Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1897 results about "Encryption system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An encryption system in which the sender and receiver of a message share a single, common key that is used to encrypt and decrypt the message.
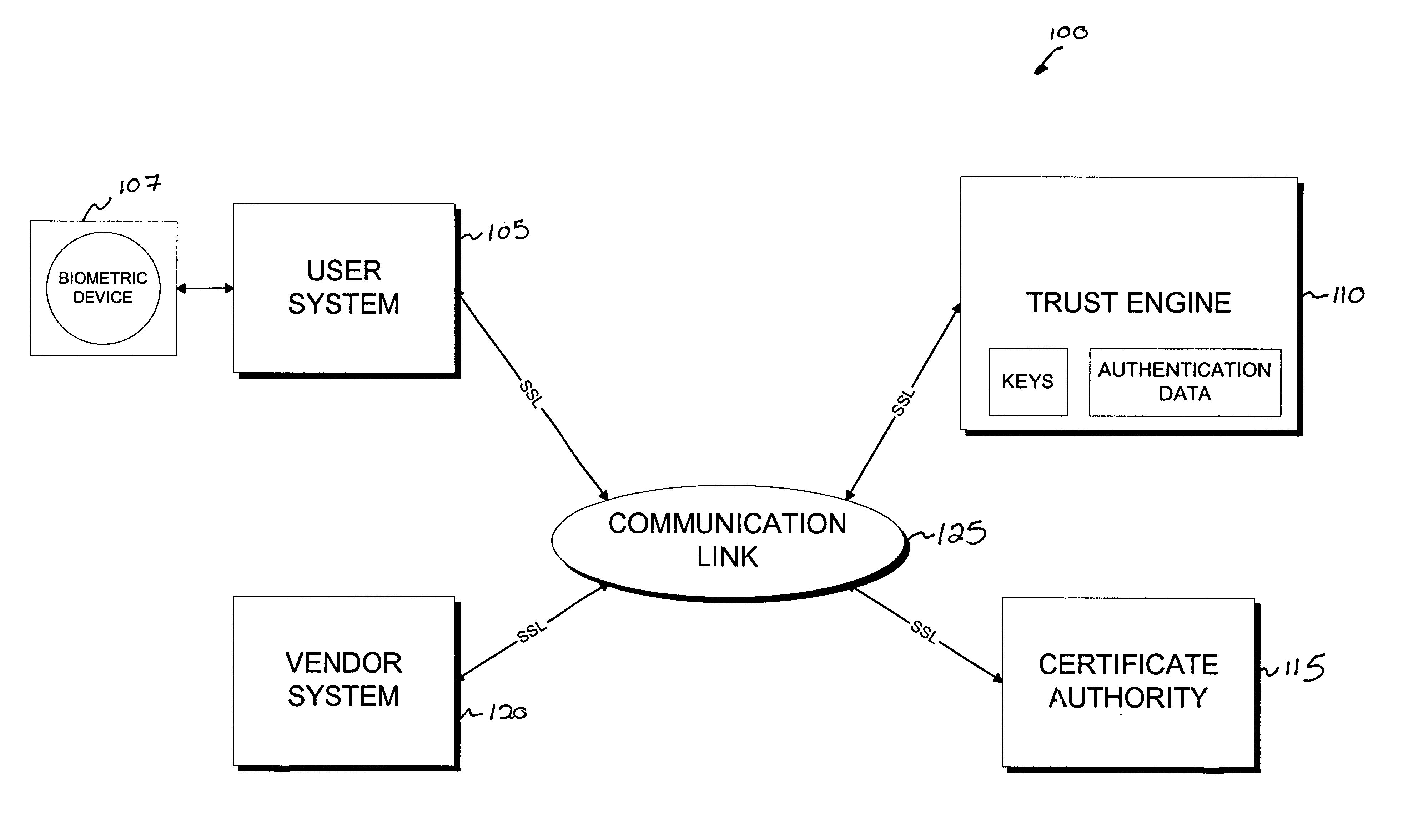
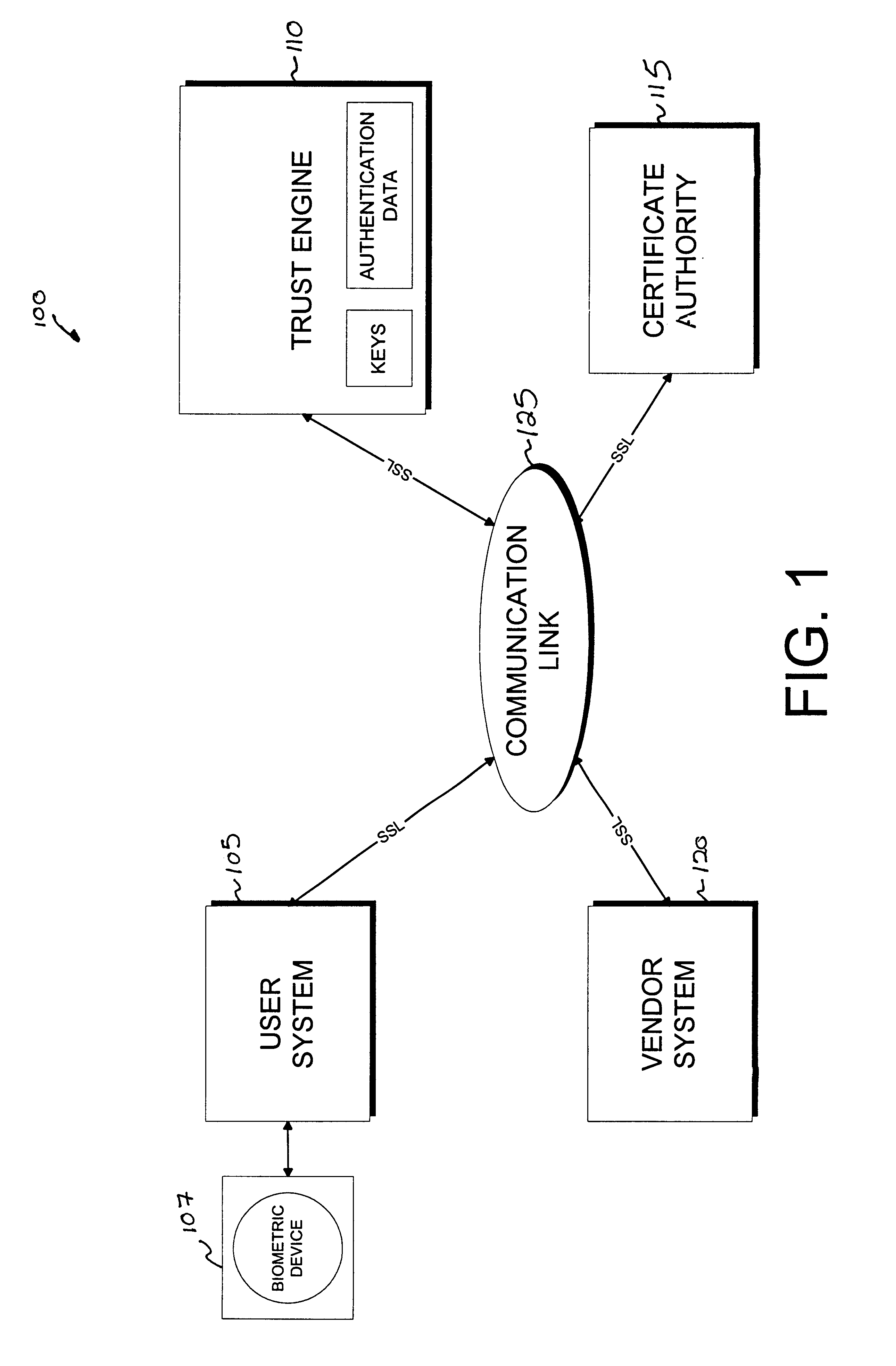
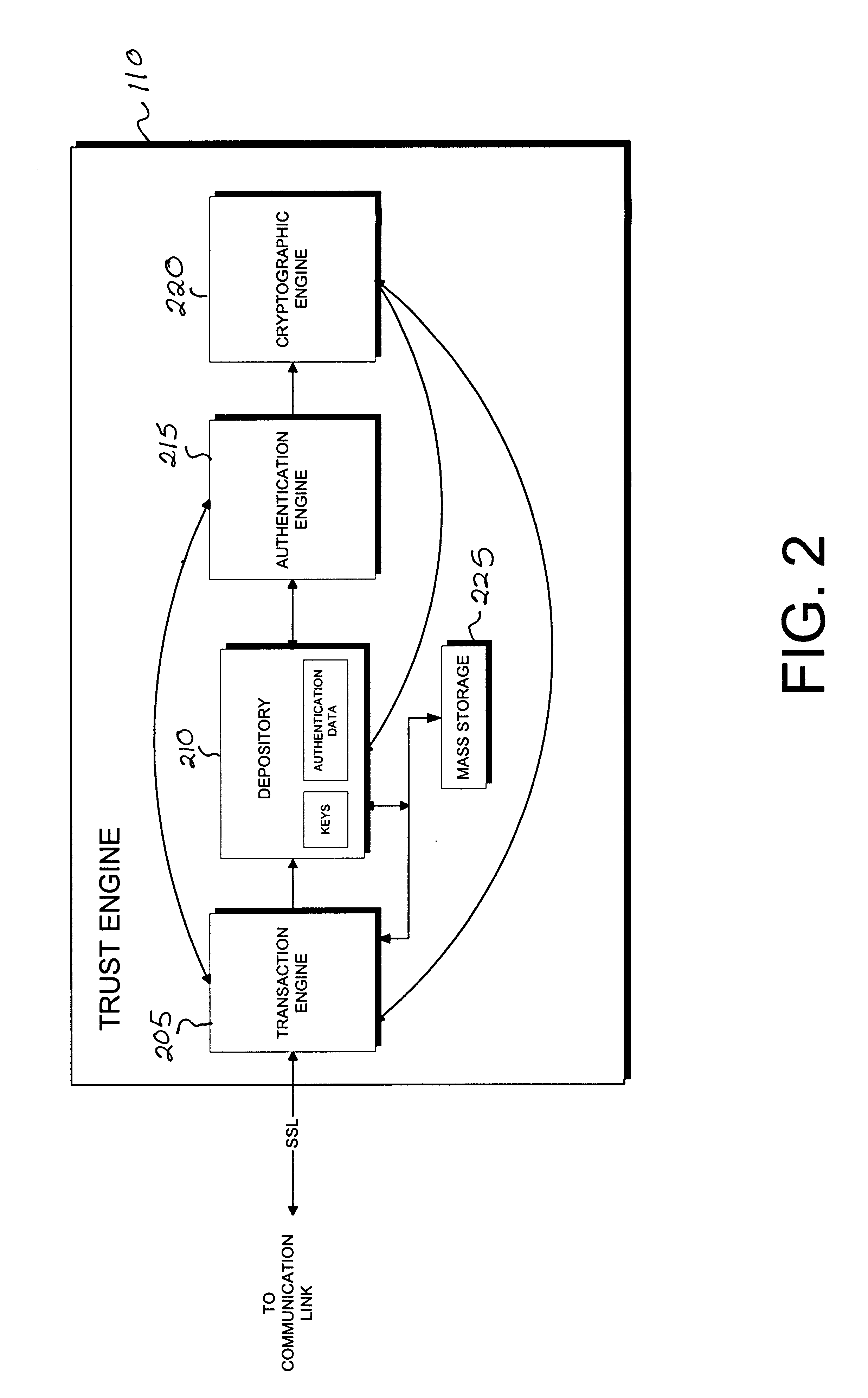
Cryptographic server with provisions for interoperability between cryptographic systems
InactiveUS6853988B1Reduce the number of timesMinimal compute resourceDigital data authenticationBuying/selling/leasing transactionsComputer hardwareKey storage
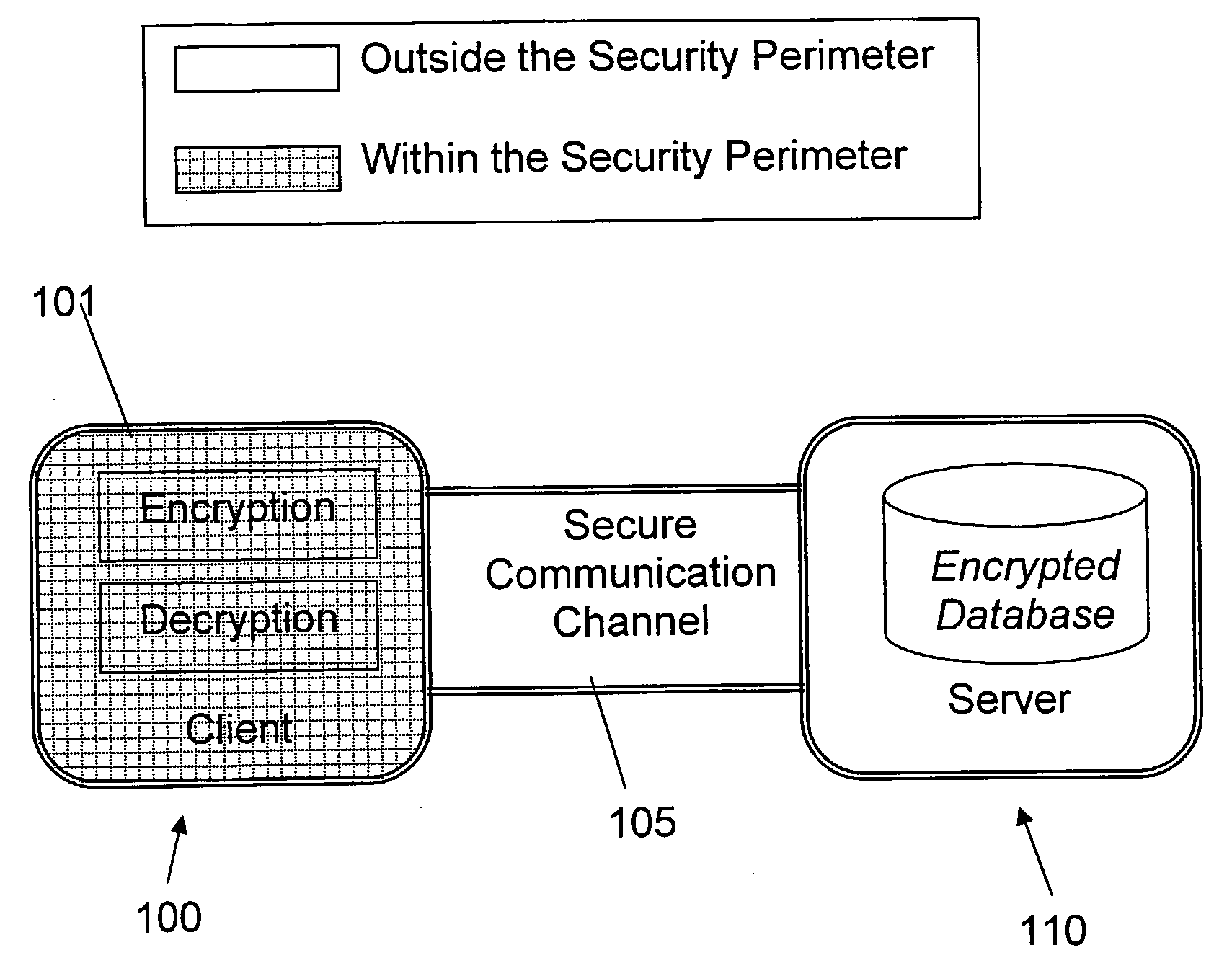
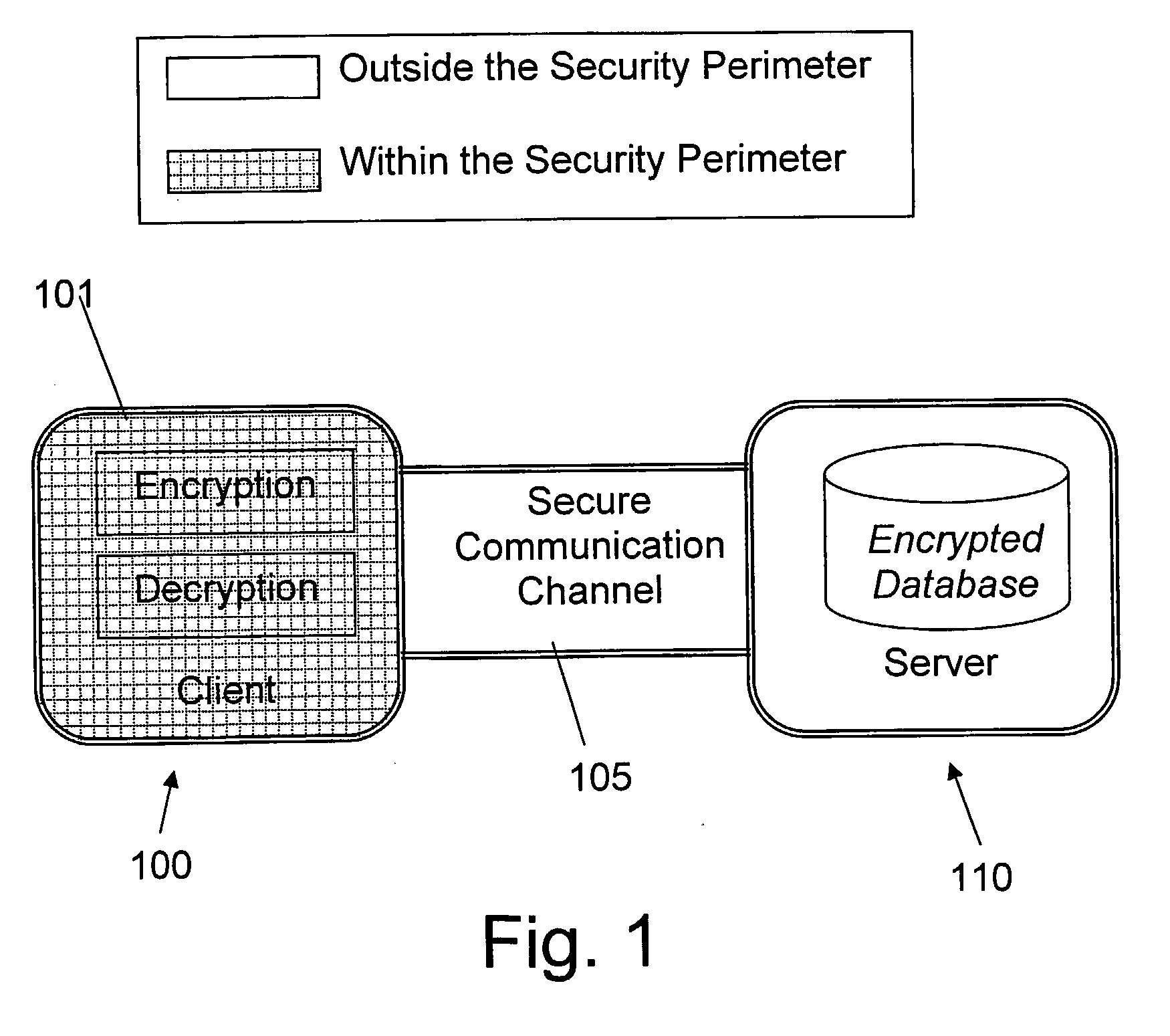
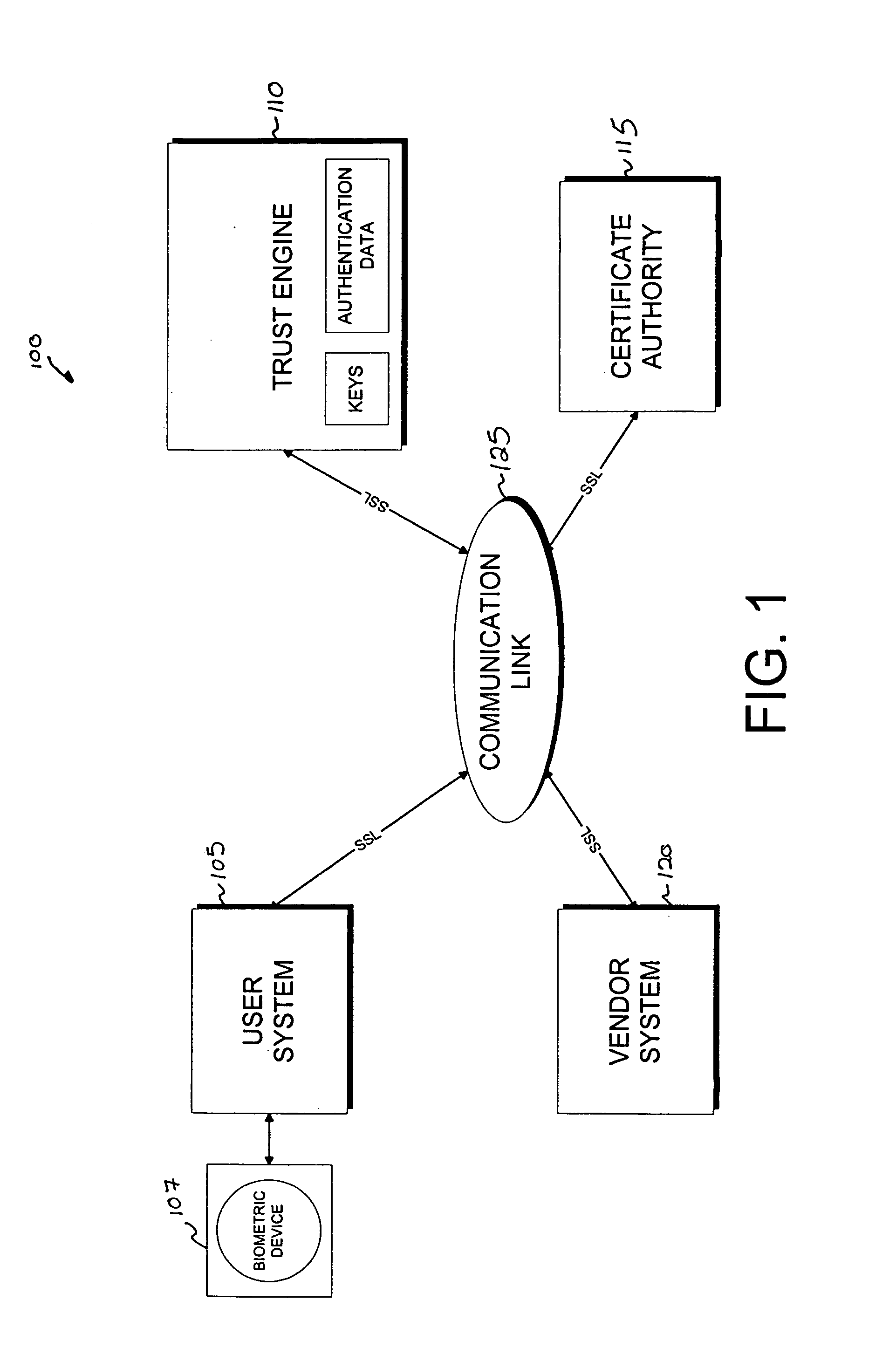
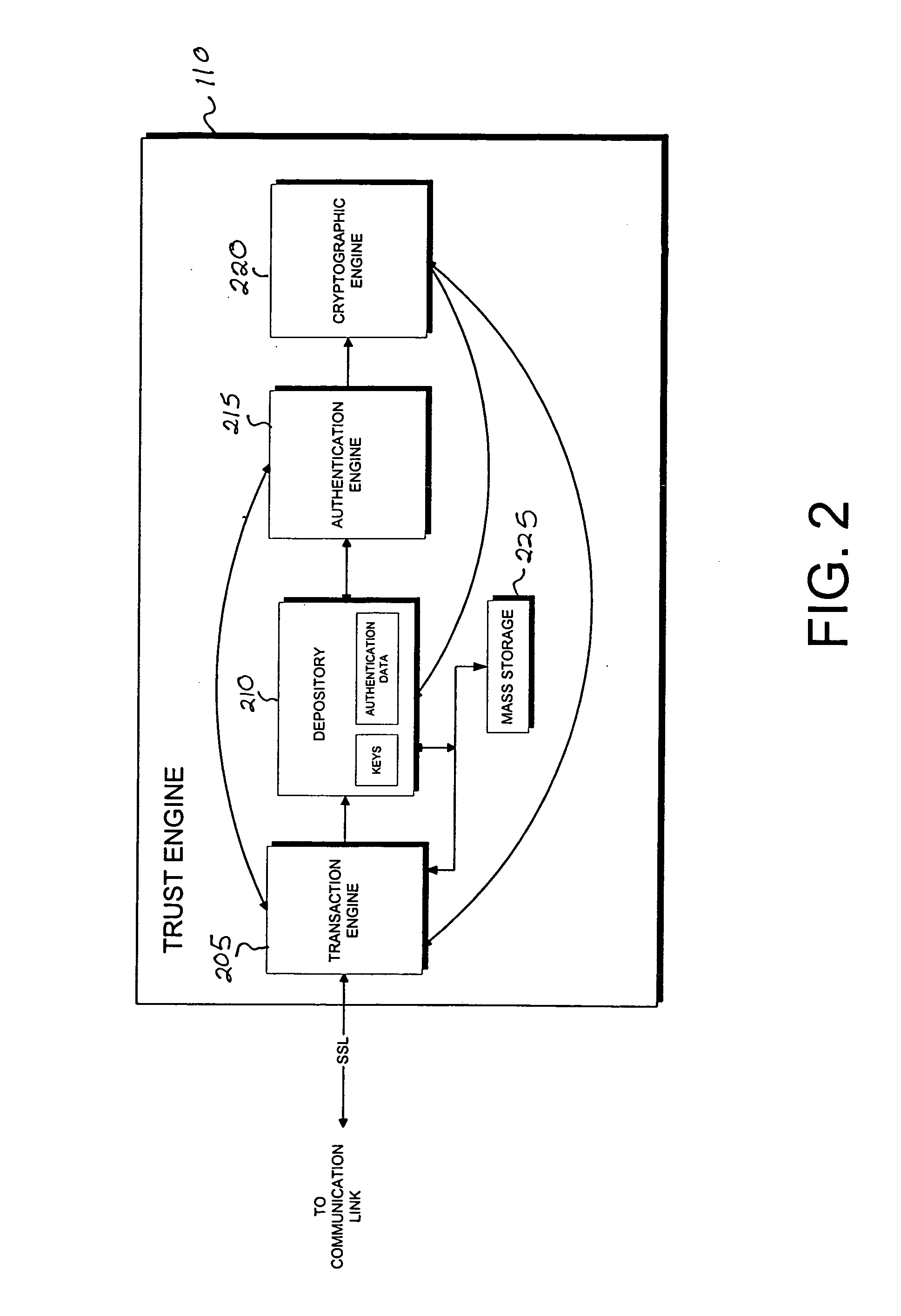
The invention is a cryptographic server providing interoperability over multiple algorithms, keys, standards, certificate types and issuers, protocols, and the like. Another aspect of the invention is to provide a secure server, or trust engine, having server-centric keys, or in other words, storing cryptographic keys on a server. The server-centric storage of keys provides for user-independent security, portability, availability, and straightforwardness, along with a wide variety of implementation possibilities.
Owner:SECURITY FIRST INNOVATIONS LLC
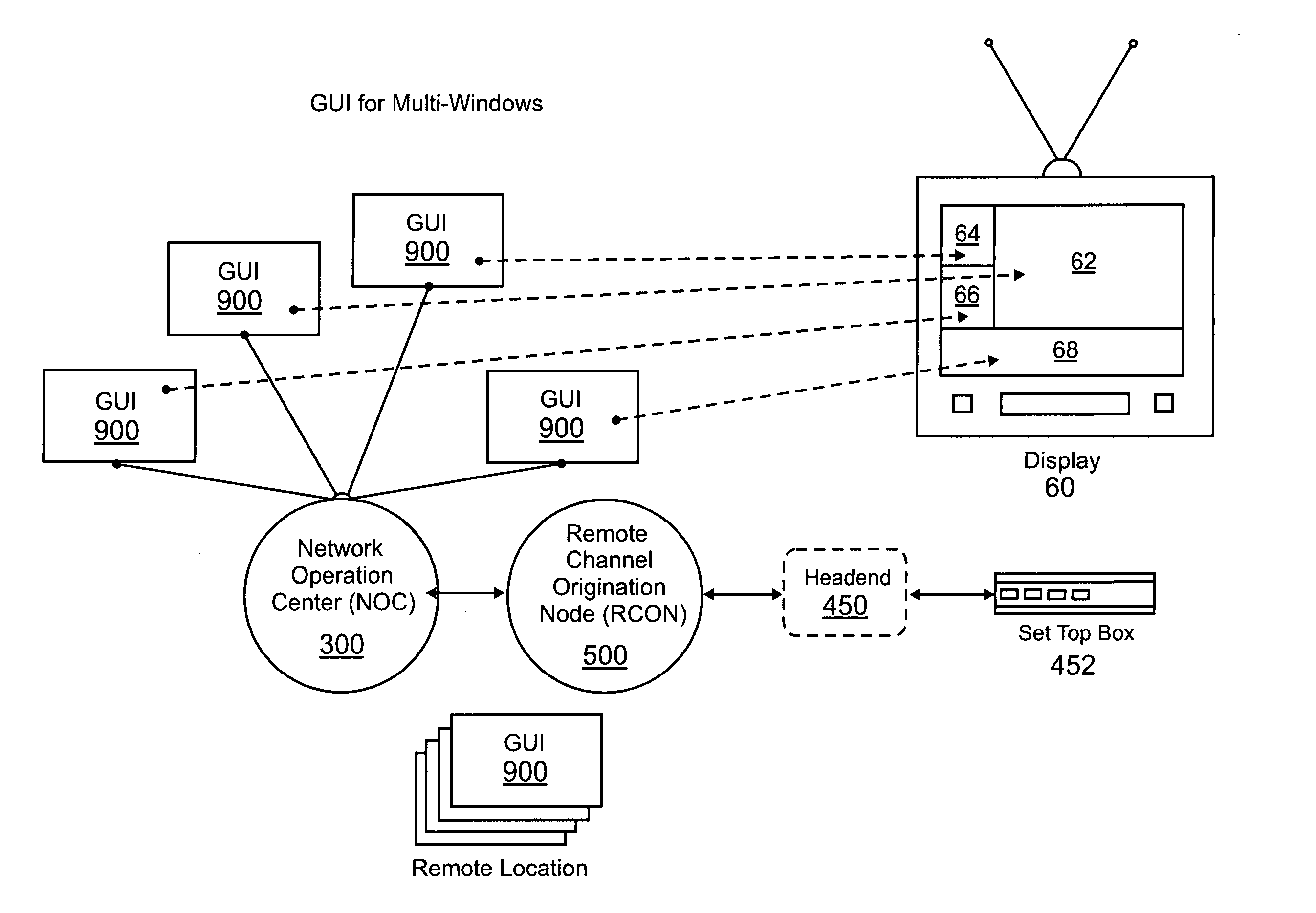
Encapsulated, streaming media automation and distribution system
ActiveUS20050060759A1Low costReduce operating costsTelevision system detailsGHz frequency transmissionDisplay deviceApplication software
Disclosed are systems and methods for creating and distributing programming content carried by a digital streaming media to be a plurality of remote nodes located over a large geographic area to create customized broadcast quality programming at the remote nodes. At the remote nodes, a multi-window screen display simultaneously shows different programming including national programming and local programming content. The remote nodes utilize a remote channel origination device to assemble the customized programming at the remote location that can be controlled from a central location. An encapsulated IP and IP encryption system is used to transport the digital streaming media to the appropriate remote nodes. Also disclosed is a graphical user interface (“GUI”) providing a software control interface for creating and editing shows or programs that can be aired or played on a remote display device having a multi-window display. The intuitive GUI Software provides the user the ability to easily manage and assemble a series of images, animations and transitions as a single broadcast quality program to be displayed on a remote display device. Another application software system is capable of automating the production of audio narration reports. The disclosed audio concatenation engine automates the creation of audio narration using prerecorded audio segments to minimize the requirement for live, on-air personnel to record audio narration segments.
Owner:CALLAHAN CELLULAR L L C
Structure Preserving Database Encryption Method and System
ActiveUS20080133935A1Easy accessAvoid contactKey distribution for secure communicationMultiple keys/algorithms usageDatabase indexMulti user environment
A database encryption system and method, the Structure Preserving Database Encryption (SPDE), is presented. In the SPDE method, each database cell is encrypted with its unique position. The SPDE method permits to convert a conventional database index into a secure one, so that the time complexity of all queries is maintained. No one with access to the encrypted database can learn anything about its content without the encryption key. Also a secure index for an encrypted database is provided. Furthermore, secure database indexing system and method are described, providing protection against information leakage and unauthorized modifications by using encryption, dummy values and pooling, and supporting discretionary access control in a multi-user environment.
Owner:BEN GURION UNIVERSITY OF THE NEGEV
Format-preserving cryptographic systems
ActiveUS20080170693A1Error detection/correctionCryptography processingData processing systemOne-way function
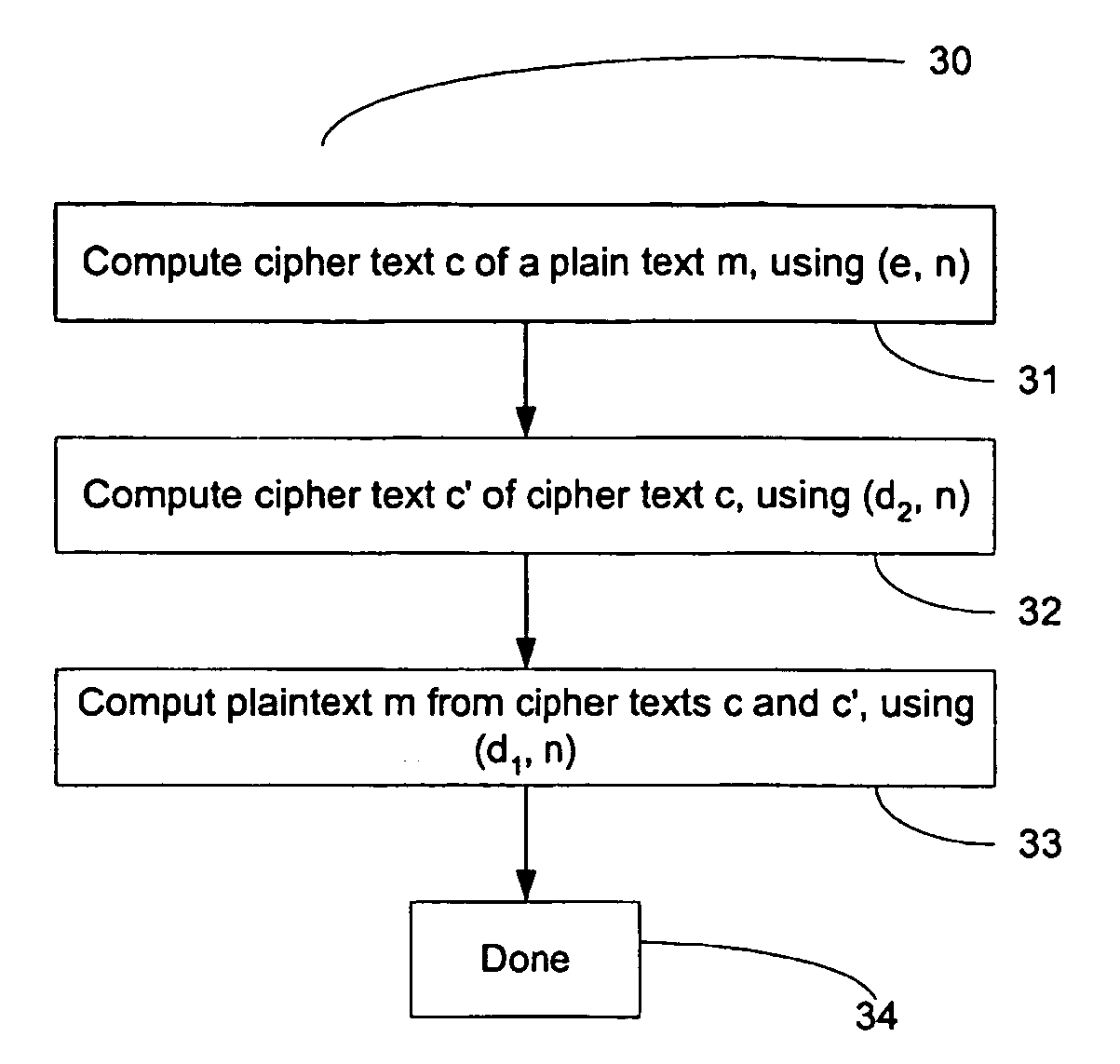
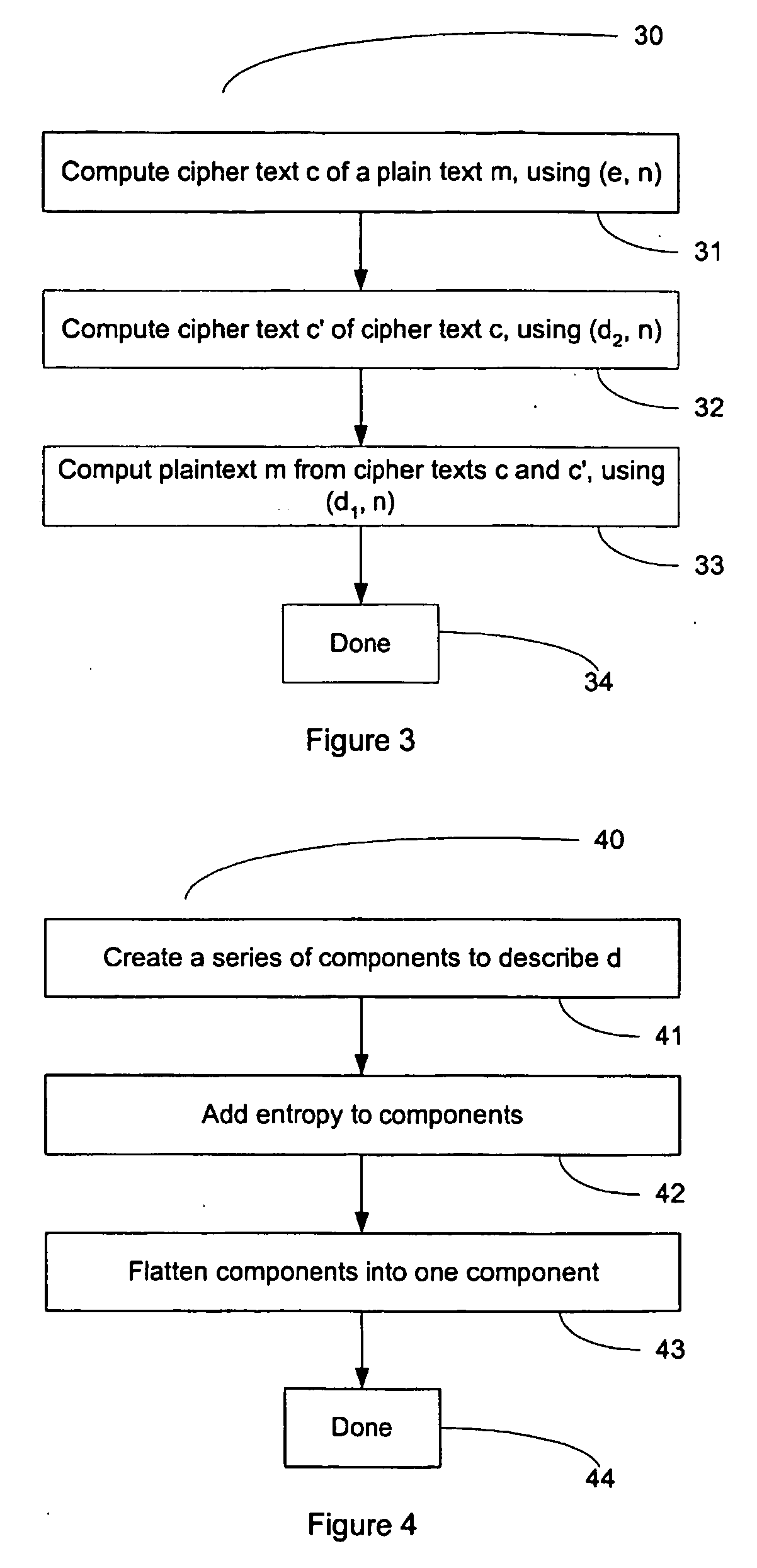
Key requests in a data processing system may include identifiers such as user names, policy names, and application names. The identifiers may also include validity period information indicating when corresponding keys are valid. When fulfilling a key request, a key server may use identifier information from the key request in determining which key access policies to apply and may use the identifier in determining whether an applicable policy has been satisfied. When a key request is authorized, the key server may generate a key by applying a one-way function to a root secret and the identifier. Validity period information for use by a decryption engine may be embedded in data items that include redundant information. Application testing can be facilitated by populating a test database with data that has been encrypted using a format-preserving encryption algorithm. Parts of a data string may be selectively encrypted based on their sensitivity.
Owner:MICRO FOCUS LLC
Context sensitive dynamic authentication in a cryptographic system
InactiveUS7260724B1Minimal compute resourceAvoid the needUser identity/authority verificationComputer security arrangementsInternet privacyTrust level
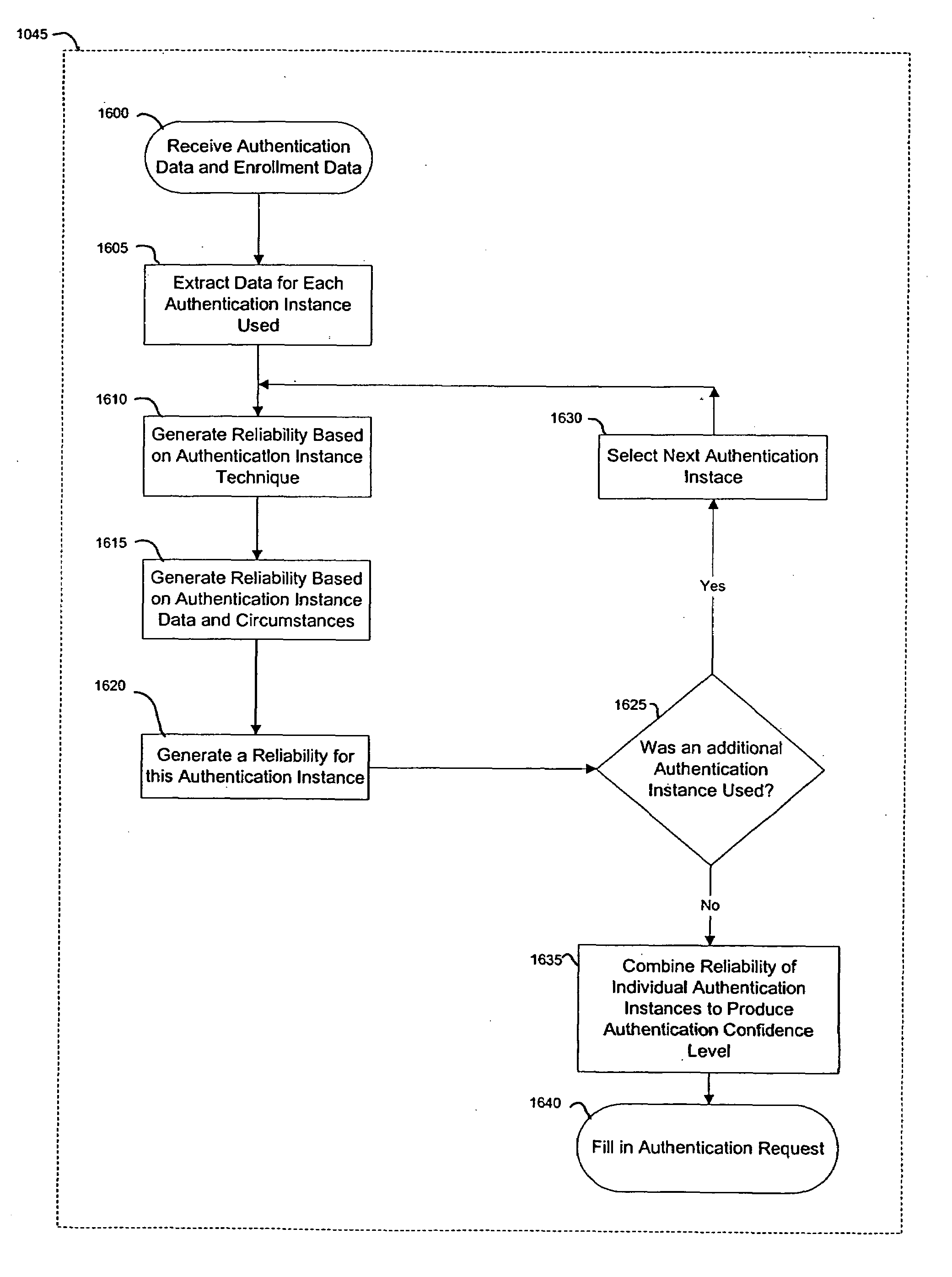
A system for performing authentication of a first user to a second user includes the ability for the first user to submit multiple instances of authentication data which are evaluated and then used to generate an overall level of confidence in the claimed identity of the first user. The individual authentication instances are evaluated based upon: the degree of match between the user provided by the first user during the authentication and the data provided by the first user during his enrollment; the inherent reliability of the authentication technique being used; the circumstances surrounding the generation of the authentication data by the first user; and the circumstances surrounding the generation of the enrollment data by the first user. This confidence level is compared with a required trust level which is based at least in part upon the requirements of the second user, and the authentication result is based upon this comparison.
Owner:SECURITY FIRST INNOVATIONS LLC
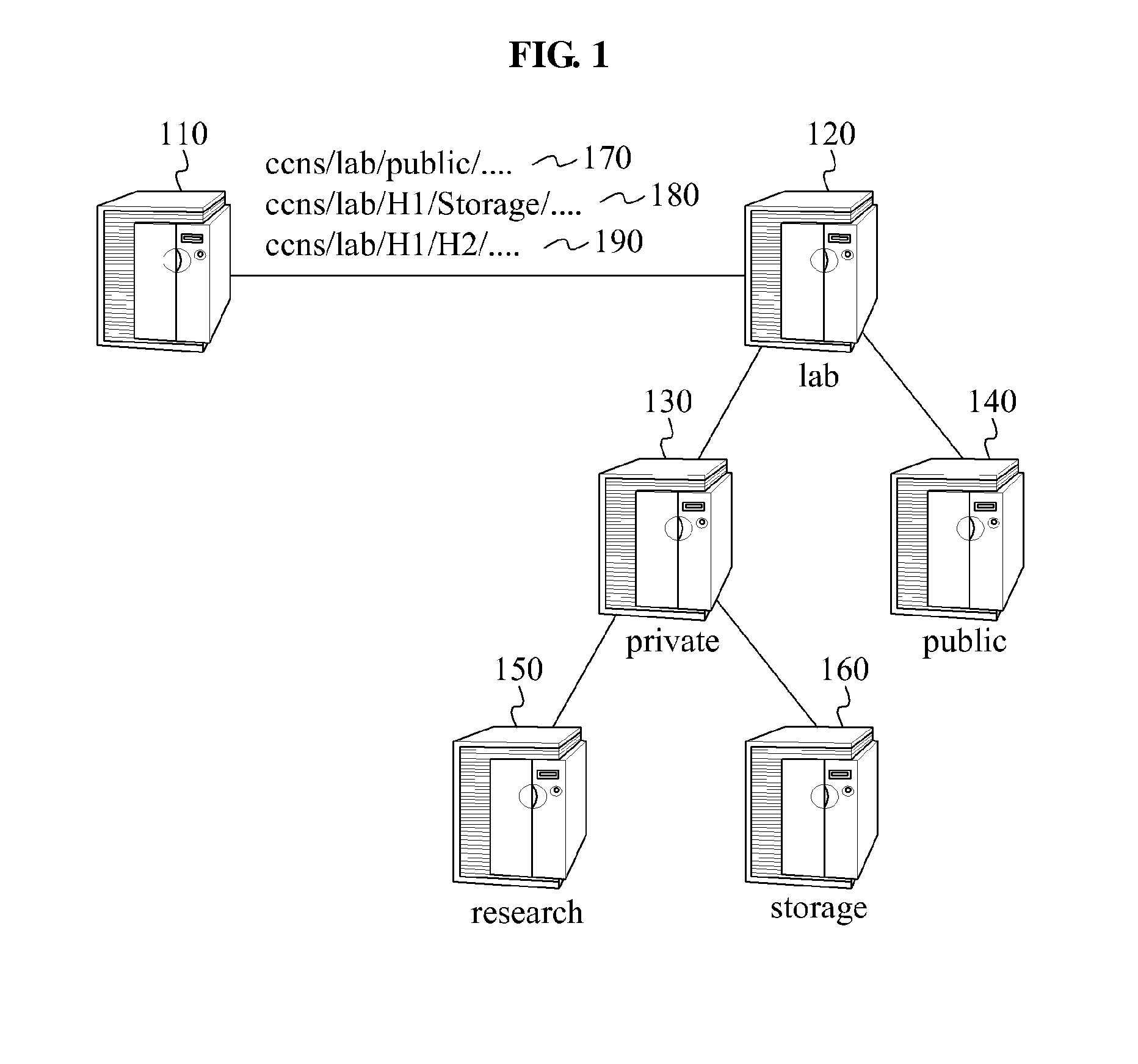
System for encrypting content name
InactiveUS20140149733A1Well formedEncryption apparatus with shift registers/memoriesComputer networkHash function
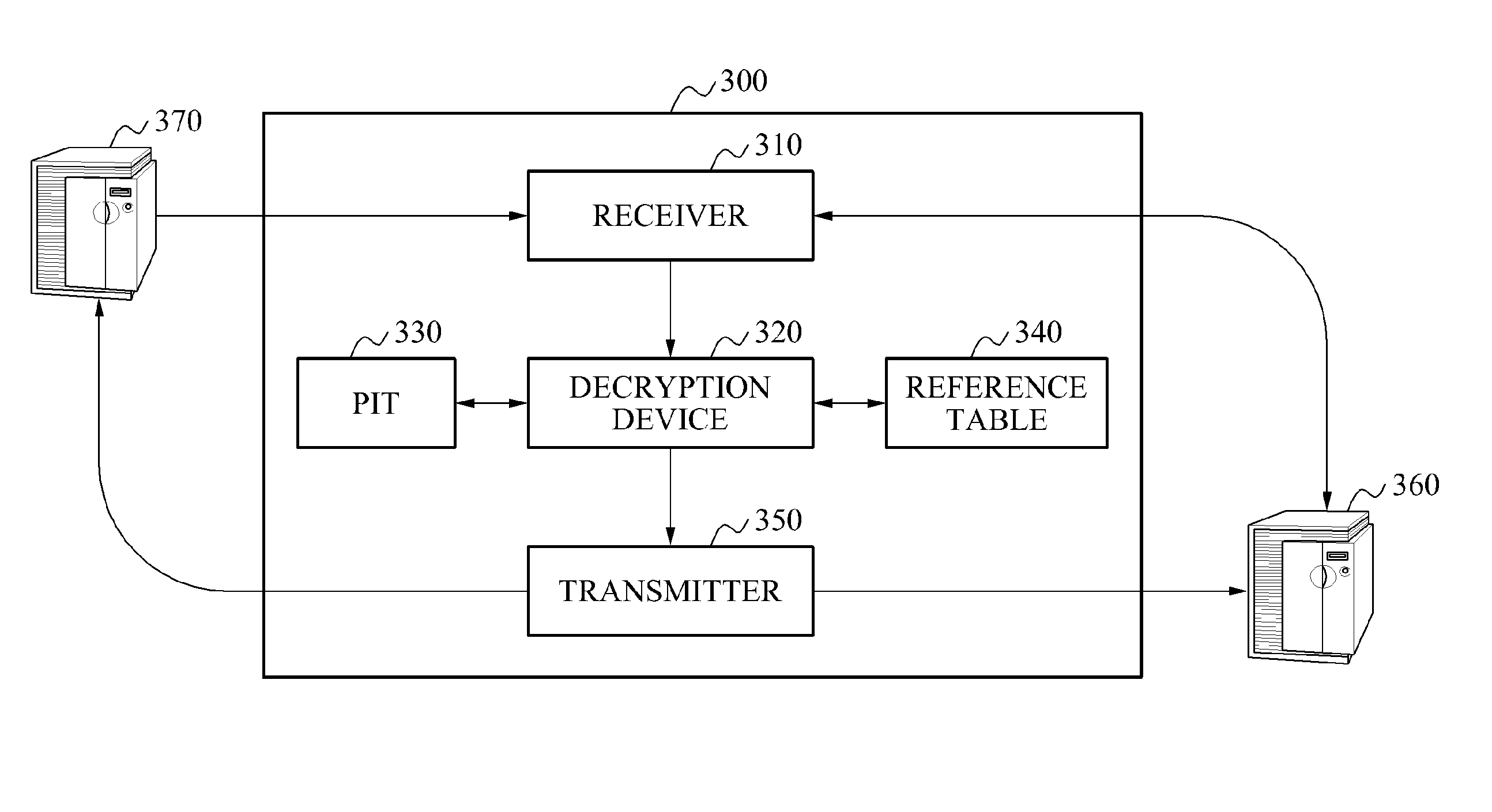
A system encrypts a name of content stored in a node of a hierarchical structure. A content receiving node encrypts a name of a predetermined node among names of nodes included in a content name, such as by using a hash function, and transmits the encrypted content name to receive the stored content. A relay node receives the content name including the encrypted name of the node and decrypts the encrypted name of the node, such as by using a reference table. The relay node uses the decrypted node name to relay the content request to the content storage node. Since the content name is encrypted, content routing may be performed without disclosing information associated with a hierarchical structure in which the content is stored.
Owner:SAMSUNG ELECTRONICS CO LTD
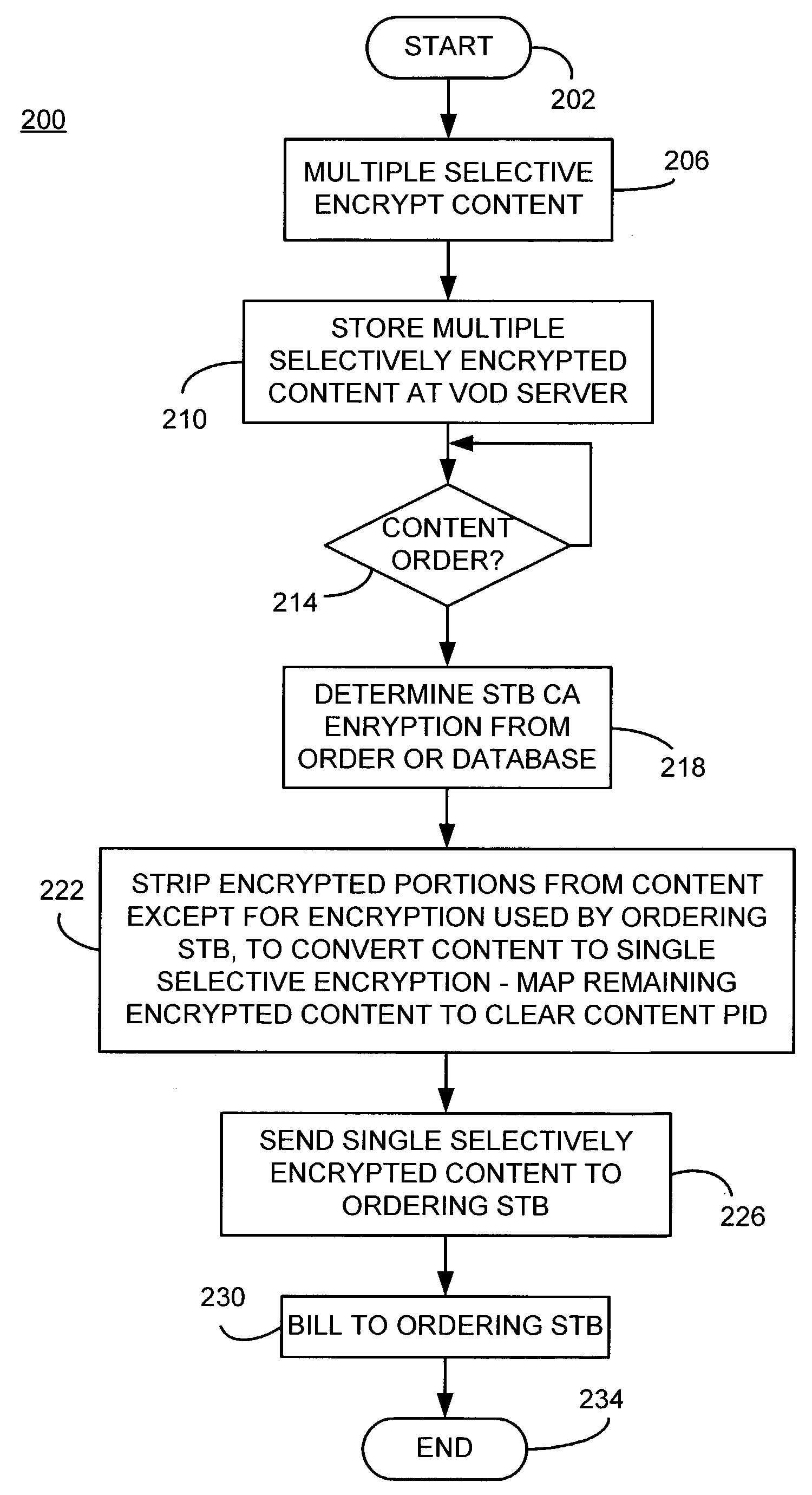
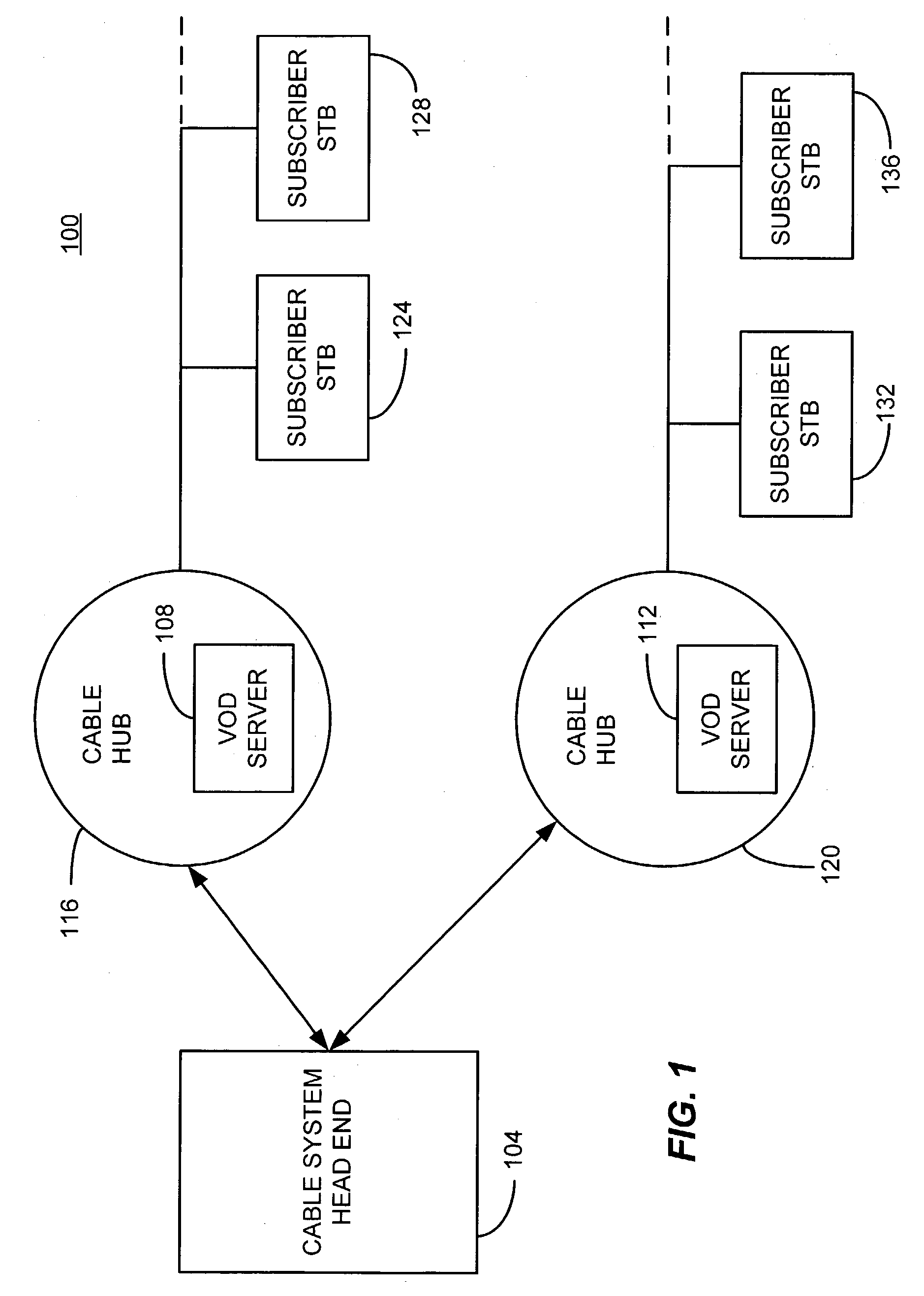
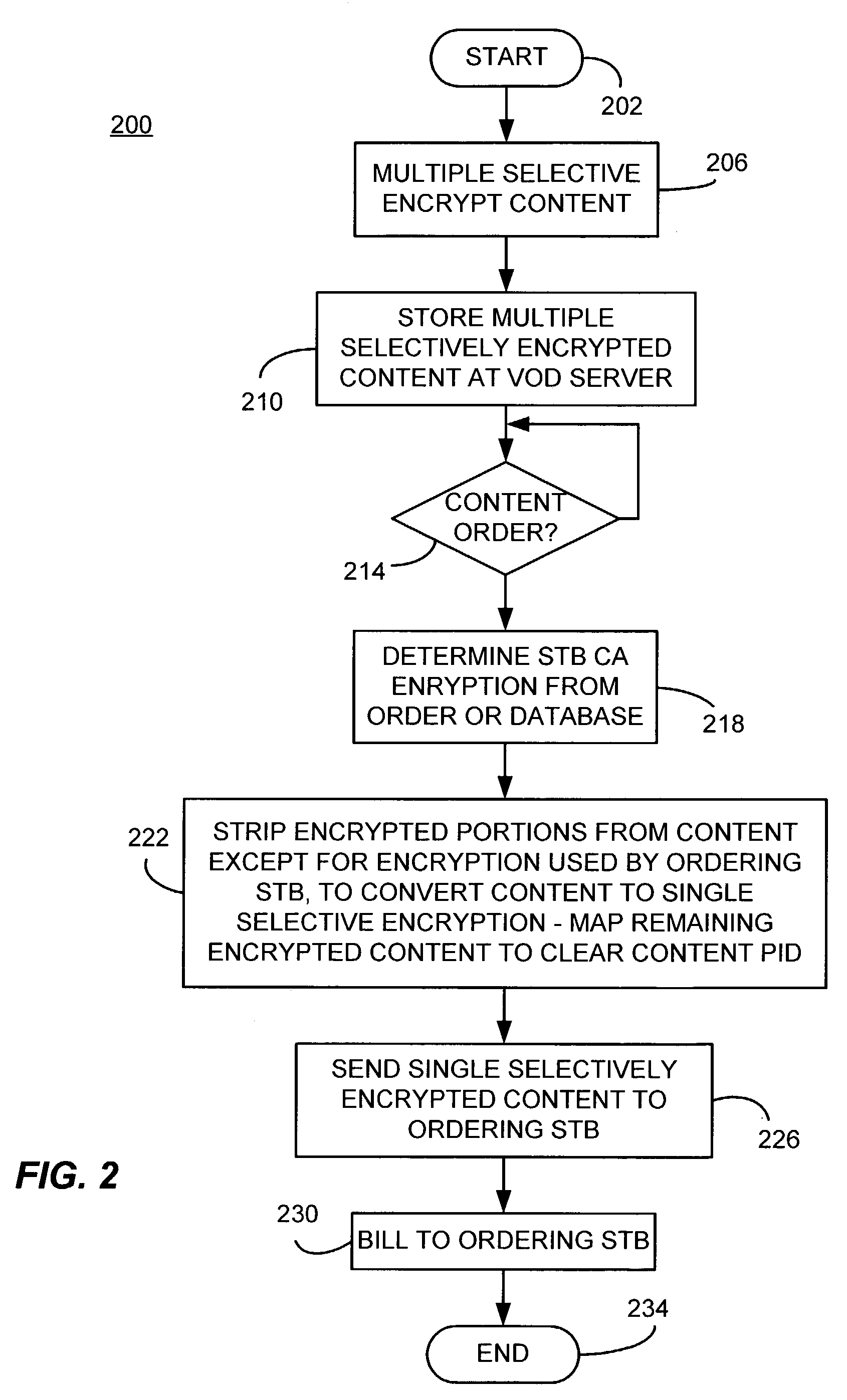
Selective encryption for video on demand
InactiveUS7039938B2Analogue secracy/subscription systemsTwo-way working systemsConditional access systemsDigital content
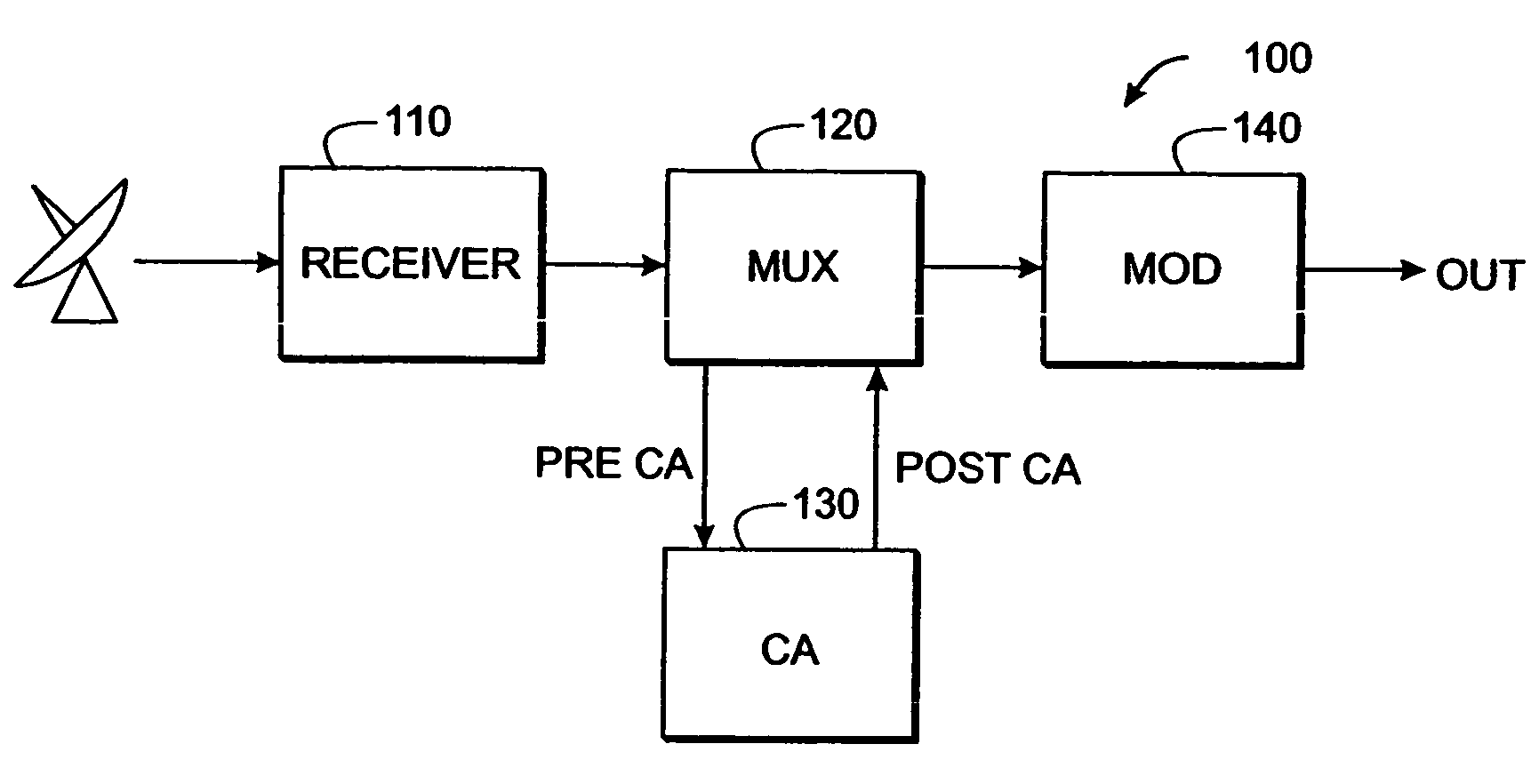
A video on demand (VOD) method, consistent with the invention involves storing multiple selective encrypted VOD content on a VOD server; receiving an order for the VOD content specifying delivery to a target decoder; determining what CA encryption system is associated with the order; stripping all encrypted segments from the multiple selectively encrypted content that are not associated with the order to produce single selectively encrypted VOD content; and sending the single selectively encrypted VOD content to the target decoder. The multiple selectively encrypted VOD content can be created by examining unencrypted data representing digital content to identify segments of content for encryption; encrypting the identified segments of content using a first encryption method associated with a first conditional access system to produce first encrypted segments; encrypting the identified segments of content using a second encryption method associated with a second conditional access system to produce second encrypted segments; and replacing the identified segments of content with the first encrypted content and the second encrypted content in the digital content, to produce the multiple selectively encrypted VOD content.
Owner:SONY CORP +1
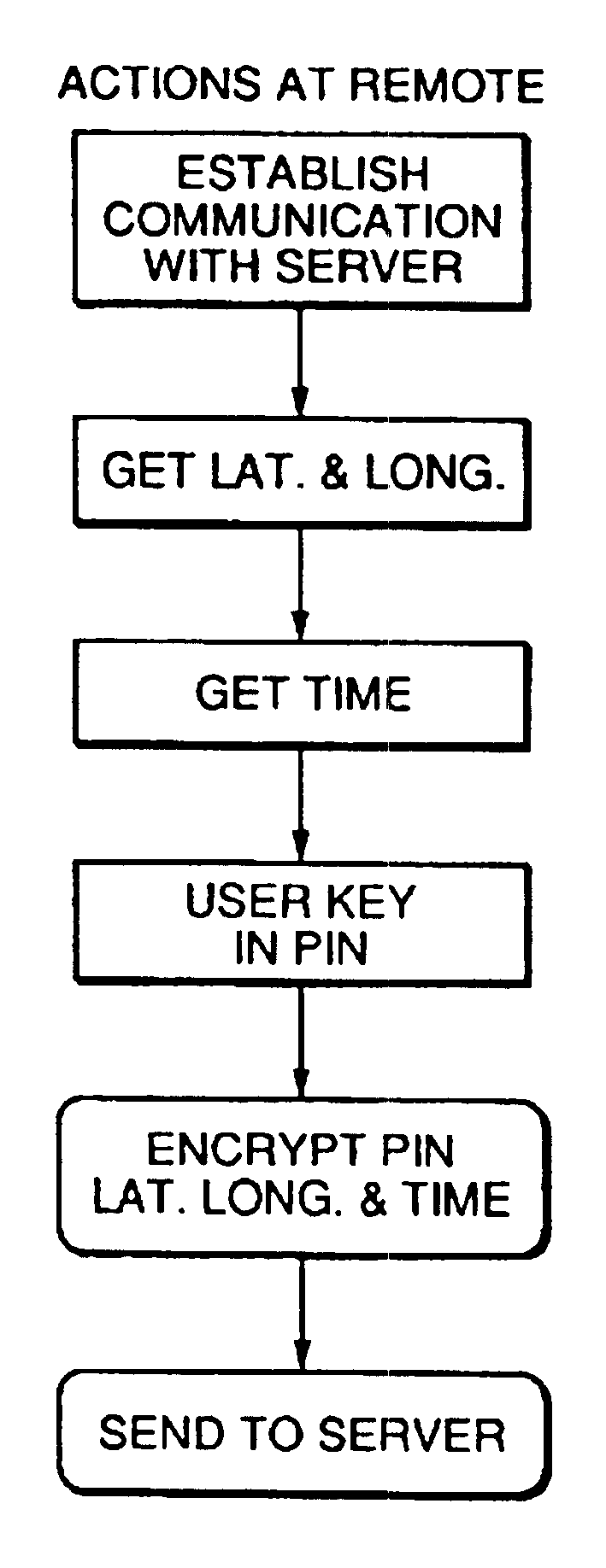
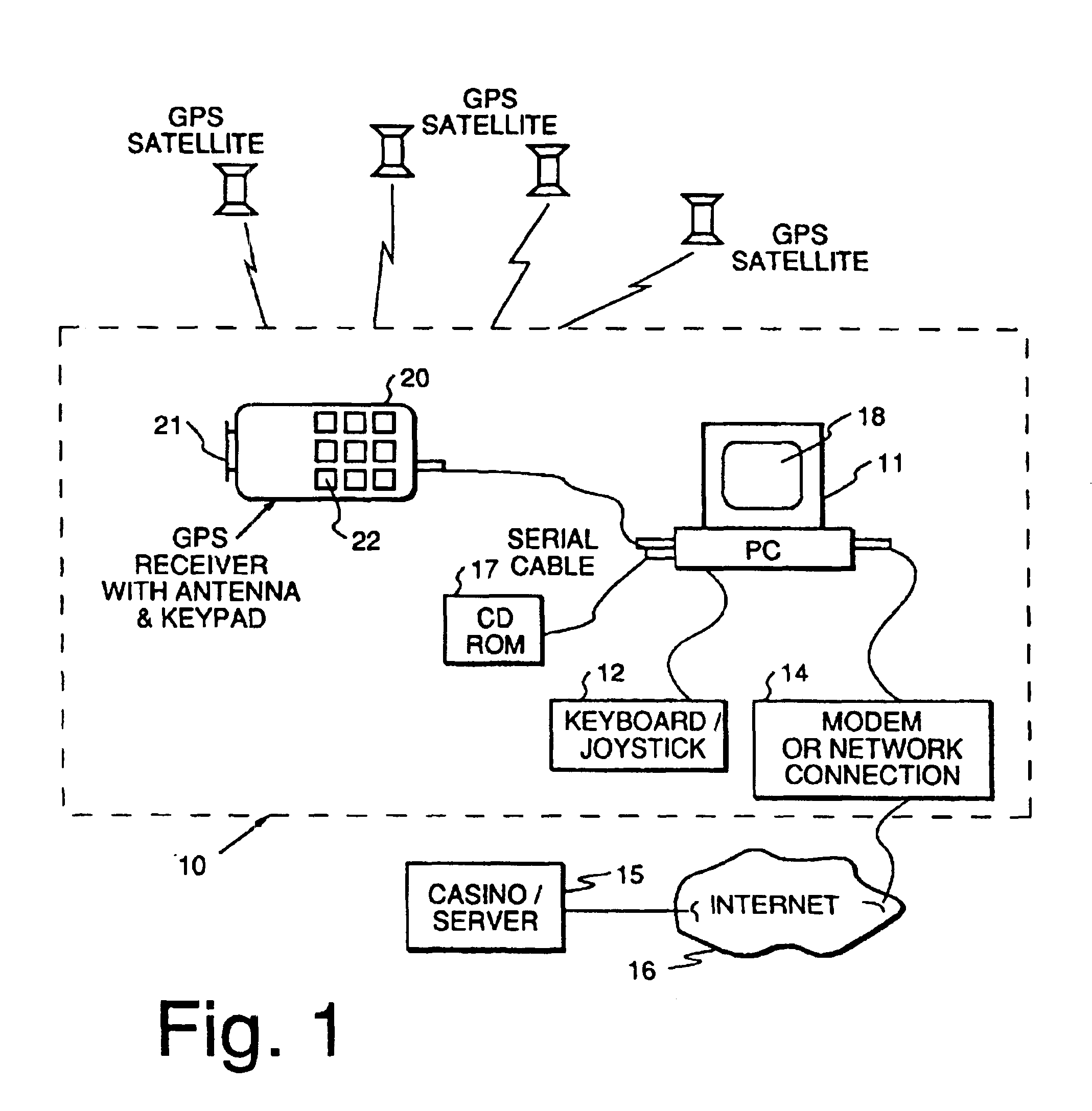
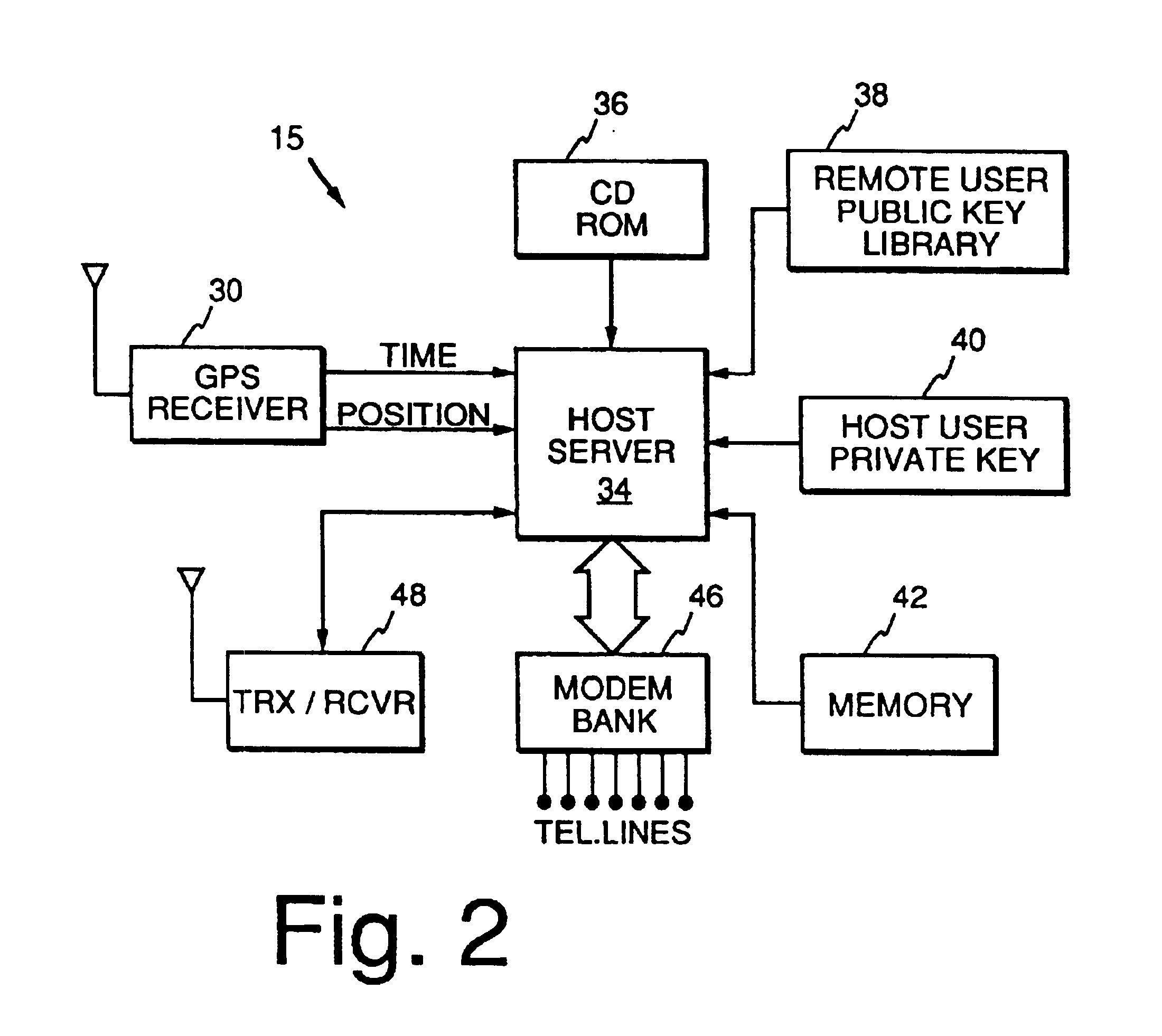
Method and apparatus using geographical position and universal time determination means to provide authenticated, secure, on-line communication between remote gaming locations
InactiveUSRE39644E1Facilitates denialAccurately determineSecret communicationApparatus for meter-controlled dispensingGeolocationThe Internet
Method and apparatus for providing authenticated, secure, on-line communication between remote locations including a user terminal adapted to enable a player in one location to remotely communicate via a communications medium such as the Internet with a gaming host in another location. Location of the remote user terminal, the host server and universal time are determined using means for accessing signals generated by geostationary navigational transmitters, such as in the global positioning satellite (GPS) system. Player authentication (identity verification) is determined by use of a personal identification number (PIN) and an electronic signature verification service. Security of communication is accomplished through use of a public-key / private-key encryption system. The remote user terminal may be comprised of one or more discreet components adapted to be used with a laptop or desktop personal computer (PC), or may be embodied in a stand alone or self-contained single unit that is portable and communicates via radio waves, telephone lines or the Internet to a host server.
Owner:IGT
System and method for variable length encryption
InactiveUS20120039469A1Ensure data securityImprove securityCryptography processingPayment architecturePlaintextVariable length
Systems and methods for performing a secure transaction provided. In one embodiment, the method includes: reading data on a command token, reading data on a token; encrypting the token data with a key; encrypting an authentication data with a clear text token data; and transmitting the encrypted authentication data with the encrypted token data to a remote device.
Owner:VERIFONE INC
Method and system for securing a computer network and personal identification device used therein for controlling access to network components
InactiveUS7310734B2Real-time authenticationDigital data processing detailsUser identity/authority verificationDigital signatureIdentification device
An improved computer network security system and a personal identifier device used for controlling network with real time authentication of both a person's identity and presence at a computer workstation is provided. A new user is registered to a portable personal digital identifier device and, within the portable personal digital identifier device, an input biometric of the user is received and a master template is derived therefrom and securely maintained in storage. A private key and public key encryption system is utilized to authenticate a user registered to the portable personal digital identifier device. The personal digital identifier device verifies the origin of a digitally signed challenge message from the network security manager component. A digitally and biometrically signed challenge response message is produced and transmitted by the personal digital identifier device in response to the verified challenge message.
Owner:3M INNOVATIVE PROPERTIES CO
Relational database management encryption system
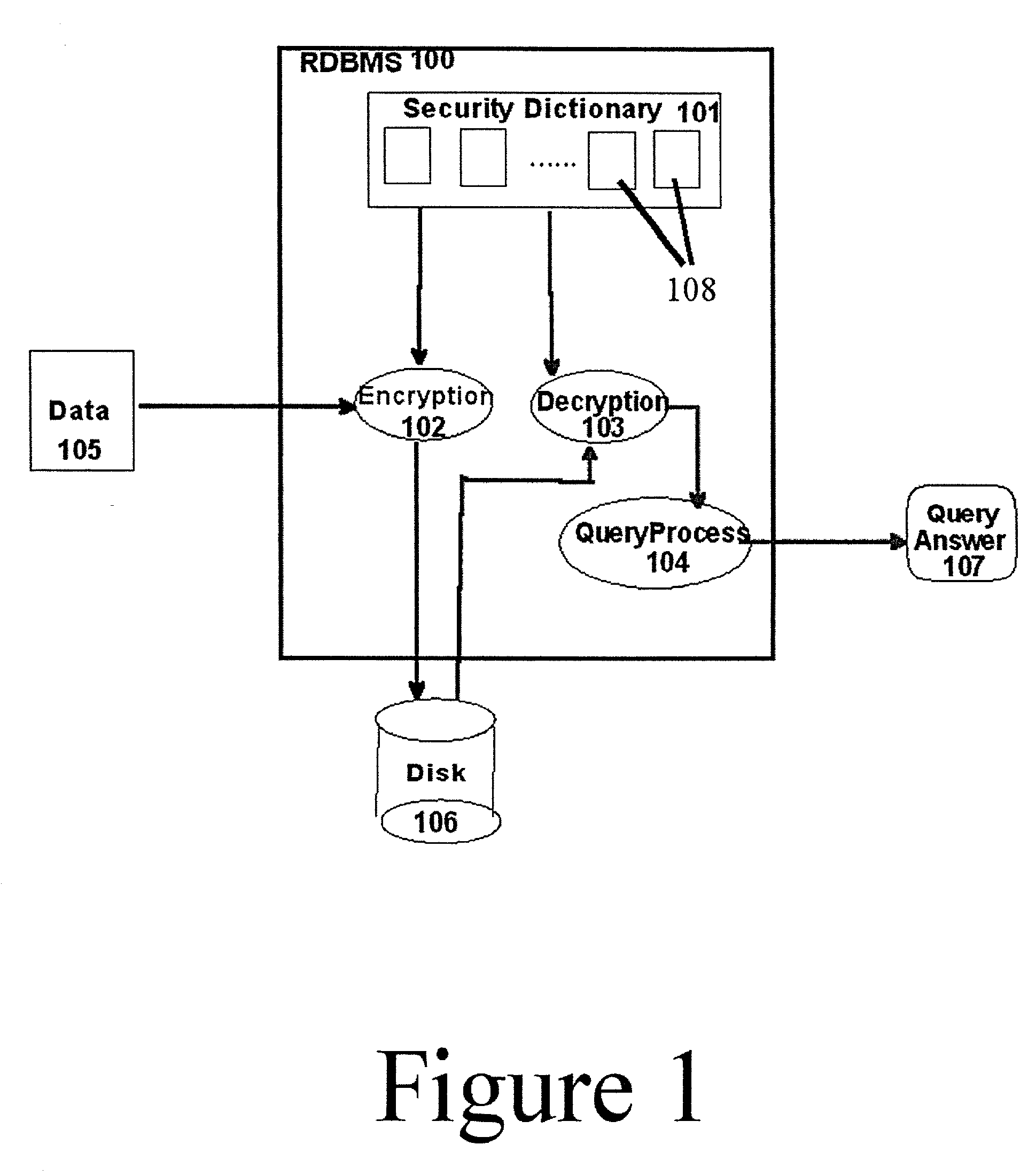
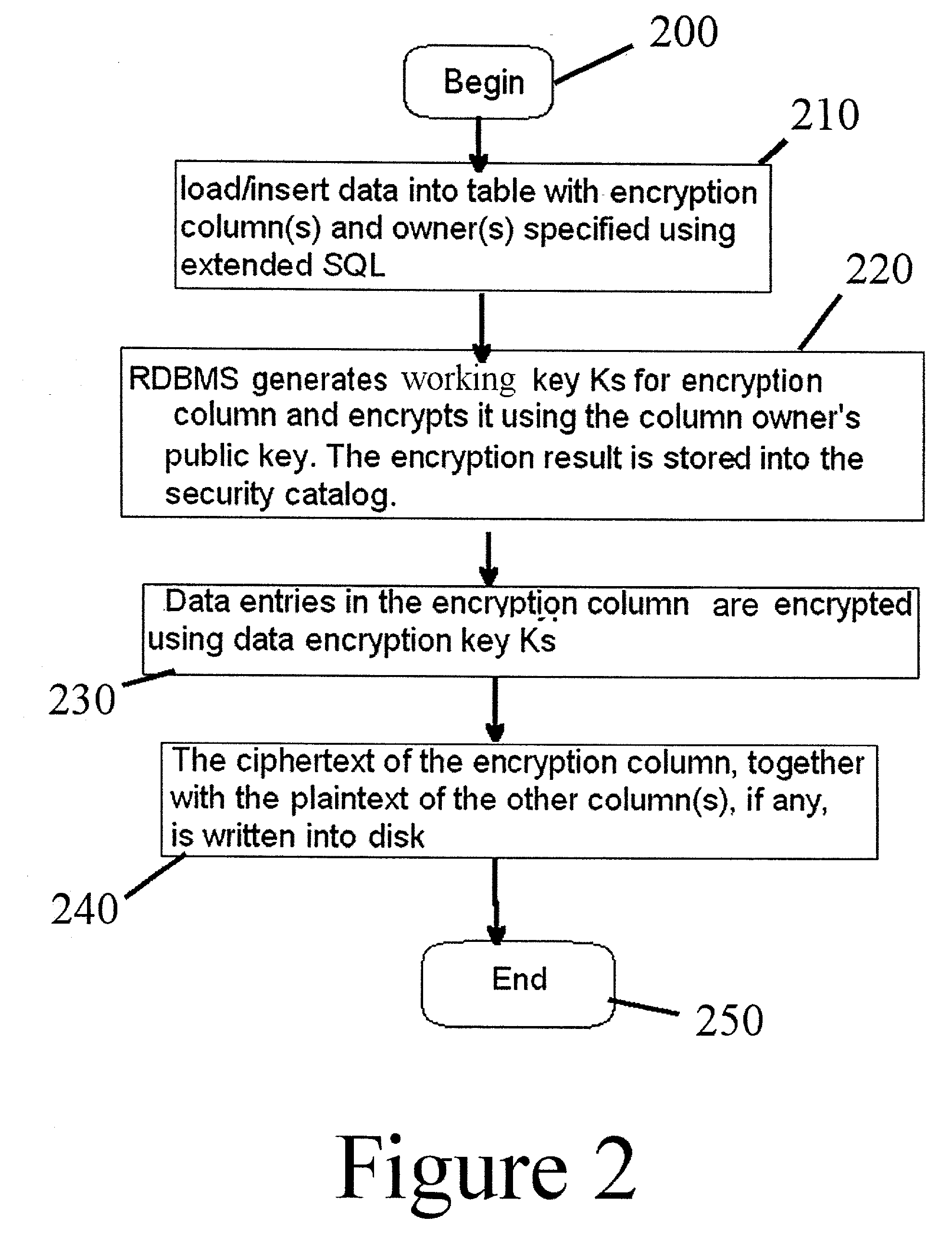
ActiveUS20030123671A1Key distribution for secure communicationUser identity/authority verificationRelational databaseEncryption system
Disclosed is a method of internally encrypting data in a relational database, comprising the steps of providing a security dictionary comprising one or more security catalogs, receiving data from a user associating said data with a database column and at least one authorized user, generating a working encryption key, internally encrypting said working encryption key using a public key from an authorized user, storing said encrypted working key in a security catalog, and using said working key to internally encrypt said data.
Owner:GOOGLE LLC
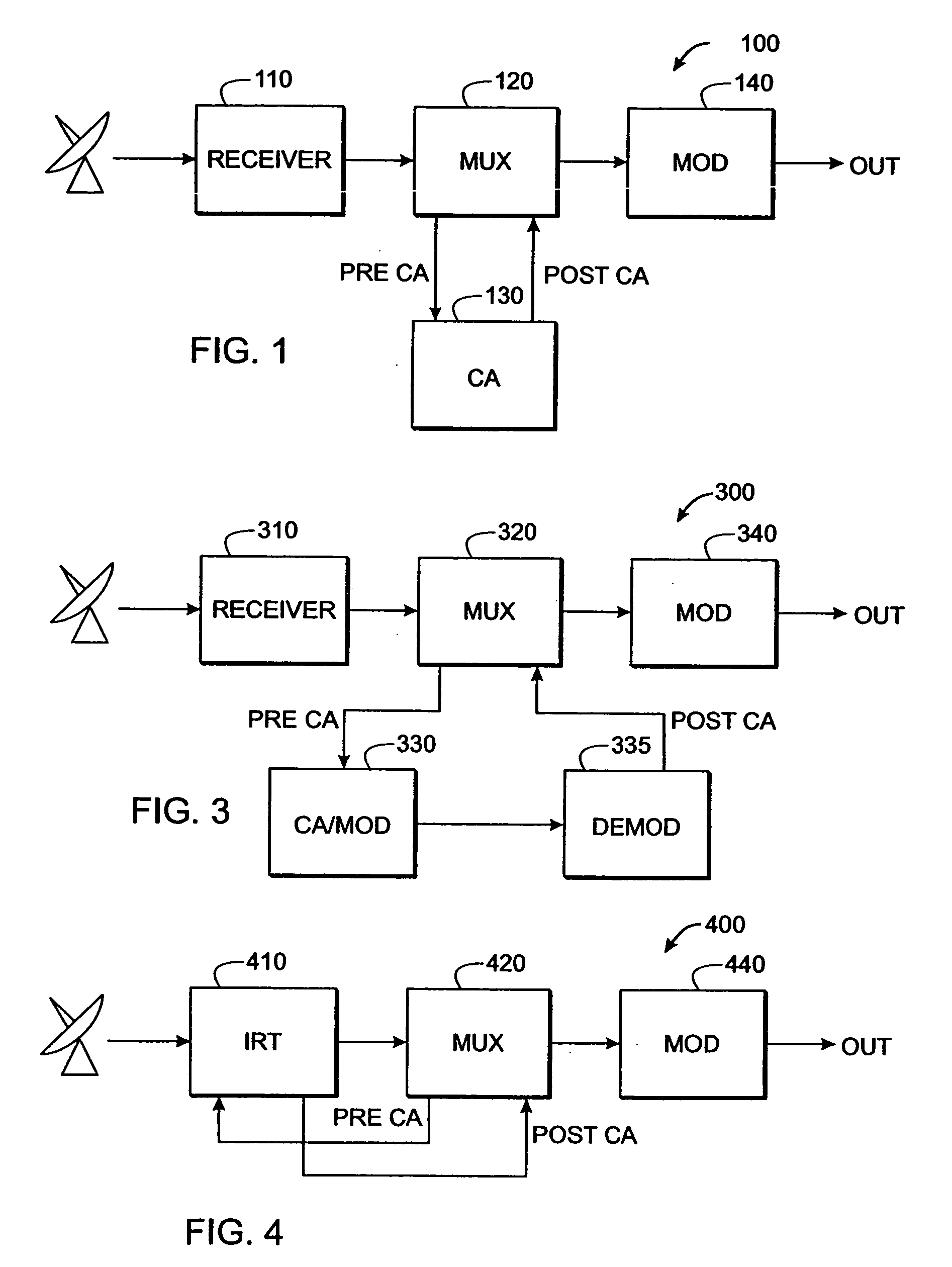
Time-multiplexed multi-program encryption system
ActiveUS20050180568A1Increase the number ofImprove throughputPulse modulation television signal transmissionSecret communicationComputer hardwareRe sequencing
A system and method are described for greatly increasing the number of services that can be encrypted with existing conditional access equipment. The method is most useful when many digitally compressed programs are encrypted at the same time. Only the most critical components of each compressed video, audio, or data stream are selected and then sequenced into a single stream. Additional formatting causes this sequence of segments from multiple sources to appear as a single continuous stream to the conditional access system. Once this stream has been encrypted, it is demultiplexed and the components are restored and re-sequenced into their respective programs. Messages such as the Entitlement Control Messages that are inserted into the stream by the encryption system, are also adjusted and included with each of the reconstructed programs. The technique not only allows encryption systems to be designed using less encryption hardware, but also simplifies the management of encryption sessions, particularly in on-demand programming applications.
Owner:IMAGINE COMM
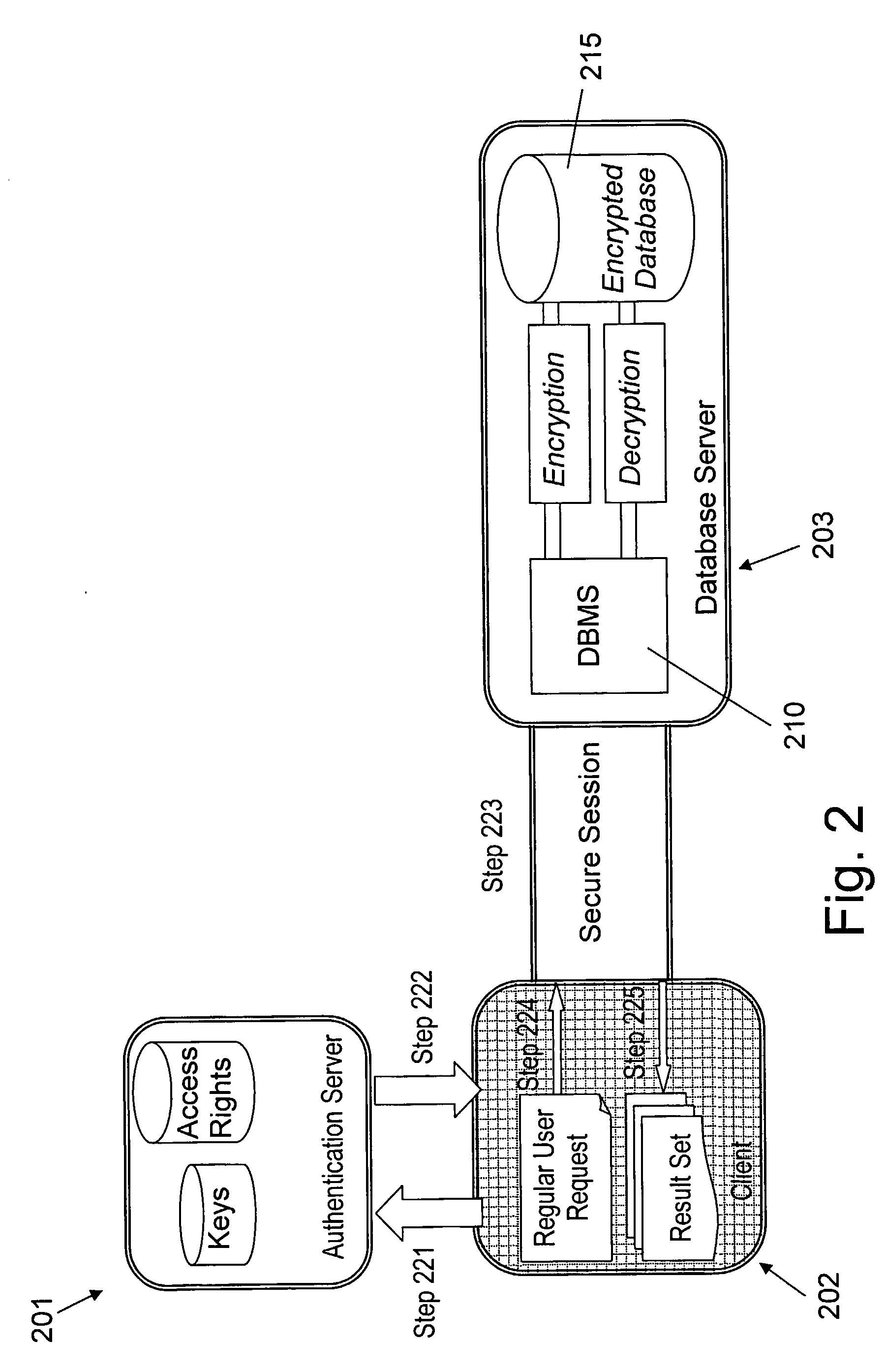
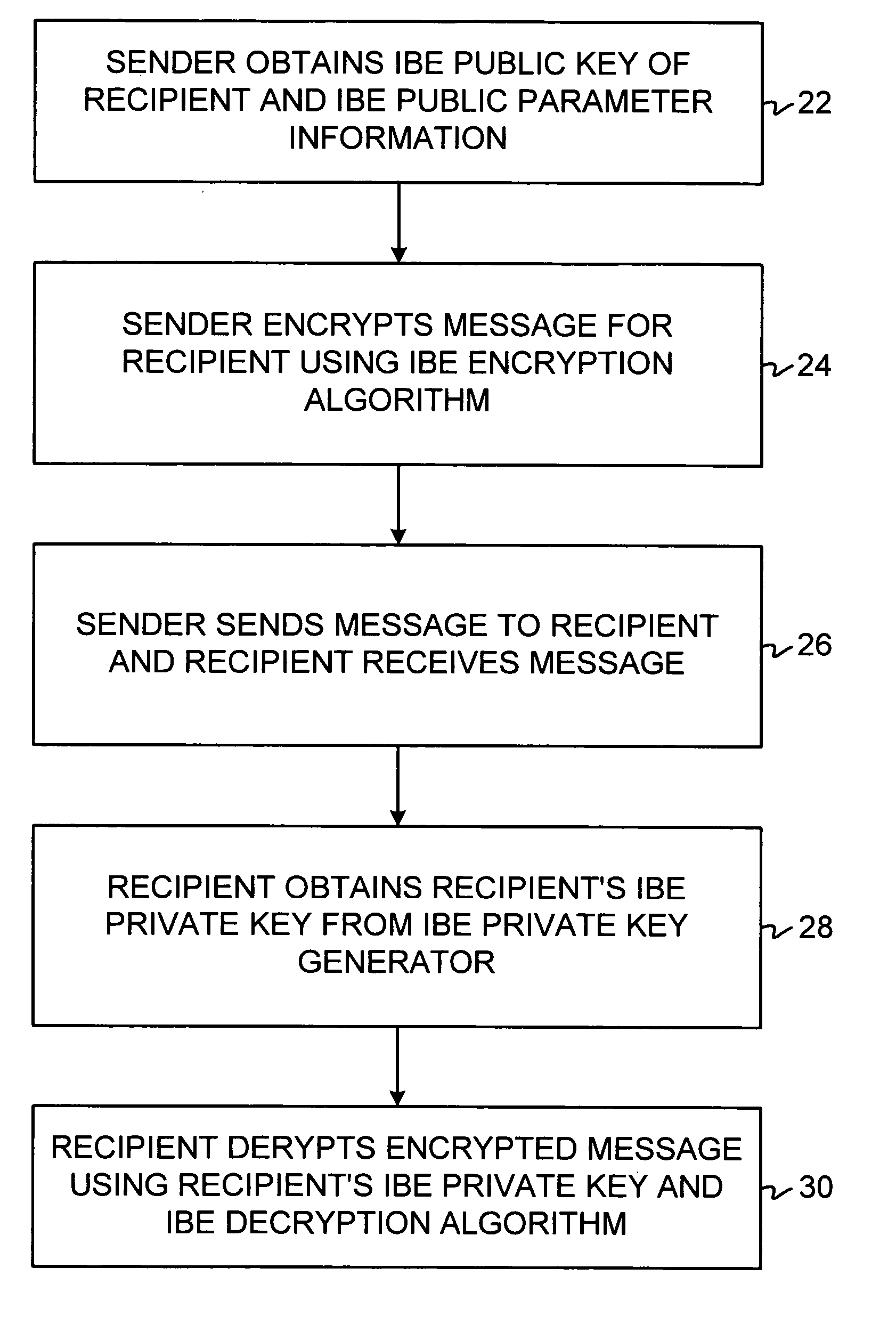
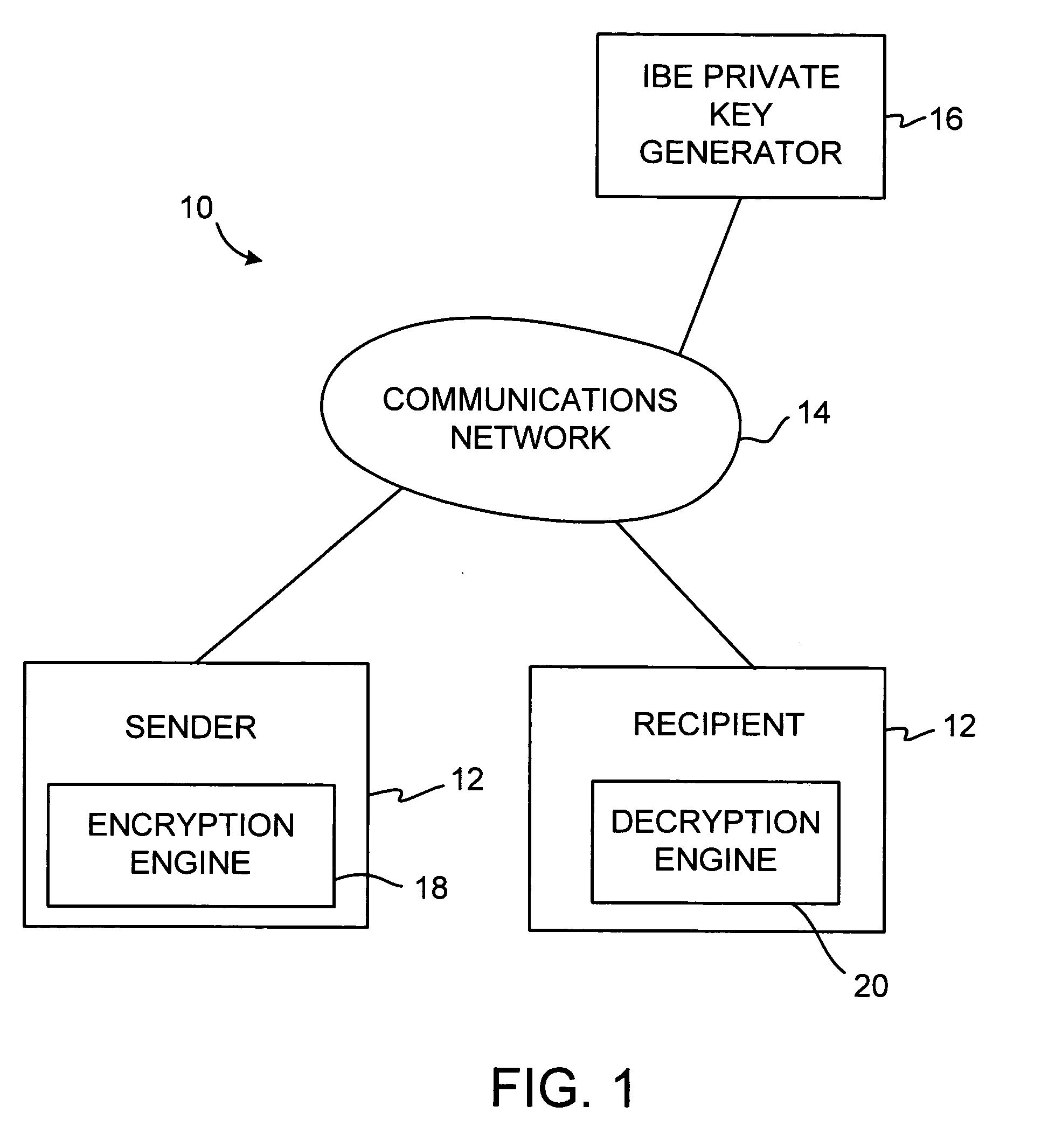
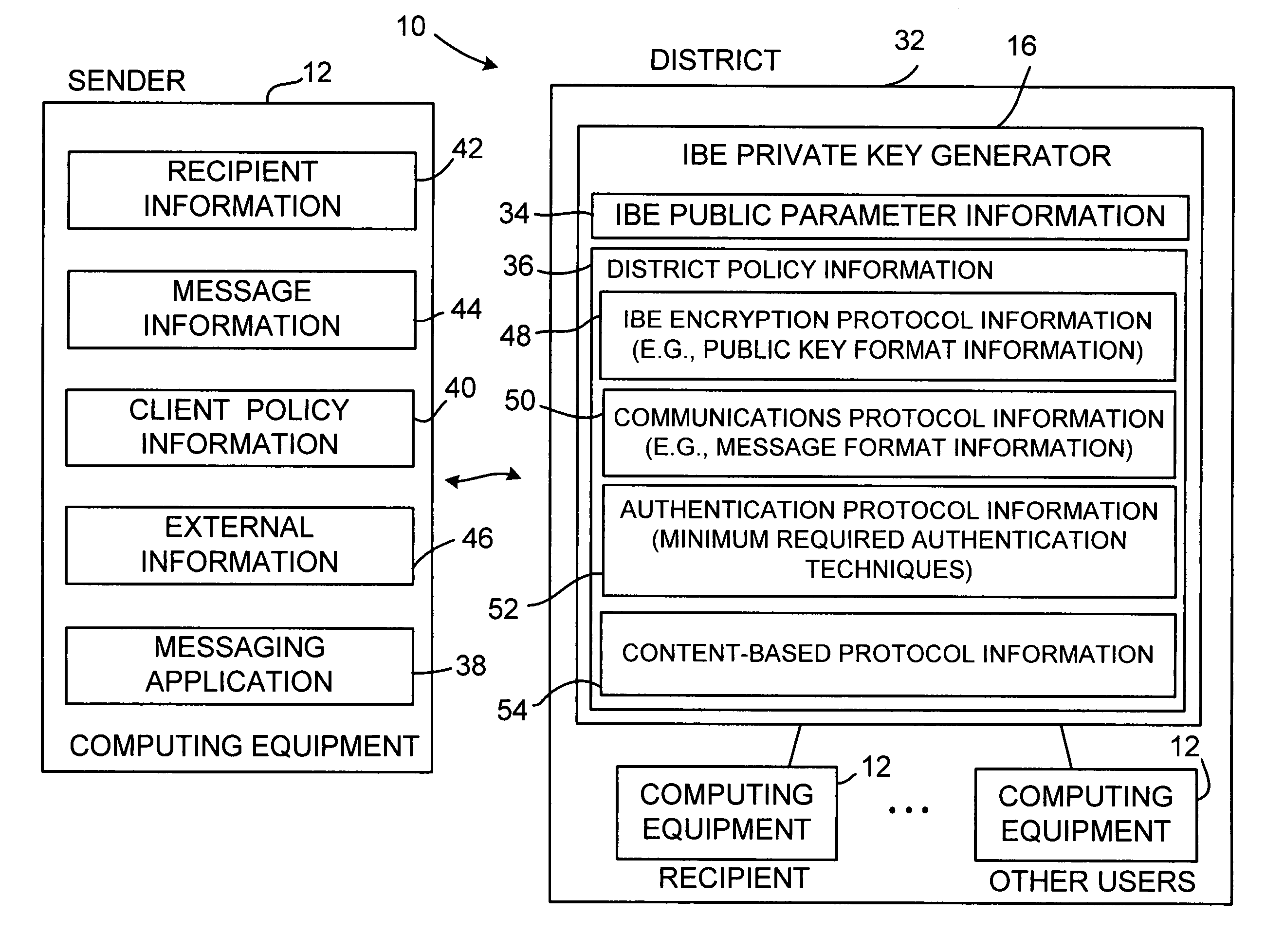
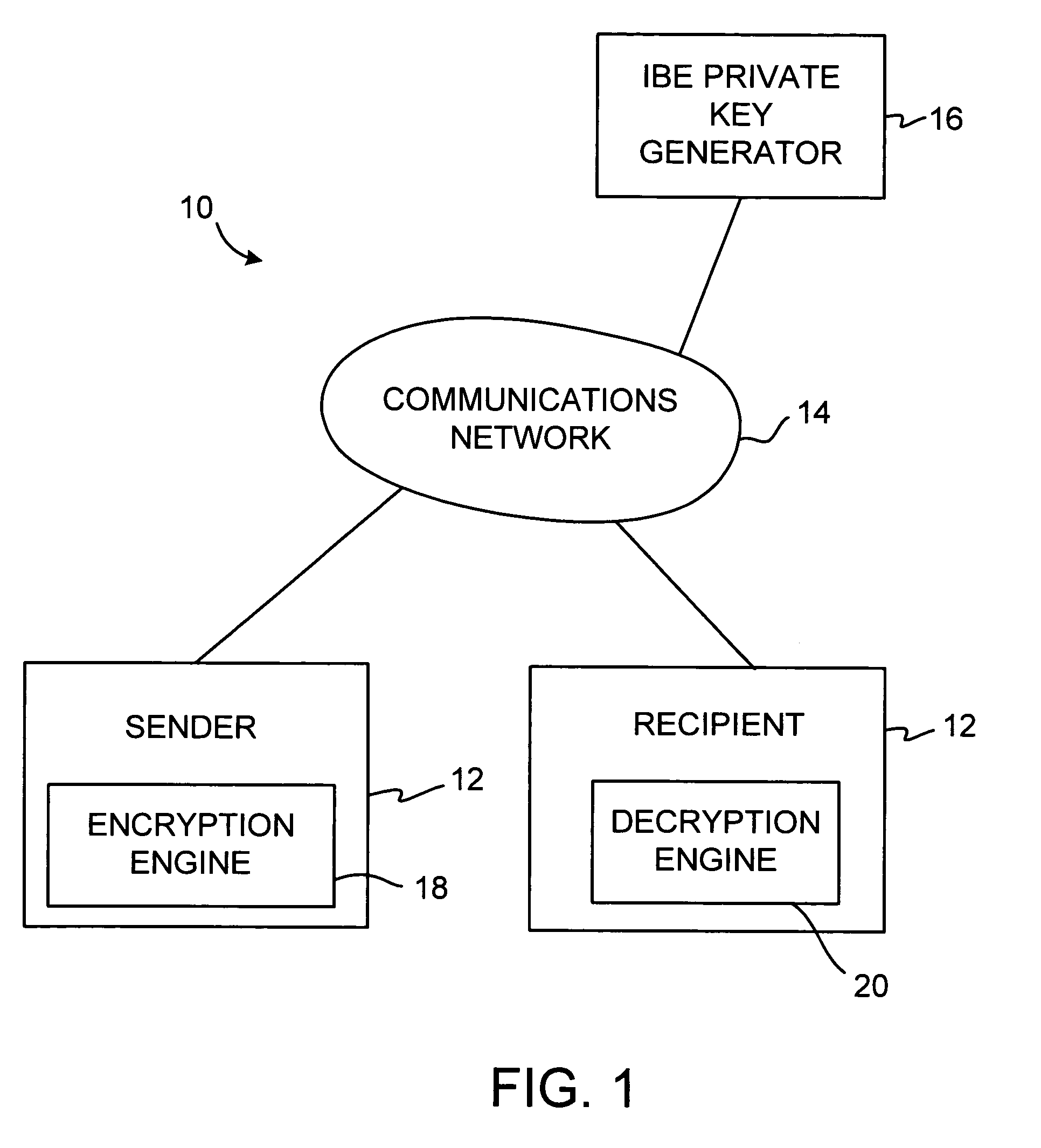
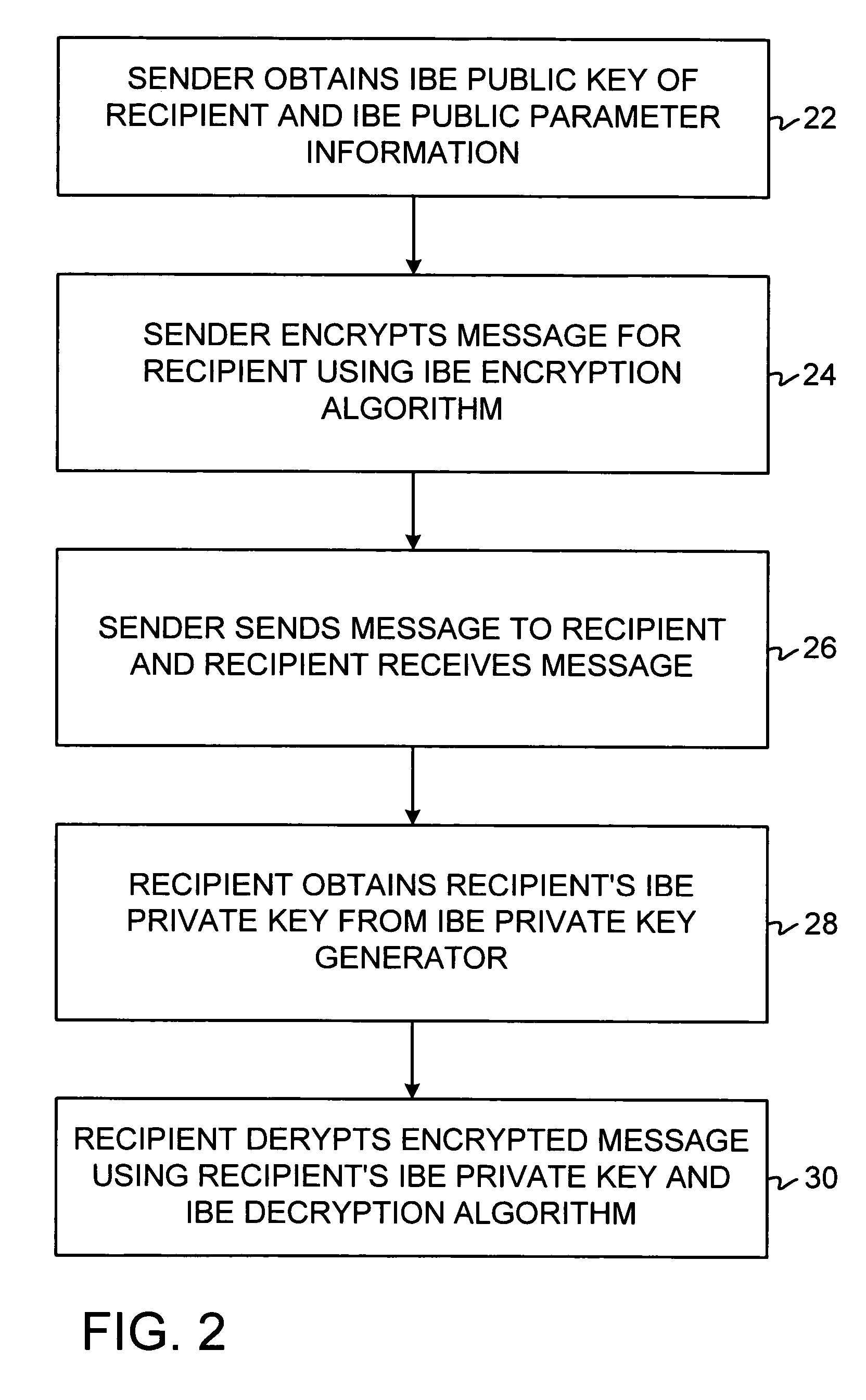
Identity-based-encryption system with district policy information
ActiveUS20050084100A1Public key for secure communicationSecret communicationNetwork Communication ProtocolsInformation security
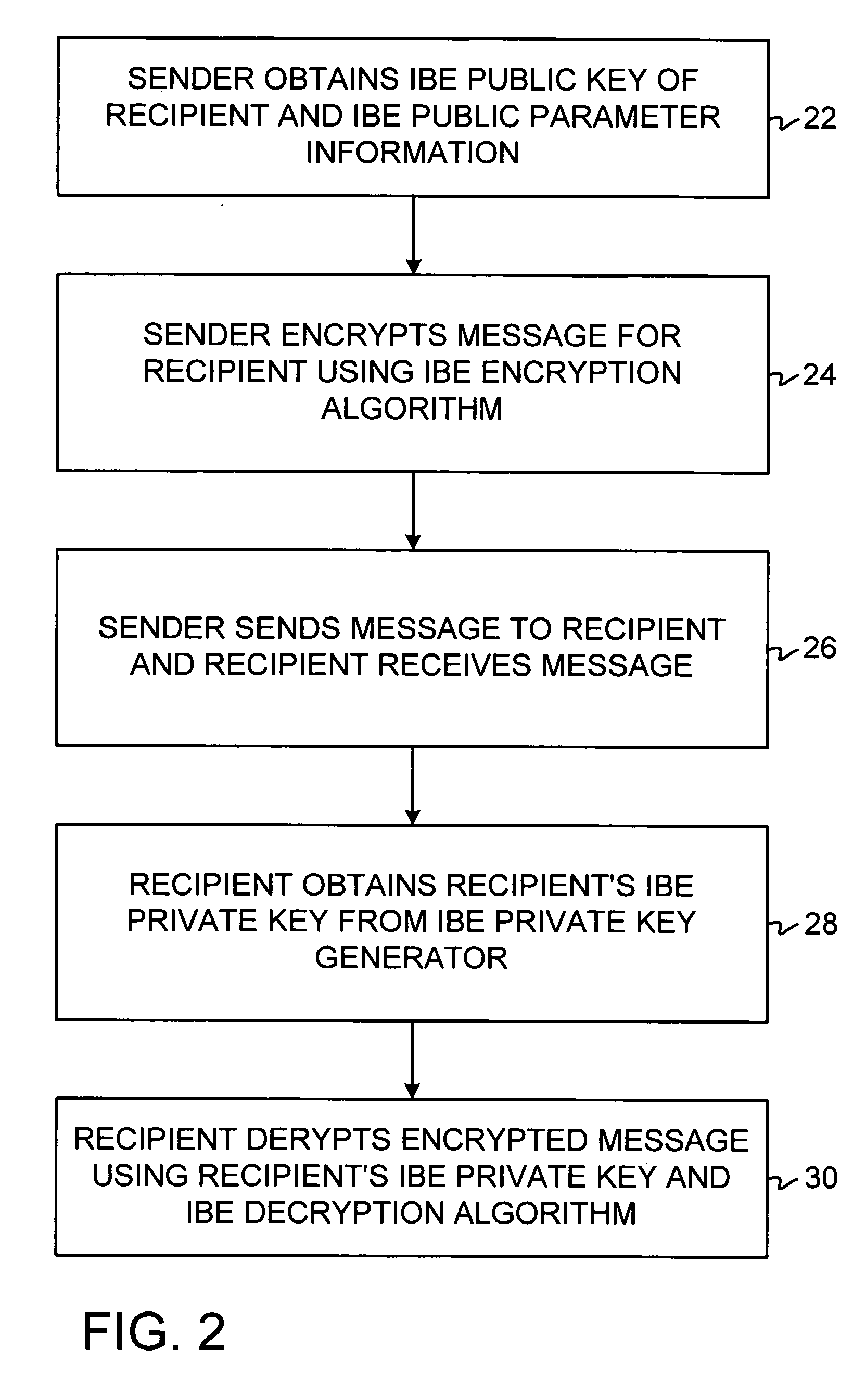
A system is provided that uses identity-based encryption (IBE) to allow a sender to securely convey information in a message to a recipient over a communications network. IBE public key information may be used to encrypt messages and corresponding IBE private key information may be used to decrypt messages. The IBE private keys may be provided to message recipients by an IBE private key generator. The IBE private key generator and the recipients who obtain their IBE private keys from that generator form a district. District policy information may be provided by the IBE private key generator that specifies which encryption and communications protocols are used by the district. The district policy information may also specify which authentication protocols are used by the district and may set forth how content-based protocols are implemented. This information may be used by senders in sending messages to recipients.
Owner:MICRO FOCUS LLC
System for verifying use of credit/identification card including recording physical attributes of unauthorized users
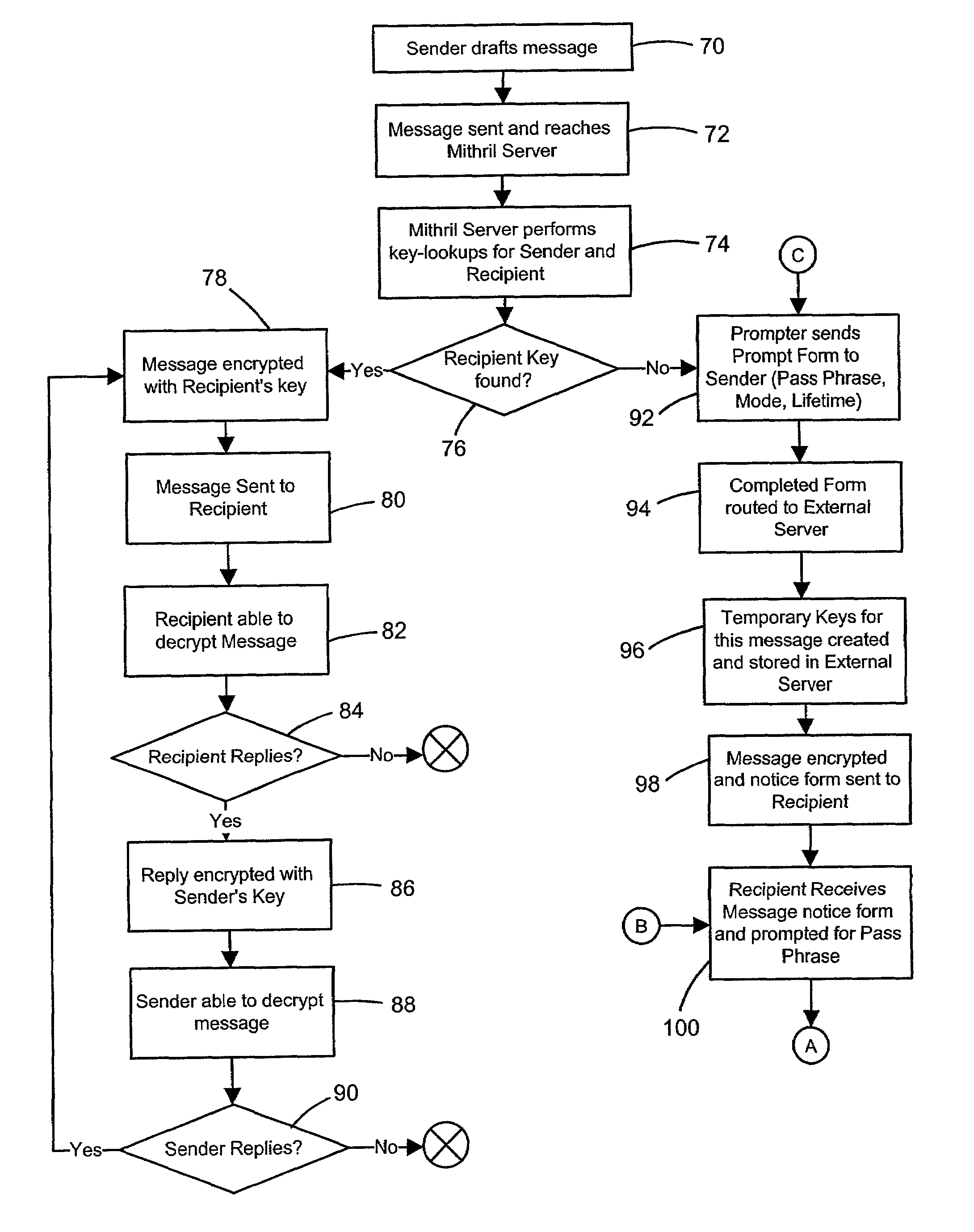
InactiveUSRE36580E1Reduce usageElectric signal transmission systemsImage analysisCredit cardComputer hardware
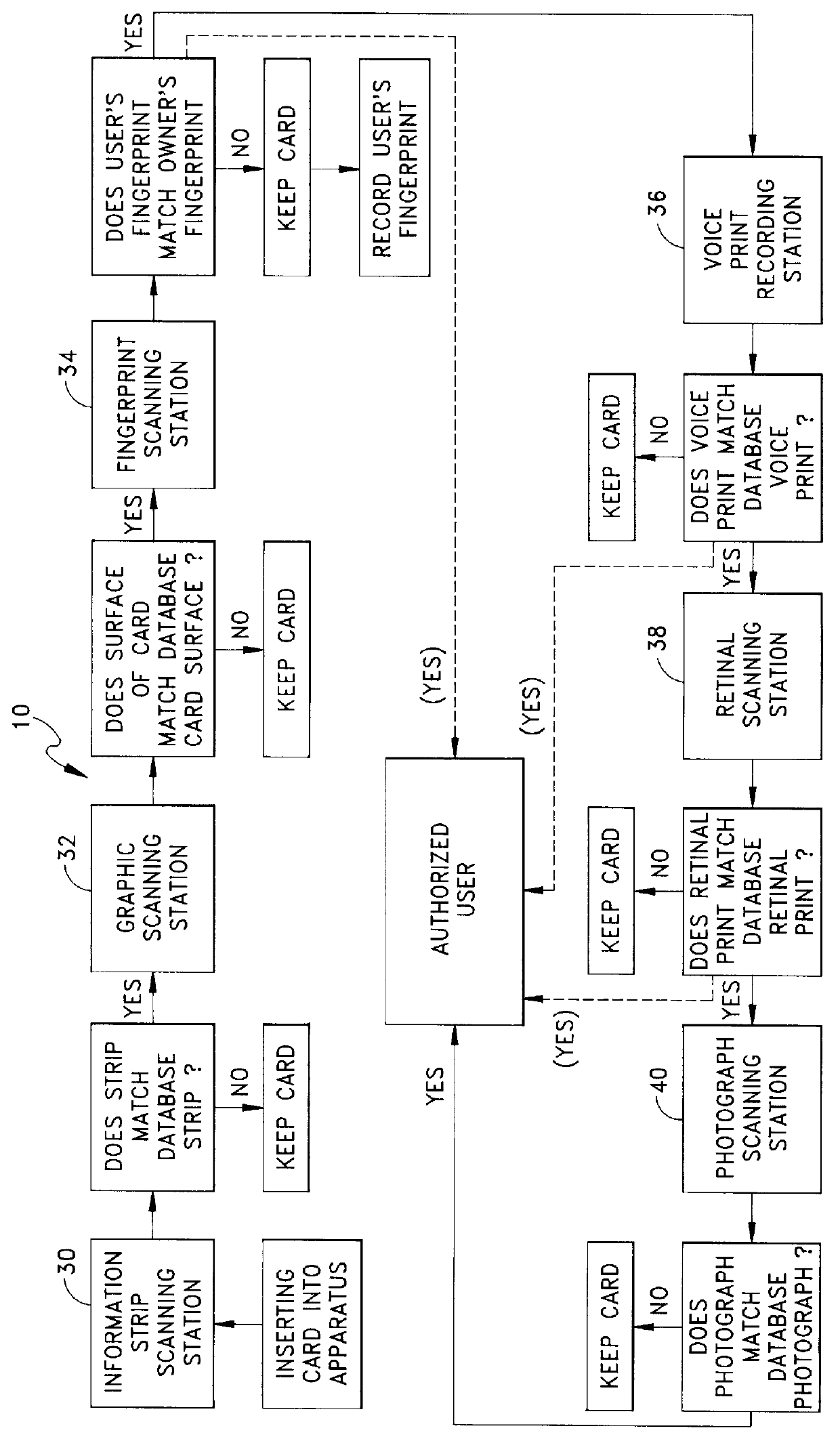
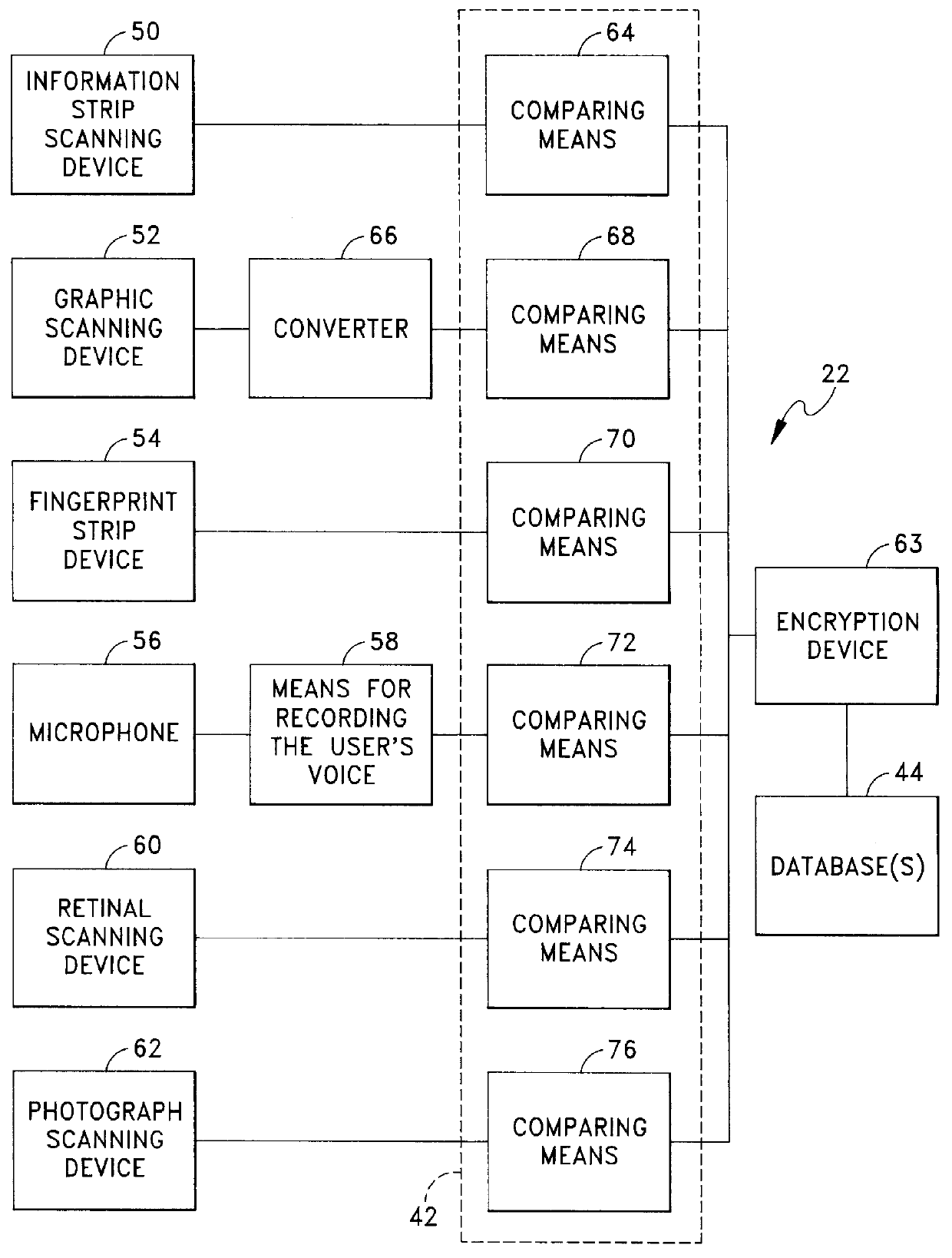
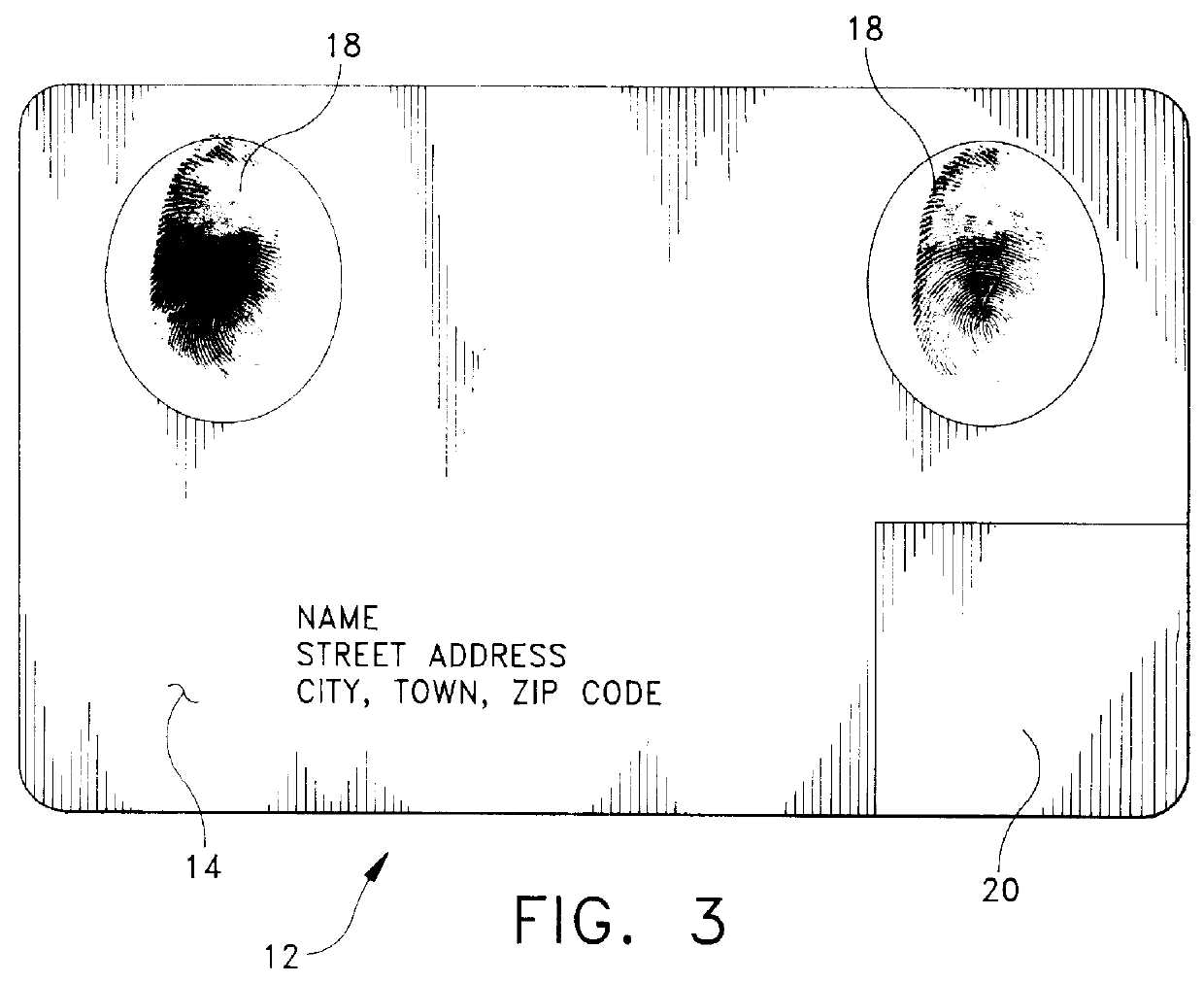
The present invention is directed to a method and apparatus for verifying an authorized user of a credit / identification card. The method includes the steps of scanning the card with an apparatus having a plurality of scanning devices for scanning a bar code, scanning the card for evidence of tampering, scanning at least one fingerprint on the card, and any other detectable information, and comparing the scanned information on the card to information of the owner stored on at least one accessible database in communication with the apparatus. Data transmissions between the apparatus and databases are protected by an encryption system. If the information on the card does not match the information germane to the owner of the card which is stored in the database, the card is withheld from the user. Otherwise, the user of the card is free to use it for a desired purpose.
Owner:WIZARDS
System and method of hiding cryptographic private keys
ActiveUS20050002532A1Key distribution for secure communicationPublic key for secure communicationComputer hardwareEnd user
The invention relates to a system and method of hiding cryptographic private keys. While public / private key encryption systems are considered to be secure, the private keys ultimately must be stored in some location—in fact, in some digital commerce systems the private key is sent to the end user as part of an executable file such as an audio player and audio file. Thus, attackers can obtain access to the private key. The broad concept of the invention is to split the private key up into parts which are obfuscated, but still kept in a form that allows the encrypted data to be decrypted. One technique for obfuscating the private key uses modulo arithmetic.
Owner:IRDETO ACCESS
Selective encryption system and method for I/O operations
InactiveUS7428636B1Unauthorized memory use protectionHardware monitoringComputer hardwareVirtual machine
Upon occurrence of a trigger condition, writes of allocation units of data (including code) to a device, such as writes of blocks to a disk, are first encrypted. Each allocation unit is preferably a predetermined integral multiple number of minimum I / O units. A data structure is marked to indicate which units are encrypted. Upon reads from the device, only those allocation units marked as encrypted are decrypted. The disk protected by selective encryption is preferably the virtual disk of a virtual machine (VM). The trigger condition is preferably either that the virtual disk has been initialized or that the VM has been powered on. Mechanisms are also provided for selectively declassifying (storing in unencrypted form) already-encrypted, stored data, and for determining which data units represent public, general-use data units that do not need to be encrypted. The “encrypt-on-write” feature of the invention may be used in conjunction with a “copy-on-write” technique.
Owner:VMWARE INC
Cryptographic apparatus and method
InactiveUS7177424B1Quick implementationEasy to operateEncryption apparatus with shift registers/memoriesUnauthorized memory use protectionPlaintextComputer hardware
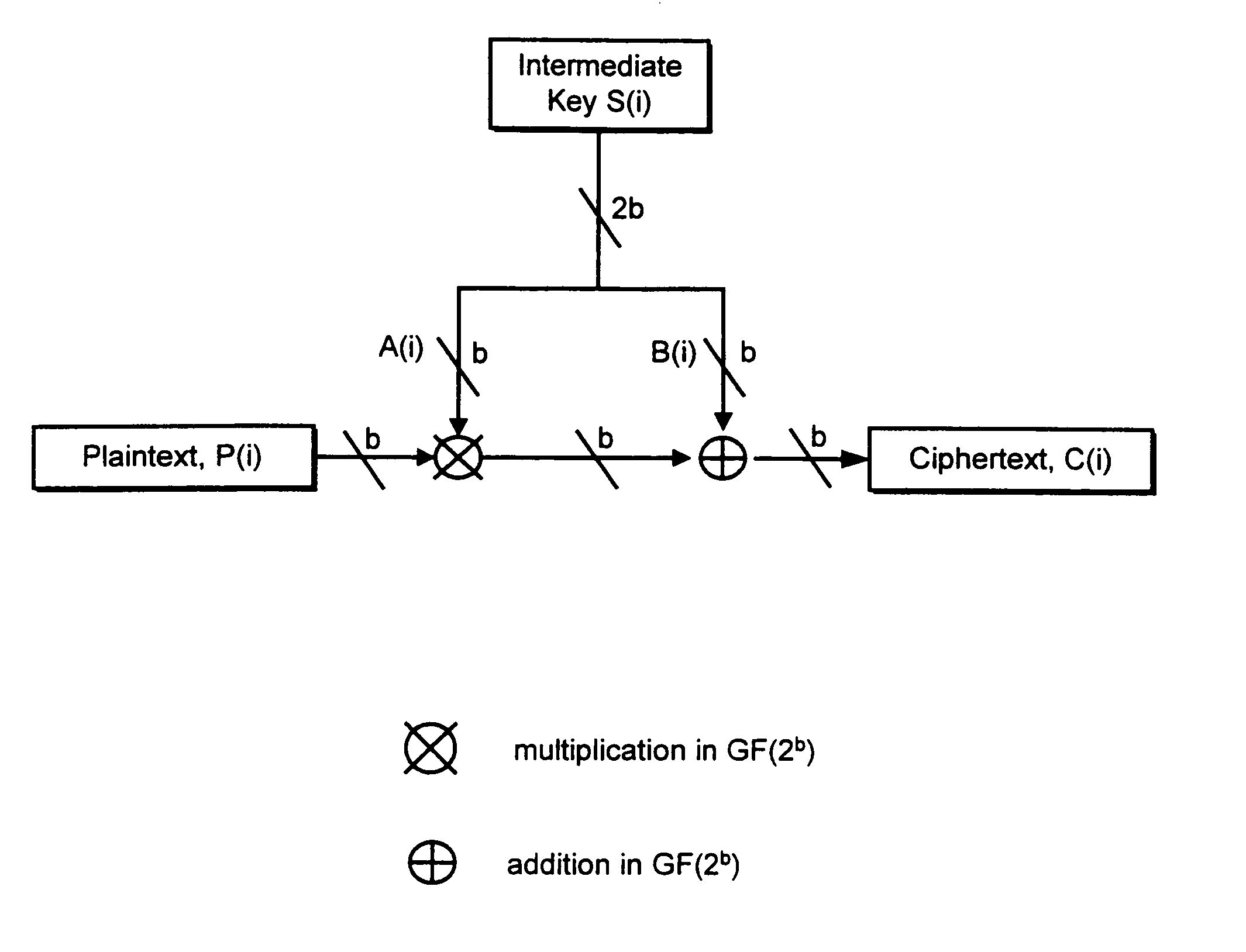
An encryption system comprises a pseudo-random number generator (KS) for generating a long pseudo-random sequence (S) from a shorter encryption key (K) and, if necessary, a nonce value (N), and a mixing function (MX) for combining the sequence with a plaintext message (P) on a block-by-block basis, where successive blocks (S(i)) of 128 bits of the sequence are combined with successive 64-bit blocks of plaintext (P(i)) to produce successive 64-bit blocks of ciphertext. The blockwise use of a long pseudo-random sequence preserves the advantages of a block cipher in terms of data confidentiality and data integrity, as well as benefiting from the speed advantages of a stream cipher.
Owner:HITACHI LTD
Utilizing data reduction in steganographic and cryptographic systems
InactiveUS20070064940A1Improve securitySafe formMultiple keys/algorithms usageTelevision systemsData signalComputer science
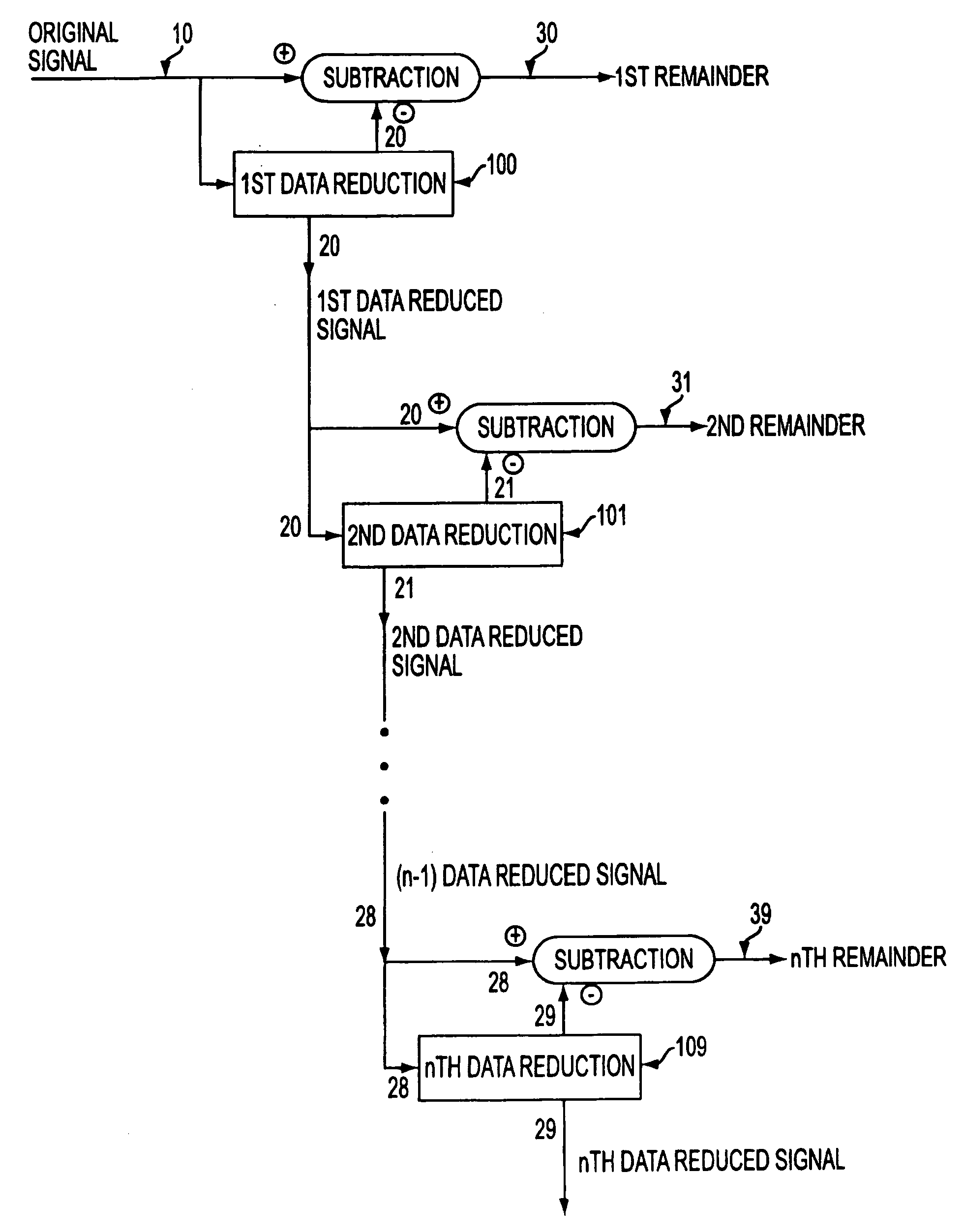
The present invention relates to methods for protecting a data signal using the following techniques: applying a data reduction technique to reduce the data signal into a reduced data signal; subtracting the reduced data signal from the data signal to produce a remainder signal; embedding a first watermark into the reduced data signal to produce a watermarked, reduced data signal; and adding the watermarked, reduced data signal to the remainder signal to produce an output signal. A second watermark may be embedded into the remainder signal before the final addition step. Further, cryptographic techniques may be used to encrypt the reduced data signals and to encrypt the remainder signals before the final addition step. The present invention also relates to a system for securing a data signal including: computer devices for applying a data reduction technique to reduce the data signal into a reduced data signal; means to subtract the reduced data signal from the data signal to produce a remainder signal; means to apply a first cryptographic technique to encrypt the reduced data signal to produce an encrypted, reduced data signal; means to apply a second cryptographic technique to encrypt the remainder signal to produce an encrypted remainder signal; and means to add the encrypted, reduced data signal to the encrypted remainder signal to produce an output signal.
Owner:WISTARIA TRADING INC
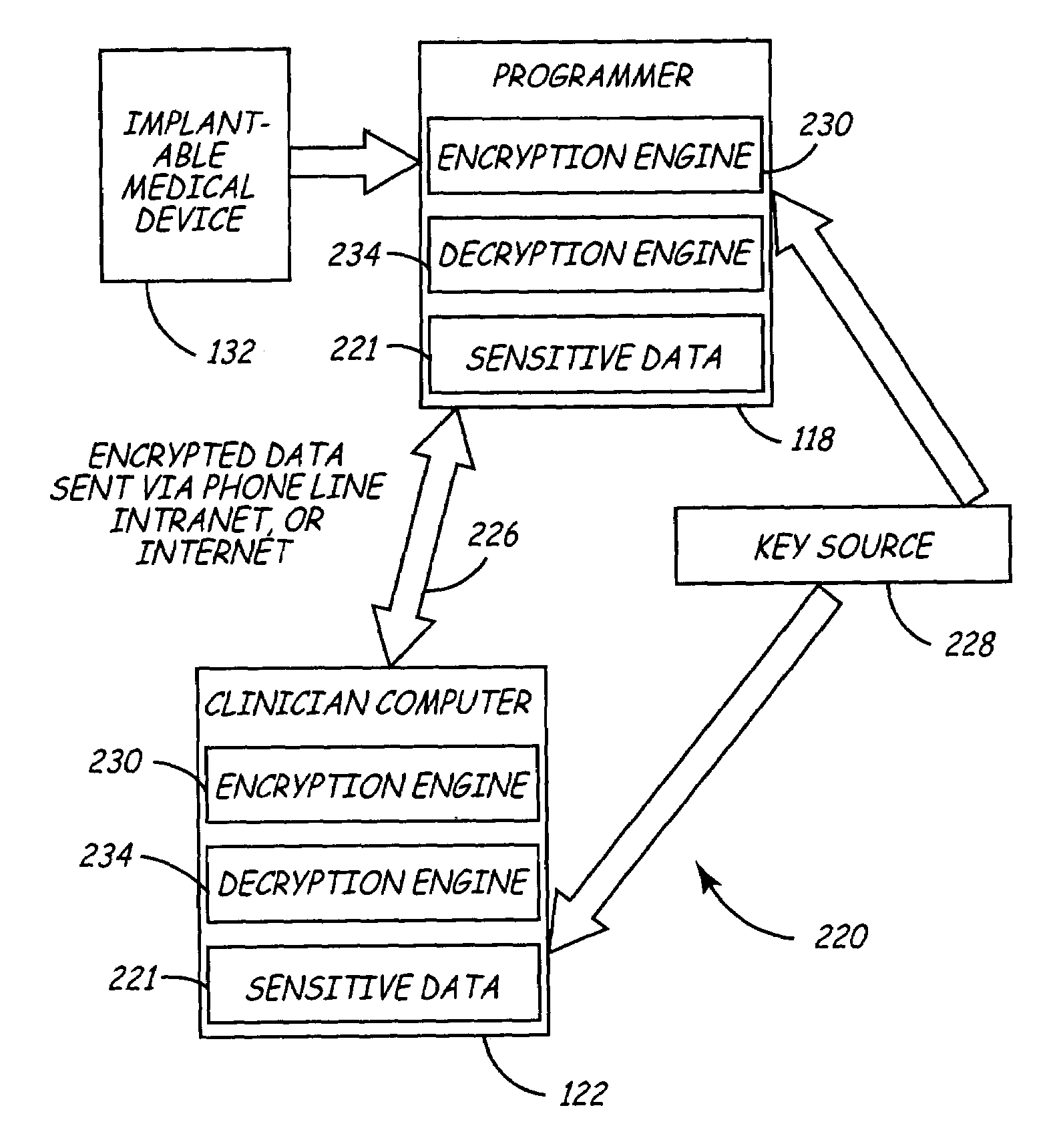
Variable encryption scheme for data transfer between medical devices and related data management systems
InactiveUS7027872B2Ensure authenticityEnsure integrityElectrotherapyData processing applicationsData centerData management
Owner:MEDTRONIC INC
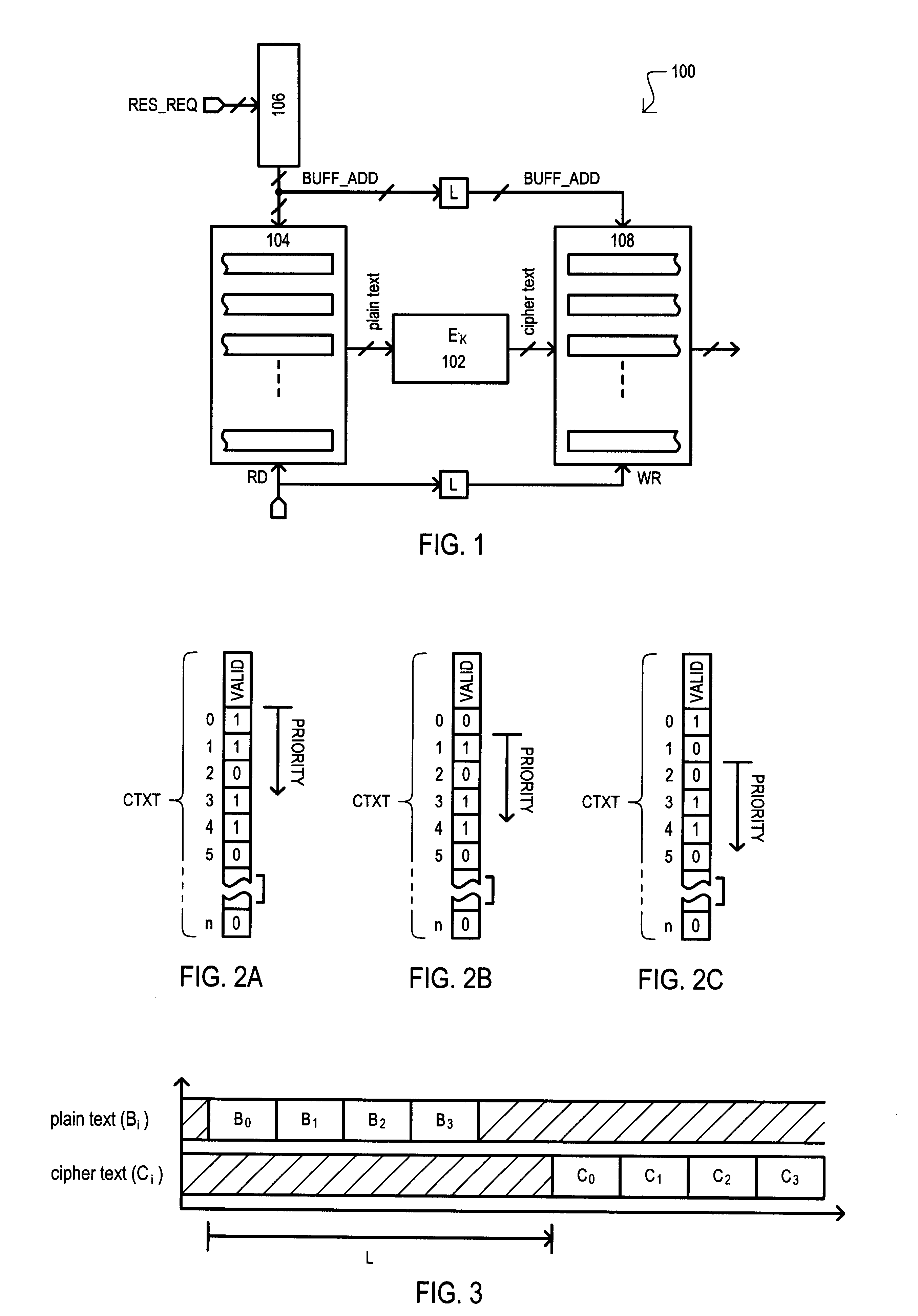
High throughput system for encryption and other data operations
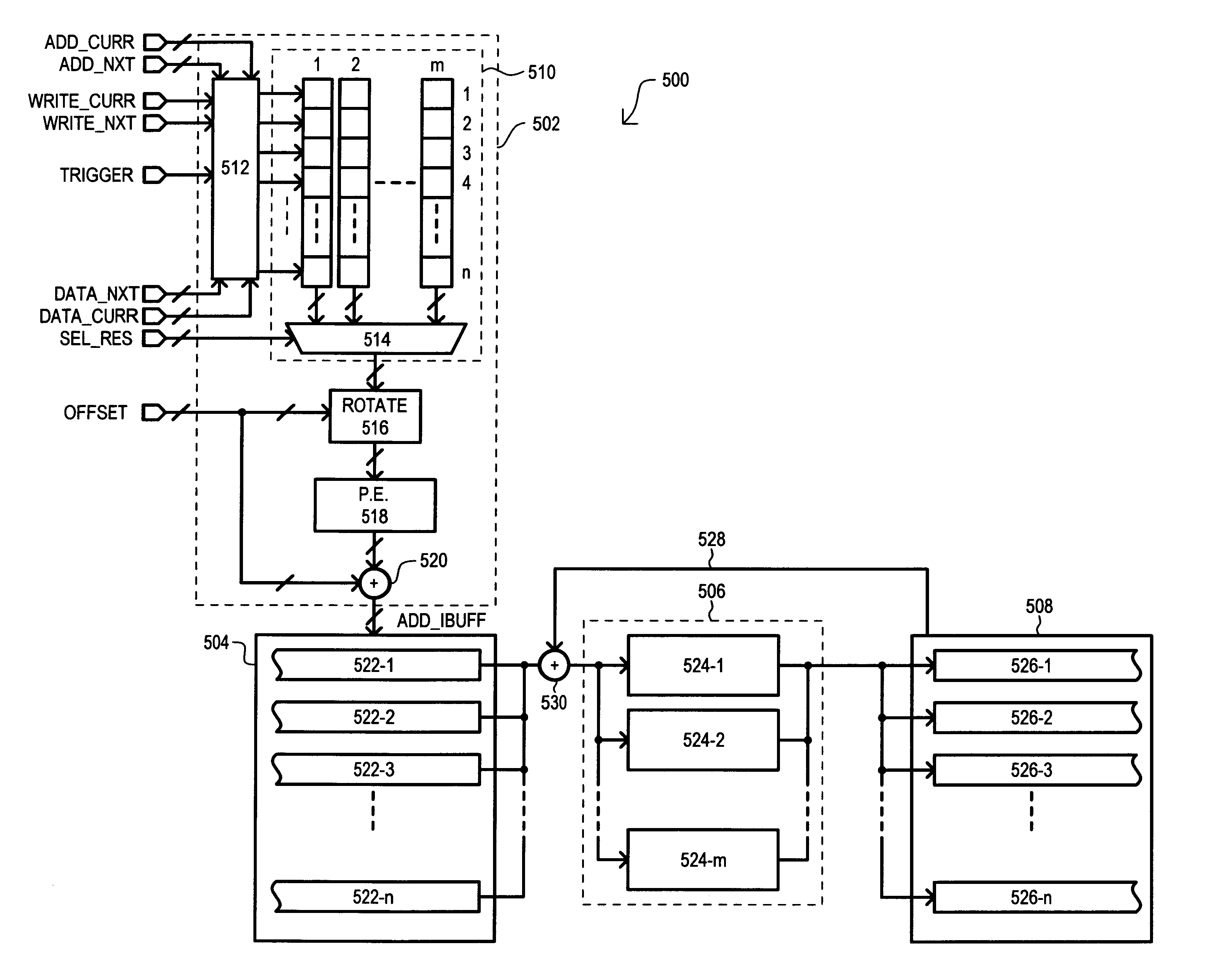
InactiveUS6870929B1Encryption apparatus with shift registers/memoriesPublic key for secure communicationMultiplexerData operations
According to one embodiment, an encryption system (500) includes an input buffer (504) that can provide data blocks from different contexts (522-1 to 522-n) to a selected encryption circuit (524-1 to 524-m) according to a scheduling section (502). A scheduling section (502) can include a register array (510) having rows that each correspond to a context and columns that correspond to an encryption circuit. Each register array (510) row can store one “hot” bit that designates a context with a particular encryption circuit. A column can be selected by a multiplexer (514) and its values prioritized and encoded by a priority encoder (518) to generate an address that results in the selection of a data block from a particular context. Priority may be varied by shifting a column value with a rotate circuit (516) according to an offset value (OFFSET).
Owner:JUMIPER NETWORKS INC
End-to-end encryption method and system for emails
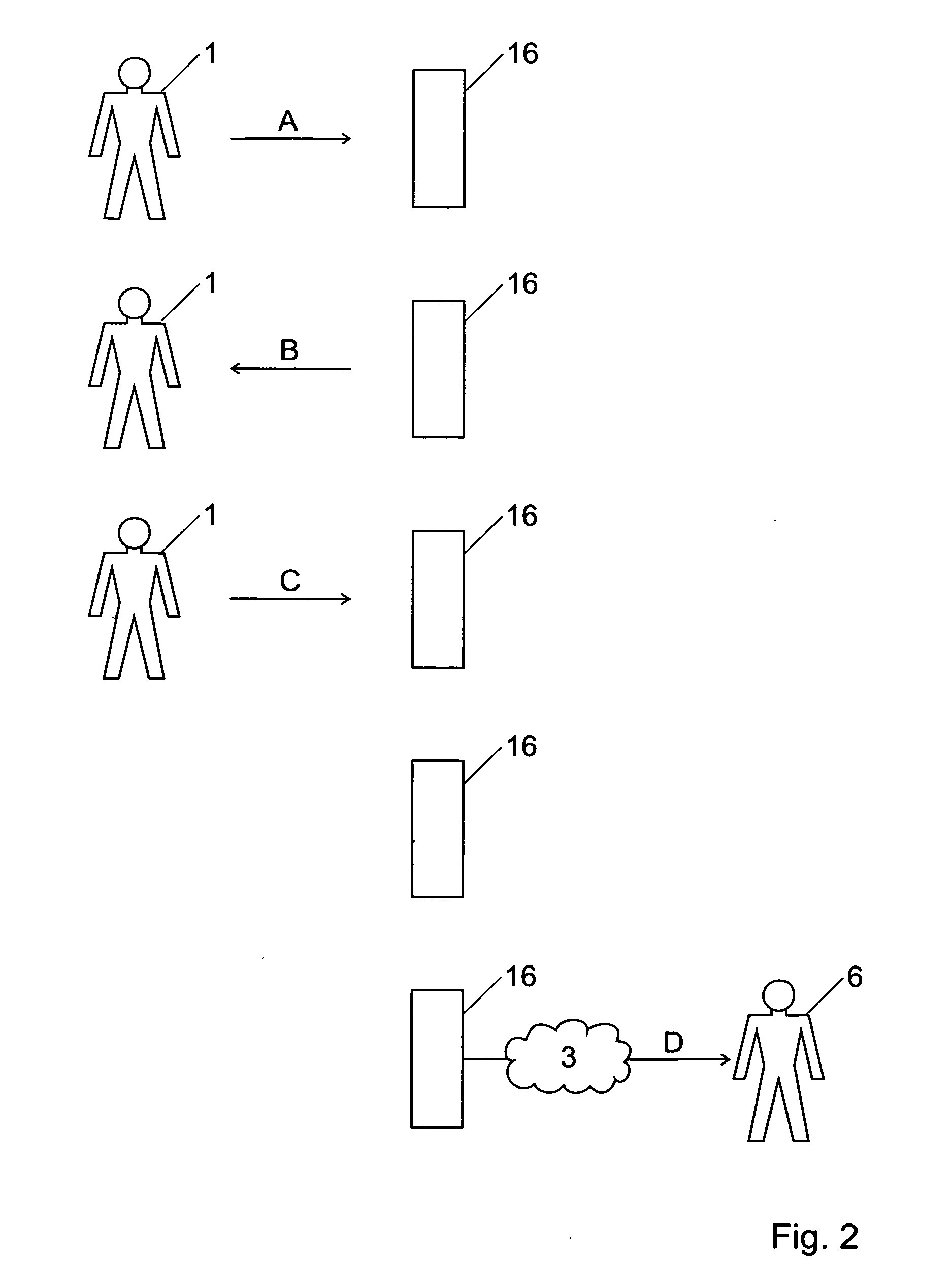
ActiveUS20050114652A1Easy to installControl lossData switching networksSecuring communicationEnd-to-end encryptionInternet privacy
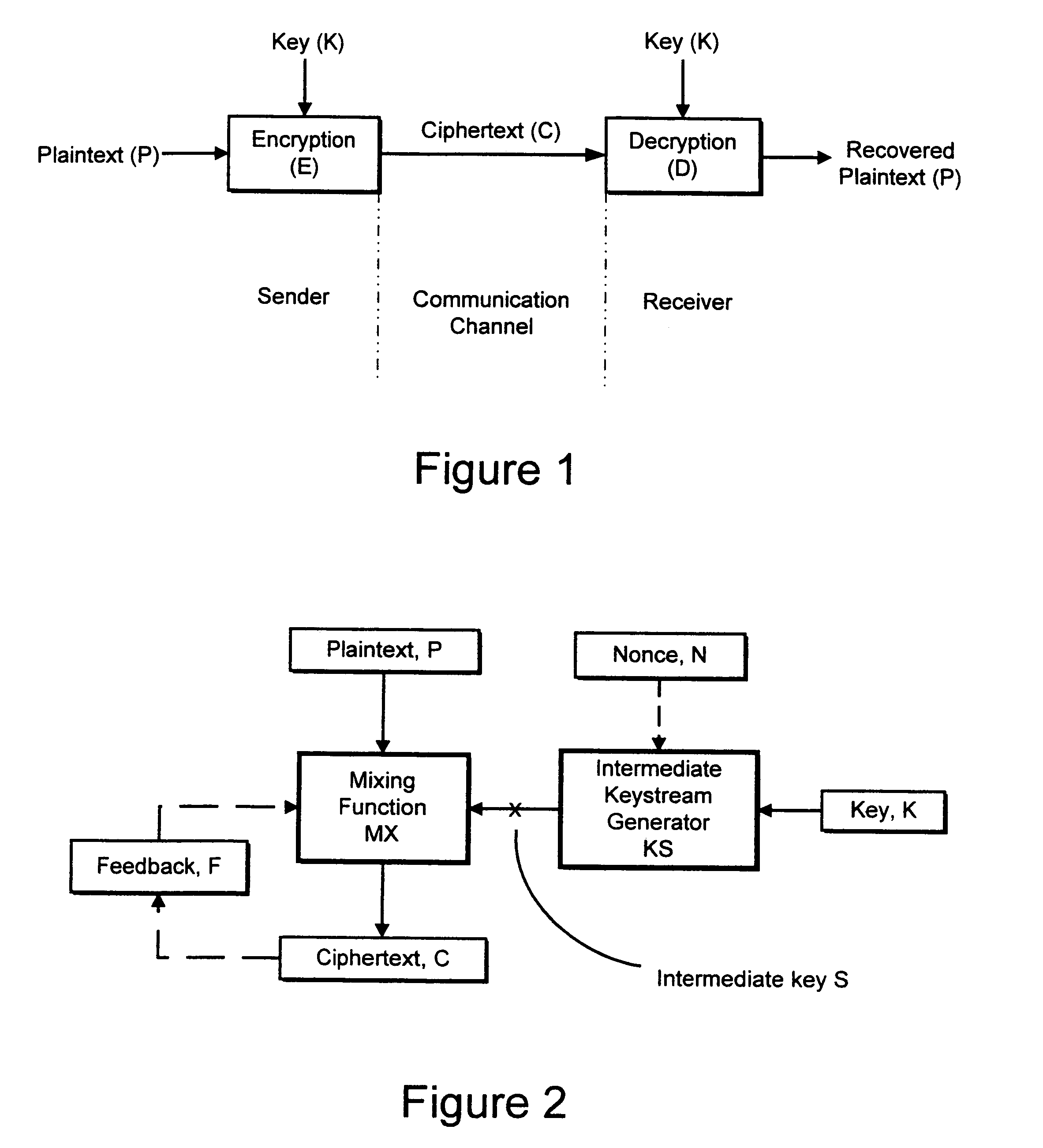
End-to-end encryption method for emails sent from a sender (1) to a recipient (6), comprising the following steps: [0001]the sender requests from an encryption system (16) a certificate corresponding to said recipient (6), [0002]the encryption system (16) returns to said sender (11) a first, proforma certificate corresponding to said recipient (6), [0003]the sender (1) sends with his email client (11) an outgoing email to said recipient encrypted with said proforma certificate, [0004]said email is forwarded through said encryption system (16), [0005]said encryption system (16) decrypts said email using a private key corresponding to said certificate, [0006]said encryption system makes the content of said email available to said recipient (6).
Owner:TOTEMO
Dynamic password update for wireless encryption system
ActiveUS20040083393A1Key distribution for secure communicationDigital data processing detailsCommunications systemPassword
A method and system for dynamically changing password-keys in a secured wireless communication system includes initiating a password key change, generating a new password key, embedding the new password key and a password key indicator in a first message, encrypting the first message using an old password key, storing the new password key, sending the formatted encrypted first message over a wireless communication system, receiving a subsequent second message, and decrypting the subsequent second message using the new password key.
Owner:AT&T MOBILITY II LLC
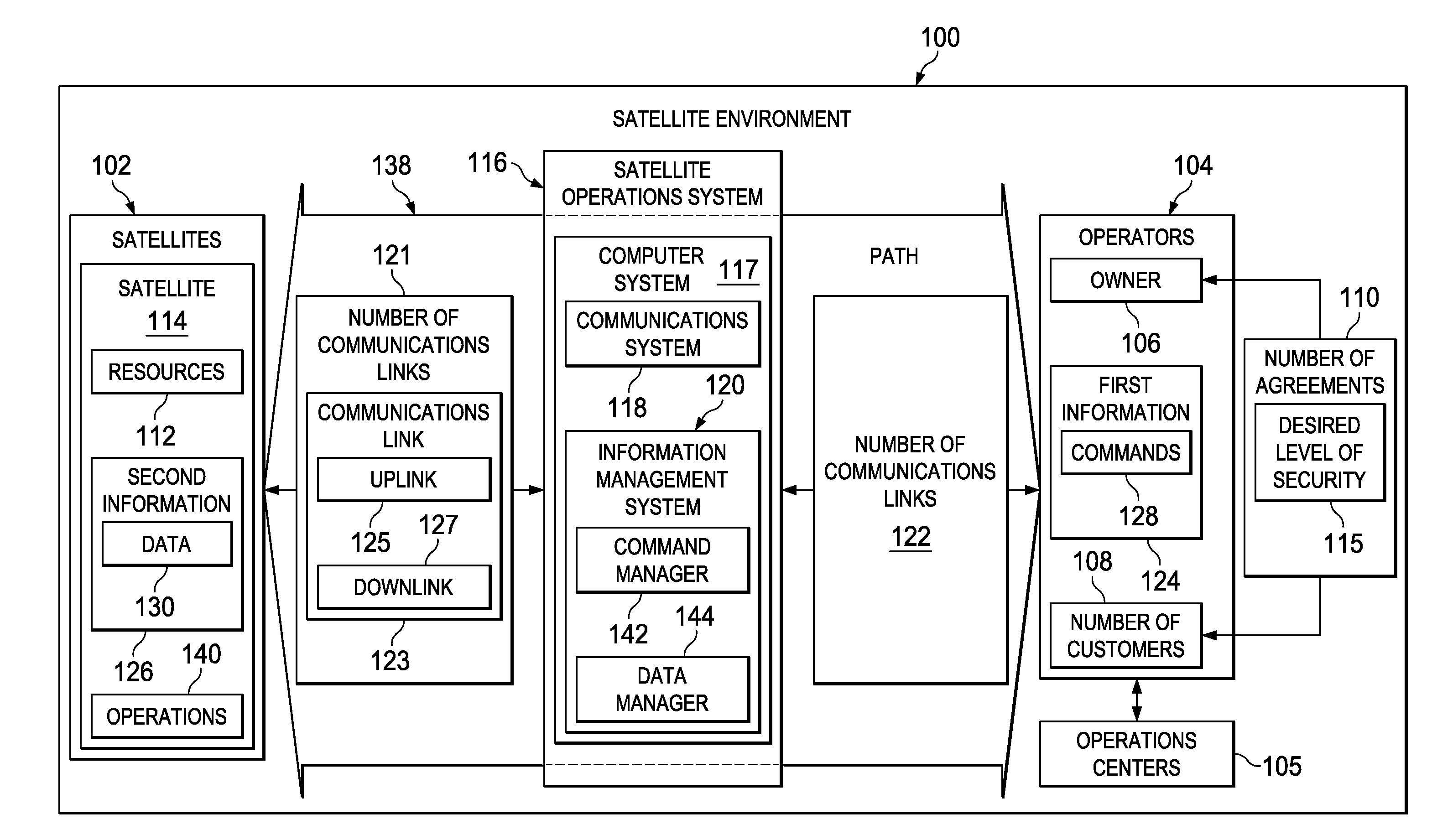
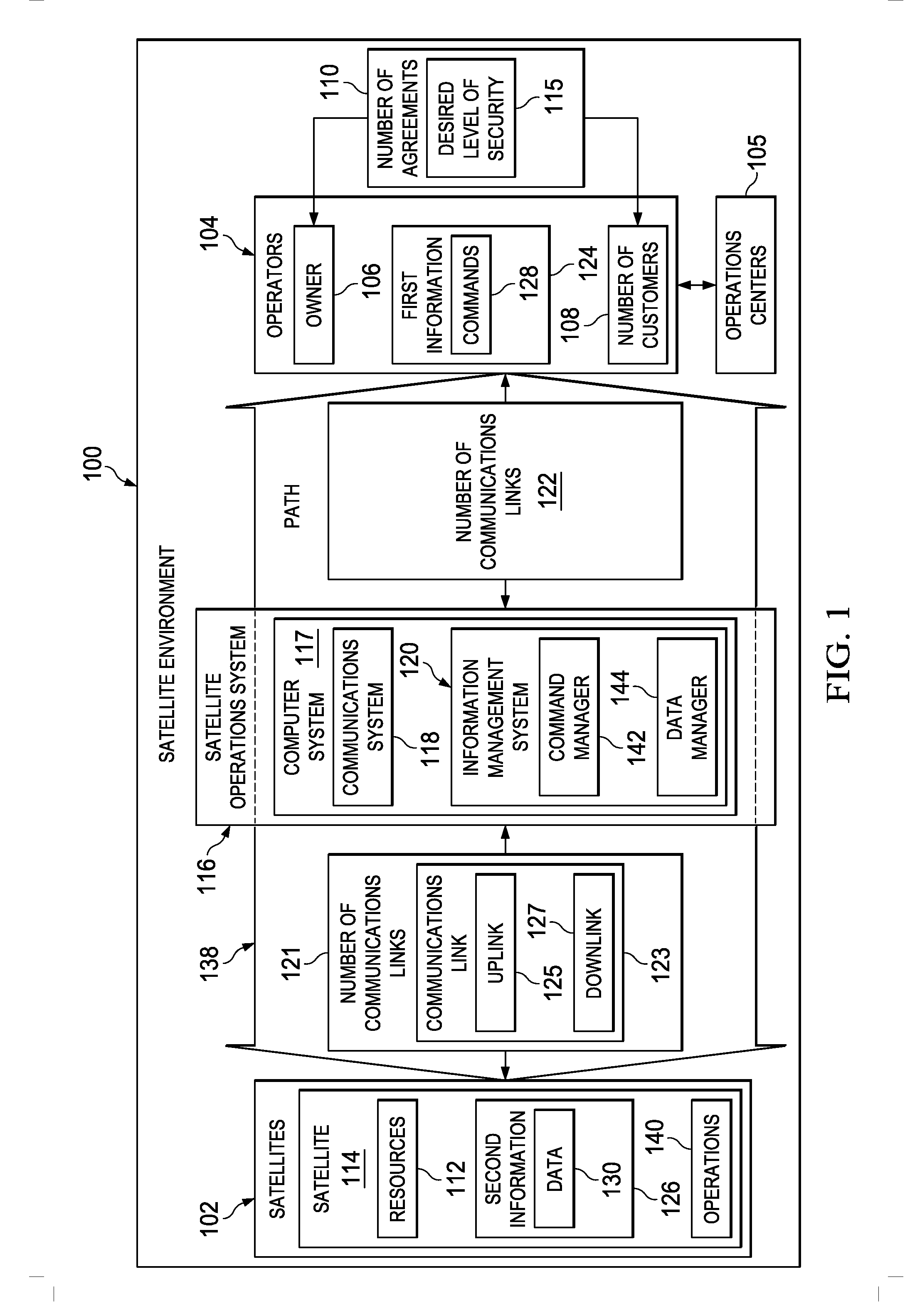
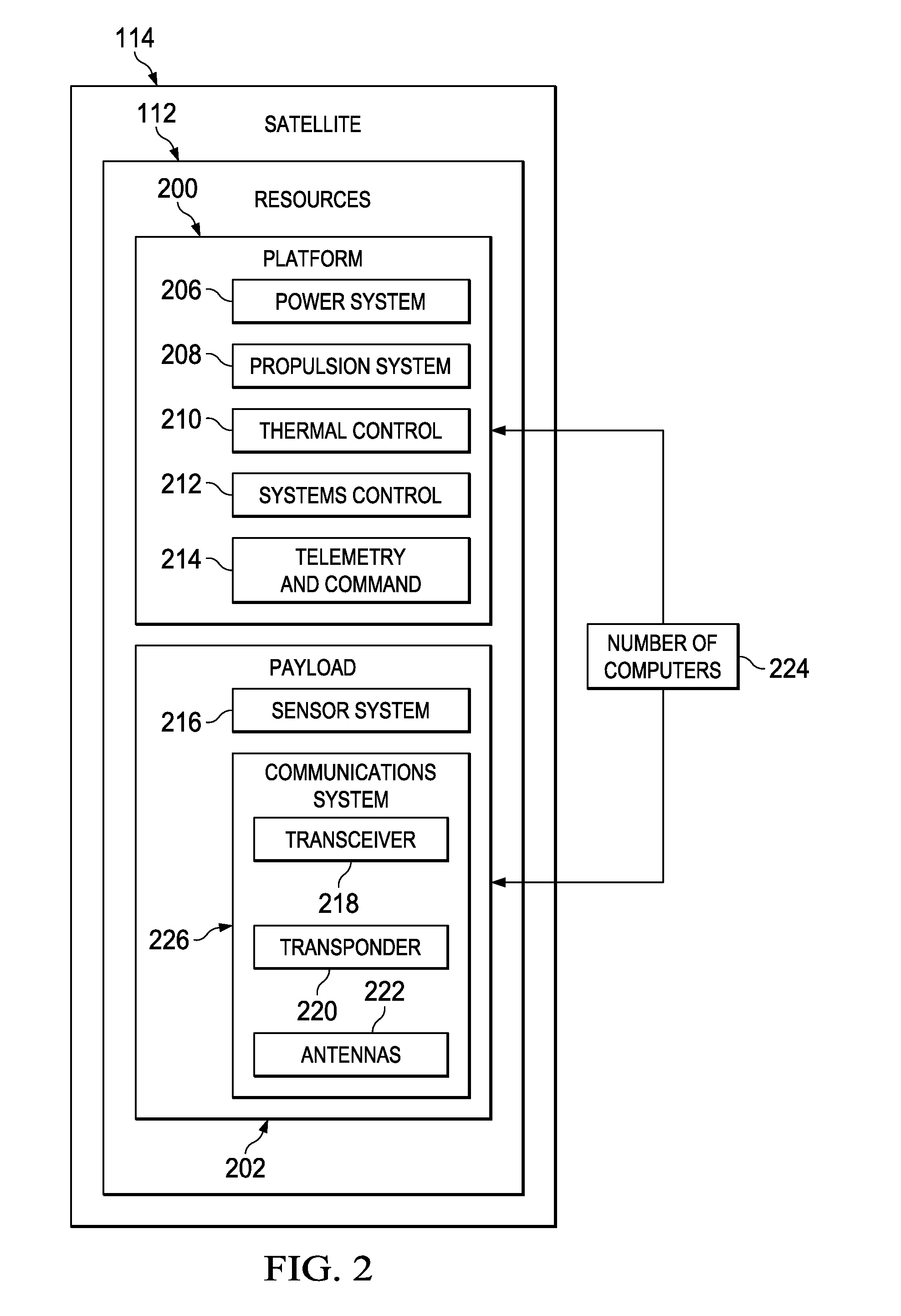
Selective Downlink Data Encryption System for Satellites
ActiveUS20130077788A1Secret communicationRadio transmissionTelecommunications linkCommunications system
A method and apparatus for a satellite system. A satellite system is comprised of a communications system in a satellite and a number of computers associated with the satellite. The communications system is configured to receive first information and transmit second information from the satellite to a remote platform over a number of communications links. The number of computers is configured to identify a block of information for encryption from instructions in the first information. The number of computers is further configured to generate a key from a portion of the block of information based on the instructions. The number of computers is further configured to perform an exclusive OR operation on the block of information using the key to form a block of encrypted information. The number of computers is further configured to transmit the block of encrypted information.
Owner:THE BOEING CO
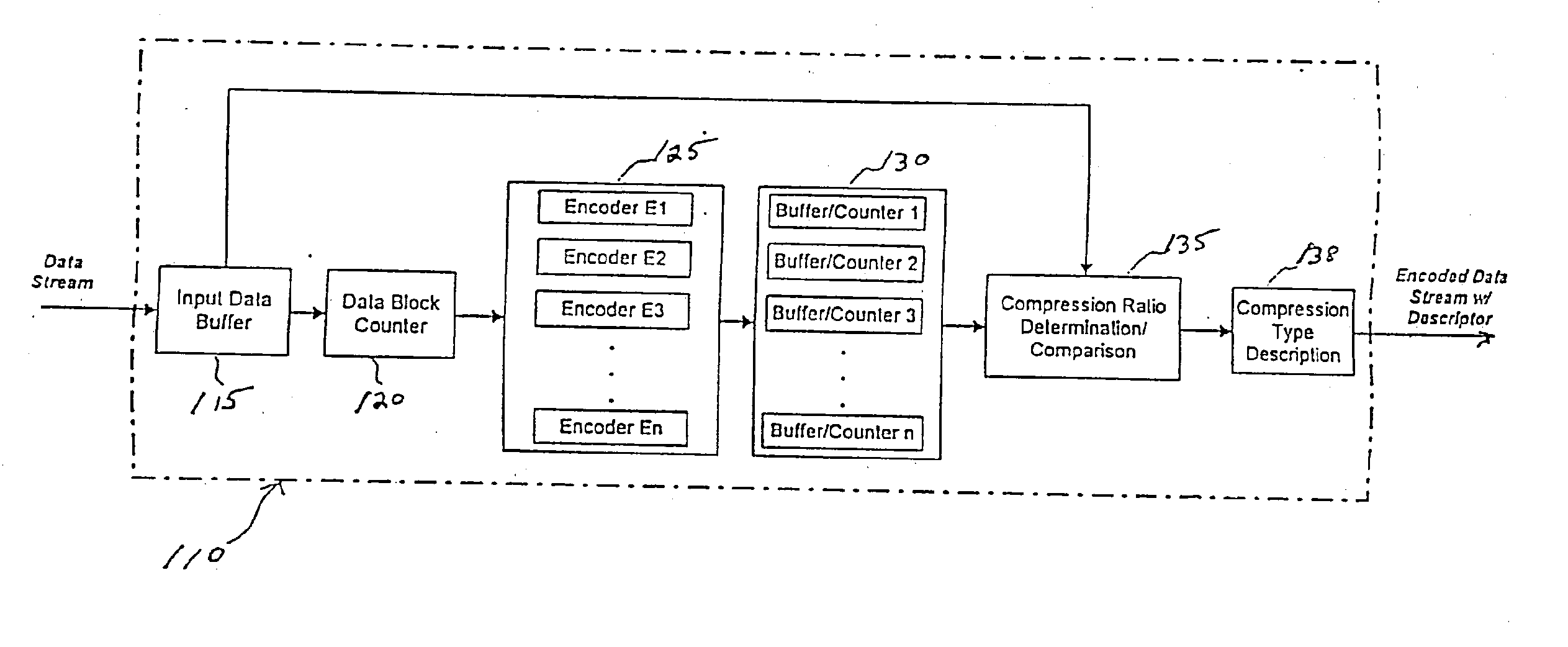
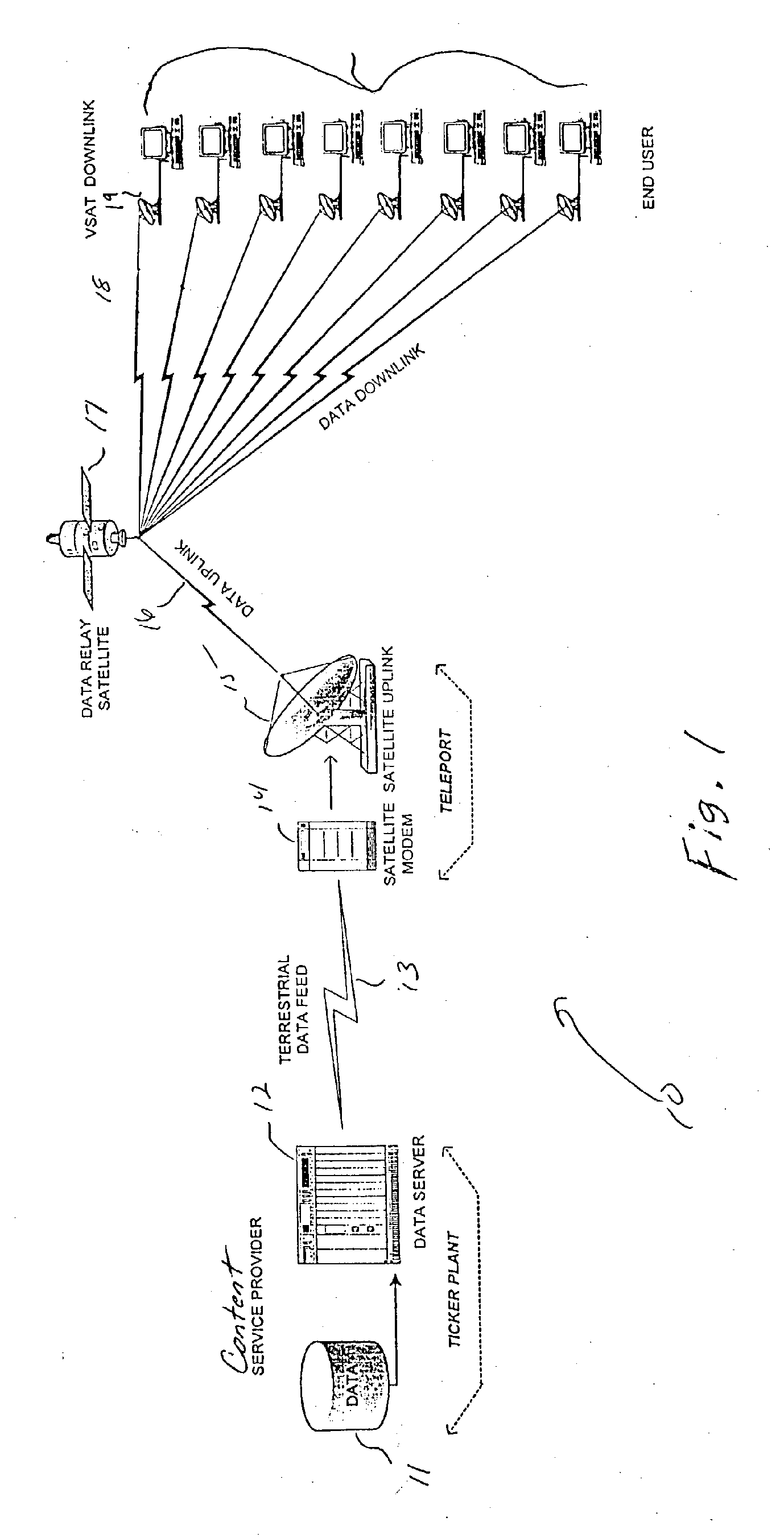
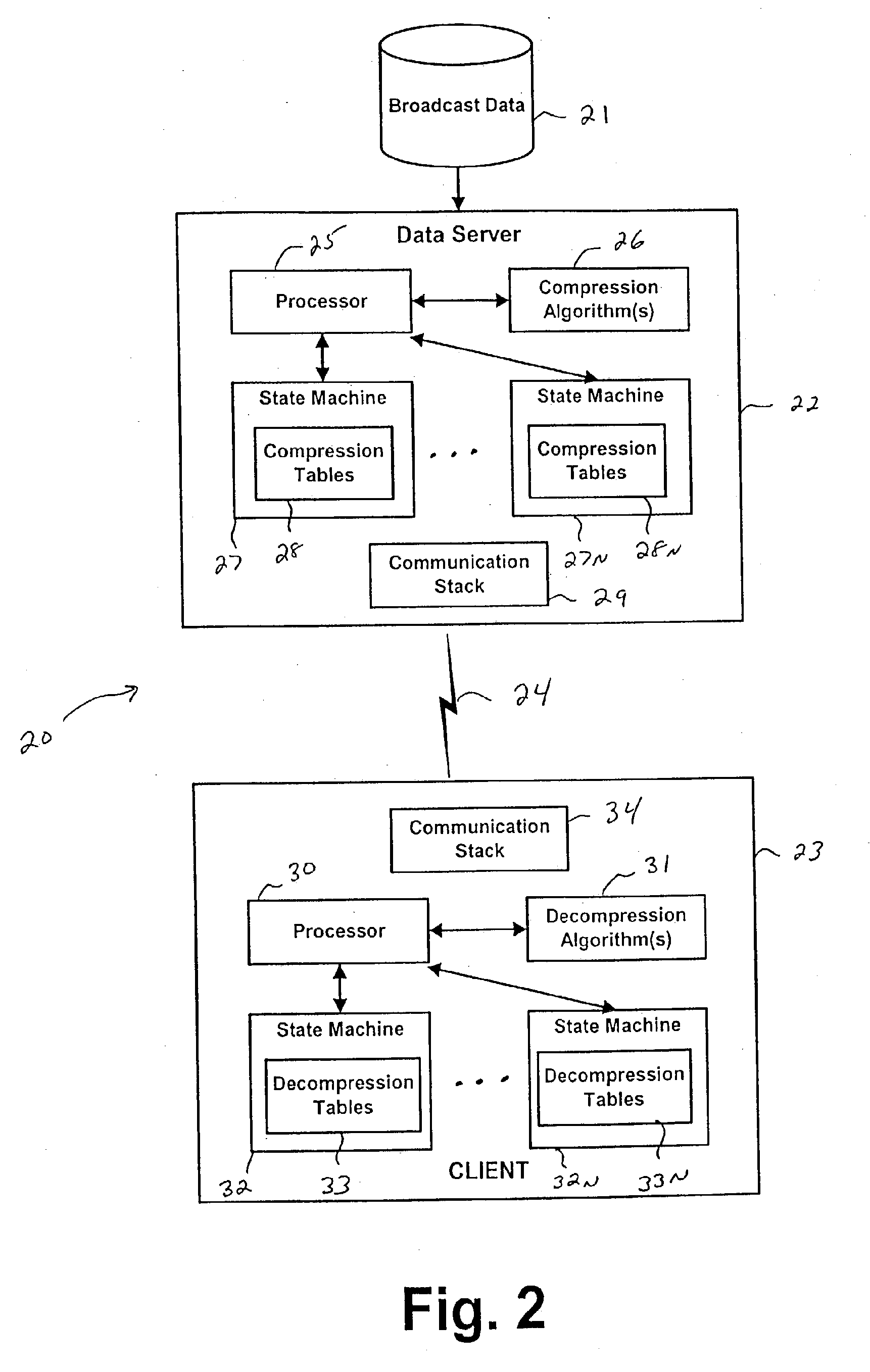
System and method for data feed acceleration and encryption
InactiveUS20070174209A1Long latency timeHigh bandwidthSpecial service provision for substationFinanceData compressionData feed
Systems and methods for providing accelerated transmission of broadcast data, such as financial data and news feeds, over a communication channel using data compression and decompression to provide secure transmission and transparent multiplication of communication bandwidth, as well as reduce the latency associated with data transmission of conventional systems.
Owner:REALTIME DATA
Identity-based-encryption system with district policy information
ActiveUS7103911B2Key distribution for secure communicationDigital data processing detailsNetwork Communication ProtocolsKey generator
A system is provided that uses identity-based encryption (IBE) to allow a sender to securely convey information in a message to a recipient over a communications network. IBE public key information may be used to encrypt messages and corresponding IBE private key information may be used to decrypt messages. The IBE private keys may be provided to message recipients by an IBE private key generator. The IBE private key generator and the recipients who obtain their IBE private keys from that generator form a district. District policy information may be provided by the IBE private key generator that specifies which encryption and communications protocols are used by the district. The district policy information may also specify which authentication protocols are used by the district and may set forth how content-based protocols are implemented. This information may be used by senders in sending messages to recipients.
Owner:MICRO FOCUS LLC
Encryption and communication apparatus and method using modulated delay time feedback chaotic system
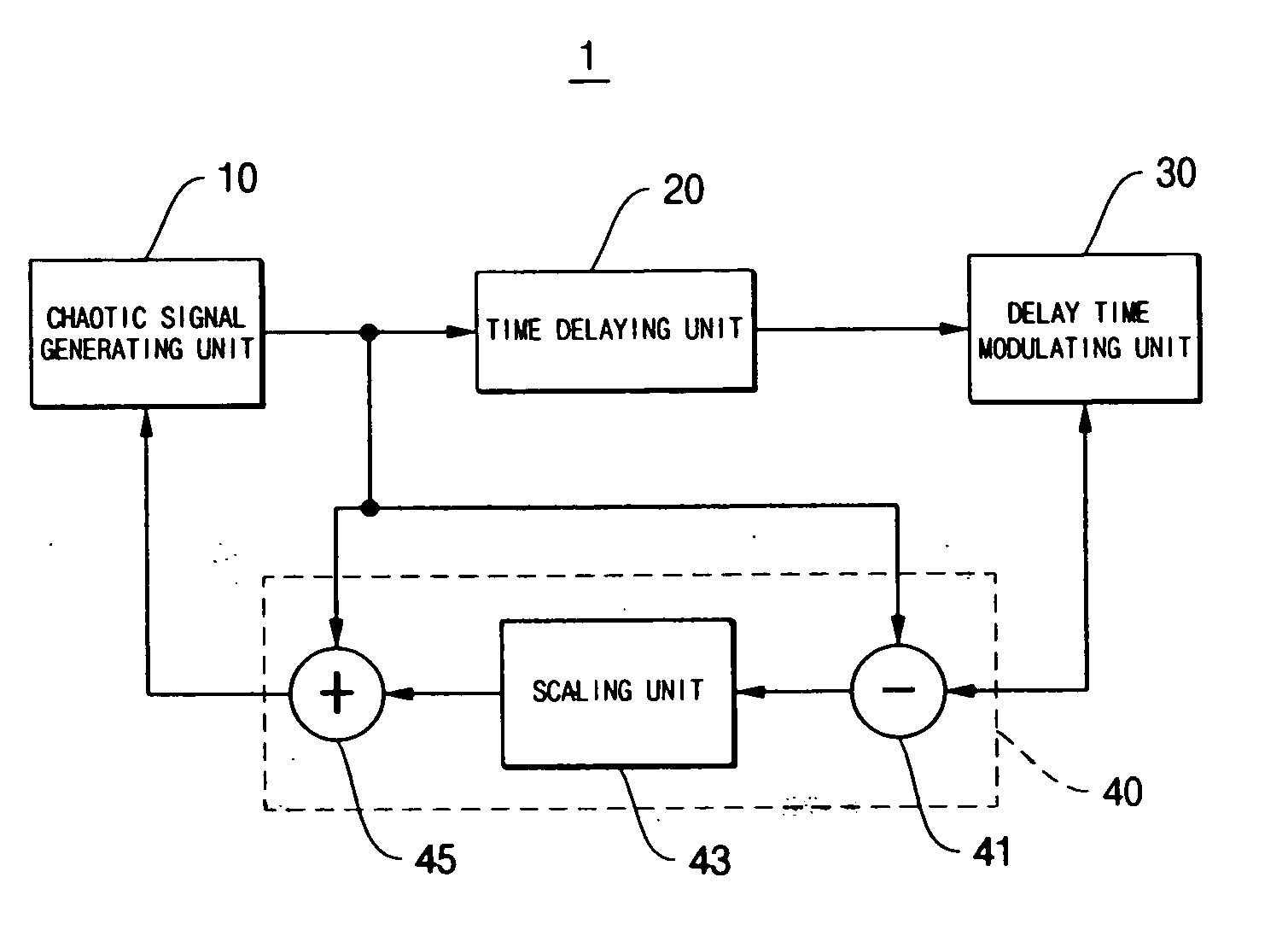
InactiveUS20050089169A1Avoid attackImpossible to detectEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsDelayed timeChaotic systems
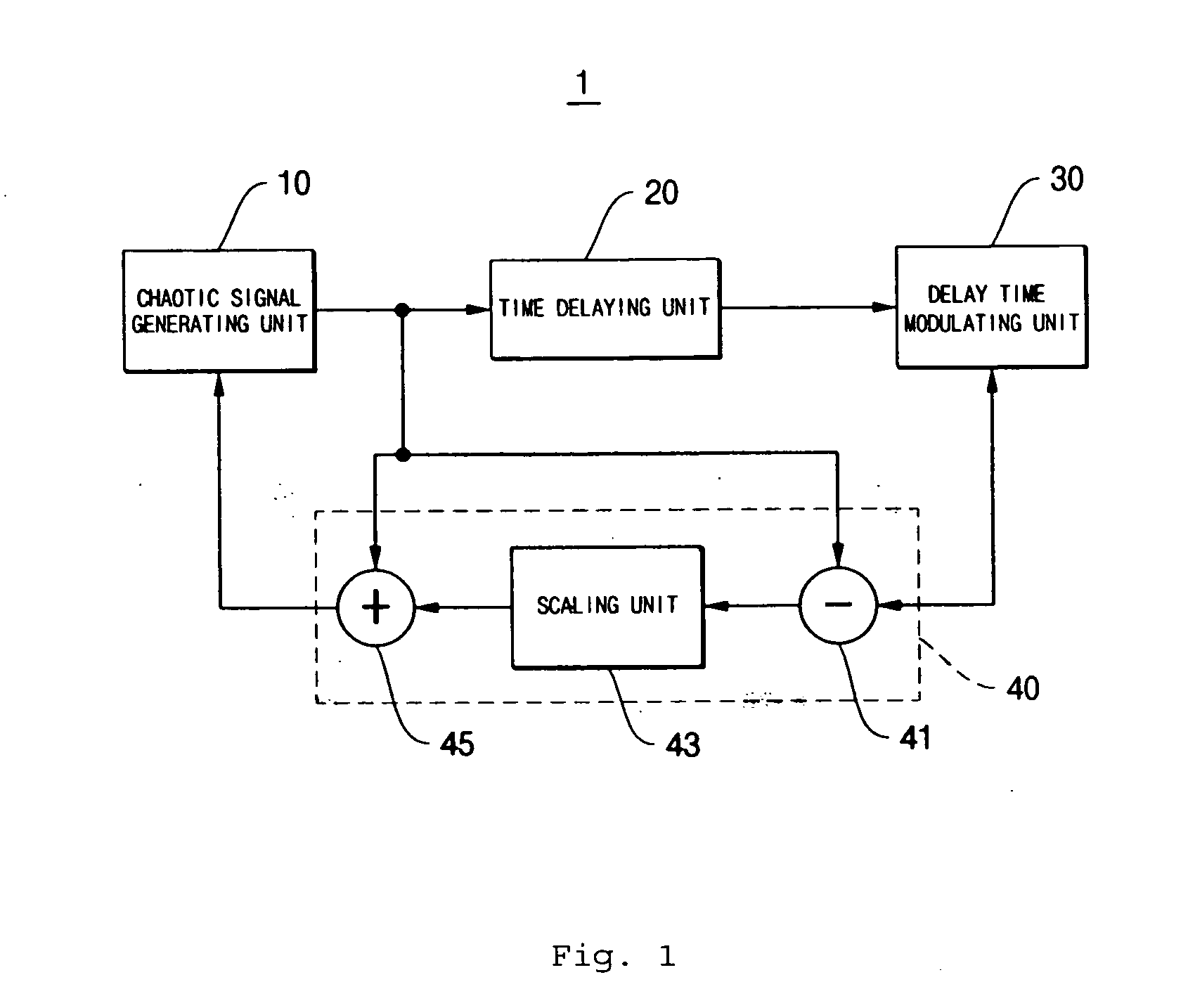
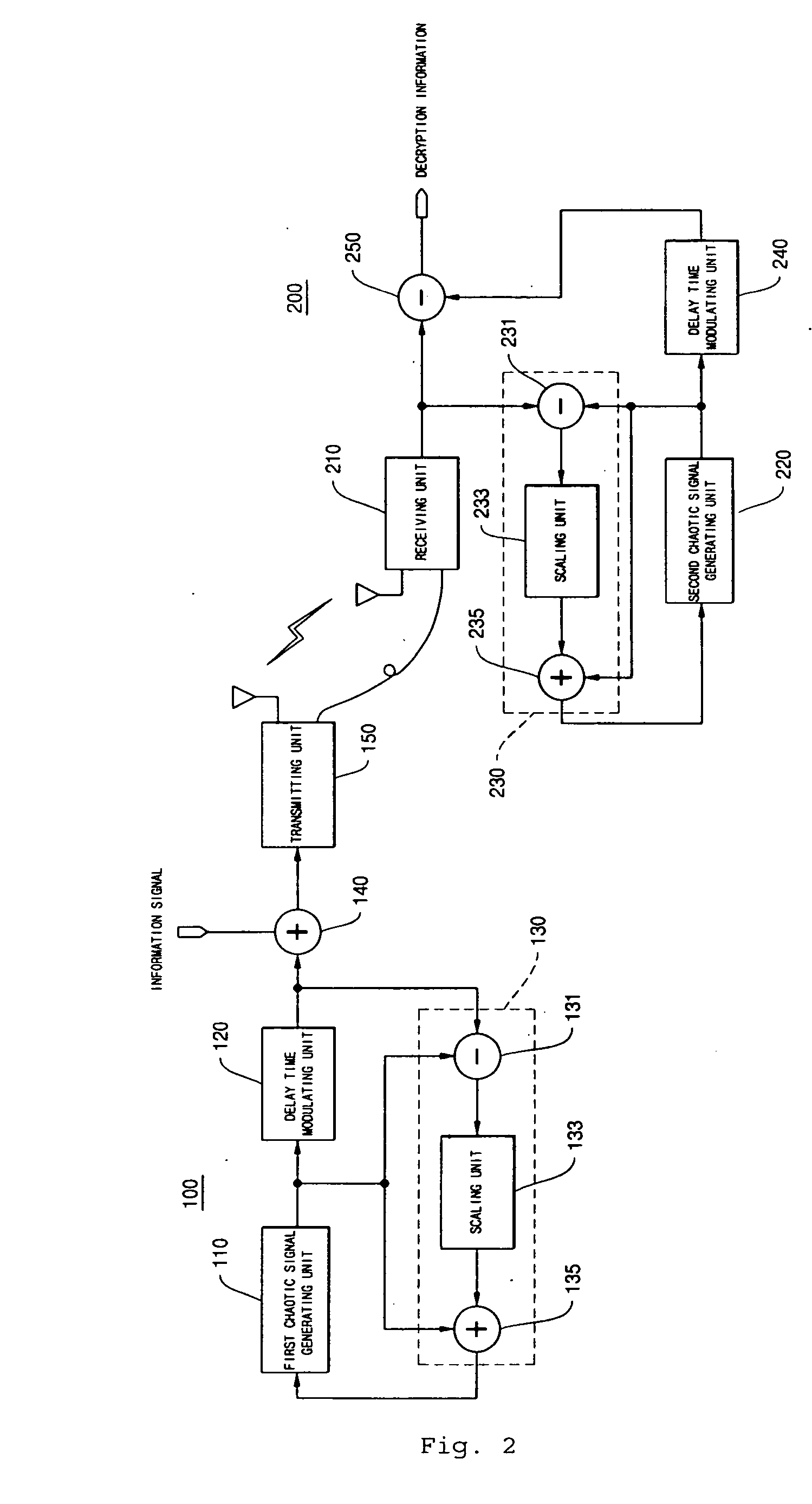
Disclosed herein is an encryption and communication apparatus and method using a modulated delay time feedback chaotic system. The encryption apparatus of the present invention includes chaotic signal generating means for generating a high-dimensional chaotic signal in response to an original chaotic signal and a predetermined feedback chaotic signal, delay time modulating means for delaying the high-dimensional chaotic signal output from the chaotic signal generating means by a predetermined time and modulating the time-delayed chaotic signal, and feedback means for receiving the chaotic signal output from the chaotic signal generating means and the modulated time-delayed signal output from the delay time modulating means, performing addition and subtraction operations with respect to the received signals, and feeding the operated result back to the chaotic signal generating means. Accordingly, the present invention is advantageous in that it modulates a delay time so as to prevent an information signal contained in a chaotic signal from being attacked from the outside, so that it is impossible to detect an exact delay time contained in a modulated time-delayed chaotic signal and to decrypt the information signal, thus constructing a more robust and reliable encryption system.
Owner:EDUCATIONAL
Cryptographic system with methods for user-controlled message recovery
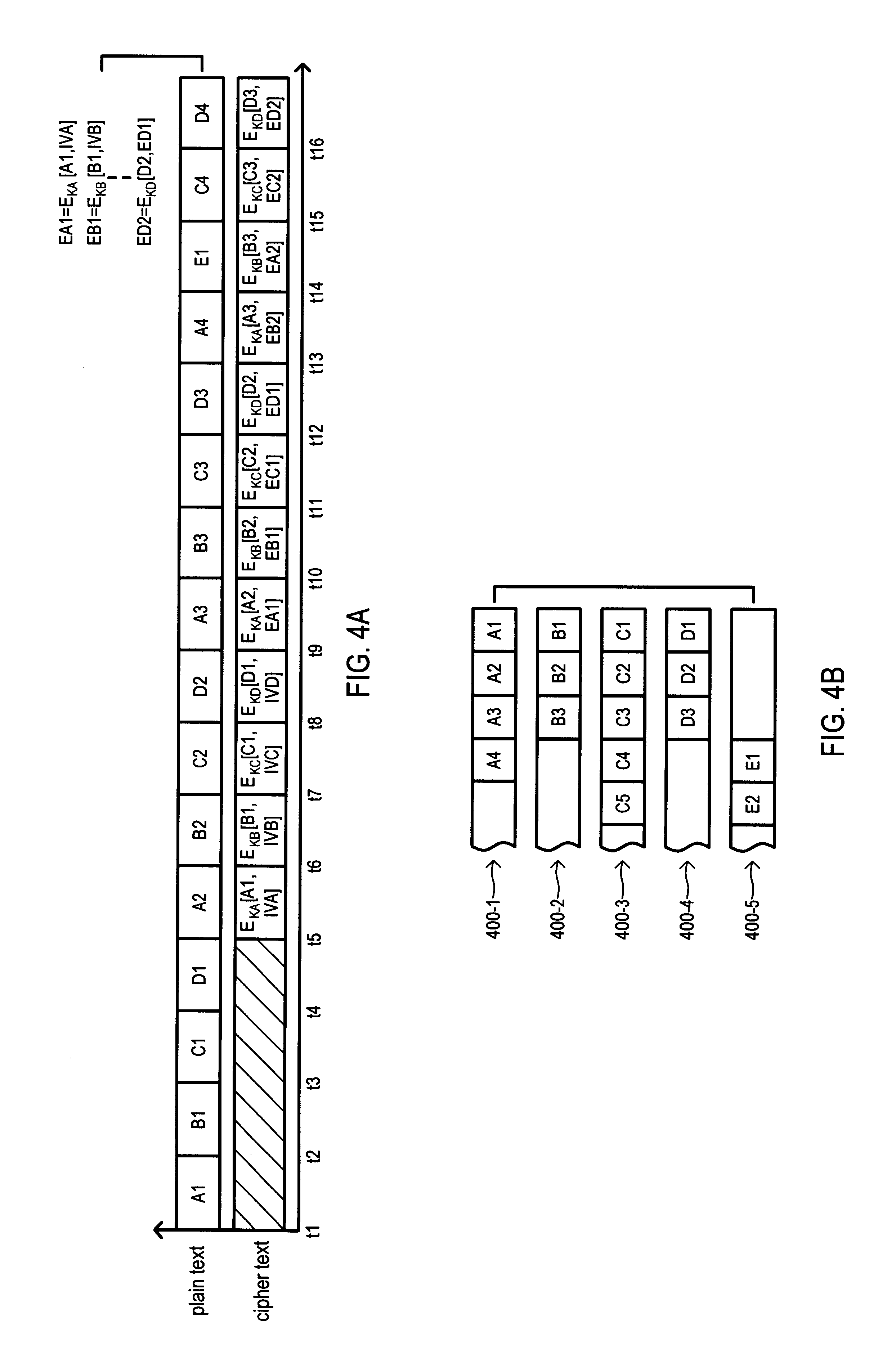
InactiveUS7139399B1Storage requirement increaseKey distribution for secure communicationS/KEYCryptosystem
A cryptosystem is described which automatically provides an extra “message recovery” recipient(s) when an encrypted message is generated in the system. The system is typically configured such that the extra recipient or “message recovery agent” (MRA)—an entity which itself has a public key (i.e., a MRA public key)—is automatically added, under appropriate circumstances, as a valid recipient for an encrypted message created by a user. In a corporate setting, for example, the message recovery agent is the “corporate” message recovery agent designated for that company (firm, organization, or other group) and the user is an employee (or member) of that company (or group). In operation, the system embeds a pointer (or other reference mechanism) to the MRA public key into the public key of the user or employee, so that encrypted messages sent to the company's employees from outside users (e.g., those individuals who are not employees of the company) can nevertheless still be recovered by the company. Alternatively, the MRA public key itself can be embedded within the public key of the employee or user (i.e., a key within a key), but typically at the cost of increasing the storage requirement of the user's key. By including in the user's key (e.g., an employee) a pointer to a message recovery agent's key (or the MRA key itself), the system provides a mechanism for assisting a user outside a group (e.g., a user who is outside a particular company) with the task of including in an automatic and non-intrusive manner the key of an additional recipient, such as one intended for message recovery.
Owner:CA TECH INC
Quantum-key-distribution-network-based mobile encryption system and communication method thereof
ActiveCN102196425AReduce computationGuaranteed distribution securitySecurity arrangementPlaintextTelecommunications
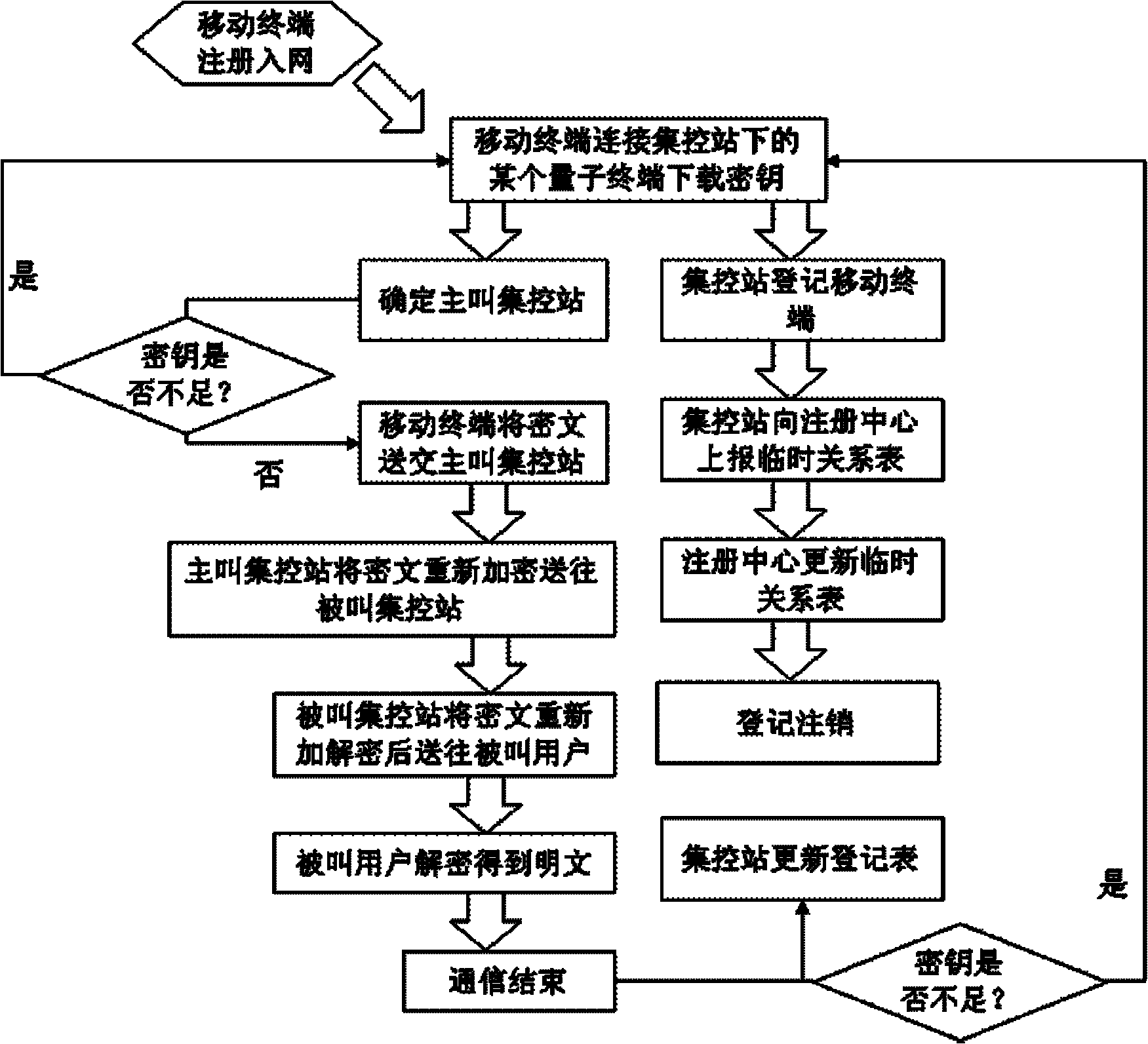
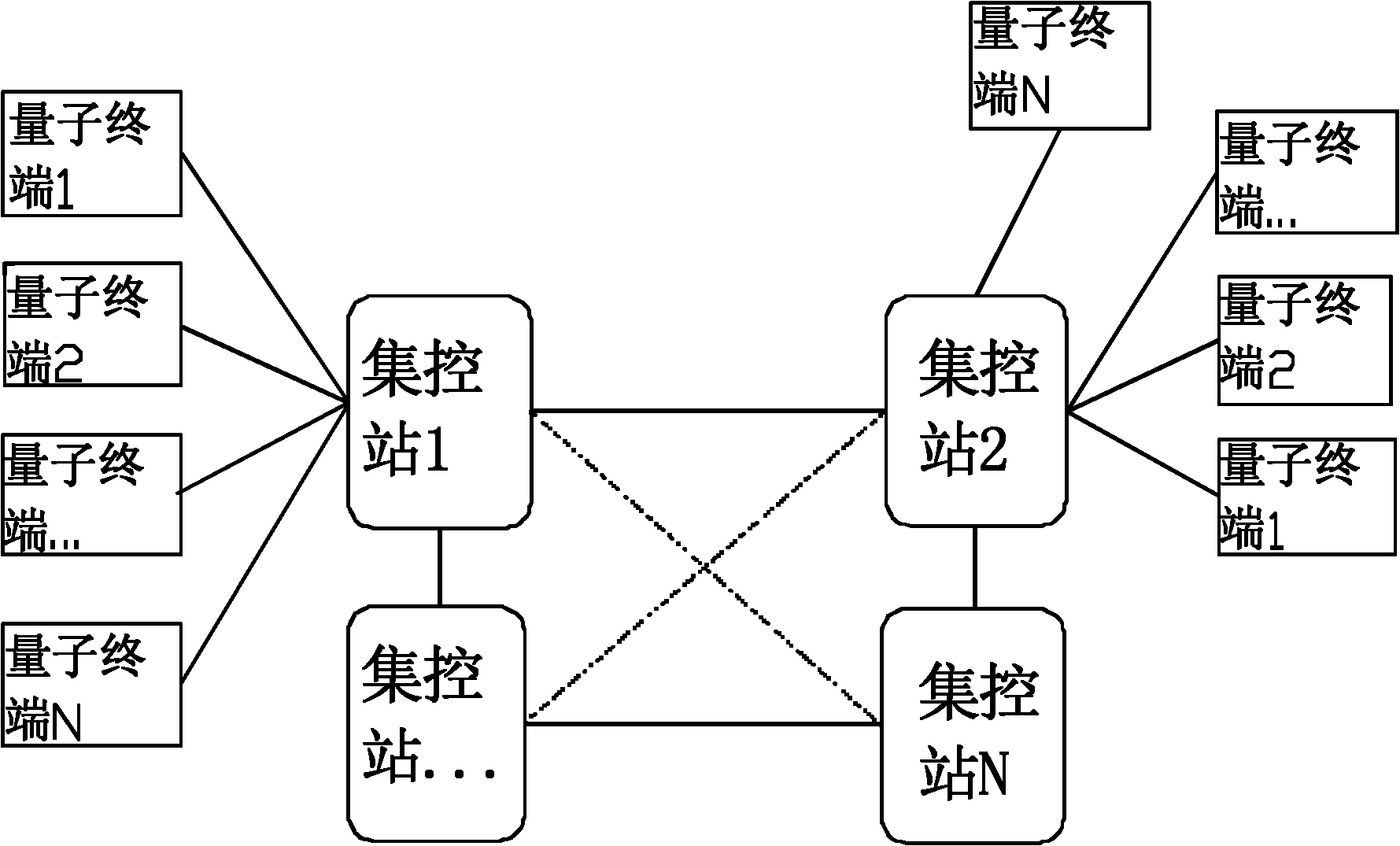
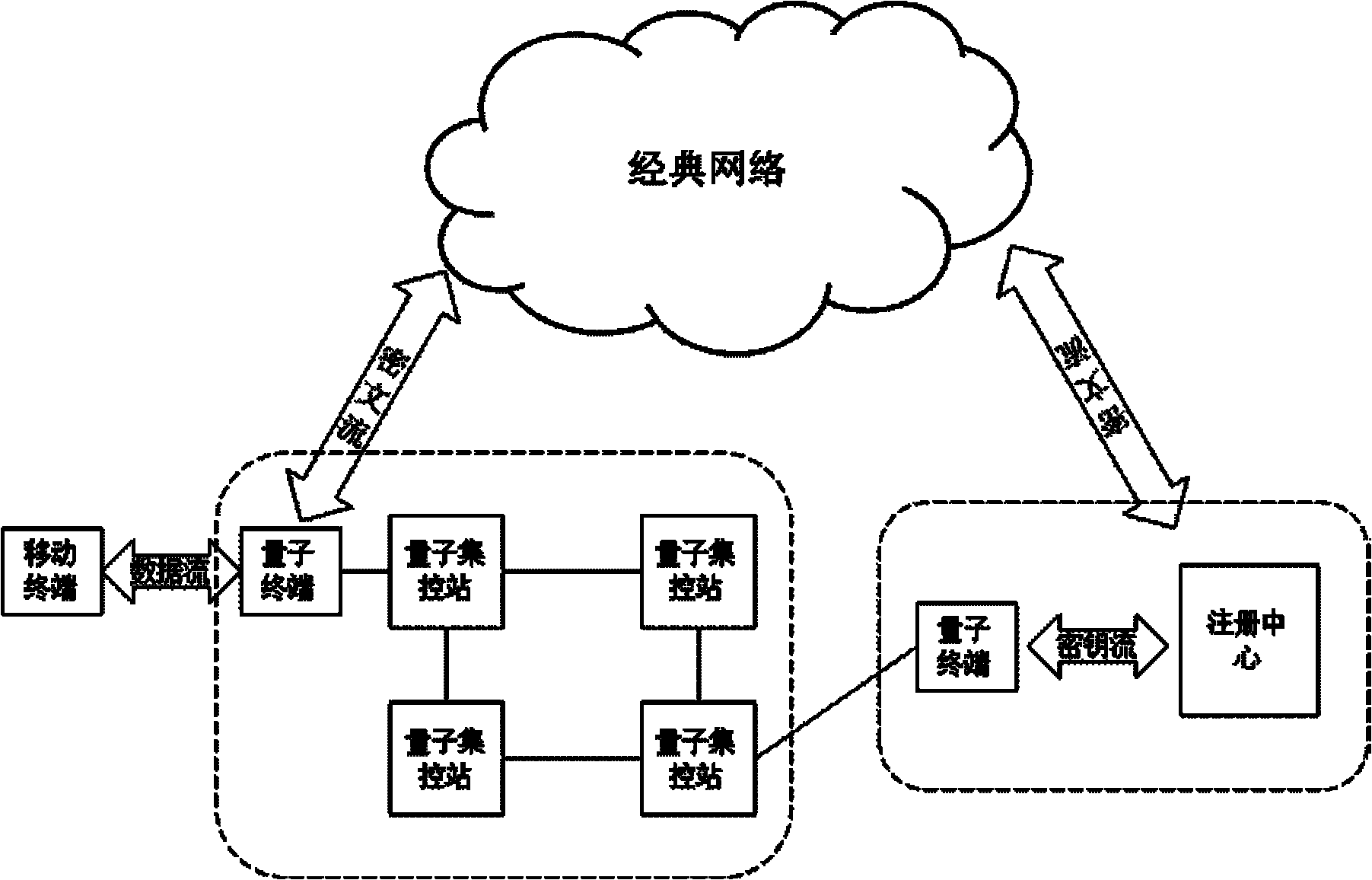
The invention discloses a quantum-key-distribution-network-based mobile encryption system and a communication method thereof. The method comprises that: a mobile terminal is registered in a network; the registered mobile terminal is connected with any quantum terminal by a key updating interface, and applies for the downloading of shared keys in a certain data volume to the quantum terminal; after the mobile terminal downloads the keys, the quantum terminal transmits a quantum centralized control station address to the mobile terminal for updating, and the mobile terminal takes a centralized control station on the quantum centralized control station address as a calling centralized control station; after the calling centralized control station is determined, the mobile terminal submits a cipher text to the calling centralized control station; the calling centralized control station re-encrypts the cipher text, and transmits the re-encrypted cipher text to a called centralized control station; the called centralized control station re-encrypts the cipher text, and transmits the re-encrypted cipher text to a called user; and after the called user decrypts the re-encrypted cipher text to obtain a plaintext, the communication is finished. In the method, the encryption does not require multiple matrix multiplication operations, so the computational load of the encryption is greatlyreduced; and simultaneously, the key distribution security of the highest level can be ensured in the key distribution of a quantum key distribution network.
Owner:QUANTUMCTEK +1
System and method for computerized global messaging encryption
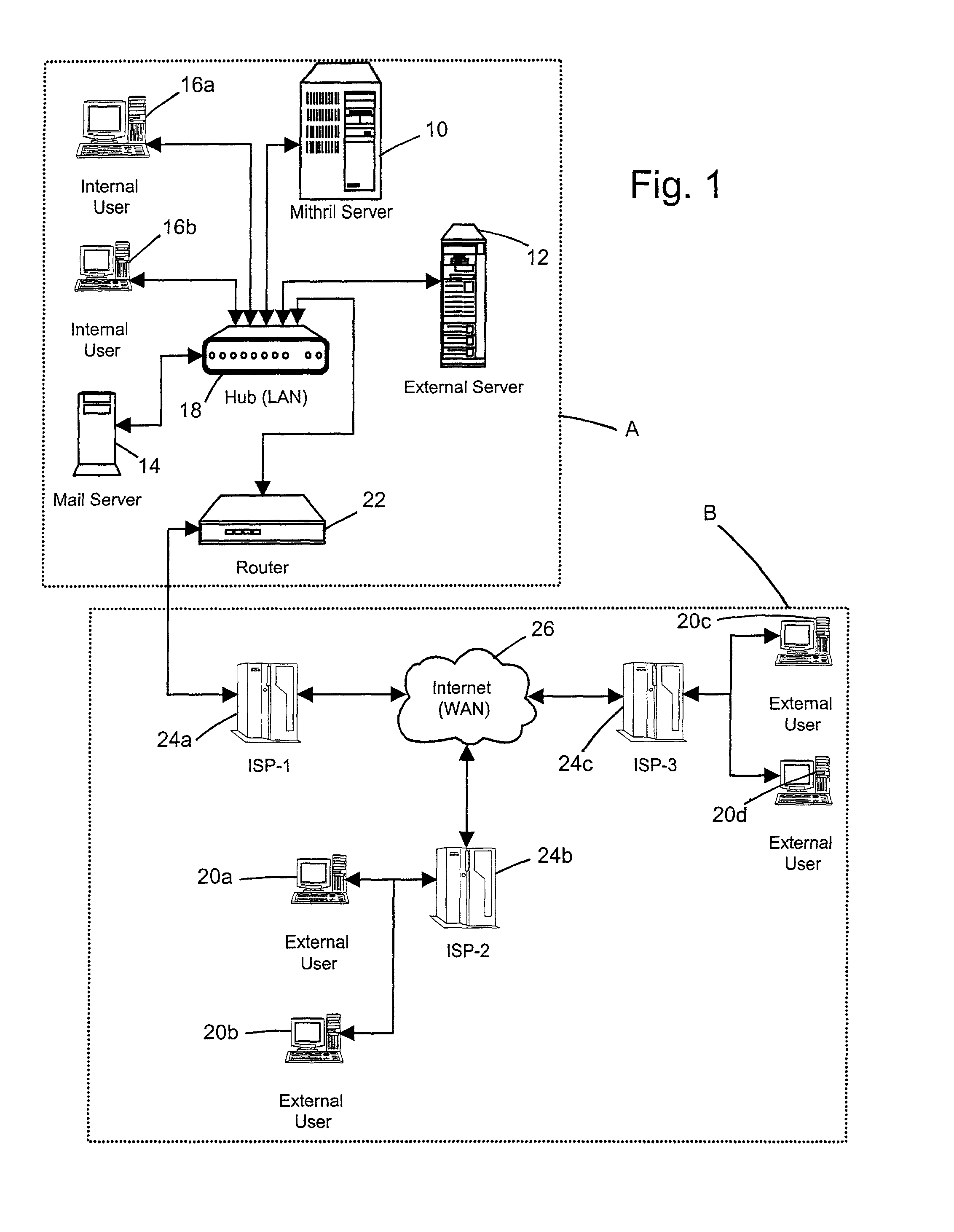
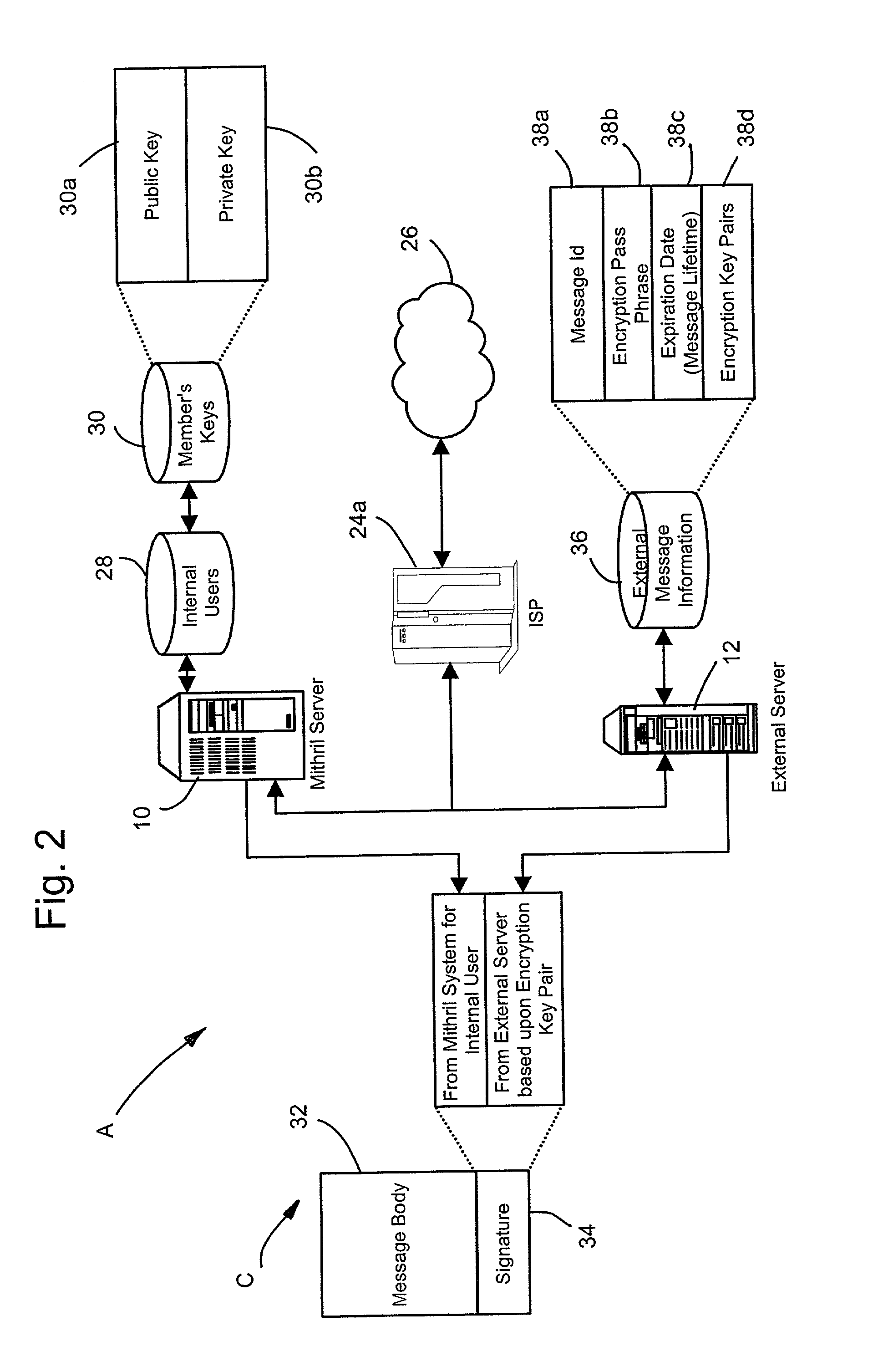
InactiveUS7082536B2Key distribution for secure communicationPublic key for secure communicationPassphrasePhrase
A computer based message encryption system for transmitting encrypted message between a sending member of an internal messaging system and a receiving non-member or receiving member external user without requiring the sender or recipient member to maintain and support encryption key pairs themselves. An internal system that contains an external server for creating key pairs for message encryption between the senders and receives for the encryption of messages. The key pairs are encrypted themselves according to an encryption pass-phrase so that the pass-phrase may used to decrypt the key pair which in turn may be used to decrypt the message. In response to a predetermined time or destroy command, said encryption key pairs are destroyed.
Owner:GLOBALCERTS LLC
System for establishing a cryptographic key depending on a physical system
ActiveUS20120072737A1Reduction of informationReduce decreaseKey distribution for secure communicationDigital data processing detailsComputer hardwareCryptographic nonce
In systems for establishing a cryptographic key depending on a physical uncloneable function (PUF) it may be a problem that internal information correlated with the cryptographic key is leaked to the outside of the system via a side-channel. To mitigate this problem a cryptographic system for reproducibly establishing a cryptographic key is presented. The system comprises a physical system comprising a physical, at least partially random, configuration of components from which an initial bit-string is derived. An error corrector corrects deviations occurring in the initial bit-string. Through the use of randomization the error corrector operates on a randomized data. Information leaking through a side channel is thereby reduced. After error correction a cryptographic key may be derived from the initial bit-string.
Owner:INTRINSIC ID
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com