Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5047results about How to "Reduce the number of times" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
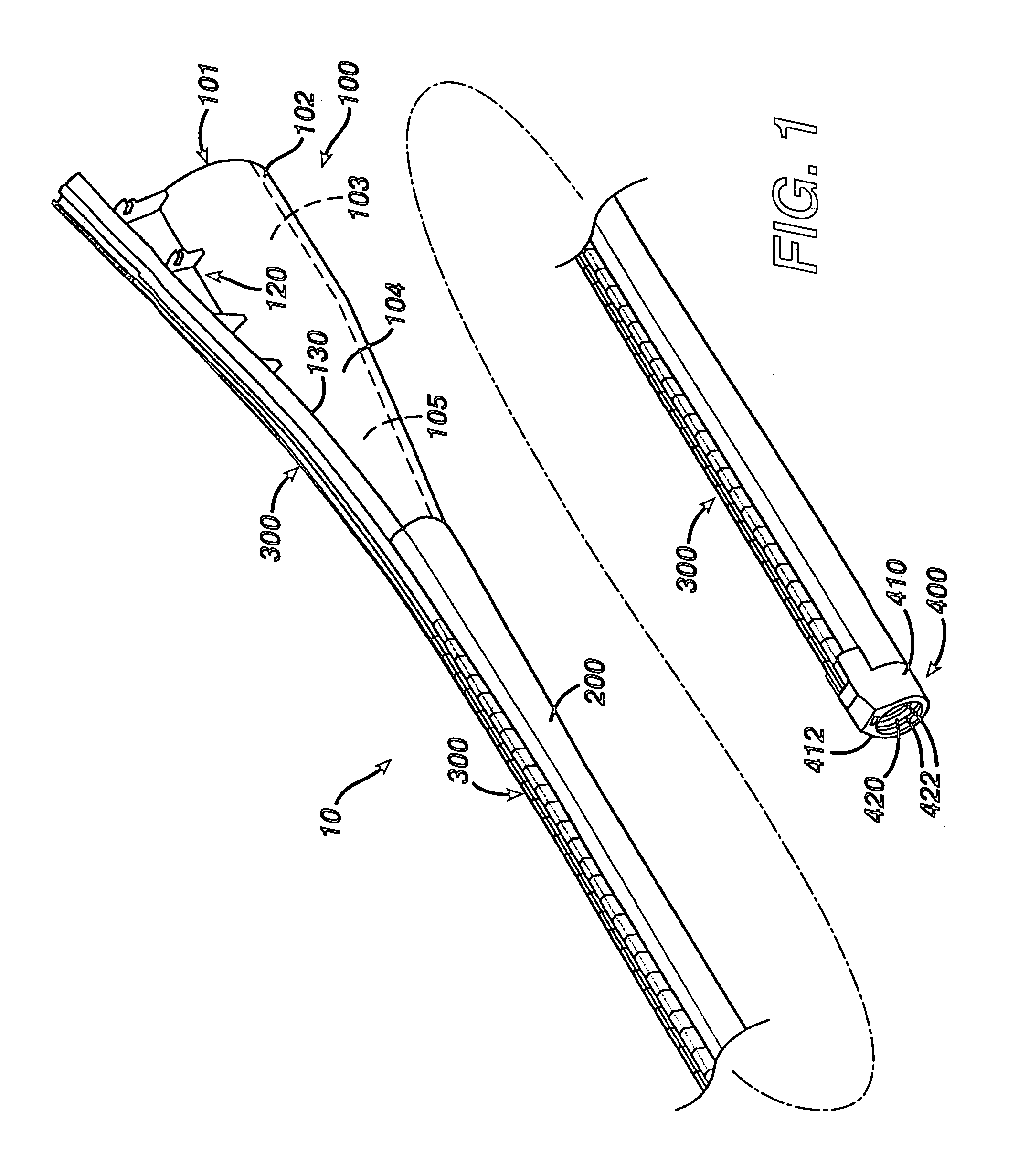
Track for medical devices
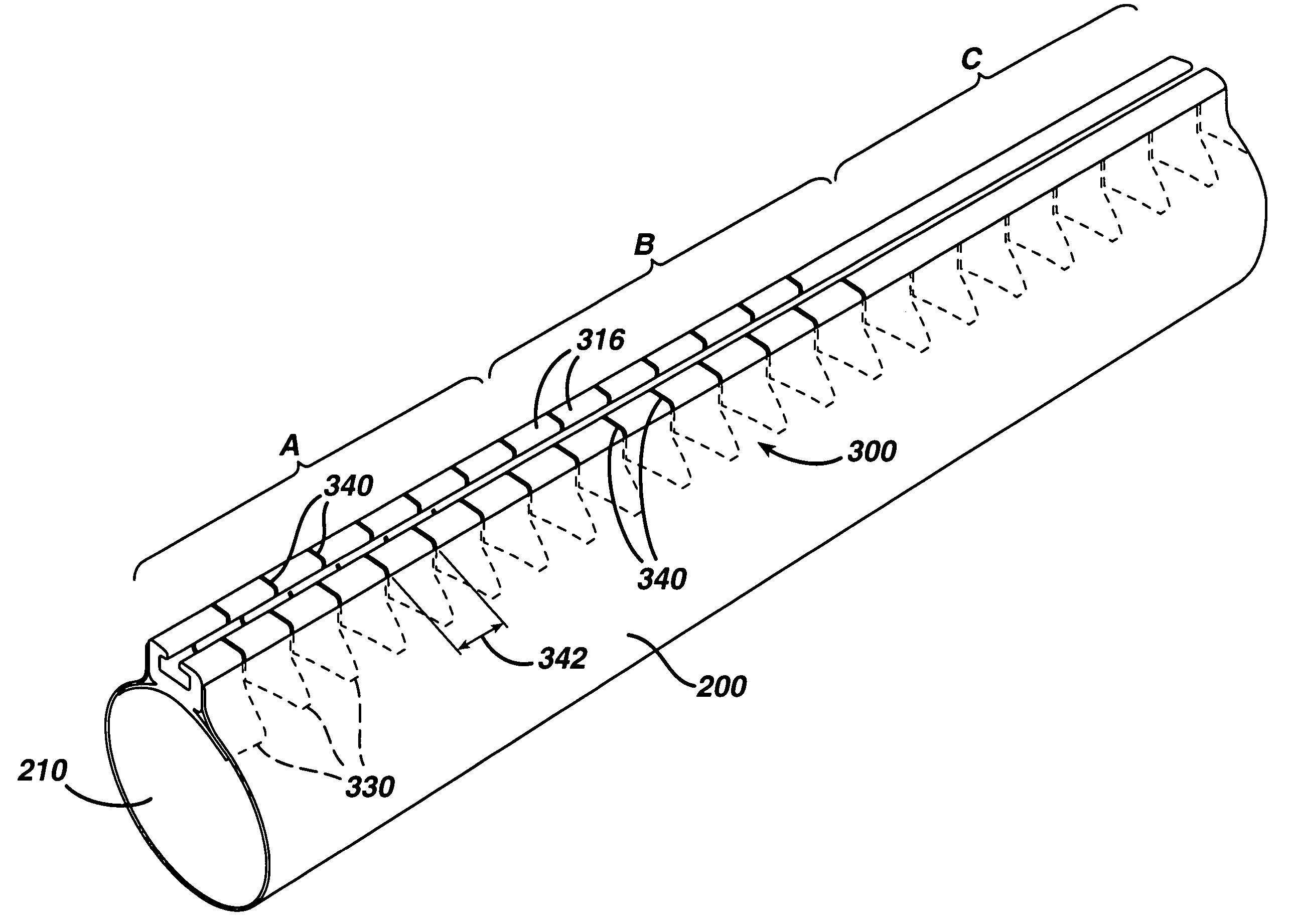
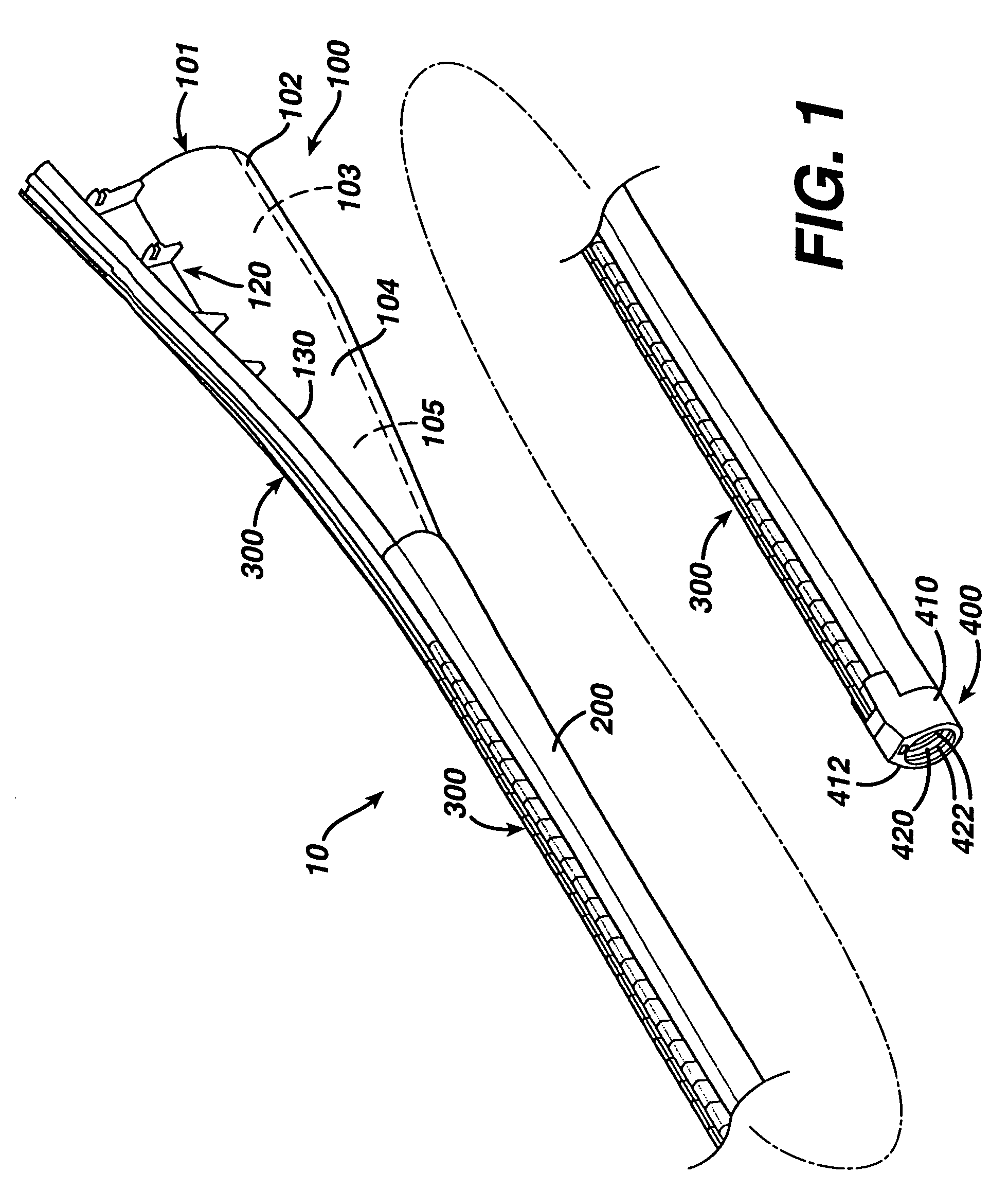
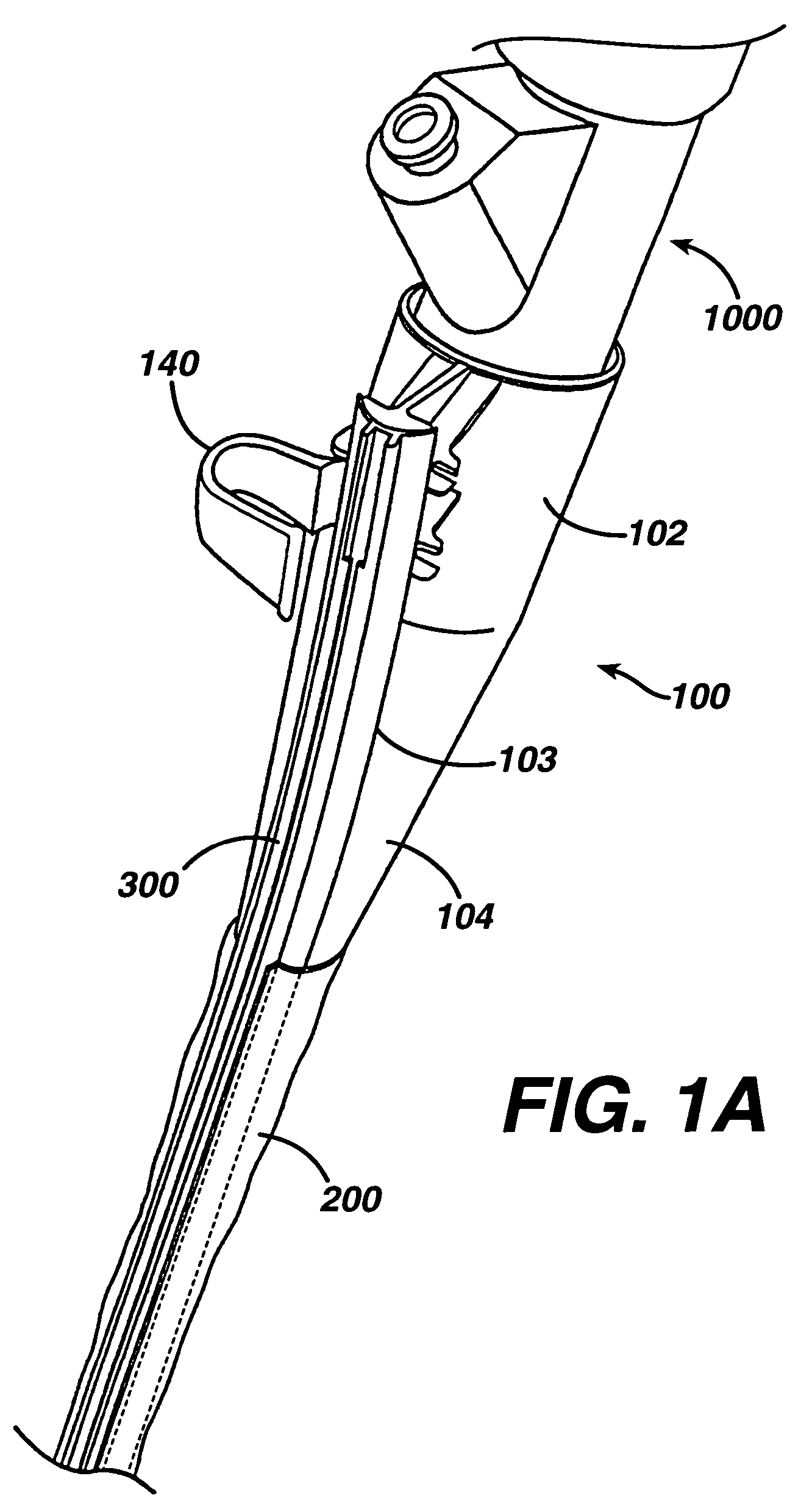
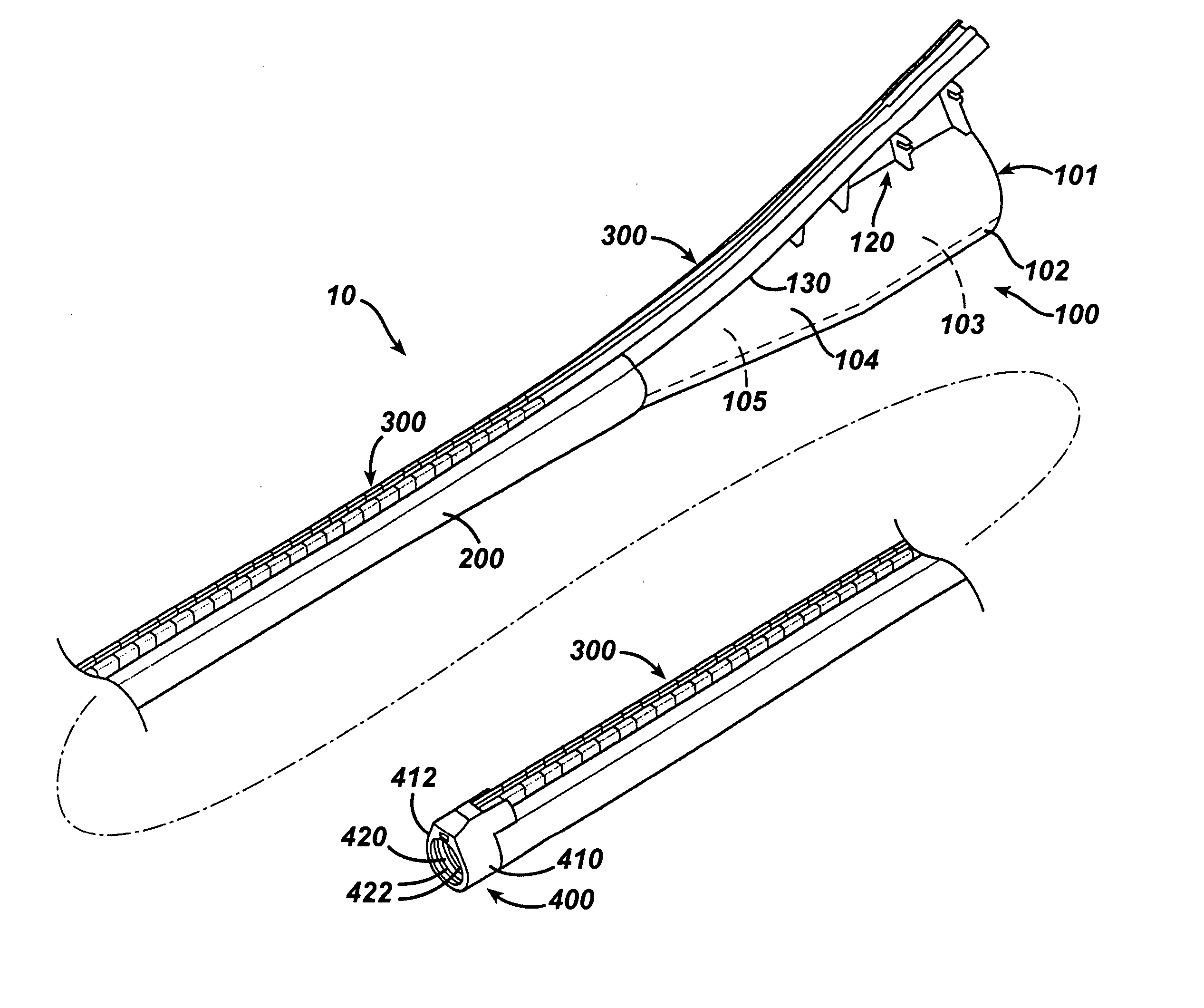
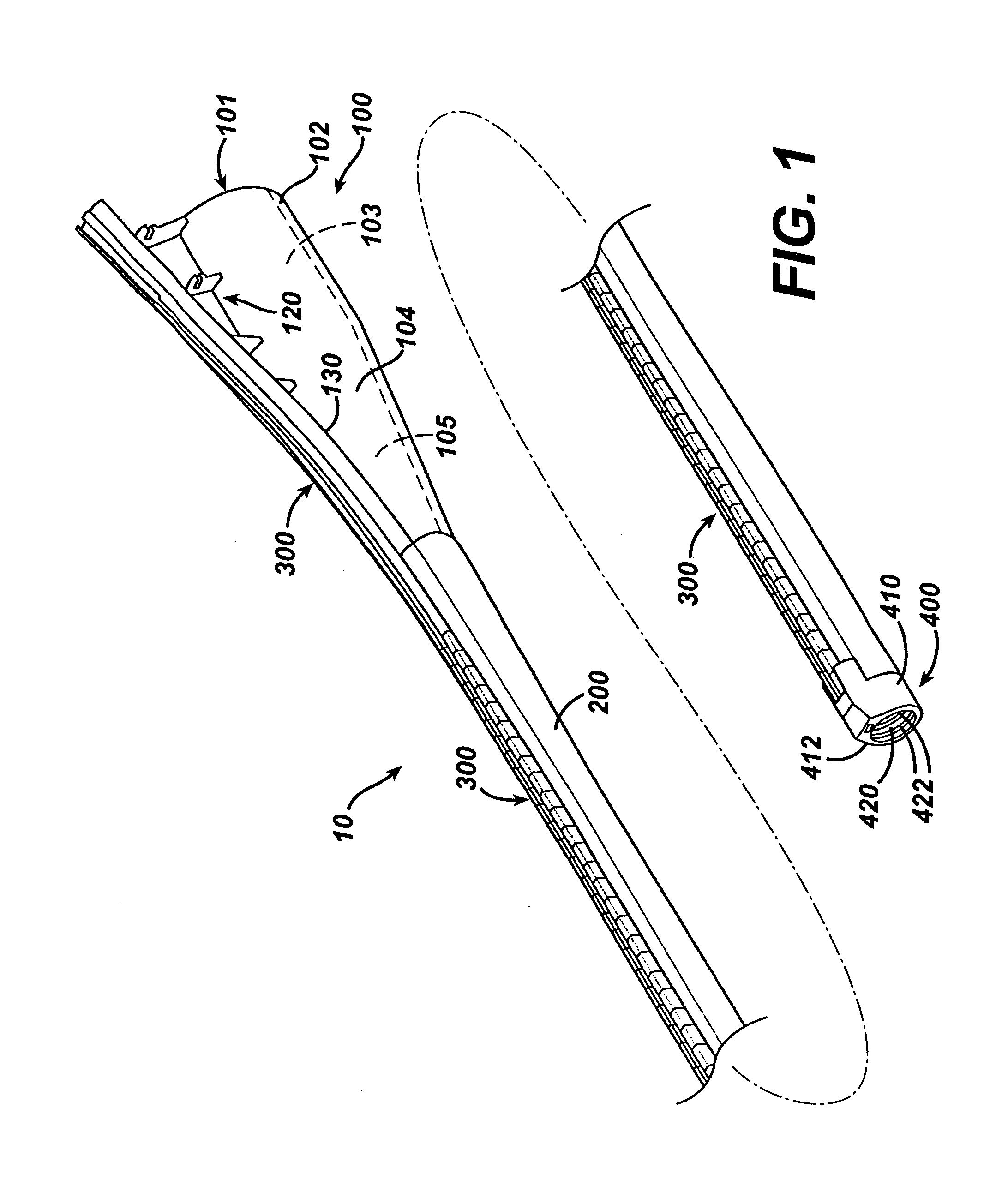
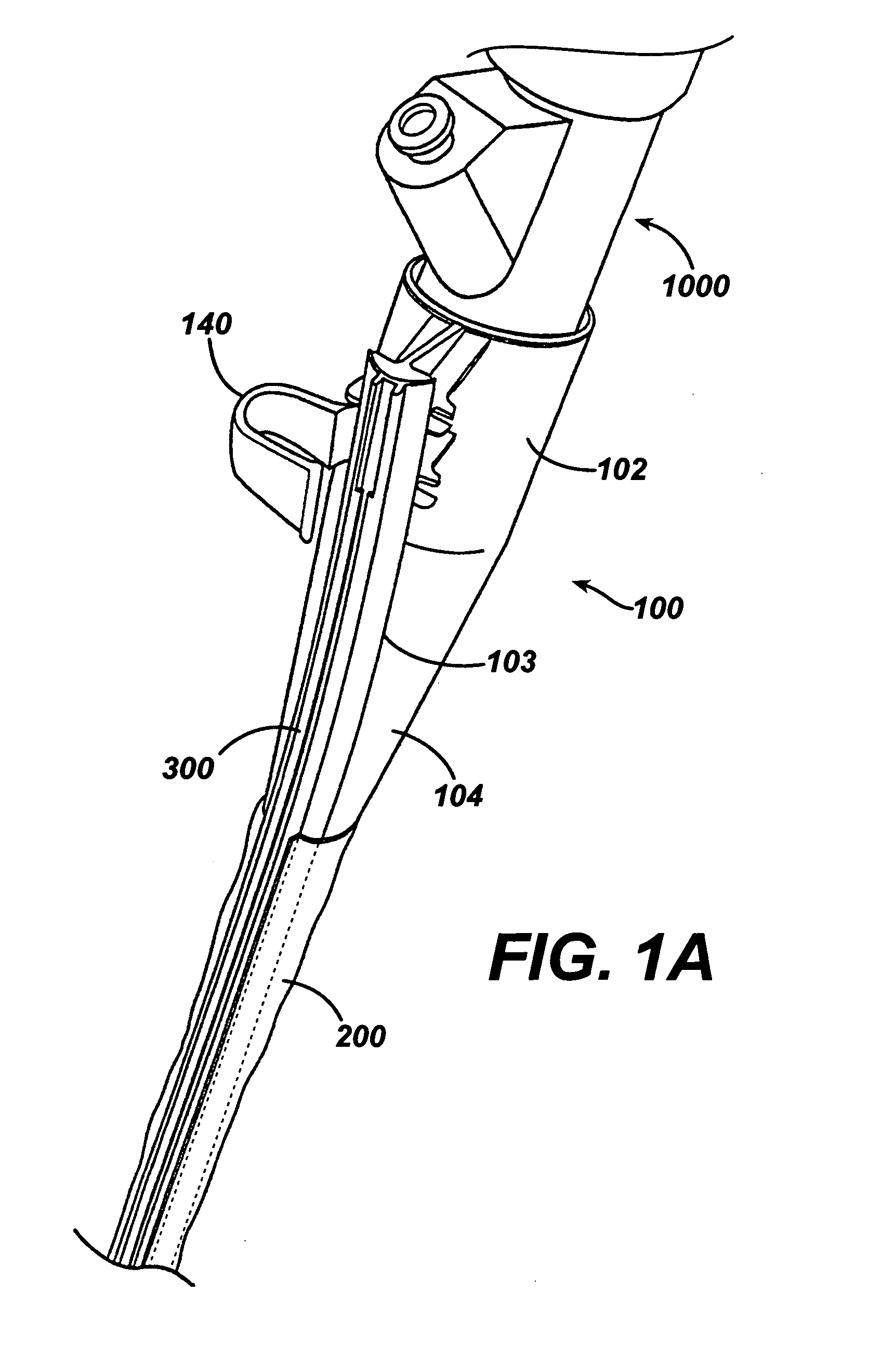
ActiveUS7615003B2Reduce in quantityQuickly and consistentlyGastroscopesCannulasMedical deviceFeeding tube
A medical apparatus and method useful for positioning one or more members within the gastro-intestinal tract is disclosed. The medical apparatus can include a track supported on a sheath sized to receive an endoscope, and a carrier slidable with respect to the track. A feeding tube accessory adapted to slidably engage the carrier is disclosed.
Owner:ETHICON ENDO SURGERY INC
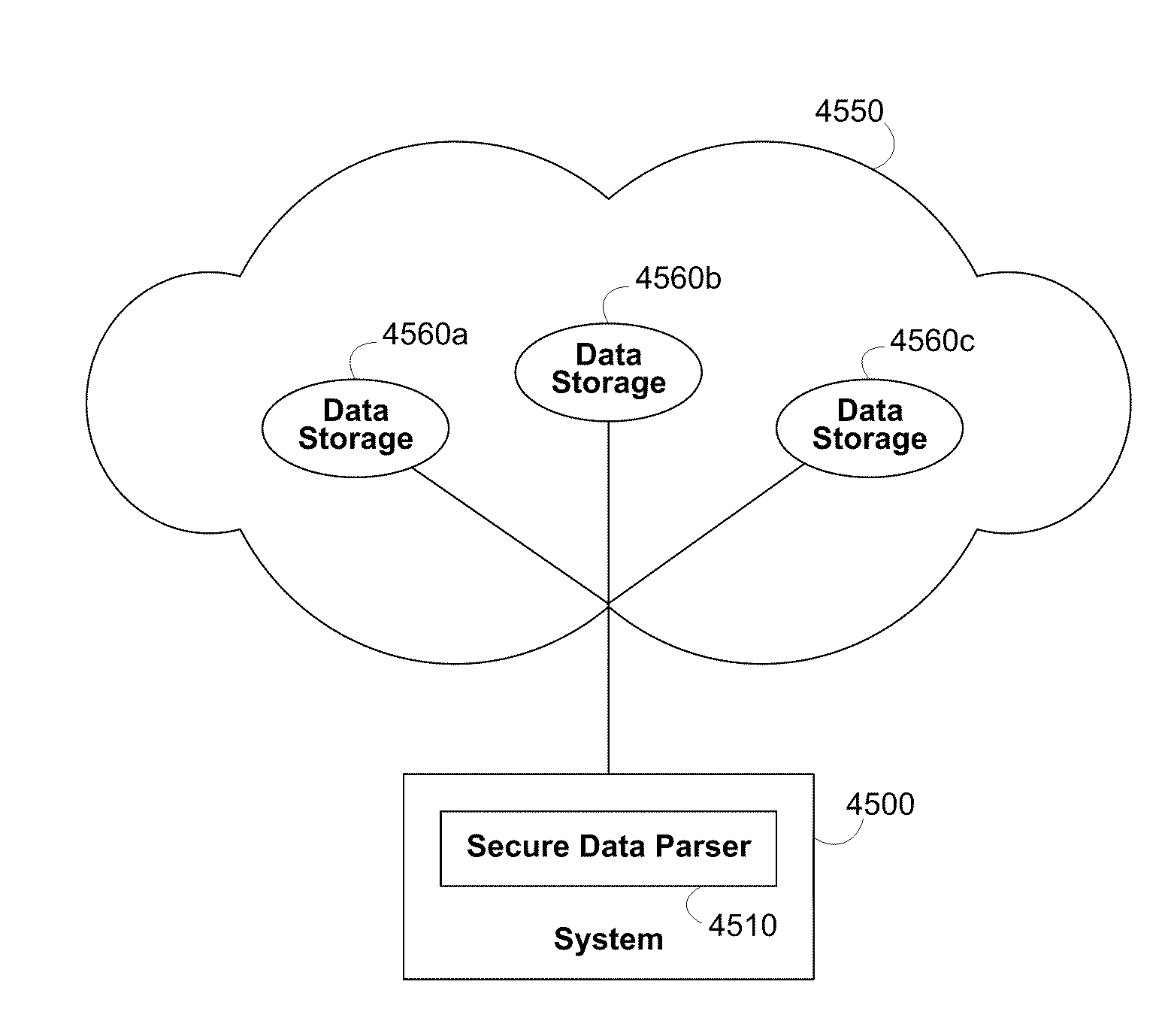
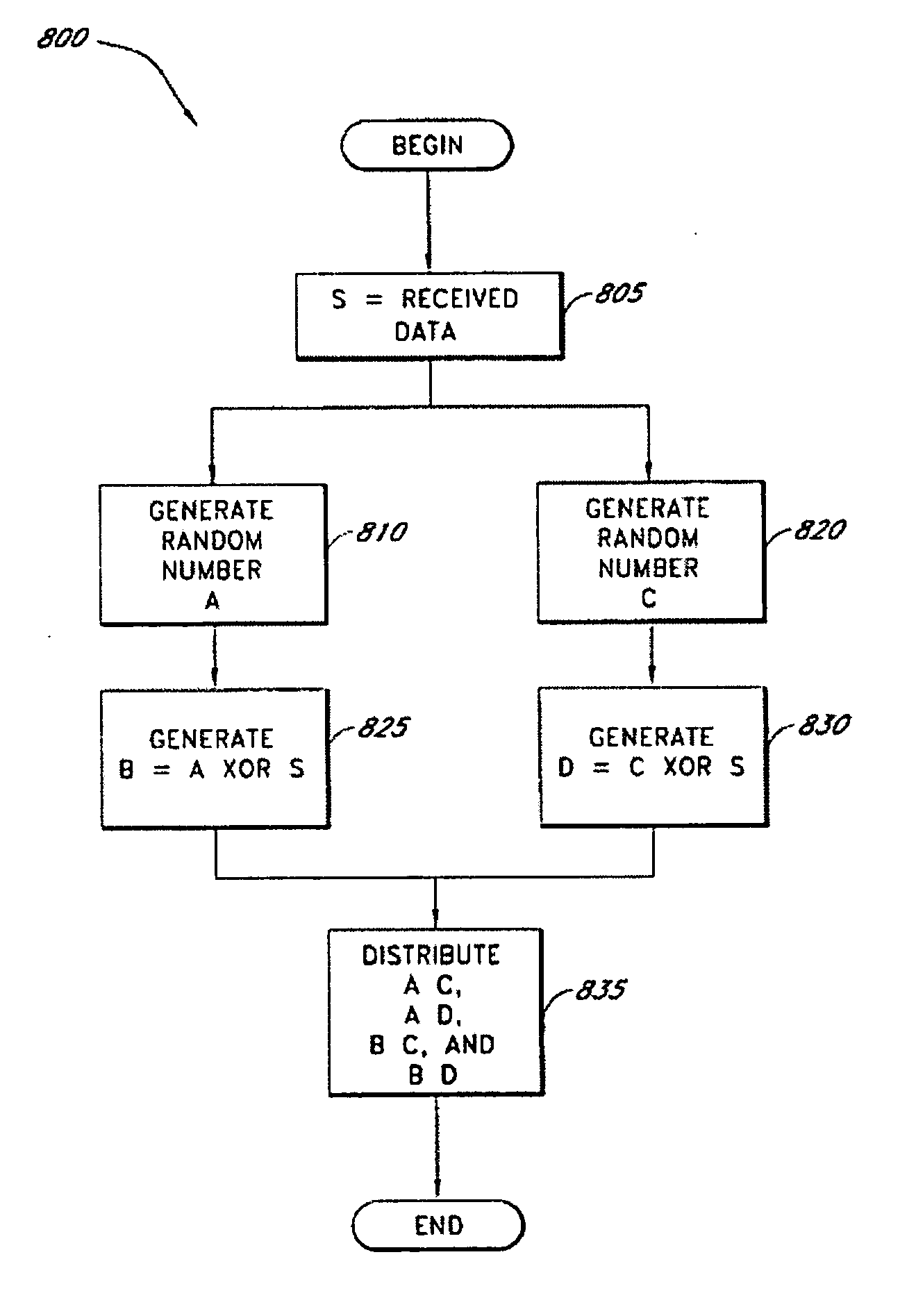
Systems and methods for securing data in the cloud
ActiveUS20100299313A1Minimal compute resourceAvoid the needMultiple keys/algorithms usageDigital data processing detailsCloud computingEncryption
A secure data parser is provided that may be integrated into any suitable system for securely storing data in and communicating data with cloud computing resources. The secure data parser parses data and then splits the data into multiple portions that are stored or communicated distinctly. Encryption of the original data, the portions of data, or both may be employed for additional security.
Owner:SECURITY FIRST INNOVATIONS LLC
Secure data parser method and system
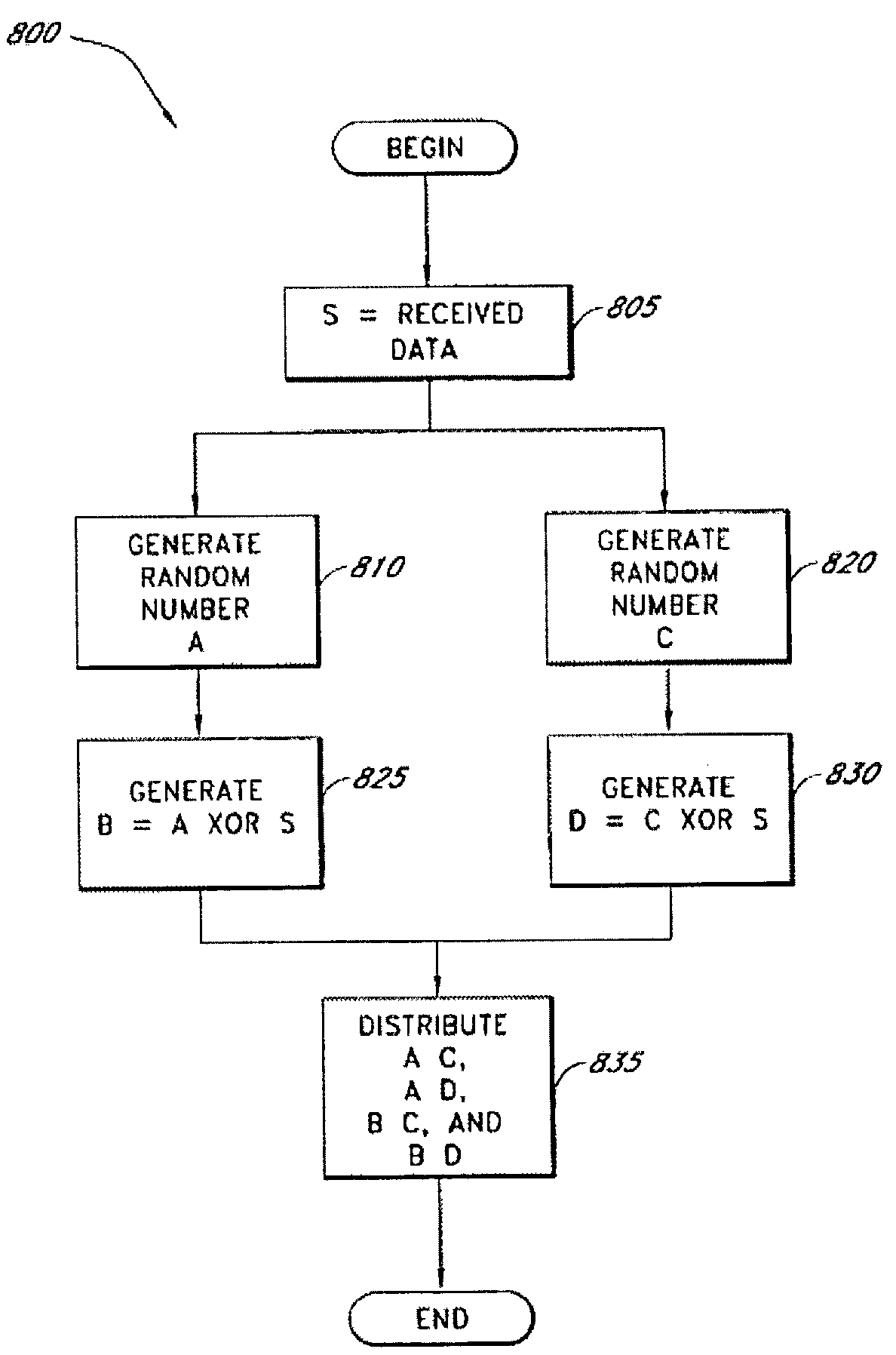
InactiveUS20060177061A1Minimal compute resourceAvoid the needKey distribution for secure communicationError detection/correctionOriginal dataEncryption
A secure data parser is provided that may be integrated into any suitable system for securely storing and communicating data. The secure data parser parses data and then splits the data into multiple portions that are stored or communicated distinctly. Encryption of the original data, the portions of data, or both may be employed for additional security. The secure data parser may be used to protect data in motion by splitting original data into portions of data, that may be communicated using multiple communications paths.
Owner:SECURITY FIRST INNOVATIONS LLC
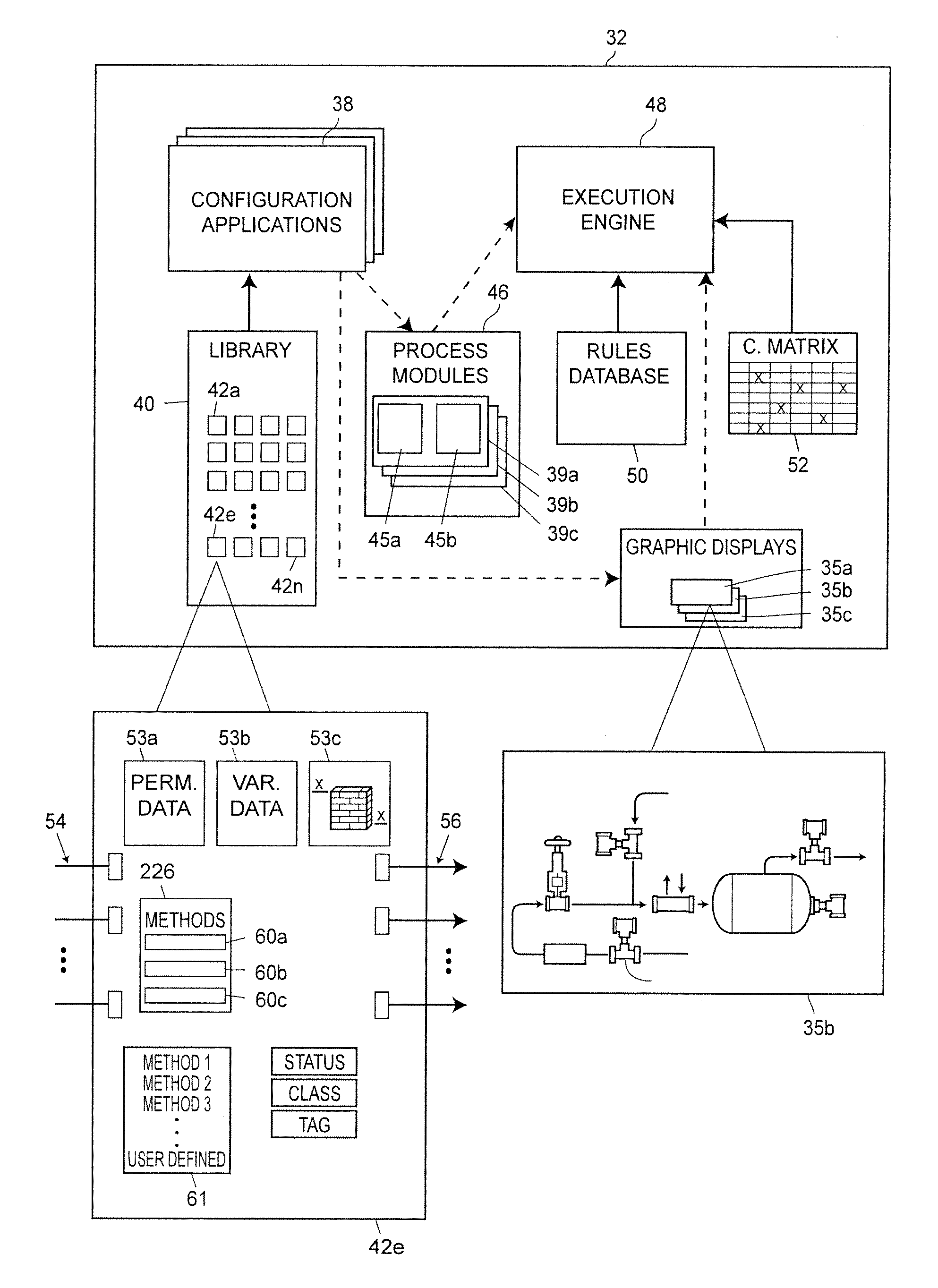
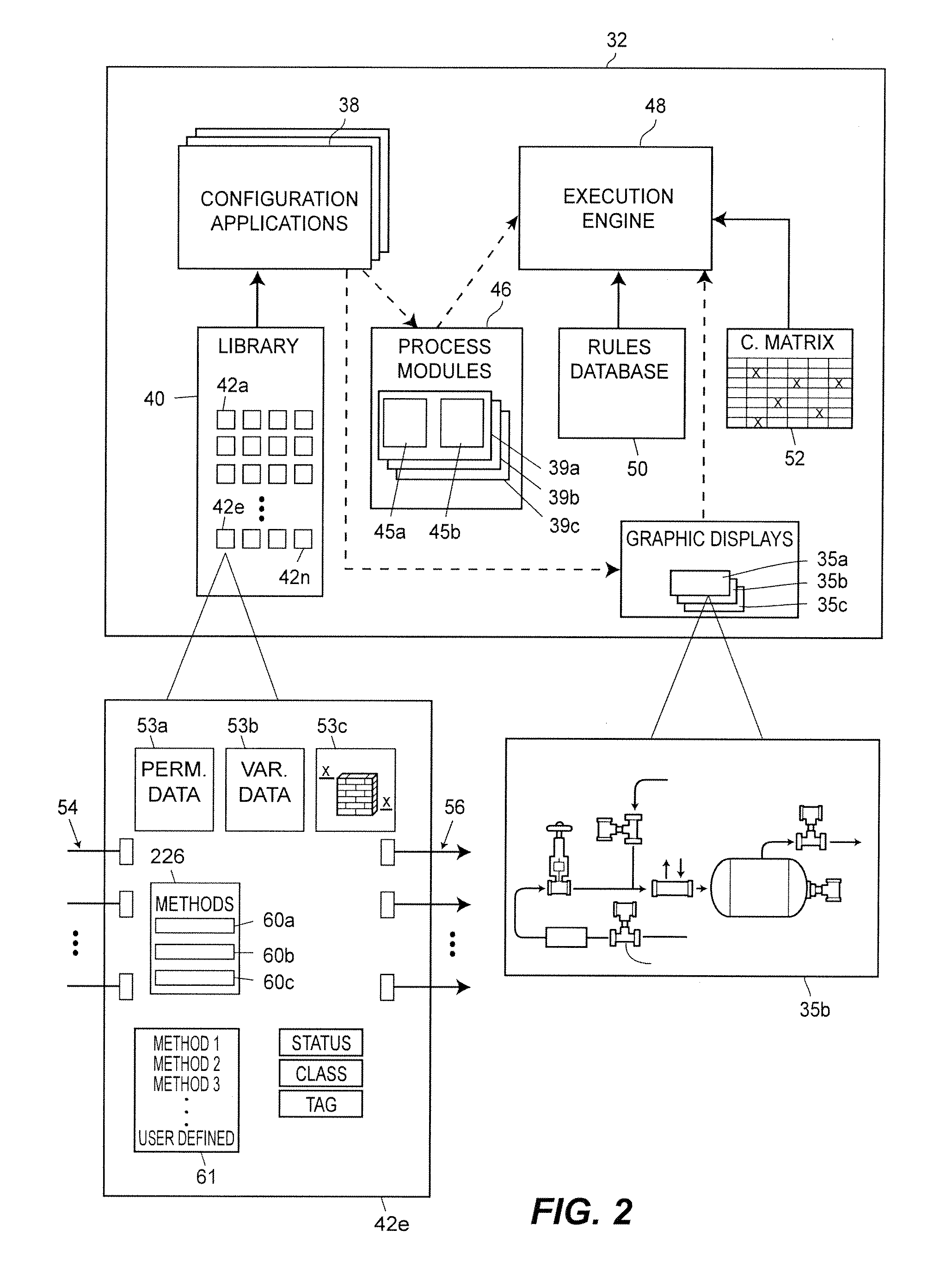
Dynamic User Interface for Configuring and Managing a Process Control System
ActiveUS20120029661A1Reduce the number of timesImprove convenienceElectric controllersIgnition automatic controlControl systemComputerized system
A process control management method in a computer system for configuring and supervising a process plant includes providing an interactive user interface to manage a plurality of objects in the process plant, where each of the plurality of objects corresponds to a physical or logical entity in the process plant, including generating a navigation pane to display a set of selectable items, each in the set of selectable items corresponding to a respective one of the plurality of objects, and generating a command pane to display a set of selectable controls, each in the set of selectable controls corresponding to a task to be performed on at least one of the plurality of objects in the process plant; receiving a selection of one of an item in the set of selectable items via the navigation panel and a control in the set of selectable controls via the command panel; determining an operational context based on the received selection, wherein the operational context corresponds to one of a range of actions applicable to the selection if the selection is an item selection, or a range of items to which the selection is applicable if the selection is a control selection; and adjusting one of the navigation pane or the command pane according to the operational context, including displaying a subset of selectable items in the navigational pane, wherein each in the subset of selectable items is within the range applicable to the selection, if the selection is a control selection, and displaying a subset of selectable controls in the command pane, wherein each in the subset of selectable controls is within the range applicable to the selection, if the selection is an item selection.
Owner:FISHER-ROSEMOUNT SYST INC
Secure data parser method and system
ActiveUS20070160198A1Minimal compute resourceAvoid the needDigital data protectionSecret communicationOriginal dataComputer science
A secure data parser is provided that may be integrated into any suitable system for securely storing and communicating data. The secure data parser parses data and then splits the data into multiple portions that are stored or communicated distinctly. Encryption of the original data, the portions of data, or both may be employed for additional security. The secure data parser may be used to protect data in motion by splitting original data into portions of data, that may be communicated using multiple communications paths.
Owner:SECURITY FIRST INNOVATIONS LLC
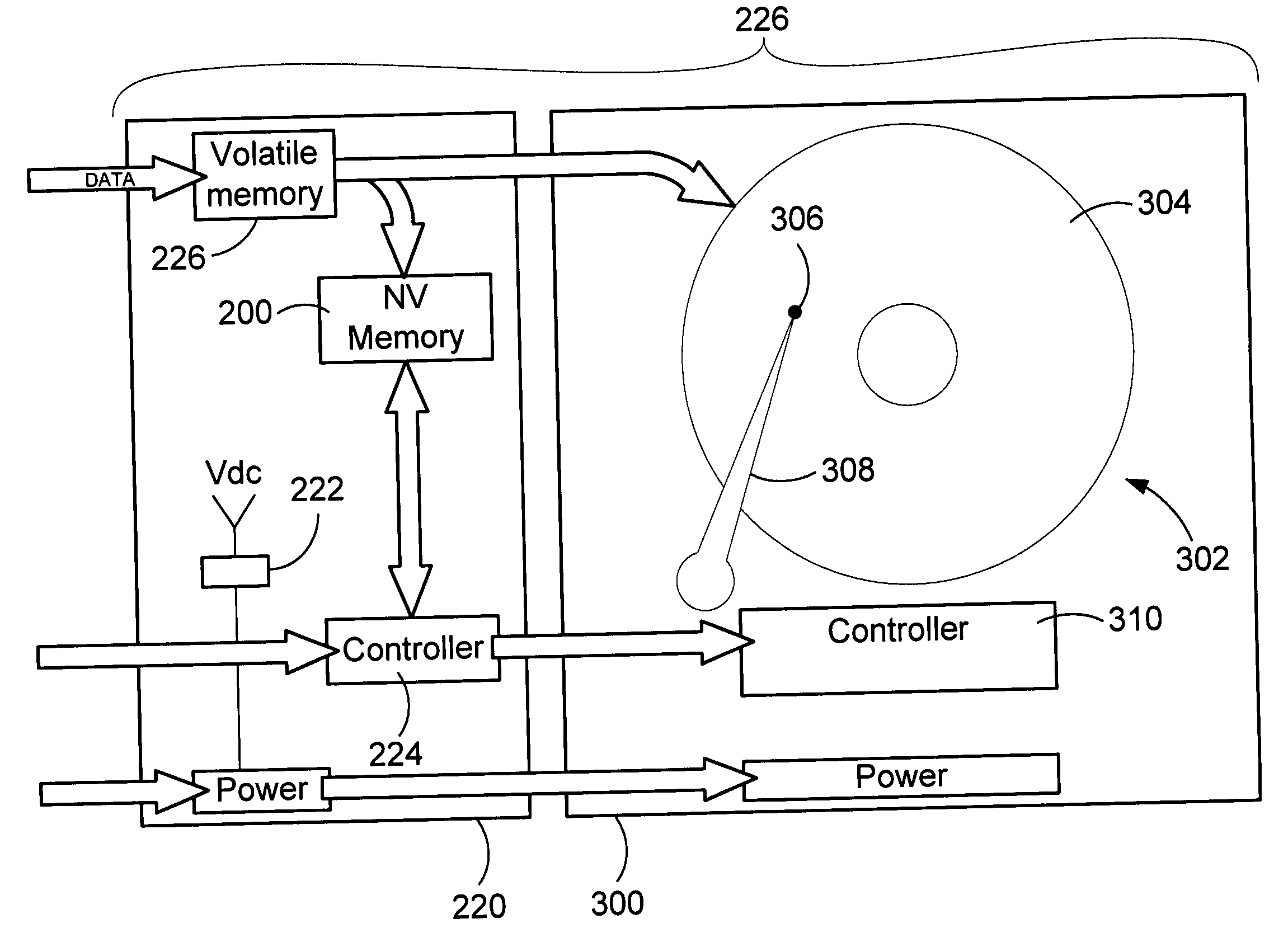
In-line non volatile memory disk read cache and write buffer
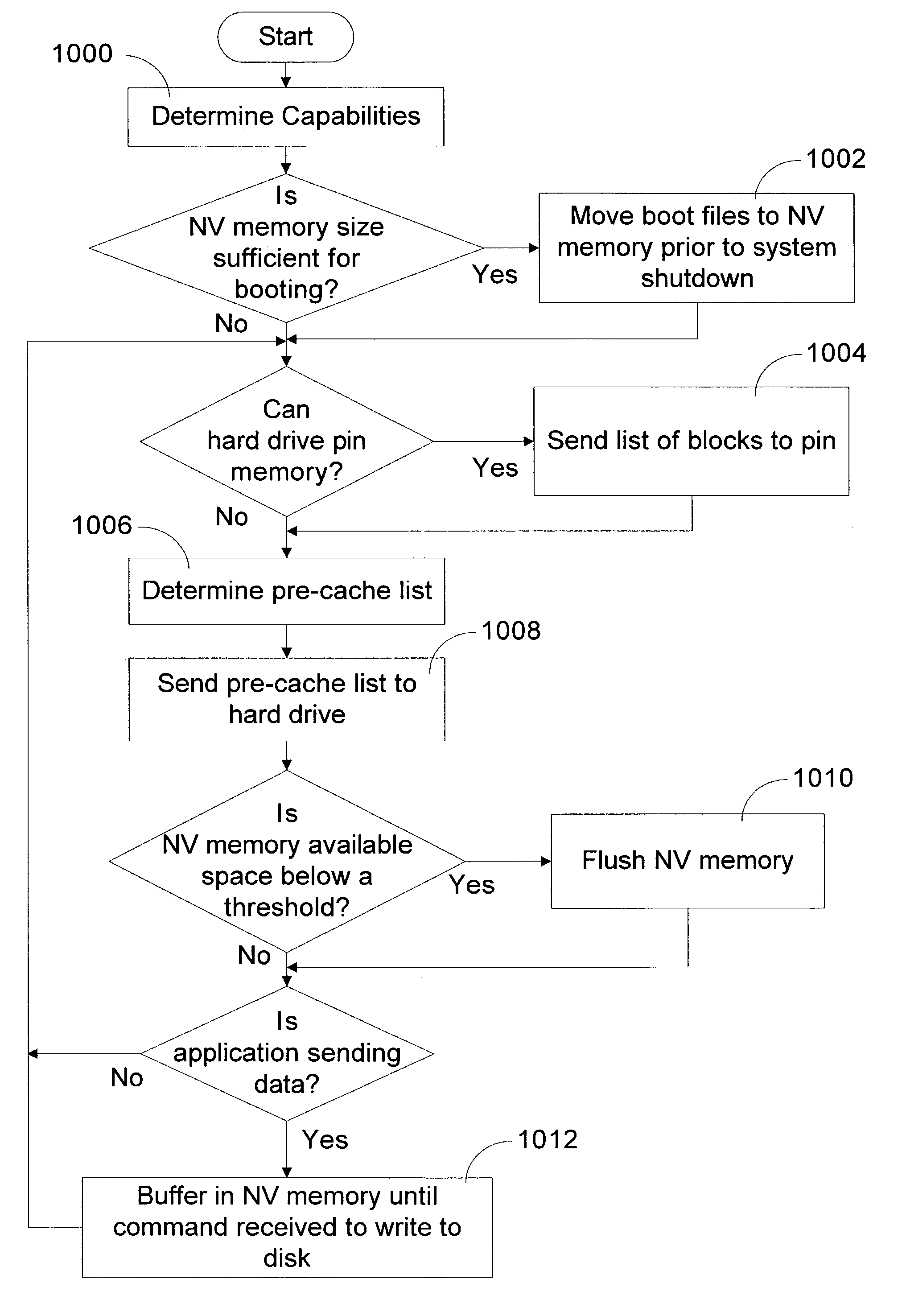
ActiveUS20060248387A1Read/write performance of hardReduce the number of timesData buffering arrangementsError detection/correctionHard disc driveWrite buffer
A method and apparatus to improve the read / write performance of a hard drive is presented. A device having solid state, non-volatile (NV) memory is added in-line to the conventional hard drive and acts as a read / write cache. Data specified by the operating system is stored in the NV memory. The operating system provides a list of data to be put in NV memory. The data includes data to be pinned in NV memory and data that is dynamic. Pinned data persists in NV memory until the operating system commands it to be flushed. Dynamic data can be flushed by the hard drive controller. Data sent by an application for storage is temporarily stored in NV memory in data blocks until the operating system commits it to the disk.
Owner:MICROSOFT TECH LICENSING LLC
Secure data parser method and system
InactiveUS7391865B2Minimal compute resourceAvoid the needDigital data processing detailsUser identity/authority verificationGovernmental agencyVariospora
The present invention provides a method and system for securing sensitive data from unauthorized access or use. The method and system of the present invention is useful in a wide variety of settings, including commercial settings generally available to the public which may be extremely large or small with respect to the number of users. The method and system of the present invention is also useful in a more private setting, such as with a corporation or governmental agency, as well as between corporation, governmental agencies or any other entity.
Owner:SECURITY FIRST INNOVATIONS LLC
Systems and methods for securing data using multi-factor or keyed dispersal
ActiveUS20090177894A1Minimal compute resourceAvoid the needUnauthorized memory use protectionHardware monitoringInformation dispersalOriginal data
A secure data parser is provided that may be integrated into any suitable system for securely storing and communicating data. The secure data parser parses data and then splits the data into multiple portions that are stored or communicated distinctly. Encryption of the original data, the portions of data, or both may be employed for additional security. The secure data parser may be used to protect data in motion by splitting original data into portions of data, that may be communicated using multiple communications paths. A keyed information dispersal algorithm (keyed IDA) may also be used. The key for the keyed IDA may additionally be protected by an external workgroup key, resulting in a multi-factor secret sharing scheme.
Owner:SECURITY FIRST INNOVATIONS LLC
Systems and methods for managing cryptographic keys
ActiveUS20090097661A1Minimal compute resourceAvoid the needKey distribution for secure communicationDigital data processing detailsPublic interfaceComputer hardware
A common interface for managing cryptographic keys is provided. A request to manage a cryptographic key may be received in a first interface format, translated to a common interface format, and then executed remotely from the first interface. Return arguments may then be translated from the common interface format to a format compatible with the first interface and communicated securely to the first interface. The cryptographic keys may be used in connection with a secure data parser that secures data by randomly distributing data within a data set into two or more shares.
Owner:SECURITY FIRST INNOVATIONS LLC
Secure data parser method and system
InactiveUS20080244277A1Minimal compute resourceAvoid the needEncryption apparatus with shift registers/memoriesDigital data processing detailsGovernmental agencyVariospora
The present invention provides a method and system for securing sensitive data from unauthorized access or use. The method and system of the present invention is useful in a wide variety of settings, including commercial settings generally available to the public which may be extremely large or small with respect to the number of users. The method and system of the present invention is also useful in a more private setting, such as with a corporation or governmental agency, as well as between corporation, governmental agencies or any other entity.
Owner:SECURITY FIRST INNOVATIONS LLC
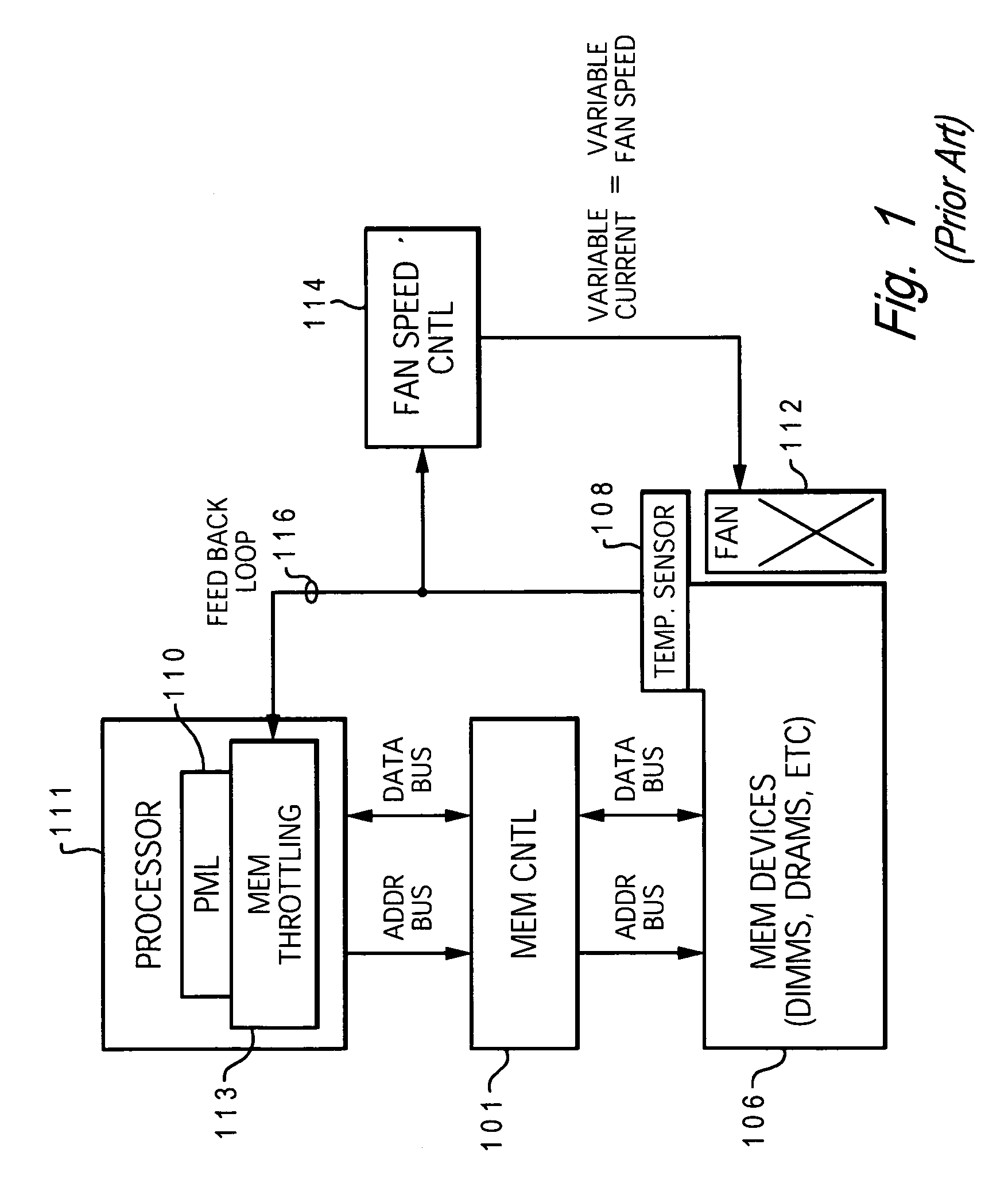
Dynamic power management via DIMM read operation limiter
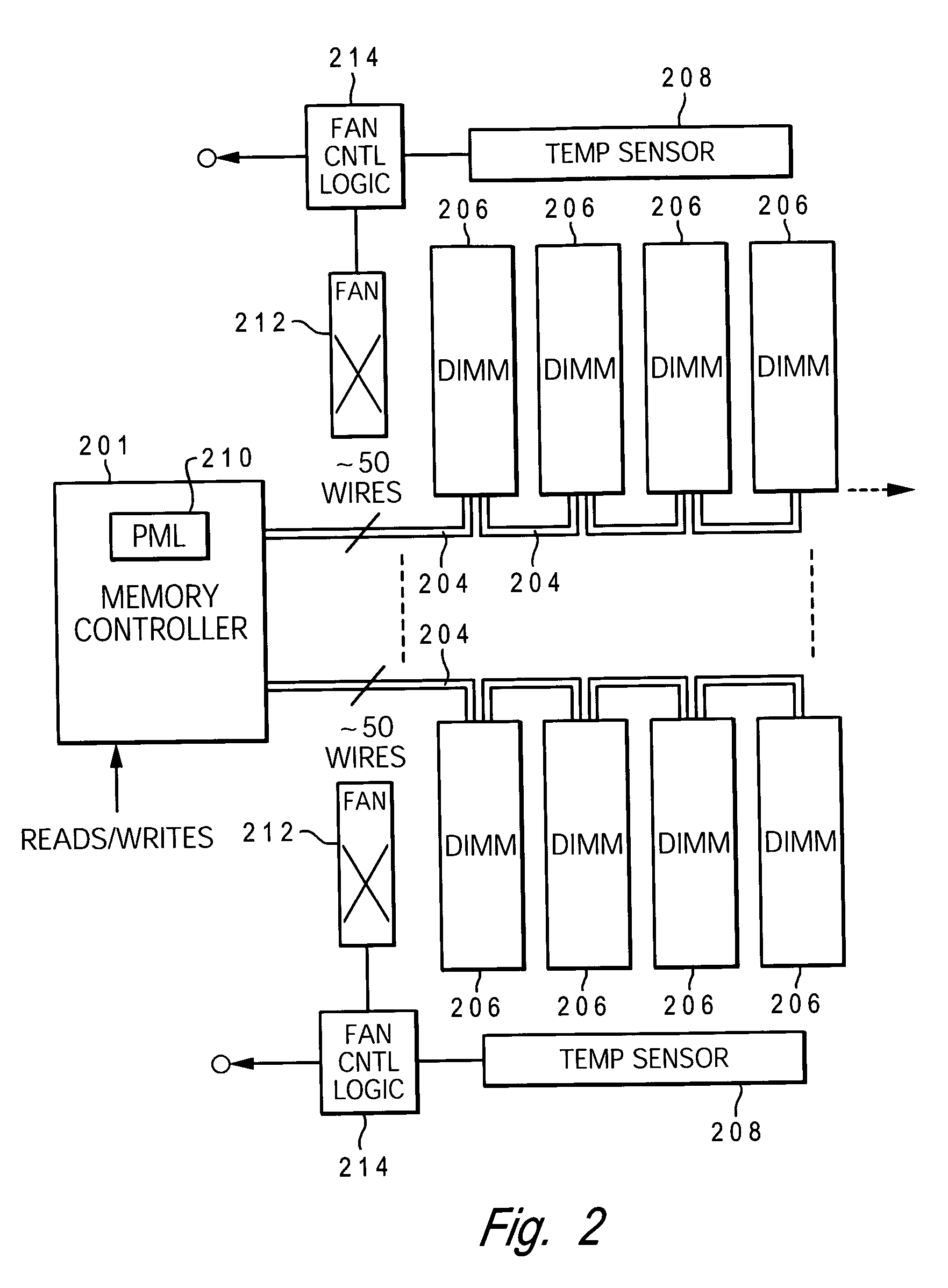
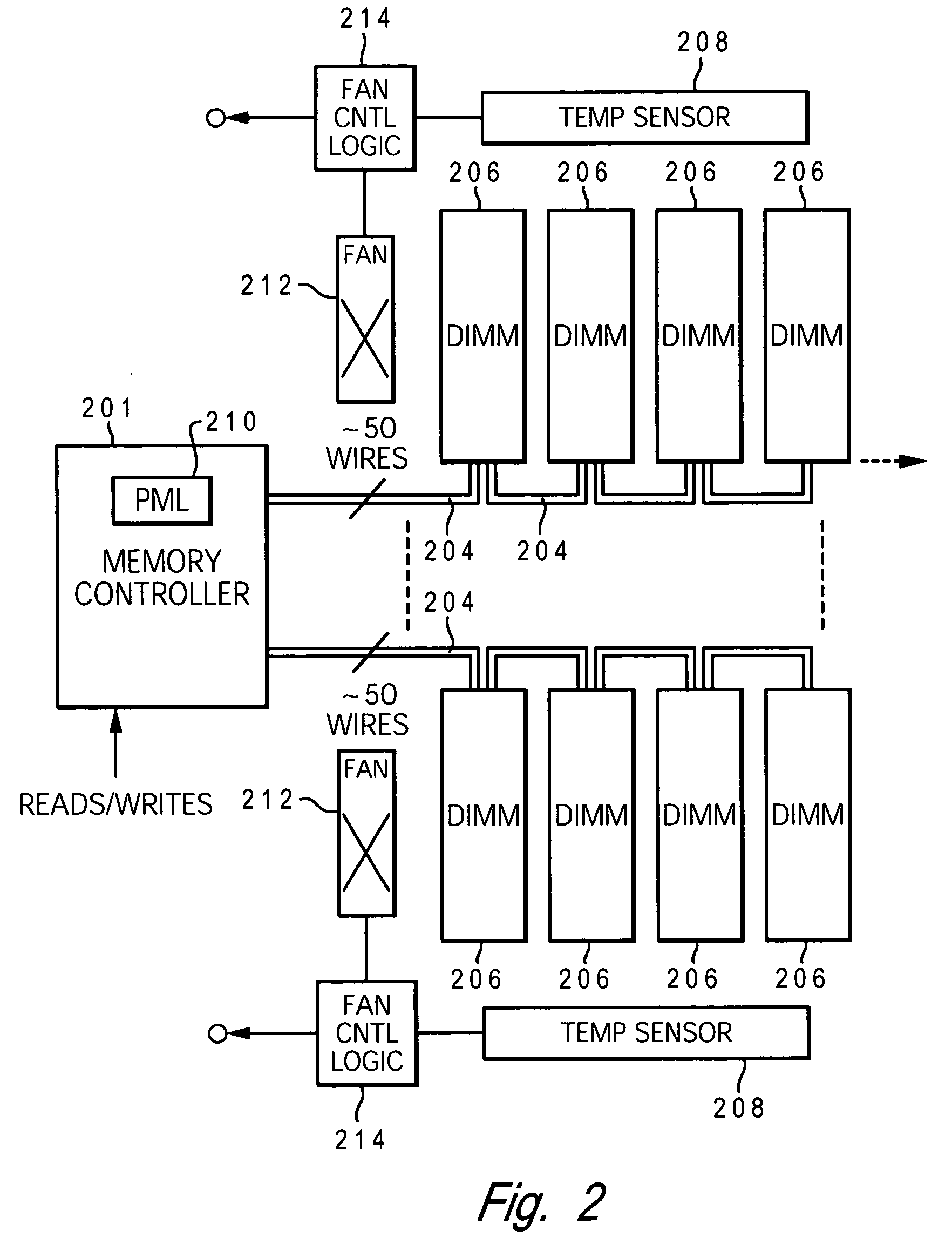
InactiveUS20060179334A1Little or no usePower usageEnergy efficient ICTVolume/mass flow measurementDIMMDynamic power management
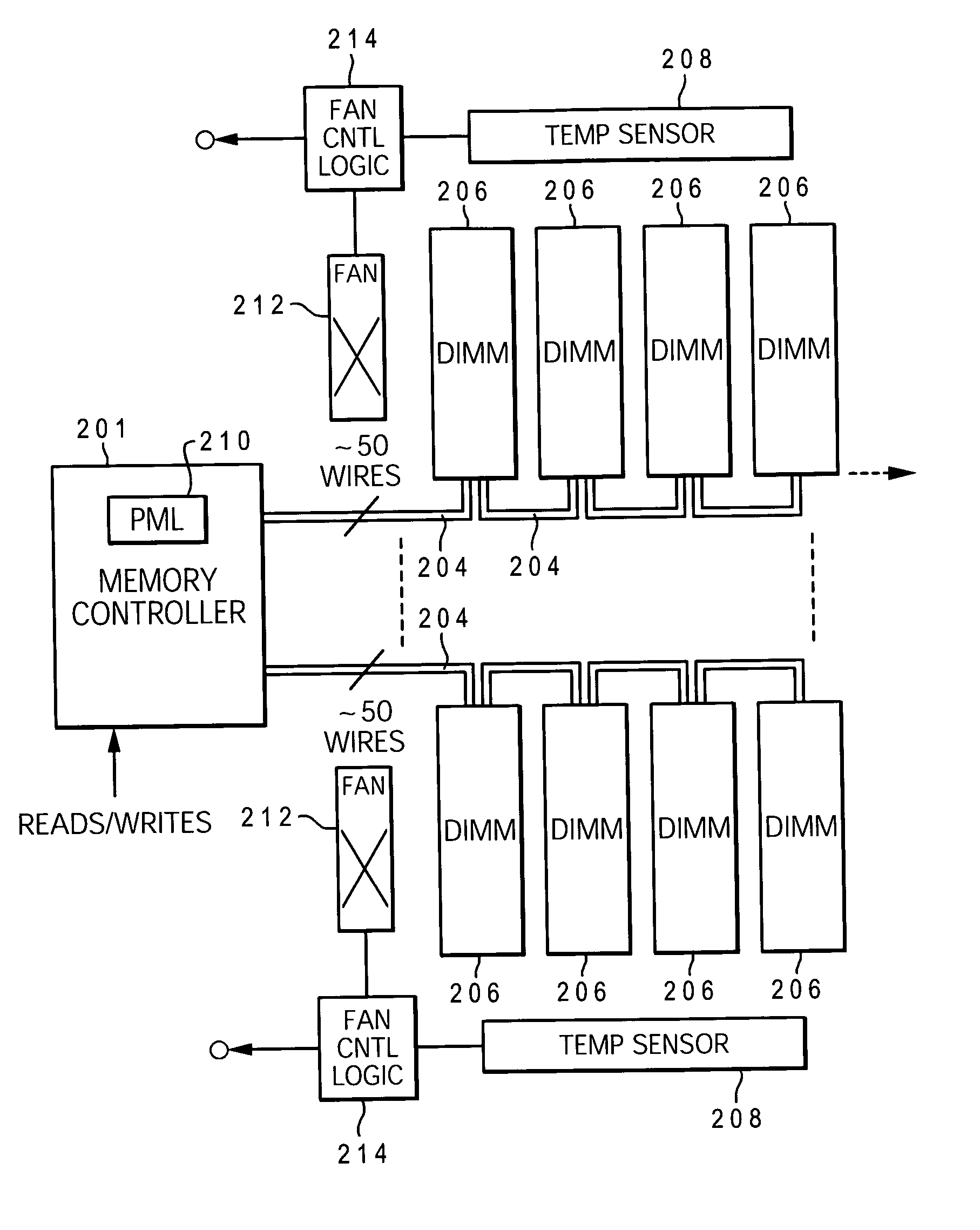
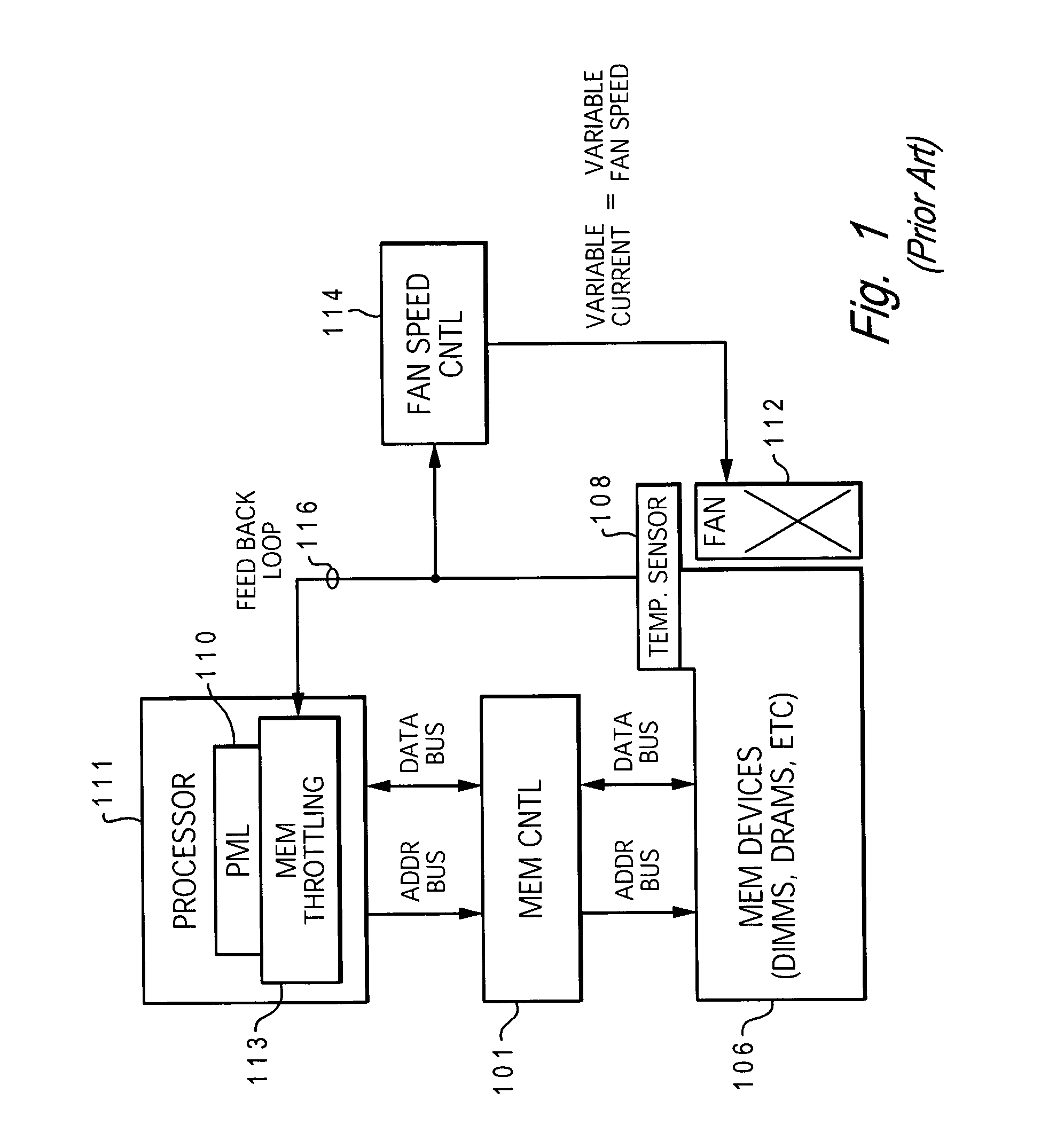
A method and system for enabling directed temperature / power management at the DIMM-level and / or DRAM-level utilizing intelligent scheduling of memory access operations received at the memory controller. Hot spots within the memory subsystem, caused by operating the DIMMs / DRAMs above predetermined / preset threshold power / temperature values for operating a DIMM and / or a DRAM, are avoided / controlled by logic within the memory controller. The memory controller logic throttles the number / frequency at which commands (read / write operations) are issued to the specific DIMM / DRAM based on feedback data received from the specific DIMM / DRAM reaching the preset threshold power usage value.
Owner:IBM CORP
Method and apparatus to reduce power consumption and improve read/write performance of hard disk drives using non-volatile memory
InactiveUS7082495B2Read/write performance of hardReduce the number of timesEnergy efficient ICTInput/output to record carriersHard disc driveOperational system
A method and apparatus to improve the read / write performance of a hard drive is presented. The hard drive includes solid state, non-volatile (NV) memory as a read / write cache. Data specified by the operating system is stored in the NV memory. The operating system provides a list of data to be put in NV memory. The data includes data to be pinned in NV memory and data that is dynamic. Pinned data persists in NV memory until the operating system commands it to be flushed. Dynamic data can be flushed by the hard drive controller. Data sent by an application for storage is temporary stored in NV memory in data blocks until the operating system commits it to the disk.
Owner:MICROSOFT TECH LICENSING LLC
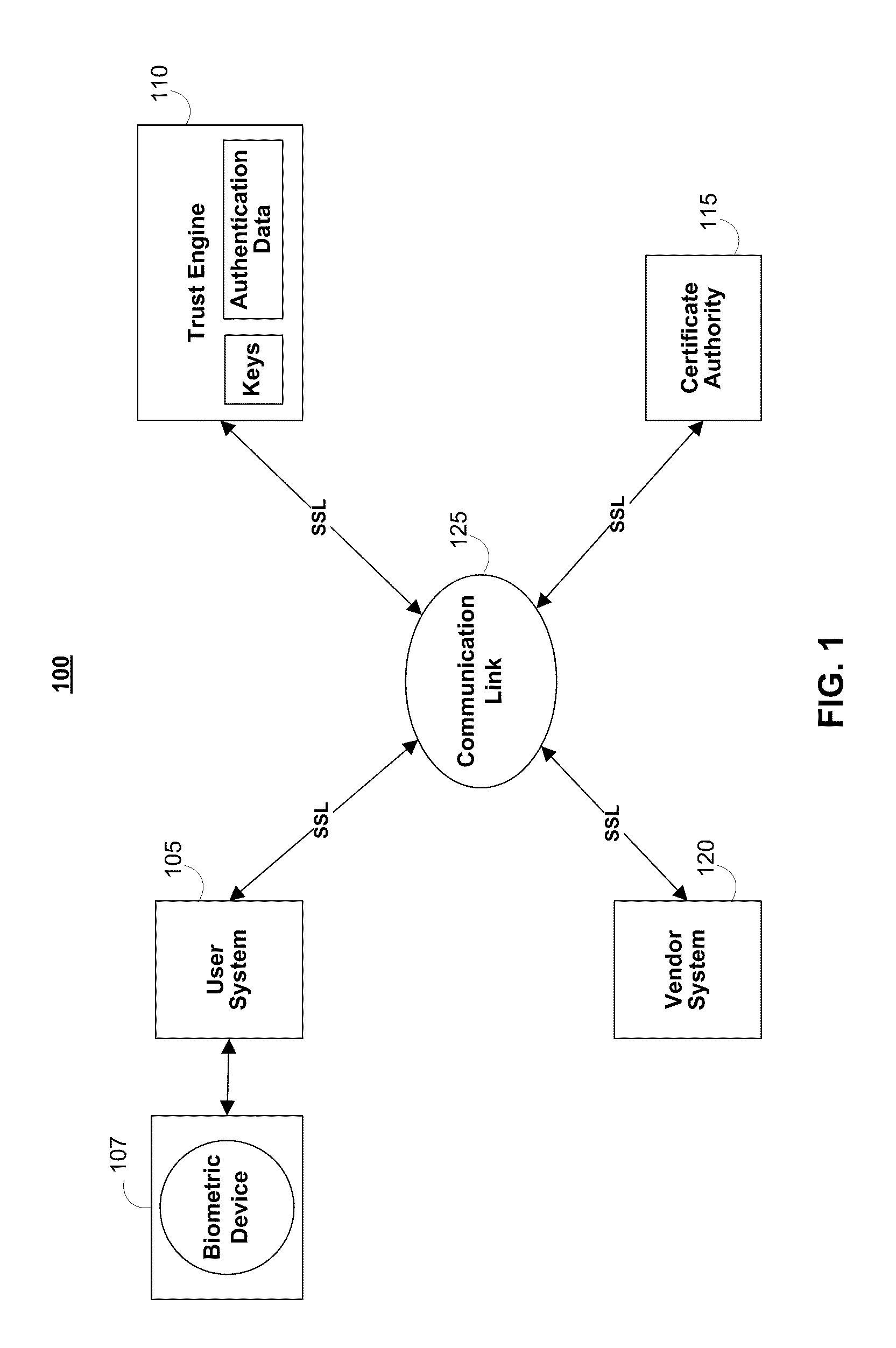
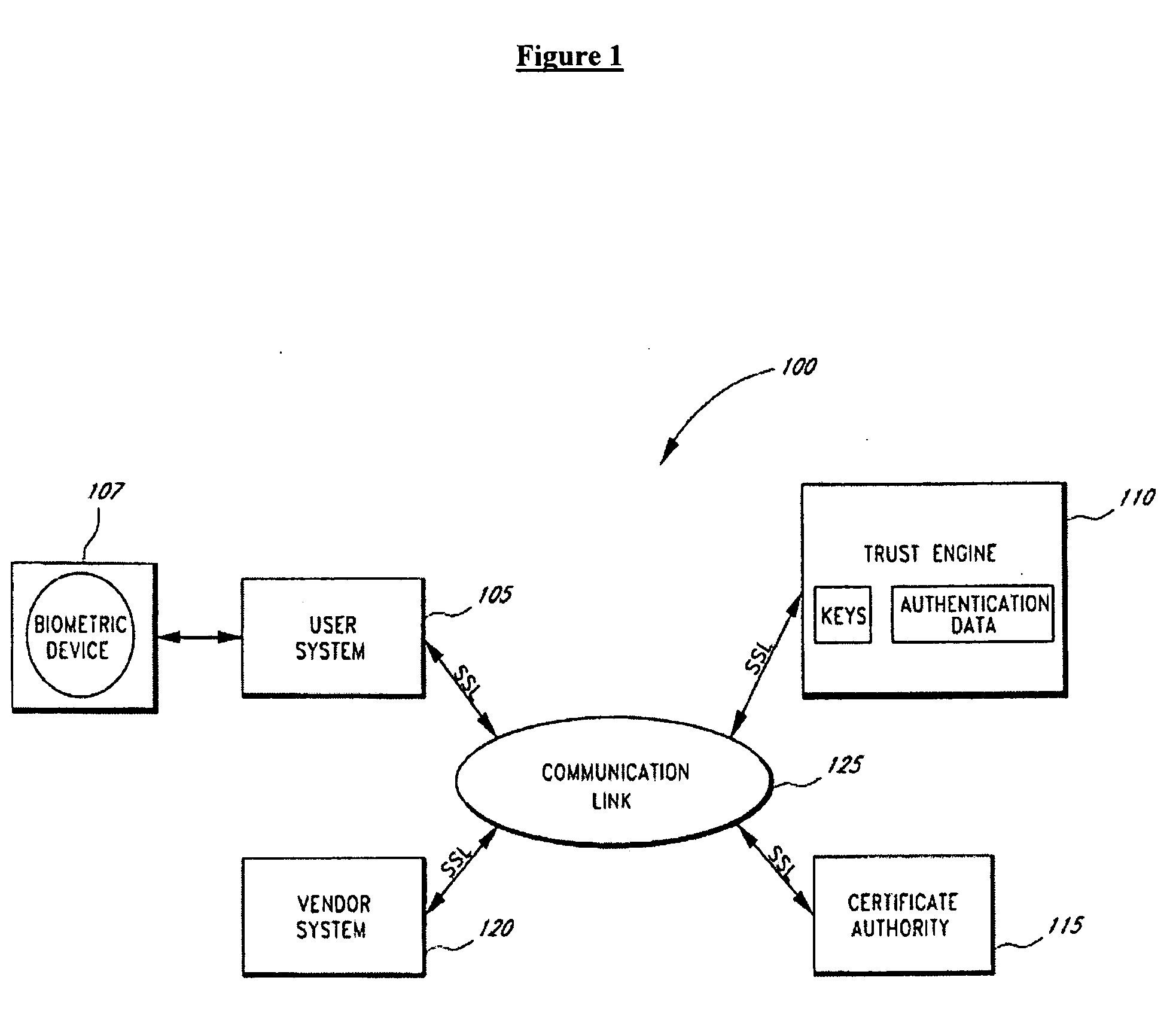
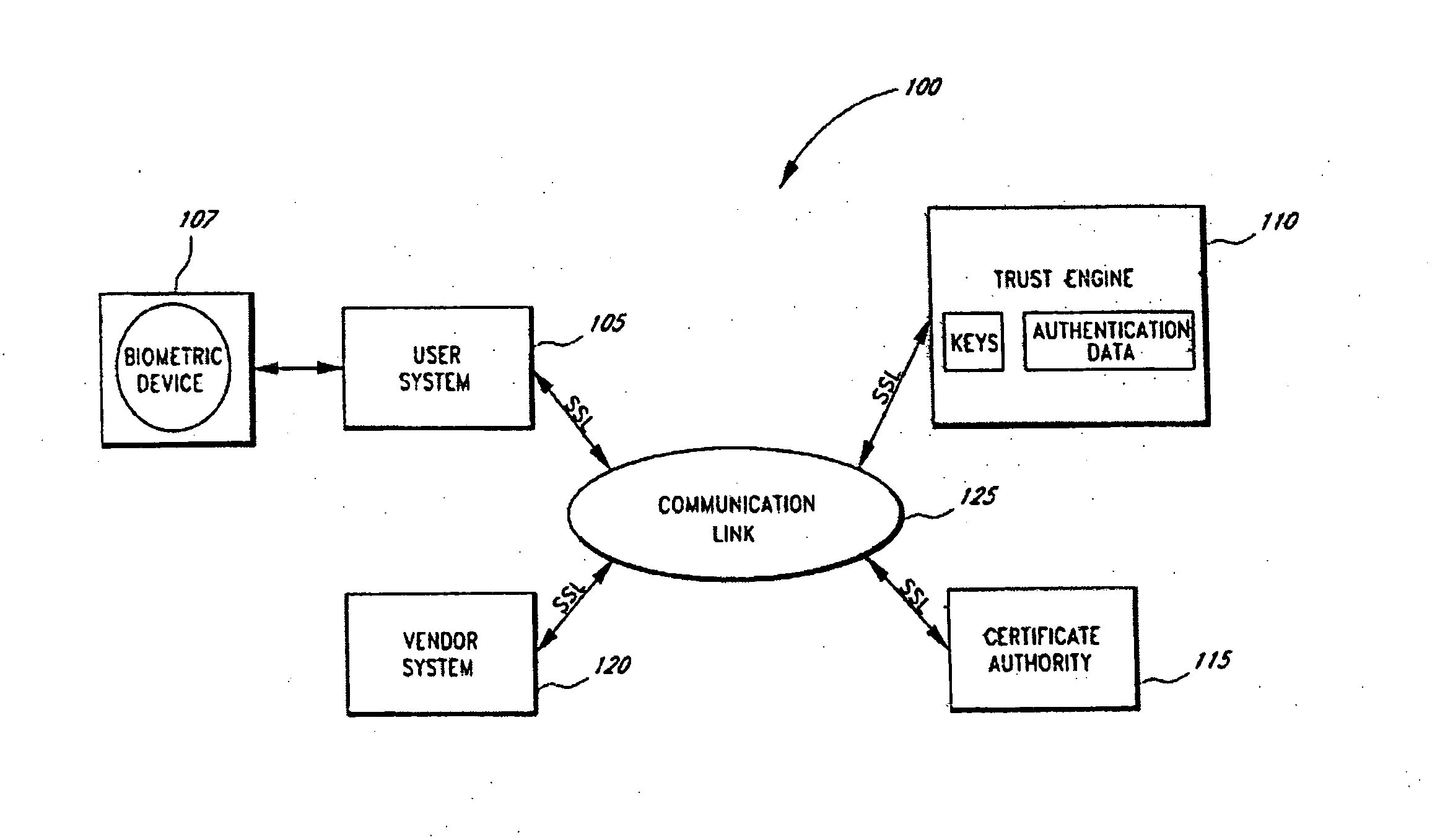
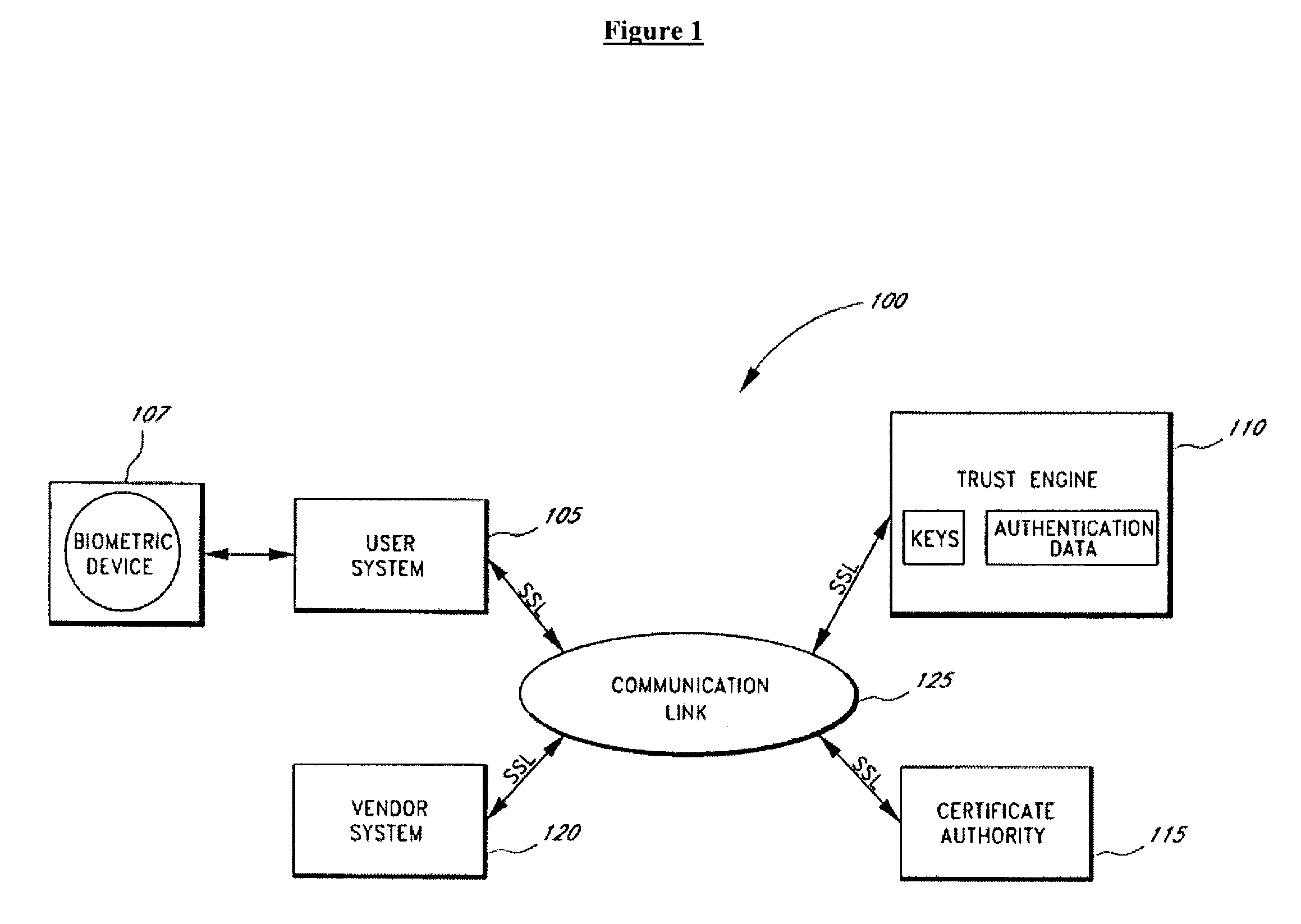
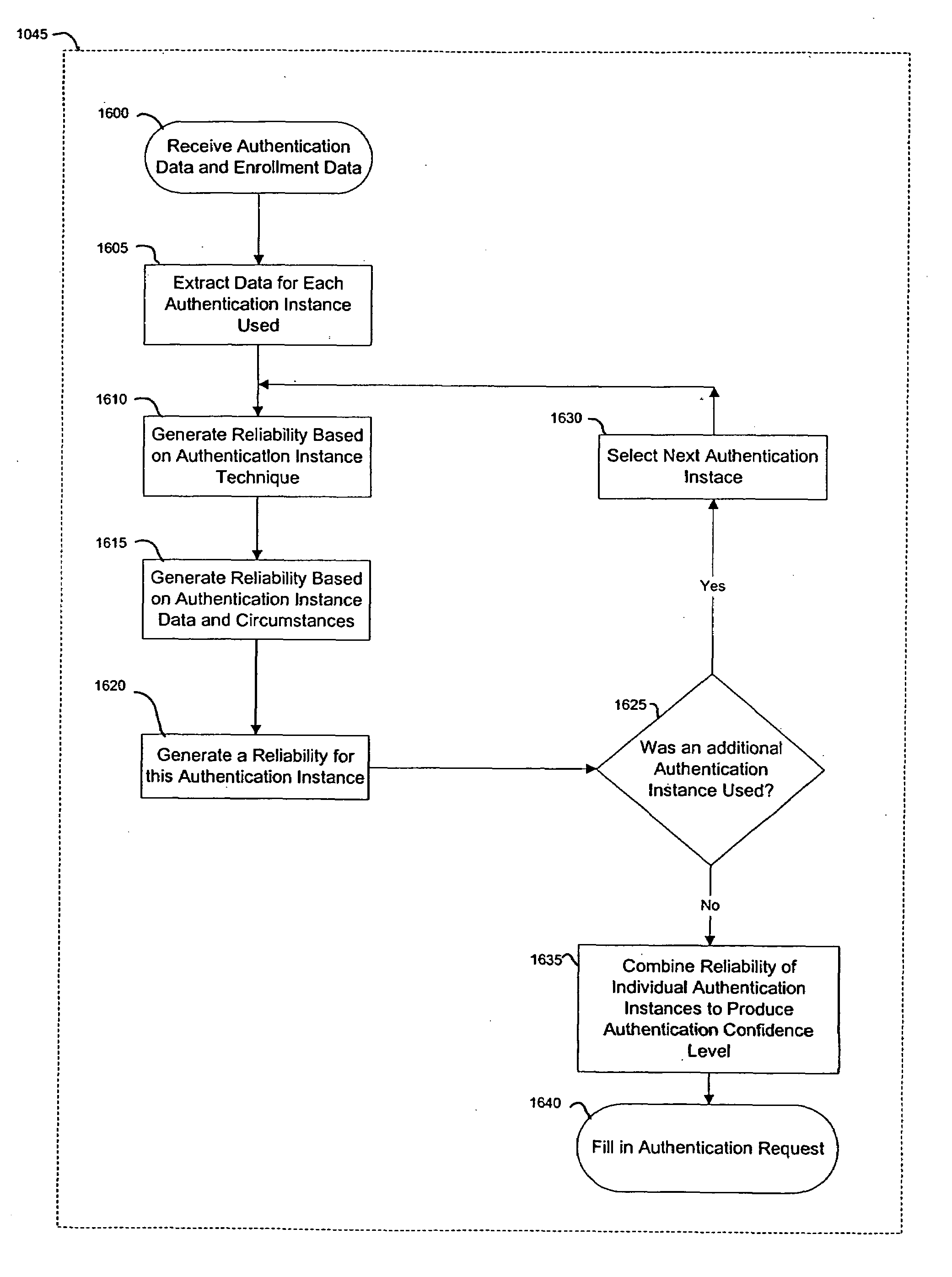
Context sensitive dynamic authentication in a cryptographic system
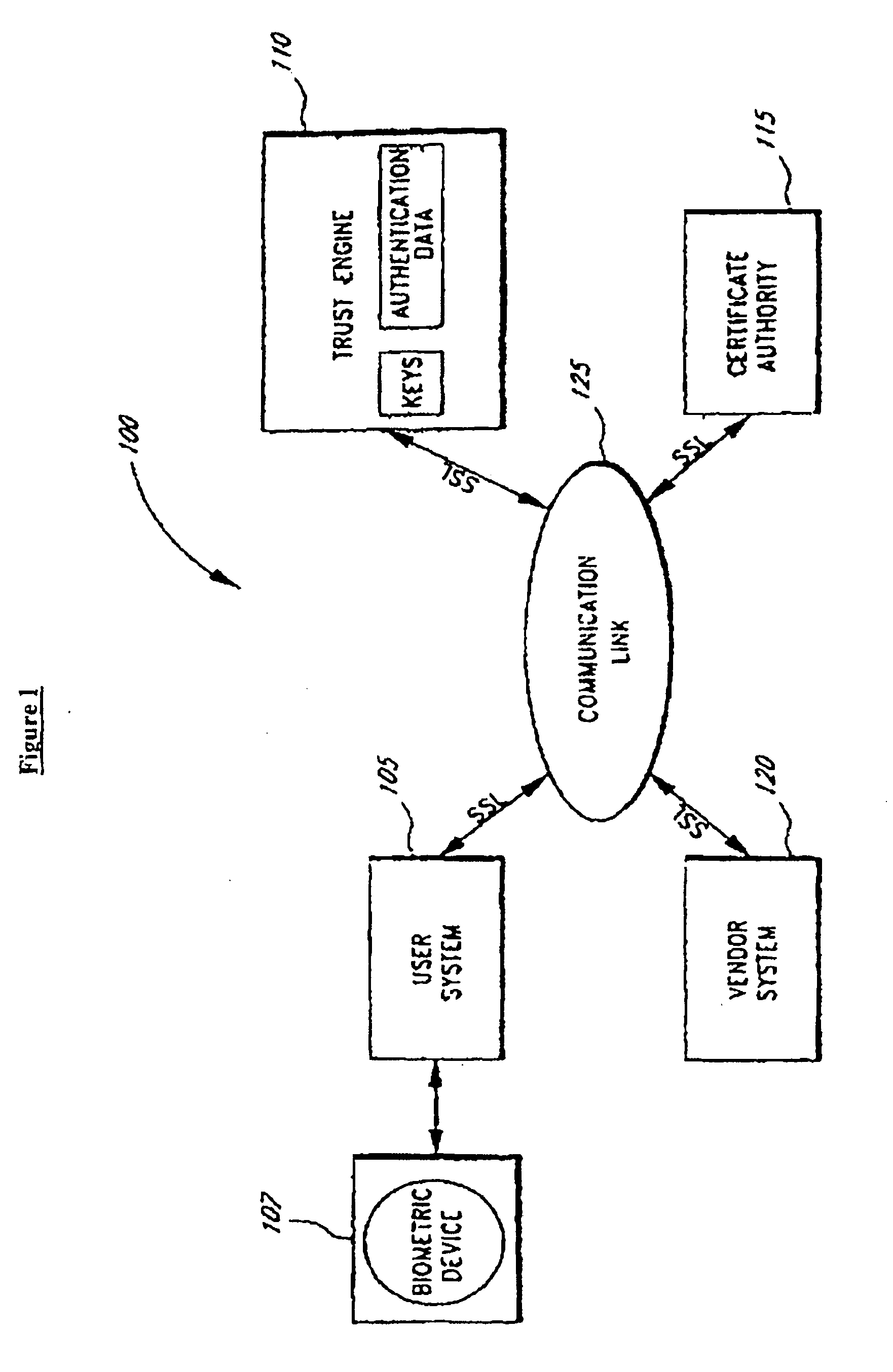
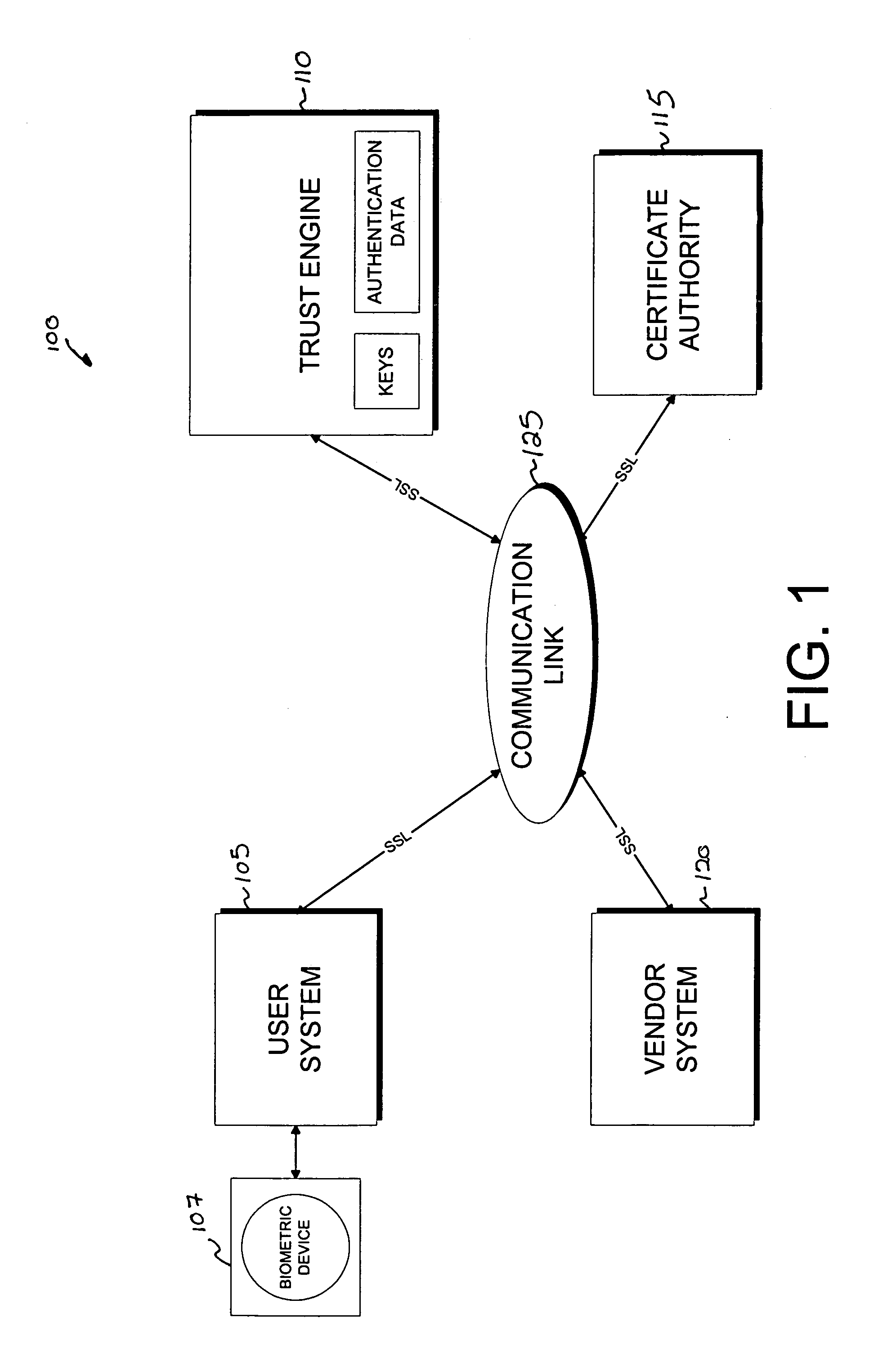
InactiveUS7260724B1Minimal compute resourceAvoid the needUser identity/authority verificationComputer security arrangementsInternet privacyTrust level
A system for performing authentication of a first user to a second user includes the ability for the first user to submit multiple instances of authentication data which are evaluated and then used to generate an overall level of confidence in the claimed identity of the first user. The individual authentication instances are evaluated based upon: the degree of match between the user provided by the first user during the authentication and the data provided by the first user during his enrollment; the inherent reliability of the authentication technique being used; the circumstances surrounding the generation of the authentication data by the first user; and the circumstances surrounding the generation of the enrollment data by the first user. This confidence level is compared with a required trust level which is based at least in part upon the requirements of the second user, and the authentication result is based upon this comparison.
Owner:SECURITY FIRST INNOVATIONS LLC
Tape backup method
InactiveUS20080183992A1Minimal compute resourceAvoid the needMemory architecture accessing/allocationMemory loss protectionOriginal dataMagnetic tape
A secure data parser is provided that may be integrated into any suitable system for securely storing and communicating data. The secure data parser parses data and then splits the data into multiple portions that are stored or communicated distinctly. Encryption of the original data, the portions of data, or both may be employed for additional security. The secure data parser may be used to protect data in motion by splitting original data into portions of data, that may be communicated using multiple communications paths.
Owner:SECURITY FIRST INNOVATIONS LLC
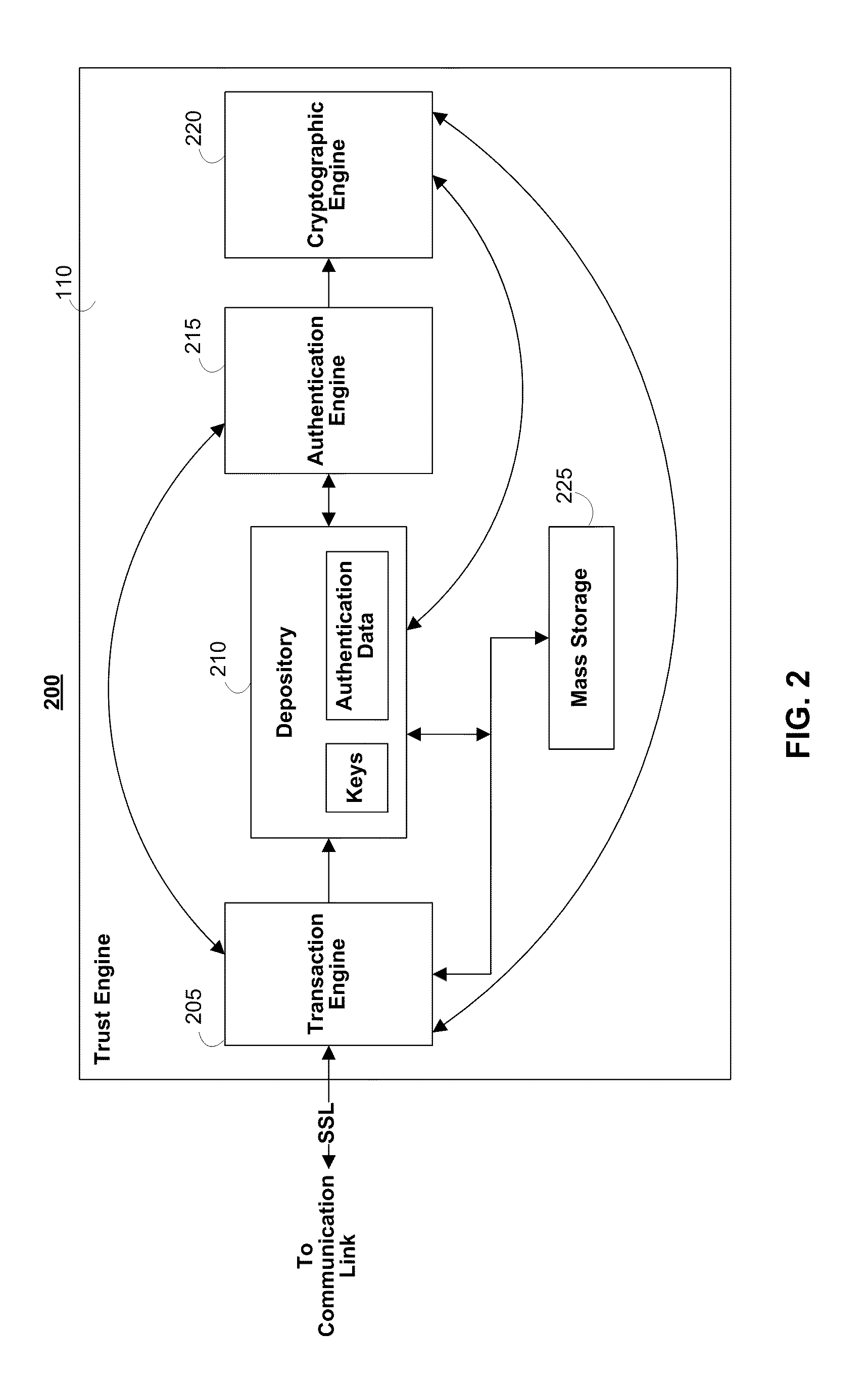
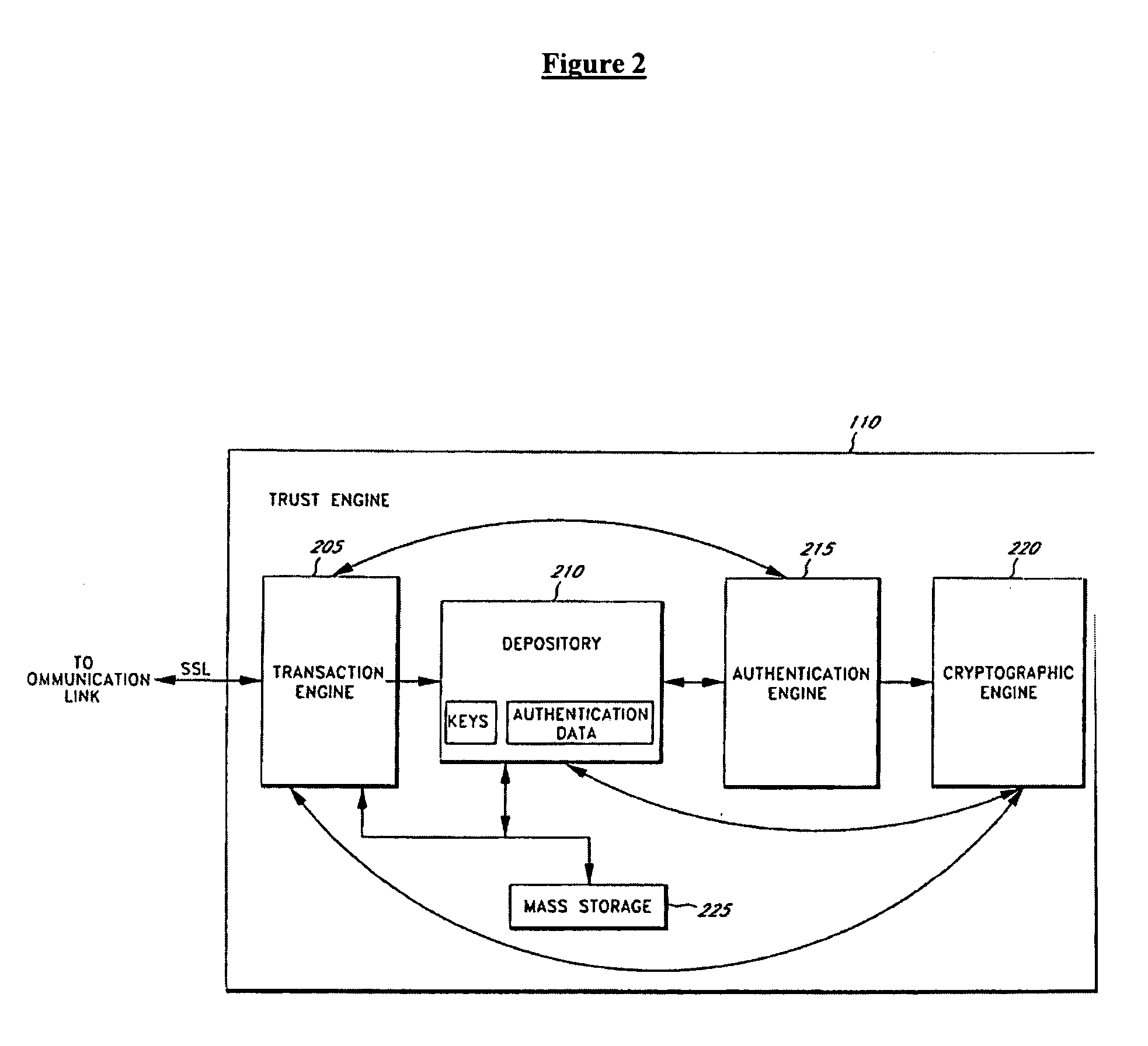
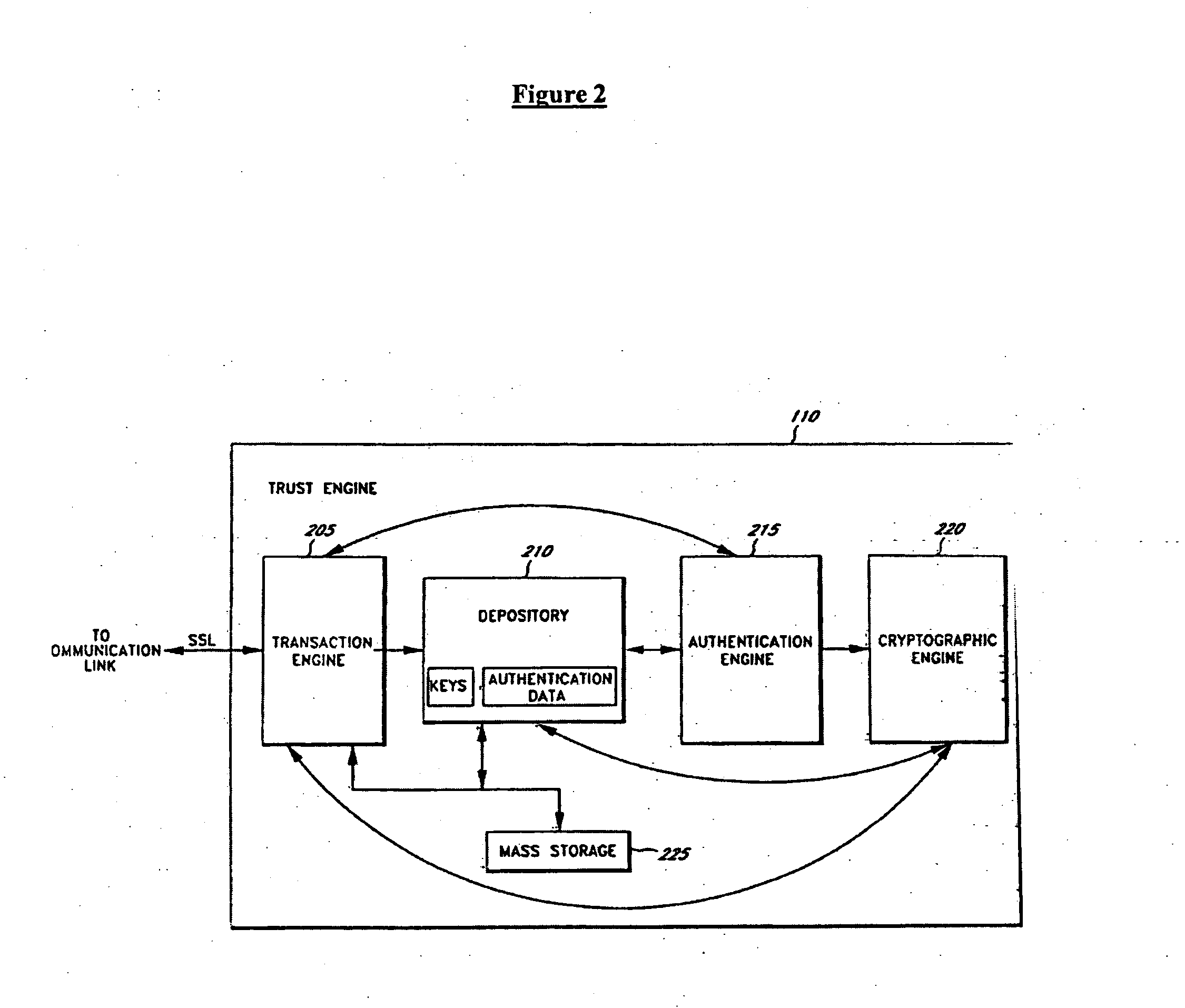
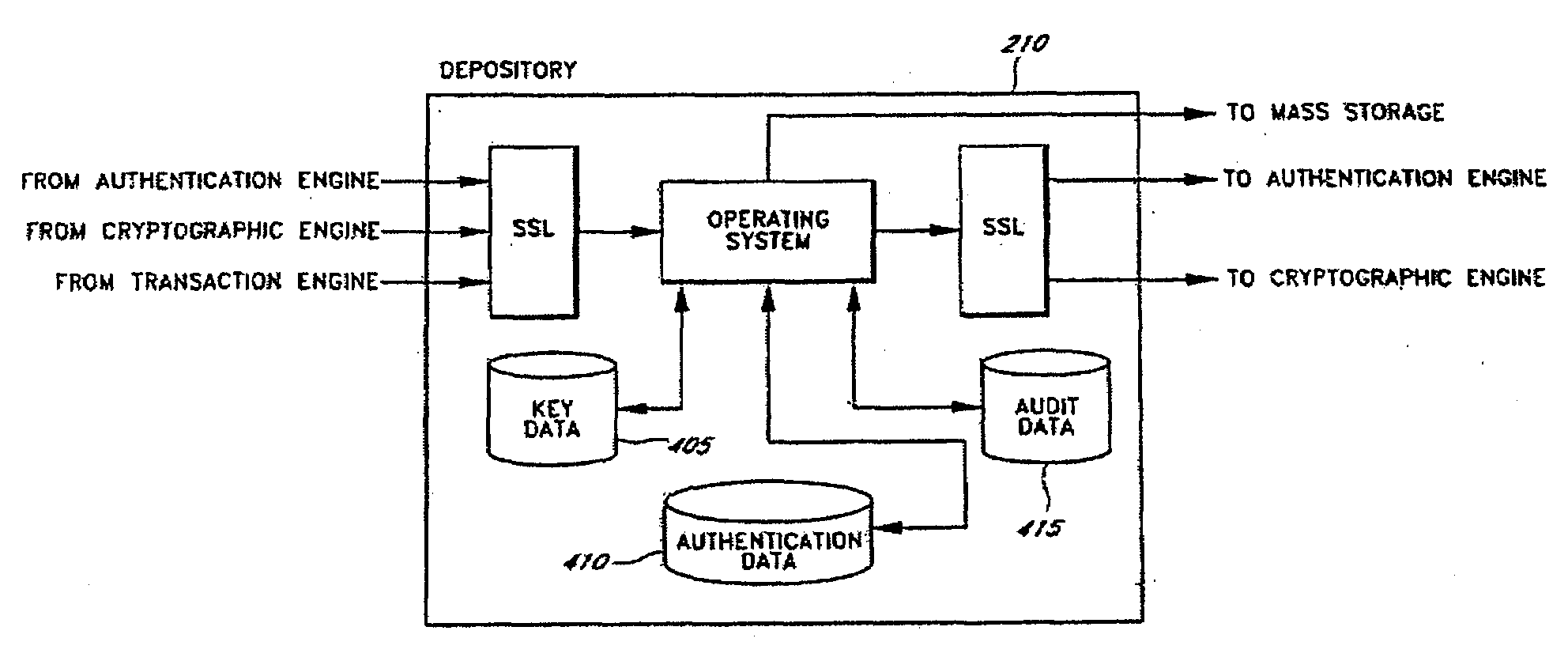
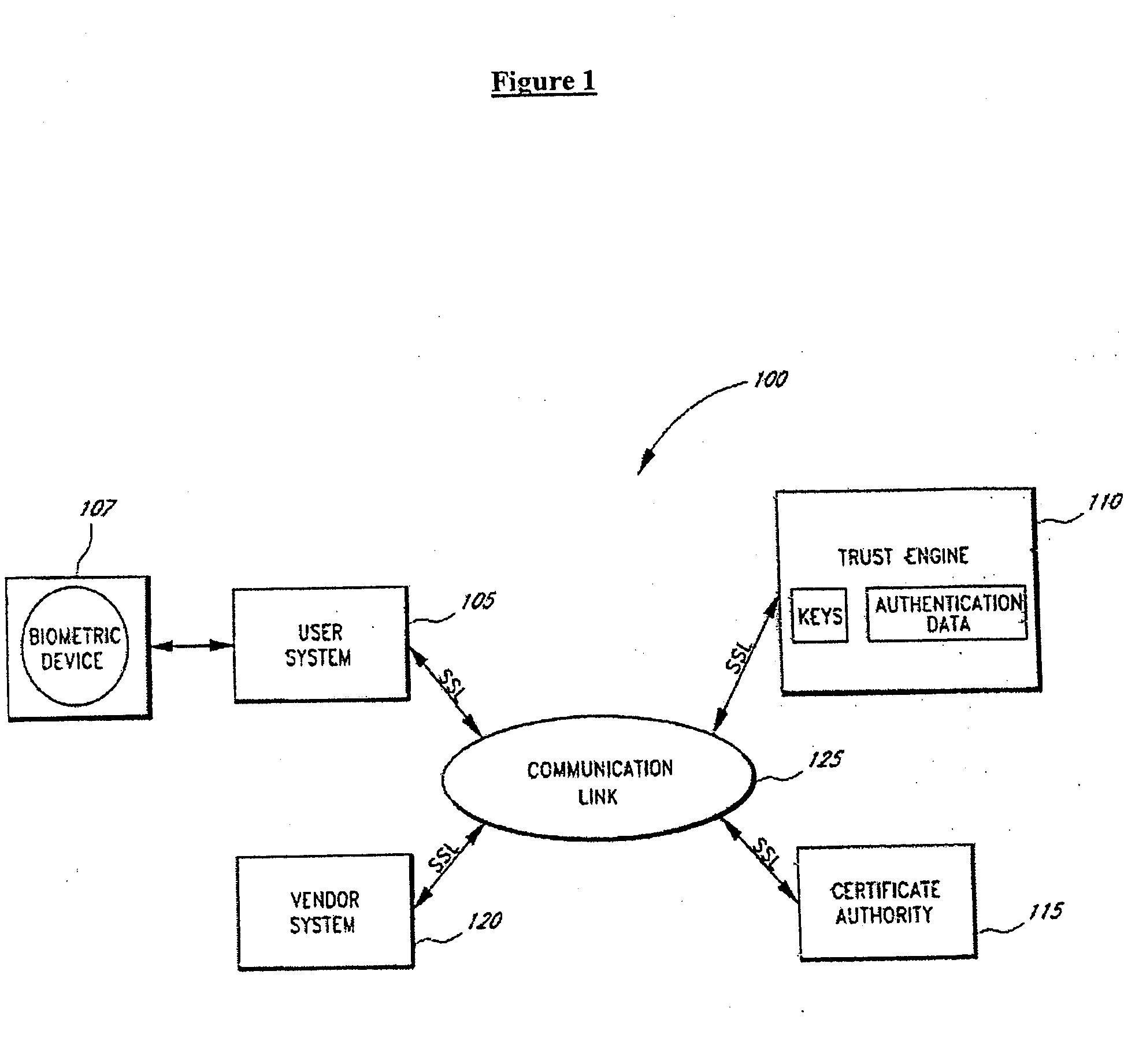
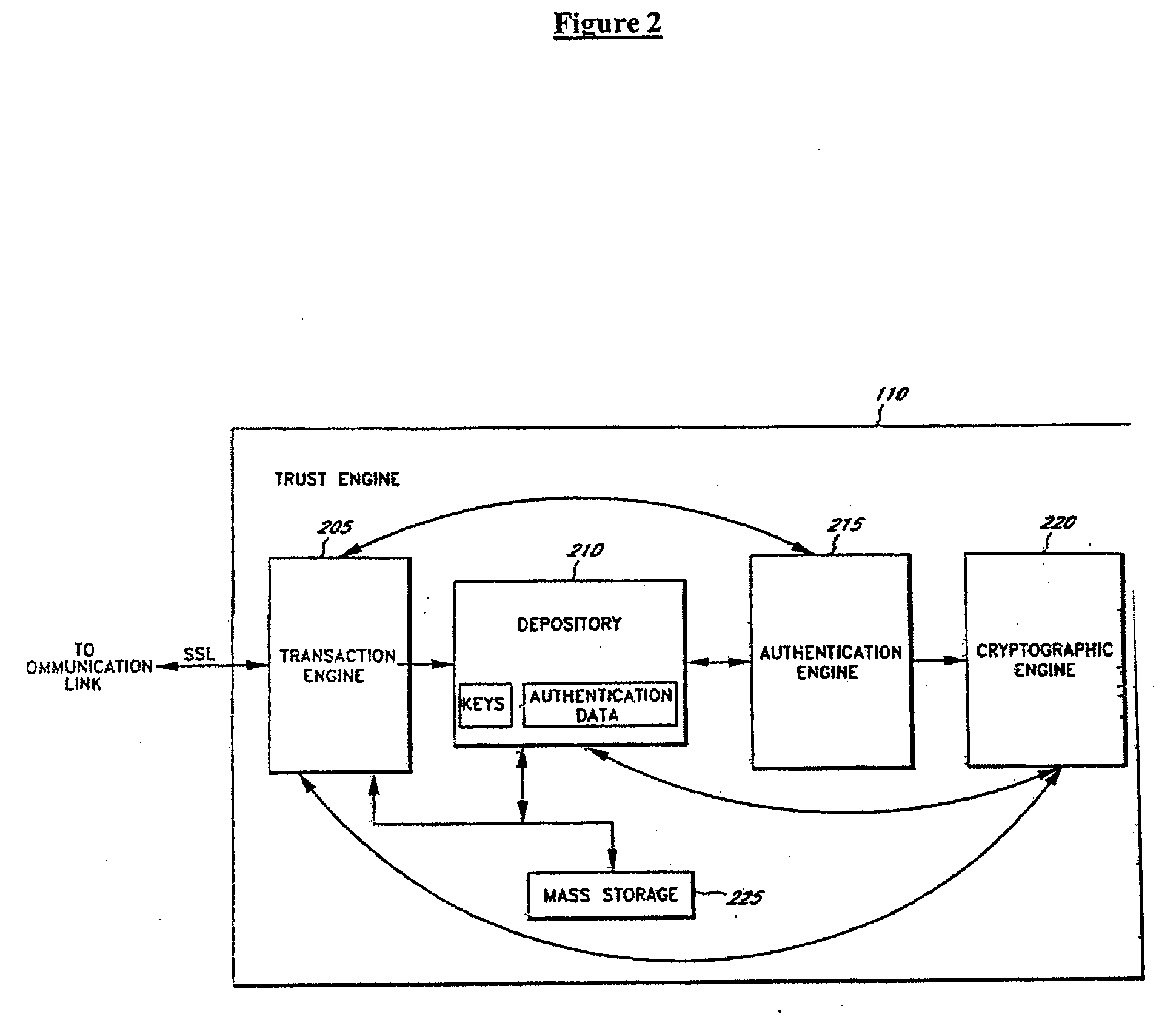
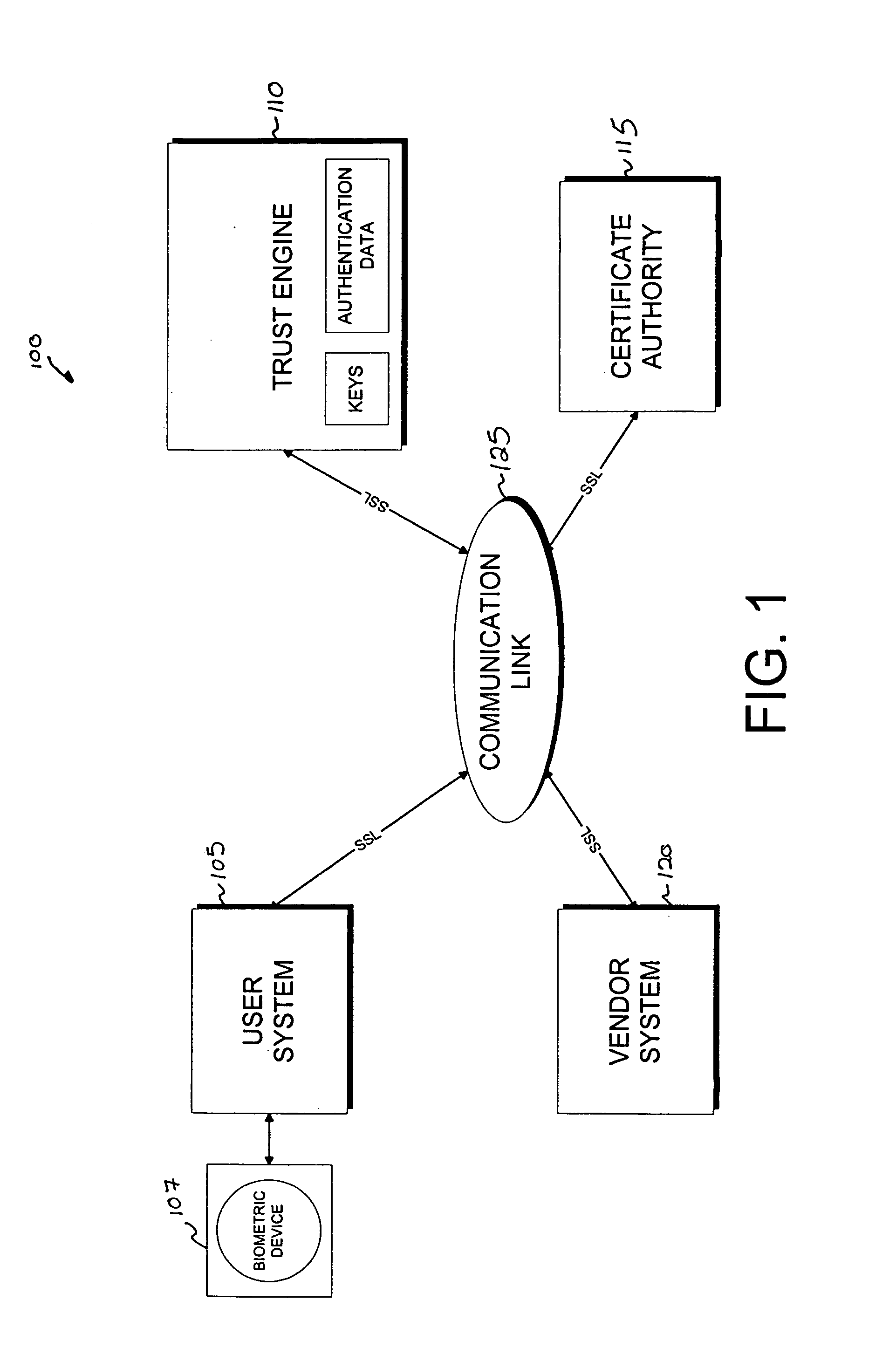
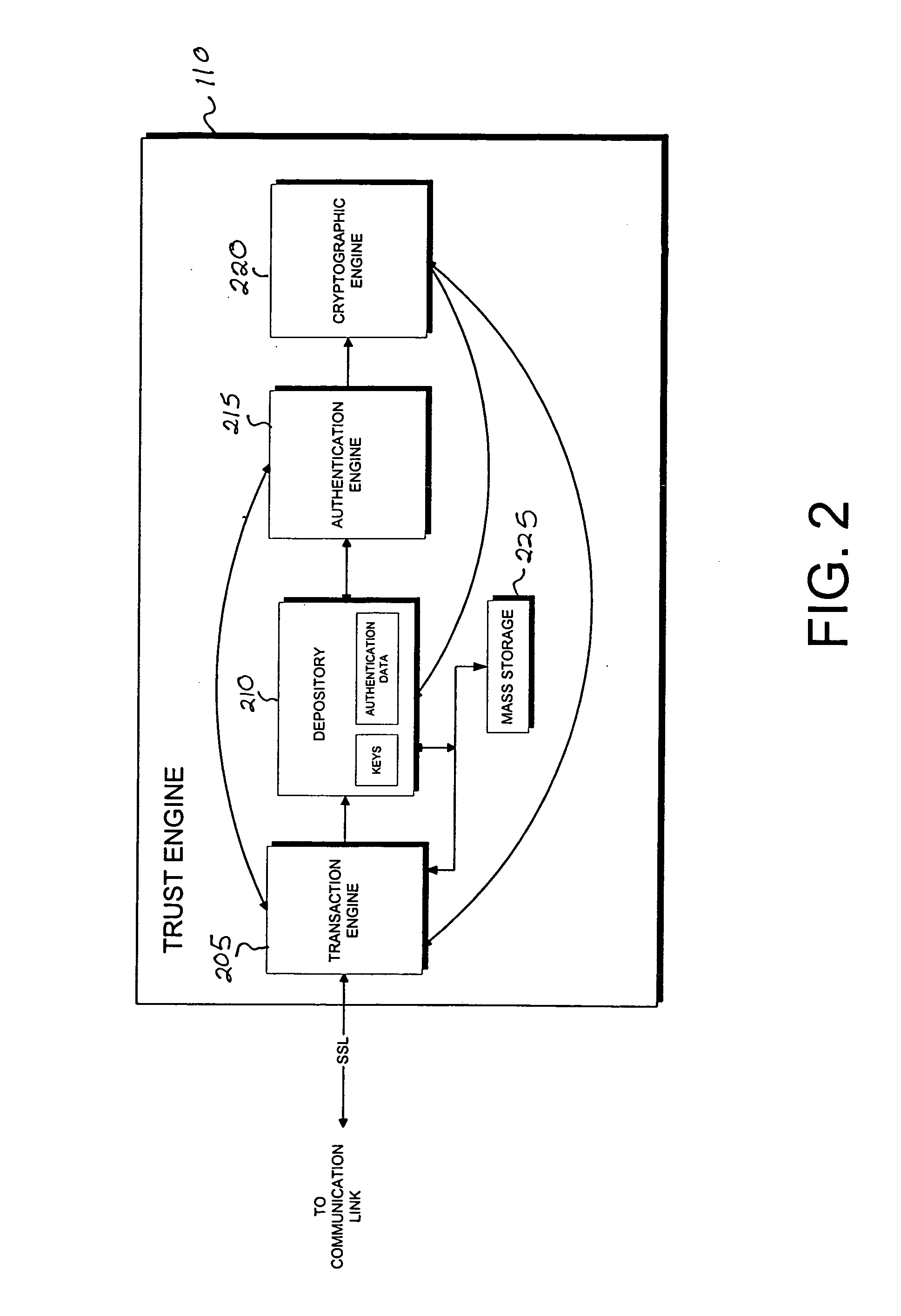
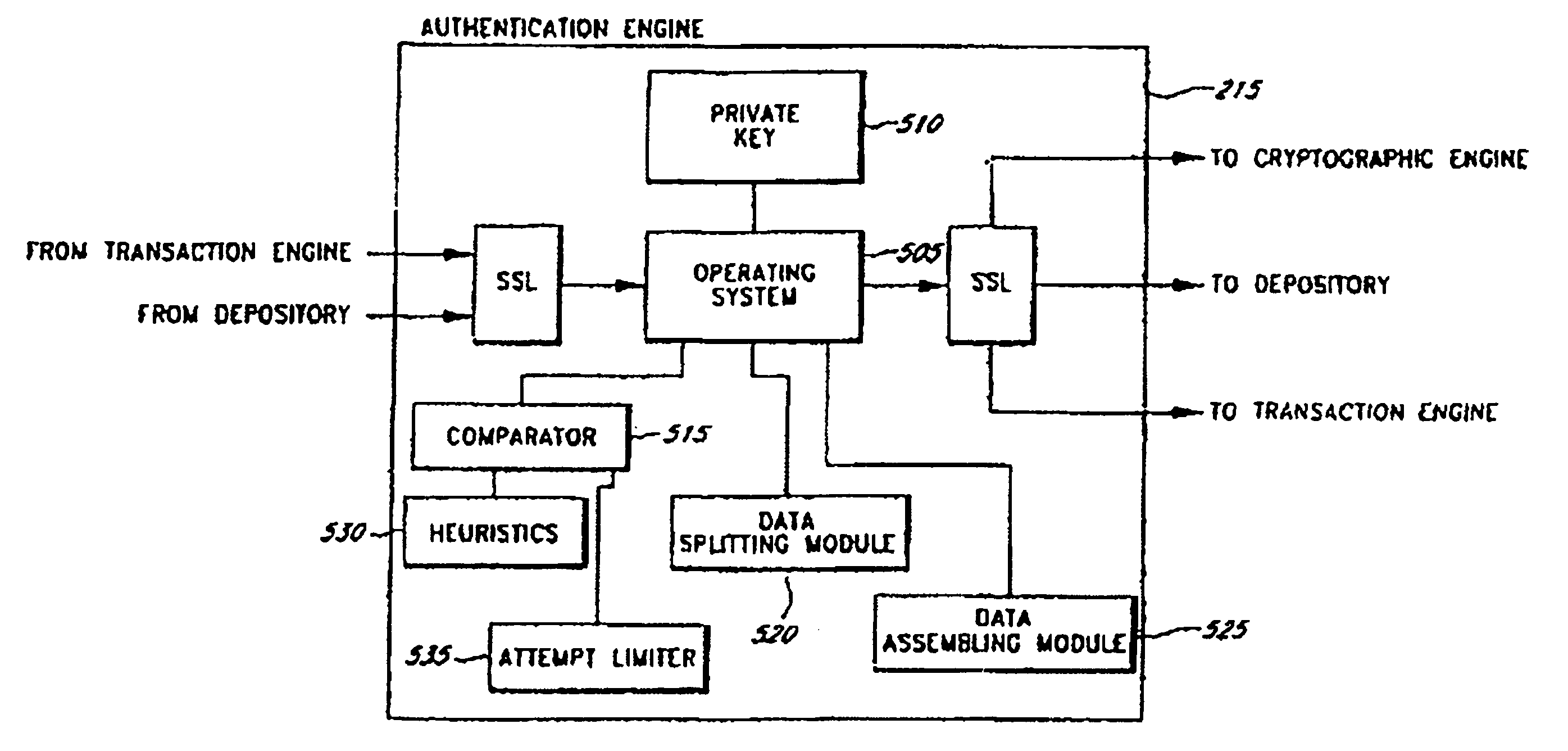
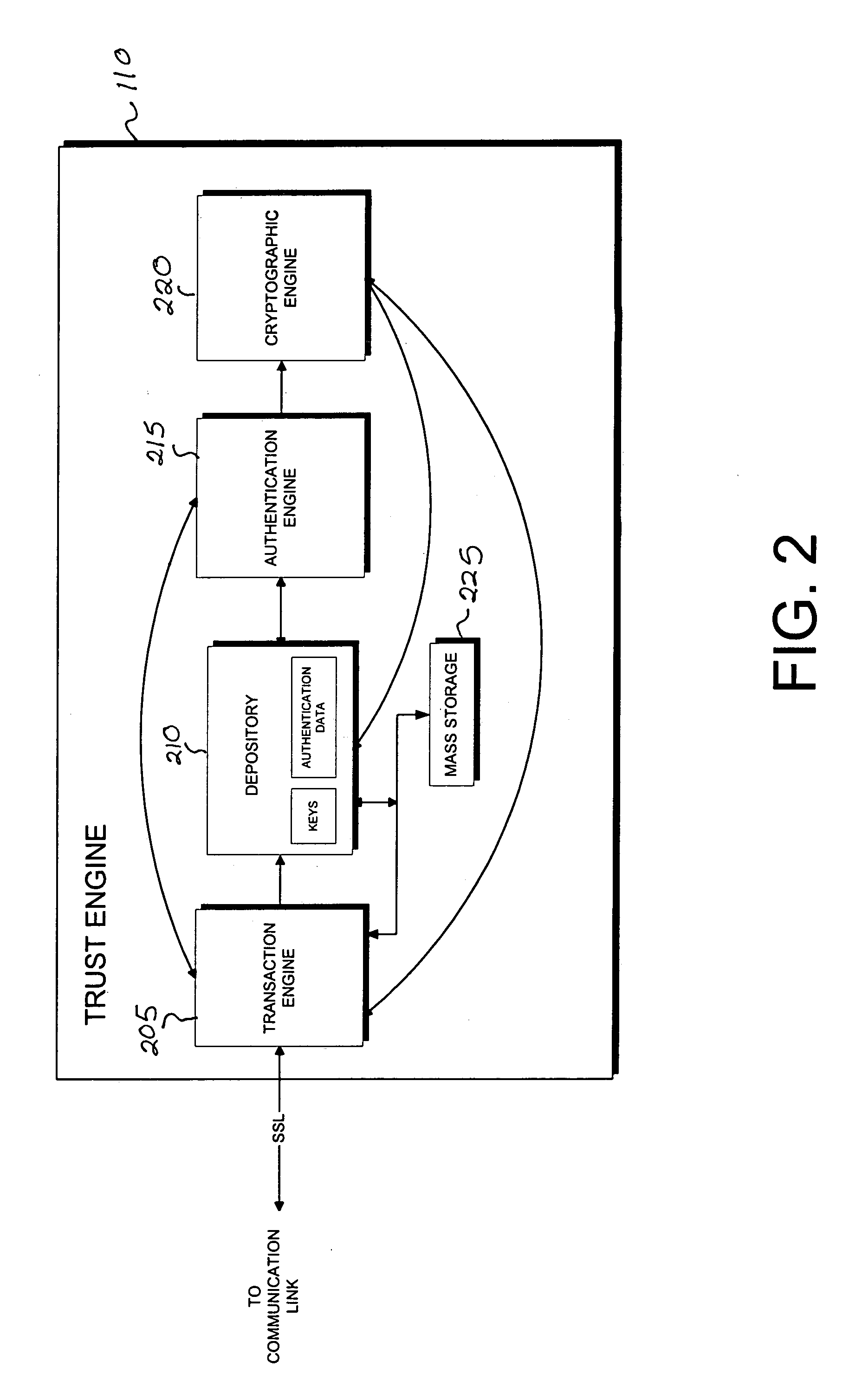
Server-side implementation of a cryptographic system
InactiveUS7187771B1Minimal compute resourceAvoid the needDigital data processing detailsUser identity/authority verificationUser authenticationEncrypted function
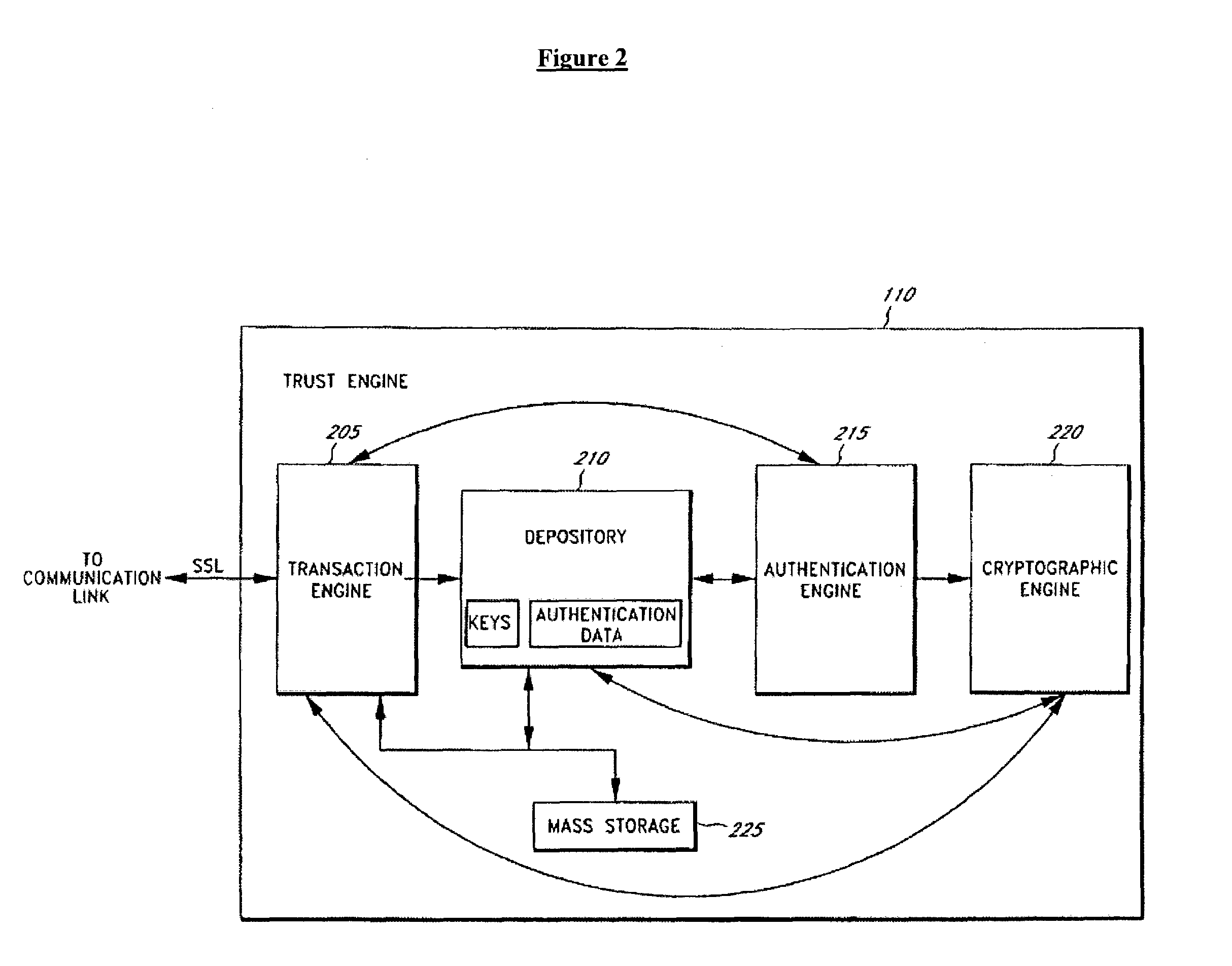
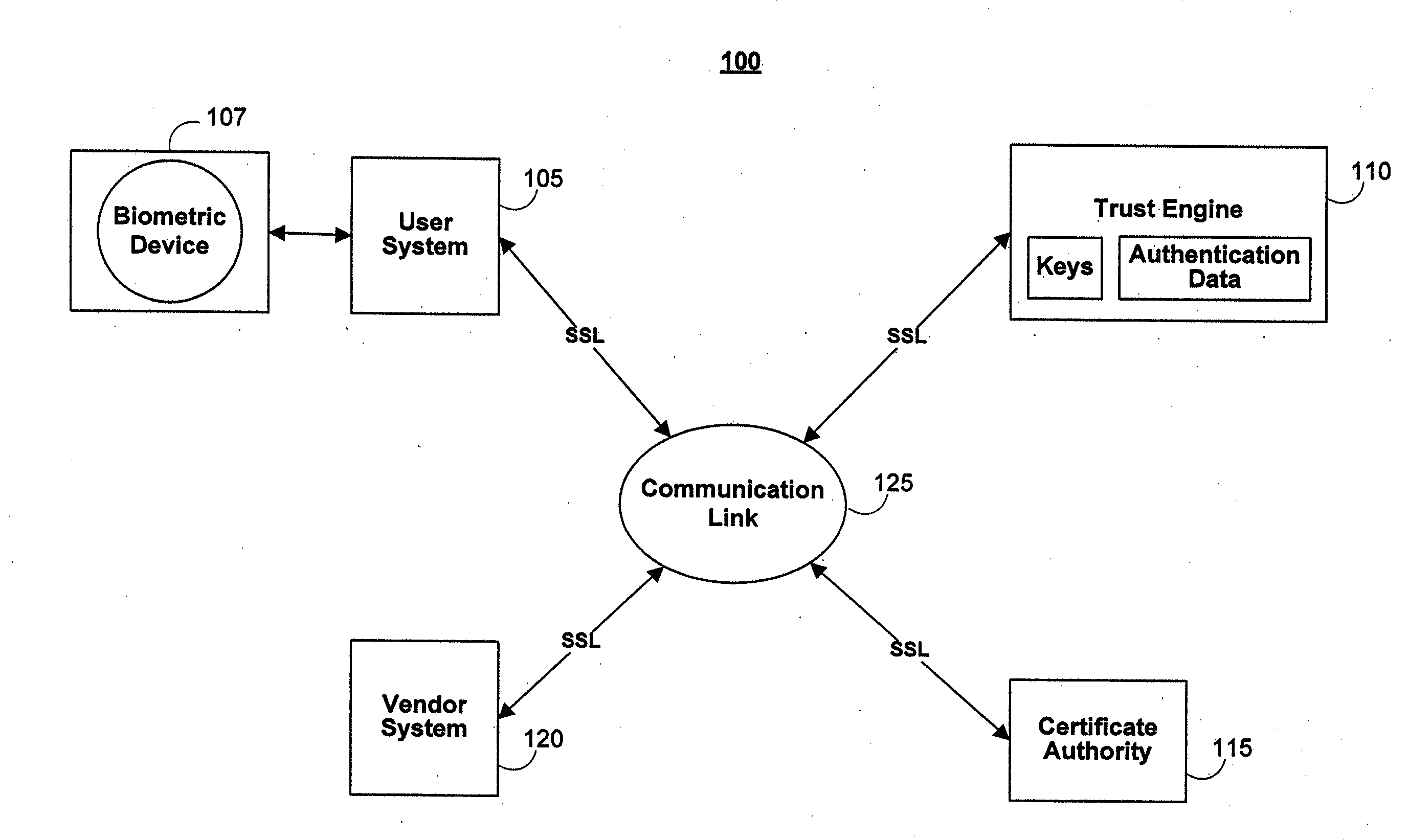
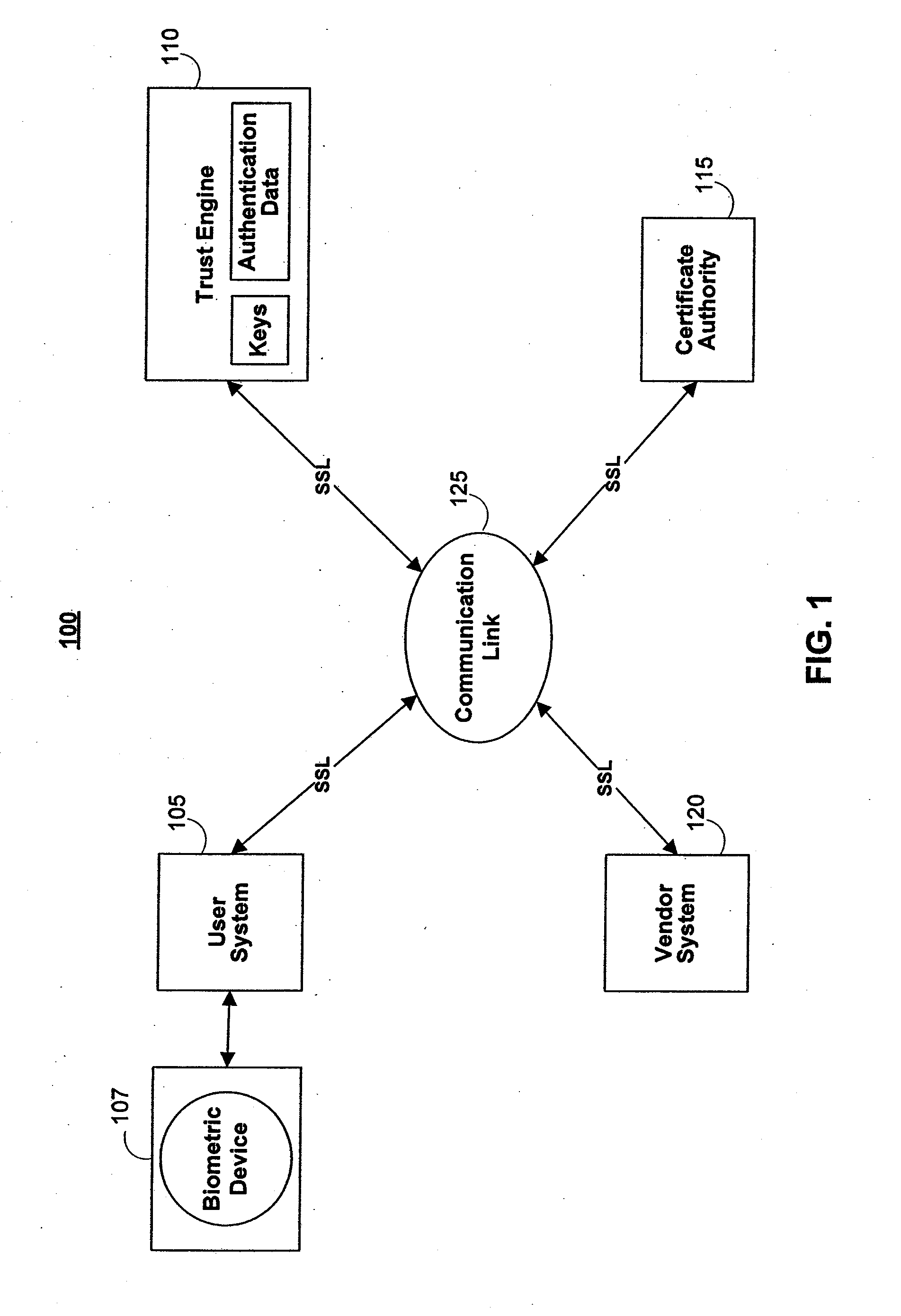
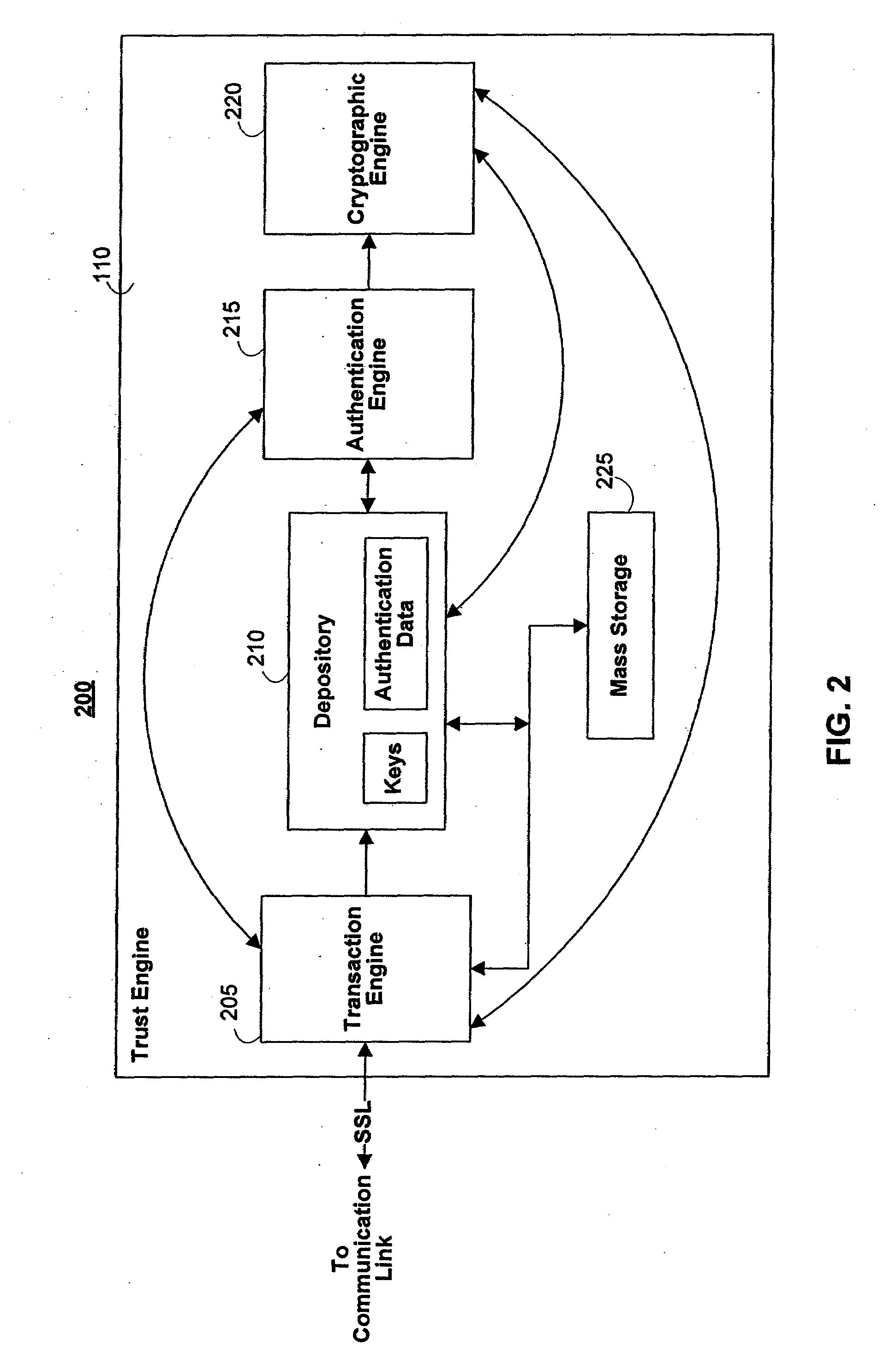
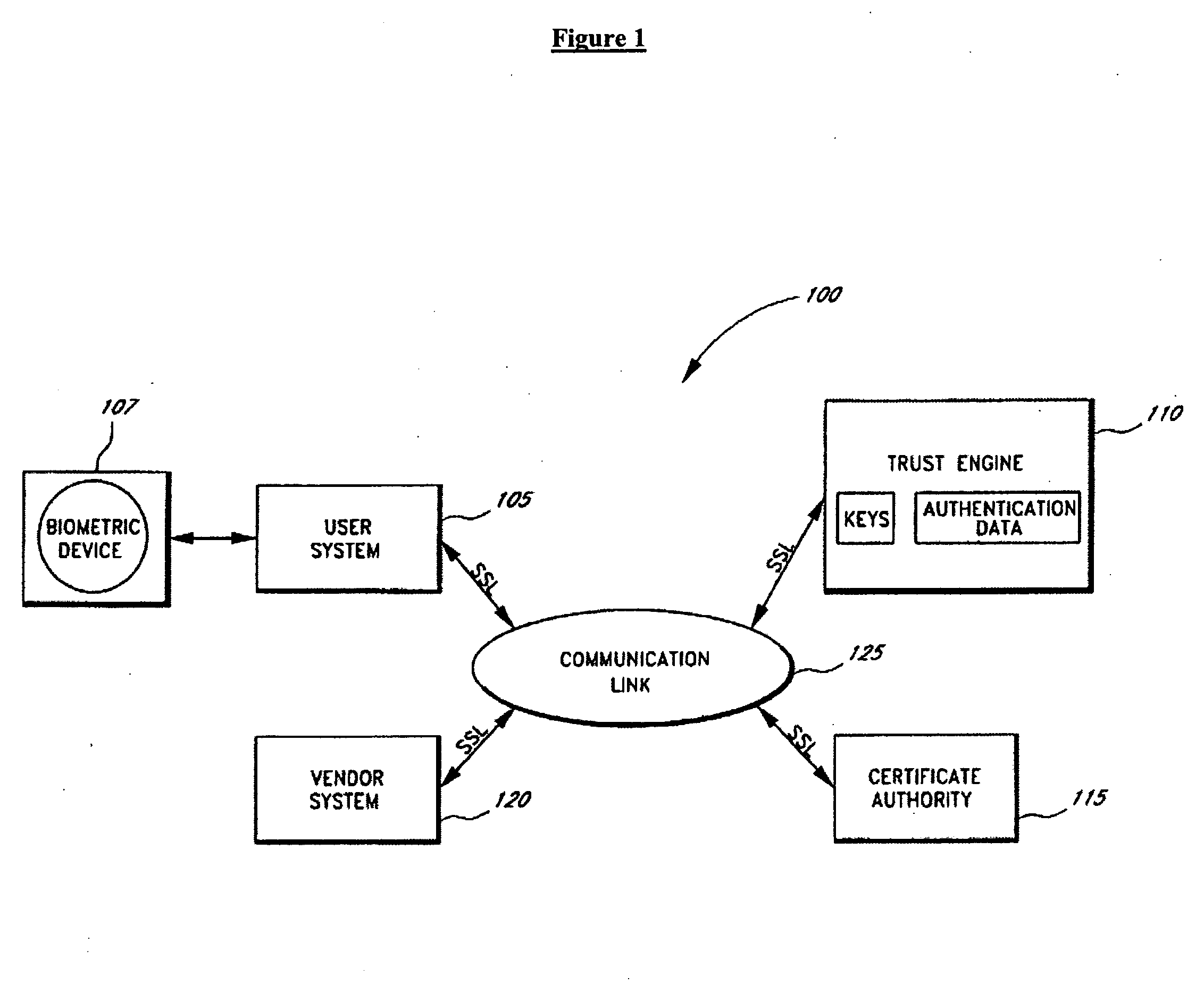
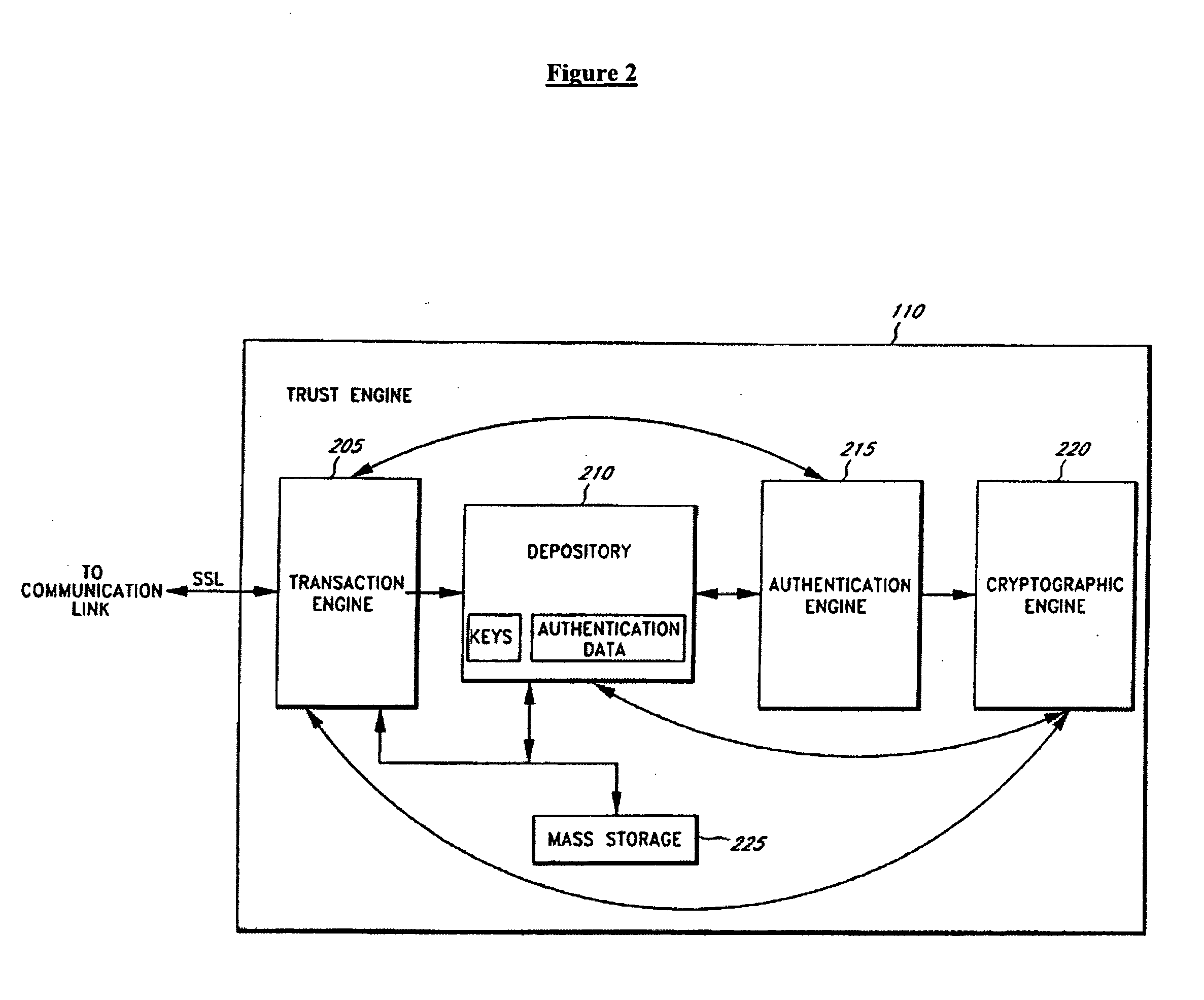
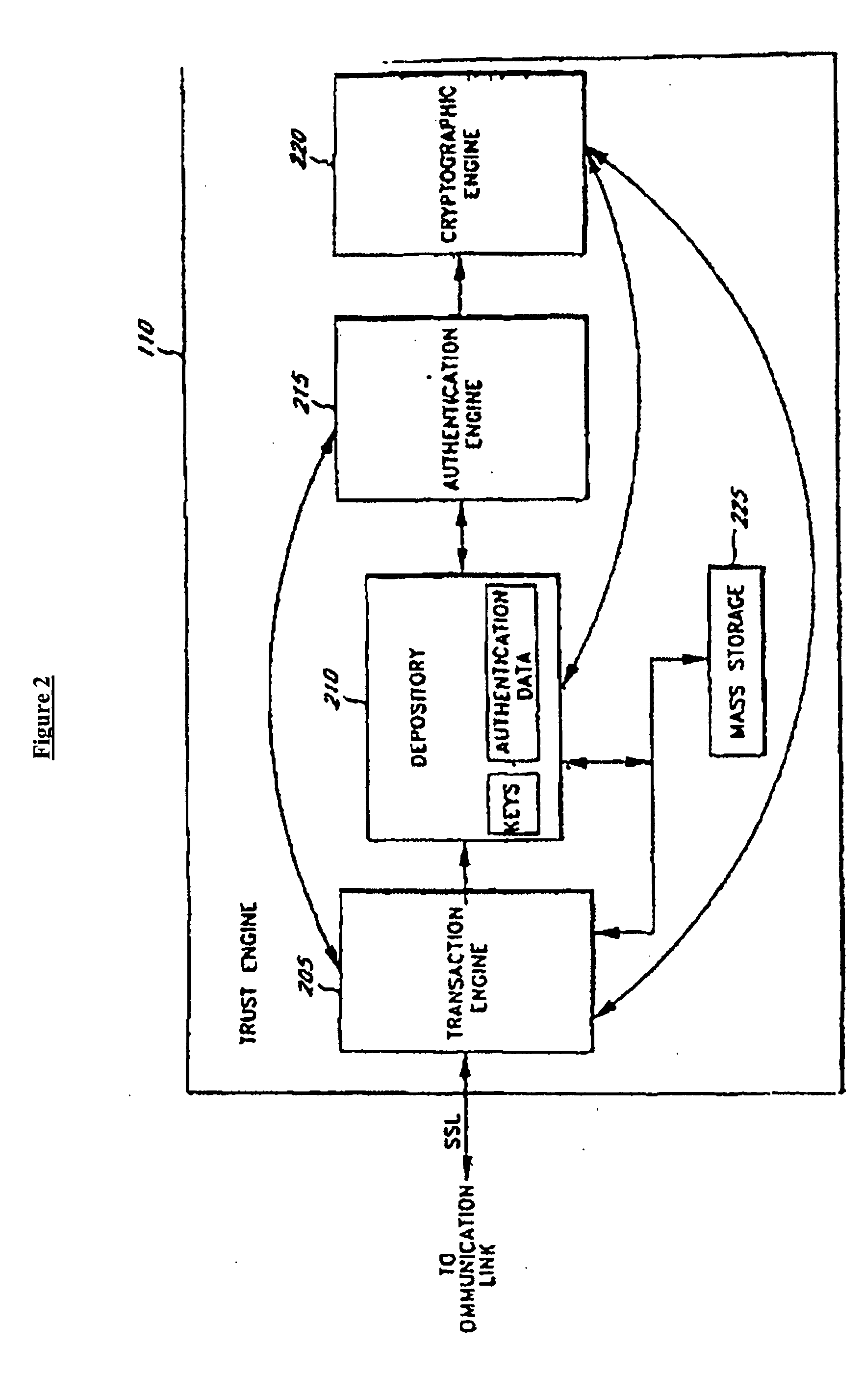
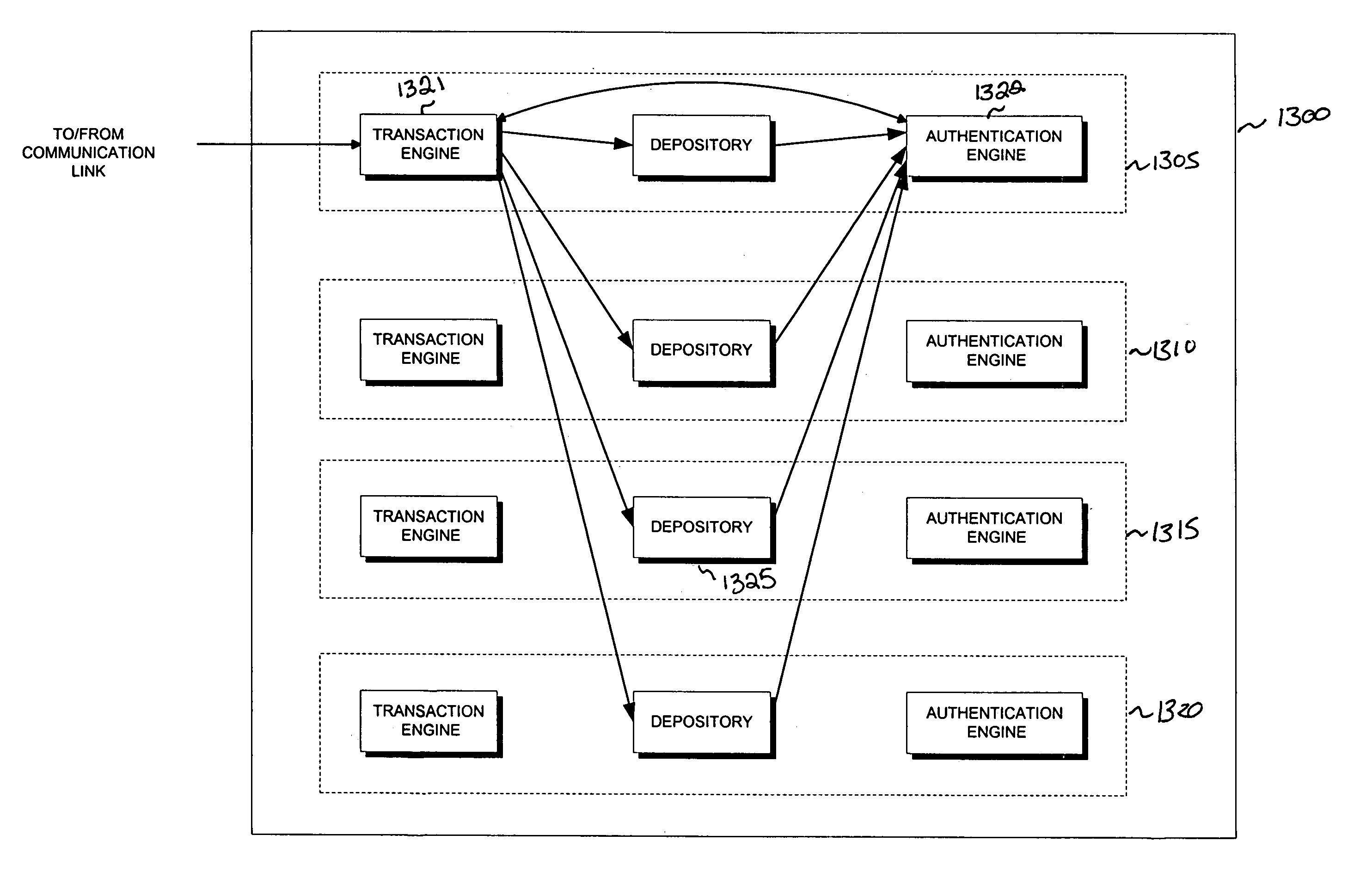
The invention is a secure server, or trust engine, having server-centric keys, or in other words, storing cryptographic keys and user authentication data on a server. Users access cryptographic functionality through network access to the trust engine; however, the trust engine does not release actual cryptographic keys or other authentication data. Therefore, the system provides that the keys and data remain secure. The server-centric storage of keys and authentication data provides for user-independent security, portability, availability, and straightforwardness, along with a wide variety of implementation possibilities.
Owner:SECURITY FIRST INNOVATIONS LLC
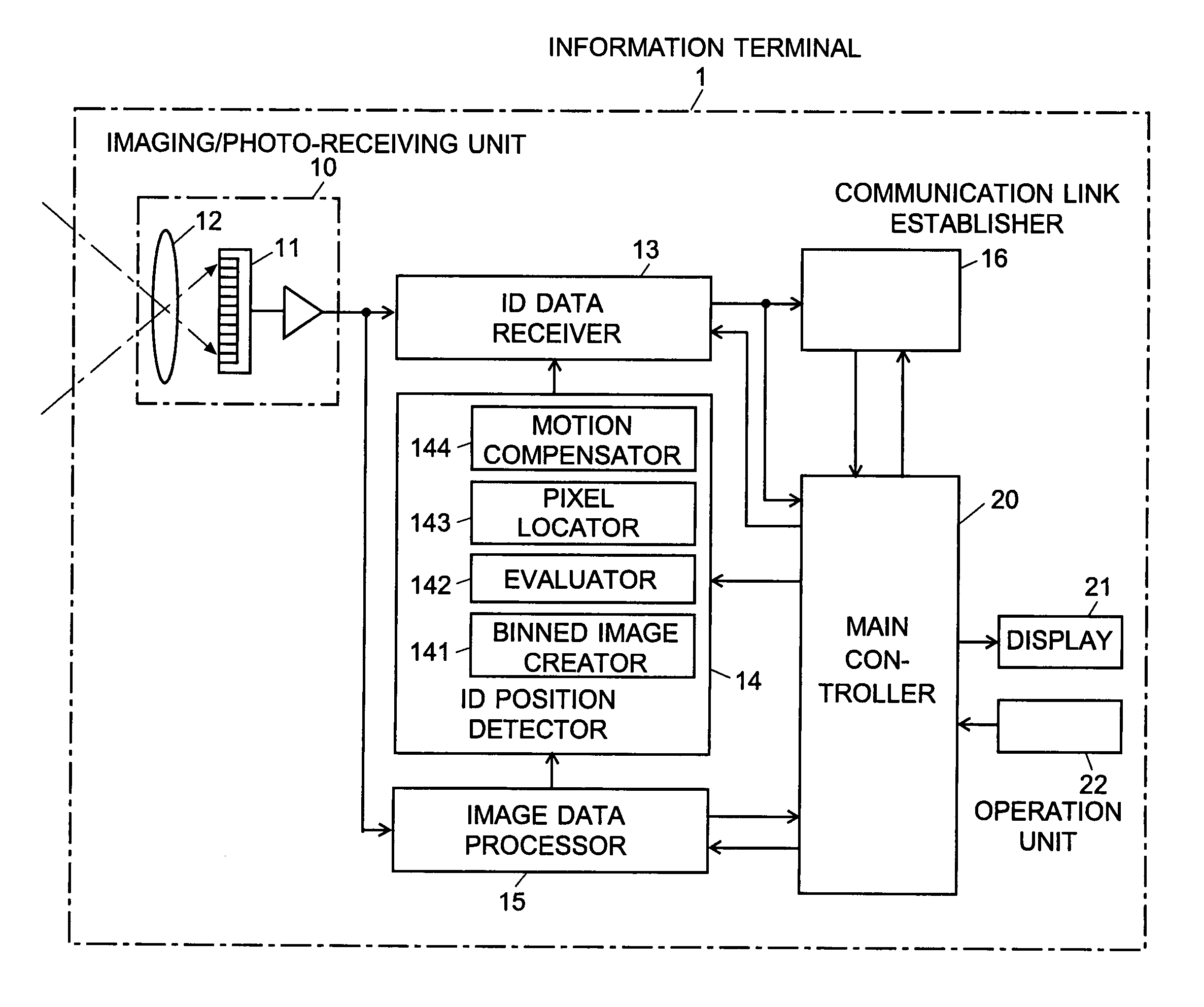
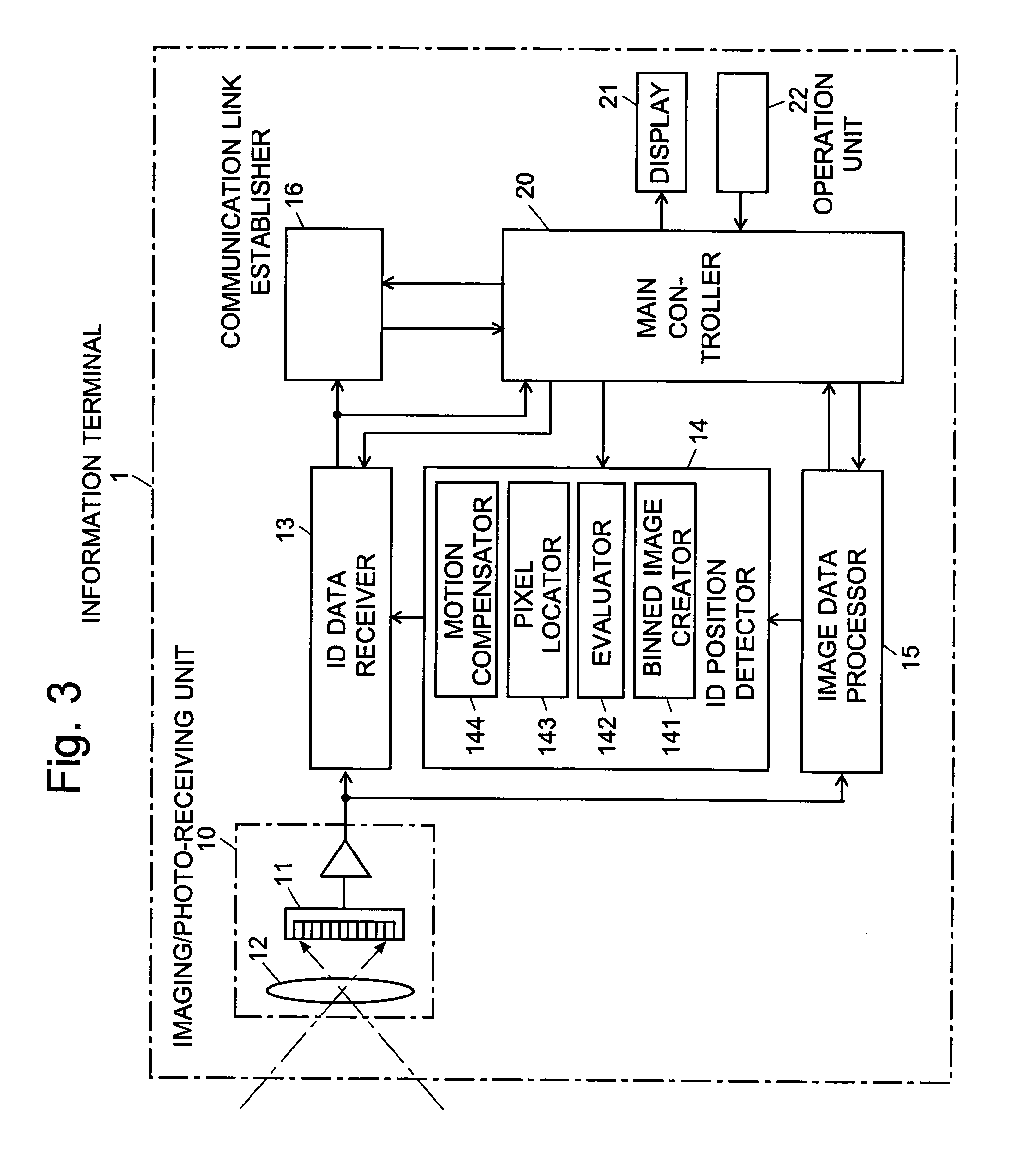
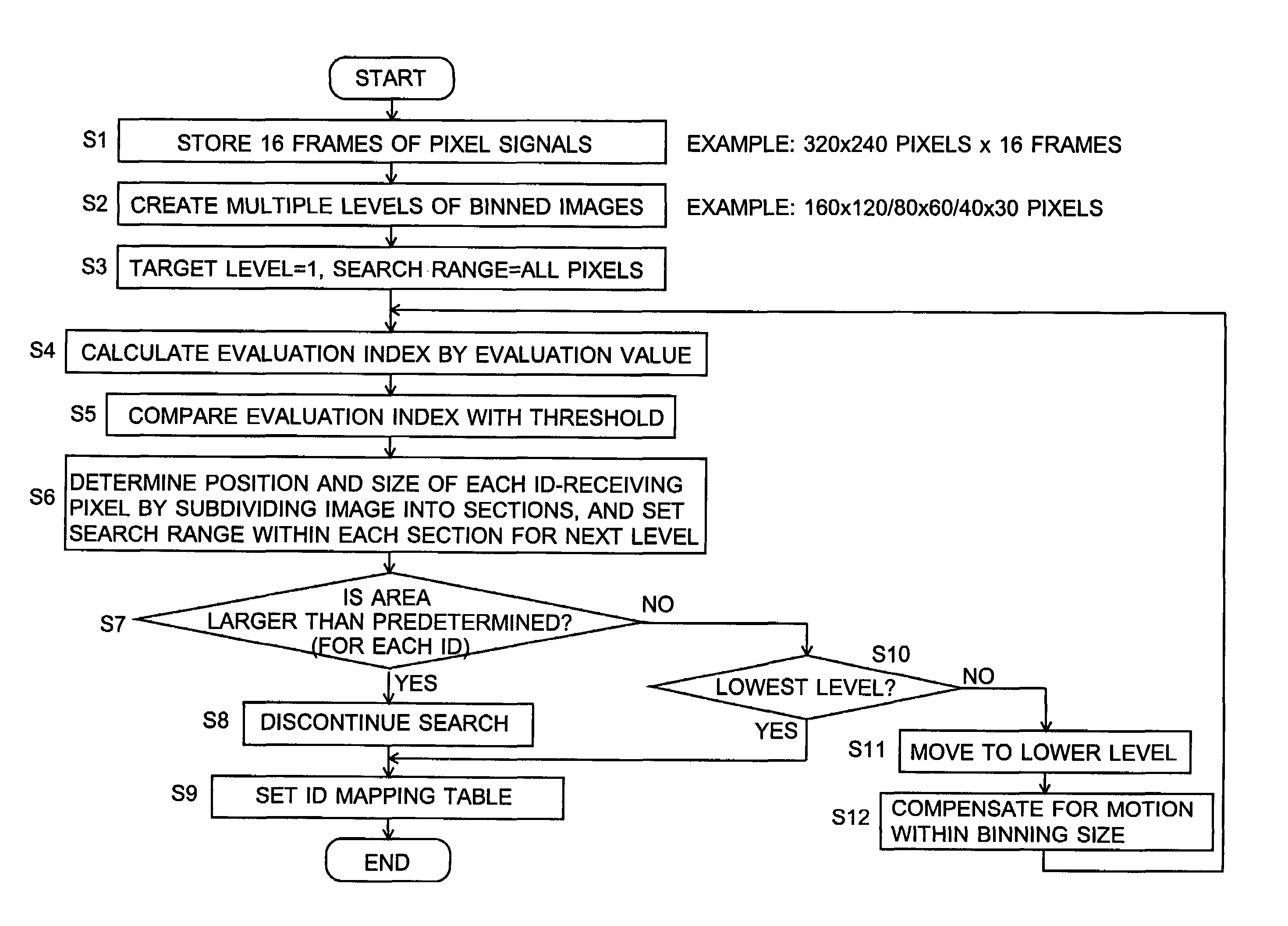
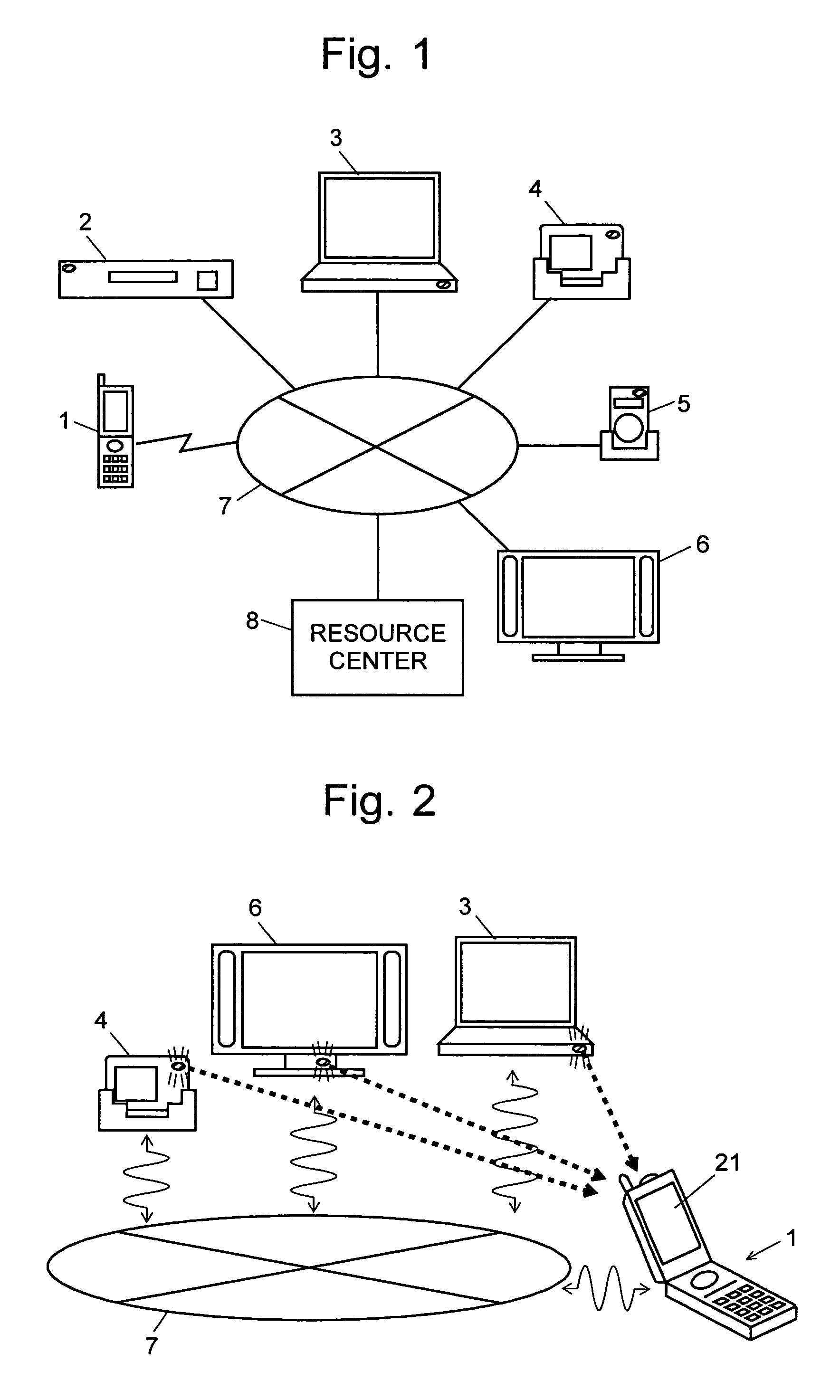
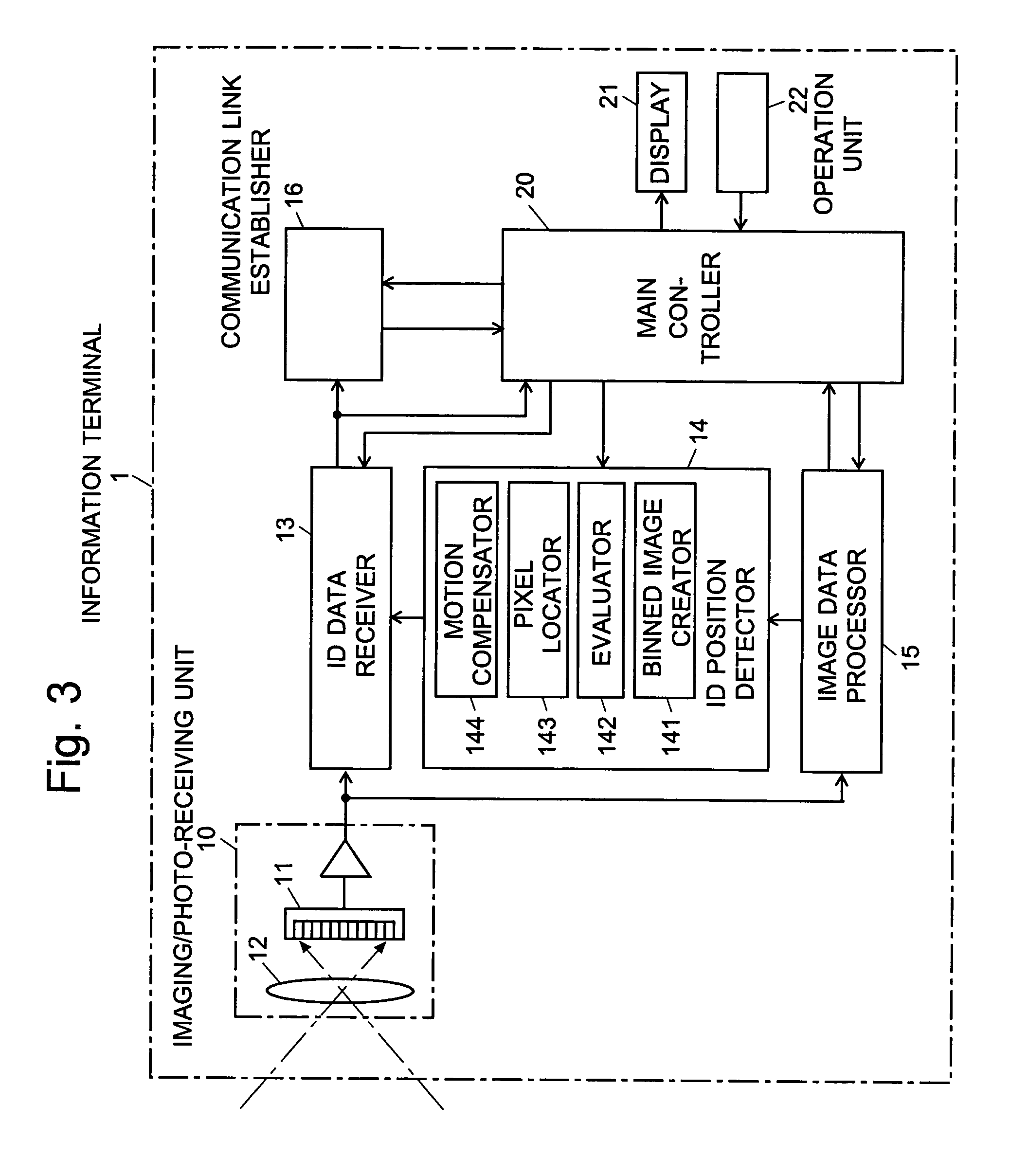
Information-processing device and information-processing system
InactiveUS20070070060A1Reduce in quantityReduce the number of timesTelevision system detailsTelevision system scanning detailsInformation processingFourier transform on finite groups
For an information terminal to be operated by users for collecting predetermined pieces of information from remote information devices by free-space optical communication, the present invention provides a technique for suppressing the power consumption of the information terminal by minimizing the amount of calculation performed to collect the aforementioned information. According to the present invention, each information device emits ID light on which a low-frequency pilot signal is superimposed. The information terminal captures a series of frames of images including the ID light and locates the ID light within the images by the following steps: (1) creating multiple levels of binned images having different resolutions for each frame of the image; (2) calculating an evaluation index for each pixel within a target range of the binned images at each level, from the lowest to the highest resolution, where the target range is narrowed every time the process switches over to a lower level. In (2), the evaluation index is calculated by an evaluation function including fast Fourier transformation performed throughout the series of frames of images. The evaluation index thus calculated is compared with a threshold to determine whether the pixel concerned is receiving ID light. The present technique significantly reduces the number of pixel to be analyzed and evaluated, thereby decreasing the total number of arithmetic operations to be performed using the evaluation function. Thus, the power consumption is suppressed.
Owner:JAPAN SCI & TECH CORP +2
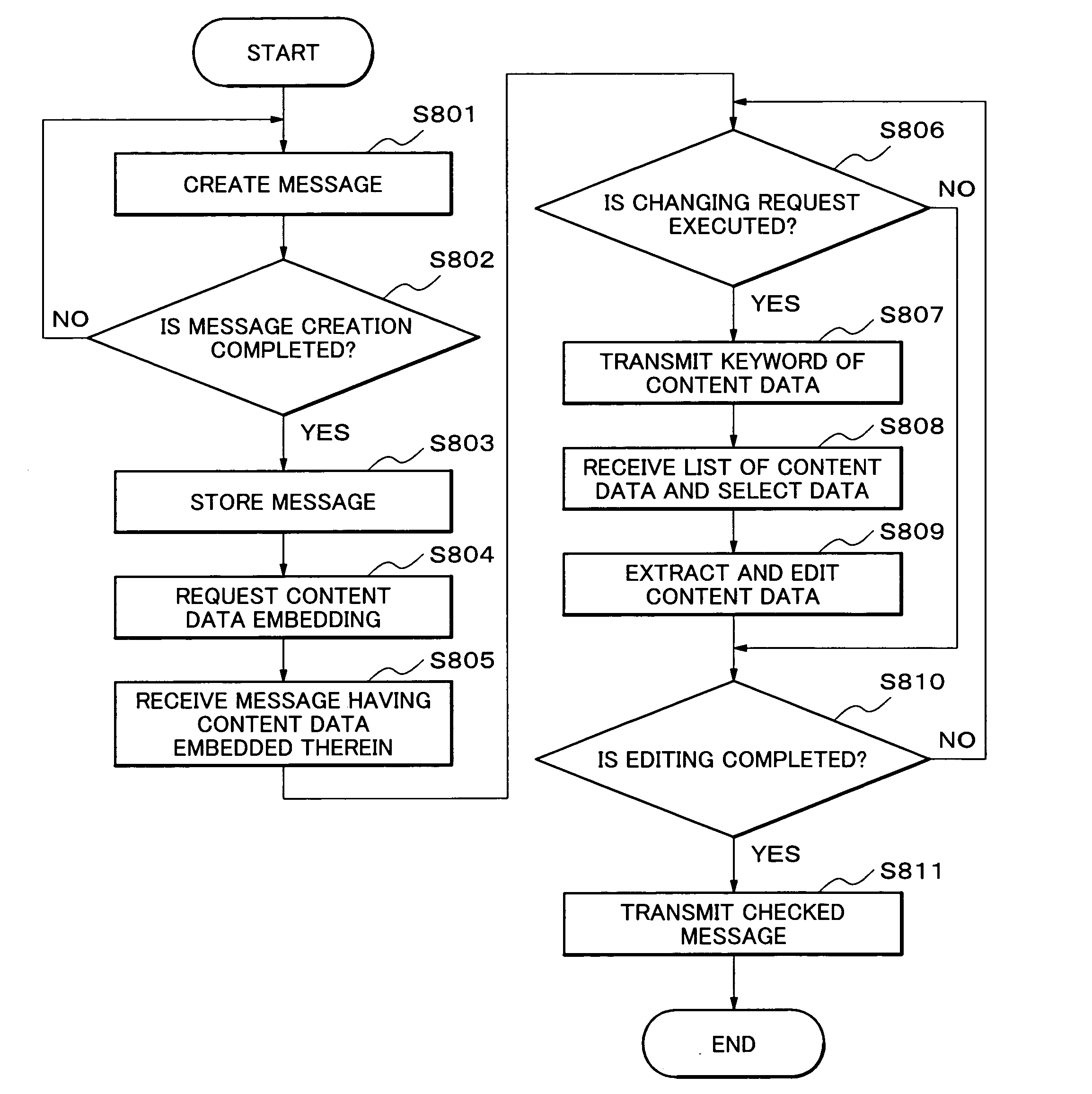
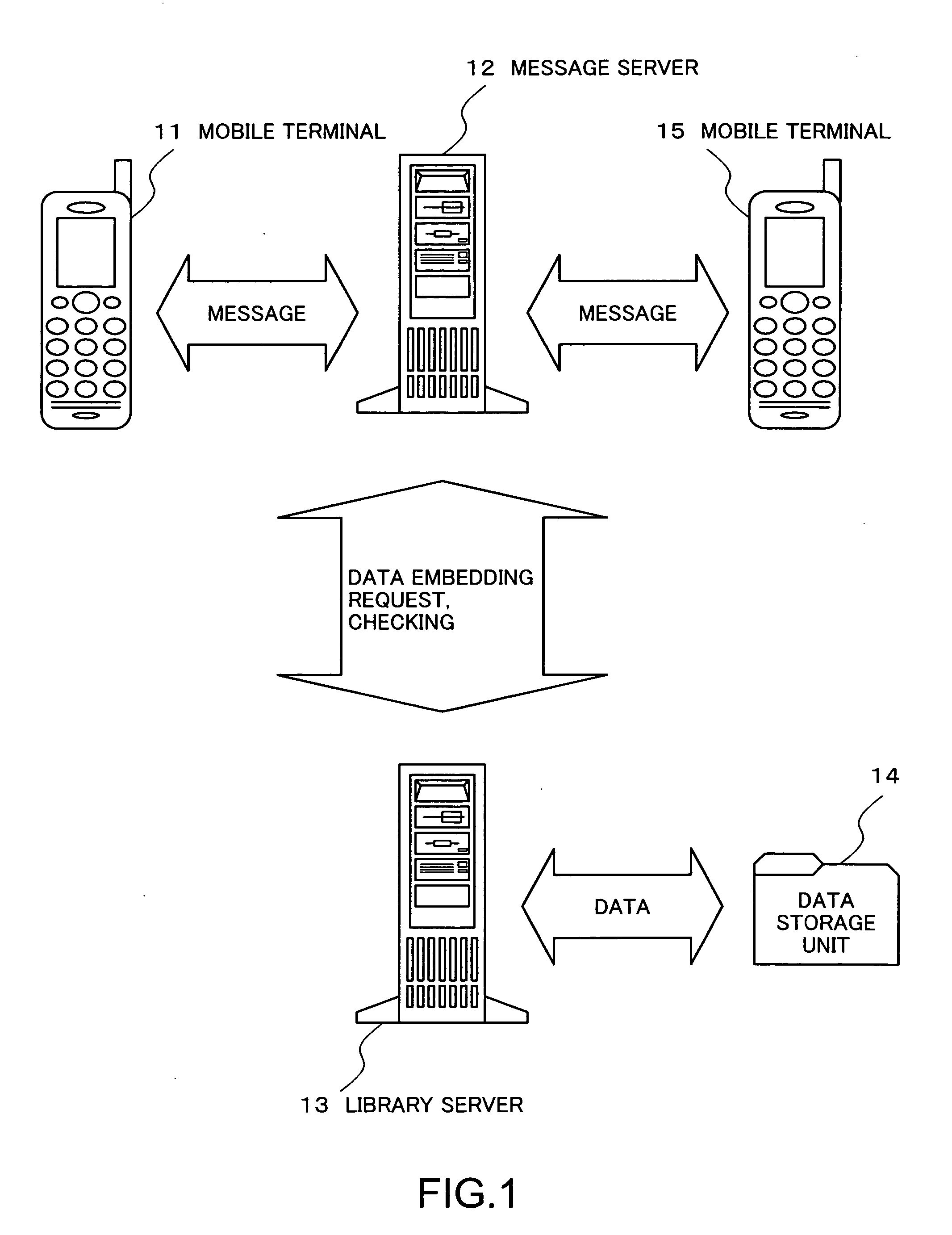
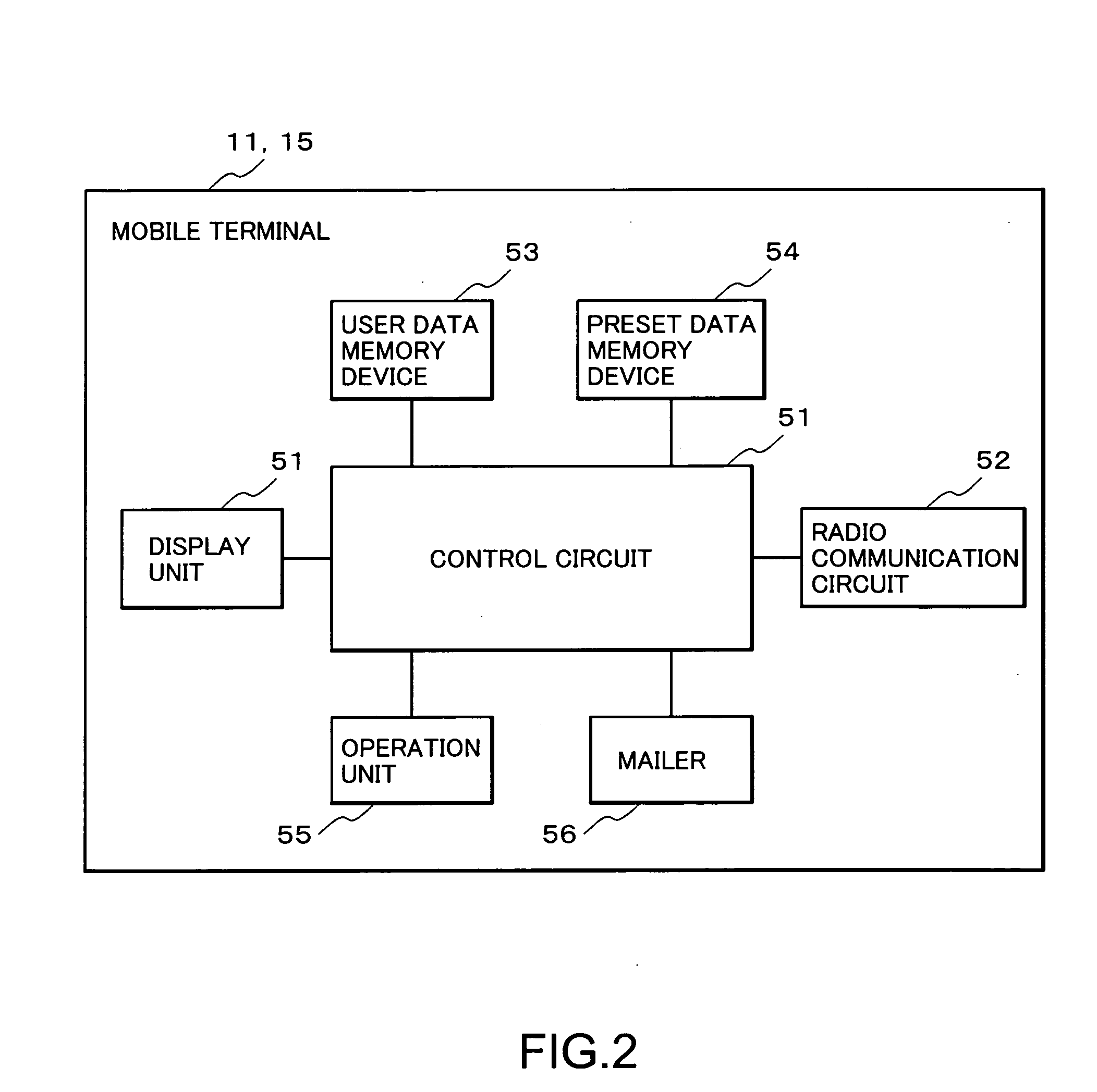
Message distribution system, server, mobile terminal, data storage unit, message distribution method, and message distribution computer program product
ActiveUS20050221802A1Reduce the number of timesShorten the timeSpecial service for subscribersSubstation equipmentDistribution methodDistribution system
A message distribution system which distributes messages for transmission / reception between mobile terminals, comprising: a message distribution server which receives a message transmitted from one of the mobile terminals and distributes the message to the mobile terminal on a receiving side; and a library server which includes: a data storage unit storing a plurality of content data corresponding to a keyword; and a control circuit which executes a search to determine matching with the keyword stored in the data storage unit by using a word contained in a body of the message as a key upon a request from one of the message distribution server and the mobile terminal; extracts, when the word matches the keyword, all content data corresponding to the keyword from the data storage unit, and extract content data similar to predetermined condition information from the extracted content data; and embeds the extracted content data similar to the condition information in the message.
Owner:LENOVO INNOVATIONS LTD HONG KONG
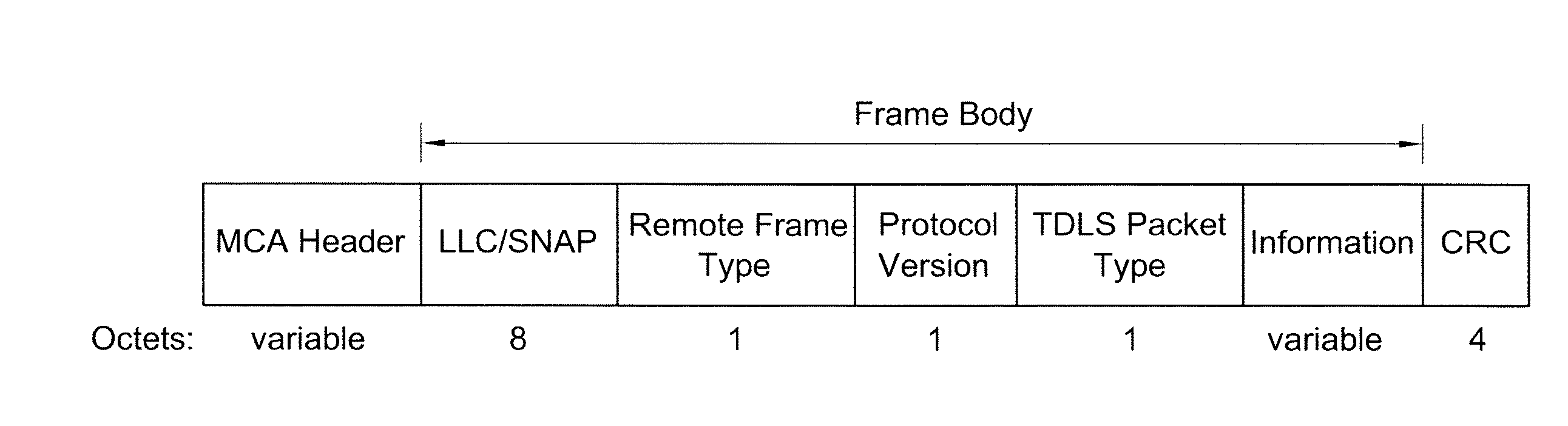
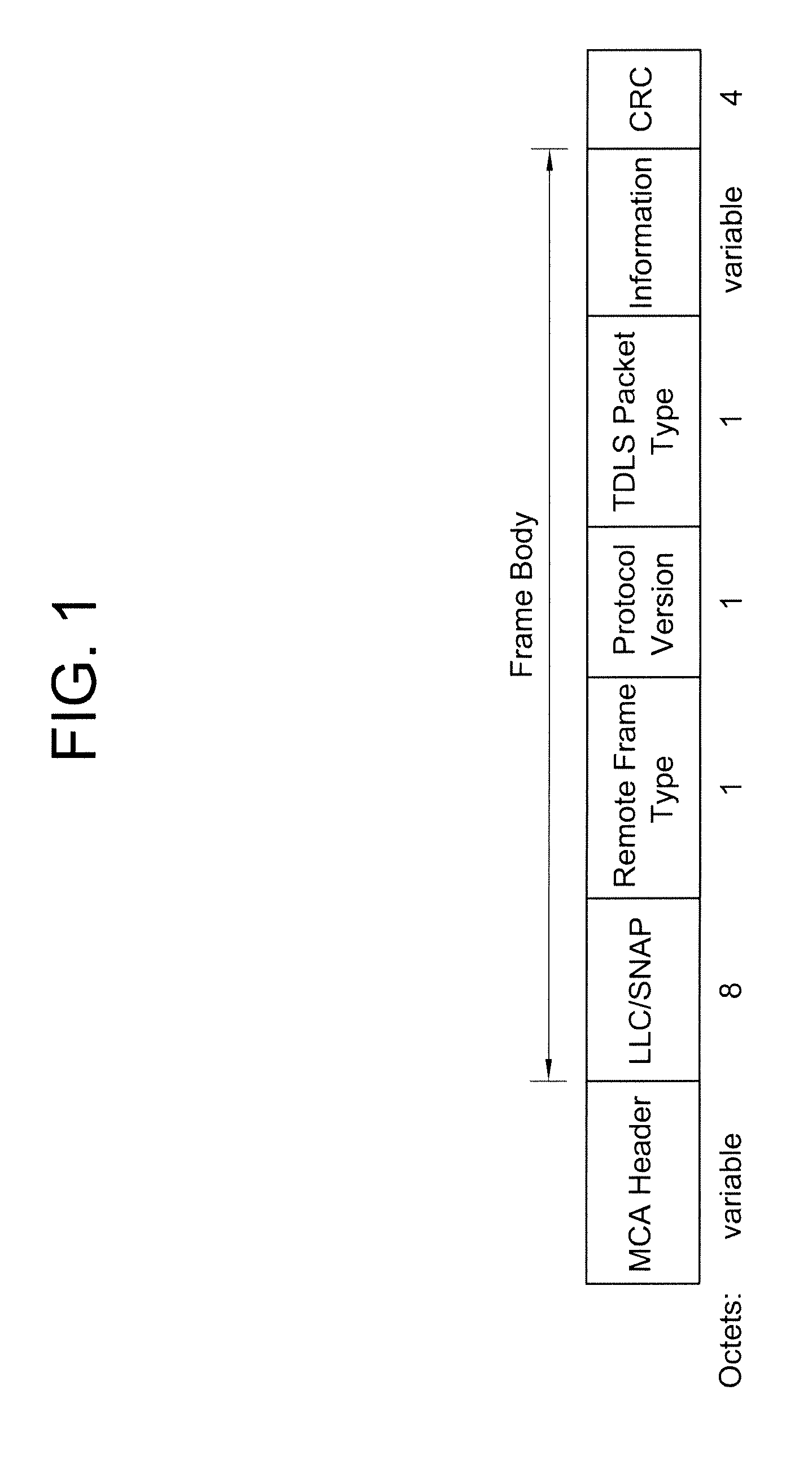
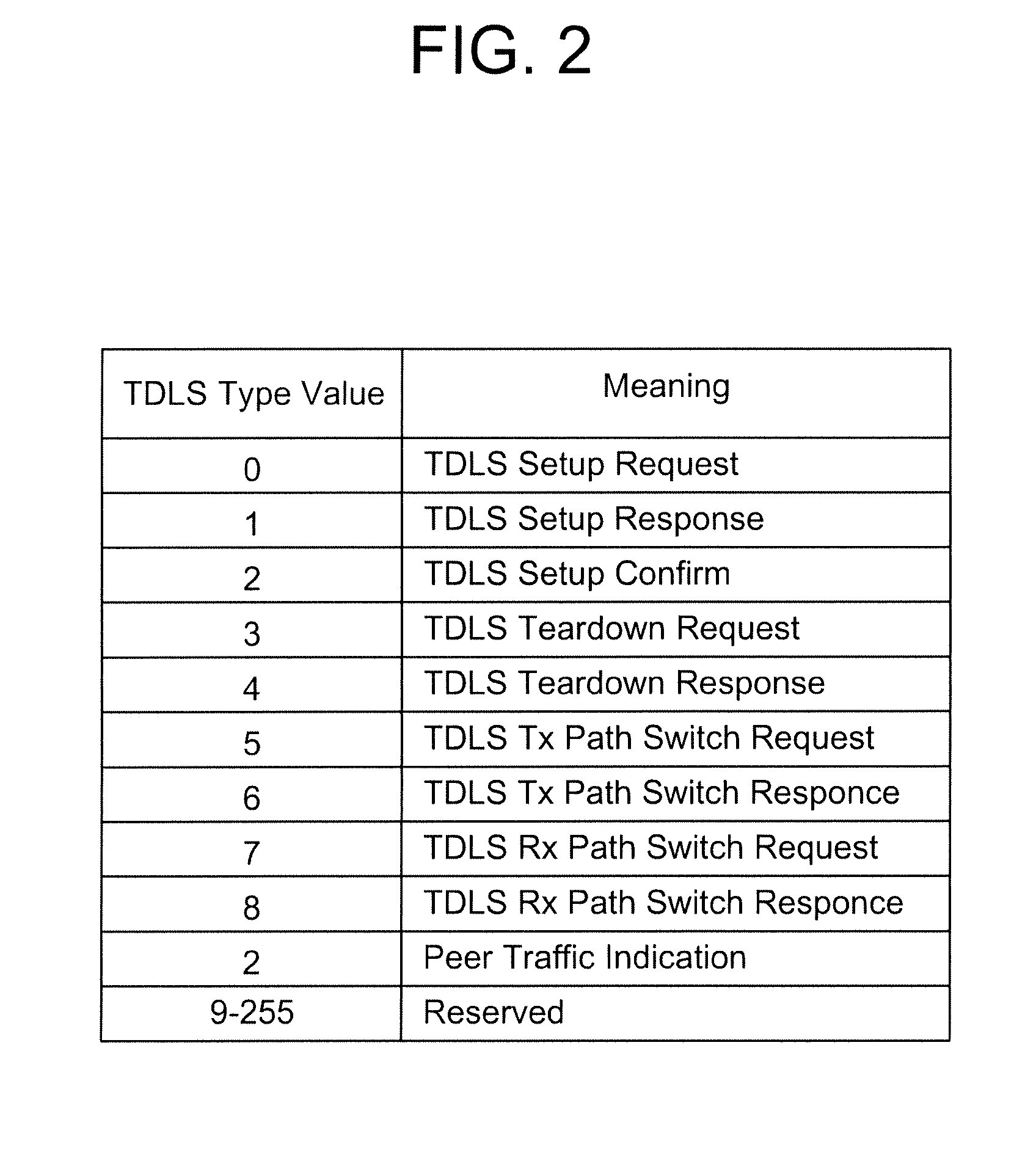
Peer power save mode in tunneled direct link setup (TDLS) wireless network
ActiveUS20080219228A1Reduce number of timeEffective supportPower managementEnergy efficient ICTData transmissionClient-side
A protocol for a peer power save mode (PPSM) in a tunneled direct link setup (TDLS) wireless network and a system therefor are provided. A station (STA) set up a TDLS link can send a frame having a power management bit set to a peer STA to enter into a power save mode (PSM). In this case, the station entering into the PSM operates in a PPSM client mode. When the peer STA operates in the PPSM client mode, the STA can operate in the PPSM access point (AP) mode or can enter into the PPSM client mode. The STA operating in the PPSM AP mode buffers data for the STA operating in the PPSM client mode and informs the peer STA of information indicating that there is buffered data by the use of a peer traffic indication frame or the like. In principle, a U-APSD procedure can be applied to the transmission of data through a direct link from the STA operating in the PPSM AP mode to the STA operating in the PPSM client mode.
Owner:LG ELECTRONICS INC
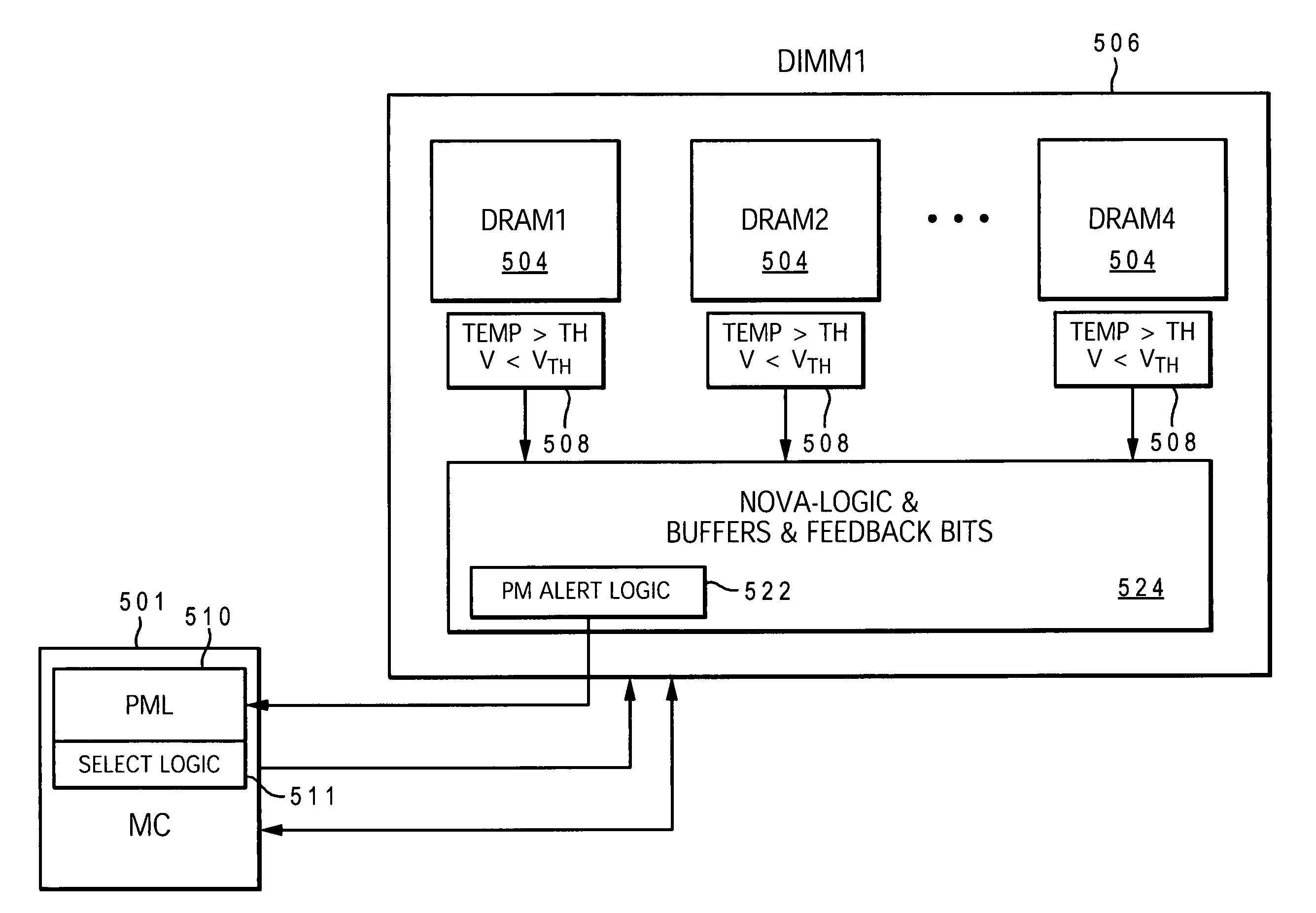
Power management via DIMM read operation limiter
InactiveUS20060179333A1Little or no usePower usageVolume/mass flow measurementHardware monitoringMemory controllerDIMM
A method and system for enabling directed temperature / power management at the DIMM-level and / or DRAM-level utilizing intelligent scheduling of memory access operations received at the memory controller. Hot spots within the memory subsystem, caused by operating the DIMMs / DRAMs above predetermined / preset threshold power / temperature values for operating a DIMM and / or a DRAM, are avoided / controlled by logic within the memory controller. The memory controller logic throttles the number / frequency at which commands (read / write operations) are issued to the specific DIMM / DRAM based on stored parameter values and tracking of outstanding operations issued to the memory subsystem devices.
Owner:IBM CORP
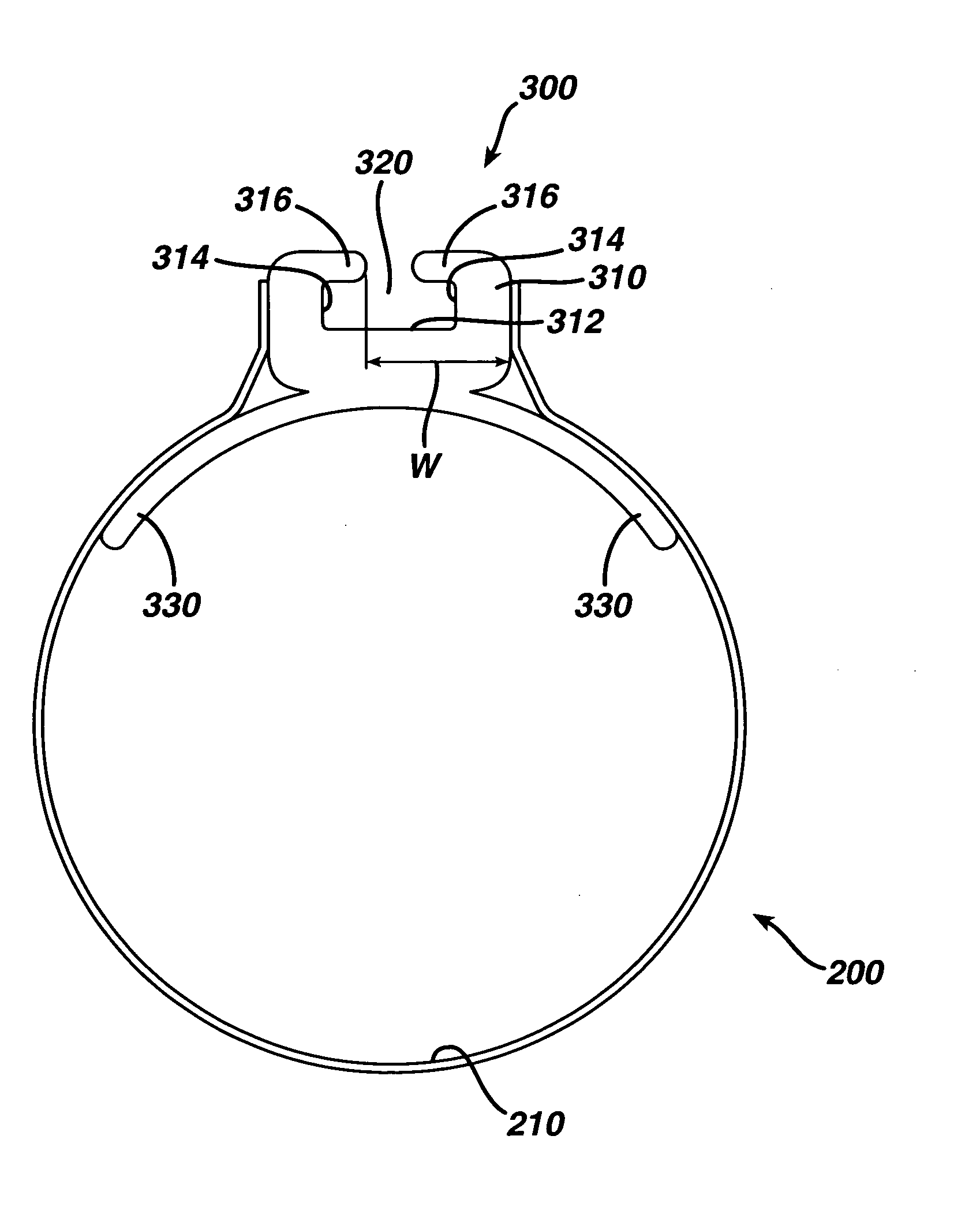
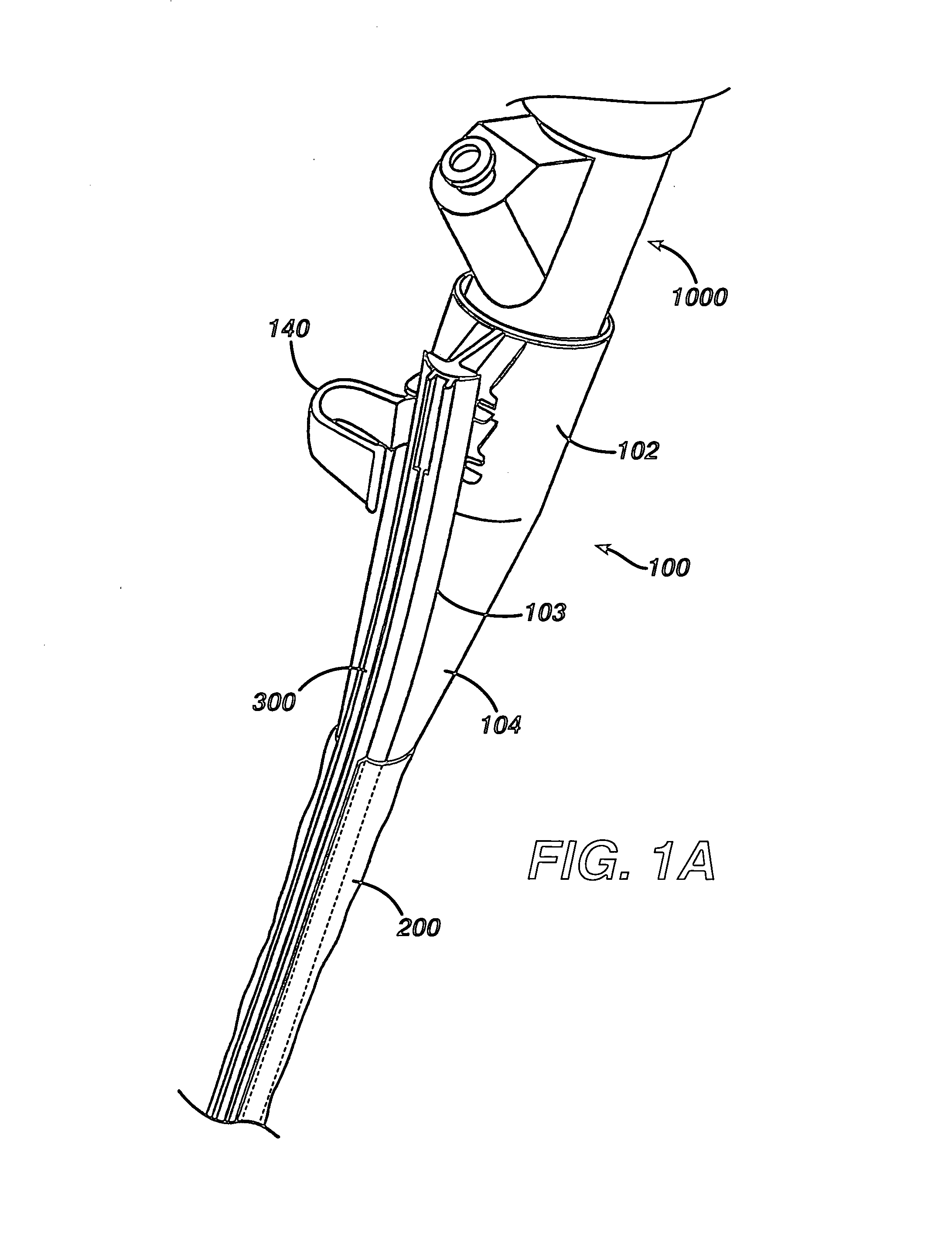
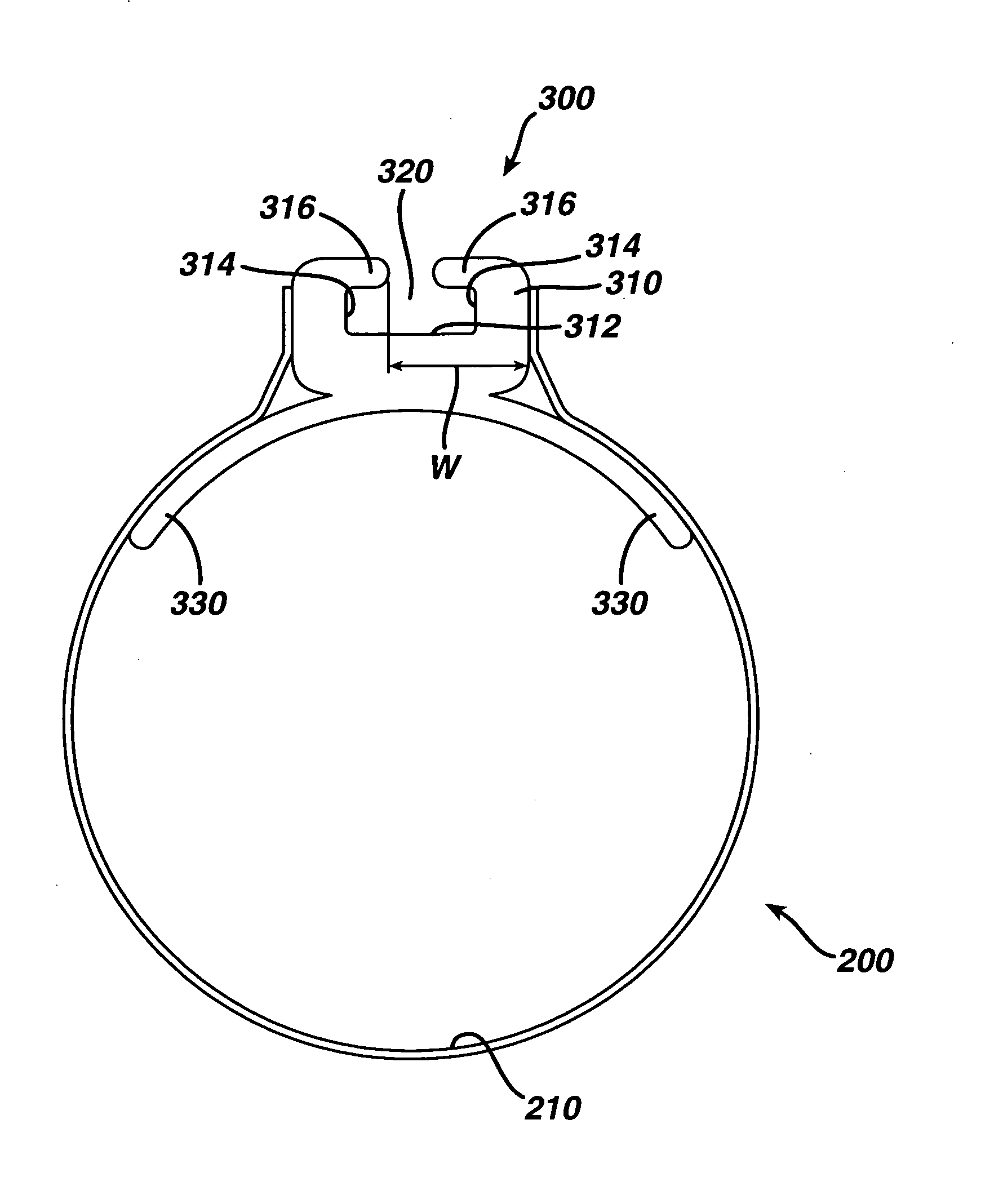
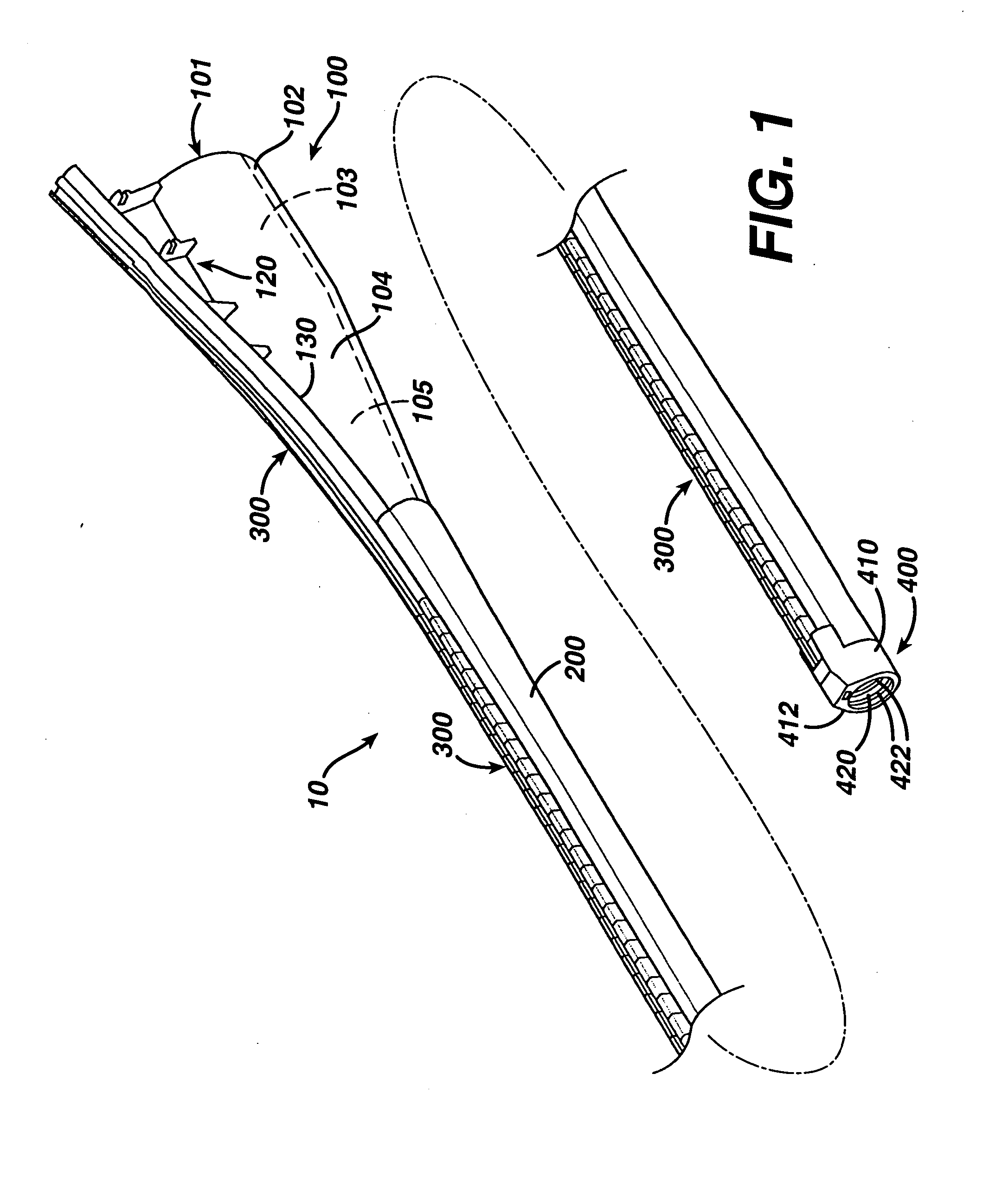
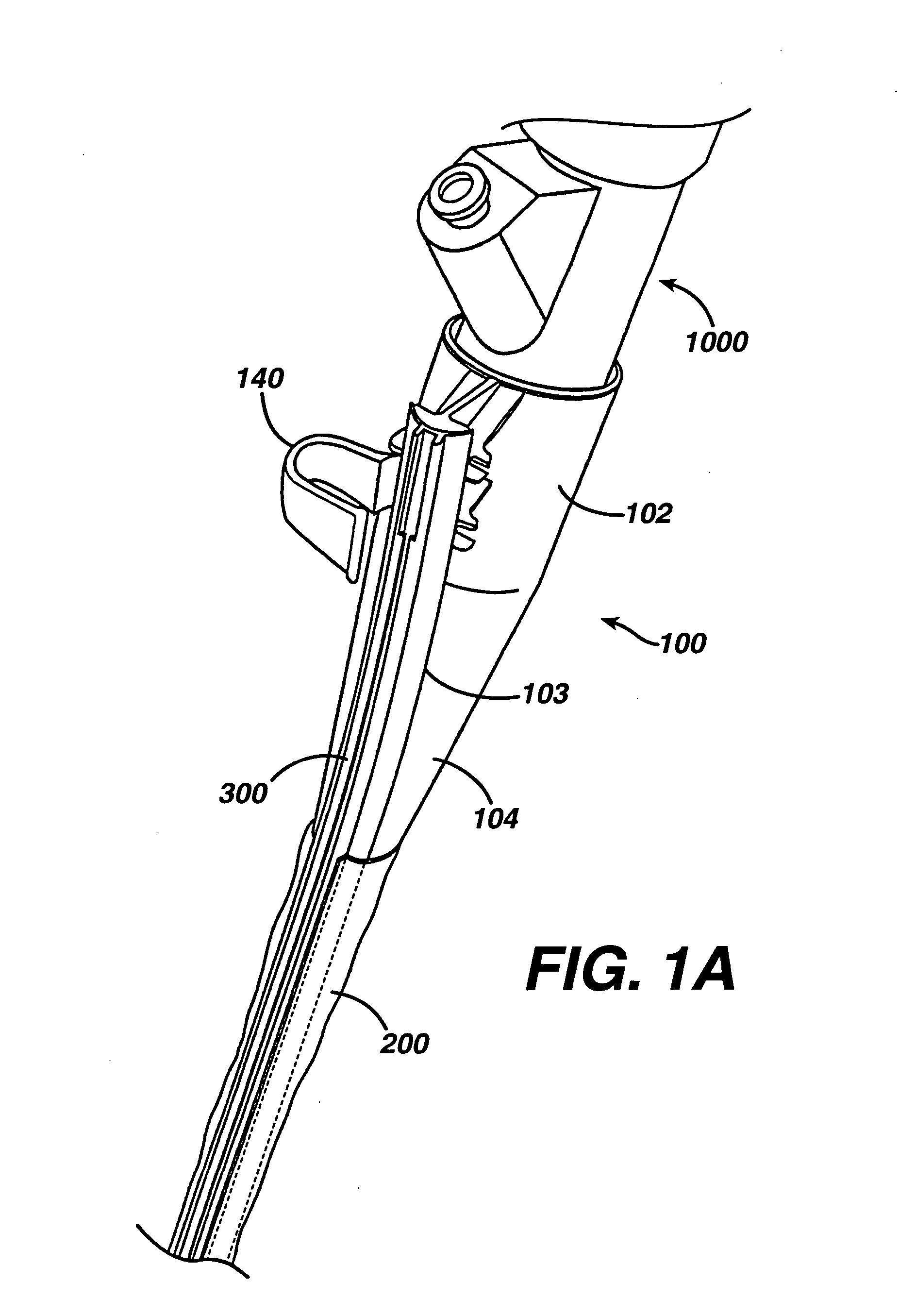
Feeding tube
InactiveUS20060259010A1Reduce numberReduce number of stepSurgical needlesEndoscopesGastric tube feedingEngineering
A feeding tube and an apparatus useful for positioning a feeding tube are disclosed. The apparatus can include a track supported on a sheath sized to receive an endoscope, and a carrier slidable with respect to the track. A feeding tube having a rail feature for slidable engagement with a carrier is disclosed.
Owner:ETHICON ENDO SURGERY INC
Mobile radio terminal
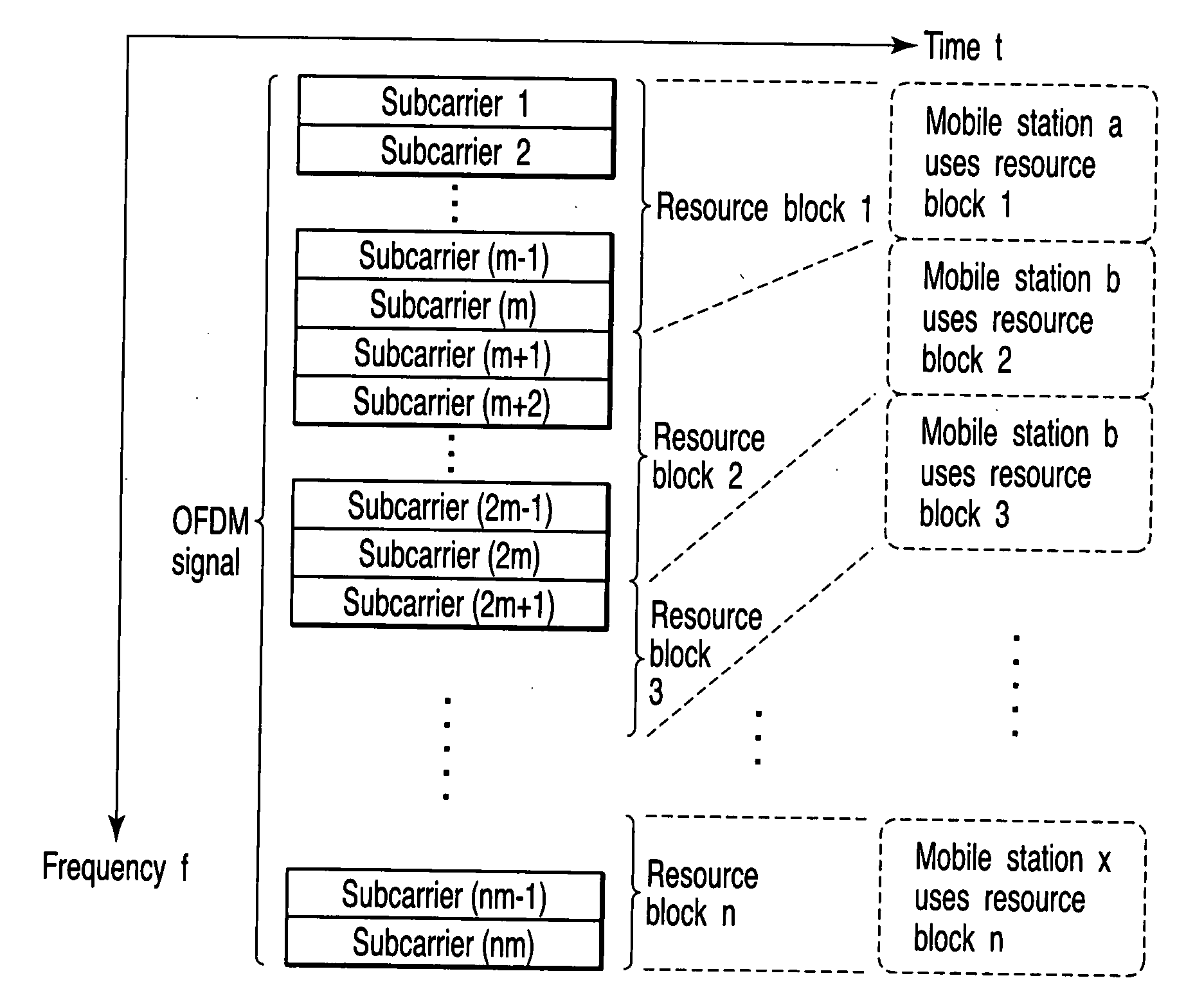
InactiveUS20080049813A1Reduce amountPreventing deterioration of throughputModulated-carrier systemsFrequency-division multiplex detailsMobile stationMobile radio
On the basis of control information for CQI transmission of which a base station notifies a mobile station, the mobile station transmits CQI information for each sub-frame in a case of best effort type service or transmits the base station the CQI information at one time for every four sub-frames in a case of rate preservation type service.
Owner:FUJITSU TOSHIBA MOBILE COMM LTD
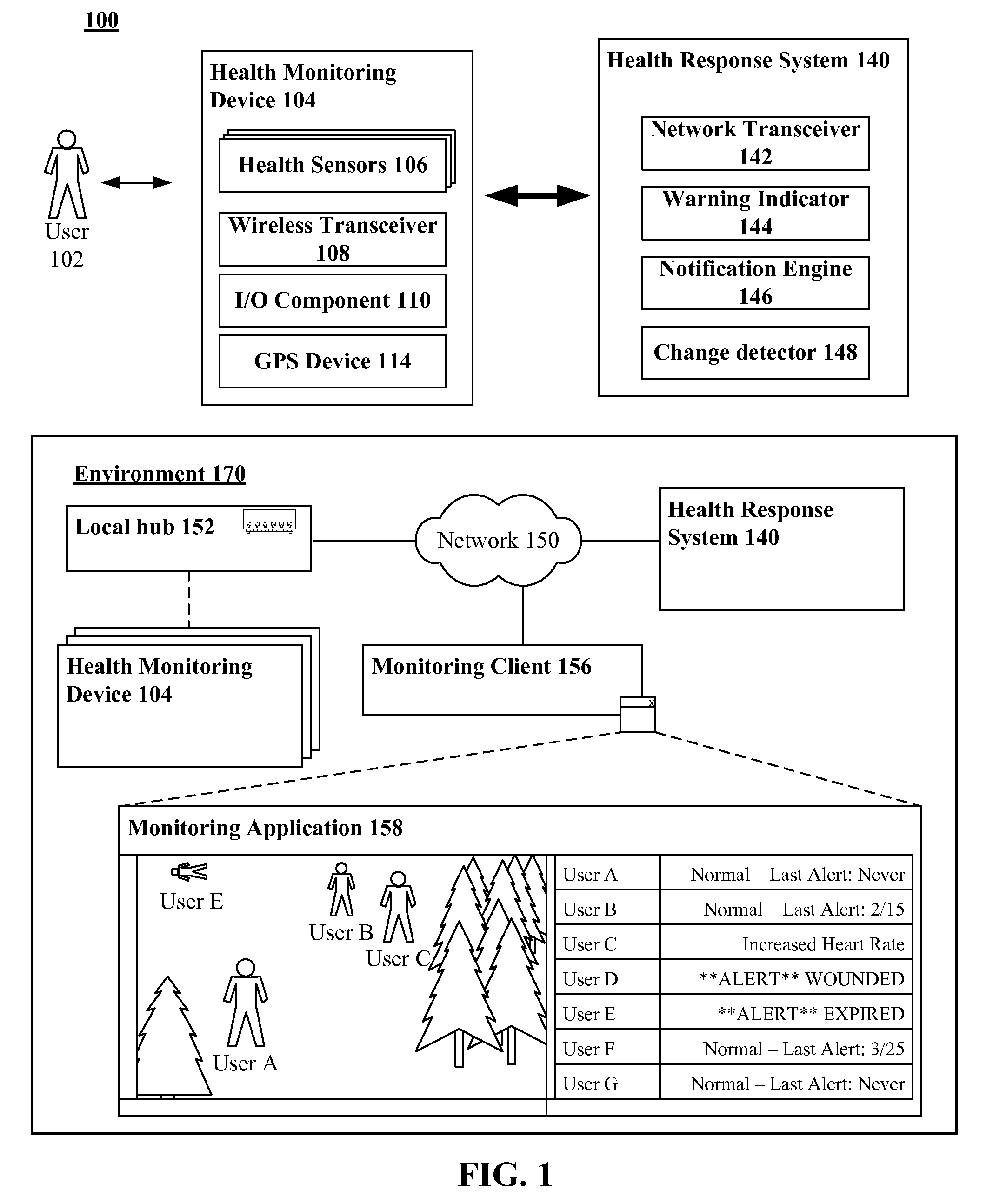
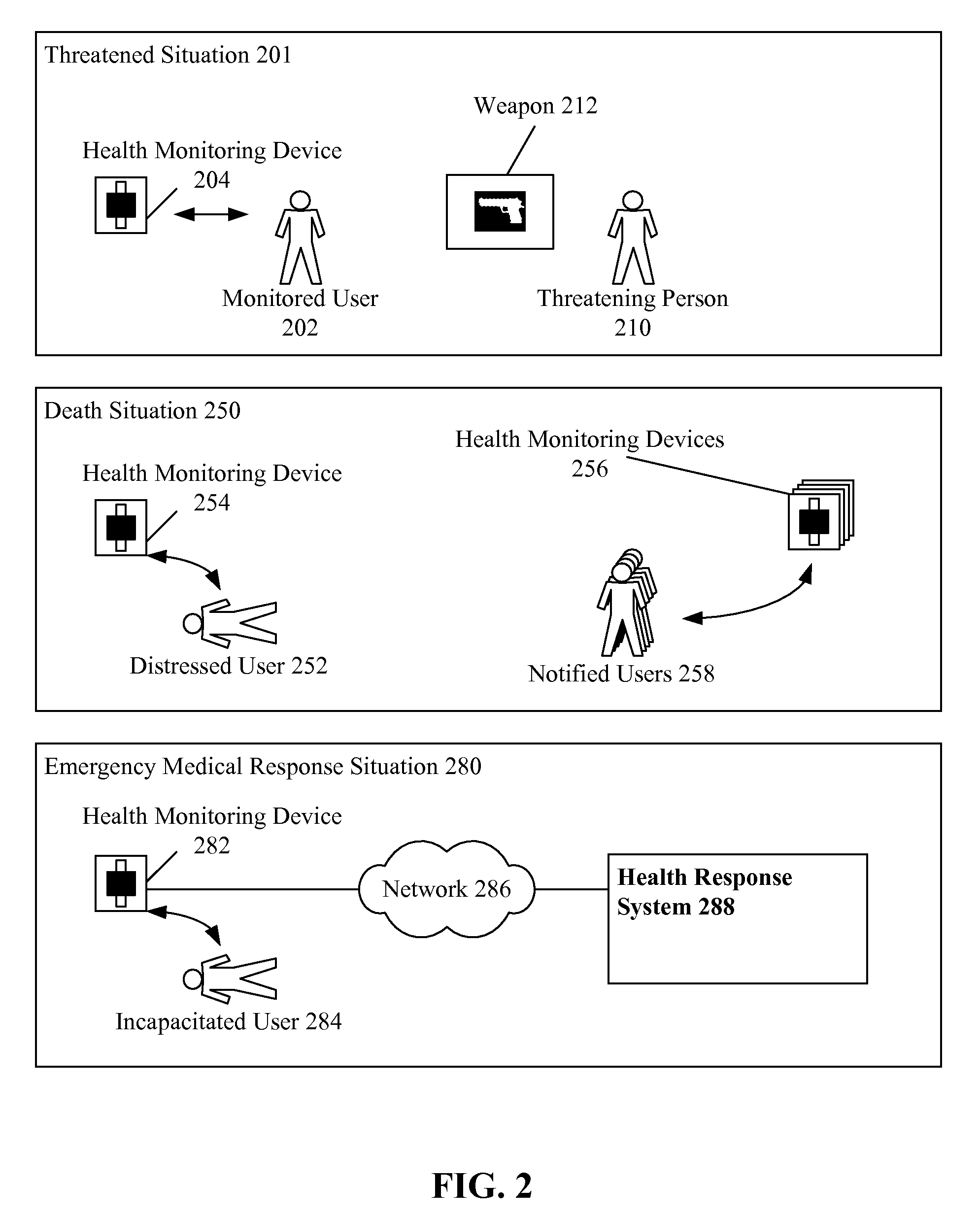
Remotely taking real-time programmatic actions responsive to health metrics received from worn health monitoring devices
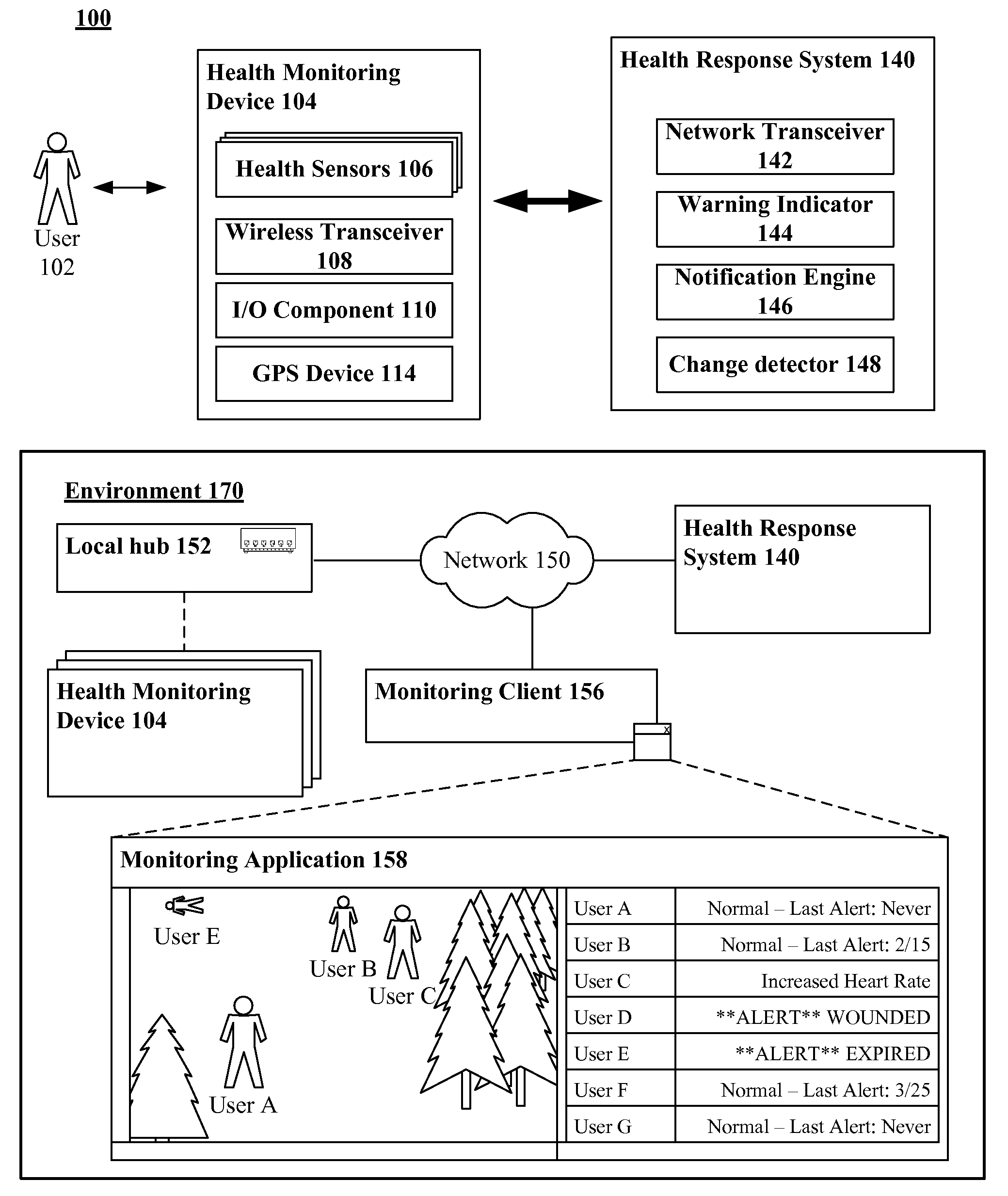
InactiveUS20100023348A1Reduce the number of timesData processing applicationsDiagnostic recording/measuringProximateEngineering
Health metrics can be received from at least one person wearing a health monitoring device in an unencumbered fashion that permits free motion. The health monitoring device can wirelessly convey the heath metrics to a remotely located computing device. The received health metrics can be compared against at least one configurable, yet previously established threshold. A change in a situation proximate to the person can be inferred based upon comparison results. A programmatic event can be fired based upon the inferred change. At least one programmatic action can be automatically initiated responsive to the firing of the programmatic event, wherein the programmatic action initiates a response to the inferred change.
Owner:IBM CORP
Sheath for use with an endoscope
ActiveUS20060258908A1Reduce in quantityQuickly and consistentlyGastroscopesCannulasEndoscopeMedical device
A medical apparatus and method useful for positioning one or more members within the gastro-intestinal tract is disclosed. The sheath can be provided with texture on an inside surface to facilitate installation of the endoscope in the sheath, and to permit the endoscope to be gripped through the sheath.
Owner:ETHICON ENDO SURGERY INC
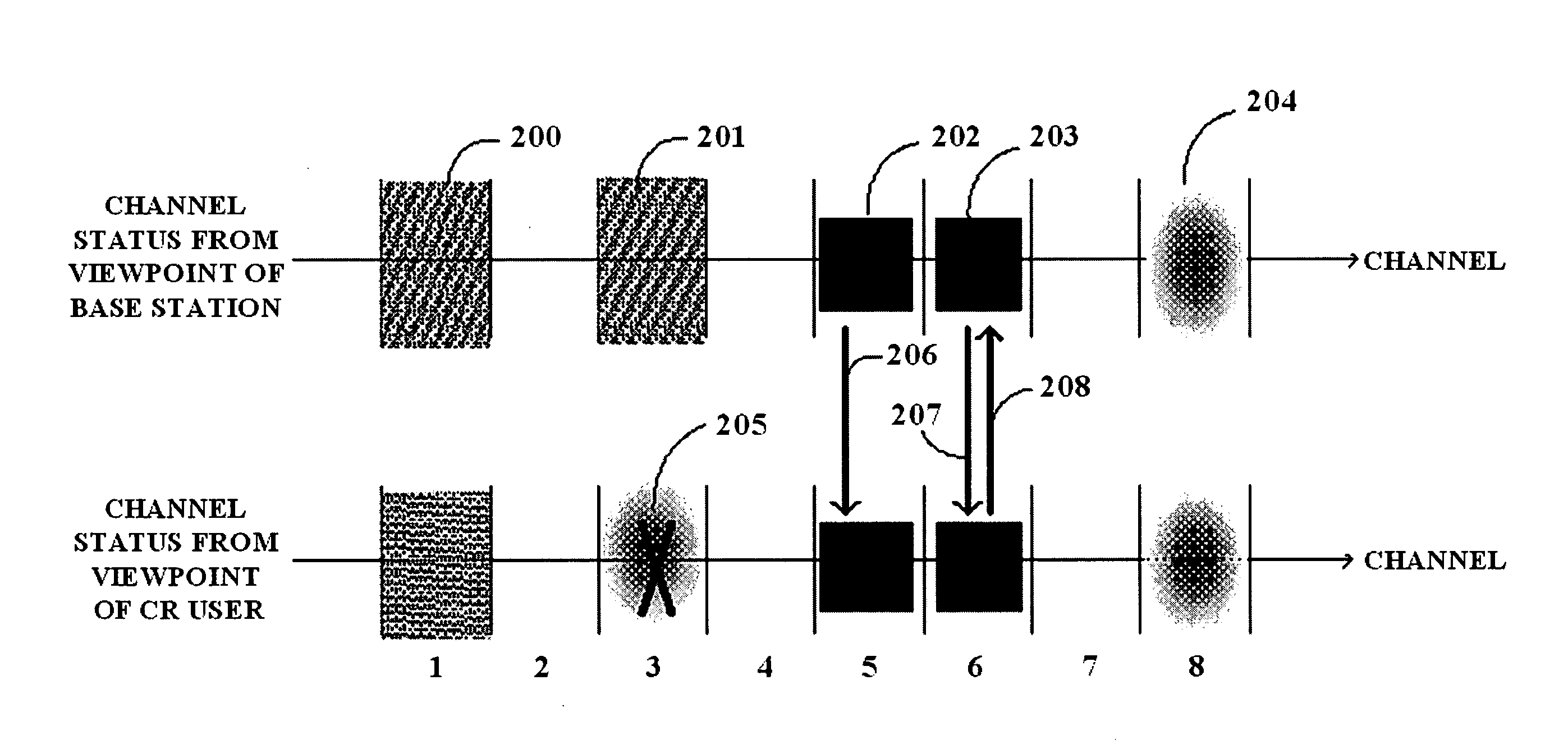
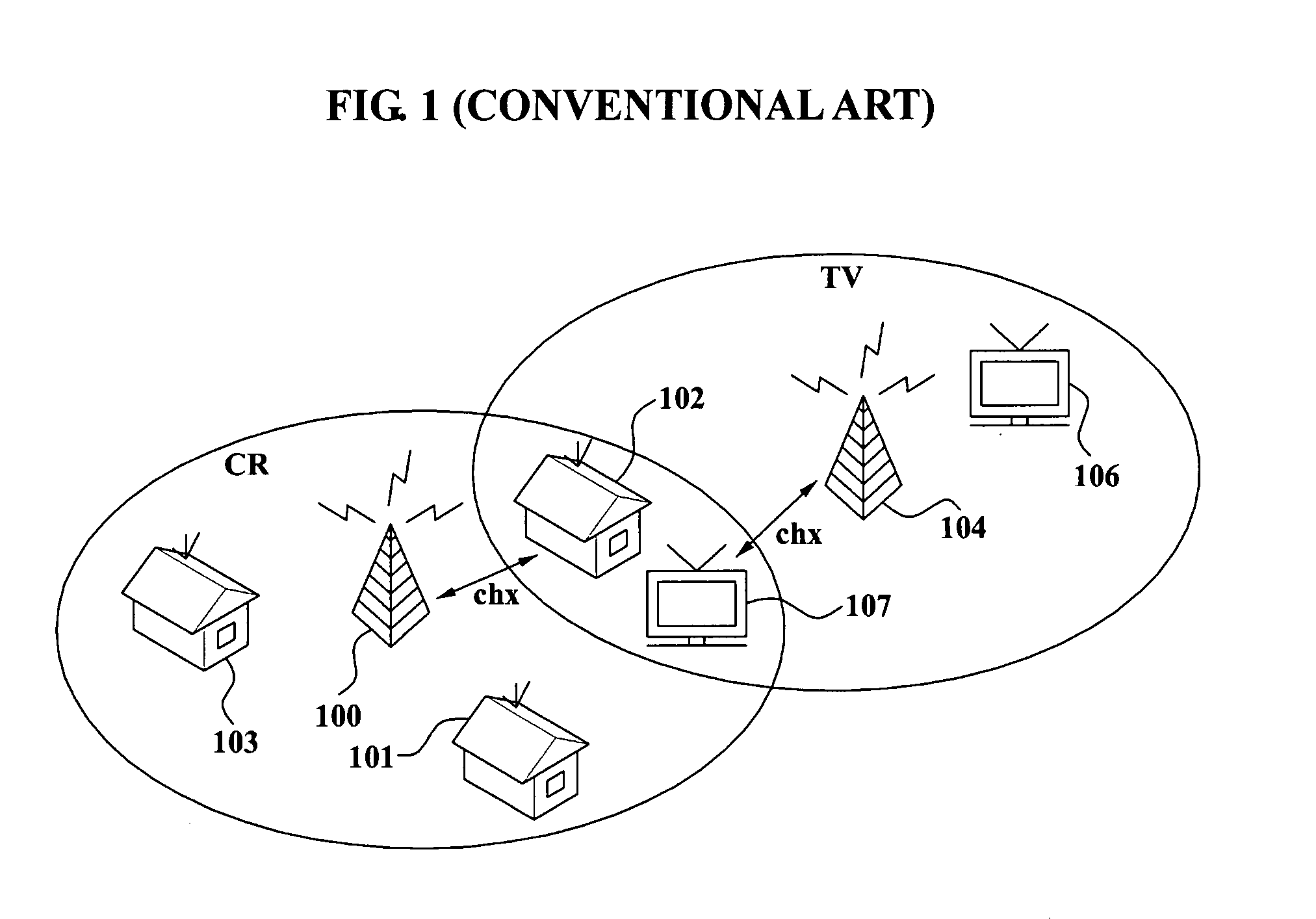
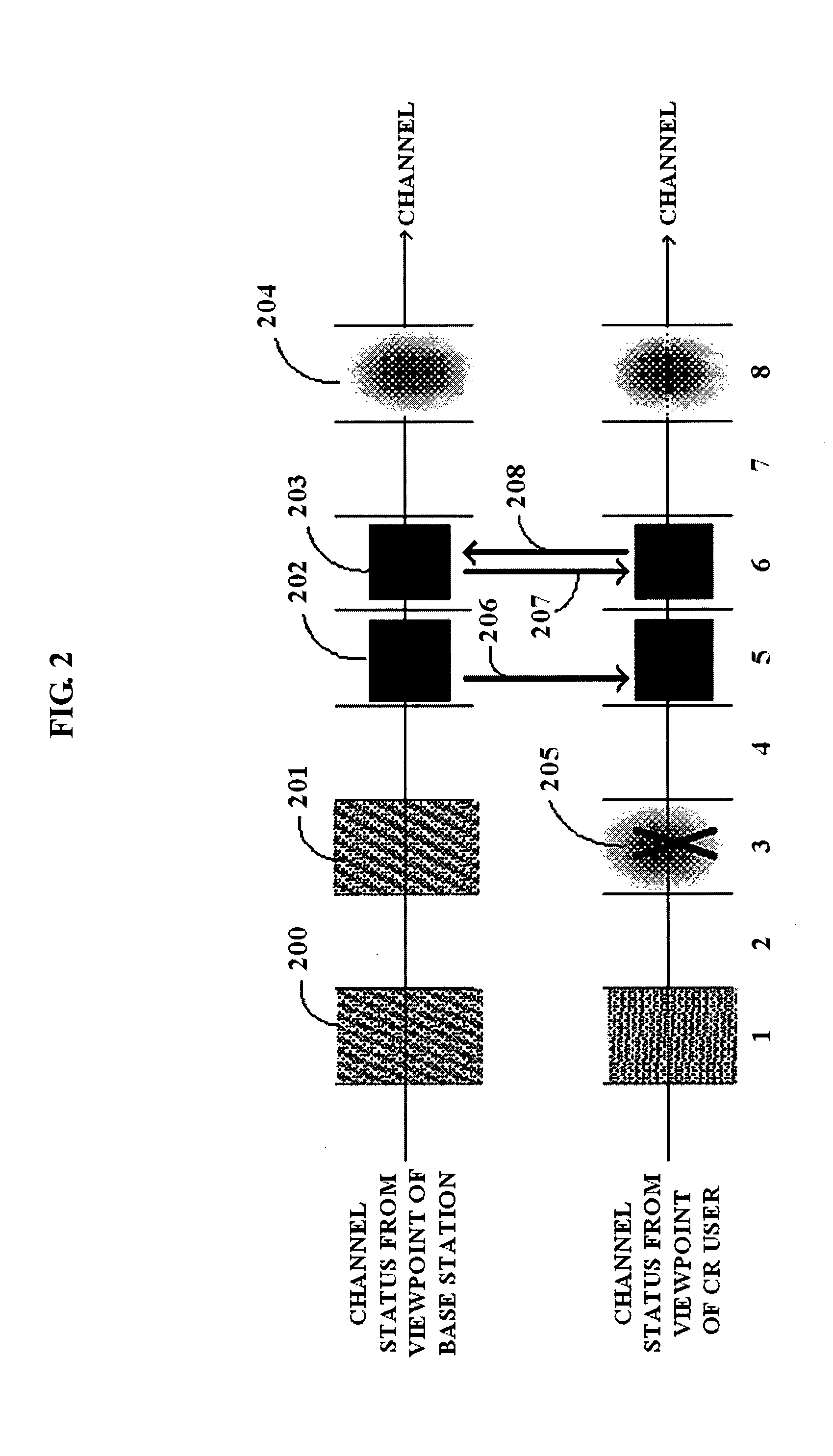
Signalling method of detecting hidden incumbent system in cognitive radio environment and channel fractioning method used to enable the method
InactiveUS20080014880A1Reduce impactQuicklySpectral gaps assessmentTransmission path divisionTelecommunicationsCognitive radio
A signaling method between a cognitive radio (CR) base station and a CR terminal in a CR environment, and a channel division method used for the signaling method, includes: detecting a channel usage of an incumbent system, which communicates with a CR base station; sensing an outband channel to communicate with the CR base station; receiving an EOS, which is broadcasted from the CR base station via the outband channel according to a predetermined period; and transmitting a sensing report signal with respect to the channel to the CR base station.
Owner:SAMSUNG ELECTRONICS CO LTD
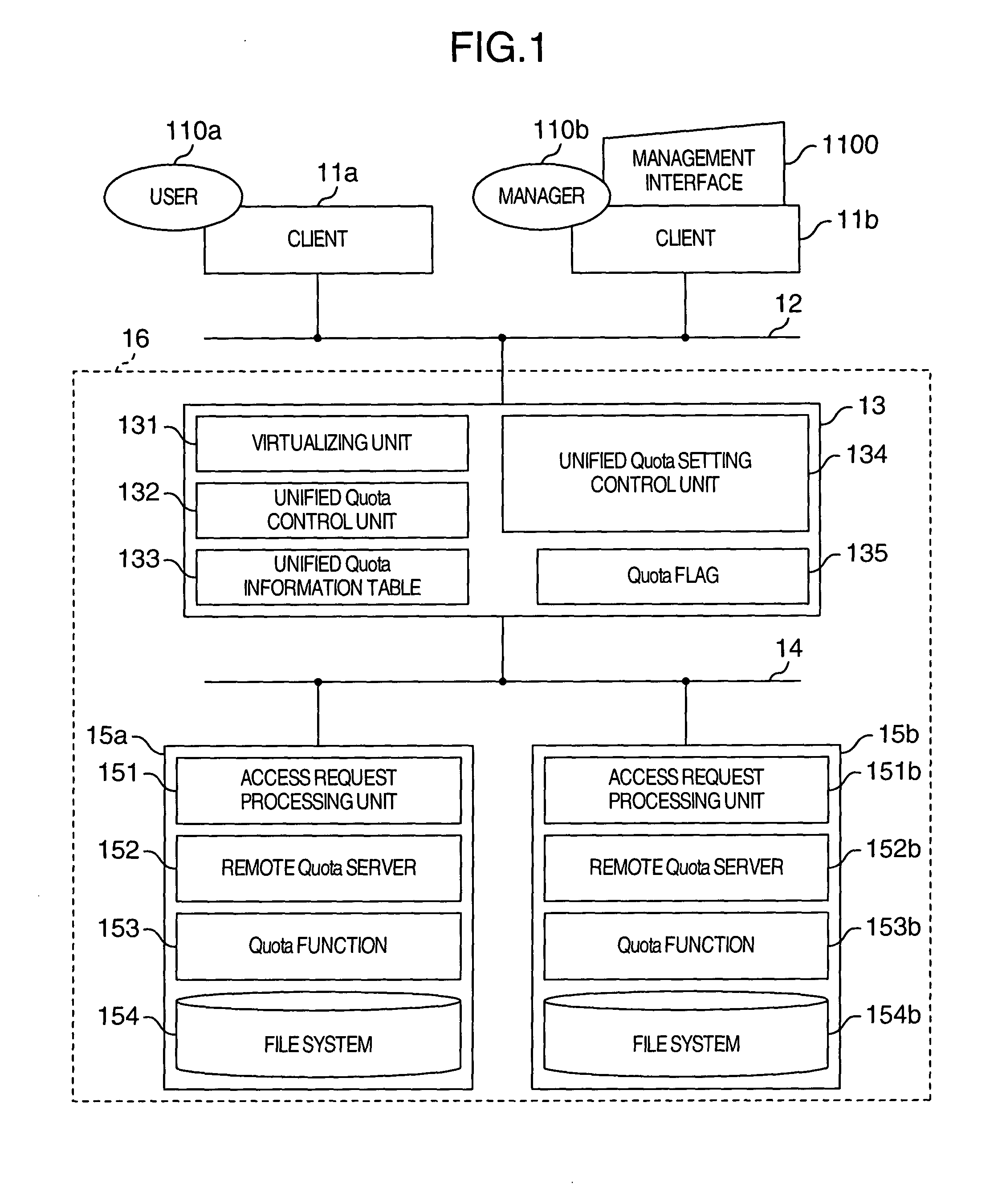
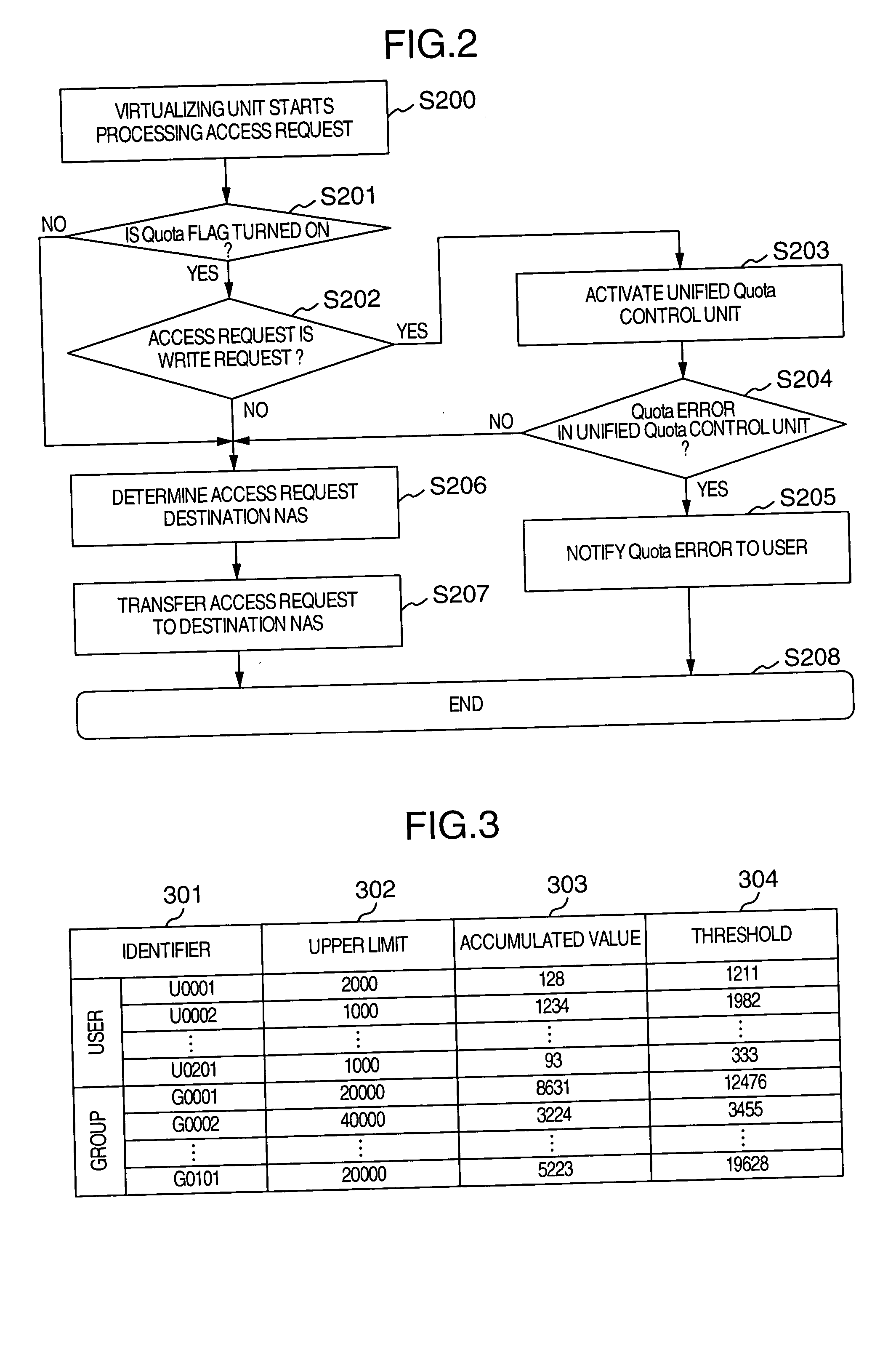
Method of controlling total disk usage amount in virtualized and unified network storage system
InactiveUS20050044198A1Improve efficiencyLower performance requirementsInput/output to record carriersMultiple digital computer combinationsVirtualizationFile system
A system having at least a user and a file system connected to the user through a network is disclosed, in which an estimated write size of the user into the file system is managed as an accumulated value, the timing of judging the limit of the disk usage amount is specified from the accumulated value and a predetermined threshold value, and the limit of the disk usage amount is judged at the specified timing.
Owner:HITACHI LTD
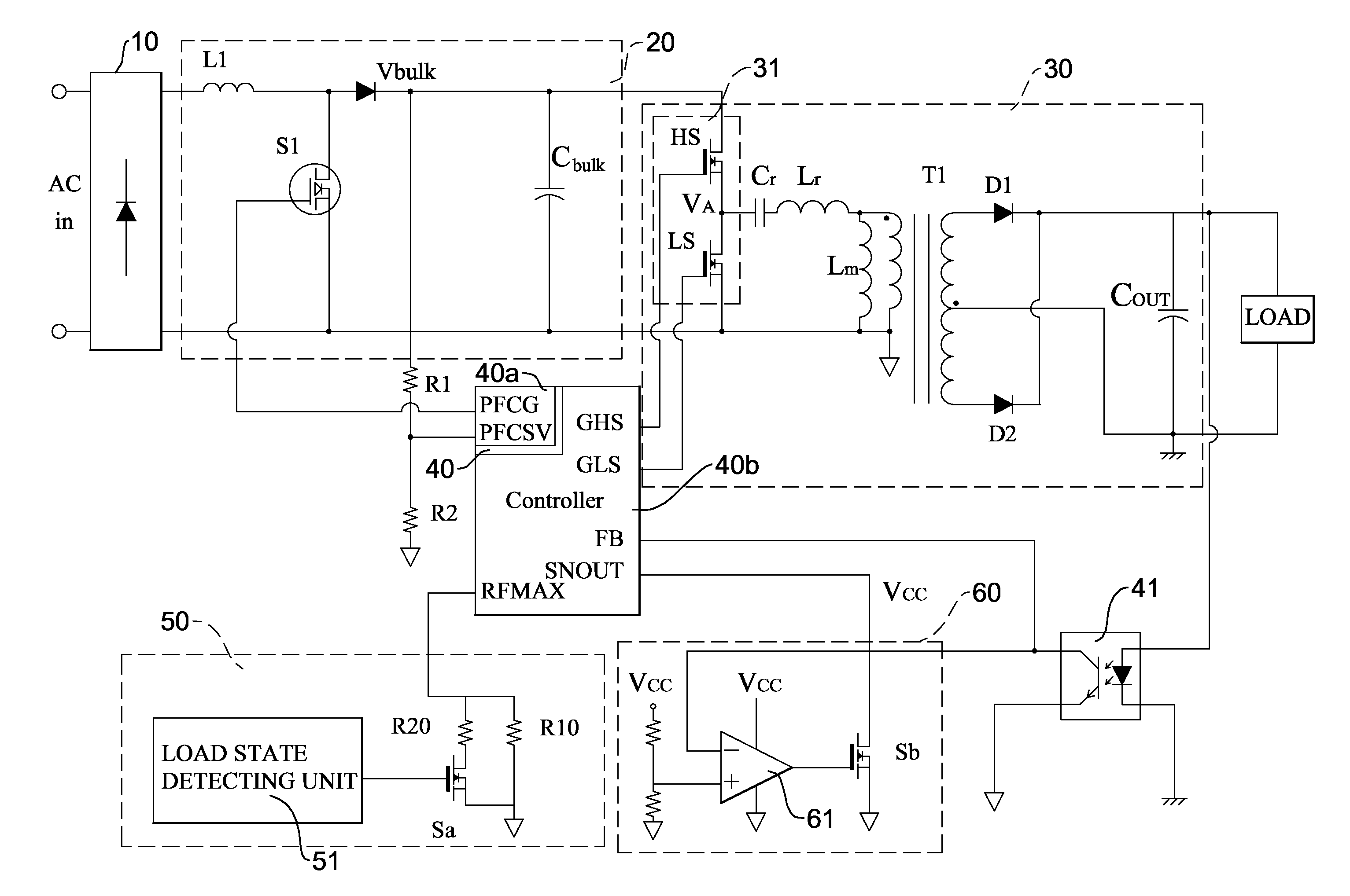
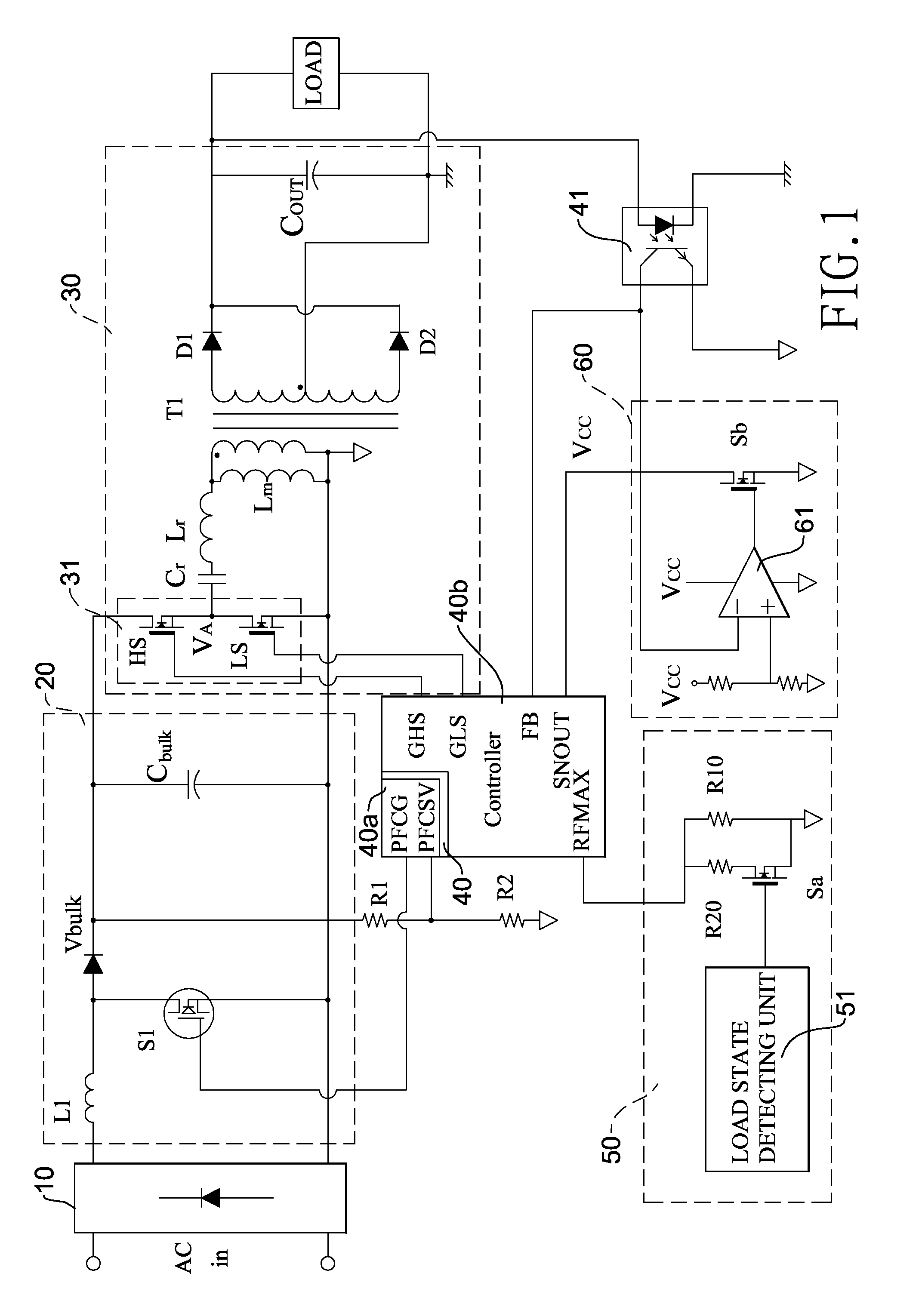
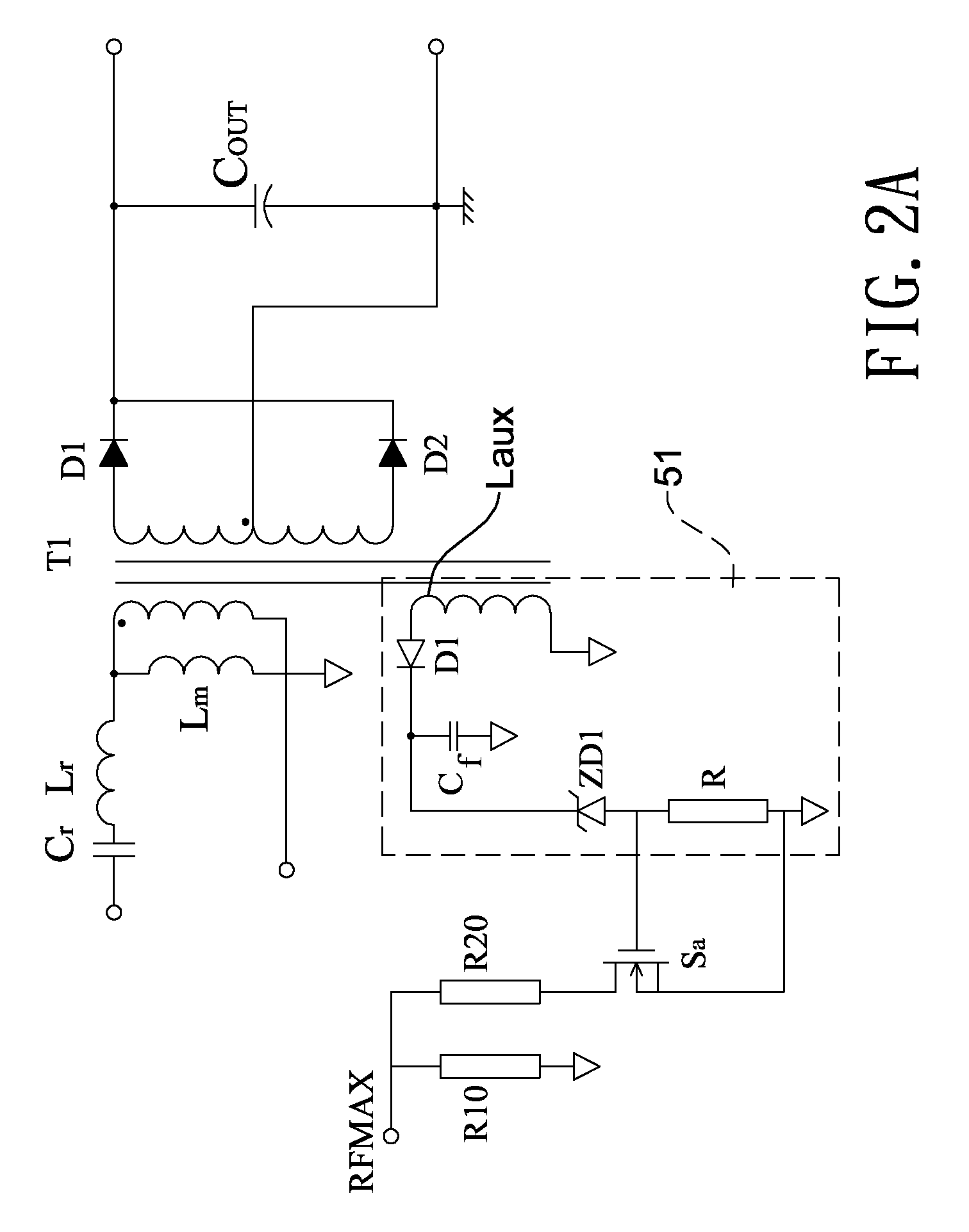
Burst mode resonant power converter with high conversion efficiency
InactiveUS20110085354A1Improve conversion efficiencyLowering maximum switch frequencyEfficient power electronics conversionDc-dc conversionTransformerResonant power converters
A burst mode resonant power converter with high conversion efficiency has a rectifier, a power factor correction circuit, a resonant circuit, a controller, and a burst mode triggering unit. The maximum frequency switching end of the controller is connected to a maximum frequency variable circuit. When the load is medium or heavy, the maximum frequency variable circuit increases the maximum switch frequency of the controller. When the load is in the no-load or the light conditions, it reduces the maximum switch frequency thereof. Therefore, the controller reduces the number of times that the resonant circuit switches the bridge switch circuit. The conduction cycle of the 50% pulse signal output to the bridge switch circuit becomes longer. Larger energy can be transmitted at a time to the secondary coil of the transformer. This increases the overall efficiency.
Owner:ACBEL POLYTECH INC
Information-processing device and information-processing system
InactiveUS7502053B2Reduce in quantityReduce the number of timesTelevision system detailsTelevision system scanning detailsInformation processingInformation device
For an information terminal to be operated by users for collecting predetermined pieces of information from remote information devices by free-space optical communication, the present invention provides a technique for suppressing the power consumption of the information terminal by minimizing the amount of calculation performed to collect the aforementioned information. According to the present invention, each information device emits ID light on which a low-frequency pilot signal is superimposed. The information terminal captures a series of frames of images including the ID light and locates the ID light within the images by the following steps: (1) creating multiple levels of binned images having different resolutions for each frame of the image; (2) calculating an evaluation index for each pixel within a target range of the binned images at each level, from the lowest to the highest resolution, where the target range is narrowed every time the process switches over to a lower level. In (2), the evaluation index is calculated by an evaluation function including fast Fourier transformation performed throughout the series of frames of images. The evaluation index thus calculated is compared with a threshold to determine whether the pixel concerned is receiving ID light. The present technique significantly reduces the number of pixel to be analyzed and evaluated, thereby decreasing the total number of arithmetic operations to be performed using the evaluation function. Thus, the power consumption is suppressed.
Owner:JAPAN SCI & TECH CORP +2
Track for medical devices
ActiveUS20060258907A1Reduce in quantityQuickly and consistentlyGastroscopesCannulasMedical deviceFeeding tube
A medical apparatus and method useful for positioning one or more members within the gastro-intestinal tract is disclosed. The medical apparatus can include a track supported on a sheath sized to receive an endoscope, and a carrier slidable with respect to the track. A feeding tube accessory adapted to slidably engage the carrier is disclosed.
Owner:ETHICON ENDO SURGERY INC
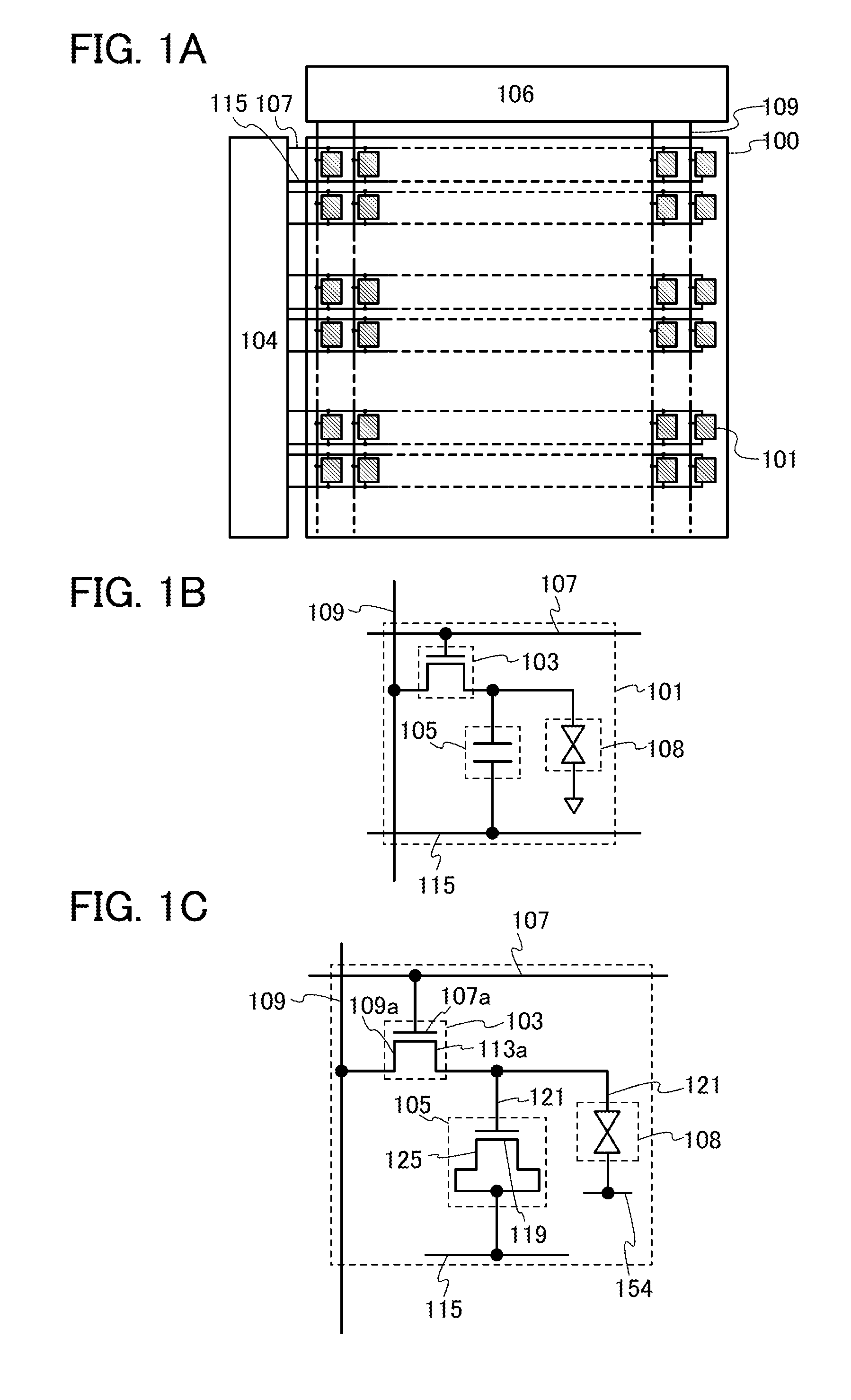
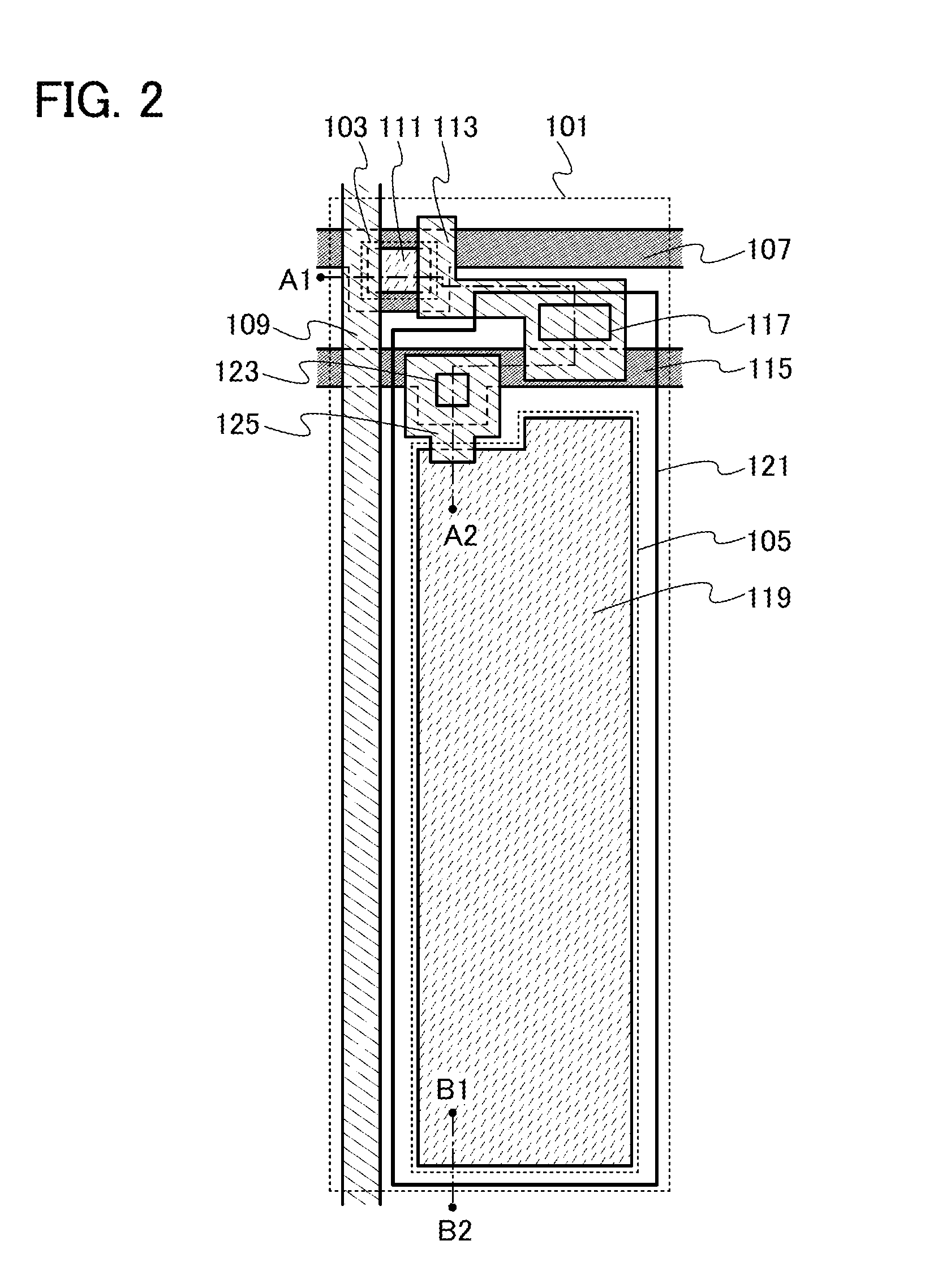
Semiconductor device
ActiveUS20140034954A1Increase the aperture ratioImprove charging effectSolid-state devicesNon-linear opticsPower semiconductor deviceIndium
To provide a semiconductor device including a capacitor whose charge capacity is increased without reducing the aperture ratio. The semiconductor device includes a transistor including a light-transmitting semiconductor film, a capacitor where a dielectric film is provided between a pair of electrodes, an insulating film provided over the light-transmitting semiconductor film, and a light-transmitting conductive film provided over the insulating film. In the capacitor, a metal oxide film containing at least indium (In) or zinc (Zn) and formed on the same surface as the light-transmitting semiconductor film in the transistor serves as one electrode, the light-transmitting conductive film serves as the other electrode, and the insulating film provided over the light-transmitting semiconductor film serves as the dielectric film.
Owner:SEMICON ENERGY LAB CO LTD
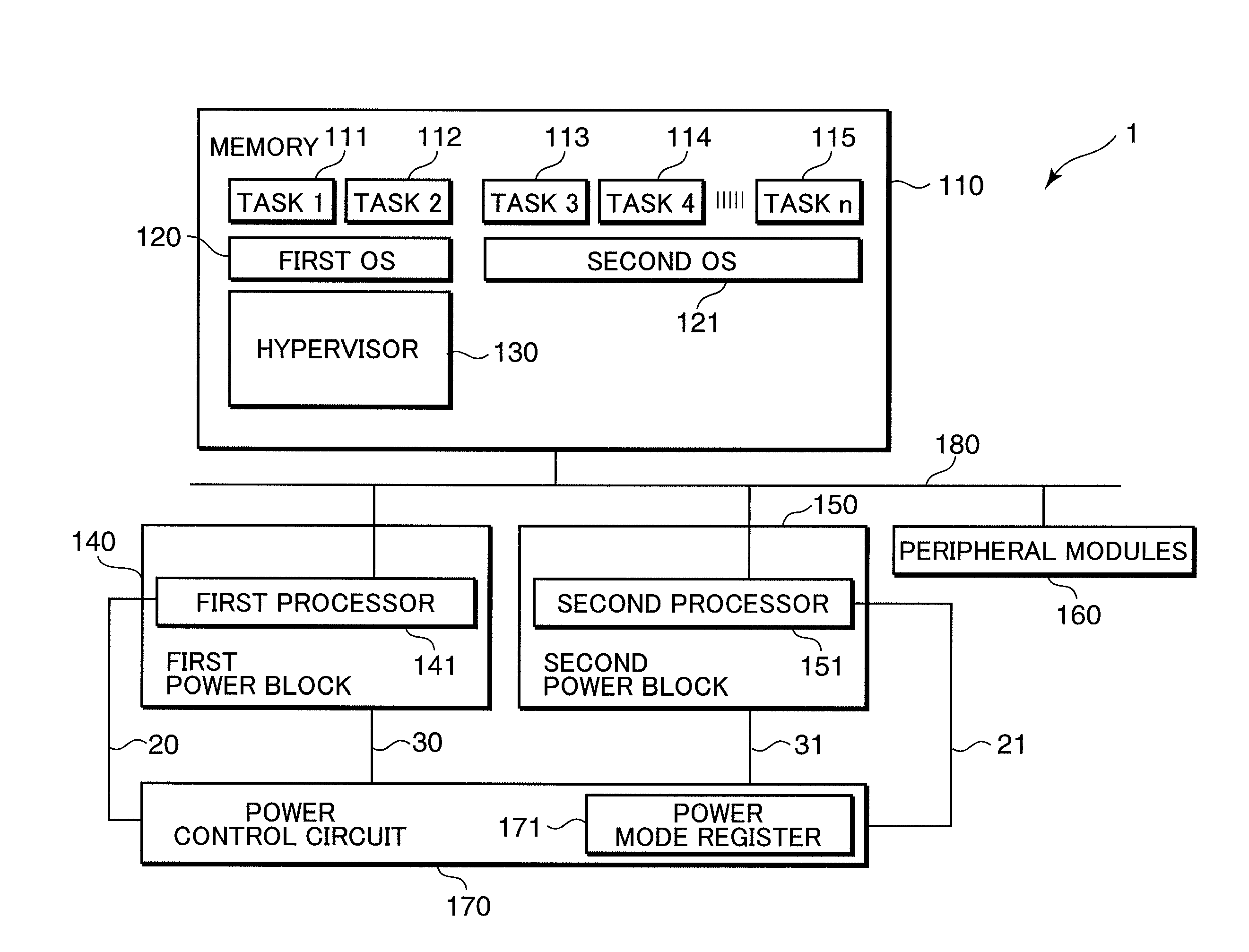
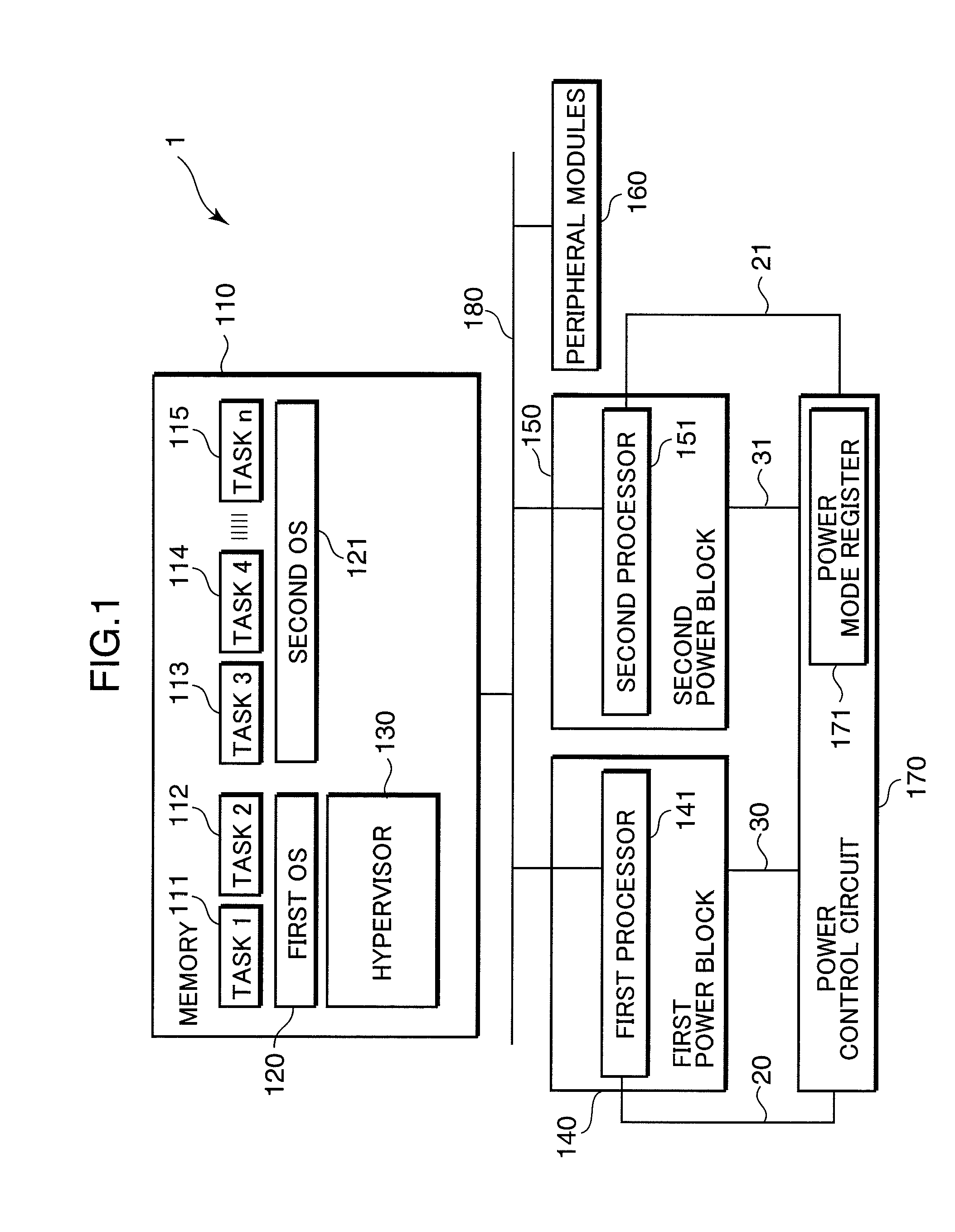
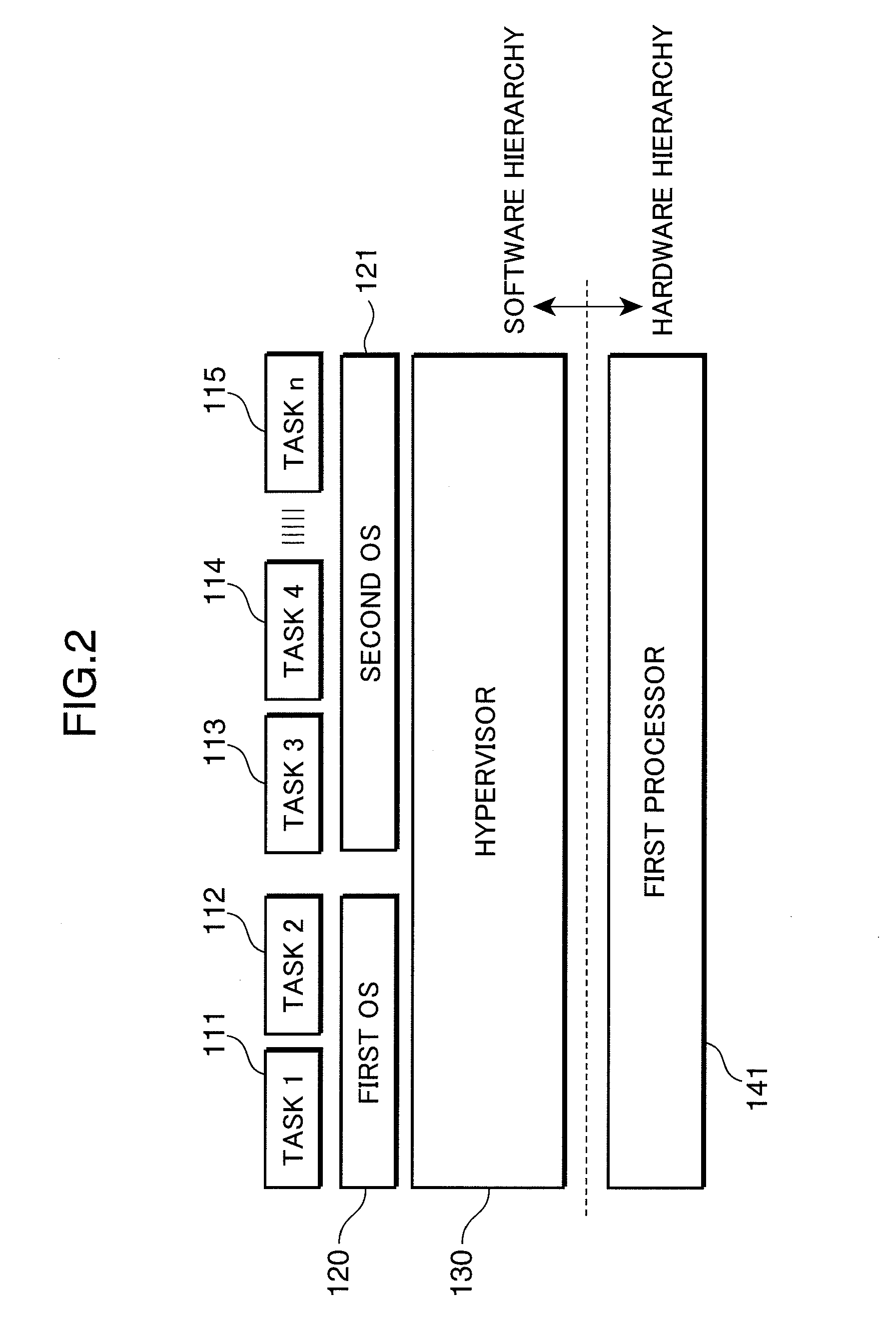
Multiprocessor control apparatus, multiprocessor control method, and multiprocessor control circuit
ActiveUS20100185833A1Reduce power consumptionReduce the number of timesMemory architecture accessing/allocationSusbset functionality useMulti processorParallel computing
An object of the invention is to reduce the electric power consumption resulting from temporarily activating a processor requiring a large electric power consumption, out of a plurality of processors. A multiprocessor system (1) includes: a first processor (141) which executes a first instruction code; a second processor (151) which executes a second instruction code, a hypervisor (130) which converts the second instruction code into an instruction code executable by the first processor (141); and a power control circuit (170) which controls the operation of at least one of the first processor (141) and the second processor (151). When the operation of the second processor (151) is suppressed by the power control circuit (170), the hypervisor (130) converts the second instruction code into the instruction code executable by the first processor (141), and the first processor (141) executes the converted instruction code.
Owner:GK BRIDGE 1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com