Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
85 results about "Integrity assessment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
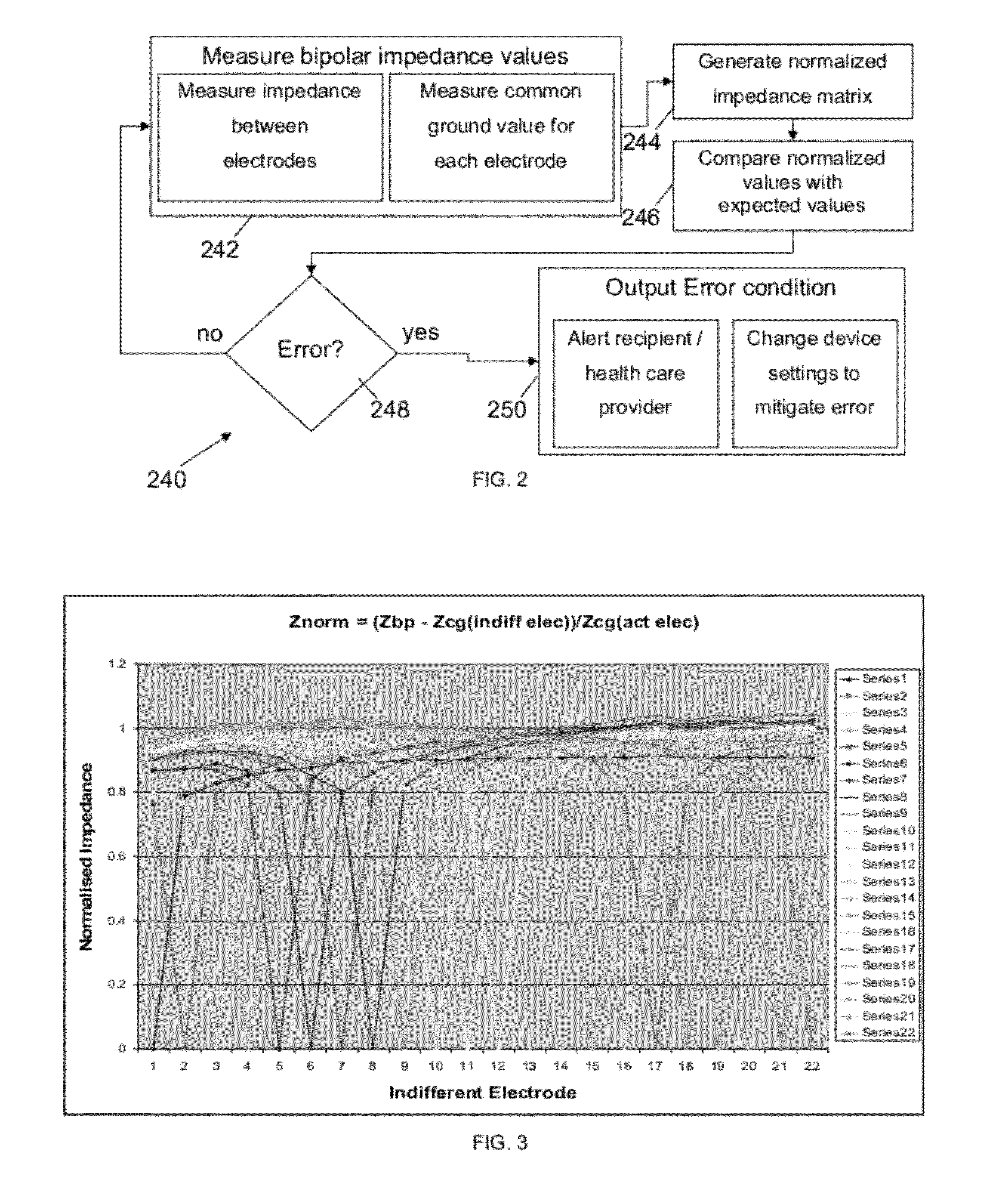
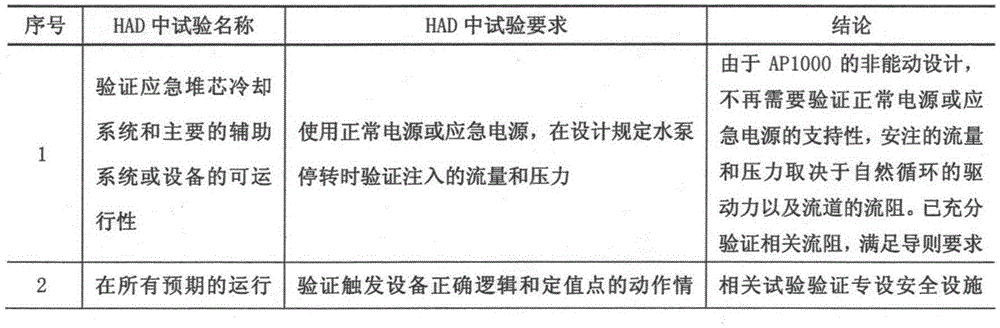
Integrity Assessment - Providing visibility, maximizing efficiencies and ensuring integrity. As pipelines age, the threat to integrity rises and without a high level of understanding of the pipeline’s condition, the risk of failure is high.
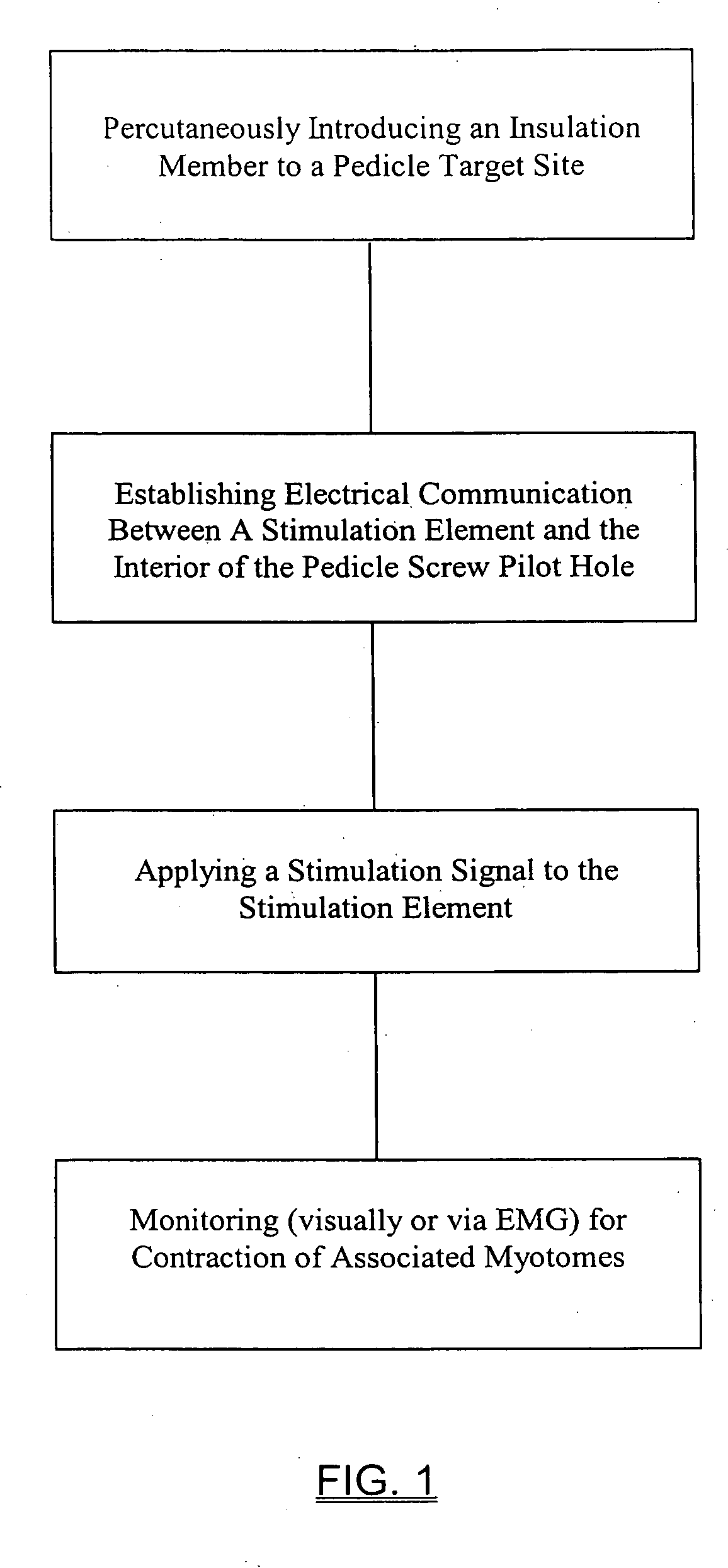
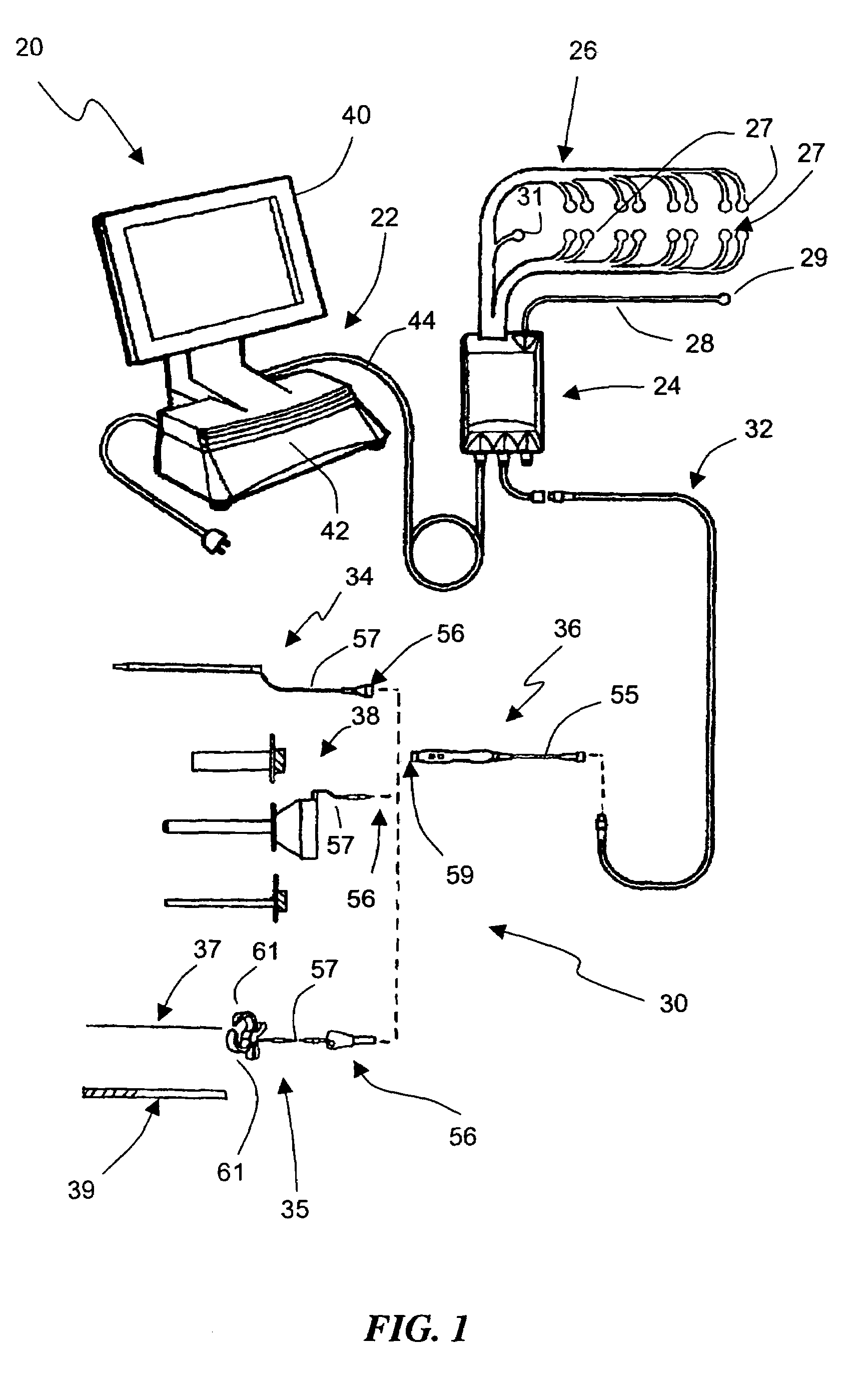
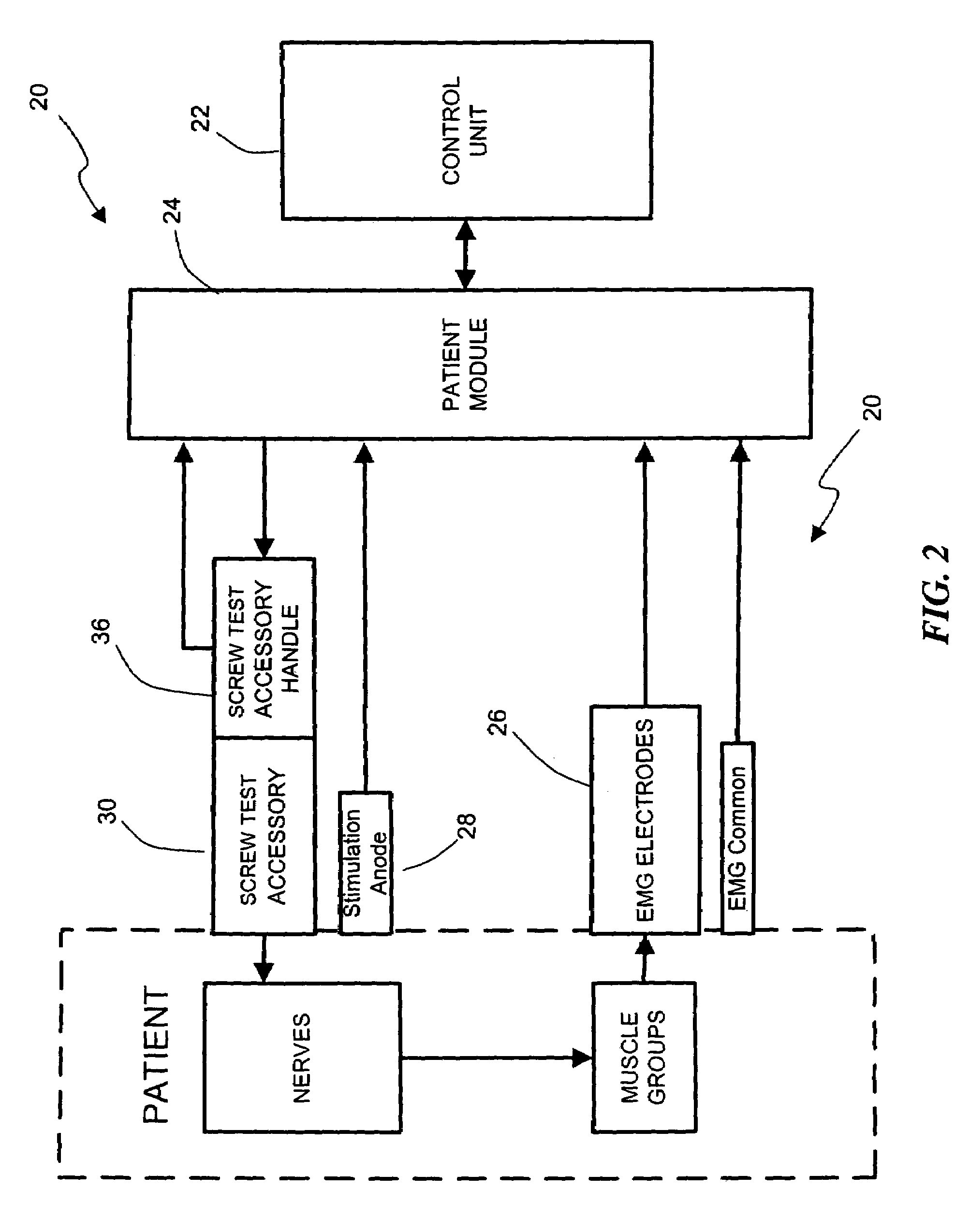
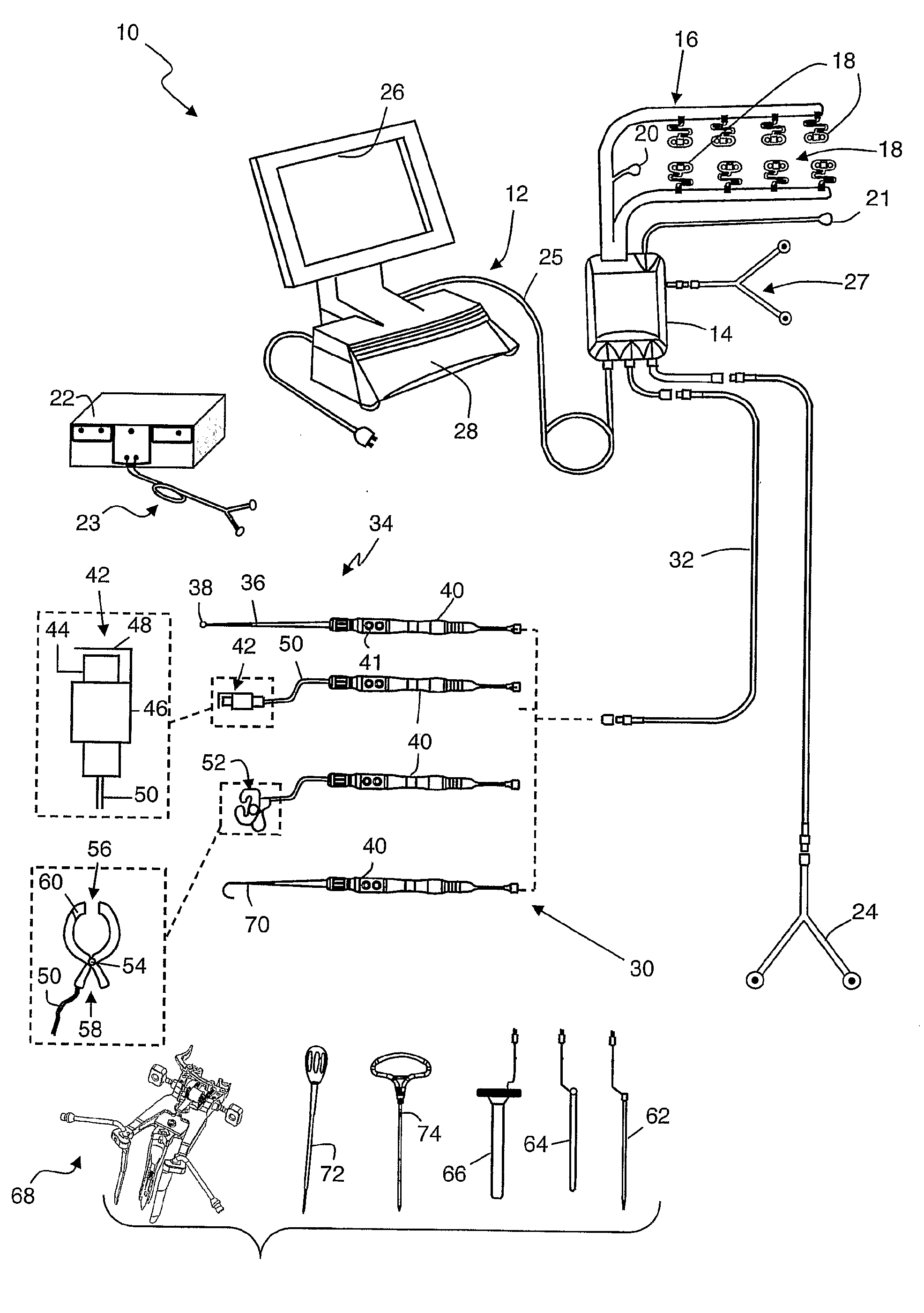
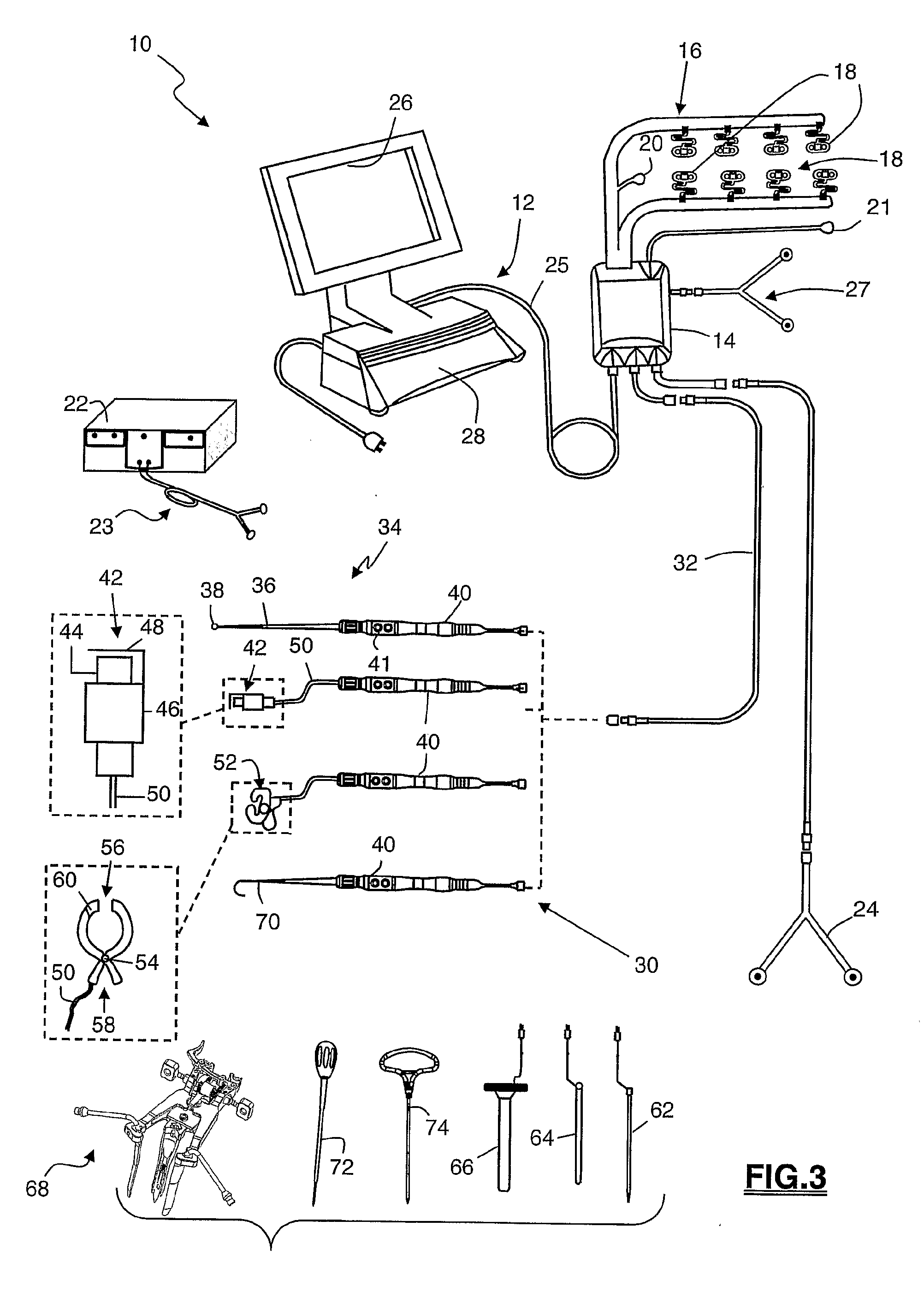
System and methods for performing dynamic pedicle integrity assessments
ActiveUS20060025703A1Overcomes drawbackSurgical needlesInternal electrodesIntegrity assessmentEngineering
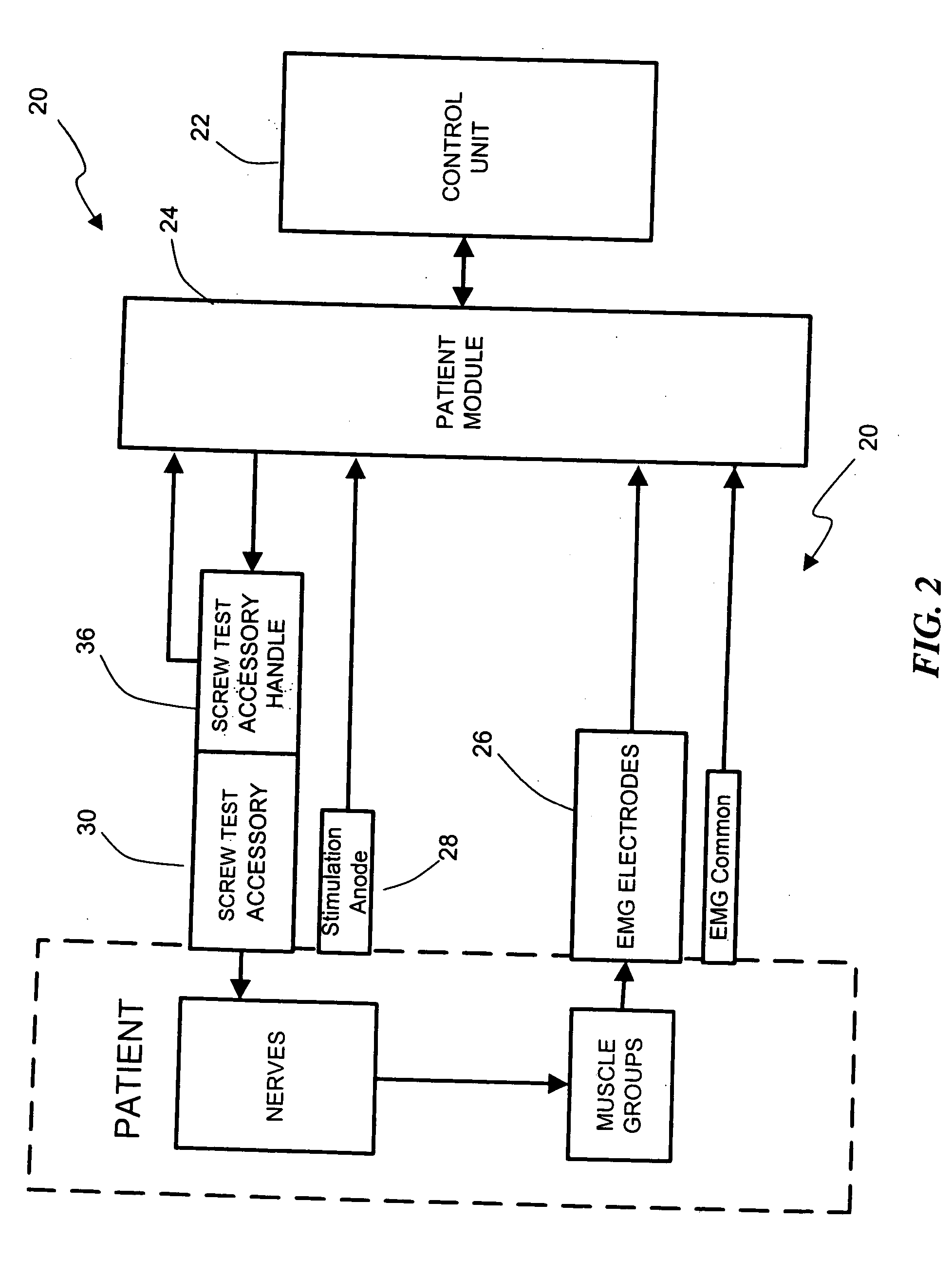
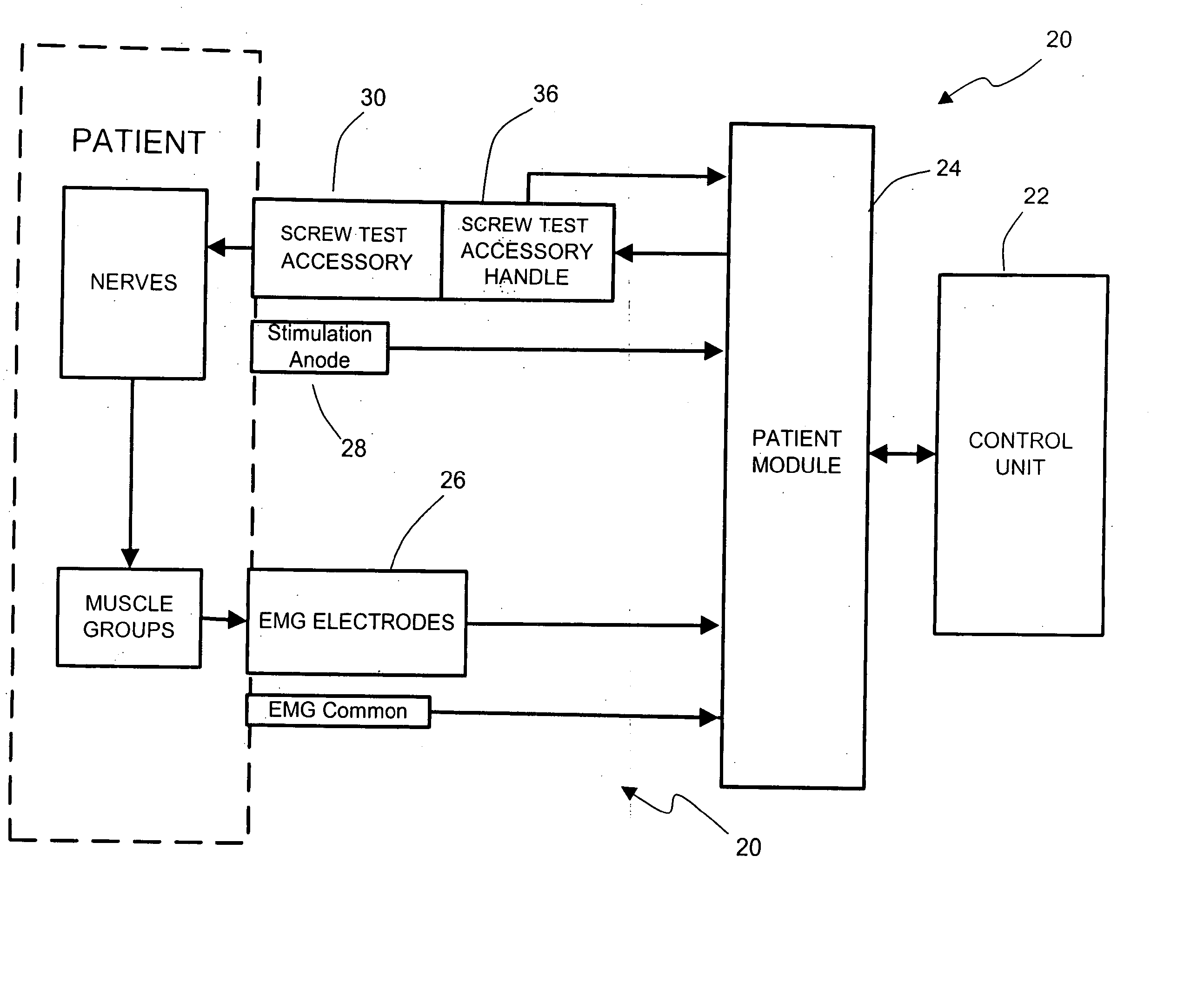
The present invention involves systems and related methods for performing dynamic pedicle integrity assessments involving the use of neurophysiology.
Owner:NUVASIVE
System and methods for performing percutaneous pedicle integrity assessments
The present invention involves systems and related methods for performing percutaneous pedicle integrity assessments involving the use of neurophysiology.
Owner:NUVASIVE
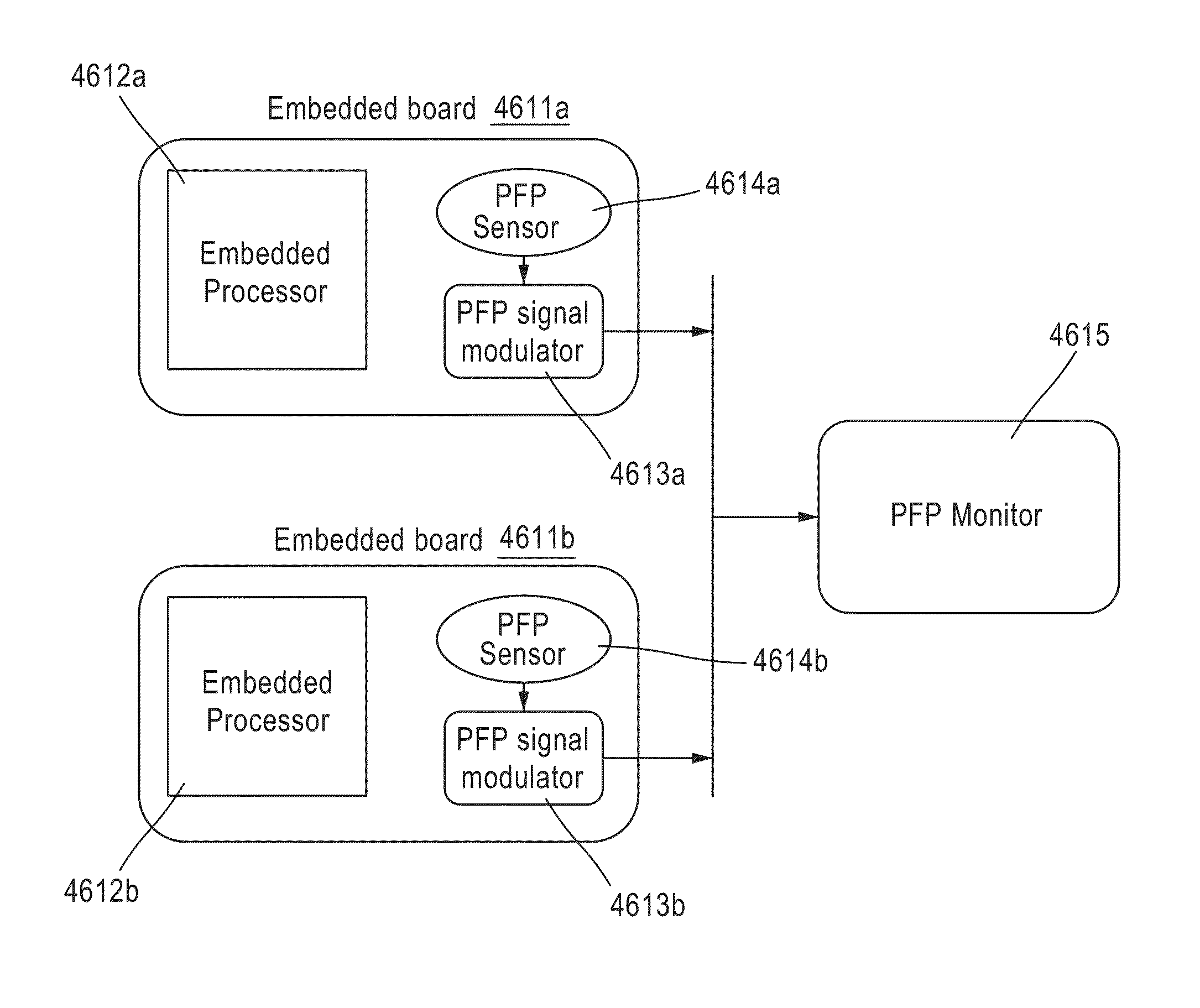
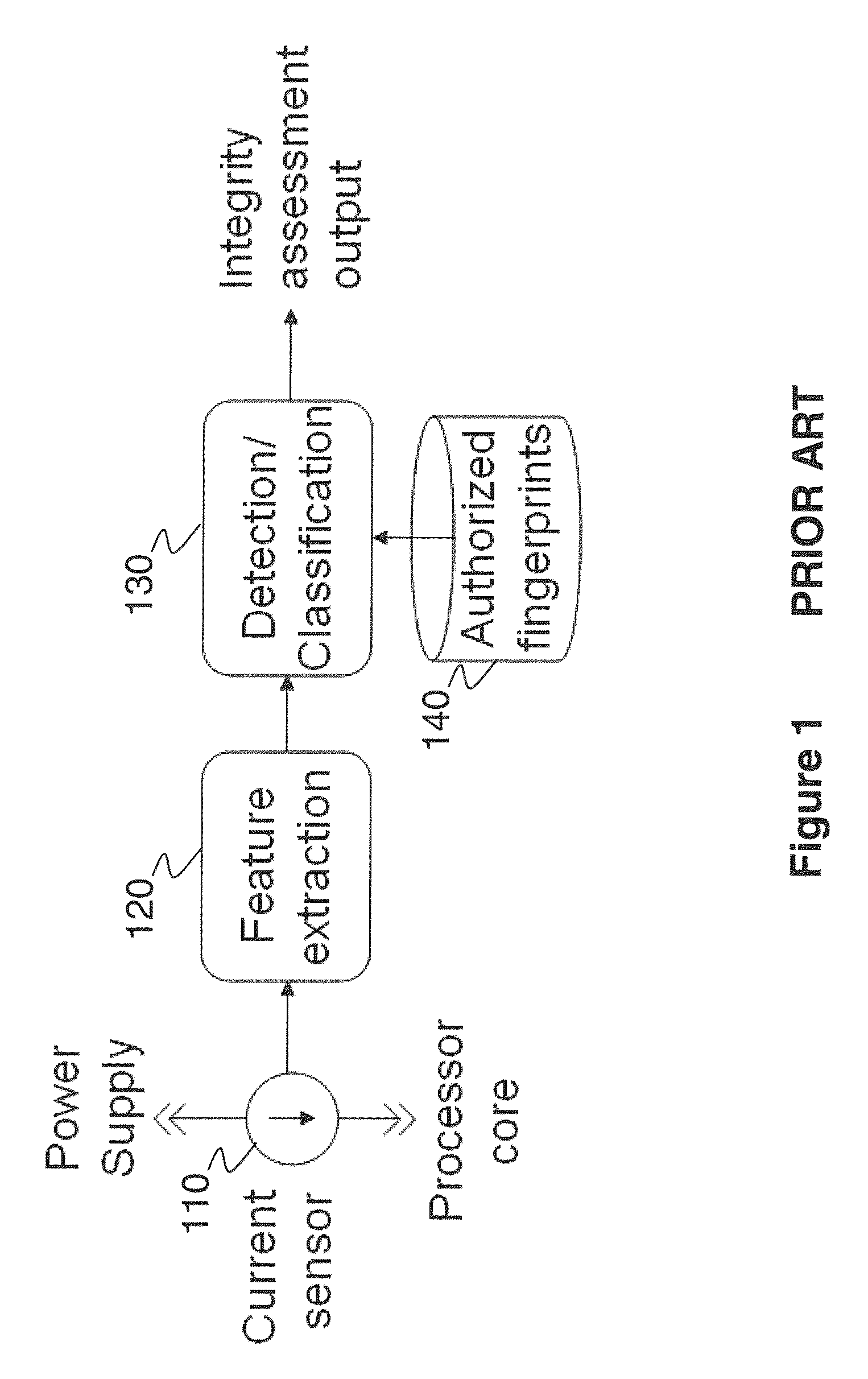
Using Power Fingerprinting (PFP) to Monitor the Integrity and Enhance Security of Computer Based Systems
ActiveUS20130318607A1Enhancing target system execution integrity assessmentImprove abilitiesMemory loss protectionDetecting faulty computer hardwareIntegrity assessmentComputerized system
Procedures are described for enhancing target system execution integrity determined by power fingerprinting (PFP): by integrating PFP into the detection phase of comprehensive defense-in-depth security; by deploying a network of PFP enabled nodes executing untrusted devices with predefined inputs forcing a specific state sequence and specific software execution; by embedding module identification information into synchronization signaling; by combining signals from different board elements; by using malware signatures to enhance PFP performance; by automatic characterization and signature extraction; by providing secure signature updates; by protecting against side-channel attacks; performing real-time integrity assessment in embedded platform by monitoring their dynamic power consumption and comparing it against signatures from trusted code, including pre-characterizing power consumption of the platform by concentrating on trace sections carrying the most information about the internal execution status; by using PFP from sequence of bit transitions to detect deviations from authorized execution of software in a digital processor.
Owner:VIRGINIA TECH INTPROP INC
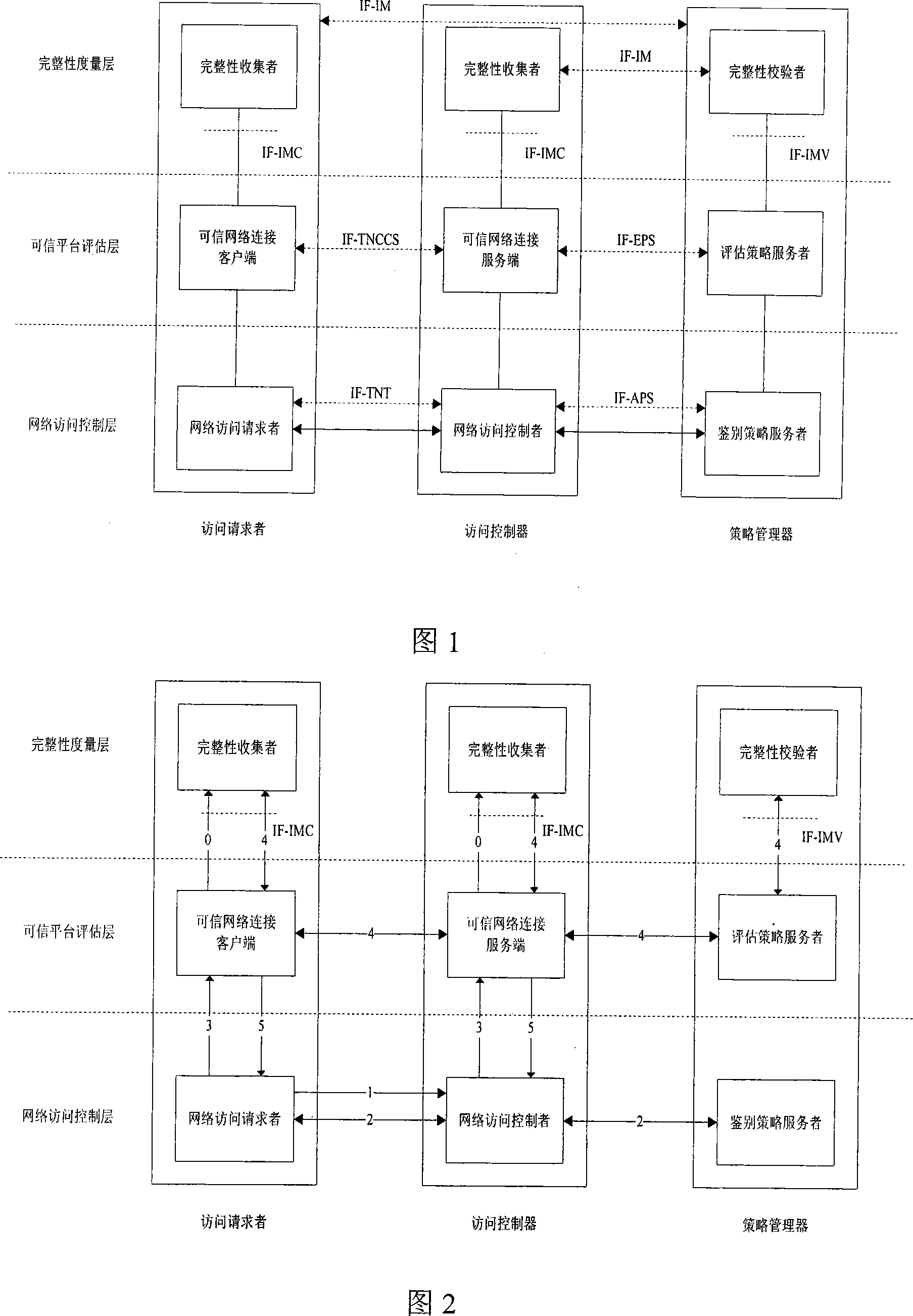
Reliable network access framework
InactiveCN101136928AEasy to manage centrallyImprove distributionData switching by path configurationNetwork connectionsIntegrity assessmentExtensibility
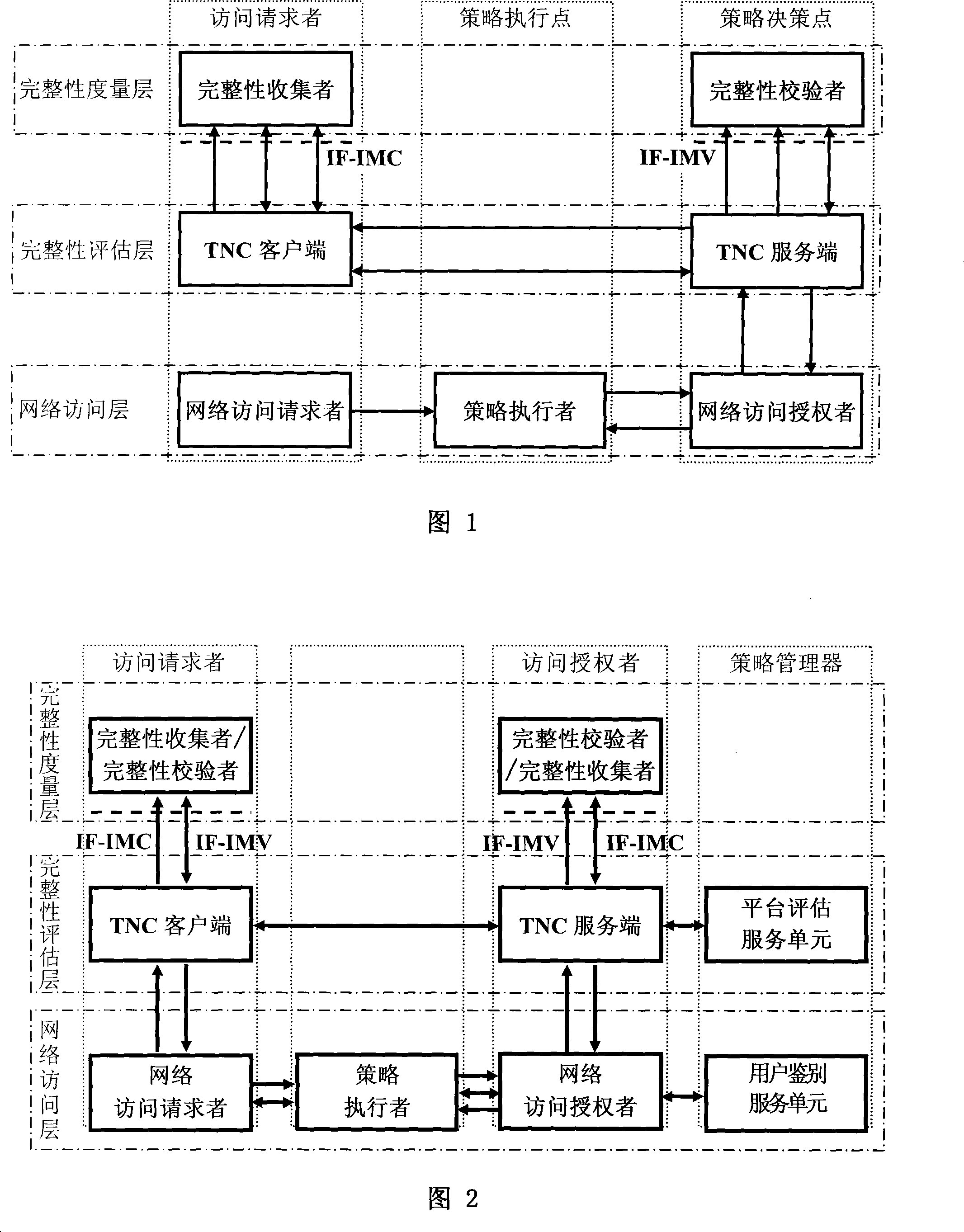
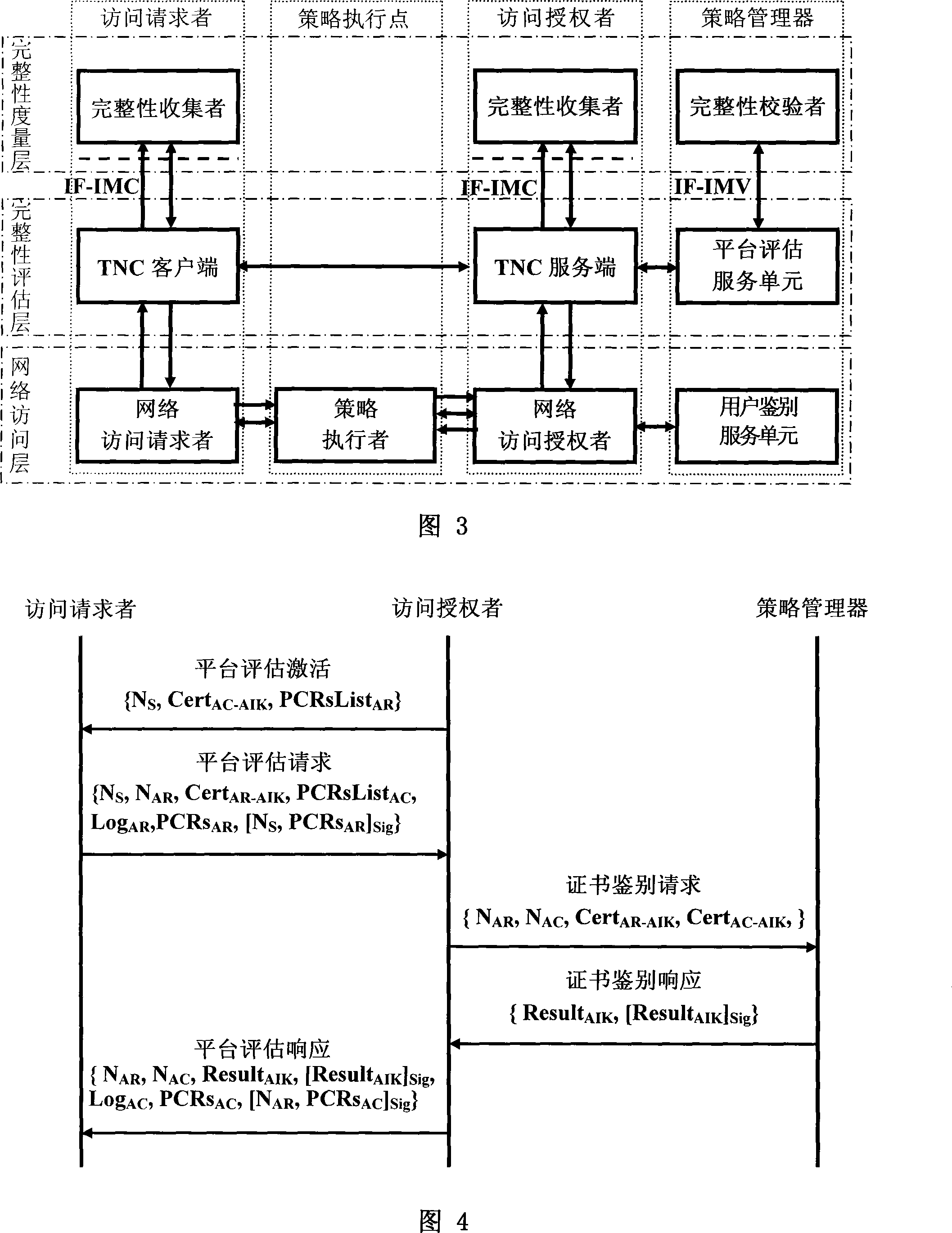
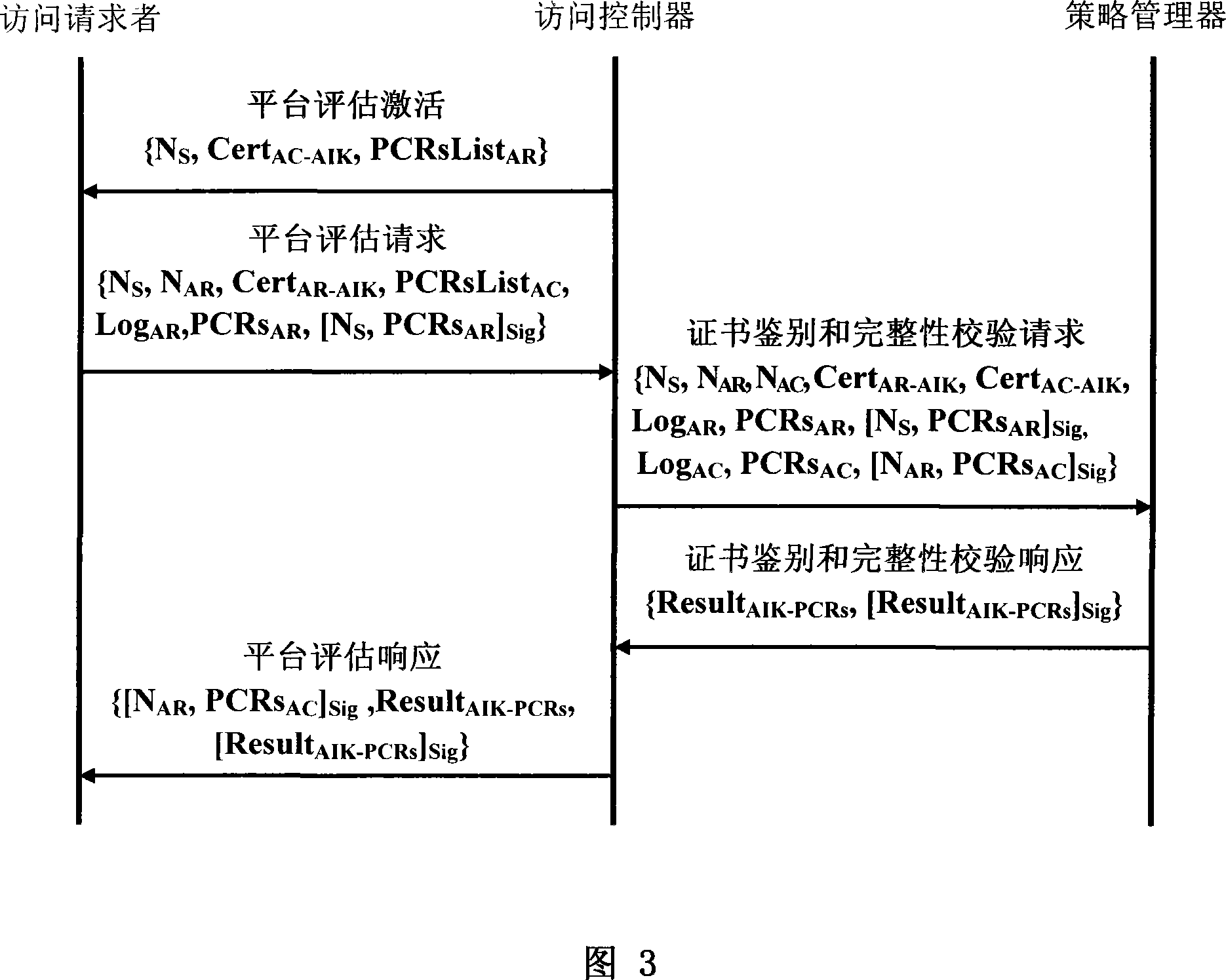
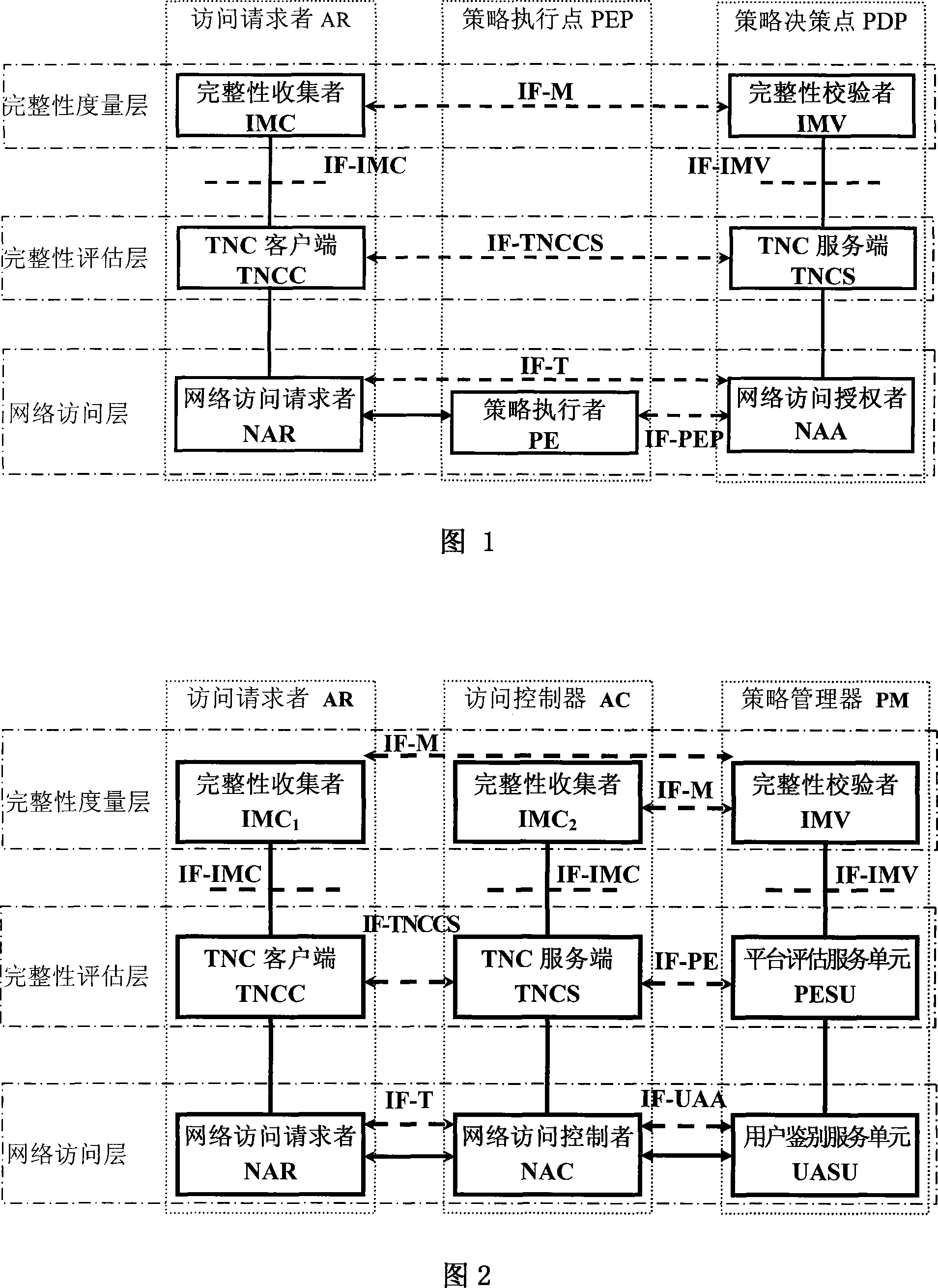
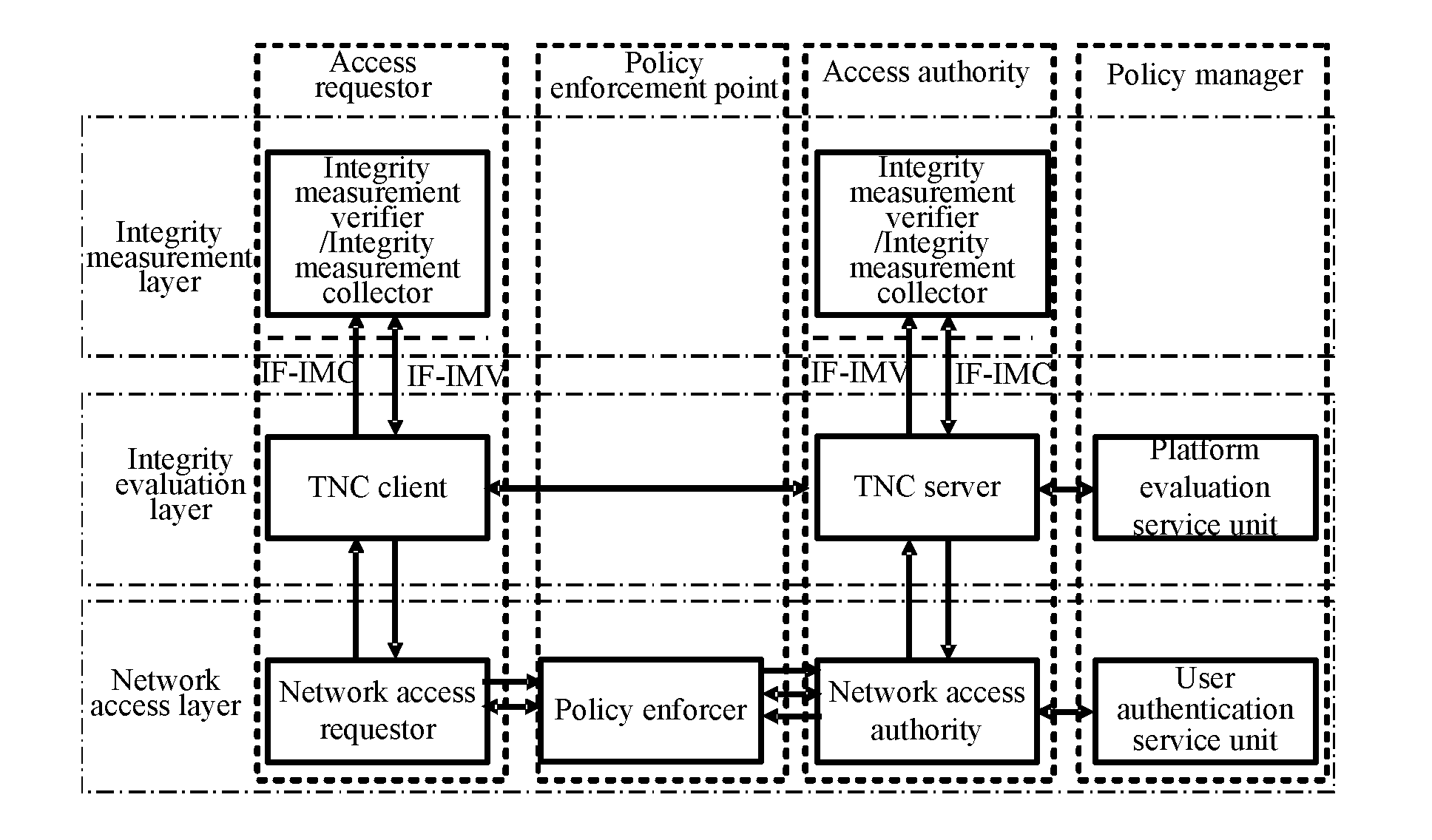
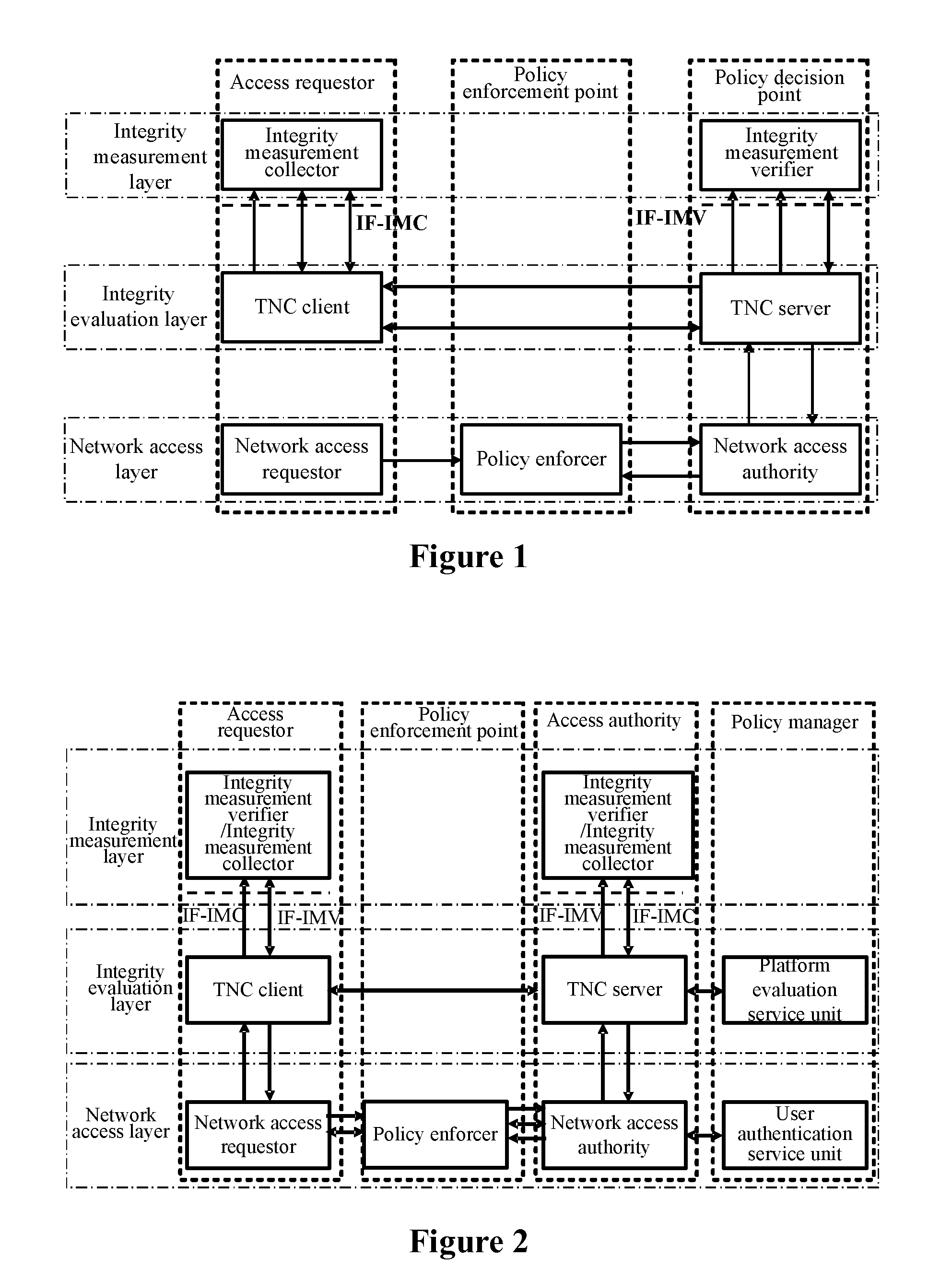
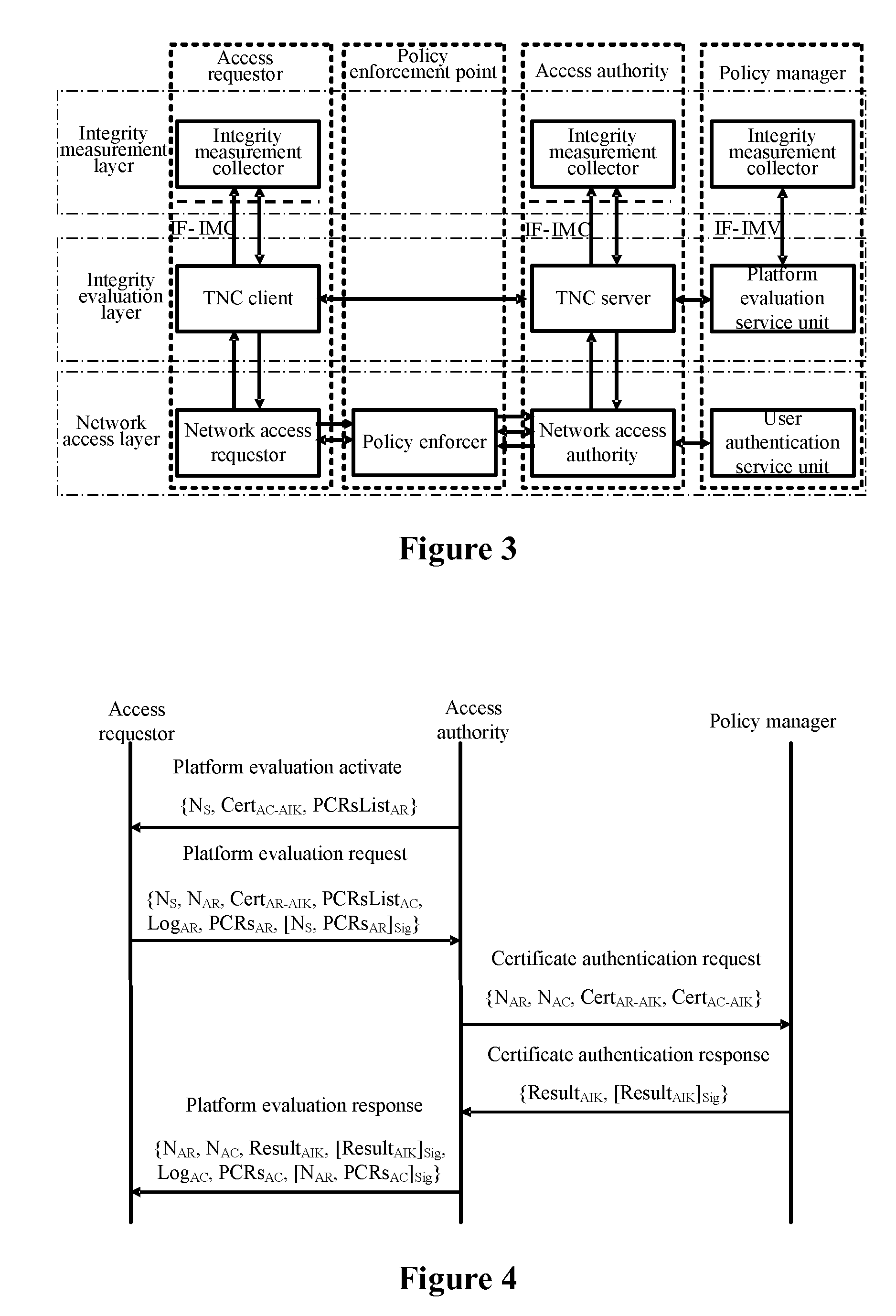
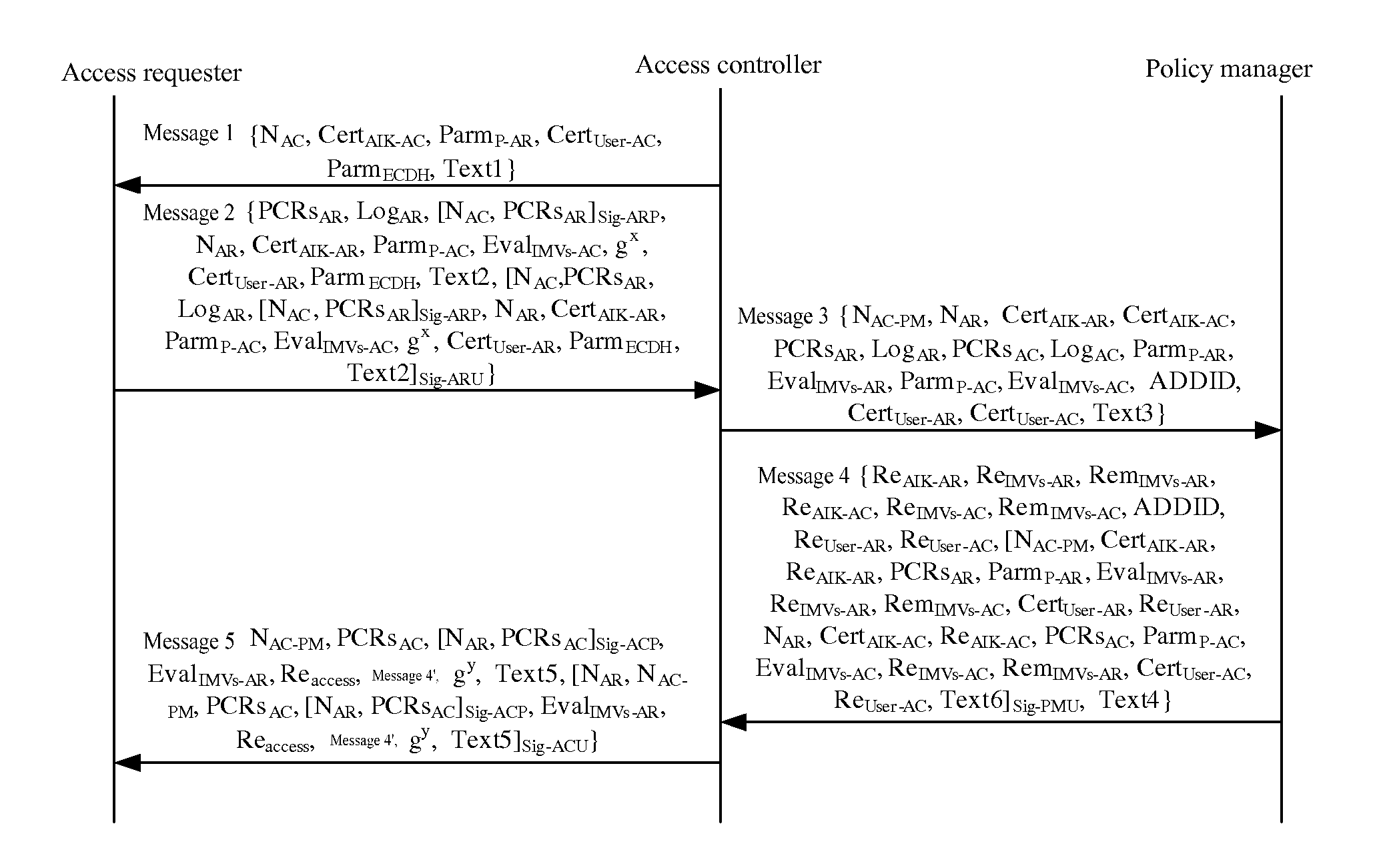
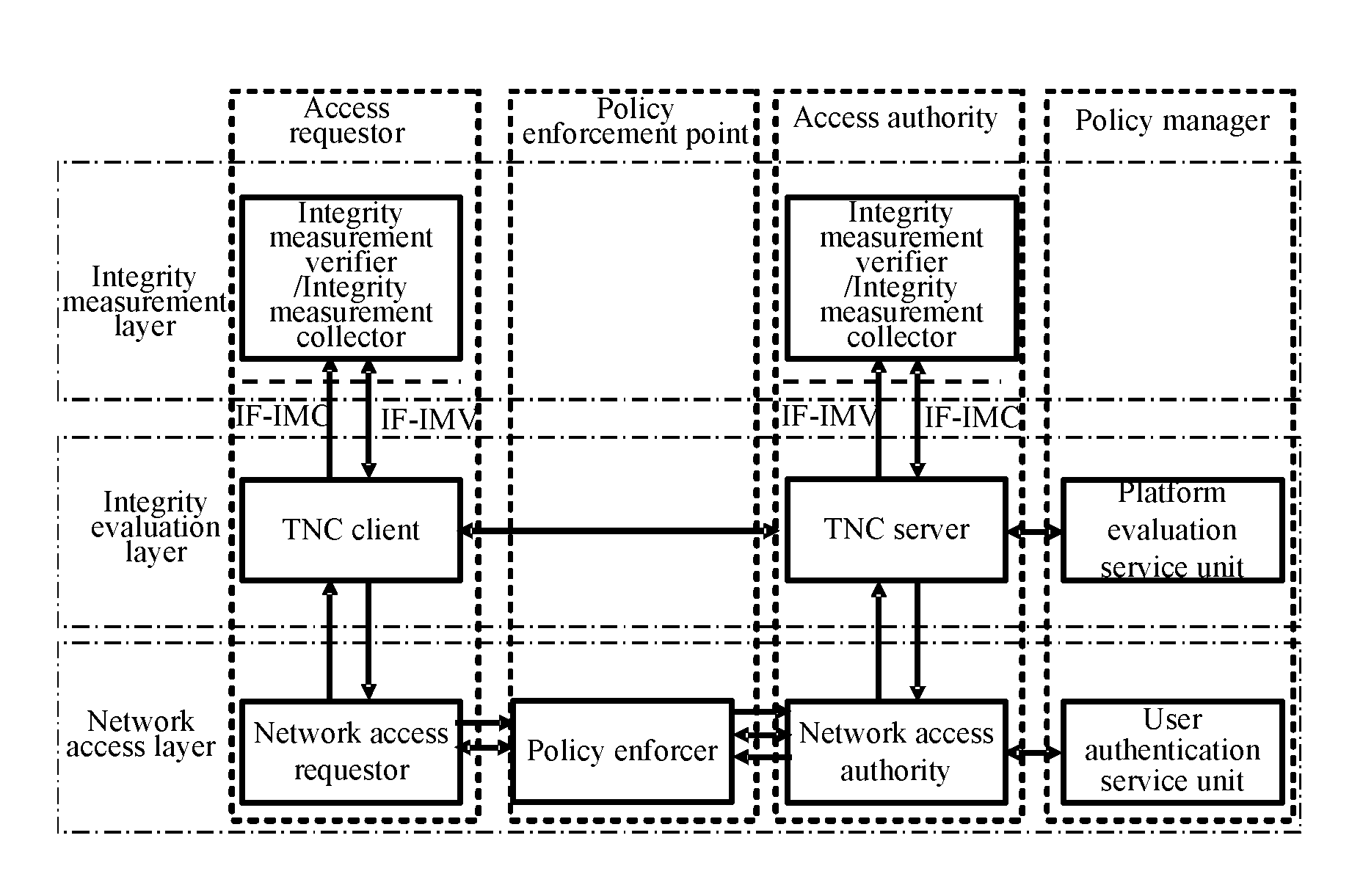
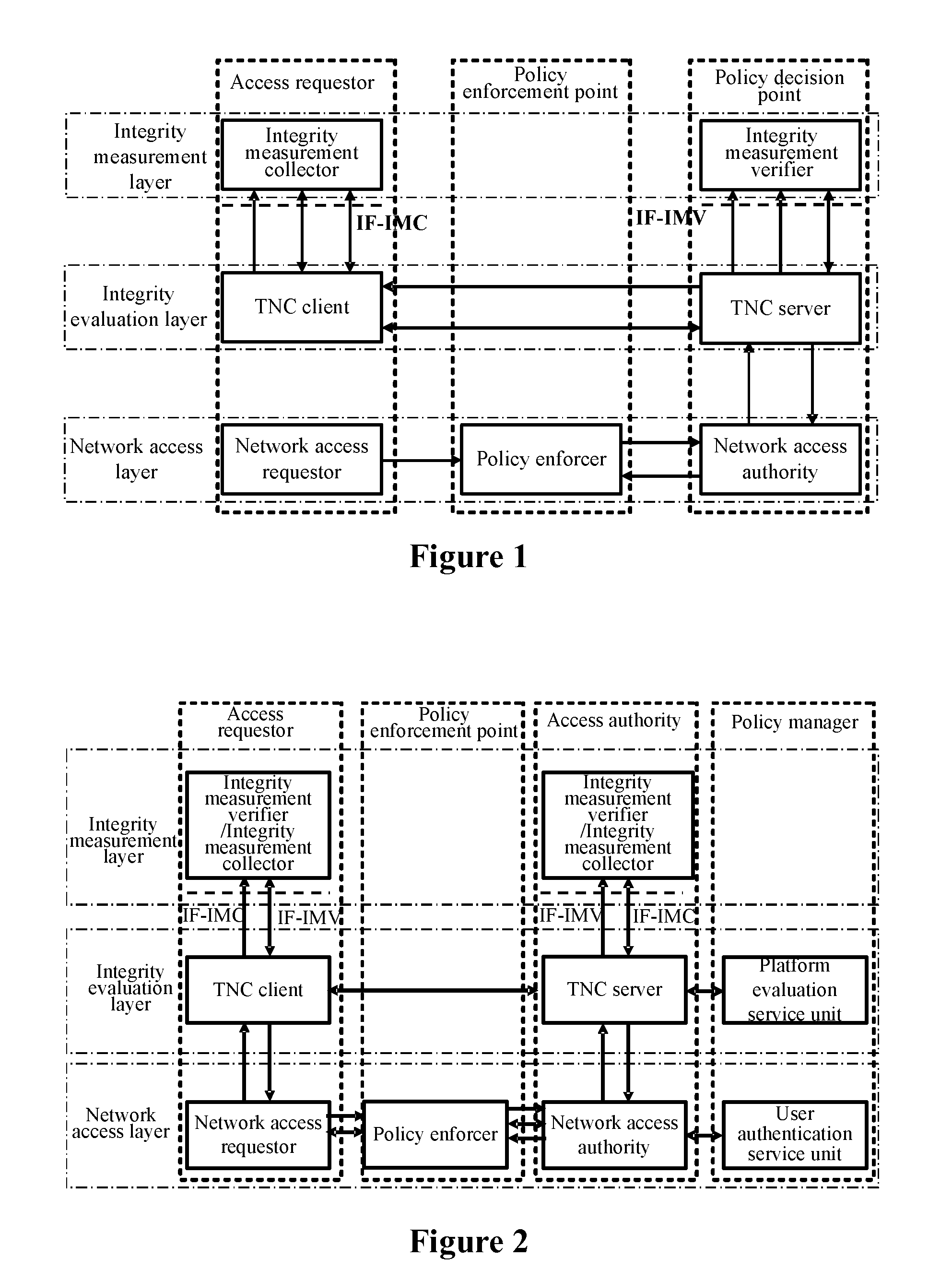
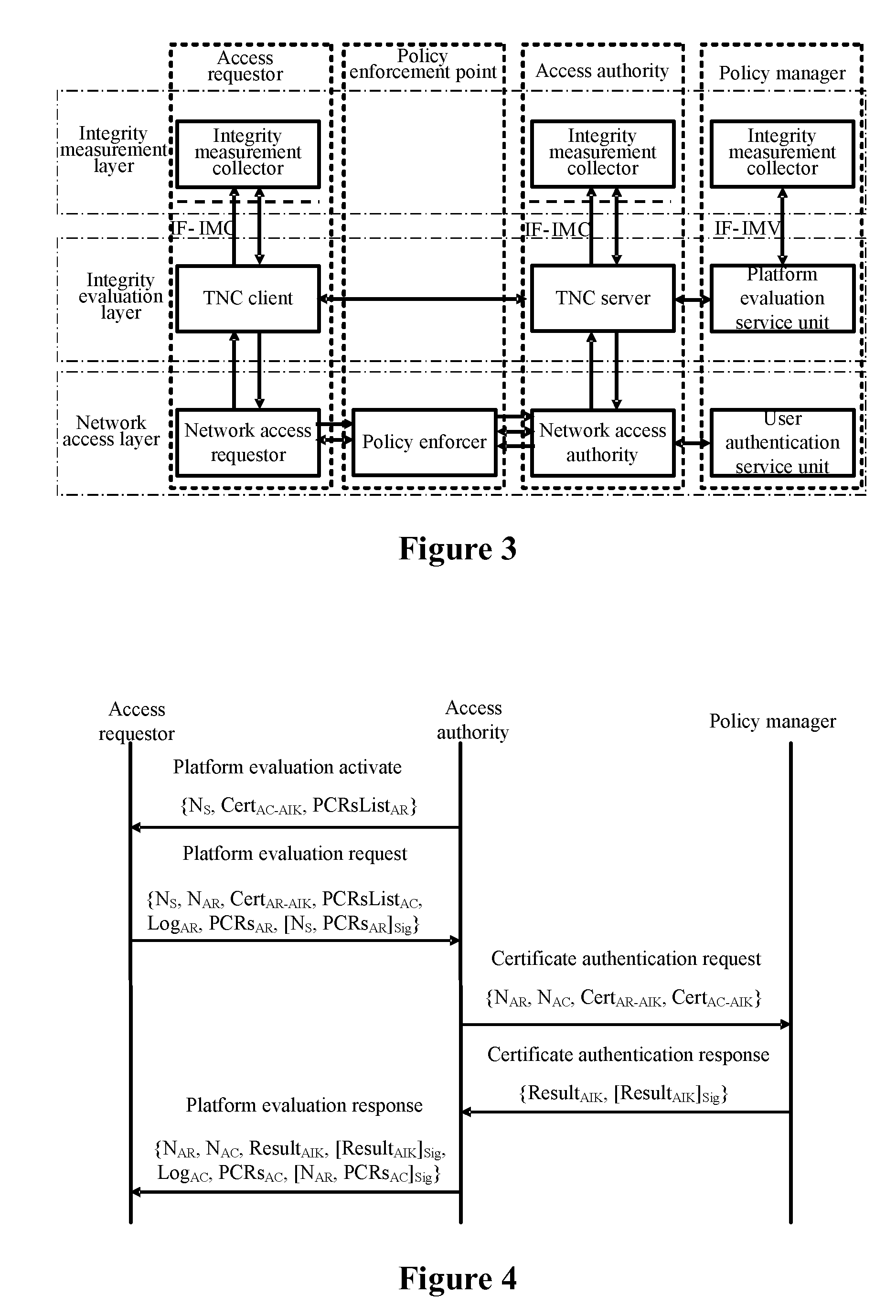
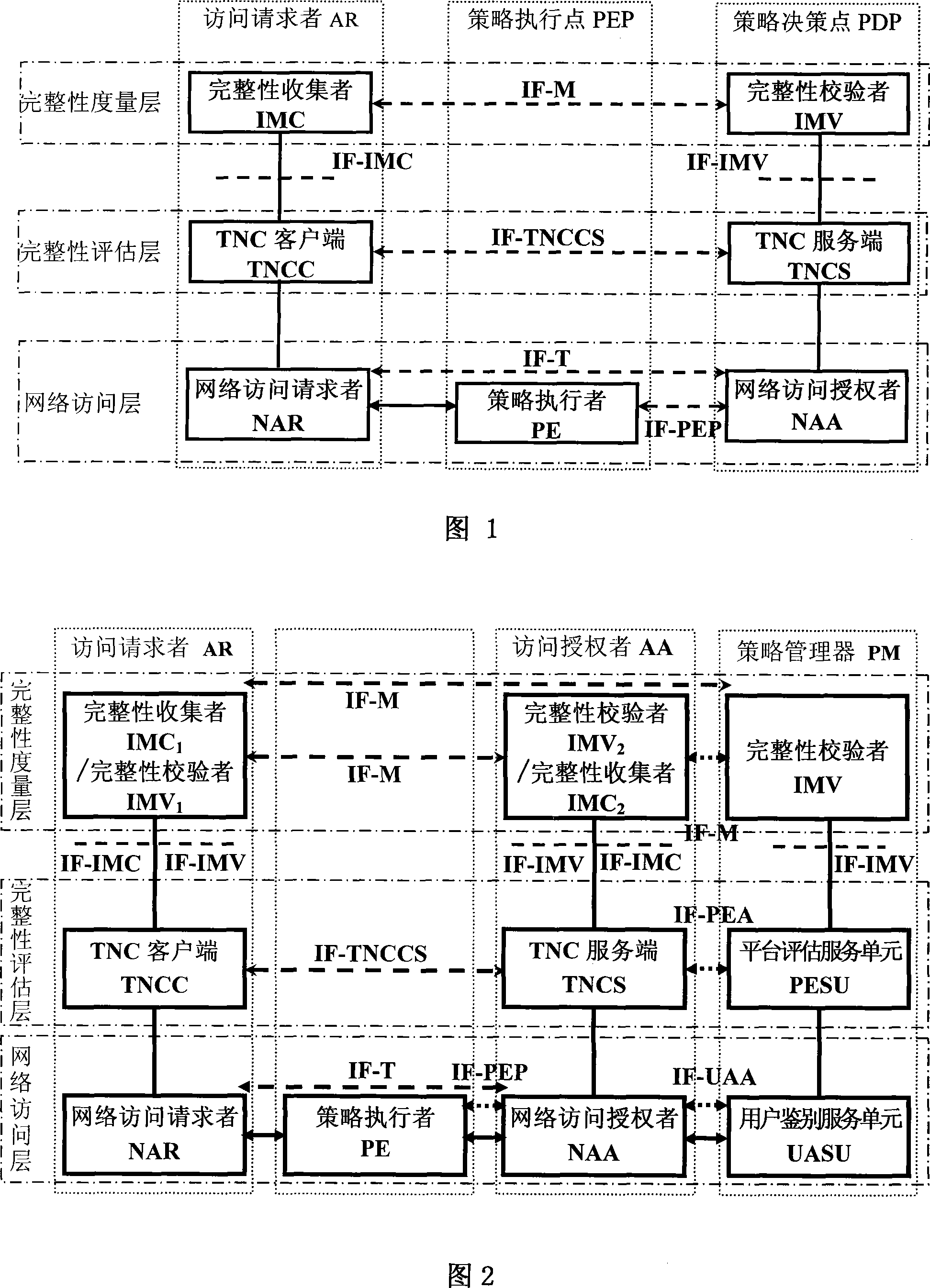
Frame of the invention includes three entities: accessing requestor, accessing controller, and strategy manager. The strategy manager manages the accessing requestor and the accessing controller as well as implements bidirectional user ID authentication between them, and evaluates integrality of platform. Based on decision made from the strategy manager, the accessing requestor and the accessing controller control local ports. Before terminal is connected to network, trusty network connection architecture (TNCA) measures state of platform. Based on secure protocol of trusty third party, the invention implements the said authentication and evaluation of platform so as to guarantee security of TNCA. Introducing strategy manager simplifies key management of the architecture, raises extensibility of the architecture. Features are: higher security for evaluating integrality of platform, centralized verifying integrality, and higher universality.
Owner:BEIJING UNIV OF TECH
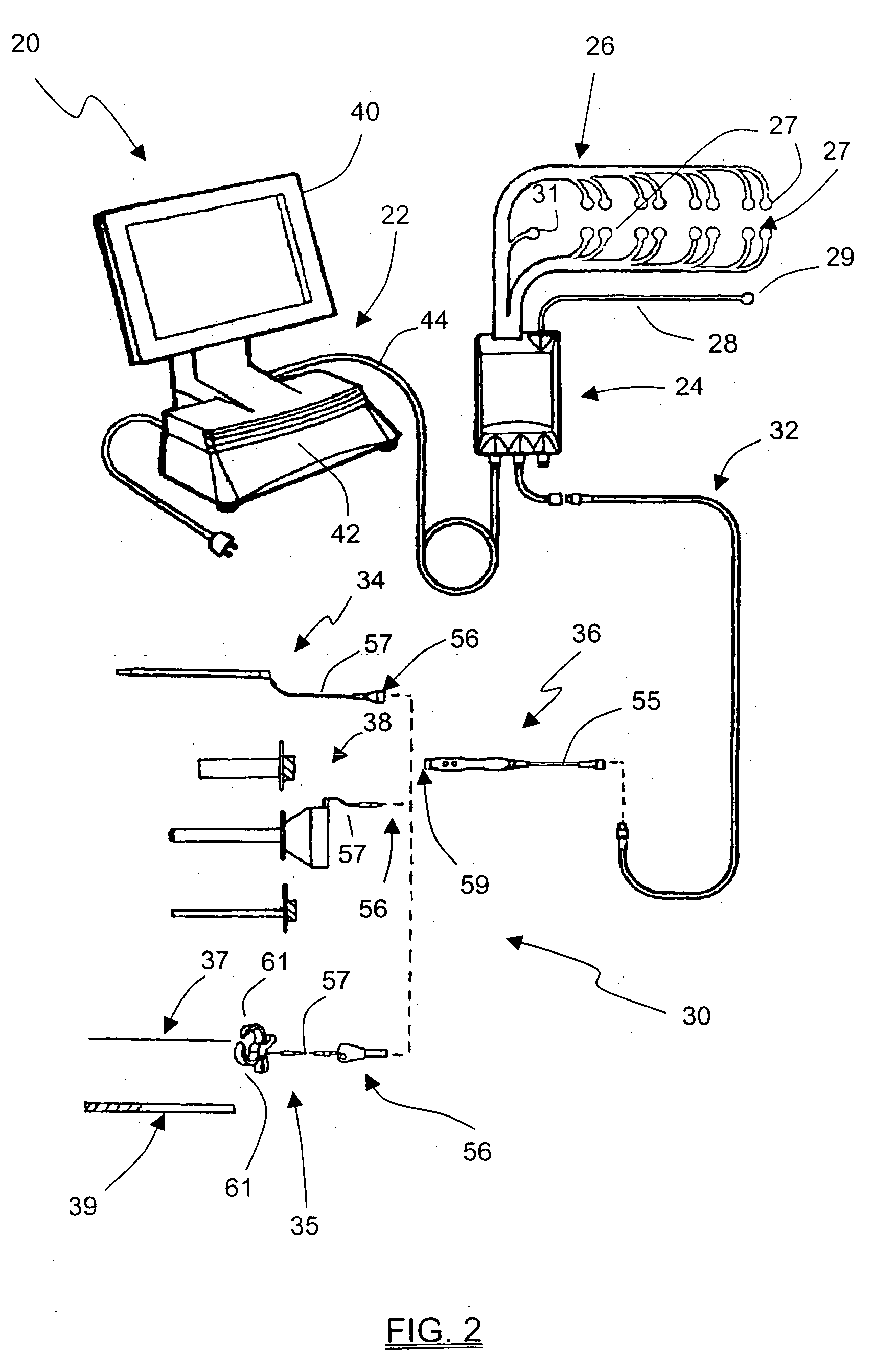
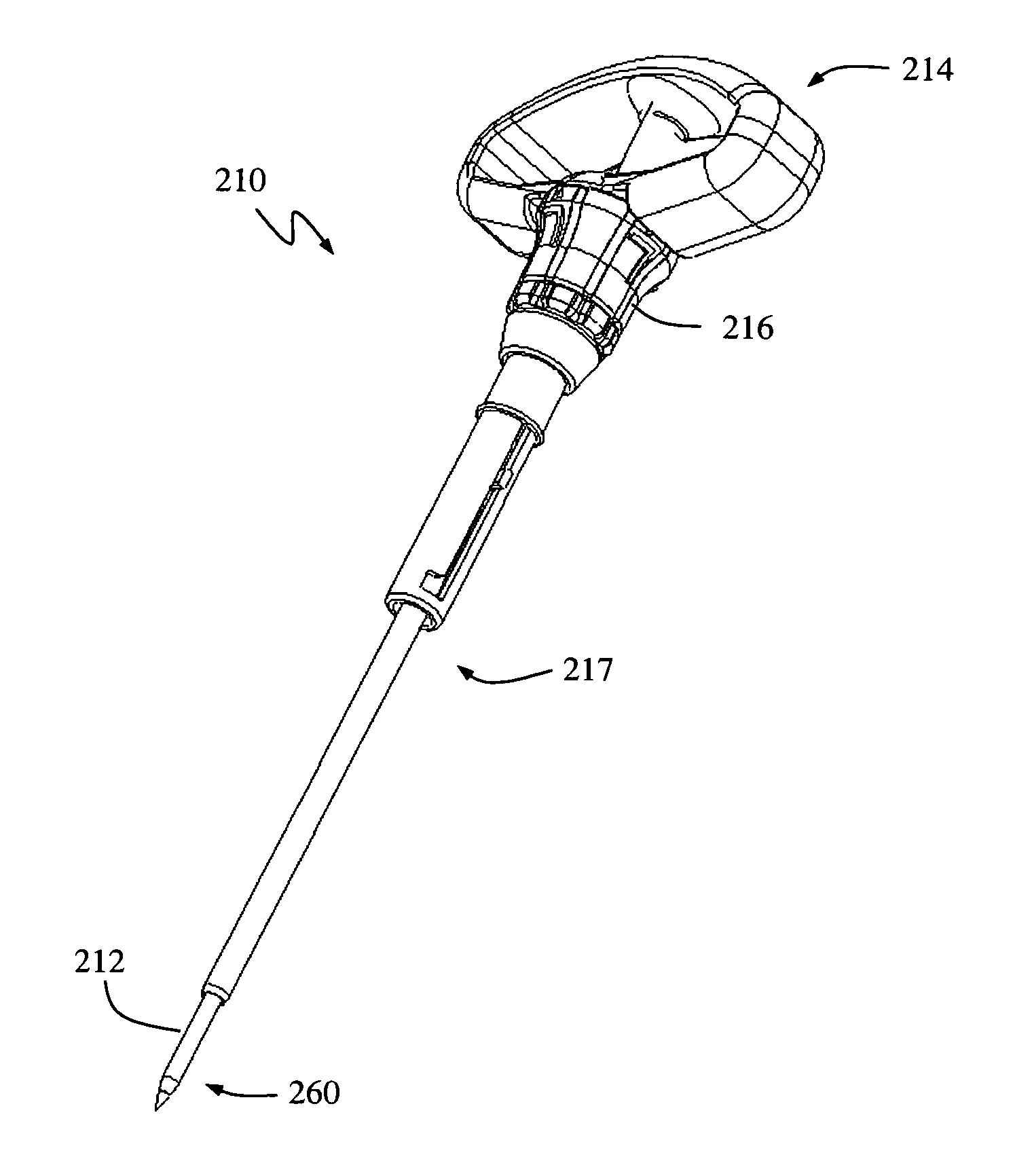
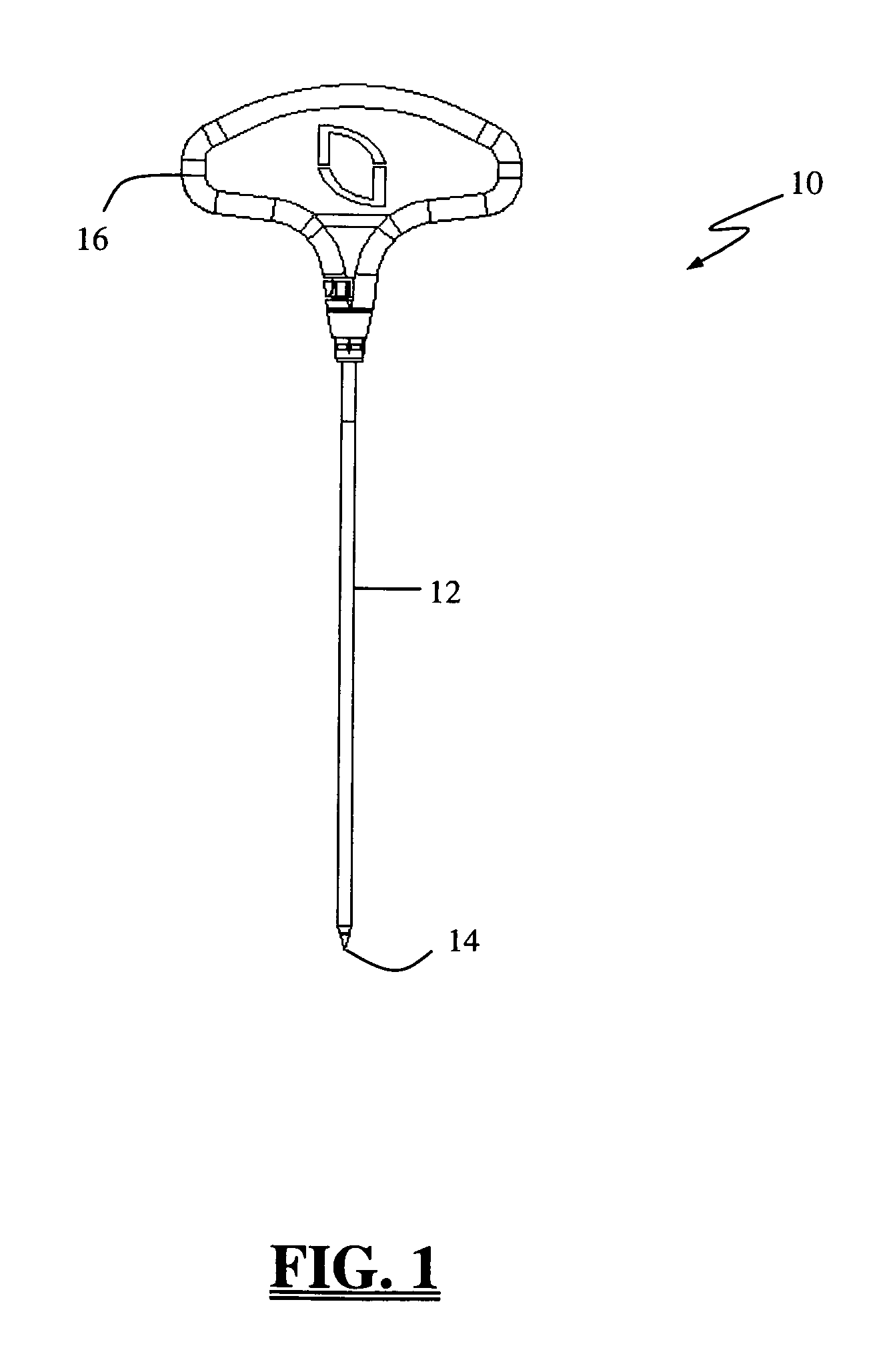
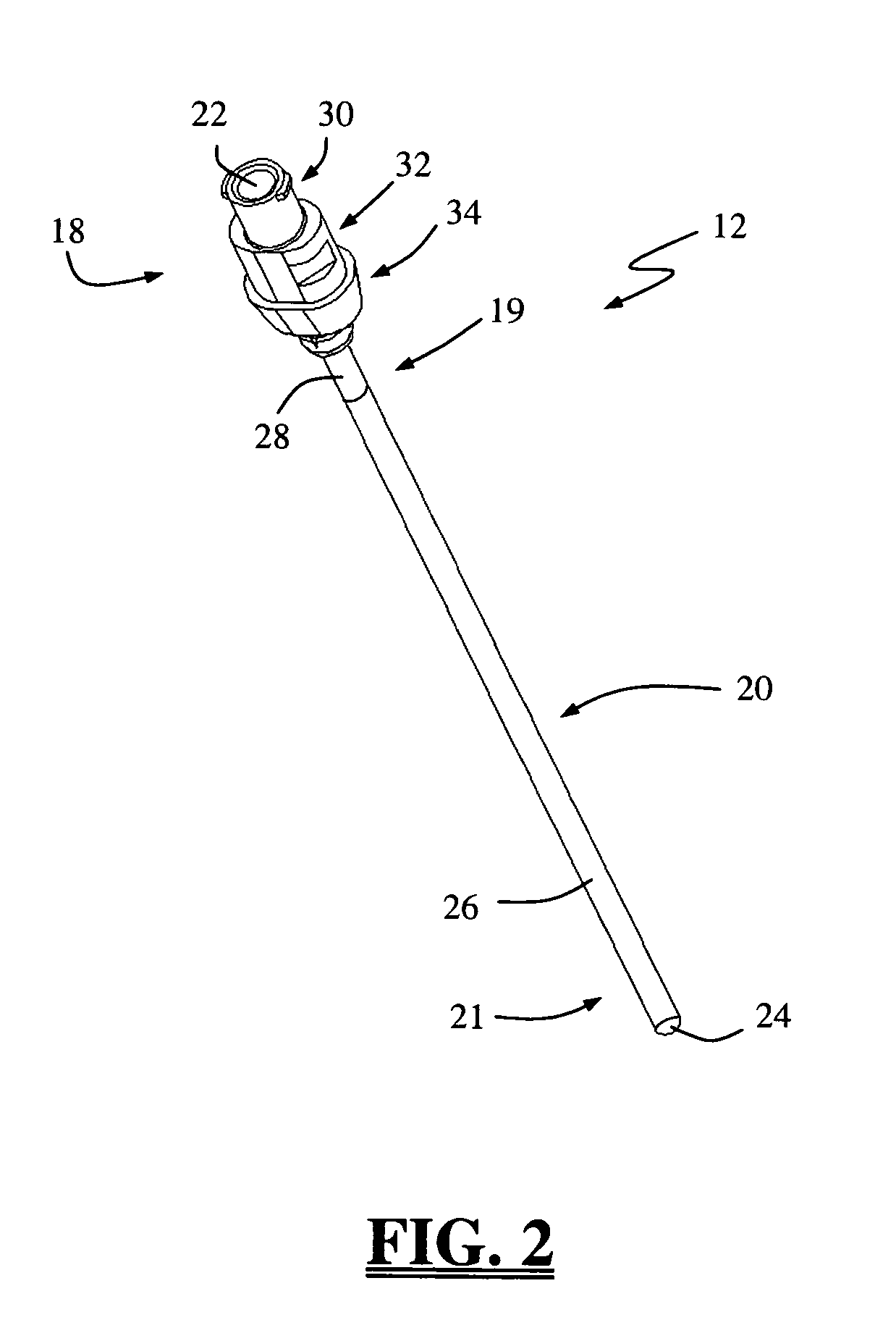
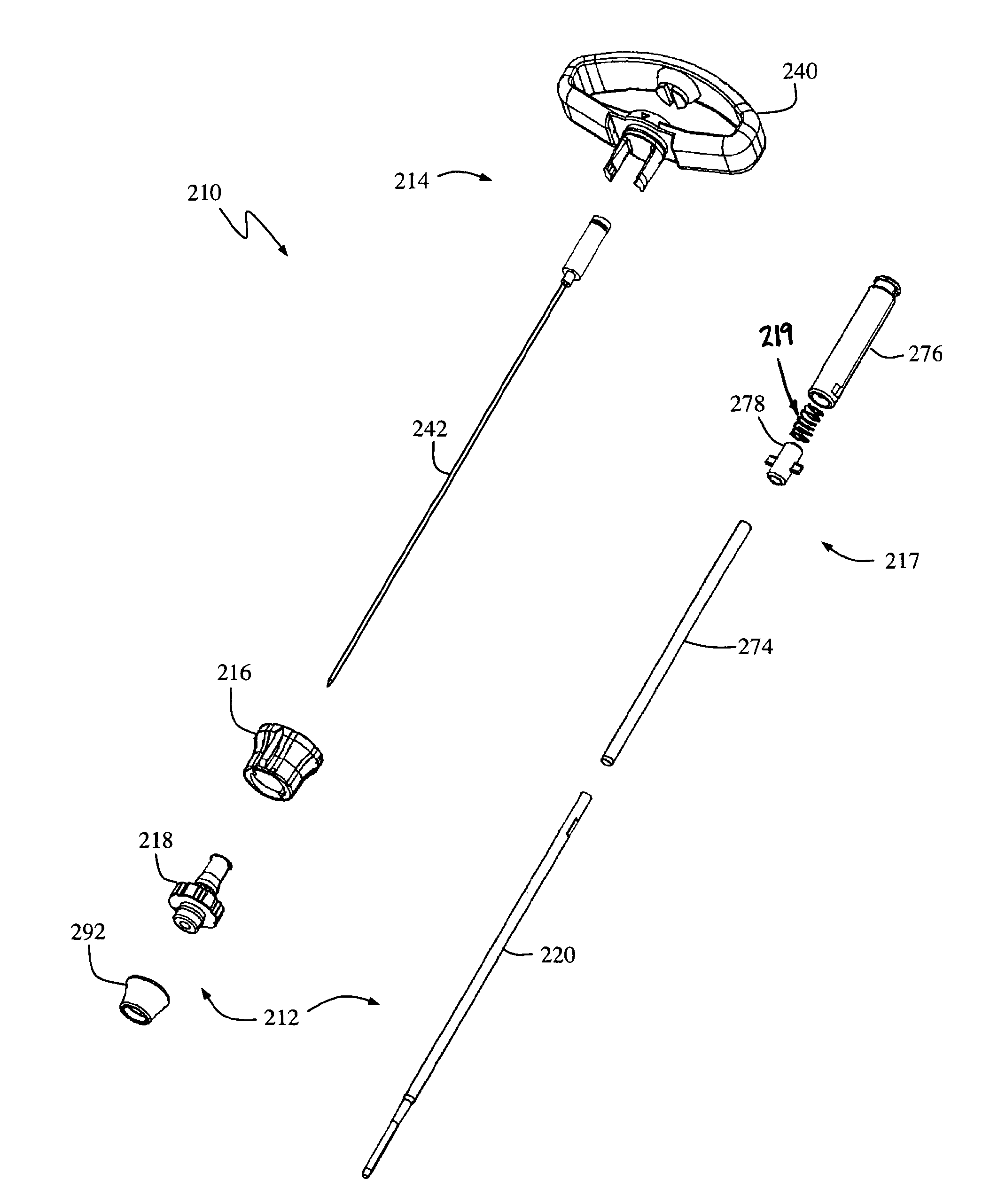
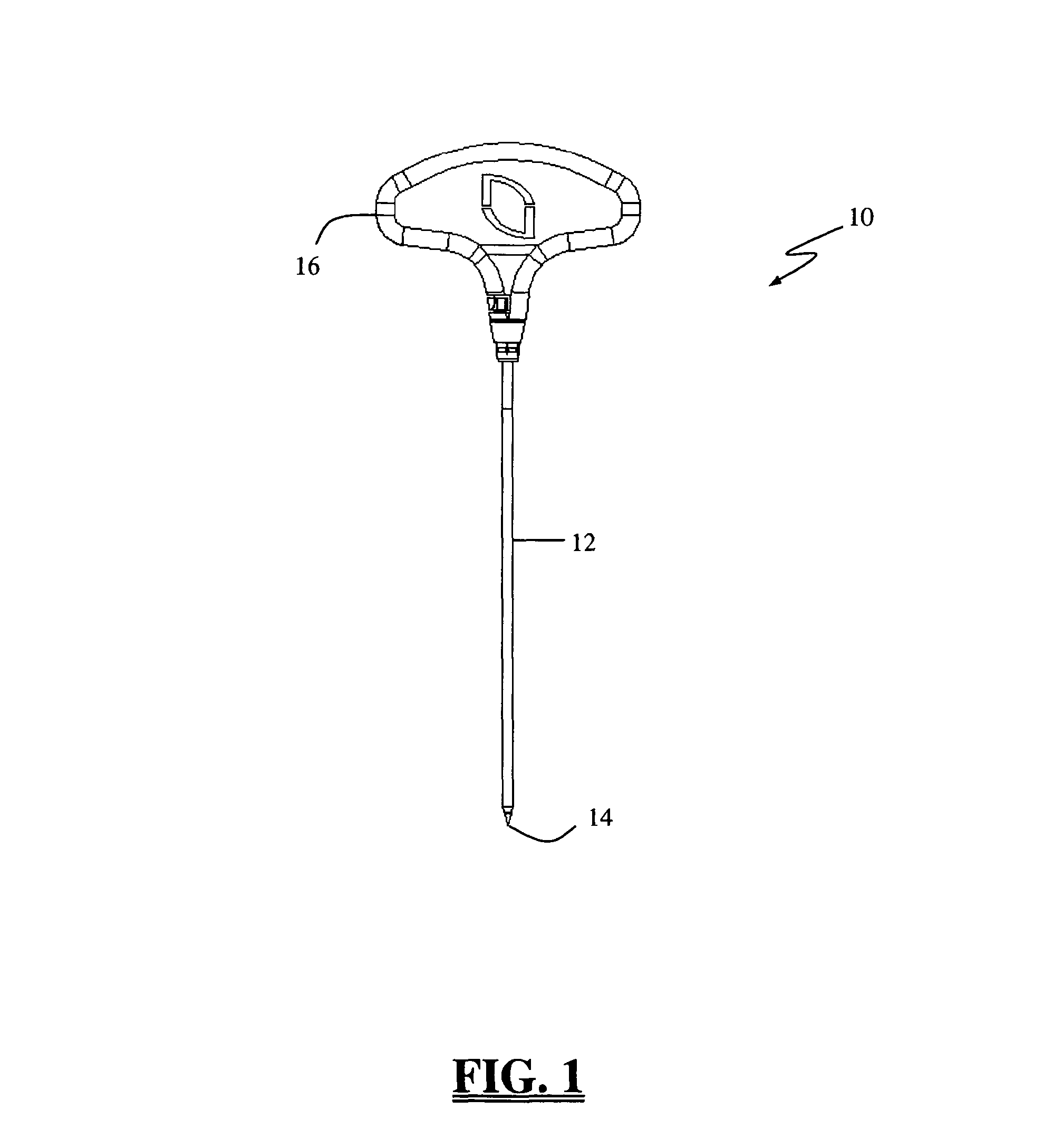
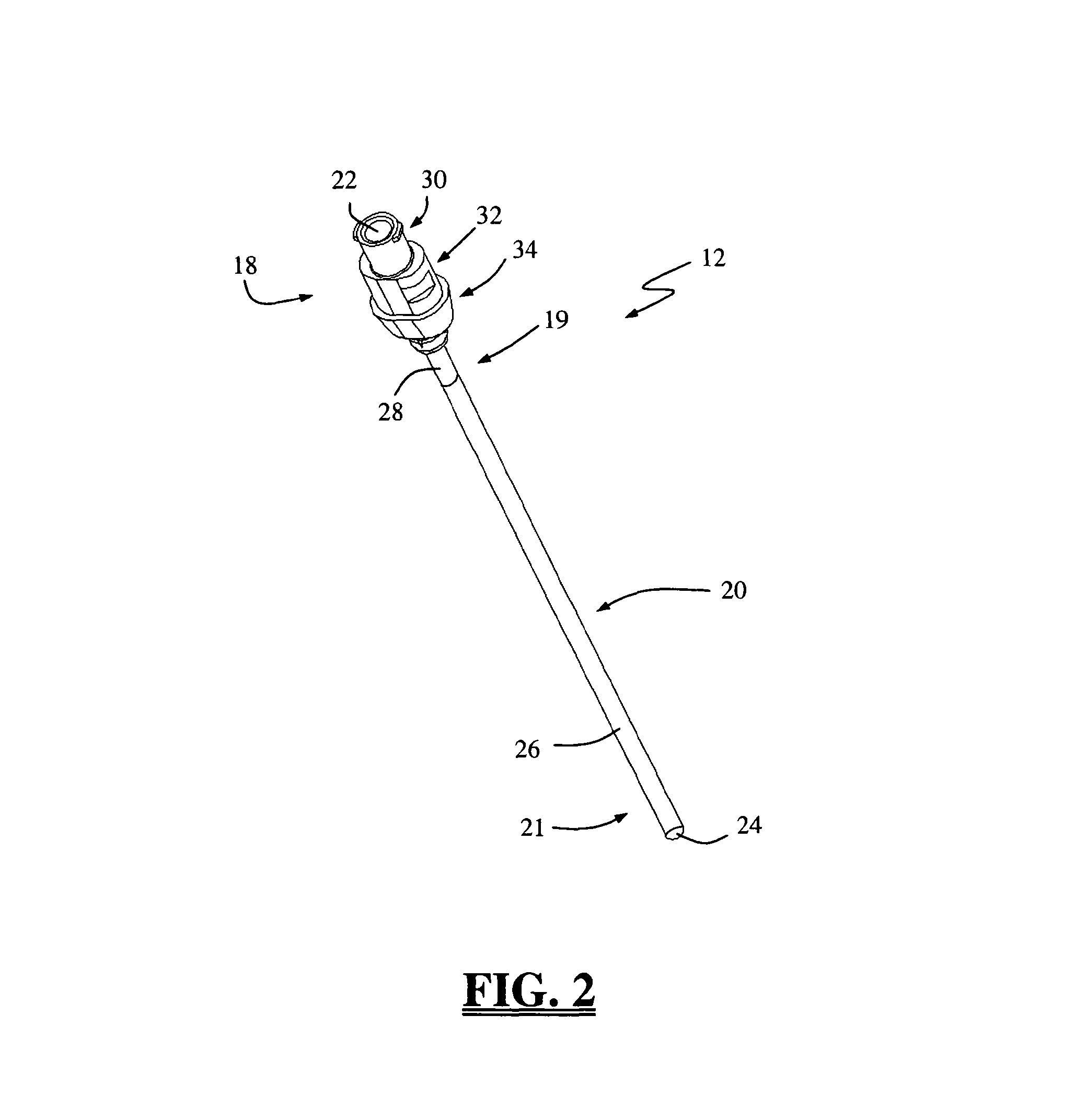
Insulated pedicle access system and related methods
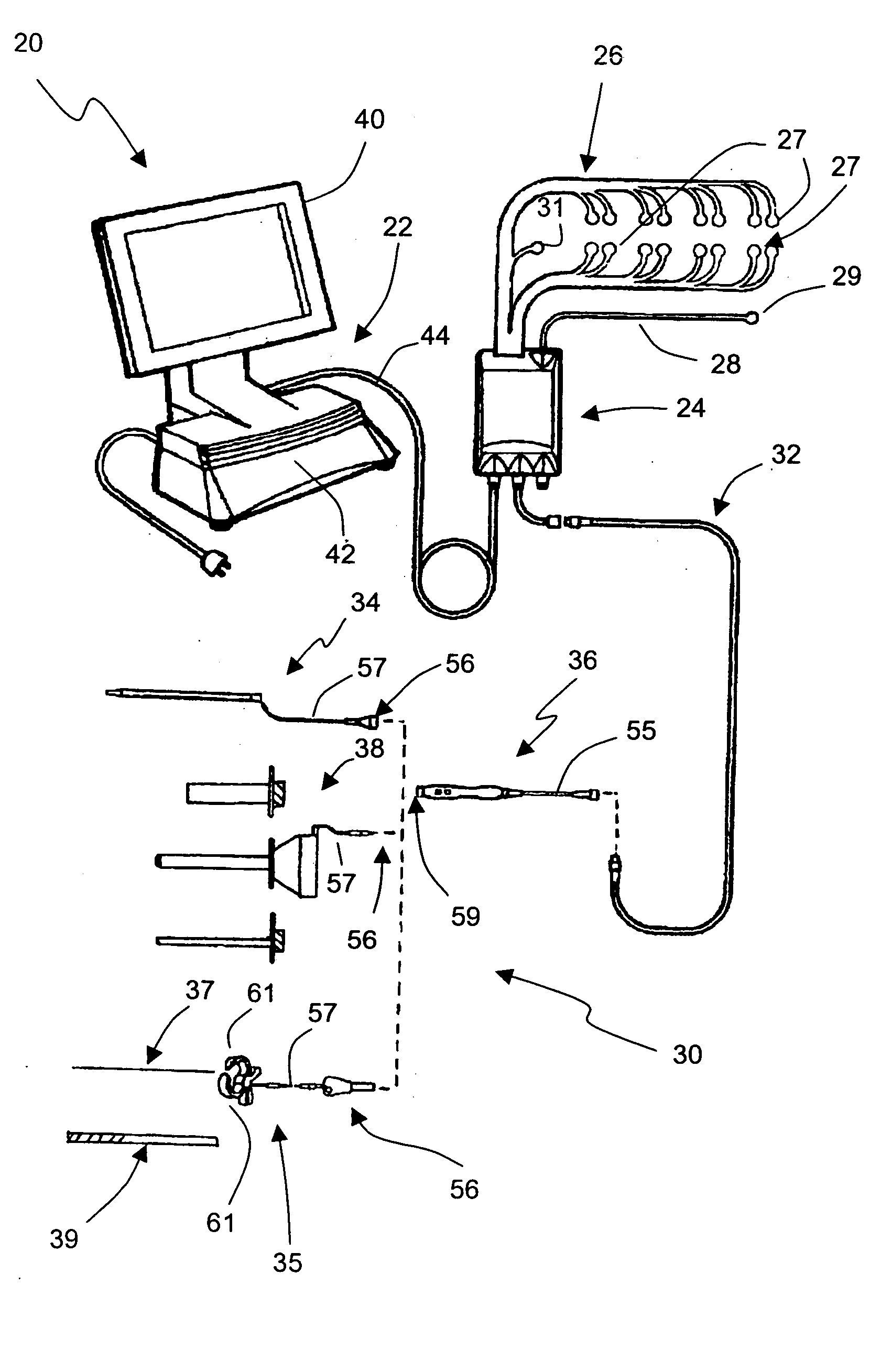
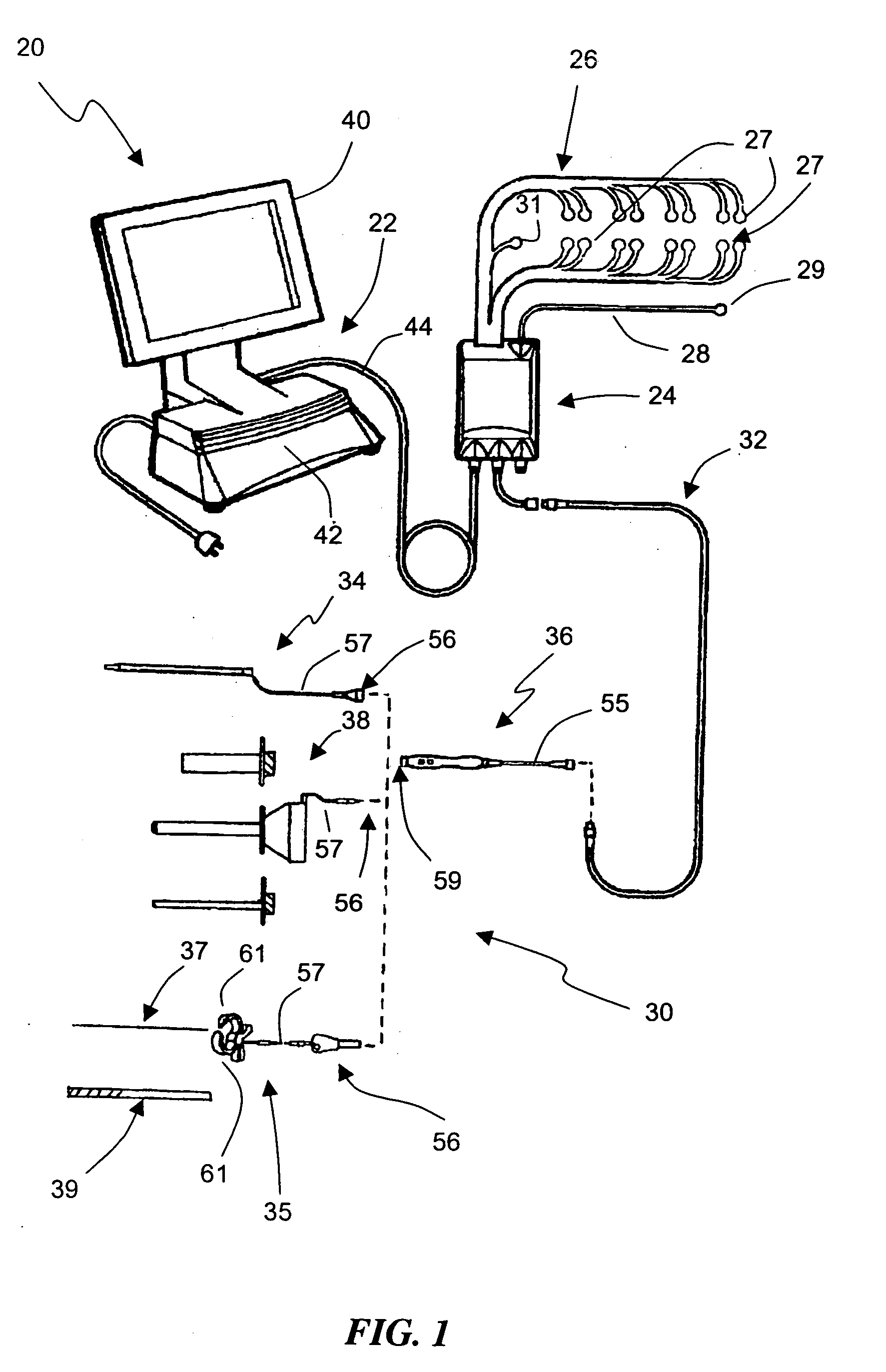
ActiveUS7942826B1Easy to operateFacilitate easy movement and positioningSpinal electrodesElectromyographyIntegrity assessmentPilot hole
A pedicle access system including a cannula, a stylet, and a removable T-handle. The pedicle access system may be used to percutaneously approach the pedicle, initiate pilot hole formation, and conduct a stimulation signal to the target site for the purposes of performing a pedicle integrity assessment during the pilot hole formation. To do this, the cannula and stylet are locked in combination and inserted through an operating corridor to the pedicle target site, using the T-handle to facilitate easy movement and positioning of the cannula / stylet combination. A stimulation signal may be applied during pilot hole formation to conduct the pedicle integrity assessment. In a significant aspect, the T-handle may be detached from the cannula / stylet combination to facilitate the use of various surgical tools as necessary.
Owner:NUVASIVE
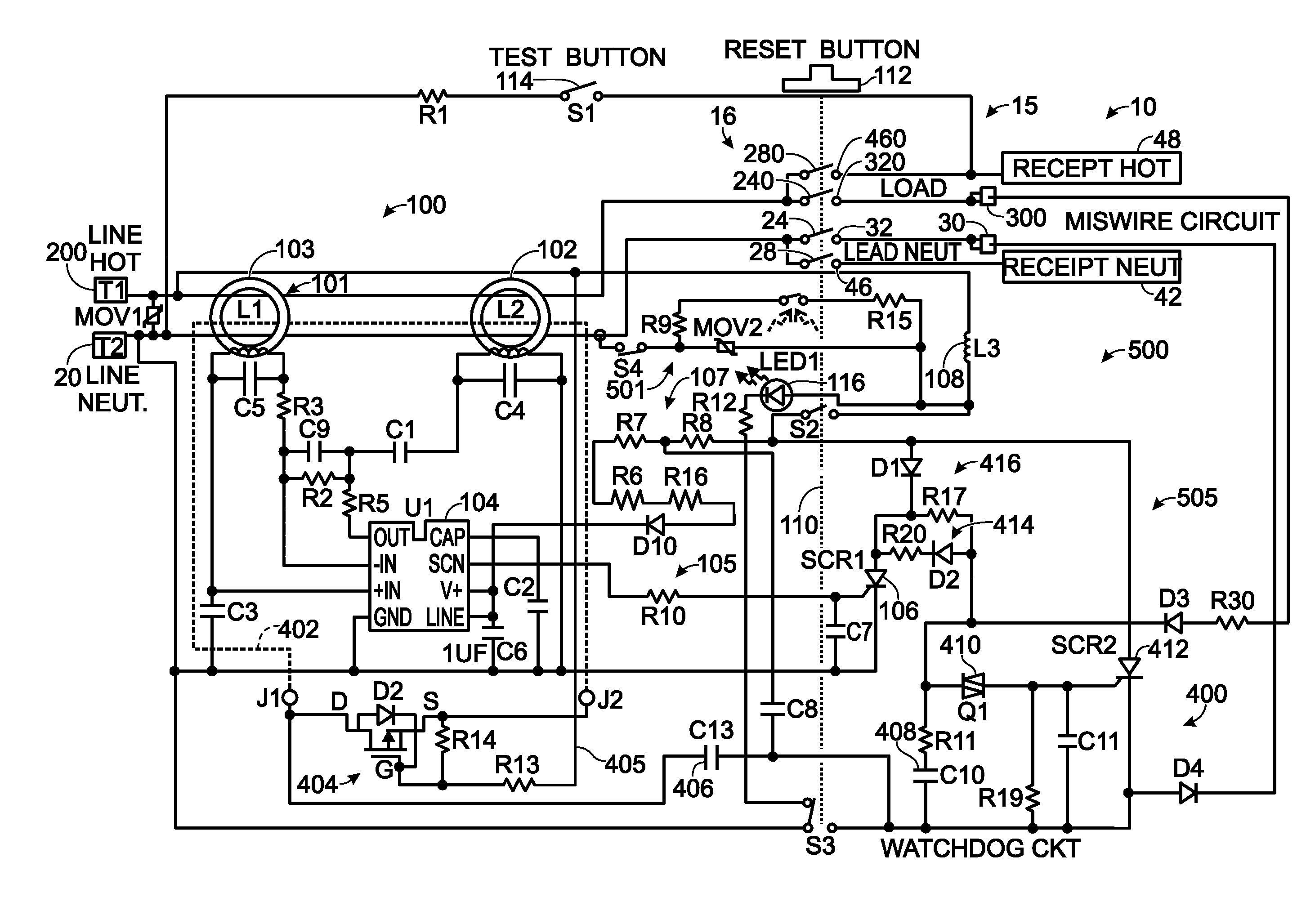
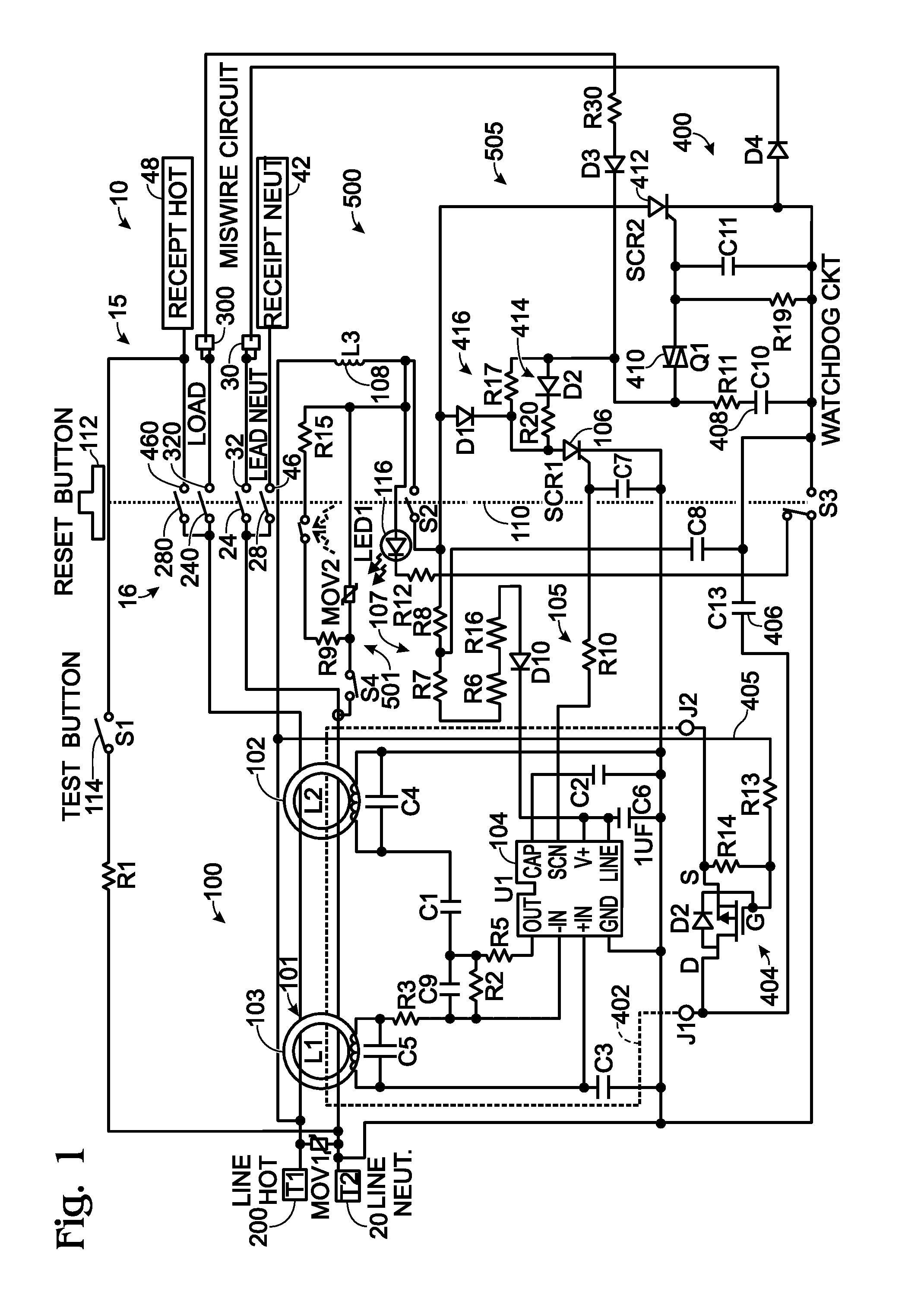
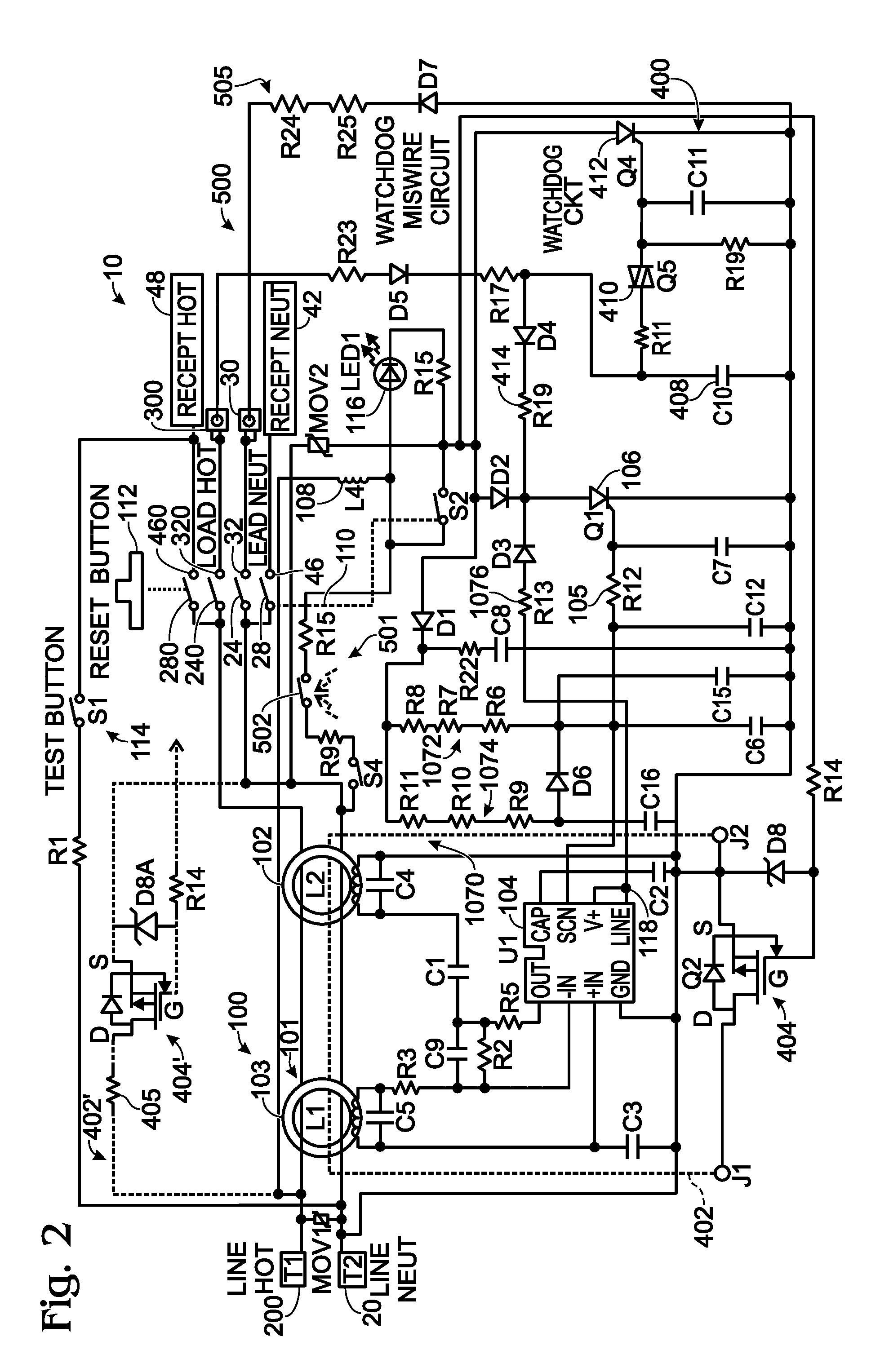
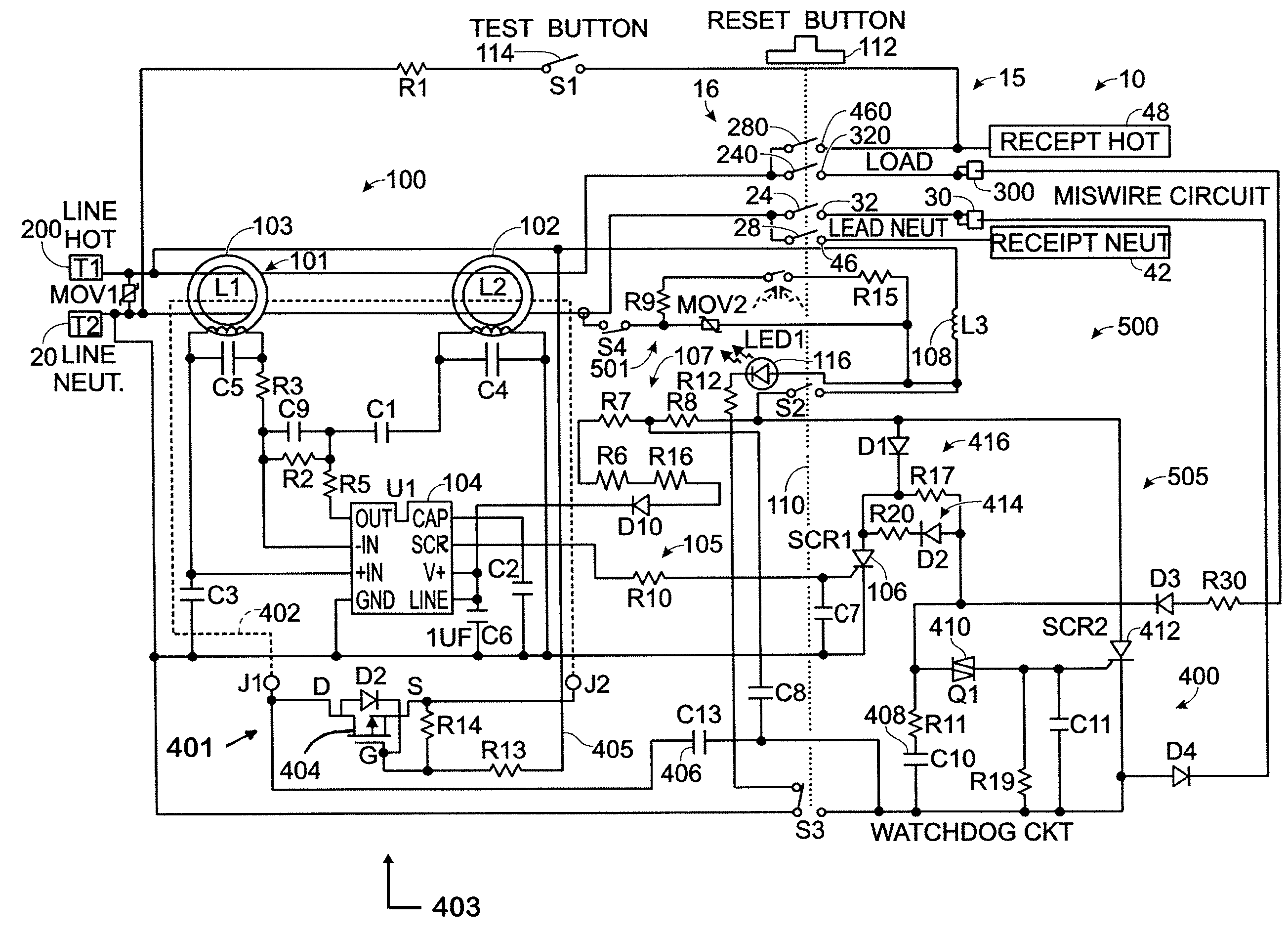
Electrical wiring device with protective features
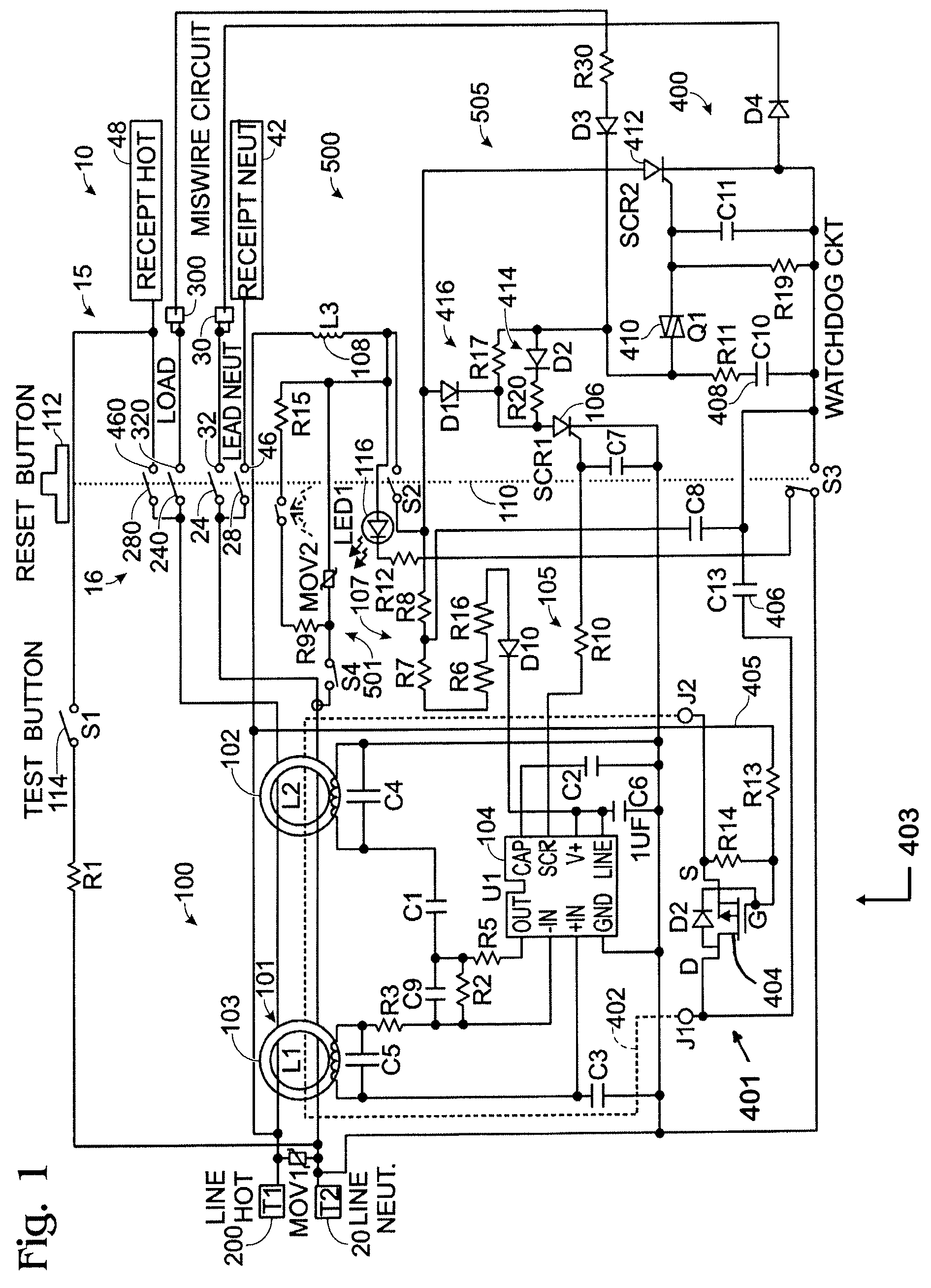
InactiveUS20120154972A1Inexpensively detectsElectrical testingContact testing/inspectionElectricityIntegrity assessment
The present invention is directed to an electrical wiring device for use in an electrical distribution system. The device includes a plurality of line terminals configured to terminate the plurality of line conductors and a plurality of load terminals configured to terminate the plurality of load conductors. The protective circuit assembly includes at least one fault detector configured to generate a fault detection signal based on electrical perturbations propagating on at least one of the plurality of line terminals or at least one of the plurality of load terminals. A device integrity evaluation circuit includes a timing circuit coupled to the source of AC power by way of the plurality of load terminals and configured to generate a time measurement. The device integrity evaluation circuit is configured to reset the time measurement if the protective circuit assembly generates the fault detection signal during a predetermined test interval in the properly wired condition. The device integrity evaluation circuit is configured to generate a device integrity fault signal when the time measurement exceeds a predetermined threshold. A circuit interrupter assembly includes movable contacts configured to be latched into a reset state in response to a reset stimulus. The movable contacts are configured to be driven into a tripped state in response to the fault detection signal or the device integrity fault signal.
Owner:PASS SEYMOUR
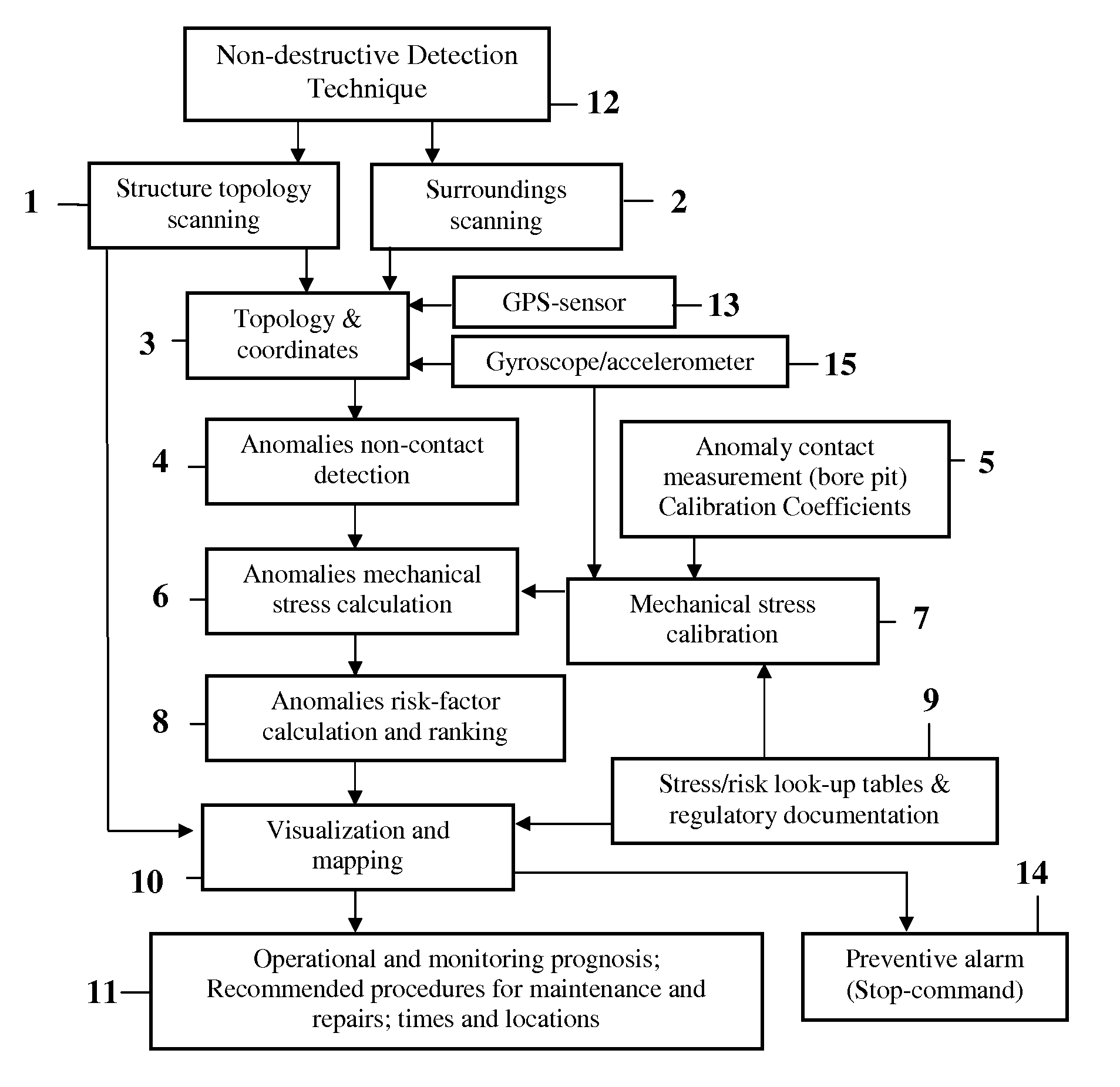
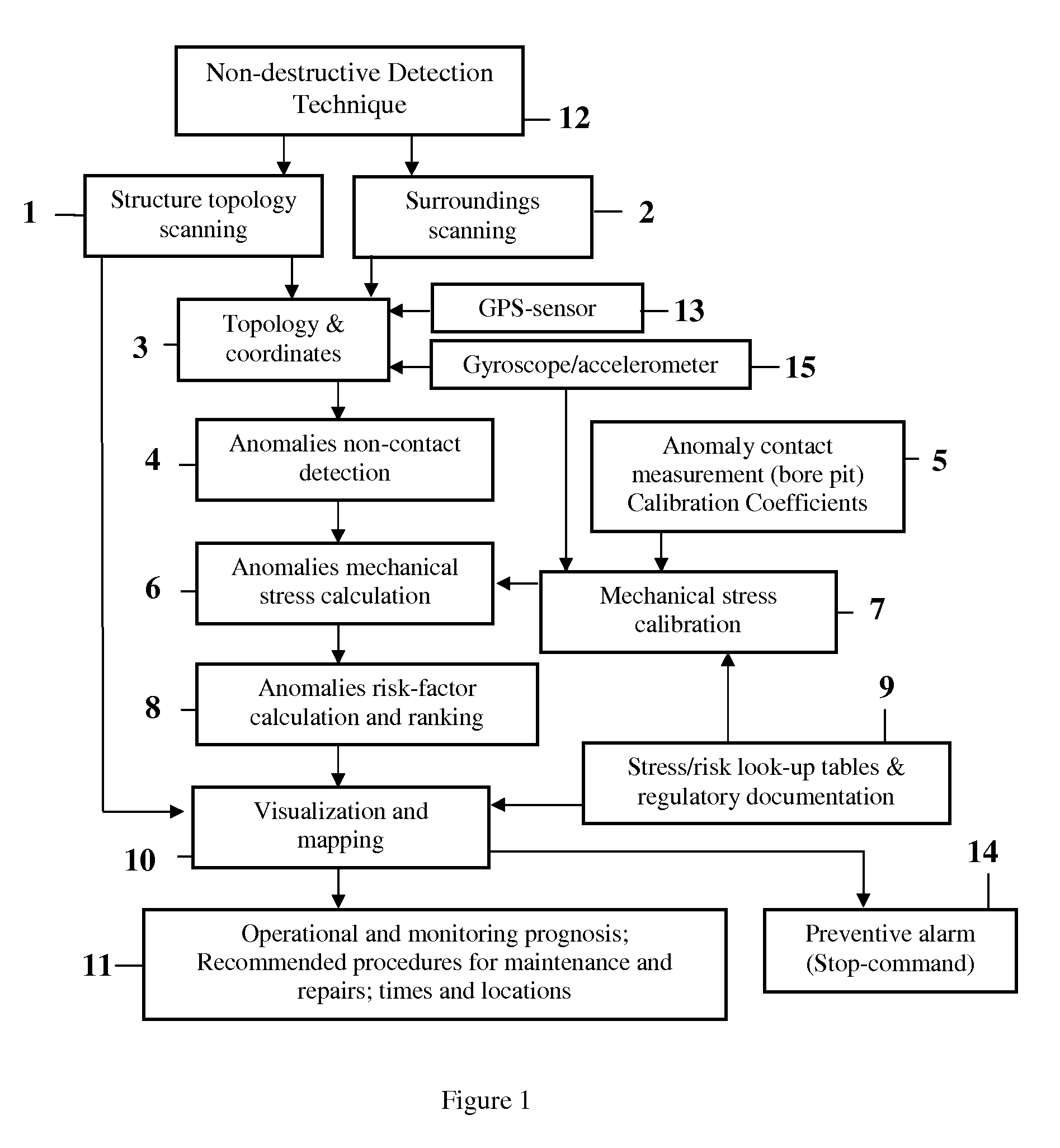
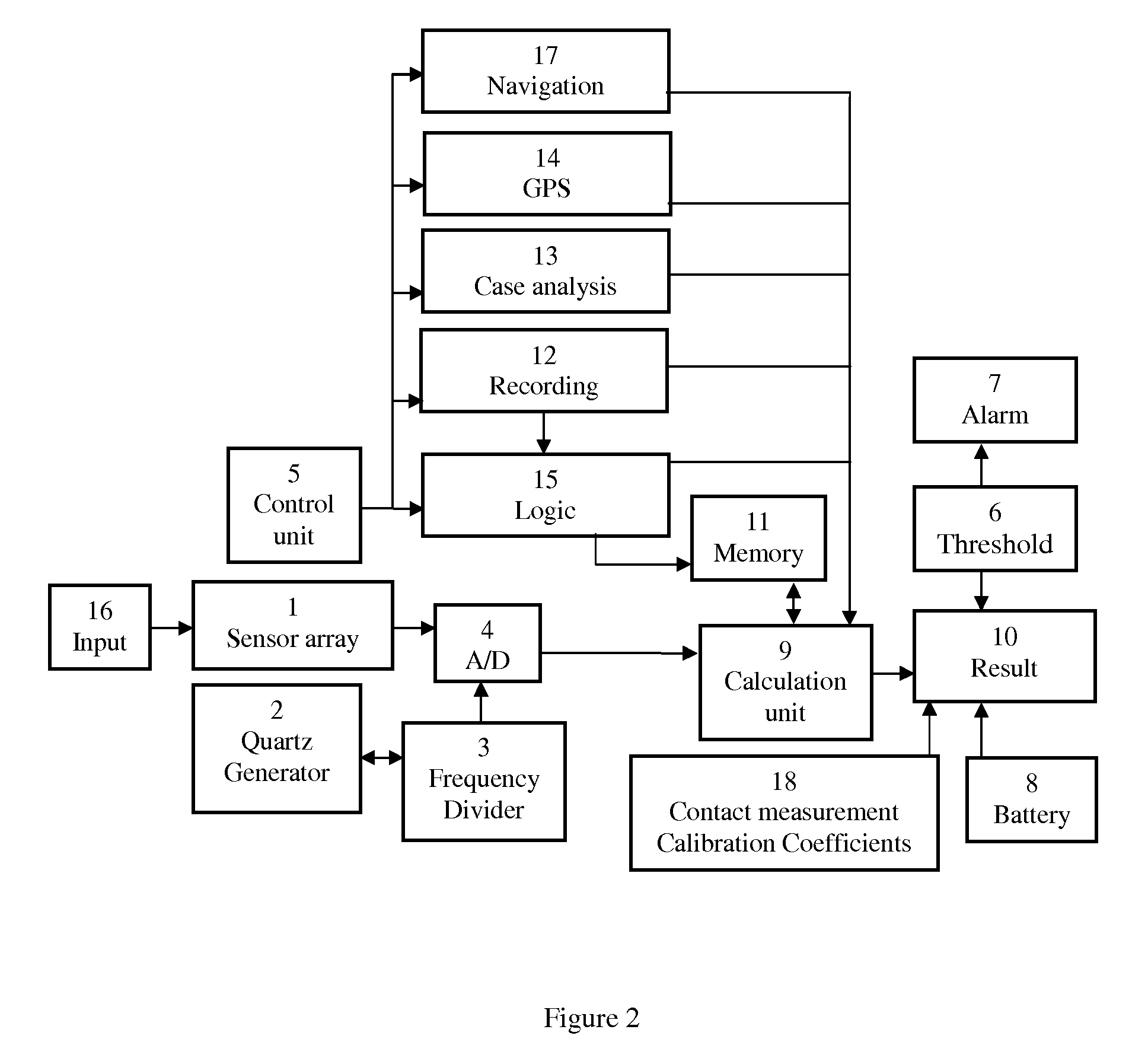
Metallic constructions integrity assessment and maintenance planning method
ActiveUS8447532B1Easy maintenancePromote repairPlug gaugesForce measurement by measuring magnetic property varationMaintenance planningHeavy duty
A method for metallic structure maintenance is disclosed. The method includes a magneto-graphic / Magnetic Tomography technique to identify stress-related defects. The method is specifically optimized for extended, non-accessible underground and underwater metallic structures in providing quality control, emergency alarms as well as timeline planning for structural repairs and maintenance work. Examples of the method implementation include pipes for oil and gas industry, detection of flaws in rolled products in metallurgical industry, welding quality of heavy duty equipment such as ships reservoirs, etc. It is especially important for loaded constructions, such as pressured pipes, infrastructure maintenance, nuclear power plant monitoring, bridges, corrosion prevention and environment protection.
Owner:GOROSHEVSKIY VALERIAN +2
System and Methods for Performing Pedicle Integrity Assessments of the Thoracic Spine
ActiveUS20080221473A1Good reproducibilityReliable stimulation threshold determinationElectrotherapyElectromyographyIntegrity assessmentPilot hole
The present invention includes a system and methods aimed at surgery, and more particularly to a system and methods for monitoring nervous tissue to assess the integrity of a pedicle wall during or after pilot hole formation and before, during, or after screw implantation, particularly in the thoracic spine. The system also performs other neurophysiologic assessments including, but not necessarily limited to, neuromuscular pathway status, nerve proximity detection, nerve pathology monitoring, and spinal cord health monitoring.
Owner:NUVASIVE
A trusted network connection method for enhancing security
ActiveCN101242267AImprove securityEasy to manageUser identity/authority verificationIntegrity assessmentNetwork connection
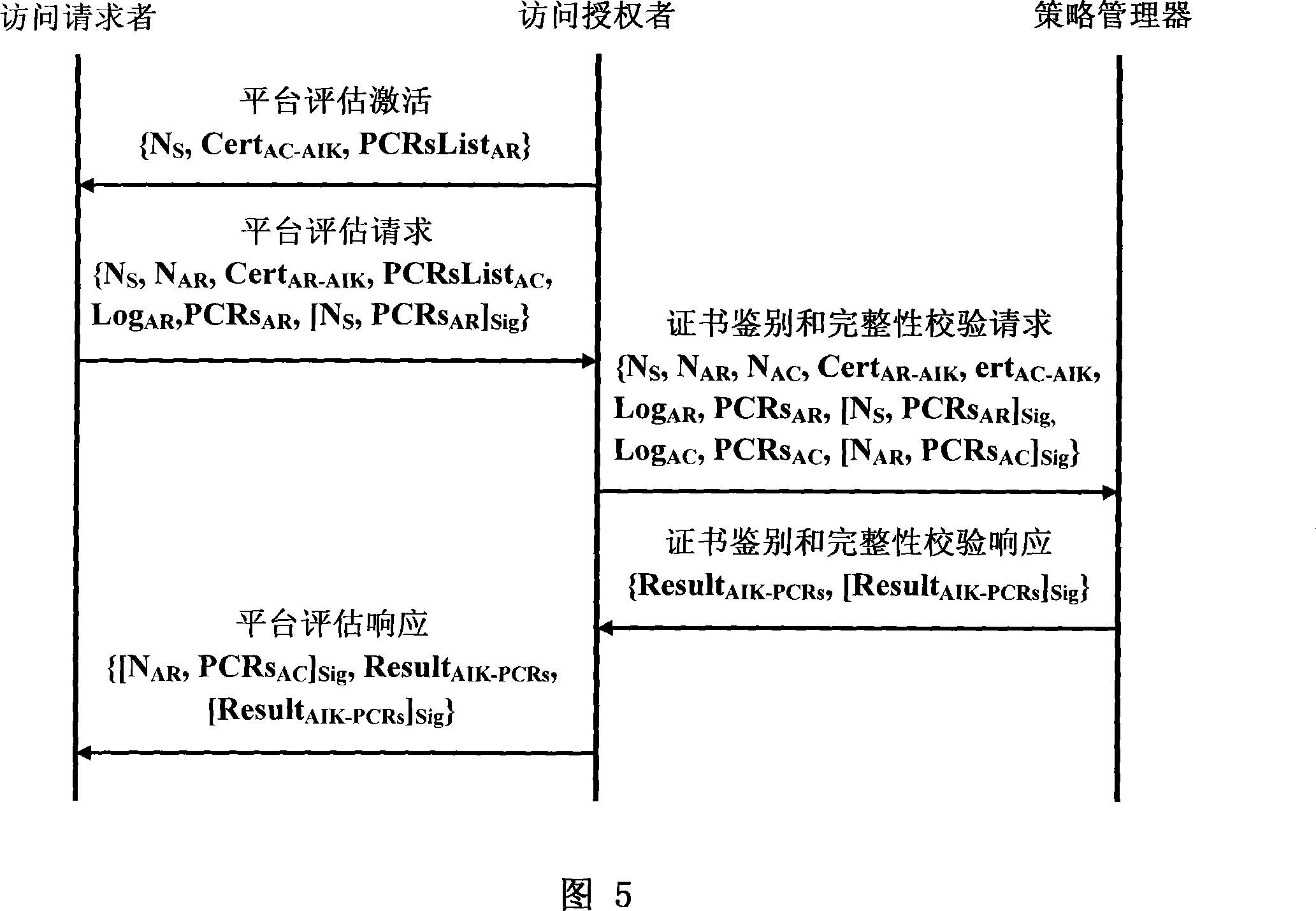
The invention provides a trusted network connection method for enhancing security, which pre-prepares a platform integrality information, prepares an integrality authentication request. A network access requester sends a access request to a network access controller, the network access controller starts a two-way authentication process of users, and user authentication service unit performs an equal authentication protocol. After the two-way user authentication is success, a TNC client-side and a TNC service side execute a platform integrality evaluate. The network access requester and network access authorizer achieve an inter access control between the access requester and a access authorizer based on a recommended control terminal respectively. The invention solves the technical problems in background technology that the security is low, the access requester may not validate validity of AIK certificate and the platform integrality evaluate is unequal. The invention simplifies the key management and integrality authentication mechanism, expands the range of applicability of trusted network connection.
Owner:CHINA IWNCOMM
A trusted network connection method based on three-element peer authentication
ActiveCN101242266ASimplify the negotiation processImprove securityUser identity/authority verificationIntegrity assessmentNetwork connection
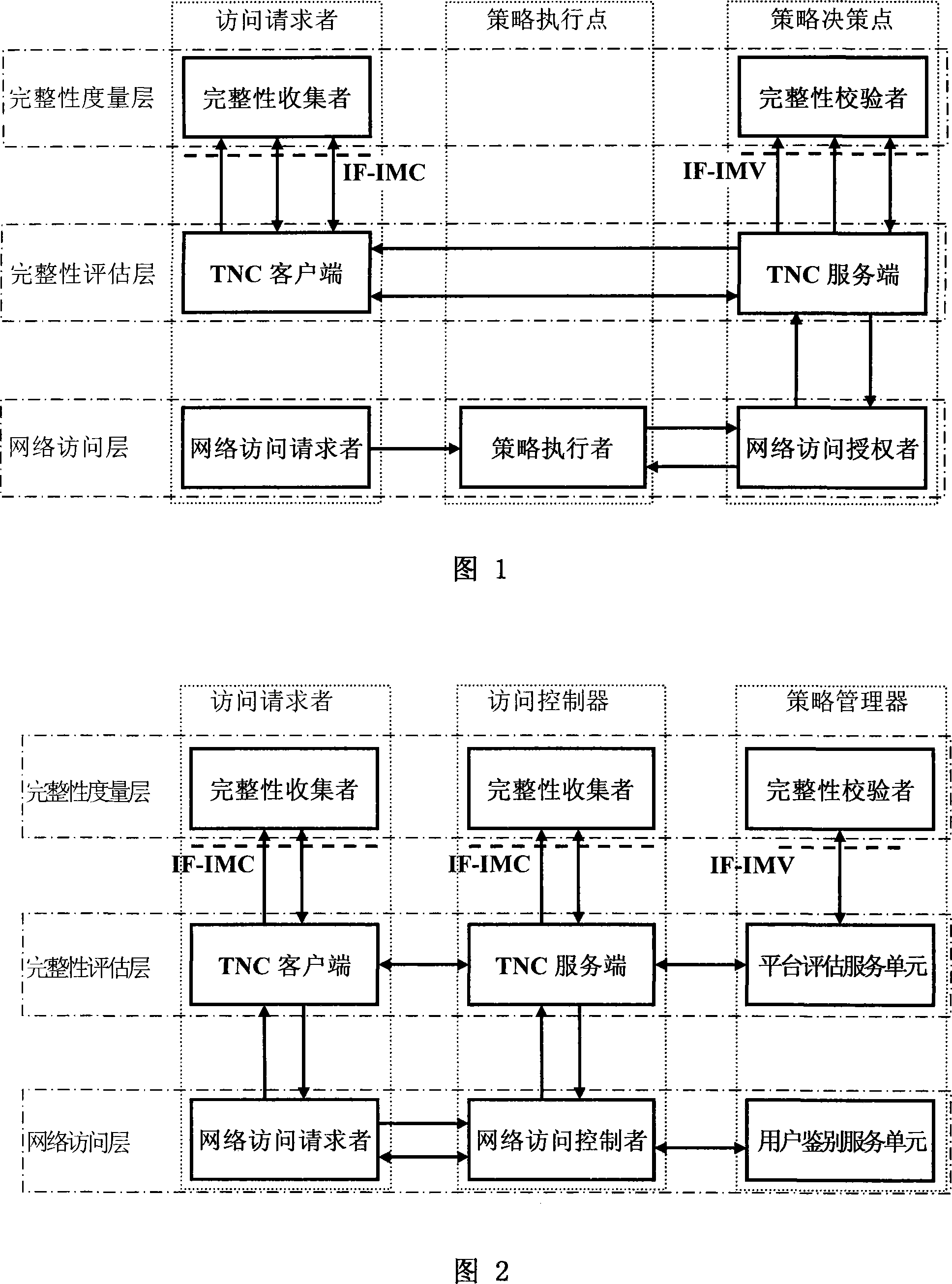
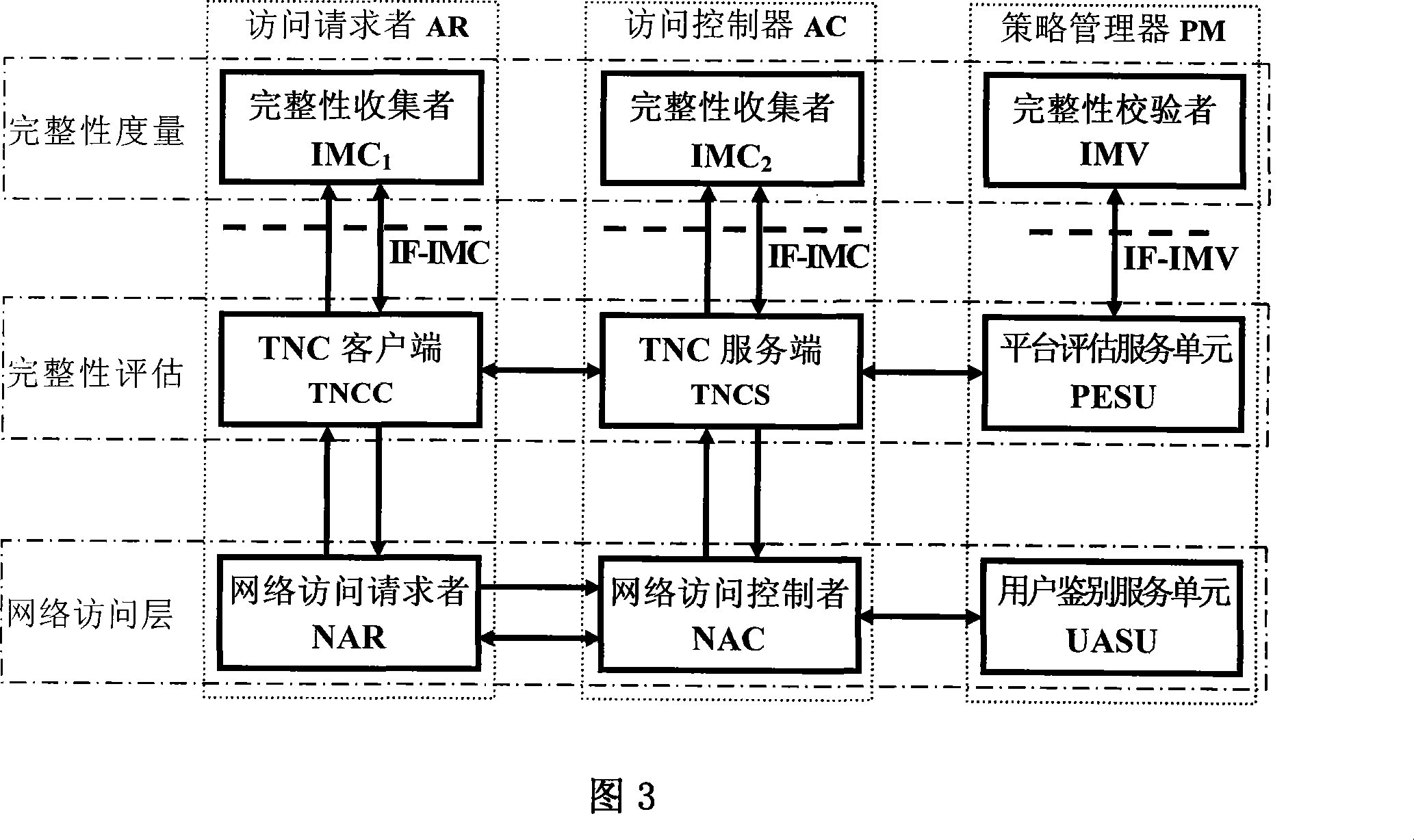
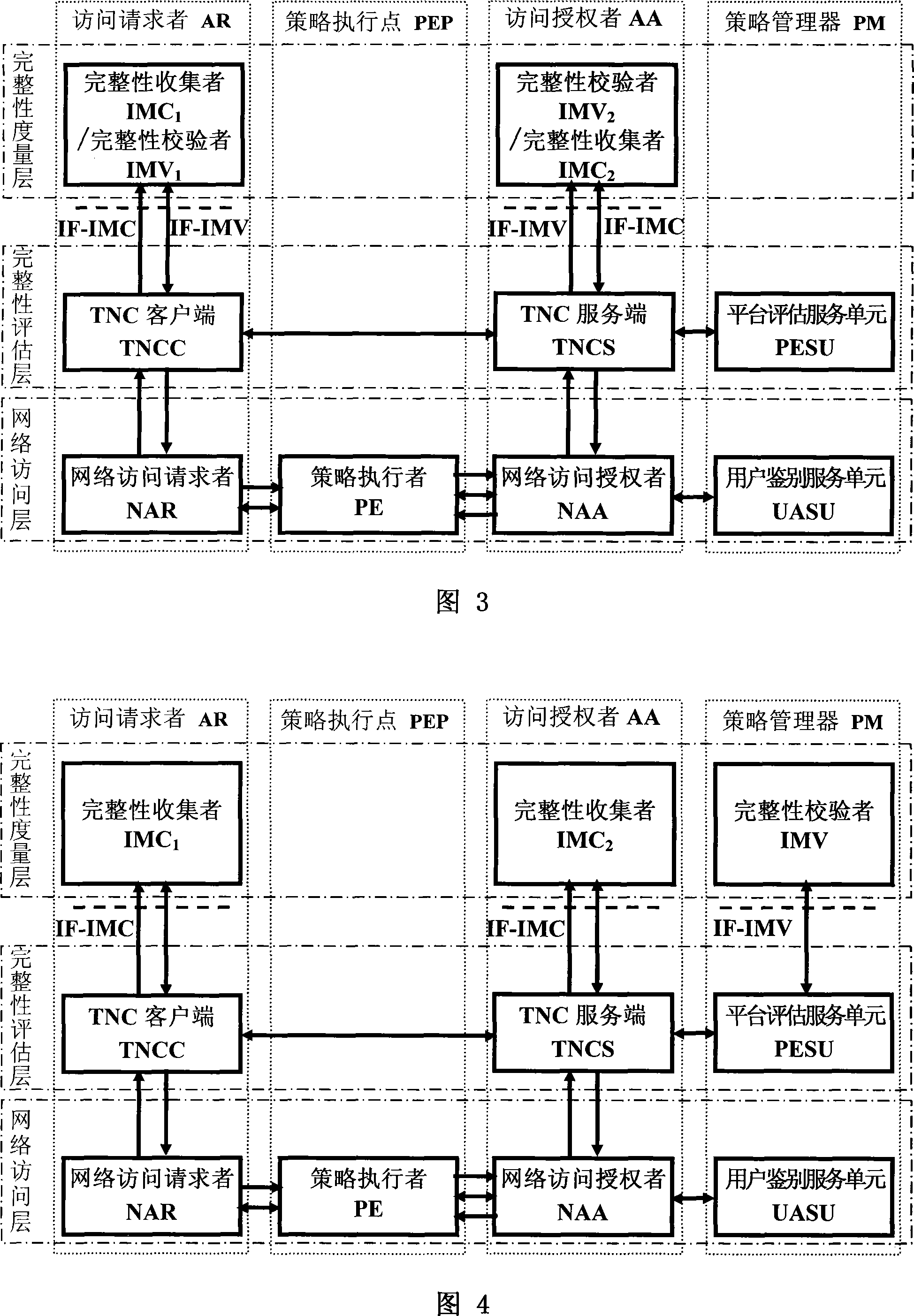
The invention provides a trusted network connection method based on ternary equal authentication, which pre-prepares a platform integrality information, prepares an integrality authentication request. A network access requester sends a access request to a network access controller, the network access controller starts a two-way authentication process of users, and user authentication service unit performs an equal authentication protocol. After the two-way user authentication is success, a TNC client-side, a TNC service side and a platform evaluate service unit execute a platform integrality evaluate by using the ternary equal authentication method. The network access requester and network access controller achieve an inter access control between the access requester and a access controller based on a recommended control terminal received respectively. The invention solves the technical problems in background technology that expandability is poor, the key arrangement process is complex, and the security is low and the platform integrality evaluate is unequal. The invention simplifies the key management and integrality authentication mechanism of trusted network connection, expands the range of applicability of trusted network connection.
Owner:CHINA IWNCOMM
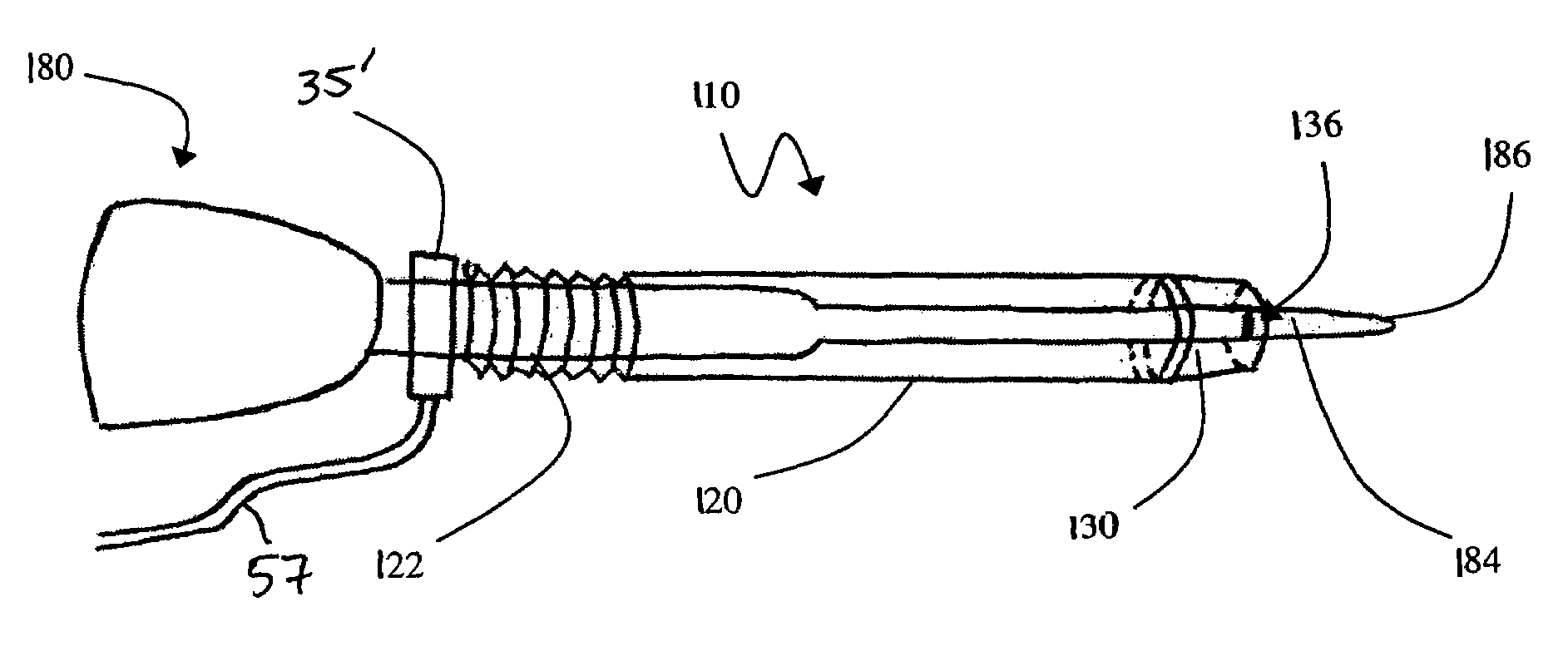
Insulated pedicle access system and related methods
ActiveUS8784330B1Easy to operateFacilitate easy movement and positioningSpinal electrodesInternal osteosythesisIntegrity assessmentPilot hole
A pedicle access system including a cannula, a stylet, and a removable T-handle. The pedicle access system may be used to percutaneously approach the pedicle, initiate pilot hole formation, and conduct a stimulation signal to the target site for the purposes of performing a pedicle integrity assessment during the pilot hole formation. To do this, the cannula and stylet are locked in combination and inserted through an operating corridor to the pedicle target site, using the T-handle to facilitate easy movement and positioning of the cannula / stylet combination. A stimulation signal may be applied during pilot hole formation to conduct the pedicle integrity assessment. In a significant aspect, the T-handle may be detached from the cannula / stylet combination to facilitate the use of various surgical tools as necessary.
Owner:NUVASIVE
Electrical wiring device with protective features
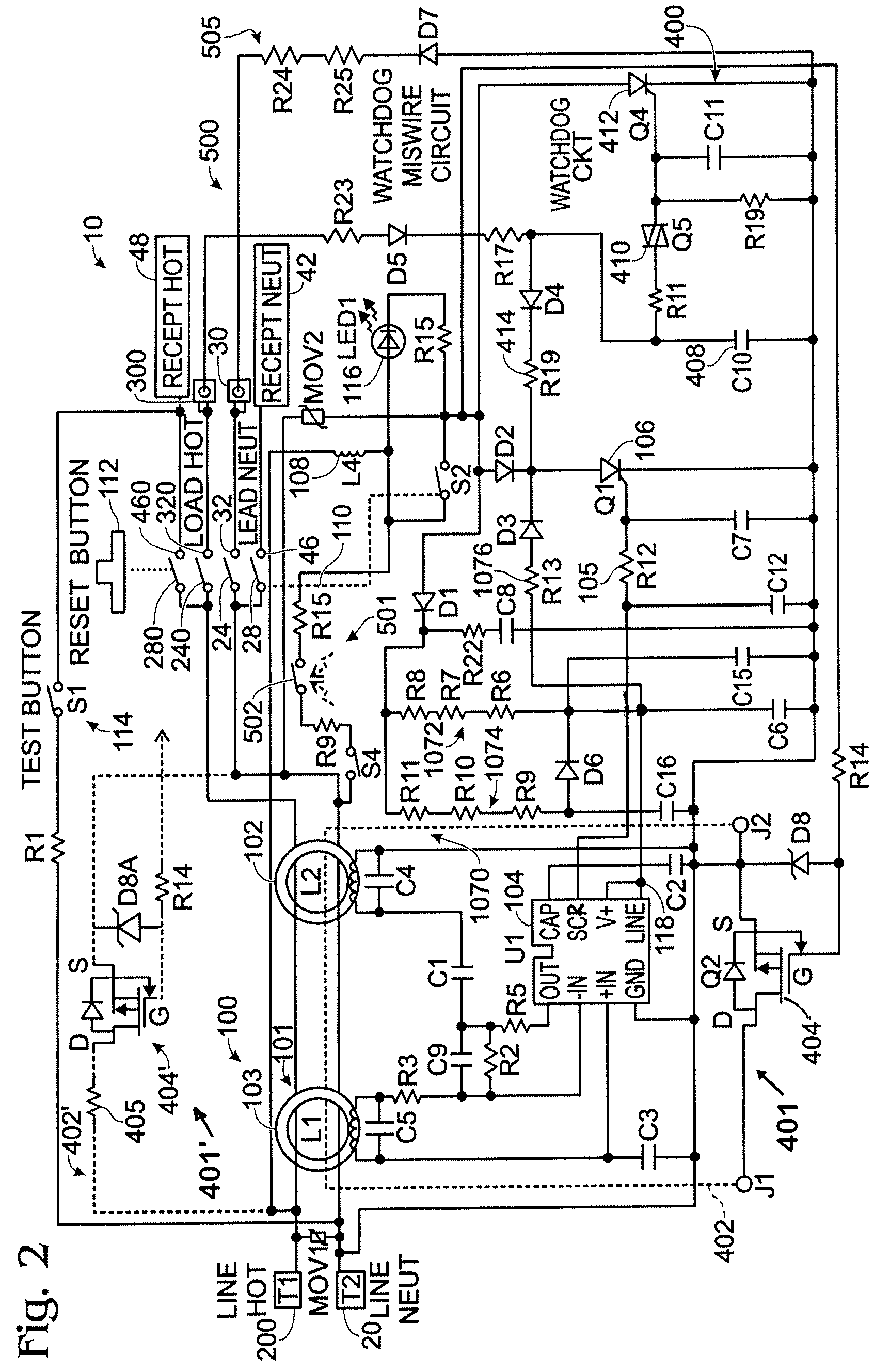
InactiveUS8861146B2Inexpensively detectsElectrical testingContact testing/inspectionIntegrity assessmentElectricity
The present invention is directed to an electrical wiring device for use in an electrical distribution system. The device includes a plurality of line terminals configured to terminate the plurality of line conductors and a plurality of load terminals configured to terminate the plurality of load conductors. The protective circuit assembly includes at least one fault detector configured to generate a fault detection signal based on electrical perturbations propagating on at least one of the plurality of line terminals or at least one of the plurality of load terminals. A device integrity evaluation circuit includes a timing circuit coupled to the source of AC power by way of the plurality of load terminals and configured to generate a time measurement. The device integrity evaluation circuit is configured to reset the time measurement if the protective circuit assembly generates the fault detection signal during a predetermined test interval in the properly wired condition. The device integrity evaluation circuit is configured to generate a device integrity fault signal when the time measurement exceeds a predetermined threshold. A circuit interrupter assembly includes movable contacts configured to be latched into a reset state in response to a reset stimulus. The movable contacts are configured to be driven into a tripped state in response to the fault detection signal or the device integrity fault signal.
Owner:PASS SEYMOUR
A trusted network connection system based on three-element peer authentication
ActiveCN101242268ASimplify the negotiation processImprove securityUser identity/authority verificationDigital data authenticationExtensibilityIntegrity assessment
The invention provides a trusted network connection system based on ternary equal authentication, wherein a network access requester is connected with a TNC client-side by a data carrying manner, and a TNC client-side is connected with an integrality collector by an integrality measurement collecting interface. A network access controller of an access controller is connected with a TNC service side by the data carrying manner, the TNC service side is connected with an integrality collector by the integrality measurement collecting interface. A user authentication service unit of a policy manager is connected with a platform evaluate service unit by the data carrying manner, and the platform evaluate service unit is connected with an integrality verifier by an integrality measurement verify interface. The invention solves the technical problems in background technology that expandability is poor, the key arrangement process is complex, and the security is low. The network access layer and integrality evaluate layer of the invention use ternary equal authentication to realize a two-way user authentication and a platform integrality evaluate, so, the invention can improve the security of the whole trusted network connecting construction.
Owner:CHINA IWNCOMM
Trusted network connect method for enhancing security
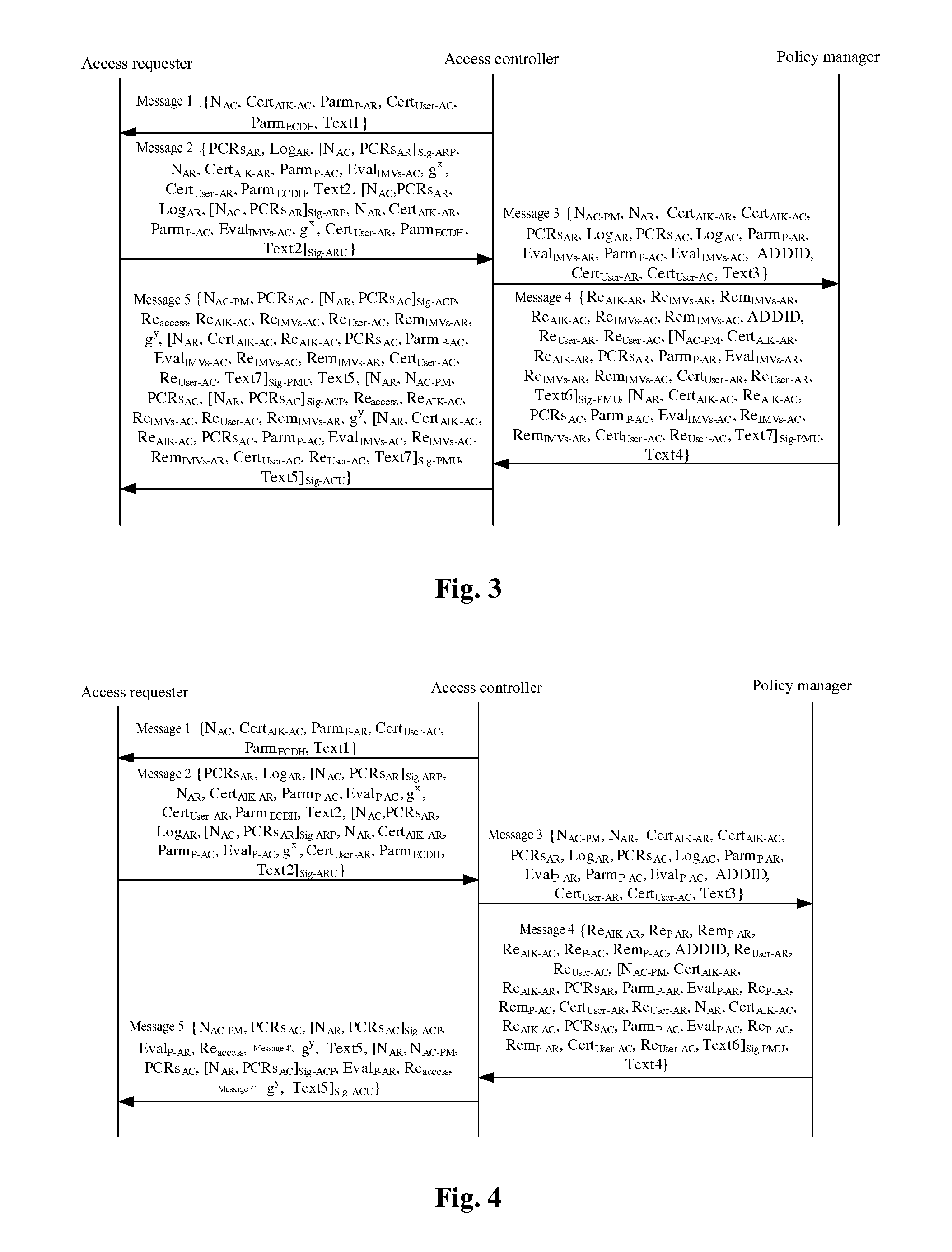
ActiveUS20110191579A1Improve securitySimplify key managementKey distribution for secure communicationUser identity/authority verificationIntegrity assessmentUser authentication
A trusted network connect method for enhancing security, it pre-prepares platform integrity information, sets an integrity verify demand. A network access requestor initiates an access request, a network access authority starts a process for bi-directional user authentication, begins to perform the triplex element peer authentication protocol with a user authentication service unit. After the success of the bi-directional user authentication, a TNC server and a TNC client perform bi-directional platform integrity evaluation. The network access requestor and the network access authority control ports according to their respective recommendations, implement the mutual access control of the access requestor and the access authority. The present invention solves the technical problems in the background technologies: the security is lower relatively, the access requestor may be unable to verify the validity of the AIK credential and the platform integrity evaluation is not parity. The present invention may simplify the management of the key and the mechanism of integrity verification, expand the application scope of the trusted network connect.
Owner:CHINA IWNCOMM
System and methods for performing pedicle integrity assessments of the thoracic spine
ActiveUS8591431B2Good reproducibilityReliable stimulation threshold determinationElectrotherapyElectromyographyIntegrity assessmentPilot hole
The present invention includes a system and methods aimed at surgery, and more particularly to a system and methods for monitoring nervous tissue to assess the integrity of a pedicle wall during or after pilot hole formation and before, during, or after screw implantation, particularly in the thoracic spine. The system also performs other neurophysiologic assessments including, but not necessarily limited to, neuromuscular pathway status, nerve proximity detection, nerve pathology monitoring, and spinal cord health monitoring.
Owner:NUVASIVE
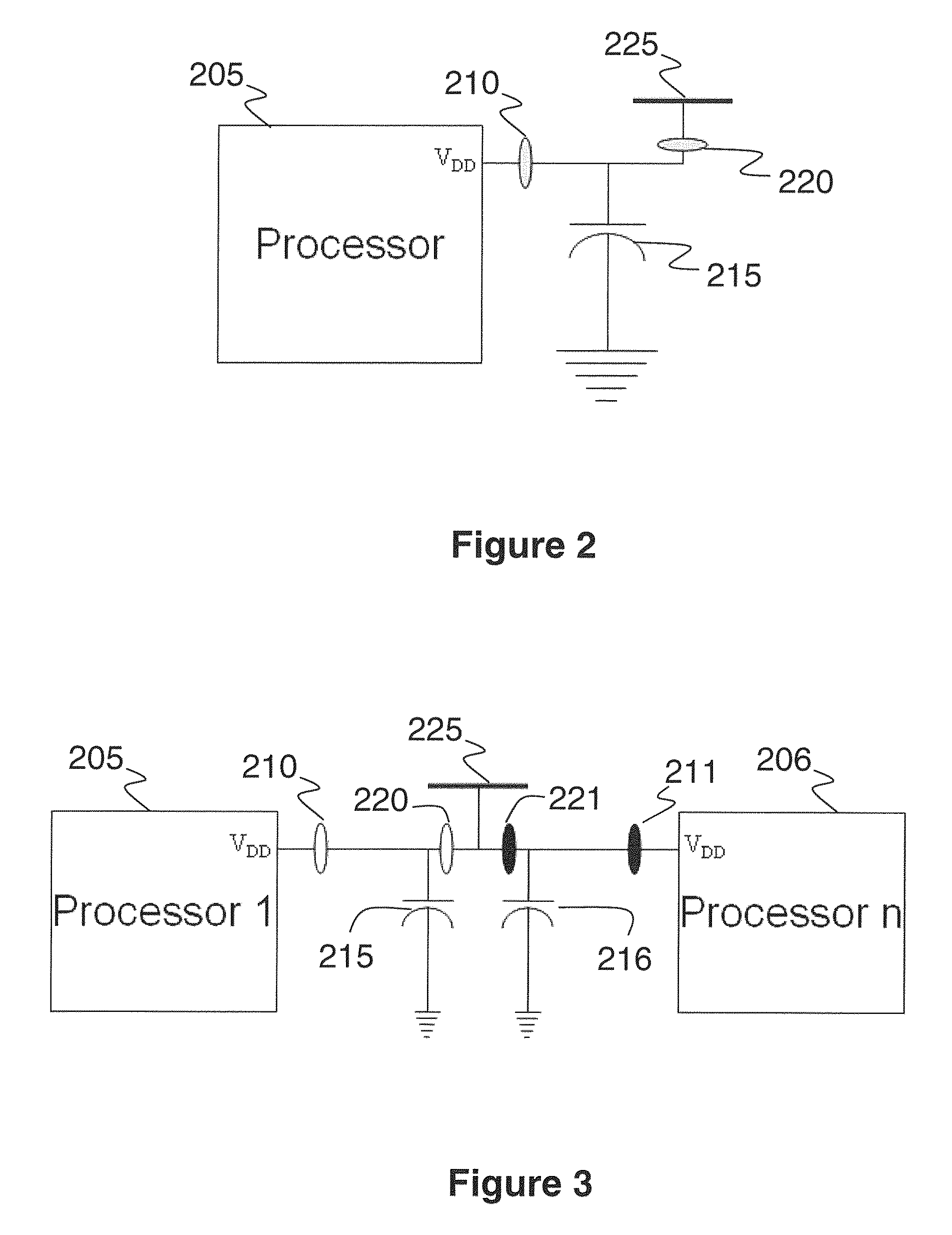
Systems, methods, and apparatus to enhance the integrity assessment when using power fingerprinting systems for computer-based systems
Owner:POWER FINGERPRINTING
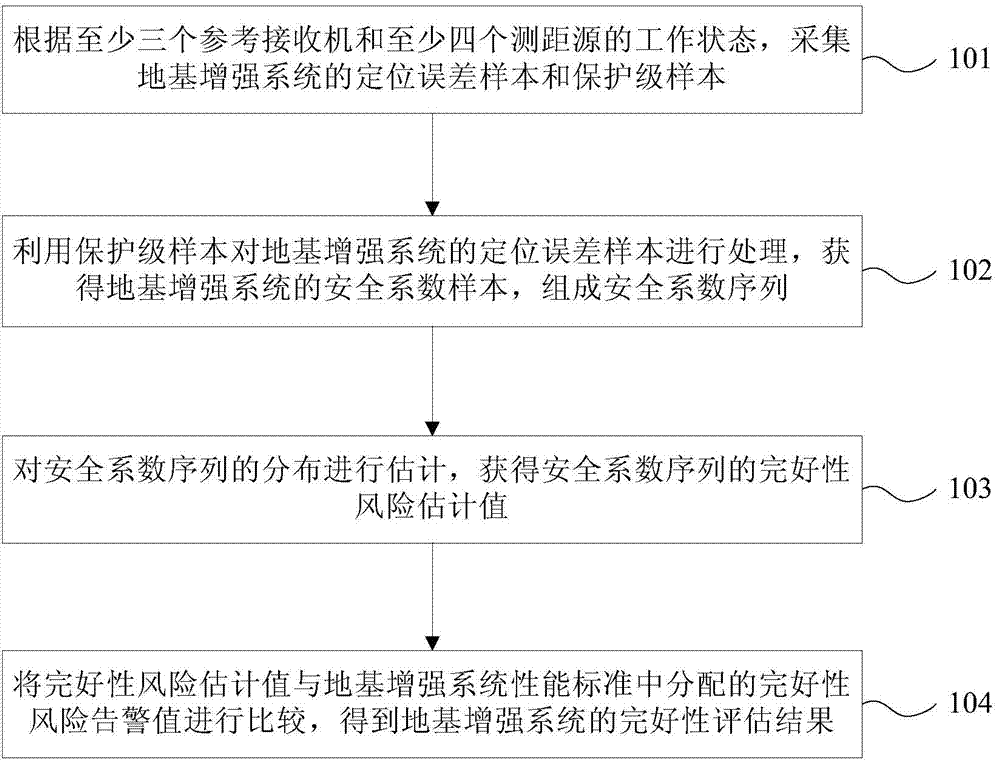
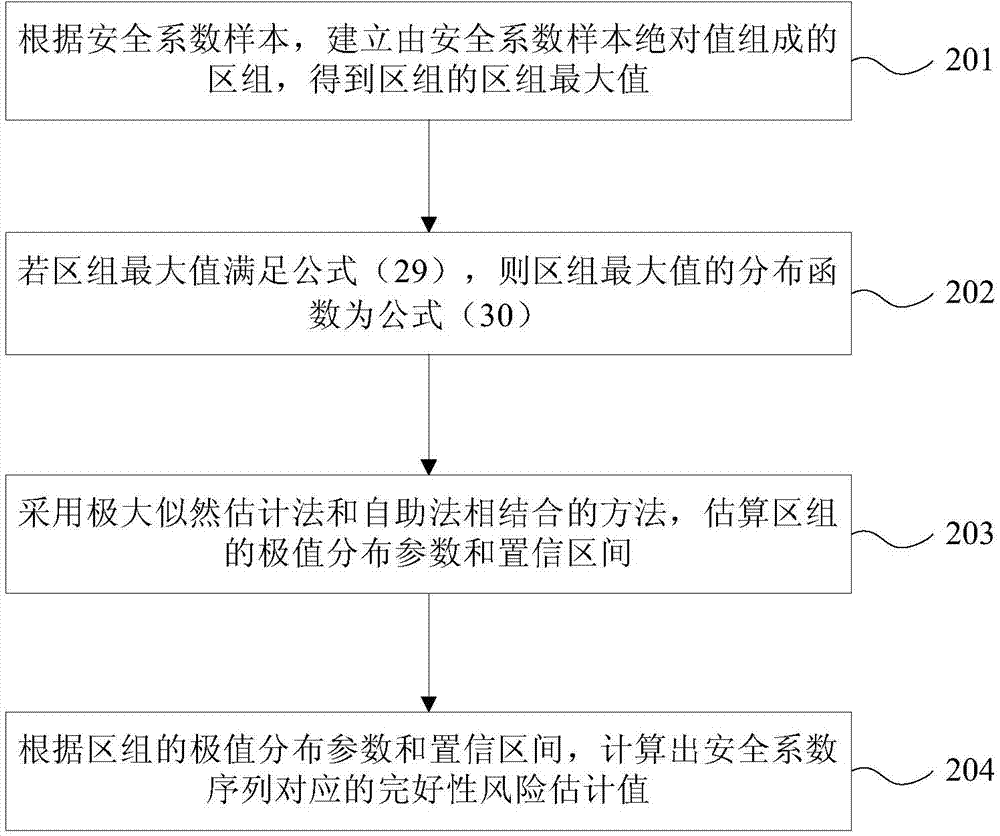
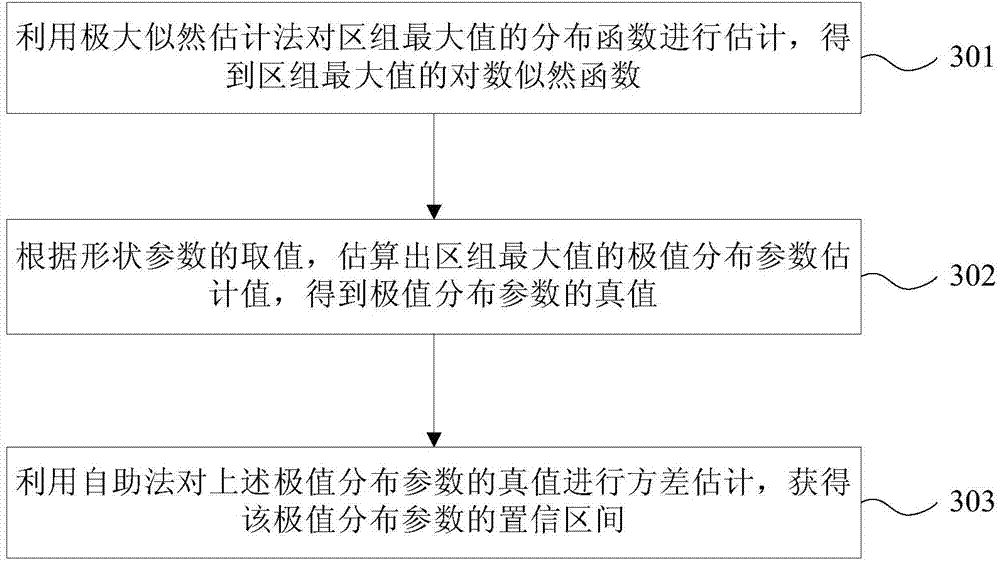
Integrity assessment method of ground base strengthening system
ActiveCN104849728AIntegrity Assessment ImplementationIntegrity Assessment Results Simplified and AccurateSatellite radio beaconingIntegrity assessmentEnvironmental resource management
The present invention provides an integrity assessment method of a ground base strengthening system. The method comprises the steps of collecting the positioning error sample and protection level sample of the ground base strengthening system according to the working states of at least three reference receivers and at least four ranging sources, processing the positioning error sample by using the protection level sample, obtaining the safety factor sample of the ground base strengthening system, forming a safety factor sequence, estimating the distribution of the safety factor sequence, obtaining the integrity risk assessment value of the safety factor sequence, and finally comparing the integrity risk assessment value and the integrity risk alarm value distributed in a ground base strengthening system performance standard to obtain the integrity assessment result of the ground base strengthening system. According to the method, the integrity assessment result of a protection level is simplified and fined systematically, and the integrity assessment of the ground base strengthening system is realized.
Owner:BEIHANG UNIV
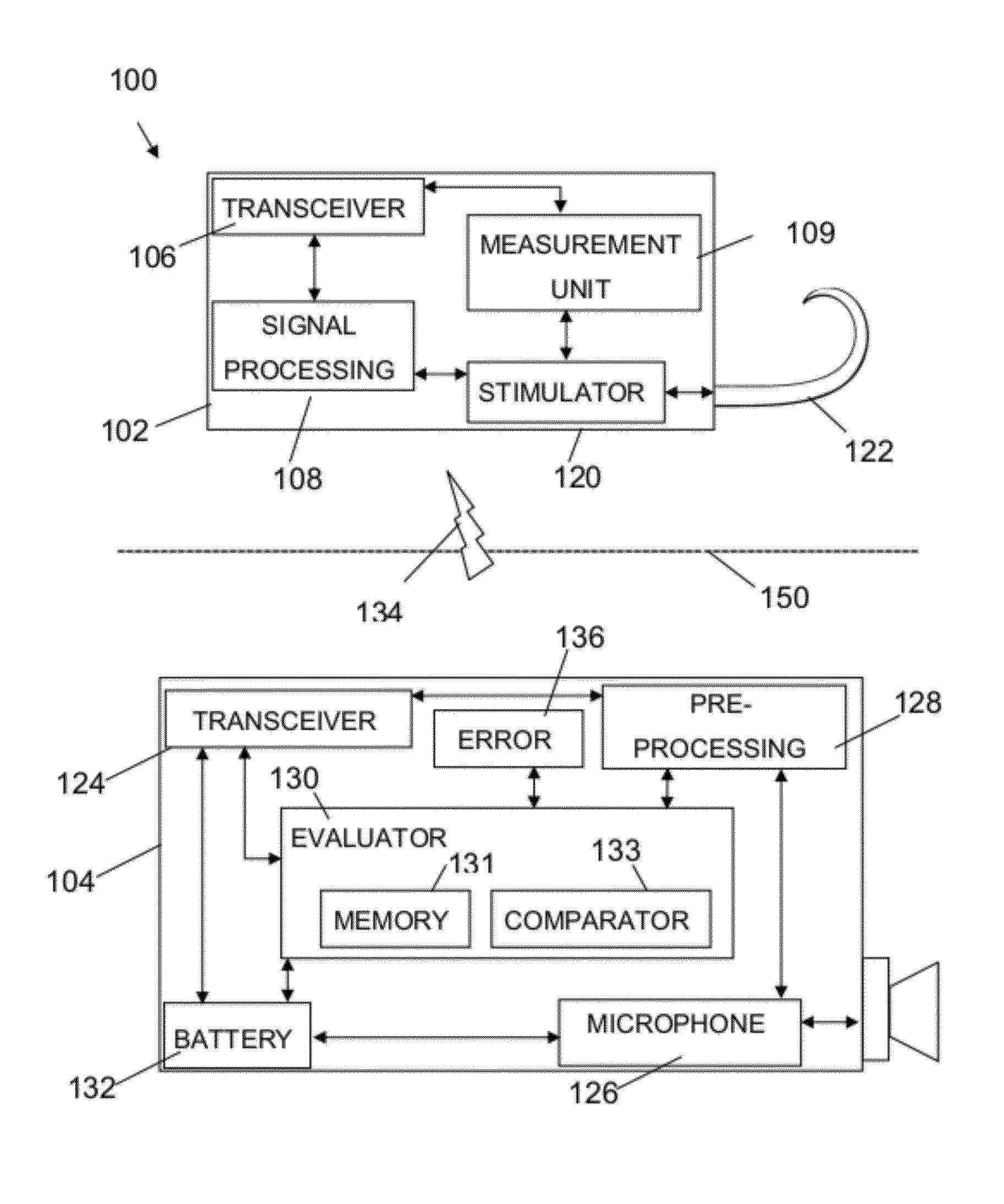
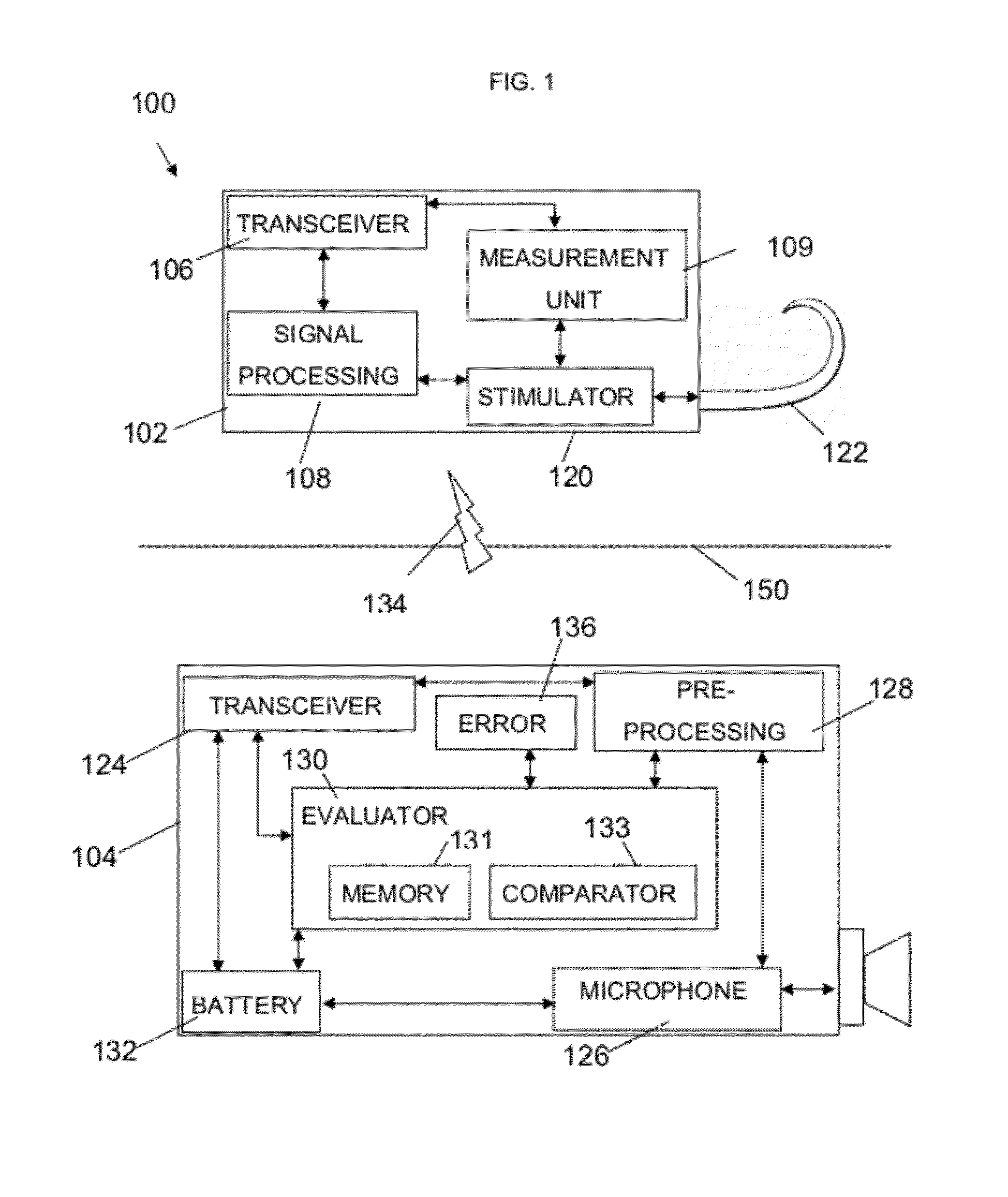
Integrity evaluation system in an implantable hearing prosthesis
An implantable hearing prosthesis, comprising an integrated integrity system. The integrity system is configured to measure one or more electrical characteristics of at least one component of the prosthesis, to evaluate the integrity of the prosthesis based on the measurements, and to perform at least one diagnostic operation based on the evaluation.
Owner:COCHLEAR LIMITED
Trusted network connect handshake method based on tri-element peer authentication
InactiveUS20110238996A1Improve securityImprove efficiencyUser identity/authority verificationComputer security arrangementsIntegrity assessmentNetwork connection
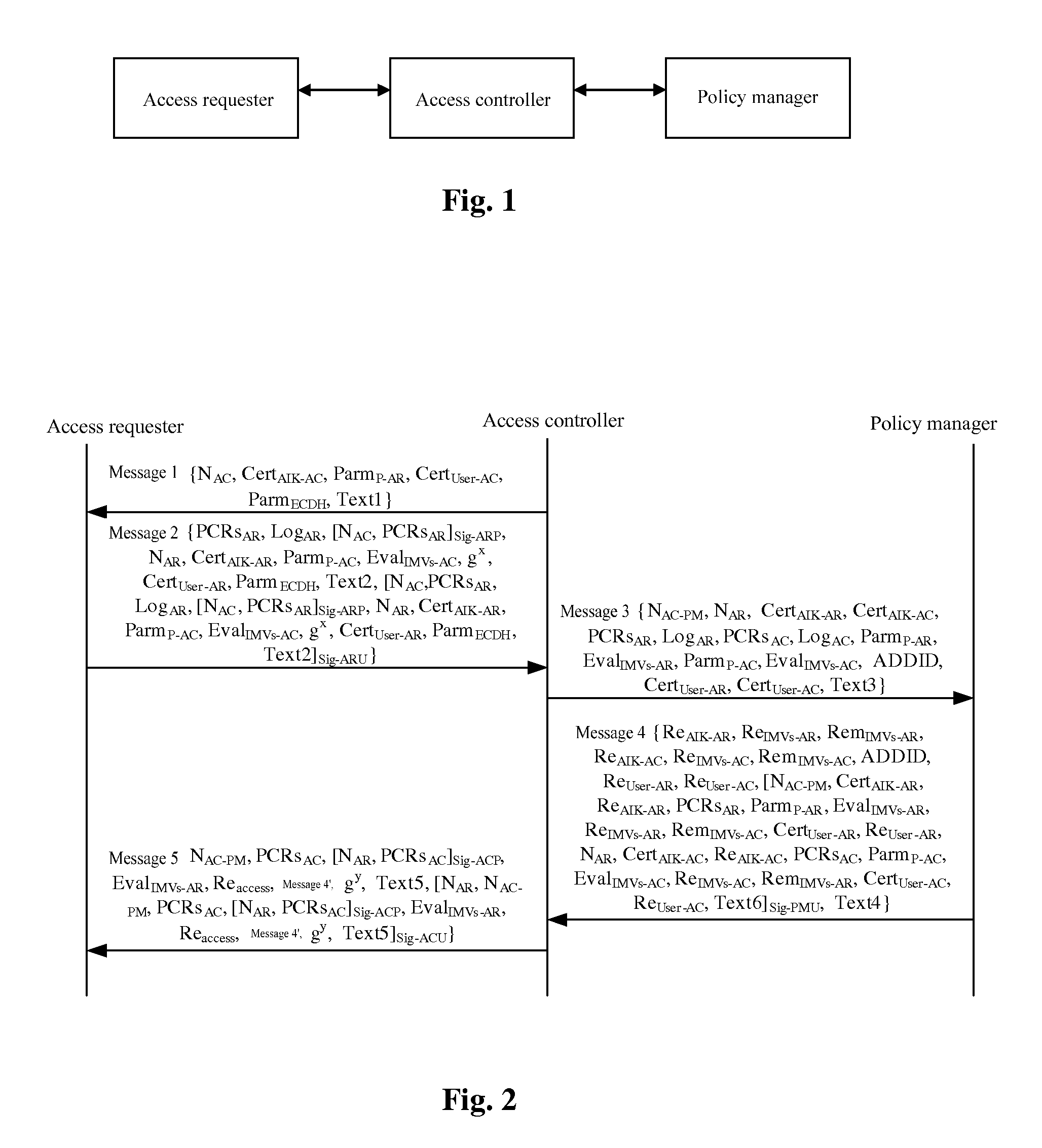
A trusted network connect handshake method based on tri-element peer authentication is provided, which comprises the following steps. An access controller (AC) sends message 1 for handshake activation to an Access Requestor (AR). The AR sends message 2 for access handshake request to the AC after receiving message 1. The AC sends message 3 for certificate authentication and integrity evaluation request to a Policy Manager (PM) after receiving message 2. The PM sends message 4 for certificate authentication and integrity evaluation response to the AC after receiving message 3. The AC sends message 5 for access handshake response to the AR after receiving message 4. The trusted network connect handshake is completed after the AR receives message 5.
Owner:CHINA IWNCOMM
Trusted network connect method for enhancing security
ActiveUS8271780B2Improve securitySimplified managementKey distribution for secure communicationDigital data processing detailsIntegrity assessmentUser authentication
A trusted network connect method for enhancing security, it pre-prepares platform integrity information, sets an integrity verify demand. A network access requestor initiates an access request, a network access authority starts a process for bi-directional user authentication, begins to perform the triplex element peer authentication protocol with a user authentication service unit. After the success of the bi-directional user authentication, a TNC server and a TNC client perform bi-directional platform integrity evaluation. The network access requestor and the network access authority control ports according to their respective recommendations, implement the mutual access control of the access requestor and the access authority. The present invention solves the technical problems in the background technologies: the security is lower relatively, the access requestor may be unable to verify the validity of the AIK credential and the platform integrity evaluation is not parity. The present invention may simplify the management of the key and the mechanism of integrity verification, expand the application scope of the trusted network connect.
Owner:CHINA IWNCOMM
Using power fingerprinting (PFP) to monitor the integrity and enhance security of computer based systems
ActiveUS9262632B2Improve integrityImprove performanceMemory loss protectionDetecting faulty computer hardwareIntegrity assessmentMalware
Procedures are described for enhancing target system execution integrity determined by power fingerprinting (PFP): by integrating PFP into the detection phase of comprehensive defense-in-depth security; by deploying a network of PFP enabled nodes executing untrusted devices with predefined inputs forcing a specific state sequence and specific software execution; by embedding module identification information into synchronization signaling; by combining signals from different board elements; by using malware signatures to enhance PFP performance; by automatic characterization and signature extraction; by providing secure signature updates; by protecting against side-channel attacks; performing real-time integrity assessment in embedded platform by monitoring their dynamic power consumption and comparing it against signatures from trusted code, including pre-characterizing power consumption of the platform by concentrating on trace sections carrying the most information about the internal execution status; by using PFP from sequence of bit transitions to detect deviations from authorized execution of software in a digital processor.
Owner:VIRGINIA TECH INTPROP INC
Machining and manufacturing method for spiral weld defects of pipelines
ActiveCN102950444AGuaranteed curingGuaranteed positionStrength propertiesIntegrity assessmentPerformance index
The invention discloses a machining and manufacturing method for spiral weld defects of pipelines. The machining and manufacturing method includes marking a metal plate which is required to be cut off and contains a spiral weld joint on the surface of a pipeline by a marking pen, and cutting off the metal plate containing the spiral weld joint by a cutting machine; machining a penetrating defect with a preset length and a preset width at the position corresponding to the spiral weld joint of the metal plate by means of cutting, grinding and polishing, then filling a brass strip with the size the same with that of the designed defect to the position with the defect, performing backing weld for two sides of the defect buried by the brass strip or one side of the opening defect, and performing filling welding until the shape of the metal plate is normal; and finally welding the metal plate containing the machined spiral weld defect onto the pipeline, and grinding excess weld metal of the weld joint welded back to the pipeline so as to complete machining and manufacturing for the weld defect. By the machining and manufacturing method, machining and manufacturing of the spiral weld defects with different sizes and at different positions can be performed, the machining and manufacturing method can be used for traction experiments, calibration of detectors and verification for performance indexes can be completed, and the accuracy of pipeline integrity assessment results is improved.
Owner:PIPECHINA SOUTH CHINA CO
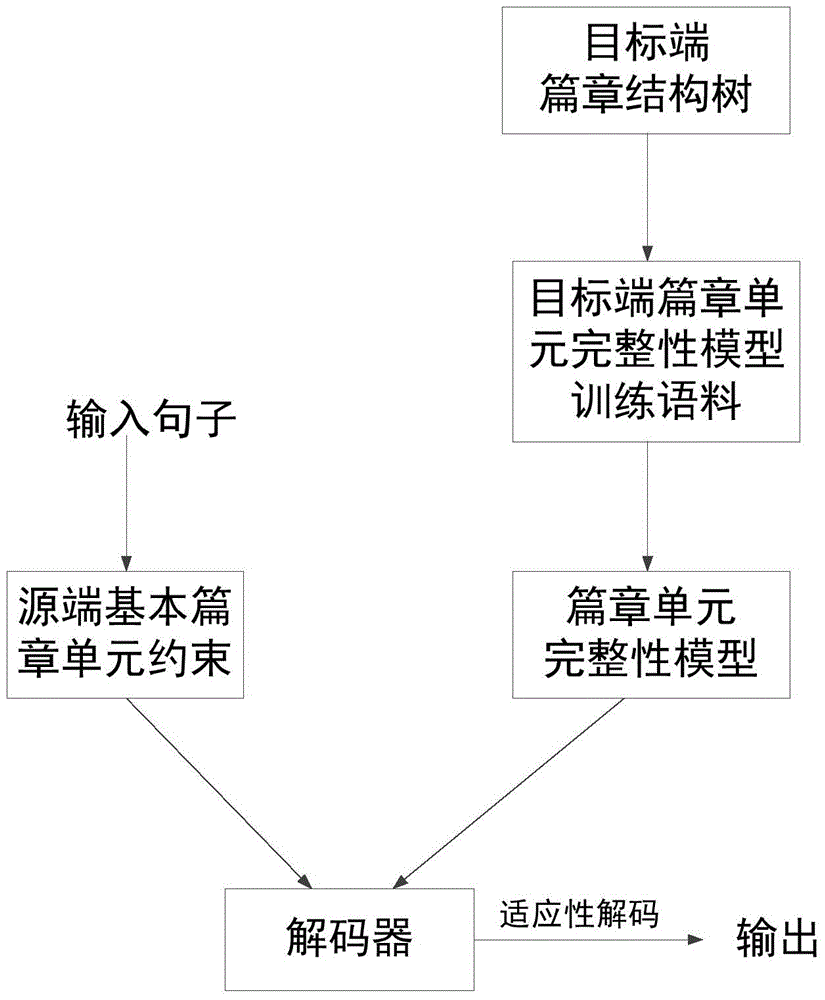
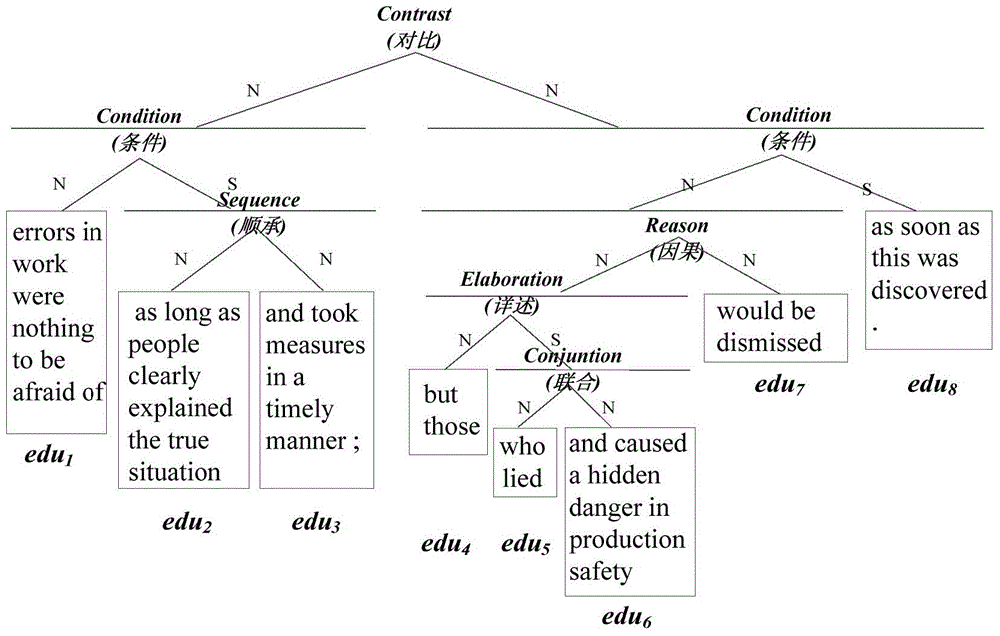
Translation text integrity evaluation method based on bilingual text structure information
ActiveCN104915337AImprove translation qualityIncrease the BLEU valueSpecial data processing applicationsIntegrity assessmentDecoding methods
The invention discloses a translation text integrity evaluation method based on bilingual text structure information. The method includes the following steps of firstly, extracting training corpus used for establishing a target end text unit integrity model from a target end texture structure tree; secondly, establishing the target end text unit integrity model through the training corpus generated in the first step; thirdly, integrating the target end text unit integrity model in a logarithm linear translation model, and conducting translation generation through an adaptability decoding method. According to the method, with the help of the bilingual text structure information, a decoder can further improve the translation quality of the current statistical machine translation by fully and approximately utilizing the semantic integrity information based on bilingual text language knowledge.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
GBAS integrity performance evaluation method based on pseudo-range error distribution model
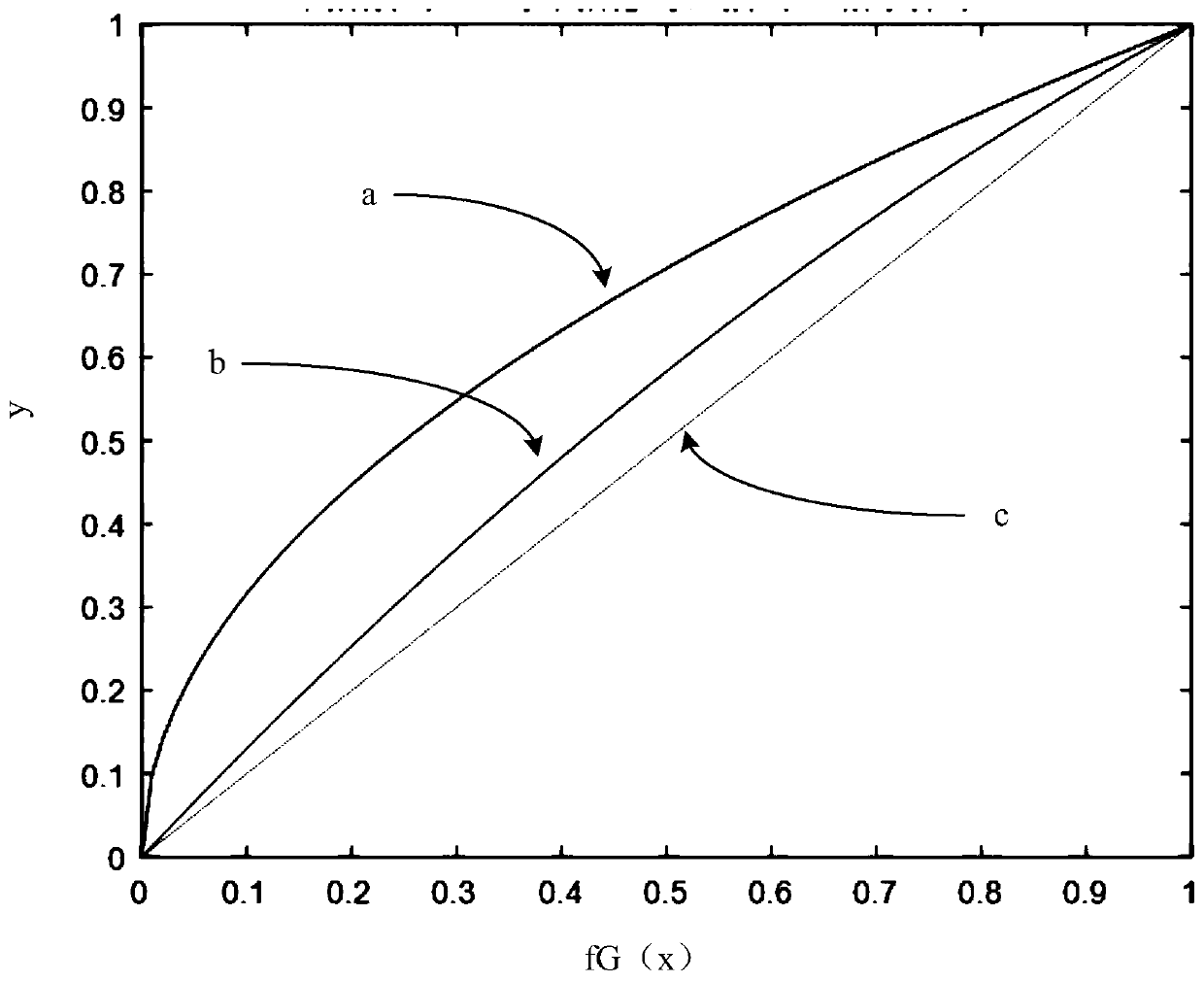
ActiveCN109901204AHigh precisionImprove envelope tightnessSatellite radio beaconingIntegrity assessmentErrors and residuals
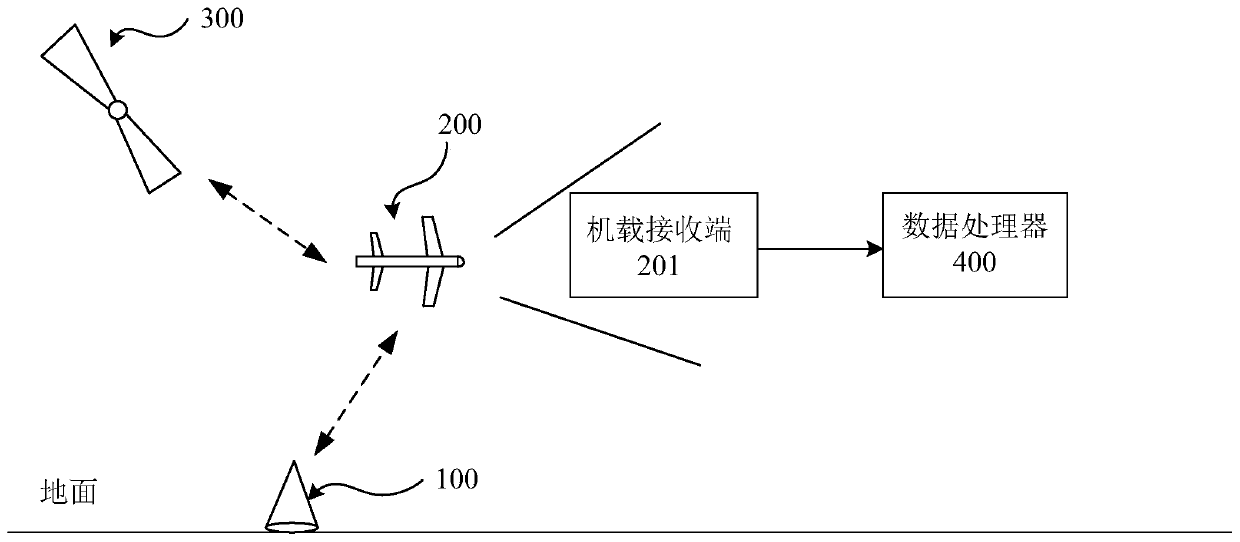
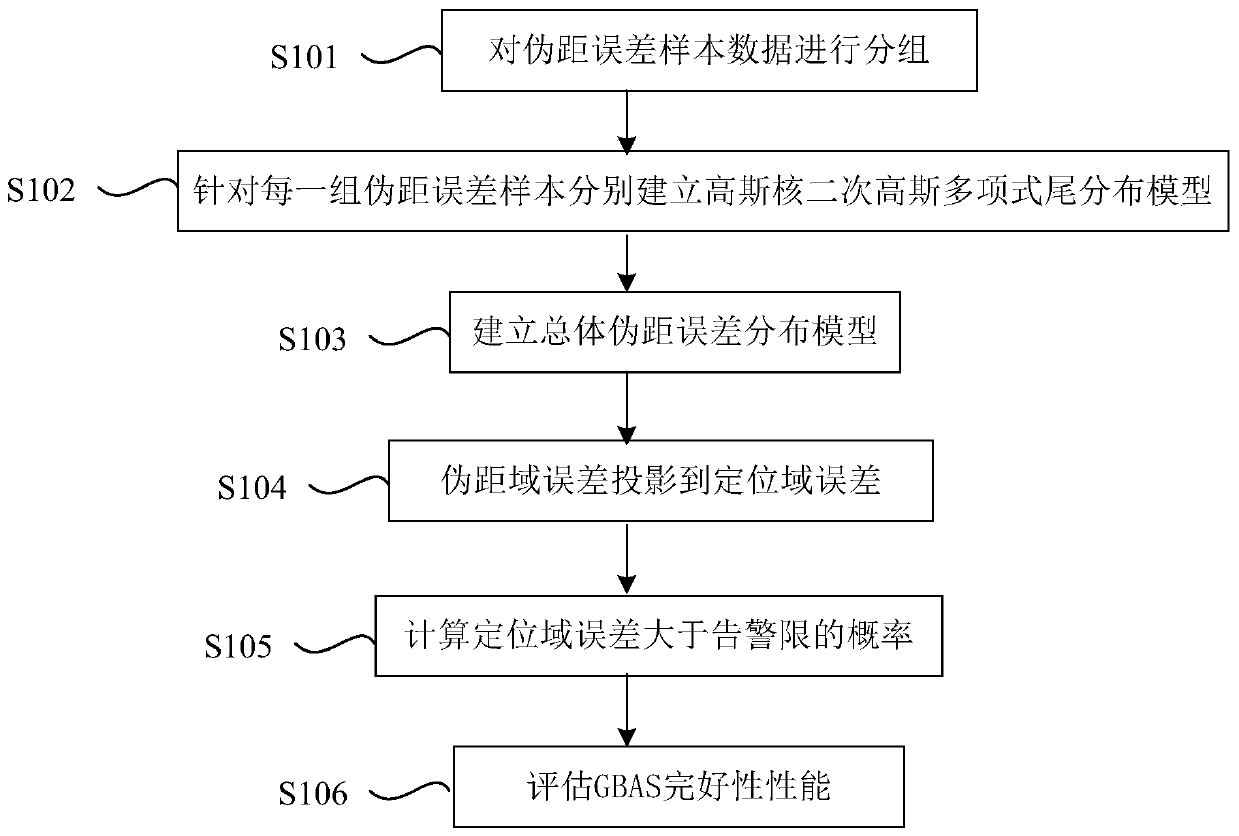
The invention provides a GBAS integrity performance evaluation method based on a pseudo-range error distribution model. The method is characterized in that an airborne receiving end collects pseudo-range error sample data for GBAS integrity performance evaluation, and comprises the following steps: a) grouping the pseudo-range error sample data; b) for each group of pseudo-range error samples, establishing a Gaussian kernel quadratic Gaussian polynomial tail distribution model; c) carrying out weighted sum on each group of pseudo-range error distribution model to obtain an overall pseudo-rangeerror distribution model; d) projecting the pseudo-range domain error to positioning domain error; e) calculating the probability that the positioning domain error is larger than an alarm limit to obtain an integrity risk probability value; and f) evaluating the integrity performance of a GBAS system. The GBAS integrity performance evaluation method based on the pseudo-range error distribution model improves calculation accuracy of the integrity risk probability value and improves effectiveness of integrity assessment.
Owner:BEIHANG UNIV
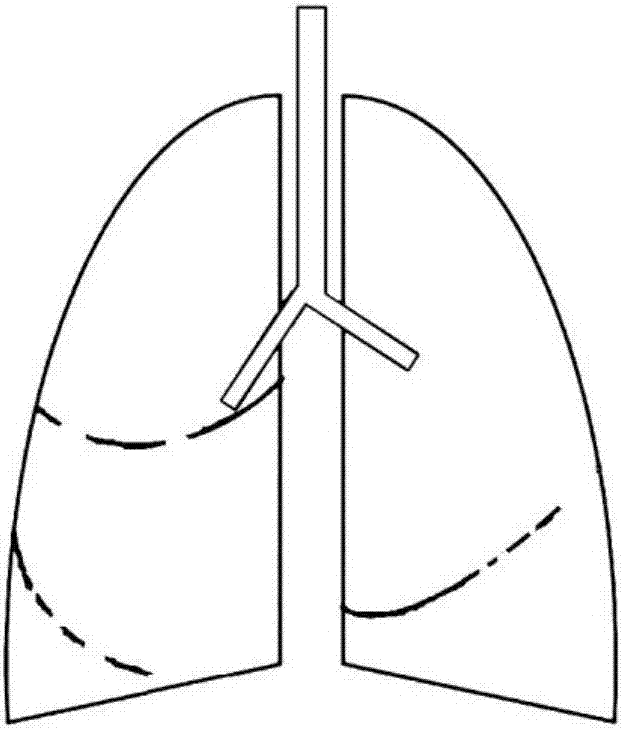
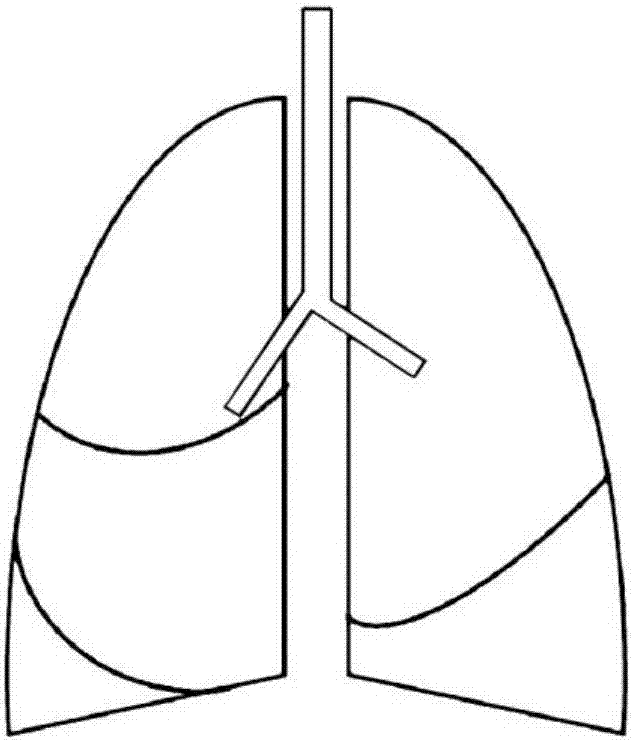
Lung fissure integrity assessment method, device and system
InactiveCN106875379AAccuracy and completenessImprove completeness assessment accuracyImage enhancementImage analysisIntegrity assessmentRadiology
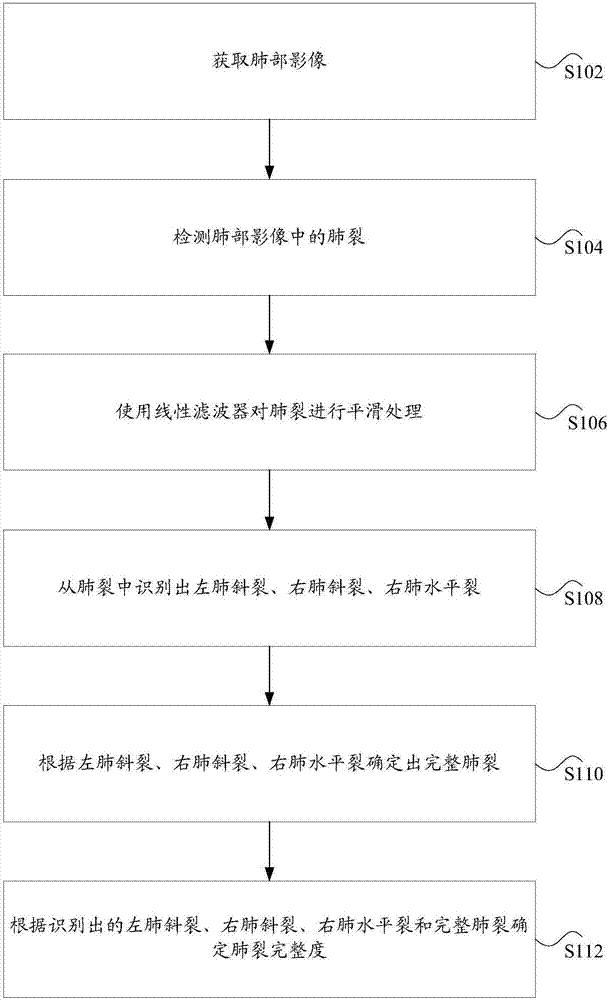
The invention discloses a lug fissure integrity assessment method, device and system. The method comprises the steps: obtaining a lung image; detecting the lung fissure in the lung image; carrying out the smoothing of the lung fissure through a linear filter; recognizing the left lung oblique fissure, right lung oblique fissure and right lung horizontal fissure from the lung fissure; determining the complete lung fissure according to the left lung oblique fissure, right lung oblique fissure and right lung horizontal fissure; and determining the lug fissure integrity according to the recognized left lung oblique fissure, right lung oblique fissure, right lung horizontal fissure and the complete lung fissure. The method solves a technical problem in the prior art that the accuracy of lung fissure assessment is low.
Owner:陕西渭南神州德信医学成像技术有限公司
A trusted network connection system for security enhancement
ActiveCN101242401AImprove securityEasy to manageSecuring communicationIntegrity assessmentTransmission protocol
The invention relates to a safety-enhanced trusted network connecting system, the access requestor is network connected with a policy enforcement point in authentication protocol manner, the access requestor is network connected with an access authorizer by network authorizing transmission protocol interface, integrity evaluation interface and integrity measurement interface, the policy enforcement point is network connected with the access authorizer by policy implementation interface, the access authorizer is network connected with a policy manager by user identification authorization interface, platform evaluation authorization interface and integrity measurement interface, the access requestor is network connected with the policy manager by integrity measurement interface. The invention solves following technology problems: low security, inability of the access requestor to verify the validation of AIK certificate, and non-equivalence of platform integrity evaluation. The invention employs three-element equivalent identification protocol in network access layer and integrity evaluation layer, which improves the whole trusted network connection architecture and extends the application scope of trusted network connection.
Owner:CHINA IWNCOMM
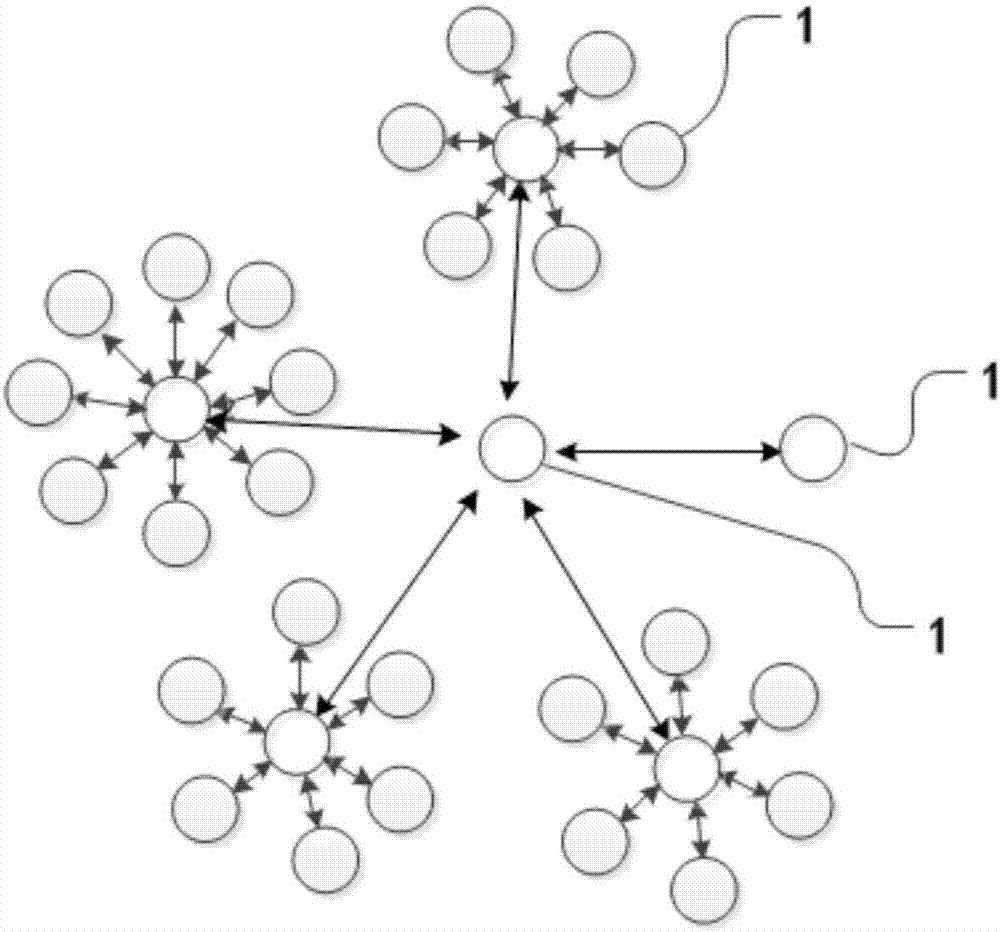
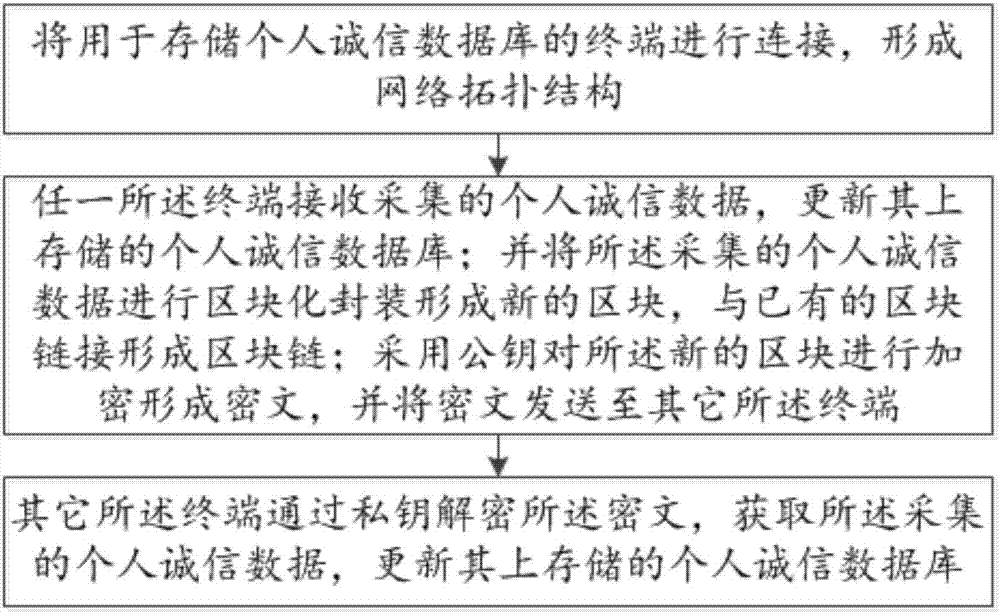
Block-chain-technology-based personal integrity system and implementation method thereof
InactiveCN106910073AAchieve decentralizationRealize distributed sharingCustomer relationshipPublic key for secure communicationIntegrity assessmentCiphertext
The invention relates to a block-chain-technology-based personal integrity system and an implementation method thereof. Terminals for storing personal integrity databases are connected to form a network topology structure; any of the terminals receives collected personal integrity data and updates the stored personal integrity database; block packaging is carried out on the collected personal integrity data to form new blocks and the new blocks and the existing blocks are linked to form a block chain; the new blocks are encrypted by using a public key to form ciphertexts and the ciphertexts are sent to the other terminals; and the other terminals decrypt the ciphertexts by private keys to obtain the collected personal integrity data and then update the stored personal integrity databases. Therefore, on the basis of the block chain technology, the personal integrity data are stored in all participant terminals to realize decentration and distributed sharing of the personal integrity data; the information transparency is high; and the objectivity and reliability of integrity assessment are improved.
Owner:WUHAN HUITONGYUN INFORMATION TECH CO LTD
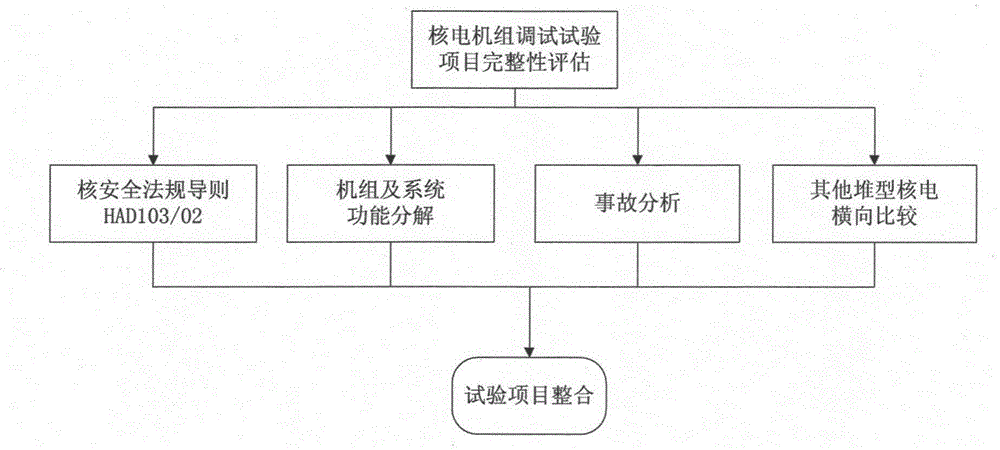
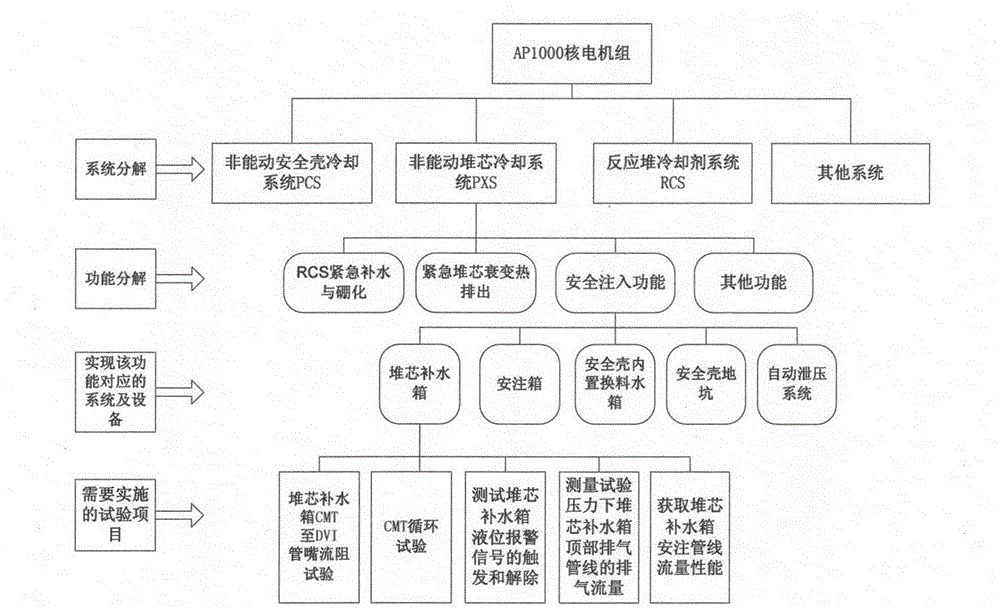
Method for completeness evaluation of nuclear power plant debugging test projects
ActiveCN105304148AComprehensive integrity assessmentIncrease coverageNuclear energy generationNuclear monitoringNuclear plantIntegrity assessment
The invention discloses a method for completeness evaluation of nuclear power plant debugging test projects. The completeness evaluation is performed in four dimensions including a nuclear safety regulatory guideline dimension, a system and machine unit function decomposition dimension, an accident analysis dimension and other reactor type nuclear power plant transverse comparison dimensions; through the four-dimension test project completeness evaluation, the obtained test projects are integrated; relatively complete test projects can be obtained. The test projects evaluated by the invention conform to the requirements of the Chinese nuclear safety regulatory guideline; the verification on the response event sequence of accidents in the nuclear power plant safety probability analysis is included; the important significance is realized on the overall verification of the nuclear power plant design function and requirements and the guarantee of safe and reliable operation of the machine unit.
Owner:SHANGHAI NUCLEAR ENG RES & DESIGN INST CO LTD
GBAS integrity assessment and processing method and system
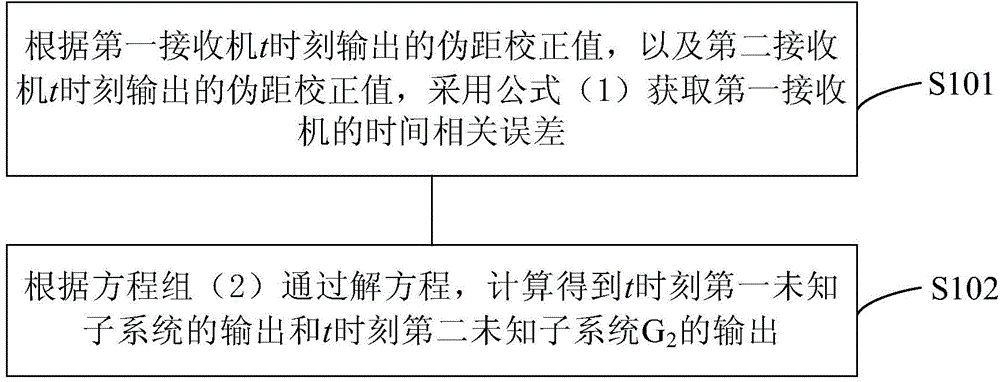
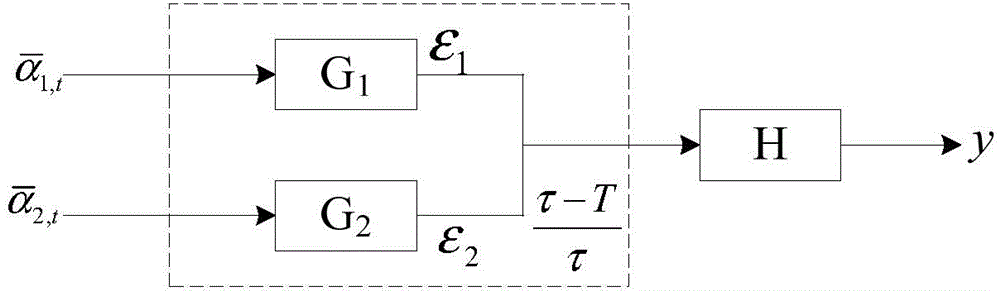
ActiveCN104880713AImprove usabilityHigh sampling frequencySatellite radio beaconingIntegrity assessmentModel parameters
The invention provides a GBAS integrity assessment and processing method and system. The method comprises the steps of obtaining a time-related error of a GBAS, decomposing the obtained linear system based on the time-related error to obtain a first unknown sub system G1, a second unknown sub system G2 and a known sub system H; conducting timing model fitting for the first unknown sub system G1 and the second unknown sub system G2 respectively to obtain the model parameter and fitting residue of the first unknown sub system G1 and the model parameter and fitting residue of the second unknown sub system G2; obtaining the envelope of the time-related error according to the model parameter and fitting residue of the first unknown sub system G1, the model parameter and fitting residue of the second unknown sub system G2, and the unit pulse response of the unknown sub system H; obtaining the protection level of the GBAS according to the envelope of the time-related error; and comparing the protection level and a preset alarm limit, and generating an alarm signal when the protection level exceeds the preset alarm limit.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com