Method and device for defending denial of service attack
A denial of service attack, server technology, applied in the field of communication, can solve the problems of low defense accuracy, difficult TCP/IP protocol stack, accidental injury, etc., to achieve the effect of effective defense
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
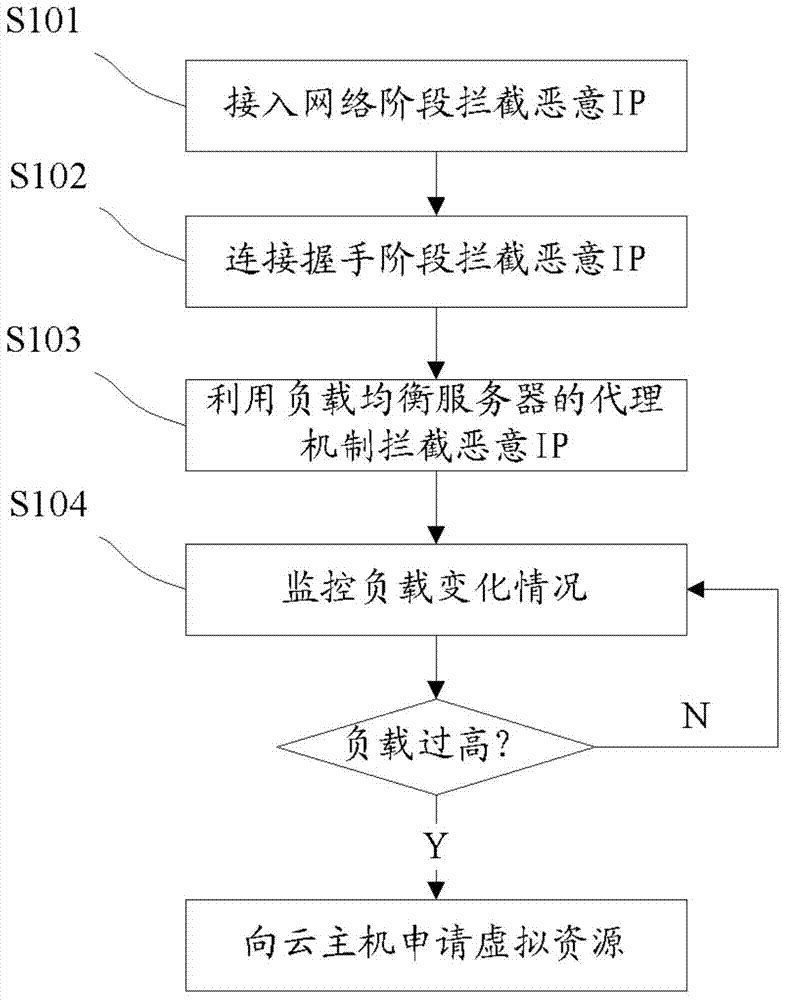
[0028] In order to make the technical solutions and advantages of the present invention clearer, the exemplary embodiments of the present invention will be described in further detail below in conjunction with the accompanying drawings. Obviously, the described embodiments are only a part of the embodiments of the present invention, rather than all implementations. Exhaustive list of examples.
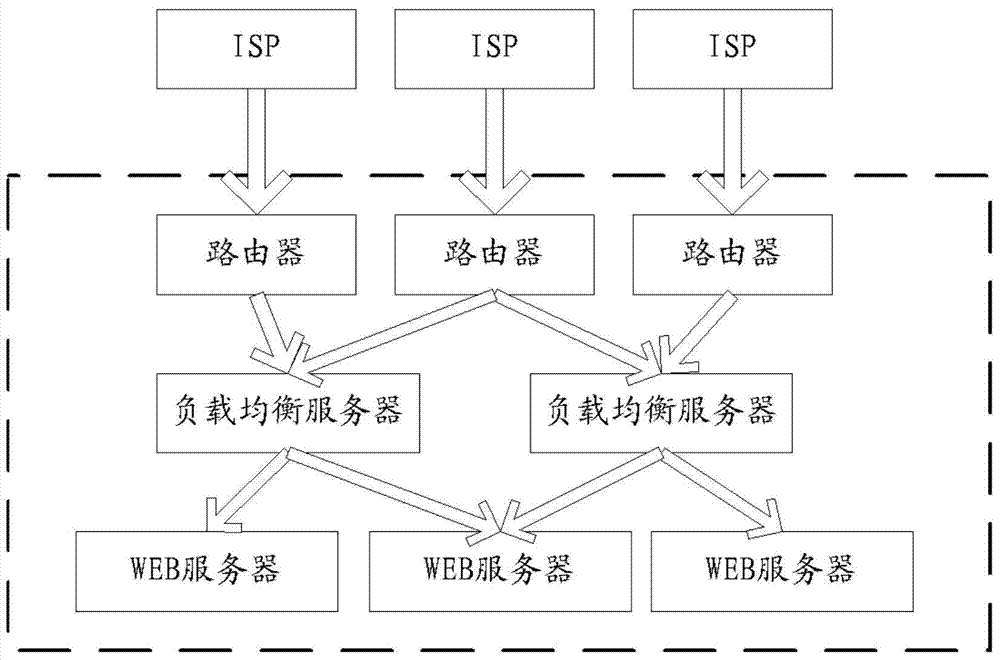
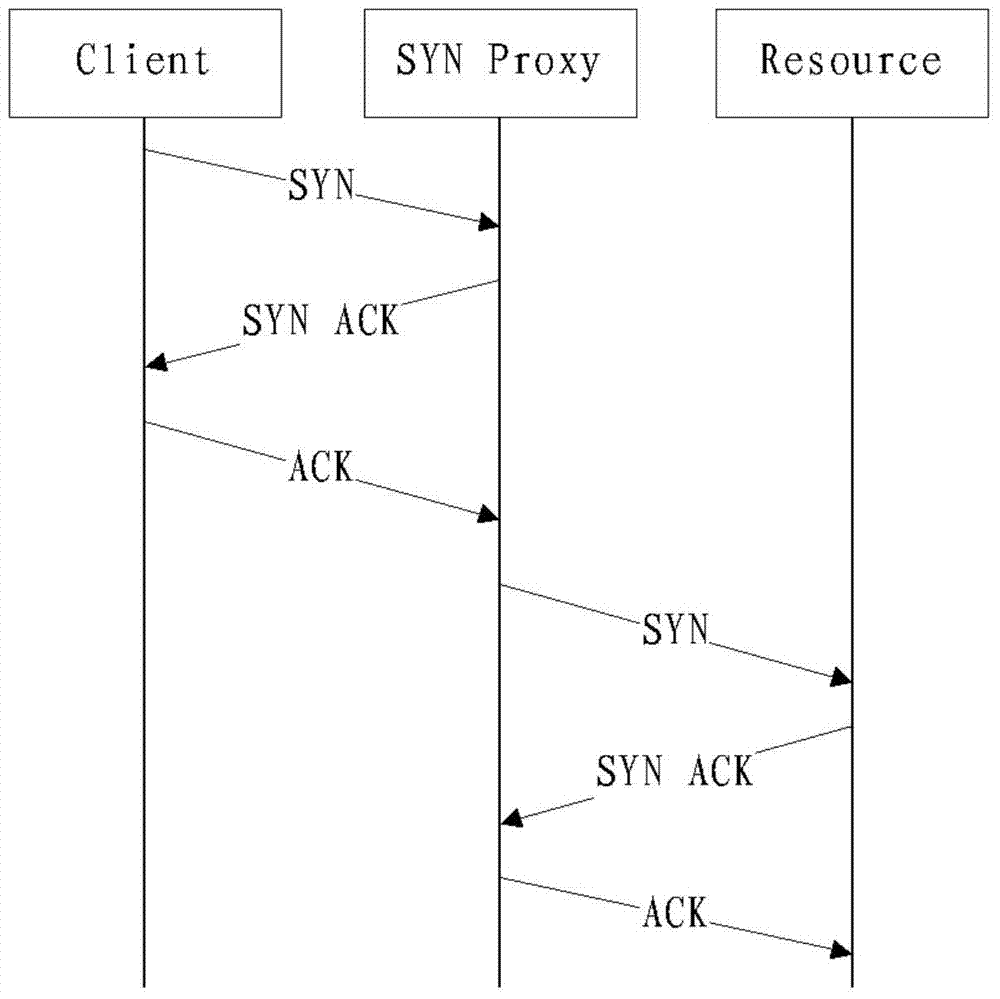
[0029] The present invention sets reasonable strategies to prevent malicious users from accessing from the network access, and uses the agent program in load balancing to achieve further defense, and web resources can be adaptively adjusted in the face of attacks under the load balancing mechanism, Realize effective defense against malicious attacks. The so-called load balancing refers to the use of load balancing strategies to expand the bandwidth of network equipment and servers, increase throughput, strengthen network data processing capabilities, and improve network flexibility and av...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com