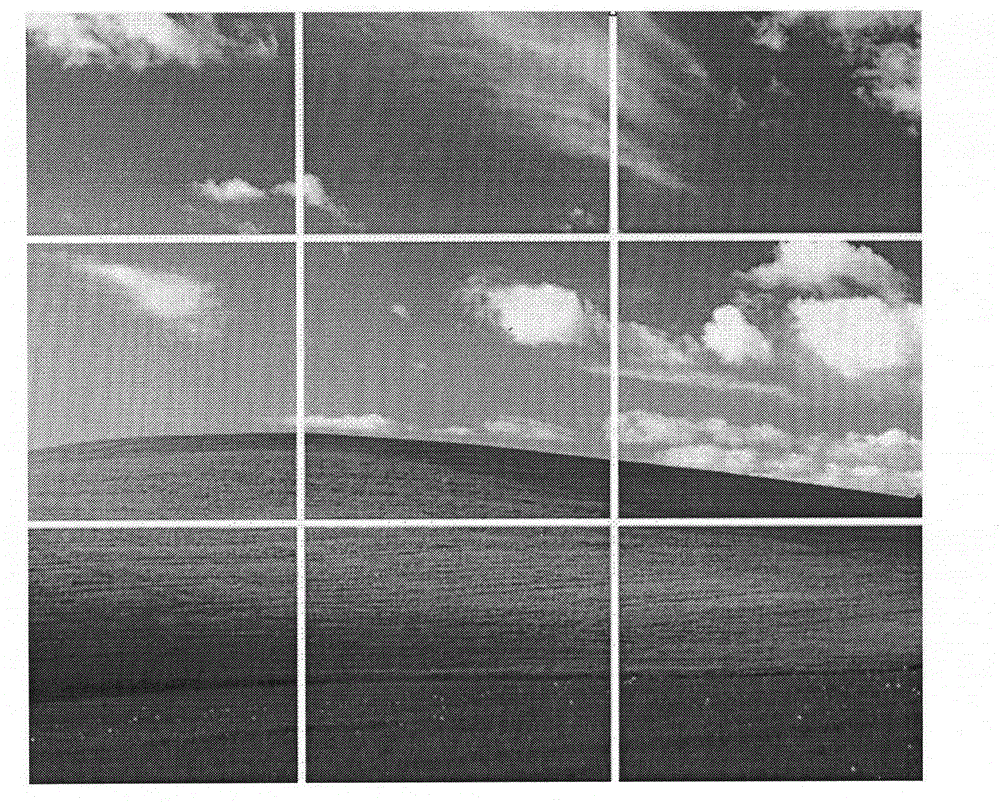
InactiveCN104134022ASecurityFlexible divisionProgram/content distribution protectionEncryptionInformation hiding
The invention provides an information hiding and protecting method based on an image and belongs to the technical field of computer applications. According to the information hiding and protecting method, original information to be transmitted is encrypted and hidden into an image, a user without a decryption password can only see the disguising image, and setting of an encryption password and a decryption password is completed by operations carried on the image; the operations carried on the image are composed of one behavior conducted on the area of the image by a user or multiple behaviors conducted on the area of the image by the user; during decryption, when the user inputs a correct decryption password, the coding data of the image are read, decrypted original information is extracted from the coding data, and the original information is displayed after the original information is decrypted through the decryption password. The information hiding and protecting method based on the image is high in safety and usability, capable of being applied to a mobile computing platform and a non-mobile computing platform and also capable of being applied to encrypted storage of local information and encrypted transmission or encrypted copying of information, and therefore the information safety of the user is effectively protected.
Owner:BEIJING DEEP AI INTELLIGENT TECH
Driving safety prompt method and driving recorder equipment
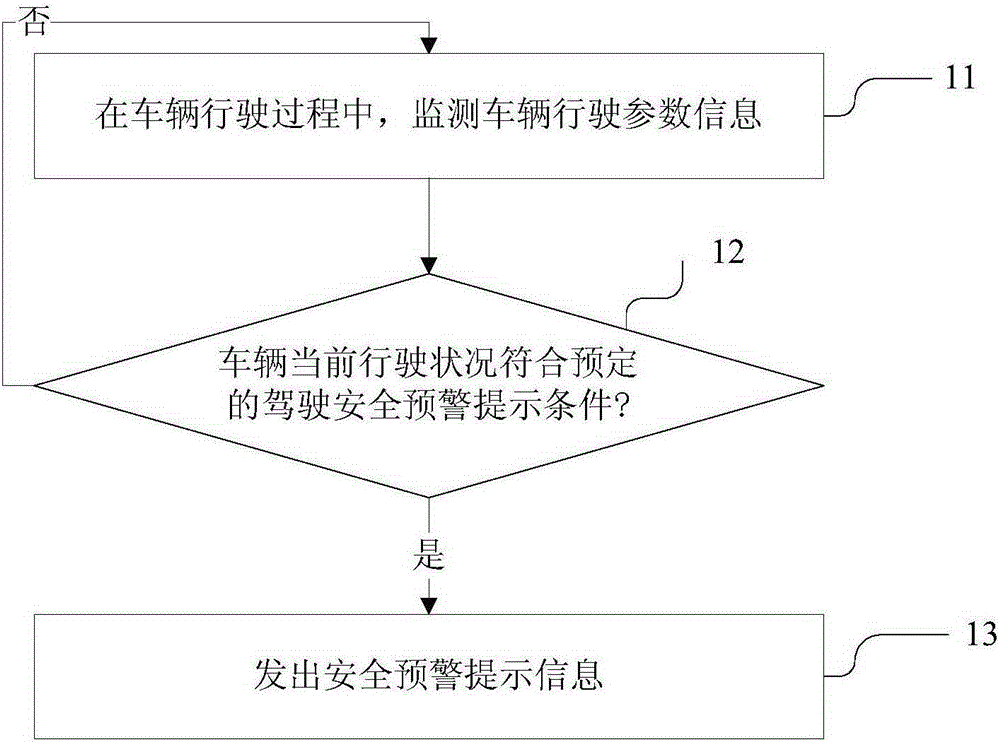
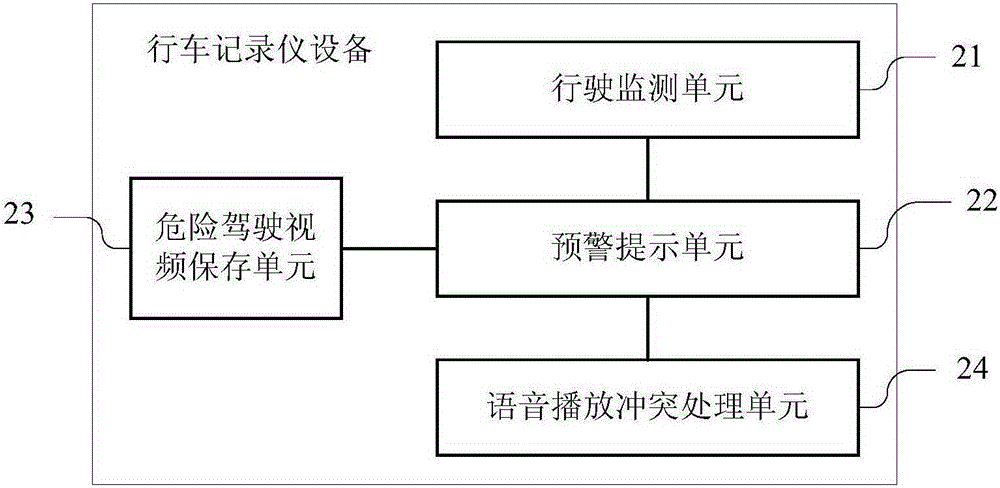
InactiveCN105303764ASecurityEnsure safetyRegistering/indicating working of vehiclesAlarmsDriving safetyRoad condition
The invention discloses a driving safety prompt method and driving recorder equipment. The driving safety prompt method comprises steps that, vehicle driving parameter information is monitored in a vehicle driving process; whether the present driving situation is in accordance with a predetermined safety driving early warning prompt condition is determined according to the driving parameter information, safety early warning prompt information is emitted. Through the driving safety prompt method, pertinent safety early warning prompt can be carried out in a vehicle driving process according to practical situations, early warning prompt can be emitted in the vehicle driving process according to driving and road situations, and thereby more safety guarantee is provided in a driving process for travelers.
Owner:SHENZHEN CARELAND TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com