Information hiding and protecting method based on image
An information hiding and picture technology, applied in the field of picture-based information hiding and protection, can solve the problems of unfriendly user interaction, poor information camouflage and concealment, single form, etc. The effect of strong confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
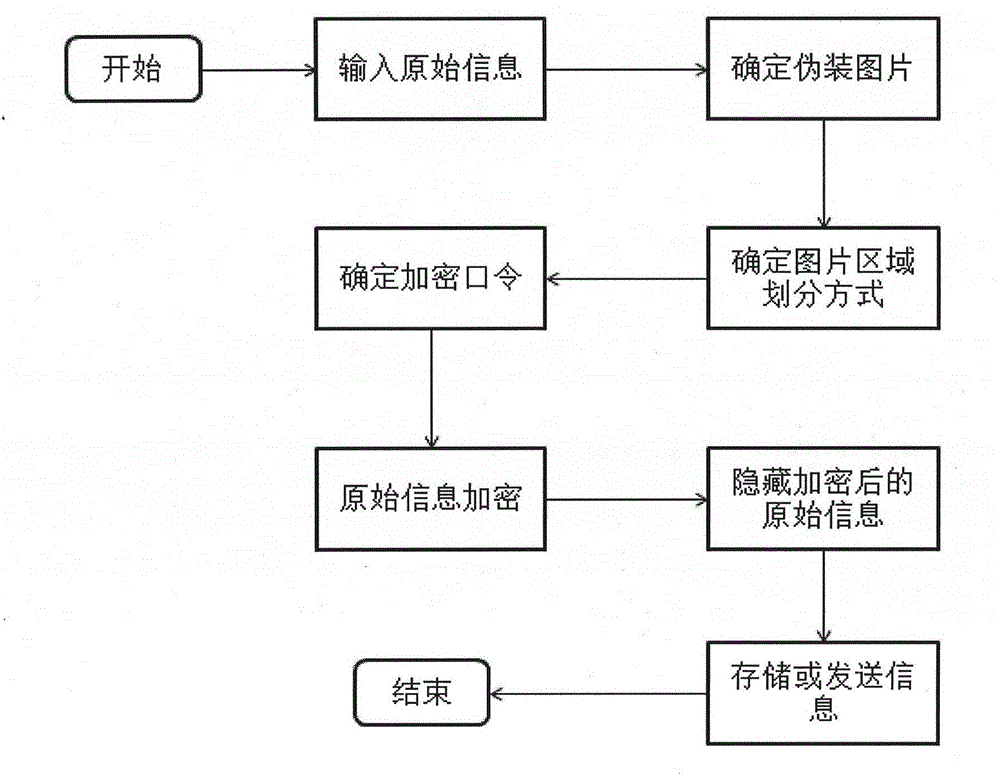
[0045] The information hiding and protection method proposed by the present invention is applied to mobile computing devices represented by smart phones. The following is an example where the user wishes to hide and protect the text message "HelloWorld" on the mobile phone. Information hiding process such as figure 1 shown.
[0046] The information encryption process is as follows:
[0047] Step 1: Input the original information, for example, the user enters the text information "HelloWorld";
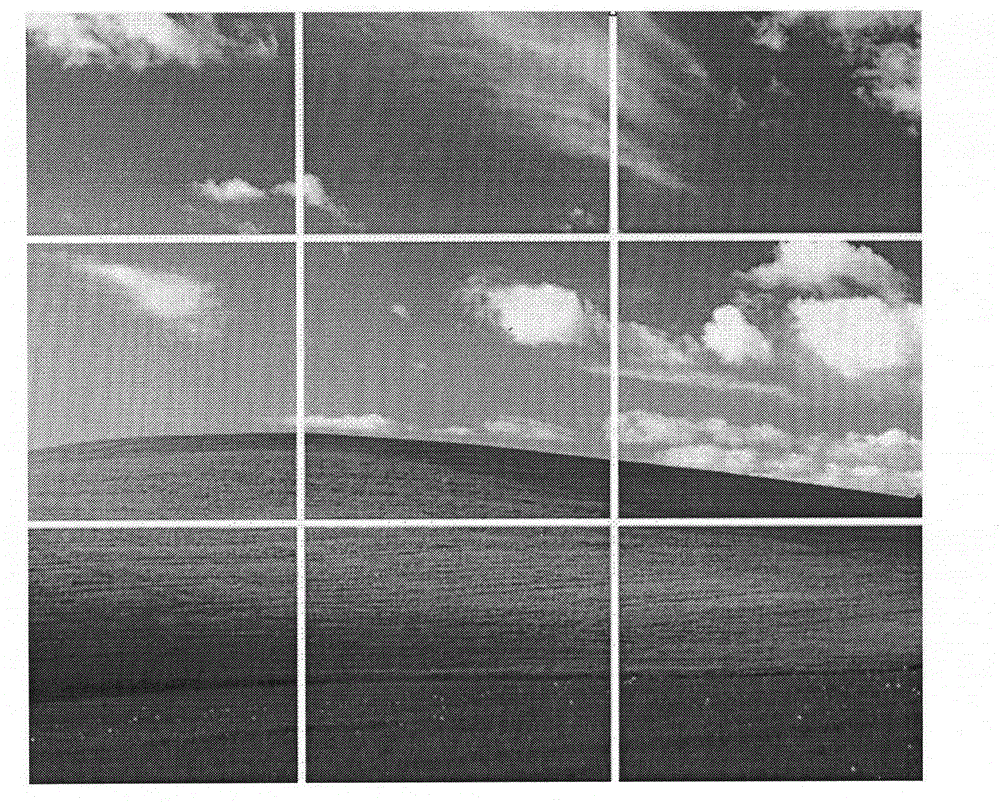
[0048] Step 2: Select an existing image as a camouflage image, for example, the user selects a landscape image as a camouflage image, such as figure 2 shown;
[0049] Step 3: Divide the image area, for example, the user selects the nine-square grid to divide the camouflage picture, such as image 3 shown. Among them, the display of the dividing line is only for the convenience of operation, and will not be used as an integral part of the image;
[0050] Step 4: Determine the enc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com