Consortium chain permission control method based on digital certificates and CA authentication system
A digital certificate and CA certification technology, applied in digital transmission systems, user identity/authority verification, transmission systems, etc., can solve the problems of large granularity of blockchain authority and no access function, to solve authority control and satisfy privacy needs, and the effect of meeting the safety requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
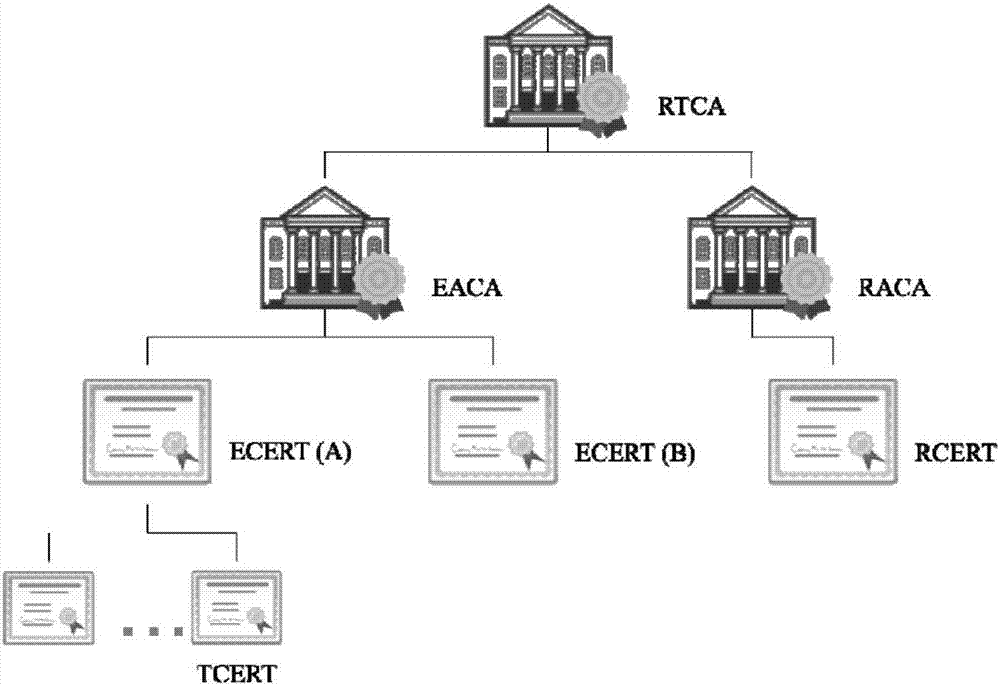
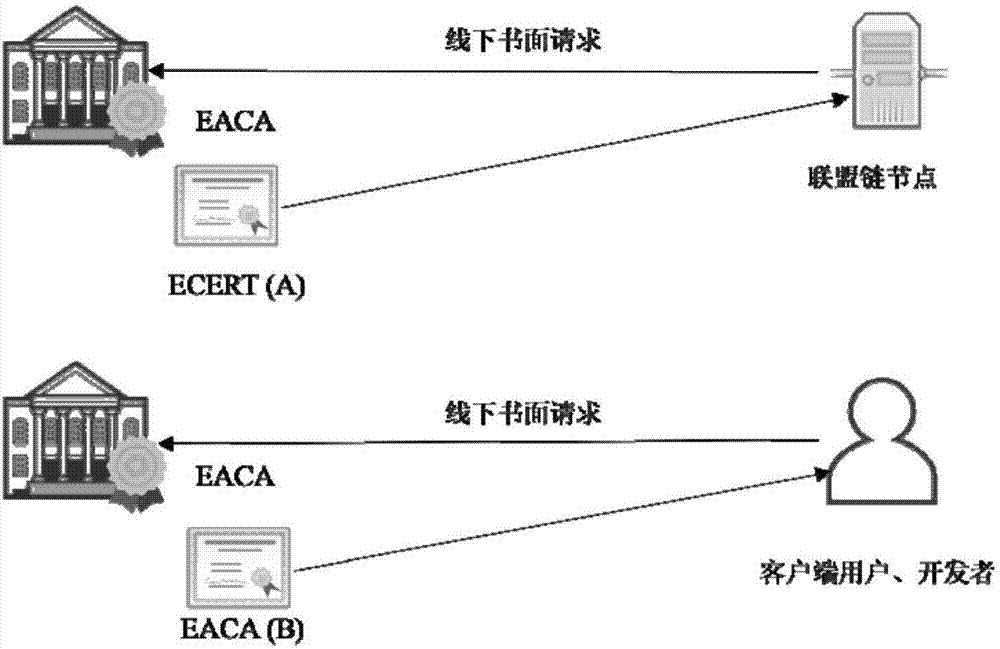
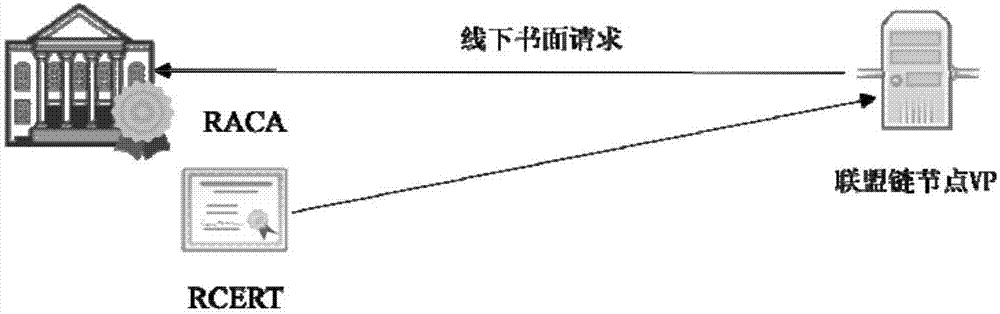
[0050] The alliance chain verification node applies to EACA for the corresponding ECERT through an offline written request, such as figure 2 As shown, after obtaining the ECERT, apply for the corresponding RCERT to RACA through an offline written request, such as image 3 shown. Assume that the alliance chain has four nodes ABCD, each of which obtains the corresponding ECERT and RCERT through offline channels, and then ABCD establishes a P2P connection with each other, and at the same time verifies the legitimacy of the sent ECERT and RCERT, such as Figure 4 shown.
[0051] At this time, if there is a new non-verification node E that needs to join, node E will provide ECERT to the VP node to prove that it has permission to access the alliance chain, but cannot provide RCERT. At the same time, verification node A will provide ECERT to non-verification node E and RCERT to prove the identity of its verification node, such as Figure 5 shown.
[0052] If the client needs to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com