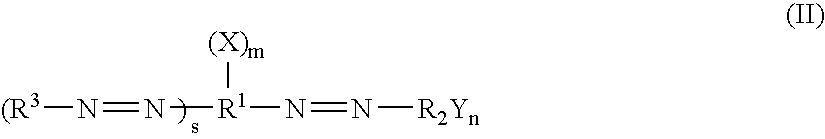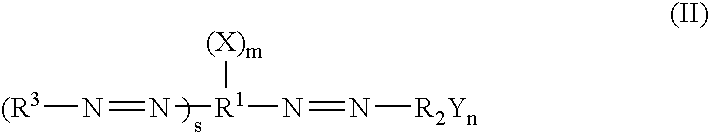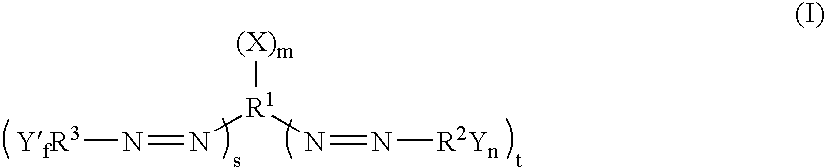Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
283 results about "Black hole" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A black hole is a region of spacetime exhibiting gravitational acceleration so strong that nothing—no particles or even electromagnetic radiation such as light—can escape from it. The theory of general relativity predicts that a sufficiently compact mass can deform spacetime to form a black hole. The boundary of the region from which no escape is possible is called the event horizon. Although the event horizon has an enormous effect on the fate and circumstances of an object crossing it, no locally detectable features appear to be observed. In many ways, a black hole acts like an ideal black body, as it reflects no light. Moreover, quantum field theory in curved spacetime predicts that event horizons emit Hawking radiation, with the same spectrum as a black body of a temperature inversely proportional to its mass. This temperature is on the order of billionths of a kelvin for black holes of stellar mass, making it essentially impossible to observe.
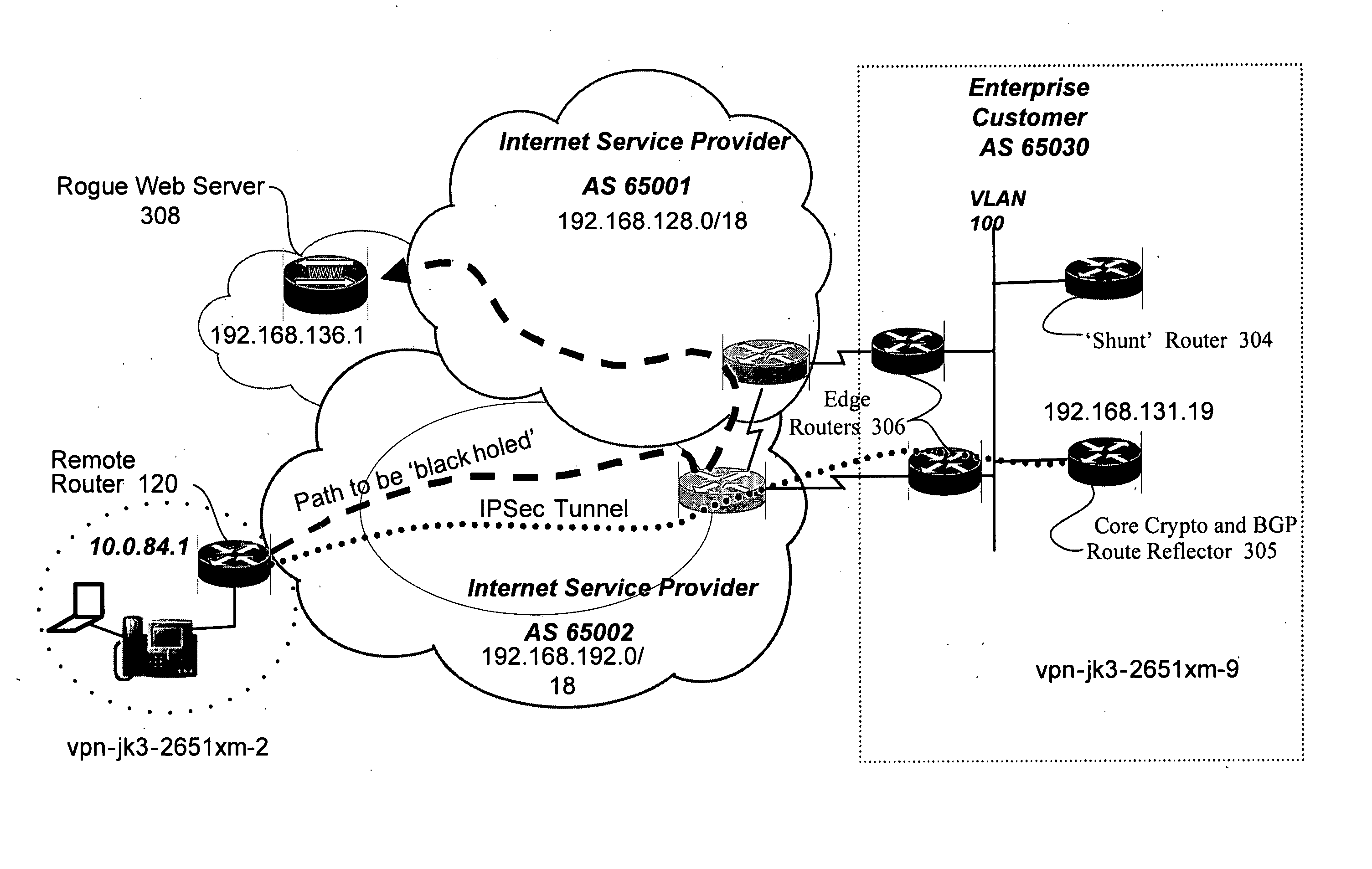
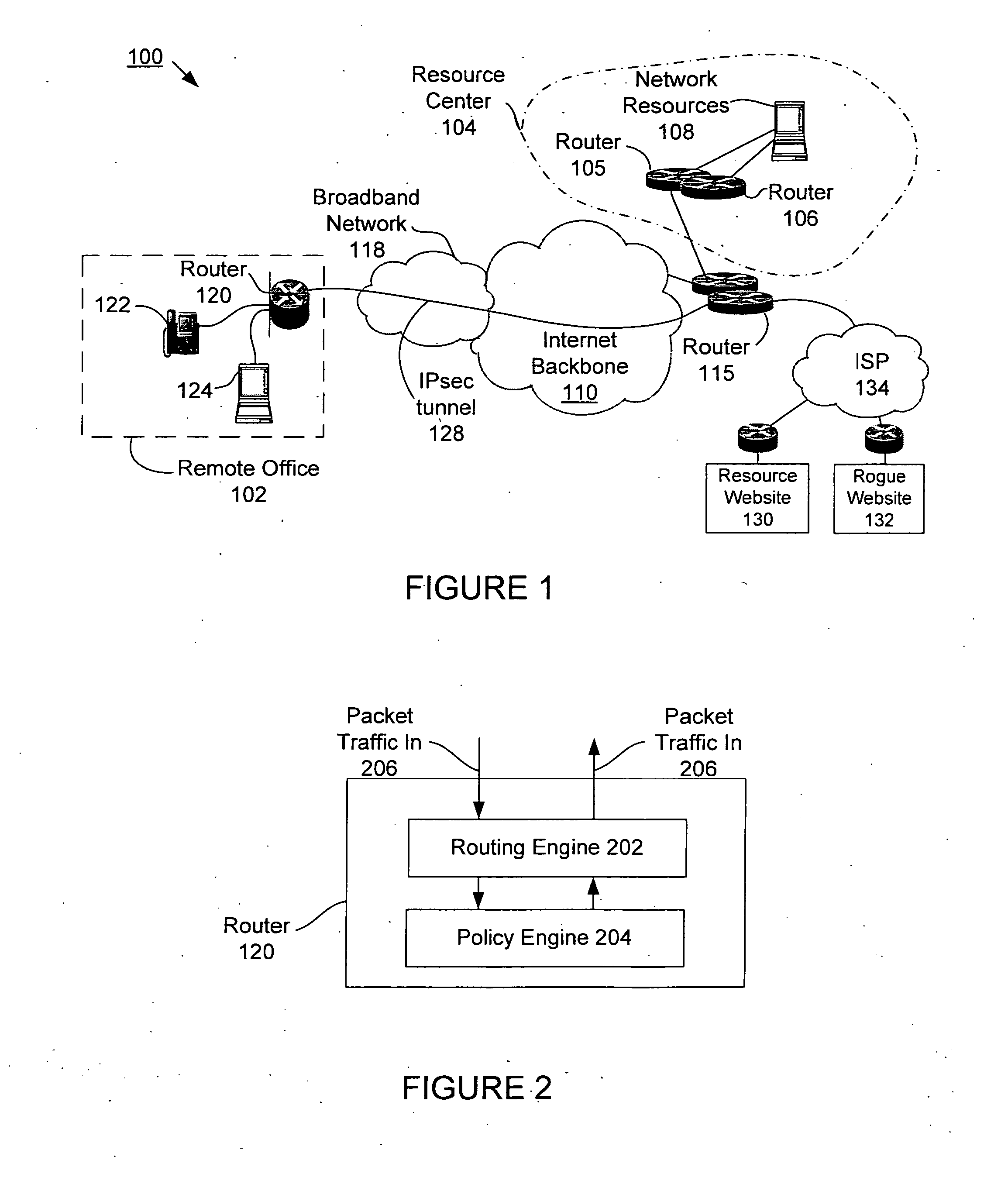
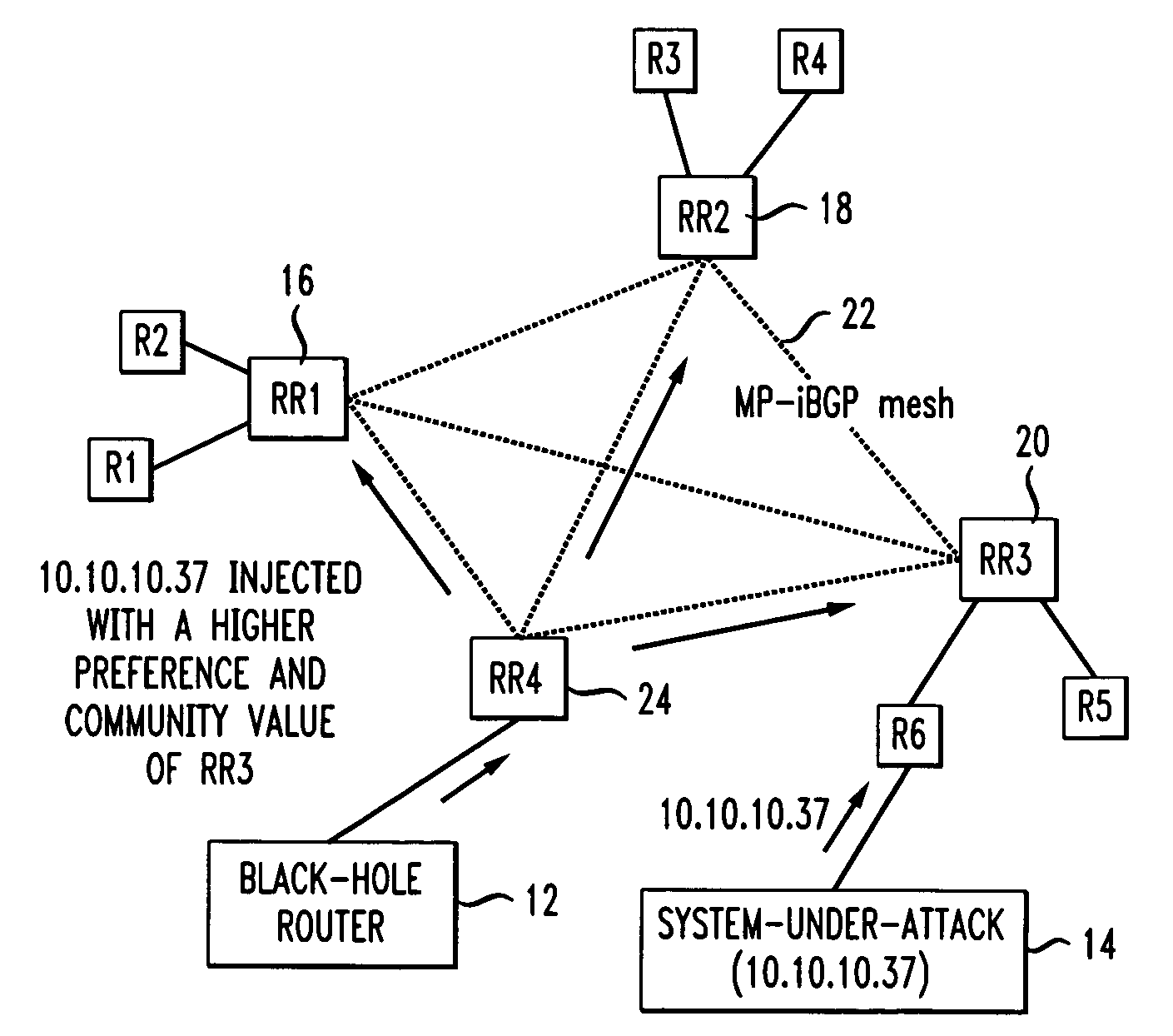
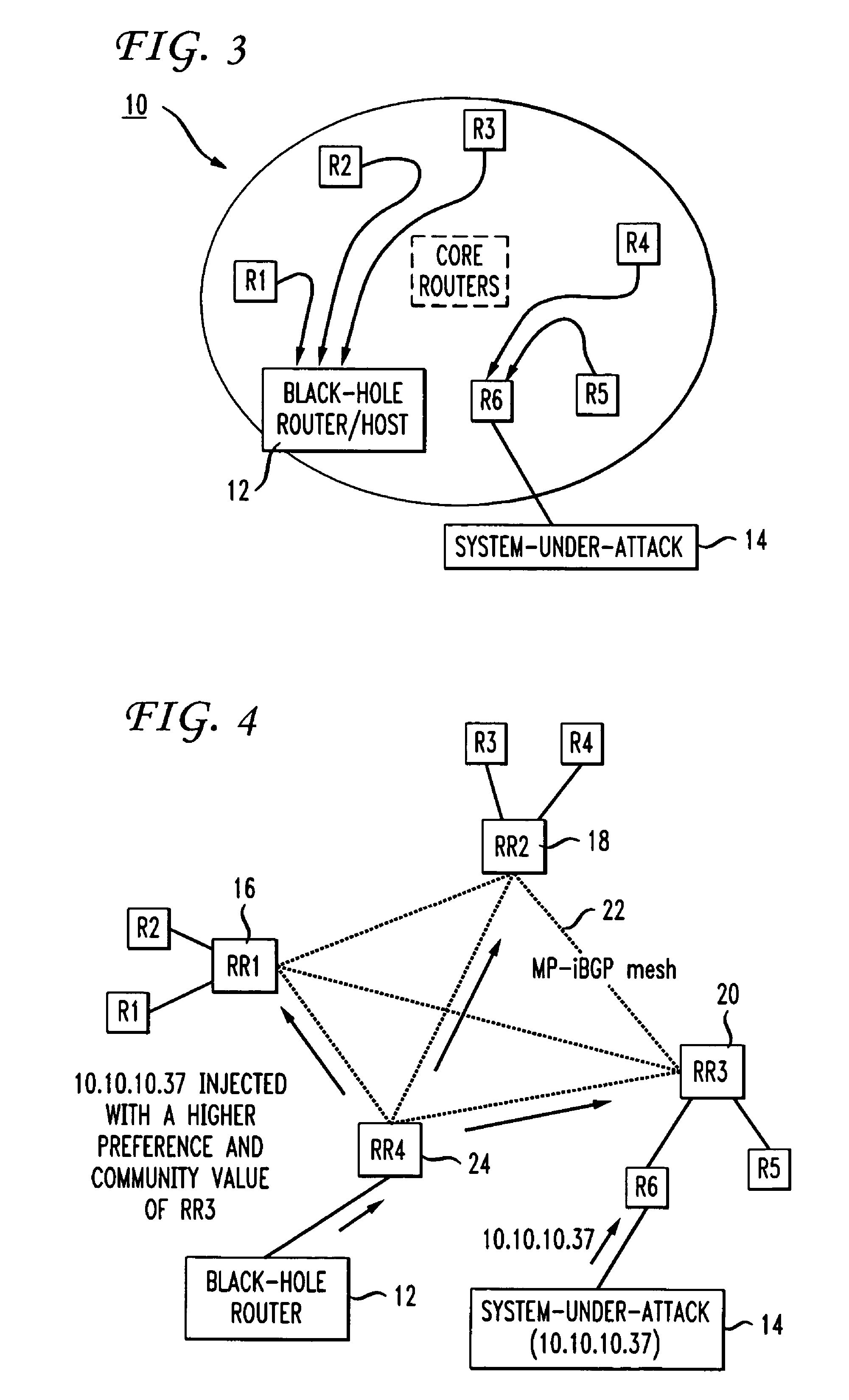
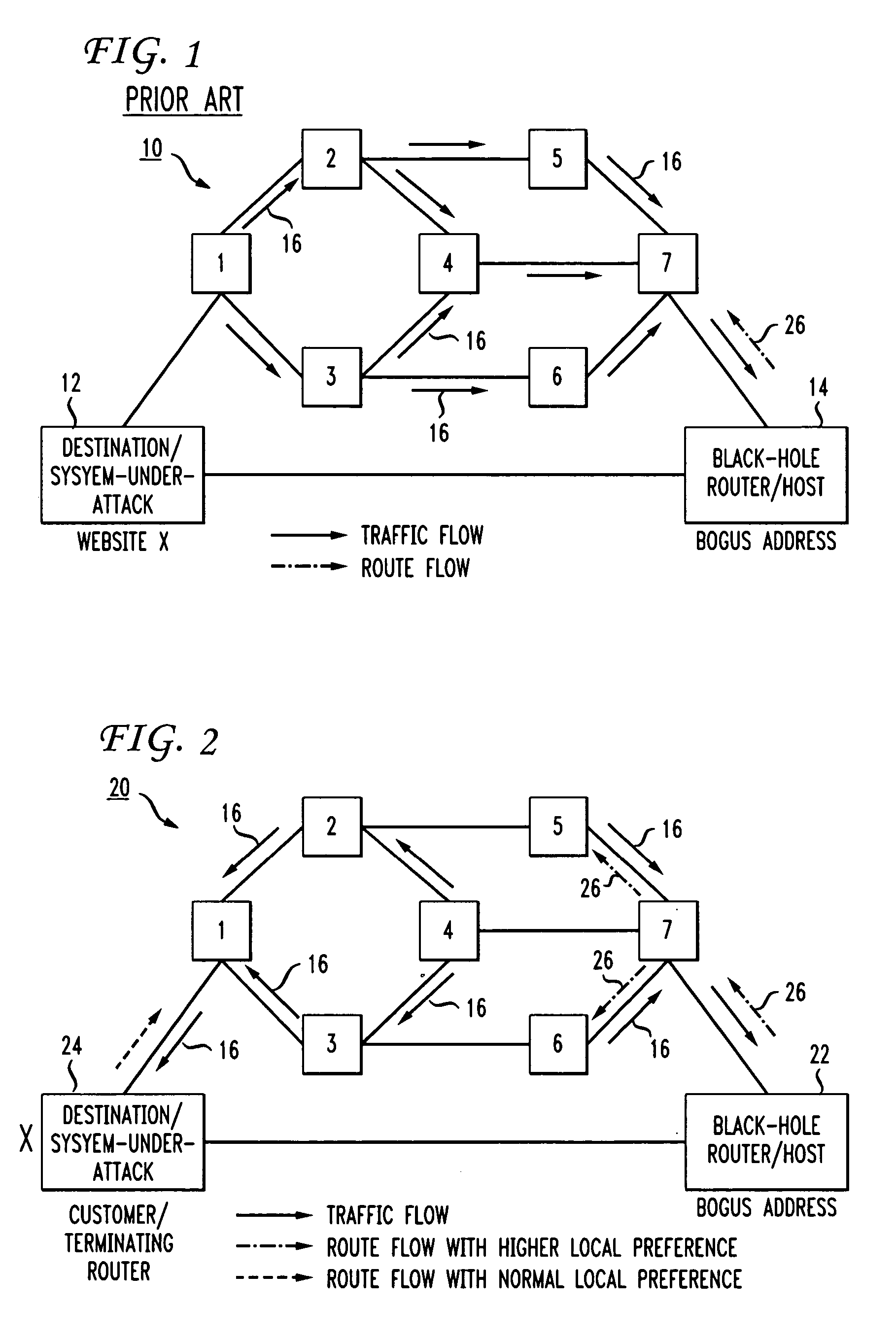
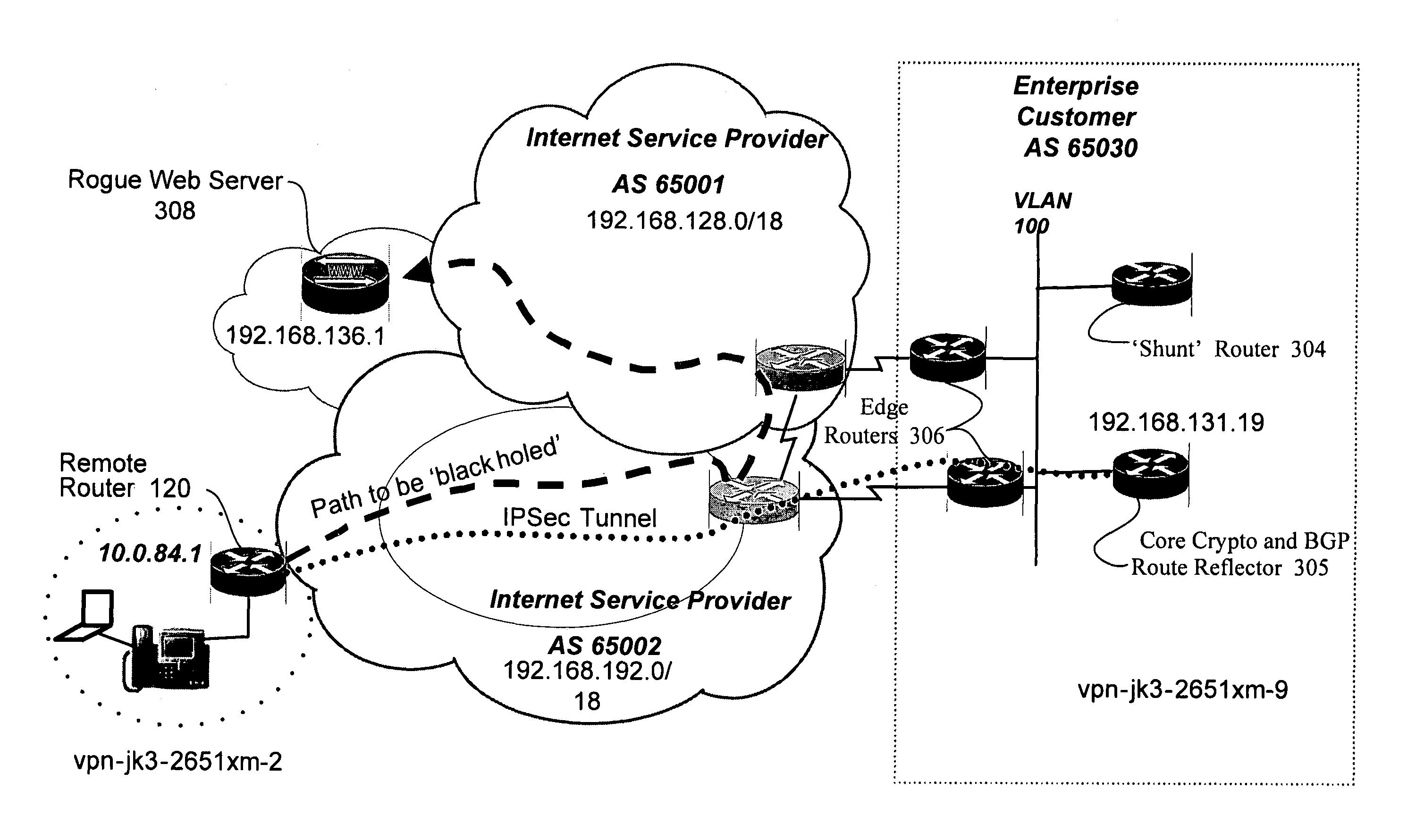
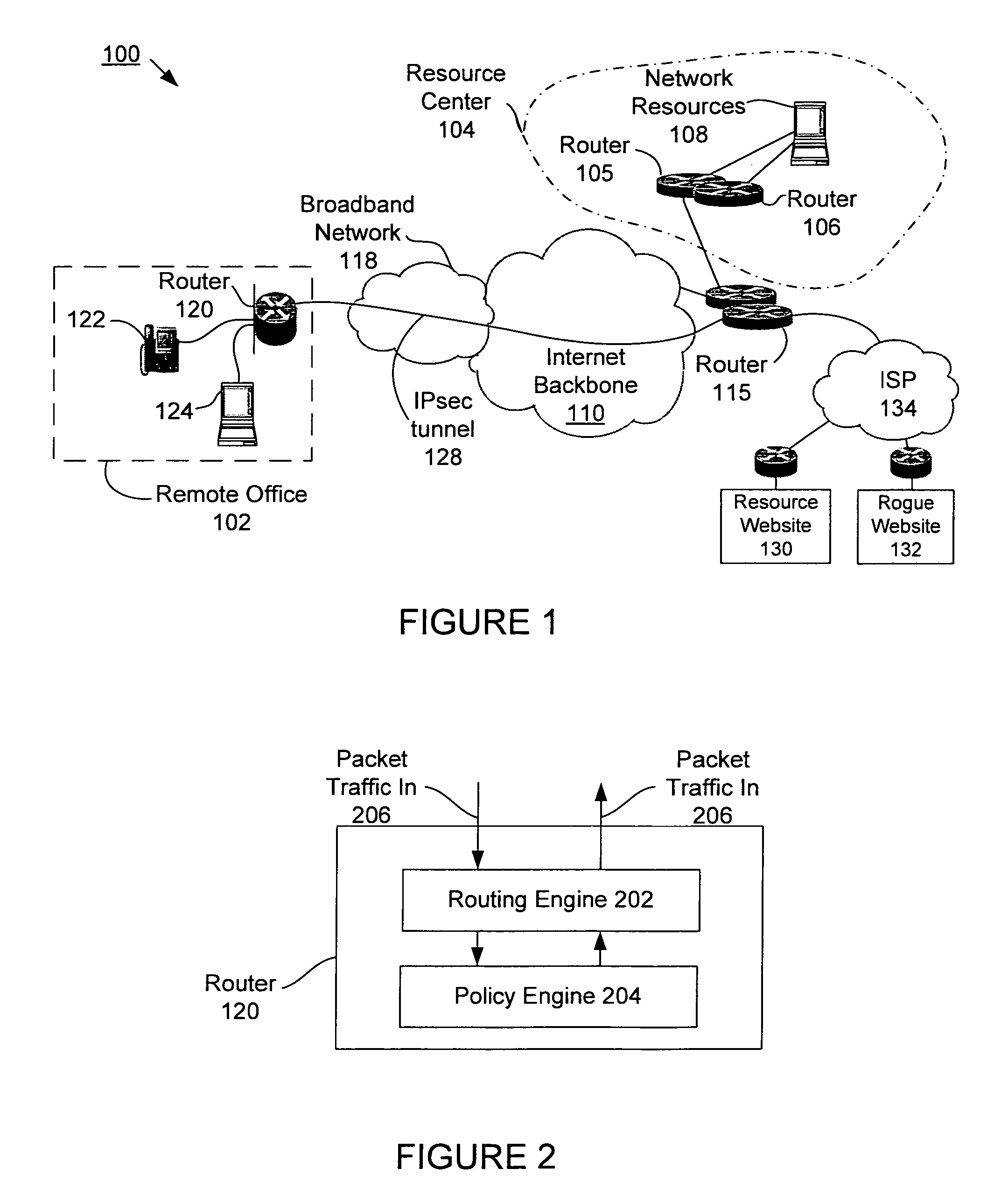
Propagating black hole shunts to remote routers with split tunnel and IPSec direct encapsulation
Remote routers are configured to block the return path to malicious websites with the use of split tunneling while allowing paths to third party resource websites. The iBGP protocol runs on the agent's router, advertises routes and enables the head-end to set up a policy at each remote router. Enterprise policies for blocking access to “blackholed” website addresses are centrally administered but third party website traffic is not routed to the enterprise's network resources. Since remote offices may connect directly to third party websites, latency is minimized and network resources at the enterprise are not unduly burdened.
Owner:CISCO TECH INC
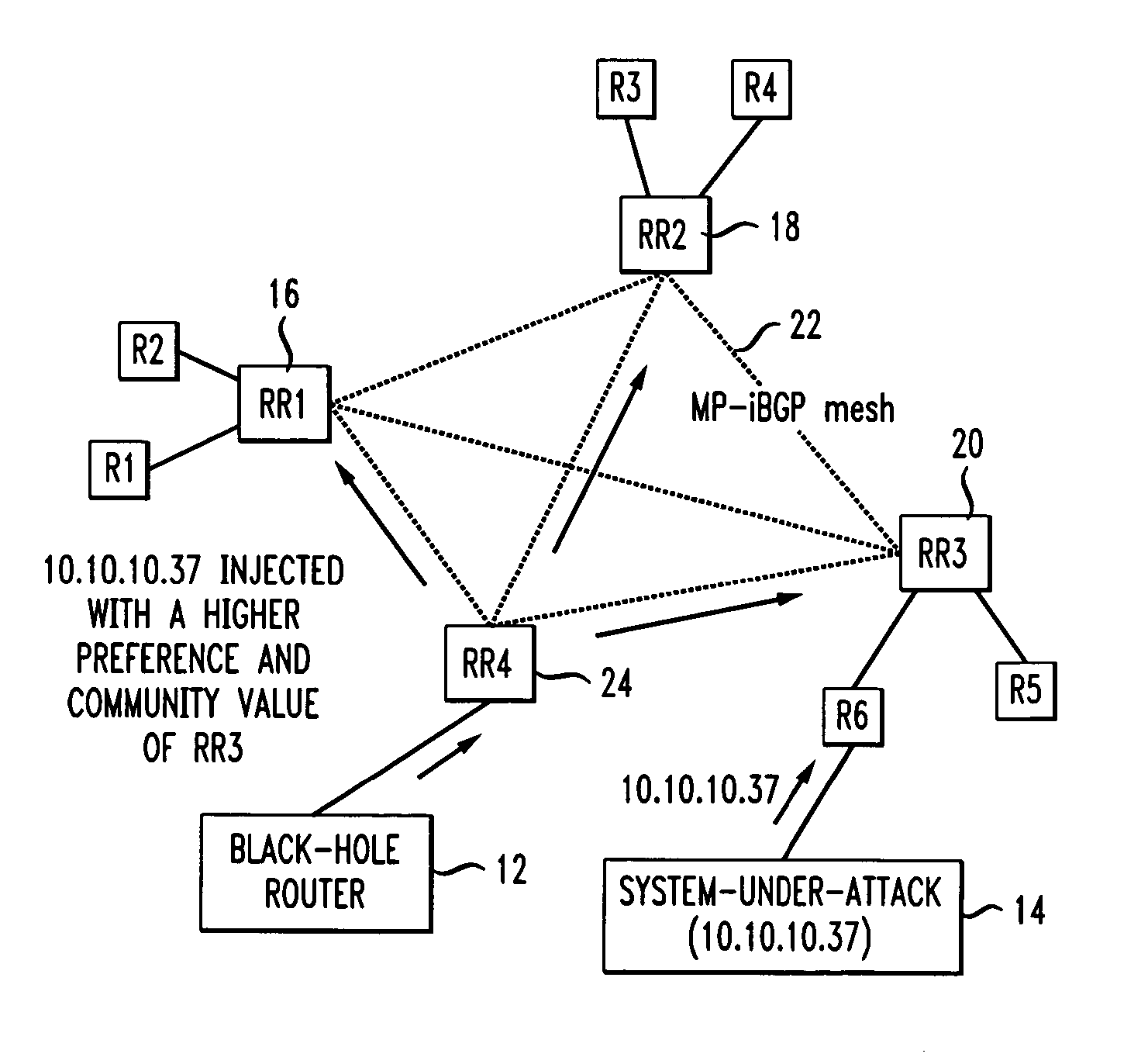
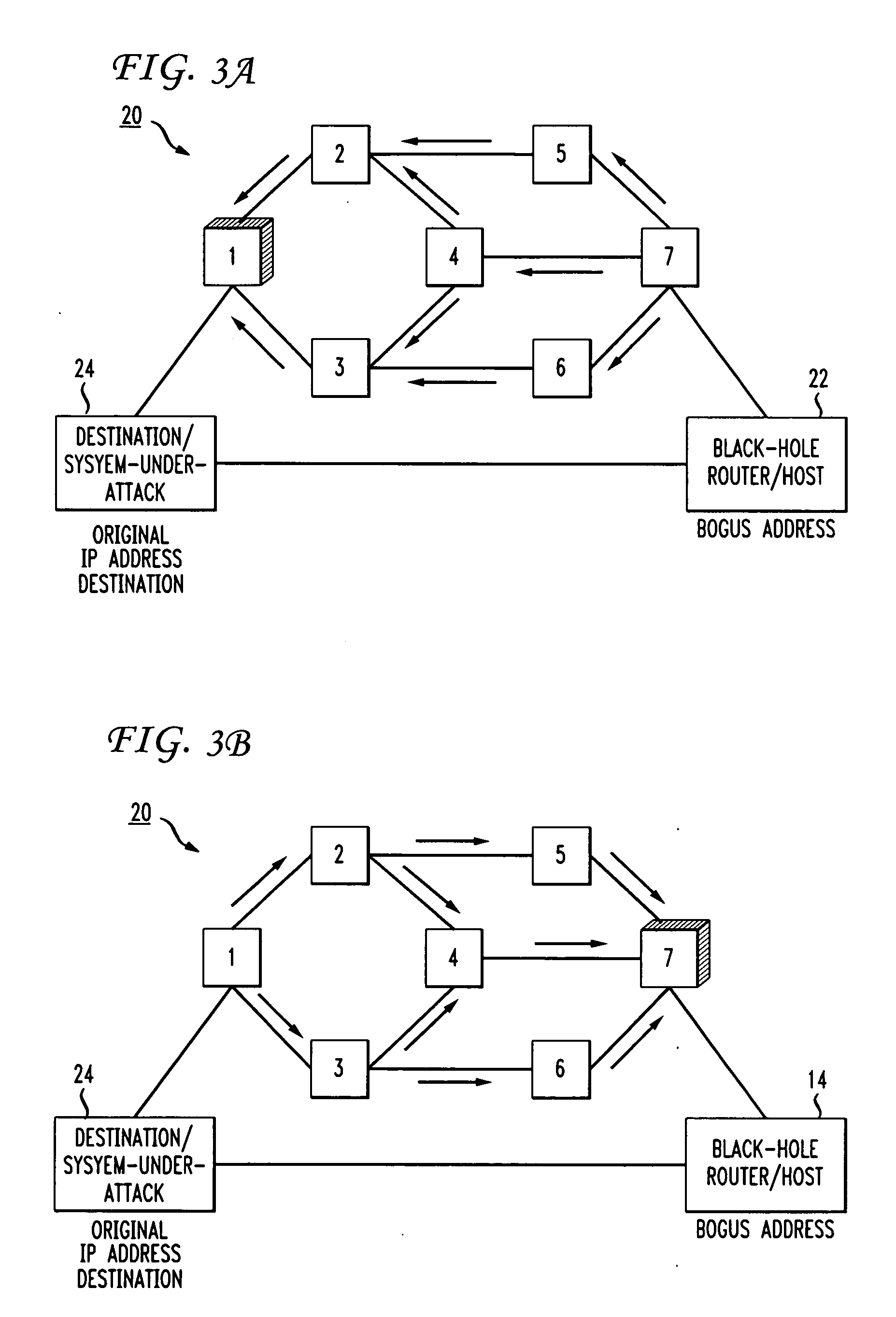
Method for distributed denial-of-service attack mitigation by selective black-holing in MPLS VPNS
ActiveUS20050180416A1Data switching by path configurationComputer security arrangementsEntry pointBlack hole
A system and method for aiding the handling of DDoS attacks in which VPN traffic entering an ISP network at some points will be black-holed, while VPN traffic entering the ISP network at other points will be routed, as it should be, to the system-under-attack. Thus, the system-under-attack is made available to some of the user community and made unavailable to suspect portions of the user community. Furthermore, the number of entry points where black-holing of VPN traffic occurs can be selected and changed in real-time during a DDoS attack.
Owner:AT&T INTPROP I L P
Dark quenchers for donor-acceptor energy transfer
InactiveUS7019129B1Minimize fluorescenceEnhanced interactionBioreactor/fermenter combinationsBiological substance pretreatmentsEnergy transferExcited state
Owner:HSBC TRUSTEE COMPANY UK LIMITED AS SECURITY AGENT
Dark quenchers for donor-acceptor energy transfer
InactiveUS20050272088A1Minimize fluorescenceEnhanced interactionAnthraquinone-azo dyesMonoazo dyesEnergy transferExcited state
The present invention provides a family of dark quenchers, termed Black Hole Quenchers (“BHQs”), that are efficient quenchers of excited state energy but which are themselves substantially non-fluorescent. Also provided are methods of using the BHQs, probes incorporating the BHQs and methods of using the probes.
Owner:HSBC TRUSTEE COMPANY UK LIMITED AS SECURITY AGENT
Optical system for barcode scanner
InactiveUS20070205287A1Visual representatino by photographic printingSensing by electromagnetic radiationSensor arraySlant angle
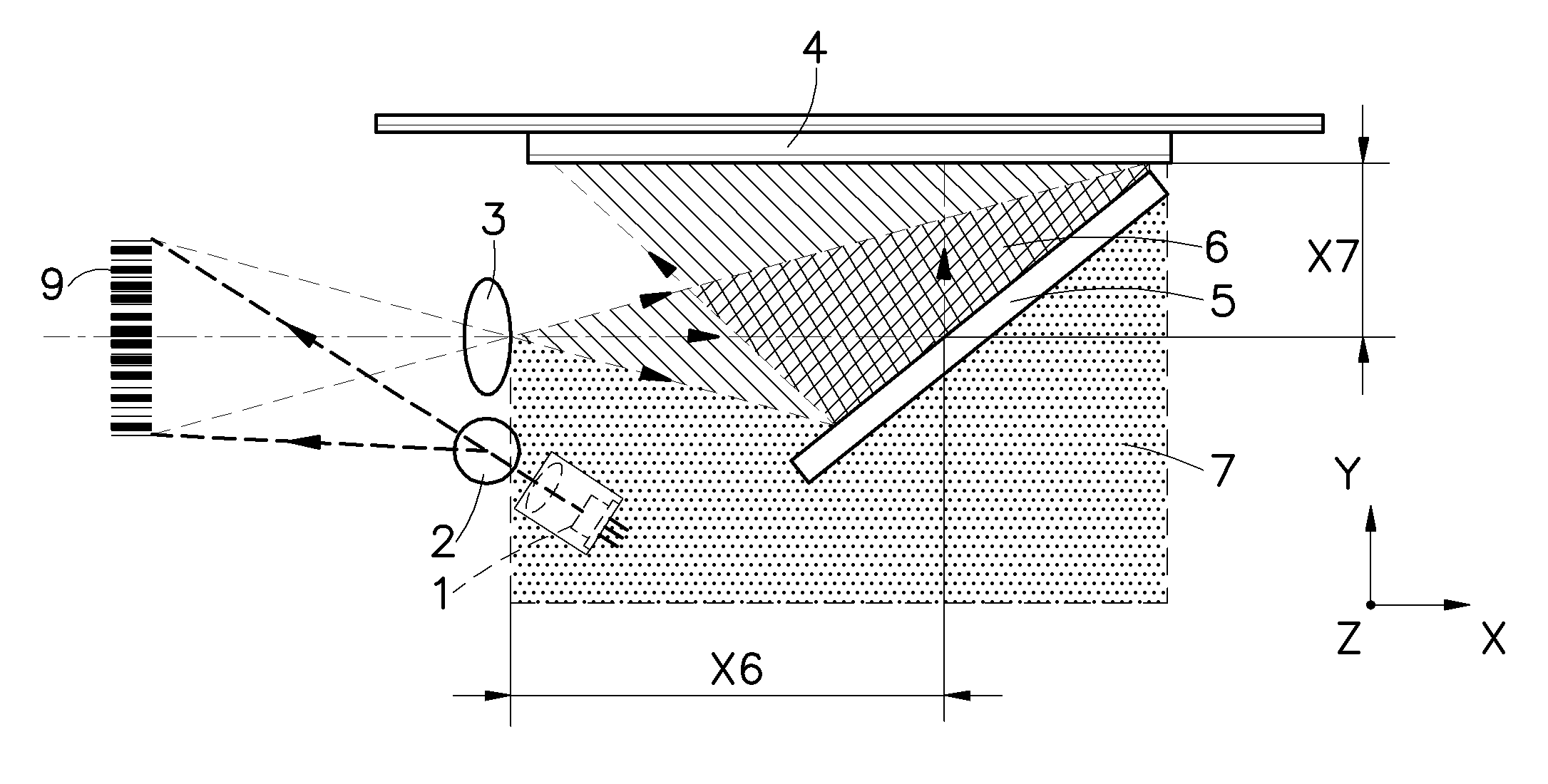
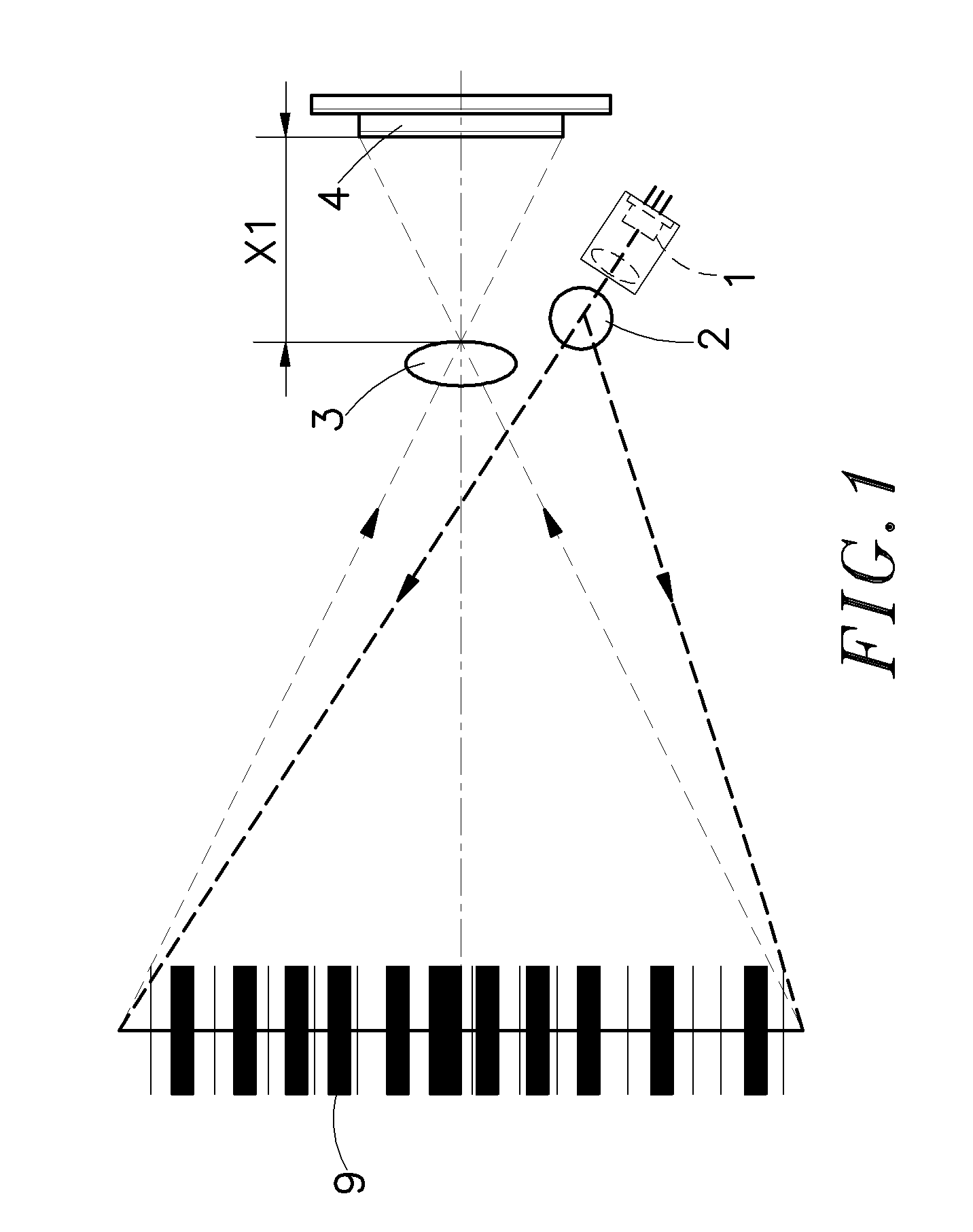
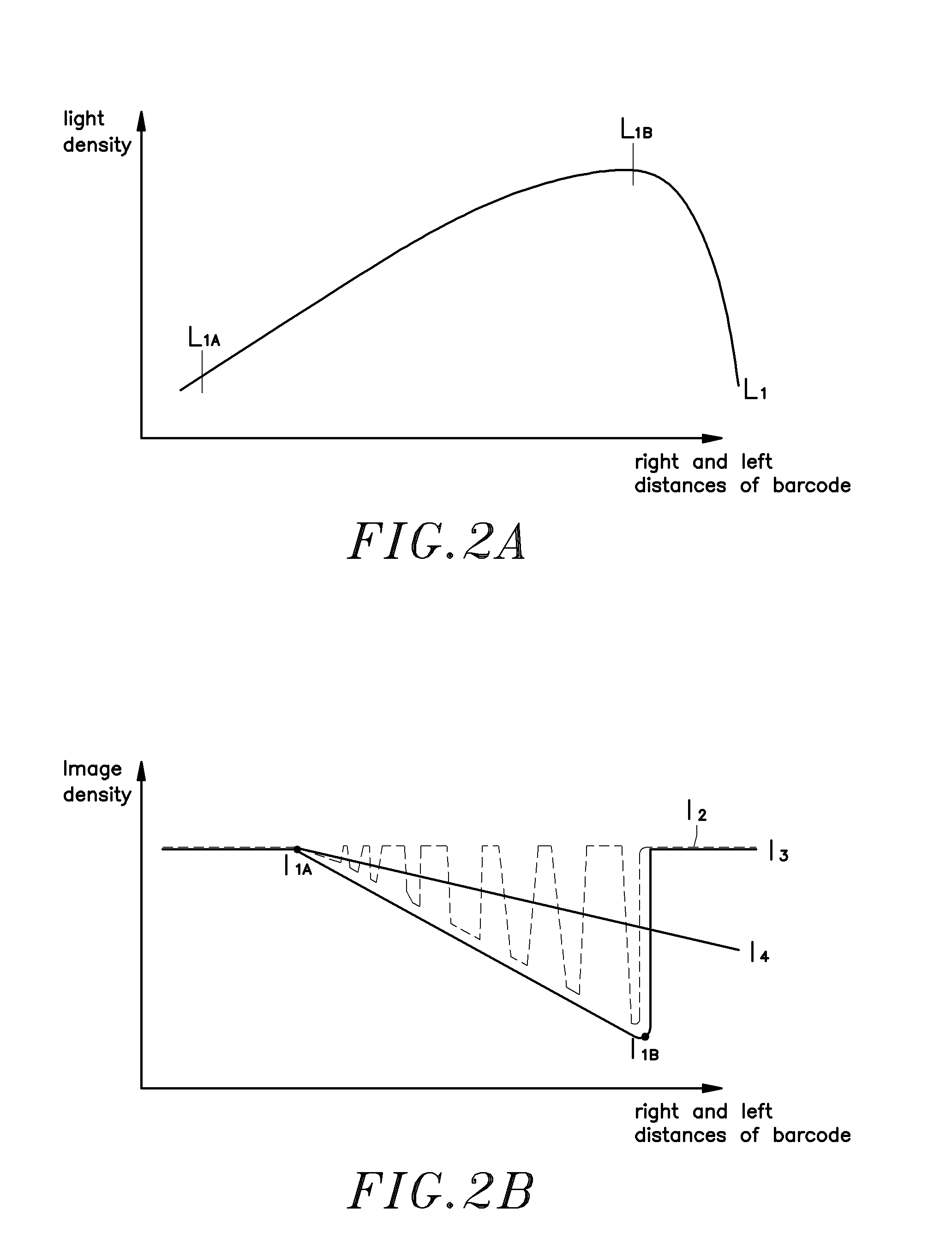
An optical system used in a barcode scanner is disclosed to include a light source for emitting a dot-shaped light beam in a slanting angle, a standing cylindrical lens for expanding the dot-shaped light beam produced by the light source as a line-shaped light beam onto a barcode of a product in a slanting angle, which line-shaped light beam showing a light intensity distribution curve that is asymmetric between the left side and the right side, a linear sensor array, and a focusing lens for focusing a reflective image of the barcode onto the linear sensor array. A reflector means can be provided for overlapping the light path to reduce the size of the barcode scanner. Further, a shaking means may be used to cause reciprocation of the light beam in direction perpendicular to the light path of the light source, thereby eliminating image noises due to existence of black holes.
Owner:RIOTEC
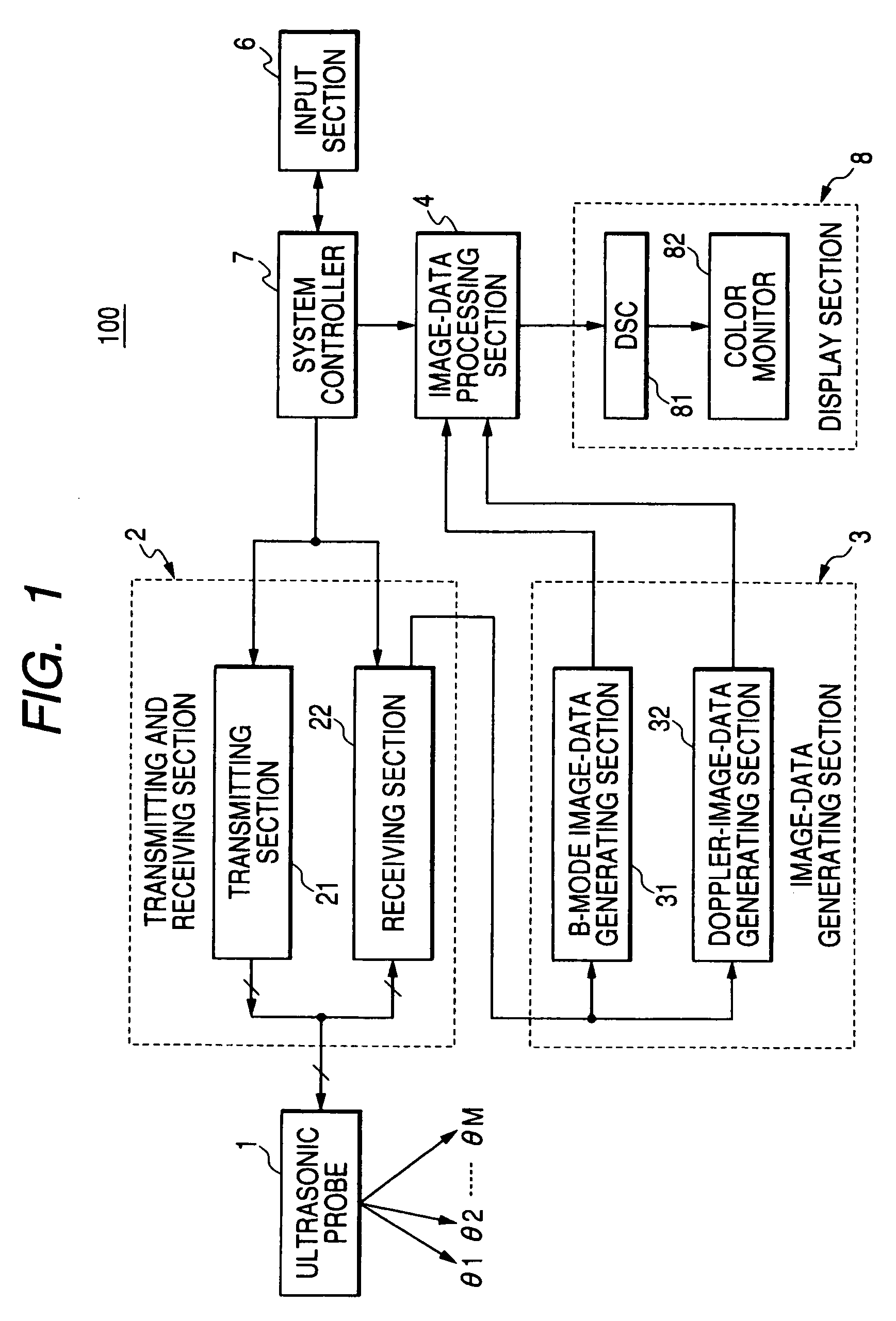
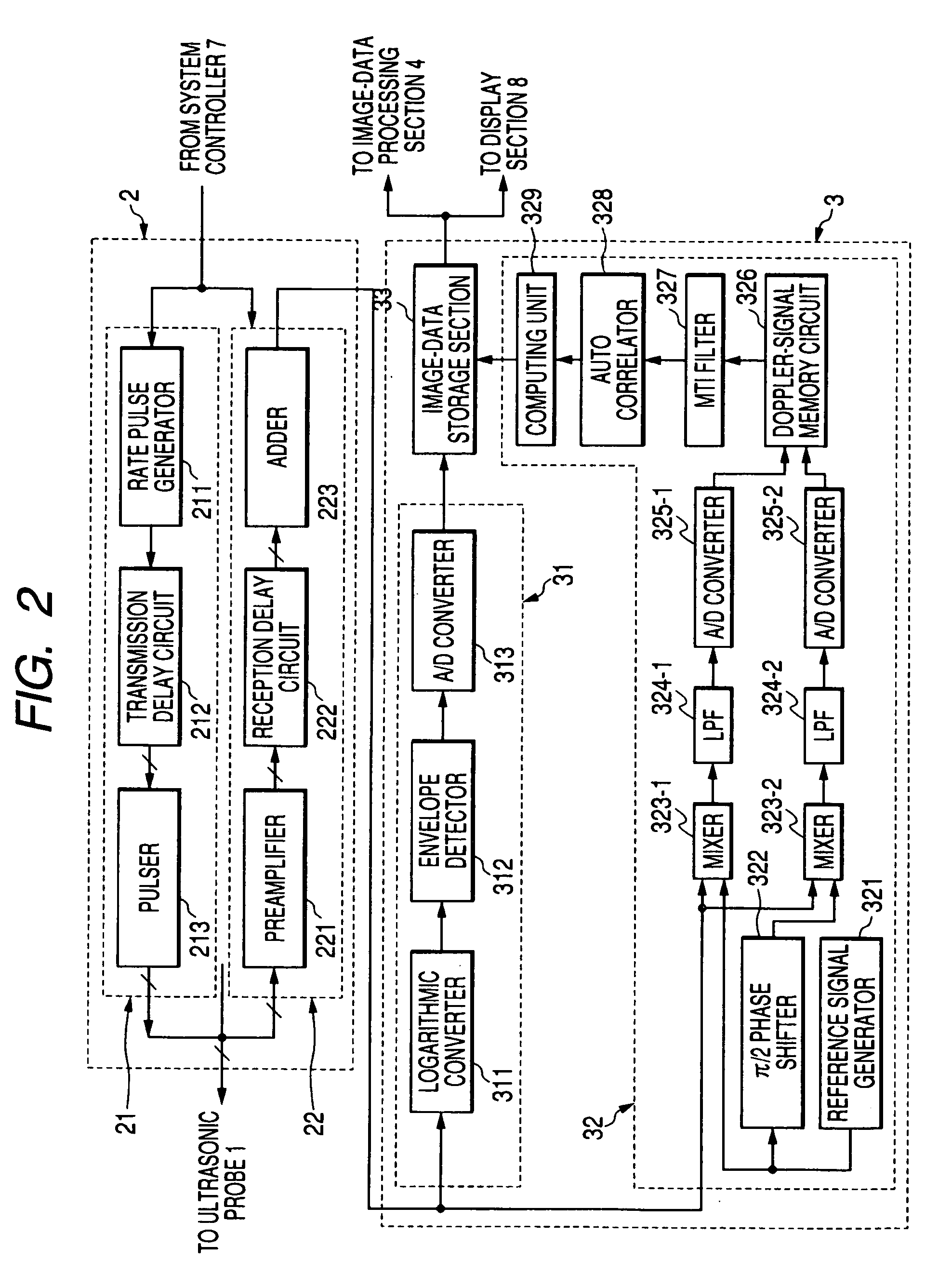
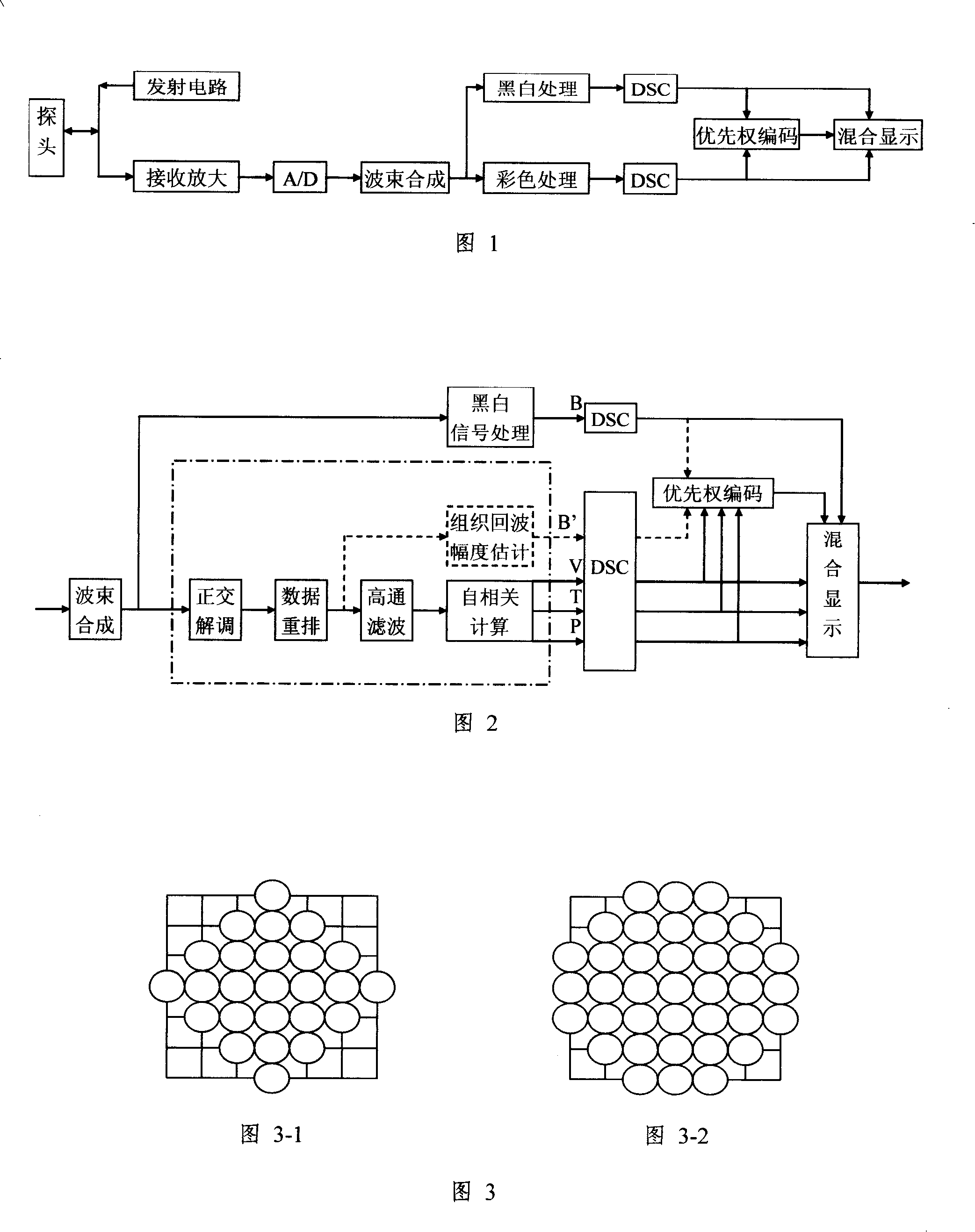
Image data processing method and apparatus for ultrasonic diagnostic apparatus, and image processing apparatus
InactiveUS20050215897A1Reducing black hole patternsImage enhancementMaterial analysis using sonic/ultrasonic/infrasonic wavesColor dopplerImaging processing
The ultrasonic diagnostic system according to the present invention includes a kernel-data generating section for extracting first image data in a specified range set with reference to a specified pixel of a generated image data to generate kernel data, a pixel-value arranging section for modulating the values and arranging the values or the modulated values in descending order, a pixel-value selecting section for either selecting a pixel value in a specified rank or selecting a modulated pixel value in a specified rank and demodulating the modulated value, a characteristic determination section for determining the characteristic of the image from the pixel value of the first image data, and a second image-data generating section for selecting one of the value of a specified pixel in the first image data and the value in the specified rank or the demodulated value selected by the pixel selecting section to generate second image data. This allows reduction of black hole and highlighting of turbulent mosaic patterns without degradation in spatial resolution in an ultrasonic color Doppler method.
Owner:TOSHIBA MEDICAL SYST CORP
Method for distributed denial-of-service attack mitigation by selective black-holing in MPLS VPNS
A system and method for aiding the handling of DDoS attacks in which VPN traffic entering an ISP network at some points will be black-holed, while VPN traffic entering the ISP network at other points will be routed, as it should be, to the system-under-attack. Thus, the system-under-attack is made available to some of the user community and made unavailable to suspect portions of the user community. Furthermore, the number of entry points where black-holing of VPN traffic occurs can be selected and changed in real-time during a DDoS attack.
Owner:AT&T INTPROP II L P
Intelligent illuminating method and device for road tunnel
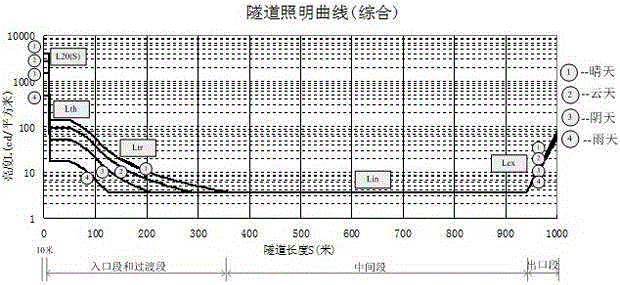
InactiveCN102176799ALow costImprove securityPoint-like light sourceElectric circuit arrangementsSmart lightingOver-illumination
Owner:GUIZHOU UNIV
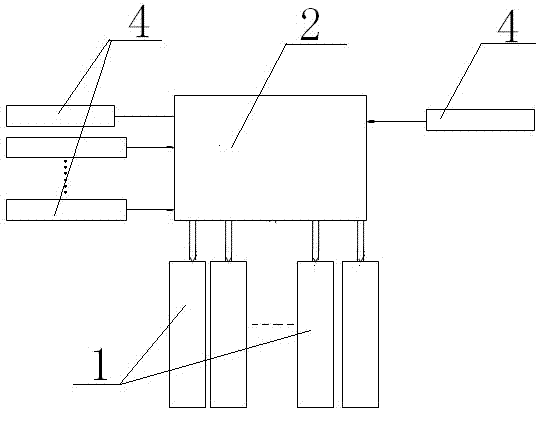
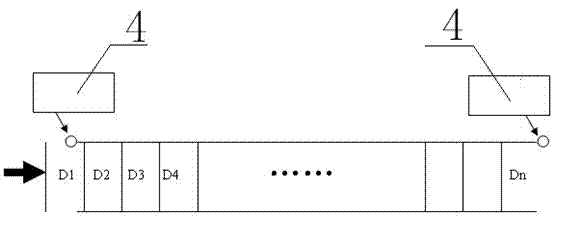
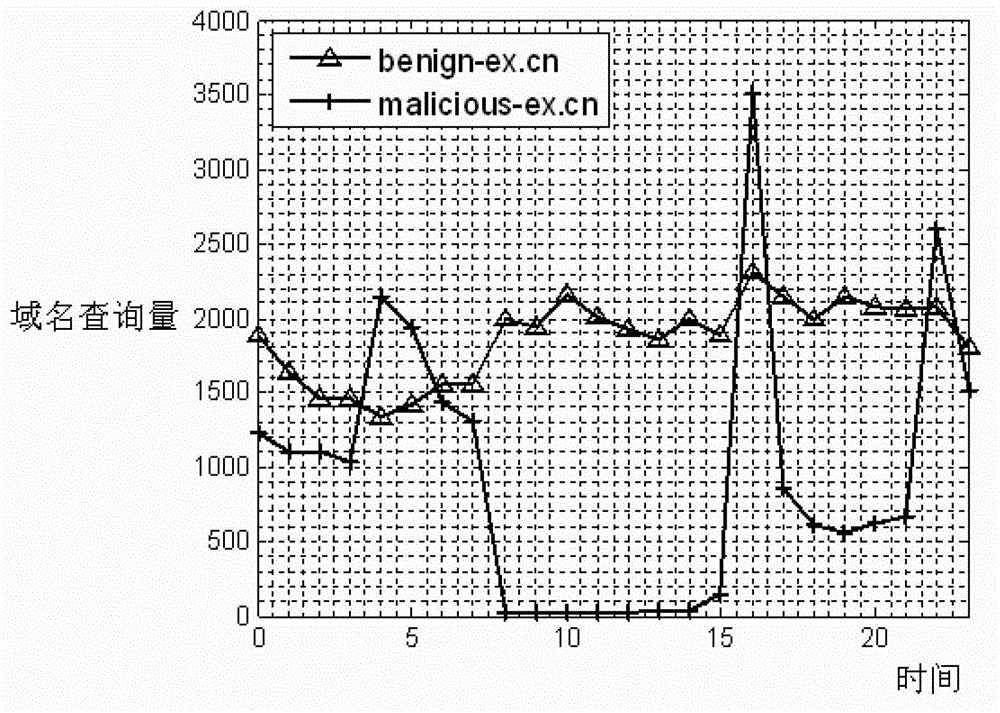
Detection and processing method and system for botnet domain names
The invention relates to a detection and processing method and a system for botnet domain names. The detection and processing system is composed of an input module, an output module, a real-time calibration module and a processing module. The method comprises the step: 1) carrying out log query on a to-be-detected network domain name, and obtaining a log record of domain name query and inputting the log record to a detection port; 2) extracting and obtaining characteristics of the domain name according to the log record of the domain name query, and carrying out machine learning on the characteristics of the domain name; 3) after the machine learning, extracting the botnet domain names in a domain name on an outgoing line and / or a local domain name log; and 4) building a data base of the botnet domain names, carrying out breakdown through a black hole authoritative server, and finishing the processing. According to the detection and processing method and the system for the botnet domain names, while the botnet domain names can be extracted from a domain name server (DNS) to be broken down and separated so as to crack down botnet crimes, the botnet domain names are collected, and a network bad action that a botnet host is connected with a controlling end through the domain names so as to receive vicious commands is effectively prevented.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Automatic passenger and driving safety alarm device based on intelligent voice recognition and method thereof
PendingCN108877146AReduce security regulatory black holesReduce crimeAlarmsSpeech recognitionVoice communicationEngineering
The invention discloses an automatic passenger and driving safety alarm device based on intelligent voice recognition. The voice data in a vehicle are collected in real time through a multi-path microphone pickup circuit, the device collects audio data in the vehicle in real time, and the audio is subjected to amplification filtering and voice extraction after preprocessing, and real-time communication is carried out with the cloud background through a wireless communication module. The invention further provides an automatic passenger and driving safety alarm method based on intelligent voicerecognition. The voice data are subjected to preprocessing and then are sent for feature extraction, the voice is transmitted to an acoustic model for comparison. If the voice falls into the alarm preset sensitive words, the alarm text information is output to the background, and the background is fed back to an online ride-hailing platform, so that the abnormal situation can be immediately processed. The safety supervision black hole of current online ride-hailing is reduced. The life and the safety of people in the vehicle can be guaranteed, voice communication can be directly carried out with a party involved, and illegal criminals of online ride-hailing can be effectively reduced.
Owner:深圳市尼欧科技有限公司
Double-layer-board sonic black hole vibration and noise reduction structure
ActiveCN106023978AShorten speedReach absorbencySound producing devicesSonic black holeVibration control
The invention discloses a double-layer-board sonic black hole vibration and noise reduction structure. The double-layer-board sonic black hole vibration and noise reduction structure is formed by combining two plate structures A1, wherein each plate structure A1 comprises a uniform area and a sonic black hole area connected with the uniform area, after the two plate structures A1 are placed together vertically, the sonic black hole areas are assembled to form a cavity area, and the cavity area is filled with a damping material and a sound absorption material. According to the double-layer-board sonic black hole vibration and noise reduction structure, the intrinsic material of the plate structures is removed, the high-efficiency energy absorption or vibration and noise reduction can be realized by combining with a small amount of damping material and sound absorption material, wherein the damping material consumes the most bending wave energy, so that the purpose of energy absorption or vibration control is achieved, the sound absorption material dissipates the transmitted energy, and thus the purpose of efficient energy absorption or vibration and noise reduction is achieved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Distributed denial-of-service attack mitigation by selective black-holing in IP networks
ActiveUS20060031575A1Sure easyData switching by path configurationMultiple digital computer combinationsIp addressThe Internet
In an IP network during a DDoS attack on a website or other internet entity having an IP address, selective black-holing of attack traffic is performed such that some of the traffic destined for the IP address under attack continues to go to the IP address under attack while other traffic, destined for the same IP address is, rerouted via BGP sessions to a black-hole router. Such a selective black-holing scheme can be used to allow some traffic to continue in route to the IP address under attack, while other traffic is diverted.
Owner:AT&T INTPROP I L P
Propagating black hole shunts to remote routers with split tunnel and IPSec direct encapsulation
Owner:CISCO TECH INC
Adaptive segmentally controlled tunnel illumination control system and method
InactiveCN105188229AEasy to changeRealize data transmissionElectric light circuit arrangementEngineeringSelf adaptive
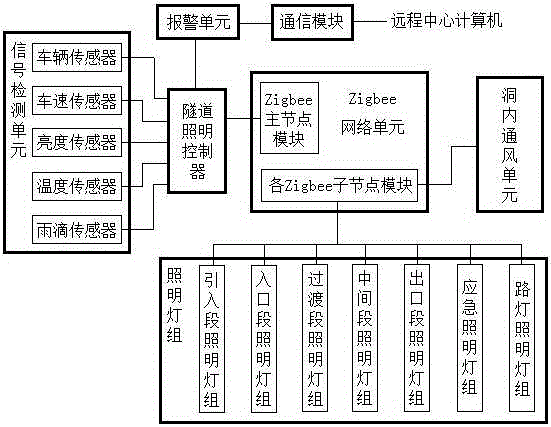
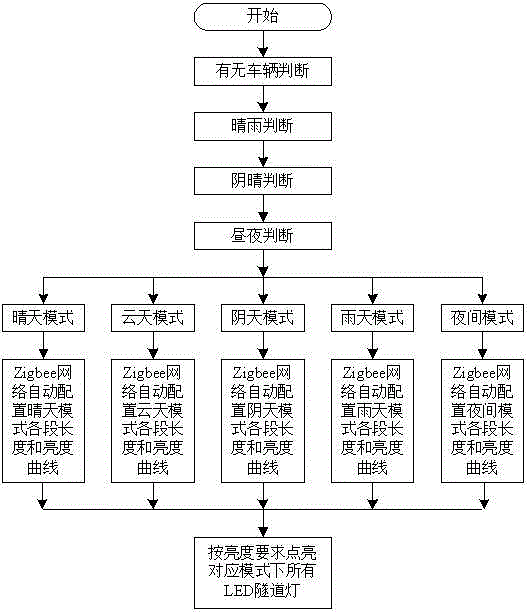
The invention relates to an adaptive segmentally controlled tunnel illumination control system and method; the system comprises a tunnel illumination controller, a signal detection unit, a Zigbee network unit, and a plurality of illumination lamp sets; the signal detection unit comprises a vehicle sensor, a vehicle speed sensor, a brightness sensor, a temperature sensor, and a raindrop sensor; the Zigbee network unit comprises Zigbee main node module connected with the tunnel illumination controller, and a plurality of Zigbee node modules respectively connected with the illumination lamp sets; the illumination lamp sets comprise an introduction segment lamp set arranged outside the tunnel, an illumination lamp set arranged in the entrance segment in the tunnel, a transition segment illumination lamp set, a middle segment illumination lamp set, an exit segment illumination lamp set, and a road lamp illumination lamp set arranged outside the tunnel, and also comprise an emergency illumination lamp set. The adaptive segmentally controlled tunnel illumination control system can realize tunnel illumination, satisfies illumination curve demands of human eyes, thus eliminating black frame, black hole and white hole effects.
Owner:FUJIAN CHUANZHENG COMM COLLEGE
System for automatically generating document in software development process
InactiveCN102495832AQuick buildCompile syncSpecial data processing applicationsEditing/combining figures or textSoftware development processSoftware engineering
The invention discloses a system for automatically generating a document in the software development process. The system comprises a collection module, wherein the collection module is used for collecting the name of a module, and variables, methods and comments which are used by the module according to a software module. The system is characterized by also comprising a monitoring module and an output module, wherein the monitoring module is used for monitoring the change behavior of the software module; and the output module is used for outputting the name of the module, and the variables, the methods and the comments which are used by the module to form the document, and changing and revising the formed document according to a monitoring result of the monitoring module. By adoption of the system, the black hole phenomenon of projects can be avoided, and the implementation efficiency of the projects is improved; and the projects can be monitored in real time through the document, and a project progress document can be quickly generated.
Owner:FOUNDER INTERNATIONAL CO LTD
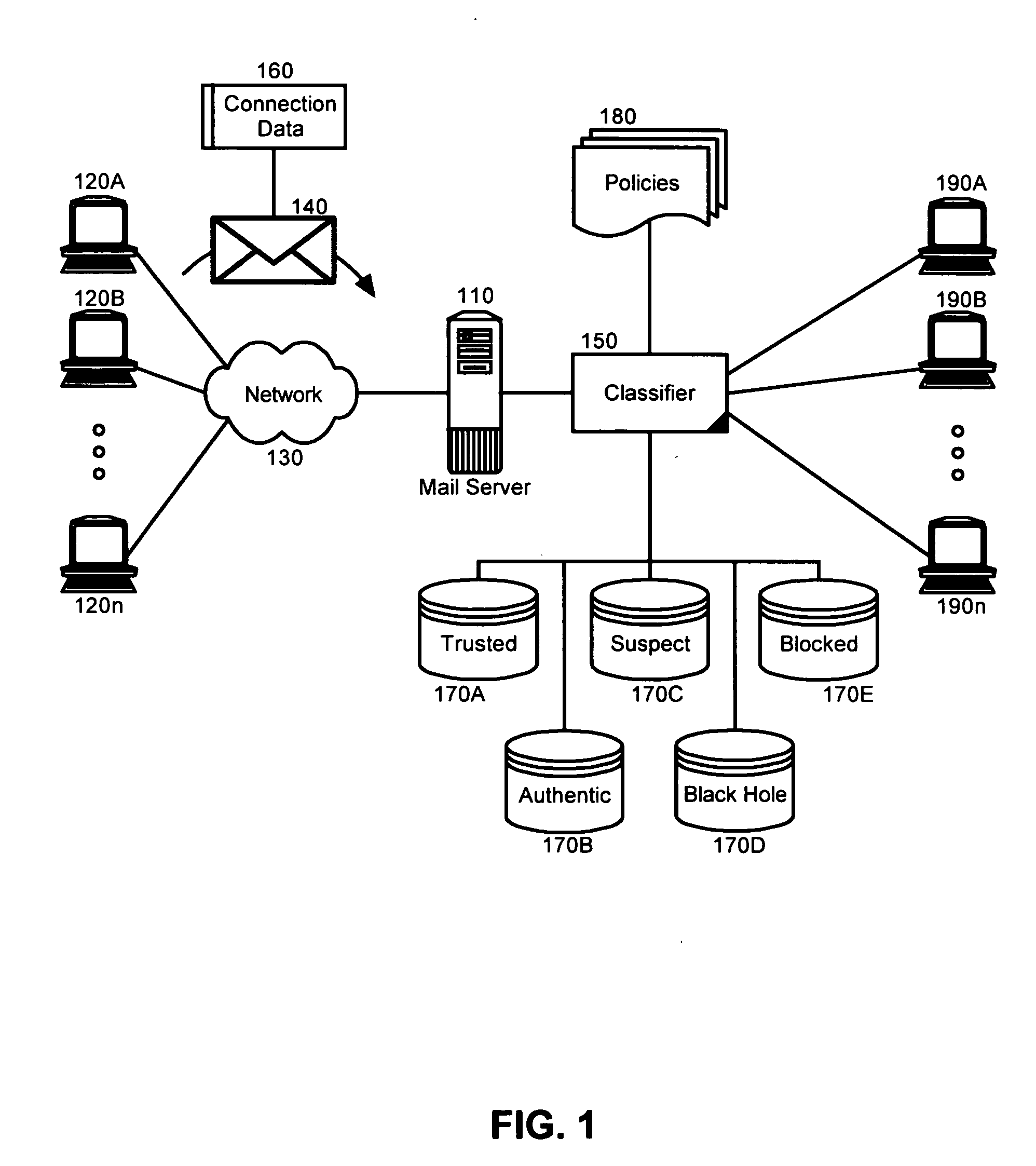
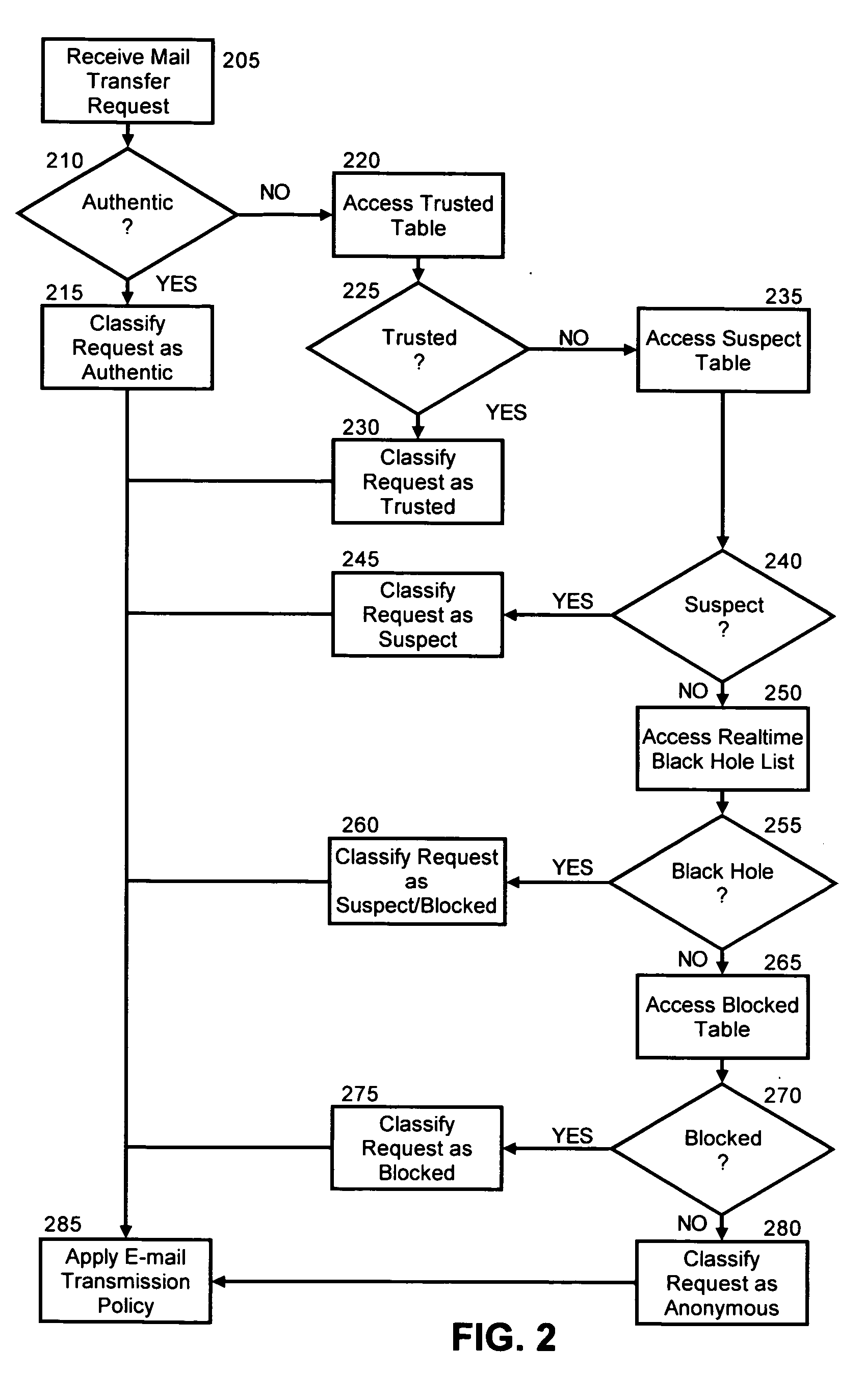
Classifying e-mail connections for policy enforcement
InactiveUS20050193072A1Multiple digital computer combinationsOffice automationNetwork addressingNetwork address
A method and system for the policy-based restriction of electronic mail transmissions. A method for classifying electronic mail message transfer requests for policy enforcement can include identifying a source of an incoming electronic message, classifying the source, and applying a message transfer policy associated with the classification for the source. In particular, the identifying step can include identifying a network address for the source. The classifying step by comparison, can include classifying the source as one of a trusted source, a blocked source, and a suspect source. The classifying step also can include classifying the source as one of an authenticated source and an anonymous source. Finally, the classifying step further can include classifying the source as a blocked source where the source appears in a realtime black hole list.
Owner:IBM CORP
Concealing a network connected device
ActiveUS6973496B2Comprehensive understandingUser identity/authority verificationMultiple digital computer combinationsNetwork connectionThe Internet
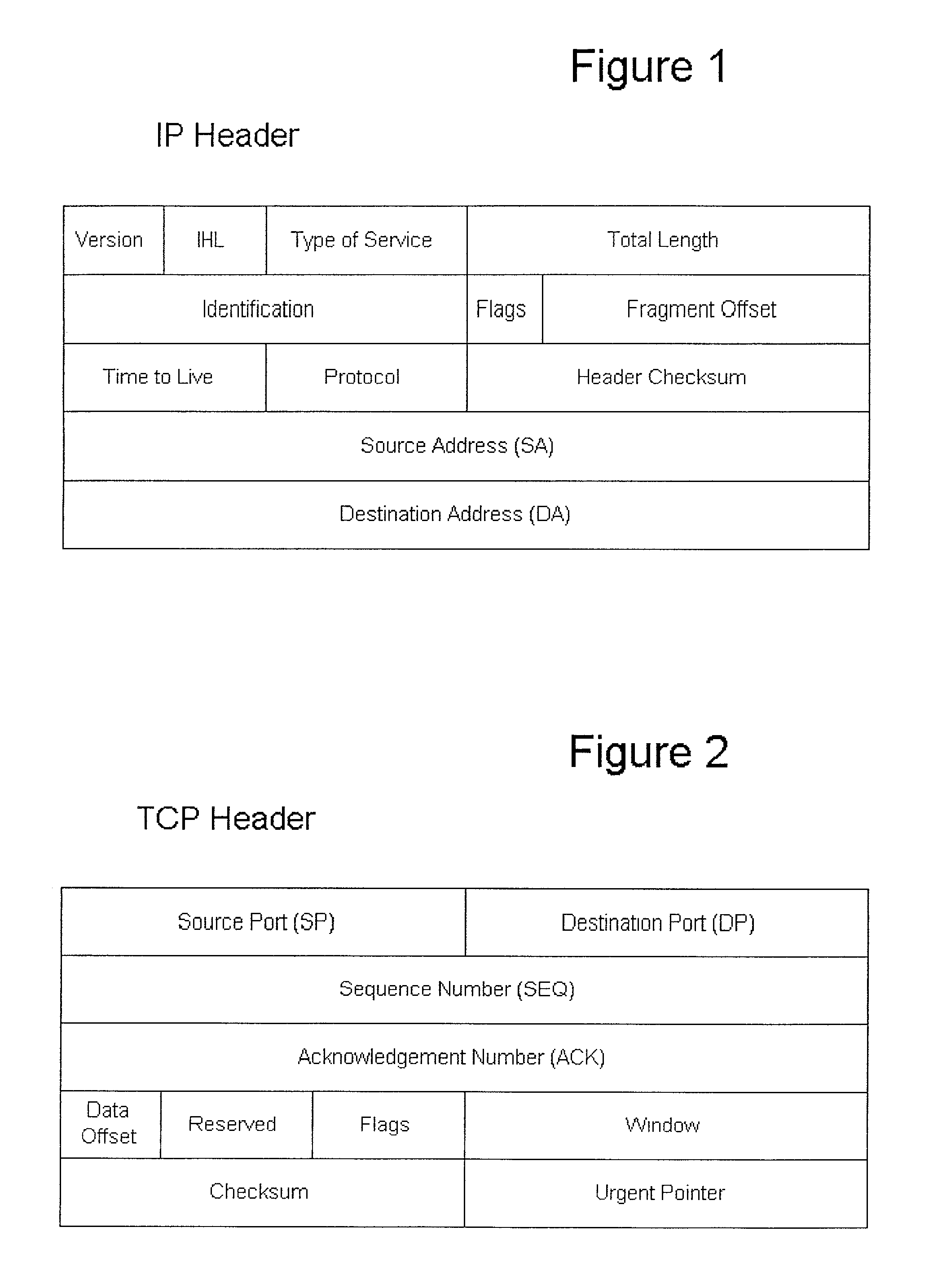
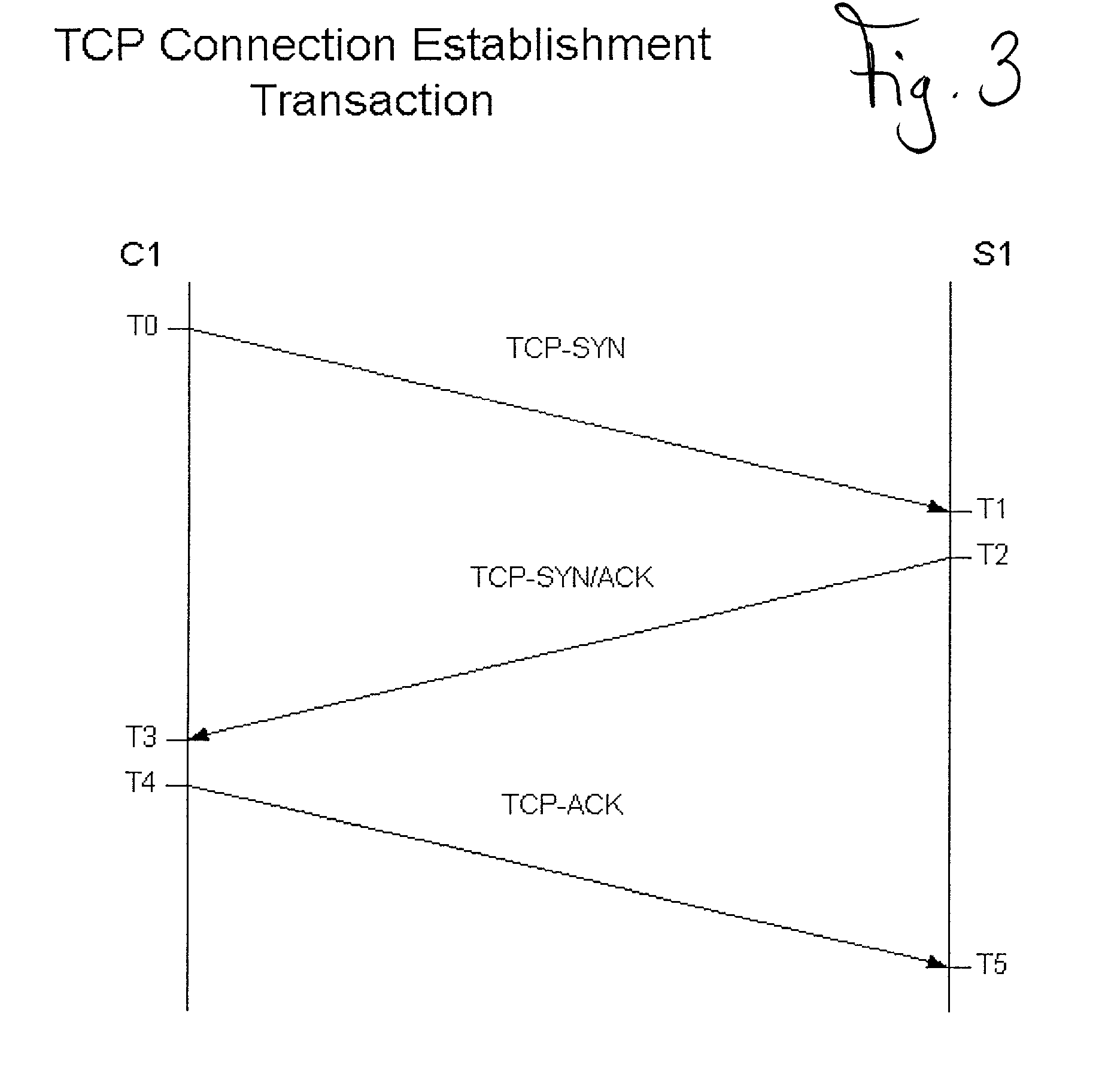
In a preferred embodiment of the invention, a network client inserts a validation key into the SEQ and ACK fields of a TCP connection request (TCP-SYN). The TCP connection request is sent to a validating server. The validating server extracts the validation key and uses it, with other implicit and explicit data contained within the TCP connection request to validate the connection establishment request. If the connection request is validated, the validating server responds with a TCP-SYN / ACK as described in the TCP protocol specification. If the TCP connection request is denied, the request is discarded and nothing is sent back to the requestor, in this case the network client. When an internet port scanner sends a TCP connection request to a validating network server without the proper key, the request is silently discarded or “black-holed.” This makes the validating server appear to the Internet port scanner to not exist. The validating server has completely concealed itself from unauthorized and unvalidated connections.
Owner:INVISINET TECH LLC
Dark quenchers for donor-acceptor energy transfer
InactiveUS20060035262A1Minimize fluorescenceEnhanced interactionAnthraquinone-azo dyesMonoazo dyesEnergy transferExcited state
The present invention provides a family of dark quenchers, termed Black Hole Quenchers (“BHQs”), that are efficient quenchers of excited state energy but which are themselves substantially non-fluorescent. Also provided are methods of using the BHQs, probes incorporating the BHQs and methods of using the probes.
Owner:HSBC TRUSTEE COMPANY UK LIMITED AS SECURITY AGENT
Hole blackening solution and preparation thereof
ActiveCN101394712AImprove conductivityThe functional method is simpleNanoinformaticsPrinted circuit aspectsSurface-active agentsSolvent
The invention discloses a black hole solution and a preparation method thereof. The black hole solution comprises carbon nanotubes, a surface active agent, an alkaline matter and a proper amount of liquid solvent, wherein the carbon nanotubes are stably dispersed in the black hole solution under the action of a dispersant after being subjected to functionalization processing. The preparation method comprises the following steps: providing a carbon nanotube material; conducting functionalization processing for the carbon nanotube material; mixing the functionalized carbon nanotubes with the alkaline matter; adding the mixture into the liquid solvent to obtain a suspended solution; adding the surface active agent into the suspended solution; and mechanically agitating the suspended solution to obtain the black hole solution.
Owner:TSINGHUA UNIV +1
WLAN (Wireless Local Area Network) equipment self-adaptive energy-saving method
ActiveCN103517389ATo achieve the purpose of energy saving and emission reductionTake advantage ofPower managementNetwork topologiesSelf adaptiveRadio frequency
The invention discloses a WLAN equipment self-adaptive energy-saving method. The method comprises the steps of periodically maintaining neighbor information and load information of an AP (Access Point), and calculating the reverse neighbor number; periodically inspecting the load of the AP in the condition that coverage is satisfied, and self-adaptively closing the AP without user load; simultaneously covering signal black holes caused by the closing of the current AP by selfadaptively increasing the power of peripheral neighbor APs; periodically inspecting the load of the AP in the condition that coverage is satisfied, self-adaptively opening the AP closed for saving energy if the load exceeds a set threshold value, so as to improve the access performance; simultaneously reducing radio-frequency interference caused by the increasing of the AP by self-adaptively reducing the power of the peripheral neighbor APs. The method adjusts relevant AP power by self-adaptively closing part of AP power supplies or radio frequency functions in the condition that coverage is satisfied, and achieves the purpose of saving energy and reducing emission to the hilt.
Owner:BEIJING JIAOTONG UNIV
Vibration damping and noise reduction device of acoustic black hole
ActiveCN108133700AAchieve full-band noise reductionAvoid local high dynamic responseNon-rotating vibration suppressionSound producing devicesNoise reductionUltimate tensile strength
The invention discloses a vibration damping and noise reduction device of an acoustic black hole. The vibration damping and noise reduction device comprises a disk-shaped structure whose distance between upper and lower surfaces is reduced gradually from the central axis to the external periphery, the disk-shaped structure comprises a block hole area, the distance between upper and lower surfacesof the black hole area is changed in the form of power exponent from the central axis to the external periphery, the disk-shaped structure is added to a noise reduced structure to carry out vibrationdamping and noise reduction on the noise reduced structure, the thickness of the noise reduced structure needs not to be reduced, and the noise reduced structure is avoided from locally high dynamic response or reduction of the structural intensity.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
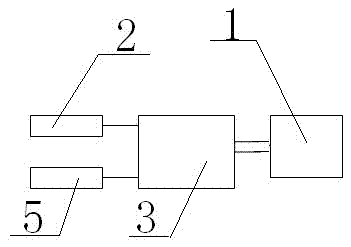
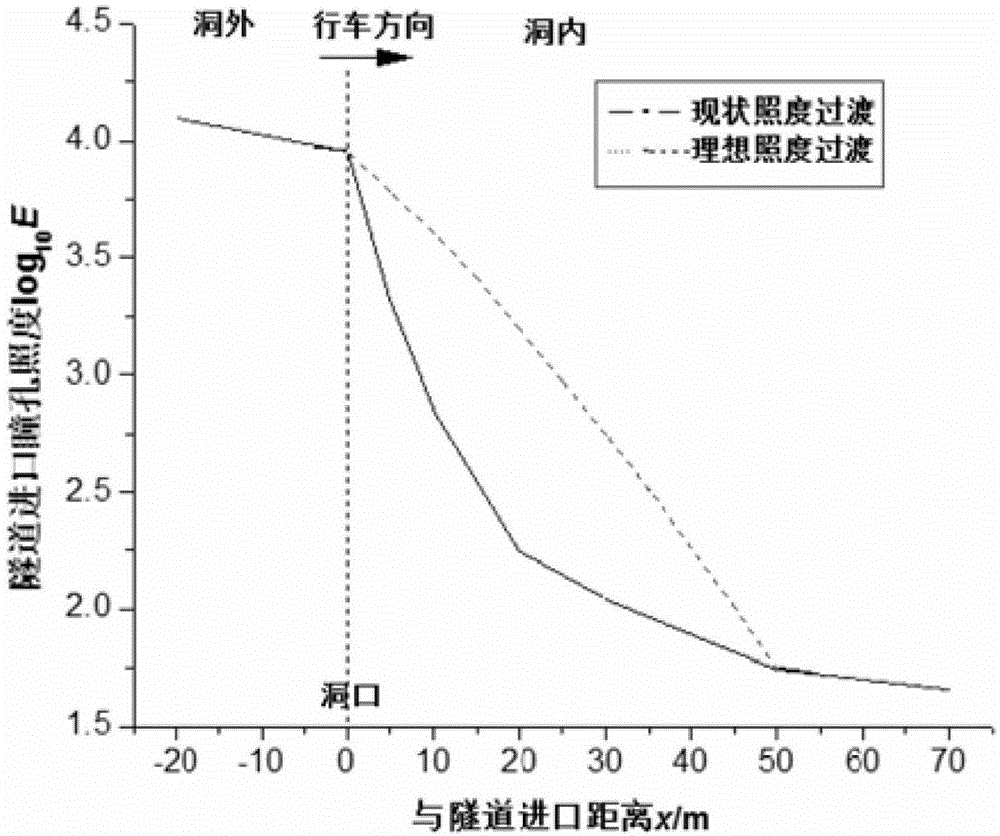
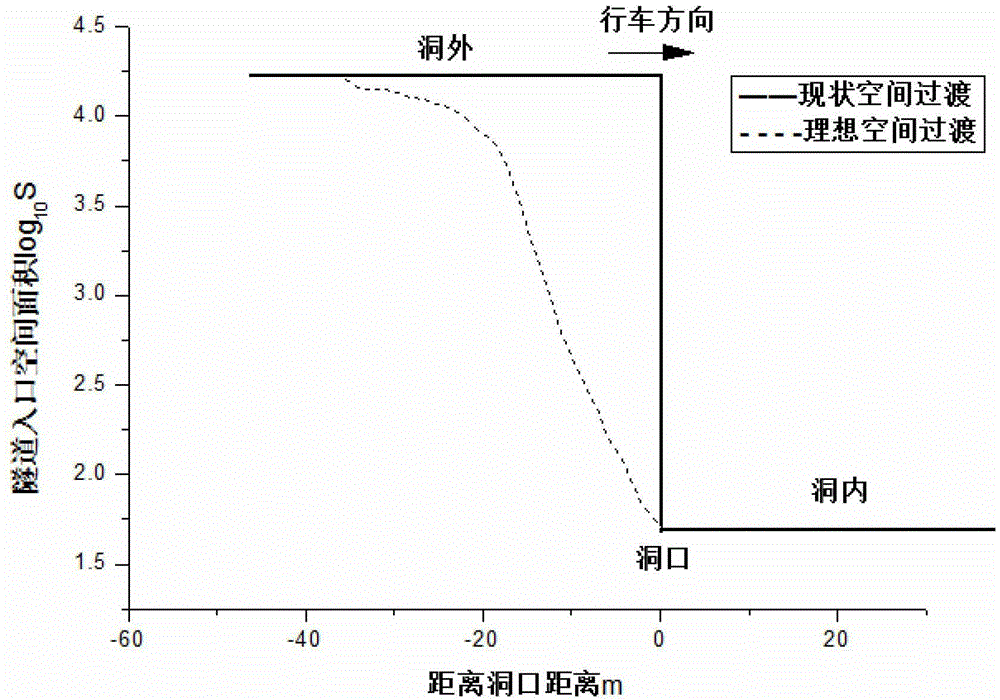
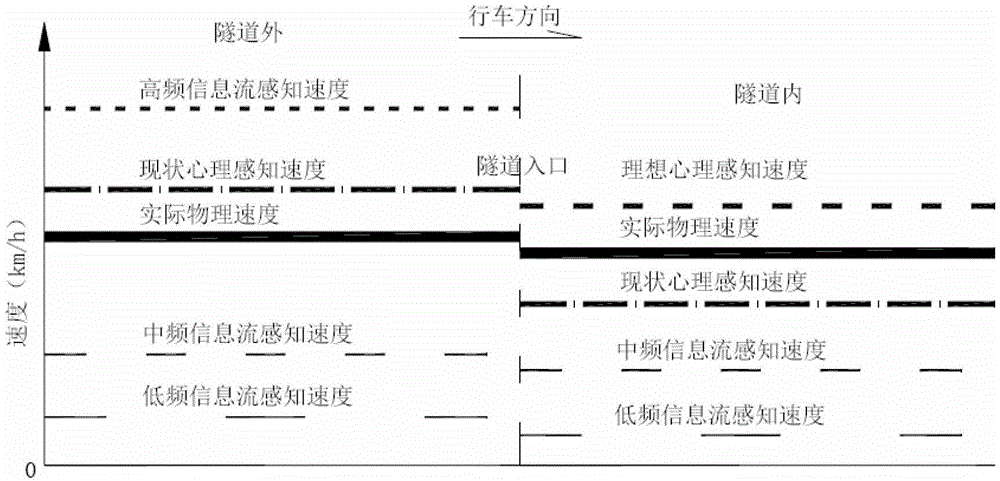
Method for designing shading transition facility for road tunnel entrance
The invention relates to a method for designing a shading transition facility for a road tunnel entrance. The facility mainly comprises transparent toughened glass plates (2), a plurality of arched steel-structure upright columns (3), cicada-wing-shaped nontransparent shading films (5) and a shading transition retroreflection system, wherein the arched steel-structure upright columns (3) are gradually heightened outwardly from tunnel cave entrance end walls (1), and horn-shaped openings are formed by the arched steel-structure upright columns (3) and the transparent toughened glass plates (2) on the upright columns; the cicada-wing-shaped nontransparent shading films are arranged on inner layers of the transparent toughened glass plates, and contour line planes and side face projections of the shading films are Boltzmann curves, and the two sides of each arched steel structure are triangularly hollowed; the retroreflection system comprises medium-frequency steel-structure upright column contour marks (7), medium-frequency guardrail contour marks (8), high-frequency guardrail facade marks (9), high-frequency pavement marking lines (10) and high-frequency pavement protrusion marks (11). The shading transition facility has the advantages that the intense transition of space, luminance and reference of the tunnel entrance can be improved, and the black-hole effect on the tunnel entrance is relieved.
Owner:WUHAN UNIV OF TECH
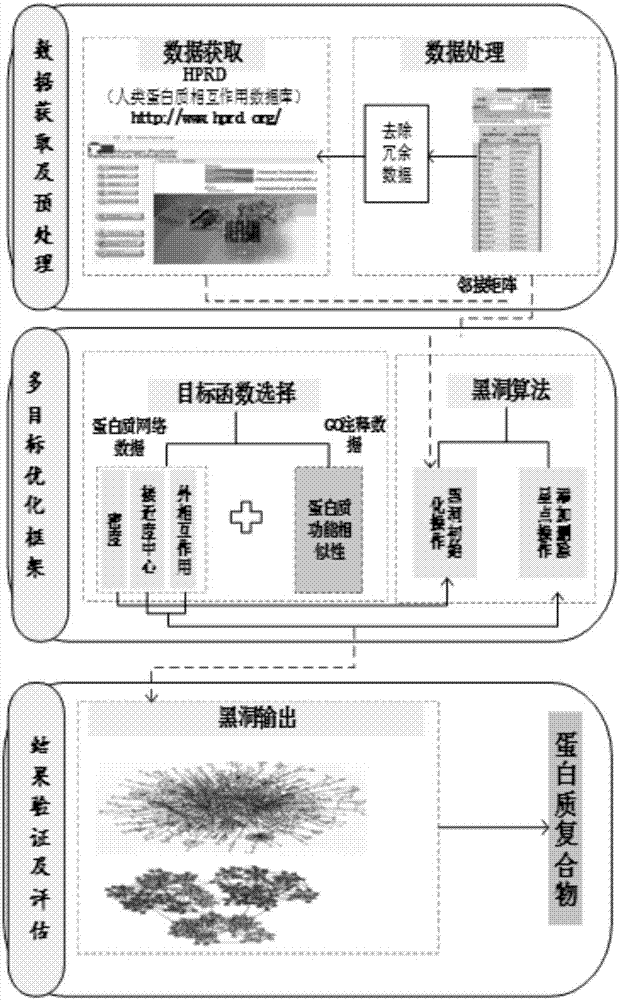
Protein complex recognizing method based on multi-source data fusion and multi-target optimization
InactiveCN108009403AImprove accuracyRecognition speed is fastSpecial data processing applicationsComplex network analysisAlgorithm
The invention discloses a protein complex recognizing method based on multi-source data fusion and multi-target optimization, comprising: preprocessing protein interaction network data to obtain adjacent matrixes; primarily clustering protein complexes to obtain an initial protein complex module; further optimizing the initial protein complex module, fusing topological structural features of the protein interaction network data and functional similar features of GO (gene ontology) annotation data during optimizing, and performing optimizing operation in conjunction with an adaptive multi-target blackhole optimization algorithm to obtain a more precise protein complex module; postprocessing to obtain a final optimal protein complex. The method of the invention has the advantages that protein complex recognition speed and precision are increased, the method is applicable to protein interaction networks and extensible to the analysis of other complex community networks, and the method isvery practical in complex network analysis.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
Priority coding after-treatment method and device colorful blood stream imaging
ActiveCN101210966AAchieve smoothIncrease costImage enhancementWave based measurement systemsFiltrationTwo step
A post treatment method and a device for colorful blood flow priority coding, relates to a general image data processing technique for a real-time colorful blood flow imaging system in medical field. The method comprises the following steps of: using the dilation operation and erosion operation of mathematical morphology, directly performing two-step non-linear filtration of the binary image outputted from the priority coding or simply accumulating the number of image elements of the colorful blood flow within a certain area; and confirming one point in the area as the image space of the blood flow or as image space of tissue, or as tissue image space. The binary image outputted from the priority coding obtained from the calculation realizes the filling of black hole and elimination of isolated point. The post treatment method and the device has the advantages that on the premise of increasing small cost, the invention realizes the flatness of colorful priority coding and keep the integrated shape of blood flow not changing so as to further improve the display appearance of the colorful blood flow.
Owner:SHENZHEN MINDRAY BIO MEDICAL ELECTRONICS CO LTD
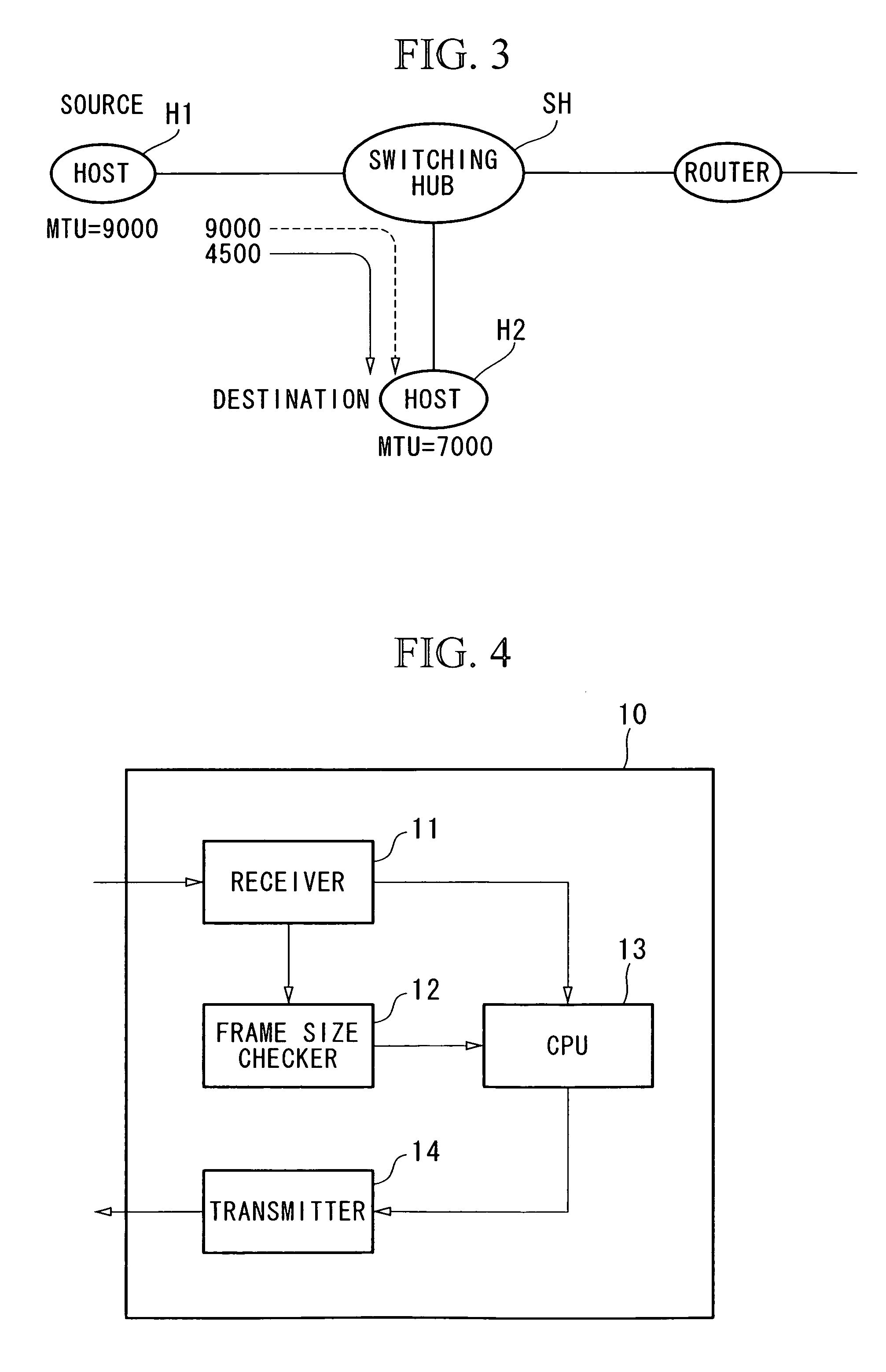
IP communication device and IP communication system therefor
InactiveUS20070076618A1Improve communication efficiencyQuick fixError prevention/detection by using return channelFrequency-division multiplex detailsCommunications systemIp address
A pair of IP communication devices (called a source device and a destination device) perform communication using IP packets (e.g., MAC frames or jumbo frames) over a communication path lying therebetween. The IP communication device checks whether or not the size of an MAC frame exceeds the maximum frame size that is determined in advance; then, an ICMP error is sent back to the source device having an IP address, which is included in a prescribed part of the MAC frame. The source device also executes path MTU discovery so as to determine an appropriate MTU, thus improving the communication efficiency without causing a black hole in communication.
Owner:YAMAHA CORP
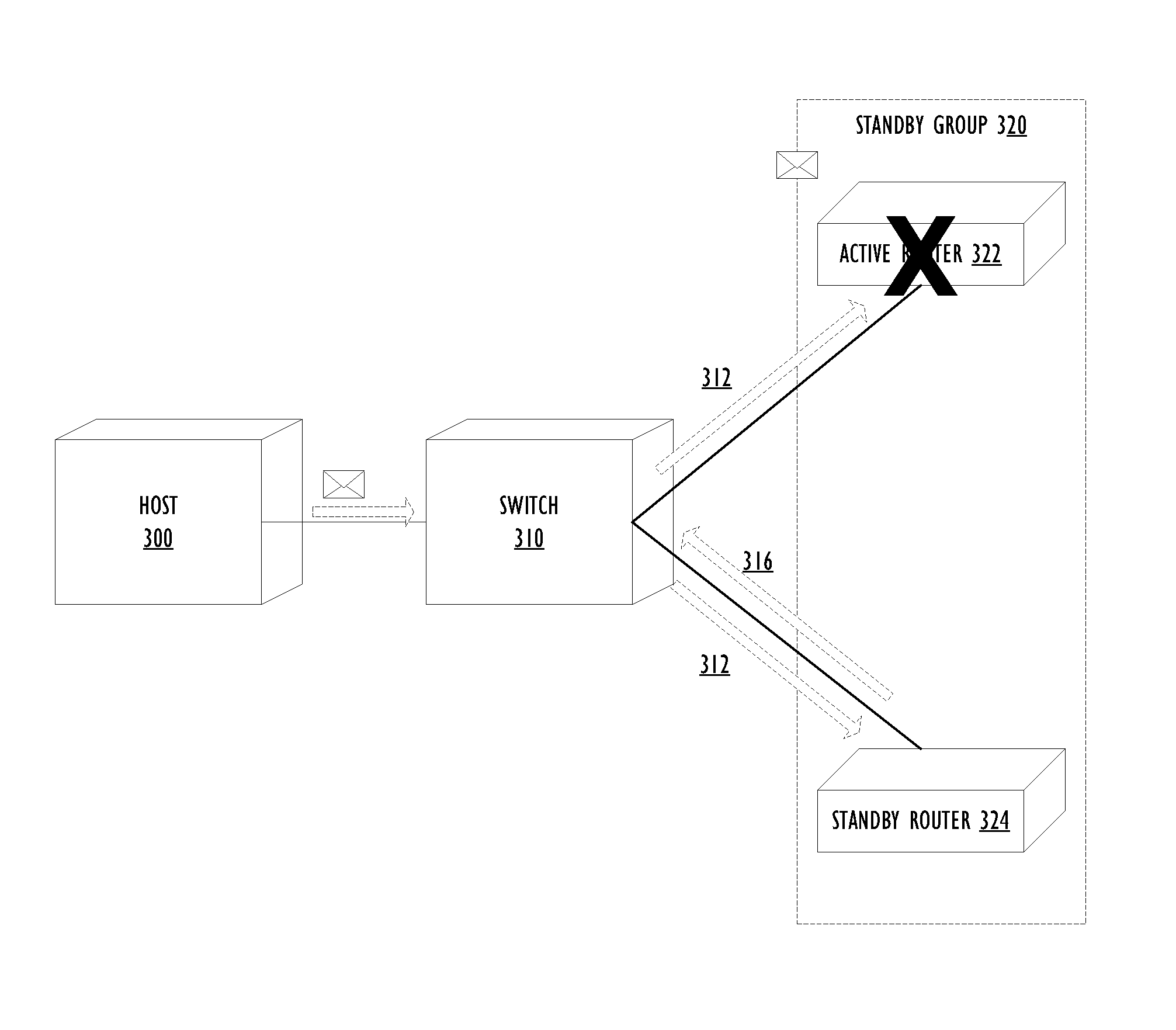
Performing Failover in a Redundancy Group
InactiveUS20140143591A1Reduced black hole conditionTransmissionRedundant hardware error correctionFailoverDistributed computing
A method, system, and computer program product for performing failover in a redundancy group, where the redundancy group comprises a plurality of routers including an active router and a standby router, the failover being characterized by zero black hole or significantly reduced black hole conditions versus a conventional failover system. The method comprises the steps of: receiving an incoming message at a switch; sending a request of identification to the plurality of routers to identify a current active router, where the current active router represents a virtual router of the redundancy group; and in response to receiving a reply containing an identification from the current active router within a predetermined time, forwarding the incoming message to the current active router.
Owner:IBM CORP
Communication stage and display systems
ActiveUS20180176506A1Small sizeIncrease contactStatic indicating devicesAutomatic exchangesDual modeDisplay device
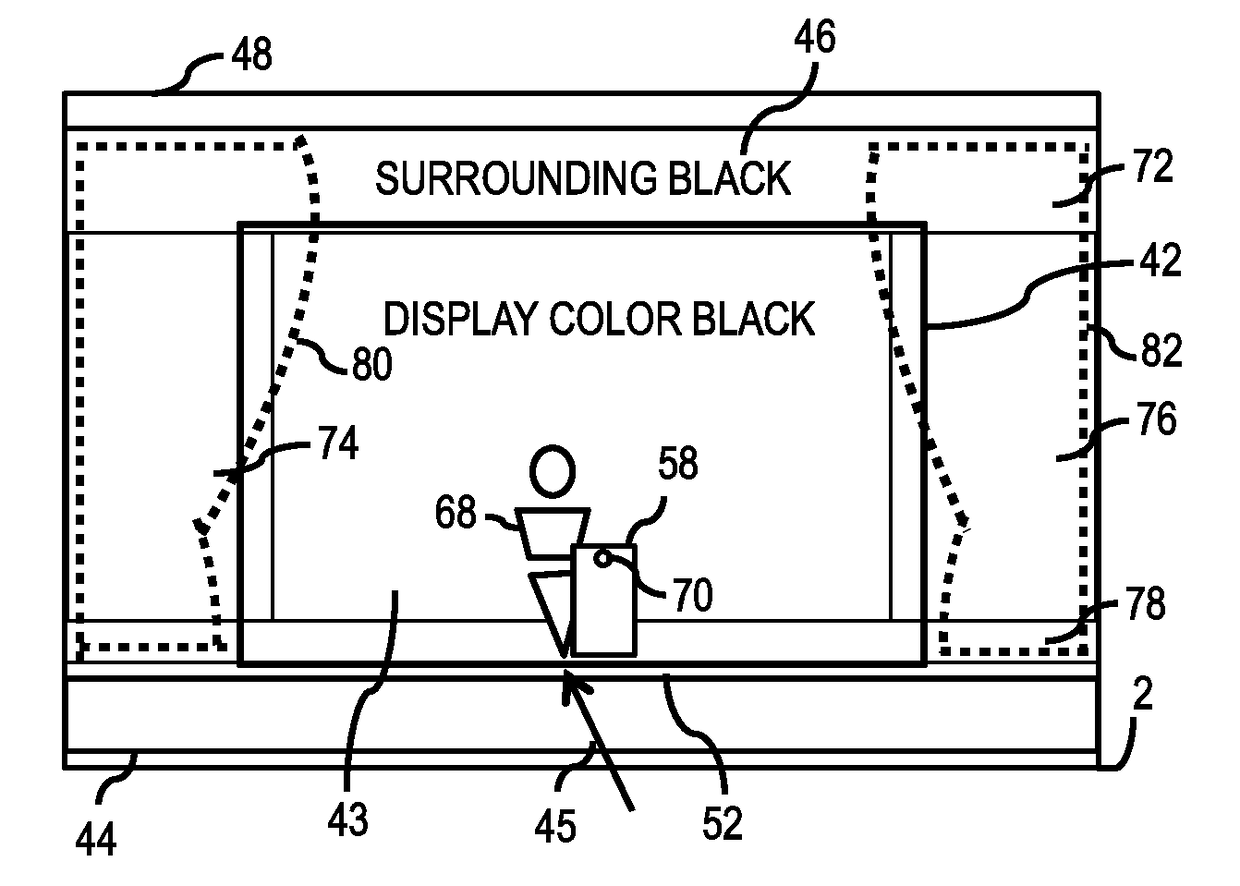
Enterprise communication display systems enable life-like images for videoconferencing and entertainment productions. Life-like images appear in a 3D environment where imaged people are visible through the use of specially configured see-through displays. Imaged people can also be viewed amongst a reflected foreground. A dual mode large high-resolution display is inventively configured for watching and working. Methods for enterprise wide deployments for corporate, healthcare, education, and government communications, including hotel properties and a property management system are shown. The invention further discloses an online production system for events. Further, a black void illusion is described and is applicable to numerous displays including event and live theater stages and movie theaters. Numerous inventive features are described enabling and advancing the black void illusion.
Owner:MCNELLEY STEVE H +1
Polysilicon solar battery piece appearance contamination defect detection method
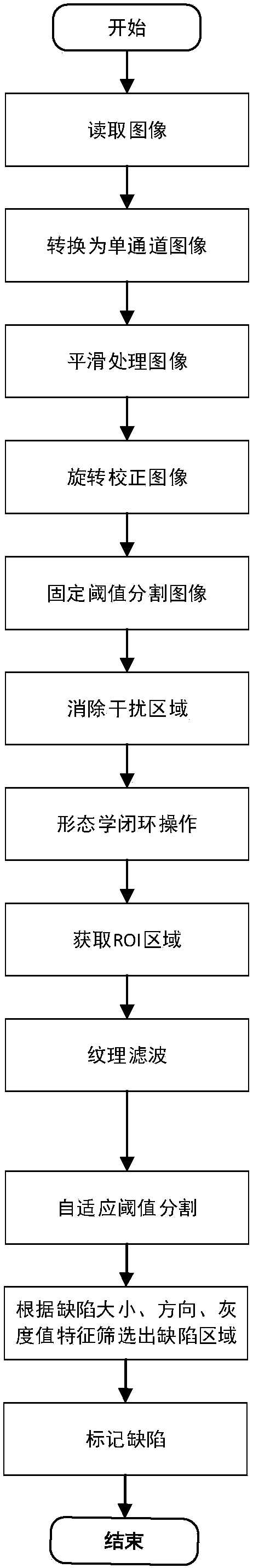
ActiveCN107768269ASuppress interferenceTo achieve the purpose of detection of appearance dirt defectsImage enhancementImage analysisClosed loopEngineering
The invention provides a polysilicon solar battery piece appearance contamination defect detection method. The method mainly comprises two steps, wherein the first step comprises pretreatment of a battery piece and acquisition of an interested region, and the subsequent operations are performed by taking the first step as the foundation; and the second step comprises recognizing and marking of thecontamination regions. Pretreatment comprises the steps of dividing collected three-channel images into R channel images, G channel images and B channel images, and selecting the R channel images with relatively high defect and background comparison degree for performing subsequent treatment; performing smoothening treatment on the selected R channel images, suppressing interference from image noise and high frequency components, next, performing rotary correction operation on the images, enabling the image edges to be parallel to a coordinate system, next, performing fixed threshold value image cutting, setting upper and lower critical values according to the area, and removing interference from a conveyor belt region on the image processing; and next, performing morphology closed-loop operation on the images, removing small sized black holes generated by insufficient threshold value cutting, and finally realizing polysilicon solar battery piece appearance contamination defect detection.
Owner:HEBEI UNIV OF TECH +1
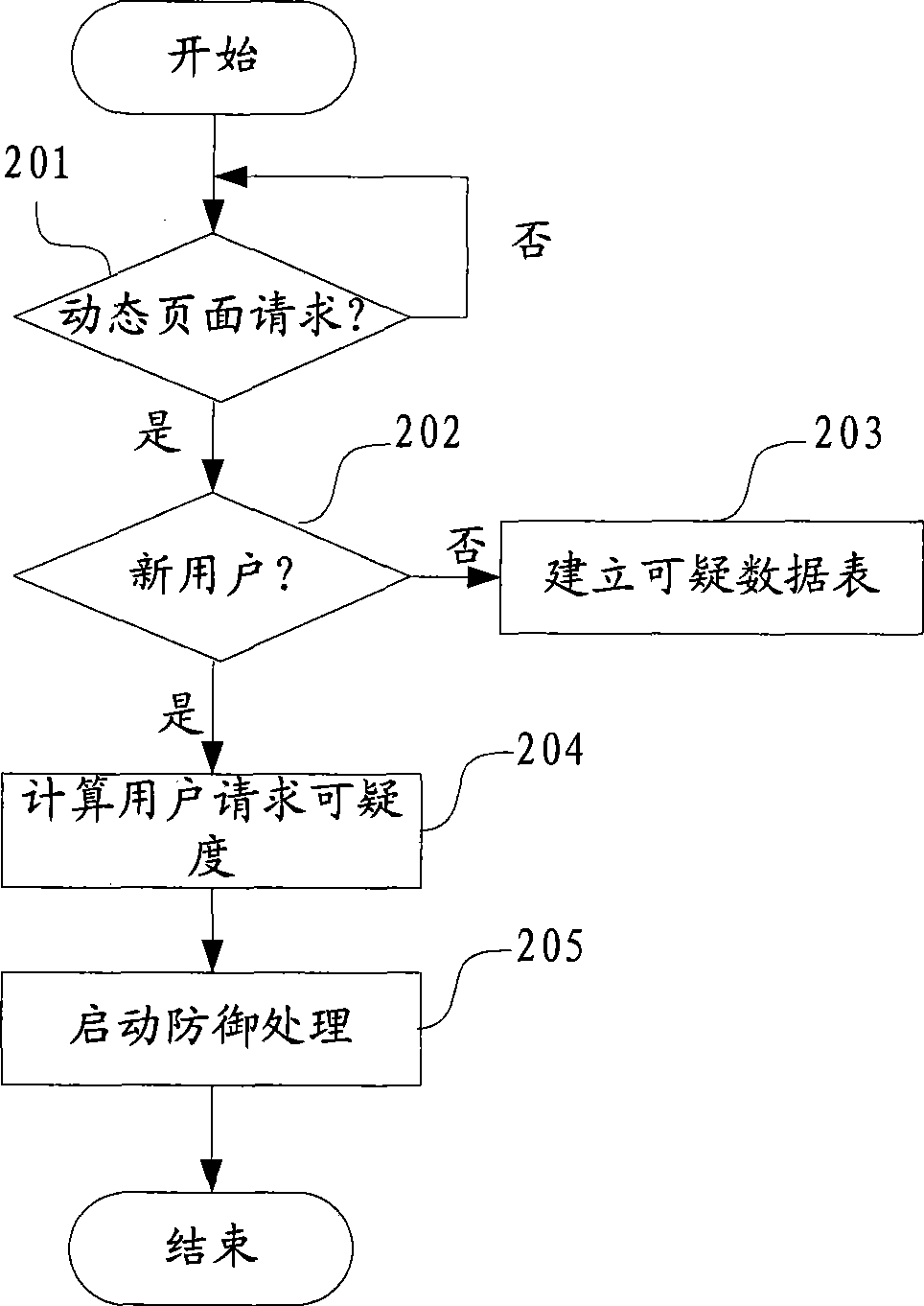
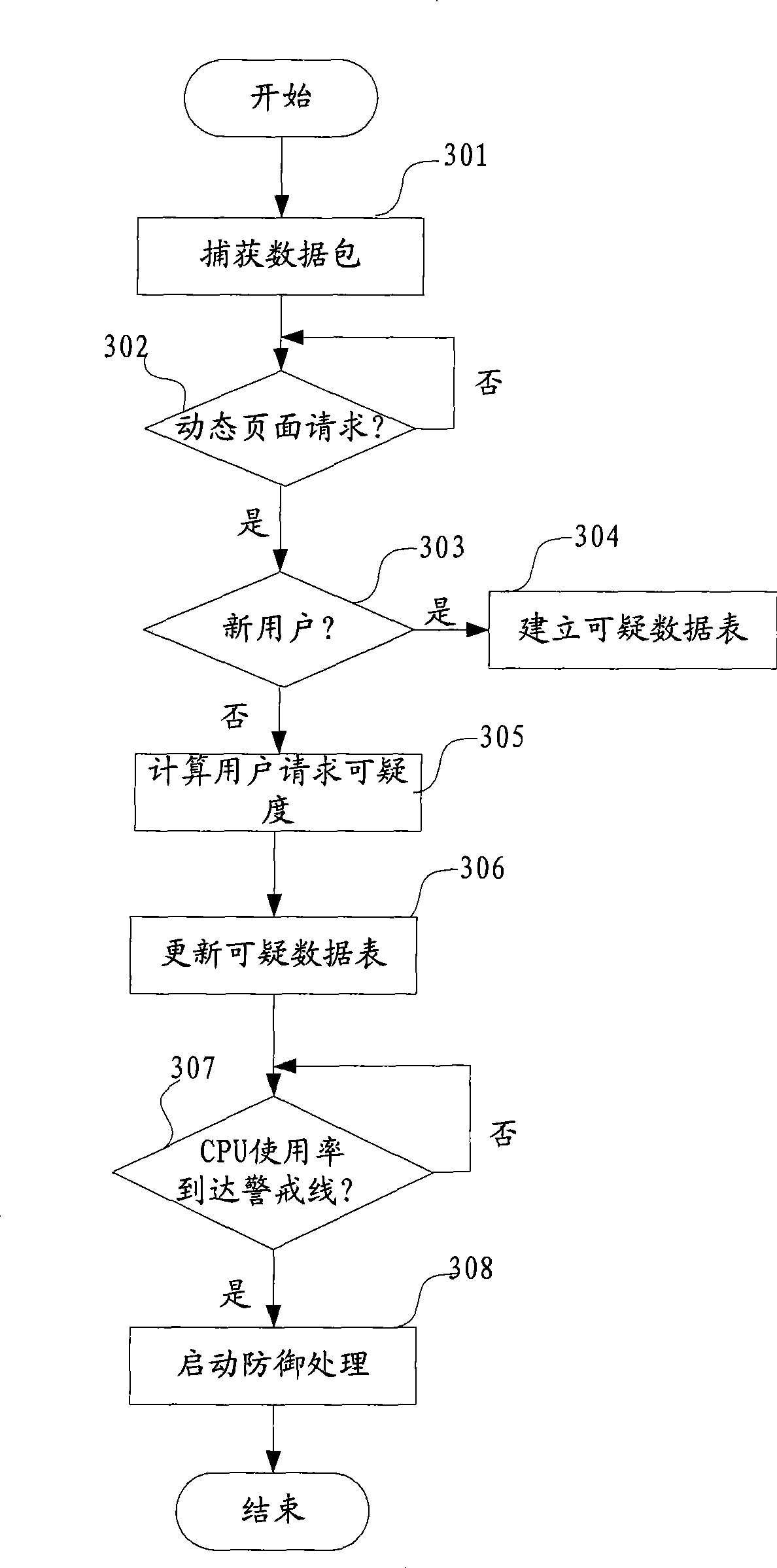
Challenging black hole attack defense method and device
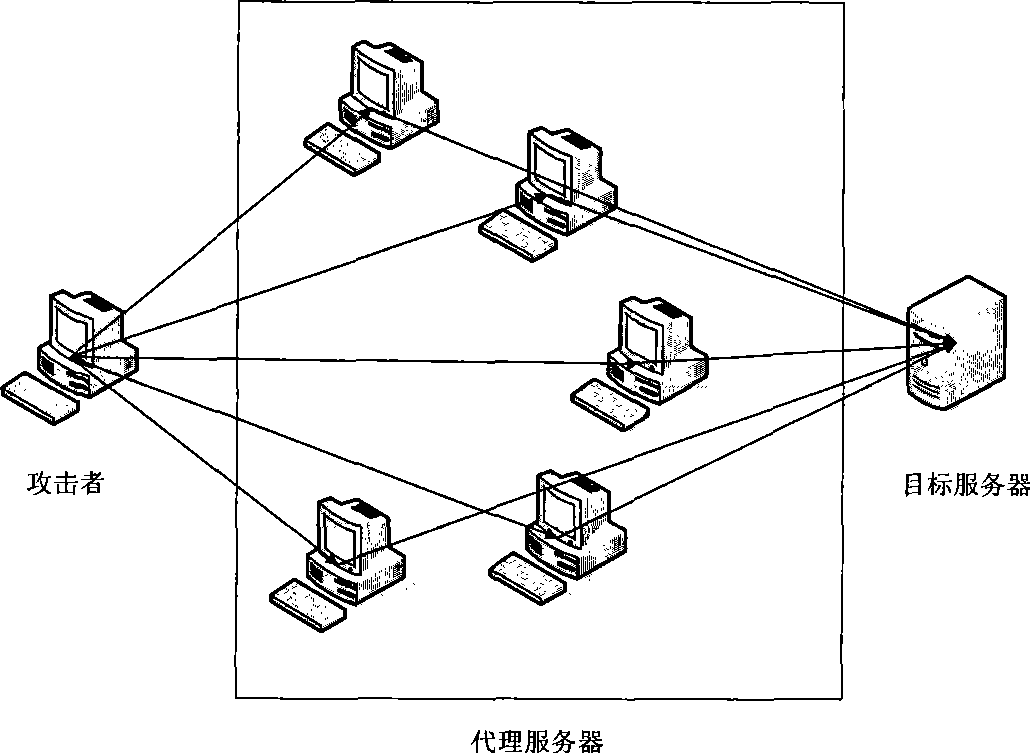
The embodiment of the invention provides a method for defending challenge collapsar attack, which comprises the following steps: whether the WEB page requested by a client is a dynamic page is judged according to obtained data packets; if the WEB page requested by the client is a dynamic page, every client corresponds to a client request distrustful degree; and the dynamic page requests of the client is filtered according to the client request distrustful degree. In addition, the embodiment of the invention also provides a device for defending challenge collapsar attack. With the technical proposal of the embodiment of the invention, the challenge collapsar attack can be accurately identified, and corresponding defending measurements can be dynamically adopted to realize effective protection for a target host.
Owner:CHENGDU HUAWEI TECH
No-distortion integrated imaging three-dimensional displaying method based on Kinect
ActiveCN106920263AHigh image qualityOvercome physical limitationsImage enhancementImage analysisDistortionBlack hole
The invention discloses a no-distortion integrated imaging three-dimensional displaying method based on a Kinect sensor. The method comprises the steps of acquiring a depth image of a three-dimensional scene by means of the Kinect sensor, and performing black hole filling on the depth image obtained by the Kinect according to a rapid stepping method; performing combined bilateral filtering on the depth image after filling according to a corresponding colorful image, and obtaining the depth image with continuous depth change and smooth edge; and finally obtaining a primitive image array of a large-field-depth complex scene by means of an optical field model, thereby realizing no-distortion three-dimensional integrated imaging displaying. According to the primitive image array obtained through the method of the invention, because of an ideal state without influence by scattering and refraction, the image quality is better than that of the primitive image array which is obtained through a microlens array. The no-distortion integrated imaging three-dimensional displaying method can effectively overcome physical restriction of a micro-lens array in recording the large-field-depth scene and furthermore can realize no-distortion three-dimensional integrated imaging displaying for the large-field-depth compliex scene.
Owner:DALIAN UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com