Security protection method of smart home security gateway
A smart home and security gateway technology, applied in network connections, electrical components, transmission systems, etc., can solve problems such as insecure routing, lack of Mirai virus and its variant defense and prevention, lack of protection against smart home protocol attacks, etc. The effect of protecting network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The specific implementation of the present invention will be further described below in conjunction with accompanying drawings and examples, but the implementation and protection of the present invention are not limited thereto. Achieved with technology.
[0053] A security protection method for a smart home security gateway in this example is mainly composed of four steps, the steps are as follows:
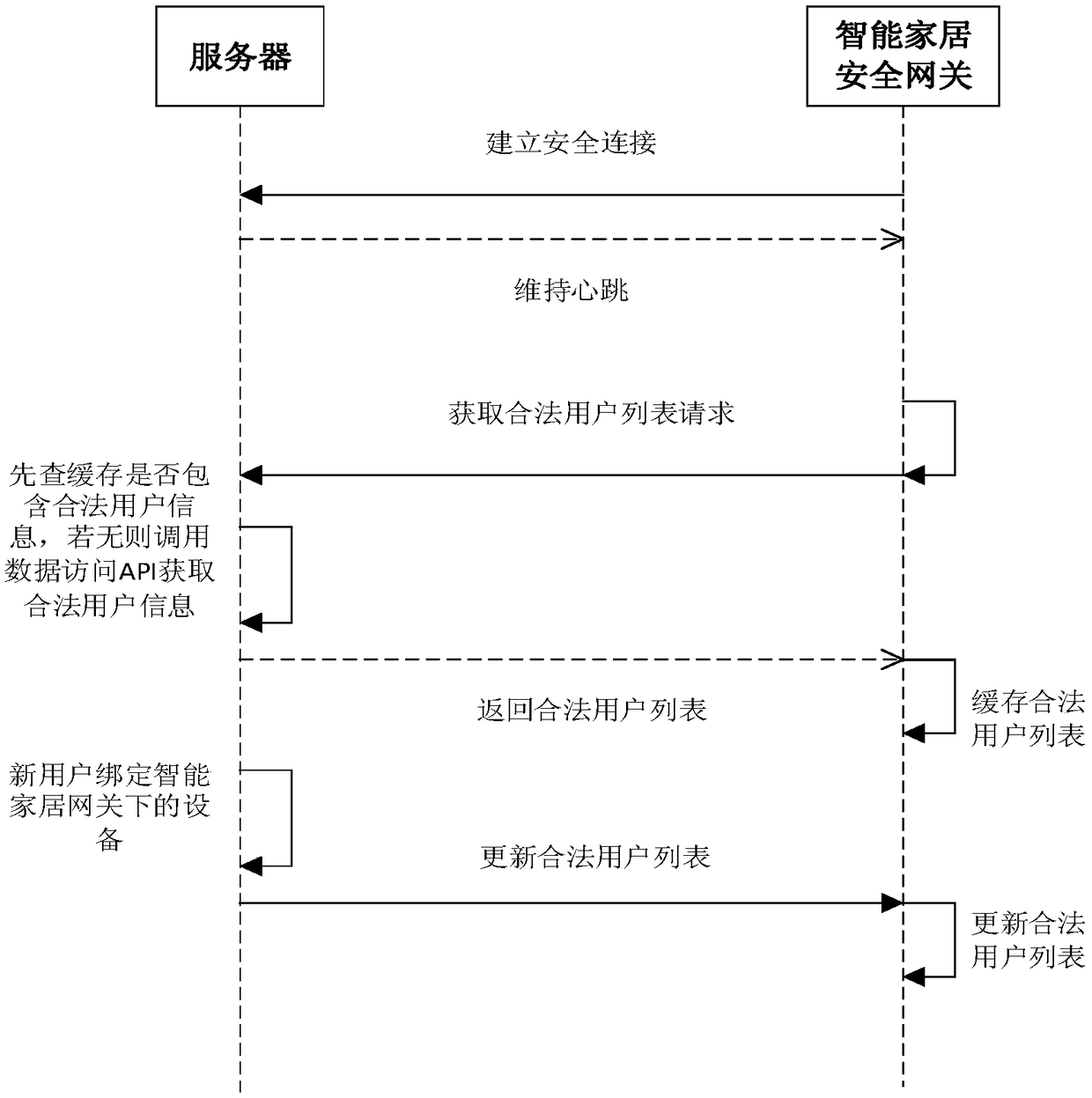
[0054] Step 1: Power on the smart home gateway, start the dual network card according to the configuration file, and establish a secure connection with the server;
[0055] Step 2: The gateway obtains the legal user list from the server and caches it. The specific process is as follows figure 1 shown;
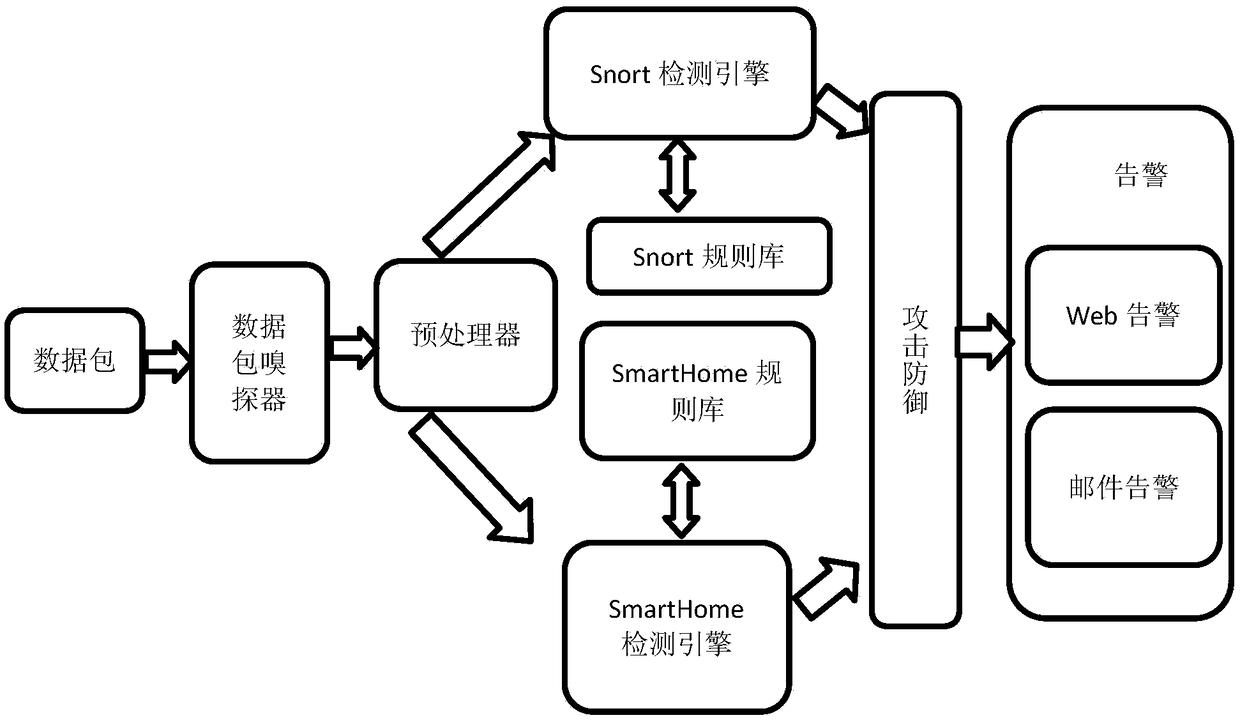
[0056] Step 3: Start the snort-wireless wireless network attack detection function according to the configuration;
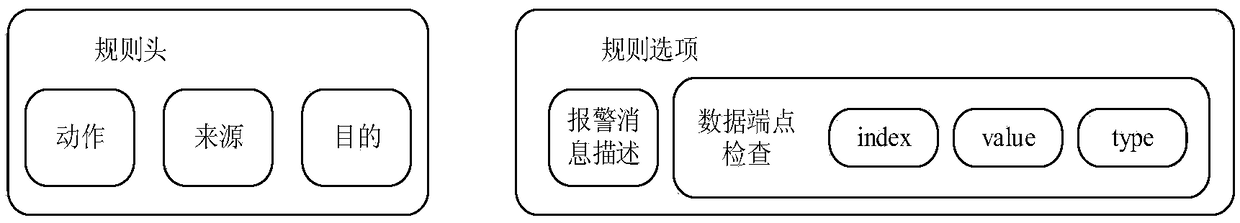
[0057] Step 4: Start the smart home protocol attack detection system. Specifically include:
[0058] a) Extract the attack features of the smart home pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com