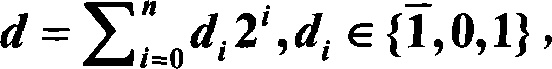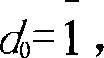Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
467 results about "Side channel attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer security, a side-channel attack is any attack based on information gained from the implementation of a computer system, rather than weaknesses in the implemented algorithm itself (e.g. cryptanalysis and software bugs). Timing information, power consumption, electromagnetic leaks or even sound can provide an extra source of information, which can be exploited.
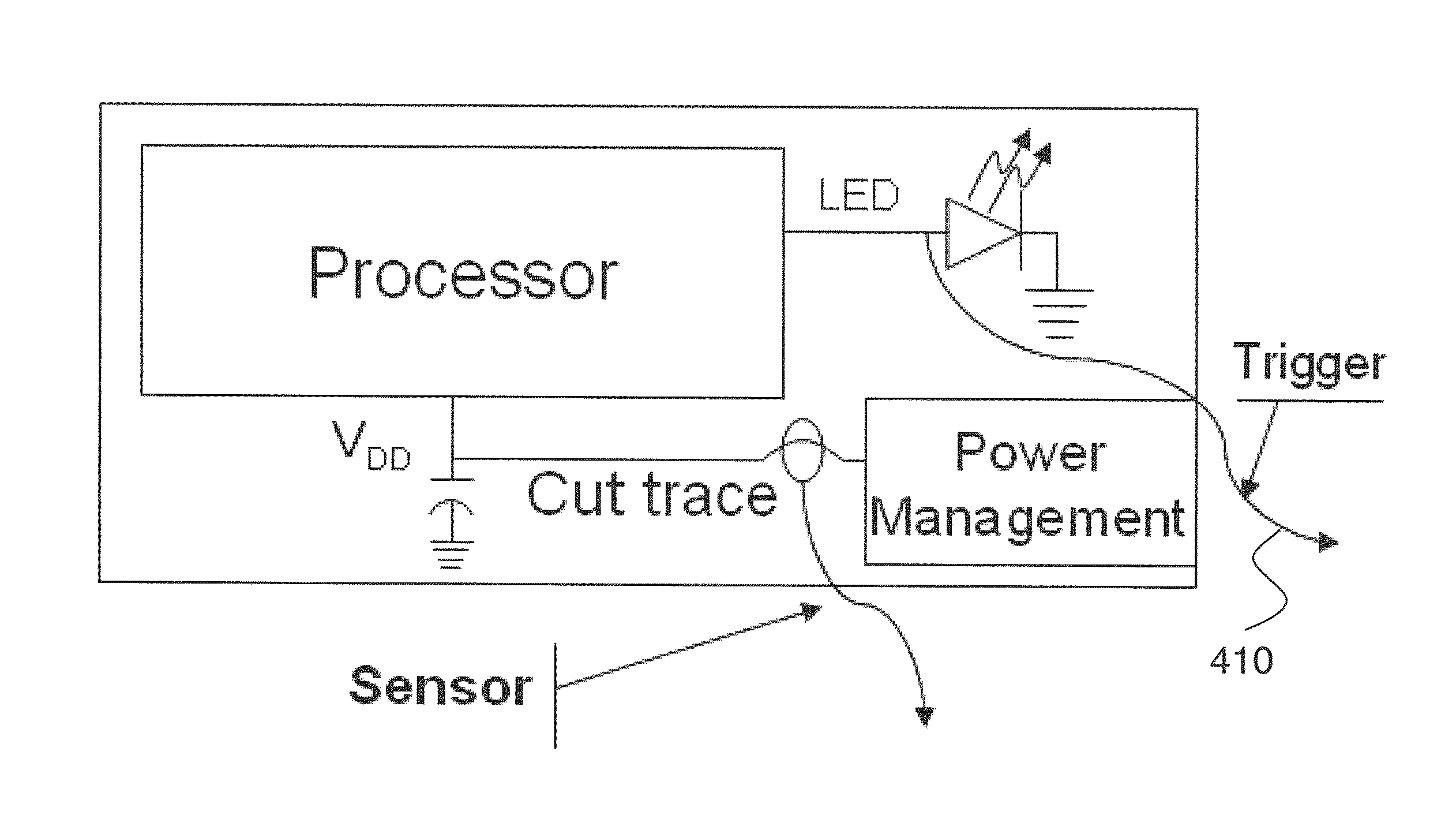
Using Power Fingerprinting (PFP) to Monitor the Integrity and Enhance Security of Computer Based Systems
ActiveUS20130318607A1Enhancing target system execution integrity assessmentImprove abilitiesMemory loss protectionDetecting faulty computer hardwareIntegrity assessmentComputerized system
Procedures are described for enhancing target system execution integrity determined by power fingerprinting (PFP): by integrating PFP into the detection phase of comprehensive defense-in-depth security; by deploying a network of PFP enabled nodes executing untrusted devices with predefined inputs forcing a specific state sequence and specific software execution; by embedding module identification information into synchronization signaling; by combining signals from different board elements; by using malware signatures to enhance PFP performance; by automatic characterization and signature extraction; by providing secure signature updates; by protecting against side-channel attacks; performing real-time integrity assessment in embedded platform by monitoring their dynamic power consumption and comparing it against signatures from trusted code, including pre-characterizing power consumption of the platform by concentrating on trace sections carrying the most information about the internal execution status; by using PFP from sequence of bit transitions to detect deviations from authorized execution of software in a digital processor.
Owner:VIRGINIA TECH INTPROP INC
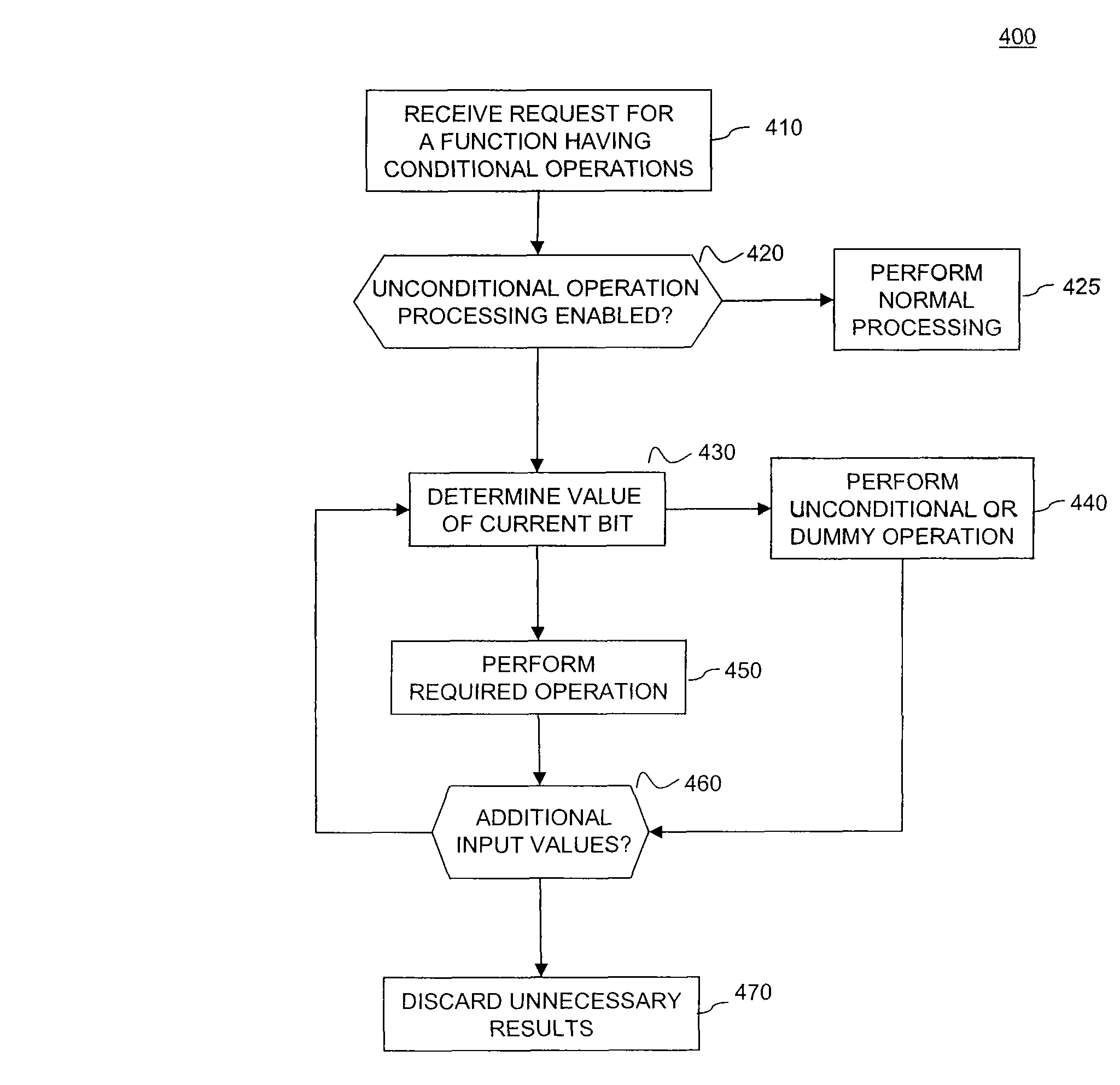
System and Methods for Side-Channel Attack Prevention
InactiveUS20090010424A1Internal/peripheral component protectionSecret communicationProcessor registerCryptosystem
A side channel attack utilizes information gained from the physical implementation of a cryptosystem. Software and hardware-based systems and methods for preventing side channel attacks are presented. Cryptographic hardware may introduce dummy operations to compensate for conditional math operations in certain functions such as modular exponentiation. Cryptographic hardware may also introduce random stalls of the data path to introduce alterations in the power profile for the operation. A cryptographic function may be mapped to a micro code sequence having a plurality of instructions. Firmware in the cryptosystem may alter the micro code sequence by altering the order of instructions, add dummy operations in the micro code sequence, break the micro code sequence into multiple sub micro code sequences and / or change the register location for source and destination operands used in the sequence. These alterations are designed to randomly change the timing and power profile of the requested function.
Owner:AVAGO TECH INT SALES PTE LTD
Prevention of side channel attacks against block cipher implementations and other cryptographic systems
InactiveUS20060045264A1Safe leakageEasy to convertEncryption apparatus with shift registers/memoriesDigital data processing detailsPlaintextSignal-to-noise ratio (imaging)
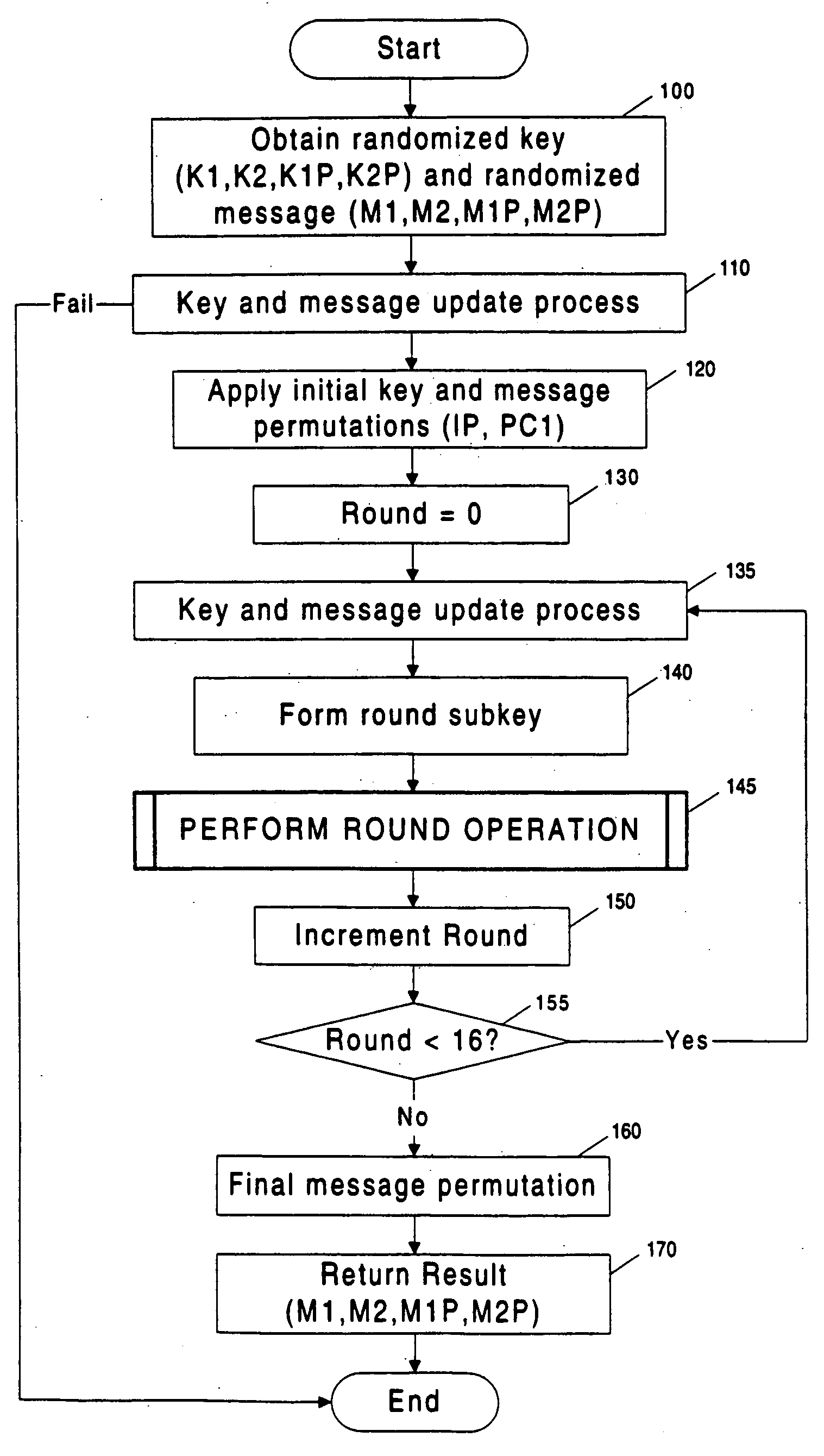
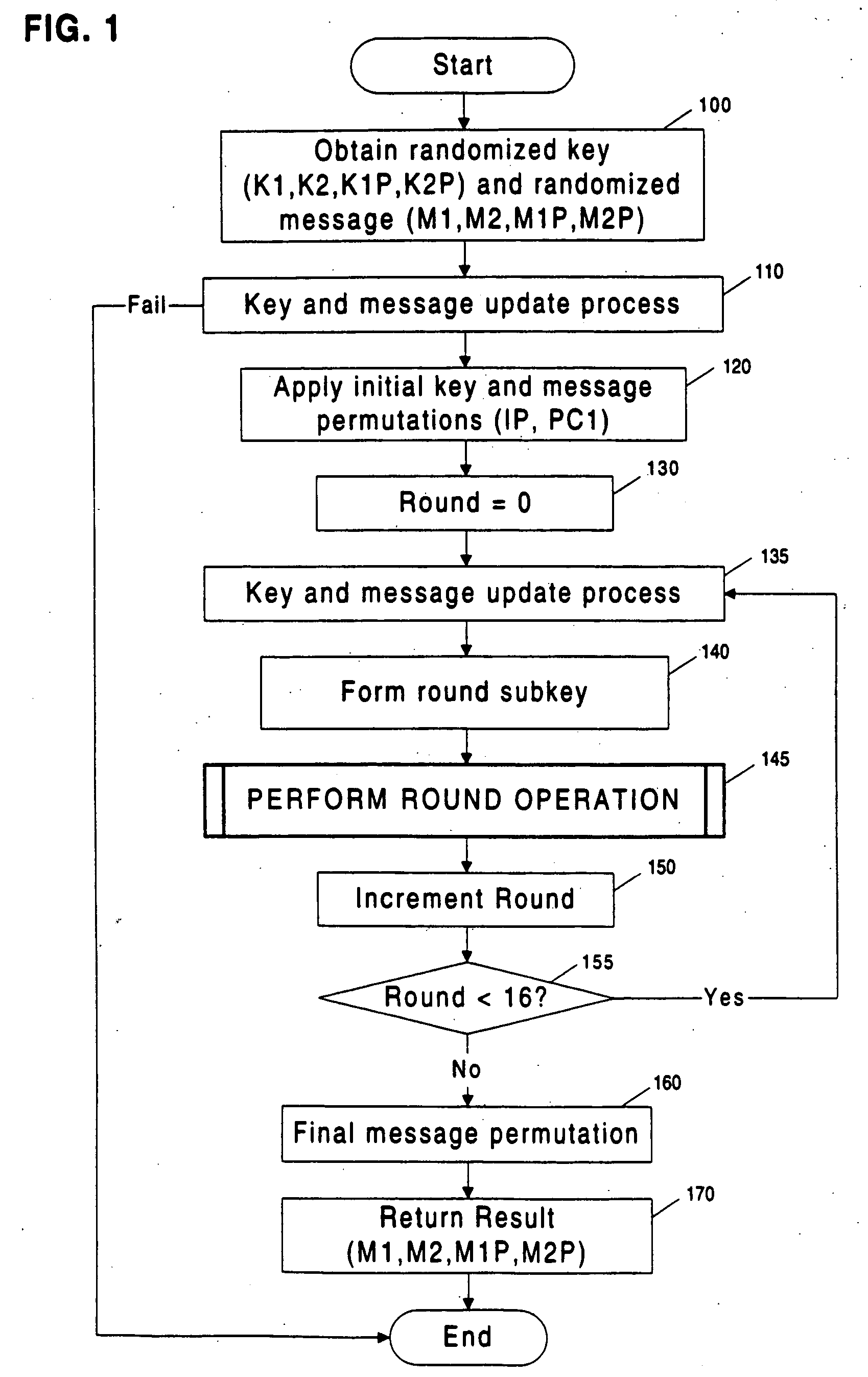
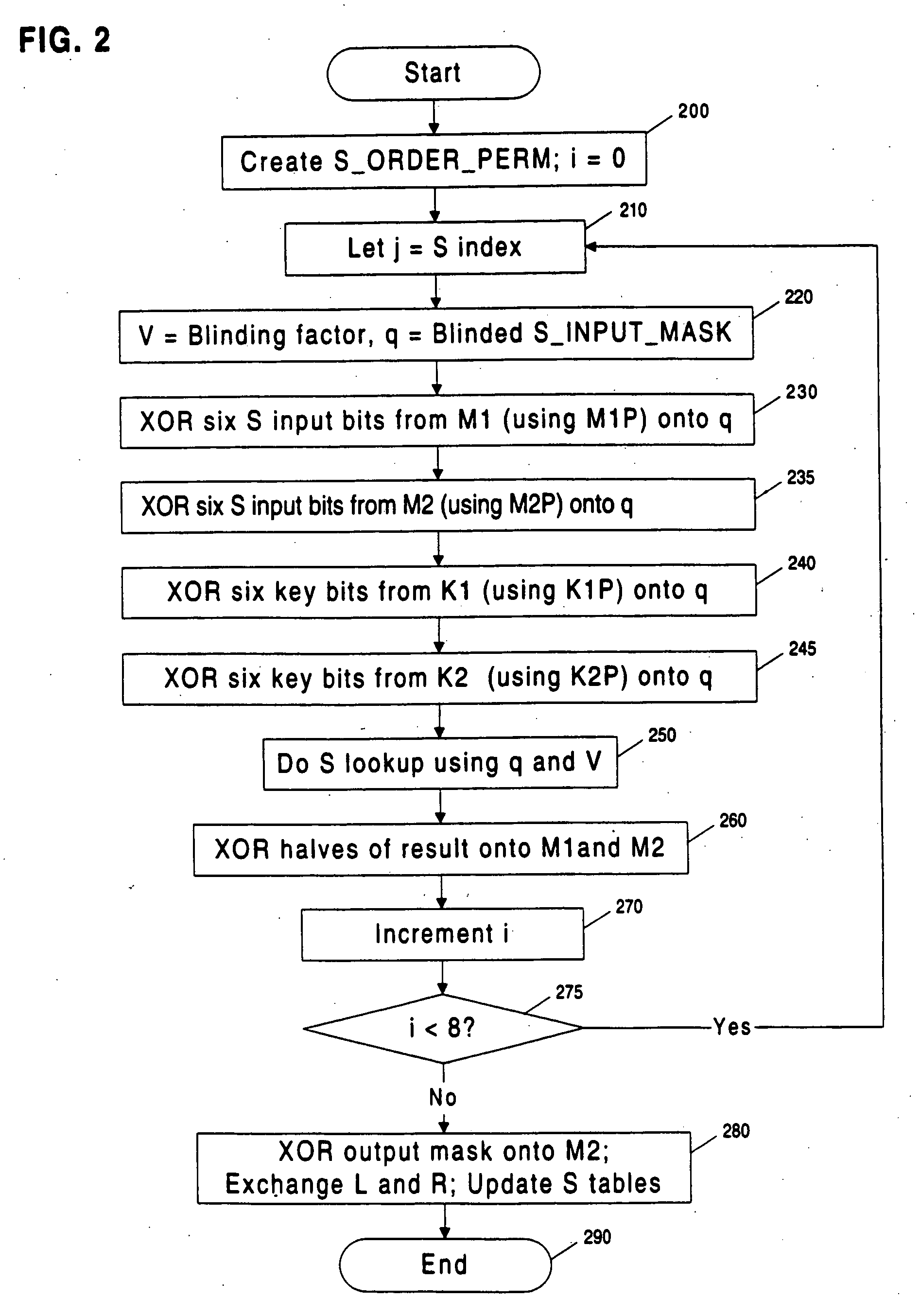
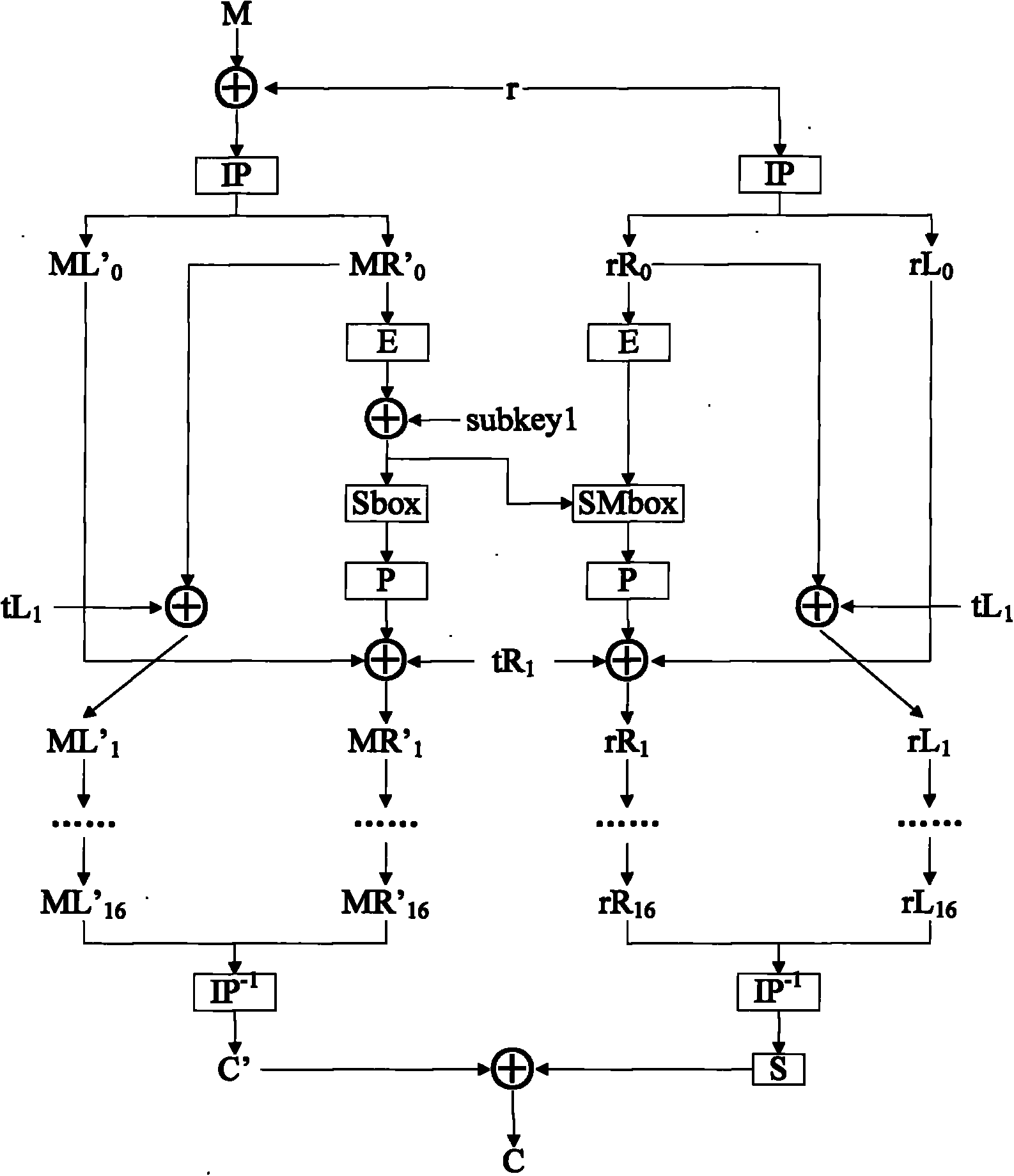
Methods and apparatuses are disclosed for improving DES and other cryptographic protocols against external monitoring attacks by reducing the amount (and signal-to-noise ratio) of useful information leaked during processing. An improved DES implementation of the invention instead uses two 56-bit keys (K1 and K2) and two 64-bit plaintext messages (M1 and M2), each associated with a permutation (i.e., K1P, K2P and M1P, M2P) such that K1P{K1} XOR K2P{K2} equals the “standard” DES key K, and M1P{M1} XOR M2P{M2} equals the “standard” message. During operation of the device, the tables are preferably periodically updated, by introducing fresh entropy into the tables faster than information leaks out, so that attackers will not be able to obtain the table contents by analysis of measurements. The technique is implementable in cryptographic smartcards, tamper resistant chips, and secure processing systems of all kinds.
Owner:CRYPTOGRAPHY RESEARCH
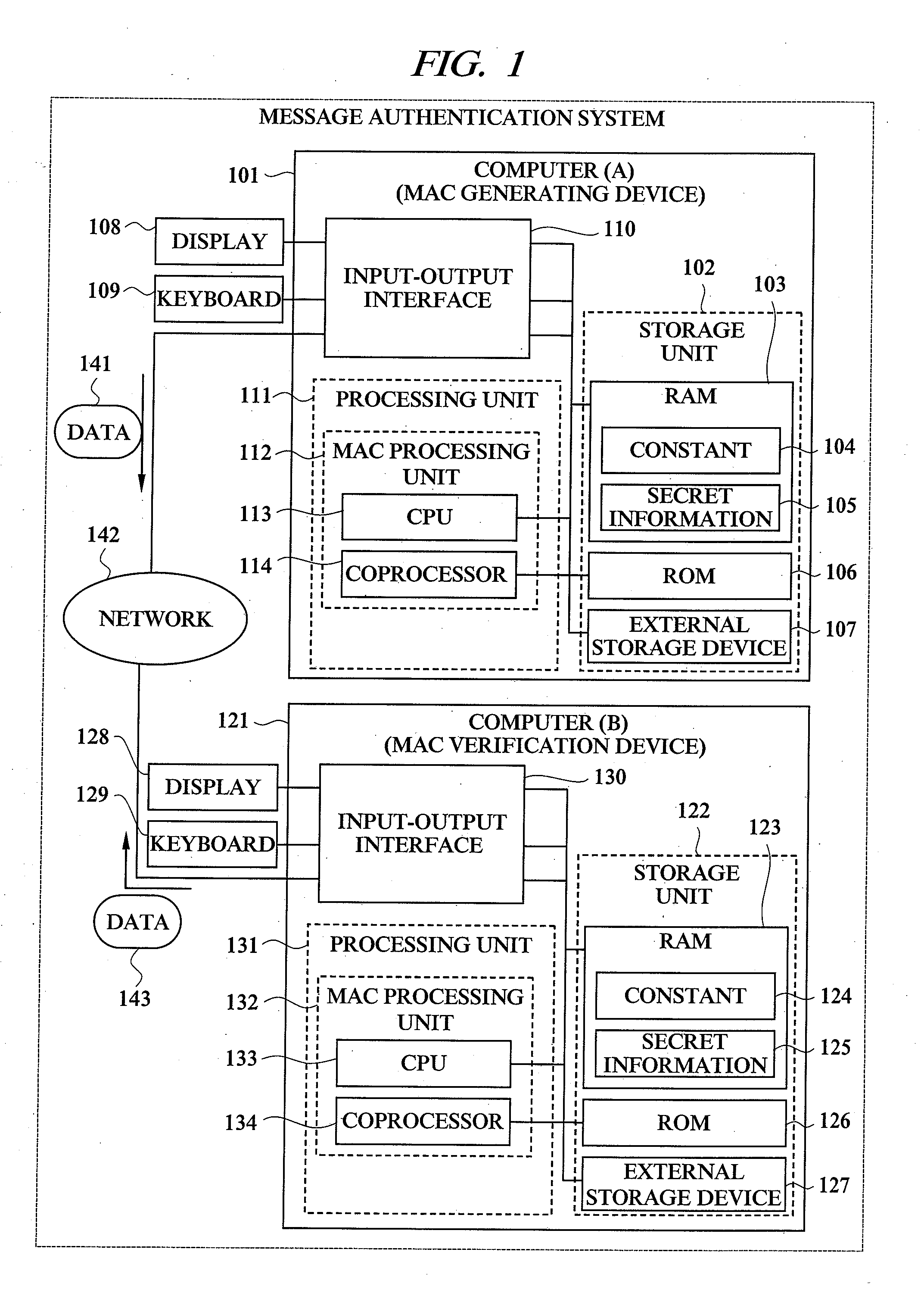
Message authentication code generating device, message authentication code verification device, and message authentication system
InactiveUS20070245147A1User identity/authority verificationMultiple digital computer combinationsComputer hardwareMessage authentication code
A message authentication technology capable of securing against side channel attack is provided. In a message authentication code generating device for calculating a message authentication code for a message from the message, a process in which disturbance information is generated from a temporary use numerical value, a process in which a conversion message is calculated from the message; and a process in which the message authentication code is calculated from the disturbance information and the conversion message are performed. In the process of calculating the message authentication code, process information is disturbed or concealed by the disturbance information. Therefore, the message authentication which is secure against side channel attack can be realized.
Owner:RENESAS ELECTRONICS CORP
Logic system with resistance to side-channel attack by exhibiting a closed clock-data eye diagram
InactiveUS20110285420A1Improve the immunityReduce sensitivityComputer security arrangementsElectric pulse generatorMonitoring systemEngineering
An improvement in the security of a logic system by minimising observable features such as the power supply or electromagnetic radiation, so called, “side-channel attacks”. Specifically, the present invention comprises a technique and methods for reducing the ability of an intruder to monitor the relationship between currents in the system and the data in the system through the use of a randomised clock wherein the clock eye diagram is closed and without significant reduction in maximum operating speed compared to the reduction in maximum operating frequency that occurs when using conventional means of additive jitter. A system where the clock eye diagram is completely closed is provably more secure than systems where the clock eye diagram is partially open.
Owner:DEAS ALEXANDER ROGER +1
Elliptic curve cryptosystem apparatus, elliptic curve cryptosystem method, elliptic curve cryptosystem program and computer readable recording medium storing the elliptic curve cryptosystem program
InactiveUS20060093137A1Increase speedProvide securityPublic key for secure communicationUnauthorized memory use protectionSoftware engineeringMechanical engineering
An elliptic curve cryptosystem apparatus performing an elliptic curve cryptosystem process has a coordinate transforming unit for transforming coordinates (X:Y:Z) on a point P on an elliptic curve over a finite field GF(pˆm) to coordinates (r1×(X−s1):r2×(Y−s2):r3×(Z−s3)) (where, p is a prime number, m is an integer not less than 1, r1, r2 and r3 are integers not less than 1 and not larger than (p−1), s1, s2 and s3 are integer not less than 0 and not larger than (p−1), and a code “ˆ” represents power), and a scalar multiplication operating unit for performing scalar multiplication on the point on the elliptic curve transformed by the coordinate transforming unit, wherein at least one of the parameters s1, s2 and s3 has a value other than 0. The apparatus can perform the scalar multiplication in the elliptic curve cryptosystem, with resistance to side channel attacks.
Owner:FUJITSU LTD
Method for communicating securely over an insecure communication channel
InactiveUS20060098814A1Improve securityMemory loss protectionDigital data processing detailsSecure communicationObject based
A method for enhancing the security of cryptographic systems against side channel attacks and cryptanalysis is based on the concept of object hopping or dynamic transformation of elements between objects that share the same category and / or floating objects which facilitate object hopping. The use of floating objects and floating finite fields to facilitate field hopping is also disclosed. Further, the use of curve hopping and floating elliptic curves to facilitate curve hopping and / or key floating when keys used in cryptosystems are floated through floating fields are also used for enhancing the security of cryptographic systems.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
Synchronous logic system secured against side-channel attack
InactiveUS20110285421A1Run fastReduce sensitivityInternal/peripheral component protectionSynchronising arrangementMonitoring systemEye closure
An improvement in the security of a logic system from attacks that observable features such as the power supply or electromagnetic radiation, so called, “side-channel attacks”. Specifically, the present invention comprises a technique and method for reducing ability to monitor the relationship between currents in the system and the data in the system by closing the overall clock eye diagram, whilst keeping the eye diagram for connected stages open. The degree of eye closure for connected pipeline stages allows the system to run closer to its maximum operating speed compared to the use of system wide clock jitter, yet the overall closure provides security that is absent from systems with a partially open eye.
Owner:DEAS ALEXANDER ROGER +1
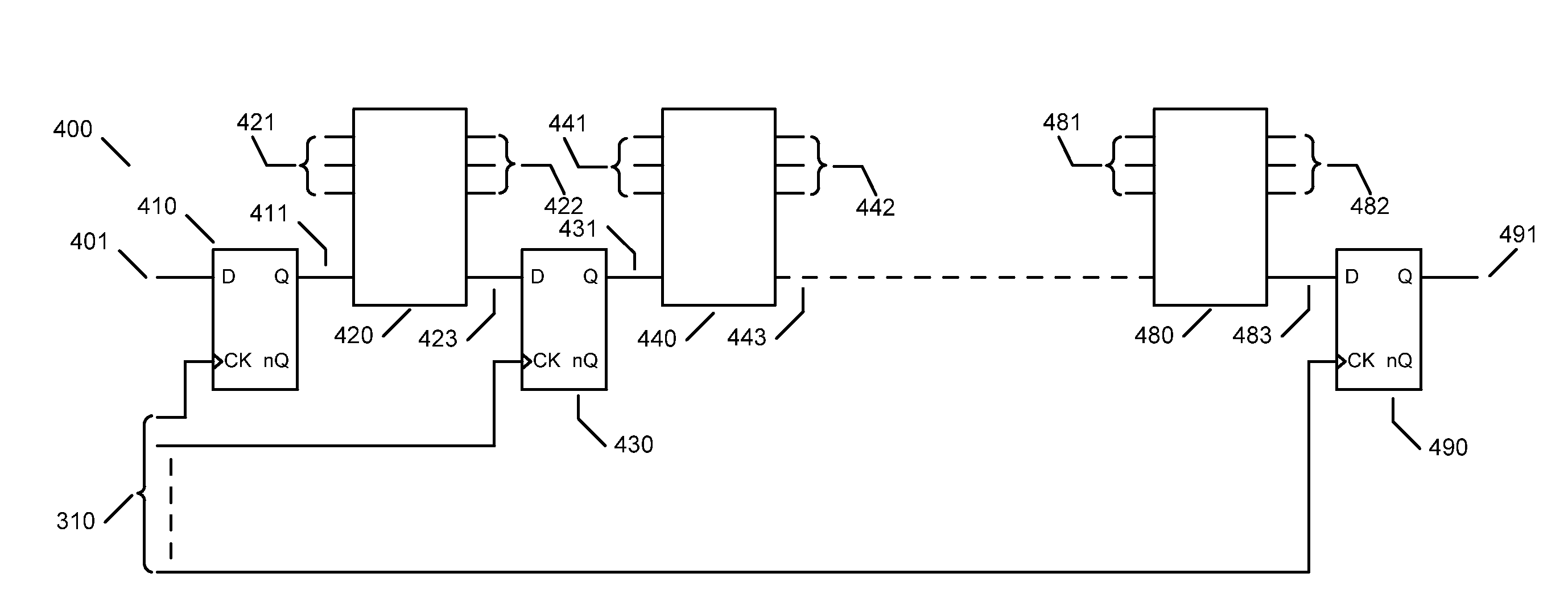
Virtual machine deployment method oriented to side channel attack defense of cloud computation environment
ActiveCN102571746ADecrease in isostatic rateImprove isolation strengthTransmissionSoftware simulation/interpretation/emulationResource poolResource utilization
The invention provides a virtual machine deployment method oriented to side channel attack defense of a cloud computation environment. The virtual machine deployment method comprises the following steps of: (1) user resource pool mapping based on number of virtual machines; (2) computation of user credibility; (3) user resource pool mapping based on credibility; and (4) deployment of the virtual machines. Due to adoption of the virtual machine deployment disclosed by the invention, the co-residing rate of the virtual machines in a system can be reduced by about 30 percent, and the resource utilization rate is reduced by about 5 percent; the isolation strength of a user virtual machine executing environment is effectively enhanced by reducing the co-residing rate of the virtual machines; and the virtual machine deployment method disclosed by the invention has the capability of effectively improving the side channel attack defense power of a cloud computation system and does not excessively lose resource utilization rate.
Owner:XI AN JIAOTONG UNIV
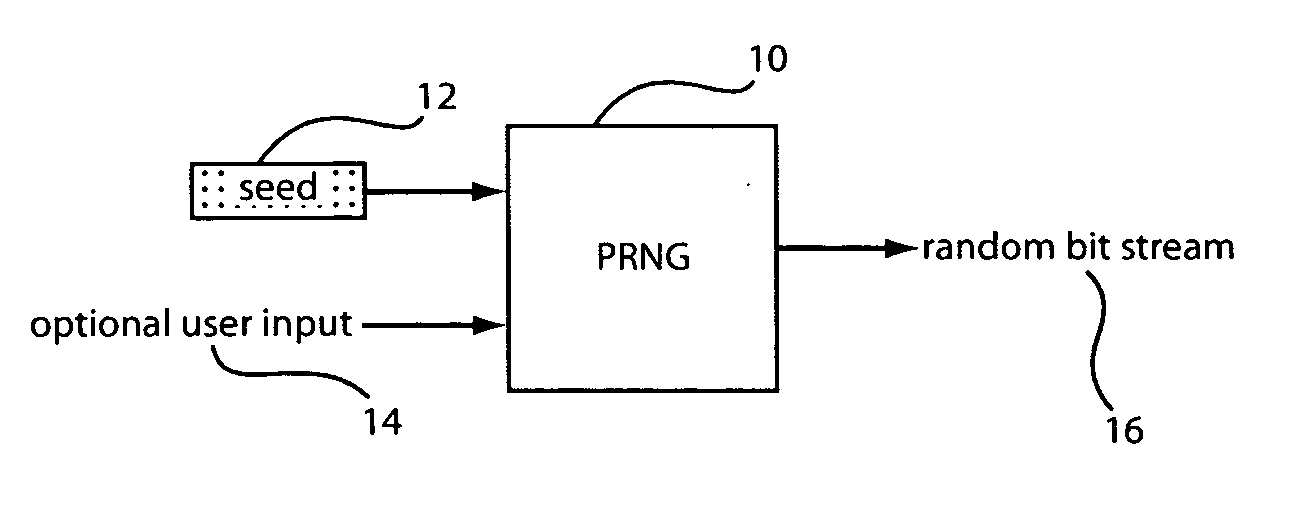
Method, apparatus and system for resistance to side channel attacks on random number generators
InactiveUS20060104443A1Random number generatorsCryptographic attack countermeasuresBiological activationNumber generator
A random number generator (RNG) resistant to side channel attacks includes an activation pseudo random number generator (APRNG) having an activation output connected to an activation seed input to provide a next seed to the activation seed input. A second random number generator includes a second seed input, which receives the next seed and a random data output, which outputs random data in accordance with the next seed. An input seed memory is connected to the activation seed input and a feedback connection from the activation output so that the next seed is stored in the input seed memory to be used by the APRNG as the activation seed input at a next startup cycle.
Owner:IBM CORP
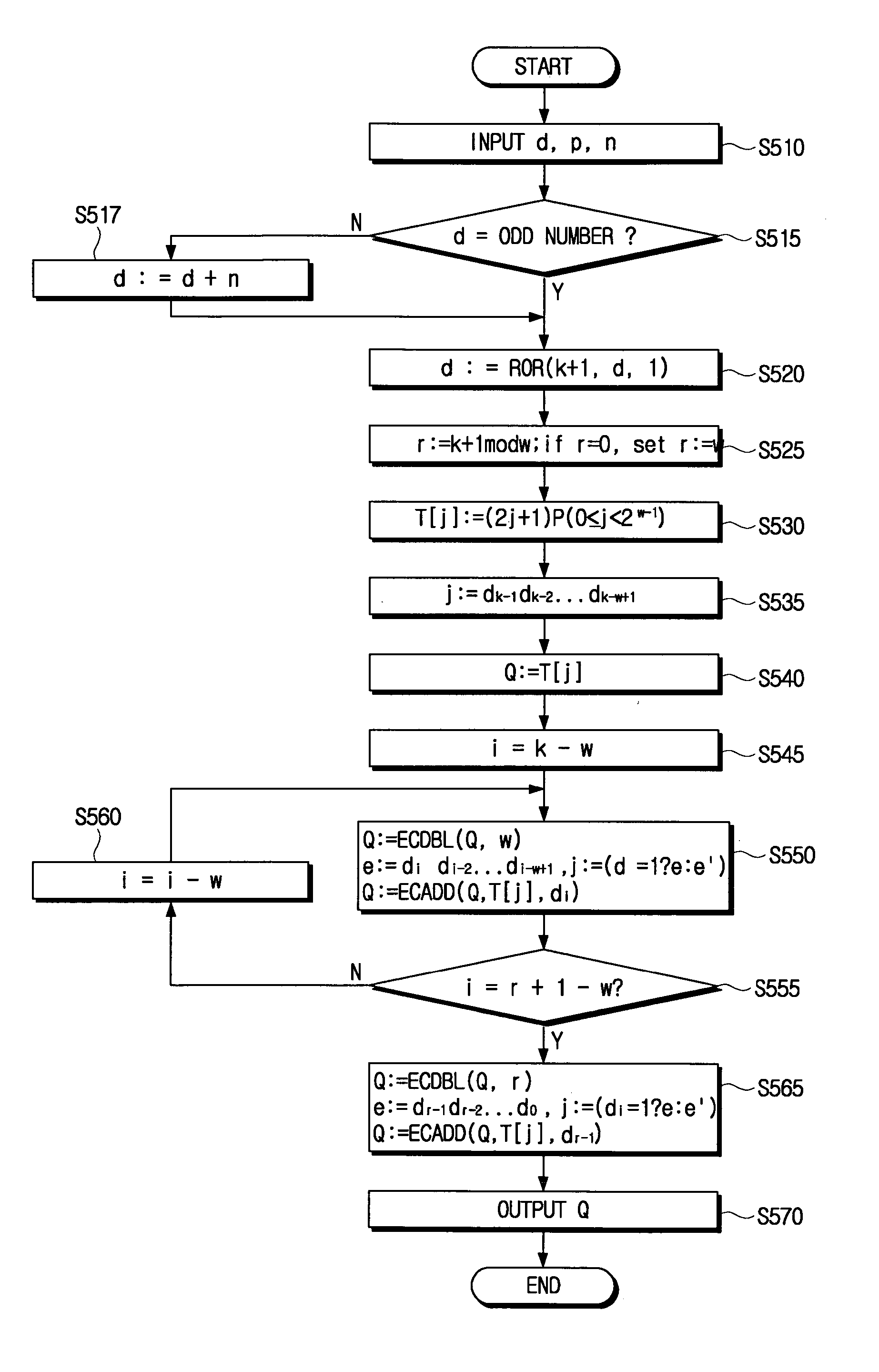
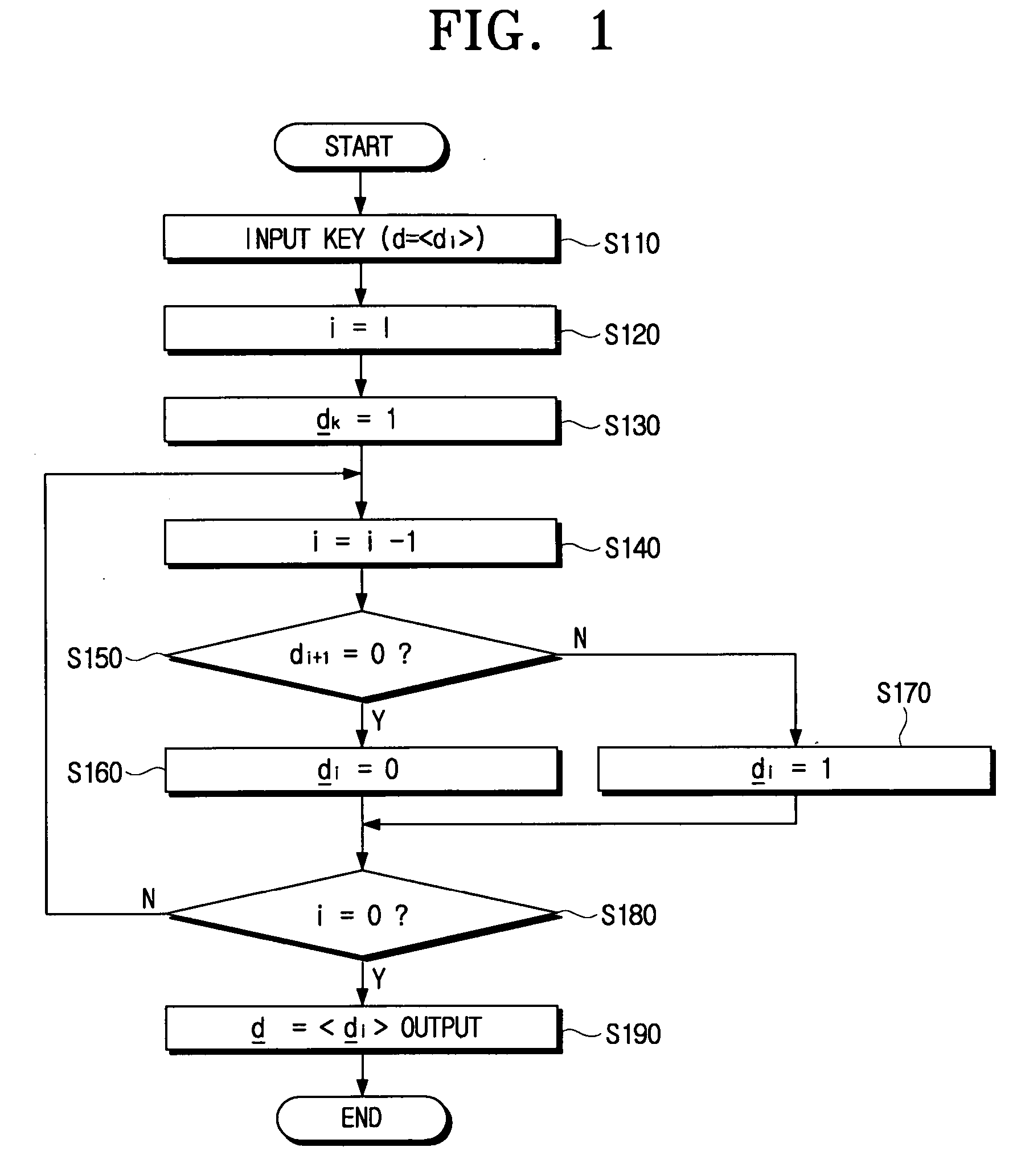
Cryptographic method capable of protecting elliptic curve code from side channel attacks
ActiveUS20050169462A1Requires minimizationSafe and efficientKey distribution for secure communicationPublic key for secure communicationScalar multiplicationElliptic curve cryptography
An elliptic curve cryptography method which generates a public key for use in a communication encryption using an elliptic curve, including: changing a number of a secret key (d) of (k) bits to an odd number; encoding the secret key to yield an encoded secret key (d) in which a most significant bit (MSB) is (1) and a rest positional number is (1) or (−1); and computing the public key (Q=Dp) by multiplying the encoded secret key (d) by a predetermined point (P) on the elliptic curve by a scalar multiplication.
Owner:SAMSUNG ELECTRONICS CO LTD
Multimode reconfigurable encryption method based on advanced encryption standard (AES) encryption algorithm
InactiveCN102185692AAvoid Side Channel AttacksEasy to operateEncryption apparatus with shift registers/memoriesComputer hardwareS-box
The invention discloses a multimode reconfigurable encryption method based on an advanced encryption standard (AES) encryption algorithm. In the method, five operating modes are provided for a user to select, and an all-random S box generation way and a biased random S box generation way are provided. The method comprises the following steps of: judging whether the operating mode and an S box selected by the user are rational or not; if the selected operating mode and the selected S box are irrational, prompting the user to perform reselection; if the selected operating mode and the selected S box are rational, further calculating the smallest encryption round number according to the differential uniformity and nonlinearity of the generated S box, and determining a final encryption round number according to the requirements of the user; selecting a source file for an encryption or decryption operation; and finally storing the encrypted or decrypted data file, and providing the encrypted or decrypted data file for the user to view. By the method, side channel attacks possibly on encryption realized by adopting hardware are effectively avoided, and an operating way of the reconfigurable encryption method is optimized; the method is applied to the configuration of a set of reconfigurable software encryption system, and the reconfiguration and integration of block ciphers into the same software system; and convenience is brought to operations and management.
Owner:BEIHANG UNIV
Synchronous logic system secured against side-channel attack
InactiveUS20110260749A1Run fastReduce sensitivityReliability increasing modificationsAcutation objectsMonitoring systemEye closure
An improvement in the security of a logic system from attacks that observable features such as the power supply or electromagnetic radiation, so called, “side-channel attacks”. Specifically, the present invention comprises a technique and method for reducing ability to monitor the relationship between currents in the system and the data in the system by closing the overall clock eye diagram, whilst keeping the eye diagram for connected stages open. The degree of eye closure for connected pipeline stages allows the system to run closer to its maximum operating speed compared to the use of system wide clock jitter, yet the overall closure provides security that is absent from systems with a partially open eye.
Owner:DEAS ALEXANDER ROGER +1
Semiconductor device
InactiveUS20070180285A1No concern for defectImprove securityDigital data processing detailsUser identity/authority verificationNumber generatorRead-only memory
To make it difficult to obtain a secret key from a power change or EM emission intercepted when an IC card encounters a power analysis attack or an electromagnetic wave analysis attack. An arithmetic circuit and a circuit for transmitting / receiving a signal to / from outside are included. The arithmetic circuit includes a central processing unit, an auxiliary arithmetic unit, a random number generator, and a read only memory. The read only memory stores a program for processing of blocking a side-channel attack in signal transmission / reception to / from outside. By additionally providing the random number generator and the auxiliary arithmetic unit, time change of physical data which leaks from an IC chip can be made more complex. This operation is executed by the program. Therefore, it takes time to obtain inside data from physical data intercepted by the third party, thereby security can be improved.
Owner:SEMICON ENERGY LAB CO LTD
Realization method of elliptic curve cryptosystem for preventing side-channel attack
The invention relates to an elliptic curve cryptosystem (Elliptic Curve Cryptosystem, called ECC for short) for preventing side-channel attack (Side-Channel Attacks, called SCA for short), which belongs to the field of cryptographic algorithm. The realization method of the elliptic curve cryptosystem for preventing side-channel attack comprises the following steps: the operational step of dot multiplication is determined by a cryptographic key during the processes of encryption and decryption, and the dot multiplication step is finished through the operational combination of point addition and point double with balanced operational flow. By balancing the operational flow of the point addition and the point double, the operation time of the two are the same, and the consumed power is also the same, therefore, the difference of the side channel information leaked from the point addition and the point double is eliminated, and the side-channel attach method based on the difference of the point addition and the point double is failed to attack the ECC during the entire dot multiplication process.
Owner:SHENZHEN INST OF ADVANCED TECH
DES masking method for resisting side-channel attack
InactiveCN103647638AIncrease the difficultyEncryption apparatus with shift registers/memoriesComputer moduleElectronic chip
The invention provides a DES masking method capable of resisting side-channel attack technology. The method is implemented by two DESs, wherein one DES is used for data encryption and decryption after masking, and the other DES is used for off-masking value calculation. In the DES implementation process, before an initial IP is replaced, masking is carried out first, and 16 different random numbers are respectively introduced into 16 sub wheels for masking. The correlation between power consumption and operating data is substantially eliminated, and the cost for attackers to attack DES with the use of a side-channel means is greatly increased. Therefore, the method can be widely used in an electronic chip with a DES security calculation module.
Owner:BEIJING CEC HUADA ELECTRONIC DESIGN CO LTD
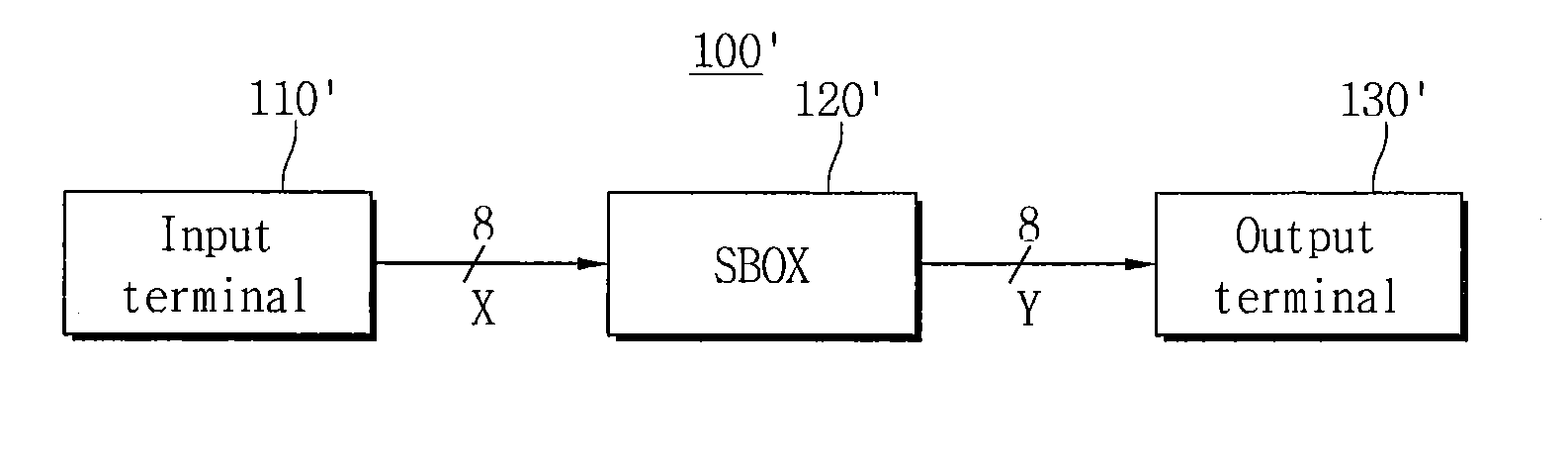
Endecryptor preventing side channel attack, driving method thereof and control device having the same
InactiveUS20160065361A1Reduce areaRun at high speedSecret communicationCryptographic attack countermeasuresComputer hardwareData transformation
An endecryptor and a control device are provided. The endecryptor includes a first SBOX configured to replace first input data with first substitution data, a transformation unit configured to replace the first input data with second substitution data and an output terminal configured to output encrypted or decrypted output data based on the first and second substitution data.
Owner:SAMSUNG ELECTRONICS CO LTD
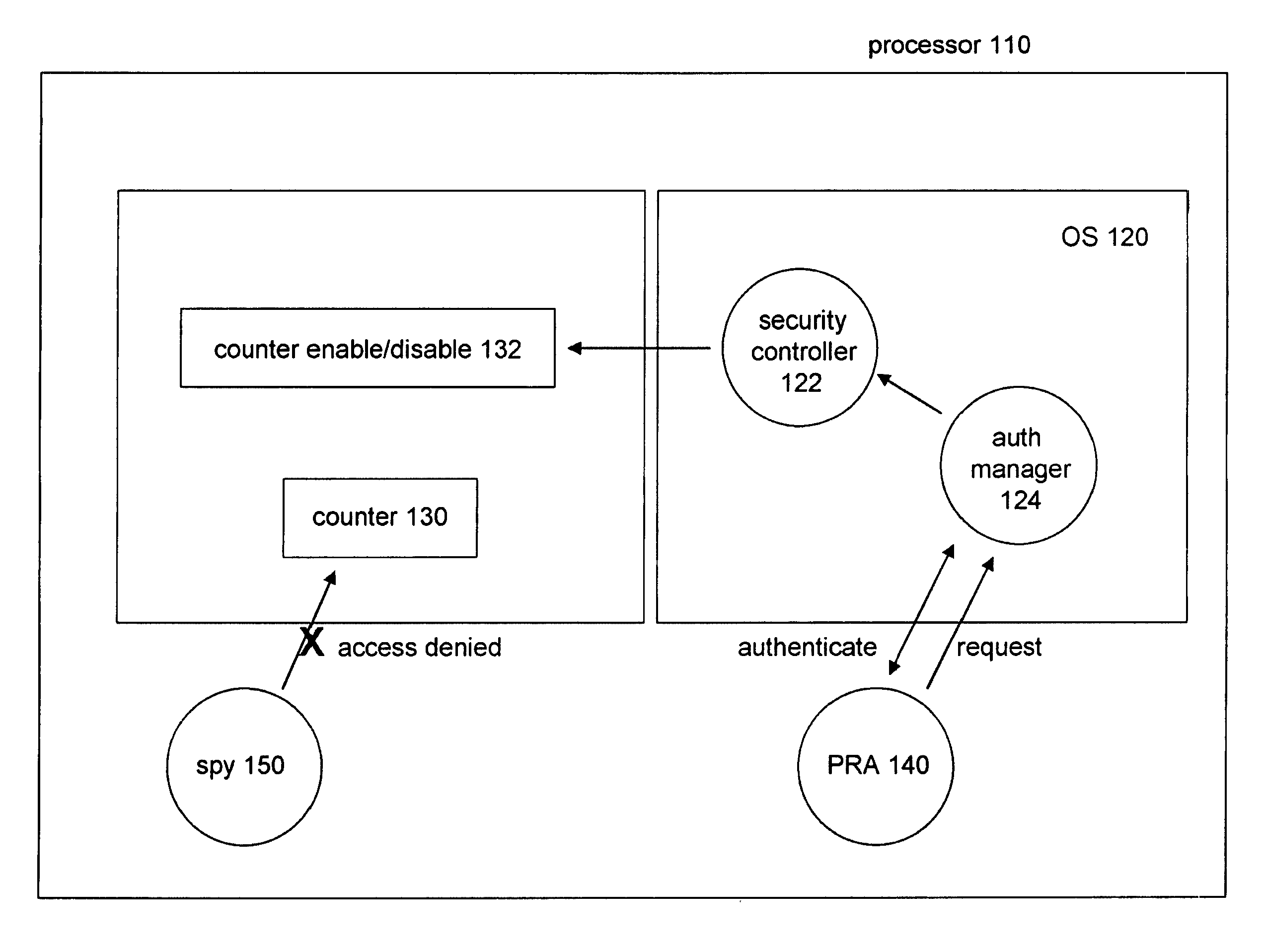
Mitigating Branch Prediction and Other Timing Based Side Channel Attacks
InactiveUS20080155679A1Digital data processing detailsUnauthorized memory use protectionTimestampOperational system
To provide hardware protection against timing based side channel attacks, a processor's microarchitecture enables an OS to determine which applications have the privilege to read timestamp and performance counters. Using a white list of applications, and an authentication mechanism to authenticate applications, a legitimate Protection Required Application (PRA) may temporarily prevent other applications from reading timestamp and performance counters while it executes (or excutes sensitive operations).
Owner:INTEL CORP
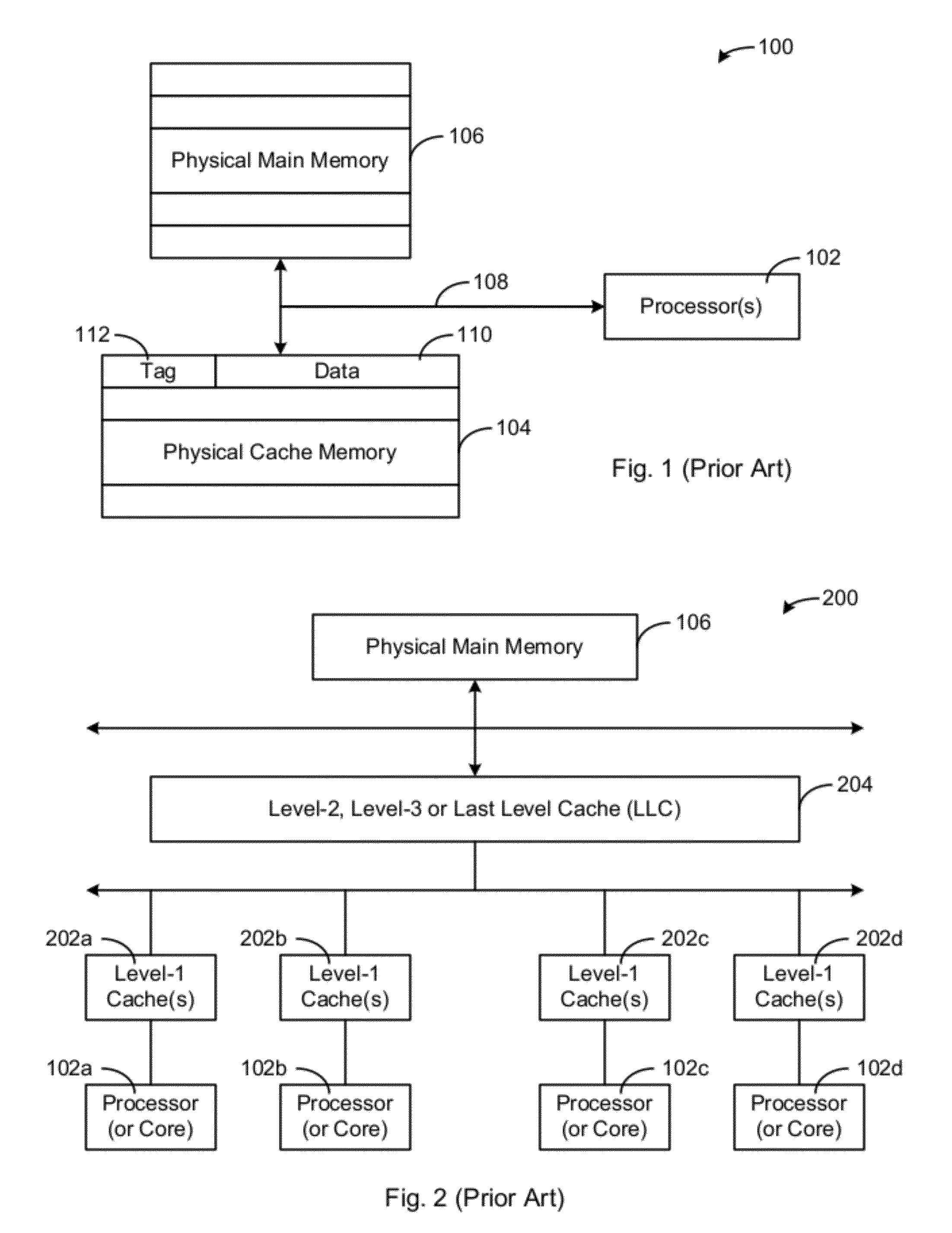
Method and apparatus for improving computer cache performance and for protecting memory systems against some side channel attacks
ActiveUS20120297110A1Increase profitReduce probabilityMemory architecture accessing/allocationMemory adressing/allocation/relocationAddress decoderParallel computing
A physical cache memory that is divided into one or more virtual segments using multiple circuits to decode addresses is provided. An address mapping and an address decoder is selected for each virtual segment. The address mapping comprises two or more address bits as set indexes for the virtual segment and the selected address bits are different for each virtual segment. A cache address decoder is provided for each virtual segment to enhance execution performance of programs or to protect against the side channel attack. Each physical cache address decoder comprises an address mask register to extract the selected address bits to locate objects in the virtual segment. The foregoing can be implemented as a method or apparatus for protecting against a side channel attack.
Owner:UNIVERSITY OF NORTH TEXAS
Systems and Methods for Random Fill Caching and Prefetching for Secure Cache Memories
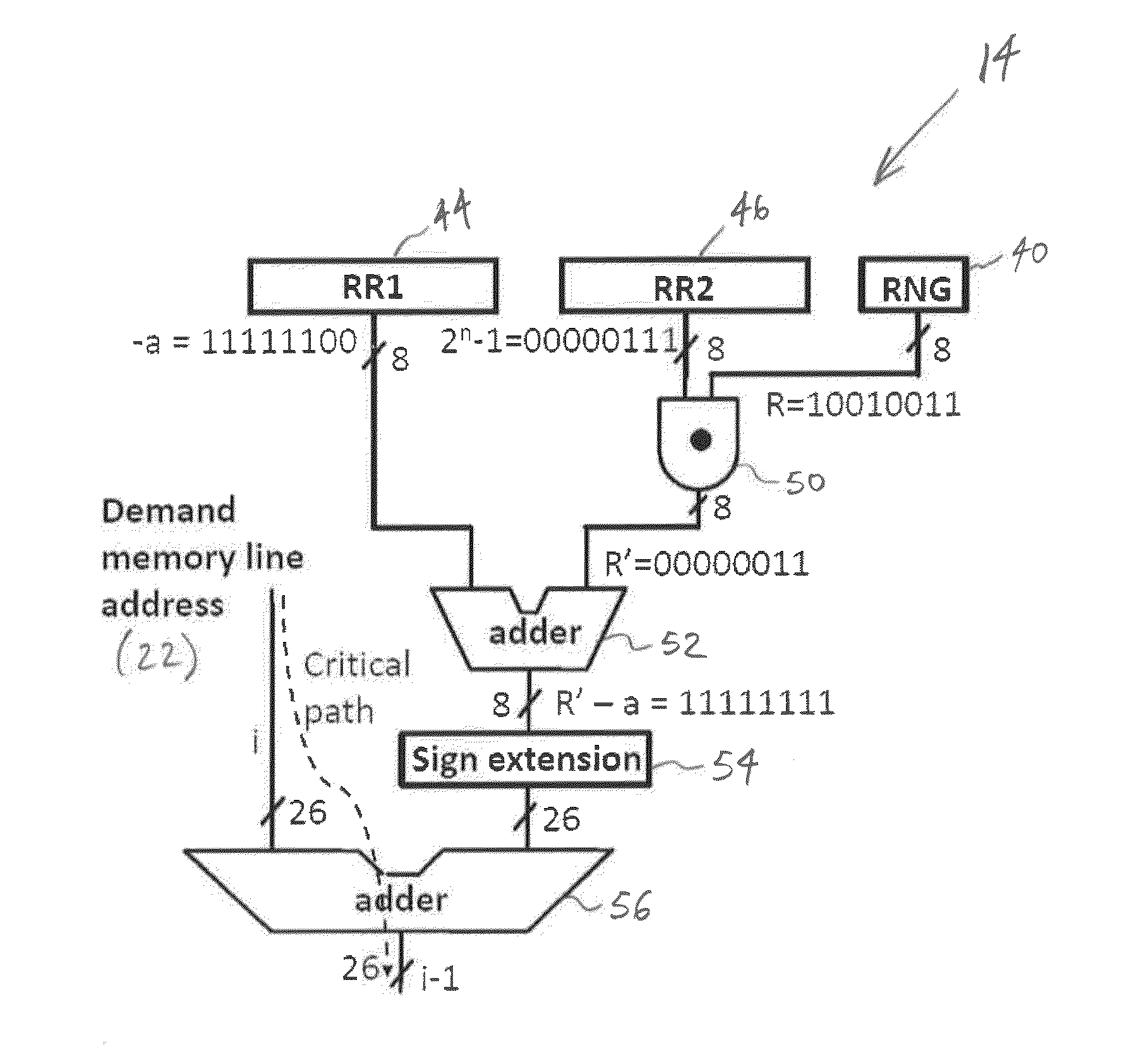
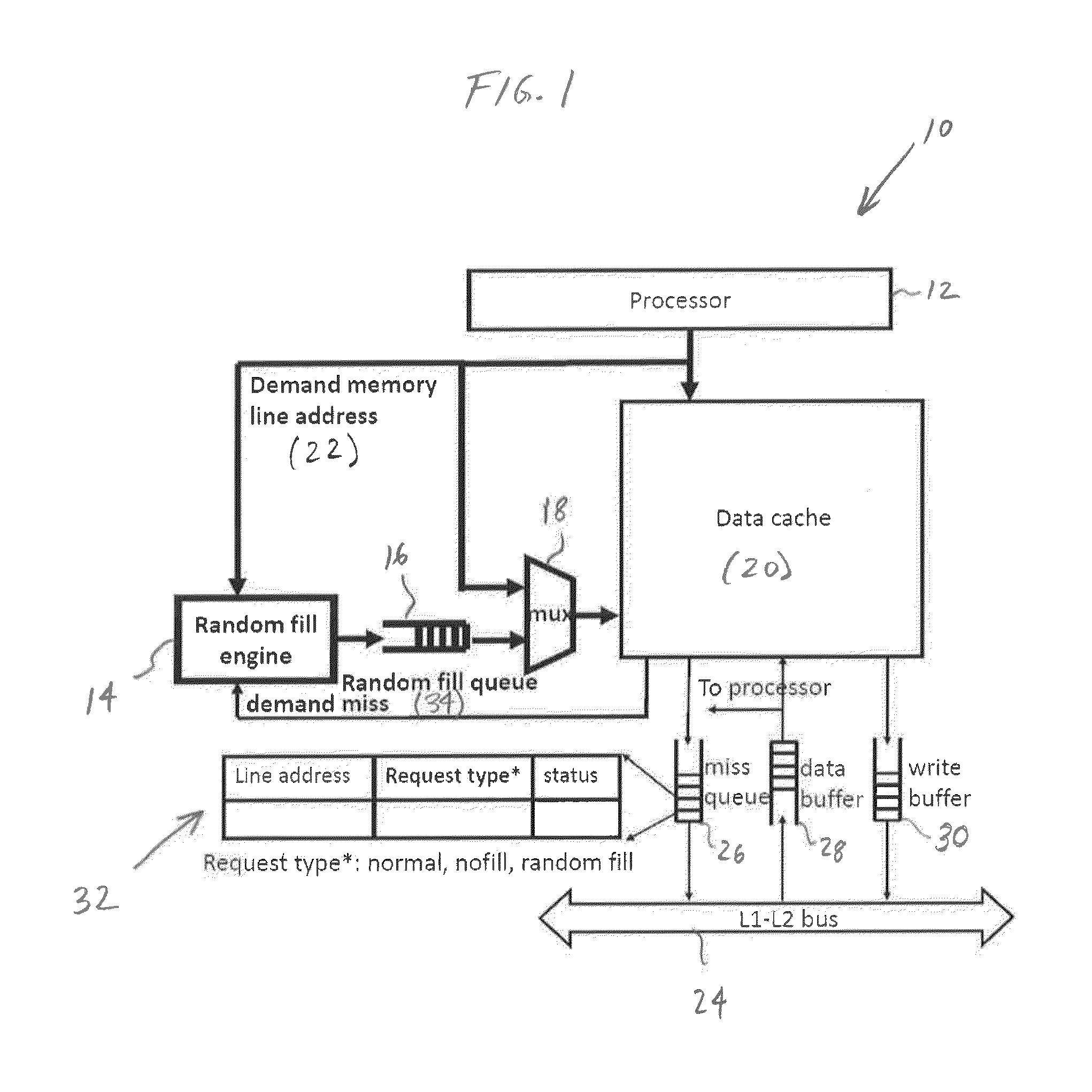
ActiveUS20160170889A1Improve securityImprove system performanceMemory architecture accessing/allocationInput/output to record carriersParallel computingWorkload
Systems and methods for random fill caching and prefetching for secure cache memories are provided. The system dynamically de-correlates fetching a cache line to the processor from filling the cache with this cache line, due to a demand memory access, in order to provide greater security from information leakage due to cache side-channel attacks on cache memories. The system includes a random fill engine which includes a random number generator and an adjustable random fill window. Also provided is an adaptive random fill caching system which dynamically adapts the random fill window to a wide variety of computational workloads. Systems and methods for cache prefetching to improve system performance using adaptive random fill prefetching and random fill prefetching are also provided.
Owner:CORESECURE TECH LLC
Protecting a secure boot process against side channel attacks
Embodiments of an invention for protecting a secure boot process against side channel attacks are disclosed. In one embodiment, an apparatus includes cryptography hardware, a non-volatile memory, a comparator, and control logic. The cryptography hardware is to operate during a first boot process. The non-volatile memory includes a storage location in which to store a count of tampered boots. The comparator is to perform a comparison of the count of tampered boots to a limit. The control logic is to, based on the first comparison, transfer control of the apparatus from the first boot process to a second boot process.
Owner:INTEL CORP
Encrypted Communication System with Limited Number of Stored Encryption Key Retrievals
ActiveUS20110078449A1Frustrates attackerReduce noiseKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareCommunications system
A system for encrypted communication with external entities is configured to frustrate side channel attacks attempting to determine an encryption key. The system has a device with an encryption key stored in memory, an external entity with identity data for transmission to the device to initiate communication such that in response the device applies a one way function to the encryption key and the identity data to generate a variant key used to authenticate communications between the device and the external entity. The device is configured to limit the number of times the encryption key is allowed to be retrieved from the first memory to a pre-determined threshold.
Owner:MEMJET TECH LTD
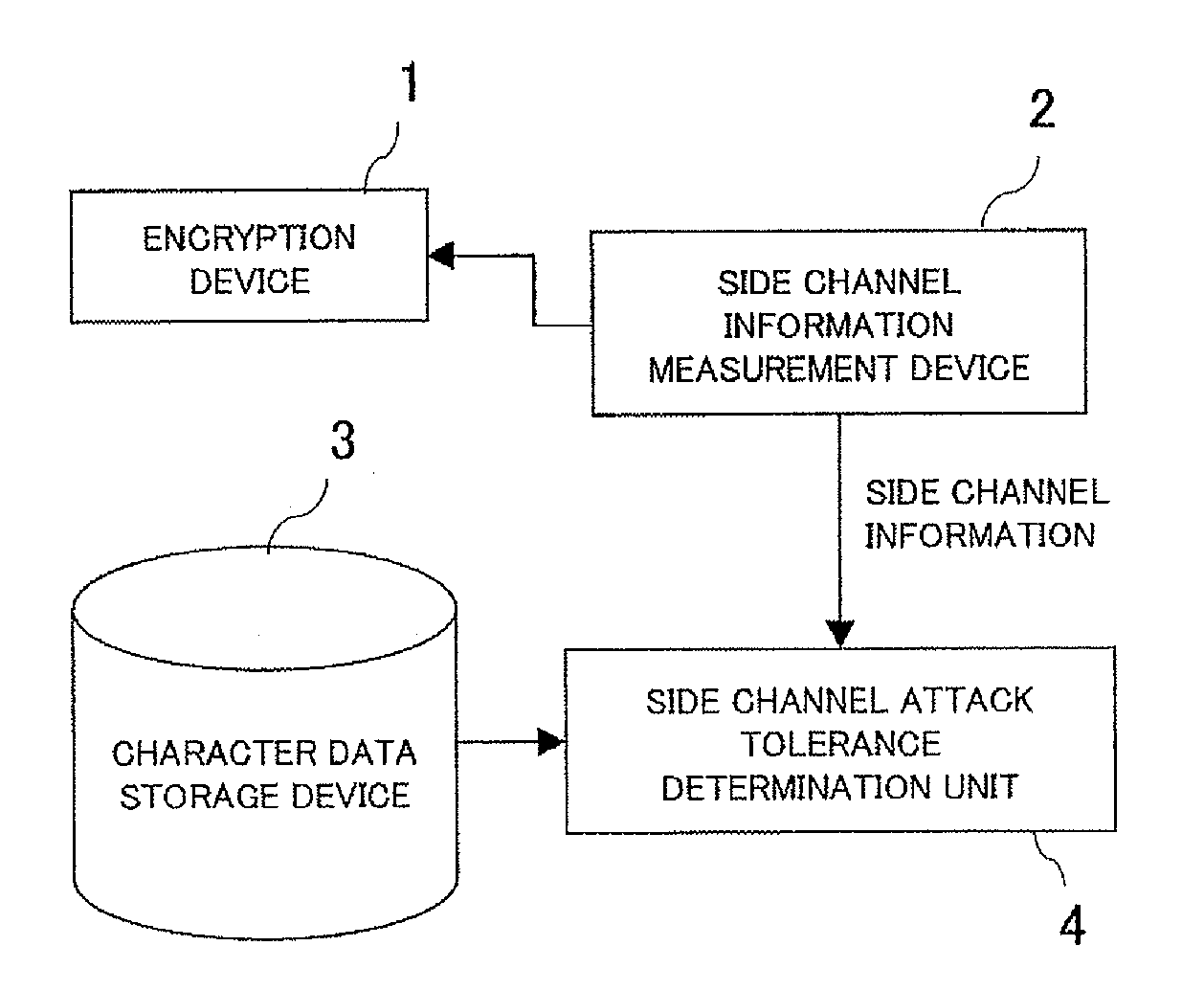
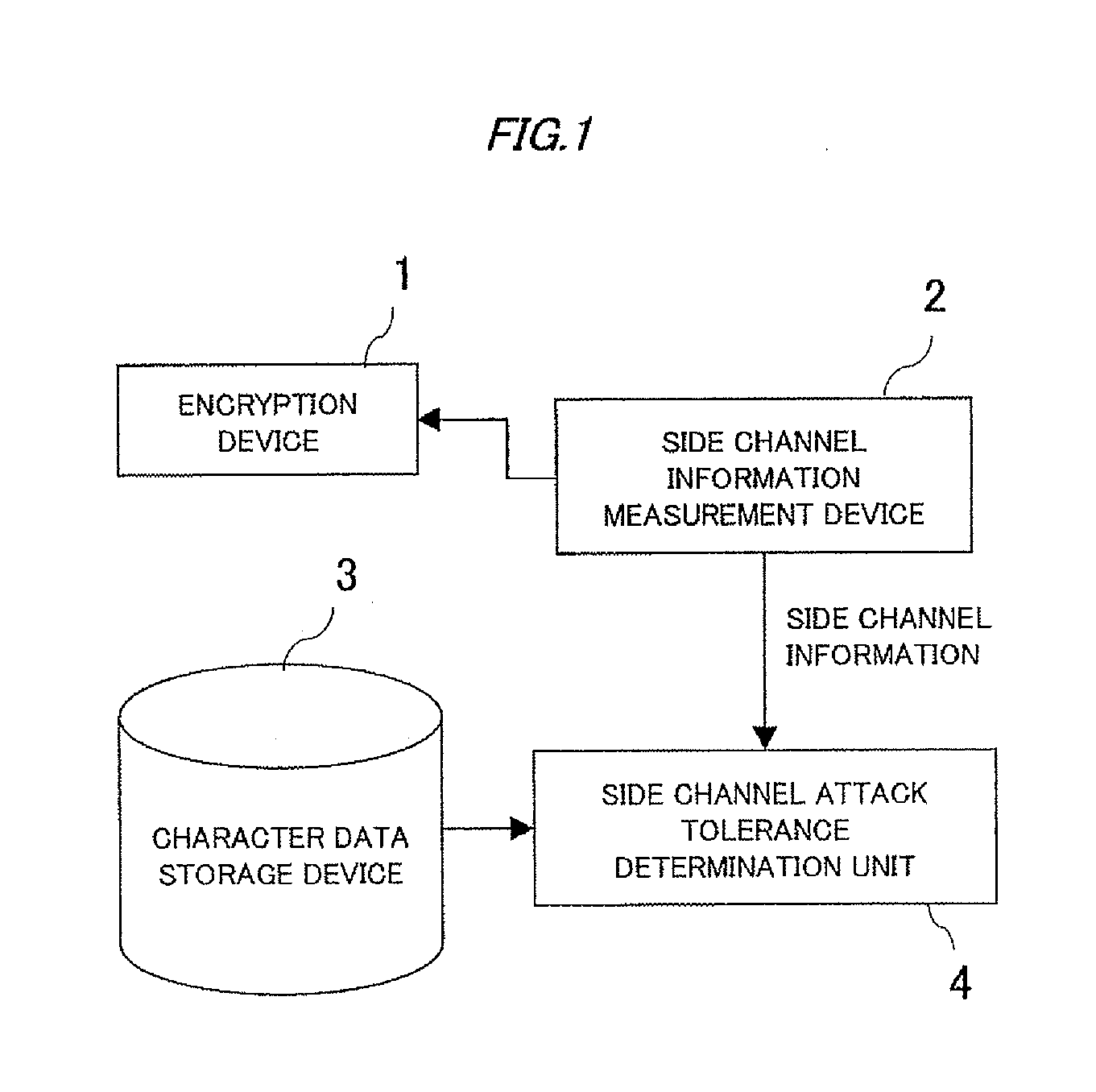
Side channel attack tolerance evaluation apparatus, method and program
InactiveUS20100246808A1Memory loss protectionError detection/correctionAttack toleranceMeasurement device
Provided is a side channel attack tolerance evaluation device capable of evaluating the propriety of the estimation of an encryption algorism, processing timing, and determination of a processing sequence of the encryption algorism using side channel information. The side channel attack tolerance evaluation device, which performs evaluation of tolerance to a side channel attack by using side channel information leaking from an encryption device, is provided with a storage unit (character data storage device), a measurement unit (side channel information measurement device), and a processing unit (side channel attack tolerance evaluation unit). The storage unit stores side channel information that has been previously acquired by executing a predetermined encryption algorithm in an encryption device or information obtained by applying predetermined processing to the side channel information. The measurement unit measures the side channel information generated from an encryption device to be evaluated. The processing unit calculates a correlation value between the side channel information acquired by the measurement unit and character data stored in the storage unit to determine the propriety of tolerance of the encryption device to be evaluated to the side channel attack.
Owner:NEC CORP
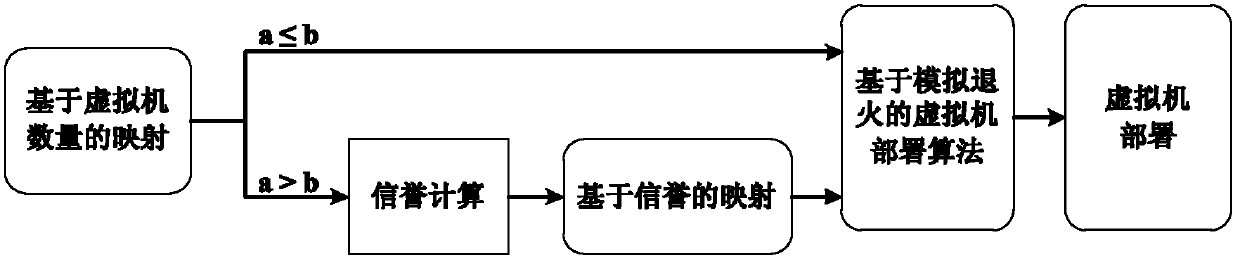
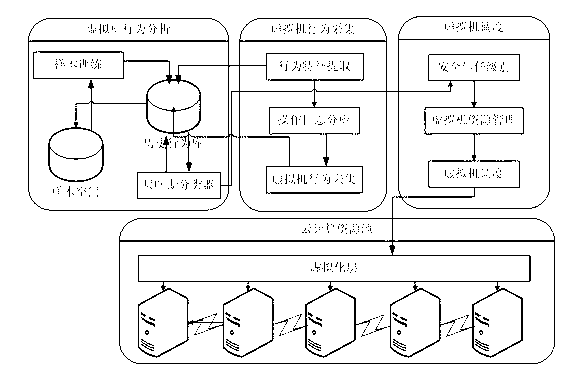
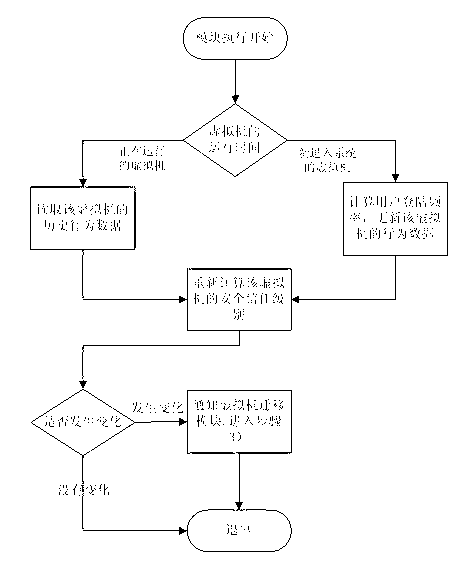
Method for guarding against side channel attack virtual machine in cloud computing environment
ActiveCN102843385AEnsure safetyProtection against side channel attacksTransmissionData centerTrust level
The invention discloses a method for guarding against a side channel attack virtual machine in a cloud computing environment. The method comprises the following steps of: step 1) acquiring the behavior data of all the virtual machines in an execution cycle of a data center in real time according to the behavior characteristics of the virtual machine executing side channel attacks and the behavior characteristics of a normal virtual machine; step 2) classifying the behavior data of all the virtual machine acquired in real time in the step 1) by a Bayes method, and obtaining the high, intermediate, low, or extremely low security trust level of each virtual machine; and step 3) reading the security trust levels of all the virtual machines in the current data center topology, migrating the threatening virtual machines in the current environment, and placing the virtual machines with different security trust levels in different physical hosts. The method physically isolates the malicious users from the normal users, thereby terminating the behaviors of the side channel attack virtual machines and protecting the data security and privacy security of the virtual machines in the cloud computing environment.
Owner:SOUTHEAST UNIV
System and methods for side-channel attack prevention
InactiveUS8781111B2Digital data processing detailsInternal/peripheral component protectionProcessor registerCryptosystem
Owner:AVAGO TECH INT SALES PTE LTD
Resisting method of circuit on side channel attack based on pseudo-operation
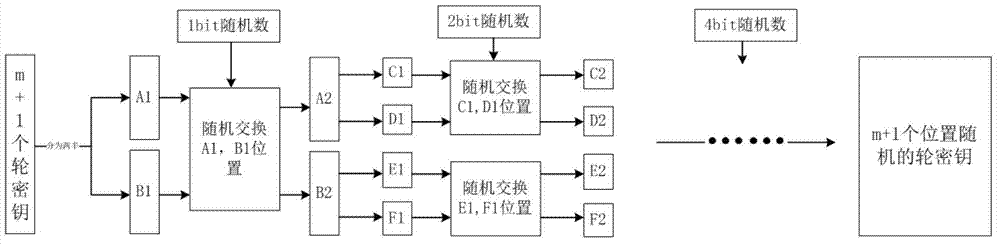
The invention discloses a resisting method of a circuit on the side channel attack based on the pseudo-operation, and belongs to the technical field of computer security. A round secret key sequence is composed by m pseudo-round secret keys and one real-round secret key to conduct the first round SMS4 encrypting calculation, a second round SMS4 encrypting calculation is conducted on the result of the first round SMS4 encrypting calculation with the participation of the real-round secret key, and a ciphertext is acquired. According to the resisting method of the circuit on the side channel attack based on the pseudo-operation, the position of the generated first round SMS4 encrypting calculation is random, and an attacker cannot align with a power-consumption curve, so that the attack cannot be realized; in addition, compared with an unprotected circuit, the energy consumption cannot exceed the two times of the original energy consumption.
Owner:SHANGHAI JIAO TONG UNIV +2
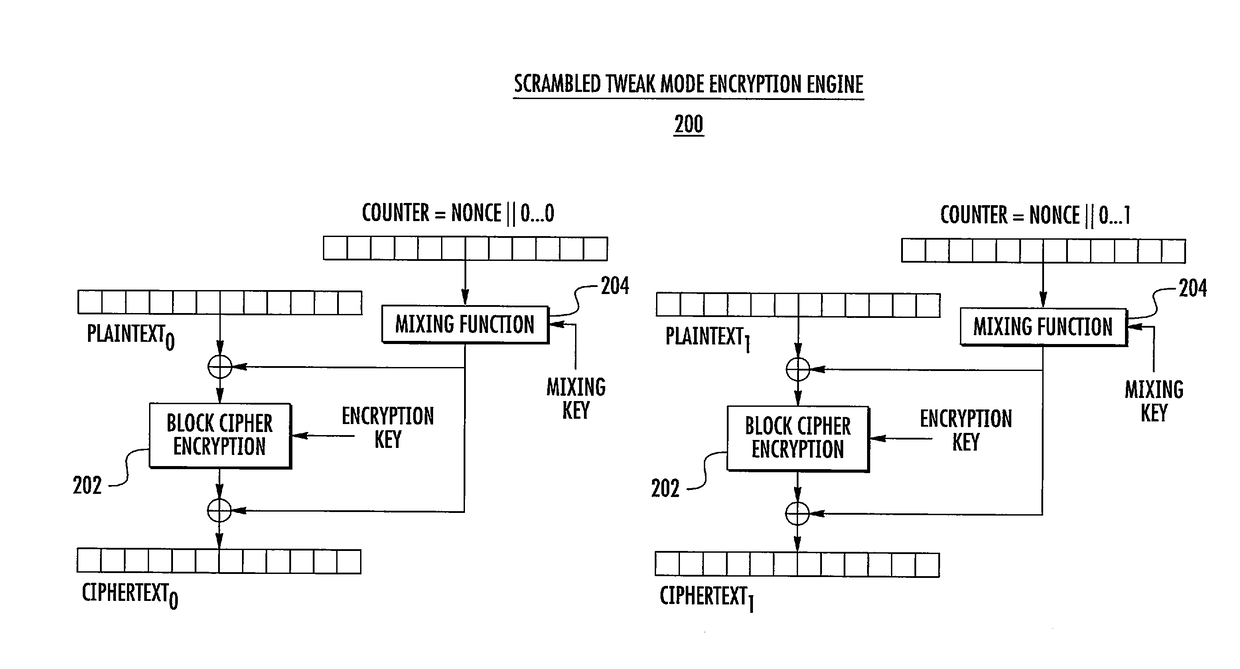
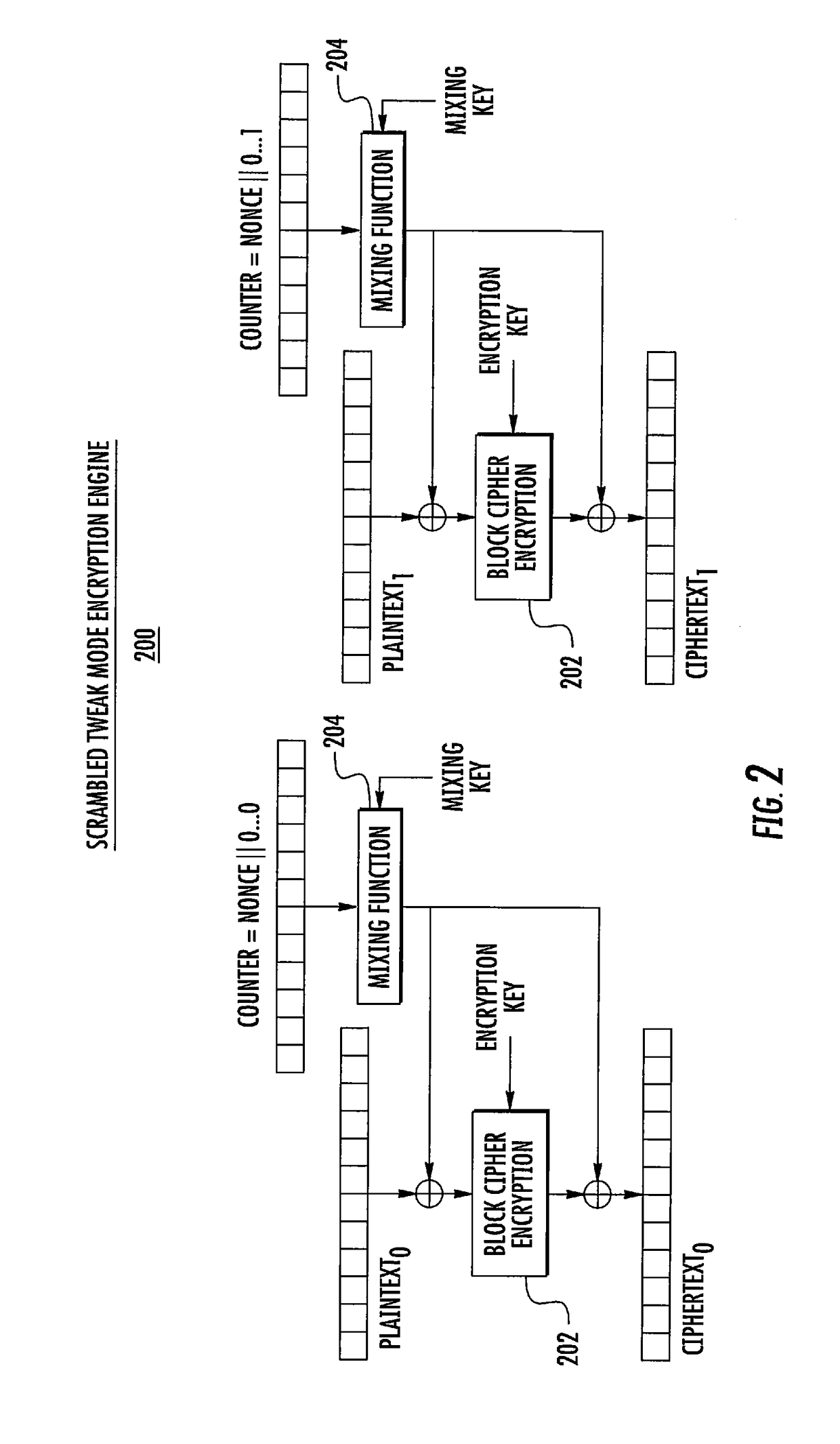
Scrambled tweak mode of blockciphers for differential power analysis resistant encryption
ActiveUS20170104586A1Improve securityEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresComputer hardwarePower analysis
A system and method for providing a scrambled tweak mode of block cipher encryption for a device that mitigates the effect of side channel attacks based on differential power analysis (DPA). The scrambled tweak mode encryption engine creates noise at the start of the encryption process by obfuscating the counter value with the use of the very fast mixing function, such as a mixing function based on a XOR tree, substitution-permutation networks, or double-mix Feistel networks. The mixing function uses some secret key material, which diversifies its behavior between different instantiations. Because the counter values are scrambled and the mixing functions operate very fast in parallel hardware, the input of the block cipher is pseudorandom and groups of blocks can't be correlated.
Owner:THE BOEING CO
Elliptic curve anti-bypass attack method based on randomizing multiplication with symbol scalar
InactiveCN101197668AImprove securityImproving the ability to defend against power consumption attacksPublic key for secure communicationComputations using residue arithmeticPassword crackingSide channel attack
The invention belongs to the information security technical field and provides an elliptical curve bypass attack-proof method based on the randomization tape symbol scalar multiplication. The elliptical curve bypass attack-proof method based on the randomization tape symbol scalar multiplication of the invention comprises the following steps that: firstly, a key in binary system is represented to be a randomization tape symbol binary number; secondly, a finite state machine for realizing the randomization tape symbol scalar product is obtained basing on a randomization addition and subtraction chains of the elliptical curve scalar product; finally, the elliptical curve scalar production operation is completed basing on the finite state machine and the improvement of the ability of the elliptical curve cryptograph to resist the bypass attack is realized. The invention which improves the security of the realization of the method can be applicable to the fields such as the cryptograph theory, the password cracking, the security chip design and the smart card design.
Owner:SHANGHAI JIAO TONG UNIV
Data encryption without padding
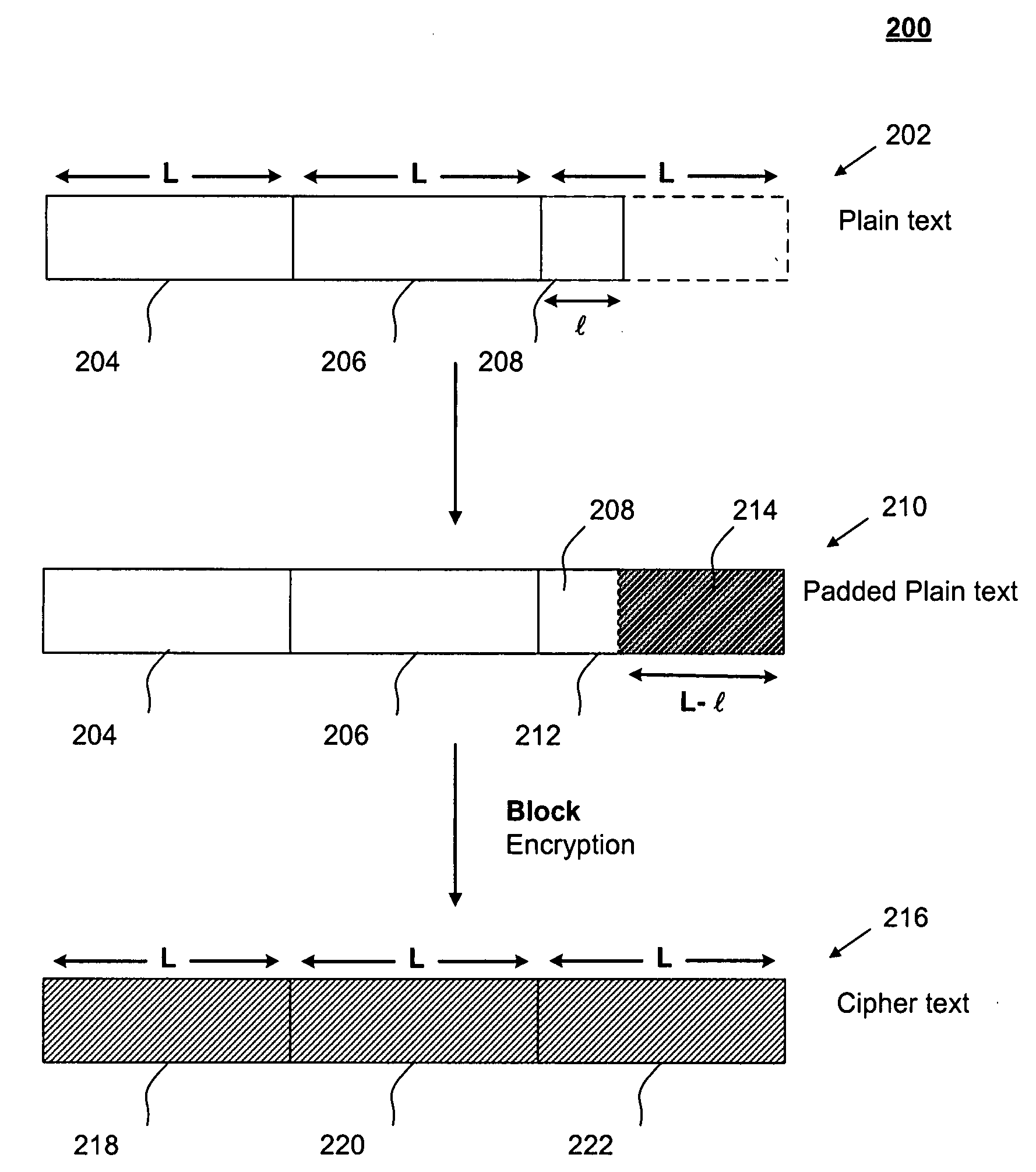
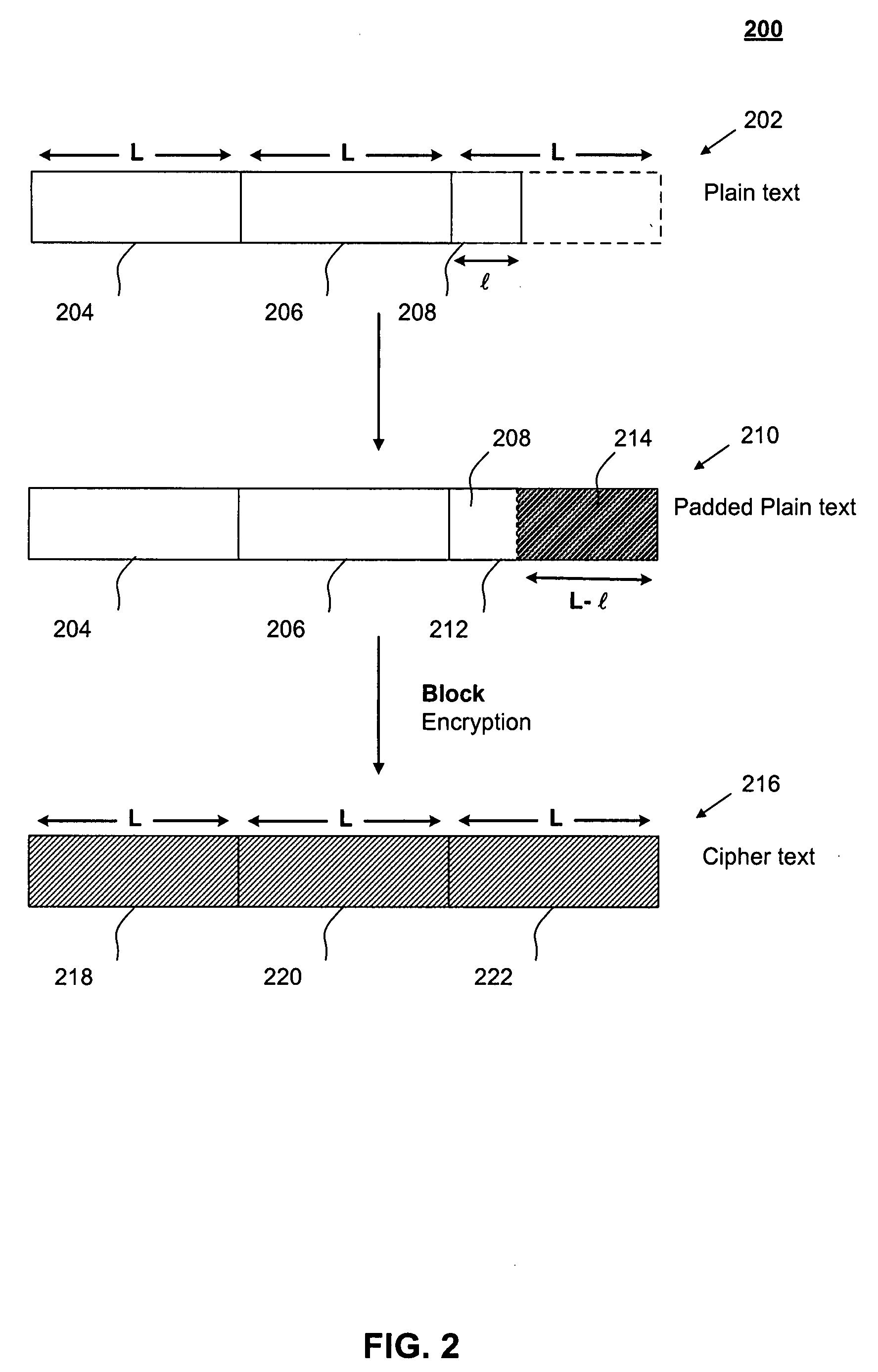
InactiveUS20080192924A1Encryption overhead savingAvoid paddingSecret communicationSecuring communicationPlaintextBlock cipher
The present invention relates generally to data encryption. In particular, the present invention relates to methods of block cipher encryption and decryption. Embodiments of the present invention avoid padding in encrypting plain text messages having lengths that are non-integral multiples of a pre-determined block size. As such, encryption overhead savings can be achieved. Further, security from side-channel attacks can be increased.
Owner:SYBASE INC
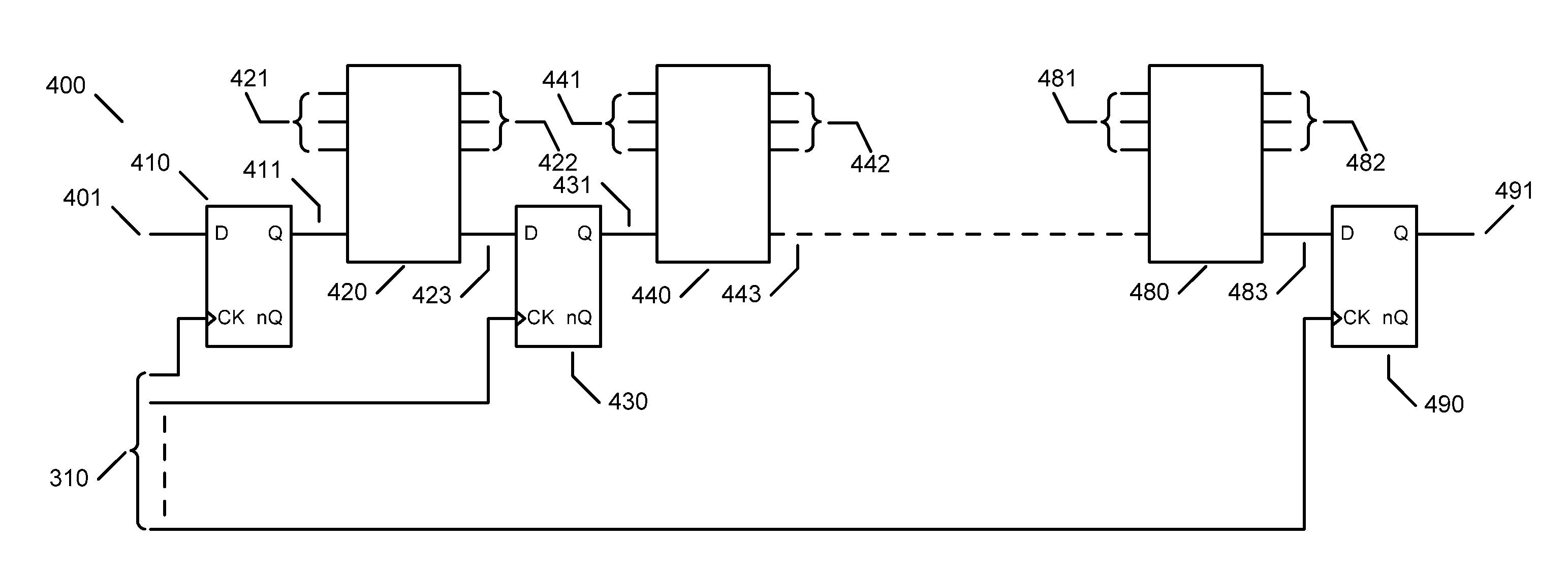
Side-channel attack resisting processor architecture based on random instruction delay
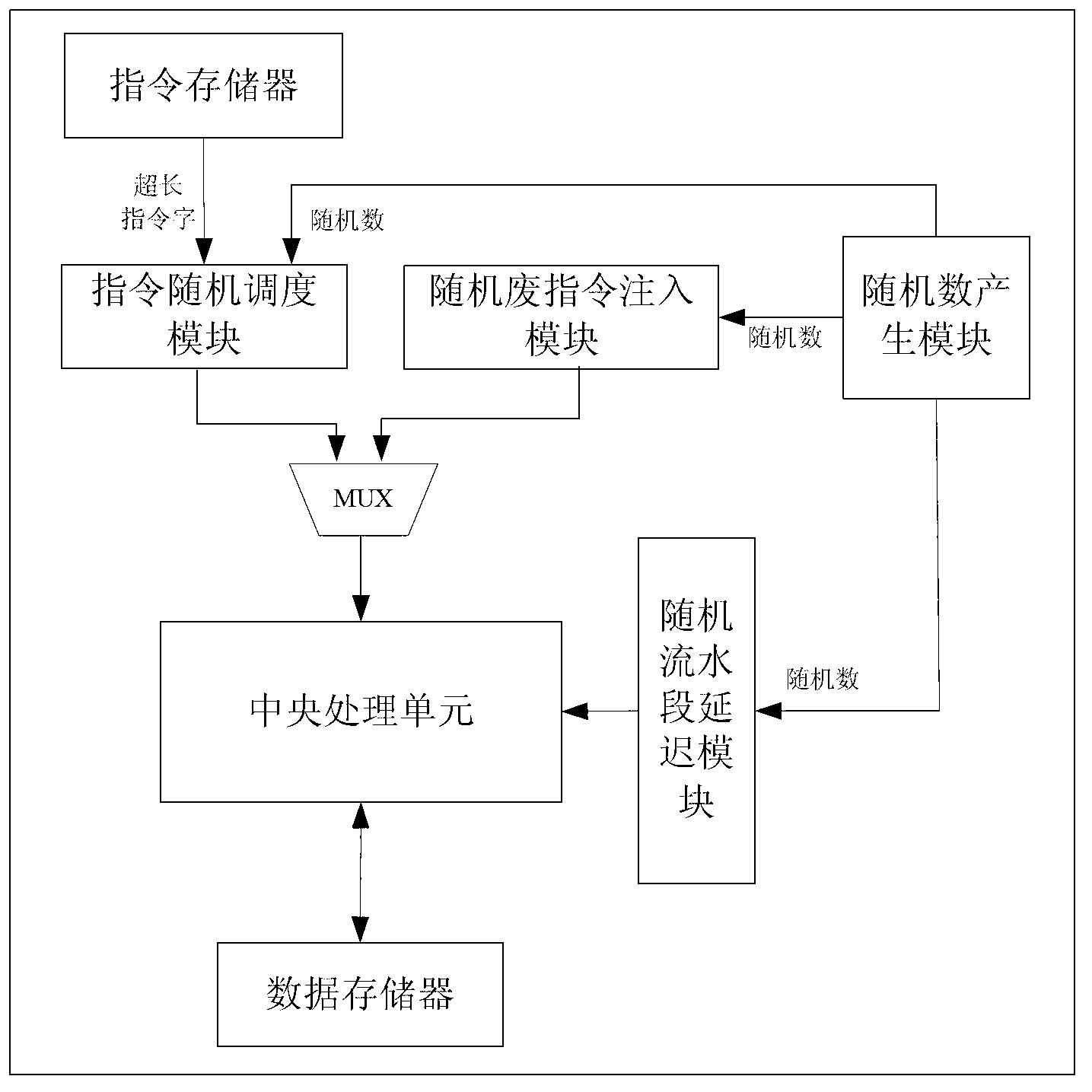
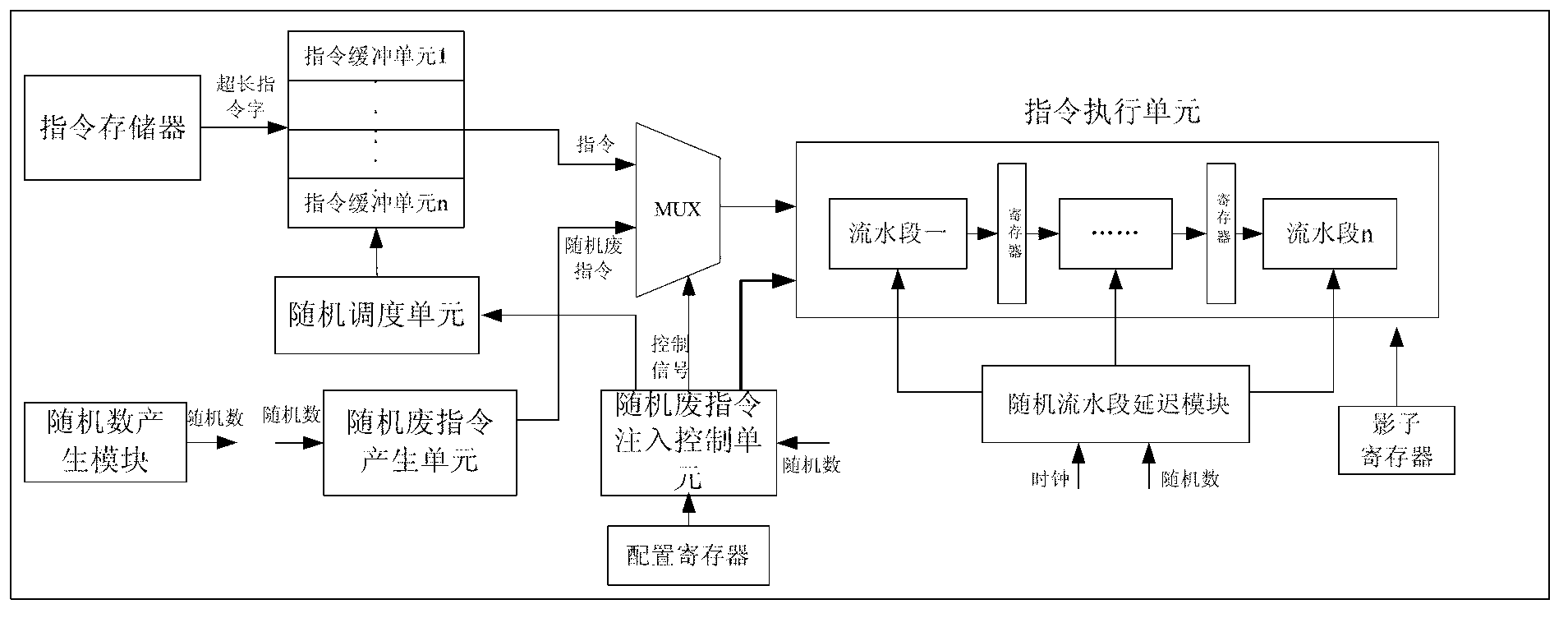
ActiveCN103324467AReduce signal to noise ratioIncrease attack difficultyConcurrent instruction executionInternal/peripheral component protectionInstruction memoryStatistical analysis
The invention discloses a side-channel attack resisting processor architecture based on random instruction delay. The architecture is that an instruction memory is connected with an instruction random scheduling module, a central processing unit is connected with a multi-channel selector, a random flowing water section delay module and a data memory respectively, the multi-channel selector is connected with the instruction random scheduling module and a random waste instruction injection module respectively, and a random number generating module is connected with the random waste instruction injection module, the instruction random scheduling module and the random flowing water section delay module respectively. The side-channel attack resisting processor architecture enables a specific operation execution time point of side-channel attack not to be confirmed through an instruction random scheduling and out-of-order execution mode, a random waste instruction injection mode, a random flowing water section operation delay mode and the like, accordingly enables statistic analysis to be difficult to perform, greatly enhances the side-channel attack resisting capacity of a system and avoids cryptographic algorithm decryption caused by leakage of side-channel information.
Owner:戴葵
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com