Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
663results about How to "Easy to manage centrally" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
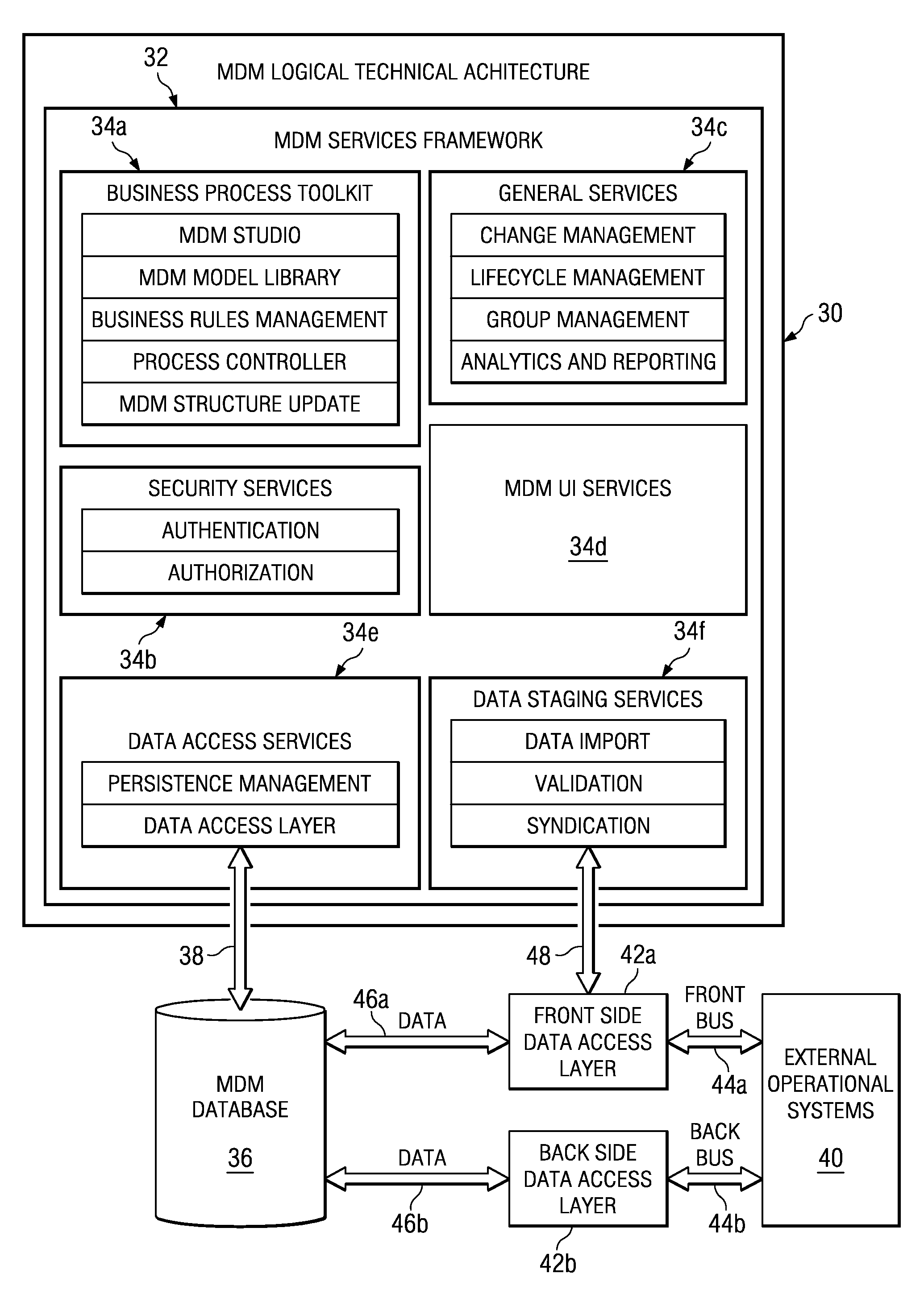
Data management system providing a data thesaurus for mapping between multiple data schemas or between multiple domains within a data schema
InactiveUS20050021541A1Easy to manage centrallyOffice automationResourcesOperational systemWork flow
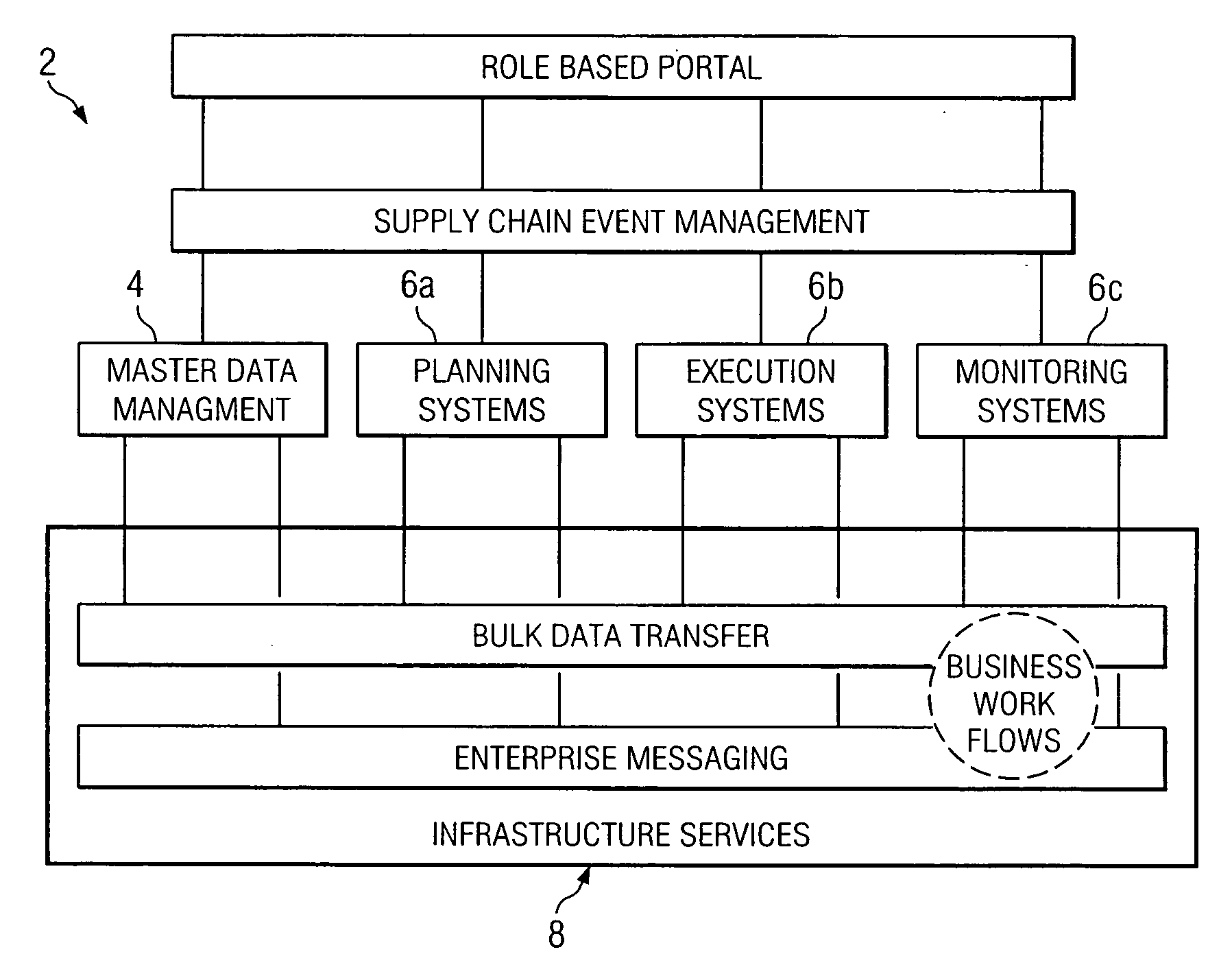
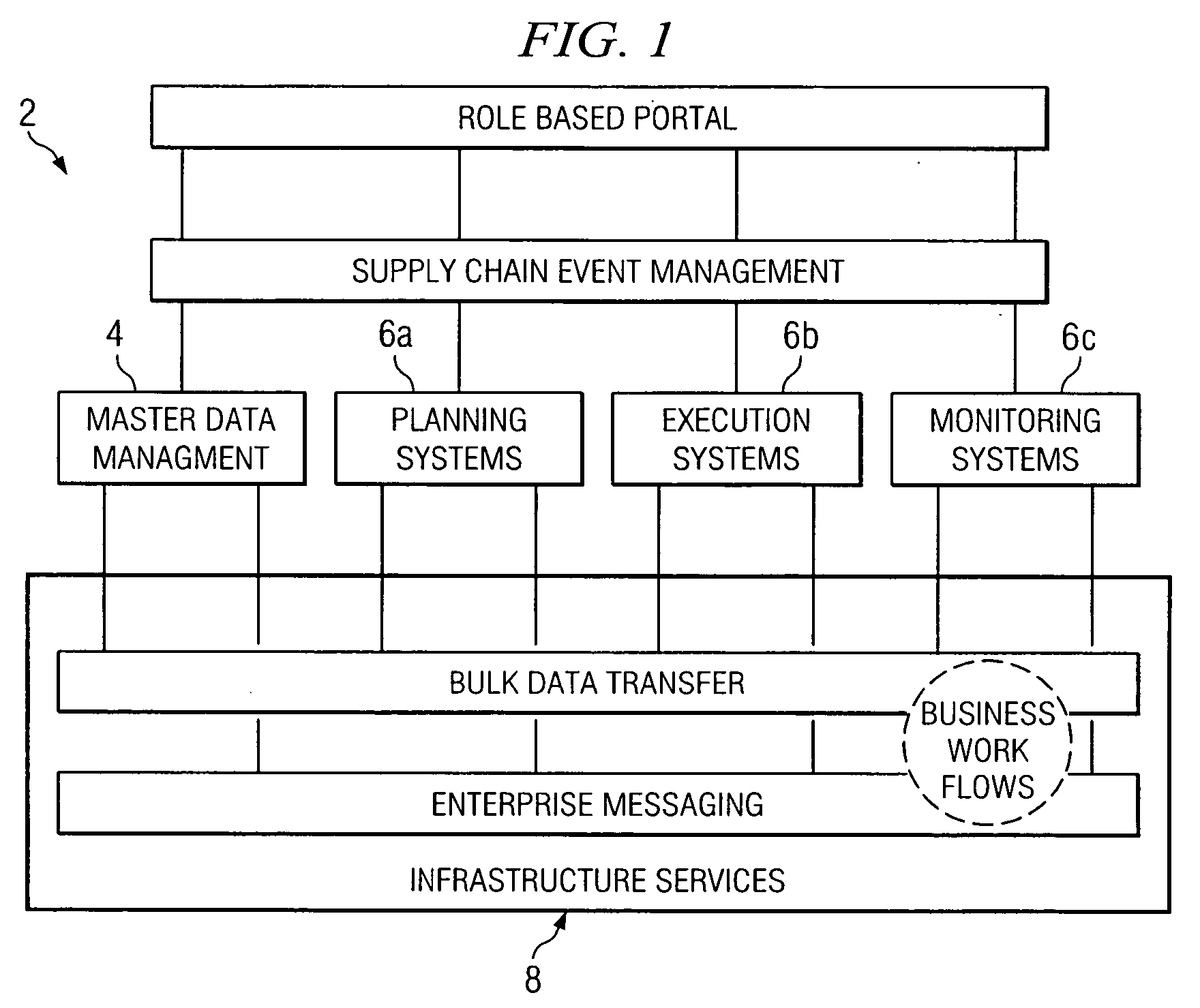
In one embodiment, a system is provided for managing a centrally managed master repository for core enterprise reference data associated with an enterprise. A centralized master repository contains the reference data, the reference data being associated with multiple schemas, each schema including one or more data models for reference data, each data model including one or more fields. A data management services framework coupled to the repository provides services for managing the reference data in the repository. The services framework supports a master schema including a union of multiple models and associated fields in the multiple schemas. The services framework also supports a thesaurus including, for each field in the master schema, a set of synonyms each representing a mapping between the field in the master schema and a corresponding field in a particular one of the multiple schemas. The master schema and thesaurus facilitate centralized management of the reference data in the repository across multiple heterogeneous external operational systems that have different associated data models and are provided indirect access to the reference data in the repository for operational use of the reference data according to associated business workflows.
Owner:BLUE YONDER GRP INC
Security system using indirect key generation from access rules and methods therefor
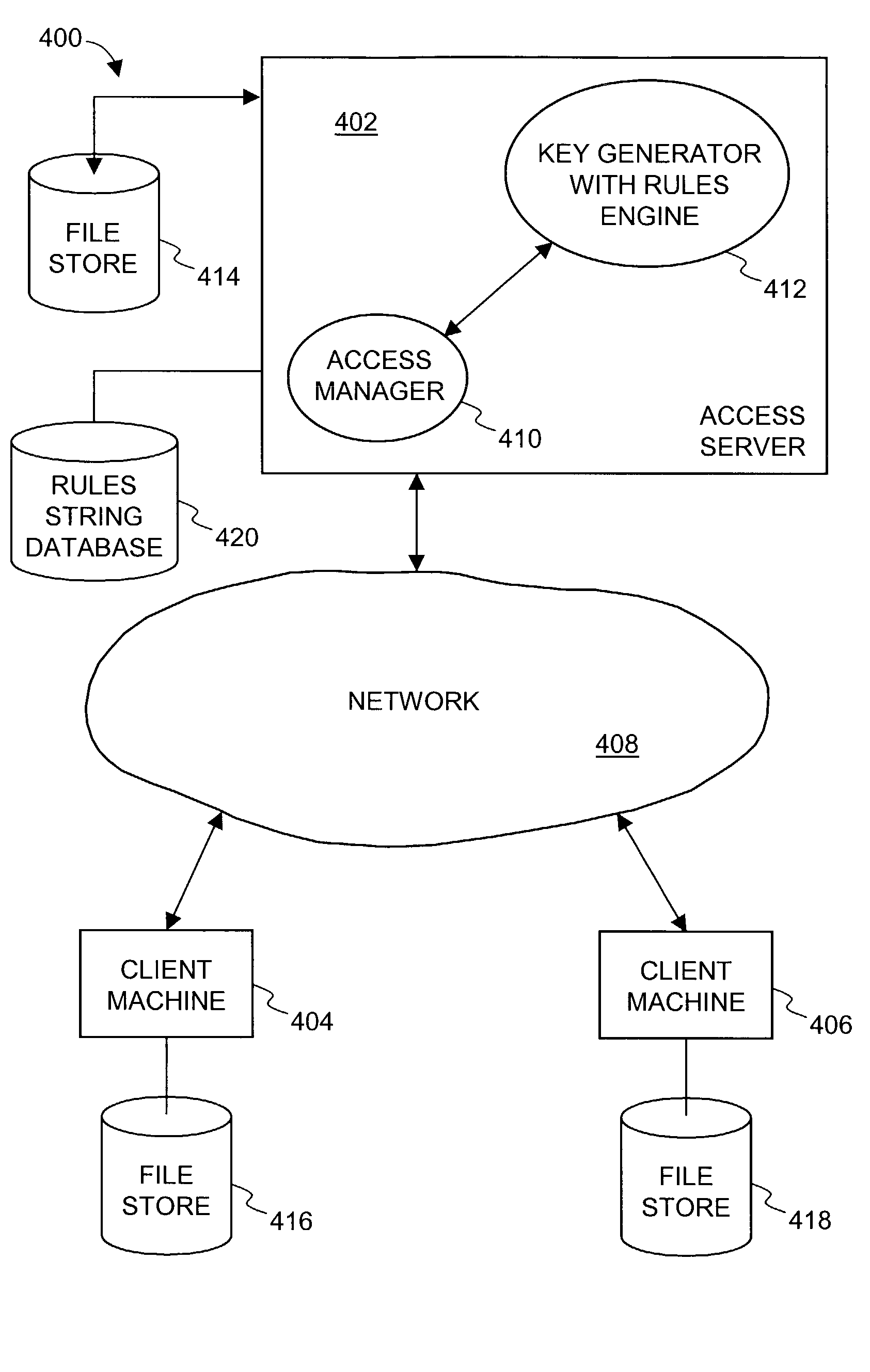
ActiveUS7921450B1Improve approachLimited accessKey distribution for secure communicationDigital data processing detailsComputer scienceKey generation
Improved system and approaches for centralized storage of access restrictions which are associated with public keys are disclosed. The access restrictions serve to limit access to files secured by a security system. According to one aspect of the present invention, identifiers, or encoded versions thereof, are used as public keys to identify particular access restrictions. The identifiers to the access restrictions are used in a decentralized manner for public keys, while the access restrictions themselves are maintained in a centralized manner. As compared to the access restrictions, the public keys based on identifiers tend to be smaller and more uniform in size. The centralized storage of the access restrictions also facilitates subsequent changes to access restrictions for previously secured files. The improved system and approaches is particularly suitable in an enterprise environment.
Owner:INTELLECTUAL VENTURES I LLC
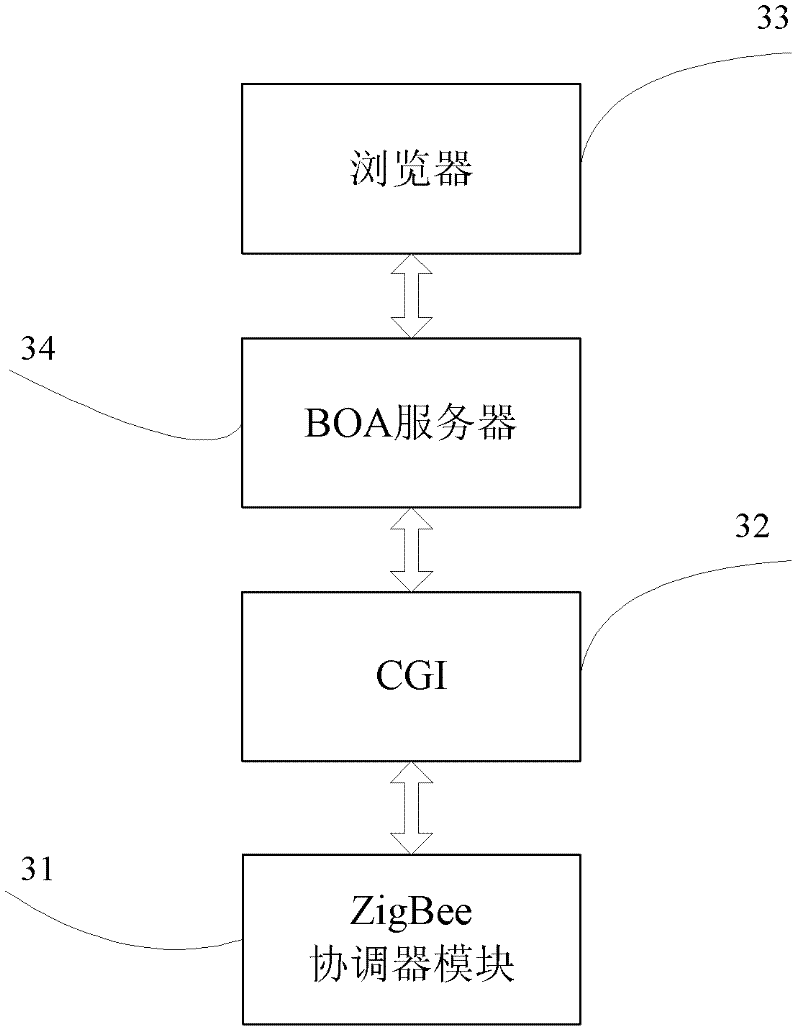
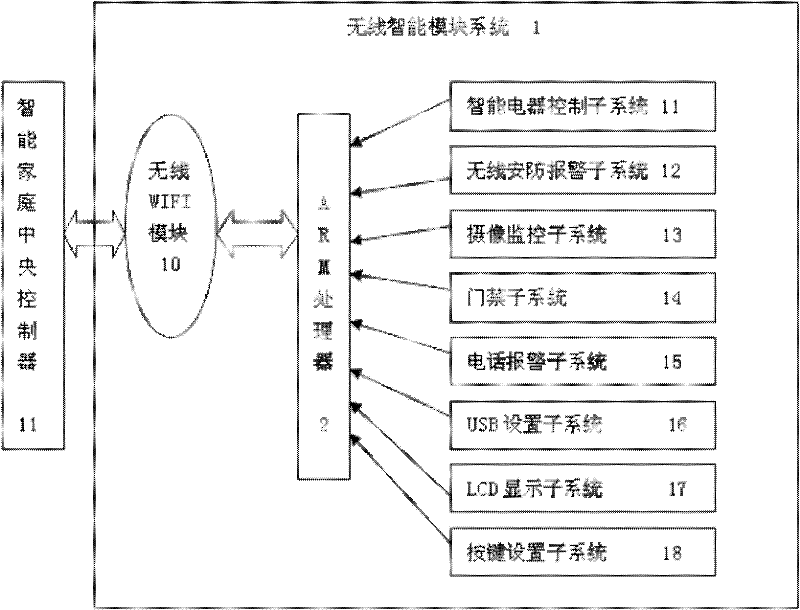
Intelligent household electric appliance system based on ZigBee and page generation and implementation method thereof
InactiveCN102238236AImprove versatilityEasy to manage centrallyProgramme controlTransmission systemsWeb serviceSynchronous dynamic random-access memory
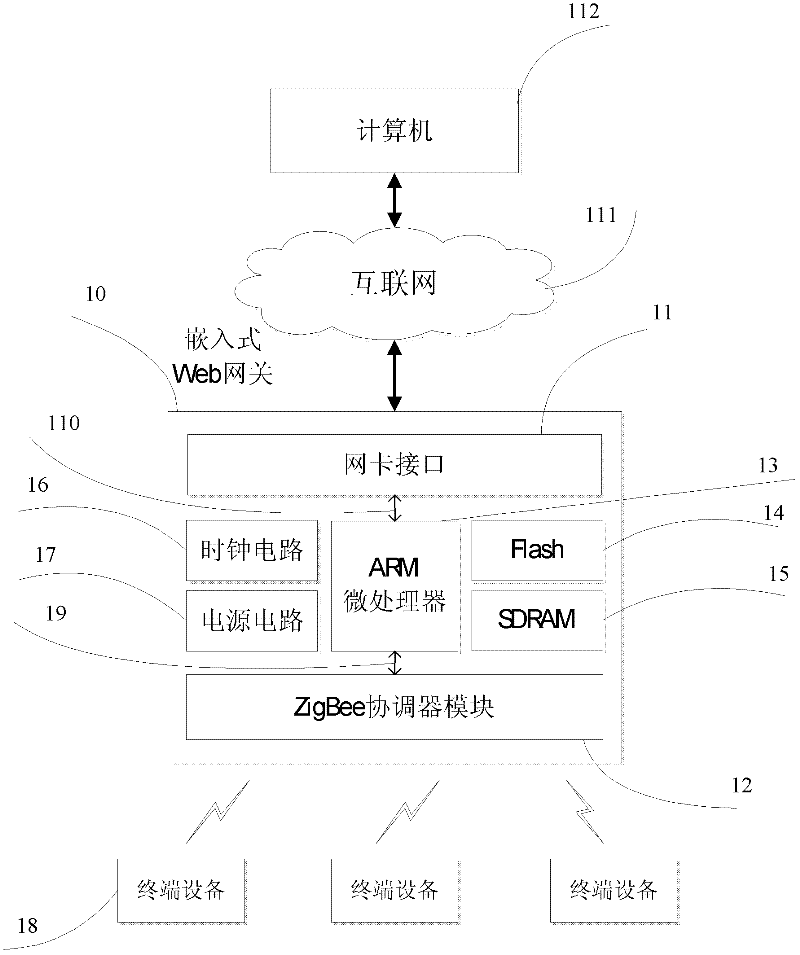
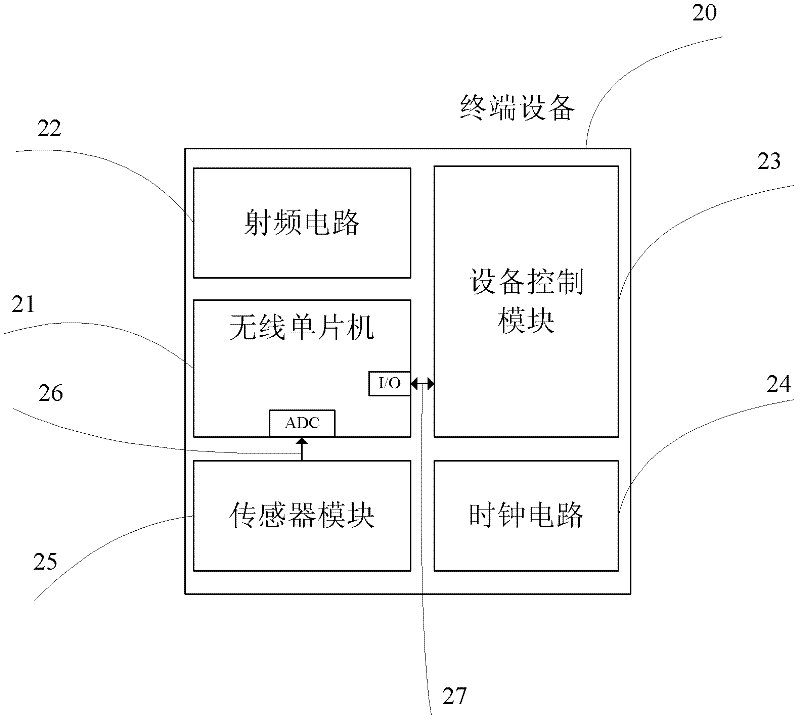
The invention provides an intelligent household electric appliance system based on ZigBee and page generation and an implementation method thereof, wherein the system comprises a computer, an embedded Web gateway and a plurality of terminal devices. The embedded Web gateway comprises an ARM (Advanced RISC Machine) microprocessor, a Flash SDRAM (synchronous dynamic random access memory), a time circuit, a power circuit, a network card interface and a ZigBee coordinator module, wherein the automatic generation of the household electric appliance control page is achieved based on the embedded Web server. The ZigBee coordinator module is wirelessly connected with the terminal devices via a ZigBee protocol for transmitting operation instructions and uploading the date of the terminal devices. The terminal devices receive the gateway instructions, execute the control instructions and unload the operation state of the devices and the environment parameter data. The computer remotely accesses the embedded Web gateway via the internet so as to obtain the household electric appliance control page, to manage the names of the terminal devices and to check and control the operation state of the devices and the environment parameter.
Owner:SOUTH CHINA UNIV OF TECH
Data management system providing a data thesaurus for mapping between multiple data schemas or between multiple domains within a data schema
InactiveUS7310646B2Easy to manage centrallyDigital data processing detailsOffice automationOperational systemMultiple Models
Owner:BLUE YONDER GRP INC
Man-machine identification method and system
ActiveCN104036780AAvoid abuseImprove experiencePayment architectureDigital data authenticationMan machineDeclassification
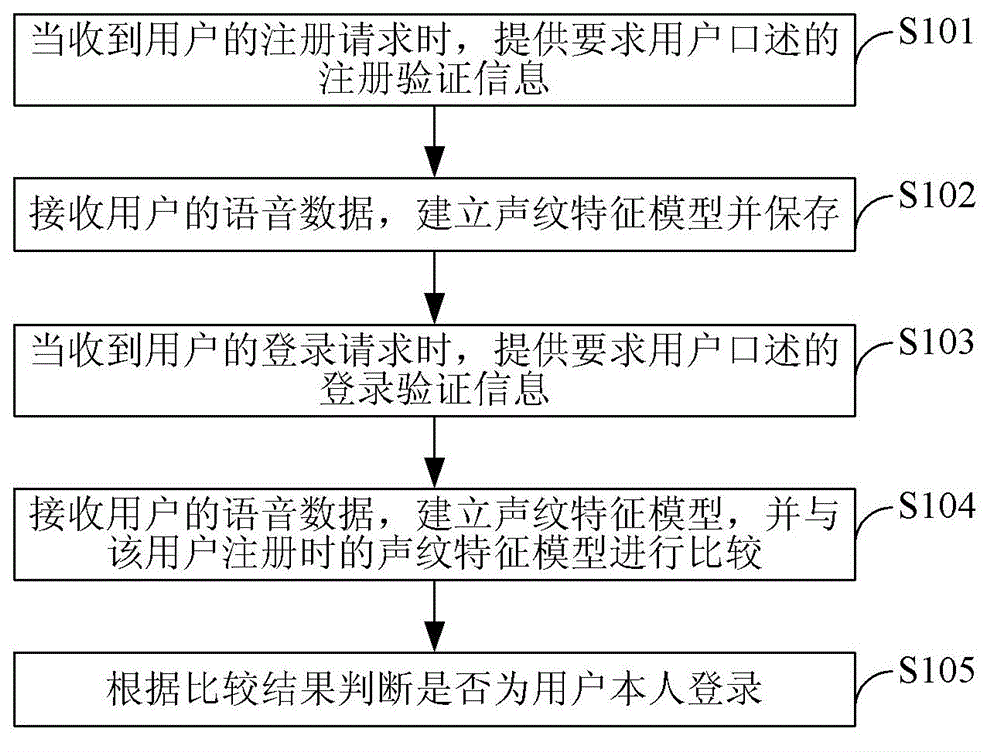
The invention discloses a man-machine identification method and system. The method comprises: when a registration request of a user is received, providing registration verification information which the user is requested to orally state; receiving voice data of the user, and establishing a voiceprint characteristic model for storage; when a login request of the user is received, providing login verification information which the user is requested to orally state; receiving voice data of the user, and establishing a voiceprint characteristic model, and comparing with the voiceprint characteristic model during registration of the user; and according to a comparison result, determining whether the user himself logs in. The man-machine identification method and system can improve declassification difficulties in man-machine identification.
Owner:ALIBABA GRP HLDG LTD
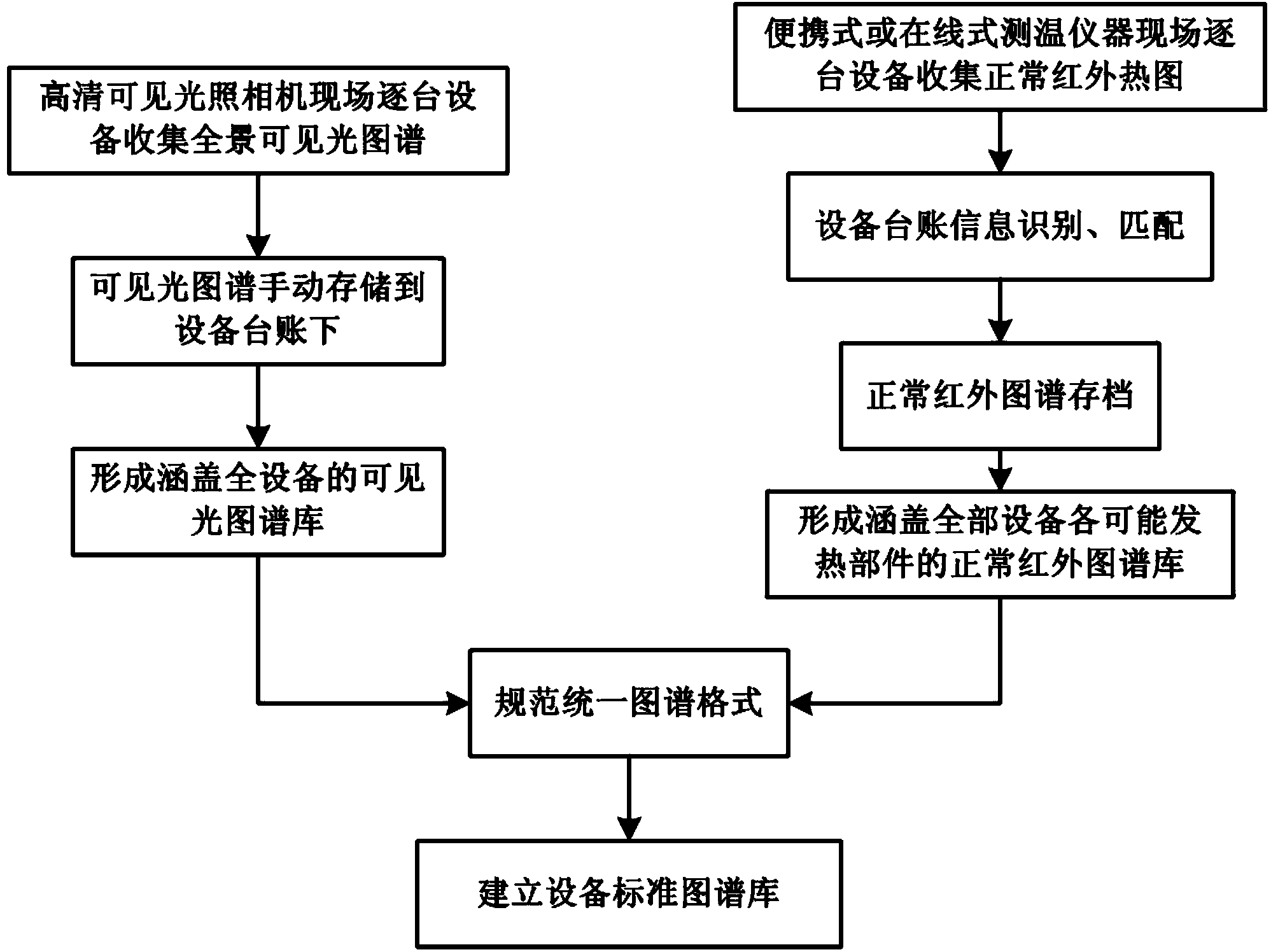
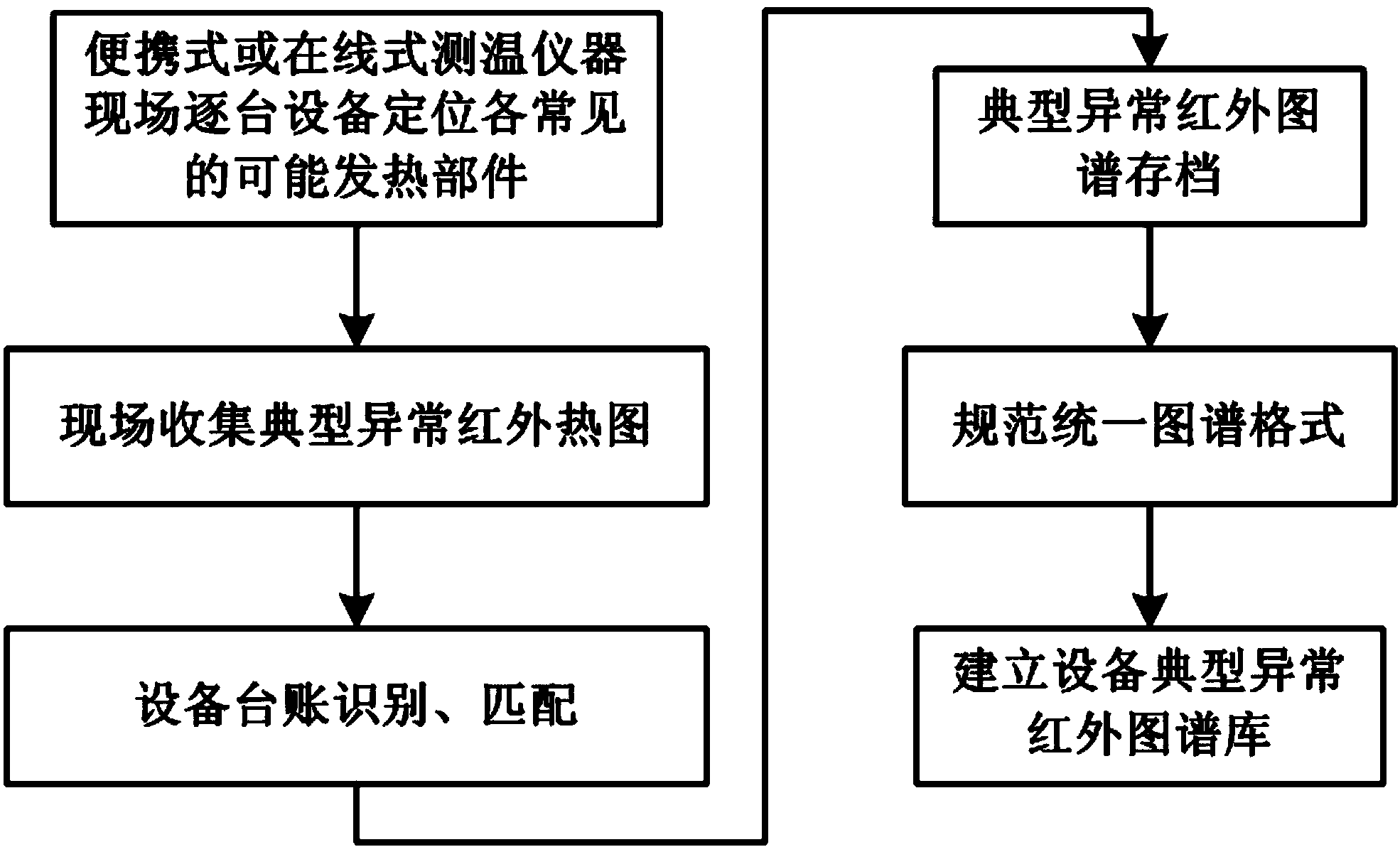
Method for diagnosing equipment overheating defects by utilizing infrared spectrum analysis
InactiveCN103901072AEasy to manage centrallyImprove accuracyMaterial flaws investigationInformation sharingDecision taking
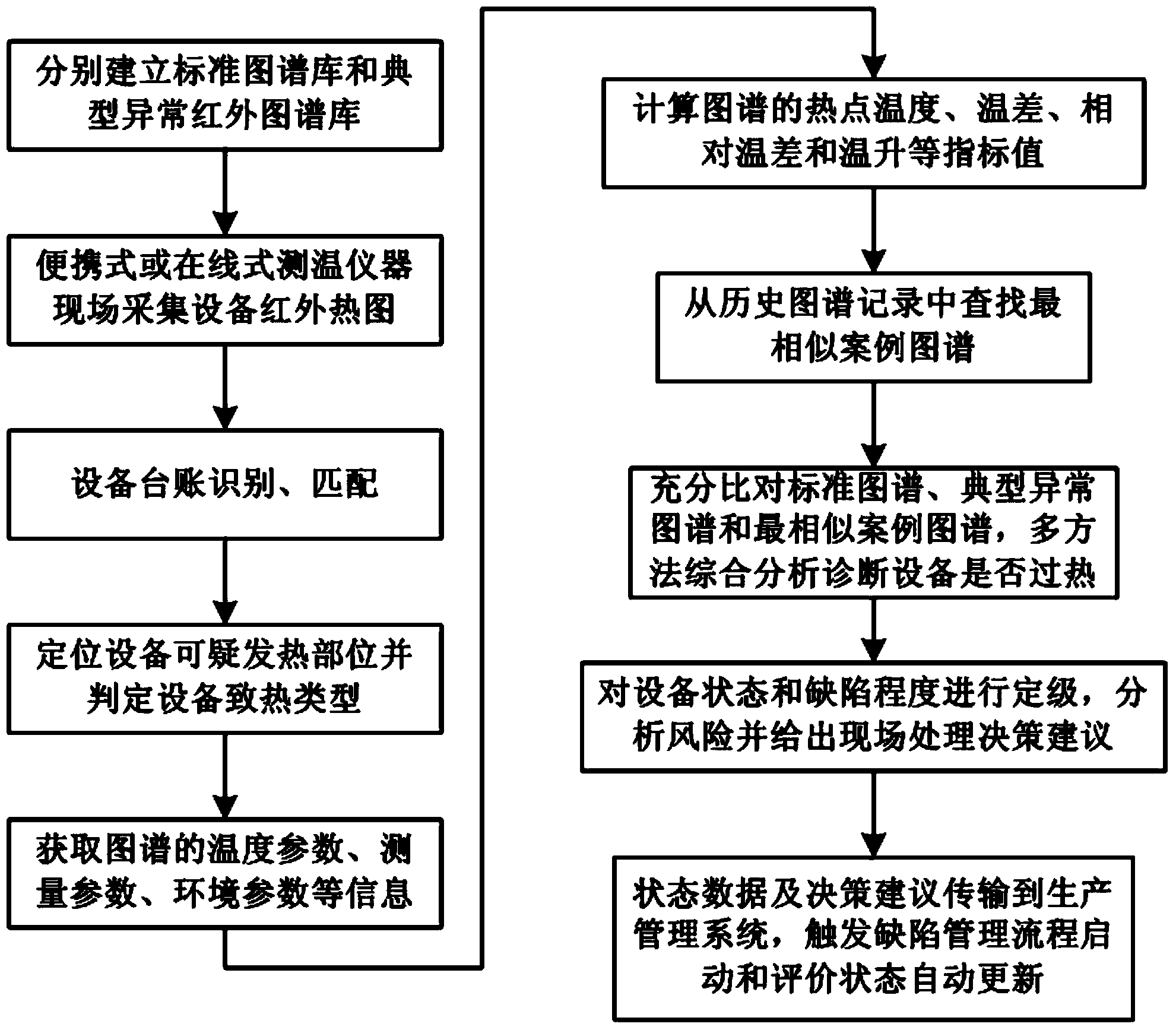
The invention discloses a method for diagnosing equipment overheating defects by utilizing infrared spectrum analysis. The method comprises the following steps: establishing a standard spectrum library and a typical abnormal infrared spectrum library; acquiring an infrared chart of equipment on site and identifying and matching standing book information of the equipment; calculating related temperature indexes of the spectrum, and automatically extracting the most similar case spectrum; fully contrasting the standard spectrum, the typical abnormal spectrum and the most similar case spectrum, and analyzing and judging whether the equipment is overheated; judging and ranking the equipment state and defect degree, analyzing the risk and giving processing decision suggestions; and transmitting the state data and decision suggestions to a production management system. According to the method for diagnosing equipment overheating defects by utilizing infrared spectrum analysis, centralized management and information sharing of the spectrums are conveniently realized, the accuracy and reliability of spectrum analysis and diagnosis are improved, ad the method provides decision suggestions for field defect processing, is in interactive cooperation with the production management system and has a positive effect of thoroughly promoting equipment state maintenance.
Owner:HUAINAN POWER SUPPLY CO OF STATE GRID ANHUI ELECTRIC POWER CORPORATIO
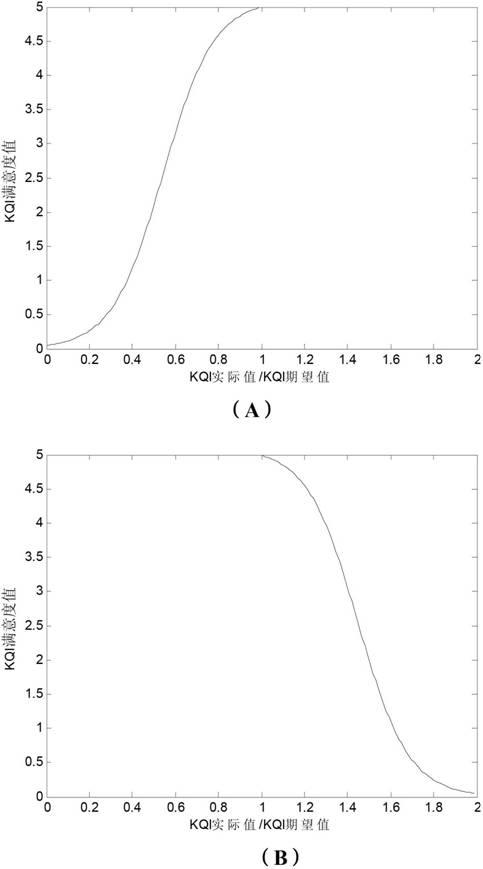
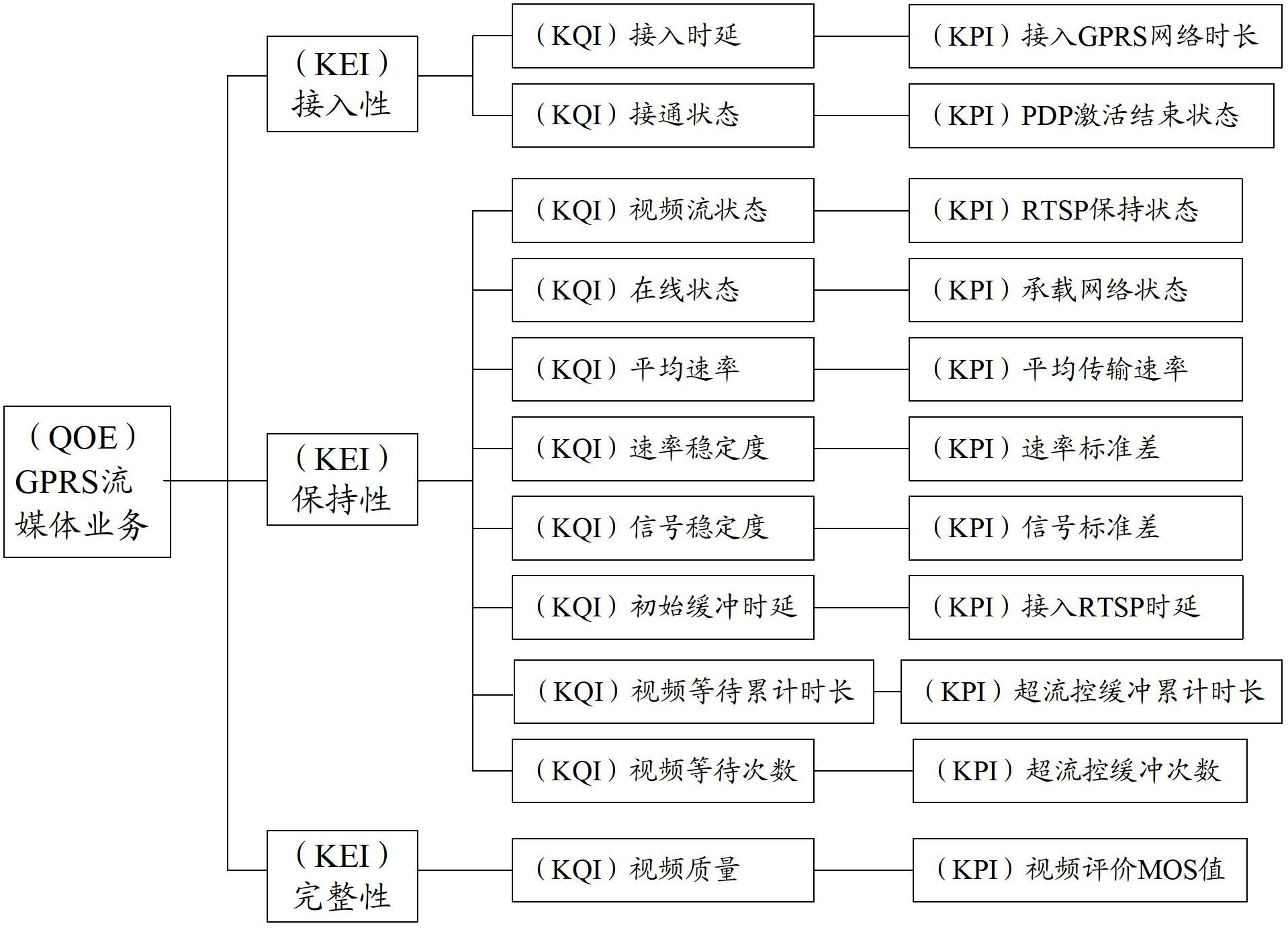
Method for evaluating QoE (Quality of Experience) of mobile streaming media service perception experience by simulating user behaviors
InactiveCN102685790AEasy to manage centrallyParameter standard objectiveSelective content distributionWireless communicationPsychological ModelsComputation complexity
The invention discloses a method for evaluating QoE (Quality of Experience) of mobile streaming media service perception experience by simulating user behaviors. The method comprises the following steps of: firstly, setting a mobile streaming media service QoE evaluation index system in which the user perception experience of mobile streaming media services are divided into parameters in three aspects of service access, service continuance and service completion; secondly, simulating the whole process of a user using the mobile streaming media services by a test terminal, and acquiring, respectively calculating key performance indexes (KPI) of the mobile streaming media services, calculating key quality indexes (KQI) of corresponding services of the mobile streaming media services, and performing comprehensive operation on the KQIs by means of a psychological model to obtain key experience indexes (KEI) of the corresponding services; and finally, comprehensively analyzing the KEI indexes to obtain a streaming media service QoE value which is in a five-grade marking system and equivalent to international standard MOS (Mean Opinion Score). The method disclosed by the invention is objective and practicable in evaluation parameter standard, simple in operation step, low in calculation complexity and easy to integrate, and is capable of obtaining relatively objective, just user experience perception quality by simulating the mobile streaming media service user.
Owner:北京东方文骏软件科技有限责任公司 +1
Method and system for preventing ARP message attack
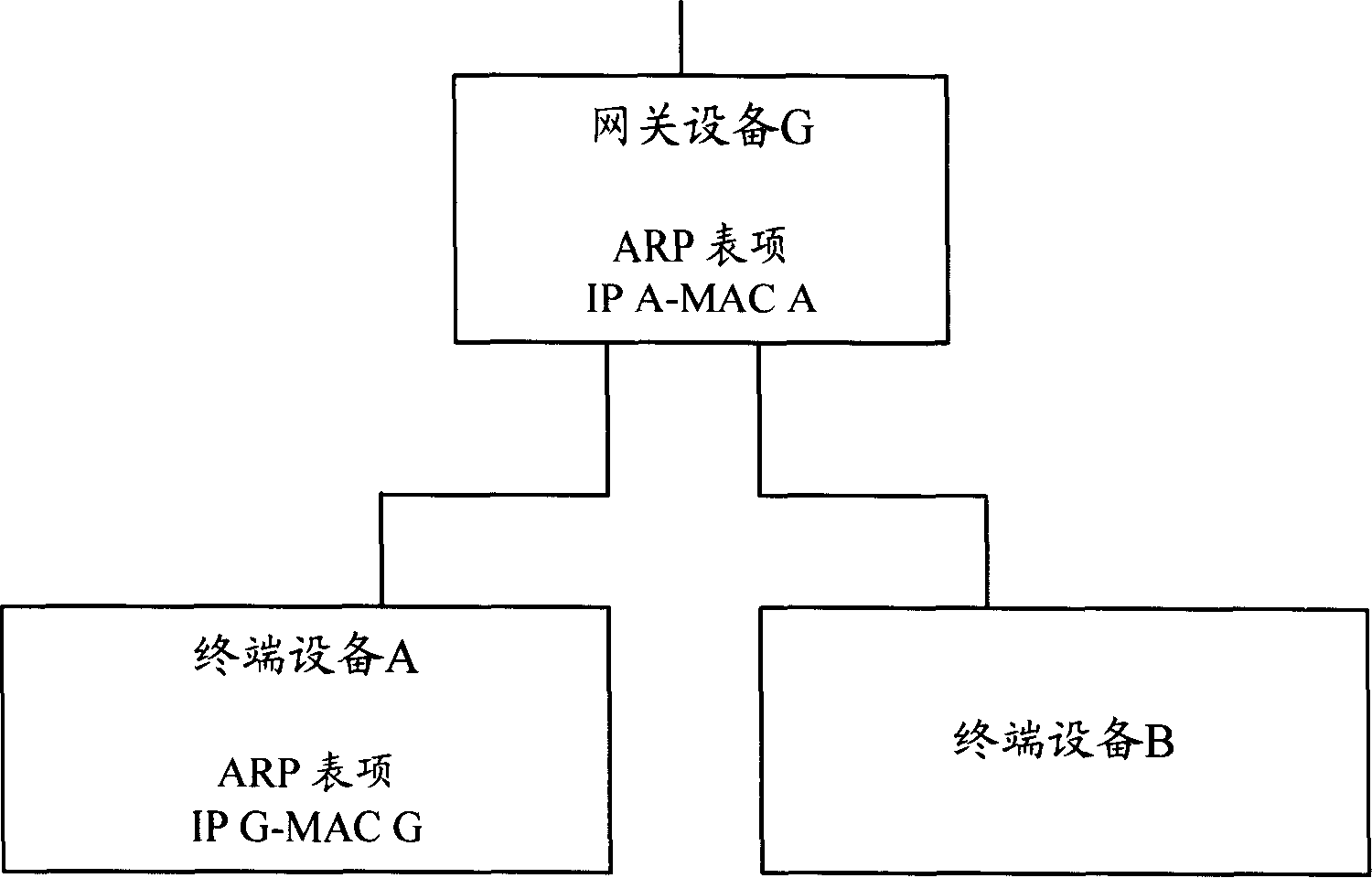
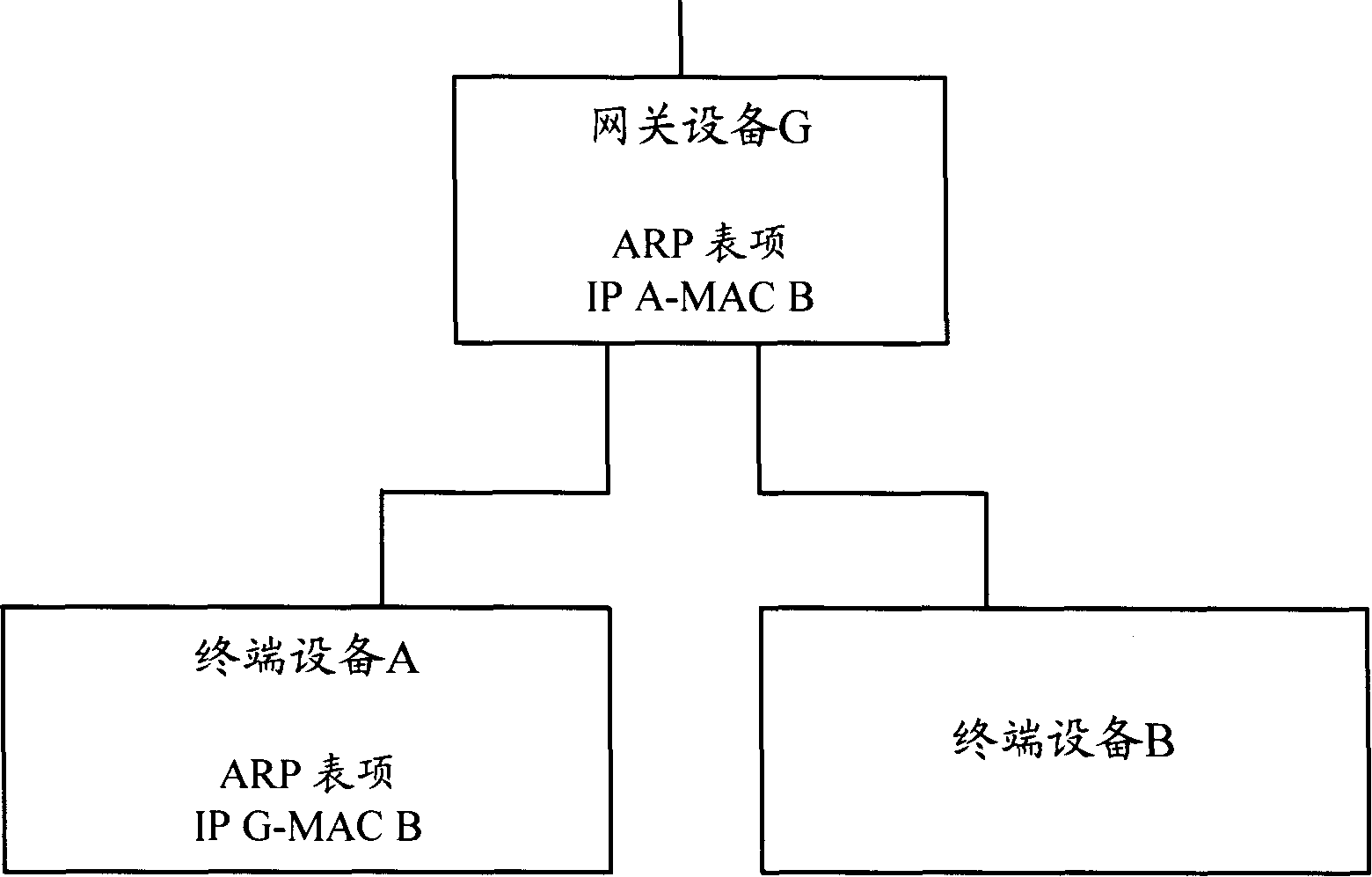
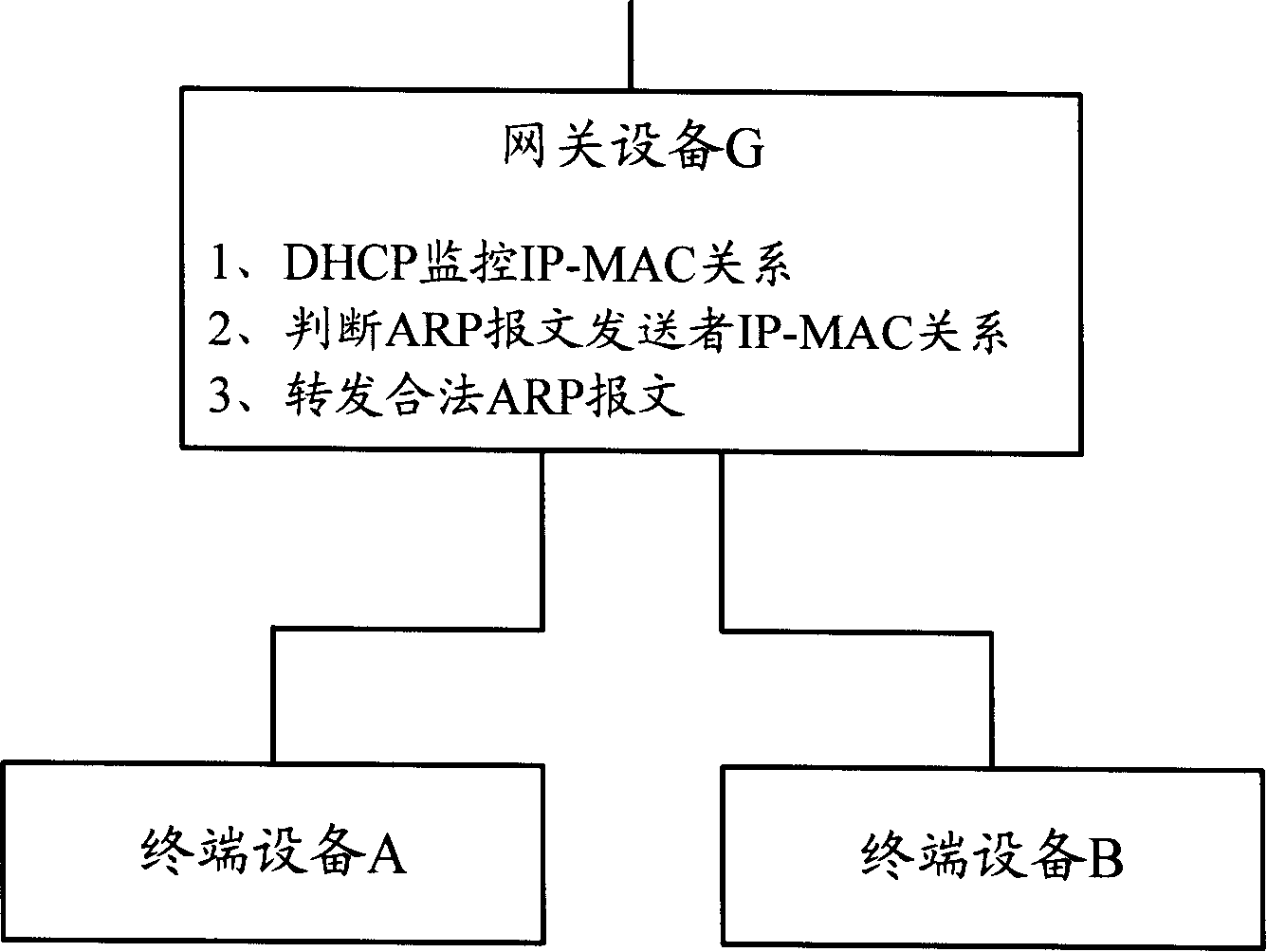
InactiveCN101175080AEffective defenseEasy to manage centrallyNetwork connectionsSecuring communicationAddress Resolution ProtocolIp address
The invention discloses a method for preventing ARP (address resolution protocol) message attack, which comprises the following procedures: a DHCP (dynamic host configuration protocol) server adds IP address-MAC address into DHCP message and sends to a user terminal; the user terminal receives the DHCP message, analyzes the IP address-MAC address couple included in the DHCP message and changes the message into local ARP table which can not be dynamically rewritten, so as to prevent the network from attacking of the attack message through rewriting the ARP table of user terminal. The invention also discloses a system for preventing ARP message attack. With the invention, the gateway device in network and the user terminal are capable of defending the received ARP attack message. In addition, the important ARP tables of user terminals in network are under unified configuration by DHCP server, which is convenient for centralized management.
Owner:NEW H3C TECH CO LTD
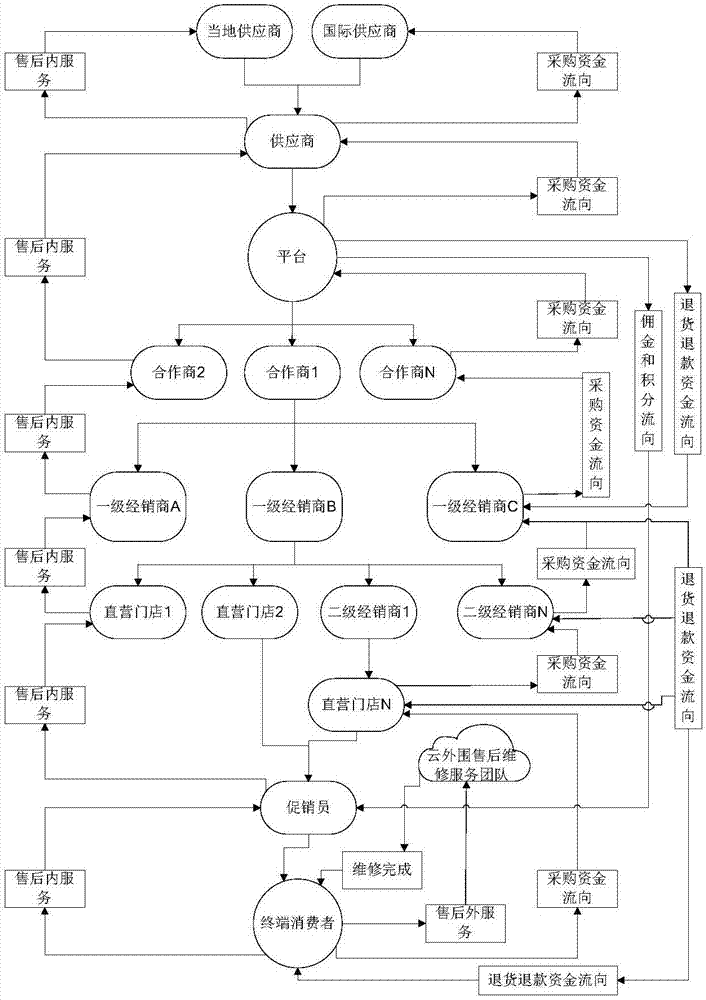
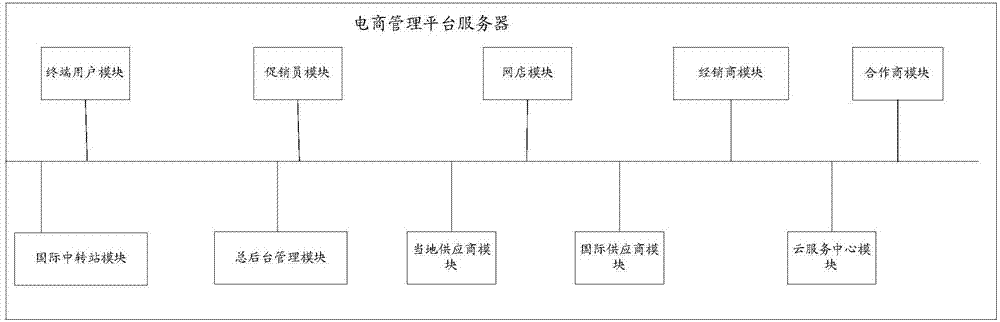
Cross-border vertical e-commerce management method
ActiveCN107886391AImprove user experienceEasy to manage centrallyBuying/selling/leasing transactionsPaymentSystem integration
The invention discloses a cross-border vertical e-commerce management method, and the method is based on an industrial e-commerce management platform which integrates a supplier, an importer, a dealer, a second-level dealer, a direct-sales store, a sales promoter, a terminal consumer, and an aftersales cloud service center. The method achieves the system integration of the industrial resources ina mode of Internet + conventional channels, facilitates the central management, and can provide more and more scientific data for each role or provide parameters for each role so as to help the rolesmake decisions. Moreover, all parties participating in the transaction can complete the transaction through the e-commerce management platform built through the cross-border vertical e-commerce management method. For example, the method can achieve the information transmission, quick ordering, payment, sales promotion, aftersales and cloud maintenance services, greatly reduces the time cost and manpower and material cost of transaction for all parties, and improves the success rate of trades. The method also provides corresponding data and analyses of market conditions for each role, providesreference for each role for each decision making, and improves the user experience.
Owner:兰世德
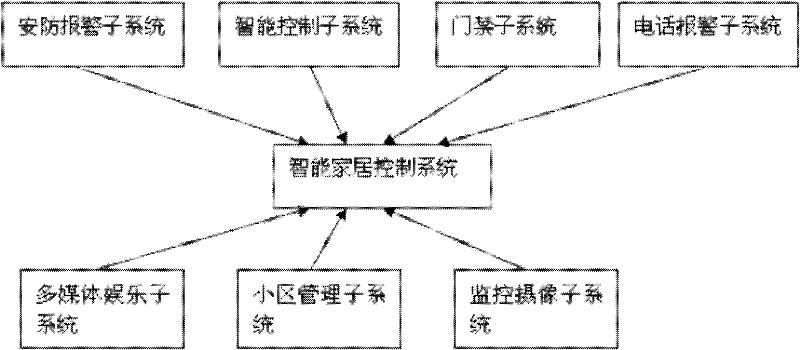
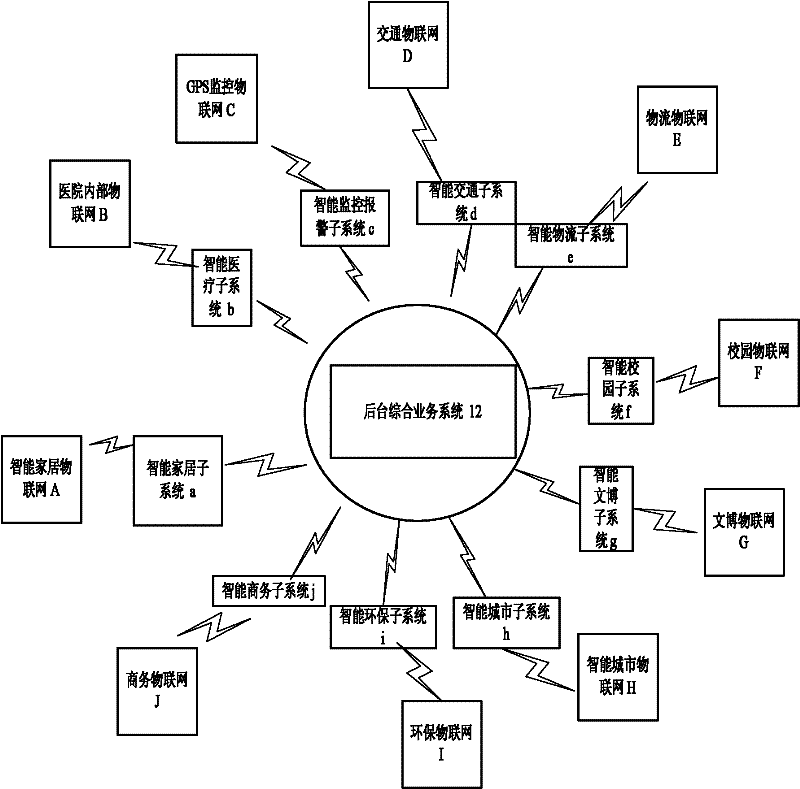
Smart home service system and its working method
ActiveCN102279589AEasy to controlAll-round smart home serviceData switching networksProgramme total factory controlLogistics managementIntelligent city
The invention discloses an intelligent family service system and a working method thereof. The intelligent family service system comprises an intelligent home subsystem, an intelligent medical care subsystem, an intelligent monitoring alarming subsystem, an intelligent traffic subsystem, an intelligent logistics subsystem, an intelligent campus subsystem, an intelligent relics and antiquities subsystem, an intelligent city subsystem, an intelligent environmental protection subsystem, and an intelligent commerce subsystem, wherein the above-mentioned subsystems are managed and controlled by a background integrated service system. The above-mentioned subsystems are respectively connected with an intelligent home internet of things, a hospital internal internet of things, a GPS monitoring internet of things, a traffic internet of things, a logistics internet of things, a campus internet of things, a relics and antiquities internet of things, a city internet of things, a environmental protection internet of things, and a commerce internet of things. According to the invention, all the subsystems are connected with communication of all the internets of things, so that an intelligent production and living system is generated and a user can really enjoy all-round intelligent home services; moreover, the services can be selected by then user willfully according to demands.
Owner:杭州洪奇信息科技有限公司
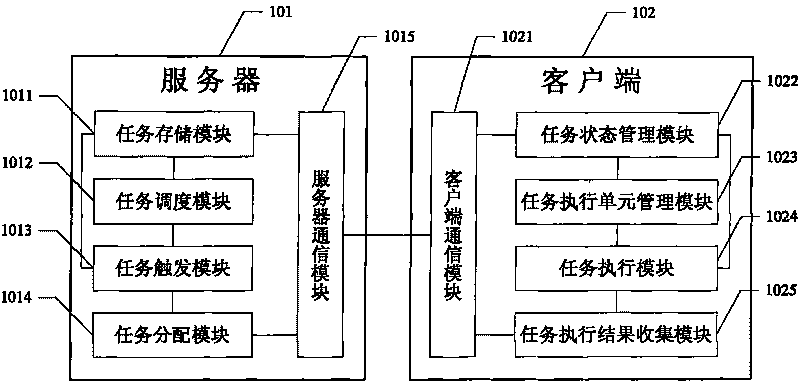
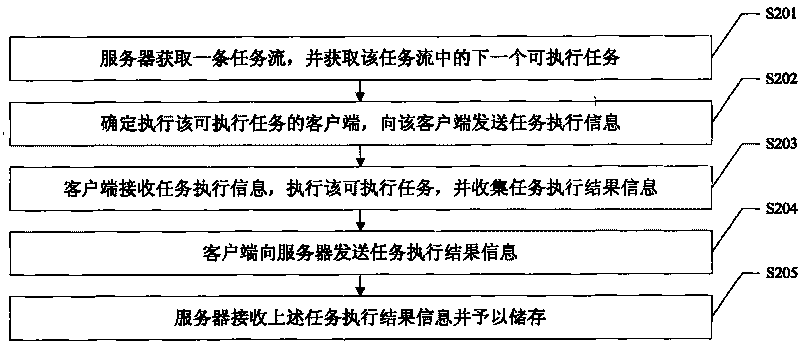
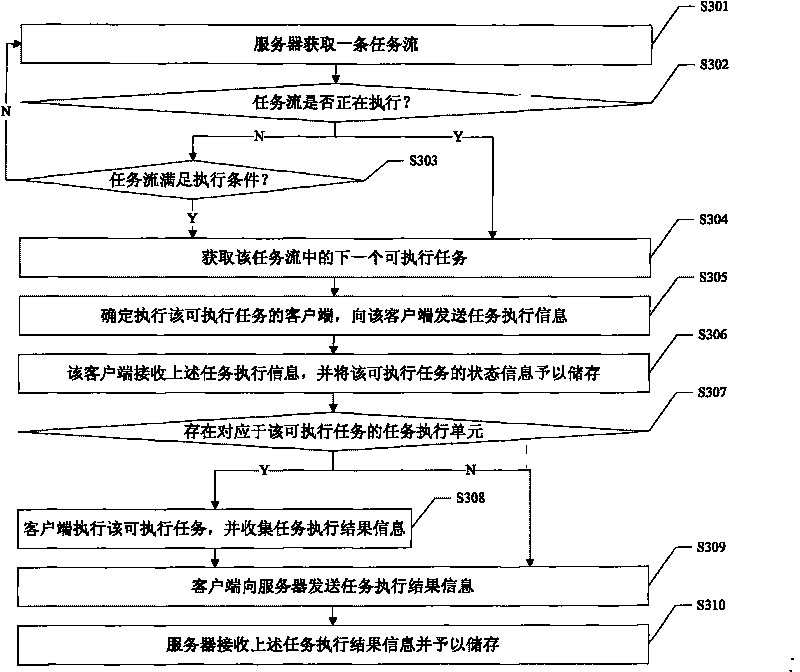
Distributed system and method for processing task flow thereof
InactiveCN101741885ADistributed task processing implementationRealize network collaborationMultiprogramming arrangementsTransmissionClient-sideDistributed computing
The invention discloses a distributed system and a method for processing a task flow thereof, and the method comprises the following steps: acquiring a task flow and an executable task in the task flow by a server, distributing a client side for executing the executable task to the executable task and transmitting the task executing information for executing the executable task to the client side, wherein the information executing information comprises the executable task; receiving and executing the executable task by the client side, and transmitting the task executing result to the server; receiving and storing the task executing result information by the server. When the task flow is processed by the scheme in the invention, aiming at different executable tasks in the task flow, the server can respectively distribute different client sides to the different executable tasks for processing, thus realizing distributed processing on the task flow and network collaboration of the task flow.
Owner:珠海市西山居软件有限公司
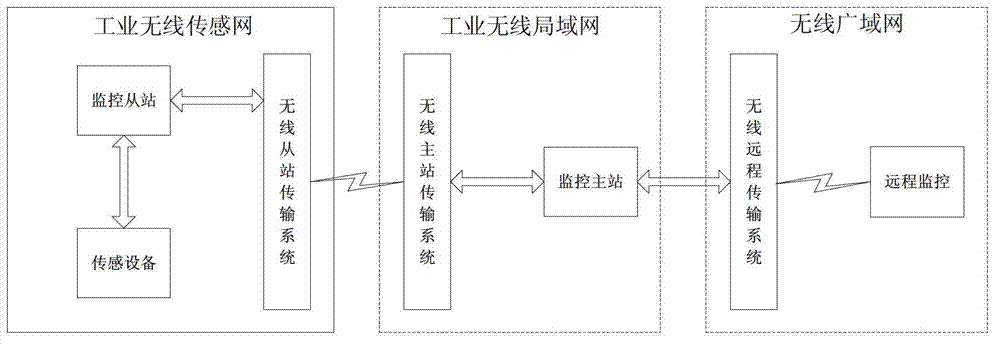
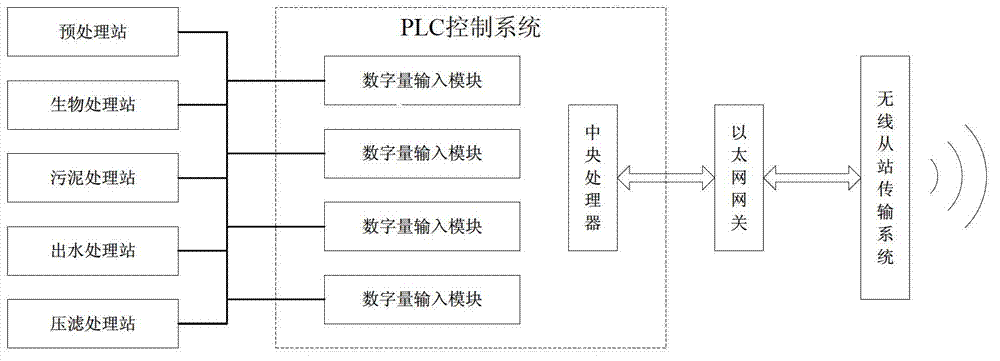
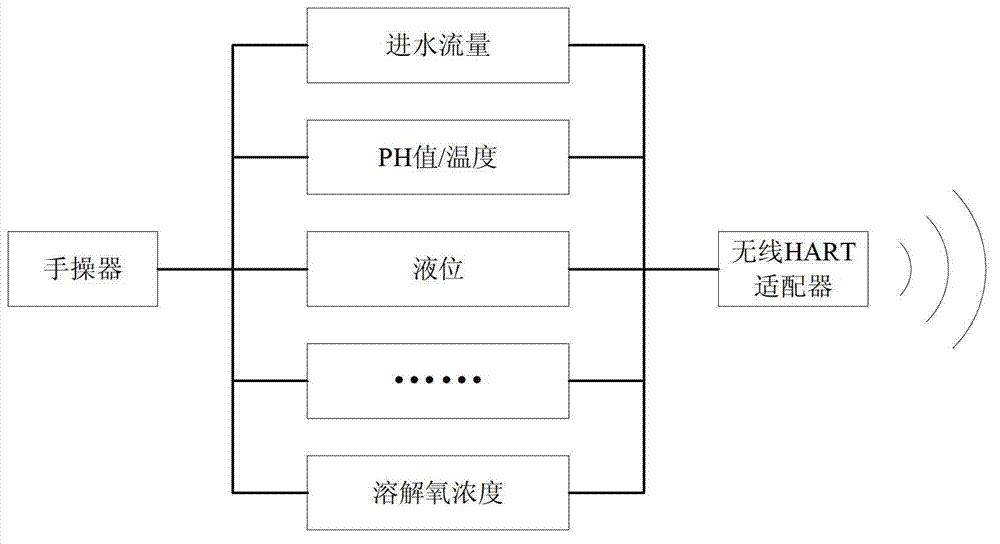
Wastewater treatment process monitoring system based on wireless network
ActiveCN103034211AReduce cable costsEasy and flexible installationTotal factory controlProgramme total factory controlLocal area networkEngineering
The invention discloses a wastewater treatment process monitoring system based on a wireless network. The wastewater treatment process monitoring system based on the wireless network comprises an industrial wireless sensor network, an industrial wireless local area network and a wireless wide area network. The industrial wireless sensor network is responsible for collecting information of field devices of each process of the wastewater treatment. The industrial wireless local area network is responsible for processing the information which is sent by the industrial wireless sensor network and returning the processed data to the field devices at the same time. The wireless wide area network is responsible for transmitting and replying remote monitoring application and sending stoppage information to appointed technical people automatically at regular intervals during the period from stoppage occurrence to stoppage resolution. A traditional distributed collecting and distributing control system is updated to a network control system through different wireless networks, and therefore wireless remote real-time monitoring is truly realized.
Owner:无锡轻大百特环保工程有限公司
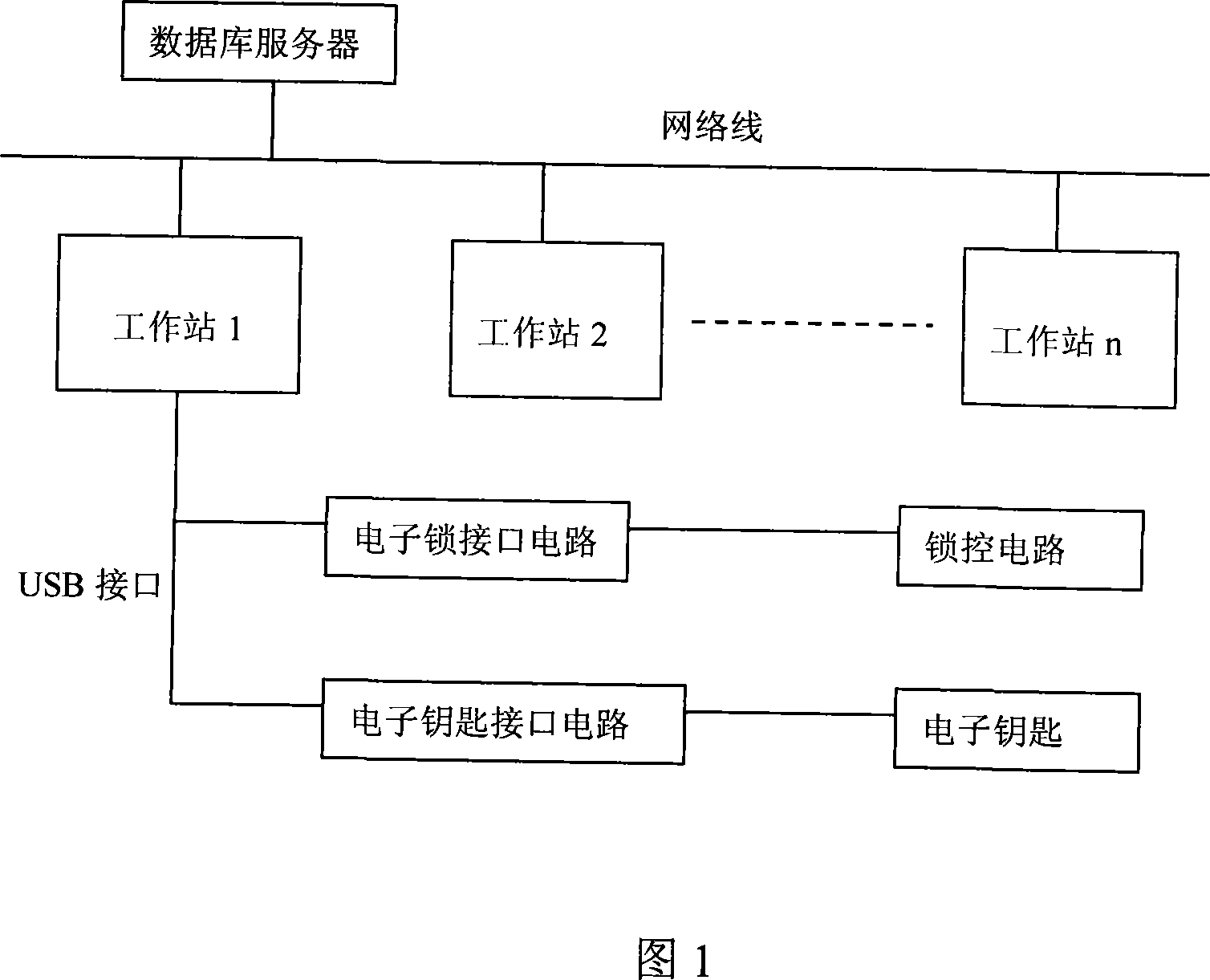
Electronic lock management system
ActiveCN101216959AReduce volumeSimple key circuitIndividual entry/exit registersPrimary stationDatabase server
An electronic lock management system is characterized in that a main station system includes a database server and a set of network workstations; the database server is used for recording an unlocking process, storing unlocking authority of an electronic key and organization and personal information of a management department, and depositing parameters of the electronic lock and the electronic key; the database server and the set of network workstations constitute a network system; system management software is disposed in the network workstations, and provides management of an organizational structure, electronic lock initialization setting, electronic key initialization setting, electronic key authority management, and electronic key unlocking process management; and the network workstations are used for reading information in the electronic key for the electronic lock or downloading information into the electronic lock and the electronic key. The inventive system can satisfy management of electronic key unlocking process, and has the advantages of no need of electronic lock networking, low system cost and low power consumption.
Owner:HUAINAN POWER SUPPLY CO OF STATE GRID ANHUI ELECTRIC POWER CORPORATIO +1
Energy Efficient Management of Heterogeneous Multi-Hop Wireless Networks
ActiveUS20160212698A1Reduce in quantityReduce collisionPower managementTransmission systemsTime scheduleTransceiver
A wireless multi-hope network of nodes including data nodes and at least one sink node. The data nodes include battery-powered nodes (BPNs) having active and sleep periods and mains-powered nodes (MPNs) having only active periods, wherein each data node transmits the packets only within corresponding active periods. A BPN includes a transceiver for transmitting and receiving data packets and a processor for determining a schedule of active and sleep periods of the BPN independently from the active and sleep periods of other data nodes in the network and independently from commands transmitted by the sink node, and a battery for providing energy to the transceiver and the processor. The processor switches the transceiver ON and OFF according to the schedule.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Method, device and system for signal shielding of wireless communication system
InactiveCN102868421APrecision interferenceInterference goals are clear and controllableEnergy efficient ICTSynchronisation arrangementCommunications systemBase station
The invention discloses a method, a device and a system for signal shielding of a wireless communication system. The method comprises the steps of: obtaining community configuration information of the wireless communication system in a shielded range by monitoring signals of the wireless communication system in the shielded range; generating all or part of downlink public channel signals and / or public signals with the same format as a target shielded community according to corresponding community configuration information of the target shielded community in the community configuration information; and sending the generated downlink public channel signals and / or public signals to the shielded range. The invention also discloses a device and a system for signal shielding of the wireless communication system. By adopting the method, the device and the system, the specific targeted downlink interference can be performed on the signals of the wireless communication system to be shielded, the interference to uplink signals of a base station of the wireless communication system and the interference to the wireless communication system needing no interference can be avoided, and the interference transmission power can be reduced.
Owner:赵训威
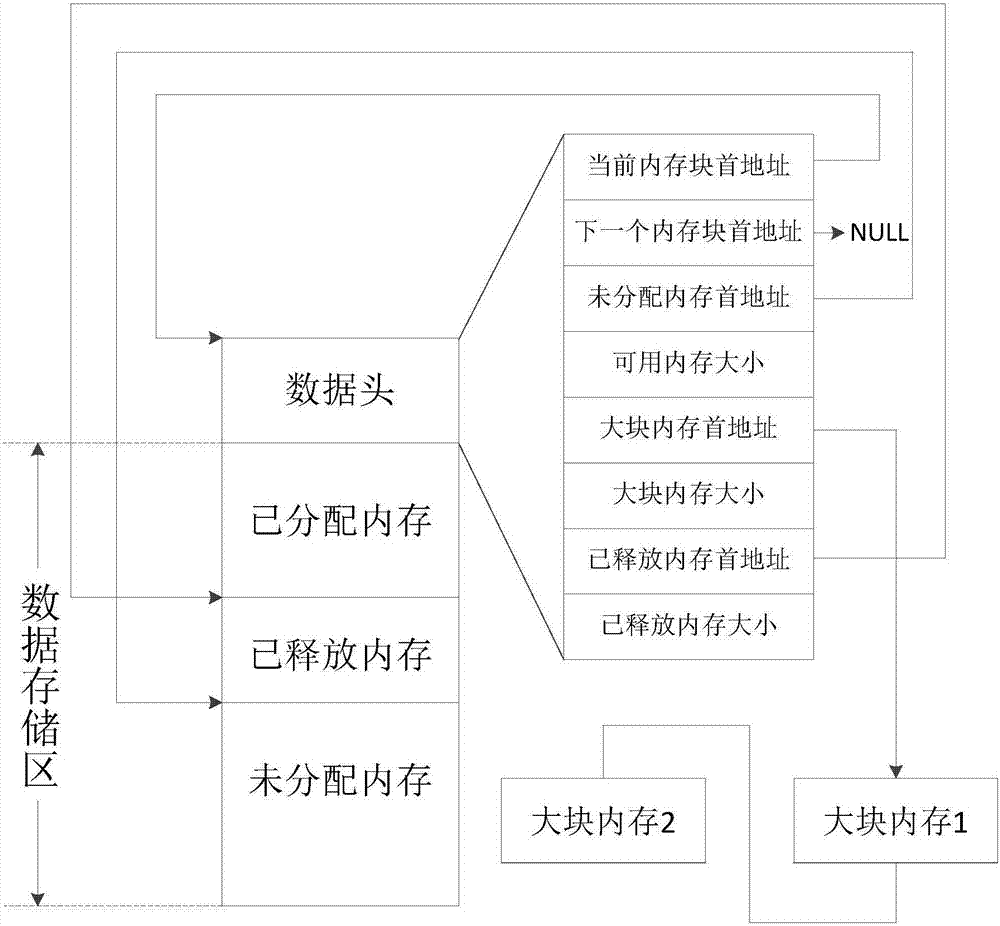
Memory allocation processing method and device
InactiveCN107153618AReduce memory fragmentationImprove space utilizationMemory systemsOptimization systemMemory block
The embodiment of the application discloses a memory allocation processing method and device. The method comprises the steps that memory application information is obtained, and whether or not the applied memory is less than the maximum allocable memory of the memory blocks in the established memory pool is judged; when it is determined that the memory application is greater than the maximum allocable memory, according to the recorded large block of memory information in the data header of the memory block, the memory is allocated from the large block of memory to the application memory; otherwise, whether or not the application memory is greater than the free memory of current memory block is judged, when it is determined that the application memory is less than the free memory of current memory block, whether or not the current remaining space of current memory block meets the needs for the application memory is judged; if the current remaining space of current memory block meets the demand by the application memory, the memory is allocated from the current remaining space of current block memory block to the application memory. By the method and device, the time spent for memory allocation can be reduced, the memory utilization rate of a system is increased, and memory allocation efficiency of the system is optimized.
Owner:ADVANCED NEW TECH CO LTD
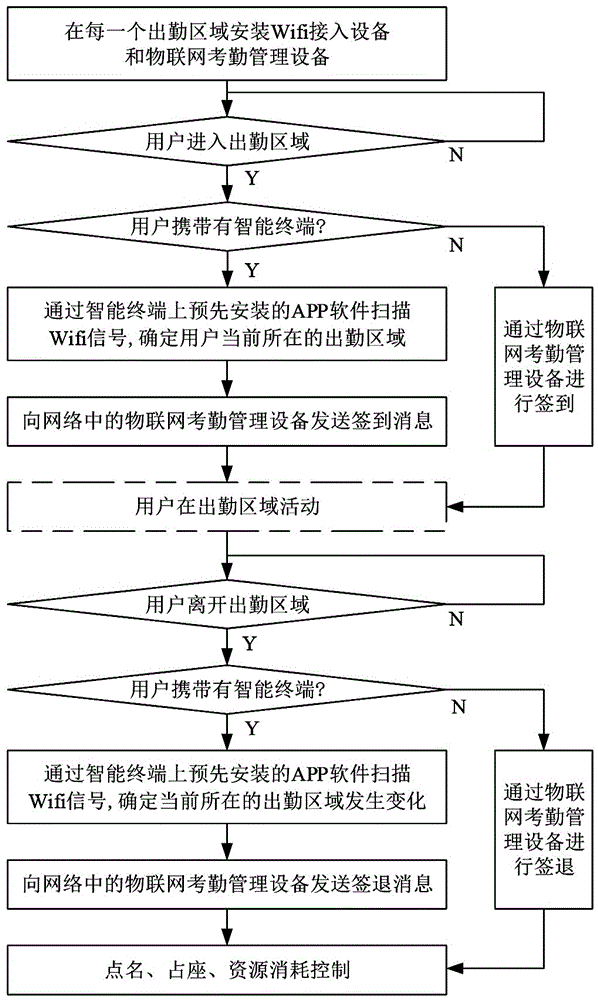
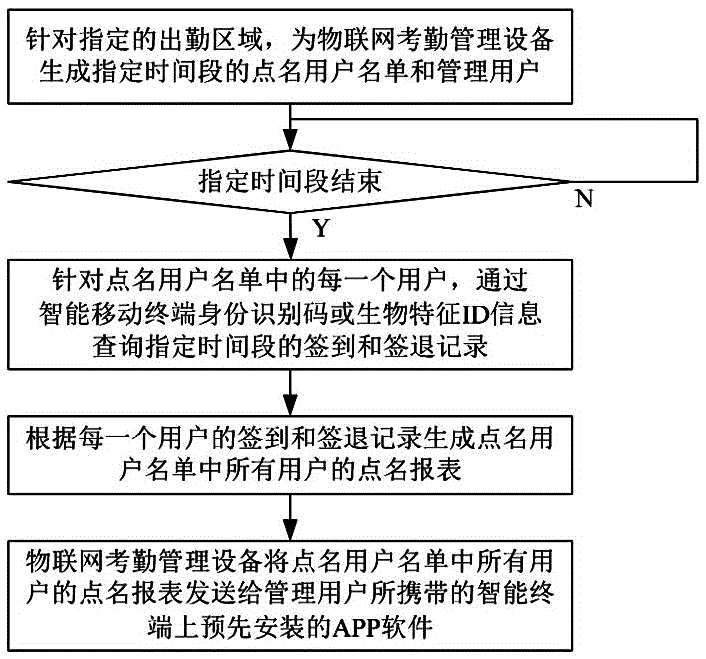
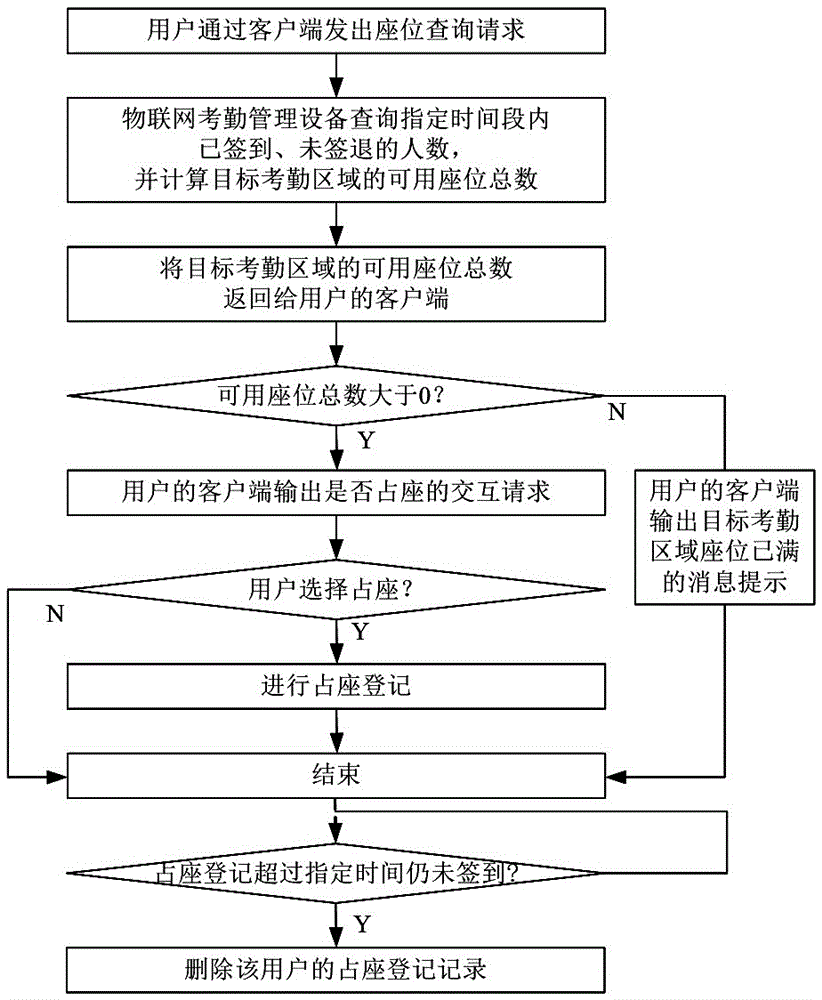
WiFi positioning based attendance management method and system
ActiveCN105825555AEasy to useQuick implementationRegistering/indicating time of eventsComputer networkReal-time computing
The invention discloses a WiFi positioning based attendance management method and system. The method comprises the following steps: installing WiFi access equipment and things of internet attendance management equipment in an attendance area in advance; carrying out automatic check-in on an intelligent mobile terminal or artificial check-in through things of internet attendance management equipment, when an user enters the attendance area; and carrying out automatic check-out on an intelligent mobile terminal or artificial check-out through things of internet attendance management equipment, when an user leaves the attendance area. The system comprises an attendance area equipment unit and a computer, and the attendance area equipment unit comprises WiFi access equipment and things of internet attendance management equipment. The check-ins and check-outs of users can be managed by combining the WiFi positioning and attendance, basic data of attendance management of users can be provided; according to the basic data, extended functions such as roll call, occupation, comprehensive resource consumption control, and the like can be realized.
Owner:谷振宇
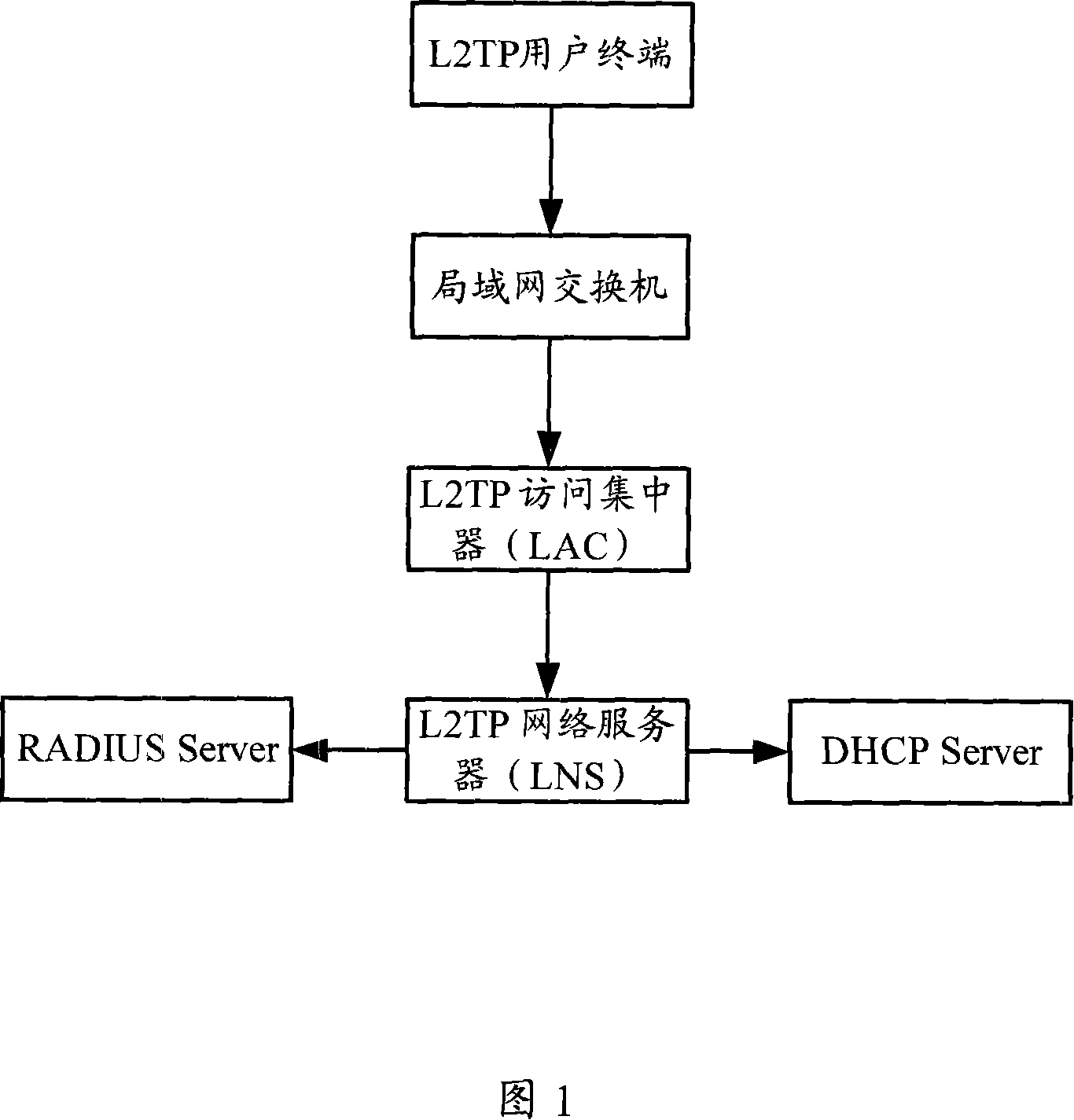
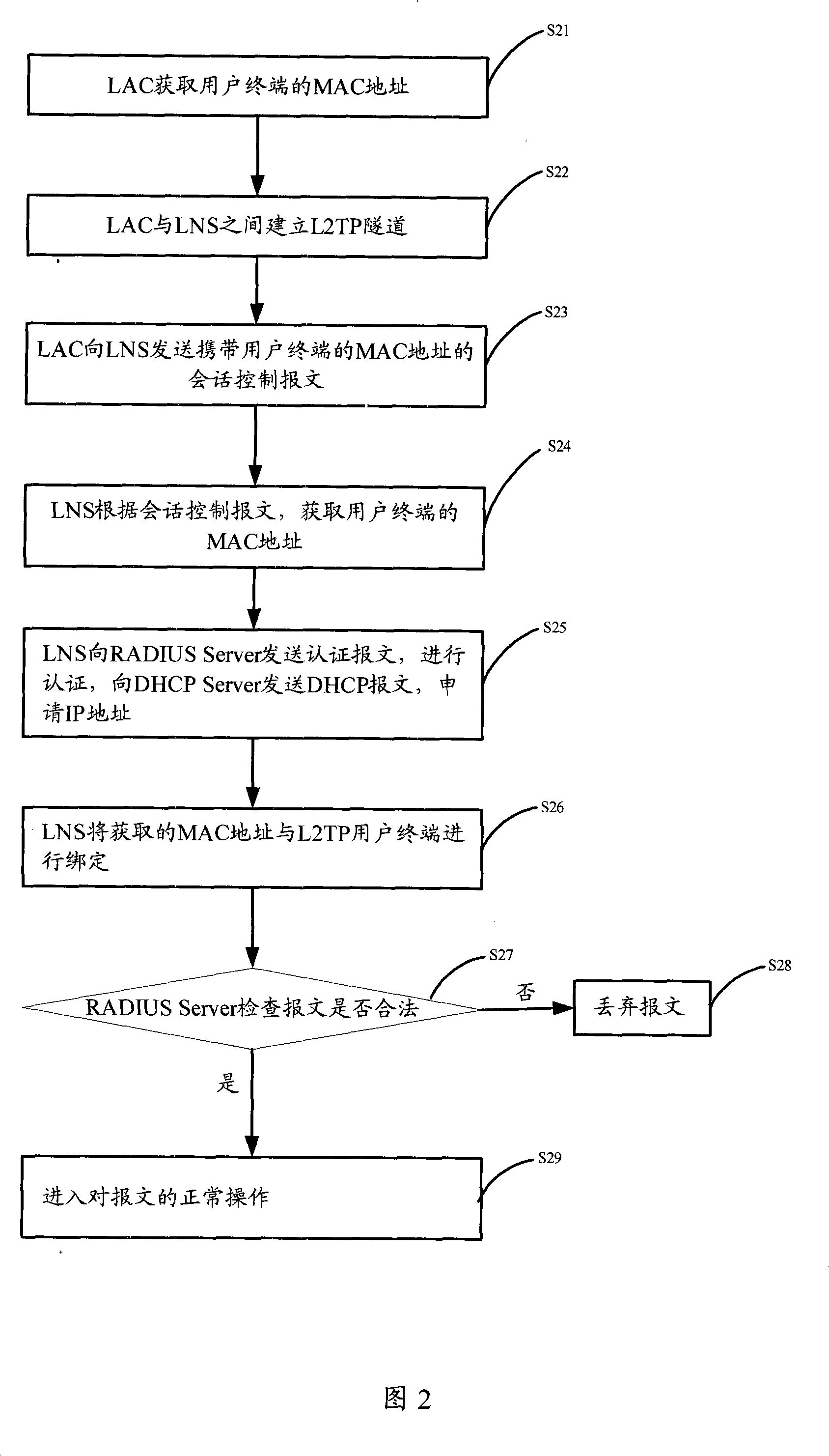
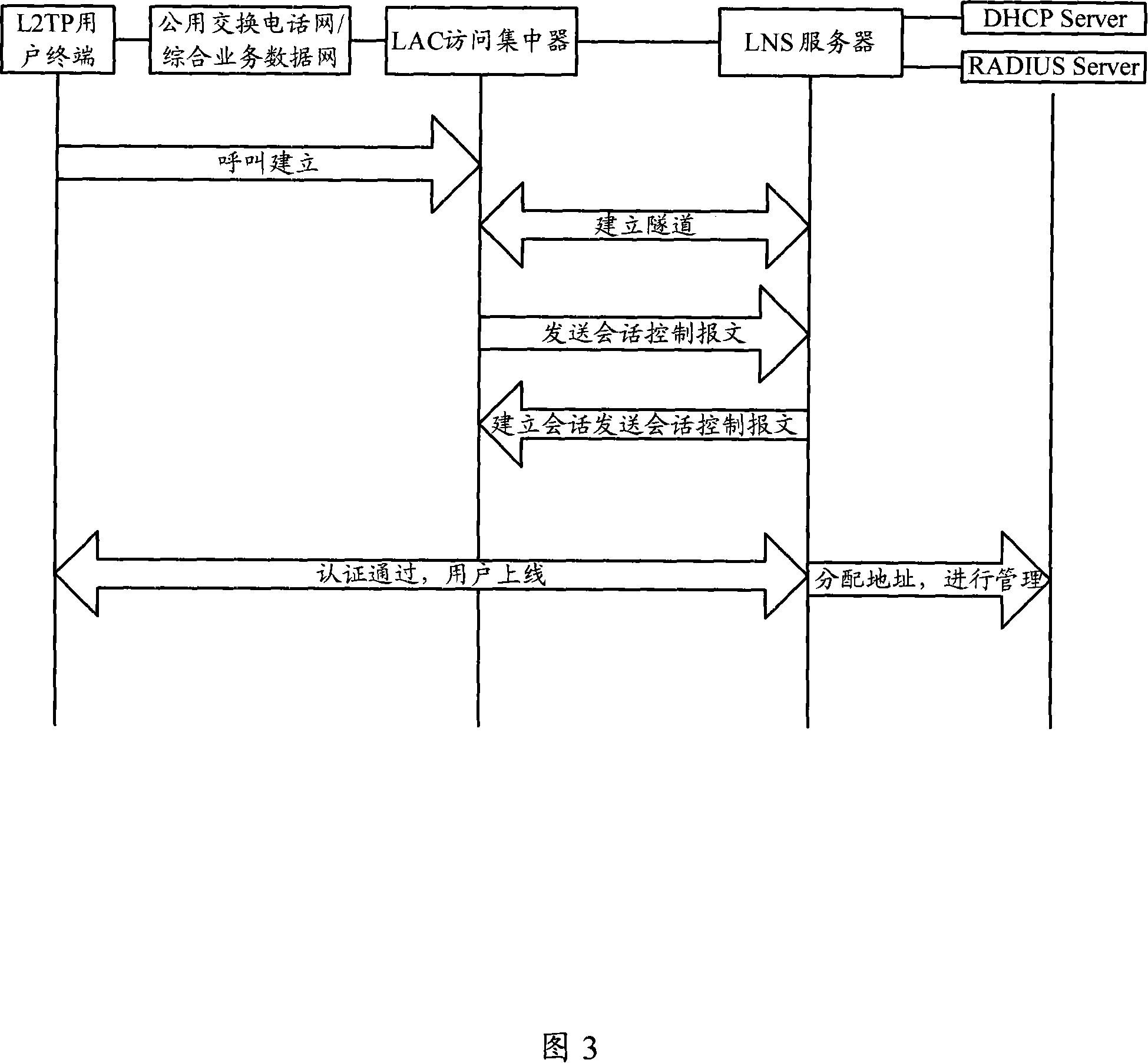
Method, device and system for obtaining medium access control address
The present invention discloses a method for getting the MAC address, which relates to the network communication field. First, an LAC gets the MAC address of a user terminal; then, the LAC sends a session control message carrying the MAC address of the user terminal to an LNS; at last, the LNS gets the MAC address of the user terminal according to the session control message. The present invention also discloses a system for getting the MAC address, an LAC and an LNS. The present invention makes the LNS capable of getting the MAC address of the user terminal through the session control message carrying the MAC address of the user terminal. A DHCP server can allocate IP addresses for the user terminal according to the MAC address of the user terminal, which is favorable for the IP addresses centralized management. Moreover, a RADIUS Server can also perform authentication, accounting and management to the users according to the MAC address of the user terminal.
Owner:HUAWEI TECH CO LTD
Hybrid wavelength-division and time-division multiplexing passive sensing optical network
ActiveCN101715153AIncrease capacityRealize multi-region monitoringMultiplex system selection arrangementsTerminal equipmentOptical sensing
The invention provides a hybrid wavelength-division and time-division multiplexing passive sensing optical network which comprises optical terminal equipment, a passive optical network and an optical sensing unit, wherein a two-way port of the optical terminal equipment is connected to a two-way port of the passive optical network by an optical fiber, and the passive optical network is also connected with the optical sensing unit. The invention mixes a wavelength-division and time-division multiplexing technology and an optical fiber sensing technology and has large multiplexing volume and wide monitoring range.
Owner:HUAZHONG UNIV OF SCI & TECH
Device networking and network-accessing management method for intelligent housing system
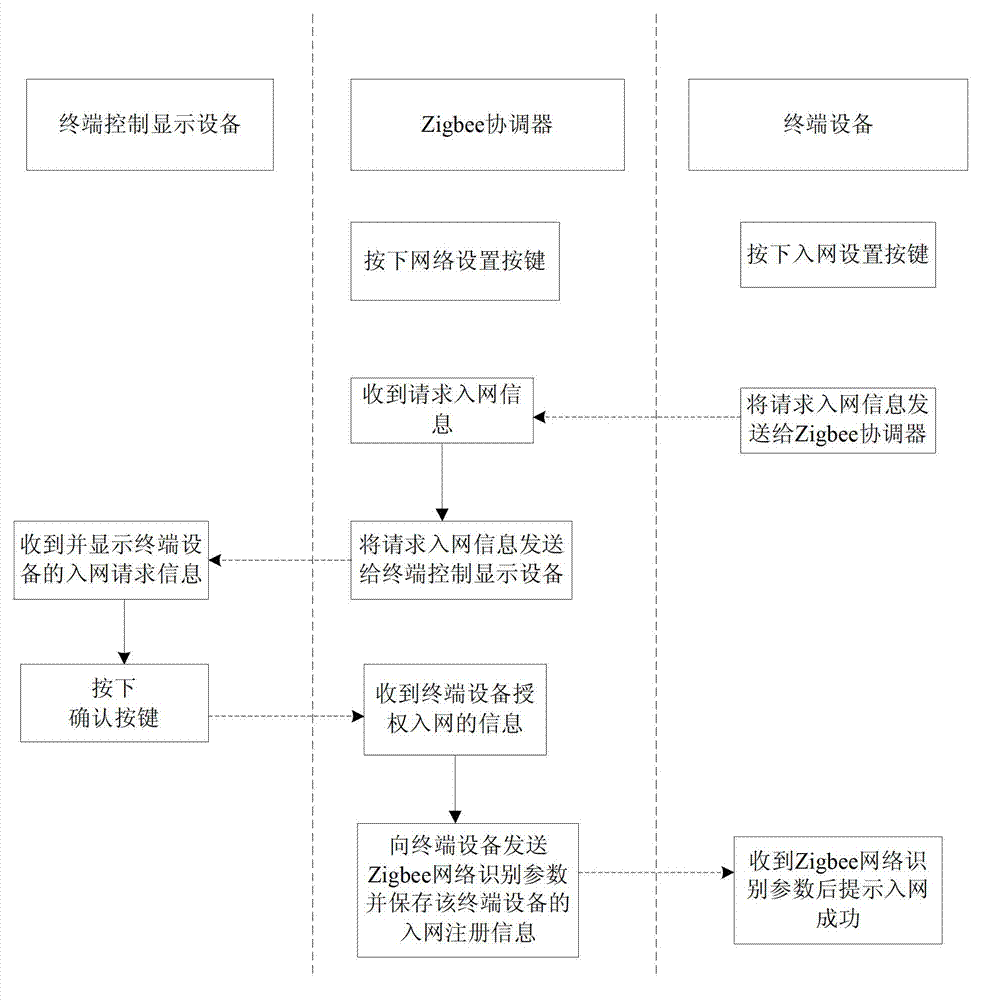
InactiveCN102905396ADistribution without limitEasy to manage centrallyNetwork topologiesTerminal equipmentDisplay device
The invention relates to a device networking and network-accessing management method for an intelligent housing system. The device networking and network-accessing management method is characterized in that a terminal device in the intelligent housing system is connected with a Zigbee coordinator through a Zigbee wireless transport protocol, so as to form the Zigbee netowork of the intelligent housing system; and the Zigbee coordinator is further connected with a terminal control display device. The method comprises the following steps that: the terminal device in the intelligent housing system sends the network-network request information to the Zigbee coordinator; the Zigbee coordinator receives the network-network request information, and sends the network-network request information to the terminal control display device; the terminal control display device receives authorized network-accessing information confirmed by the outside, and returns the information authorizing the terminal device to access to the network to the Zigbee coordinator; the Zigbee coordinator sends Zigbee network identification parameters to the terminal device, and saves the network-accessing log-in message of the terminal device; the terminal device prompts that network accessing is successful after receiving Zigbee network identification parameters, thus the terminal device acquires the network-accessing authority. The device networking and network-accessing management method has high safety.
Owner:NINGBO HAIBO GRP CO LTD
High yield breeding method of bean hawk moth
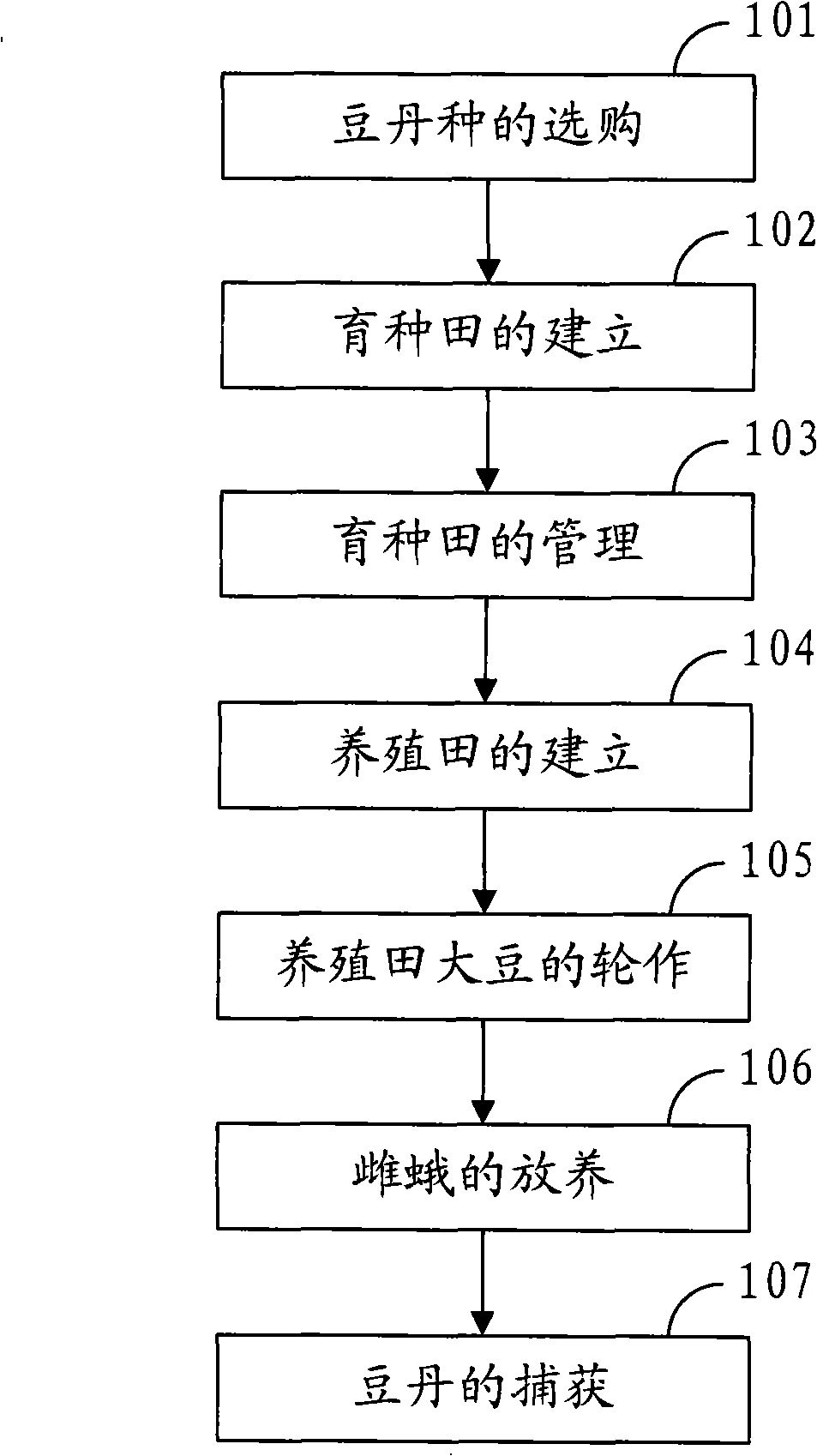
InactiveCN101356905ALong supply cycleImprove yield per muHorticultureAnimal husbandryGreenhouseEconomic benefits
The invention discloses a high-yield greenish brown hawk moth breeding method, which belongs to the technical field of insect breeding and solves the problems of short supply cycle, low per mu yield and low economic benefit of greenish brown hawk moth breeding in the prior art. The high-yield greenish brown hawk moth breeding method comprises the following steps: (1) choosing the greenish brown hawk moth species; (2) establishing a breeding field; (3) managing the breeding field: a greenhouse in the breeding field is divided into three blocks; the first block is used for growing soybeans in the middle ten days of March, the second block is used for growing the soybeans in the middle ten days of April, and the third block is used for growing the soybeans in the first ten days of June; (4) establishing a breeding field; (5) rotation of the soybeans in the breeding field: the breeding field is divided into blocks, the soybeans are planted in batches next year, and the soybean planting way is the same as the management mode of the breeding field; (6) breeding female moths: from the last ten days of April, the greenish brown hawk moth adults fly out successively, and after mating, the female moths are caught and put in the breeding field; (7) catching the greenish brown hawk moth: from the first ten days of May to early October, the greenish brown hawk moths at the right age are caught at regular intervals.
Owner:吴胜军 +2
Catering service system and method based on Internet platform
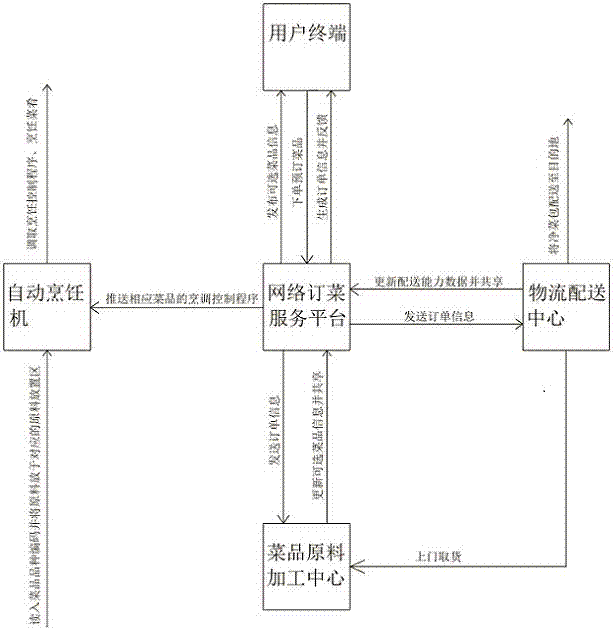
ActiveCN107133850AEnsure safetyAvoid wasteful situationsBuying/selling/leasing transactionsLogisticsLogistics managementUser input
The invention discloses a catering service system and method based on the Internet platform, and relates to the field of the application of the computer and Internet technology. The system comprises a dish raw material processing center, a network dish ordering service platform, a logistics delivery center, a user terminal, and an automatic cooking machine. The network dish ordering service platform is used for issuing the information of selectable dishes, receiving the order-placing information, generating the order information and transmitting the order information to the dish raw material processing center, the logistics delivery center and the user terminal, carrying out the call of a corresponding cooking control program and providing the cooking control program for the automatic cooking machine. The dish raw material processing center is used for receiving the order information, and processing dish raw materials into clean dish packages with the marks. The logistics delivery center is used for delivering the clean dish packages to a destination according to the order information. The user terminal is used by a user for inputting the order-placing information and receiving the feedback order information. The automatic cooking machine is used for reading the marks of the clean dish packages, receiving the control of the cooking control program and completing the cooking of the corresponding dish for the user.
Owner:谢志强 +1
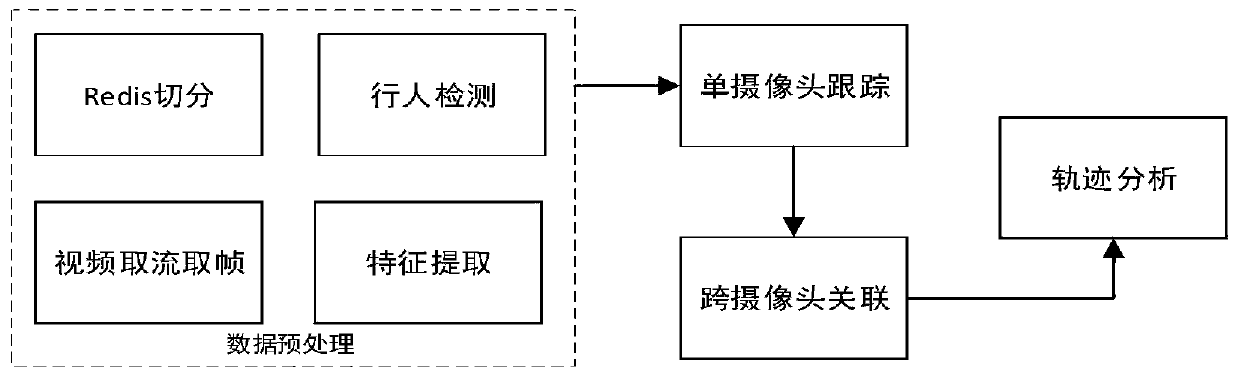
A pedestrian behavior identification and trajectory tracking method
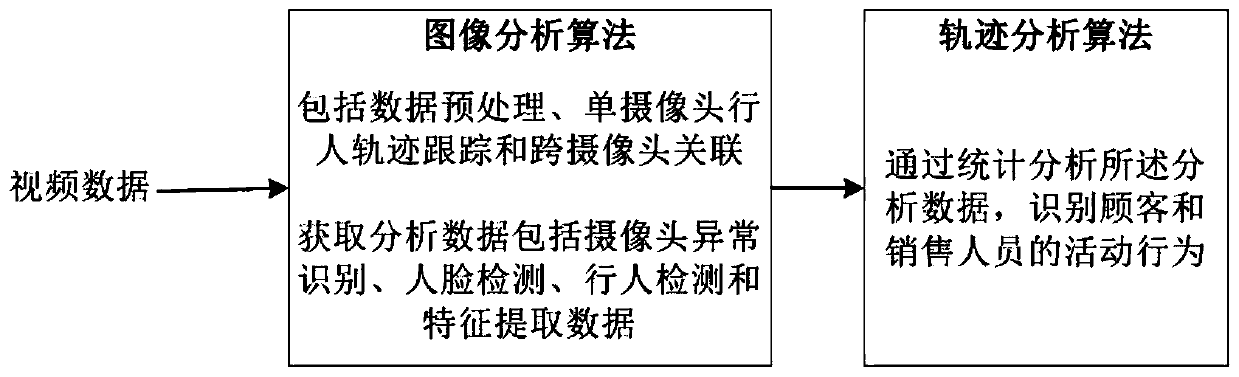
ActiveCN109784162AImplement trackingIntelligent judgment of behavior statusCharacter and pattern recognitionMarketingFace detectionFeature extraction
The invention discloses a pedestrian behavior recognition and trajectory tracking method, which comprises an image analysis algorithm and a trajectory analysis algorithm. collected video data sequentially passes through an image analysis algorithm module and a trajectory analysis algorithm module; The image analysis algorithm comprises the steps of data preprocessing, single-camera pedestrian trajectory tracking and cross-camera association, and camera abnormity recognition, and can achieve face detection, pedestrian detection and feature extraction; And a trajectory analysis algorithm includes calculating and analyzing trajectory data of the pedestrian from the acquired image, and identifying activity behaviors of the customer and the sales. The pedestrian behavior track can be monitoredand recognized in real time, the behavior state of pedestrians is intelligently judged, centralized management of the behavior track of customers and sales is facilitated, and more optimized and moreintelligent services are provided for the customers.
Owner:CHENGDU UNION BIG DATA TECH CO LTD
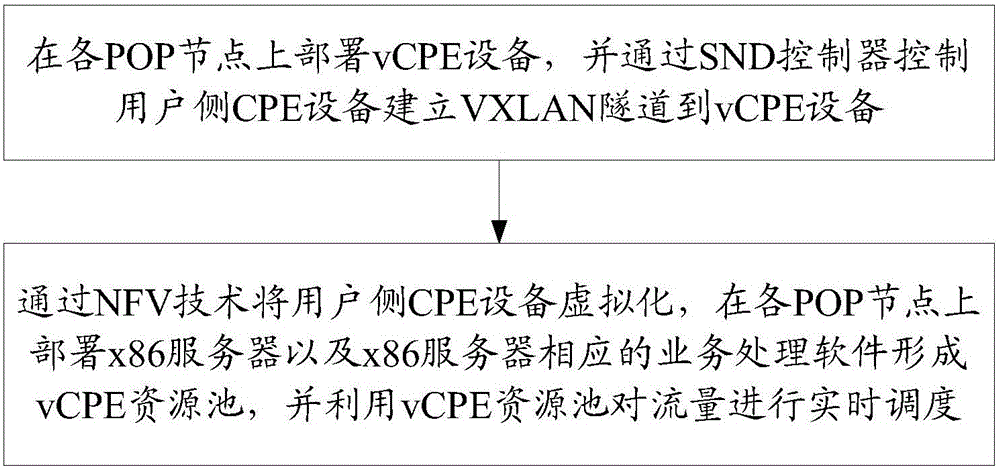
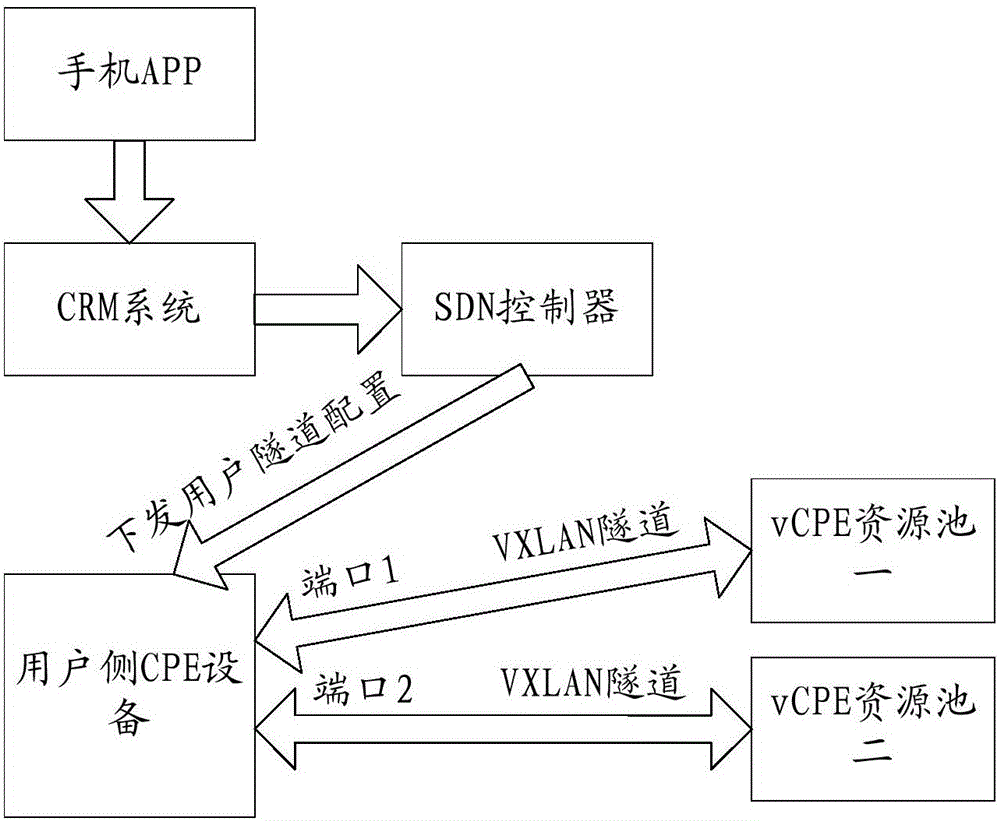
Individual line user smart access method
ActiveCN106130850AIntelligent Scheduling SeparationEasy to manage centrallyNetworks interconnectionTraffic capacityVirtualization
The invention provides an individual line user smart access method. The method comprises the steps of 1, deploying vCPE devices on various POP nodes, and controlling to establish VXLAN tunnels from user side CPE devices to vCPE devices through an SND controller; and 2, virtualizing the user side CPE devices through an NFV technology, deploying x86 servers and service processing software corresponding to the x86 servers on the POP nodes, thereby forming vCPE resource pools, and carrying out real-time scheduling on traffic by employing the vCPE resource pools. The method has the advantages that the VXLAN tunnels are established between the user side CPE devices and the vCPE devices through a VXLAN tunnel technology, smart scheduling separation can be carried out on the user traffic, and the individual service business of the user traffic can be customized.
Owner:中电福富信息科技有限公司
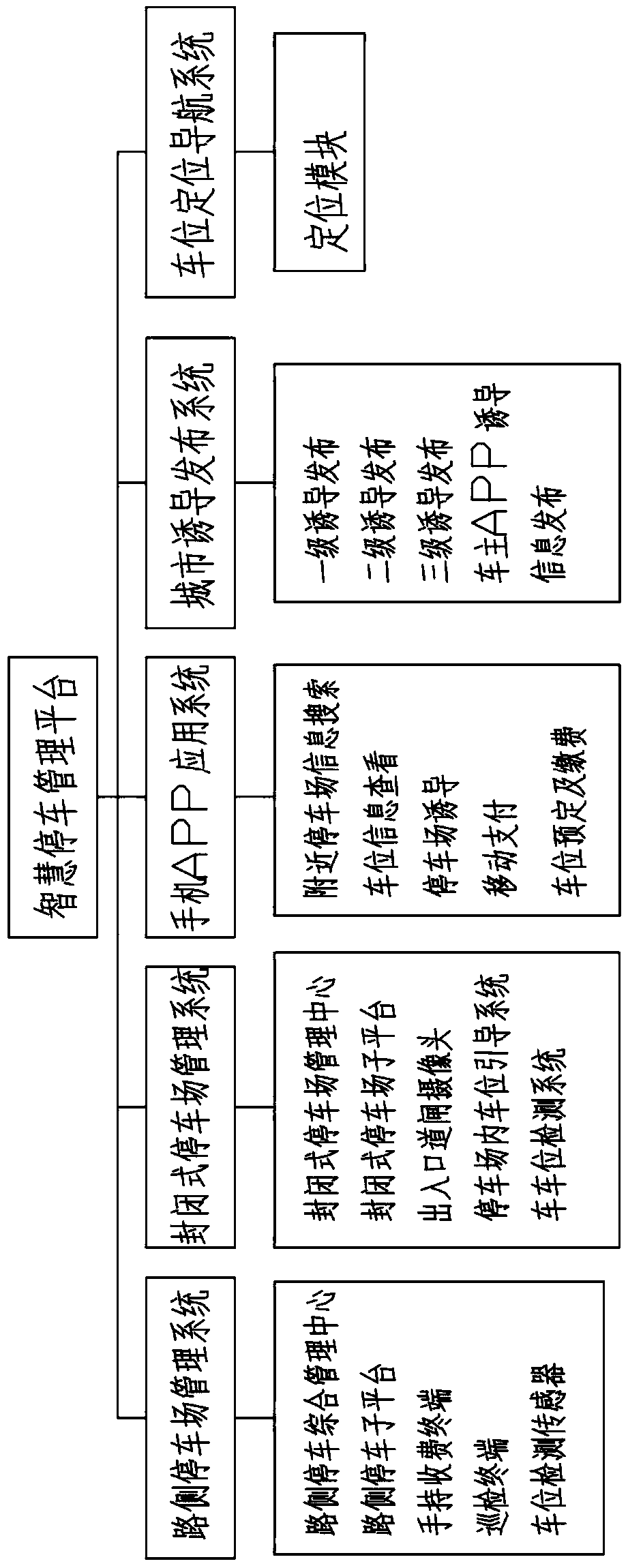
Urban smart parking management system and method based on SAAS mode
InactiveCN109559391AIncrease profitEase the difficulty of finding a parking spaceTicket-issuing apparatusReservationsMobile appsThe Internet
Provided in the invention is an urban smart parking management system based on an SAAS mode. The system comprises a smart parking management platform built on a cloud computing server, a roadside parking management system i, an enclosed parking lot management system and an Internet Mobile APP application system, wherein the roadside parking management system, the enclosed parking lot management system and the Internet Mobile APP application system are in communication connection with the smart parking management platform. The Internet Mobile APP application system is used for developing a vehicle owner mobile phone APP based on an Internet mobile terminal and realizing GIS-map-based near parking lot information searching, parking space information checking, parking lot induction, mobile payment, parking space reservation and payment based on the Internet technology. According to the invention, the parking management system is combined with the static induction and dynamic induction functions in the urban smart parking management system closely and has advantages of high practicability, high intelligence and flexible charging, so that the parking order is managed well, the utilization rate of limited parking spaces is increased effectively, and problems of difficult parking space finding, difficult parking, and difficult charging in city are solved.
Owner:连云港杰瑞电子有限公司
Method and system for column control temporary speed limit
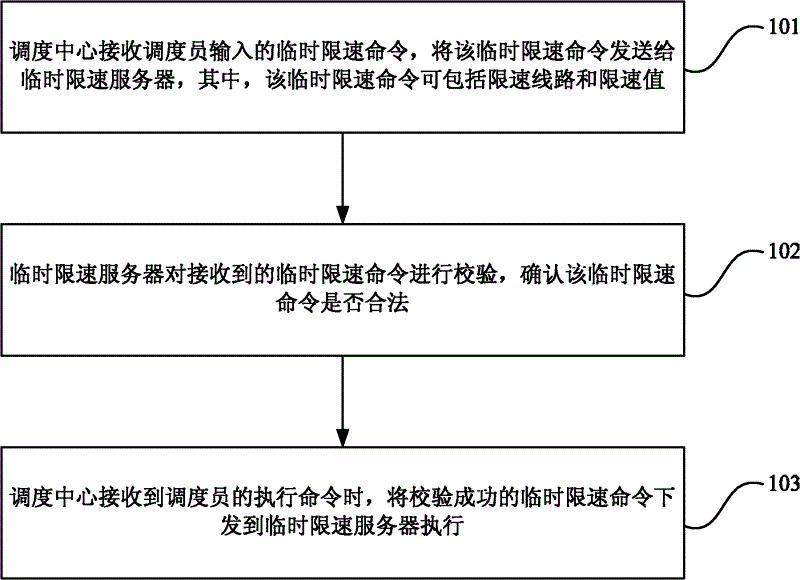
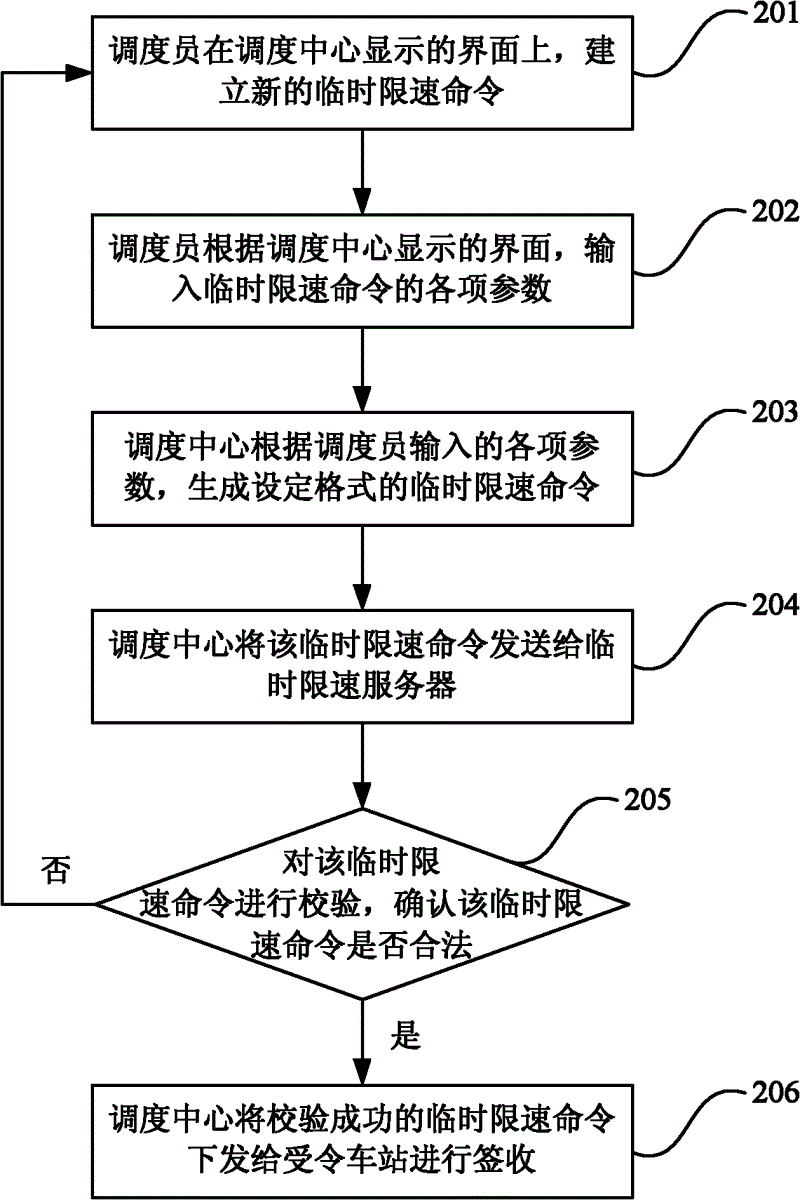
InactiveCN102616259AEasy to manage centrallyGuaranteed accuracyAutomatic systemsSimulationControl theory
The invention discloses a method and a system for column control temporary speed limit. The method includes the following steps: a dispatching center receives a temporary speed limit command input by a dispatcher and sends the temporary speed limit command to a temporary speed limit server, wherein the temporary speed limit command comprises a speed limit line, a speed limit value and a speed limit range; the temporary speed limit server verifies the received temporary speed limit command and confirms whether the temporary speed limit command is legal or not; the dispatching center receives an executive command of the dispatcher and sends the temporary speed limit command verified to be legal to the temporary speed limit server to be executed. According to the technical scheme, the column control temporary speed limit command can be issued, and accuracy and reliability of issuance of the temporary speed limit command are improved.
Owner:CHINA RAILWAYS CORPORATION +1
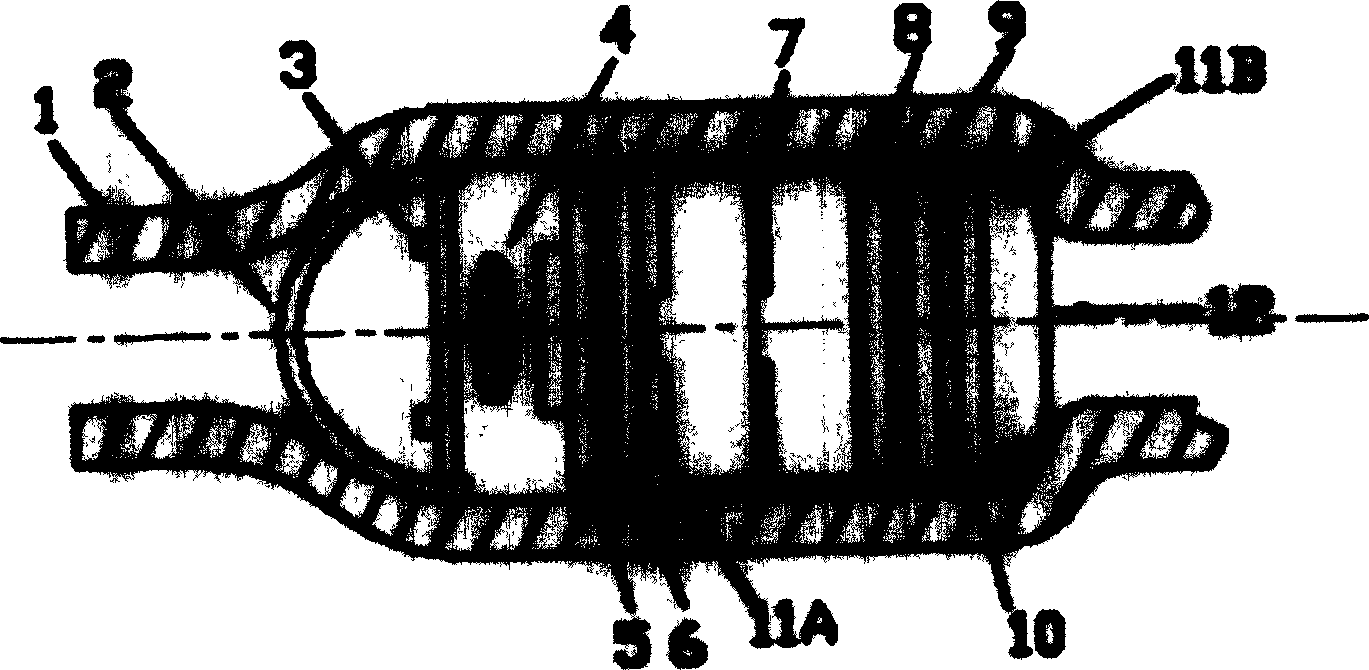
Duplex multipath intelligent capsule wireless endoscope system
The duplex multichannel intelligent capsule wireless endoscope system includes intelligent capsule endoscope for digestive tract, and image recording and intelligent capsule controlling instrument. The present invention features the image recording and intelligent capsule controlling instrument with microprocessor connected to control keyboard and display screen or connected to PDA via RS232 or USB interface, radio transceiving module communicating with RF transceiving module in the intelligent capsule endoscope in duplex multichannel mode. The system can realize in-situ real-time image observation and real-time on the capsule endoscope and can operate in complicated environment without interference. Therefore, several systems may operate simultaneously to reduce the amount of the intelligent capsule workstations for flexible use; and stereo image may be realized to raise the disease focus detecting rate.
Owner:CHONGQING JINSHAN SCI & TECH GRP
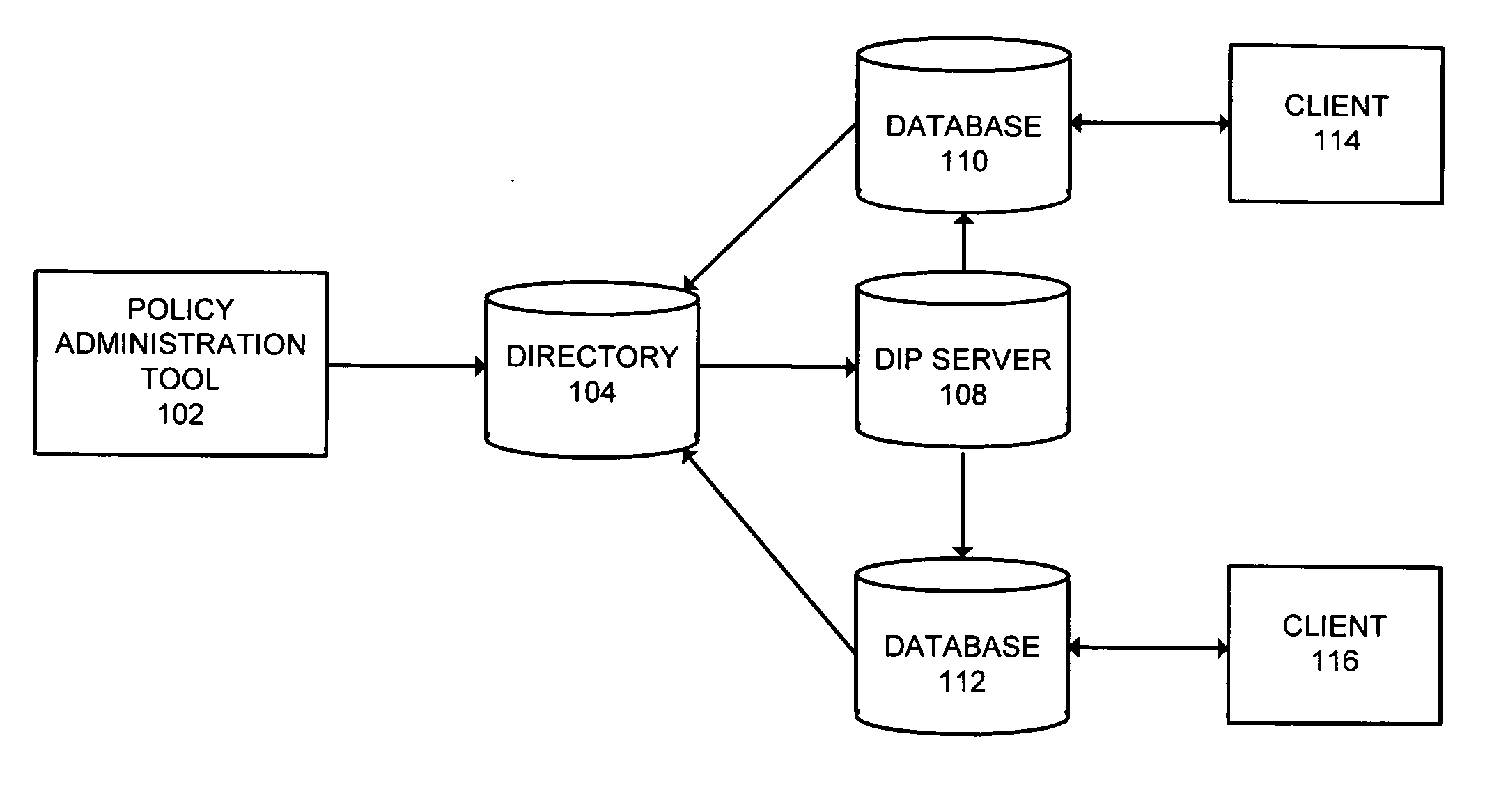
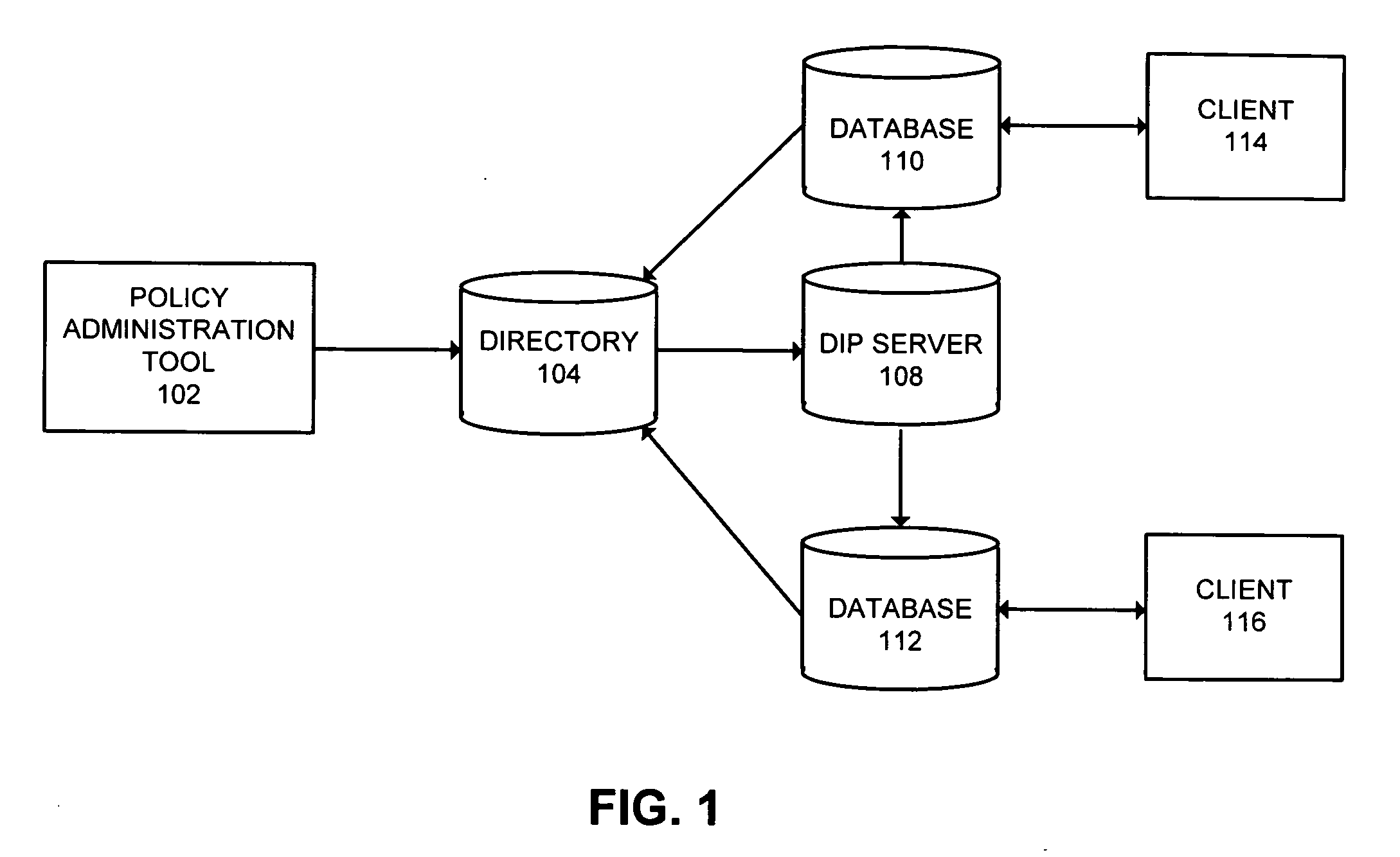
Method and system for managing security policies for databases in a distributed system
ActiveUS20060085837A1Facilitates managing security policyEasy to manageDigital data processing detailsComputer security arrangementsCentralized managementSecurity policy
One embodiment of the present invention provides a system that facilitates managing security policies for databases in a distributed system. During operation, the system creates multiple label security policies. The system stores these security policies in a directory and automatically propagates them from the directory to each database within the distributed system. In doing so, the system allows for applying policies to individual tables and schema in any database in the distributed system. The system facilitates centralized administration of security policies and removes the need for replicating policies, since the policy information is available in the directory.
Owner:ORACLE INT CORP
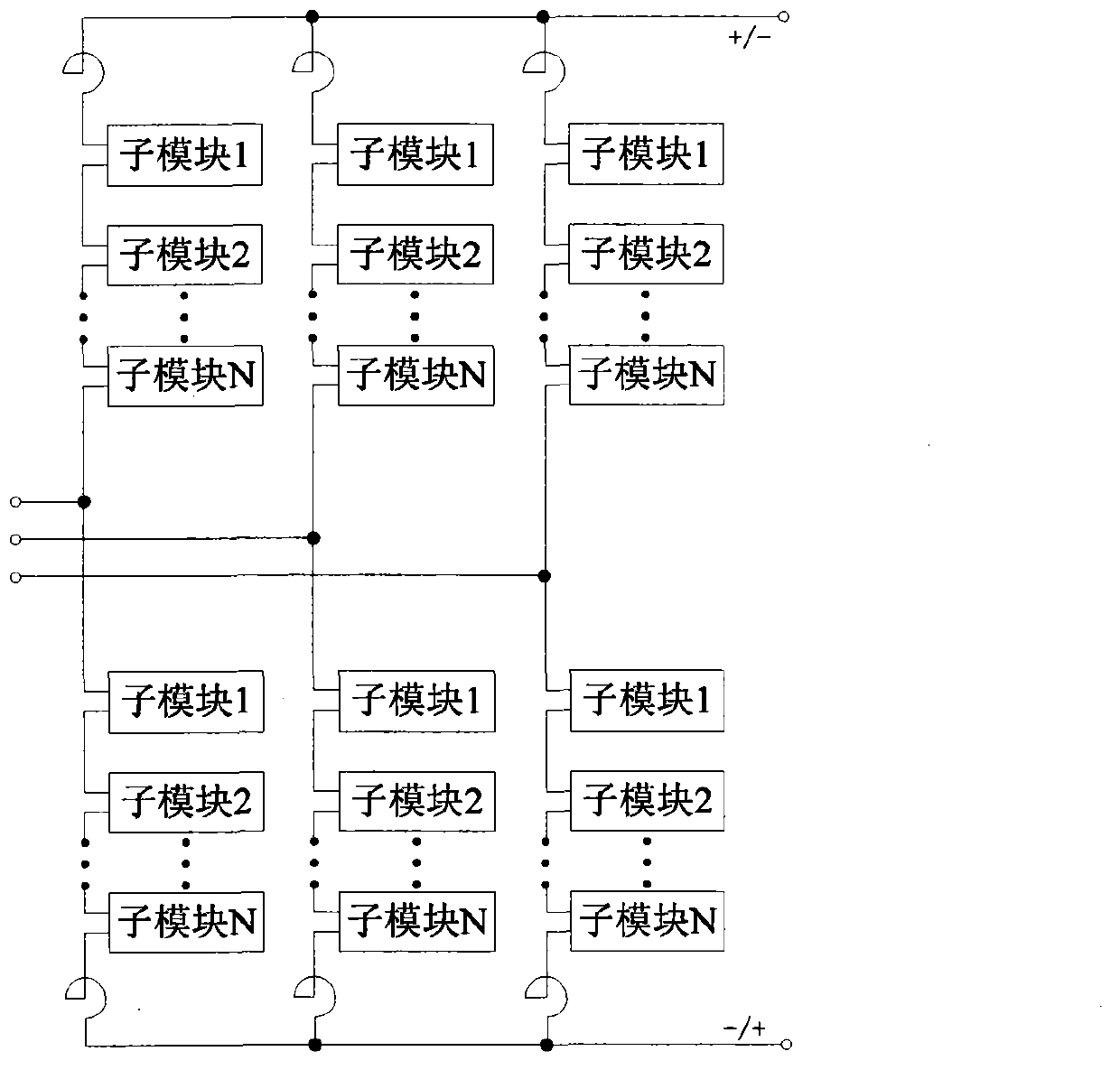
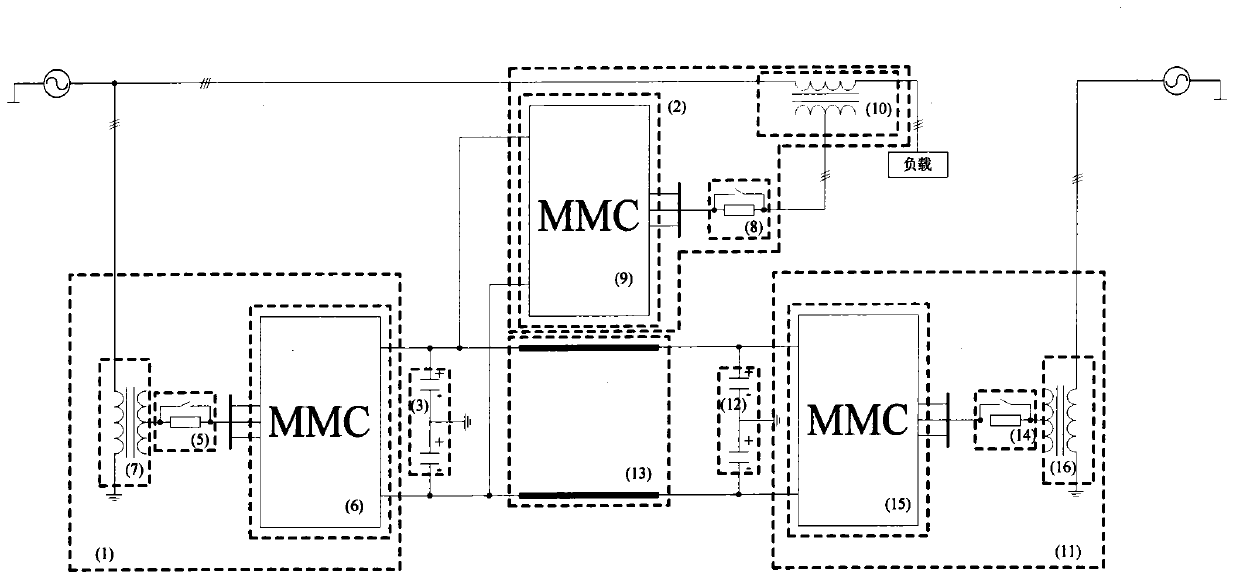
HVDC (high voltage direct current controller) and UPFC (unified power flow controller) system based on modularized multi-level converter
ActiveCN103001242AIncrease device capacitySave engineering construction cost and investmentAc-dc conversionElectric power transfer ac networkTransmission lineEngineering
The invention provides an HVDC (high voltage direct current controller) and UPFC (unified power flow controller) system based on a modularized multi-level converter. The HVDC and UPFC system comprises converting devices (1, 2 and 11), grounding circuits (3 and 12) and a direct current transmission line (13). The UPFC is formed by the converting device (1) and the converting device (2). The HVDC is formed by the converting device (1) and converting device (11). The HVDC and the UPFC shares one converting device, so that cost and investment for engineering construction are saved, equipment utilization rate is improved, concentrated management and control are facilitated. The converting devices use the topological structure of the modularized multi-level converter, so that technical difficulty in component serial connection is avoided, split-phase control and modularization are facilitated, fault units can be bypassed through redundancy, operation stability of the devices is improved, on and off frequency of components is low, and device operation loss is low.
Owner:CHINA EPRI SCIENCE & TECHNOLOGY CO LTD +2
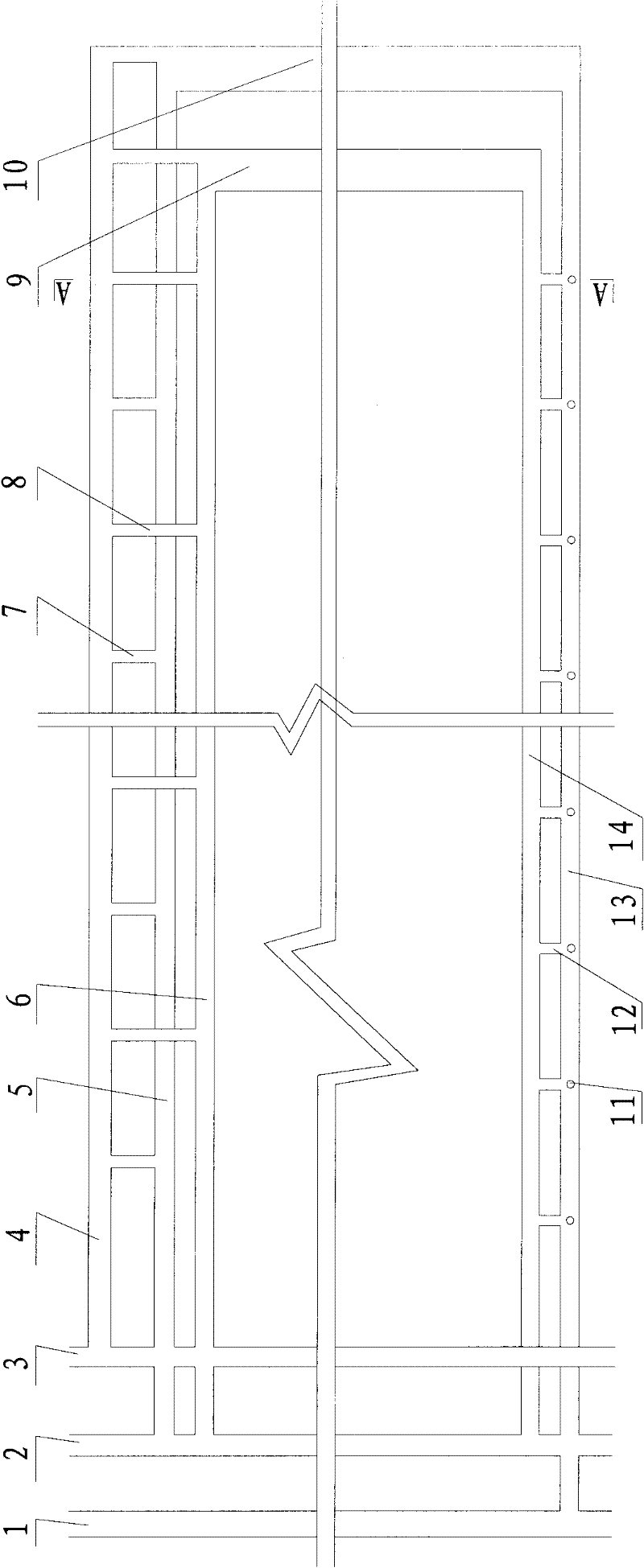
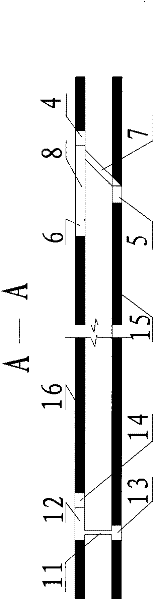
Close-range thin coal layer simultaneous mining and parallel transporting method
InactiveCN102392640AReduce the amount of excavation workIncrease productionUnderground miningSlitting machinesCentralized managementCoal
The invention discloses a close-range thin coal layer simultaneous mining and parallel transporting method, aiming to solve the problems caused by layer mining of the existing close-range thin coal layers, such as resource waste, serious flood, difficult mining distribution of lower layer coal, long mining period, low yield, high tunneling and supporting difficulties, high cost and the like. The method is characterized by arranging a centralized transport roadway, a centralized track roadway and a centralized air return roadway along the coal layers or top and bottom plates of the coal layers, simultaneously arranging two coal faces on the close-range thin coal layers and simultaneously mining and transporting coal. The method has the following beneficial effects: simultaneous mining and centralized transporting of the upper and lower coal layers are realized; relative to layer mining, by adopting the method, the tunneling quantities of the roadways are reduced, a belt conveyer can be simultaneously omitted, and the convenience is provided for centralized management of production; and especially for the close-range thin coal layers, the production system is simplified, the convenience is provided for centralized management, the production cost is lowered, and the mine output and the production efficiency are improved.
Owner:SHANXI LUAN ENVIRONMENTAL ENERGY DEV +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com