Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
573 results about "Randomization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Randomization is the process of making something random; in various contexts this involves, for example...
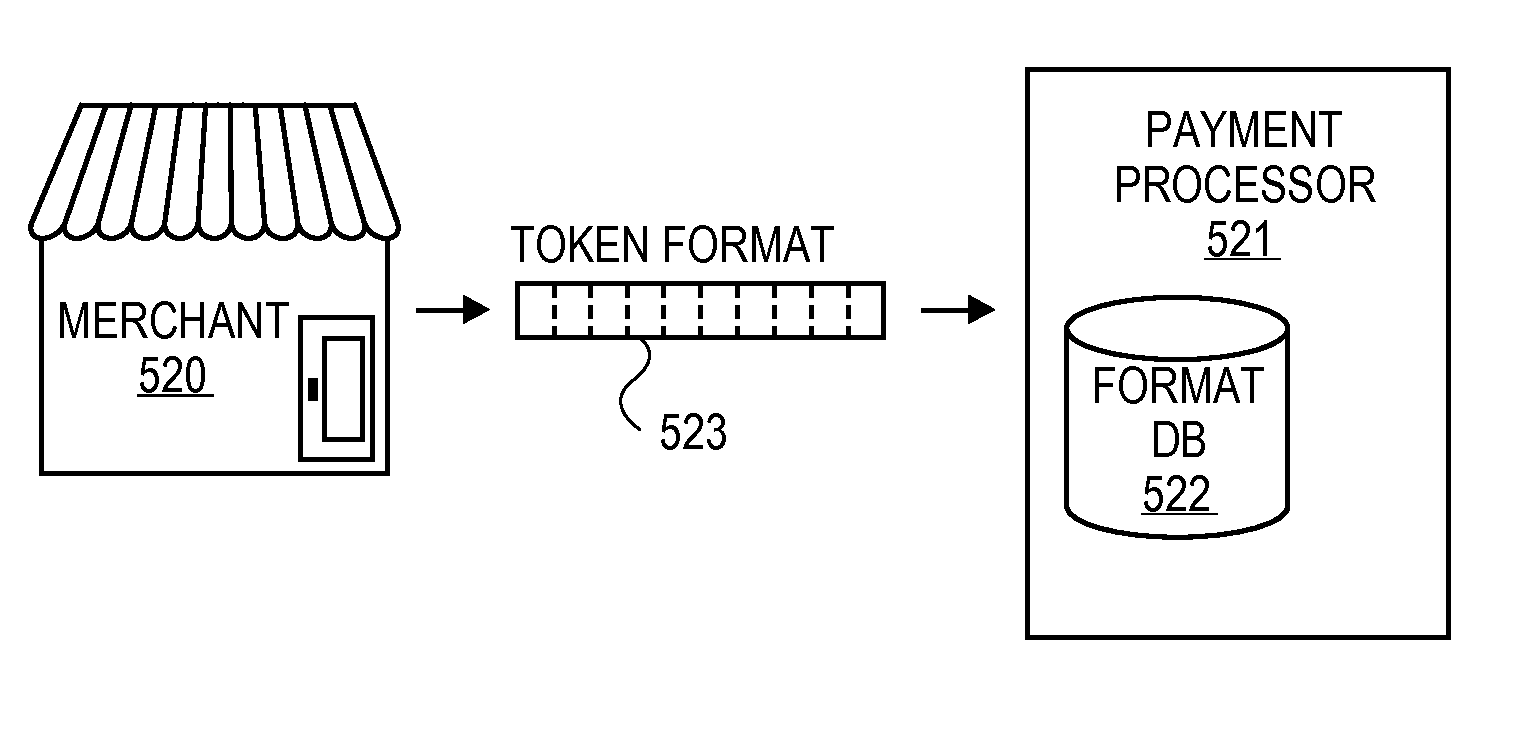
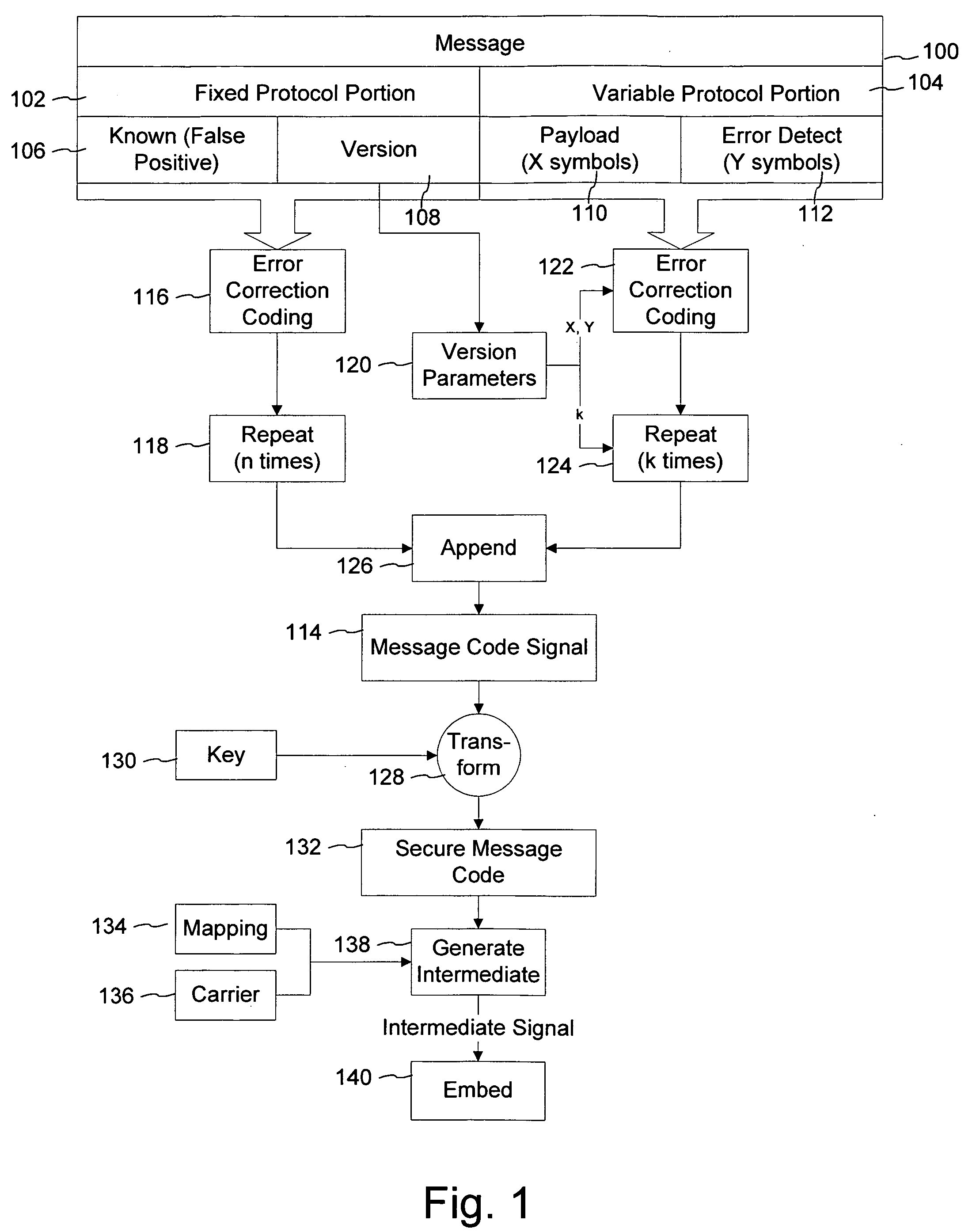
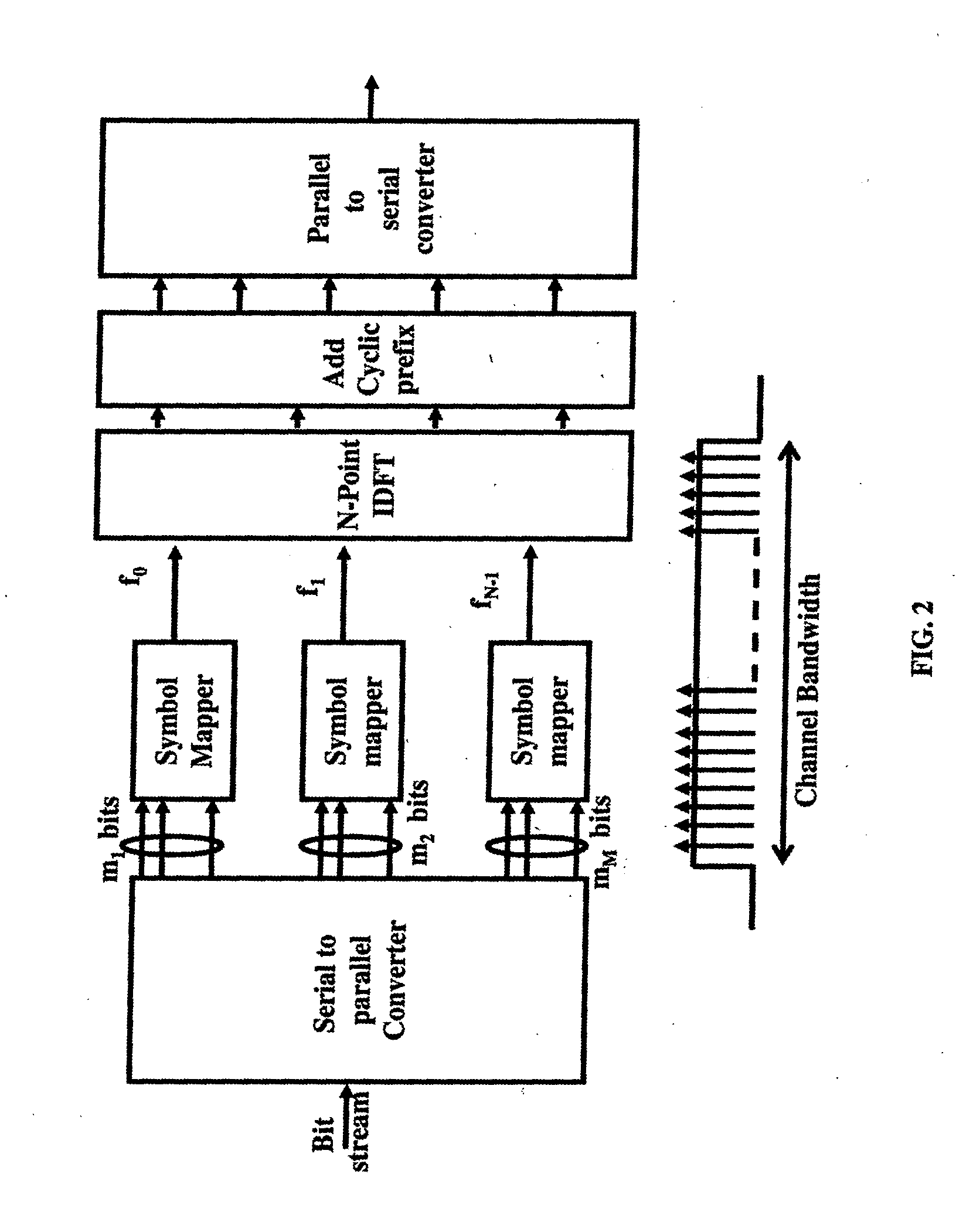
Configurable payment tokens
Methods and systems are disclosed for the generation and use of merchant-customizable token formats that define tokens that represent credit card and other payment numbers in online transactions. The tokens, which are used instead of the card numbers themselves for security, can be specified by the token format to have a certain number of characters, have certain fields reserved for major card identifiers, use encryption and / or randomization, be alphanumeric, and have other formatting. The customized tokens can be used with legacy equipment that uses longer or shorter card numbers than the standard sixteen-digit payment card number format and can be less likely to be recognized as related to card numbers by identify thieves.
Owner:VISA USA INC (US)
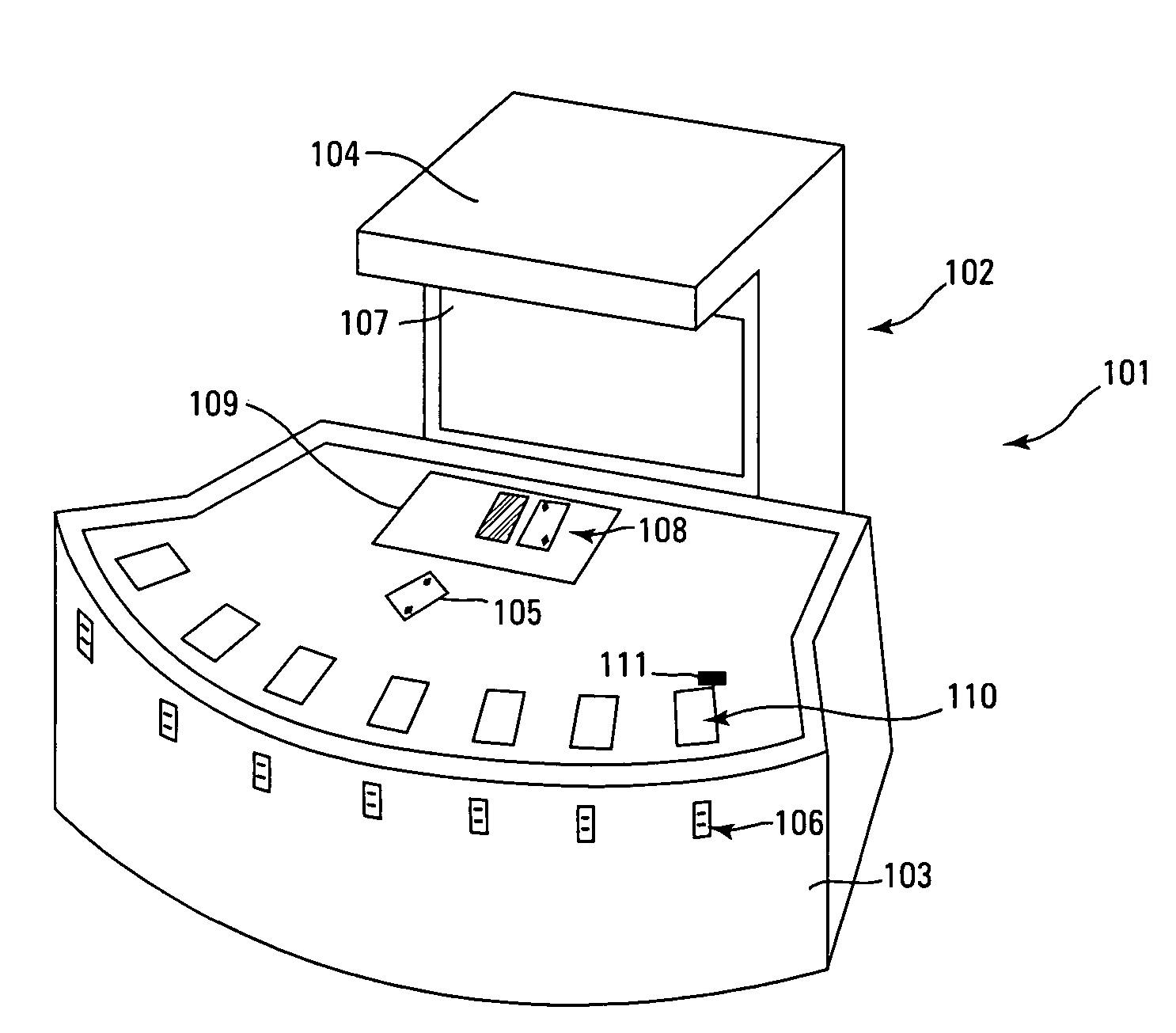
Card shuffler with reading capability integrated into multiplayer automated gaming table
A gaming system simulates events in a casino table card wagering game where there has traditionally been a dealer, whether or not the dealer is an active player in the game. Two distinct video areas are preferably provided, one providing video images of a virtual dealer, and the second video display providing a simulation of a table top for player cards, and optionally also dealer cards. The players have individual play areas with player input, and these play areas have individual processing intelligence that communicates directly with at least one processor. Delivery order of cards is determined by actual shuffling or randomization of a physical deck of cards, reading the cards, then creating an electronic file of the order of the shuffled or randomized cards, then using an order of cards contained in the electronic file to deliver virtual cards to players, dealer and flop as needed.
Owner:LNW GAMING INC
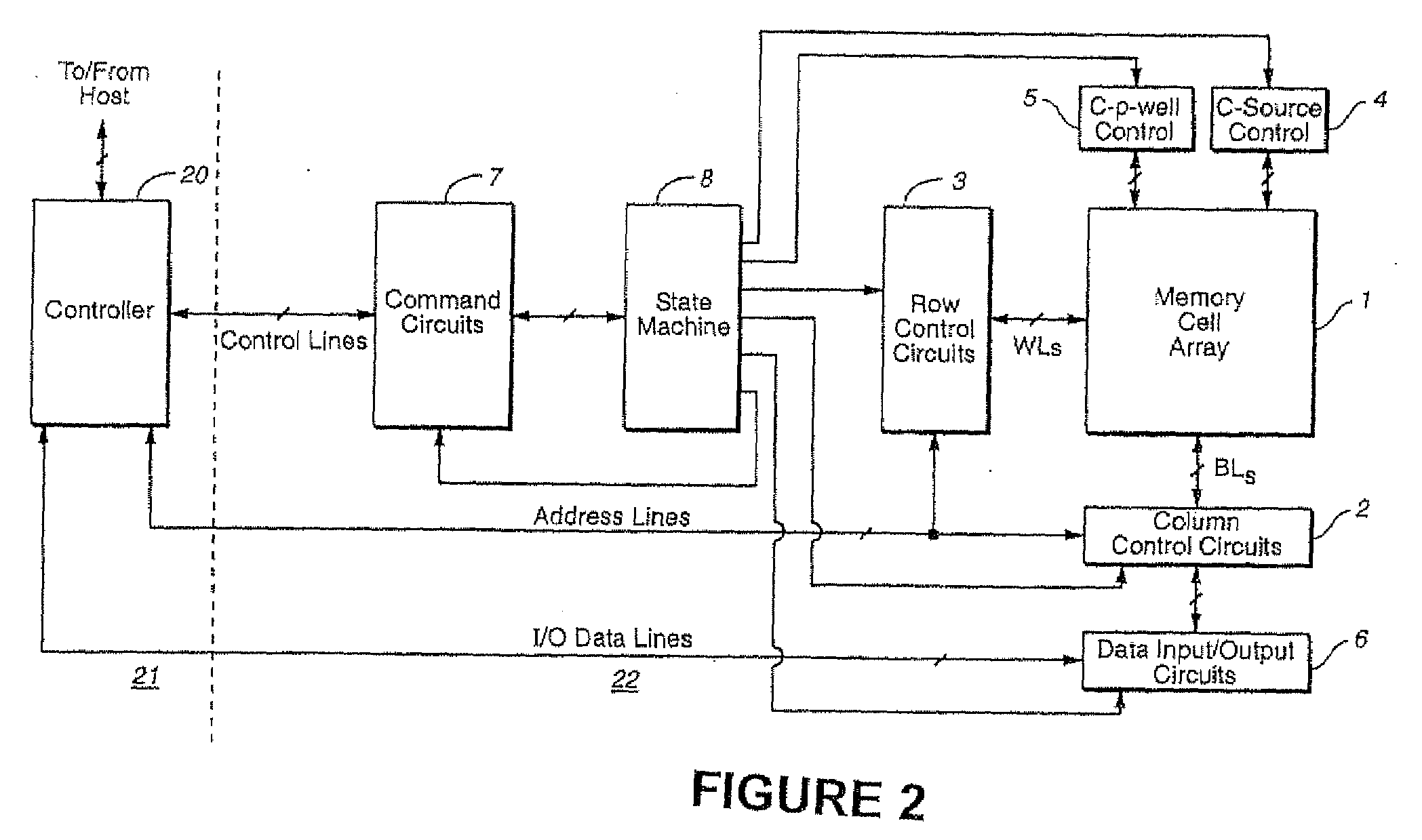
Randomizing for suppressing errors in a flash memory
Original data to be stored in a nonvolatile memory are first randomized while preserving the size of the original data, In response for a request for the original data, the randomized data are retrieved, derandomized and exported without authenticating the requesting entity. ECC encoding is applied either before or after randomizing; correspondingly, ECC decoding is applied either after or before derandomizing.
Owner:SANDISK TECH LLC
Method and apparatus for printing raster lines in a selective deposition modelling system
InactiveUS6136252AImprove system throughputSimple technologyAdditive manufacturing apparatusAuxillary shaping apparatusGratingSelective deposition
Owner:3D SYST INC
Access probe randomization for wireless communication system
ActiveUS20070076682A1Reduce collisionAvoid collisionNetwork traffic/resource managementTime-division multiplexCommunications systemStart time
A method and apparatus for randomizing access probes from co-located mobile terminals in order to reduce collisions is provided. By each mobile terminal or group of mobile terminals computing a random delay between a minimum delay value and a maximum delay value and using the random delay to delay the starting time of access probes, collisions between access probes from different mobile terminals may be reduced.
Owner:LG ELECTRONICS INC
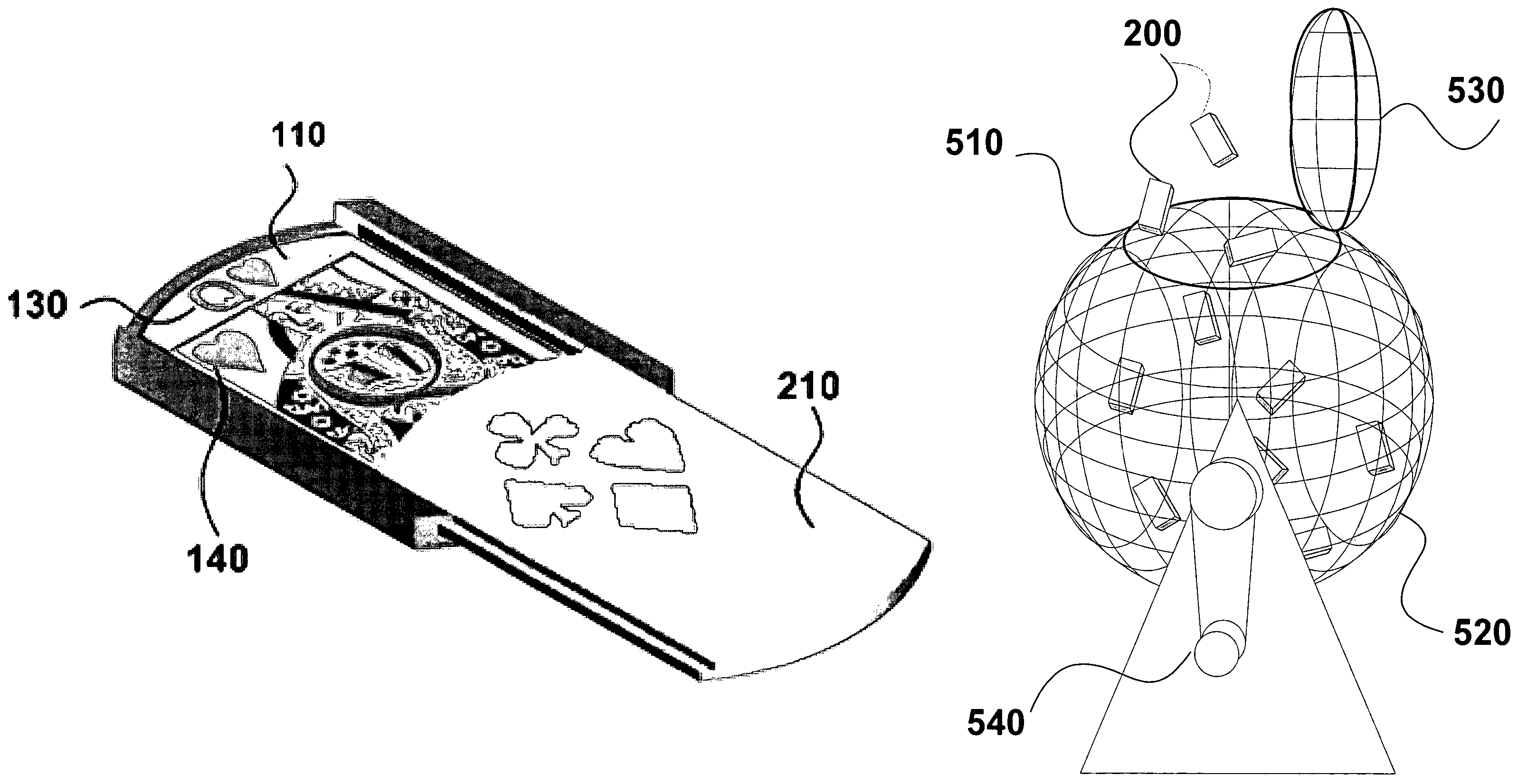
Playing card system
InactiveUS7549643B2Manipulation can be minimizedLottery apparatusBoard gamesPlaying cardRandomization
A playing card system is disclosed comprising a face side displaying markings, which can be hidden and revealed by an adjustable barrier. A set of these playing cards may be used in the same games as those using a standard deck of cards. A shuffler randomizes the order and / or arrangement of the one or more sets through an agitation mechanism. The shuffling system allows for heightened randomization and secrecy of the markings, and minimizes opportunities for manipulation.
Owner:QUACH BINH
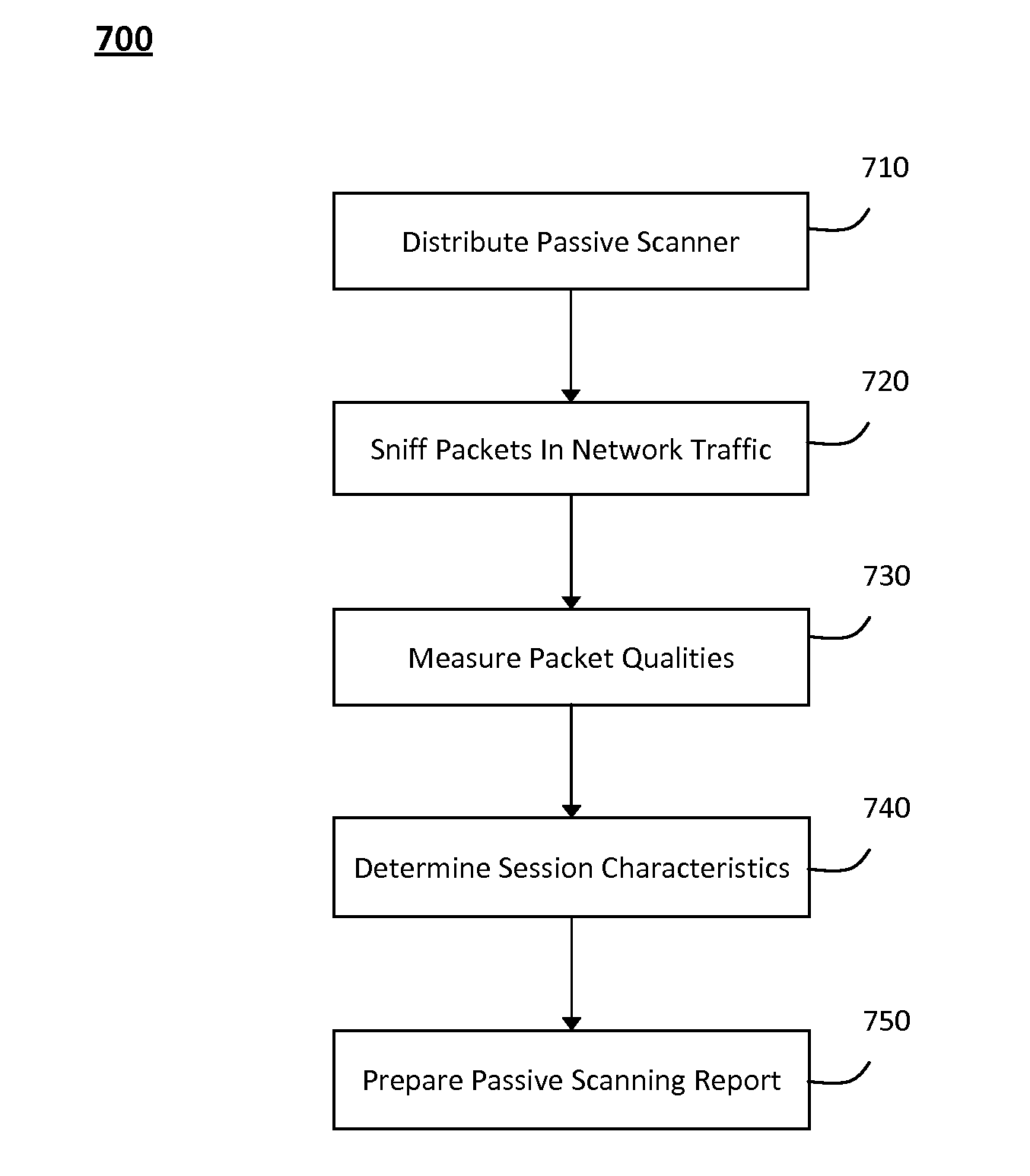
System and method for passively identifying encrypted and interactive network sessions
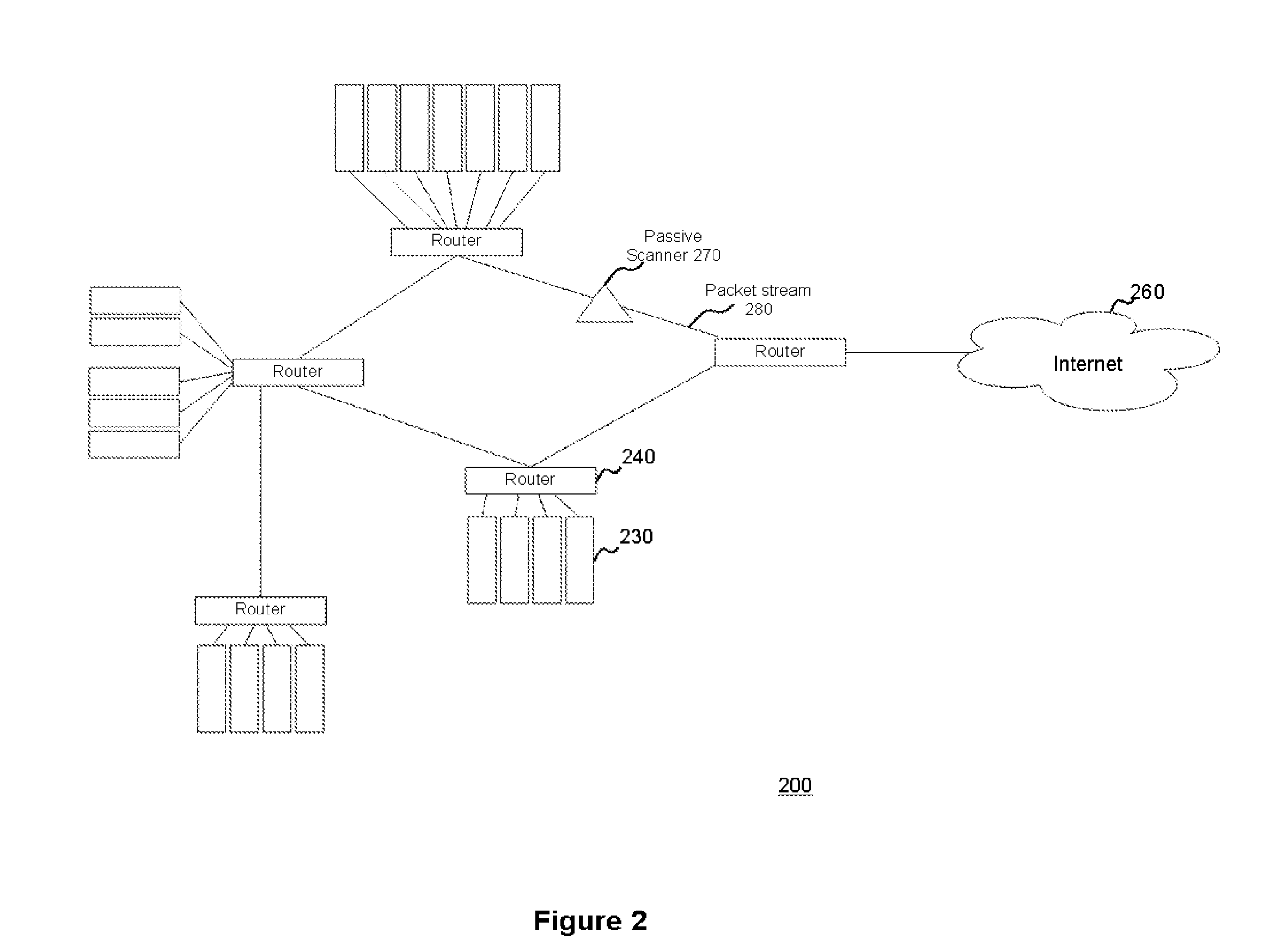
The system and method for passively identifying encrypted and interactive network sessions described herein may distribute a passive vulnerability scanner in a network, wherein the passive vulnerability scanner may observe traffic travelling across the network and reconstruct a network session from the observed traffic. The passive vulnerability scanner may then analyze the reconstructed network session to determine whether the session was encrypted or interactive (e.g., based on randomization, packet timing characteristics, or other qualities measured for the session). Thus, the passive vulnerability scanner may monitor the network in real-time to detect any devices in the network that run encrypted or interactive services or otherwise participate in encrypted or interactive sessions, wherein detecting encrypted and interactive sessions in the network may be used to manage changes and potential vulnerabilities in the network.
Owner:TENABLE INC
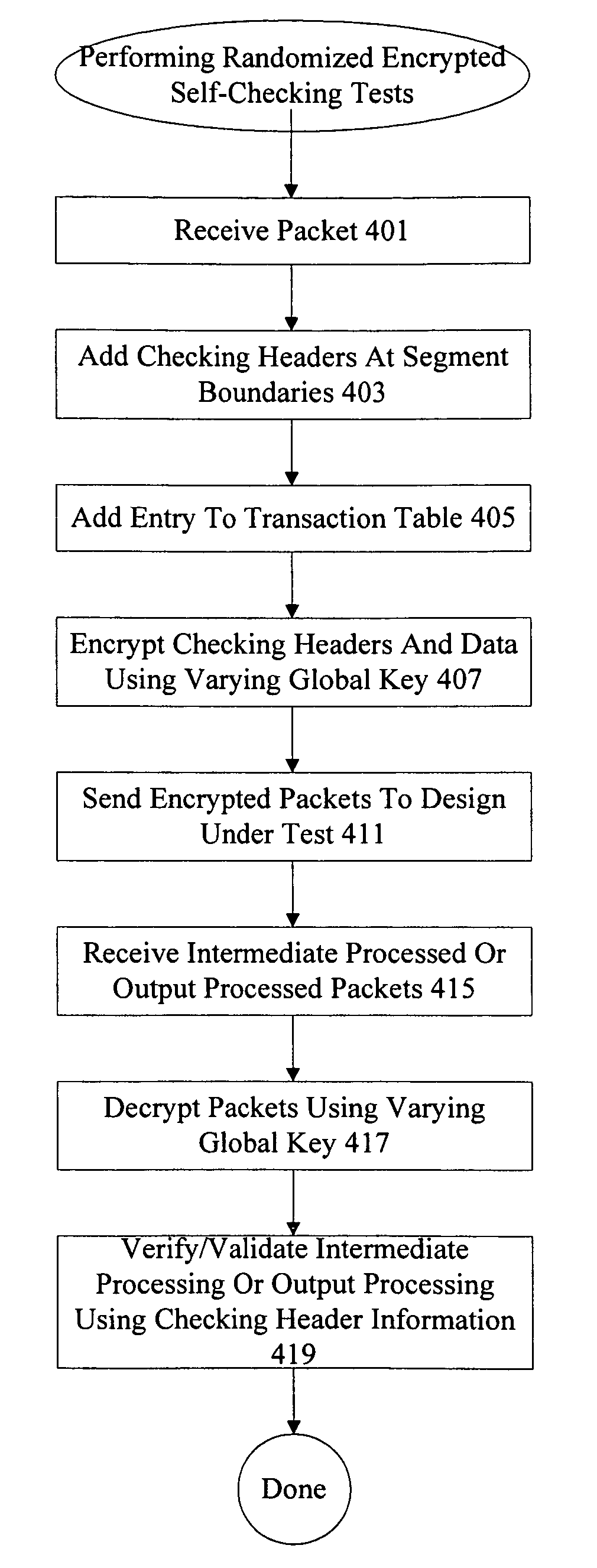
Randomized self-checking test system
ActiveUS7334178B1Data representation error detection/correctionElectrical testingRandomizationData sequences
Methods and apparatus are provided for verifying and validating operation of a design under test (DUT). Input data sequences having information used to check expected outputs are provided to a DUT. The input data sequences include checking headers and data. The checking headers and data are randomized using encryption to verify and validate operation of the DUT on a variety of bit sequences. Different keys are used to allow further scrambling.
Owner:ORACLE INT CORP
System for establishing a cryptographic key depending on a physical system
ActiveUS20120072737A1Reduction of informationReduce decreaseKey distribution for secure communicationDigital data processing detailsComputer hardwareCryptographic nonce
In systems for establishing a cryptographic key depending on a physical uncloneable function (PUF) it may be a problem that internal information correlated with the cryptographic key is leaked to the outside of the system via a side-channel. To mitigate this problem a cryptographic system for reproducibly establishing a cryptographic key is presented. The system comprises a physical system comprising a physical, at least partially random, configuration of components from which an initial bit-string is derived. An error corrector corrects deviations occurring in the initial bit-string. Through the use of randomization the error corrector operates on a randomized data. Information leaking through a side channel is thereby reduced. After error correction a cryptographic key may be derived from the initial bit-string.
Owner:INTRINSIC ID
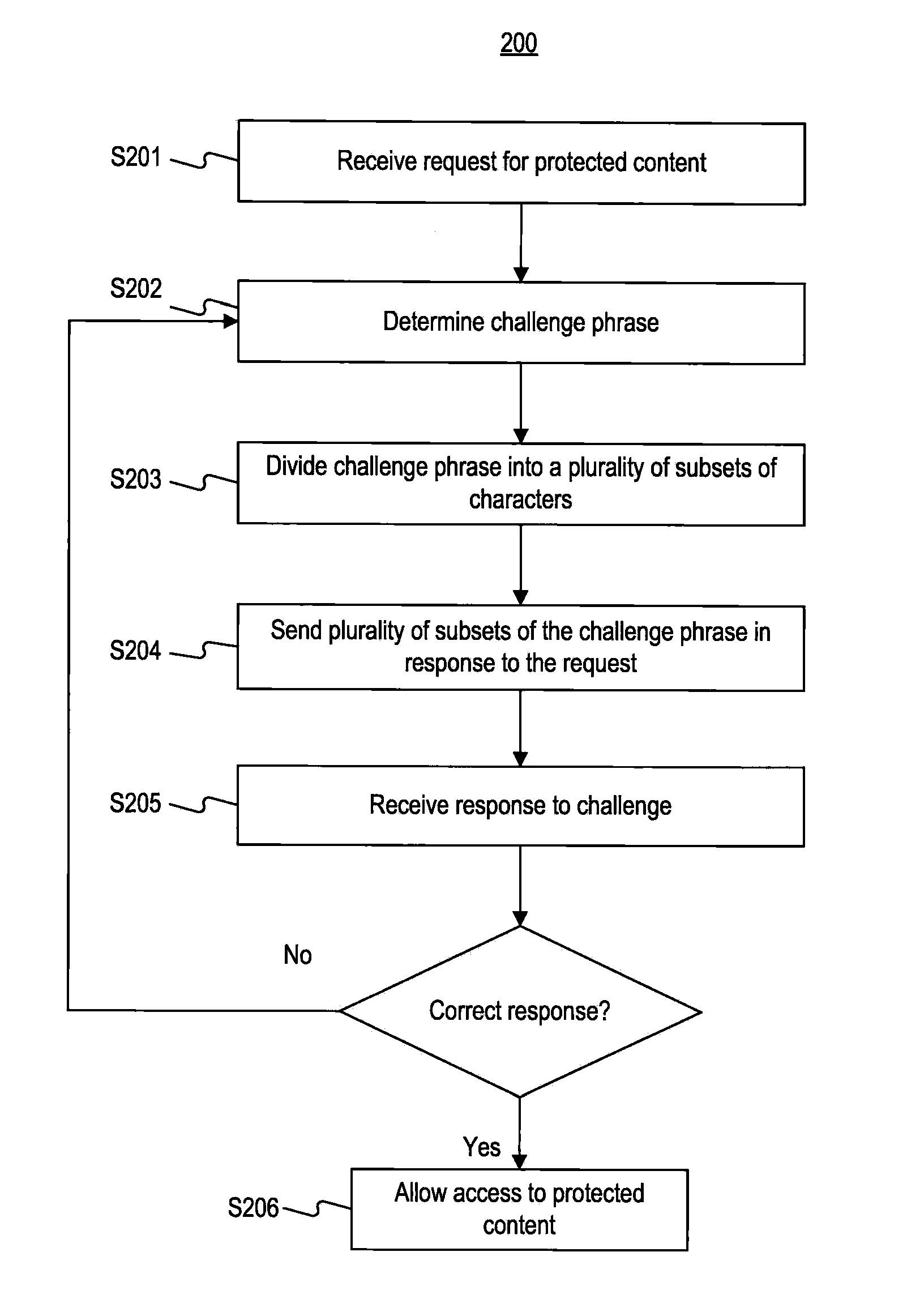
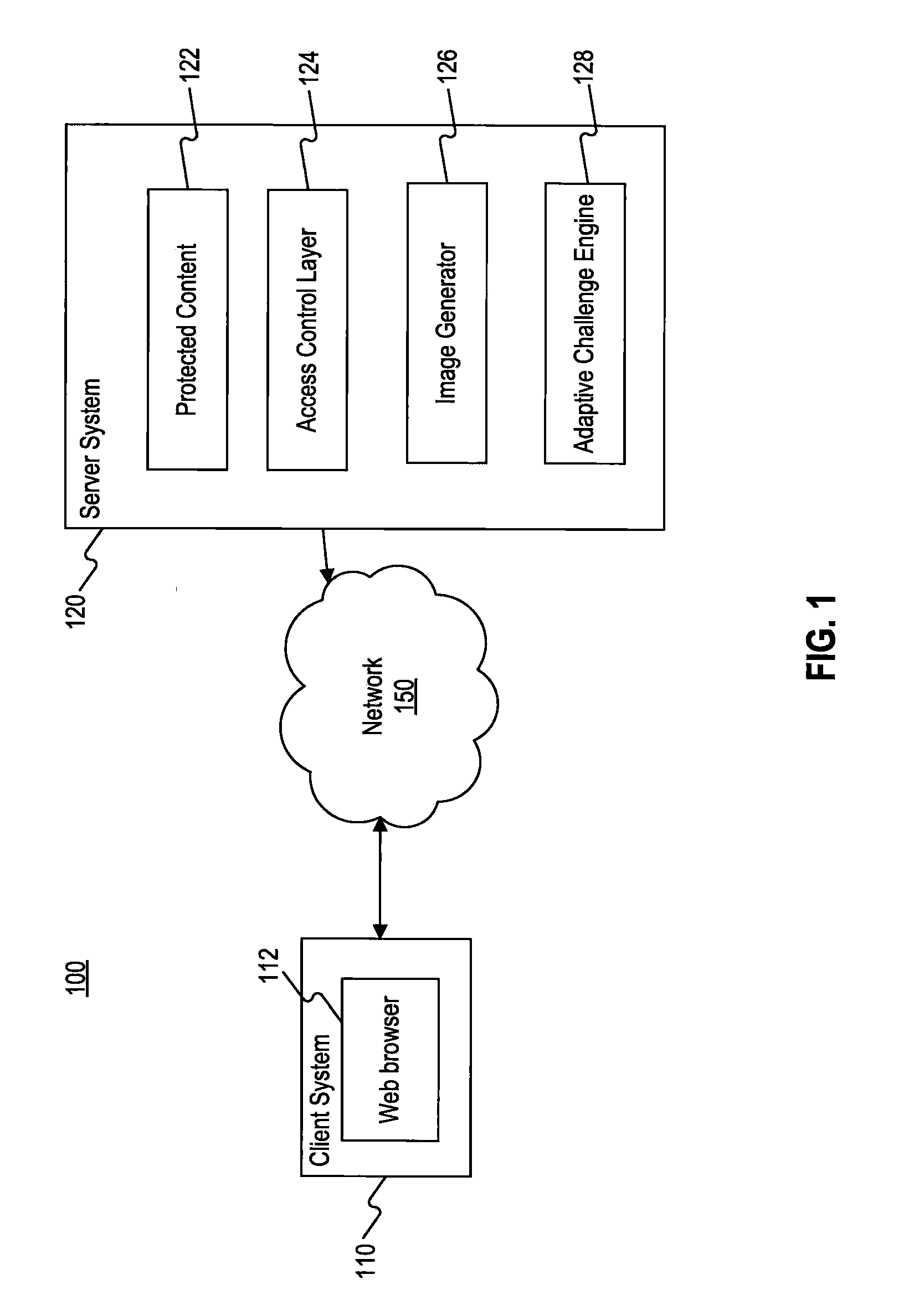
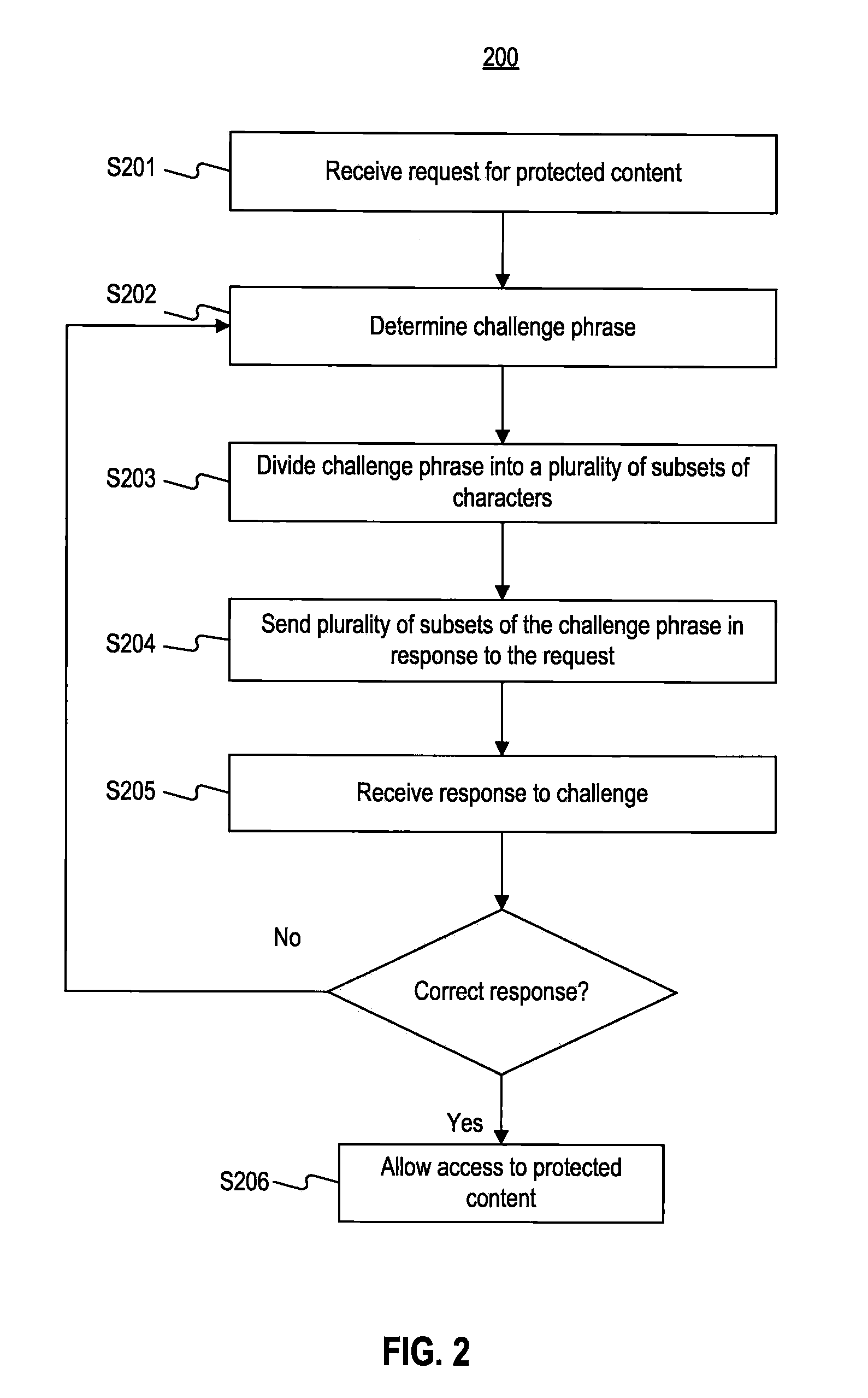
Systems and Methods for Challenge-Response Animation and Randomization Testing
ActiveUS20100251388A1Limited accessAccess to protected is limitedDigital data processing detailsUser identity/authority verificationAnimationInternet privacy
Systems and methods are provided for challenge / response animation. In one implementation, a request for protected content may be received from a client, and the protected content may comprise data. A challenge phrase comprising a plurality of characters may be determined, and a computer processor may divide the challenge phrase into at least two character subsets selected from the characters comprising the challenge phrase. Each of the at least two character subsets may include less than all of the characters comprising the challenge phrase. The at least two character subsets may be sent to the client in response to the request; and an answer to the challenge phrase may be received from the client in response to the at least two character subsets. Access to the protected content may be limited based on whether the answer correctly solves the challenge phrase.
Owner:VERIZON PATENT & LICENSING INC
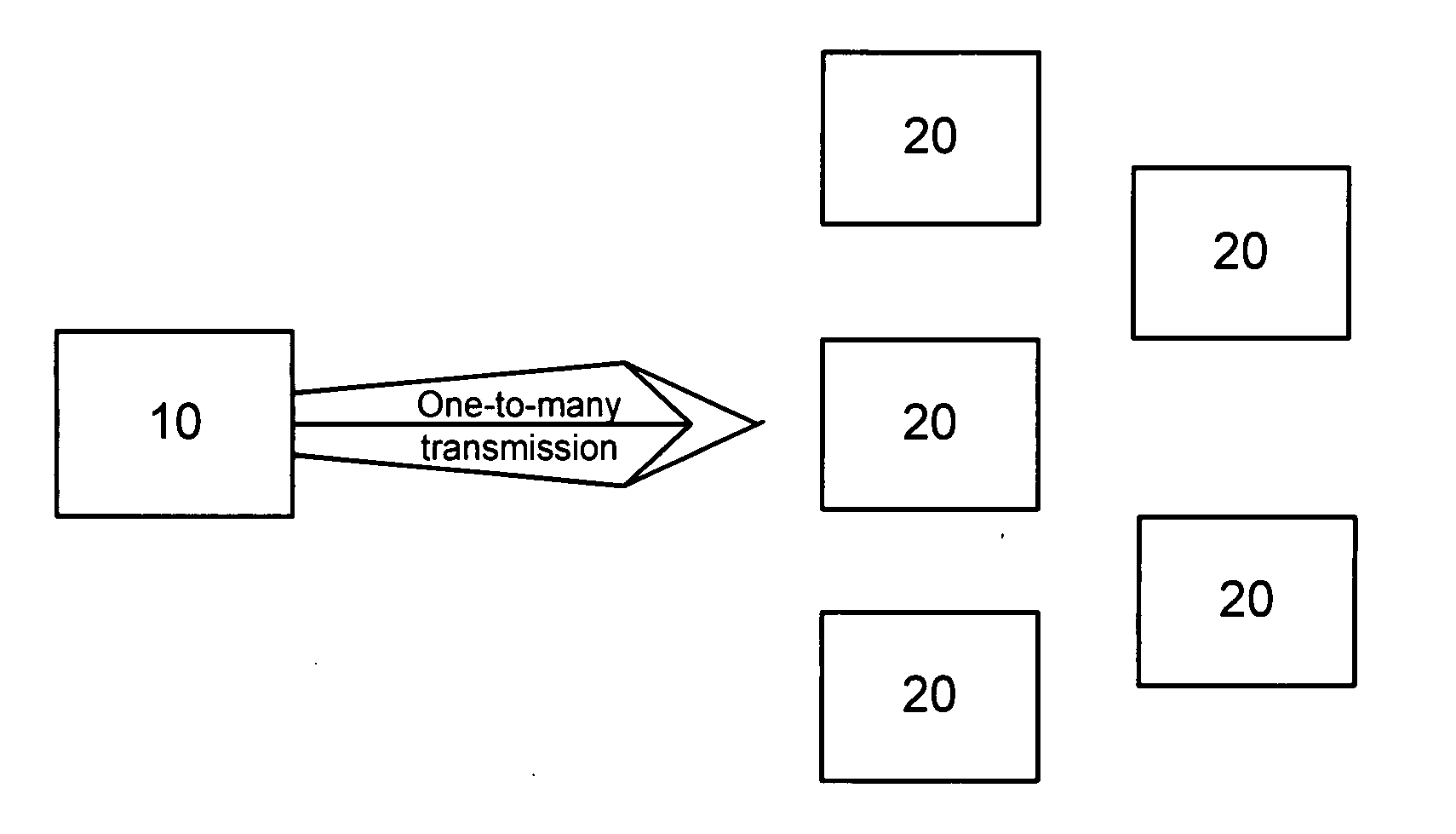
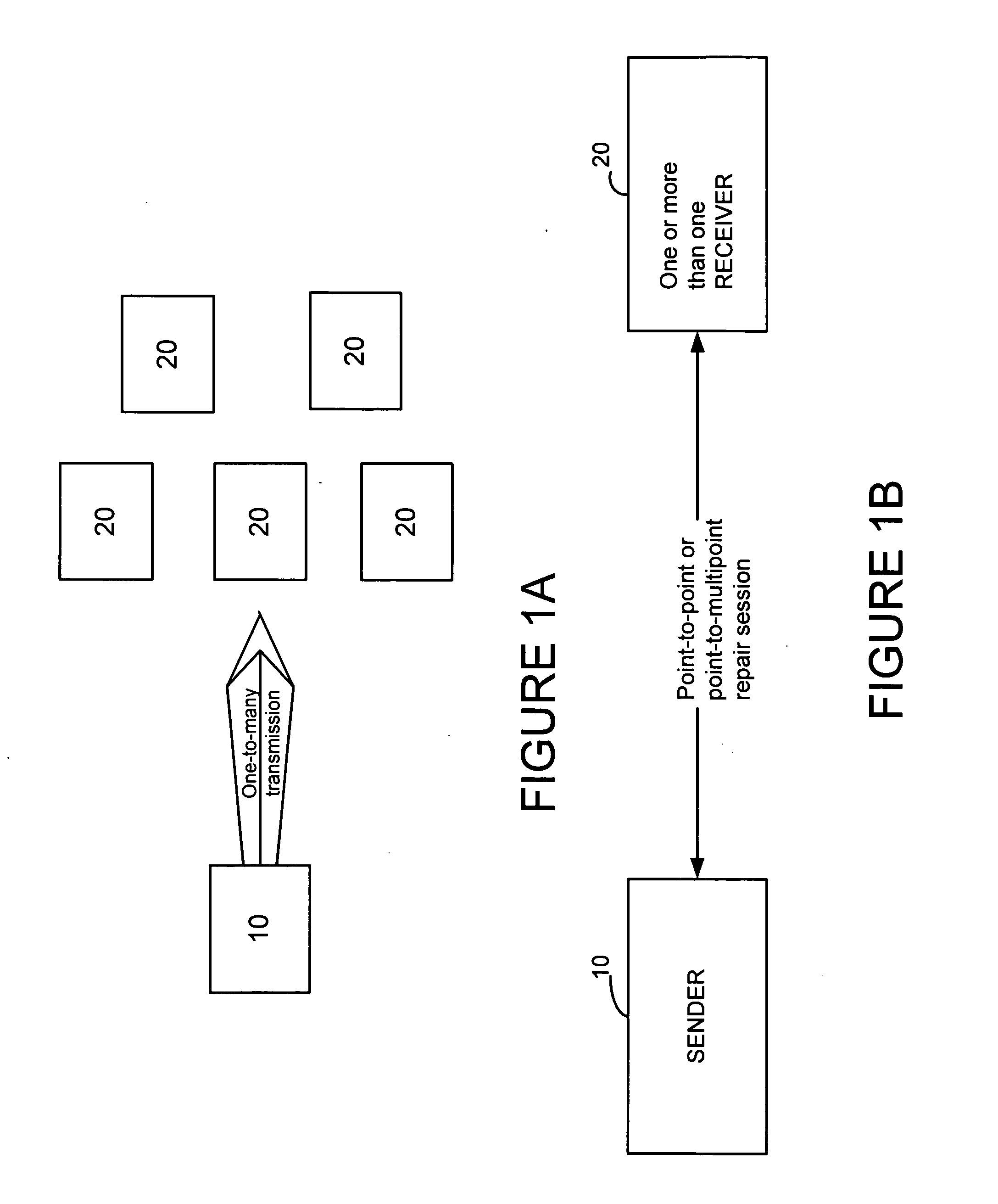
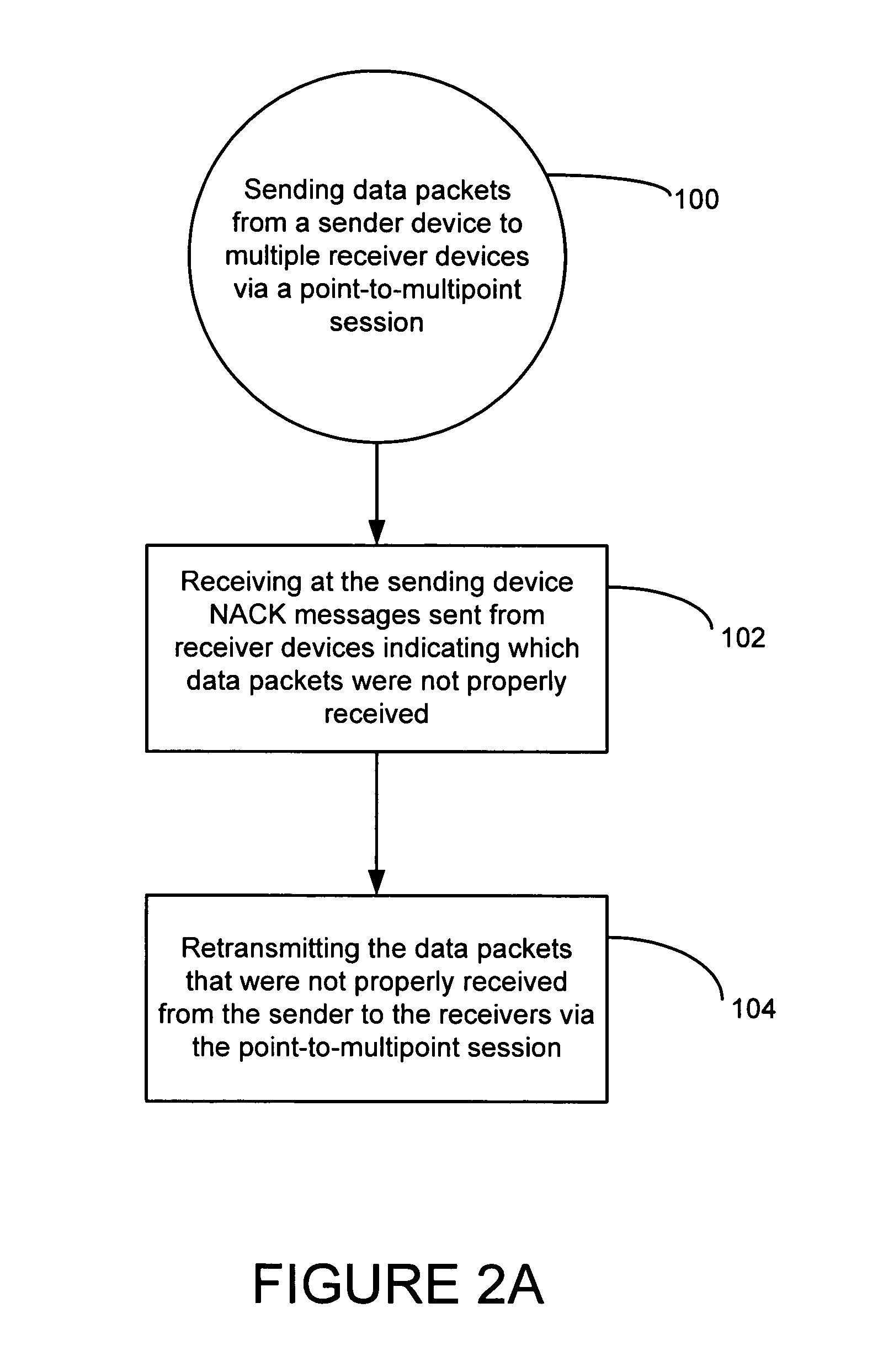
Data repair enhancements for multicast/broadcast data distribution
ActiveUS20050216812A1Special service provision for substationError prevention/detection by using return channelBroadcast dataRandomization
A method, system, device, and computer code product is disclosed in which a sender transmits data to a plurality of receivers via a point-to-multipoint session. The receiver sends data repair requests to the sender requesting data expected but not received and the sender retransmits the expected but not received data via the point-to-multipoint session. The sender can also schedule point-to-point data repair sessions with individual receivers if the retransmission via the point-to-multipoint session does not correct all errors. The sender can be configured to delay point-to-point repair sessions using a randomization mechanism based on the number of receivers using the point-to-multipoint session.
Owner:NOKIA TECHNOLOGLES OY
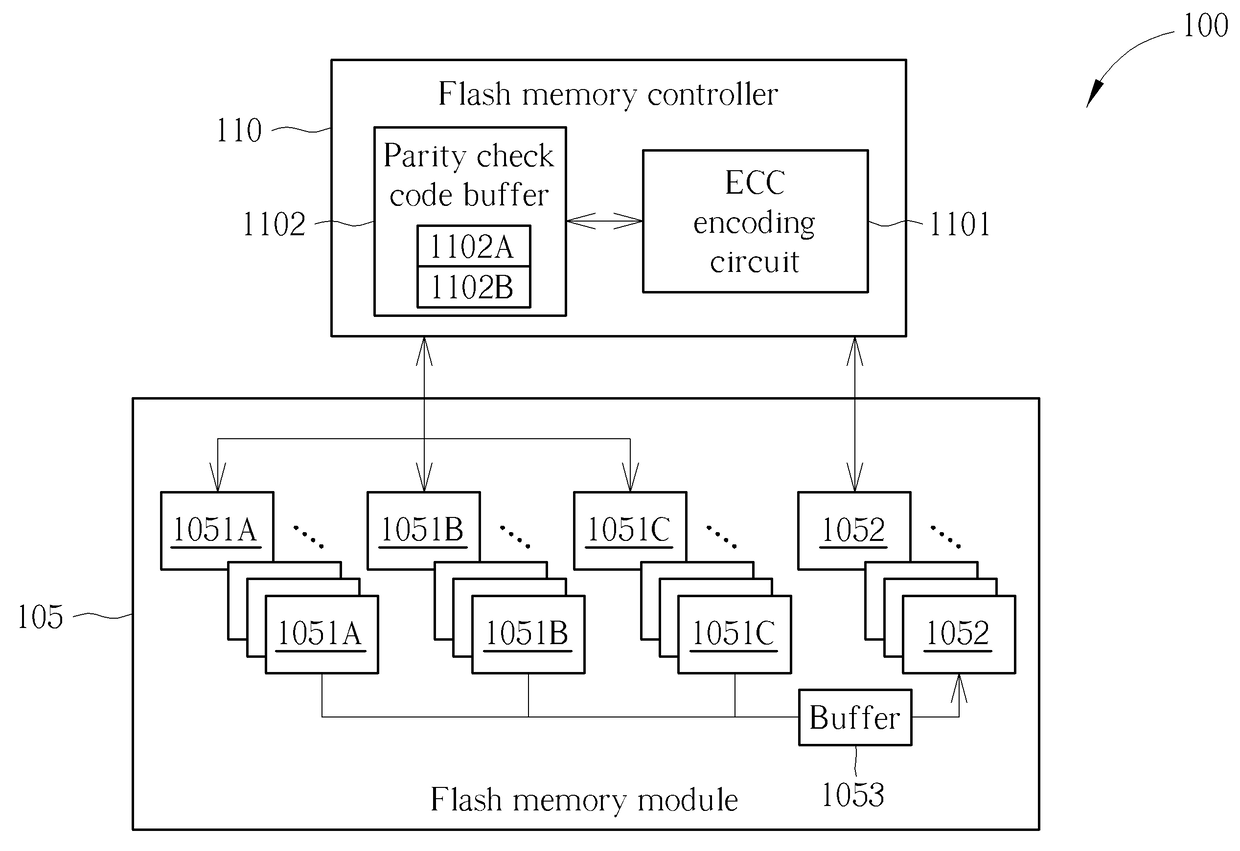
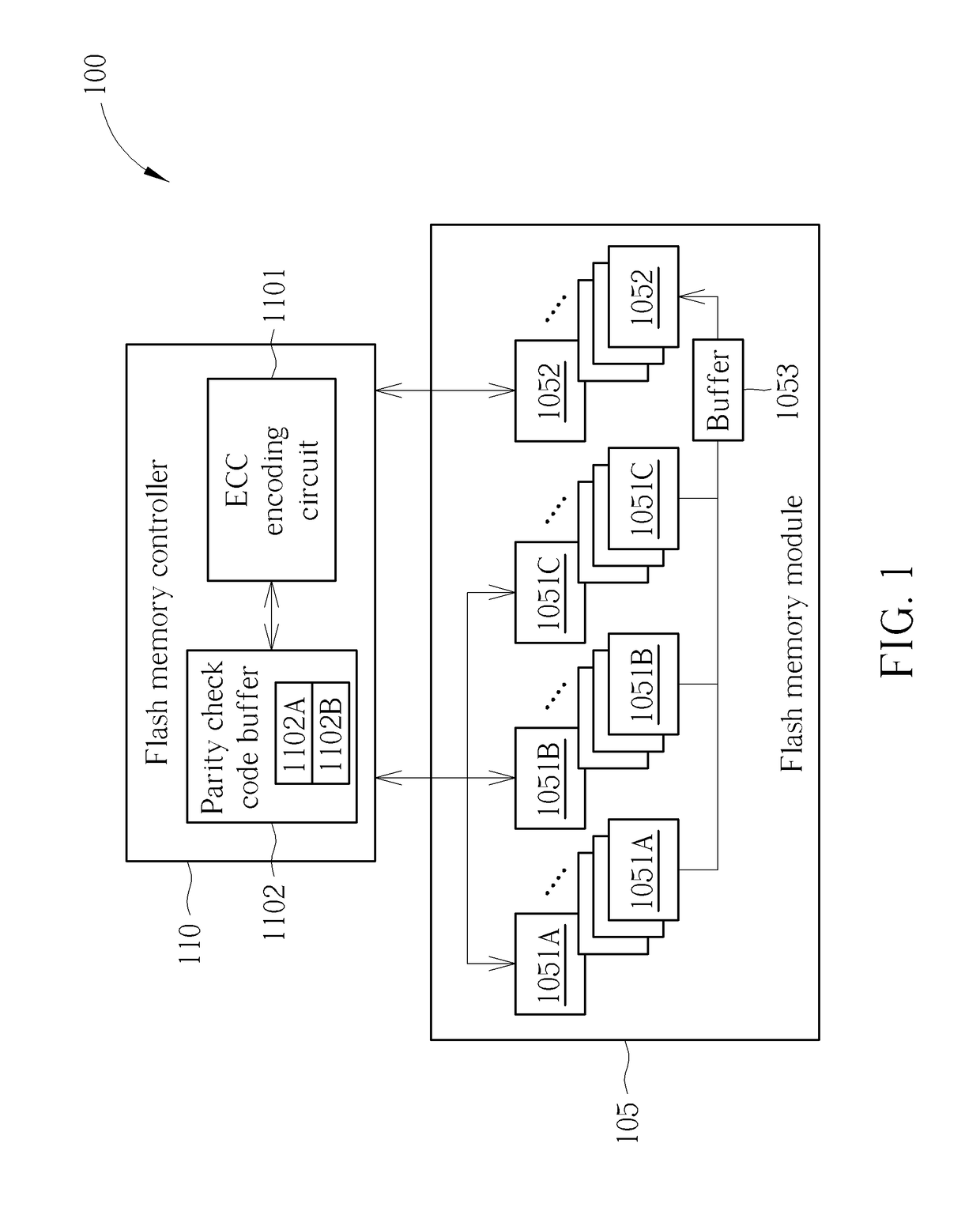
Flash memory apparatus and storage management method for flash memory
A method used for a flash memory module having a plurality of storage blocks each can be used as a first block or a second block includes: classifying data into a plurality of groups of data; respectively executing error code encoding to generate a first corresponding parity check code to store the groups of data and the first corresponding parity check code into the flash memory module as first blocks; reading out the groups of data from the first blocks; executing error correction and de-randomize operation upon read out data to generate de-randomized data; executing randomize operation upon the de-randomized data according to a set of seeds to generate randomized data; performing error code encoding upon the randomized data to generate a second corresponding parity check code; and storing the randomized data and the second corresponding parity check code into the flash memory module as the second block.
Owner:SILICON MOTION INC (TW)
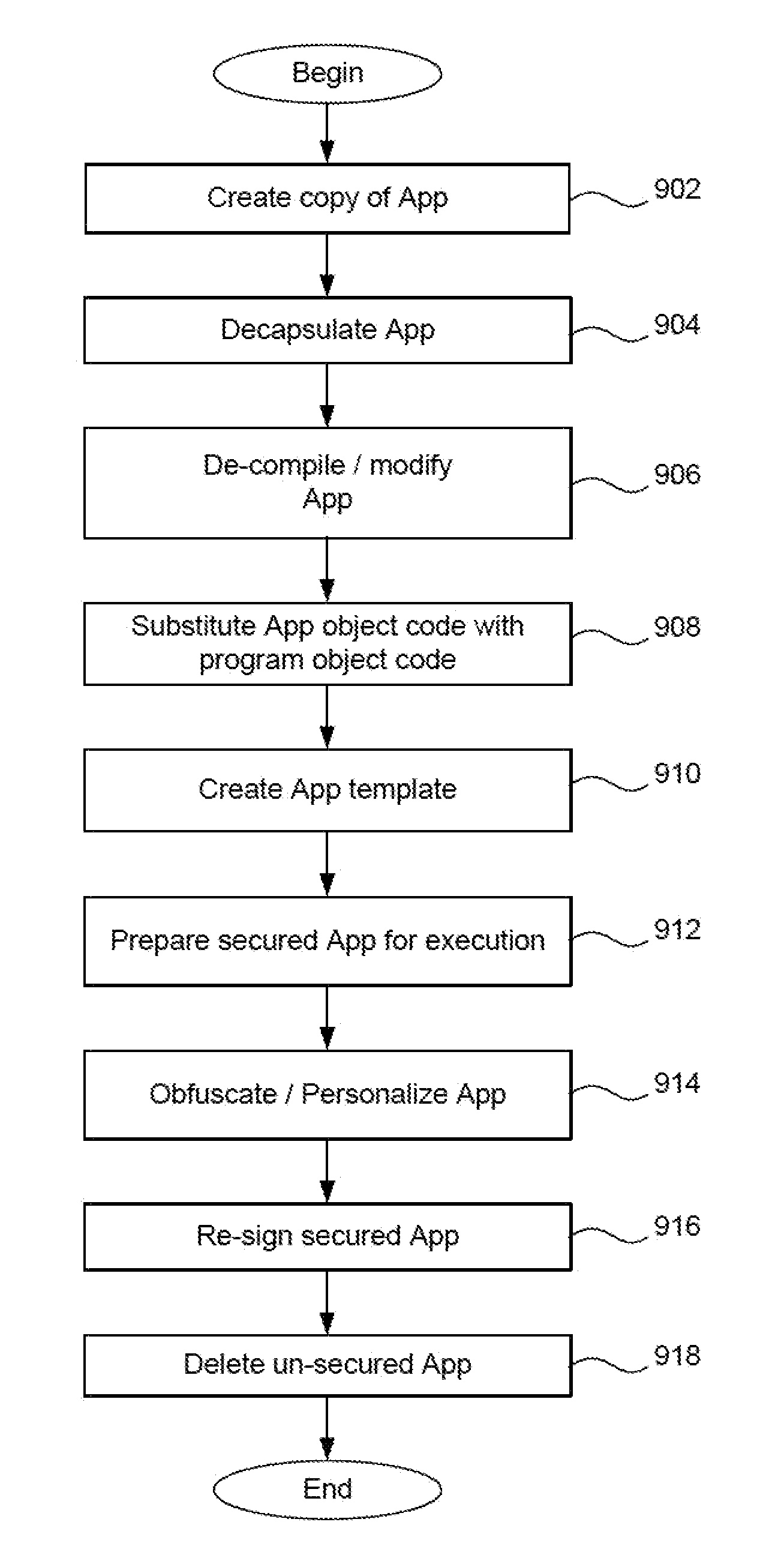
Secure execution of unsecured apps on a device
ActiveUS20120246484A1Minimize damageMinimize data lossUnauthorized memory use protectionHardware monitoringRandomizationApplication software
Given the volume of apps being developed and downloaded, performing operations to enable security for mobile devices, such as locating relevant classes and substituting different classes, can become very inefficient when done to a very high number of apps. In the invention, a device is enabled with an app security enforcement layer. The consumer can download unsecured apps and have the app execute on the phone in a secure manner, where potential data loss to the device, such as a smart phone or tablet, is minimized. To make the security wrapping process more efficient, an app template containing markers is created. This template is merged with data in an active user policy or is used to randomize or obfuscate the code to add more security. The process of security wrapping an app becomes more efficient.
Owner:BLUE CEDAR NETWORKS INC
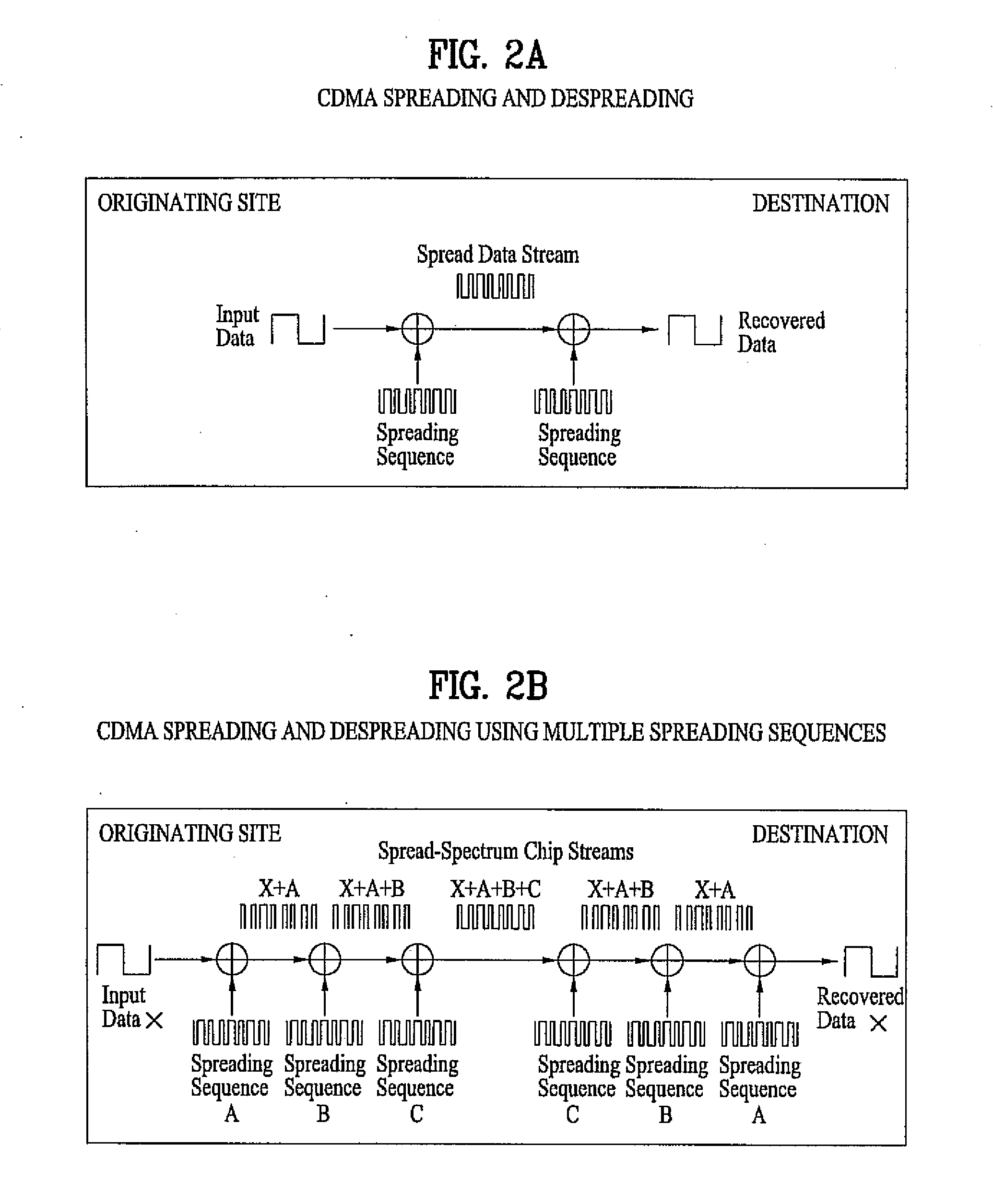
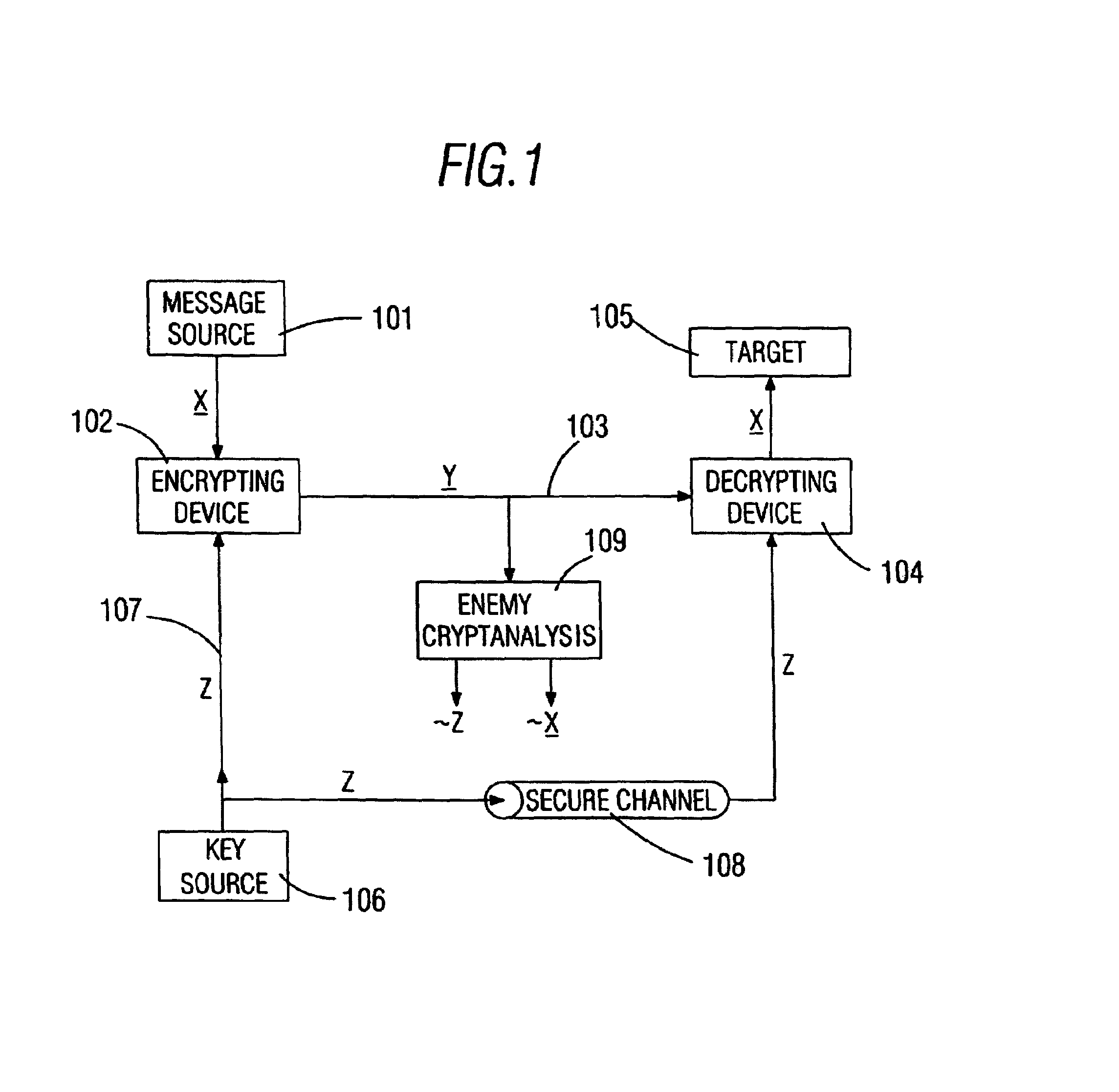
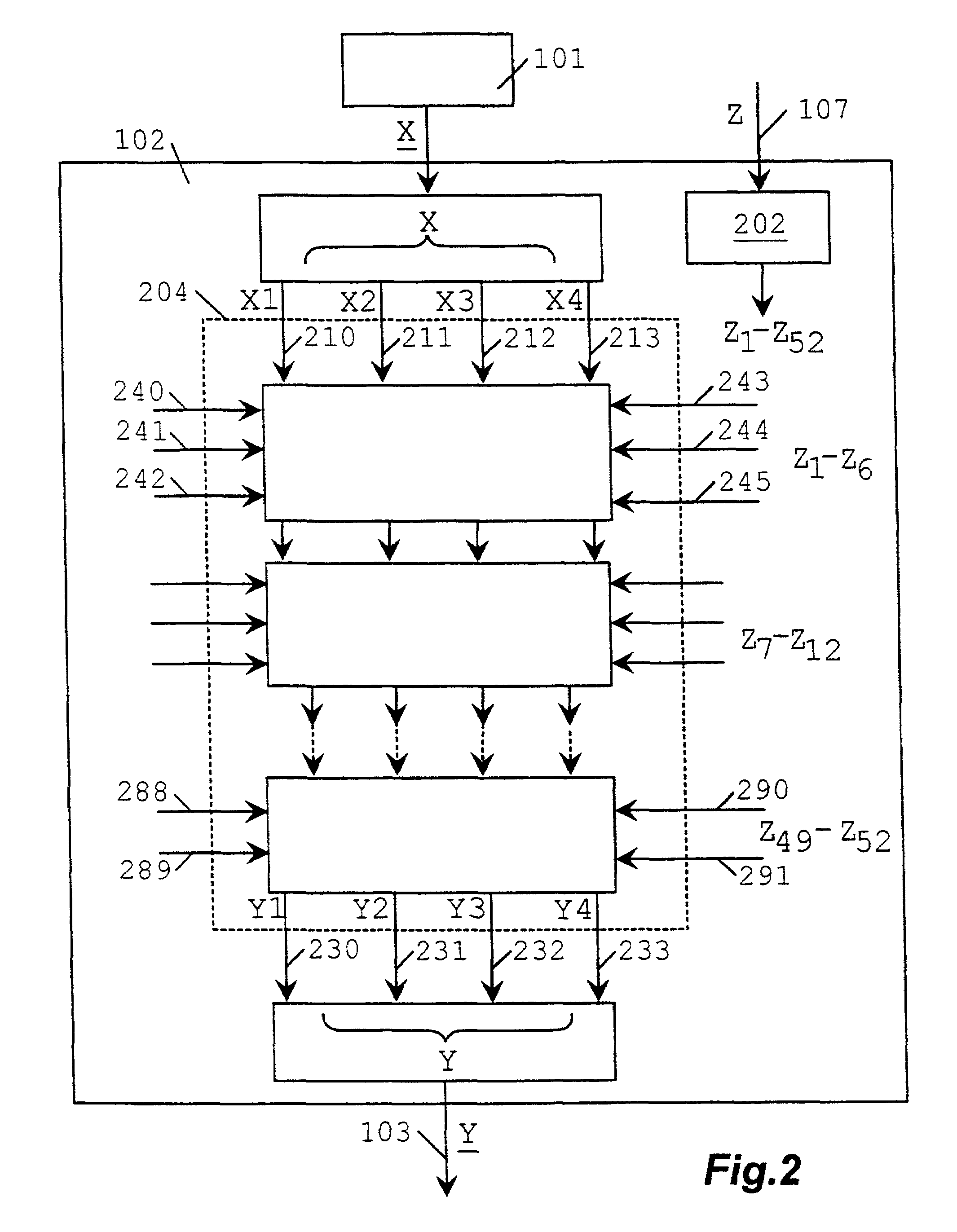
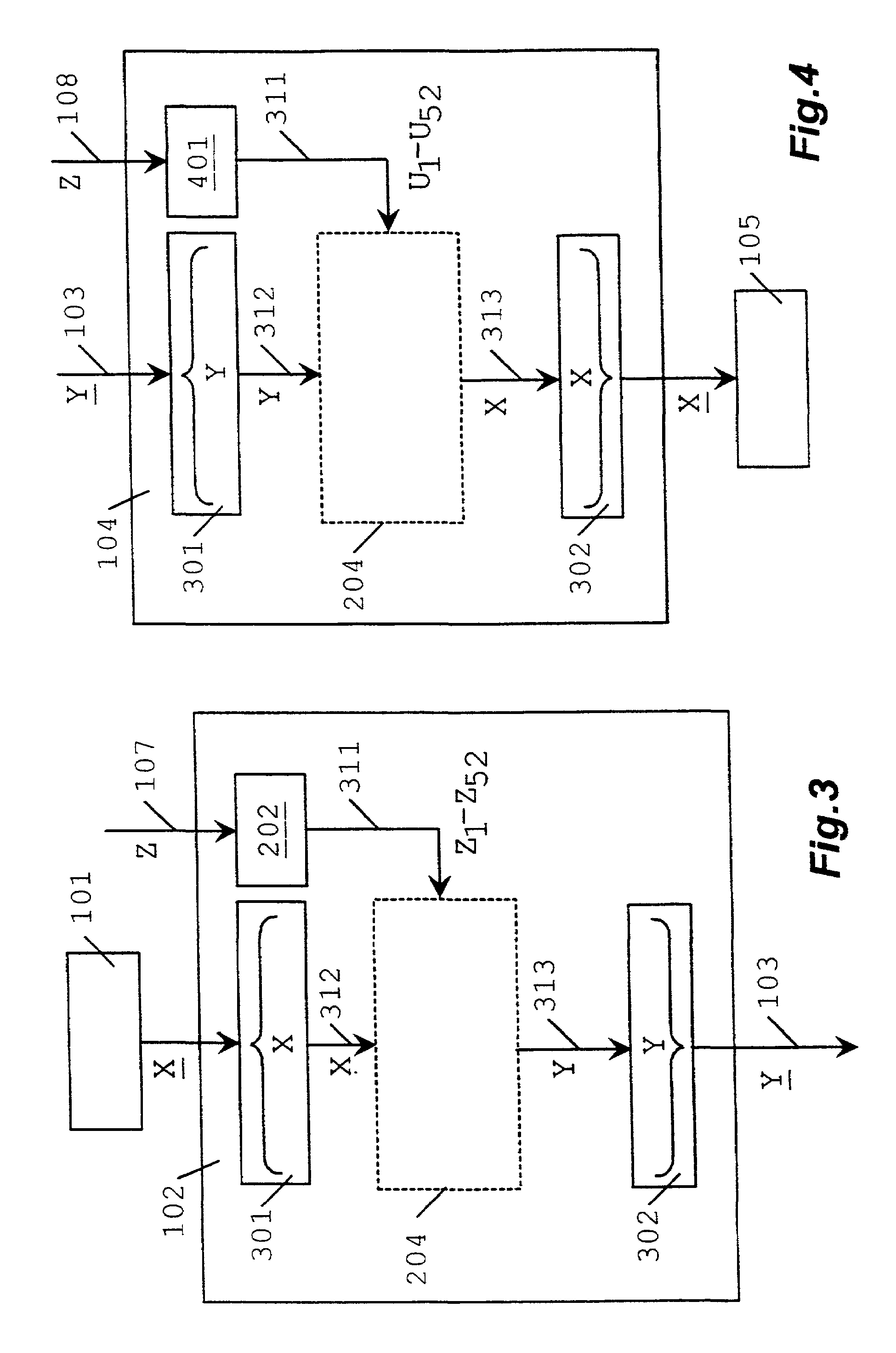
Randomization-encryption system
InactiveUS7050580B1Encryption apparatus with shift registers/memoriesSecret communicationDiffusionComputer hardware
Data sequence randomization encryption system such that having supplied data sequence (X) and randomization-encryption key (Kp) generates random data sequence (Yp), so that laypersons in encryption are able to measure objectively the diffusion and confusion of the generated sequence (Yp) with the particular randomization-encryption key (Kp) which has been used. Data sequence (X) is divided into blocks (XI), each block (XI) gets into group with transformer block (WTI), generated by transformer block generator (1002) by making use of control initial block (R) and previous output block (YI), resulting in grouped block (VI), result of the group, which is encrypted by means of the device in U.S. Pat. No. 5,214,703 (204), generating output block (YI) which is supplied to transformer block generator (1002), the succession of output blocks (YI) results in output randomized-encrypted sequence (Yp).
Owner:FERRE HERRERO ANGEL JOSE
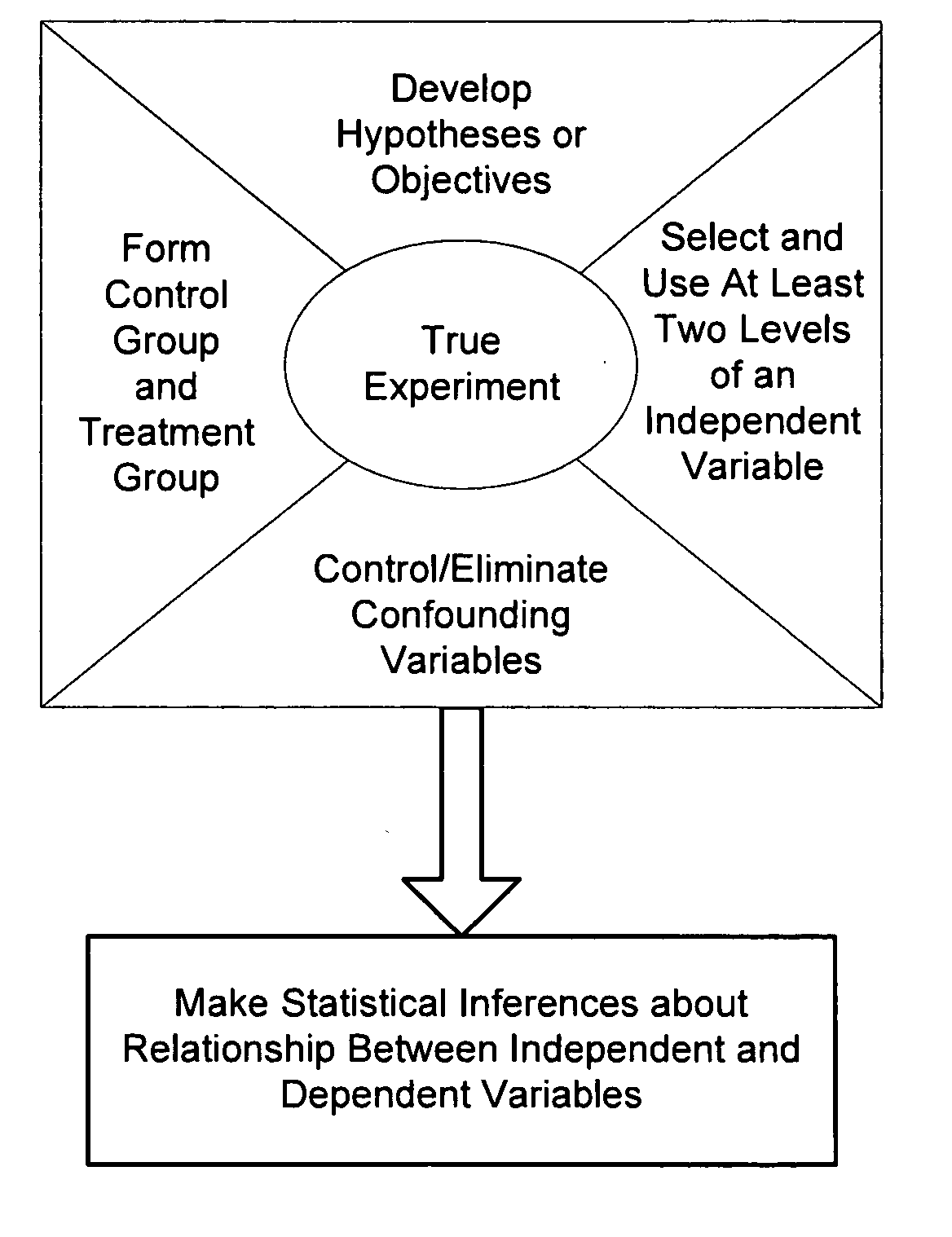
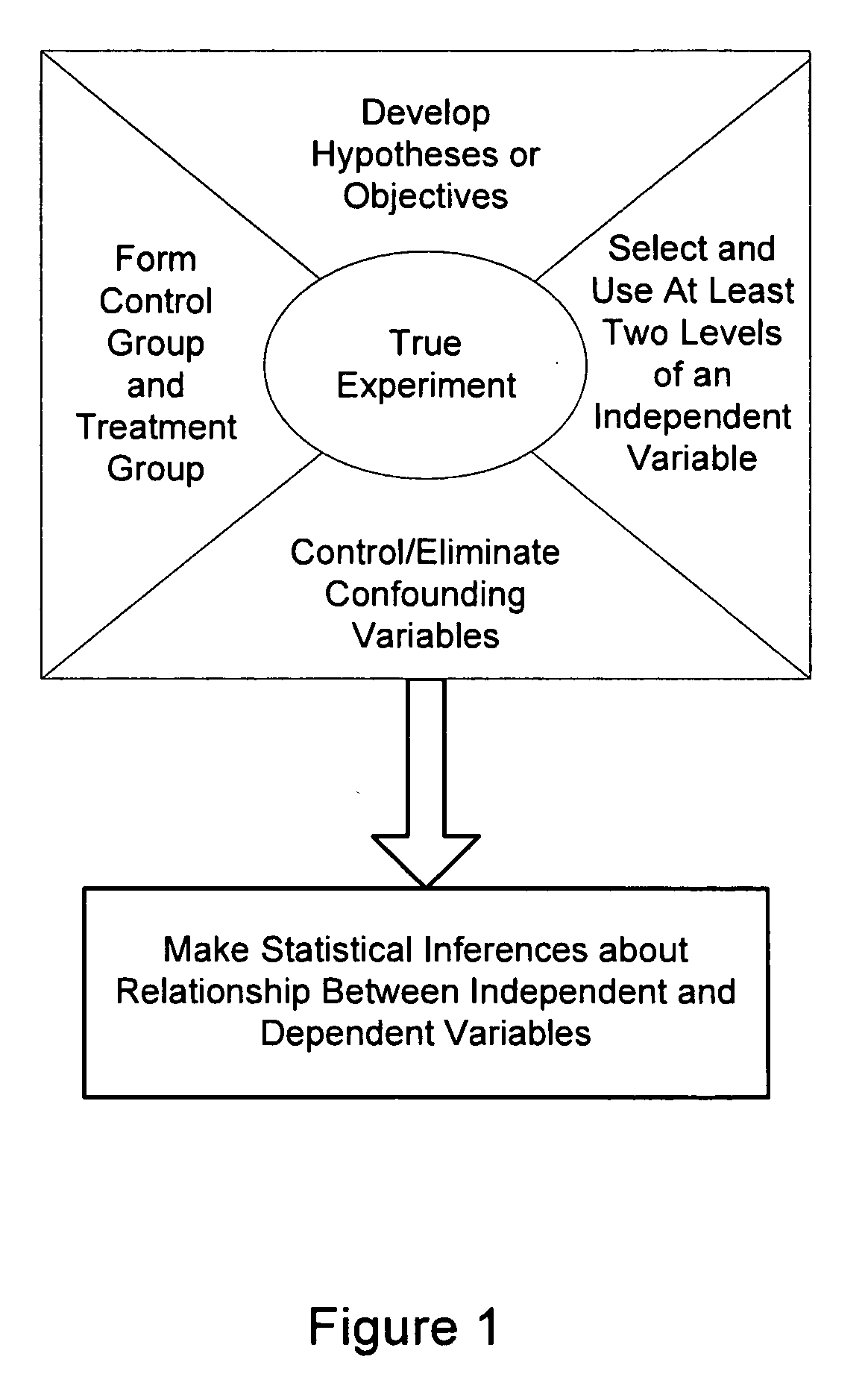
Systems and methods for designing experiments
InactiveUS20070156382A1Reduce the impactReduce impactNatural language data processingProgram controlRandomizationCausality
Methods and systems for designing an experiment using a computer to determine whether the experiment is a true experiment are described. These approaches allow a user who is unsophisticated in the complexities of true experimental design to design and deploy an experiment that produces substantially confound-free results and can be used to determine and quantify any causal relationship between independent and dependent variables. The computer may select one or more independent and / or dependent variables of the experiment or may assist the user in selection of independent and / or dependent variables. Formation of control and treatment groups, randomization and / or blocking to reduce the effects of confounding variables may be performed by the computer with or without input from the user.
Owner:3M INNOVATIVE PROPERTIES CO
Controlled randomized porous structures and methods for making same
ActiveUS20120321878A1High strengthImprove performanceGeometric CADAdditive manufacturing apparatusRandomizationMaterials science
Improved randomized porous structures and methods of manufacturing such porous structures are disclosed. The scaffold of the porous structures are formed from by dividing the space between a plurality of spatial coordinates of a defined volume, where the plurality of spatial coordinates have been moved in a random direction and a random finite distance according to a predetermined randomization limit.
Owner:SMITH & NEPHEW INC
Methods and apparatus for masking and securing communications transmissions
InactiveUS7949032B1Reduce impulseInexpensive hardwareSynchronising transmission/receiving encryption devicesPublic key for secure communicationFiberSecure communication
A secure information transmission system includes one or more transmitters and one or more receivers. The transmission waveform employed includes highly randomized, independent stochastic processes, and is secured as a separate entity from the information it carries. The signal, using novel modulation methodology reducing impulse responses, has a paucity of spectral information and may be detected, acquired and demodulated only by communicants generating the necessary receiving algorithm coefficients. The physical area of signal reception is restricted to that of each intended communicant, reception areas following movements of mobile communicants. A unique instant in time is used as basis for communications keys to the securing algorithms dynamically generated on a one-time basis and never exchanged or stored by communicants. Technology is applicable to both fixed and mobile communications and may be applied to communications systems using wireless, fiber-optic, copper, acoustic and any other man-made or naturally occurring transmission media.
Owner:FROST EDWARD G
Method and apparatus for scalable peer-to-peer inquiries in a network of untrusted parties
ActiveUS7325034B2Broadcast transmission systemsMultiple digital computer combinationsComputer hardwareRandomization
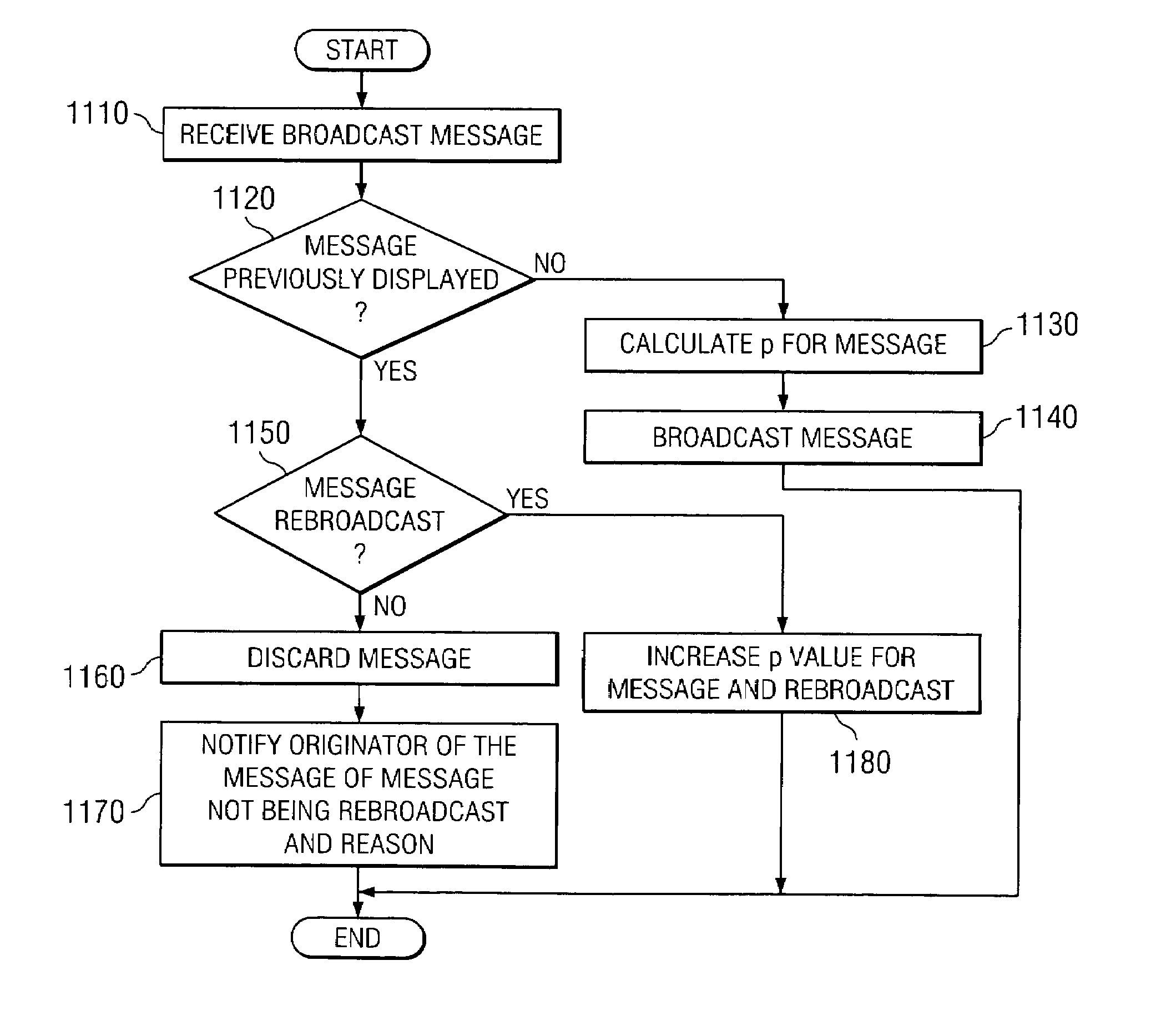
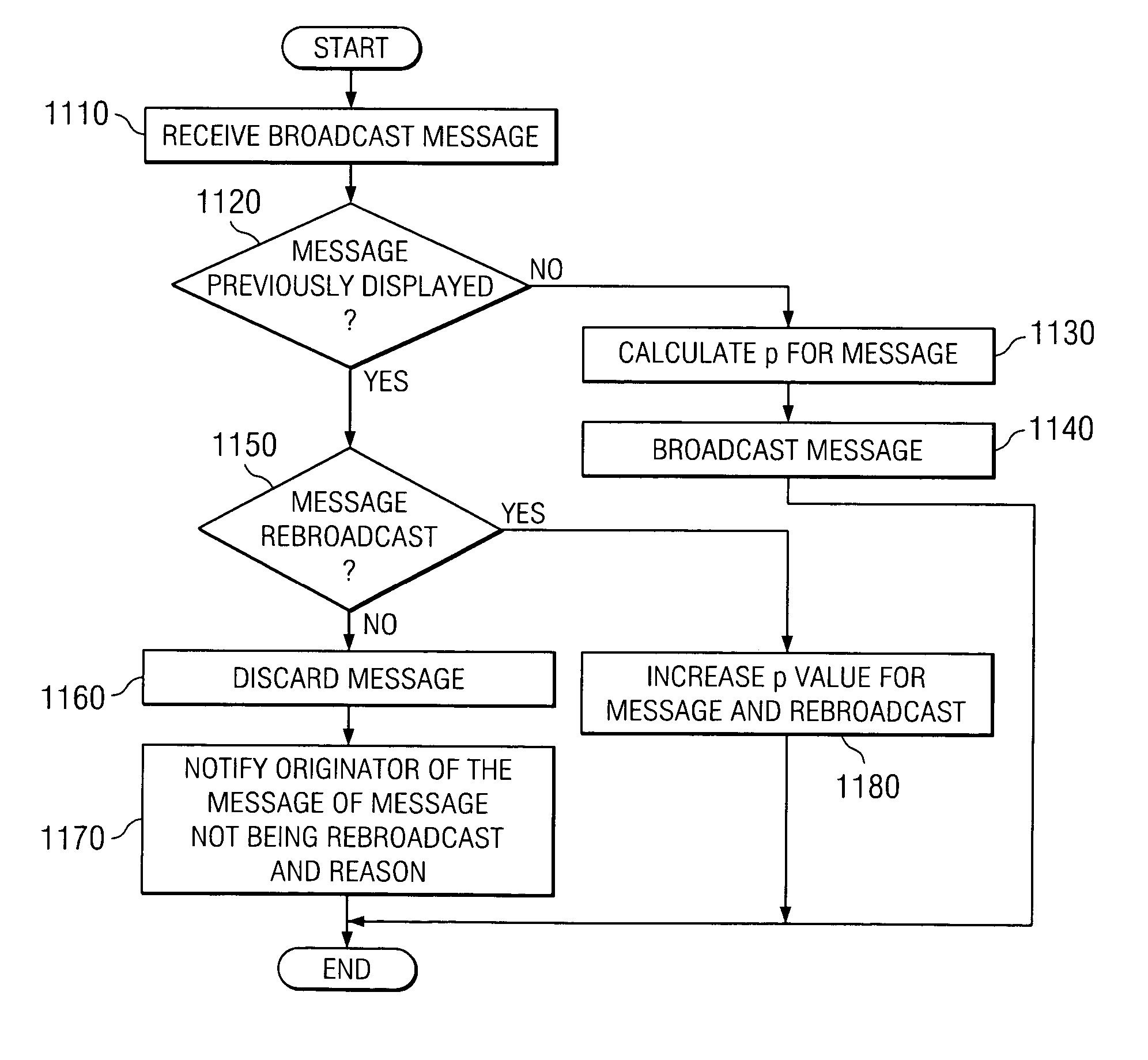
A method and apparatus for scalable inquiries in a network of communicating peers are provided. The method and apparatus of the present invention make use of communal filters and randomization to determine which client devices will output a message that is to be broadcast to a community of client devices. Each message is assigned a probability value that is determined based on various criteria or may be determined randomly. The message is then transmitted to the client devices who apply their own respective display criteria to the message parameters to determine if the message is one that is of interest to the user of the client device. If the message is not of interest to the user of the client device, the message is discarded. If the message is of interest to the user, logic is applied to the parameters of the message to determine whether the message should be displayed to the user or not. This logic may involve determining whether the message has been previously displayed to the user, whether the message has been received but not previously displayed, and the like. In addition, if the message has not been previously displayed to the user, a randomly generated number, which may be weighted based on other criteria, is generated and compared with the probability value associated with the message. Based on this comparison, the message is either displayed or not displayed on the client device. This probability value of the message may be adjusted with each subsequent rebroadcast of the message to increase the size of the subset of users that will see the message.
Owner:GOOGLE LLC
Nonvolatile memory and method for on-chip pseudo-randomization of data within a page and between pages
ActiveUS20090067244A1Reducing NAND string resistance effectIncreasing memory enduranceRead-only memoriesDigital storageLimited resourcesMemory chip
Features within an integrated-circuit memory chip enables scrambling or randomization of data stored in an array of nonvolatile memory cells. In one embodiment, randomization within each page helps to control source loading errors during sensing and floating gate to floating gate coupling among neighboring cells. Randomization from page to page helps to reduce program disturbs, user read disturbs, and floating gate to floating gate coupling that result from repeated and long term storage of specific data patterns. In another embodiment, randomization is implemented both within a page and between pages. The scrambling or randomization may be predetermined, or code generated pseudo randomization or user driven randomization in different embodiments. These features are accomplished within the limited resource and budget of the integrated-circuit memory chip.
Owner:SANDISK TECH LLC
Watermark payload encryption for media including multiple watermarks
ActiveUS20050262351A1Key distribution for secure communicationColor burst signal generation/insertionRandomizationEncryption
The present invention provides encryption techniques useful with digital watermarking payloads. In a first implementation, we encrypt one of two different cooperating watermark payloads, but the encryption and payload data structure helps to authenticate both payloads. Another implementation provides a three encryption key pair system for managing messages and watermark embedding. Still another aspect of the invention is a watermark embedding process that uses encryption to whiten, randomize or spread a message, instead of convention spread-spectrum modulation.
Owner:DIGIMARC CORP
Method and apparatus for scalable peer-to-peer inquiries in a network of untrusted parties
ActiveUS20050065632A1Digital computer detailsBroadcast transmission systemsComputer hardwareRandomization
A method and apparatus for scalable inquiries in a network of communicating peers are provided. The method and apparatus of the present invention make use of communal filters and randomization to determine which client devices will output a message that is to be broadcast to a community of client devices. Each message is assigned a probability value that is determined based on various criteria or may be determined randomly. The message is then transmitted to the client devices who apply their own respective display criteria to the message parameters to determine if the message is one that is of interest to the user of the client device. If the message is not of interest to the user of the client device, the message is discarded. If the message is of interest to the user, logic is applied to the parameters of the message to determine whether the message should be displayed to the user or not. This logic may involve determining whether the message has been previously displayed to the user, whether the message has been received but not previously displayed, and the like. In addition, if the message has not been previously displayed to the user, a randomly generated number, which may be weighted based on other criteria, is generated and compared with the probability value associated with the message. Based on this comparison, the message is either displayed or not displayed on the client device. This probability value of the message may be adjusted with each subsequent rebroadcast of the message to increase the size of the subset of users that will see the message.
Owner:GOOGLE LLC
Random early detection policer using randomization of packet drops
InactiveUS7149187B1Error prevention/detection by using return channelFrequency-division multiplex detailsRandom early detectionRandomization
A Random Early Detection (RED) policer in accordance with the invention does not tail-drop arriving packets as being non-conforming. For instance, because the RED policer uses a running estimate such as an exponential weighted moving average (EWMA), for example, it allows the policer to absorb traffic bursts. The policer uses randomization in choosing which packets to drop; with this method, the probability of dropping a packet from a particular sending node is roughly proportional to the node's bandwidth share, hence the packets of different flows are fairly dropped.
Owner:CISCO TECH INC
Randomization-based encryption apparatus and method
InactiveUS20050002531A1Reduce computational complexityIncrease variabilityDigital data protectionDigital storageObfuscationTheoretical computer science
A method for encryption data subdivided into segments of random lengths. A data source having a state corresponding to initialization parameters and the number of patterns output therefrom provides for a reversible encryption process. Decryption is accomplished by repeating encryption using a data source having an identical initial state. The data source consists random pattern generation machines (RPGMs). A portion of RPGMs may each contain patterns of a different length. Randomly selecting an RPGM and outputting a pattern therefrom effectively provides a pattern of random length. The data source may output patterns interpreted to govern the behavior of obfuscation operations. Patterns output from the data source may be interpreted as instructions as to what obfuscation to perform and what parameters shall define the obfuscation.
Owner:MICHAELSEN DAVID L
Systems and methods providing wear leveling using dynamic randomization for non-volatile memory
InactiveUS20120324141A1Increased durabilityLow costMemory architecture accessing/allocationMemory adressing/allocation/relocationPhase-change memoryOperational system
Systems and methods for dynamically remapping elements of a set to another set based on random keys. Application of said systems and methods to dynamically mapping regions of memory space of non-volatile memory, e.g., phase-change memory, can provide a wear-leveling technique. The wear leveling technique can be effective under normal execution of typical applications, and in worst-case scenarios including the presence of malicious exploits and / or compromised operating systems, wherein constantly migrating the physical location of data inside the PCM avoids information leakage and increases security; wherein random relocation of data results in the distribution of memory requests across the physical memory space increases durability; and wherein such wear leveling schemes can be implemented to provide fine-grained wear leveling without overly-burdensome hardware overhead e.g., a look-up table.
Owner:GEORGIA TECH RES CORP
Methods and Systems for Interference Mitigation
ActiveUS20110110304A1Interference mitigation is substantially improvedGood reliefAmplitude-modulated carrier systemsInter user/terminal allocationCarrier signalRandomization
Embodiments herein provide methods and systems for enhancing interference mitigation using conjugate symbol repetition and phase randomization on a set of subcarriers. The repeated data tone in the signal is complex-conjugated before transmission, when the repetition factor is two. When the repetition factor is greater than two, a combination of conjugate repetition and random / deterministic phase variation of the repeated tones is used to mitigate the interference mitigation. Embodiments further disclose Collision Free Interlaced Pilot PRU Structures that can be used with or without conjugate symbol repetition and phase randomization for interference mitigation.
Owner:CENT OF EXCELLENCE & WIRELESS TECH
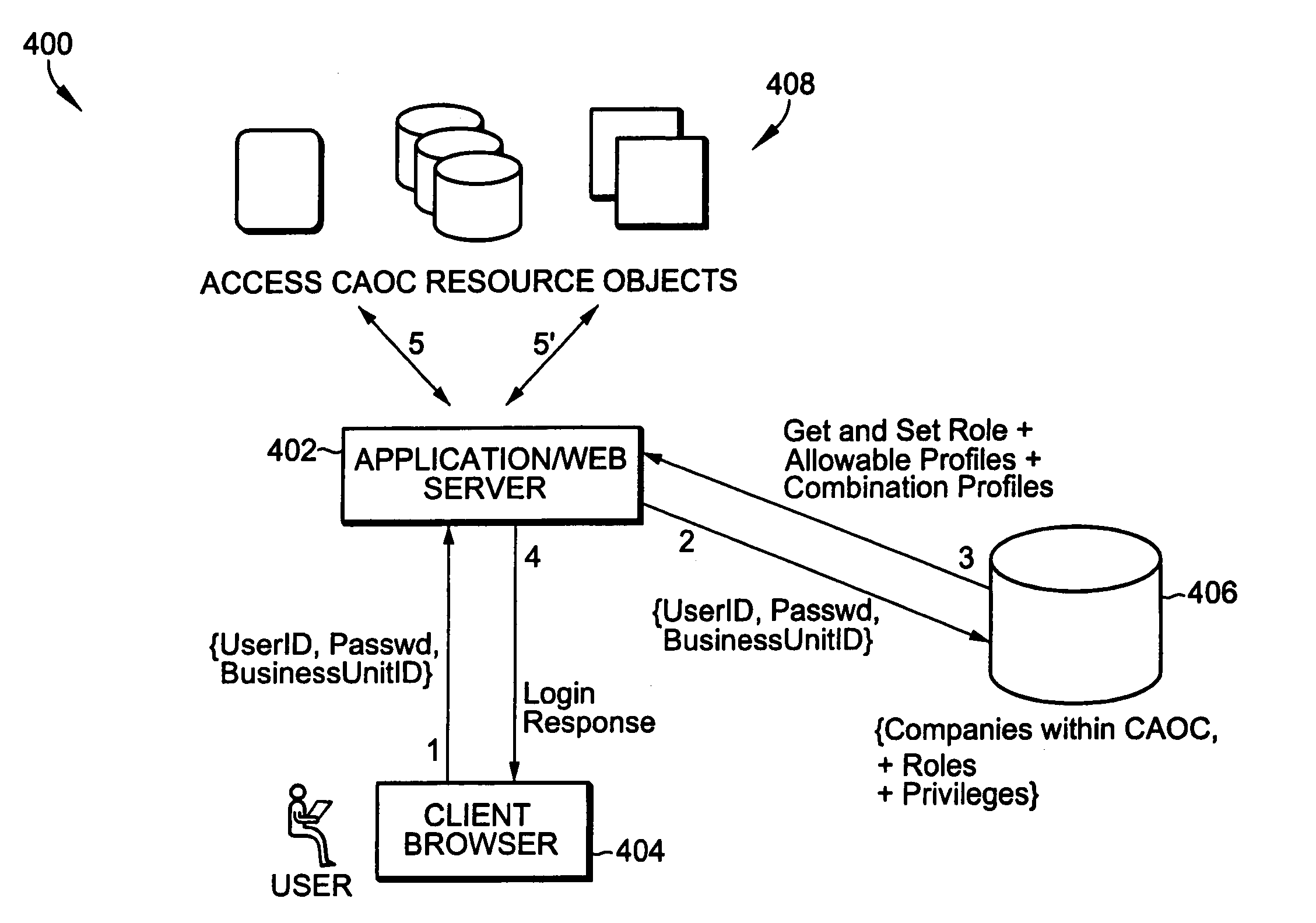
Role-based access using combinatorial inheritance and randomized conjugates in an internet hosted environment
ActiveUS7730523B1Improve functionalityHigh processDigital data processing detailsMultiple digital computer combinationsPasswordWeb service
A method for remote services authentication in an internet hosted environment includes a high level process and functionality for a secure, practical and logically optimized inter-network authentication mechanism by employees, partners and customers of an enterprise into the hosted Internet site. The lightweight authentication and authorization mechanism can be most effectively implemented in Java as part of the application or web server servlet. The method for remote services authentication includes initial secure password establishment, subsequent authentication and authorization, as well as authentication and authorization upon resuming previously run sessions with the hosted server using Internet cookies.
Owner:ORACLE INT CORP
Randomized value generation
InactiveUS20120030268A1Effective monitoringMaximize lengthRandom number generatorsSecuring communication by chaotic signalsRandomizationVoltage
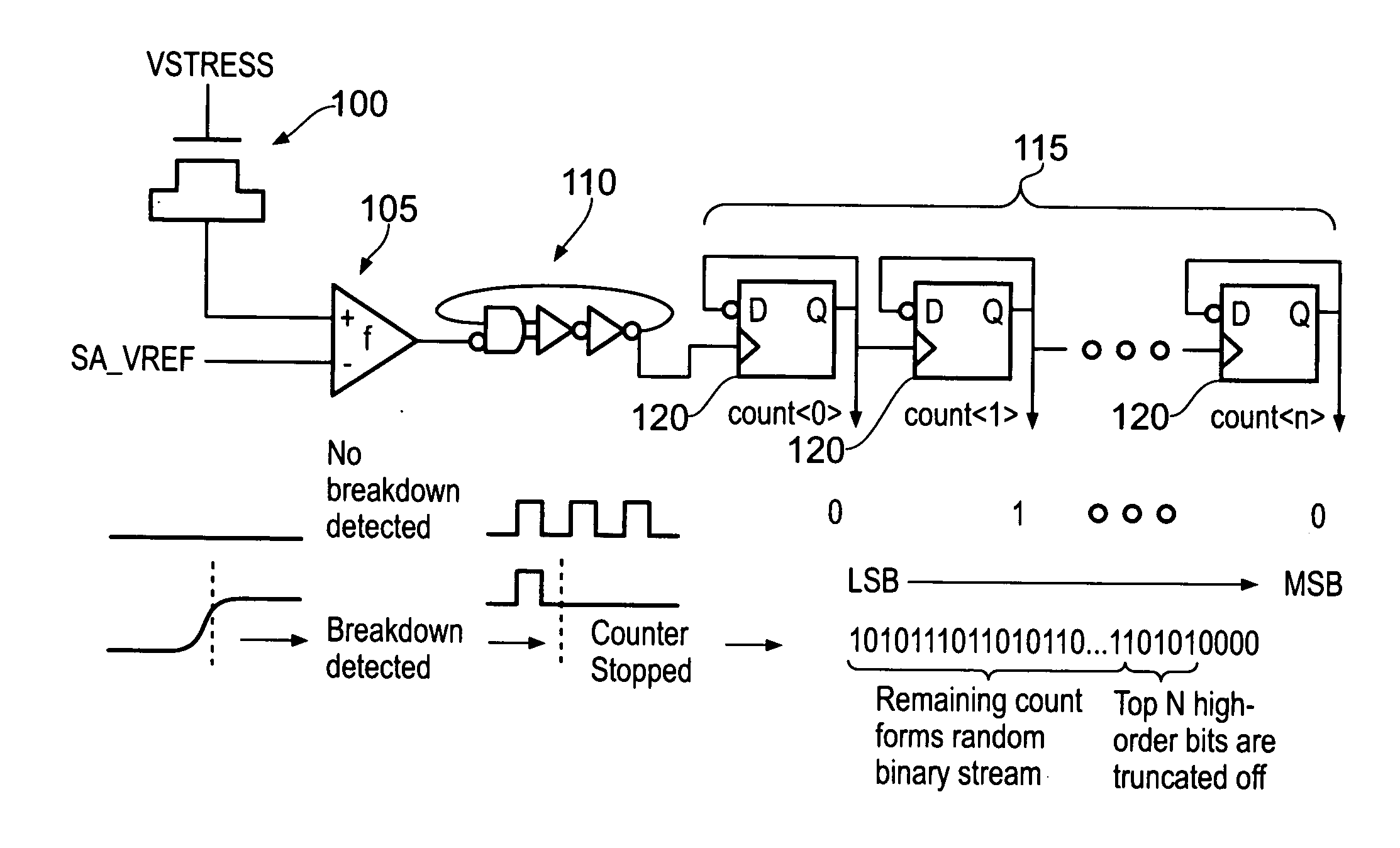
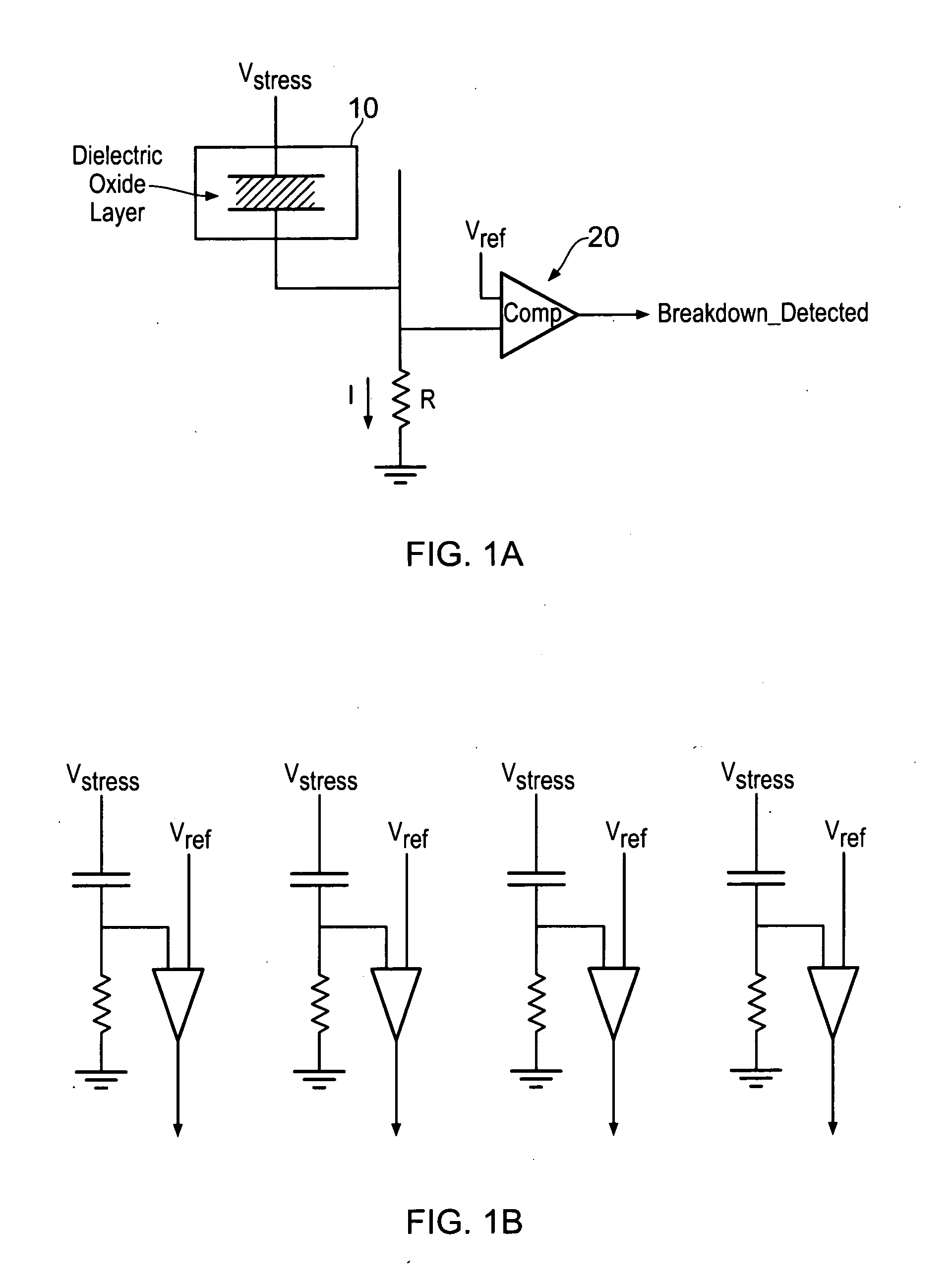
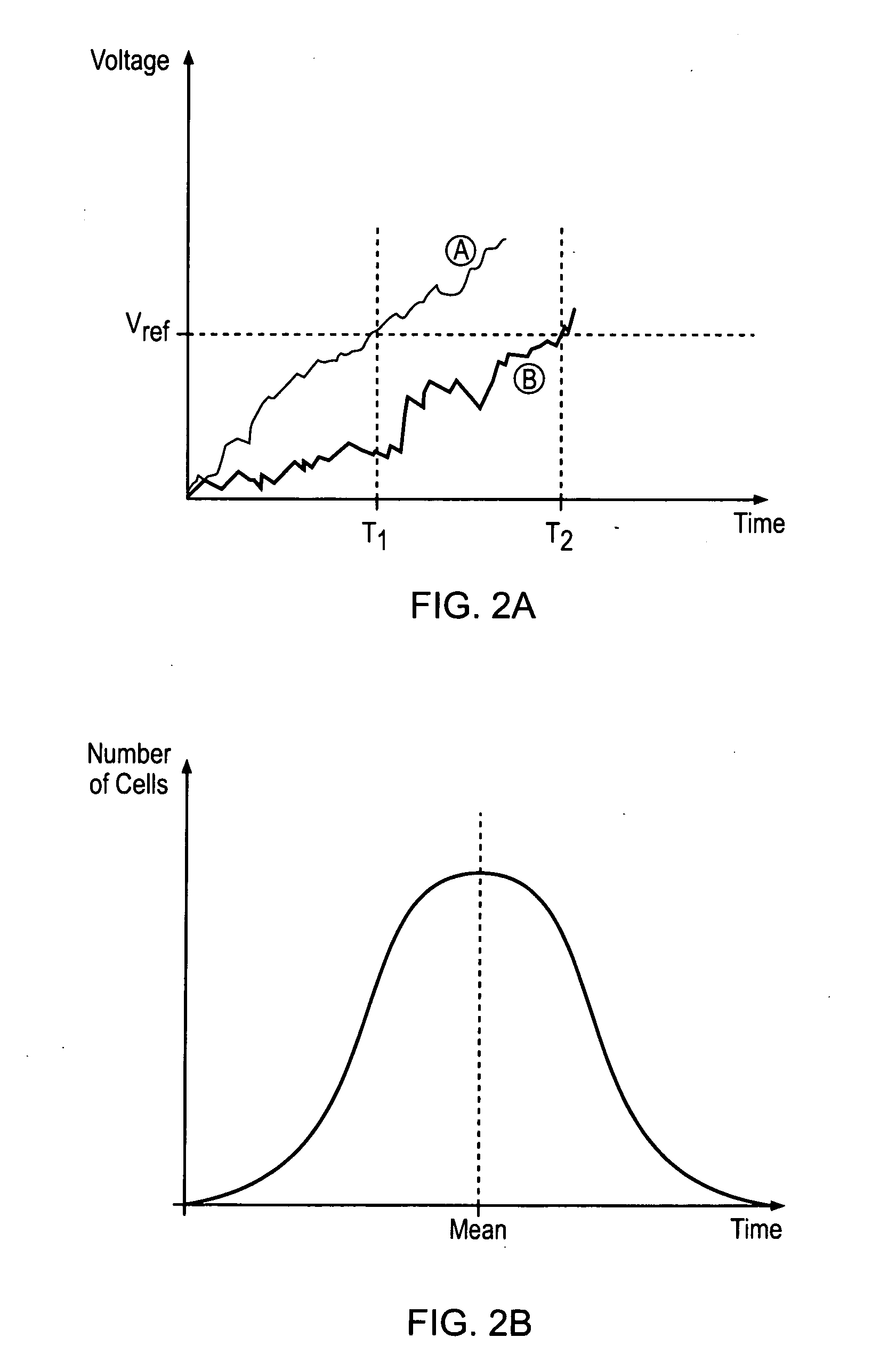
A data processing apparatus is provided for producing a randomized value. A cell in the data processing apparatus comprises a dielectric oxide layer and stress voltage circuitry is configured to apply a stress voltage across the dielectric oxide layer of the cell to cause an oxide breakdown process to occur. Oxide breakdown detection circuitry is configured to determine a current extent of the oxide breakdown process by measuring a response of the dielectric oxide layer to the stress voltage and randomized value determination circuitry is configured to determine a randomized value in dependence on the current extent of the oxide breakdown process.
Owner:RGT UNIV OF MICHIGAN
Sequence generation and mapping method of reference signals and transmission device
InactiveCN101662443APerfectly compatibleGuaranteed Interference RandomizationSignal allocationMulti-frequency code systemsMimo transmissionRandomization
The invention discloses a sequence generation and a mapping method of reference signals and a transmission device. The method comprises the following steps: generating the sequence of the reference signals according to the frequency domain bandwidth of the reference signals; mapping the generated sequence of the reference signals to physical time-frequency resources, wherein, identical sequences are mapped on each OFDM symbol transmitting the references in the time cell to transmit the reference signals. While ensuring interference randomization, the invention also ensures the property of transmission simultaneously, and can carry out compatibility on the current LTE system better, thus realizing high order MIMO transmission, supporting the use of corresponding techniques and improving theoverall performance of the system.
Owner:ZTE CORP
Privacy preserving computation protocol for data analytics
PendingUS20180373882A1Efficient privacy-preservingEfficient privacy-preserving protocolKey distribution for secure communicationMultiple keys/algorithms usagePlaintextEncrypted function
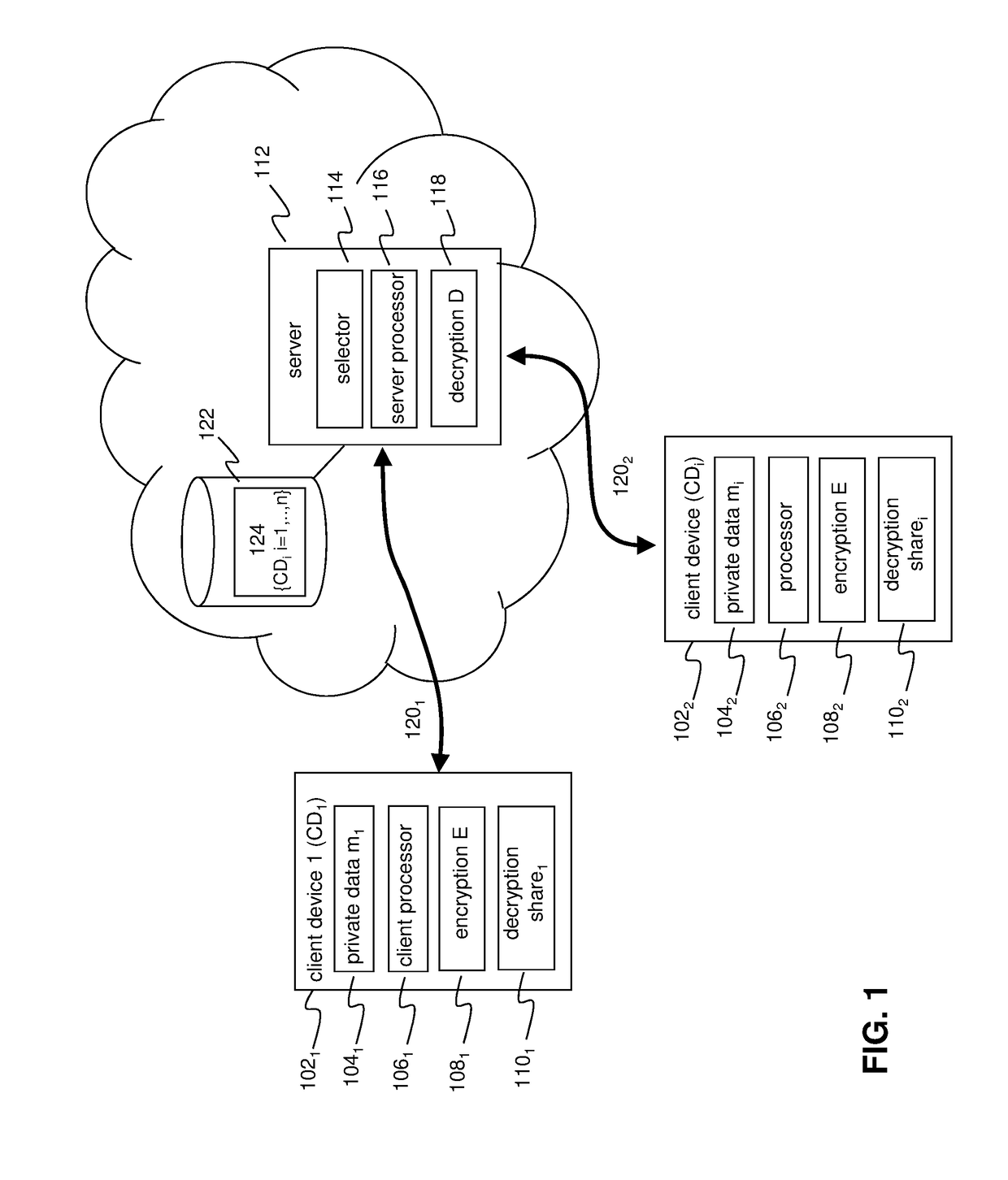
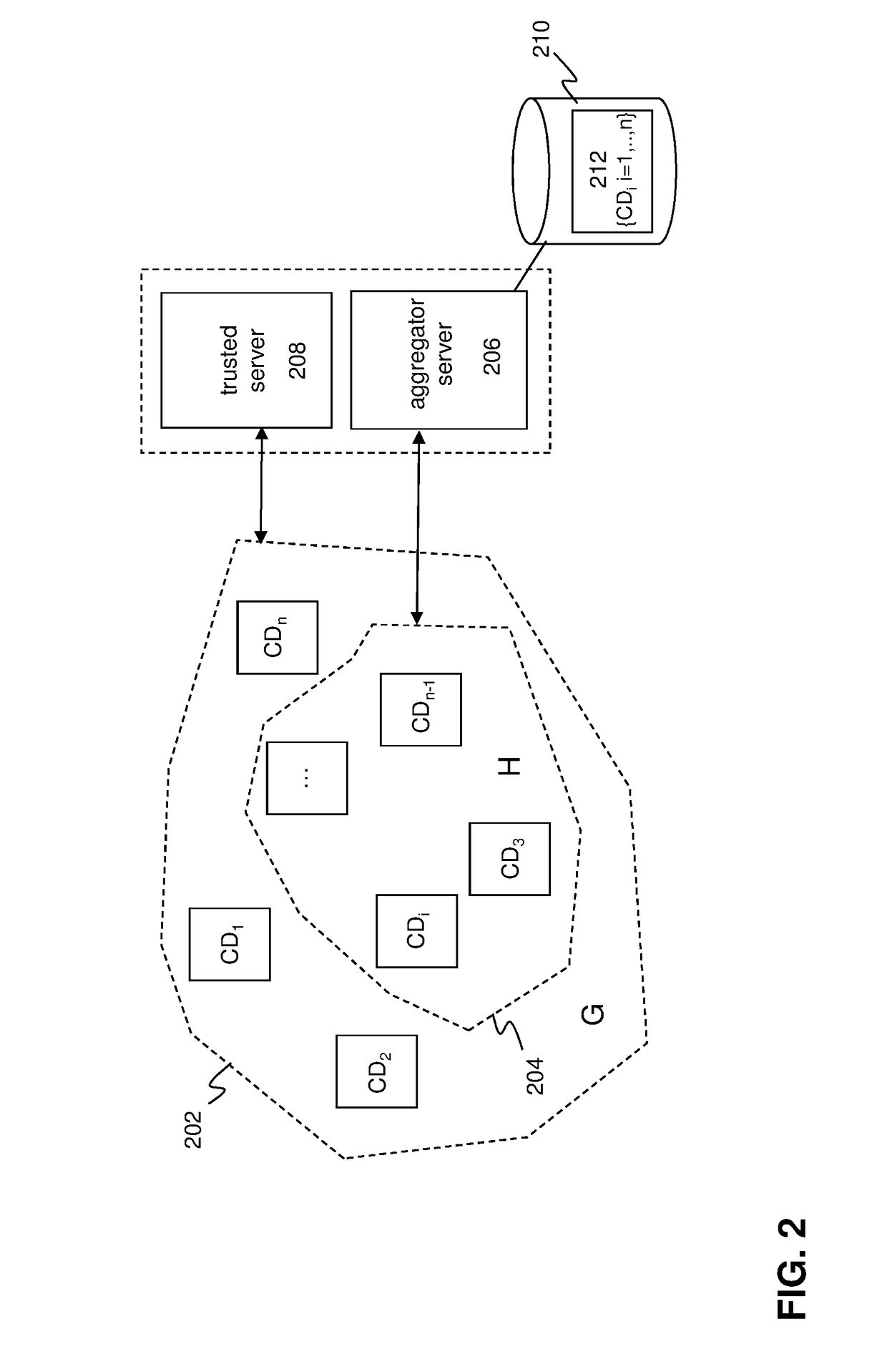
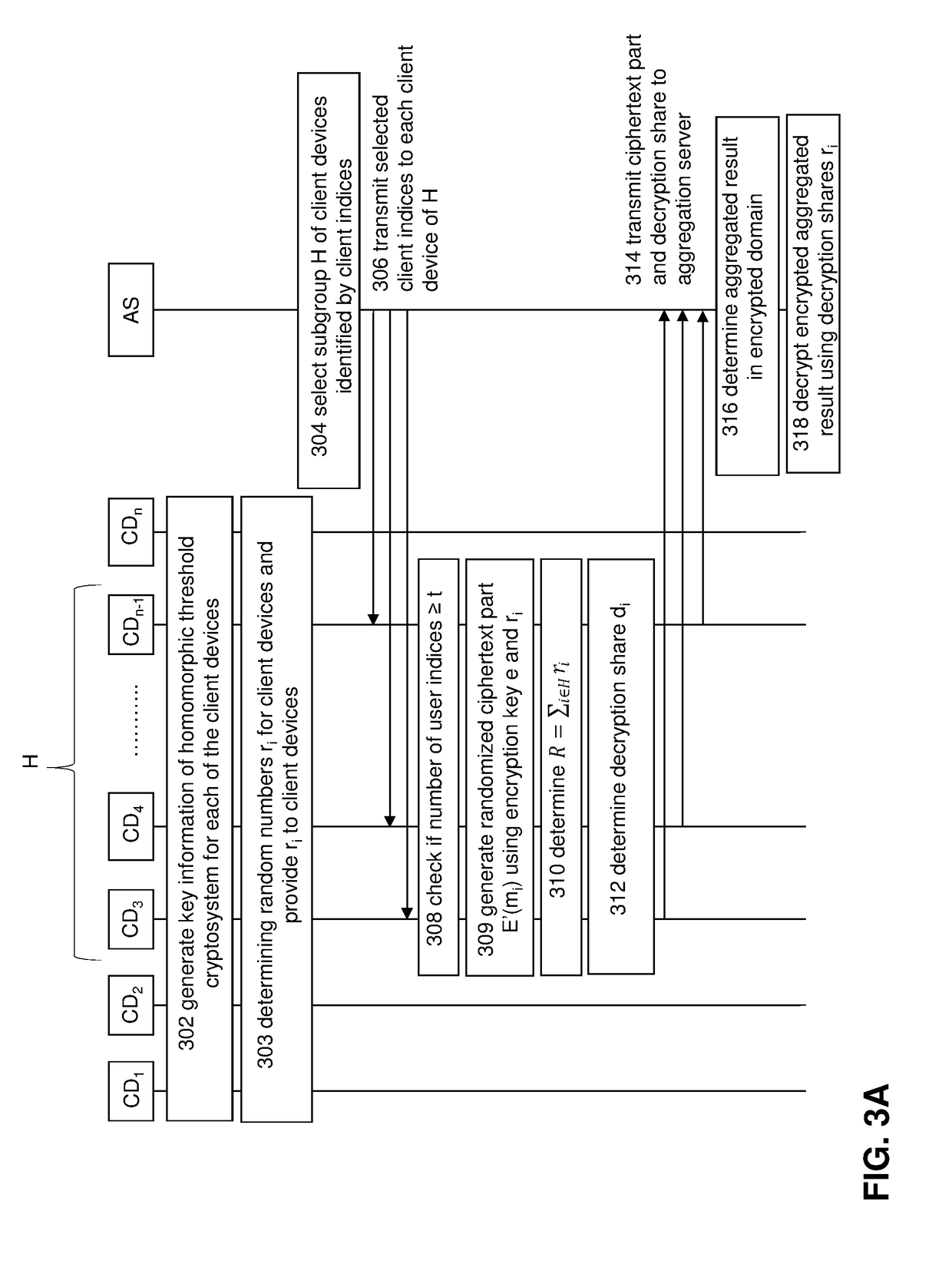
A privacy preserving computation protocol for data analytics is described. The protocol includes a method for privacy-preserving computation of aggregated private data of a group of client devices wherein the method comprises: a server selecting at least t client devices from the group of client devices, each client device in the group: being identifiable by client index i; comprising an encryption function; being provided with key information including an encryption key e and a decryption key of a homomorphic threshold cryptosystem; generating or being provided with an random value ri and having access to or being provided with the random values of the other client devices in the group; the server transmitting client information to each selected client device, the client information including client indices identifying the selected client devices, the client information signalling a client device that the server would like aggregate encrypted private data of each of the selected client devices; the server receiving randomized encrypted private data and an associated decryption share from each selected client device, the decryption shares being configured such that decryption key d can be reconstructed on the basis of t decryption shares; and, the server aggregating, preferably summing or adding, the received randomized encrypted private data of the selected client devices using the homomorphic properties of the cryptosystem and using the decryption shares for decrypting the aggregated randomized encrypted private data into cleartext.
Owner:FLYTXT MOBILE SOLUTIONS
Binary Translation and Randomization System for Application Security
ActiveUS20150047049A1Digital data processing detailsAnalogue secracy/subscription systemsParallel computingExecution unit
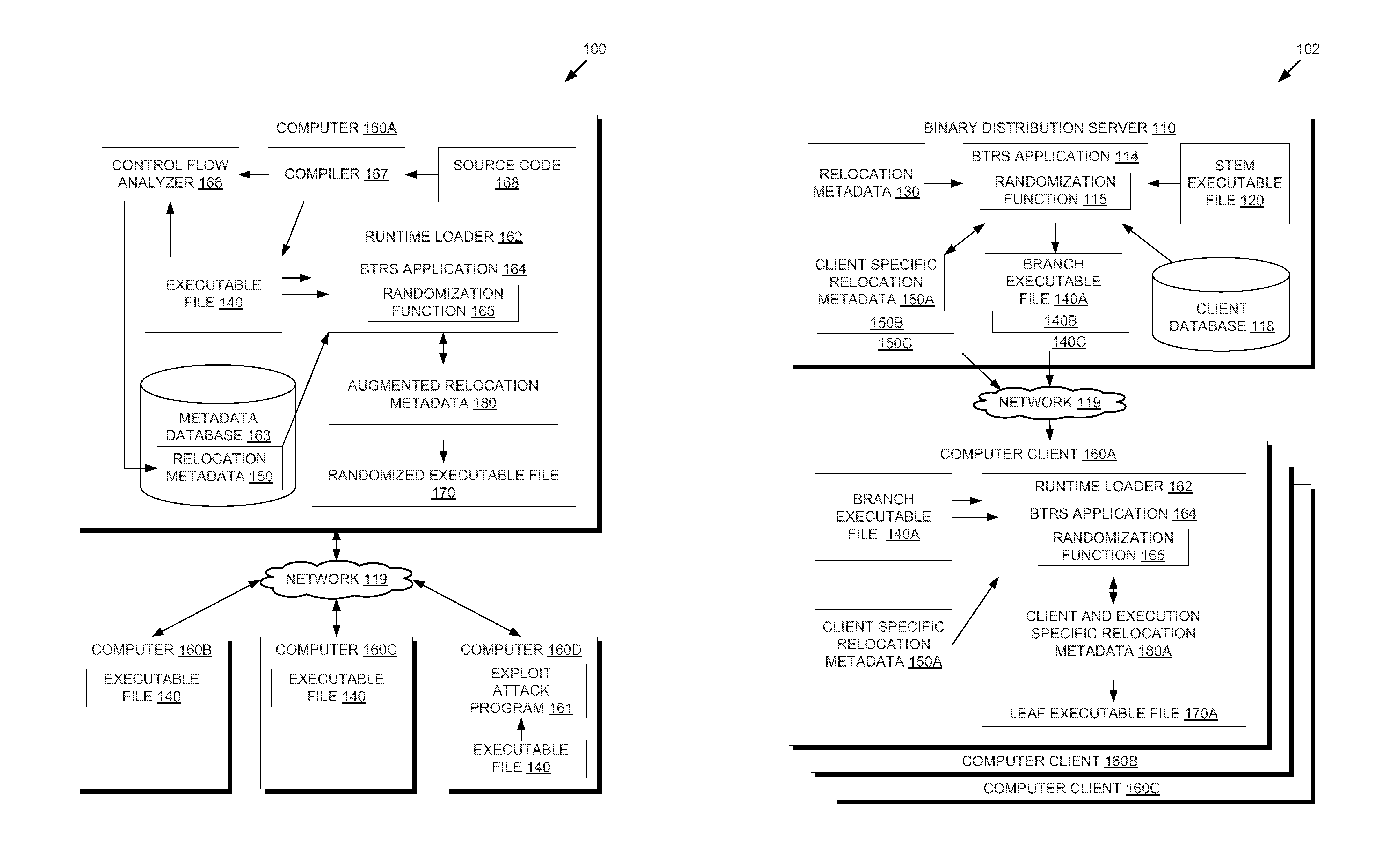
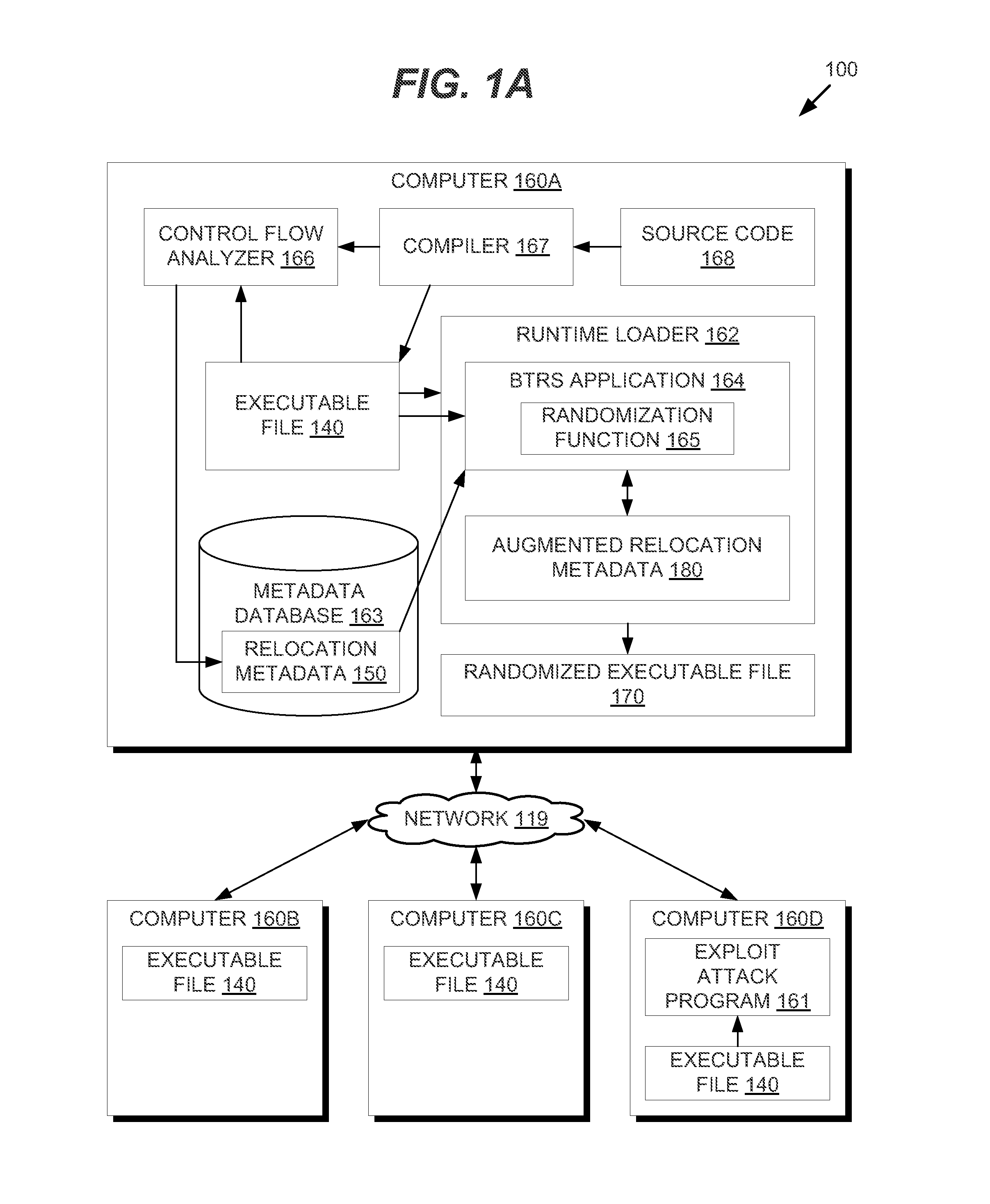
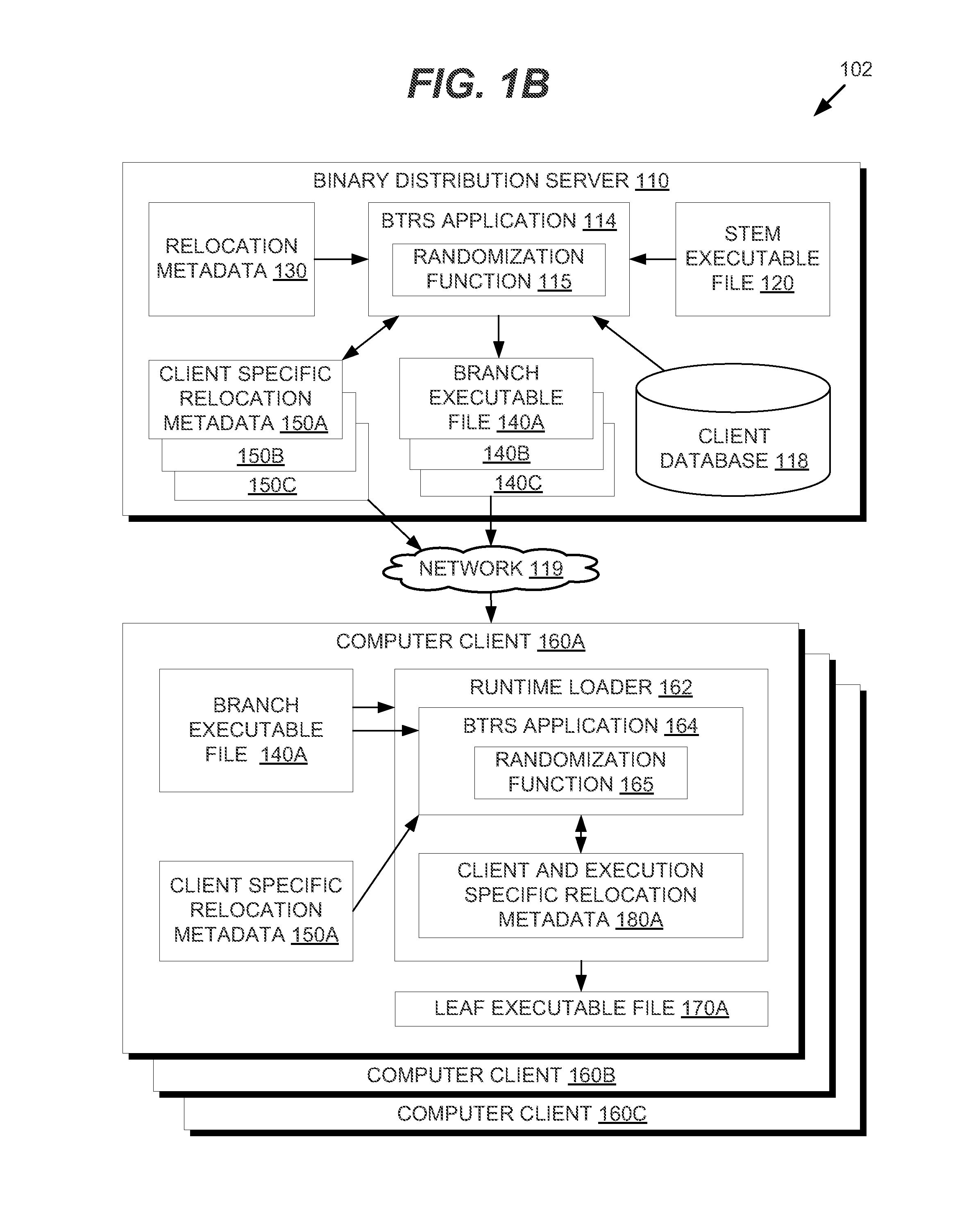
In one embodiment, methods are described to provide a binary translation and randomization system. Relocation metadata is received, which comprises, for each of a plurality of execution units in an executable file, a mapping from the executable file into an address space range. For at least one of the plurality of execution units, the mapping is modified to replace instructions within the address space range with a relocated copy of the instructions at a randomly located address space range. An order of the plurality of execution units may thus be modified. An image is generated from the executable file using the relocation metadata, and an execution of the image is caused. The randomization may be carried out in two passes to provide executable files that are uniquely randomized for each computer and for each execution.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com