Side-channel attack resisting processor architecture based on random instruction delay
A processor architecture and bypass attack technology, applied in the field of information security, can solve problems such as reducing the signal-to-noise ratio of DPA attacks, and achieve the effect of enhancing the ability to resist side-channel attacks and increasing the number of states.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] All features disclosed in this specification, or steps in all methods or processes disclosed, may be combined in any manner, except for mutually exclusive features and / or steps.
[0047] The present invention will be described in further detail below in conjunction with the accompanying drawings.
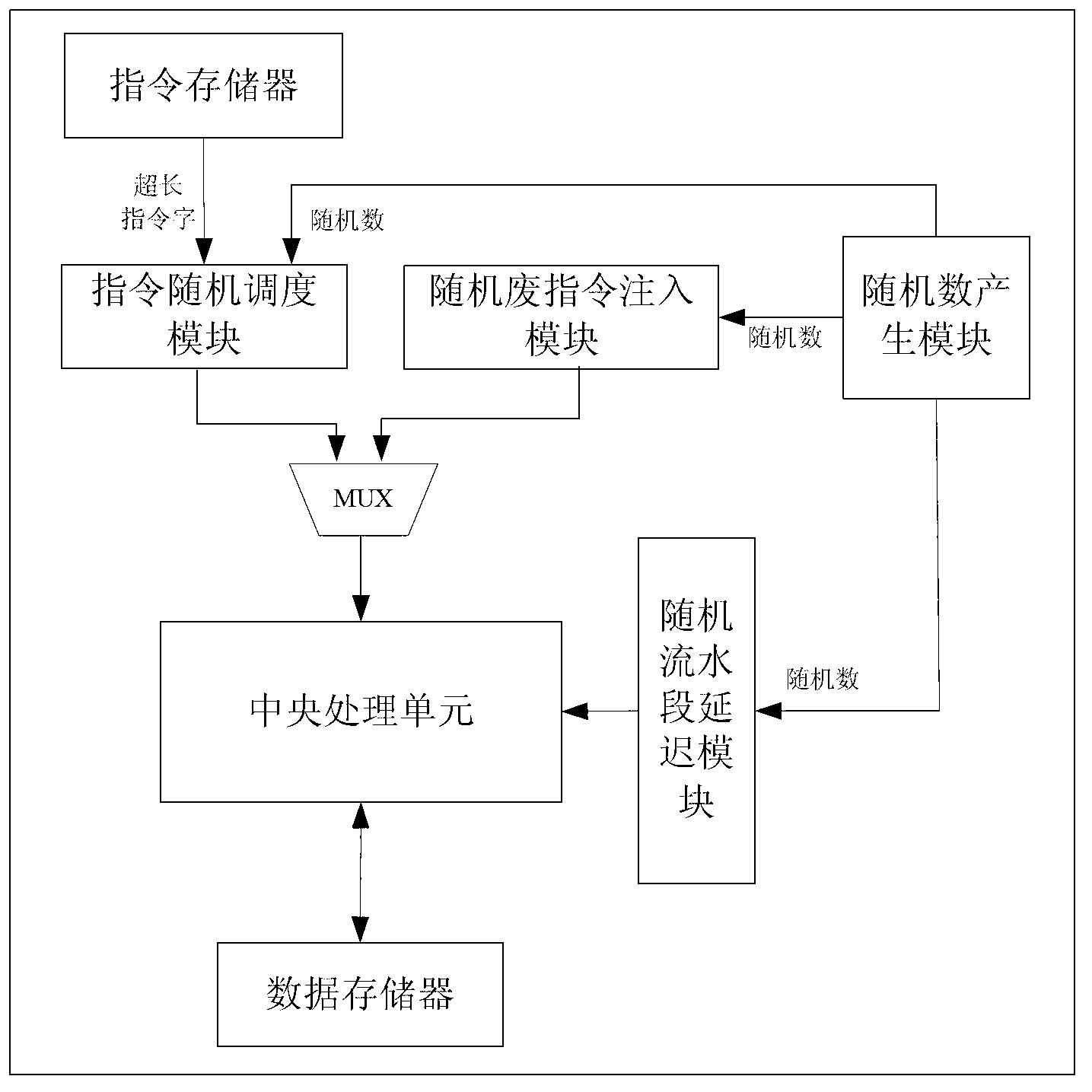
[0048] figure 1 Shown is a block diagram of the processor architecture of the present invention, and the instruction storage of the present invention is used to store all super long instruction words required by the instruction random scheduling module;
[0049] The instruction random scheduling module can randomly schedule multiple instructions that can be executed in parallel and issue them out of order;
[0050] The data memory is used to store the data required for execution by the central processing unit;
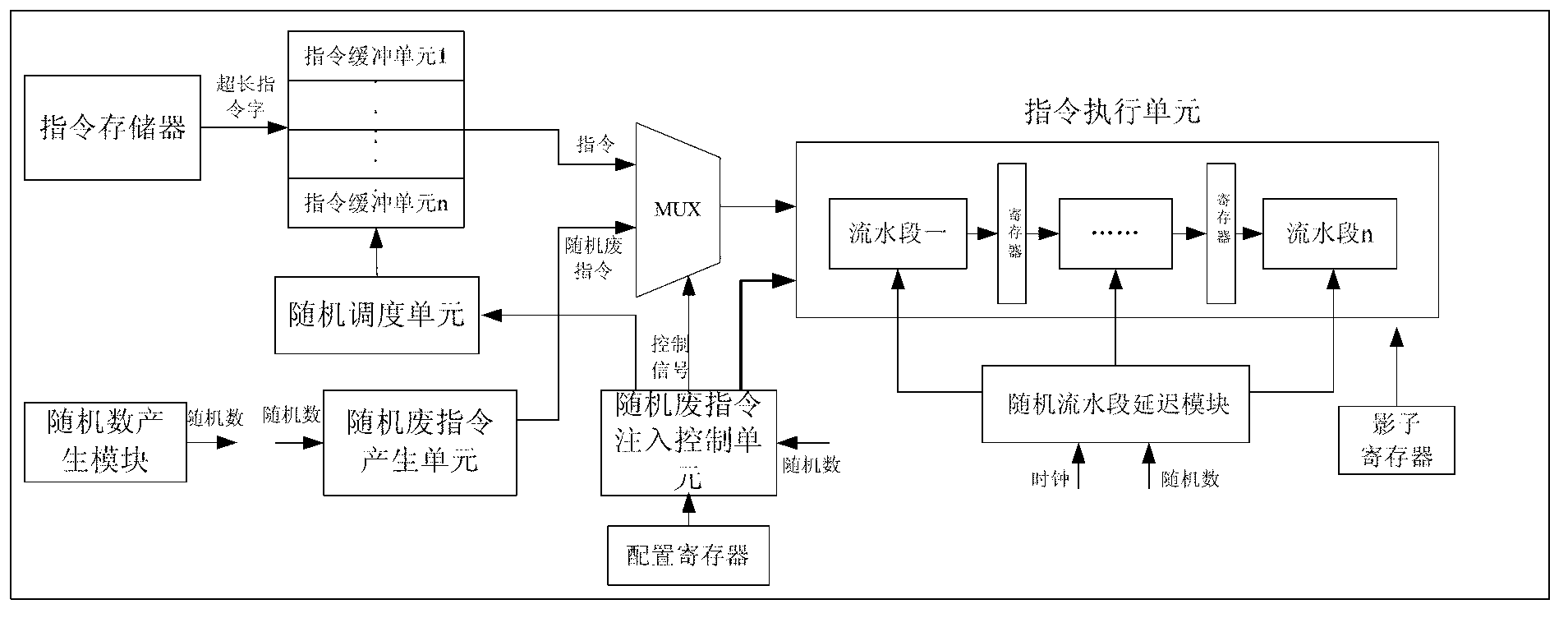
[0051] The central processing unit is used to execute instructions, that is, an instruction execution unit, and the instruction execution unit is divided into n pip...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com