Network attack defending system and method for defending network attacks
A network attack and defense system technology, applied in the field of network security, can solve problems such as the inability to realize logical judgment and bottlenecks in processing capabilities at the application layer, and achieve the effect of effective defense
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
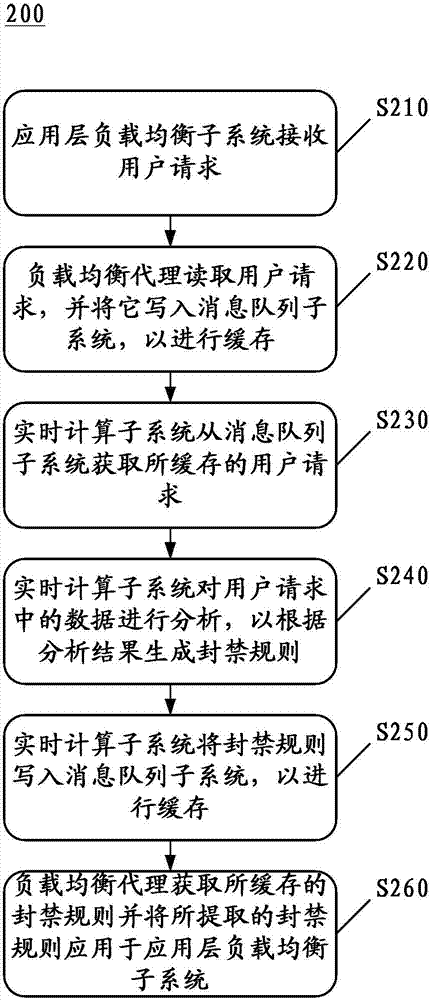
[0027] It should be noted that, in the description of the following specific embodiments of the present invention, for the sake of convenience, part of the content may be described for a specific network protocol (for example, HTTP protocol), but it should be understood that the embodiments of the present invention are not limited to these specific protocols.
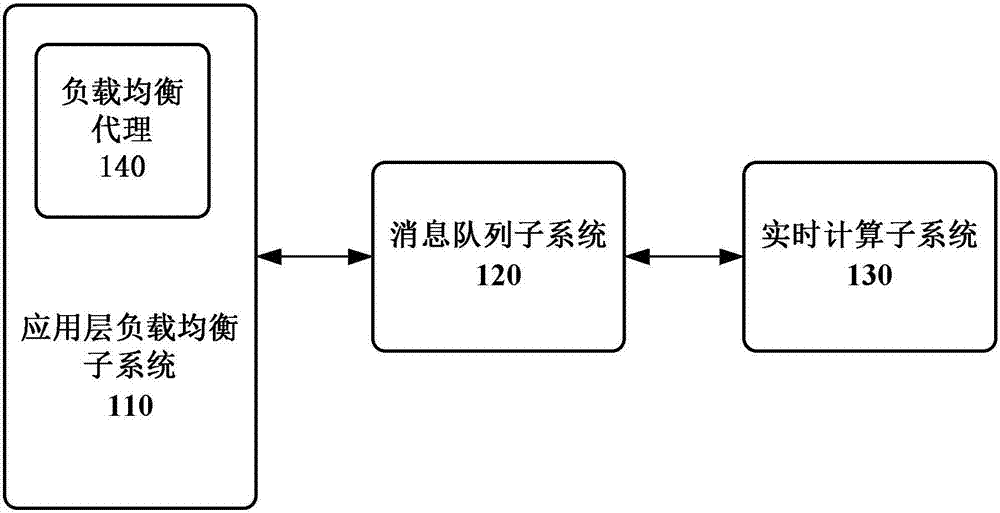
[0028] The term "subsystem" used in the present invention can be implemented as a single computer or server, or as a cluster composed of multiple computers and / or servers, and all the computers included in the same cluster cooperate to realize the same specific function. Specifically, a "subsystem" may be a cluster composed of multiple x86 servers. In addition, an interpretation of the term "load balancing" in the present invention includes front-end forwarding for balancing the access pressure of back-end business servers. It should be understood that, the above explanation instructions for the terms of the present in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com