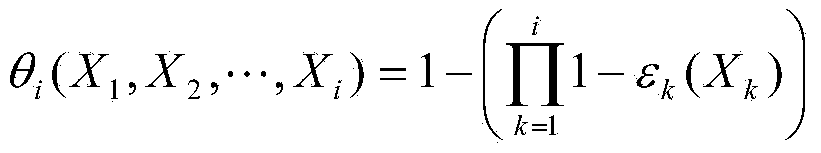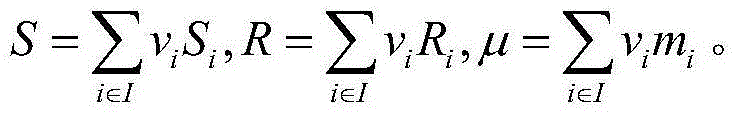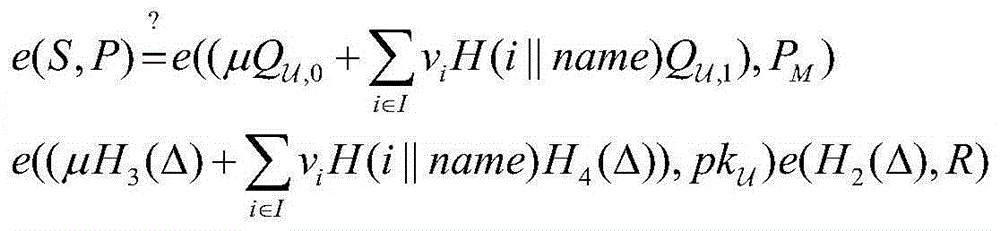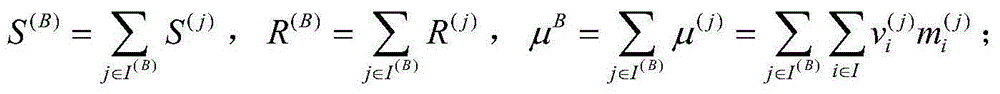Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
204results about How to "Effective defense" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
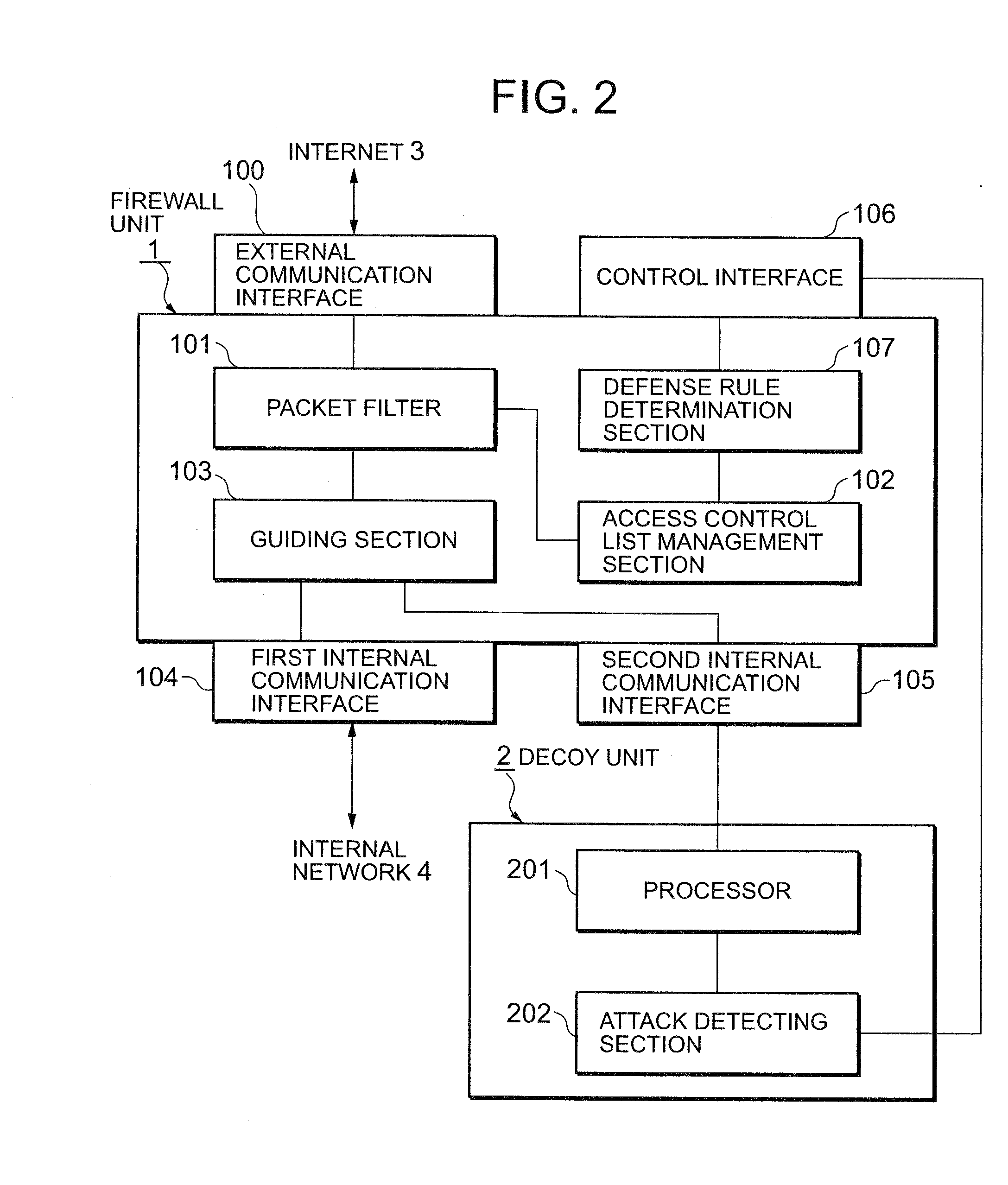
System and methods for anomaly detection and adaptive learning
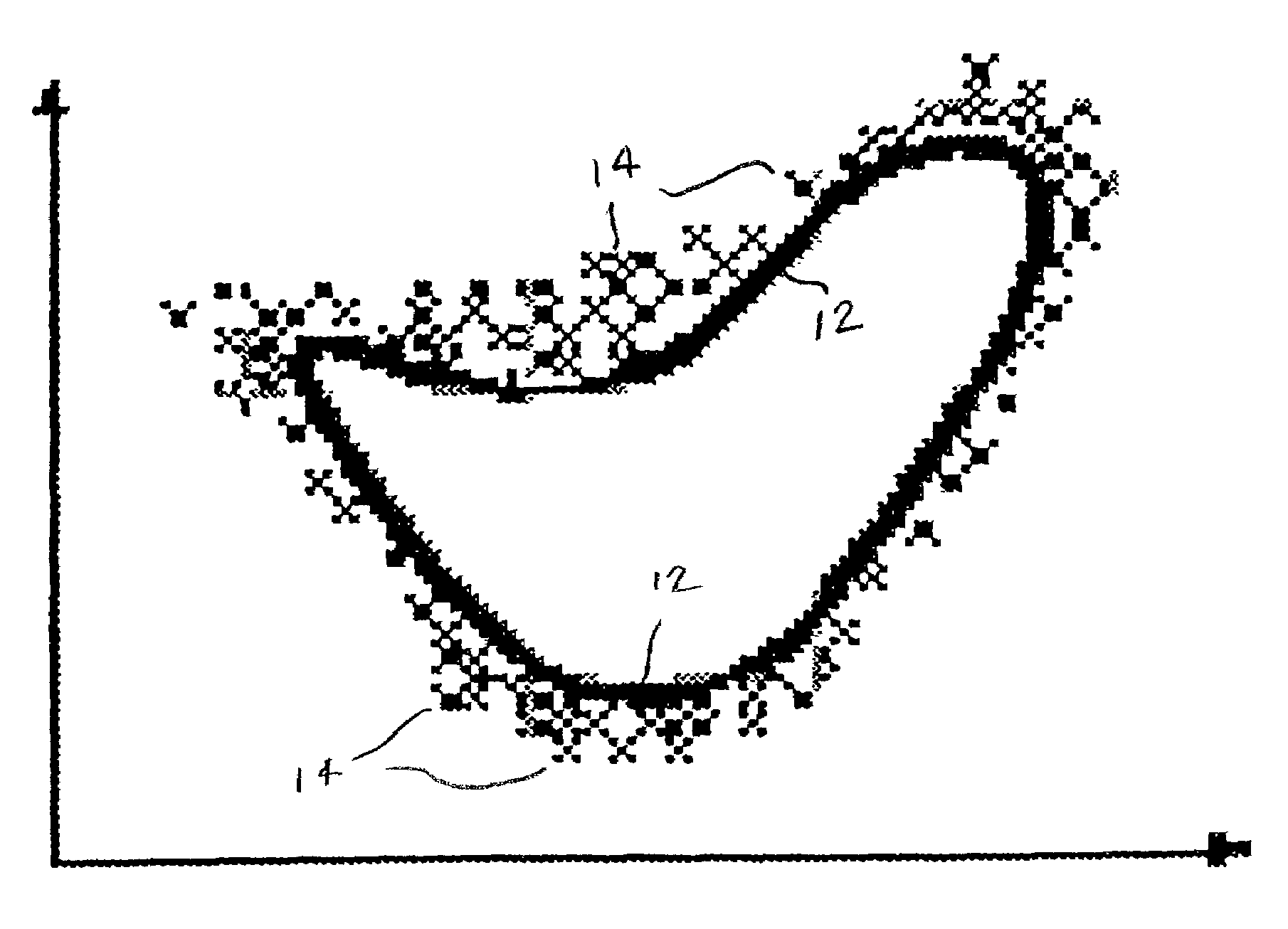
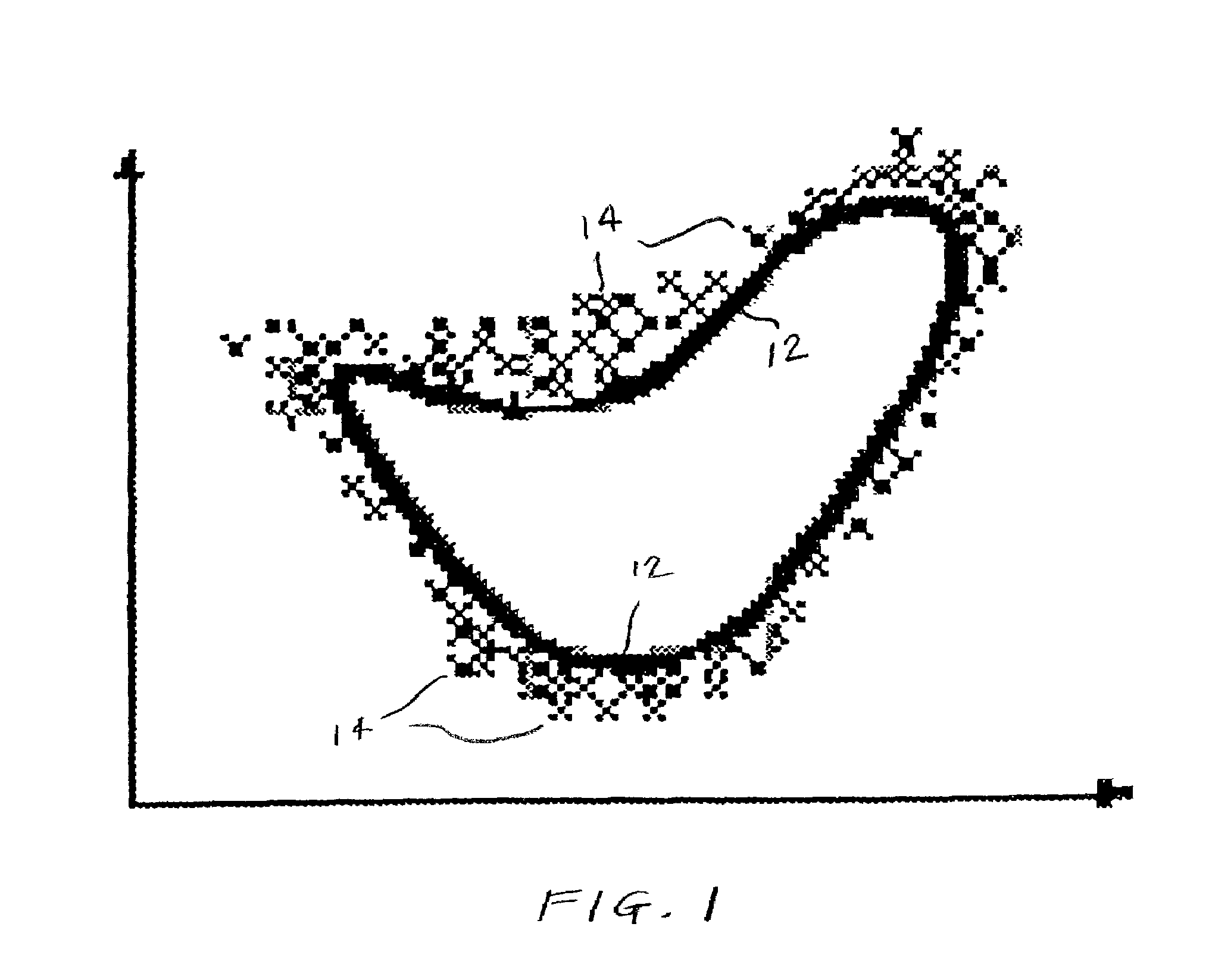
ActiveUS7424619B1Effective defenseMaintaining ability to detectMemory loss protectionUser identity/authority verificationAdaptive learningAnomaly detection
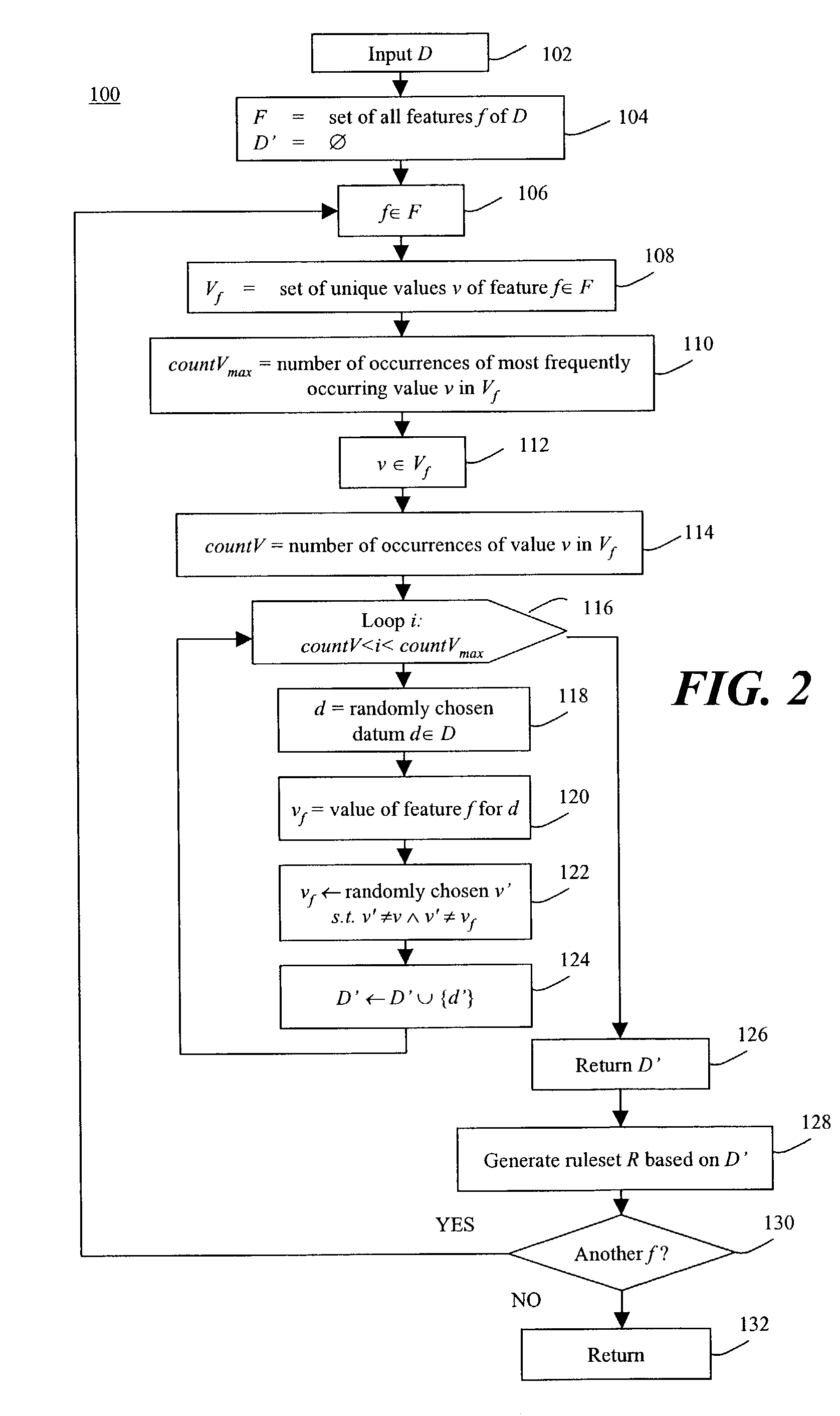
In a method of generating an anomaly detection model for classifying activities of a computer system, using a training set of data corresponding to activity on the computer system, the training set comprising a plurality of instances of data having features, and wherein each feature in said plurality of features has a plurality of values. For a selected feature and a selected value of the selected feature, a quantity is determined which corresponds to the relative sparsity of such value. The quantity may correspond to the difference between the number occurrences of the selected value and the number of occurrences of the most frequently occurring value. These instances are classified as anomaly and added to the training set of normal data to generate a rule set or other detection model.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
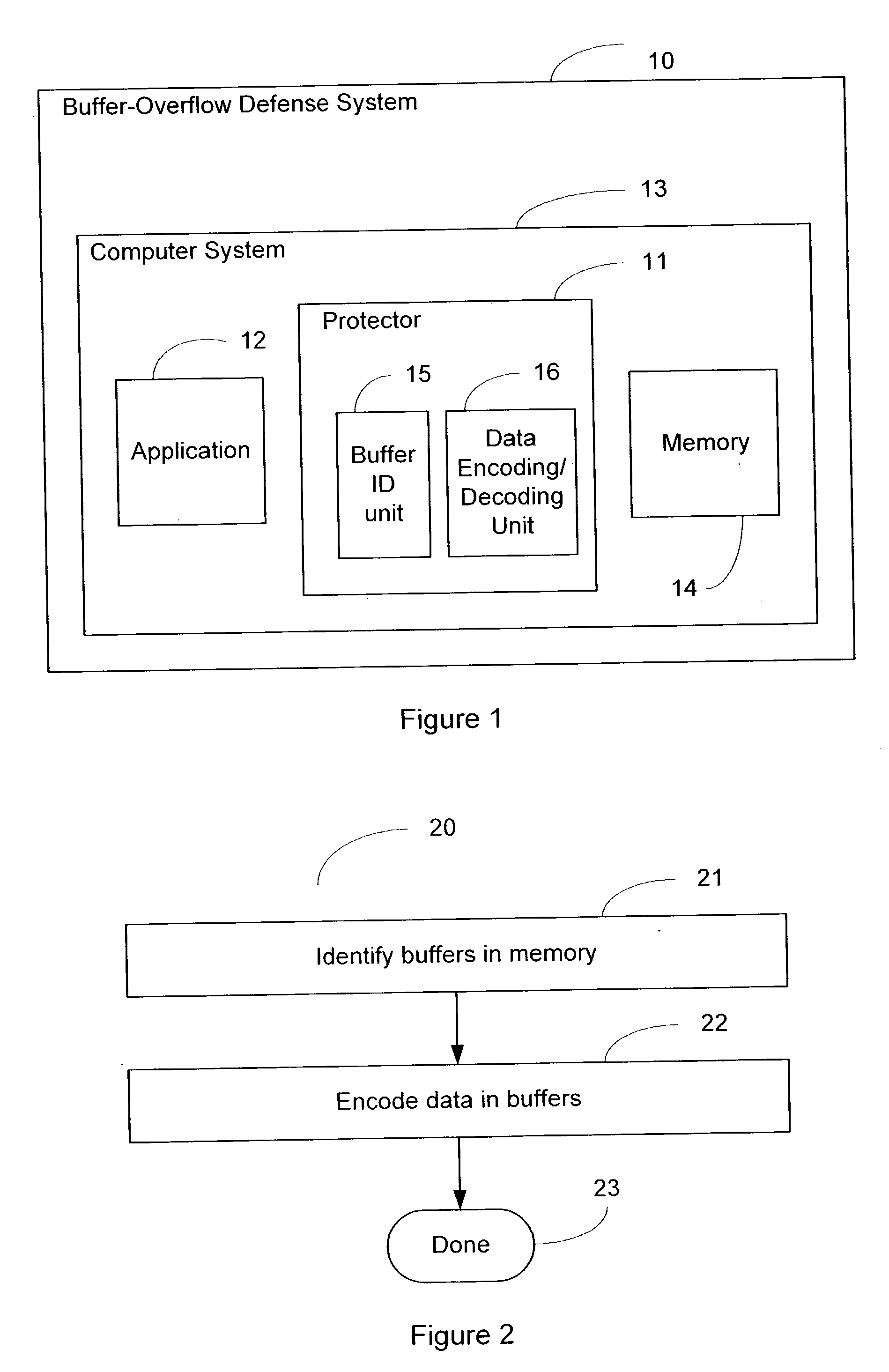
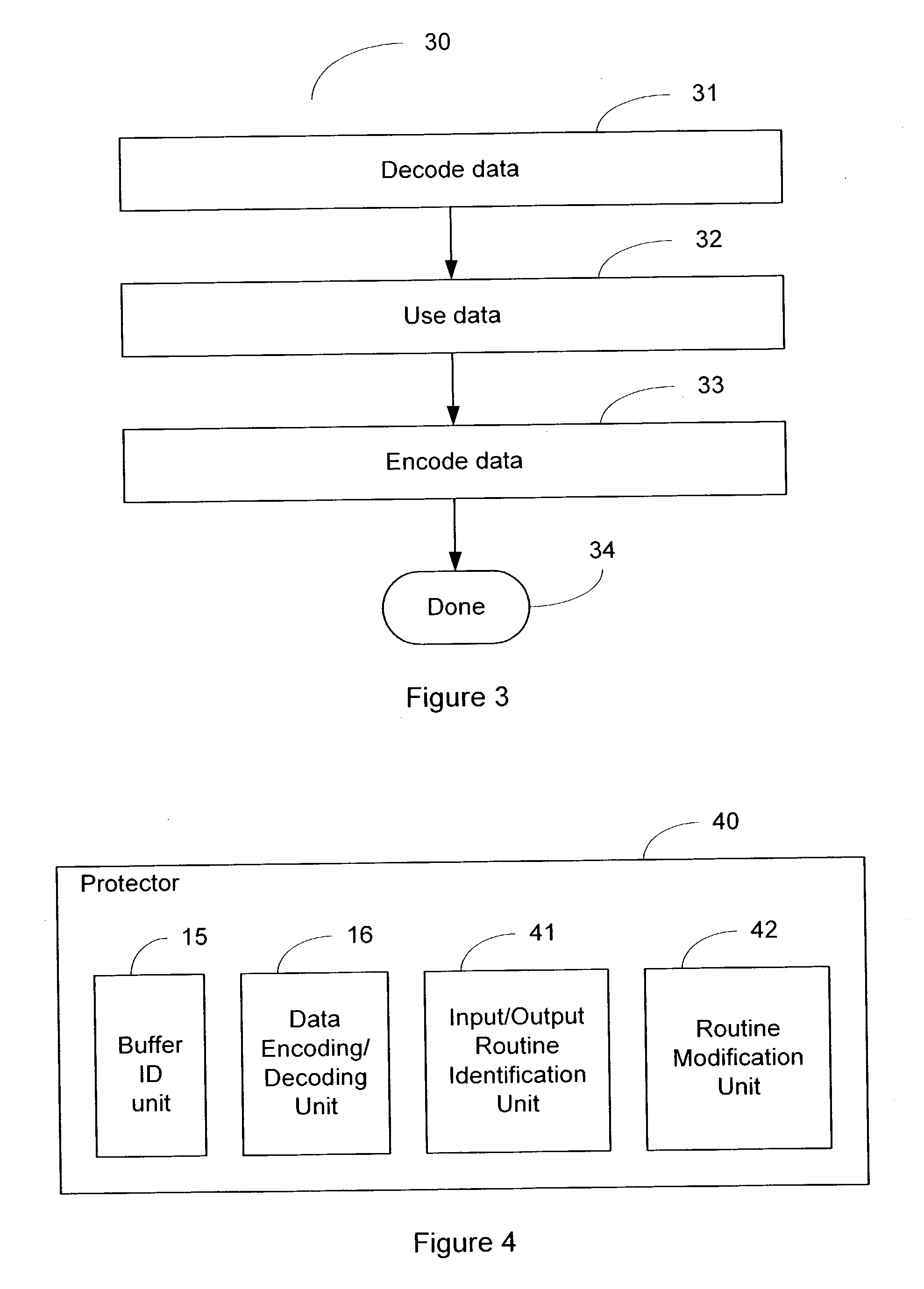
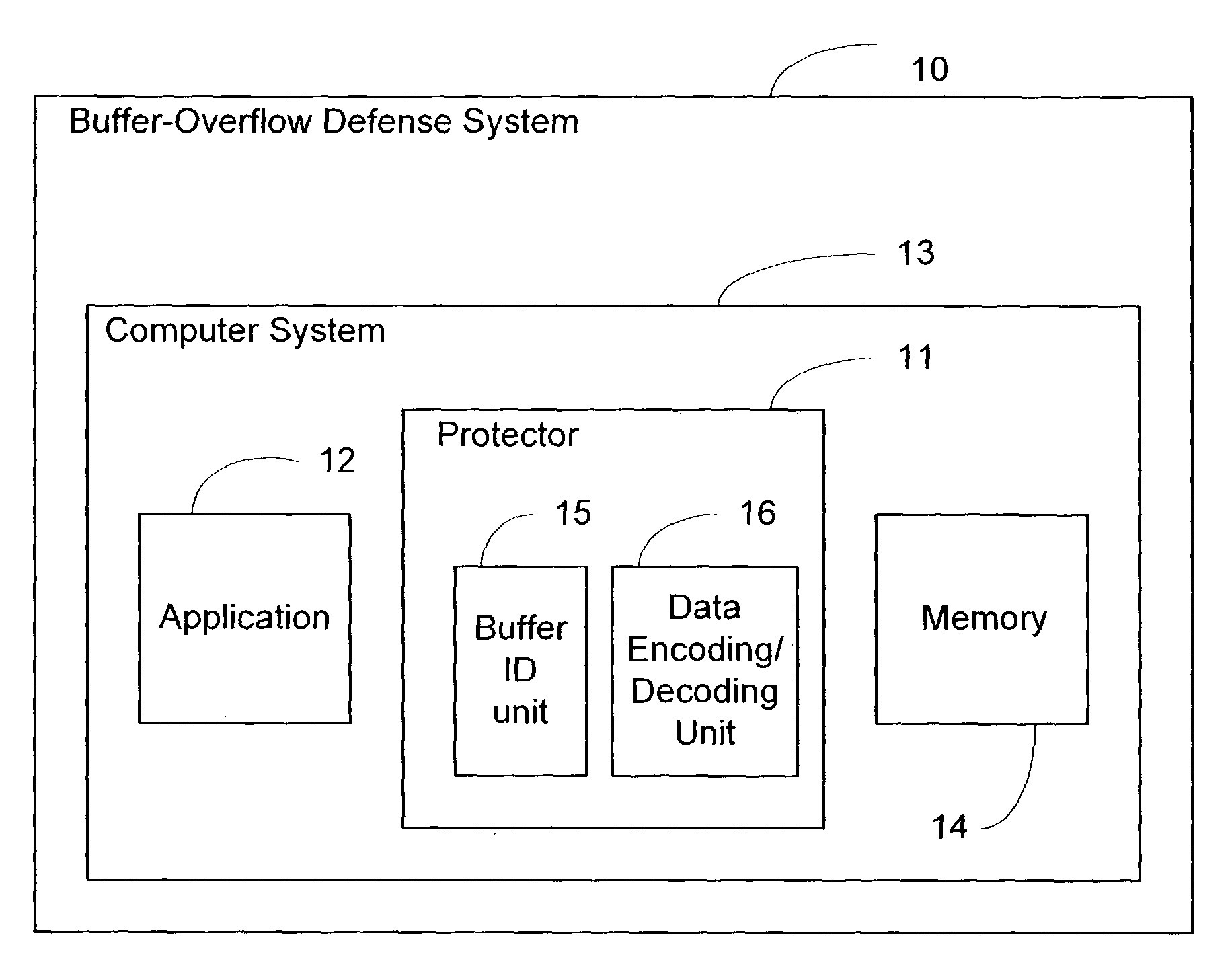
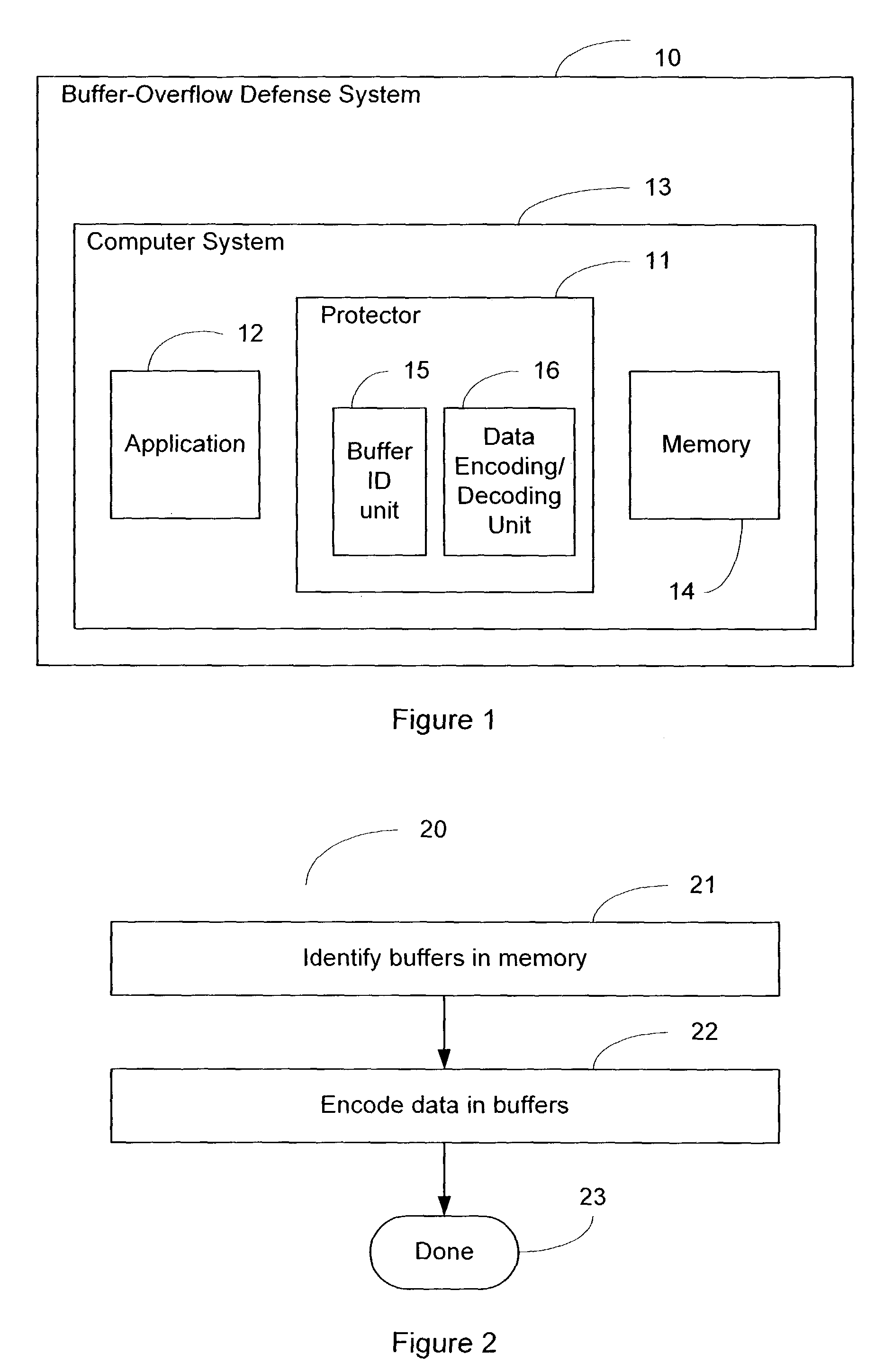
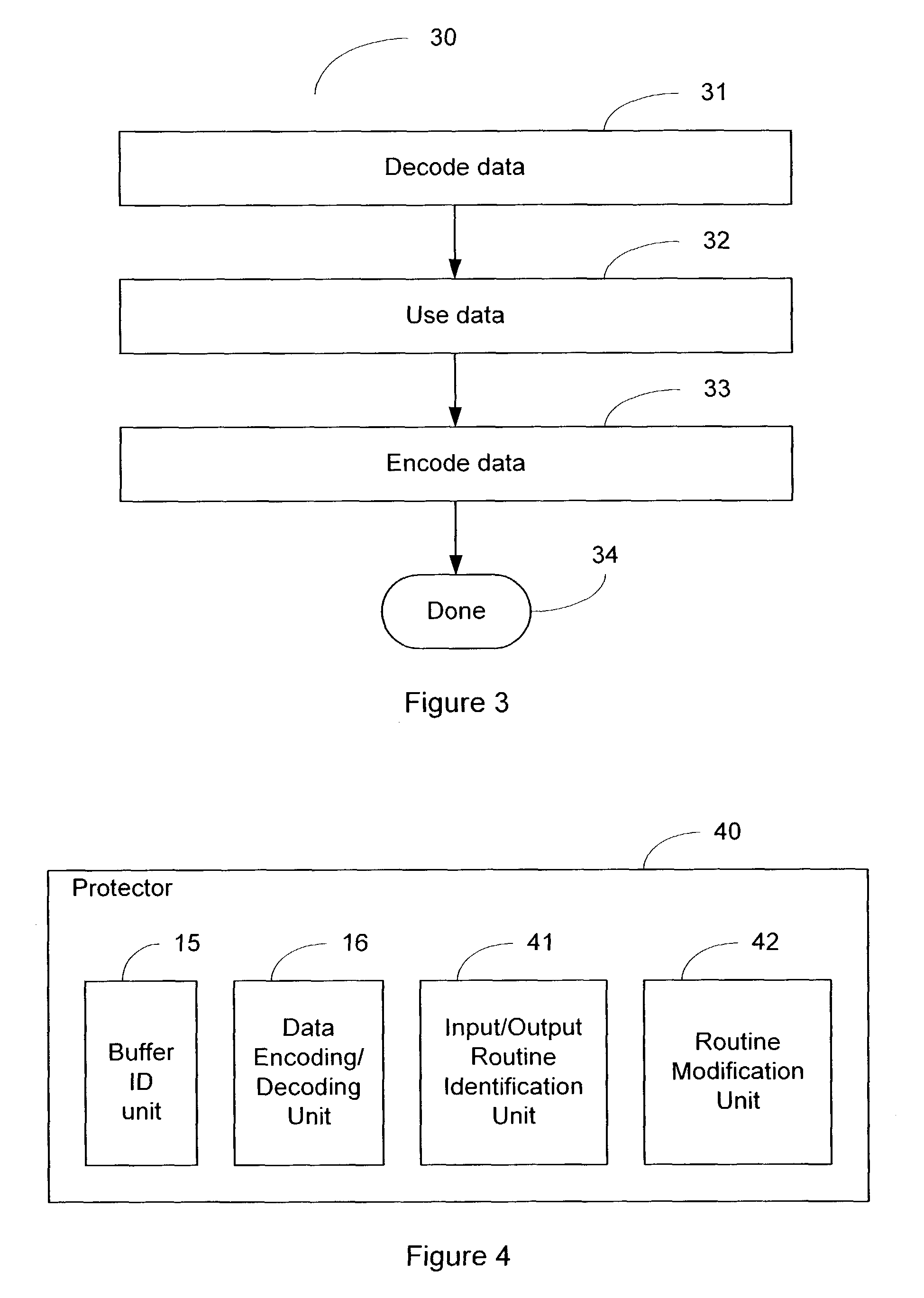
System and method of foiling buffer-overflow and alien-code attacks
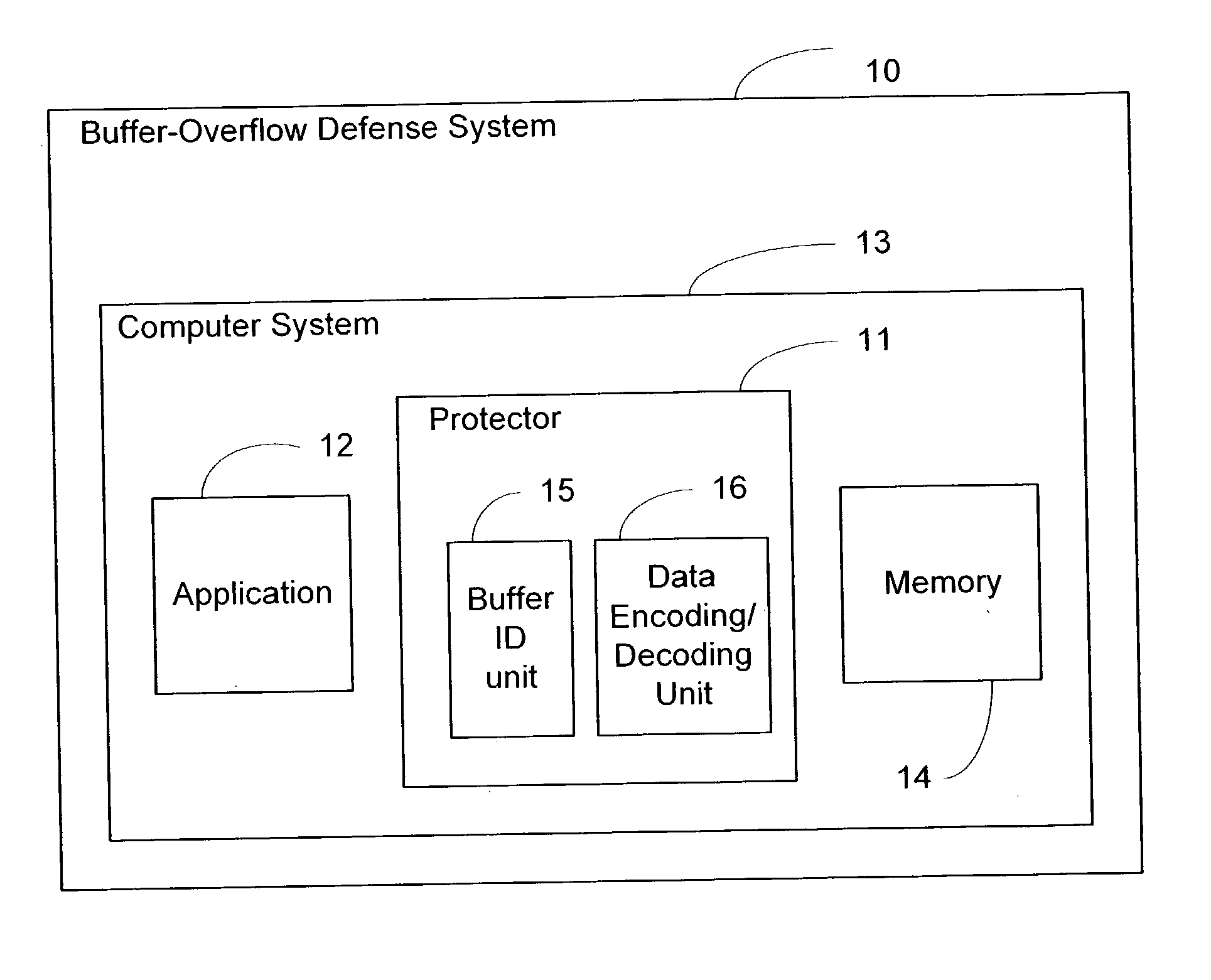
InactiveUS20030172293A1Protected growthShuts down buffer overflow attacksMemory loss protectionUnauthorized memory use protectionBuffer overflowApplication software
The present invention relates generally to computer software, and more specifically, to a system and method of foiling buffer-overflow and alien-code attacks. The invention protects computers from such attacks by encoding data placed in storage, and varying the encodings used in different storage areas. When the data is needed by a software application, the data is simply decoded in a complementary manner. This prevents storage areas written according to one usage from being used effectively for some other purpose. The method of the invention can be done in a number of ways. For example, a "protector" engine can be placed between a software application and memory, or the function calls in the software application itself, could be amended to include encoding and decoding. Other embodiments and alternatives are also described.
Owner:IRDETO CANADA CORP
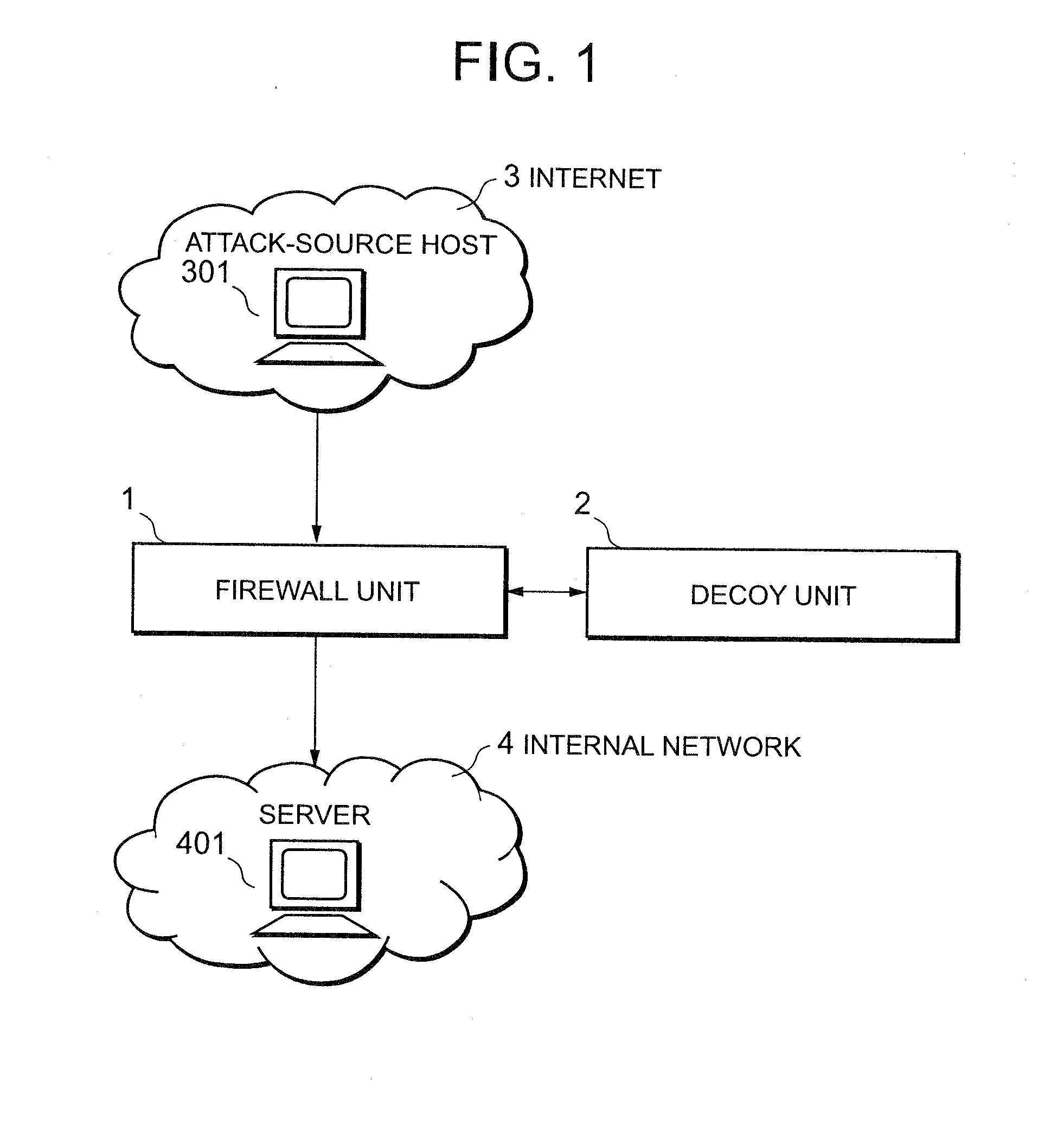
Attack defending system and attack defending method
InactiveUS20080282339A1Effective defenseEffective attackDigital data processing detailsUnauthorized memory use protectionCommunications systemDecoy
Owner:NEC CORP
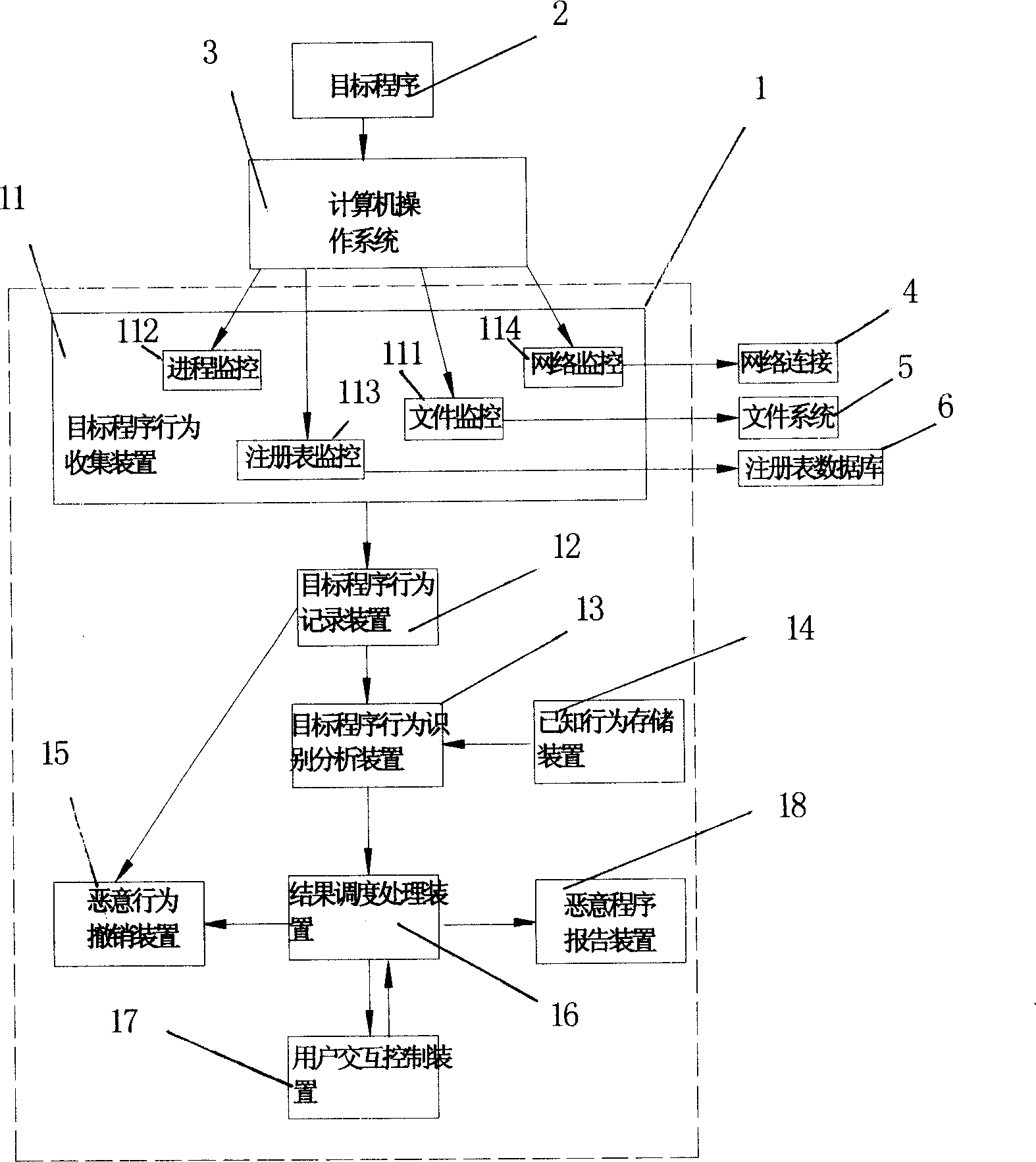
System and method for detecting and defending computer worm
ActiveCN1737722AEffective defenseOccupies less system resourcesDigital data processing detailsComputer wormOperational system
This invention relates to test and protective computer ill-purpose program system, which comprises the following parts: computer operation system monitor device to collect aim programs operation information; aim program operation record device to store aim programs operation records and to record repaired files, register form; known action characteristics memory device to store known, processed operation information and to store each operation relative danger degree weigh; aim program action identification analysis device to compare the aim program with known action; ill-purpose action removal device to remove the ill-purpose program.
Owner:ZHUHAI KINGSOFT SOFTWARE CO LTD
Malicious software image format detection model-oriented black box attack defense method and device thereof
ActiveCN110826059ADefense against attackImprove applicabilityCharacter and pattern recognitionPlatform integrity maintainanceData setAttack model
A malicious software image format detection model-oriented black box attack defense method comprises the steps of 1) obtaining a data set, and dividing the data set into a training set and a test set;2) converting into a malicious software image format; 3) constructing a black box attack model for generating disturbance based on a deep convolutional generative adversarial network (DCGAN), whereinthe structure of the black box attack model is divided into two parts, namely a generator and a discriminator; 4) through the continuous confrontation process between the generator and the discriminator constructed in the step 3), the generator finally generating a confrontation sample capable of simulating the sample B; 5) optimizing retraining of the malicious software assembly format detectionmodel by using the adversarial sample obtained in the step 4) to obtain a malicious software detection model capable of defending against the adversarial attack; and 6) identifying the malicious software by utilizing the malicious software detection model capable of defending against the attack. The invention further comprises a device for implementing the malicious software image format detection model-oriented black box attack defense method.
Owner:ZHEJIANG UNIV OF TECH
Implicit user verification and privacy protection method based on multi-dimensional behavior characteristics
ActiveCN103533546AEffective defenseEasy to useSecurity arrangementHigh level techniquesFeature vectorUser verification
The invention relates to an implicit user verification and privacy protection method based on multi-dimensional behavior characteristics. The method comprises the steps as follows: a, data of mobile equipment operation behaviors of a legitimate user is collected; b, a legitimate user operation characteristic model is established; c, a support vector machine is utilized for comparing current behavior characteristic vector with the legitimate user operation characteristic model, so that an operation comparing conclusion about whether a current user is legitimate is obtained, and the confidence level of the operation comparing conclusion is obtained; and d, probability that the current user is legitimate is calculated by a confidence level algorithm according to the current behavior characteristic vector and the confidence level, when the probability of the legitimate user is higher than a set threshold value, the current user is confirmed to be legitimate, otherwise, mobile equipment starts a privacy protection protocol which is set in advance. According to the implicit user verification and privacy protection method based on the multi-dimensional behavior characteristics, the power consumption is low, the probability of simulation and attack is low, accurate user identity recognition can be performed under the condition that the user cannot perceive, and a corresponding privacy protective measure is taken.
Owner:苏州美信互联信息技术有限公司
Method and system for preventing ARP message attack
InactiveCN101175080AEffective defenseEasy to manage centrallyNetwork connectionsSecuring communicationAddress Resolution ProtocolIp address
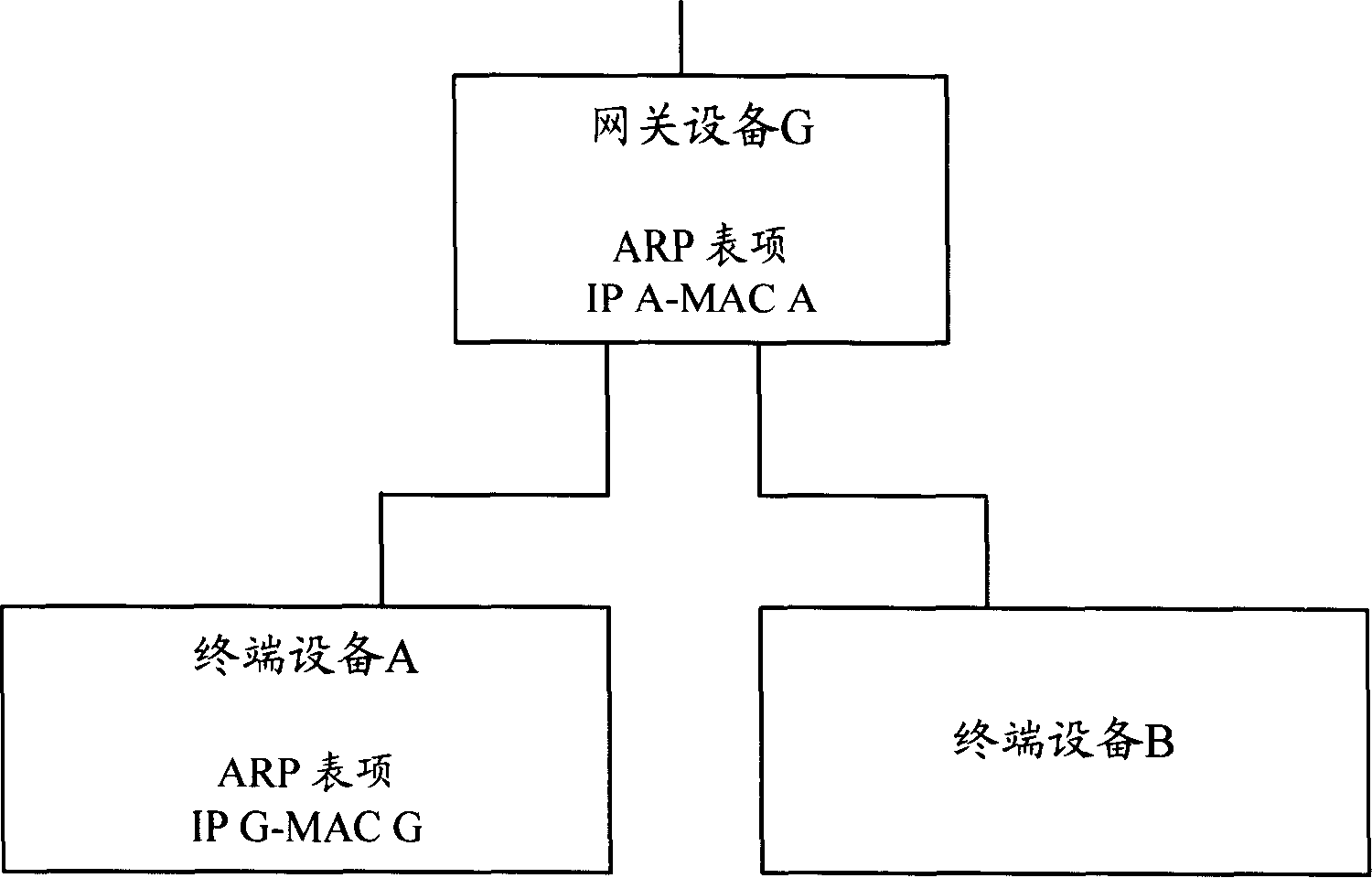
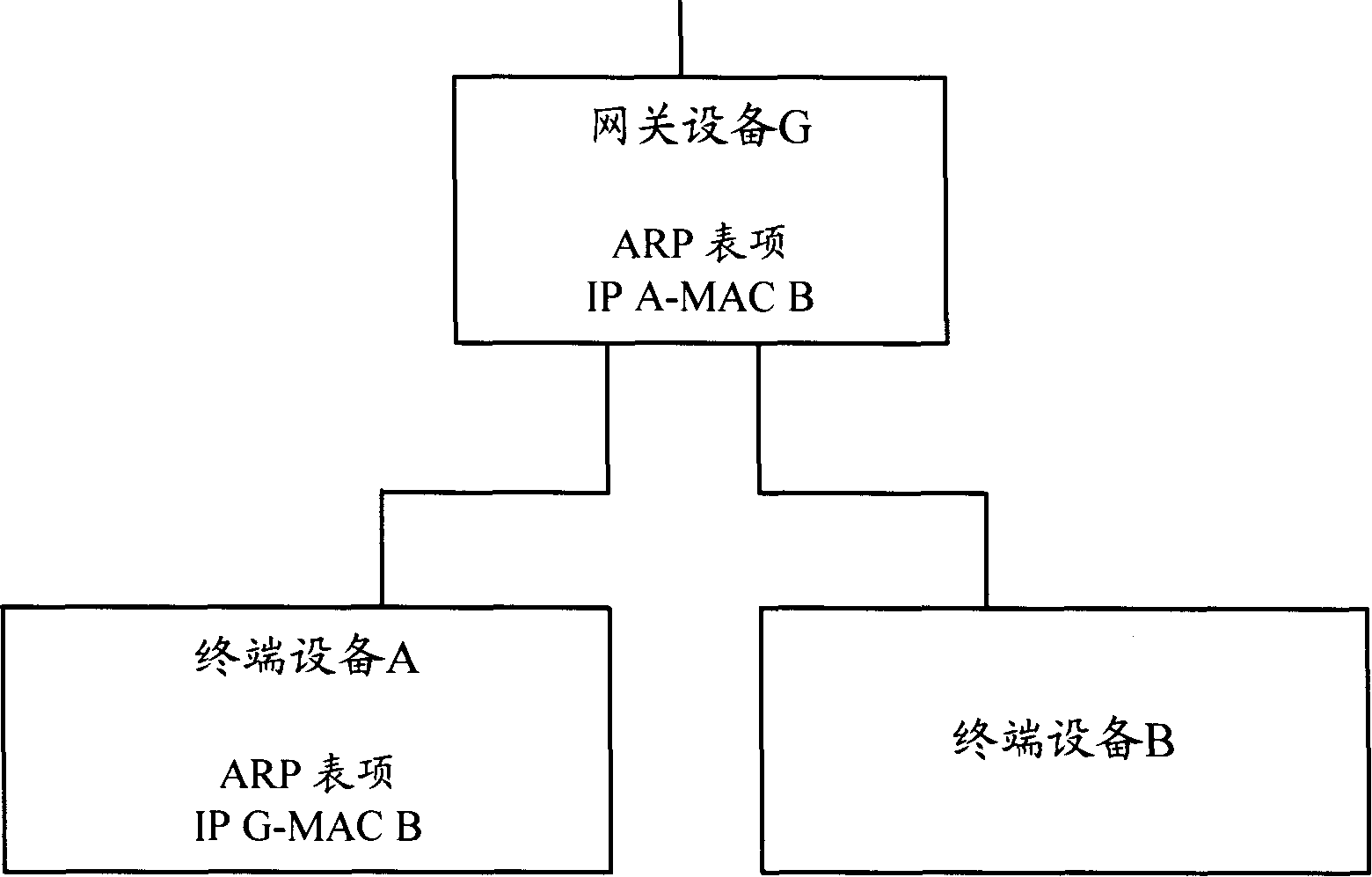
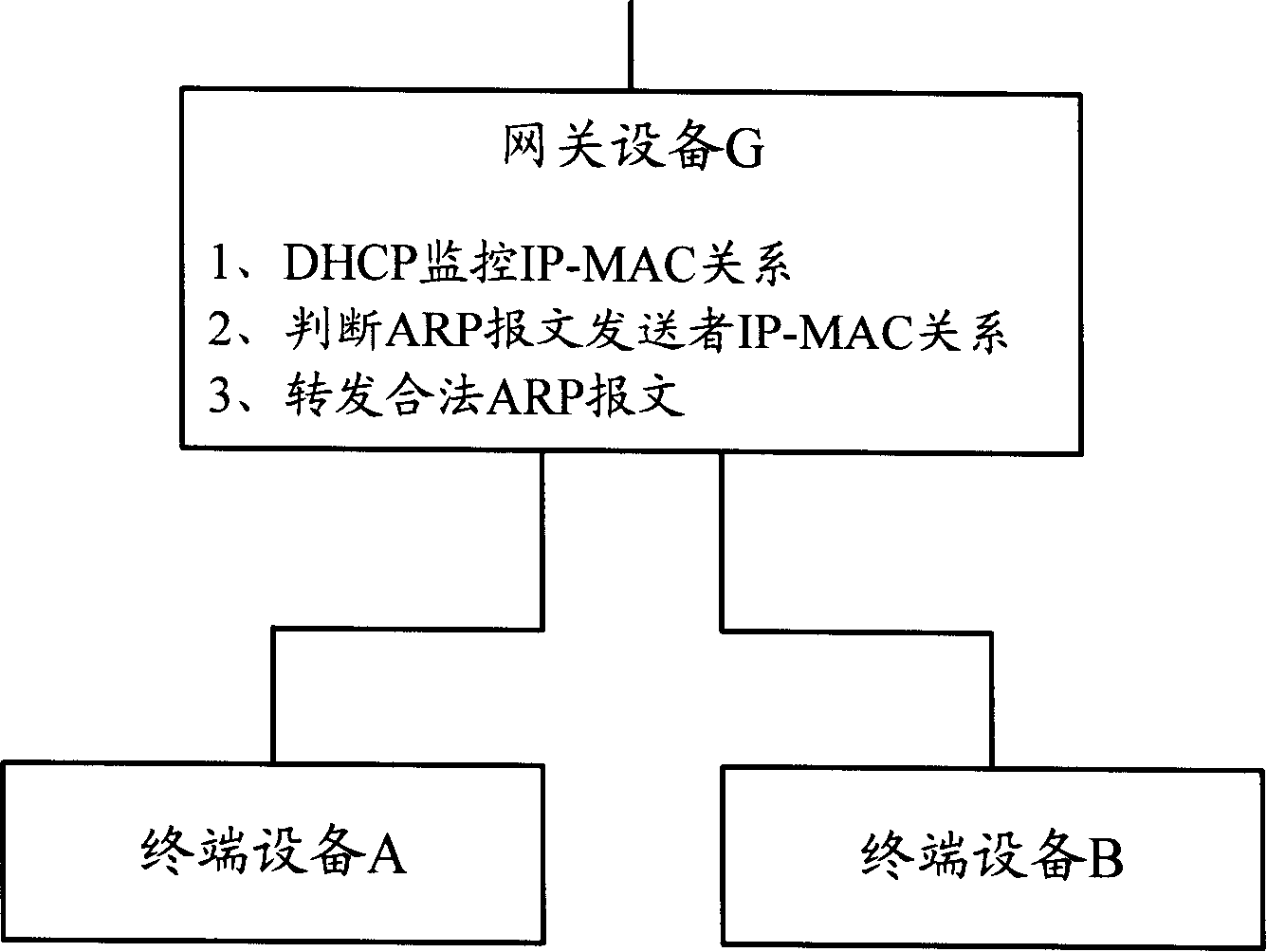
The invention discloses a method for preventing ARP (address resolution protocol) message attack, which comprises the following procedures: a DHCP (dynamic host configuration protocol) server adds IP address-MAC address into DHCP message and sends to a user terminal; the user terminal receives the DHCP message, analyzes the IP address-MAC address couple included in the DHCP message and changes the message into local ARP table which can not be dynamically rewritten, so as to prevent the network from attacking of the attack message through rewriting the ARP table of user terminal. The invention also discloses a system for preventing ARP message attack. With the invention, the gateway device in network and the user terminal are capable of defending the received ARP attack message. In addition, the important ARP tables of user terminals in network are under unified configuration by DHCP server, which is convenient for centralized management.
Owner:NEW H3C TECH CO LTD
Method for testing integrity of cloud storage data
InactiveCN104993937AEffective defenseSecurity is not threatenedUser identity/authority verificationThird partyCloud user
The invention belongs to the field of communication technology, and specifically relates to a method for testing integrity of cloud storage data. The method provided by the invention mainly comprises: a system initializes and allocates a signature key and a corresponding authentication key to a user; the user uploads storage data to a cloud server; an independent third party auditor tests the integrity of the storage data stored on the cloud server; and the user judges the test correctness of the third party auditor. The process provided by the invention has the following advantages: the third party auditor needs no user management certificate, namely TPA faces no certificate management problem; moreover, the method in the scheme can be used for effectively resisting malicious third party auditors, and when the third party auditor deviates correct protocol contents, the security of the scheme will not be threatened, and the third party auditor cannot successfully cheat the cloud user and (or) the cloud server.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
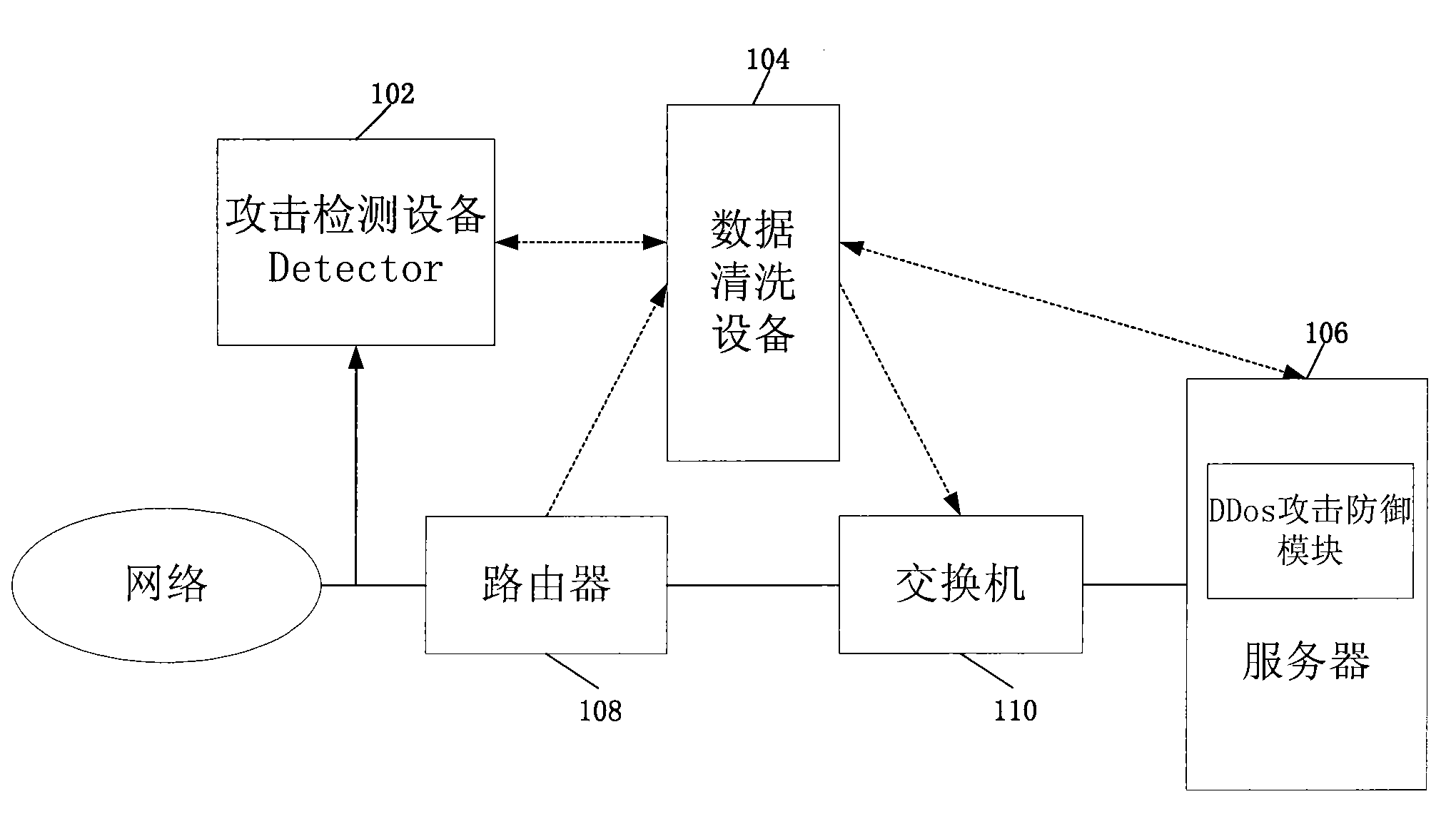
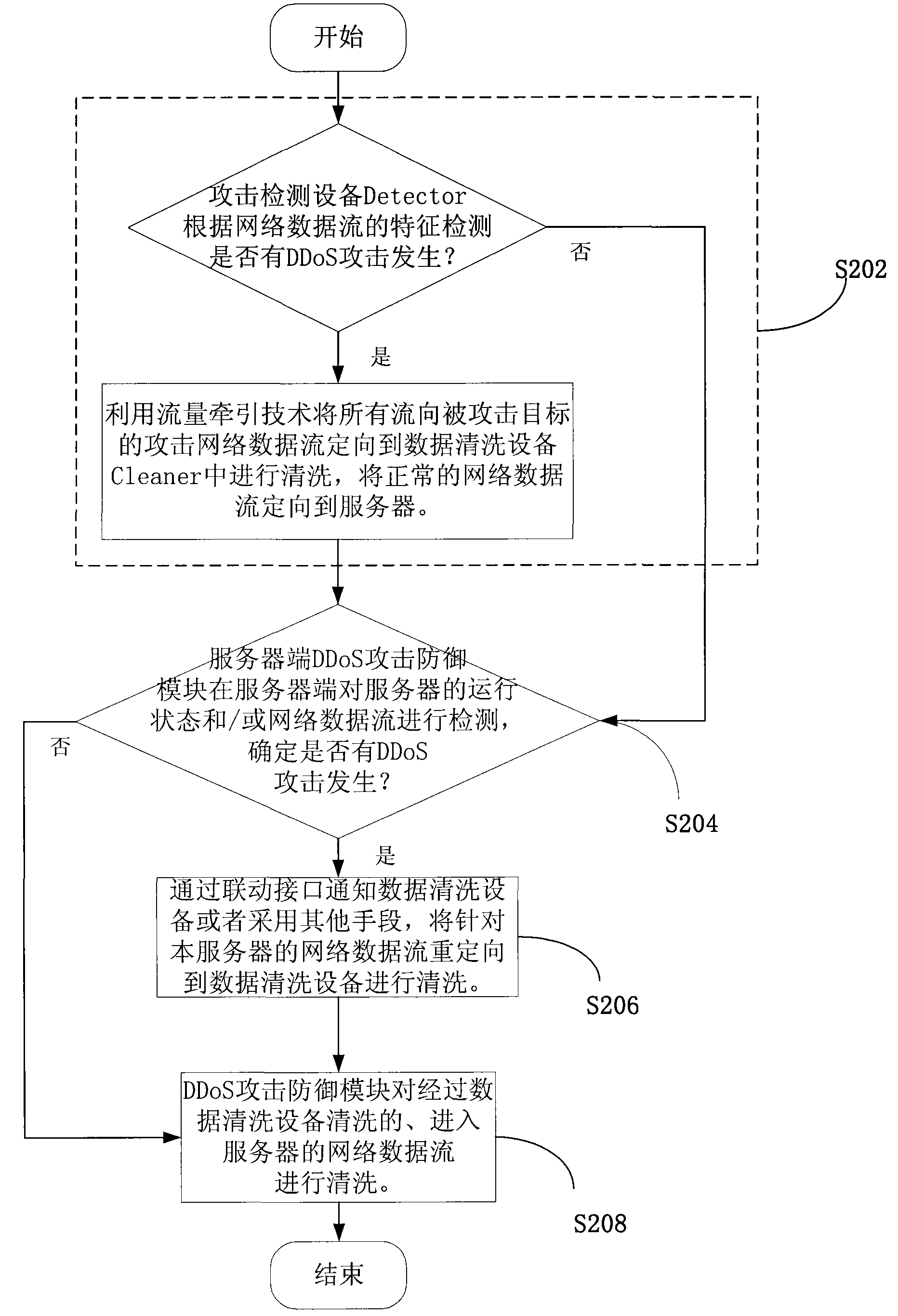
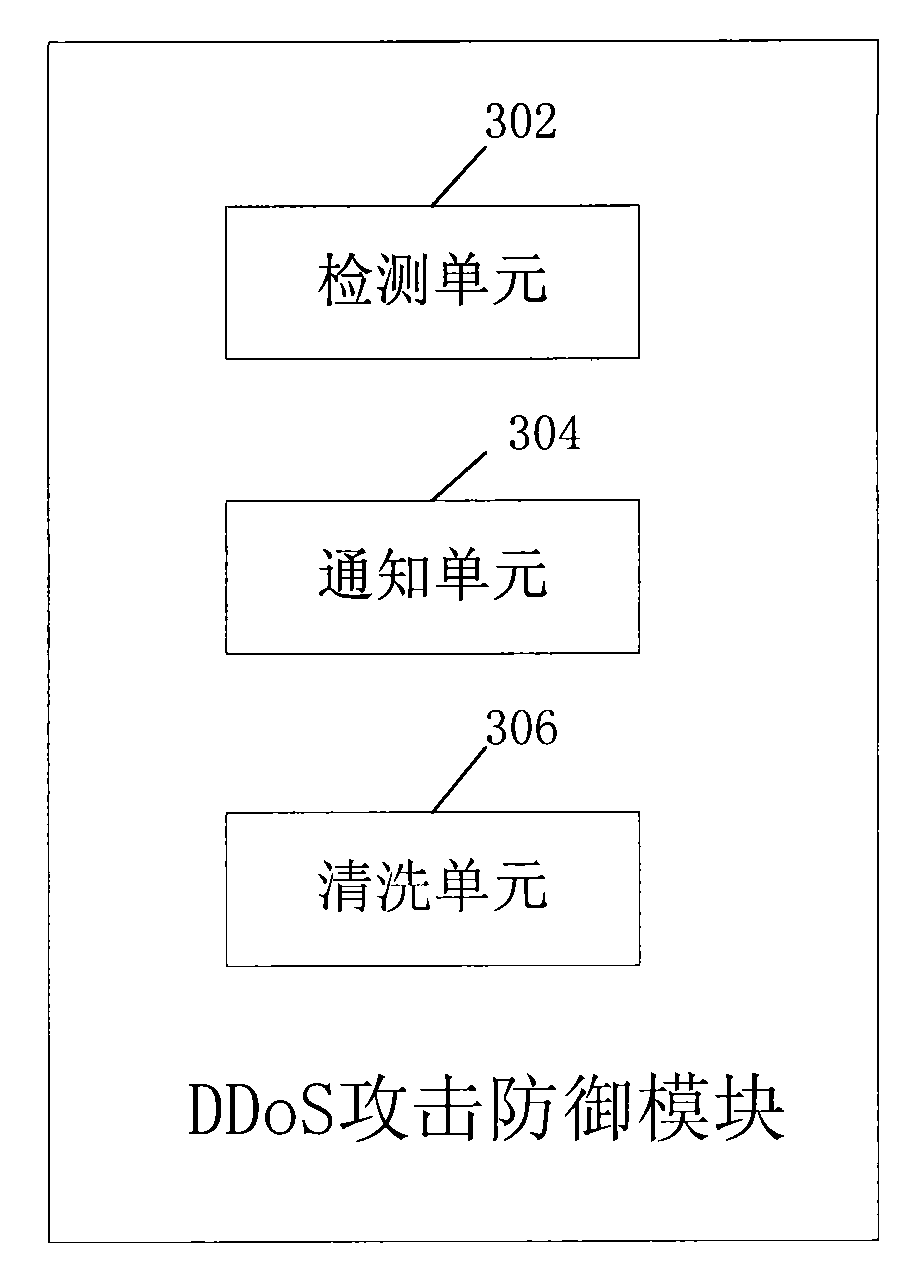
Method, network equipment and network system for defending distributed denial service DDoS attack
The embodiment of the invention discloses a method for defending distributed denial service DDoS attack, comprising the following steps: detecting the running state of a server at a server terminal or network data flow which enters the server, and judging whether DDoS attack which aims at the server occurs or not; and informing data cleaning equipment of cleaning the network data flow which flows to the server if the DDoS attack which aims at the server occurs. The embodiment of the invention also discloses network equipment and a network system. By the embodiment of the invention, detection and initial defense can be carried out from a target terminal which is attacked, the attack state can be accurately obtained, and information required by defense can be provided, thereby the DDoS attack is effectively defended.
Owner:HUAWEI TECH CO LTD
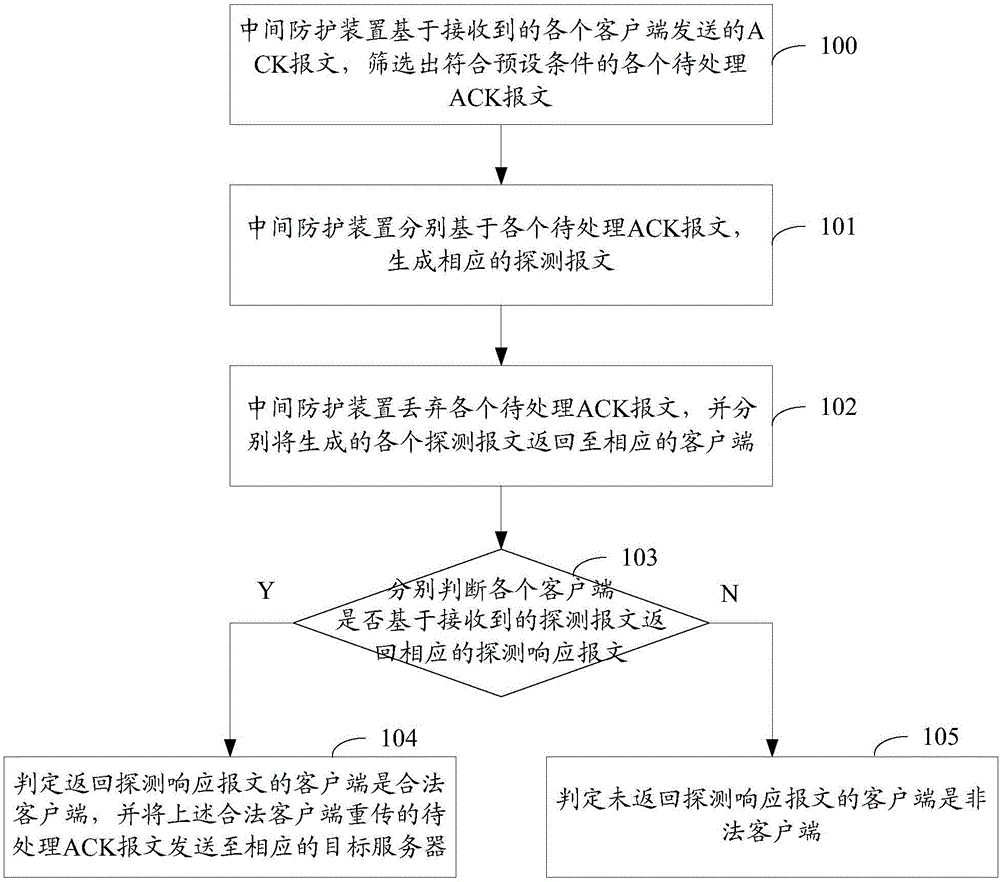
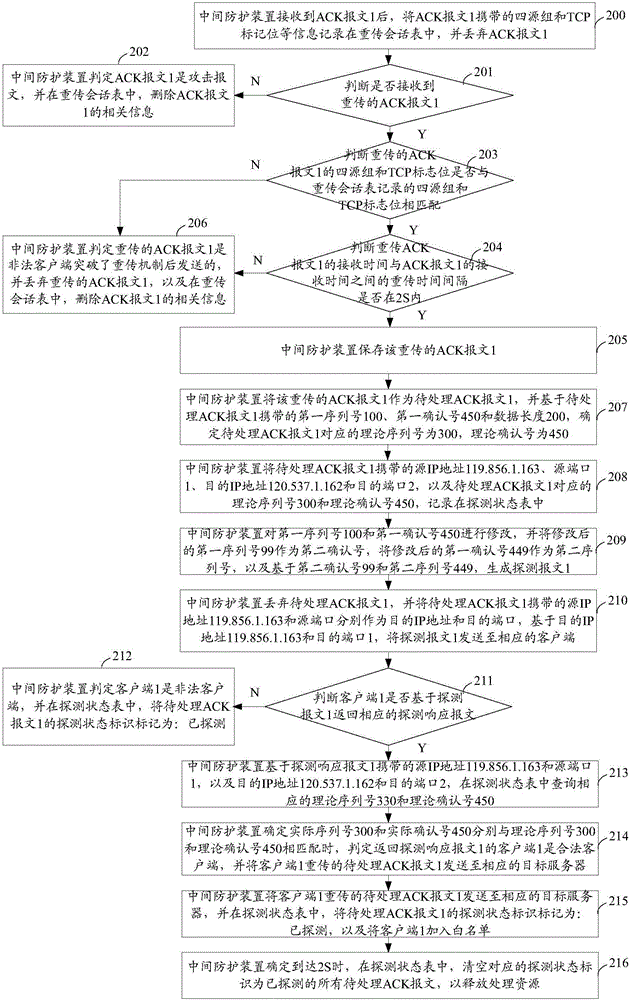
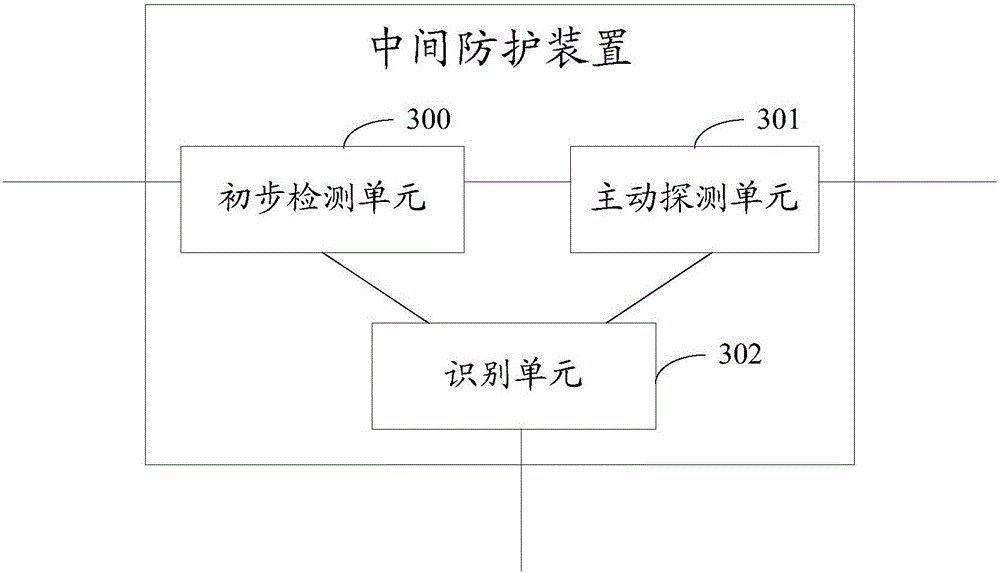
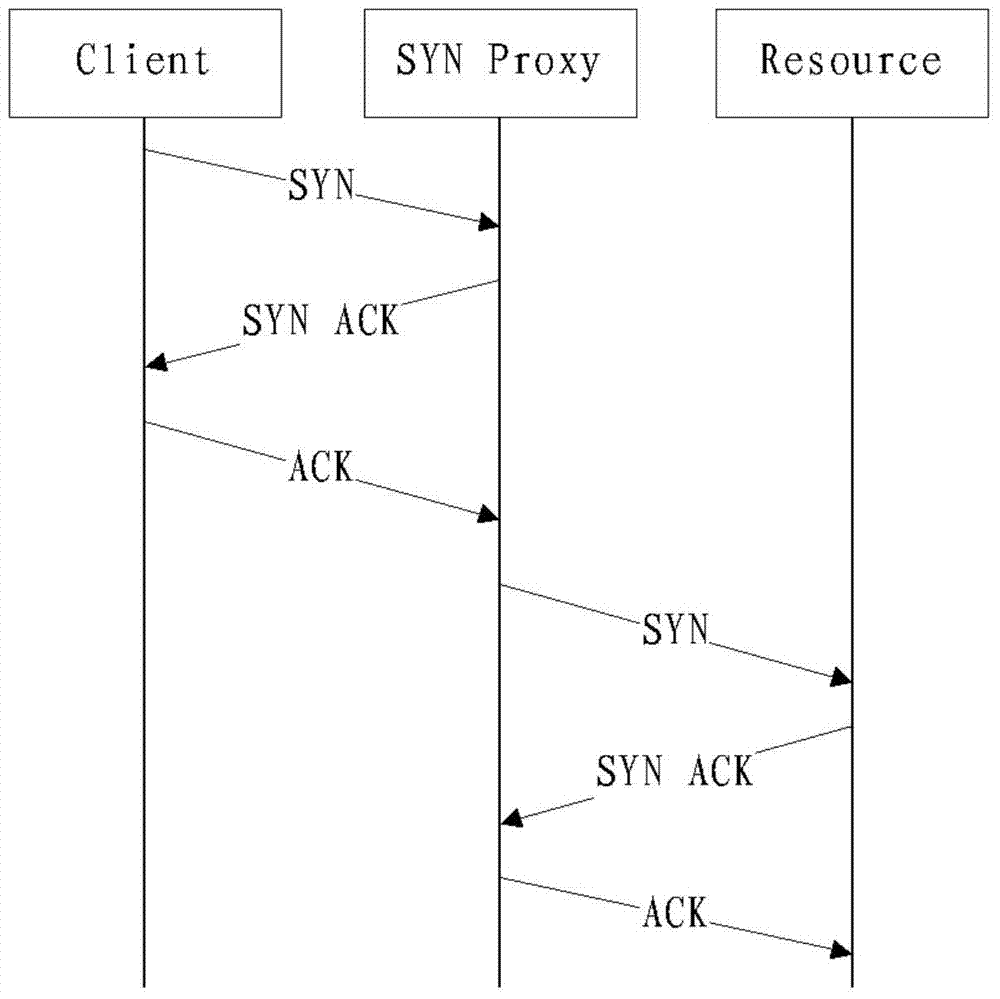
ACK Flood attack protection method and intermediate protection device
The invention discloses an ACK Flood attack protection method and an intermediate protection device for improving the ACK Flood attack protection effect while ensuring a non-interrupted connection between clients and target servers. The method comprises the steps that the intermediate protection device generates corresponding detection messages based on to-be-processed ACK messages respectively, discards the to-be-processed ACK messages, respectively returns the detection messages to corresponding clients, whether the clients returning detection response messages are legal clients, and to-be-processed ACK messages retransmitted by the legal clients are sent to corresponding target servers; and the clients that do not return the detection response messages are determines as illegal clients. In this way, the intermediate protection device can identify the illegal clients while ensuring the non-interrupted connection between clients and target servers so as to improve the ACK Flood attack protection effect.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Safe positioning method of wireless sensor network based on trust level evaluation
ActiveCN105873065AEffective defensePrecise positioningNetwork topologiesSecurity arrangementNODALWireless mesh network
The invention provides a safe positioning method of a wireless sensor network based on trust level evaluation. A positioning attribute set is provided for a trust entity to carry out evaluation behaviors. According to the positioning attribute set, trust levels of beacon nodes are provided in a value form by quantifying key behavior expressions in node positioning processes. Moreover, a threshold value is determined; attack nodes are filtered; and moreover, the work of normal nodes cannot be influenced. When the attack nodes invade a system, as trust relationship is established, the attack nodes are filtered and will not participate in the positioning processes of the normal nodes.
Owner:NANJING UNIV OF POSTS & TELECOMM
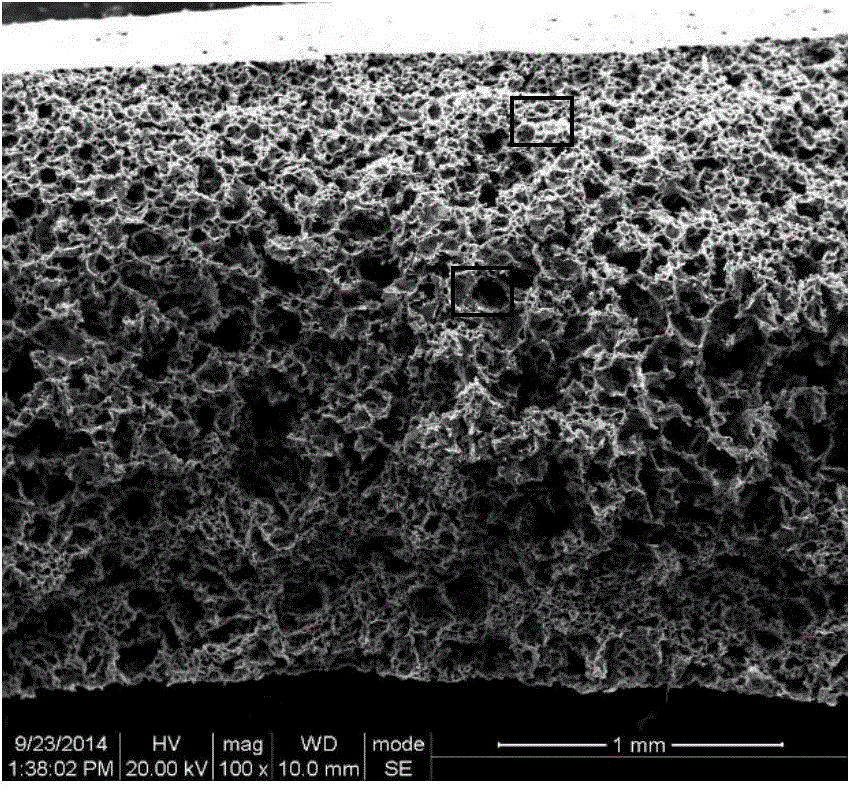
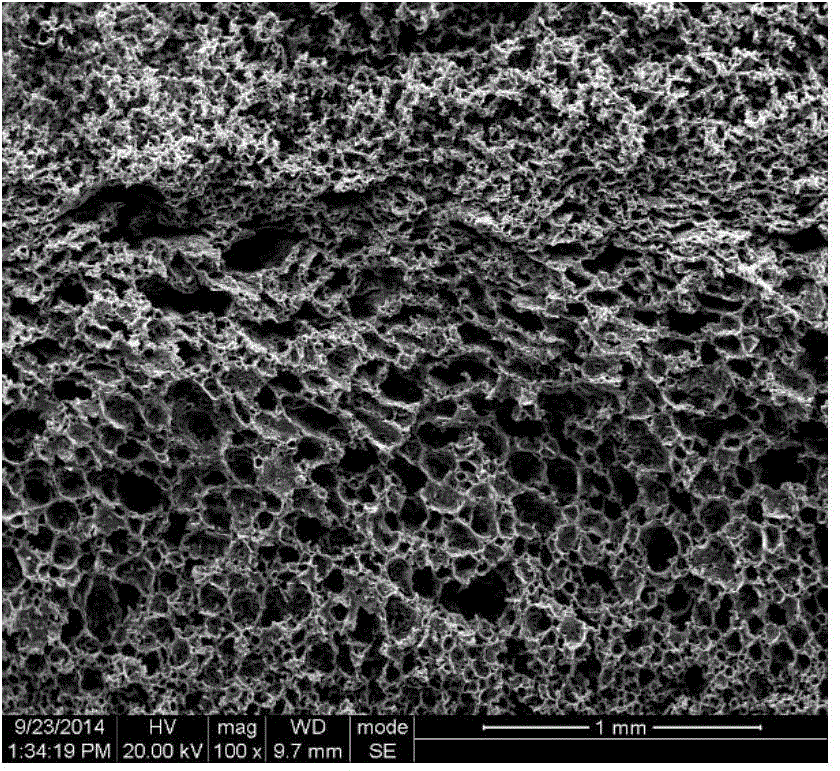
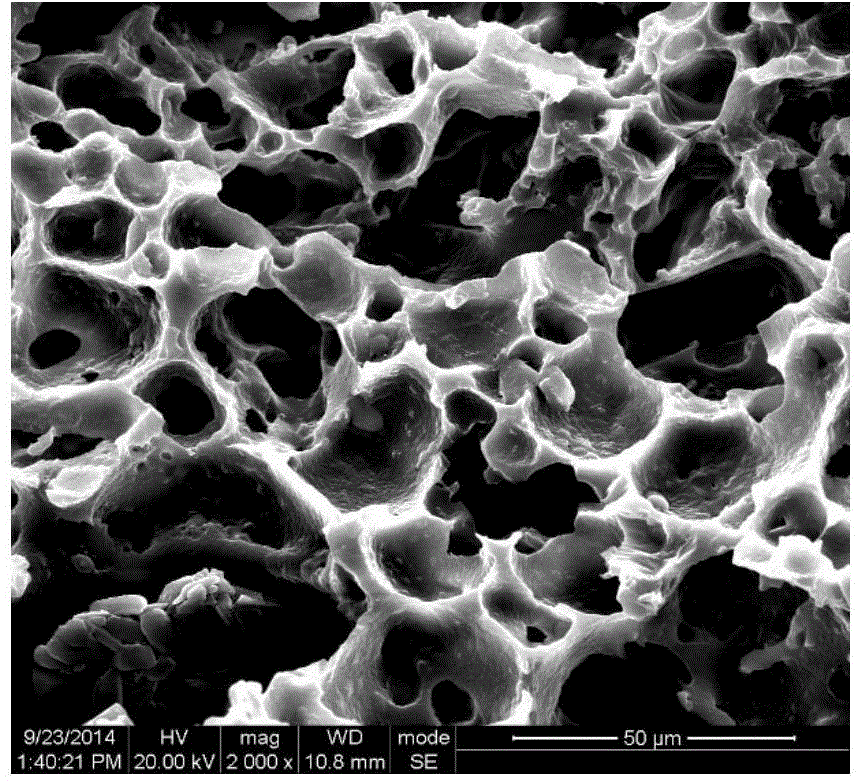
Porous polyurethane film used for artificial skin and having gradient porous structure and preparation method of porous polyurethane
The invention discloses a preparation method of a porous polyurethane film with a gradient porous structure. The preparation method is characterized by comprising the following steps: adding polyurethane into a solvent for dissolving, adding a pore-foaming agent, and mechanically stirring for a period of time to obtain suspension; defoaming the suspension in vacuum, carrying out film casting on a mold, carrying out curing film formation in absolute ethyl alcohol coagulation bath, soaking the film in deionized water to dissolve the pore-foaming agent and completely remove the pore-foaming agent; taking out the film, drying the film in a blast oven to obtain the porous polyurethane film with the gradient porous structure, the upper and lower surfaces of the porous polyurethane film are trim and not curled, and the hand feeling is good. The film can be used as artificial skin and has the advantages of good water and air permeability, high water absorption, excellent mechanical properties, good biological affinity, etc.
Owner:SICHUAN UNIV
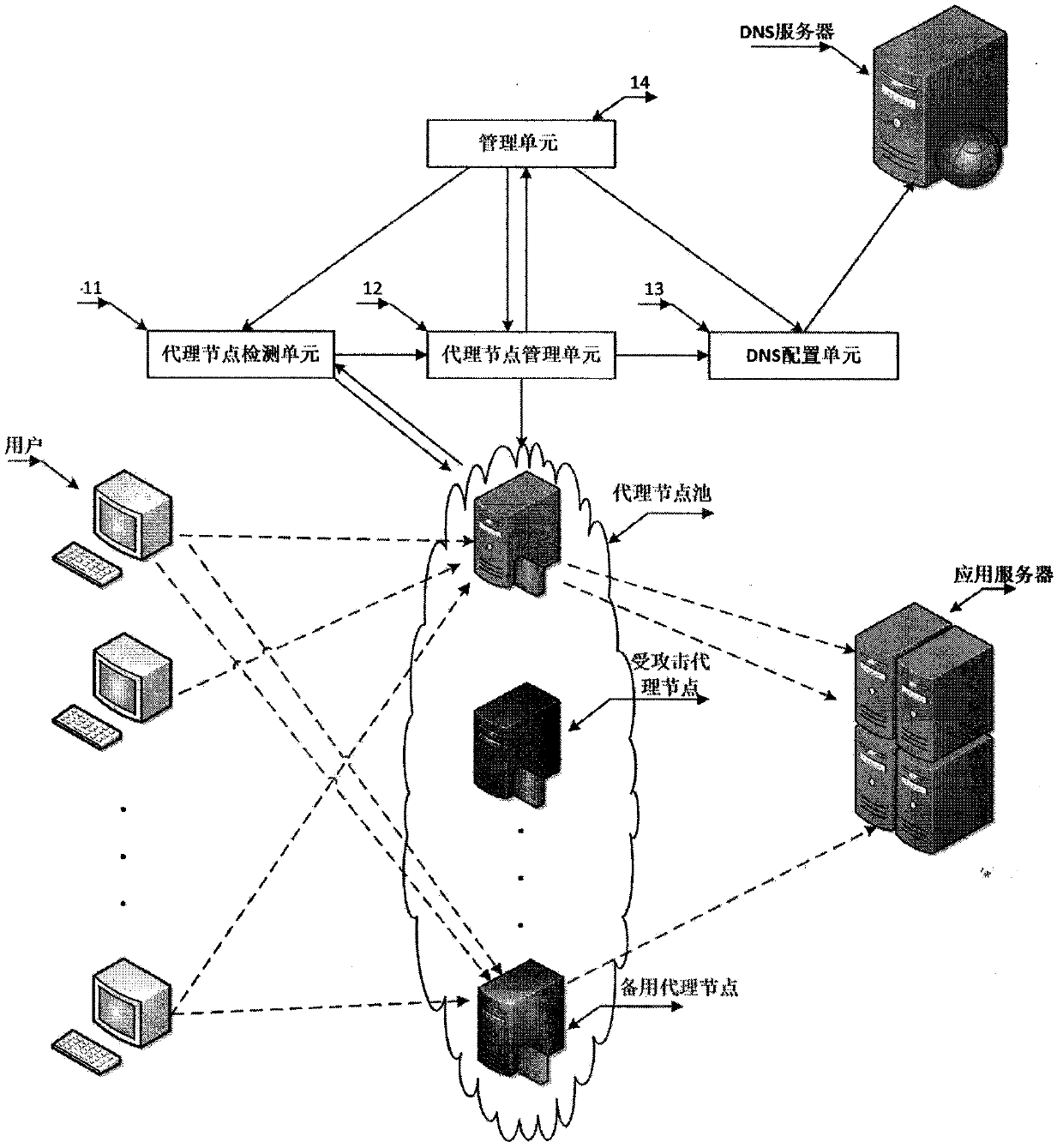
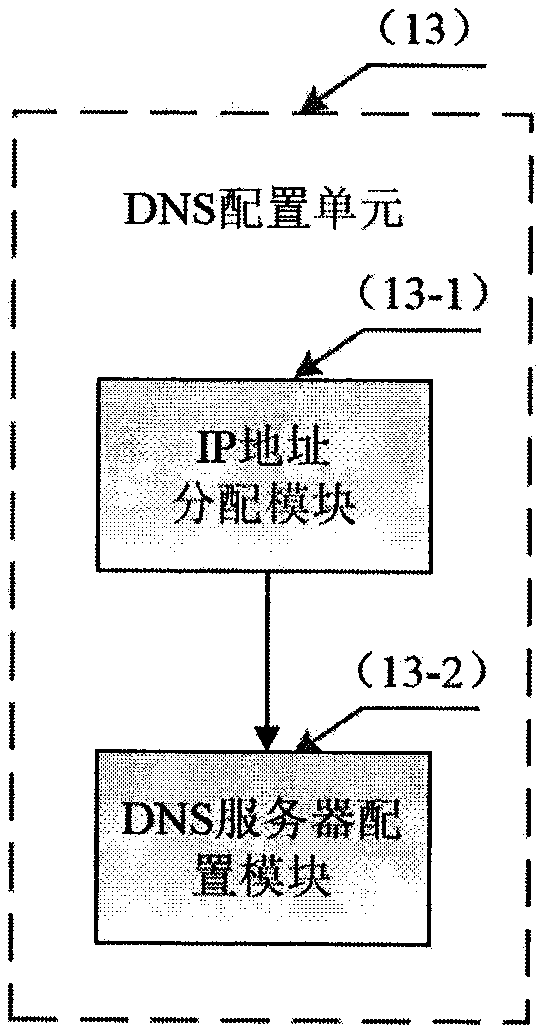
DDoS attack defense system and method based on dynamic transformation
The invention provides a DDoS attack defense system and method based on dynamic transformation, which break through the characteristics of traditional passive defense and static defense. The method has the basic thought that: under normal flow, a small number of proxy nodes are adopted to transmit communication between a user and an application server, so that normal communication requirements aremet, and resources are saved; and when a DDoS attack is received, a large number of dynamic proxy nodes are started to transmit communication between the user and the application server, the standbyproxy node is continuously used for replacing the attacked proxy node, the user flow is migrated to the new proxy node, and the attacked proxy node is closed, so that the DDoS attack strength is rapidly reduced, and the purpose of defending against large-flow attacks with small bandwidth is achieved. In addition, the dynamic change of the proxy node enables the attacker not to obtain the internalnetwork topology structure of the system, so that the scanning detection of the attacker on the system can be effectively blocked. The system does not increase user load, is transparent to users, andprovides continuous and stable service for the users.
Owner:北京卫达信息技术有限公司
Permanent magnet direct-drive wind-powered generator, system and stator thereof
ActiveCN104810942AReduce risk of erosionGuaranteed insulation reliabilityEngine sealsMagnetic circuit stationary partsPropellerEngineering
The invention provides a permanent magnet direct-drive wind-powered generator, system and stator thereof. The stator comprises a stator bracket, a stator iron core, a propeller side gear pressing plate and a propeller side enclosing plate; the propeller side gear pressing plate is arranged on the axial end surface of propeller side of the stator iron core; a first air hole is formed in the peripheral wall of the stator bracket; a second air hole is formed in the propeller side gear pressing plate; the stator further comprises an air channel for communicating the first air hole with the second air hole; the air channel passes through the inner part of the stator iron core; a comb teeth air feeding hole is formed in the propeller side enclosing plate and is connected with the second air hole through an air guide tube; a first spiral comb teeth structure is annular in the whole appearance and is communicated with the comb teeth air feeding hole is arranged on the propeller side enclosing plate; first spiral comb teeth are positioned in annular gaps formed by the propeller side enclosing plate and a rotor sealing ring. According to the technical scheme, the rotor has the advantage that the multi-phase airflow sealing can be performed for the annular gap between the propeller side enclosing plate and the rotor sealing ring.
Owner:XINJIANG GOLDWIND SCI & TECH
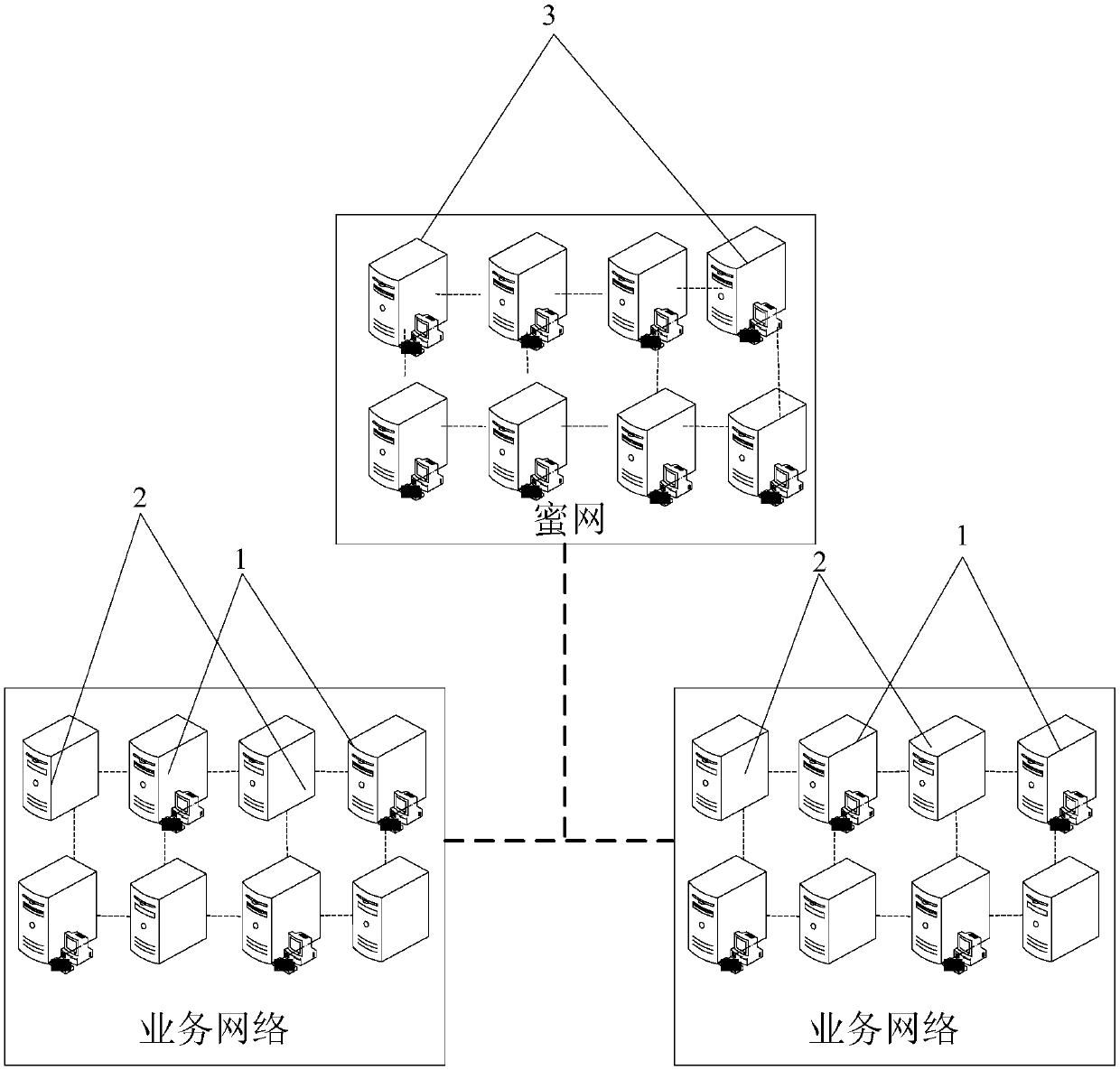
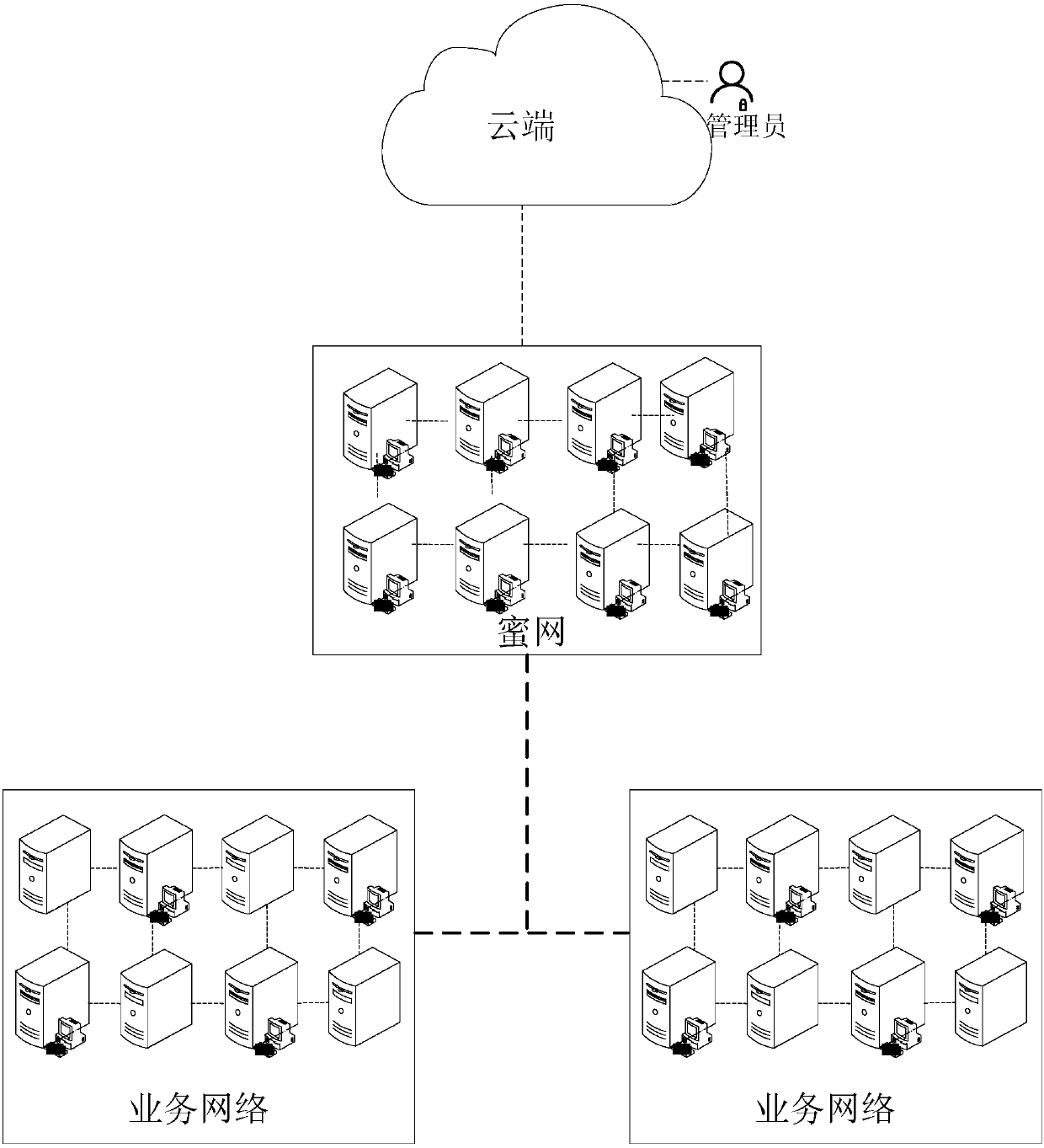
Network security protection system and related method
The invention discloses a network security protection system and a related method, and relates to the field of the network security. The network security protection system comprises at least one boundary honeypot and a honeynet connected with at least one boundary honeypot, wherein at least one boundary honeypot is located in a service network, and at least one honeynet is isolated from the service network; at least one boundary honeypot is used for inducing an attacker to attack itself and guiding the attacker to enter the connected honeynet. The network security protection system disclosed by the invention induces the attacker to attack the boundary honeypot, and further guides the attacker to enter the honeynet from the boundary honeypot; since the honeynet is isolated from the servicenetwork, in comparison with the prior art, the attacker can be induced and cheated through the boundary honeypot and the honeynet compared with the prior art on the one hand, the more effective defense can be realized through the known attack way or unknown attack way, and the attack time of the attacker can be delayed to change the attack patch of the attacker, thereby timely blocking the attackon the normal service network by the attacker.
Owner:北京长亭未来科技有限公司
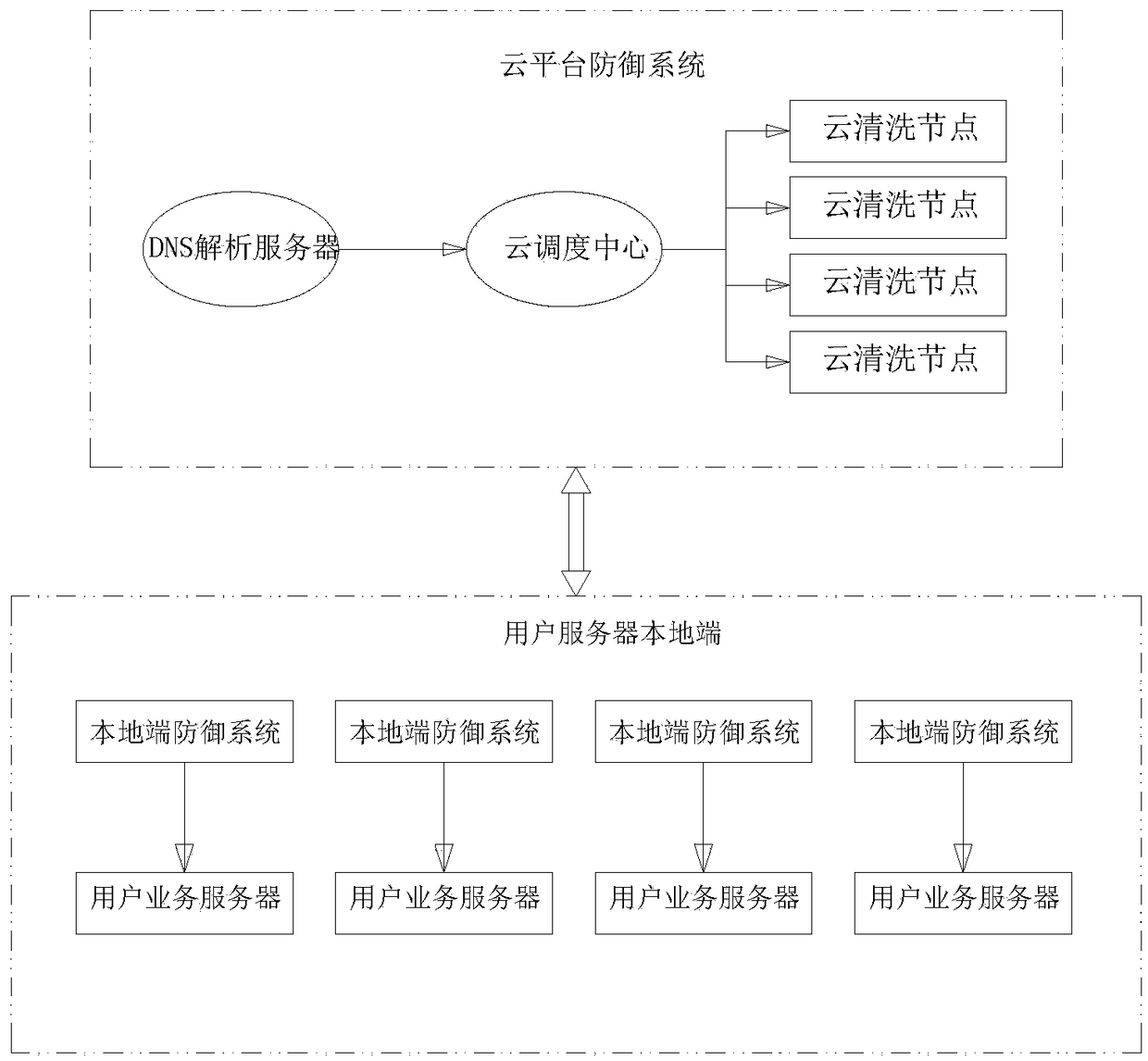
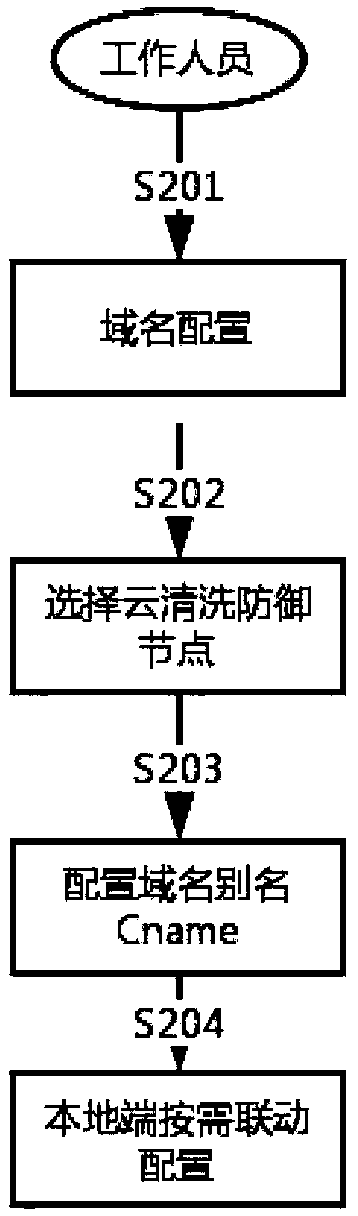
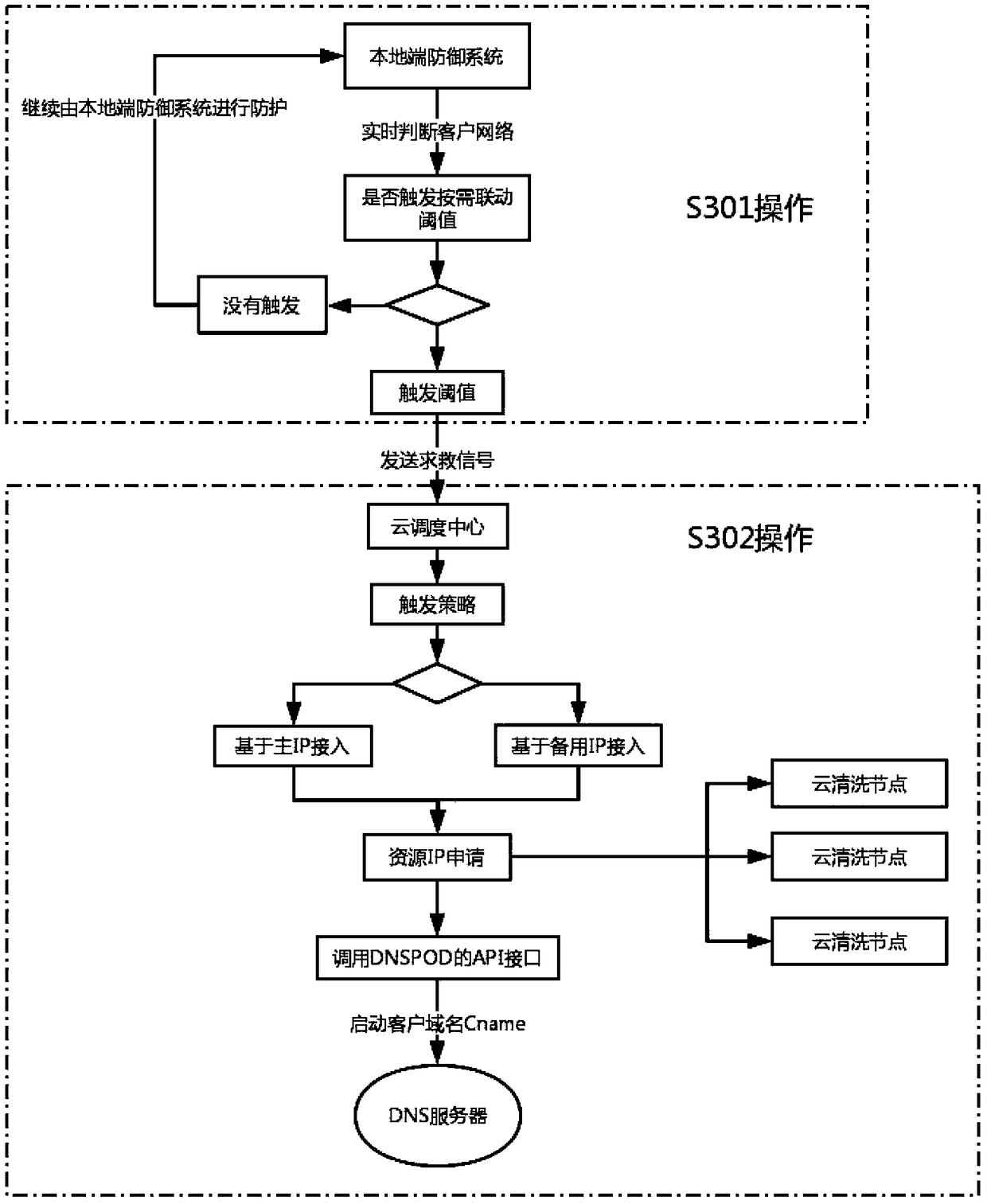
Large-scale DDoS attack detection and defense system based on cloud + end device on-demand linkage mode, and defense method
ActiveCN109450841ABreak through the bottleneck of anti-D defenseComprehensive defense against DDoS attacksTransmissionGranularitySystem protection
The invention relates to the technical field of network cloud security protection, and specifically relates to a large-scale DDoS attack detection and defense system based on a cloud + end device on-demand linkage mode. The system comprises a cloud platform defense system and a local end defense system, the cloud defense system comprises a cloud scheduling center, a cloud cleaning node device anda DNS near-source resolution server, and the local end defense system is used for performing fine-granularity cleaning protection for access service server traffic, performing cooperative processing with the cloud cleaning node device and performing message forwarding. Relative to single local end defense system protection, the large-scale DDoS attack detection and defense system provided by the invention can take advantages of high-capacity cleaning capability of cloud distributed cleaning nodes, and can break anti-D defense bottleneck of local bandwidth limit; and relatively to single continuous access cloud protection, the large-scale DDoS attack detection and defense system provided by the invention can realize more comprehensive defense to DDoS attacks and better cleaning effects through cloud node distributed cleaning and secondary fine filtering of the local end defense system.
Owner:ANHUI ZHONGXIN SOFTWARE
Process of realizing cultivating annual black fungus through punching bags by using intelligent sunlight greenhouse
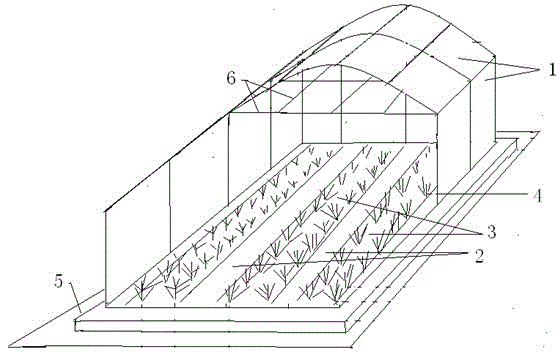
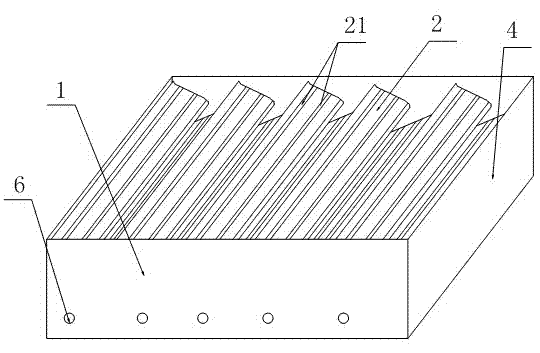
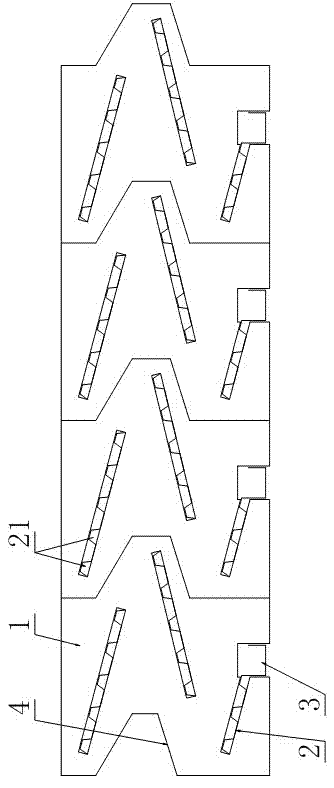
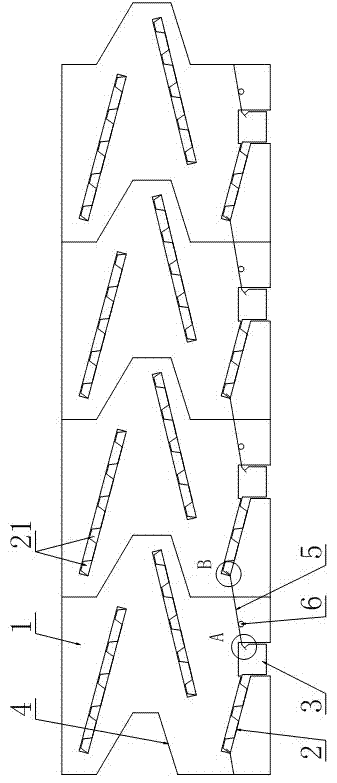
InactiveCN104885784AHigh technology contentSave landCultivating equipmentsMushroom cultivationPunchingGreenhouse
The invention relates to a process of realizing cultivating annual black fungus through punching bags by using an intelligent sunlight greenhouse. Fungus bags suspended in the sunlight greenhouse, according to the temperature and humidity in the sunlight greenhouse (1), can be automatically or manually sprayed and humidified, automatically or manually ventilated, and automatically or manually heated, so as to realize cultivating annual black fungus through punching bags by using the intelligent sunlight greenhouse in such ways of saving the land and being unaffected by the weather. The black funguses can be cultivated by the process so that the land saving can be realized and the black funguses are not unaffected by the weather, the growing trend can be controlled, the four-season cultivation can be realized, and the yield and benefit can be improved; furthermore, the small-scale distributed black fungus plantation can be changed into an intensive, specialized, standardized, mechanical and standard factory type production way, so that the high quality, high efficiency and high yield of the black funguses can be realized, the technological content of the black fungus cultivation can be improved, the production cost can be reduced, and the targets of increasing yield, synergia, increase income and stable earnings of the annual production can be realized.
Owner:黑龙江佰盛食用菌有限公司
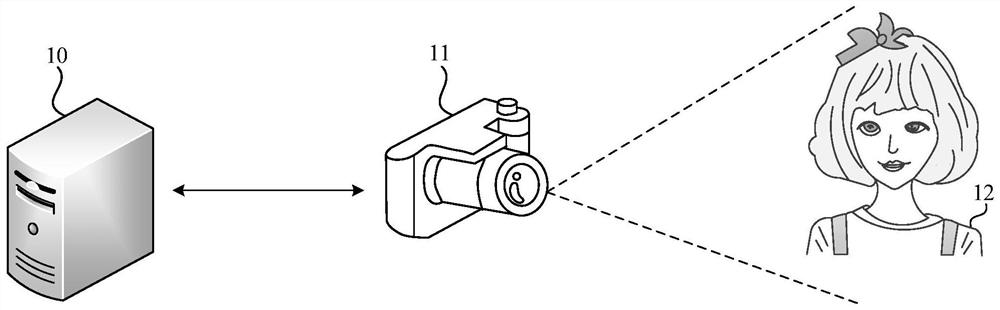
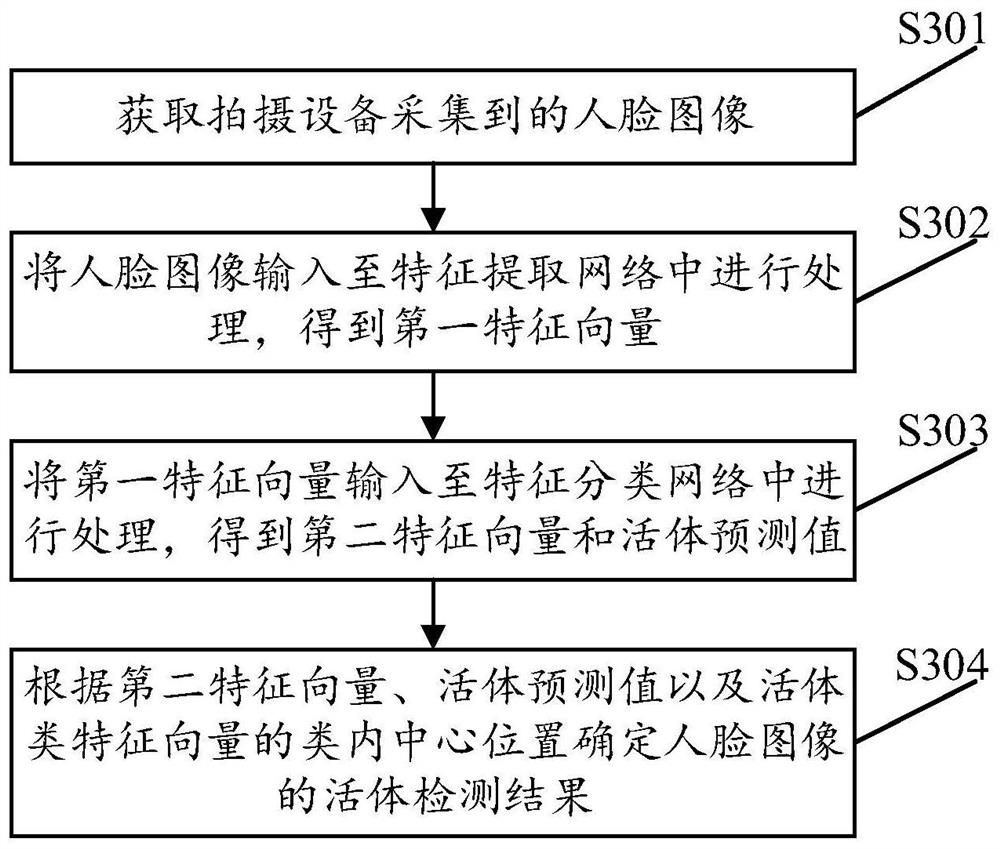
Human face living body detection method and device, computer equipment and storage medium
PendingCN111767900AImprove accuracyEffective defenseNeural architecturesNeural learning methodsFeature vectorFeature extraction
The embodiment of the invention provides a human face living body detection method and device, computer equipment and a storage medium. The method comprises the steps: acquiring a human face image collected by shooting equipment; inputting the face image into a feature extraction network obtained by training in combination with a metric learning device for processing to obtain a first feature vector; inputting the first feature vector into a feature classification network obtained by training in combination with a classification learner for processing to obtain a second feature vector and a living body prediction value; and determining the living body detection result of the face image according to the second feature vector, the living body prediction value and the intra-class center position of the living body feature vector. Through the embodiment of the invention, the accuracy of human face living body detection can be effectively improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
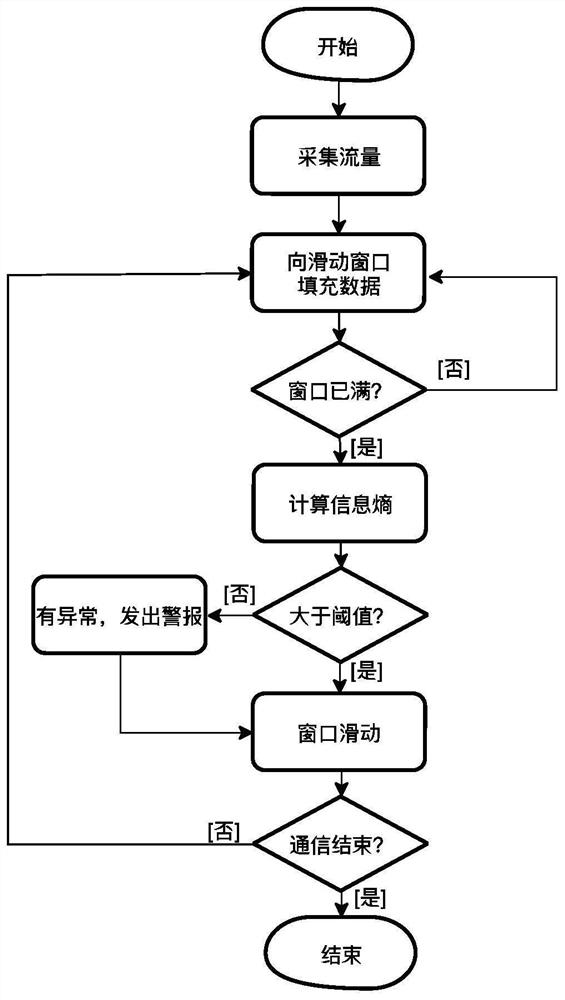
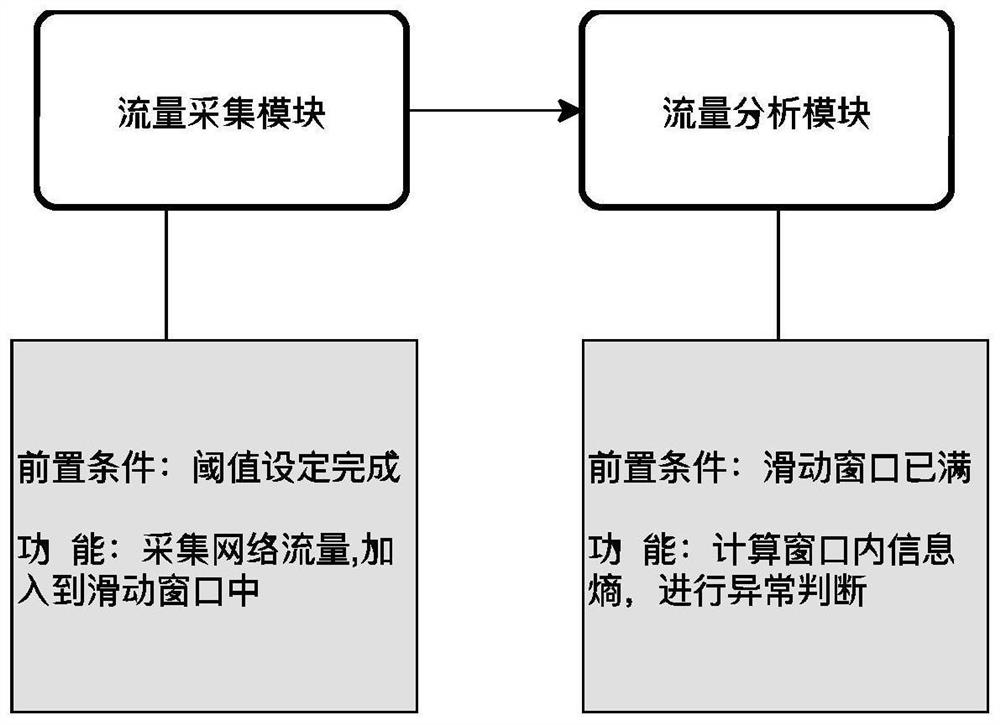
Vehicle-mounted network flow anomaly detection defense method and defense system based on information entropy
InactiveCN111818037AEffective defenseParticular environment based servicesIn-vehicle communicationIn vehicleInternet traffic
The invention provides a vehicle-mounted network flow anomaly detection defense method based on information entropy. The method comprises the following steps: 1, setting a sliding window; 2, setting athreshold value; 3, collecting and processing flow; 4, when the window is full, calculating the information entropy in the sliding window; and 5, detecting the flow of the CAN bus and the vehicle-mounted Ethernet by using a threshold value. According to the method, the influence of the abnormal flow on the information entropy is utilized, the information entropy in the sliding window is calculated in real time and compared with the preset threshold value, so that whether abnormality occurs or not is detected, and a safety protection scheme for effectively detecting the injection attack of theautomatic driving vehicle-mounted network is realized.
Owner:上海工业控制安全创新科技有限公司 +1
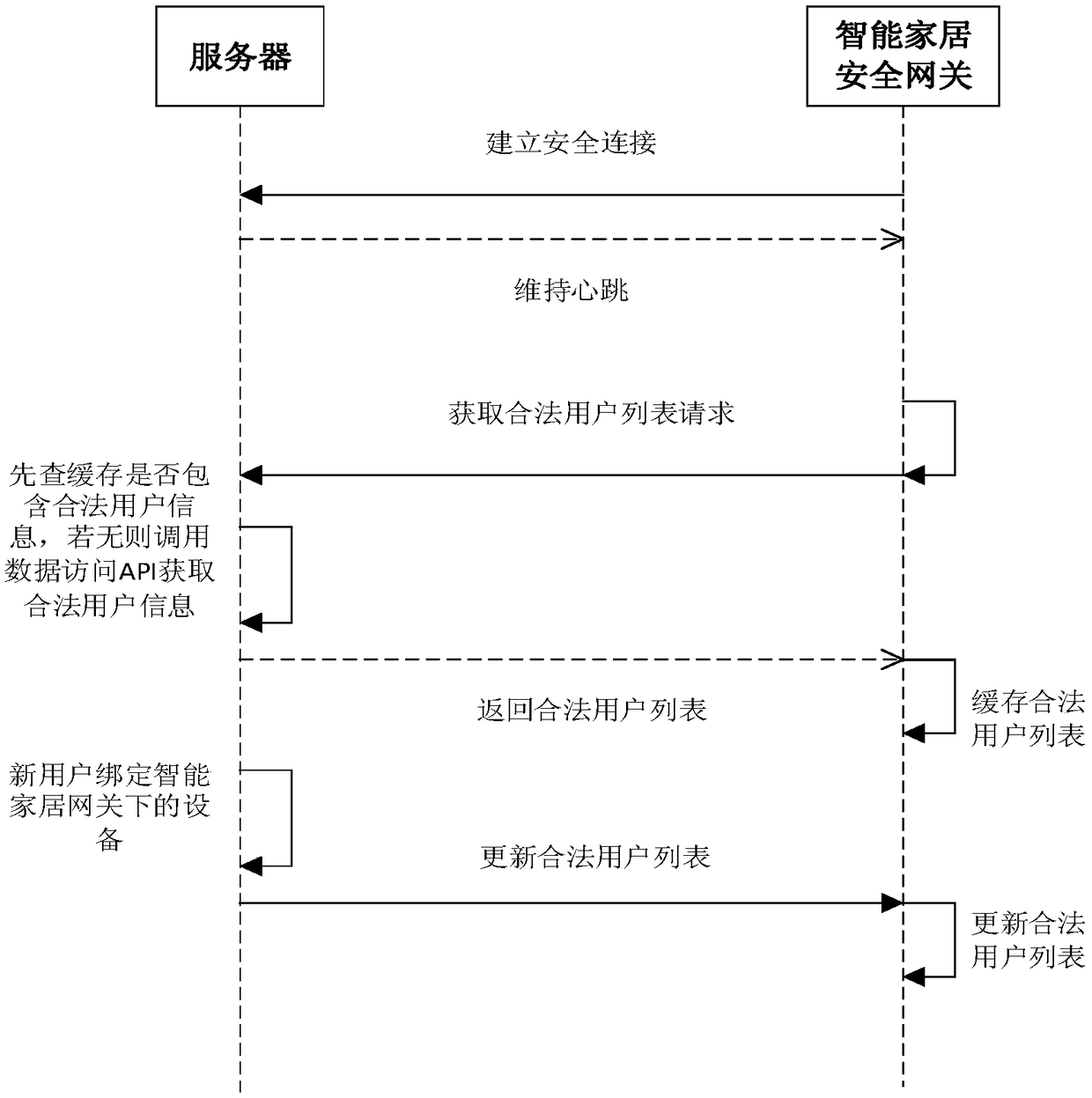
Security protection method of smart home security gateway
ActiveCN108809970AAvoid insecurityEnsure normal communicationNetwork connectionsCommunications securityProtection system
The invention discloses a security protection method of a smart home security gateway. According to the security protection method disclosed by the invention, the dual network card adaptation technology and the wireless network attack detection technology are adopted to solve the insecure problem of the smart home routing; an intrusion detection system is improved to add the intrusion detection and defense against the smart home protocol attack; access control is implemented on files and progresses, and the gateway security is monitored by using integrity measure and remote proof to form a virus protection system; and dual network card traffic analysis provides detection and defense of the Mirai virus and the variants thereof. By adoption of the security protection method disclosed by theinvention, in addition to ensuring the security of the device that performs communication by using a smart home protocol in the intranet, the communication security of other devices connected to a security gateway hotspot is also ensured, the attacks against the smart home protocol are defended, the detection and defense against viruses are provided, effective detection and protection are performed on a botnet formed by the viruses, the network security of the dual-network planes of the internal home network and the external home network is protected, and solutions and ideas are provided for smart home security and even the Internet of Things security.
Owner:SOUTH CHINA UNIV OF TECH
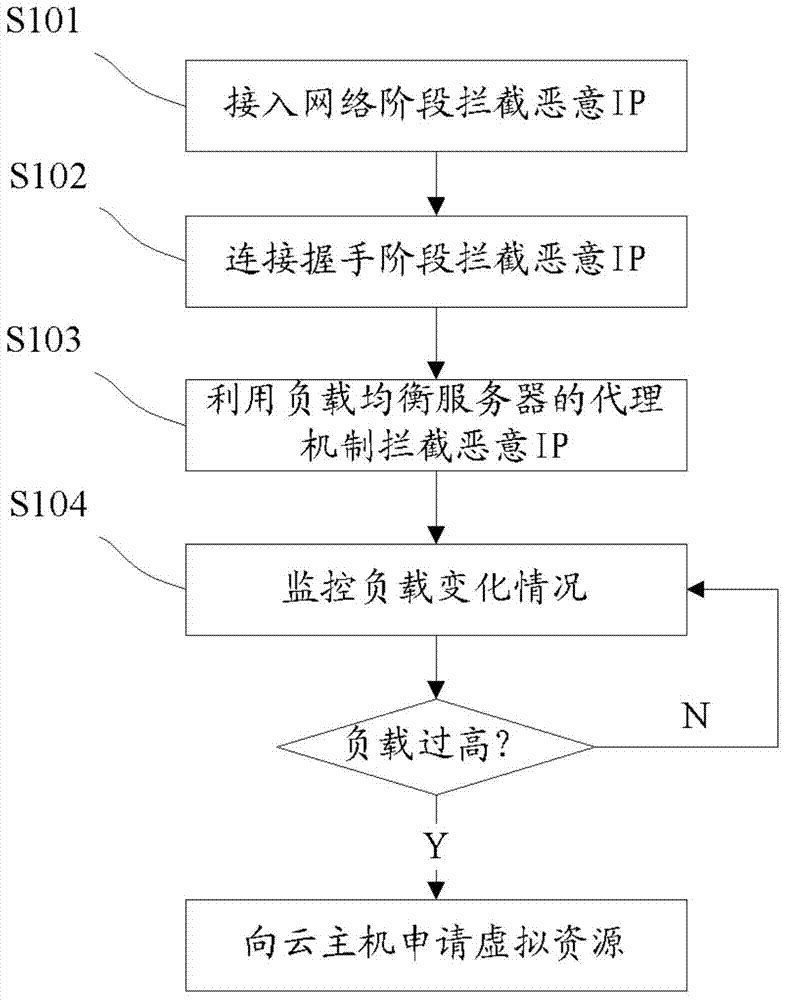
Method and device for defending denial of service attack
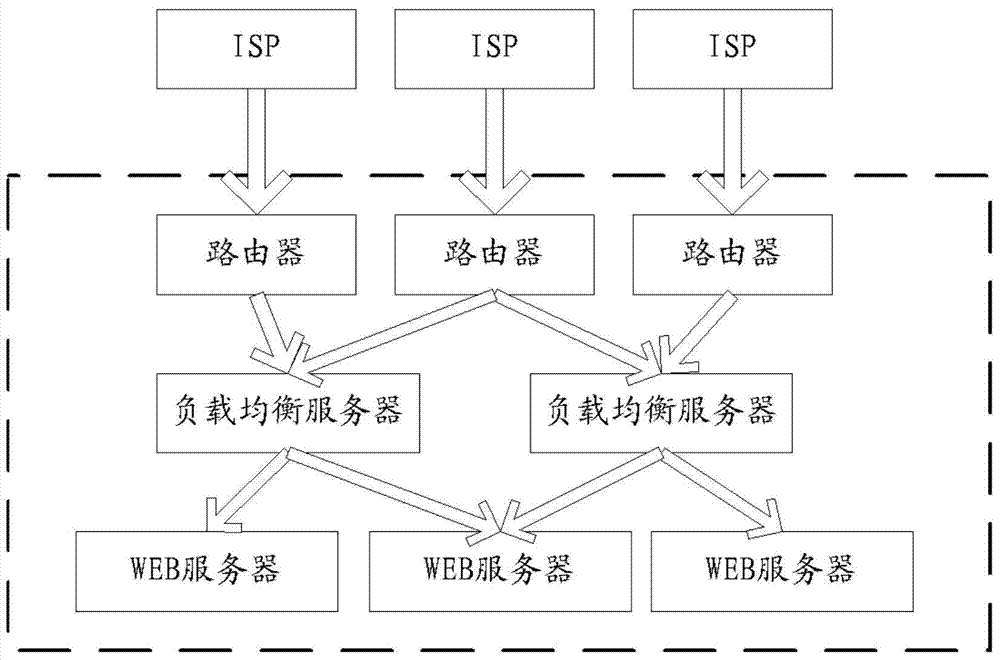
The invention provides a method for defending denial of service attacks. The method for defending denial of service attacks comprises the following steps: intercepting rogue access IP (Internet Protocol) according to a preset intercepting strategy respectively in a network access period and a TCP connection handshake period; shielding the rogue access IP by using the proxy mechanism of a load balancing server arranged between the router and a WEB server; monitoring the load of the WEB server, when the load of the WEB server exceeds a threshold value, applying to a cloud host for virtual resource, and adding into the load balancing server to share flow. The invention further provided a system for defending denial of service attack According to the method for defending denial of service attack, the reasonable strategy is set from the beginning of network access to prevent the access of malicious users, further defense is achieved by the proxy mechanism in the load balancing server, when facing attack, the WEB resource can be self-adaptively adjusted under the load balancing mechanism, and thus effective defense to malicious attacks is achieved.
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
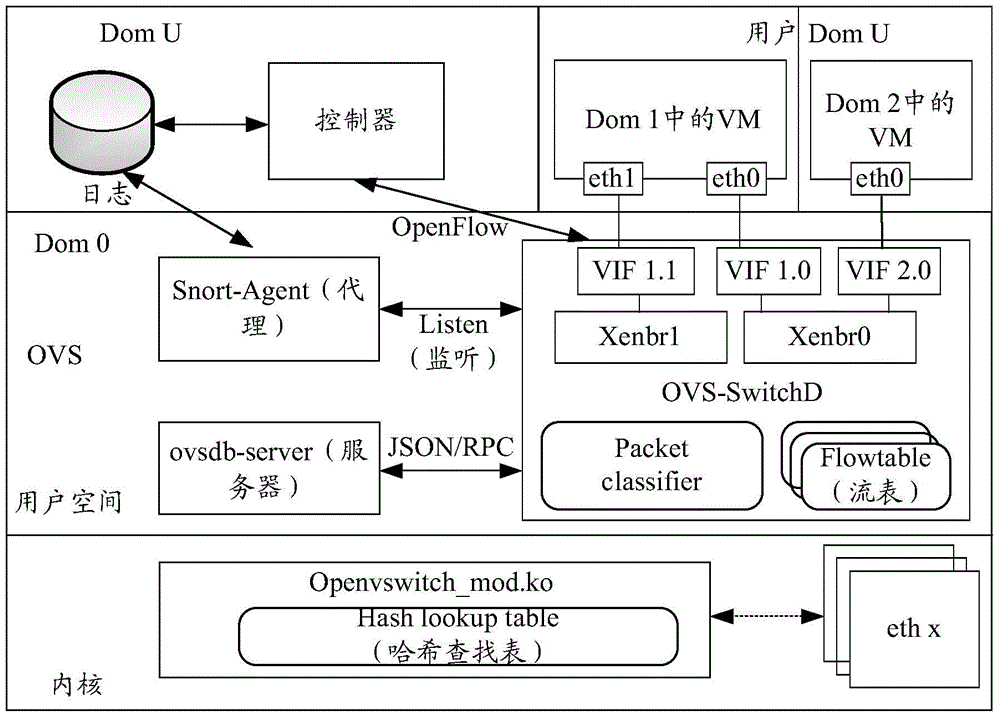
Intrusion prevention method applied to cloud virtual network, device, network device and system
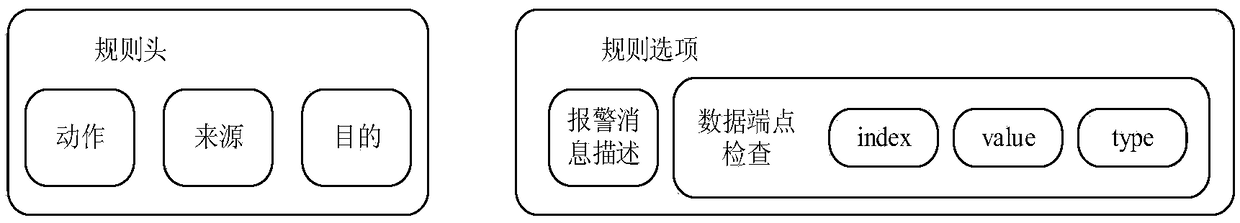
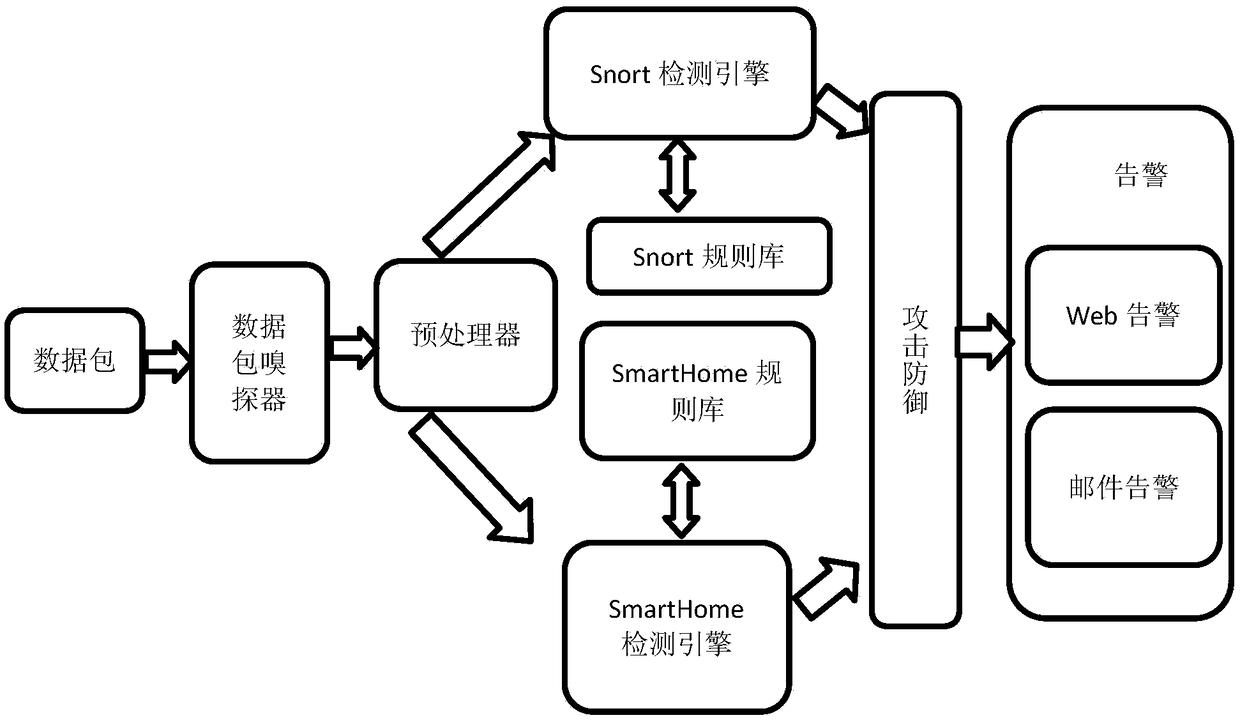
InactiveCN105871787ADynamic defenseEffective isolationNetworks interconnectionTraffic volumeIntrusion prevention system
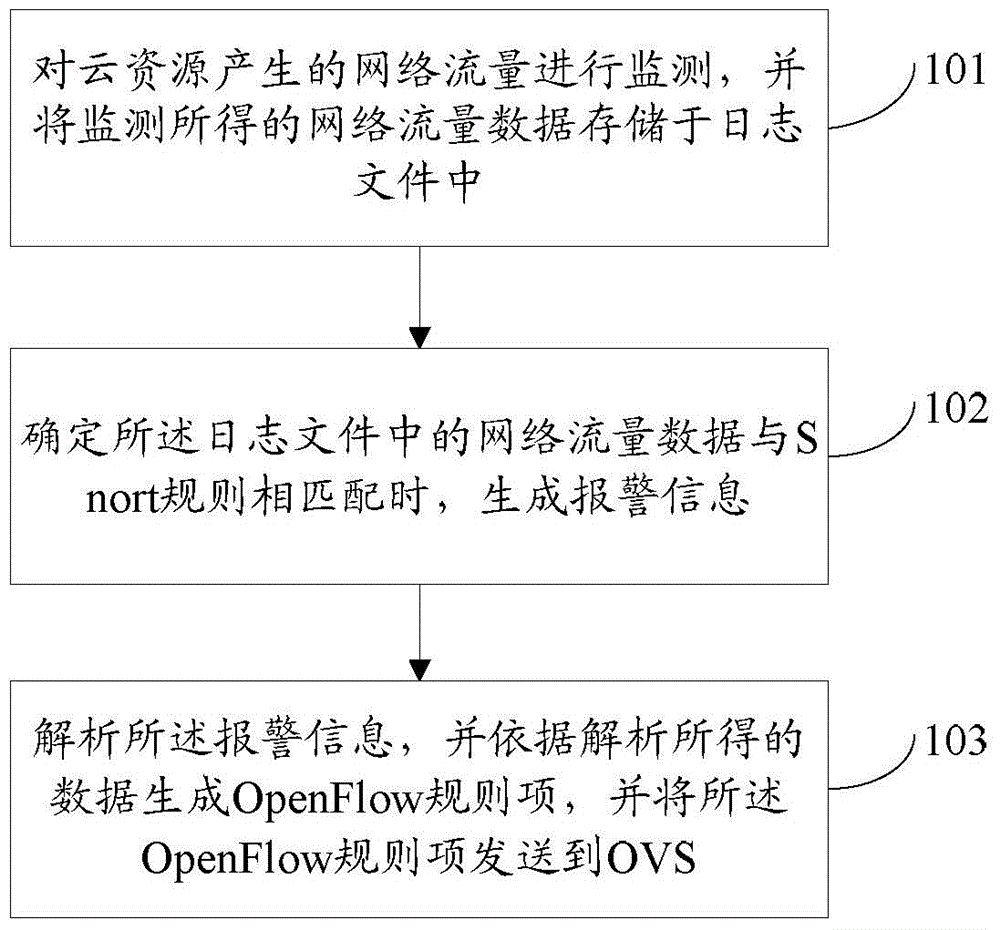
The invention discloses an intrusion prevention method applied to a cloud virtual network. The method includes the following steps that: network flow generated by cloud resources is monitored, and network flow data obtained through monitoring are stored in a log file; when it is determined that the network flow data in the log file are matched with Snort rules, alarm information is generated; and the alarm information is analyzed, an OpenFlow rule term is generated according to data obtained through analysis, and the OpenFlow rule term is sent to an OVS, wherein the OpenFlow rule term is used for the OVS to update a flow table. The invention also discloses a network device for realizing the method and a system.
Owner:CHINA MOBILE COMM GRP CO LTD
Traditional Chinese herbal medicine mask
InactiveCN109832691AEffective defenseEffective defense against inhalableAntibacterial agentsAntiviralsAdditive ingredientHoneysuckle
The invention provides a traditional Chinese herbal medicine mask, which is prepared from the following ingredients in proportion by weight: 30 to 50g of honeysuckle flowers, 35 to 45g of liquorice roots, 20 to 40g of rhizoma coptidis, 35 to 50g of chrysanthemum flowers, 50 to 60g of lemon, 45 to 60g of herba menthae, 25 to 40g of rhizoma dioscoreae and 35 to 55g of pericarpium citri reticulatae.Traditional Chinese herbal medicine mixed raw materials and distilled water are put into a ceramic tank to be steamed and boiled for 15 minutes and are cooled to the room temperature; and a middle cotton gauze layer is put into the ceramic tank to be soaked for 2 hours. The traditional Chinese herbal medicine mask has the effective antibacterial antivirus and body immunity improving functions; thedefense on inhalable particles can be effectively realized; the respiratory tract health can be well protected; meanwhile, the used cotton gauze has fresh and natural smell; the green and environmental-friendly effects are achieved; no chemical additive exists; the respiratory organ stimulation and body damage are avoided; and the ventilation performance is good.
Owner:新昌县熠凡花木专业合作社
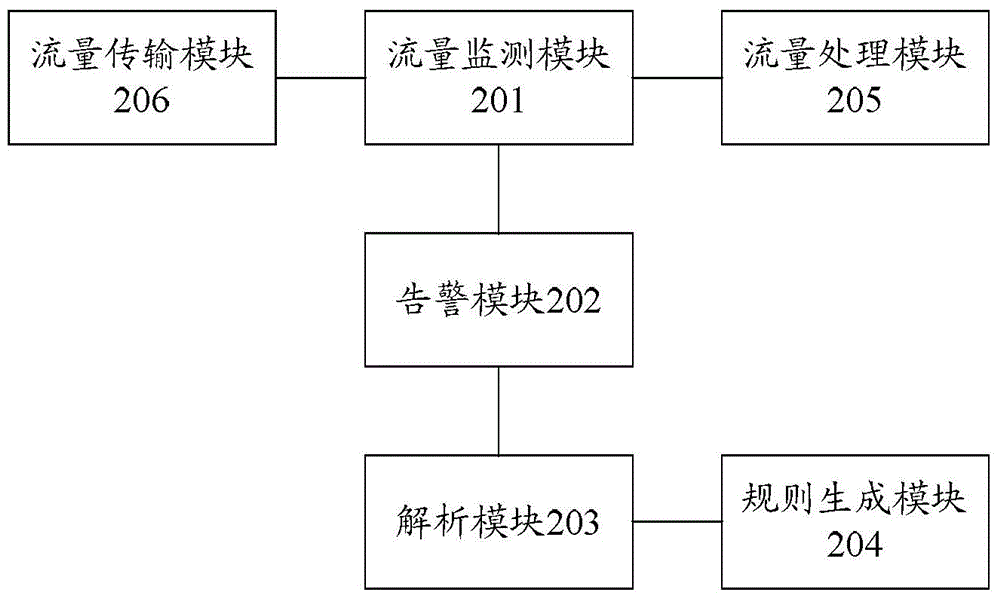
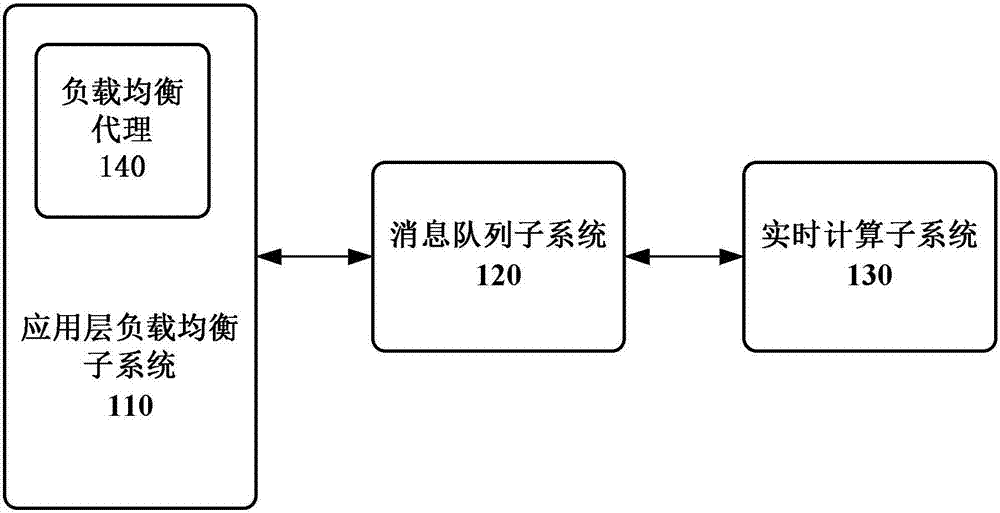
Network attack defending system and method for defending network attacks
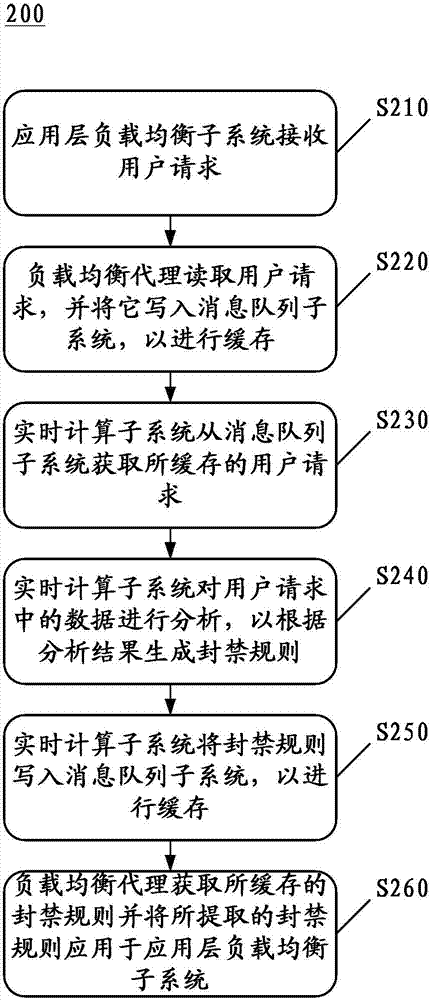
The invention discloses a network attack defending system and a method for defending network attacks. The system comprises an application layer load balancing subsystem, a message queue subsystem and a real-time computing subsystem; the application layer load balancing subsystem is configured to receive a user request and contains a load balancing agent, and the load balancing agent is configured to read the user request from the application layer load balancing subsystem and write the user request into the message queue subsystem; the message queue subsystem is configured to cache the user request written by the load balancing agent; and the real-time computing subsystem is configured to acquire the cached user request from the message queue subsystem, analyze data in the user request, generate a banning rule according to an analysis result and write the banning rule into the message queue subsystem; and specifically, the message queue subsystem is further configured to cache the banning rule, and the load balancing agent is further configured to acquire the cached banning rule from the message queue subsystem and apply the extracted banning rule to the application layer load balancing subsystem.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
System and method of foiling buffer-overflow and alien-code attacks
InactiveUS7730322B2Shuts down buffer overflow attacksProtected growthMemory loss protectionUnauthorized memory use protectionBuffer overflowApplication software
The present invention relates generally to computer software, and more specifically, to a system and method of foiling buffer-overflow and alien-code attacks. The invention protects computers from such attacks by encoding data placed in storage, and varying the encodings used in different storage areas. When the data is needed by a software application, the data is simply decoded in a complementary manner. This prevents storage areas written according to one usage from being used effectively for some other purpose. The method of the invention can be done in a number of ways. For example, a “protector” engine can be placed between a software application and memory, or the function calls in the software application itself, could be amended to include encoding and decoding. Other embodiments and alternatives are also described.
Owner:IRDETO CANADA CORP
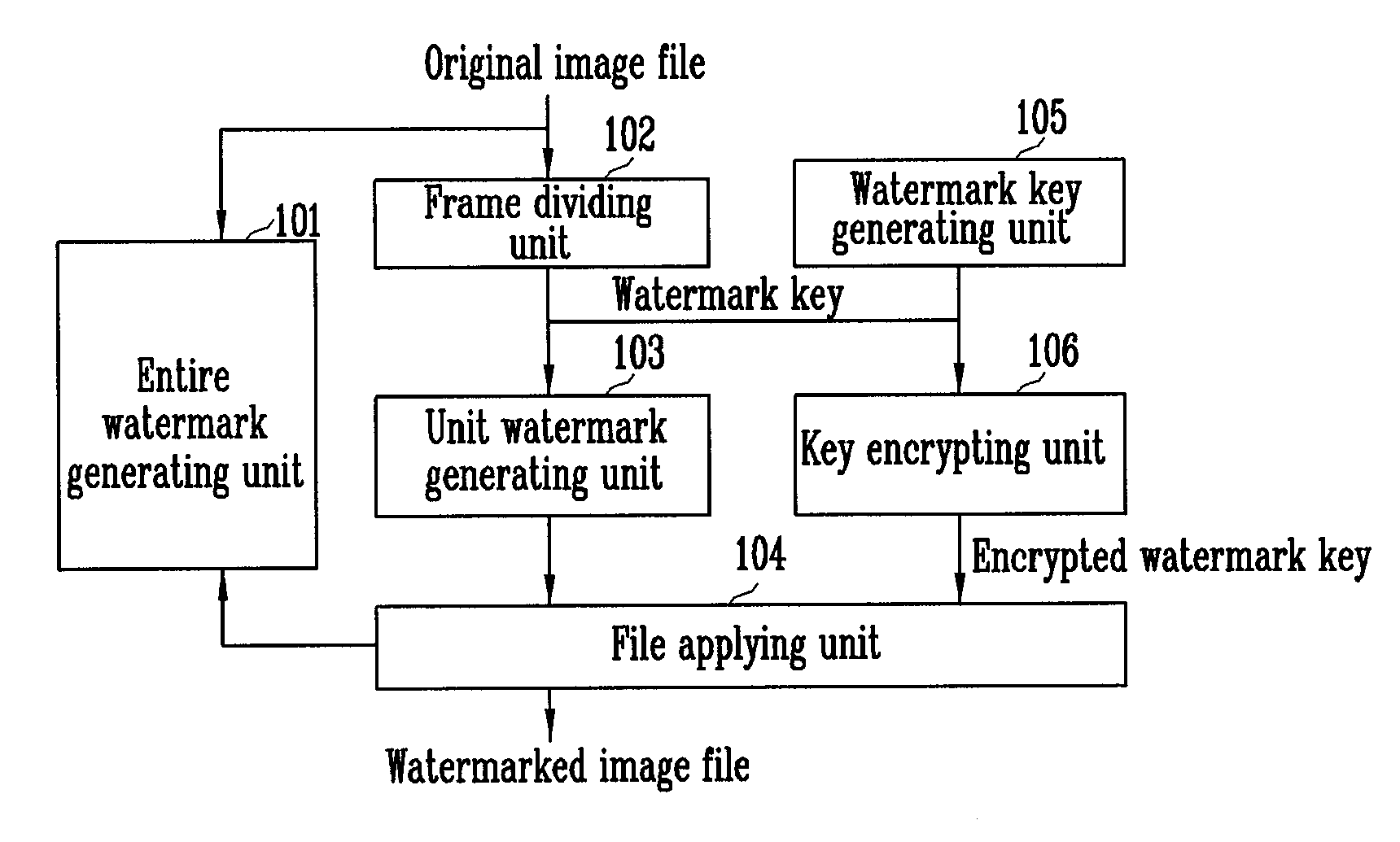
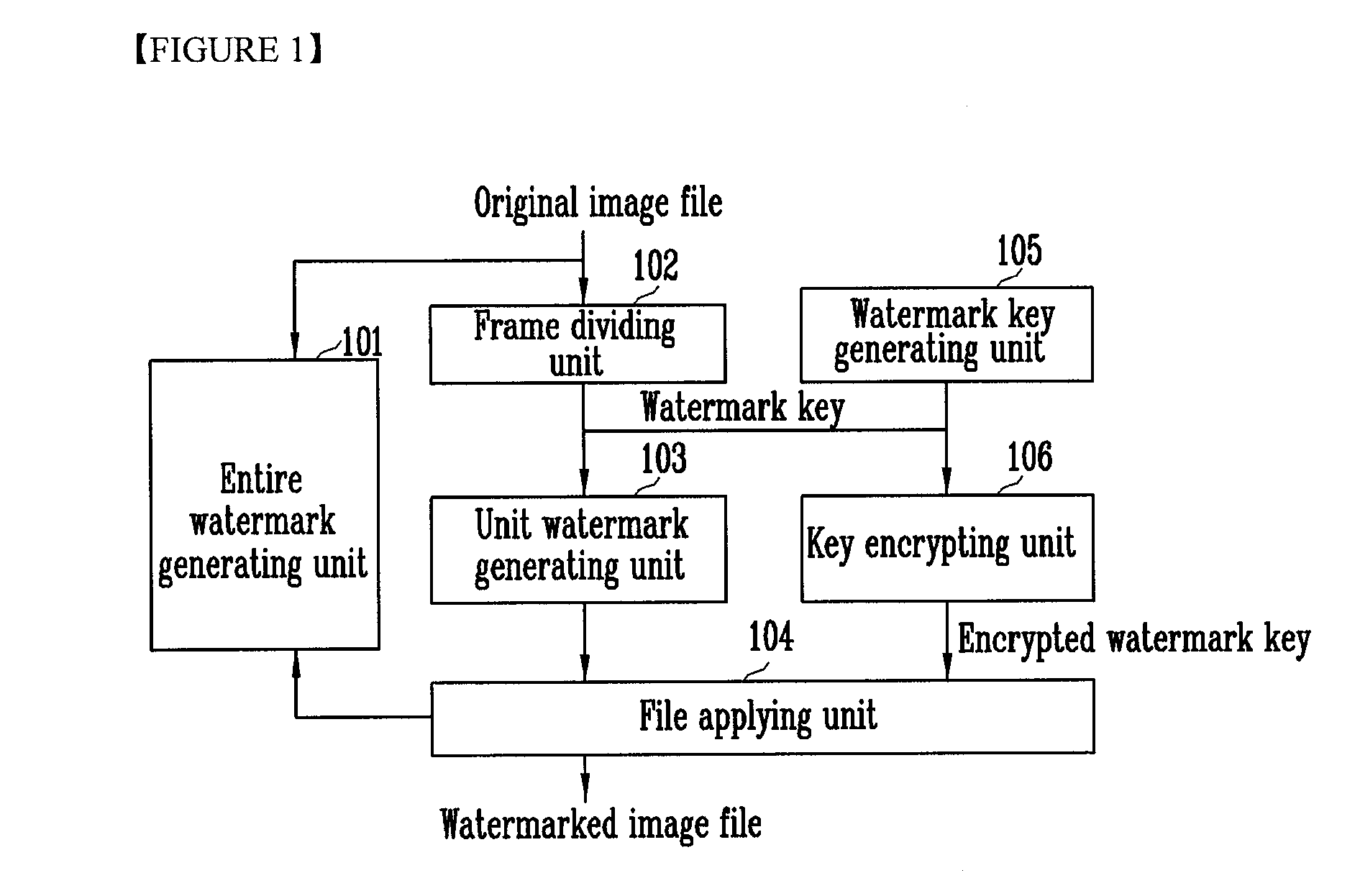
Watermarking method, watermark checking method, watermarking device, and watermark checking device
InactiveUS20090310817A1Reduce the amount of solutionEffective defenseTelevision system detailsCharacter and pattern recognitionComputer graphics (images)Watermark method
A watermarking method is provided. The method includes: the steps of creating an entire watermark for an image frame by using a secret key; dividing an image frame of the digital image file into divided frames by at least one row and at least one column; applying a predetermined watermark creating algorithm to pixel data of each divided frame to generate a unit watermark; and applying the unit watermarks with the digital image file. The step of creating the unit watermark uses a public key or applies a keyless algorithm. Another watermarking method includes the steps of dividing the image frame into a plurality of divided frames, each divided frame partially overlapping neighboring divided frames; applying a predetermined watermark creating algorithm to pixel data of each divided frame to generate a unit watermark; and applying the unit watermarks with the digital image file. With the watermarking method and the checking method, a forged or faked area of the image frame can be detected without increasing the amount of computation.
Owner:POS DATA CO LTD
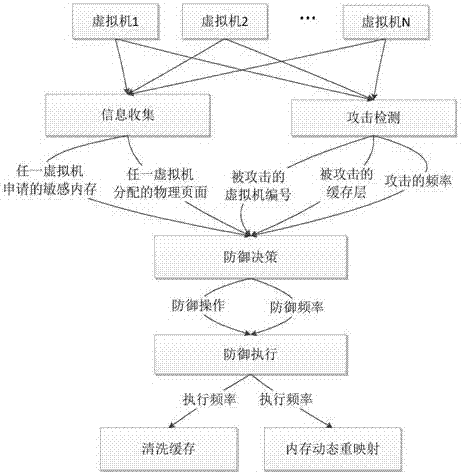
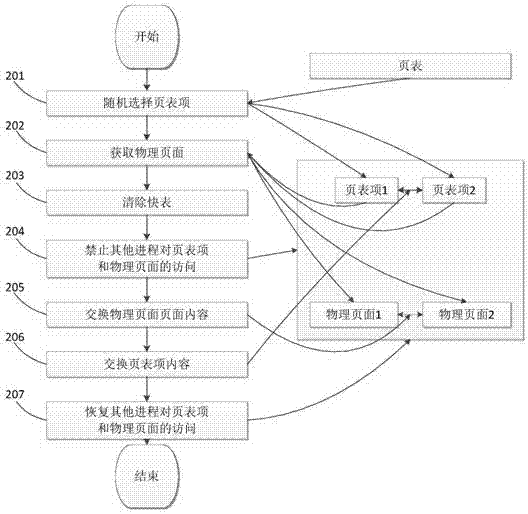
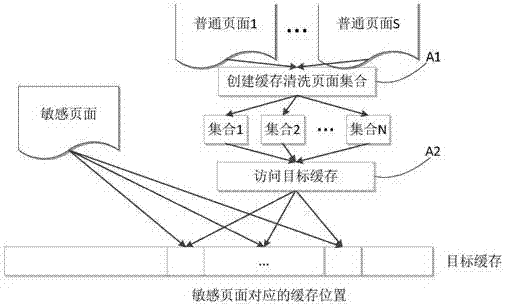
Side channel attack defense method and device based on dynamic memory remapping and cache cleaning
ActiveCN107169346ATaking into account operating efficiencyAvoid wastingPlatform integrity maintainanceSoftware simulation/interpretation/emulationAttack frequencyCloud computing
The invention relates to a side channel attack defense method and device based on dynamic memory remapping and cache cleaning. The method comprises the steps of collecting information of virtual machines operating on a virtual machine monitor, wherein the information at least comprises physical pages occupied by each virtual machine and protection memory submitted by the virtual machines; monitoring side channel attacks currently generated based on caches in real time, thereby obtaining attack target information, wherein the attack target information at least comprises attacked target virtual machines, attack frequencies and attacked cache layers; and selecting defense operation, wherein according to the defense operation, cache cleaning operation or memory dynamic remapping operation is selected according to the attacked cache layers in the attack target information. According to the method and the device, the operation efficiency of the virtual machine monitor is taken into consideration; targeted defense is carried out; resource waste is avoided; the security of a cloud computing industry is ensured; the side channel attacks based on the caches can be sensed in real time; and the efficient defense is realized on the basis of not influencing resource sharing to the greatest extent.
Owner:THE PLA INFORMATION ENG UNIV
Breeding method and device for young tussah
InactiveCN102715135AReduce lossesSolve the problem that the silkworm reduction rate remains high in the young silkworm stageAnimal husbandryHabitSeedbed
The invention discloses a breeding method and a breeding device for young tussah. A greenhouse is built, hatching tree seedlings are planted in the greenhouse, and a hatching seedling bed is formed; after the fixed planting of the hatching tree seedlings, the hatching tree seedlings are bred into low-trunk tree forms, and 5 to 6 branches are left for each strain; graine is loaded into a kraft paper bag for hastening the hatching of silkworms, after the breakthrough of young silkworms, an opening of the kraft paper bag is opened, after the silkworm head tree climbing completion, the paper bag is removed, and the hatching is completed; the temperature in the greenhouse is maintained at 16 DEG C to 28 DEG C; the young silkworms are fed to 2 to 3 days at the molting of primary sleeping silkworms, and the silkworm heads are moved to a field silkworm plant for breeding outside cages before 9 o'clock in the morning or after 17 o'clock in the afternoon in sunny days. The young tussah is bred through adopting a mode of building three-dimensional breeding environment in rooms, the harm to the young tussah caused by natural environment and natural enemy can be effectively prevented, the labor work for picking and storing oak leaves is also avoided, the ventilation three-dimensional breeding environment is provided, the natural attributives of upward climbing habit, scattering habit and the like of the tussah are met, the disease rate of the silkworm body is reduced, the management requirement is reduced, the disease prevention difficulty and the cost are reduced.
Owner:GUIZHOU SERICULTURE RES INST GUIZHOU PEPPER RES INST
Structural waterproof parallel air flue type natural ventilator
ActiveCN103206762AReduce flow ratePlay the role of drainageLighting and heating apparatusSpace heating and ventilation detailsNatural ventilationEngineering
The invention discloses a structural waterproof parallel air flue type natural ventilator. The natural ventilator comprises a support framework, at least two groups of ventilation components arranged in the support framework parallelly, and an outer protective plate wrapped on the outer side of the support framework. Each group of ventilation components comprises at least two flashing boards in up-down staggered arrangement and a drainage channel connected with the lower edge of the bottom flashing board, a plurality of convex ribs in transversal arrangement and used for slowing down flowing of rainwater and guiding flow and drainage are arranged on each flashing board, and an adjustable opening and closing device is arranged on the drainage channel in each group of the ventilation components, is fastened at the edge of the bottom flashing board of the adjacent group of ventilation components, is capable of blocking and conducting indoor and outdoor air flues, and is used for waterproofing when closed. By means of simple and ingenuous improvement, rainwater can be defended, drained, collected and removed effectively, and the natural ventilator has good application effect and broad application prospect.
Owner:SICHUAN MCWELL TECH
Method and device for resisting cooperative type sensing data falsification attack through cognitive wireless network
InactiveCN103731834AImprove perceptionImprove detection rateSecurity arrangementSensing dataAttack strategy
The invention relates to the technical field of wireless communication, in particular to a method and device for resisting cooperative type sensing data falsification attack through a cognitive wireless network. The method includes the steps of clustering sensing results and judging the sensing results within clusters, dividing sensing users with similar sensing result reports into the same clusters, recognizing and isolating malicious users, and then judging the real channel occupancy state of main users according to the judgment result of each cluster. According to the method, the malicious users are recognized and isolated by means of the self-adaption clustering technology by fully using sensing report historical data of the sensing users under the condition that prior knowledge such as the number of attackers and the attack strategies does not exist; all aspects of sensing performance of the system is improved, the aims of lowering system false alarm probability and improving system detection probability are achieved, and therefore the cooperative type sensing data falsification attack is effectively defended.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com