Safety isolation method for cloud side multi-tenant data storage
A data storage and security isolation technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve tenants' unauthorized access, illegal viewing, hidden dangers of data leakage, etc., to solve unauthorized viewing and improve security performance, and the effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
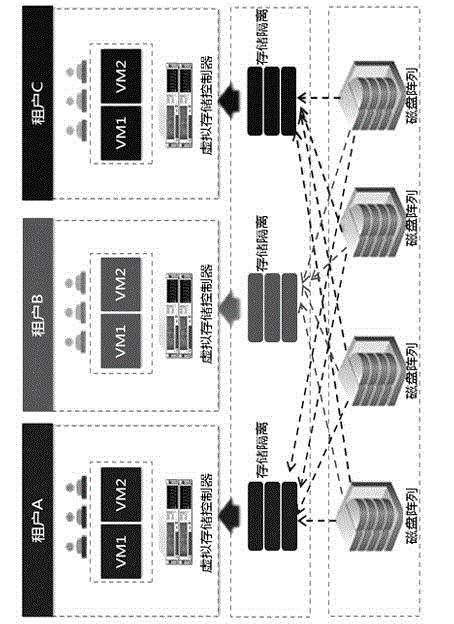
[0011] The cloud multi-tenant data storage security isolation method of the present invention will be described in detail below with reference to the accompanying drawings.
[0012] When cloud tenant A wants to access 1G data, first encrypt the private data through the key mechanism of the multi-tenant data storage To the cloud data center, the cloud storage software slices the data according to a specific algorithm. For example, if each slice is 128M in size, the data will be divided into 8 parts, and then the data will be transmitted to isolated spaces scattered in different physical locations. . When a tenant reads or queries data, after the cloud storage server passes the identity verification, the tenant completes operations such as querying, reading or deleting data through the virtual view provided by the distributed storage manager, and then the distributed storage manager passes through the virtual view provided by the device. record table, perform corresponding oper...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com